Nonrigid Image Registration Using Free-Form Deformations with a Local Rigidity Constraint
SDIO spec

f in eo nIn fio nI n fTechnical Committee SD Card Associationf in eo nIn fi ne o n I nf in eo nIRevision HistoryDate Version Changes compared to previous issueApril 3, 2006 1.10 Simplified Version Initial ReleaseFebruary 8, 20072.00(1) Added method to change bus speed (Normal Speed up to 25MHzand High Speed up to 50 MHz)(2) Operational Voltage Requirement is extended to 2.7-3.6V(3) Combine sections 12 (Physical Properties) and 13 (MechanicalExtensions) and add miniSDIO to the new section 13 (Physical Properties)(4) Add Embedded SDIO ATA Standard Function Interface Code (5) Reference of Physical Ver2.00 supports SDHC combo card. (6) Some typos in Ver1.10 are fixed.f in eo nIn fi ne o n I nf in eo nI Release of SD Simplified SpecificationThe following conditions apply to the release of the SD simplified specification ("Simplified Specification") by the SD Card Association. The Simplified Specification is a subset of the complete SD Specification which is owned by the SD Card Association.Publisher:SD Association2400 Camino Ramon, Suite 375 San Ramon, CA 94583 USA Telephone: +1 (925) 275-6615 Fax: +1 (925) 886-4870 E-mail: office@Copyright Holder: The SD Card AssociationNotes:This Simplified Specification is provided on a non-confidential basis subject to the disclaimers below. Any implementation of the Simplified Specification may require a license from the SD Card Association or other third parties.Disclaimers:The information contained in the Simplified Specification is presented only as a standard specification for SD Cards and SD Host/Ancillary products and is provided "AS-IS" without any representations or warranties of any kind. No responsibility is assumed by the SD Card Association for any damages, any infringements of patents or other right of the SD Card Association or any third parties, which may result from its use. No license is granted by implication, estoppel or otherwise under any patent or other rights of the SD Card Association or any third party. Nothing herein shall be construed as an obligation by the SD Card Association to disclose or distribute any technical information, know-how or other confidential information to any third party.f in eo nIn fi ne o n I nf in eo nConventions Used in This DocumentNaming ConventionsSome terms are capitalized to distinguish their definition from their common English meaning. Words not capitalized have their common English meaning.Numbers and Number BasesHexadecimal numbers are written with a lower case “h” suffix, e.g., FFFFh and 80h. Binary numbers are written with a lower case “b” suffix (e.g., 10b).Binary numbers larger than four digits are written with a space dividing each group of four digits, as in 1000 0101 0010b.All other numbers are decimal.Key WordsMay: Indicates flexibility of choice with no implied recommendation or requirement.Shall: Indicates a mandatory requirement. Designers shall implement such mandatory requirements to ensure interchangeability and to claim conformance with the specification.Should: Indicates a strong recommendation but not a mandatory requirement. Designers should give strong consideration to such recommendations, but there is still a choice in implementation.Application NotesSome sections of this document provide guidance to the host implementers as follows: Application Note:This is an example of an application note.f in eo nIn fi ne o n I nf in eo nTable of Contents1. General Description.................................................................................................................................1 1.1 SDIO Features....................................................................................................................................1 1.2 Primary Reference Document.............................................................................................................1 1.3 Standard SDIO Functions....................................................................................................................1 2. SDIO Signaling Definition........................................................................................................................2 2.1 SDIO Card Types................................................................................................................................2 2.2 SDIO Card modes...............................................................................................................................2 2.2.1 SPI (Card mandatory support).....................................................................................................2 2.2.2 1-bit SD Data Transfer Mode (Card Mandatory Support).............................................................2 2.2.3 4-bit SD Data Transfer Mode (Mandatory for High-Speed Cards, Optional for Low-Speed).........2 2.3 SDIO Host Modes...............................................................................................................................2 2.4 Signal Pins..........................................................................................................................................3 3. SDIO Card Initialization............................................................................................................................4 3.1 Differences in I/O card Initialization.....................................................................................................4 3.2 The IO_SEND_OP_COND Command (CMD5).................................................................................10 3.3 The IO_SEND_OP_COND Response (R4)........................................................................................11 3.4 Special Initialization considerations for Combo Cards.......................................................................12 3.4.1 Re-initialize both I/O and Memory..............................................................................................12 3.4.2 Using a Combo Card as SDIO only or SD Memory only after Combo Initialization....................12 3.4.3 Acceptable Commands after Initialization..................................................................................12 3.4.4 Recommendations for RCA after Reset.....................................................................................12 3.4.5 Enabling CRC in SPI Combo Card.............................................................................................14 4. Differences with SD Memory Specification..........................................................................................15 4.1 SDIO Command List.........................................................................................................................15 4.2 Unsupported SD Memory Commands...............................................................................................15 4.3 Modified R6 Response......................................................................................................................16 4.4 Reset for SDIO..................................................................................................................................16 4.5 Bus Width..........................................................................................................................................16 4.6 Card Detect Resistor.........................................................................................................................17 4.7 Timings..............................................................................................................................................17 4.8 Data Transfer Block Sizes.................................................................................................................18 4.9 Data Transfer Abort...........................................................................................................................18 4.9.1 Read Abort.................................................................................................................................18 4.9.2 Write Abort.................................................................................................................................18 4.10 Changes to SD Memory Fixed Registers..........................................................................................18 4.10.1 OCR Register.............................................................................................................................19 4.10.2 CID Register...............................................................................................................................19 4.10.3 CSD Register.............................................................................................................................19 4.10.4 RCA Register.............................................................................................................................19 4.10.5 DSR Register.............................................................................................................................19 4.10.6 SCR Register.............................................................................................................................19 4.10.7 SD Status...................................................................................................................................19 4.10.8 Card Status Register..................................................................................................................19 5. New I/O Read/Write Commands............................................................................................................21 5.1 IO_RW_DIRECT Command (CMD52)..............................................................................................21 5.2 IO_RW_DIRECT Response (R5)......................................................................................................22 5.2.1 CMD52 Response (SD modes)..................................................................................................22 5.2.2 R5, IO_RW_DIRECT Response (SPI mode).............................................................................23 5.3 IO_RW_EXTENDED Command (CMD53). (24)f in eo nIn fi ne o n I nf in eo nI 5.3.2 Special Timing for CMD53 Multi-Block Read..............................................................................25 6. SDIO Card Internal Operation................................................................................................................26 6.1 Overview...........................................................................................................................................26 6.2 Register Access Time........................................................................................................................26 6.3 Interrupts...........................................................................................................................................26 6.4 Suspend/Resume..............................................................................................................................27 6.5 Read Wait..........................................................................................................................................27 6.6 CMD52 During Data Transfer............................................................................................................27 6.7 SDIO Fixed Internal Map...................................................................................................................27 6.8 Common I/O Area (CIA)....................................................................................................................28 6.9 Card Common Control Registers (CCCR).........................................................................................28 6.10 Function Basic Registers (FBR)........................................................................................................35 6.11 Card Information Structure (CIS).......................................................................................................37 6.12 Multiple Function SDIO Cards...........................................................................................................37 6.13 Setting Block Size with CMD53.........................................................................................................37 6.14 Bus State Diagram............................................................................................................................38 7. Embedded I/O Code Storage Area (CSA).............................................................................................39 7.1 CSA Access.......................................................................................................................................39 7.2 CSA Data Format..............................................................................................................................39 8. SDIO Interrupts.......................................................................................................................................40 8.1 Interrupt Timing.................................................................................................................................40 8.1.1 SPI and SD 1-bit Mode Interrupts ..............................................................................................40 8.1.2 SD 4-bit Mode............................................................................................................................40 8.1.3 Interrupt Period Definition ..........................................................................................................40 8.1.4 Interrupt Period at the Data Block Gap in 4-bit SD Mode (Optional)..........................................40 8.1.5 Inhibited Interrupts (Removed Section)......................................................................................40 8.1.6 End of Interrupt Cycles...............................................................................................................40 8.1.7 Terminated Data Transfer Interrupt Cycle ..................................................................................41 8.1.8 Interrupt Clear Timing.................................................................................................................41 9. SDIO Suspend/Resume Operation........................................................................................................42 10. SDIO Read Wait Operation.....................................................................................................................43 11. Power Control.........................................................................................................................................44 11.1 Power Control Overview....................................................................................................................44 11.2 Power Control support for SDIO Cards.............................................................................................44 11.2.1 Master Power Control ................................................................................................................44 11.2.2 Power Selection.........................................................................................................................45 11.2.3 High-Power Tuples.....................................................................................................................45 11.3 Power Control Support for the SDIO Host.........................................................................................45 11.3.1 Version 1.10 Host.......................................................................................................................45 11.3.2 Power Control Operation............................................................................................................46 12. High-Speed Mode...................................................................................................................................47 12.1 SDIO High-Speed Mode....................................................................................................................47 12.2 Switching Bus Speed Mode in a Combo Card...................................................................................47 13. SDIO Physical Properties......................................................................................................................48 13.1 SDIO Form Factors...........................................................................................................................48 13.2 Full-Size SDIO ..................................................................................................................................48 13.3 miniSDIO...........................................................................................................................................48 14. SDIO Power.............................................................................................................................................48 14.1 SDIO Card Initialization Voltages......................................................................................................48 14.2 SDIO Power Consumption................................................................................................................48 15. Inrush Current Limiting..........................................................................................................................50 16. CIS Formats.. (51)f in eo nIn fi ne o n I nf in eo nI 16.2 Basic Tuple Format and Tuple Chain Structure.................................................................................51 16.3 Byte Order Within Tuples ..................................................................................................................51 16.4 Tuple Version ....................................................................................................................................52 16.5 SDIO Card Metaformat......................................................................................................................52 16.6 CISTPL_MANFID: Manufacturer Identification String Tuple..............................................................53 16.7 SDIO Specific Extensions..................................................................................................................53 16.7.1 CISTPL_FUNCID: Function Identification Tuple.........................................................................53 16.7.2 CISTPL_FUNCE: Function Extension Tuple..............................................................................54 16.7.3 CISTPL_FUNCE Tuple for Function 0 (common).......................................................................54 16.7.4 CISTPL_FUNCE Tuple for Function 1-7....................................................................................55 16.7.5 CISTPL_SDIO_STD: Function is a Standard SDIO Function.....................................................58 16.7.6 CISTPL_SDIO_EXT: Tuple Reserved for SDIO Cards...............................................................58 Appendix A.....................................................................................................................................................59 A.1 SD and SPI Command List....................................................................................................................59 Appendix B.....................................................................................................................................................61 B.1 Normative References...........................................................................................................................61 Appendix C.....................................................................................................................................................62 C.1 Abbreviations and Terms...................................................................................................................62 Appendix D.. (64)f in eo nIn fi ne o n I nf in eo nI Table of TablesTable 3-1 OCR Values for CMD5.....................................................................................................................10 Table 4-1 Unsupported SD Memory Commands.............................................................................................16 Table 4-2 R6 response to CMD3.....................................................................................................................16 Table 4-3 SDIO R6 Status Bits.........................................................................................................................16 Table 4-4 Combo Card 4-bit Control................................................................................................................17 Table 4-5 Card Detect Resistor States.............................................................................................................17 Table 4-6 is blanked.........................................................................................................................................17 Table 4-7 SDIO Status Register Structure .......................................................................................................20 Table 5-1 Flag data for IO_RW_DIRECT SD Response..................................................................................23 Table 5-2 IO_RW_ EXTENDED command Op Code Definition.......................................................................24 Table 5-3 Byte Count Values ...........................................................................................................................25 Table 6-1 Card Common Control Registers (CCCR).......................................................................................29 Table 6-2 CCCR bit Definitions........................................................................................................................34 Table 6-3 Function Basic Information Registers (FBR)....................................................................................35 Table 6-4 FBR bit and field definitions.............................................................................................................36 Table 6-5 Card Information Structure (CIS) and reserved area of CIA.............................................................37 Table 11-1 Reference Tuples by Master Power Control and Power Select......................................................45 Table 16-1 Basic Tuple Format........................................................................................................................51 Table 16-2 Tuples Supported by SDIO Cards..................................................................................................52 Table 16-3 CISTPL_MANFID: Manufacturer Identification Tuple.....................................................................53 Table 16-4 CISTPL_FUNCID Tuple.................................................................................................................53 Table 16-5 CISTPL_FUNCE Tuple General Structure.....................................................................................54 Table 16-6 TPLFID_FUNCTION Tuple for Function 0 (common)....................................................................54 Table 16-7 TPLFID_FUNCTION Field Descriptions for Function 0 (common).................................................54 Table 16-8 TPLFID_FUNCTION Tuple for Function 1-7..................................................................................55 Table 16-9 TPLFID_FUNCTION Field Descriptions for Functions 1-7.............................................................57 Table 16-10 TPLFE_FUNCTION_INFO Definition...........................................................................................57 Table 16-11 TPLFE_CSA_PROPERTY Definition...........................................................................................57 Table 16-12 CISTPL_SDIO_STD: Tuple Reserved for SDIO Cards................................................................58 Table 16-13 CISTPL_SDIO_EXT: Tuple Reserved for SDIO Cards.................................................................58 Table A-14 SD Mode Command List................................................................................................................59 Table A-15 SPI Mode Command List (60)f in eo nIn fi ne o n I nf in eo nI Table of FiguresFigure 2-1 Signal connection to two 4-bit SDIO cards.......................................................................................3 Figure 3-1 SDIO response to non-I/O aware initialization..................................................................................4 Figure 3-2 Card initialization flow in SD mode (SDIO aware host)....................................................................7 Figure 3-3 Card initialization flow in SPI mode (SDIO aware host)....................................................................9 Figure 3-4 IO_SEND_OP_COND Command (CMD5).....................................................................................10 Figure 3-5 Response R4 in SD mode...............................................................................................................11 Figure 3-6 Response R4 in SPI mode..............................................................................................................11 Figure 3-7 Modified R1 Response....................................................................................................................11 Figure 3-8 Re-Initialization Flow for I/O Controller...........................................................................................13 Figure 3-9 Re-Initialization Flow for Memory controller ...................................................................................13 Figure 5-1 IO_RW_DIRECT Command...........................................................................................................21 Figure 5-2 R5 IO_RW_DIRECT Response (SD modes)..................................................................................22 Figure 5-3 IO_RW_DIRECT Response in SPI Mode.......................................................................................23 Figure 5-4 IO_RW_EXTENDED Command.....................................................................................................24 Figure 6-1 SDIO Internal Map..........................................................................................................................28 Figure 6-2 State Diagram for Bus State Machine (38)f in eo nIn fi ne o n I nf in eo nI 1. General DescriptionThe SDIO (SD Input/Output) card is based on and compatible with the SD memory card. This compatibility includes mechanical, electrical, power, signaling and software. The intent of the SDIO card is to provide high-speed data I/O with low power consumption for mobile electronic devices. A primary goal is that an SDIO card inserted into a non-SDIO aware host shall cause no physical damage or disruption of that host or it’s software. In this case, the SDIO card should simply be ignored. Once inserted into an SDIO aware host, the detection of the card proceeds via the normal means described in this specification with some extensions. In this state, the SDIO card is idle and draws a small amount of power (15 mA averaged over 1 second). During the normal initialization and interrogation of the card by the host, the card identifies itself as an SDIO card. The host software then obtains the card information in a tuple (linked list) format and determines if that card’s I/O function(s) are acceptable to activate. This decision is based on such parameters as power requirements or the availability of appropriate software drivers. If the card is acceptable, it is allowed to power up fully and start the I/O function(s) built into it.1.1 SDIO Features• Targeted for portable and stationary applications• Minimal or no modification to SD Physical bus is required • Minimal change to memory driver software• Extended physical form factor available for specialized applications • Plug and play (PnP) support• Multi-function support including multiple I/O and combined I/O and memory • Up to 7 I/O functions plus one memory supported on one card. • Allows card to interrupt host• Operational Voltage range: 2.7-3.6V (Operational Voltage is used for Initialization) • Application Specifications for Standard SDIO Functions. • Multiple Form Factors:• Full-Size SDIO • miniSDIO1.2 Primary Reference DocumentThis specification is based on and refers extensively to the SDA document:SD Memory Card SpecificationsPart 1 PHYSICAL LAYER SPECIFICATION Version 2.00 May 9, 2006The reader is directed to this document for more information on the basic operation of SD cards. In addition, other documents are referenced in this specification. A complete list can be found in appendix B.1.This specification can apply to any released versions of Physical Layer Specification after Version 2.00.1.3 Standard SDIO FunctionsAssociated with the base SDIO specification, there are several Application Specifications for Standard SDIO Functions. These common functions such as cameras, Bluetooth cards and GPS receivers have a standard register interface, a common operation method and a standard CIS extension. Implementation of the standard interfaces are optional for any card vendor, but compliance with the standard allows the use of standard drivers and applications which will increase the appeal of these cards to the consumer. Full information on these standard interfaces can be found in the Application Specifications for Standard SDIO Functions maintained by the SDA.。
Computer-Vision计算机视觉英文ppt

Its mainstream research is divided into three stages:
Stage 1: Research on the visual basic method ,which take the model world as the main object;
Stage 2: Research on visual model ,which is based on the computational theory;
the other is to rebuild the three dimensional object according to the two-dimensional projection images .
History of computer vision
1950s: in this period , statistical pattern recognition is most applied in computer vision , it mainly focuse on the analysis and identification of two-dimensional image,such as: optical character recognition, the surface of the workpiece, the analysis and interpretation of the aerial image.
基于模板的人脸点云补洞方法

基于模板的人脸点云补洞方法孙晓斐;宋万忠【摘要】为得到完整的三维人脸点云数据,首先提出一种在点云生成过程中自动提取三维人脸特征点的方法,然后根据三维特征点对人脸点云模型进行剖分变形.还对非刚体最近点迭代算法进行改进,加入以对应点拓扑结构为依据的剔除错误点对应点机制和优化的迭代策略,实现更快更好的配准,继而完成点云的补洞.试验结果表明,该方法对人脸点云孔洞填补效果较好,特别是在人眼、鼻子等复杂部位,补洞真实,优势明显.【期刊名称】《现代计算机(专业版)》【年(卷),期】2017(000)005【总页数】5页(P59-63)【关键词】三维人脸;孔洞修补;点云;非刚体最近点迭代算法;三维人脸特征点【作者】孙晓斐;宋万忠【作者单位】四川大学计算机学院,成都610065;四川大学计算机学院,成都610065【正文语种】中文采用结构光三维面形测量技术获取的原始人脸点云数据,因受人脸面形起伏产生的遮挡、局部区域反射率差异较大(眉毛、眼睛、化妆后脸部反光)等影响,会导致人脸表面某些区域无法测量,造成测量的数据不完整形成孔洞。
孔洞不仅影响美观,而且不方便纹理等后续处理,实际应用前需要自动孔洞填补。
文献[1-2]对通用性的点云孔洞填补方法进行了介绍,文献[3-4]介绍了针对人体点云孔洞的填补方法。
泊松曲面重建[5]是一种隐函数表面重建方法,将其用于人脸点云孔洞填补时存在填补后的局部区域面形明显失真的问题,比如重建后的眼球是凹陷的。
采用曲面拟合的点云孔洞填补方法[6-8]也存在类似问题,其原因是:如需要填补的孔洞原有面形起伏较大,孔洞附近的面形不足以提供生成较为准确的孔洞填补所需信息。
在三维人脸识别和三维人脸建模应用,面形较大的局部区域常对应三维人脸上的特征区域,较为准确地获取(或恢复)其面形数据,直接影响到系统应用效果。
本文结合3D人脸点云模型和非刚体ICP配准算法[12],提出了一种基于三维人脸模板的人脸点云自动补洞方法,主要包括3个步骤:(1)根据人脸点云模型和实际测量点云上特征点间的对应关系,对人脸点云模板进行三维缩放;(2)采用非刚体ICP策略将人脸点云模型向人脸测量点云配准;(3)将原始测量点云中孔洞区域用变形后的人脸点云模型中的点云来替换实现补洞。
研究实例:非刚性配准

N N
Cost Matrix(NxN)
扫浴室
拖地
擦窗户
A B C
$1 $3 $3
$2 $3 $3
$3 $3 $2
Linear Assignment Solution
A 扫浴室 B 拖地 C 擦窗户
Shape Context Method
Step 4: Finding the matching that minimizes total cost
GMMREG: Gaussian Mixture Model Registration
•配准两个Gaussian Mixture Models
GMMREG: Gaussian Mixture Model Registration
GMMREG: Performance
GMMREG: Limitation
TPS-RPM(Robust Point Matching)Chui et al. 2003
•迭代法:包含Correspondence estimation(对应评估)和 Transformation Updating(几何变换更新)。 •Correspondence Estimation:运用了Fuzzy Correspondence(模糊 对应)。 •Transformation Updating:运用了Annealing(退火法)。
• 不断更新Source Point Set的位置和形状,使得Source的位置和形态越 来越接近Target,同时配准变得更容易 。
•增加了计算量
思考:上述Shape context method 和 Graph based methods是否可以转化为迭代法?
Iterative Closest Point (ICP):定义
自动化处理图片元数据的Python技巧

自动化处理图片元数据的Python技巧在当今数字化的时代,图片已经成为了我们生活和工作中不可或缺的一部分。
无论是个人的照片库,还是企业的大量图像资源,管理和处理图片元数据都变得至关重要。
Python 作为一种强大而灵活的编程语言,为我们提供了许多工具和技巧来实现图片元数据的自动化处理。
首先,让我们来了解一下什么是图片元数据。
简单来说,图片元数据就是关于图片的信息,例如拍摄时间、地点、相机型号、图片尺寸、作者等等。
这些信息对于图片的管理、分类、搜索和分析都非常有帮助。
```pythonfrom PIL import Imagedef get_image_info(image_path):try:image = Imageopen(image_path)width, height = imagesizeformat = imageformatmode = imagemodeprint(f"图片宽度: {width} 像素")print(f"图片高度: {height} 像素")print(f"图片格式: {format}")print(f"图片模式: {mode}")except Exception as e:print(f"处理图片时发生错误: {e}")image_path ="your_imagejpg"get_image_info(image_path)```上述代码中,我们定义了一个`get_image_info`函数,它接受图片的路径作为参数。
通过`Imageopen`打开图片,然后获取图片的宽度、高度、格式和模式等基本信息。
```pythonimport exifreaddef get_exif_data(image_path):try:with open(image_path, 'rb') as f:tags = exifreadprocess_file(f)for tag in tagskeys():if tag not in ('JPEGThumbnail','TIFFThumbnail','Filename','EXIF MakerNote'):print(f"{tag}:{tagstag}")except Exception as e:print(f"获取元数据时发生错误: {e}")image_path ="your_imagejpg"get_exif_data(image_path)```在这个示例中,我们以二进制模式打开图片文件,然后使用`exifreadprocess_file`获取图片的元数据。
斑马技术公司DS8108数字扫描仪产品参考指南说明书

DIRART (Deformable Image Registration and Adaptive Radiotherapy) Software Suite

1
Table of Content DIRART (Deformable Image Registration and Adaptive Radiotherapy) Software Suite.............. 1 (Version 1.0a) ................................................................................................................................. 1 User Instruction Manual ................................................................................................................. 1 Version 0.1...................................................................................................................................... 1 Deshan Yang, PhD...................................................................................................................... 1 Issam El Naqa, PhD .................................................................................................
基于Demon算法的乳房核磁共振图像配准

万方数据但是,在长达十多分钟的乳房DCEMRI获取过程中,由于病人的移动以及呼吸运动而产生不同时间点图像中各组织器官在减影时的误对齐,从而在减影图像中得到错误的高亮区,导致更长的读片时间以及病情的误诊断。
因此在不同时间点的MRI图像在减影之前首先应该进行空间上的配准。
123时赢分)5678图l注入造影剂之后信号的增强曲线实例当两幅具有同一模态(在此均为MRI-T1图像)的图像s和M进行配准时,对于图像上一个给定的点p,让s代表原图像s上该点的强度,而柳代表运动图像M上该点的强度。
最初的Demon算法来自于光流理论,提出通过对M中点P的强度按式(1)的参数仇迭代修正以匹配M中相应点的强度‘10,11]。
(m—s)亏s饥一——(1)}号5I2+(埘一i)2其中,i=(%,啮),称之为“静态”变化参数,专s是图像s中相应点的梯度,表示来自于图像的内部力,m—s为来自于s与M图像之间相互的作用力,称之为外部力。
为了提高配准速度,给出了另外一个基于活动图像梯度信息的类似于式(1)的等式‘12]:(s—m)专m‰~(2)I亏mI2+(s~m)2其中,诜被称之为“活动”变化参数,寺m是图像M中相应点的梯度。
这样结合式(1)及式(2),点p的总变化参数可用下式计算:;=矗+矗=(m--s)×Vs(——1i7mI亏sI2+(m一5)2I亏mI2+(s—m)2应用式(3)可以更快的速度和更少的迭代次数完成基图像与形变图像的匹配。
3结合Demon算法及强度校正的乳房核磁共振图像配准3.1配准模型尽管Demon配准算法的速度显著快于其他配准算法,但是该算法假设图像之间只有形变,没有或只有极小的强度变化,因此不适合被直接应用于随时间强度发生变化的乳房DCEMRI问题。
这样,可通过首先对待配准图像进行强度校正使之从强度上与基准图像相匹配,再应用Demon算法实现几何变形匹配。
图2为本文提出的配准模型示意图。
假设图2(a)为注入造影剂之前的乳房成像,n,b分别为不同的组织,·262·P为图像中一点。
基于血管内超声图像自动识别易损斑块

基于血管内超声图像自动识别易损斑块张麒;汪源源;马剑英;钱菊英;施俊;严壮志【摘要】为克服手工判别动脉粥样硬化易损斑块耗时耗力、主观性强、重复性差等缺点,研究了基于血管内超声自动识别易损斑块的方法.首先将Contourlet变换与Snake模型相结合进行斑块的图像分割,提取内腔轮廓与外弹力膜.接着实现经典形态特征的计算机自动提取,并提取纹理、弹性两类新特征以量化斑块属性,其中纹理特征包括一阶统计量和灰度共生矩阵特征,弹性特征的提取则基于非刚性图像配准.最后设计Fisher线性判别、支撑向量机、广义相关学习矢量量化3种分类器进行分类判决.对124例斑块(36例易损,88例非易损)的实验结果表明:20个形态特征、24个纹理特征和6个弹性特征在两类斑块间存在显著性差异(P<0.05);采用三类特征由支撑向量机进行分类时效果最好,在测试集上敏感性、特异性、准确率和约登指数分别达到91.7%、97.7%、96.7%和89.4%,表明利用血管内超声图像中斑块的三类特征能自动、准确地识别易损斑块.%In order to overcome drawbacks in manual identification of vulnerable atherosclerotic plaques, a methodfor automatic identification of vulnerable plaques is proposed based on computerized analysis of intravascular ultrasound images. First, the Contourlet transform is combined with the Snake model to segment images and detect lumen borders and external elastic membranes. Two categories of new features representing texture and elasticity of plaques are then automatically extracted to quantitate the features of plaques . The texture features consist of first - order statistics and features from the gray-level coocurrence matrix, and the elastic features are extracted from strain tensors estimated by nonrigid image registration. Finally, three typesof features are used to design classifiers including Fisher linear discrimination, support vector machines, and generalized relevance learning vector quantization. The experimental results on 124 plaques, consisting of 36 vulnerable and 88 nonvul-nerable ones, reveals that 20 morphological features, 24 texture features and 6 elastic features has significant difference (P<0. 05) between the two types of plaques. The Support Vector Machine(SVM) outperformes the other two classifiers with the sensitivity, specificity, correct rate, and Youden's index of 91. 7% , 97. 7% , 96. 7% , and 89. 4% , respectively. Therefore, the proposed method can automatically and accurately identify vulnerable plaques.【期刊名称】《光学精密工程》【年(卷),期】2011(019)010【总页数】13页(P2507-2519)【关键词】血管内超声;动脉粥样硬化易损斑块;特征提取;模式识别;图像分割【作者】张麒;汪源源;马剑英;钱菊英;施俊;严壮志【作者单位】上海大学通信与信息工程学院,上海200072;复旦大学电子工程系,上海200433;复旦大学附属中山医院心内科,上海200032;复旦大学附属中山医院心内科,上海200032;上海大学通信与信息工程学院,上海200072;上海大学通信与信息工程学院,上海200072【正文语种】中文【中图分类】TB559;TP391.41 引言全球每年有近2000万人经历急性心血管病事件,大多数人事先并无症状[1],导致急性心血管病事件的主要原因是动脉粥样硬化斑块破裂从而引发血栓。
自组织映射(SOM)R包说明书

Package‘som’October14,2022Version0.3-5.1Date2010-04-08Title Self-Organizing MapAuthor Jun Yan<***************.edu>Maintainer Jun Yan<***************.edu>Depends R(>=2.10)Description Self-Organizing Map(with application in gene clustering).License GPL(>=3)Repository CRANDate/Publication2016-07-0610:26:15NeedsCompilation yesR topics documented:filtering (1)normalize (2)plot.som (3)qerror (4)som (4)summary.som (7)yeast (7)Index9 filtering Filter data before feeding som algorithm for gene expression dataDescriptionFiltering data by certainfloor,ceiling,max/min ratio,and max-min difference.12normalizeUsagefiltering(x,lt=20,ut=16000,mmr=3,mmd=200)Argumentsx a data frame or matrix of input data.ltfloor value replaces those less than it with the valueut ceiling value replaced those greater than it with the valuemmr the max/min ratio,rows with max/min<mmr will be removedmmd the max-min difference,rows with(max-min)<mmd will be removed ValueAn dataframe or matrix after thefilteringAuthor(s)Jun Yan<***************.edu>See Alsonormalize.normalize normalize data before feeding som algorithmDescriptionNormalize the data so that each row has mean0and variance1.Usagenormalize(x,byrow=TRUE)Argumentsx a data frame or matrix of input data.byrow whether normalizing by row or by column,default is byrow.ValueAn dataframe or matrix after the normalizing.Author(s)Jun Yan<***************.edu>plot.som3See Alsofiltering.plot.som Visualizing a SOMDescriptionPlot the SOM in a2-dim map with means and sd bars.Usage##S3method for class somplot(x,sdbar=1,ylim=c(-3,3),color=TRUE,ntik=3,yadj=0.1,xlab="",ylab="",...)Argumentsx a som objectsdbar the length of sdbar in sd,no sdbar if sdbar=0ylim the range of y axies in each cell of the mapcolor whether or not use color plottingntik the number of tiks of the vertical axisyadj the proportion used to put the number of obsxlab x labelylab y label...other options to plotNoteThis function is not cleanly written.The original purpose was to mimic what GENECLUSTER does.The ylim is hardcoded so that only standardized data could be properly plotted.There are visualization methods like umat and sammon in SOM\_PAK3.1,but not implemented here.Author(s)Jun Yan<***************.edu>Examplesfoo<-som(matrix(rnorm(1000),250),3,5)plot(foo,ylim=c(-1,1))4som qerror quantization accuracyDescriptionget the average distortion measureUsageqerror(obj,err.radius=1)Argumentsobj a‘som’objecterr.radius radius used calculating qerrorValueAn average of the following quantity(weighted distance measure)over all x in the sample,||x−m i||h ciwhere h ci is the neighbourhood kernel for the ith code.Author(s)Jun Yan<***************.edu>Examplesfoo<-som(matrix(rnorm(1000),100),2,4)qerror(foo,3)som Function to train a Self-Organizing MapDescriptionProduces an object of class"som"which is a Self-Organizing Mapfit of the data.som5 Usagesom.init(data,xdim,ydim,init="linear")som(data,xdim,ydim,init="linear",alpha=NULL,alphaType="inverse",neigh="gaussian",topol="rect",radius=NULL,rlen=NULL,err.radius=1,inv.alp.c=NULL)som.train(data,code,xdim,ydim,alpha=NULL,alphaType="inverse",neigh="gaussian",topol="rect",radius=NULL,rlen=NULL,err.radius=1,inv.alp.c=NULL) som.update(obj,alpha=NULL,radius=NULL,rlen=NULL,err.radius=1,inv.alp.c=NULL)som.project(obj,newdat)Argumentsobj a‘som’object.newdat a new dataset needs to be projected onto the map.code a matrix of initial code vector in the map.data a data frame or matrix of input data.xdim an integer specifying the x-dimension of the map.ydim an integer specifying the y-dimension of the map.init a character string specifying the initializing method.The following are per-mitted:"sample"uses a radom sample from the data;"random"uses randomdraws from N(0,1);"linear"uses the linear grids upon thefirst two principlecomponents directin.alpha a vector of initial learning rate parameter for the two training phases.Decreaseslinearly to zero during training.alphaType a character string specifying learning rate funciton type.Possible choices arelinear function("linear")and inverse-time type function("inverse").neigh a character string specifying the neighborhood function type.The following arepermitted:"bubble""gaussian"topol a character string specifying the topology type when measuring distance in themap.The following are permitted:"hexa""rect"radius a vector of initial radius of the training area in som-algorithm for the two trainingphases.Decreases linearly to one during training.rlen a vector of running length(number of steps)in the two training phases.err.radius a numeric value specifying the radius when calculating average distortion mea-sure.inv.alp.c the constant C in the inverse learning rate function:alpha0*C/(C+t);6somValue‘som.init’initializes a map and returns the code matrix.‘som’does the two-step som training ina batch fashion and return a‘som’object.‘som.train’takes data,code,and traing parameters andperform the requested som training.‘som.update’takes a‘som’object and further train it with updated paramters.‘som.project’projects new data onto the map.An object of class"som"representing thefit,which is a list containing the following components: data the dataset on which som was applied.init a character string indicating the initializing method.xdim an integer specifying the x-dimension of the map.ydim an integer specifying the y-dimension of the map.code a metrix with nrow=xdim*ydim,each row corresponding to a code vector of a cell in the map.The mapping from cell coordinate(x,y)to the row index in thecode matrix is:rownumber=x+y*xdimvisual a data frame of three columns,with the same number of rows as in data:x and y are the coordinate of the corresponding observation in the map,and qerror is thequantization error computed as the squared distance(depends topol)betweenthe observation vector and its coding vector.alpha0a vector of initial learning rate parameter for the two training phases.alpha a character string specifying learning rate funciton type.neigh a character string specifying the neighborhood function type.topol a character string specifying the topology type when measuring distance in the map.radius0a vector of initial radius of the training area in som-algorithm for the two training phases.rlen a vector of running length in the two training phases.qerror a numeric value of average distortion measure.code.sum a dataframe summaries the number of observations in each map cell.Author(s)Jun Yan<***************.edu>ReferencesKohonen,Hynninen,Kangas,and Laaksonen(1995),SOM-PAK,the Self-Organizing Map Pro-gram Package(version3.1).http://www.cis.hut.fi/research/papers/som\_tr96.ps.ZExamplesdata(yeast)yeast<-yeast[,-c(1,11)]yeast.f<-filtering(yeast)yeast.f.n<-normalize(yeast.f)foo<-som(yeast.f.n,xdim=5,ydim=6)foo<-som(yeast.f.n,xdim=5,ydim=6,topol="hexa",neigh="gaussian")plot(foo)summary.som7 summary.som summarize a som objectDescriptionprint out the configuration parameters of a som objectUsage##S3method for class somsummary(object,...)##S3method for class somprint(x,...)Argumentsobject,x a‘som’object...nothing yetAuthor(s)Jun Yan<***************.edu>yeast yeast cell cycleDescriptionThe yeast data frame has6601rows and18columns,i.e.,6601genes,measured at18time points. Usagedata(yeast)FormatThis data frame contains the following columns:Gene a character vector of gene nameszero a numeric vectorten a numeric vectortwenty a numeric vectorthirty a numeric vectorfourty a numeric vector8yeastfifty a numeric vectorsixty a numeric vectorseventy a numeric vectoreighty a numeric vectorninety a numeric vectorhundred a numeric vectorone.ten a numeric vectorone.twenty a numeric vectorone.thirty a numeric vectorone.fourty a numeric vectorone.fifty a numeric vectorone.sixty a numeric vectorSourceReferencesTamayo et.al.(1999),Interpreting patterns of gene expression with self-organizing maps:Methods and application to hematopoietic differentiation,PNAS V96,pp2907-2912,March1999.Index∗arithqerror,4∗clustersom,4∗datasetsyeast,7∗hplotplot.som,3∗manipfiltering,1normalize,2∗printsummary.som,7filtering,1,3normalize,2,2plot.som,3print.som(summary.som),7qerror,4som,4summary.som,7yeast,79。
3GPP TS 36.331 V13.2.0 (2016-06)

3GPP TS 36.331 V13.2.0 (2016-06)Technical Specification3rd Generation Partnership Project;Technical Specification Group Radio Access Network;Evolved Universal Terrestrial Radio Access (E-UTRA);Radio Resource Control (RRC);Protocol specification(Release 13)The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented.This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organizational Partners' Publications Offices.KeywordsUMTS, radio3GPPPostal address3GPP support office address650 Route des Lucioles - Sophia AntipolisValbonne - FRANCETel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16InternetCopyright NotificationNo part may be reproduced except as authorized by written permission.The copyright and the foregoing restriction extend to reproduction in all media.© 2016, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC).All rights reserved.UMTS™ is a Trade Mark of ETSI registered for the benefit of its members3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational PartnersLTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM AssociationBluetooth® is a Trade Mark of the Bluetooth SIG registered for the benefit of its membersContentsForeword (18)1Scope (19)2References (19)3Definitions, symbols and abbreviations (22)3.1Definitions (22)3.2Abbreviations (24)4General (27)4.1Introduction (27)4.2Architecture (28)4.2.1UE states and state transitions including inter RAT (28)4.2.2Signalling radio bearers (29)4.3Services (30)4.3.1Services provided to upper layers (30)4.3.2Services expected from lower layers (30)4.4Functions (30)5Procedures (32)5.1General (32)5.1.1Introduction (32)5.1.2General requirements (32)5.2System information (33)5.2.1Introduction (33)5.2.1.1General (33)5.2.1.2Scheduling (34)5.2.1.2a Scheduling for NB-IoT (34)5.2.1.3System information validity and notification of changes (35)5.2.1.4Indication of ETWS notification (36)5.2.1.5Indication of CMAS notification (37)5.2.1.6Notification of EAB parameters change (37)5.2.1.7Access Barring parameters change in NB-IoT (37)5.2.2System information acquisition (38)5.2.2.1General (38)5.2.2.2Initiation (38)5.2.2.3System information required by the UE (38)5.2.2.4System information acquisition by the UE (39)5.2.2.5Essential system information missing (42)5.2.2.6Actions upon reception of the MasterInformationBlock message (42)5.2.2.7Actions upon reception of the SystemInformationBlockType1 message (42)5.2.2.8Actions upon reception of SystemInformation messages (44)5.2.2.9Actions upon reception of SystemInformationBlockType2 (44)5.2.2.10Actions upon reception of SystemInformationBlockType3 (45)5.2.2.11Actions upon reception of SystemInformationBlockType4 (45)5.2.2.12Actions upon reception of SystemInformationBlockType5 (45)5.2.2.13Actions upon reception of SystemInformationBlockType6 (45)5.2.2.14Actions upon reception of SystemInformationBlockType7 (45)5.2.2.15Actions upon reception of SystemInformationBlockType8 (45)5.2.2.16Actions upon reception of SystemInformationBlockType9 (46)5.2.2.17Actions upon reception of SystemInformationBlockType10 (46)5.2.2.18Actions upon reception of SystemInformationBlockType11 (46)5.2.2.19Actions upon reception of SystemInformationBlockType12 (47)5.2.2.20Actions upon reception of SystemInformationBlockType13 (48)5.2.2.21Actions upon reception of SystemInformationBlockType14 (48)5.2.2.22Actions upon reception of SystemInformationBlockType15 (48)5.2.2.23Actions upon reception of SystemInformationBlockType16 (48)5.2.2.24Actions upon reception of SystemInformationBlockType17 (48)5.2.2.25Actions upon reception of SystemInformationBlockType18 (48)5.2.2.26Actions upon reception of SystemInformationBlockType19 (49)5.2.3Acquisition of an SI message (49)5.2.3a Acquisition of an SI message by BL UE or UE in CE or a NB-IoT UE (50)5.3Connection control (50)5.3.1Introduction (50)5.3.1.1RRC connection control (50)5.3.1.2Security (52)5.3.1.2a RN security (53)5.3.1.3Connected mode mobility (53)5.3.1.4Connection control in NB-IoT (54)5.3.2Paging (55)5.3.2.1General (55)5.3.2.2Initiation (55)5.3.2.3Reception of the Paging message by the UE (55)5.3.3RRC connection establishment (56)5.3.3.1General (56)5.3.3.1a Conditions for establishing RRC Connection for sidelink communication/ discovery (58)5.3.3.2Initiation (59)5.3.3.3Actions related to transmission of RRCConnectionRequest message (63)5.3.3.3a Actions related to transmission of RRCConnectionResumeRequest message (64)5.3.3.4Reception of the RRCConnectionSetup by the UE (64)5.3.3.4a Reception of the RRCConnectionResume by the UE (66)5.3.3.5Cell re-selection while T300, T302, T303, T305, T306, or T308 is running (68)5.3.3.6T300 expiry (68)5.3.3.7T302, T303, T305, T306, or T308 expiry or stop (69)5.3.3.8Reception of the RRCConnectionReject by the UE (70)5.3.3.9Abortion of RRC connection establishment (71)5.3.3.10Handling of SSAC related parameters (71)5.3.3.11Access barring check (72)5.3.3.12EAB check (73)5.3.3.13Access barring check for ACDC (73)5.3.3.14Access Barring check for NB-IoT (74)5.3.4Initial security activation (75)5.3.4.1General (75)5.3.4.2Initiation (76)5.3.4.3Reception of the SecurityModeCommand by the UE (76)5.3.5RRC connection reconfiguration (77)5.3.5.1General (77)5.3.5.2Initiation (77)5.3.5.3Reception of an RRCConnectionReconfiguration not including the mobilityControlInfo by theUE (77)5.3.5.4Reception of an RRCConnectionReconfiguration including the mobilityControlInfo by the UE(handover) (79)5.3.5.5Reconfiguration failure (83)5.3.5.6T304 expiry (handover failure) (83)5.3.5.7Void (84)5.3.5.7a T307 expiry (SCG change failure) (84)5.3.5.8Radio Configuration involving full configuration option (84)5.3.6Counter check (86)5.3.6.1General (86)5.3.6.2Initiation (86)5.3.6.3Reception of the CounterCheck message by the UE (86)5.3.7RRC connection re-establishment (87)5.3.7.1General (87)5.3.7.2Initiation (87)5.3.7.3Actions following cell selection while T311 is running (88)5.3.7.4Actions related to transmission of RRCConnectionReestablishmentRequest message (89)5.3.7.5Reception of the RRCConnectionReestablishment by the UE (89)5.3.7.6T311 expiry (91)5.3.7.7T301 expiry or selected cell no longer suitable (91)5.3.7.8Reception of RRCConnectionReestablishmentReject by the UE (91)5.3.8RRC connection release (92)5.3.8.1General (92)5.3.8.2Initiation (92)5.3.8.3Reception of the RRCConnectionRelease by the UE (92)5.3.8.4T320 expiry (93)5.3.9RRC connection release requested by upper layers (93)5.3.9.1General (93)5.3.9.2Initiation (93)5.3.10Radio resource configuration (93)5.3.10.0General (93)5.3.10.1SRB addition/ modification (94)5.3.10.2DRB release (95)5.3.10.3DRB addition/ modification (95)5.3.10.3a1DC specific DRB addition or reconfiguration (96)5.3.10.3a2LWA specific DRB addition or reconfiguration (98)5.3.10.3a3LWIP specific DRB addition or reconfiguration (98)5.3.10.3a SCell release (99)5.3.10.3b SCell addition/ modification (99)5.3.10.3c PSCell addition or modification (99)5.3.10.4MAC main reconfiguration (99)5.3.10.5Semi-persistent scheduling reconfiguration (100)5.3.10.6Physical channel reconfiguration (100)5.3.10.7Radio Link Failure Timers and Constants reconfiguration (101)5.3.10.8Time domain measurement resource restriction for serving cell (101)5.3.10.9Other configuration (102)5.3.10.10SCG reconfiguration (103)5.3.10.11SCG dedicated resource configuration (104)5.3.10.12Reconfiguration SCG or split DRB by drb-ToAddModList (105)5.3.10.13Neighbour cell information reconfiguration (105)5.3.10.14Void (105)5.3.10.15Sidelink dedicated configuration (105)5.3.10.16T370 expiry (106)5.3.11Radio link failure related actions (107)5.3.11.1Detection of physical layer problems in RRC_CONNECTED (107)5.3.11.2Recovery of physical layer problems (107)5.3.11.3Detection of radio link failure (107)5.3.12UE actions upon leaving RRC_CONNECTED (109)5.3.13UE actions upon PUCCH/ SRS release request (110)5.3.14Proximity indication (110)5.3.14.1General (110)5.3.14.2Initiation (111)5.3.14.3Actions related to transmission of ProximityIndication message (111)5.3.15Void (111)5.4Inter-RAT mobility (111)5.4.1Introduction (111)5.4.2Handover to E-UTRA (112)5.4.2.1General (112)5.4.2.2Initiation (112)5.4.2.3Reception of the RRCConnectionReconfiguration by the UE (112)5.4.2.4Reconfiguration failure (114)5.4.2.5T304 expiry (handover to E-UTRA failure) (114)5.4.3Mobility from E-UTRA (114)5.4.3.1General (114)5.4.3.2Initiation (115)5.4.3.3Reception of the MobilityFromEUTRACommand by the UE (115)5.4.3.4Successful completion of the mobility from E-UTRA (116)5.4.3.5Mobility from E-UTRA failure (117)5.4.4Handover from E-UTRA preparation request (CDMA2000) (117)5.4.4.1General (117)5.4.4.2Initiation (118)5.4.4.3Reception of the HandoverFromEUTRAPreparationRequest by the UE (118)5.4.5UL handover preparation transfer (CDMA2000) (118)5.4.5.1General (118)5.4.5.2Initiation (118)5.4.5.3Actions related to transmission of the ULHandoverPreparationTransfer message (119)5.4.5.4Failure to deliver the ULHandoverPreparationTransfer message (119)5.4.6Inter-RAT cell change order to E-UTRAN (119)5.4.6.1General (119)5.4.6.2Initiation (119)5.4.6.3UE fails to complete an inter-RAT cell change order (119)5.5Measurements (120)5.5.1Introduction (120)5.5.2Measurement configuration (121)5.5.2.1General (121)5.5.2.2Measurement identity removal (122)5.5.2.2a Measurement identity autonomous removal (122)5.5.2.3Measurement identity addition/ modification (123)5.5.2.4Measurement object removal (124)5.5.2.5Measurement object addition/ modification (124)5.5.2.6Reporting configuration removal (126)5.5.2.7Reporting configuration addition/ modification (127)5.5.2.8Quantity configuration (127)5.5.2.9Measurement gap configuration (127)5.5.2.10Discovery signals measurement timing configuration (128)5.5.2.11RSSI measurement timing configuration (128)5.5.3Performing measurements (128)5.5.3.1General (128)5.5.3.2Layer 3 filtering (131)5.5.4Measurement report triggering (131)5.5.4.1General (131)5.5.4.2Event A1 (Serving becomes better than threshold) (135)5.5.4.3Event A2 (Serving becomes worse than threshold) (136)5.5.4.4Event A3 (Neighbour becomes offset better than PCell/ PSCell) (136)5.5.4.5Event A4 (Neighbour becomes better than threshold) (137)5.5.4.6Event A5 (PCell/ PSCell becomes worse than threshold1 and neighbour becomes better thanthreshold2) (138)5.5.4.6a Event A6 (Neighbour becomes offset better than SCell) (139)5.5.4.7Event B1 (Inter RAT neighbour becomes better than threshold) (139)5.5.4.8Event B2 (PCell becomes worse than threshold1 and inter RAT neighbour becomes better thanthreshold2) (140)5.5.4.9Event C1 (CSI-RS resource becomes better than threshold) (141)5.5.4.10Event C2 (CSI-RS resource becomes offset better than reference CSI-RS resource) (141)5.5.4.11Event W1 (WLAN becomes better than a threshold) (142)5.5.4.12Event W2 (All WLAN inside WLAN mobility set becomes worse than threshold1 and a WLANoutside WLAN mobility set becomes better than threshold2) (142)5.5.4.13Event W3 (All WLAN inside WLAN mobility set becomes worse than a threshold) (143)5.5.5Measurement reporting (144)5.5.6Measurement related actions (148)5.5.6.1Actions upon handover and re-establishment (148)5.5.6.2Speed dependant scaling of measurement related parameters (149)5.5.7Inter-frequency RSTD measurement indication (149)5.5.7.1General (149)5.5.7.2Initiation (150)5.5.7.3Actions related to transmission of InterFreqRSTDMeasurementIndication message (150)5.6Other (150)5.6.0General (150)5.6.1DL information transfer (151)5.6.1.1General (151)5.6.1.2Initiation (151)5.6.1.3Reception of the DLInformationTransfer by the UE (151)5.6.2UL information transfer (151)5.6.2.1General (151)5.6.2.2Initiation (151)5.6.2.3Actions related to transmission of ULInformationTransfer message (152)5.6.2.4Failure to deliver ULInformationTransfer message (152)5.6.3UE capability transfer (152)5.6.3.1General (152)5.6.3.2Initiation (153)5.6.3.3Reception of the UECapabilityEnquiry by the UE (153)5.6.4CSFB to 1x Parameter transfer (157)5.6.4.1General (157)5.6.4.2Initiation (157)5.6.4.3Actions related to transmission of CSFBParametersRequestCDMA2000 message (157)5.6.4.4Reception of the CSFBParametersResponseCDMA2000 message (157)5.6.5UE Information (158)5.6.5.1General (158)5.6.5.2Initiation (158)5.6.5.3Reception of the UEInformationRequest message (158)5.6.6 Logged Measurement Configuration (159)5.6.6.1General (159)5.6.6.2Initiation (160)5.6.6.3Reception of the LoggedMeasurementConfiguration by the UE (160)5.6.6.4T330 expiry (160)5.6.7 Release of Logged Measurement Configuration (160)5.6.7.1General (160)5.6.7.2Initiation (160)5.6.8 Measurements logging (161)5.6.8.1General (161)5.6.8.2Initiation (161)5.6.9In-device coexistence indication (163)5.6.9.1General (163)5.6.9.2Initiation (164)5.6.9.3Actions related to transmission of InDeviceCoexIndication message (164)5.6.10UE Assistance Information (165)5.6.10.1General (165)5.6.10.2Initiation (166)5.6.10.3Actions related to transmission of UEAssistanceInformation message (166)5.6.11 Mobility history information (166)5.6.11.1General (166)5.6.11.2Initiation (166)5.6.12RAN-assisted WLAN interworking (167)5.6.12.1General (167)5.6.12.2Dedicated WLAN offload configuration (167)5.6.12.3WLAN offload RAN evaluation (167)5.6.12.4T350 expiry or stop (167)5.6.12.5Cell selection/ re-selection while T350 is running (168)5.6.13SCG failure information (168)5.6.13.1General (168)5.6.13.2Initiation (168)5.6.13.3Actions related to transmission of SCGFailureInformation message (168)5.6.14LTE-WLAN Aggregation (169)5.6.14.1Introduction (169)5.6.14.2Reception of LWA configuration (169)5.6.14.3Release of LWA configuration (170)5.6.15WLAN connection management (170)5.6.15.1Introduction (170)5.6.15.2WLAN connection status reporting (170)5.6.15.2.1General (170)5.6.15.2.2Initiation (171)5.6.15.2.3Actions related to transmission of WLANConnectionStatusReport message (171)5.6.15.3T351 Expiry (WLAN connection attempt timeout) (171)5.6.15.4WLAN status monitoring (171)5.6.16RAN controlled LTE-WLAN interworking (172)5.6.16.1General (172)5.6.16.2WLAN traffic steering command (172)5.6.17LTE-WLAN aggregation with IPsec tunnel (173)5.6.17.1General (173)5.7Generic error handling (174)5.7.1General (174)5.7.2ASN.1 violation or encoding error (174)5.7.3Field set to a not comprehended value (174)5.7.4Mandatory field missing (174)5.7.5Not comprehended field (176)5.8MBMS (176)5.8.1Introduction (176)5.8.1.1General (176)5.8.1.2Scheduling (176)5.8.1.3MCCH information validity and notification of changes (176)5.8.2MCCH information acquisition (178)5.8.2.1General (178)5.8.2.2Initiation (178)5.8.2.3MCCH information acquisition by the UE (178)5.8.2.4Actions upon reception of the MBSFNAreaConfiguration message (178)5.8.2.5Actions upon reception of the MBMSCountingRequest message (179)5.8.3MBMS PTM radio bearer configuration (179)5.8.3.1General (179)5.8.3.2Initiation (179)5.8.3.3MRB establishment (179)5.8.3.4MRB release (179)5.8.4MBMS Counting Procedure (179)5.8.4.1General (179)5.8.4.2Initiation (180)5.8.4.3Reception of the MBMSCountingRequest message by the UE (180)5.8.5MBMS interest indication (181)5.8.5.1General (181)5.8.5.2Initiation (181)5.8.5.3Determine MBMS frequencies of interest (182)5.8.5.4Actions related to transmission of MBMSInterestIndication message (183)5.8a SC-PTM (183)5.8a.1Introduction (183)5.8a.1.1General (183)5.8a.1.2SC-MCCH scheduling (183)5.8a.1.3SC-MCCH information validity and notification of changes (183)5.8a.1.4Procedures (184)5.8a.2SC-MCCH information acquisition (184)5.8a.2.1General (184)5.8a.2.2Initiation (184)5.8a.2.3SC-MCCH information acquisition by the UE (184)5.8a.2.4Actions upon reception of the SCPTMConfiguration message (185)5.8a.3SC-PTM radio bearer configuration (185)5.8a.3.1General (185)5.8a.3.2Initiation (185)5.8a.3.3SC-MRB establishment (185)5.8a.3.4SC-MRB release (185)5.9RN procedures (186)5.9.1RN reconfiguration (186)5.9.1.1General (186)5.9.1.2Initiation (186)5.9.1.3Reception of the RNReconfiguration by the RN (186)5.10Sidelink (186)5.10.1Introduction (186)5.10.1a Conditions for sidelink communication operation (187)5.10.2Sidelink UE information (188)5.10.2.1General (188)5.10.2.2Initiation (189)5.10.2.3Actions related to transmission of SidelinkUEInformation message (193)5.10.3Sidelink communication monitoring (195)5.10.6Sidelink discovery announcement (198)5.10.6a Sidelink discovery announcement pool selection (201)5.10.6b Sidelink discovery announcement reference carrier selection (201)5.10.7Sidelink synchronisation information transmission (202)5.10.7.1General (202)5.10.7.2Initiation (203)5.10.7.3Transmission of SLSS (204)5.10.7.4Transmission of MasterInformationBlock-SL message (205)5.10.7.5Void (206)5.10.8Sidelink synchronisation reference (206)5.10.8.1General (206)5.10.8.2Selection and reselection of synchronisation reference UE (SyncRef UE) (206)5.10.9Sidelink common control information (207)5.10.9.1General (207)5.10.9.2Actions related to reception of MasterInformationBlock-SL message (207)5.10.10Sidelink relay UE operation (207)5.10.10.1General (207)5.10.10.2AS-conditions for relay related sidelink communication transmission by sidelink relay UE (207)5.10.10.3AS-conditions for relay PS related sidelink discovery transmission by sidelink relay UE (208)5.10.10.4Sidelink relay UE threshold conditions (208)5.10.11Sidelink remote UE operation (208)5.10.11.1General (208)5.10.11.2AS-conditions for relay related sidelink communication transmission by sidelink remote UE (208)5.10.11.3AS-conditions for relay PS related sidelink discovery transmission by sidelink remote UE (209)5.10.11.4Selection and reselection of sidelink relay UE (209)5.10.11.5Sidelink remote UE threshold conditions (210)6Protocol data units, formats and parameters (tabular & ASN.1) (210)6.1General (210)6.2RRC messages (212)6.2.1General message structure (212)–EUTRA-RRC-Definitions (212)–BCCH-BCH-Message (212)–BCCH-DL-SCH-Message (212)–BCCH-DL-SCH-Message-BR (213)–MCCH-Message (213)–PCCH-Message (213)–DL-CCCH-Message (214)–DL-DCCH-Message (214)–UL-CCCH-Message (214)–UL-DCCH-Message (215)–SC-MCCH-Message (215)6.2.2Message definitions (216)–CounterCheck (216)–CounterCheckResponse (217)–CSFBParametersRequestCDMA2000 (217)–CSFBParametersResponseCDMA2000 (218)–DLInformationTransfer (218)–HandoverFromEUTRAPreparationRequest (CDMA2000) (219)–InDeviceCoexIndication (220)–InterFreqRSTDMeasurementIndication (222)–LoggedMeasurementConfiguration (223)–MasterInformationBlock (225)–MBMSCountingRequest (226)–MBMSCountingResponse (226)–MBMSInterestIndication (227)–MBSFNAreaConfiguration (228)–MeasurementReport (228)–MobilityFromEUTRACommand (229)–Paging (232)–ProximityIndication (233)–RNReconfiguration (234)–RNReconfigurationComplete (234)–RRCConnectionReconfiguration (235)–RRCConnectionReconfigurationComplete (240)–RRCConnectionReestablishment (241)–RRCConnectionReestablishmentComplete (241)–RRCConnectionReestablishmentReject (242)–RRCConnectionReestablishmentRequest (243)–RRCConnectionReject (243)–RRCConnectionRelease (244)–RRCConnectionResume (248)–RRCConnectionResumeComplete (249)–RRCConnectionResumeRequest (250)–RRCConnectionRequest (250)–RRCConnectionSetup (251)–RRCConnectionSetupComplete (252)–SCGFailureInformation (253)–SCPTMConfiguration (254)–SecurityModeCommand (255)–SecurityModeComplete (255)–SecurityModeFailure (256)–SidelinkUEInformation (256)–SystemInformation (258)–SystemInformationBlockType1 (259)–UEAssistanceInformation (264)–UECapabilityEnquiry (265)–UECapabilityInformation (266)–UEInformationRequest (267)–UEInformationResponse (267)–ULHandoverPreparationTransfer (CDMA2000) (273)–ULInformationTransfer (274)–WLANConnectionStatusReport (274)6.3RRC information elements (275)6.3.1System information blocks (275)–SystemInformationBlockType2 (275)–SystemInformationBlockType3 (279)–SystemInformationBlockType4 (282)–SystemInformationBlockType5 (283)–SystemInformationBlockType6 (287)–SystemInformationBlockType7 (289)–SystemInformationBlockType8 (290)–SystemInformationBlockType9 (295)–SystemInformationBlockType10 (295)–SystemInformationBlockType11 (296)–SystemInformationBlockType12 (297)–SystemInformationBlockType13 (297)–SystemInformationBlockType14 (298)–SystemInformationBlockType15 (298)–SystemInformationBlockType16 (299)–SystemInformationBlockType17 (300)–SystemInformationBlockType18 (301)–SystemInformationBlockType19 (301)–SystemInformationBlockType20 (304)6.3.2Radio resource control information elements (304)–AntennaInfo (304)–AntennaInfoUL (306)–CQI-ReportConfig (307)–CQI-ReportPeriodicProcExtId (314)–CrossCarrierSchedulingConfig (314)–CSI-IM-Config (315)–CSI-IM-ConfigId (315)–CSI-RS-Config (317)–CSI-RS-ConfigEMIMO (318)–CSI-RS-ConfigNZP (319)–CSI-RS-ConfigNZPId (320)–CSI-RS-ConfigZP (321)–CSI-RS-ConfigZPId (321)–DMRS-Config (321)–DRB-Identity (322)–EPDCCH-Config (322)–EIMTA-MainConfig (324)–LogicalChannelConfig (325)–LWA-Configuration (326)–LWIP-Configuration (326)–RCLWI-Configuration (327)–MAC-MainConfig (327)–P-C-AndCBSR (332)–PDCCH-ConfigSCell (333)–PDCP-Config (334)–PDSCH-Config (337)–PDSCH-RE-MappingQCL-ConfigId (339)–PHICH-Config (339)–PhysicalConfigDedicated (339)–P-Max (344)–PRACH-Config (344)–PresenceAntennaPort1 (346)–PUCCH-Config (347)–PUSCH-Config (351)–RACH-ConfigCommon (355)–RACH-ConfigDedicated (357)–RadioResourceConfigCommon (358)–RadioResourceConfigDedicated (362)–RLC-Config (367)–RLF-TimersAndConstants (369)–RN-SubframeConfig (370)–SchedulingRequestConfig (371)–SoundingRS-UL-Config (372)–SPS-Config (375)–TDD-Config (376)–TimeAlignmentTimer (377)–TPC-PDCCH-Config (377)–TunnelConfigLWIP (378)–UplinkPowerControl (379)–WLAN-Id-List (382)–WLAN-MobilityConfig (382)6.3.3Security control information elements (382)–NextHopChainingCount (382)–SecurityAlgorithmConfig (383)–ShortMAC-I (383)6.3.4Mobility control information elements (383)–AdditionalSpectrumEmission (383)–ARFCN-ValueCDMA2000 (383)–ARFCN-ValueEUTRA (384)–ARFCN-ValueGERAN (384)–ARFCN-ValueUTRA (384)–BandclassCDMA2000 (384)–BandIndicatorGERAN (385)–CarrierFreqCDMA2000 (385)–CarrierFreqGERAN (385)–CellIndexList (387)–CellReselectionPriority (387)–CellSelectionInfoCE (387)–CellReselectionSubPriority (388)–CSFB-RegistrationParam1XRTT (388)–CellGlobalIdEUTRA (389)–CellGlobalIdUTRA (389)–CellGlobalIdGERAN (390)–CellGlobalIdCDMA2000 (390)–CellSelectionInfoNFreq (391)–CSG-Identity (391)–FreqBandIndicator (391)–MobilityControlInfo (391)–MobilityParametersCDMA2000 (1xRTT) (393)–MobilityStateParameters (394)–MultiBandInfoList (394)–NS-PmaxList (394)–PhysCellId (395)–PhysCellIdRange (395)–PhysCellIdRangeUTRA-FDDList (395)–PhysCellIdCDMA2000 (396)–PhysCellIdGERAN (396)–PhysCellIdUTRA-FDD (396)–PhysCellIdUTRA-TDD (396)–PLMN-Identity (397)–PLMN-IdentityList3 (397)–PreRegistrationInfoHRPD (397)–Q-QualMin (398)–Q-RxLevMin (398)–Q-OffsetRange (398)–Q-OffsetRangeInterRAT (399)–ReselectionThreshold (399)–ReselectionThresholdQ (399)–SCellIndex (399)–ServCellIndex (400)–SpeedStateScaleFactors (400)–SystemInfoListGERAN (400)–SystemTimeInfoCDMA2000 (401)–TrackingAreaCode (401)–T-Reselection (402)–T-ReselectionEUTRA-CE (402)6.3.5Measurement information elements (402)–AllowedMeasBandwidth (402)–CSI-RSRP-Range (402)–Hysteresis (402)–LocationInfo (403)–MBSFN-RSRQ-Range (403)–MeasConfig (404)–MeasDS-Config (405)–MeasGapConfig (406)–MeasId (407)–MeasIdToAddModList (407)–MeasObjectCDMA2000 (408)–MeasObjectEUTRA (408)–MeasObjectGERAN (412)–MeasObjectId (412)–MeasObjectToAddModList (412)–MeasObjectUTRA (413)–ReportConfigEUTRA (422)–ReportConfigId (425)–ReportConfigInterRAT (425)–ReportConfigToAddModList (428)–ReportInterval (429)–RSRP-Range (429)–RSRQ-Range (430)–RSRQ-Type (430)–RS-SINR-Range (430)–RSSI-Range-r13 (431)–TimeToTrigger (431)–UL-DelayConfig (431)–WLAN-CarrierInfo (431)–WLAN-RSSI-Range (432)–WLAN-Status (432)6.3.6Other information elements (433)–AbsoluteTimeInfo (433)–AreaConfiguration (433)–C-RNTI (433)–DedicatedInfoCDMA2000 (434)–DedicatedInfoNAS (434)–FilterCoefficient (434)–LoggingDuration (434)–LoggingInterval (435)–MeasSubframePattern (435)–MMEC (435)–NeighCellConfig (435)–OtherConfig (436)–RAND-CDMA2000 (1xRTT) (437)–RAT-Type (437)–ResumeIdentity (437)–RRC-TransactionIdentifier (438)–S-TMSI (438)–TraceReference (438)–UE-CapabilityRAT-ContainerList (438)–UE-EUTRA-Capability (439)–UE-RadioPagingInfo (469)–UE-TimersAndConstants (469)–VisitedCellInfoList (470)–WLAN-OffloadConfig (470)6.3.7MBMS information elements (472)–MBMS-NotificationConfig (472)–MBMS-ServiceList (473)–MBSFN-AreaId (473)–MBSFN-AreaInfoList (473)–MBSFN-SubframeConfig (474)–PMCH-InfoList (475)6.3.7a SC-PTM information elements (476)–SC-MTCH-InfoList (476)–SCPTM-NeighbourCellList (478)6.3.8Sidelink information elements (478)–SL-CommConfig (478)–SL-CommResourcePool (479)–SL-CP-Len (480)–SL-DiscConfig (481)–SL-DiscResourcePool (483)–SL-DiscTxPowerInfo (485)–SL-GapConfig (485)。
纹理物体缺陷的视觉检测算法研究--优秀毕业论文

摘 要
在竞争激烈的工业自动化生产过程中,机器视觉对产品质量的把关起着举足 轻重的作用,机器视觉在缺陷检测技术方面的应用也逐渐普遍起来。与常规的检 测技术相比,自动化的视觉检测系统更加经济、快捷、高效与 安全。纹理物体在 工业生产中广泛存在,像用于半导体装配和封装底板和发光二极管,现代 化电子 系统中的印制电路板,以及纺织行业中的布匹和织物等都可认为是含有纹理特征 的物体。本论文主要致力于纹理物体的缺陷检测技术研究,为纹理物体的自动化 检测提供高效而可靠的检测算法。 纹理是描述图像内容的重要特征,纹理分析也已经被成功的应用与纹理分割 和纹理分类当中。本研究提出了一种基于纹理分析技术和参考比较方式的缺陷检 测算法。这种算法能容忍物体变形引起的图像配准误差,对纹理的影响也具有鲁 棒性。本算法旨在为检测出的缺陷区域提供丰富而重要的物理意义,如缺陷区域 的大小、形状、亮度对比度及空间分布等。同时,在参考图像可行的情况下,本 算法可用于同质纹理物体和非同质纹理物体的检测,对非纹理物体 的检测也可取 得不错的效果。 在整个检测过程中,我们采用了可调控金字塔的纹理分析和重构技术。与传 统的小波纹理分析技术不同,我们在小波域中加入处理物体变形和纹理影响的容 忍度控制算法,来实现容忍物体变形和对纹理影响鲁棒的目的。最后可调控金字 塔的重构保证了缺陷区域物理意义恢复的准确性。实验阶段,我们检测了一系列 具有实际应用价值的图像。实验结果表明 本文提出的纹理物体缺陷检测算法具有 高效性和易于实现性。 关键字: 缺陷检测;纹理;物体变形;可调控金字塔;重构
Keywords: defect detection, texture, object distortion, steerable pyramid, reconstruction
II
unlicense使用方法

unlicense使用方法【原创版4篇】目录(篇1)I.引言A.unlicense介绍B.unlicense的特点II.unlicense的安装A.下载unlicense软件B.解压缩unlicense软件C.安装unlicense软件III.unlicense的使用A.打开unlicense软件B.选择语言C.输入文本D.保存文档IV.unlicense的注意事项A.注意事项一B.注意事项二正文(篇1)unlicense是一款免费的开源文本编辑器,它的使用方法非常简单。
首先,您需要下载并解压缩unlicense软件,然后按照以下步骤进行安装和使用:一、打开unlicense软件,选择语言。
unlicense支持多种语言,包括中文。
您可以在软件界面中选择中文,以便更好地使用unlicense。
二、在unlicense中输入文本。
您可以使用键盘输入文本,也可以使用鼠标拖拽文本块。
unlicense还支持复制和粘贴文本,以便快速地输入文本内容。
三、保存文档。
在unlicense中,您可以随时保存文档。
您可以在软件界面中选择“文件”菜单,然后选择“保存”选项,以保存您的文档。
需要注意的是,在使用unlicense时,您需要注意以下几点:一、确保您的计算机上已经安装了所需的软件和驱动程序,以便正常使用unlicense。
目录(篇2)I.引言A.unlicense的背景介绍B.unlicense的概念解释II.unlicense的使用方法A.安装unlicenseB.创建unlicense许可证C.使用unlicense许可证D.更新unlicense许可证E.备份unlicense许可证F.其他注意事项III.unlicense的优点和缺点A.unlicense的优点B.unlicense的缺点IV.结论A.unlicense的优缺点总结B.使用unlicense的注意事项正文(篇2)一、引言随着互联网的普及,开源软件已成为软件开发领域的重要组成部分。
NoiseImage4安装操作手册

数据分析
数据采集完毕,系统自动跳转到分析界面(也可通过工具栏-File直接打开选中文件),数 据为时域信号,如下图所示:
放大,可 在图上对 想要查看 的数据进 行放大
缩小,将放大 后的图像还原 至上一步
还原
回放按钮
数据分析
使用鼠标左键可以截取一段时域数据,右键列表中功能介绍如下:
基本分析,频 谱、阶次等
数据分析
精细匹配
点击Fine,进行精细匹配
首先在3D模型上选 取一个匹配点位 再从图片上选择相对 应的匹配点位
依次选取4组以上的 参考点即可完成匹配
数据分析
滤波器的使用
滤波器分为四种: Lowpass、Highpass、Bandpass、Bandstop
对于Lowpass、Highpass滤波器需要设 置其截止频率(Cutoff frequency)
选取当前 模型 关闭
•With HDR
•Without HDR
数据分析
•声源漂移修正
采集高速运行状态下的噪声信号时会出现声源漂移情况,此时需要对噪声源进 行定位修正,具体方法如下: 1、放置一个已知声源,在预定工况状态下进行声 源定位,获得已知声源坐标及声源定位点坐标。 2、(X,Y)坐标修正计算公式: X修正值=-(X声源定位点-X已知声源) Y修正值=-(Y声源定位点-Y已知声源) 3、进行正常的测试分析后,在结果图右键属性菜 单中选择如左图所示,按得到的修正坐标将鼠 标修正点定位,重新计算定位结果。
对于Bandpass、Bandstop滤波器需要 设置其频率范围(Frequency range)
2D和3D的其他分析方法的设置方式与上面介绍的基本相同,在此不做赘述
数据分析
•HDR(高动态分辨率分析)
ISO9117-1-2009_Paints_and_varnishes_—_Drying_tests_part1-Determination_of_through-dry_state

Reference number ISO 9117-1:2009(E)© ISO 2009INTERNATIONAL STANDARD ISO 9117-1First edition 2009-05-15Paints and varnishes — Drying tests — Part 1:Determination of through-dry state and through-dry timePeintures et vernis — Essais de séchage —Partie 1: Détermination du séchage à cœur et du temps de séchage à cœurCopyright International Organization for Standardization--`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E)PDF disclaimerThis PDF file may contain embedded typefaces. In accordance with Adobe's licensing policy, this file may be printed or viewed but shall not be edited unless the typefaces which are embedded are licensed to and installed on the computer performing the editing. In downloading this file, parties accept therein the responsibility of not infringing Adobe's licensing policy. The ISO Central Secretariat accepts no liability in this area.Adobe is a trademark of Adobe Systems Incorporated.Details of the software products used to create this PDF file can be found in the General Info relative to the file; the PDF-creation parameters were optimized for printing. Every care has been taken to ensure that the file is suitable for use by ISO member bodies. In the unlikely event that a problem relating to it is found, please inform the Central Secretariat at the address given below.COPYRIGHT PROTECTED DOCUMENT© ISO 2009All rights reserved. Unless otherwise specified, no part of this publication may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm, without permission in writing from either ISO at the address below or ISO's member body in the country of the requester. ISO copyright officeCase postale 56 • CH-1211 Geneva 20 Tel. + 41 22 749 01 11 Fax + 41 22 749 09 47 E-mail copyright@ Web Published in Switzerlandii © ISO 2009 – All rights reservedCopyright International Organization for Standardization --`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E)© ISO 2009 – All rights reservediiiContents PageForeword............................................................................................................................................................iv 1 Scope.....................................................................................................................................................1 2 Normative references...........................................................................................................................1 3 Terms, definitions and abbreviated terms.........................................................................................1 4 Principle.................................................................................................................................................2 5 Apparatus and materials......................................................................................................................2 6 Sampling................................................................................................................................................4 7 Test panels............................................................................................................................................4 7.1 Substrate ...............................................................................................................................................4 7.2 Preparation and coating.......................................................................................................................4 8 Procedure..............................................................................................................................................5 8.1 Preparation of apparatus.....................................................................................................................5 8.2 Drying the test panel ............................................................................................................................5 8.3 Determination of through-dry state ....................................................................................................5 8.4 Determination of through-dry time .....................................................................................................5 8.5 Thickness of coating............................................................................................................................6 9 Precision................................................................................................................................................6 10Test report (6)Bibliography (7)Copyright International Organization for Standardization --`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E)iv © ISO 2009 – All rights reservedForewordISO (the International Organization for Standardization) is a worldwide federation of national standards bodies (ISO member bodies). The work of preparing International Standards is normally carried out through ISO technical committees. Each member body interested in a subject for which a technical committee has been established has the right to be represented on that committee. International organizations, governmental and non-governmental, in liaison with ISO, also take part in the work. ISO collaborates closely with the International Electrotechnical Commission (IEC) on all matters of electrotechnical standardization. International Standards are drafted in accordance with the rules given in the ISO/IEC Directives, Part 2. The main task of technical committees is to prepare International Standards. Draft International Standards adopted by the technical committees are circulated to the member bodies for voting. Publication as an International Standard requires approval by at least 75 % of the member bodies casting a vote.Attention is drawn to the possibility that some of the elements of this document may be the subject of patent rights. ISO shall not be held responsible for identifying any or all such patent rights.ISO 9117-1 was prepared by Technical Committee ISO/TC 35, Paints and varnishes , Subcommittee SC 9, General test methods for paints and varnishes , in collaboration with CEN/TC 139, Paints and varnishes . It cancels and replaces ISO 9117:1990, which has been technically revised. The main changes are: a) failure is defined in terms of damage, rather than damage or marking;b) the former Annex A concerning required supplementary information has been integrated in the test report. ISO 9117 consists of the following parts, under the general title Paints and varnishes — Drying tests : ⎯ Part 1: Determination of through-dry state and through-dry time ⎯ Part 2: Pressure test for stackability 1) ⎯ Part 3: Surface-drying test using ballotini 2)1) To be published. (Revision of ISO 4622:1992) 2) To be published. (Revision of ISO 1517:1973)Copyright International Organization for Standardization--`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---INTERNATIONAL STANDARD ISO 9117-1:2009(E)© ISO 2009 – All rights reserved1Paints and varnishes — Drying tests —Part 1:Determination of through-dry state and through-dry time1 ScopeThis part of ISO 9117 specifies a test method for determining under standard conditions whether a single coat or a multi-coat system of paint, varnish or related material has reached the through-dry state after a specified drying period.NOTEThe test procedure may also be used to determine the time taken to achieve that state.2 Normative referencesThe following referenced documents are indispensable for the application of this document. For dated references, only the edition cited applies. For undated references, the latest edition of the referenced document (including any amendments) applies.ISO 48, Rubber, vulcanized or thermoplastic — Determination of hardness (hardness between 10 IRHD and 100 IRHD)ISO 1513, Paints and varnishes — Preparation of test samples ISO 1514, Paints and varnishes — Standard panels for testing ISO 2808, Paints and varnishes — Determination of film thicknessISO 15528, Paints, varnishes and raw materials for paints and varnishes — Sampling3 Terms, definitions and abbreviated termsFor the purposes of this document, the following terms, definitions and abbreviated terms apply. 3.1IRHD scaleinternational rubber hardness degree scale3.2through-dry statecondition of a film in which it is dry throughout its thicknessNOTE 1 The through-dry state should not be confused with the condition in which the surface of the film is dry but the bulk of the coating is still mobile.Copyright International Organization for Standardization --`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E)2© ISO 2009 – All rights reservedNOTE 2 For the purposes of this part of ISO 9117, a single coating or a multi-coat system of paint or varnish or related material is considered to be through-dry when a specified gauze under specified pressure, torsion and time does not damage the film.3.3through-dry timeperiod of time between the application of a coat to a prepared test panel and the achievement of the through-dry state, as determined by the specified test procedure4 PrincipleA coat of paint or varnish of agreed thickness is applied to a substrate and is allowed to dry under specified conditions. The completeness of drying throughout the coat is determined by examination of the surface of the coat after the application of a load, applied over a given area of the surface, and subsequent rotation of the load-applying face through 90°.5 Apparatus and materialsOrdinary laboratory apparatus and glassware together with the following:5.1 Baseplate and plunger assembly (see Figure 1 and Figure 2), consisting essentially of a baseplate and a free-sliding plunger. The plunger head shall have a diameter of at least 25 mm. It shall be designed in such a way that the underside of the head can align itself with the upper surface of the test panel.NOTE 1 If the mass of the plunger is not greater than 250 g, the apparatus described in ISO 4622 [1] is suitable for thetest.Copyright International Organization for Standardization --`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E)© ISO 2009 – All rights reserved3Key1 weights2 plunger3 ball joint4 plunger head5 baseplateFigure 1 — Baseplate and plunger assemblyA rubber disc (5.2) shall be attached to the centre of the underside of the plunger head using tape coated on both sides with adhesive. There shall be a device to firmly clamp a gauze (5.3) to the test face, and the plunger head shall be able to be rotated through 90°.NOTE 2 It is recommended that a ball-joint connection be present between the plunger and its head and that, for reasons of economy, the plunger specified in ISO 4622 be used.5.2 Flat rubber disc , of diameter (22 ± 1) mm, thickness (5 ± 0,5) mm and hardness (50 ± 5) IRHD (see ISO 48).NOTEFor reasons of economy, it is recommended that the rubber disc specified in ISO 3678 [2] be used.5.3 Gauze , of woven monofilament polyamide, minimum size 100 mm × 100 mm. The gauze thread diameter shall be 0,120 mm and the gauze aperture approximately 0,2 mm. 5.4 Weights , giving a total mass of (1 500 ± 10) g. 5.5 Stopwatch , accurate to 0,1 s.Copyright International Organization for Standardization --`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E)4© ISO 2009 – All rights reservedKey1 plunger2 clip3 rod for rotating plunger head4 gauze 5double-faced adhesive tape 6 rubber discFigure 2 — Detail showing assembled plunger head6 SamplingTake a representative sample of the product to be tested (or of each product in the case of a multi-coat system), as described in ISO 15528.Examine and prepare each sample for testing, as described in ISO 1513.7 Test panels7.1 SubstrateSelect as the substrate three test panels (or six if both the through-dry state and the through-dry time are to be determined) of a type described in ISO 1514, where possible ensuring that the substrate is equivalent to the intended application.7.2 Preparation and coatingPrepare the test panels (see 7.1) in accordance with ISO 1514 and then coat them with the product or system under test by the specified method to the thickness specified for the dry film.The coating method and dry film thickness shall be as specified by the manufacturer, or agreed between interested parties, and included in the test report [see Clause 10, items c) 2) and c) 3)].Copyright International Organization for Standardization --`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E)© ISO 2009 – All rights reserved58 Procedure8.1 Preparation of apparatusClamp the gauze (5.3) over the rubber disc (5.2) under the plunger head (see Figure 2), taking care to ensure that the exposed surface of the gauze is free from creases. Take a fresh piece of gauze for each test.8.2 Drying the test panelDry (or stove) and age, if applicable, each coated test panel in a horizontal position with free circulation of air, but shielded from draughts and direct sunlight, for the specified time under the specified conditions.The drying (or stoving) and aging time and conditions shall be as specified by the manufacturer, or agreed between the interested parties, and included in the test report [see Clause 10, items c) 4) and c) 5)].8.3 Determination of through-dry state8.3.1On completion of the specified drying time (see 8.2), place a test panel on the baseplate.8.3.2 Place the weights (5.4) on the top of the plunger. Gently lower the plunger so that the gauze is in contact with the test panel. Start the stopwatch (5.5) and allow the plunger to remain in this position for (10 ± 1) s.8.3.3 At the end of this period, turn the plunger head through an angle of 90° over a period of about 2 s. Immediately raise the plunger, remove the test panel and examine the coat in the test area using the naked eye. 8.3.4Repeat the procedure in 8.3.1 to 8.3.3 on two additional coated panels.8.3.5 If no damage is observed on any of the three test surfaces, report the result as “through-dry state achieved”. If damage is observed on one or more of the three test surfaces, report the result as “through-dry state not achieved”.Some coatings do not reach a point where they are totally unaffected by the test (i.e. a point where no mark, for instance, is left on the surface by the gauze), even when they have reached a functionally acceptable state of drying or cure. In such cases, the time when the coating reaches the stage at which the action carried out in the test does not cause deterioration of the coating to an extent where it could not perform its ultimate function shall be quoted.For some coatings, e.g. those which are applied to protect the substrate rather than for cosmetic reasons, marking of the surface would not constitute an inability of the coating to perform its function. For highly pigmented coatings, the action of the gauze can cause polishing of the surface, leaving marks which might not be detrimental to the coating’s ultimate function. In such cases, all observations shall be recorded in the test report.Take care to avoid confusion between cohesive failure within the coat (a failure under this test) and failure of the coat to adhere to the substrate (not a failure under this test).8.4 Determination of through-dry time8.4.1On completion of the specified drying time (see 8.2), place a test panel on the baseplate.8.4.2 At appropriate intervals, carry out the test described in 8.3.2 and 8.3.3. Examine the coating in the test area for damage. Stop the test when no damage occurs to the coat (see 8.3.5). 8.4.3 Repeat t he procedure in 8.4.1 and 8.4.2 on two additional coated panels.8.4.4Report the longest time taken in the three tests for the coat to reach the through-dry state.Copyright International Organization for Standardization --`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E)6© ISO 2009 – All rights reserved8.5 Thickness of coatingDetermine the thickness, in micrometres, of the coat in the through-dry state by one of the procedures specified in ISO 2808, using an untested area of the coated panel.9 PrecisionNo precision data are currently available.10 Test reportThe test report shall contain at least the following information: a) all information necessary for identification of the product tested; b) a reference to this part of ISO 9117 (ISO 9117-1:2009); c) details of the preparation of the test panels, including:1) the substrate material and the surface preparation of the substrate (see 7.1 and 7.2), 2) the method of application of the test coating to the substrate (see 7.2),3) the thickness, in micrometres, of the dry coating and the method of measurement from ISO 2808(see 8.5), and whether it is a single coating or a multi-coat system, 4) when assessing the through-dry state, the duration and conditions of drying (or stoving) the coat andthe conditions of ageing, if applicable, before testing (see 8.3), 5) when determining the through-dry time, the conditions of drying (or stoving) the coat and theconditions of ageing, if applicable, before testing, and the intervals between tests (see 8.4); d) the results of the test as specified in Clause 8, including:1) whether the coat achieved the through-dry state or not, and/or2) the through-dry time,3) all observations (see 8.3.5, third paragraph); e) any deviations from the procedure specified; f)any unusual features (anomalies) observed during the test;g) the date of the test.Copyright International Organization for Standardization --`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E) © ISO 2009 – All rights reserved 7Bibliography[1] ISO 4622, Paints and varnishes — Pressure test for stackability 3)[2] ISO 3678, Paints and varnishes — Print-free test3) Under revision. The revision will be published as ISO 9117-2.Copyright International Organization for Standardization Provided by IHS under license with ISO Licensee=Hong Kong Polytechnic Univ/9976803100 Not for Resale, 10/24/2009 22:07:36 MDT No reproduction or networking permitted without license from IHS --`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ISO 9117-1:2009(E)--`,,`,,``,```,,`,``,,````,,,``,-`-`,,`,,`,`,,`---ICS 87.040Price based on 7 pages© ISO 2009 – All rights reservedCopyright International Organization for StandardizationProvided by IHS under license with ISO Licensee=Hong Kong Polytechnic Univ/9976803100 No reproduction or networking permitted without license from IHSNot for Resale, 10/24/2009 22:07:36 MDT。
基于形变的形态测量学在脑疾病诊断中的应用

基于形变的形态测量学在脑疾病诊断中的应用夏翃;刘卫芳;童隆正;张景;周震;杨慧芳;刘苏【摘要】Deformation-based morphometry (DBM) is a tool for detection of structural changes over the entire brain,and thus can to find out the relationship between brain structure changes with disease.The method of DBM is introduced and its researches are reviewed,which can help researchers to discover the evolution of disease.%基于形变的形态测量学DBM方法是通过提取脑结构形变大小和方向等形变信息来分析生理性脑结构变化、病理性的脑部组织缺损.对DBM技术在脑图像处理中的研究方法和相关文献资料进行了研究综述,有助于利用DBM技术对脑结构图像进行分析发现脑疾病的病程演进.【期刊名称】《北华大学学报(自然科学版)》【年(卷),期】2013(014)003【总页数】3页(P302-304)【关键词】形态测量学;基于形变的形态测量学;核磁共振成像【作者】夏翃;刘卫芳;童隆正;张景;周震;杨慧芳;刘苏【作者单位】首都医科大学生物医学工程学院,北京100069;首都医科大学生物医学工程学院,北京100069;首都医科大学生物医学工程学院,北京100069;首都医科大学生物医学工程学院,北京100069;首都医科大学生物医学工程学院,北京100069;首都医科大学生物医学工程学院,北京100069;首都医科大学生物医学工程学院,北京100069【正文语种】中文【中图分类】R749.16大脑皮层的局部区域能实现大脑的具体功能,脑功能区的准确定位可协助医生分析疾病的诱因、病程发展以及治疗效果评估等.早期研究多通过采用手工绘制感兴趣区,但该方法存在诸多缺陷:费力、费时,且测量结果易受个体因素影响,而且此方法只能对特定脑区域进行测量研究,不能够对全脑进行整体分析或对比研究.利用脑体积测量法来研究脑结构也易受个体差异影响,且无法提供某些局部脑区微小变化的详细空间特征,因此存在着很大的局限性.目前,国内外研究人员开始关注形态学测量方法(Morphometry),这种方法可以用来获取脑结构的全面、客观的定量信息.1 形态测量学与脑图像处理近年来形态测量学在生物医学领域尤其是在脑图像的研究中应用日益广泛.形态测量学是由形态学与数学相结合而产生的医学图像处理技术,获取描述生物组织宏观或微观形态的图像信息数据,对它们进行数学处理,从而对生物组织的形状与结构进行定量描述、分析和解释的一门学科.形态测量学广泛应用于脑科学的临床研究中,如脑疾病研究、脑结构研究、脑认知研究等领域.形态测量学在脑功能方面研究主要有基于体素的形态测量学(Voxel-Based Morphometry,VBM)、基于形变的形态测量学(DBM)等方法,本文主要介绍DBM方法的研究现状.2 基于形变的形态测量学(DBM)基于形变的形态测量学(Deformation-Based Morphometry,DBM)是一种识别不同脑区解剖学特点的方法.该方法通过利用形变场描述不同个体的脑结构差异,从而确定脑相关结构的对应位置.DBM方法是全脑的一种全自动形态测量学方法,它基于图像配准过程中产生的形变场,从中提取能够反映个体之间对应脑结构体积变化差异的特征,进而对不同人群进行组间统计分析,在全脑范围内自动找出两组或多组数据对应结构变化的差异,从而找出脑结构变化与疾病之间的关系,更好地帮助医生从脑结构上明确病理机制.随着脑结构配准算法的不断提高和性能优化,DBM已经应用于科研人员分析脑发育、研究脑损伤等方面.DBM方法对MR图像预处理流程如图1所示,DBM分析方法见图2.首先将样本图像(图a)与标准模板(图c)配准,标准化至同一脑区定位空间,非线性标准化过程消除两个脑图像之间在解剖学上的差异(图b);其次采用形变网格算法计算图像变形(图e);最后提取位移偏量,有两种方法:可以是多元使用整个三维形变场的XYZ 位移,也可以采用Jacobian行列式作为该区域的衍生(图f);最后,计算形变相关系数[1].图1 DBM分析方法操作流程Fig.1 Processing flow involved in Deformation-Based Morphometry3 DBM在脑结构中的研究现状越来越多的国内外研究人员将DBM技术应用于脑结构的医学临床研究中.DBM 与现在普遍采用的VBM方法不同,它分析的是脑结构大小和方向等形变信息,该方法在分析生理性脑结构变化、病理性脑部组织缺损等方面越来越受到重视.Volz等[2]采用DBM方法对75位精神分裂症患者和75位对照人员的MRI图像进行分析,精神分裂症患者的以下部位体积发生减少:额叶、颞叶、丘脑、左侧小脑半球和右小脑蚓体,而右壳核的体积增大.图2 DBM分析方法Fig.2 Steps of analysis in Deformation-Based MorphometryChristian Gaser等[3]对 39名精神分裂症患者的T1-MRI图像采用DBM方法进行两种不同方法的研究.第一种研究方法:将受试者按平均脑比值分为两组,再计算位移矢量的统计图.该研究方法发现,DBM方法和视觉跟踪结果高度一致.第二种研究方法:通过对整个脑室雅可比值的平均值研究发现,DBM方法和基于视觉跟踪的脑比值相关性为0.962.研究最终结果认为,DBM方法对大脑的局部和整体形态的实验是有效的.WANG等[4]研究多动症男童时,该研究小组采用DBM技术,分析了12例患者和12例对照组人员的脑容量,并对脑MRI进行评估,统计分析局部脑容量,研究结果显示:多动症患儿的脑容量发生了重大的变化,有显著性改变.Tosun等[5]在研究儿童癫痫时采用 DBM方法,与正常儿童对照组相比,癫痫儿童的脑白质和灰质发展模式是不正常的,其小脑、丘脑、脑皮质等的神经发育是异常变化的.Zhuang等[6]研究轻度认知障碍(Mild Cognitive Impairment,MCI)时采用DBM方法测量海马体积,研究结果显示:遗忘型MCI(aMCI)患者的海马左穹窿各向异性减少,双边穹窿径向扩散增加,而非遗忘型MCI(naMCI)患者却没有发现此类变化.此外,研究还认为穹窿结构的微小改变会导致早期记忆障碍.杨春兰等[7]在研究早盲症发病脑结构所发生改变的部位时,采用HAMMER校准技术的DBM方法,对15位早盲症患者和30位匹配健康对照组的MRI图像进行对比研究发现,早盲症发病时,脑结构发生变大的部位主要位于左侧相关的视觉皮层、后扣带皮质和小脑.她们认为,在早期神经发育的关键时期,脑结构组织实际上已发生了改变,而DBM方法是一种通过检测全脑结构变化来发现早盲的有效方法.Savio[8]利用基于DBM支持向量机的CAD系统对OASIS数据库中健康对照组和AD患者的结构MRI图像数据进行对比,发现大脑中的形变位置与大多数文献报道结果一致.Gaser等[9]利用自行开发的DBM工具对老鼠脑结构标准MR图像进行测量.对于横向数据采用MATLAB软件包SPM8中低维非线性校准方法,而对纵向数据则选择高维校准,以便识别更细微的脑结构变化.研究发现,随着老鼠年龄的增大,DBM方法可以高灵敏地检测出鼠脑结构的变化.Hana等[10]对13例威廉斯综合征与13例正常对照人员进行研究,采用SPM8中提供的5种非刚性配准算法:1)自适应基线算法;2)图像配准工具包;3)FSL 非线性的图像配准工具;4)自动配准工具;5)标准化算法.结果显示:算法的选择对分组图集的产生影响不大.但是,有些区域是能被一些算法检测的,但其程度各不相同,而一些区域仅被算法的子集检测到.因此,采用DBM方法进行研究时,最好采用多种配准算法.4 结论医学图像处理技术作为临床辅助诊断的重要手段,在医学临床及基础研究中得到广泛的应用.随着成像技术的进步以及形态测量学技术的成熟,国内外研究人员在脑科学的研究中越来越多地采用了形态测量学技术.但基于形变的形态测量学技术尚处于起步阶段,许多问题还有待于通过深入研究来加以解决.如,当脑结构形变严重时,发生误配准的概率就会明显增高,从而导致统计分析结果的可信度降低等等.随着图像处理技术的发展,DBM方法也会不断发展优化,因此,优化的DBM方法在脑图像处理中的应用也会更加深入.参考文献:【相关文献】[1] Christian Gaser,Igor Nenadic,Bradley R Buchsbaum,et al.Deformation-Based Morphometry and Its Relation to Conventional Volumetry of Brain Lateral Ventricles in MRI[J].Neuro Image,2001,13:1140-1145.[2] Volz H,Gaser C,Sauer H.Supporting Evidence for the Model of Cognitive Dysmetria in Schizophrenia-a Structural MagneticResonance ImagingStudyUsing Deformation-based Morphometry [J].Schizophrenia Research,2000,46(1):45-56.[3] Christian Gaser,Igor Nenadic,Bradley R Buchsbaum,et al.Deformation-Based Morphometry and Its Relation to Conventional Volumetry of Brain Lateral Ventricles in MRI[J].Neuro Image,2001,13(6):1140-1145.[4] WANG Jian-zhe, JIANG Tian-zi, CAOQing-jiu.Characterizing Anatomic Differences in Boys with Attention-deficit/hyperactivity Disorder with the Use of Deformation-based Morphometry[J].American Journal of Neuroradiology,2007,28(3):543-547.[5] Duygu Tosun, Kevin Dabbs. Deformation-based Morphometry of Prospective Neurodevelopmental Changes in New Onset Paediatric Epilepsy [J].Brain,2011,134(4):1003-1014.[6] Lin Zhuang,WeiWen,Julian N Trollor, etal.Abnormalities of the Fornix in Mild Cognitive Impairment are Related to Episodic Memory Loss[J].Journal of Alzheimer’s Disease,2012,DOI:http://dx.doi.org/10.3233/JAD-2011-111766.[7] Chunlan Yang,ShuicaiWu,Wangsheng Lu,etal.Anatomic Differences in Early Blindness:A Deformation-Based Morphometry MRI Study[J].Neuro Image,2012,DOI:10.1111/j.1552-6569.2011.00686.x.[8] Alexandre Savio,Manuel Gra.Deformation Based Feature Selection for Computer Aided Diagnosis of Alzheimer’s Disease[J].Expert Systems with Applications,2013,40(5):1619-1628.[9] Christian Gaser,Silvio Schmidt,Martin Metzler,et al.Deformation-based Brain Morphometry in Rats[J].Neuro Image,2012,63(1):47-53.[10] Zhaoying Hana,Tricia A Thornton-Wells,Elisabeth M Dykens,et al.Effect of Nonrigid Registration Algorithms on Deformation-based Morphometry:a Comparative Study with Control and Williams Syndrome Subjects[J].Magnetic Resonance Imaging,2012,30(6):774-788.。
Spectrum Living Image 40软件操作流程
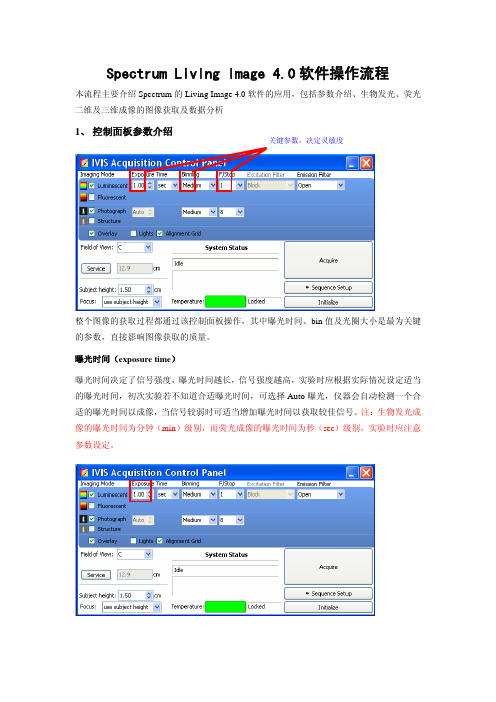
Spectrum Living Image 4.0软件操作流程本流程主要介绍Spectrum 的Living Image 4.0软件的应用,包括参数介绍、生物发光、荧光二维及三维成像的图像获取及数据分析1、 控制面板参数介绍整个图像的获取过程都通过该控制面板操作,其中曝光时间、bin 值及光圈大小是最为关键的参数,直接影响图像获取的质量。
曝光时间(exposure time )曝光时间决定了信号强度,曝光时间越长,信号强度越高,实验时应根据实际情况设定适当的曝光时间,初次实验若不知道合适曝光时间,可选择Auto 曝光,仪器会自动检测一个合适的曝光时间以成像,当信号较弱时可适当增加曝光时间以获取较佳信号。
注:生物发光成像的曝光时间为分钟(min )级别,而荧光成像的曝光时间为秒(sec )级别,实验时应注意参数设定。
关键参数,决定灵敏度Bin 值(Binning )Bin 值表述的是将多少像素作为感光单元,bin 值越大则表示应用更多的像素作为一个感光单元,因此,bin 值越大则灵敏度越高,而分辨率会有所牺牲,当信号强度较弱时可适当增加bin 值以获取信号。
光圈大小(f/stop )光圈大小决定了光的透过量,光圈越大,穿过光圈到达CCD 的光越多,面板中的数字为F/stop 中的分母数字,因此,数字越小代表光圈孔径越大,透过的光越多,当信号较弱时可通过增大光圈(减小数字)而增强信号探测能力。
f/1Large Binning (16)Medium Binning (8)Small Binning (4)视野范围(Filed of View )视野范围用于调节观测的视野大小,共有A/B/C/D 四档可选,分别代表不同大小的视野范围,实验时根据一次观察小鼠个数选择合适的视野范围进行成像。
成像聚焦(Focus )成像的聚焦包含自动聚焦和手动聚焦功能,在用小鼠进行成像时,一般默认成像对象的高度为1.5cm ,仪器会自动完成聚焦,在用其他对象进行成像时(如大鼠),可调节Subject height 参数,设定合适的聚焦高度,也可在Focus 下拉选项中选择聚焦设定 FOV A: 4.0 cm FOV B: 6.5 cm FOV C: 12.5 cm FOV D: 21.5 cm2、生物发光二维成像的图像获取勾选Luminescent、Photograph及overlay选项,设置好曝光时间(生物发光曝光时间为分钟级别)、bin值、光圈大小及视野范围等参数(软件有默认参数,可按照默认参数成像,若效果不佳,则再调整各参数,调整的次序按照曝光时间>bin值>光圈大小顺序调整),Emission Filter选项设置为open,Photograph选项的参数一般情况无需调整,所有参数设定完毕后点击Acquire按钮即可开始成像。
Deformable Medical Image Registration

Deformable Medical Image Registration:A Survey Aristeidis Sotiras*,Member,IEEE,Christos Davatzikos,Senior Member,IEEE,and Nikos Paragios,Fellow,IEEE(Invited Paper)Abstract—Deformable image registration is a fundamental task in medical image processing.Among its most important applica-tions,one may cite:1)multi-modality fusion,where information acquired by different imaging devices or protocols is fused to fa-cilitate diagnosis and treatment planning;2)longitudinal studies, where temporal structural or anatomical changes are investigated; and3)population modeling and statistical atlases used to study normal anatomical variability.In this paper,we attempt to give an overview of deformable registration methods,putting emphasis on the most recent advances in the domain.Additional emphasis has been given to techniques applied to medical images.In order to study image registration methods in depth,their main compo-nents are identified and studied independently.The most recent techniques are presented in a systematic fashion.The contribution of this paper is to provide an extensive account of registration tech-niques in a systematic manner.Index Terms—Bibliographical review,deformable registration, medical image analysis.I.I NTRODUCTIOND EFORMABLE registration[1]–[10]has been,alongwith organ segmentation,one of the main challenges in modern medical image analysis.The process consists of establishing spatial correspondences between different image acquisitions.The term deformable(as opposed to linear or global)is used to denote the fact that the observed signals are associated through a nonlinear dense transformation,or a spatially varying deformation model.In general,registration can be performed on two or more im-ages.In this paper,we focus on registration methods that involve two images.One is usually referred to as the source or moving image,while the other is referred to as the target orfixed image. In this paper,the source image is denoted by,while the targetManuscript received March02,2013;revised May17,2013;accepted May 21,2013.Date of publication May31,2013;date of current version June26, 2013.Asterisk indicates corresponding author.*A.Sotiras is with the Section of Biomedical Image Analysis,Center for Biomedical Image Computing and Analytics,Department of Radi-ology,University of Pennsylvania,Philadelphia,PA19104USA(e-mail: aristieidis.sotiras@).C.Davatzikos is with the Section of Biomedical Image Analysis,Center for Biomedical Image Computing and Analytics,Department of Radi-ology,University of Pennsylvania,Philadelphia,PA19104USA(e-mail: christos.davatzikos@).N.Paragios is with the Center for Visual Computing,Department of Applied Mathematics,Ecole Centrale de Paris,92295Chatenay-Malabry,France,and with the Equipe Galen,INRIA Saclay-Ile-de-France,91893Orsay,France,and also with the Universite Paris-Est,LIGM(UMR CNRS),Center for Visual Com-puting,Ecole des Ponts ParisTech,77455Champs-sur-Marne,France. Digital Object Identifier10.1109/TMI.2013.2265603image is denoted by.The two images are defined in the image domain and are related by a transformation.The goal of registration is to estimate the optimal transforma-tion that optimizes an energy of the form(1) The previous objective function(1)comprises two terms.The first term,,quantifies the level of alignment between a target image and a source image.Throughout this paper,we in-terchangeably refer to this term as matching criterion,(dis)sim-ilarity criterion or distance measure.The optimization problem consists of either maximizing or minimizing the objective func-tion depending on how the matching term is chosen.The images get aligned under the influence of transformation .The transformation is a mapping function of the domain to itself,that maps point locations to other locations.In gen-eral,the transformation is assumed to map homologous loca-tions from the target physiology to the source physiology.The transformation at every position is given as the addition of an identity transformation with the displacementfield,or.The second term,,regularizes the trans-formation aiming to favor any specific properties in the solution that the user requires,and seeks to tackle the difficulty associ-ated with the ill-posedness of the problem.Regularization and deformation models are closely related. Two main aspects of this relation may be distinguished.First, in the case that the transformation is parametrized by a small number of variables and is inherently smooth,regularization may serve to introduce prior knowledge regarding the solution that we seek by imposing task-specific constraints on the trans-formation.Second,in the case that we seek the displacement of every image element(i.e.,nonparametric deformation model), regularization dictates the nature of the transformation. Thus,an image registration algorithm involves three main components:1)a deformation model,2)an objective function, and3)an optimization method.The result of the registration algorithm naturally depends on the deformation model and the objective function.The dependency of the registration result on the optimization strategy follows from the fact that image regis-tration is inherently ill-posed.Devising each component so that the requirements of the registration algorithm are met is a de-manding process.Depending on the deformation model and the input data,the problem may be ill-posed according to Hadamard’s definition of well-posed problems[11].In probably all realistic scenarios, registration is ill-posed.To further elaborate,let us consider some specific cases.In a deformable registration scenario,one0278-0062/$31.00©2013IEEEseeks to estimate a vector for every position given,in general, scalar information conveyed by image intensity.In this case,the number of unknowns is greater than the number of constraints. In a rigid setting,let us consider a consider a scenario where two images of a disk(white background,gray foreground)are registered.Despite the fact that the number of parameters is only 6,the problem is ill-posed.The problem has no unique solution since a translation that aligns the centers of the disks followed by any rotation results in a meaningful solution.Given nonlinear and nonconvex objective functions,in gen-eral,no closed-form solutions exist to estimate the registration parameters.In this setting,the search methods reach only a local minimum in the parameter space.Moreover,the problem itself has an enormous number of different facets.The approach that one should take depends on the anatomical properties of the organ(for example,the heart and liver do not adhere to the same degree of deformation),the nature of observations to be regis-tered(same modality versus multi-modal fusion),the clinical setting in which registration is to be used(e.g.,offline interpre-tation versus computer assisted surgery).An enormous amount of research has been dedicated to de-formable registration towards tackling these challenges due to its potential clinical impact.During the past few decades,many innovative ideas regarding the three main algorithmic registra-tion aspects have been proposed.General reviews of thefield may be found in[1]–[7],[9].However due to the rapid progress of thefield such reviews are to a certain extent outdated.The aim of this paper is to provide a thorough overview of the advances of the past decade in deformable registration.Never-theless,some classic papers that have greatly advanced the ideas in thefield are mentioned.Even though our primary interest is deformable registration,for the completeness of the presenta-tion,references to linear methods are included as many prob-lems have been treated in this low-degree-of-freedom setting before being extended to the deformable case.The main scope of this paper is focused on applications that seek to establish spatial correspondences between medical im-ages.Nonetheless,we have extended the scope to cover appli-cations where the interest is to recover the apparent motion of objects between sequences of successive images(opticalflow estimation)[12],[13].Deformable registration and opticalflow estimation are closely related problems.Both problems aim to establish correspondences between images.In the deformable registration case,spatial correspondences are sought,while in the opticalflow case,spatial correspondences,that are associ-ated with different time points,are looked for.Given data with a good temporal resolution,one may assume that the magnitude of the motion is limited and that image intensity is preserved in time,opticalflow estimation can be regarded as a small defor-mation mono-modal deformable registration problem.The remainder of the paper is organized by loosely following the structural separation of registration algorithms to three com-ponents:1)deformation model,2)matching criteria,and3)op-timization method.In Section II,different approaches regarding the deformation model are presented.Moreover,we also chose to cover in this section the second term of the objective function, the regularization term.This choice was motivated by the close relation between the two parts.In Section III,thefirst term of the objective function,the matching term,is discussed.The opti-mization methods are presented in Section IV.In every section, particular emphasis was put on further deepening the taxonomy of registration method by grouping the presented methods in a systematic manner.Section V concludes the paper.II.D EFORMATION M ODELSThe choice of deformation model is of great importance for the registration process as it entails an important compromise between computational efficiency and richness of description. It also reflects the class of transformations that are desirable or acceptable,and therefore limits the solution to a large ex-tent.The parameters that registration estimates through the op-timization strategy correspond to the degrees of freedom of the deformation model1.Their number varies greatly,from six in the case of global rigid transformations,to millions when non-parametric dense transformations are considered.Increasing the dimensionality of the state space results in enriching the de-scriptive power of the model.This model enrichment may be accompanied by an increase in the model’s complexity which, in turns,results in a more challenging and computationally de-manding inference.Furthermore,the choice of the deformation model implies an assumption regarding the nature of the defor-mation to be recovered.Before continuing,let us clarify an important,from imple-mentation point of view,aspect related to the transformation mapping and the deformation of the source image.In the in-troduction,we stated that the transformation is assumed to map homologous locations from the target physiology to the source physiology(backward mapping).While from a theoretical point of view,the mapping from the source physiology to the target physiology is possible(forward mapping),from an implemen-tation point of view,this mapping is less advantageous.In order to better understand the previous statement,let us consider how the direction of the mapping influences the esti-mation of the deformed image.In both cases,the source image is warped to the target domain through interpolation resulting to a deformed image.When the forward mapping is estimated, every voxel of the source image is pushed forward to its esti-mated position in the deformed image.On the other hand,when the backward mapping is estimated,the pixel value of a voxel in the deformed image is pulled from the source image.The difference between the two schemes is in the difficulty of the interpolation problem that has to be solved.In thefirst case,a scattered data interpolation problem needs to be solved because the voxel locations of the source image are usually mapped to nonvoxel locations,and the intensity values of the voxels of the deformed image have to be calculated.In the second case,when voxel locations of the deformed image are mapped to nonvoxel locations in the source image,their intensities can be easily cal-culated by interpolating the intensity values of the neighboring voxels.The rest of the section is organized by following coarsely and extending the classification of deformation models given 1Variational approaches in general attempt to determine a function,not just a set of parameters.SOTIRAS et al.:DEFORMABLE MEDICAL IMAGE REGISTRATION:A SURVEY1155Fig.1.Classi fication of deformation models.Models that satisfy task-speci fic constraints are not shown as a branch of the tree because they are,in general,used in conjunction with physics-based and interpolation-based models.by Holden [14].More emphasis is put on aspects that were not covered by that review.Geometric transformations can be classi fied into three main categories (see Fig.1):1)those that are inspired by physical models,2)those inspired by interpolation and ap-proximation theory,3)knowledge-based deformation models that opt to introduce speci fic prior information regarding the sought deformation,and 4)models that satisfy a task-speci fic constraint.Of great importance for biomedical applications are the con-straints that may be applied to the transformation such that it exhibits special properties.Such properties include,but are not limited to,inverse consistency,symmetry,topology preserva-tion,diffeomorphism.The value of these properties was made apparent to the research community and were gradually intro-duced as extra constraints.Despite common intuition,the majority of the existing regis-tration algorithms are asymmetric.As a consequence,when in-terchanging the order of input images,the registration algorithm does not estimate the inverse transformation.As a consequence,the statistical analysis that follows registration is biased on the choice of the target domain.Inverse Consistency:Inverse consistent methods aim to tackle this shortcoming by simultaneously estimating both the forward and the backward transformation.The data matching term quanti fies how well the images are aligned when one image is deformed by the forward transformation,and the other image by the backward transformation.Additionally,inverse consistent algorithms constrain the forward and backward transformations to be inverse mappings of one another.This is achieved by introducing terms that penalize the difference between the forward and backward transformations from the respective inverse mappings.Inverse consistent methods can preserve topology but are only asymptotically symmetric.Inverse-consistency can be violated if another term of the objective function is weighted more importantly.Symmetry:Symmetric algorithms also aim to cope with asymmetry.These methods do not explicitly penalize asym-metry,but instead employ one of the following two strategies.In the first case,they employ objective functions that are by construction symmetric to estimate the transformation from one image to another.In the second case,two transformation functions are estimated by optimizing a standard objective function.Each transformation function map an image to a common domain.The final mapping from one image to another is calculated by inverting one transformation function and composing it with the other.Topology Preservation:The transformation that is estimated by registration algorithms is not always one-to-one and cross-ings may appear in the deformation field.Topology preserving/homeomorphic algorithms produce a mapping that is contin-uous,onto,and locally one-to-one and has a continuous inverse.The Jacobian determinant contains information regarding the injectivity of the mapping and is greater than zero for topology preserving mappings.The differentiability of the transformation needs to be ensured in order to calculate the Jacobian determi-nant.Let us note that Jacobian determinant and Jacobian are in-terchangeably used in this paper and should not be confounded with the Jacobian matrix.Diffeomorphism:Diffeomoprhic transformations also pre-serve topology.A transformation function is a diffeomorphism,if it is invertible and both the function and its inverse are differ-entiable.A diffeomorphism maps a differentiable manifold to another.1156IEEE TRANSACTIONS ON MEDICAL IMAGING,VOL.32,NO.7,JULY2013In the following four subsections,the most important methods of the four classes are presented with emphasis on the approaches that endow the model under consideration with the above desirable properties.A.Geometric Transformations Derived From Physical Models Following[5],currently employed physical models can be further separated infive categories(see Fig.1):1)elastic body models,2)viscousfluidflow models,3)diffusion models,4) curvature registration,and5)flows of diffeomorphisms.1)Elastic Body Models:a)Linear Models:In this case,the image under deforma-tion is modeled as an elastic body.The Navier-Cauchy Partial Differential Equation(PDE)describes the deformation,or(2) where is the forcefield that drives the registration based on an image matching criterion,refers to the rigidity that quanti-fies the stiffness of the material and is Lamésfirst coefficient. Broit[15]first proposed to model an image grid as an elastic membrane that is deformed under the influence of two forces that compete until equilibrium is reached.An external force tries to deform the image such that matching is achieved while an internal one enforces the elastic properties of the material. Bajcsy and Kovacic[16]extended this approach in a hierar-chical fashion where the solution of the coarsest scale is up-sam-pled and used to initialize thefiner one.Linear registration was used at the lowest resolution.Gee and Bajscy[17]formulated the elastostatic problem in a variational setting.The problem was solved under the Bayesian paradigm allowing for the computation of the uncertainty of the solution as well as for confidence intervals.Thefinite element method(FEM)was used to infer the displacements for the ele-ment nodes,while an interpolation strategy was employed to es-timate displacements elsewhere.The order of the interpolating or shape functions,determines the smoothness of the obtained result.Linear elastic models have also been used when registering brain images based on sparse correspondences.Davatzikos[18]first used geometric characteristics to establish a mapping be-tween the cortical surfaces.Then,a global transformation was estimated by modeling the images as inhomogeneous elastic ob-jects.Spatially-varying elasticity parameters were used to com-pensate for the fact that certain structures tend to deform more than others.In addition,a nonzero initial strain was considered so that some structures expand or contract naturally.In general,an important drawback of registration is that when source and target volumes are interchanged,the obtained trans-formation is not the inverse of the previous solution.In order to tackle this shortcoming,Christensen and Johnson[19]pro-posed to simultaneously estimate both forward and backward transformations,while penalizing inconsistent transformations by adding a constraint to the objective function.Linear elasticity was used as regularization constraint and Fourier series were used to parametrize the transformation.Leow et al.[20]took a different approach to tackle the incon-sistency problem.Instead of adding a constraint that penalizes the inconsistency error,they proposed a unidirectional approach that couples the forward and backward transformation and pro-vides inverse consistent transformations by construction.The coupling was performed by modeling the backward transforma-tion as the inverse of the forward.This fact was also exploited during the optimization of the symmetric energy by only fol-lowing the gradient direction of the forward mapping.He and Christensen[21]proposed to tackle large deforma-tions in an inverse consistent framework by considering a se-quence of small deformation transformations,each modeled by a linear elastic model.The problem was symmetrized by consid-ering a periodic sequence of images where thefirst(or last)and middle image are the source and target respectively.The sym-metric objective function thus comprised terms that quantify the difference between any two successive pairs of images.The in-ferred incremental transformation maps were concatenated to map one input image to another.b)Nonlinear Models:An important limitation of linear elastic models lies in their inability to cope with large defor-mations.In order to account for large deformations,nonlinear elastic models have been proposed.These models also guar-antee the preservation of topology.Rabbitt et al.[22]modeled the deformable image based on hyperelastic material properties.The solution of the nonlinear equations was achieved by local linearization and the use of the Finite Element method.Pennec et al.[23]dropped the linearity assumption by mod-eling the deformation process through the St Venant-Kirchoff elasticity energy that extends the linear elastic model to the non-linear regime.Moreover,the use of log-Euclidean metrics in-stead of Euclidean ones resulted in a Riemannian elasticity en-ergy which is inverse consistent.Yanovsky et al.[24]proposed a symmetric registration framework based on the St Venant-Kir-choff elasticity.An auxiliary variable was added to decouple the regularization and the matching term.Symmetry was im-posed by assuming that the Jacobian determinants of the defor-mation follow a zero mean,after log-transformation,log-normal distribution[25].Droske and Rumpf[26]used an hyperelastic,polyconvex regularization term that takes into account the length,area and volume deformations.Le Guyader and Vese[27]presented an approach that combines segmentation and registration that is based on nonlinear elasticity.The authors used a polyconvex regularization energy based on the modeling of the images under deformation as Ciarlet-Geymonat materials[28].Burger et al.[29]also used a polyconvex regularization term.The au-thors focused on the numerical implementation of the registra-tion framework.They employed a discretize-then-optimize ap-proach[9]that involved the partitioning voxels to24tetrahedra.2)Viscous Fluid Flow Models:In this case,the image under deformation is modeled as a viscousfluid.The transformation is governed by the Navier-Stokes equation that is simplified by assuming a very low Reynold’s numberflow(3) These models do not assume small deformations,and thus are able to recover large deformations[30].Thefirst term of theSOTIRAS et al.:DEFORMABLE MEDICAL IMAGE REGISTRATION:A SURVEY1157Navier-Stokes equation(3),constrains neighboring points to de-form similarly by spatially smoothing the velocityfield.The velocityfield is related to the displacementfield as.The velocityfield is integrated in order to estimate the displacementfield.The second term al-lows structures to change in mass while and are the vis-cosity coefficients.Christensen et al.[30]modeled the image under deformation as a viscousfluid allowing for large magnitude nonlinear defor-mations.The PDE was solved for small time intervals and the complete solution was given by an integration over time.For each time interval a successive over-relaxation(SOR)scheme was used.To guarantee the preservation of topology,the Jaco-bian was monitored and each time its value fell under0.5,the deformed image was regridded and a new one was generated to estimate a transformation.Thefinal solution was the con-catenation of all successive transformations occurring for each regridding step.In a subsequent work,Christensen et al.[31] presented a hierarchical way to recover the transformations for brain anatomy.Initially,global affine transformation was per-formed followed by a landmark transformation model.The re-sult was refined byfluid transformation preceded by an elastic registration step.An important drawback of the earliest implementations of the viscousfluid models,that employed SOR to solve the equa-tions,was computational inefficiency.To circumvent this short-coming,Christensen et al.employed a massive parallel com-puter implementation in[30].Bro-Nielsen and Gramkow[32] proposed a technique based on a convolutionfilter in scale-space.Thefilter was designed as the impulse response of the linear operator defined in its eigen-function basis.Crun et al.[33]proposed a multi-grid approach towards handling anisotropic data along with a multi-resolution scheme opting forfirst recovering coarse velocity es-timations and refining them in a subsequent step.Cahill et al.[34]showed how to use Fourier methods to efficiently solve the linear PDE system that arises from(3)for any boundary condi-tion.Furthermore,Cahill et al.extended their analysis to show how these methods can be applied in the case of other regu-larizers(diffusion,curvature and elastic)under Dirichlet,Neu-mann,or periodic boundary conditions.Wang and Staib[35]usedfluid deformation models in an atlas-enhanced registration setting while D’Agostino et al. tackled multi-modal registration with the use of such models in[36].More recently,Chiang et al.[37]proposed an inverse consistent variant offluid registration to register Diffusion Tensor images.Symmetrized Kullback-Leibler(KL)diver-gence was used as the matching criterion.Inverse consistency was achieved by evaluating the matching and regularization criteria towards both directions.3)Diffusion Models:In this case,the deformation is mod-eled by the diffusion equation(4) Let us note that most of the algorithms,based on this transforma-tion model and described in this section,do not explicitly state the(4)in their objective function.Nonetheless,they exploit the fact that the Gaussian kernel is the Green’s function of the diffu-sion equation(4)(under appropriate initial and boundary condi-tions)to provide an efficient regularization step.Regularization is efficiently performed through convolutions with a Gaussian kernel.Thirion,inspired by Maxwell’s Demons,proposed to perform image matching as a diffusion process[38].The proposed algo-rithm iterated between two steps:1)estimation of the demon forces for every demon(more precisely,the result of the appli-cation of a force during one iteration step,that is a displace-ment),and2)update of the transformation based on the cal-culated forces.Depending on the way the demon positions are selected,the way the space of deformations is defined,the in-terpolation method that is used,and the way the demon forces are calculated,different variants can be obtained.The most suit-able version for medical image analysis involved1)selecting all image elements as demons,2)calculating demon forces by considering the opticalflow constraint,3)assuming a nonpara-metric deformation model that was regularized by applying a Gaussianfilter after each iteration,and4)a trilinear interpo-lation scheme.The Gaussianfilter can be applied either to the displacementfield estimated at an iteration or the updated total displacementfield.The bijectivity of the transformation was en-sured by calculating for every point the difference between its initial position and the one that is reached after composing the forward with the backward deformationfield,and redistributing the difference to eachfield.The bijectivity of the transformation can also be enforced by limiting the maximum length of the up-date displacement to half the voxel size and using composition to update the transformation.Variants for the contour-based reg-istration and the registration between segmented images were also described in[38].Most of the algorithms described in this section were inspired by the work of Thirion[38]and thus could alternatively be clas-sified as“Demons approaches.”These methods share the iter-ative approach that was presented in[38]that is,iterating be-tween estimating the displacements and regularizing to obtain the transformation.This iterative approach results in increased computational efficiency.As it will be discussed later in this section,this feature led researchers to explore such strategies for different PDEs.The use of Demons,as initially introduced,was an efficient algorithm able to provide dense correspondences but lacked a sound theoretical justification.Due to the success of the algo-rithm,a number of papers tried to give theoretical insight into its workings.Fischer and Modersitzki[39]provided a fast algo-rithm for image registration.The result was given as the solution of linear system that results from the linearization of the diffu-sion PDE.An efficient scheme for its solution was proposed while a connection to the Thirion’s Demons algorithm[38]was drawn.Pennec et al.[40]studied image registration as an energy minimization problem and drew the connection of the Demons algorithm with gradient descent schemes.Thirion’s image force based on opticalflow was shown to be equivalent with a second order gradient descent on the Sum of Square Differences(SSD) matching criterion.As for the regularization,it was shown that the convolution of the global transformation with a Gaussian。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
640
D. Loeckx et al.
whose goal is to minimise a cost function, consisting of a first term that characterises the similarity between both images and a second term that regularises the transformation and/or penalties improbable or impossible deformations. The first term is the driving force behind the registration process and aims to maximise the similarity between the two images. The second term, which is often referred to as the regularisation or penalty term, constrains the transformation between the source and target images to avoid impossible or improbable transformations. In current literature, the penalty term is often expressed as a global energy term that imposes deformation smoothness by modelling the deforming image as a thin plate [2] or membrane [3]. However, in some applications there is a need to explicitly impose the constraint that some structures in the images to be registered should be treated as rigid objects that do not deform and can only be displaced between both images without changing shape. This is the case for instance with bony structures or contrast-enhancing lesions in intra-subject registration of pre- and post contrast images, e.g. for CT subtraction angiography. Several authors have presented different approaches for incorporating local rigidity constraints in non-rigid image registration. Tanner et al. [4] proposed a solution that locally couples the control points of a B-spline free-form deformation field such as to make the transformation rigid within the specified image region of interest. Little et al. [5] incorporate independent rigid objects in a modified thin-plate spline nonrigid registration. Both approaches require explicit identification of the rigid structures prior to or during registration. Also, they enforce the considered structures to be totally rigid, even in cases where they actually might have deformed slightly. Rohlfing et al. [6] proposed a penalty term that imposes local tissue incompressibility and volume preservation overall in the image without need for segmentation, by constraining the local Jacobian determinant to be close to unity everywhere in the image. In this paper, we extend the approach of Rohlfing et al. [6] and propose a new penalty term that punishes transformations that are not locally equivalent to a rigid transformation by imposing the local Jacobian matrix to be orthogonal. Local rigidity is controlled by a spatially varying weight factor that depends on tissue type, such that the proposed rigidity constraint can be tuned locally and tailored to the problem at hand.
Medical Image Computing (Radiology–ESAT/PSI), Faculties of Medicine and Engineering, University Hospital Gasthuisberg, Herestraat 49, B-3000 Leuven, Belgium. Dirk.Loeckx@uz.kuleuven.ac.be
Nonrigid Image Registration Using Free-Form Deformations with a Local Rigidity Constraint
Dirk Loeckx, Frederik Maes , Dirk Vandermeulen, aБайду номын сангаасd Paul Suetens
Abstract. Voxel-based nonrigid image registration can be formulated as an optimisation problem whose goal is to minimise a cost function, consisting of a first term that characterises the similarity between both images and a second term that regularises the transformation and/or penalties improbable or impossible deformations. Within this paper, we extend previous works on nonrigid image registration by the introduction of a new penalty term that expresses the local rigidity of the deformation. A necessary and sufficient condition for the transformation to be locally rigid at a particular location is that its Jacobian matrix JT at this location is orthogonal, satisfying the orthogonality condition JT JT T = 1. So we define the penalty term as the weighted integral of the Frobenius norm of JT JT T − 1 integrated over the overlap of the images to be registered. We fit the implementation of the penalty term in a multidimensional, continuous and differentiable B-spline deformation framework and analytically determine the derivative of the similarity criterion and the penalty term with respect to the deformation parameters. We show results of the impact of the proposed rigidity constraint on artificial and clinical images demonstrating local shape preservation with the proposed constraint.
Frederik Maes is Postdoctoral Fellow of the Fund for Scientific Research - Flanders (FWO-Vlaanderen, Belgium).
