外文资料翻译_基于ASP校园论坛毕业设计_相关外文资料
ASP(计算机专业)外文翻译

英文原文The Active Server Pages( ASP) is a server to carry the script plait writes the environment, using it can create to set up with circulate the development, alternant Web server application procedure. Using the ASP cans combine the page of HTML, script order to create to set up the alternant the page of Web with the module of ActiveX with the mighty and applied procedure in function that according to Web. The applied procedure in ASP develops very easily with modify.The HTML plait writes the personnel if you are a simple method that a HTML plait writes the personnel, you will discover the script of ASP providing to create to have diplomatic relation with each other page. If you once want that collect the data from the form of HTML, or use the name personalization HTML document of the customer, or according to the different characteristic in different usage of the browser, you will discover ASP providing an outstanding solution. Before, to think that collect the data from the form of HTML, have to study a plait distance language to create to set up a CGI application procedure. Now, you only some simple instruction into arrive in your HTML document, can collect from the form the data combine proceeding analysis. You need not study the complete plait distance language again or edit and translate the procedure to create to have diplomatic relation alone with each other page.Along with control to use the ASP continuously with the phonetic technique in script, you can create to set up the more complicated script. For the ASP, you can then conveniently usage ActiveX module to carry out the complicated mission, link the database for example with saving with inspectional information.If you have controlled a script language, such as VBScript, JavaScript or PERL, and you have understood the method that use the ASP.As long as installed to match the standard cowgirl in the script of ActiveX script engine, can use in the page of ASP an any a script language. Does the ASP take the Microsoft? Visual Basic? Scripting Edition ( VBScript) with Microsoft? Script? Of script engine, like this you can start the editor script immediately. PERL, REXX with Python ActiveX script engine can from the third square develops the personnel acquires. The Web develops thepersonnel if you have controlled a plait distance language, such as Visual Basic, you will discover the ASP creates a very vivid method that set up the Web application procedure quickly. Pass to face to increase in the HTML the script order any, you can create the HTML that set up the applied procedure connects. Pass to create to set up own the module of ActiveX, can will apply the business in the procedure logic seal to pack and can adjust from the script, other module or from the other procedure the mold piece that use.The usage ASP proceeds the calculating Web can convert into the visible benefits, it can make the supplier of Web provide the alternant business application but not only is to announce the contents. For example, the travel agency can compare the announcement aviation schedule makes out more; Using the script of ASP can let the customer inspect the current service, comparison expenses and prepare to book seats.Include too can lower in the Windows NT Option Microsoft in the pack Transaction Server ( MTS) on the server complexity of constructing the procedure with expenses. The MTS can resolve to develop those confidentialities strong, can ratings of and the dependable Web applies the complexity problem of the procedure. Active Server Pages modelThe browser requests from the server of Web. Hour of asp document, the script of ASP starts circulating. Then the server of Web adjusts to use the ASP, the ASP reads completely the document of the claim, carry out all scripts order any, combining to deliver the page of Web to browser.Because script is on the server but is not at the customer to carry the movement, deliver the page of Web on the browser is on the Web server born. Combining to deliver the standard HTML to browser. Because only the result that there is script returns the browser, so the server carries the not easy replication in script. The customer cans not see to create to set up them at script order that the page that view.We introduce the Basic form of the database language known as SQL, a language that allows us to query and manipulate data on computerized relational database systems. SQL has been the lingua franca for RDBMS since the early 1980s, and it is of fundamental importance for many of the concepts presented in this text. The SQLlanguage is currently in transition from the relational form (the ANSI SQL –92 standard) to a newer object-relational form (ANSI SQL -99, which was released in 1999). SQL-99 should be thought of as extending SQL-92, not changing any of the earlier valid language. Usually, the basic SQL we define matches most closely the ANSI SQL standards basic subsets, called Entry SQL -92 and core SQL-99 that are commonly implemented; our touchstone in defining basic SQL is to provide a syntax that is fully available on most of the major RDBMS products[7].We begin with an overview of SQL capabilities, and then we explain something about the multiple SQL standards and dialects and how we will deal with these in our presentation.We will learn how to pose comparable queries in SQL, using a form known as the Select statement. As we will see, the SQL select statement offers more flexibility in a number of ways than relational algebra for posing queries. However, there is no fundamental improvement in power, nothing that could not be achieved in relational algebra , given a few well-considered extensions. For this reason, experience with relational algebra gives us a good idea of what can be accomplished in SQL. At the same time, SQL and relational algebra have quite different conceptual models in a number of respects, and the insight drawn from familiarity with the relational algebra approach may enhance your understanding of SQL capabilities.The most important new feature you will encounter with SQL is the ability to pose queries interactively in a computerized environment. The SQL select statement is more complicated and difficult to master than the relatively simple relational algebra, but you should never feel list or uncertain as long as you have access to computer facilities where a few experiments can clear up uncertainties about SQL use. The interactive SQL environment discussed in the current chapter allows you to type a query on a monitor screen and get an immediate answer. Such interactive queries are sometimes called ad box queries. This term refers to the fact that an SQL select statement is meant to be composed all at once in a few type written lines and not be dependent on any prior interaction in a user session. The feature of not being dependent on prior interaction is also down as non-procedurality. SQL differs in this way even from relational algebra, where a prior alias statement might be needed inorder to represent a product of a table with itself. The difference between SQL and procedural languages such as java or c is profound: you do not need to write a program to try out an SQL query, you just have to type the relatively short, self-contained text of the query and submit it .Of course, an SQL query can be rather complex . A limited part of this full form, know as a sub-query, is defined recursively, and the full select statement form has one added clause. You should not feel intimidated by the complexity of the select statement, however. The fact that a select statement is non-procedural means that it has a lot in common with a menu driven application, where a user is expected to fill in some set of choices from a menu and then press the enter key to execute the menu choices all at once. The various clauses of the select statement correspond to menu choices: you will occasionally need all these clauses, but on not expect to use all of them every time you pose a query.Observed reliability depends on the context in which the system s used. As discussed already, the system environment cannot be specified in advance nor can the system designers place restrictions on that environment for operational systems. Different systems in an environment may react to problems in unpredictable ways, thus affecting the reliability of all of these systems. There for, even when the system has been integrated, it may be difficult to make accurate measurements of its reliability.Visual Basic Database Access prospectsWith the recent Web application software and the rapid development of the existing data stored in diverse forms, Visual Basic Database Access Solutions faces such as rapid extraction enterprises located in the internal and external business information with the multiple challenges. To this end Microsoft, a new database access strategy "unified data access" (UniversalDataAccess) strategy. "Unified data access" to provide high-performance access, including relational and non-relational data in a variety of sources, provide independent in the development of language development tools and the simple programming interface, these technologies makes enterprise integration of multiple data sources, better choice of development tools, application software, operating platforms, and will establish a maintenance easysolution possible.汉语翻译Active Server Pages(ASP)是服务器端脚本编写环境,使用它可以创建和运行动态、交互的Web 服务器应用程序。
毕业设计外文翻译_英文版

A Design and Implementation of Active NetworkSocket ProgrammingK.L. Eddie Law, Roy LeungThe Edward S. Rogers Sr. Department of Electrical and Computer EngineeringUniversity of TorontoToronto, Canadaeddie@, roy.leung@utoronto.caAbstract—The concept of programmable nodes and active networks introduces programmability into communication networks. Code and data can be sent and modified on their ways to destinations. Recently, various research groups have designed and implemented their own design platforms. Each design has its own benefits and drawbacks. Moreover, there exists an interoperability problem among platforms. As a result, we introduce a concept that is similar to the network socket programming. We intentionally establish a set of simple interfaces for programming active applications. This set of interfaces, known as Active Network Socket Programming (ANSP), will be working on top of all other execution environments in future. Therefore, the ANSP offers a concept that is similar to “write once, run everywhere.” It is an open programming model that active applications can work on all execution environments. It solves the heterogeneity within active networks. This is especially useful when active applications need to access all regions within a heterogeneous network to deploy special service at critical points or to monitor the performance of the entire networks. Instead of introducing a new platform, our approach provides a thin, transparent layer on top of existing environments that can be easily installed for all active applications.Keywords-active networks; application programming interface; active network socket programming;I. I NTRODUCTIONIn 1990, Clark and Tennenhouse [1] proposed a design framework for introducing new network protocols for the Internet. Since the publication of that position paper, active network design framework [2, 3, 10] has slowly taken shape in the late 1990s. The active network paradigm allows program code and data to be delivered simultaneously on the Internet. Moreover, they may get executed and modified on their ways to their destinations. At the moment, there is a global active network backbone, the ABone, for experiments on active networks. Apart from the immaturity of the executing platform, the primary hindrance on the deployment of active networks on the Internet is more on the commercially related issues. For example, a vendor may hesitate to allow network routers to run some unknown programs that may affect their expected routing performance. As a result, alternatives were proposed to allow active network concept to operate on the Internet, such as the application layer active networking (ALAN) project [4] from the European research community. In the ALAN project, there are active server systems located at different places in the networks and active applications are allowed to run in these servers at the application layer. Another potential approach from the network service provider is to offer active network service as the premium service class in the networks. This service class should provide the best Quality of Service (QoS), and allow the access of computing facility in routers. With this approach, the network service providers can create a new source of income.The research in active networks has been progressing steadily. Since active networks introduce programmability on the Internet, appropriate executing platforms for the active applications to execute should be established. These operating platforms are known as execution environments (EEs) and a few of them have been created, e.g., the Active Signaling Protocol (ASP) [12] and the Active Network Transport System (ANTS) [11]. Hence, different active applications can be implemented to test the active networking concept.With these EEs, some experiments have been carried out to examine the active network concept, for example, the mobile networks [5], web proxies [6], and multicast routers [7]. Active networks introduce a lot of program flexibility and extensibility in networks. Several research groups have proposed various designs of execution environments to offer network computation within routers. Their performance and potential benefits to existing infrastructure are being evaluated [8, 9]. Unfortunately, they seldom concern the interoperability problems when the active networks consist of multiple execution environments. For example, there are three EEs in ABone. Active applications written for one particular EE cannot be operated on other platforms. This introduces another problem of resources partitioning for different EEs to operate. Moreover, there are always some critical network applications that need to run under all network routers, such as collecting information and deploying service at critical points to monitor the networks.In this paper, a framework known as Active Network Socket Programming (ANSP) model is proposed to work with all EEs. It offers the following primary objectives.• One single programming interface is introduced for writing active applications.• Since ANSP offers the programming interface, the design of EE can be made independent of the ANSP.This enables a transparency in developing andenhancing future execution environments.• ANSP addresses the interoperability issues among different execution environments.• Through the design of ANSP, the pros and cons of different EEs will be gained. This may help design abetter EE with improved performance in future.The primary objective of the ANSP is to enable all active applications that are written in ANSP can operate in the ABone testbed . While the proposed ANSP framework is essential in unifying the network environments, we believe that the availability of different environments is beneficial in the development of a better execution environment in future. ANSP is not intended to replace all existing environments, but to enable the studies of new network services which are orthogonal to the designs of execution environments. Therefore, ANSP is designed to be a thin and transparent layer on top of all execution environments. Currently, its deployment relies on automatic code loading with the underlying environments. As a result, the deployment of ANSP at a router is optional and does not require any change to the execution environments.II. D ESIGN I SSUES ON ANSPThe ANSP unifies existing programming interfaces among all EEs. Conceptually, the design of ANSP is similar to the middleware design that offers proper translation mechanisms to different EEs. The provisioning of a unified interface is only one part of the whole ANSP platform. There are many other issues that need to be considered. Apart from translating a set of programming interfaces to other executable calls in different EEs, there are other design issues that should be covered, e.g., • a unified thread library handles thread operations regardless of the thread libraries used in the EEs;• a global soft-store allows information sharing among capsules that may execute over different environmentsat a given router;• a unified addressing scheme used across different environments; more importantly, a routing informationexchange mechanism should be designed across EEs toobtain a global view of the unified networks;• a programming model that should be independent to any programming languages in active networks;• and finally, a translation mechanism to hide the heterogeneity of capsule header structures.A. Heterogeneity in programming modelEach execution environment provides various abstractions for its services and resources in the form of program calls. The model consists of a set of well-defined components, each of them has its own programming interfaces. For the abstractions, capsule-based programming model [10] is the most popular design in active networks. It is used in ANTS [11] and ASP [12], and they are being supported in ABone. Although they are developed based on the same capsule model, their respective components and interfaces are different. Therefore, programs written in one EE cannot run in anther EE. The conceptual views of the programming models in ANTS and ASP are shown in Figure 1.There are three distinct components in ANTS: application, capsule, and execution environment. There exist user interfaces for the active applications at only the source and destination routers. Then the users can specify their customized actions to the networks. According to the program function, the applications send one or more capsules to carry out the operations. Both applications and capsules operate on top of an execution environment that exports an interface to its internal programming resources. Capsule executes its program at each router it has visited. When it arrives at its destination, the application at destination may either reply it with another capsule or presents this arrival event to the user. One drawback with ANTS is that it only allows “bootstrap” application.Figure 1. Programming Models in ASP and ANTS.In contrast, ASP does not limit its users to run “bootstrap” applications. Its program interfaces are different from ANTS, but there are also has three components in ASP: application client, environment, and AAContext. The application client can run on active or non-active host. It can start an active application by simply sending a request message to the EE. The client presents information to users and allows its users to trigger actions at a nearby active router. AAContext is the core of the network service and its specification is divided into two parts. One part specifies its actions at its source and destination routers. Its role is similar to that of the application in ANTS, except that it does not provide a direct interface with the user. The other part defines its actions when it runs inside the active networks and it is similar to the functional behaviors of a capsule in ANTS.In order to deal with the heterogeneity of these two models, ANSP needs to introduce a new set of programming interfaces and map its interfaces and execution model to those within the routers’ EEs.B. Unified Thread LibraryEach execution environment must ensure the isolation of instance executions, so they do not affect each other or accessThe authors appreciate the Nortel Institute for Telecommunications (NIT) at the University of Toronto to allow them to access the computing facilitiesothers’ information. There are various ways to enforce the access control. One simple way is to have one virtual machine for one instance of active applications. This relies on the security design in the virtual machines to isolate services. ANTS is one example that is using this method. Nevertheless, the use of multiple virtual machines requires relatively large amount of resources and may be inefficient in some cases. Therefore, certain environments, such as ASP, allow network services to run within a virtual machine but restrict the use of their services to a limited set of libraries in their packages. For instance, ASP provides its thread library to enforce access control. Because of the differences in these types of thread mechanism, ANSP devises a new thread library to allow uniform accesses to different thread mechanisms.C. Soft-StoreSoft-store allows capsule to insert and retrieve information at a router, thus allowing more than one capsules to exchange information within a network. However, problem arises when a network service can execute under different environments within a router. The problem occurs especially when a network service inserts its soft-store information in one environment and retrieves its data at a later time in another environment at the same router. Due to the fact that execution environments are not allowed to exchange information, the network service cannot retrieve its previous data. Therefore, our ANSP framework needs to take into account of this problem and provides soft-store mechanism that allows universal access of its data at each router.D. Global View of a Unified NetworkWhen an active application is written with ANSP, it can execute on different environment seamlessly. The previously smaller and partitioned networks based on different EEs can now be merging into one large active network. It is then necessary to advise the network topology across the networks. However, different execution environments have different addressing schemes and proprietary routing protocols. In order to merge these partitions together, ANSP must provide a new unified addressing scheme. This new scheme should be interpretable by any environments through appropriate translations with the ANSP. Upon defining the new addressing scheme, a new routing protocol should be designed to operate among environments to exchange topology information. This allows each environment in a network to have a complete view of its network topology.E. Language-Independent ModelExecution environment can be programmed in any programming language. One of the most commonly used languages is Java [13] due to its dynamic code loading capability. In fact, both ANTS and ASP are developed in Java. Nevertheless, the active network architecture shown in Figure 2 does not restrict the use of additional environments that are developed in other languages. For instance, the active network daemon, anted, in Abone provides a workspace to execute multiple execution environments within a router. PLAN, for example, is implemented in Ocaml that will be deployable on ABone in future. Although the current active network is designed to deploy multiple environments that can be in any programming languages, there lacks the tool to allow active applications to run seamlessly upon these environments. Hence, one of the issues that ANSP needs to address is to design a programming model that can work with different programming languages. Although our current prototype only considers ANTS and ASP in its design, PLAN will be the next target to address the programming language issue and to improve the design of ANSP.Figure 2. ANSP Framework Model.F. Heterogeneity of Capsule Header StructureThe structures of the capsule headers are different in different EEs. They carries capsule-related information, for example, the capsule types, sources and destinations. This information is important when certain decision needs to be made within its target environment. A unified model should allow its program code to be executed on different environments. However, the capsule header prevents different environments to interpret its information successfully. Therefore, ANSP should carry out appropriate translation to the header information before the target environment receives this capsule.III. ANSP P ROGRAMMING M ODELWe have outlined the design issues encountered with the ANSP. In the following, the design of the programming model in ANSP will be discussed. This proposed framework provides a set of unified programming interfaces that allows active applications to work on all execution environments. The framework is shown in Figure 2. It is composed of two layers integrated within the active network architecture. These two layers can operate independently without the other layer. The upper layer provides a unified programming model to active applications. The lower layer provides appropriate translation procedure to the ANSP applications when it is processed by different environments. This service is necessary because each environment has its own header definition.The ANSP framework provides a set of programming calls which are abstractions of ANSP services and resources. A capsule-based model is used for ANSP, and it is currently extended to map to other capsule-based models used in ANTSand ASP. The mapping possibility to other models remains as our future works. Hence, the mapping technique in ANSP allows any ANSP applications to access the same programming resources in different environments through a single set of interfaces. The mapping has to be done in a consistent and transparent manner. Therefore, the ANSP appears as an execution environment that provides a complete set of functionalities to active applications. While in fact, it is an overlay structure that makes use of the services provided from the underlying environments. In the following, the high-level functional descriptions of the ANSP model are described. Then, the implementations will be discussed. The ANSP programming model is based upon the interactions between four components: application client , application stub , capsule , and active service base.Figure 3. Information Flow with the ANSP.•Application Client : In a typical scenario, an active application requires some means to present information to its users, e.g., the state of the networks. A graphical user interface (GUI) is designed to operate with the application client if the ANSP runs on a non-active host.•Application Stub : When an application starts, it activates the application client to create a new instance of application stub at its near-by active node. There are two responsibilities for the application stub. One of them is to receive users’ instructions from the application client. Another one is to receive incoming capsules from networks and to perform appropriate actions. Typically, there are two types of actions, thatare, to reply or relay in capsules through the networks, or to notify the users regarding the incoming capsule. •Capsule : An active application may contain several capsule types. Each of them carries program code (also referred to as forwarding routine). Since the application defines a protocol to specify the interactions among capsules as well as the application stubs. Every capsule executes its forwarding routine at each router it visits along the path between the source and destination.•Active Service Base : An active service base is designed to export routers’ environments’ services and execute program calls from application stubs and capsules from different EEs. The base is loaded automatically at each router whenever a capsule arrives.The interactions among components within ANSP are shown in Figure 3. The designs of some key components in the ANSP will be discussed in the following subsections. A. Capsule (ANSPCapsule)ANSPXdr decode () ANSPXdr encode () int length ()Boolean execute ()New types of capsule are created by extending the abstract class ANSPCapsule . New extensions are required to define their own forwarding routines as well as their serialization procedures. These methods are indicated below:The execution of a capsule in ANSP is listed below. It is similar to the process in ANTS.1. A capsule is in serial binary representation before it issent to the network. When an active router receives a byte sequence, it invokes decode() to convert the sequence into a capsule. 2. The router invokes the forwarding routine of thecapsule, execute(). 3. When the capsule has finished its job and forwardsitself to its next hop by calling send(), this call implicitly invokes encode() to convert the capsule into a new serial byte representation. length() isused inside the call of encode() to determine the length of the resulting byte sequence. ANSP provides a XDR library called ANSPXdr to ease the jobs of encoding and decoding.B. Active Service Base (ANSPBase)In an active node, the Active Service Base provides a unified interface to export the available resources in EEs for the rest of the ANSP components. The services may include thread management, node query, and soft-store operation, as shown in Table 1.TABLE I. ACTIVE SERVICE BASE FUNCTION CALLSFunction Definition Descriptionboolean send (Capsule, Address) Transmit a capsule towards its destination using the routing table of theunderlying environment.ANSPAddress getLocalHost () Return address of the local host as an ANSPAddress structure. This isuseful when a capsule wants to check its current location.boolean isLocal (ANSPAddress) Return true if its input argument matches the local host’s address andreturn false otherwise.createThread () Create a new thread that is a class ofANSPThreadInterface (discussed later in Section VIA “Unified Thread Abstraction”).putSStore (key, Object) Object getSStore (key) removeSStore (key)The soft-store operations are provided by putSStore(), getSSTore(), and removeSStore(), and they put, retrieve, and remove data respectively. forName (PathName) Supported in ANSP to retrieve a classobject corresponding to the given path name in its argument. This code retrieval may rely on the code loading mechanism in the environment whennecessary.C. Application Client (ANSPClient)boolean start (args[])boolean start (args[],runningEEs) boolean start (args[],startClient)boolean start (args[],startClient, runningEE)Application Client is an interface between users and the nearby active source router. It does the following responsibilities.1. Code registration: It may be necessary to specify thelocation and name of the application code in some execution environments, e.g., ANTS. 2. Application initialization: It includes selecting anexecution environment to execute the application among those are available at the source router. Each active application can create an application client instance by extending the abstract class, ANSPClient . The extension inherits a method, start(), to automatically handle both the registration and initialization processes. All overloaded versions of start() accept a list of arguments, args , that are passed to the application stub during its initialization. An optional argument called runningEEs allows an application client to select a particular set of environment variables, specified by a list of standardized numerical environment ID, the ANEP ID, to perform code registration. If this argument is not specified, the default setting can only include ANTS and ASP. D. Application Stub (ANSPApplication)receive (ANSPCapsule)Application stubs reside at the source and destination routers to initialize the ANSP application after the application clients complete the initialization and registration processes. It is responsible for receiving and serving capsules from the networks as well as actions requested from the clients. A new instance is created by extending the application client abstract class, ANSPApplication . This extension includes the definition of a handling routine called receive(), which is invoked when a stub receives a new capsule.IV. ANSP E XAMPLE : T RACE -R OUTEA testbed has been created to verify the design correctnessof ANSP in heterogeneous environments. There are three types of router setting on this testbed:1. Router that contains ANTS and a ANSP daemonrunning on behalf of ASP; 2. Router that contains ASP and a ANSP daemon thatruns on behalf of ANTS; 3. Router that contains both ASP and ANTS.The prototype is written in Java [11] with a traceroute testing program. The program records the execution environments of all intermediate routers that it has visited between the source and destination. It also measures the RTT between them. Figure 4 shows the GUI from the application client, and it finds three execution environments along the path: ASP, ANTS, and ASP. The execution sequence of the traceroute program is shown in Figure 5.Figure 4. The GUI for the TRACEROUTE Program.The TraceCapsule program code is created byextending the ANSPCapsule abstract class. When execute() starts, it checks the Boolean value of returning to determine if it is returning from the destination. It is set to true if TraceCapsule is traveling back to the source router; otherwise it is false . When traveling towards the destination, TraceCapsule keeps track of the environments and addresses of the routers it has visited in two arrays, path and trace , respectively. When it arrives at a new router, it calls addHop() to append the router address and its environment to these two arrays. When it finally arrives at the destination, it sets returning to false and forwards itself back to the source by calling send().When it returns to source, it invokes deliverToApp() to deliver itself to the application stub that has been running at the source. TraceCapsule carries information in its data field through the networks by executing encode() and decode(), which encapsulates and de-capsulates its data using External Data Representation (XDR) respectively. The syntax of ANSP XDR follows the syntax of XDR library from ANTS. length() in TraceCapsule returns the data length, or it can be calculated by using the primitive types in the XDRlibrary.Figure 5. Flow of the TRACEROUTE Capsules.V. C ONCLUSIONSIn this paper, we present a new unified layered architecture for active networks. The new model is known as Active Network Socket Programming (ANSP). It allows each active application to be written once and run on multiple environments in active networks. Our experiments successfully verify the design of ANSP architecture, and it has been successfully deployed to work harmoniously with ANTS and ASP without making any changes to their architectures. In fact, the unified programming interface layer is light-weighted and can be dynamically deployable upon request.R EFERENCES[1] D.D. Clark, D.L. Tennenhouse, “Architectural Considerations for a NewGeneration of Protocols,” in Proc. ACM Sigcomm’90, pp.200-208, 1990. [2] D. Tennenhouse, J. M. Smith, W. D. Sicoskie, D. J. Wetherall, and G. J.Minden, “A survey of active network research,” IEEE Communications Magazine , pp. 80-86, Jan 1997.[3] D. Wetherall, U. Legedza, and J. Guttag, “Introducing new internetservices: Why and how,” IEEE Network Magazine, July/August 1998. [4] M. Fry, A. Ghosh, “Application Layer Active Networking,” in ComputerNetworks , Vol.31, No.7, pp.655-667, 1999.[5] K. W. Chin, “An Investigation into The Application of Active Networksto Mobile Computing Environments”, Curtin University of Technology, March 2000.[6] S. Bhattacharjee, K. L. Calvert, and E. W. Zegura, “Self OrganizingWide-Area Network Caches”, Proc. IEEE INFOCOM ’98, San Francisco, CA, 29 March-2 April 1998.[7] L. H. Leman, S. J. Garland, and D. L. Tennenhouse, “Active ReliableMulticast”, Proc. IEEE INFOCOM ’98, San Francisco, CA, 29 March-2 April 1998.[8] D. Descasper, G. Parulkar, B. Plattner, “A Scalable, High PerformanceActive Network Node”, In IEEE Network, January/February 1999.[9] E. L. Nygren, S. J. Garland, and M. F. Kaashoek, “PAN: a high-performance active network node supporting multiple mobile code system”, In the Proceedings of the 2nd IEEE Conference on Open Architectures and Network Programming (OpenArch ’99), March 1999. [10] D. L. Tennenhouse, and D. J. Wetherall. “Towards an Active NetworkArchitecture”, In Proceeding of Multimedia Computing and Networking , January 1996.[11] D. J. Wetherall, J. V. Guttag, D. L. Tennenhouse, “ANTS: A toolkit forBuilding and Dynamically Deploying Network Protocols”, Open Architectures and Network Programming, 1998 IEEE , 1998 , Page(s): 117 –129.[12] B. Braden, A. Cerpa, T. Faber, B. Lindell, G. Phillips, and J. Kann.“Introduction to the ASP Execution Environment”: /active-signal/ARP/index.html .[13] “The java language: A white paper,” Tech. Rep., Sun Microsystems,1998.。
毕业论文-外文资料翻译[管理资料]
![毕业论文-外文资料翻译[管理资料]](https://img.taocdn.com/s3/m/b6d118d2192e45361166f5e2.png)
附件1:外文资料翻译译文数据库简介1.数据库管理系统(DBMS)。
众所周知,数据库是逻辑上相关的数据元的集合。
这些数据元可以按不同的结构组织起来,以满足单位和个人的多种处理和检索的需要。
数据库本身不是什么新鲜事——早期的数据库记录在石头上或写在名册上,以及写入索引卡中。
而现在,数据库普遍记录再可磁化的介质上,并且需要用计算机程序来执行必需的存储和检索操作。
在后文中你将看到除了简单的以外,所有数据库中都有复杂的数据关系及其连接。
处理与创建、访问以及维护数据库记录有关的复杂任务的系统软件包叫做数据库管理系统(DBMS)。
DBMS软件包中的程序在数据库极其用户间建立了接口(这些用户可以是应用程序员、管理员以及其他需要信息和各种操作系统的人员)。
DBMS可组织、处理和显示从数据库中选择的数据元。
该功能使决策者可以搜索、试探和查询数据库的内容,从而对在正式报告中没有的、不再出现的且无计划的问题作出回答。
这些问题最初可能是模糊的并且是定义不清的,但是人们可以浏览数据库直到获得问题的答案。
也就是说DBMS将“管理”存储的数据项,并从公共数据库中汇集所需的数据项以回答那些非程序员的询问。
在面向文件的系统中,需要特定信息的用户可以将他们的要求传送给程序员。
该程序员在时间允许时,将编写一个或多个程序以提取数据和准备信息。
但是,使用DBMS可为用户提供一种更快的、用户可以选择的通信方式。
顺序的、直接的以及其它的文件处理方式常用于单个文件中数据的组织和构造,而DBMS能够访问和检索非关键记录字段的数据,即DBMS能够将几个大文件中逻辑相关的数据组织并连接在一起。
逻辑结构。
确定这些逻辑关系是数据管理者的任务,由数据定义语言完成。
DBMS 在存储、访问和检索操作过程中可选用以下逻辑结构技术:(1)表结构。
在该逻辑方式中,记录通过指针链接在一起。
指针是记录中的一个数据项,它指出另一个逻辑相关的记录的存储位置,例如,顾客主文件的记录将包含每个顾客的姓名和地址,而且该文件中的每个记录都由一个帐号标识。
毕业论文外文翻译两篇

毕业论文外文翻译两篇篇一:毕业论文外文翻译外文资料翻译译文:概述是一个统一的Web开发模型,它包括您使用尽可能少的代码生成企业级Web应用程序所必需的各种服务。
作为.NETFramework的一部分提供。
当您编写应用程序的代码时,可以访问.NETFramework中的类。
您可以使用与公共语言运行库(CLR)兼容的任何语言来编写应用程序的代码,这些语言包括MicrosoftVisualBasic、C#、和J#。
使用这些语言,可以开发利用公共语言运行库、类型安全、继承等方面的优点的应用程序。
包括:∙页和控件框架∙编译器∙安全基础结构∙状态管理功能∙应用程序配置∙运行状况监视和性能功能∙调试支持∙XMLWebservices框架∙可扩展的宿主环境和应用程序生命周期管理∙可扩展的设计器环境页和控件框架是一种编程框架,它在Web服务器上运行,可以动态地生成和呈现网页。
可以从任何浏览器或客户端设备请求网页,会向请求浏览器呈现标记(例如HTML)。
通常,您可以对多个浏览器使用相同的页,因为会为发出请求的浏览器呈现适当的标记。
但是,您可以针对诸如MicrosoftInternetExplorer6的特定浏览器设计网页,并利用该浏览器的功能。
支持基于Web的设备(如移动电话、手持型计算机和个人数字助理(PDA))的移动控件。
网页是完全面向对象的。
在网页中,可以使用属性、方法和事件来处理HTML元素。
页框架为响应在服务器上运行的代码中的客户端事件提供统一的模型,从而使您不必考虑基于Web的应用程序中固有的客户端和服务器隔离的实现细节。
该框架还会在页处理生命周期中自动维护页及该页上控件的状态。
使用页和控件框架还可以将常用的UI功能封装成易于使用且可重用的控件。
控件只需编写一次,即可用于许多页并集成到网页中。
这些控件在呈现期间放入网页中。
页和控件框架还提供各种功能,以便可以通过主题和外观来控制网站的整体外观和感觉。
可以先定义主题和外观,然后在页面级或控件级应用这些主题和外观。
毕业设计外文资料翻译解析

理工学院毕业设计外文资料翻译专业:通信工程姓名:张聪学号: 13L0751243外文出处: Organic Electronics(用外文写)2017年3月4日附件: 1.外文资料翻译译文;2.外文原文。
有效激发复合体有机发光二极管与双极型受体1.介绍因为他们发现,如何有效地利用产生电三线态激子辐射衰变总是在研究领域最具挑战性的问题之一有机发光二极管(OLED)。
根据选择的规则推导出量子自旋统计,在有机半导体设备,只有1/4 产生电激子的分数的单重态可以利用辐射衰变,而其他3/4的三重态激子是浪费的无辐射衰变由于量子自旋禁止原则。
这个结果在理论上最大辐射激子比(gr)25%的常规荧光发射。
整合的策略有机金属荧光粉的发射器打破了自旋禁止原则的广泛证明理论单位gr由于自旋轨道耦合效应引起的重金属原子。
然而,稀有金属的高成本在有机金属化合物仍是商业的一大障碍与有机金属发射器OLED的应用。
连续的研究工作一直致力于发展不含金属的廉价有机发射器使用单线态的能力和三线态激子辐射衰变。
最近,关注一直在支付上变频机制通过三重态-三联体毁灭(TTA)或反向系统热激活穿越(RISC)方法来获得这个目标。
考虑到所有的电可以产生生成的三线态激子单重态,100%的理论最大gr是可能的OLED的包括热激活延迟荧光(TADF)发射器通过RISC过程,理论上最大gr的OLED包含TTA发射器是有限的为62.5%(25% + 75% / 2)。
这表明TADF化合物大大有有前途的潜在开发高效的OLED。
事实上,TADF 排放迅速发达,各种高效RGB和白色组成的OLED TADF gr发射器远高于25%的报告。
TADF过程,能量差之间单线态激发态(S1)和最低三重激发态(T1)排放应该最小化等于或小于热能在室温下(25兆电子伏),一旦三联体激子在TADF分子产生电场,他们可以很容易地产生辐射S1状态协助环境热能。
一个单位的内部量子效率的有机组成TADF 发射器是如此理论上可行。
ASP外文翻译+原文

ASP Banner Ad SystemTo the Reader from Joe: This is a user-submitted tutorial by the author above. I have read the tutorial and set the format to fit HTML Goodies, but for the most part have not changed the language. I chose this tutorial because many readers have been asking for more ASP tutorials. This is a great one.Sorry I cannot show you the event here. The HTML Goodies servers do not offer ASP. I will tell you though that if you run IE5.0 or better, open the contents of the zip file into a directory and it runs just fine.If you haven't already, you may want to read my introductory ASP tutorial before this one. If not, then enjoy.There may be a point in your web design career, where your site becomes real popular. That is when companies become interested in advertising on your site. A Banner Ad system can be built to control all those advertisements that you are so willing to display, for a price. Active Server Pages makes it very easy to create a banner ad system. So easy, that the Microsoft ASP developers created an "AdRotator" component for the occasion. Before you begin reading this article, make sure you download the support material below.The files included aread.txtbanner.asp3 banner imagesclicks.aspexample.aspredirect.aspad.txtIn order for the AdRotator component to work, you must configure a text file. This text file contains all the banner ad properties. However, The text file must follow a certain format. The first four lines are as follows:REDIRECT redirect.aspWIDTH 400HEIGHT 50*REDIRECTWhen a banner is clicked, the "AdRotator" component goes to a preliminary page. This page is called a redirect page. The redirect page handles any extra programming events before directing a user to the banners destination. In this example banner system, I called the preliminary file "redirect.asp".WIDTHThis sets the width of the banner ad image. The value must be in pixels.HEIGHTThis sets the height of the banner ad image. The value must be in pixels.*The asterisk tells the "AdRotator" component that it is about to acquire banner ad information. The asterisk is required.Once you define the general properties above the asterisk, then comes the list of banners to display. In the ad.txt file, there are three banners defined below the asterisk.banner1.jpg20banner2.jpg30banner3.jpg30Each banner requires four lines of properties, which follow the format below:Image filenameWeb AddressDescriptionBanner WeightImage FileThe image filename can be a fully qualified web address or relative name that points to the image. If the image is in a different folder, then you also include the folder name as well.(/banner1.jpg, banner1.jpg, or foldername/banner.jpg)>Web AddressThe web address can be a page on your site or a fully qualified web address that leads to another site.DescriptionThe description will be displayed as a tool tip. When you rest your mouse over the banner, the description pops up.Banner WeightThe banner weight determines how much a banner is displayed. The "AdRotator" component adds all of the banner weights and determines theprobability or percent chance of a particular banner being displayed. A banner with a higher weight has better a better probability.NOTE: You can disable a banners property by substituting with a dash. banner3.jpg-30The example entry above would create a banner ad that does not have a web address.Banner.aspThis file uses the "AdRotator" component and analyzes the contents of the ad.txt file. Below is the code.sub banner(strTarget)dim bannerad, htmlset bannerad = server.CreateObject("MSWC.adrotator")bannerad.TargetFrame = strTargethtml = bannerad.GetAdvertisement("ad.txt")Response.Write htmlend subThe first thing to note is that the ASP was written with VBScript. The second thing to note is that the code is written inside a sub procedure called banner(strTarget).For those of you who do not know, a sub procedure allows you to group together a bunch of code that can be reused over and over. Like a function, it takes an argument, such as a word or variable. In the code above the argument is strTarget.Unlike a function, a sub-procedure does not return any values, it just executes the code inside line by line.Inside the sub I declare two variables...dim bannerad, htmlNext I store the "AdRotator" component inside the "bannerad" variable. When storing a component inside a variable you use the set keyword. Since we are programming server-side with ASP, we use server.CreateObject to summon the component. "MSWC.adrotator" is the component key or name value.set bannerad = server.CreateObject("MSWC.adrotator")Next I use a property of the "AdRotator" called "TargetFrame". This property is equivalent to:html = bannerad.GetAdvertisement("ad.txt")Finally, I want to print the contents of the "html" variable. This prints the code that displays the banner images.Response.Write htmlRedirect.aspThis is the file that is processed before someone is redirected to the banners web address. Inside this file, we can capture information like how many times a particular banner is clicked and so on. To start things off, I defined a variable called "strUrl".Dim strUrlNext I store a querystring value inside this new variable.strUrl = Request.Querystring("url")A querystring is nothing more than a bunch of name/value pairs attached to a web address. When a user clicks on a banner, the "AdRotator" component attaches a querystring to the redirect file. So if we were to click banner1.jpg, defined in ad.txt, we would end up with a redirect web address that looks like so.Redirect.asp?url=&image=banner1.jpgIn essence assigning "Request.Querystring("url") to "strUrl", is the same as assigning to it.Finally, I check to see which banner was clicked. I accomplish this with the VBSCript inStr( ) function.if instr(strUrl, "htmlgoodies") thenApplication.Lockapplication("htmlgoodies") = application("htmlgoodies") + 1Application.UnLockResponse.ClearResponse.Redirect strUrlend ifThe inStr( ) function returns the number position of a sub-word (sub-string) within another word (string). The format is as followsInStr(main word, sub-word)If the sub-word exist within the main word, then the function will equal a number greater-than zero or true. If the sub-word does not exist, then the function will equal zero or false. In the example above, I check to see if "htmlgoodies" exist within . Since the answer is true, then the code inside the if... then... statement will execute.Inside the if... then... I use an application variable. An application variable is native to ASP. Application variables store information as long as a web application exist, a web application ceases to exist when say someone shuts off the web hosting server. The beauty of an application variable is that you can define it on one web page and use it in other web pages within your web application. The downfall is that the users computer must have cookies enabled.Anyways, the code adds one to the application variable, every time a banner is clicked. After one is added, the code redirects to the banners web page. So if banner1 was clicked then you shall be redirected to "".Response.Redirect strUrlExample.aspThis is an example page that uses the banner ad system. When you refresh the page, you should most likely see a different banner. Whenever you want to insert the banner ad on a page, you can use the SSI directive below...<!-- #include file="banner.asp" -->Once you include the file above, then you can call the sub-procedure inside the banner.asp file like so...Call banner("_blank")Notice that I supply one of the values for the "TargetFrame" as an argument. So if the banner is clicked, then the web page should open up in a separate browser window.Clicks.aspThis is a very simple page that displays the number of clicks per banner ad. To display the number of times a banner was clicked, you just print the contents of the application variables that were created inside "redirect.asp". Pretty nifty. <% =application("htmlgoodies") %>ASP横幅广告系统乔给读者的话:这是一个由用户提交上述笔者的教程。
毕业设计(论文)外文资料翻译

南京理工大学紫金学院毕业设计(论文)外文资料翻译系:机械工程系专业:机械工程及自动化姓名:徐华俊学号:100104348外文出处:WASTE FOOD DISPOSAL SYSTEM(3)(用外文写)附件:1.外文资料翻译译文;2.外文原文。
指导教师评语:该生翻译了一篇有关《废弃食物处理系统》的论文,论文内容跟课题的研究领域相关,在将来的课题设计中可以借鉴。
译文语句基本通顺,专业术语正确,标点符号运用无误。
说明该生具备一定的英语水平和翻译能力。
但文中仍有部分语句组织得不够完善,可以进一步修改。
签名:年月日注:请将该封面与附件装订成册。
附件1:外文资料翻译译文垃圾食物处理系统(3)打开功率继电器32的驱动,关闭与其相连的常闭开关118,从而消除了在此之前被施加到定时器单元40的控制终端146的触发信号,并且需要注意的是,功率继电器30的电源开关108供应了一个类似的功能,如本文所述的,启动系统10每天第一次激活功率继电器30的时候,这个功能中断了定时器单元40的控制终端146,即先前追踪的触发信号电路,如本文所述。
进一步,在与功率继电器32相连的开关被关闭的时候,它的驱动被触发的结果是非常明显的,断开常开继电器开关119,为高流量水阀22的电磁阀80建立了一个到地面的备用路径,也就是可以追踪到电源线200;通过导线202;电磁阀80;导线204;导线416和现在被断开的功率继电器32的闭合开关119到地面,如此一来就能明显并且很方便的注意到,与功率继电器30相连的开关109执行同样的功能,通过一个完全可追踪的功率继电器30,而不是功率继电器32,使功率继电器30处于启动状态,所以在任何时期,控制单元12的电动机46可在任意一个方向操作(这取决于功率继电器30或功率继电器32处于激活状态),电磁阀80也将保持通电,来保持高流量水阀22在该段时期内处于闭合状态,这样的话,水流将会在需要大幅率的时候流通,通过管道76和78流到控制单元12,这个控制单元12的机构52正积极粉碎积累废料,并且已经积累或正在采用,接着顺着水流冲到下水道或者通过类似单元12的出口58.你将会很方便的观察到电磁阀74保持通电,并且在控制单元12积极运作期间,低流量水阀20也保持闭合,并且应当在任何特定安装情况下,把阀22的流通能力考虑在内。
毕业设计外文资料翻译ASPNET
毕业设计外文资料翻译题目技术学院XXXXXXXXXXXX专业XXXXX班级XXXX学生XX学号XXXXXXXXX指导教师XXX二〇一三年三月十日Advanced AJAX Server Controls ,2009, 177(5): 97-102.TechniqueAdam Calderon Joel Rumerman1. Building Pagesand the .NET Frameworkis part of Microsoft's overall .NET framework, which contains a vast set of programming classes designed to satisfy any conceivable programming need. In the following two sections, you learn how fits within the .NET framework, and you learn about the languages you can use in your pages.The .NET Framework Class LibraryImagine that you are Microsoft. Imagine that you have to support multiple programming languages—such as Visual Basic, JScript, and C++. A great deal of the functionality of these programming languages overlaps. For example, for each language, you would have to include methods for accessing the file system, working with databases, and manipulating strings.Furthermore, these languages contain similar programming constructs. Every language, for example, can represent loops and conditionals. Even though the syntax of a conditional written in Visual Basic differs from the syntax of a conditional written in C++, the programming function is the same.Finally, most programming languages have similar variable data types. In most languages, you have some means of representing strings and integers, for example. The maximum and minimum size of an integer might depend on the language, but the basic data type is the same.Maintaining all this functionality for multiple languages requires a lot of work. Why keep reinventing the wheel? Wouldn't it be easier to create all this functionality once and use it for every language?The .NET Framework Class Library does exactly that. It consists of a vast set of classes designed to satisfy any conceivable programming need. For example, the .NET framework contains classes for handling database access, working with the file system, manipulating text, and generating graphics. In addition, it contains more specialized classes for performing tasks such as working with regular expressions and handling network protocols.The .NET framework, furthermore, contains classes that represent all the basic variable data types such as strings, integers, bytes, characters, and arrays.Most importantly, for purposes of this book, the .NET Framework Class Library contains classes for building pages. You need to understand, however, that you can access any of the .NET framework classes when you are building your pages.Understanding NamespacesAs you might guess, the .NET framework is huge. It contains thousands of classes (over 3,400). Fortunately, the classes are not simply jumbled together. The classes of the .NET framework are organized into a hierarchy of namespaces.ASP Classic NoteIn previous versions of Active Server Pages, you had access to only five standard classes (the Response, Request, Session, Application, and Server objects). , in contrast, provides you with access to over 3,400 classes!A namespace is a logical grouping of classes. For example, all the classes that relate to working with the file system are gathered together into the namespace.The namespaces are organized into a hierarchy (a logical tree). At the root of the tree is the System namespace. This namespace contains all the classes for the base data types, such as strings and arrays. It also contains classes for working with random numbers and dates and times.You can uniquely identify any class in the .NET framework by using the full namespace of the class. For example, to uniquely refer to the class that represents a file system file (the File class), you would use the following:refers to the namespace, and File refers to the particular class.NOTEYou can view all the namespaces of the standard classes in the .NET Framework Class Library by viewing the Reference Documentation for the .NET Framework.Standard NamespacesThe classes contained in a select number of namespaces are available in your pages by default. (You must explicitly import other namespaces.) These default namespaces contain classes that you use most often in your applications:System— Contains all the base data types and other useful classes such as those related to generating random numbers and working with dates and times.— Contains classes for working with standard collection types such as hash tables, and array lists.— Contains classes that represent specialized collections such as linked lists and string collections.— Contains classes for working with configuration files files).— Contains classes for encoding, decoding, and manipulating the contents of strings.— Contains classes for performing regular expression match and replace operations.— Contains the basic classes for working with the World Wide Web, including classes for representing browser requests and server responses.— Contains classes used for caching the content of pages and classes for performing custom caching operations.— Contains classes for implementing authentication and authorization such as Forms and Passport authentication.— Contains classes for implementing session state.— Contains the basic classes used in building the user interface of pages.— Contains the classes for the HTML controls.— Contains the classes for the Web controls..NET Framework-Compatible LanguagesFor purposes of this book, you will write the application logic for your pages using Visual Basic as your programming language. It is the default language for pages. Although you stick to Visual Basic in this book, you also need to understand that you can create pages by using any language that supports the .NET Common Language Runtime. Out of the box, this includes C#, , and the Managed Extensions to C++.NOTEThe CD included with this book contains C# versions of all the code samples.Dozens of other languages created by companies other than Microsoft have been developed to work with the .NET framework. Some examples of these other languages include Python, SmallTalk, Eiffel, and COBOL. This means that you could, if you really wanted to, write pages using COBOL.Regardless of the language that you use to develop your pages, you need to understand that pages are compiled before they are executed. This means that pages can execute very quickly.The first time you request an page, the page is compiled into a .NET class, and the resulting class file is saved beneath a special directory on your server named Temporary Files. For each and every page, a corresponding class file appears in the Temporary Files directory. Whenever you request the same page in the future, the corresponding class file is executed.When an page is compiled, it is not compiled directly into machine code. Instead, it is compiled into an intermediate-level language called Microsoft Intermediate Language (MSIL). All .NET-compatible languages are compiled into this intermediate language.An page isn't compiled into native machine code until it is actually requested by a browser. At that point, the class file contained in the Temporary Files directory is compiled with the .NET framework Just in Time (JIT) compiler and executed.The magical aspect of this whole process is that it happens automatically in the background. All you have to do is create a text file with the source code for your page, and the .NET framework handles all the hard work of converting it into compiled code for you.ASP CLASSIC NOTEWhat about VBScript? Before , VBScript was the most popular language for developing Active Server Pages.does not support VBScript, and this is good news. Visual Basic is a superset of VBScript, which means that Visual Basic has all the functionality of VBScript and more. So, you have a richer set of functions and statements with Visual Basic.Furthermore, unlike VBScript, Visual Basic is a compiled language. This means that if you use Visual Basic to rewrite the same code that you wrote with VBScript, you can get better performance.If you have worked only with VBScript and not Visual Basic in the past, don't worry. Since VBScript is so closely related to Visual Basic, you'll find it easy to make the transition between the two languages.NOTEMicrosoft includes an interesting tool named the IL Disassembler (ILDASM) withthe .NET framework. You can use this tool to view the disassembled code for any of the classes in the Temporary Files directory. It lists all the methods and properties of the class and enables you to view the intermediate-level code.This tool also works with all the controls discussed in this chapter. For example, you can use the IL Disassembler to view the intermediate-level code for the TextBox control (located in a file named Controlscontrols provide the dynamic and interactive portions of the user interface for your Web application. The controls render the content that the users of your Web site actually see and interact with. For example, you can use controls to create HTML form elements, interactive calendars, and rotating banner advertisements.controls coexist peacefully with HTML content. Typically, you create the static areas of your Web pages with normal HTML content and create the dynamic or interactive portions with controls.The best way to understand how controls work in an HTML page is to look at a simple Web Forms Page.Adding Application Logic to an PageThe second building block of an page is the application logic, which is the actual programming code in the page. You add application logic to a page to handle both control and page events.If a user clicks a Button control within an HTML form, for example, the Button control raises an event (the Click event). Typically, you want to add code to the page that does something in response to this event. For example, when someone clicks the Button control, you might want to save the form data to a file or database.Controls are not the only things that can raise events. An page itself raises several events every time it is requested. For example, whenever you request a page, the page's Load event is triggered. You can add application logic to the page that executes whenever the Load event occurs.2. Building Forms with Web Server ControlsBuilding Smart FormsYou use several of the basic Web controls to represent standard HTML form elements such as radio buttons, text boxes, and list boxes. You can use these controls in your pages to create the user interface for your Web application. The following sections provide detailed overviews and programming samples for each of these Web controls.Controlling Page NavigationIn the following sections, you learn how to control how a user moves from one page to another. First, you learn how to submit an HTML form to another page and retrieve form information. Next, you learn how to use the Redirect() method to automatically transfer a user to a new page. Finally, you learn how to link pages together with the HyperLink control.Applying Formatting to ControlsIn the following sections, you learn how to make more attractive Web forms. First, you look at an overview of the formatting properties common to all Web controls; they are the formatting properties of the base control class. Next, you learn how to apply Cascading Style Sheet styles and classes to Web controls.3. Performing Form Validation with Validation ControlsUsing Client-side ValidationTraditionally, Web developers have faced a tough choice when adding form validation logic to their pages. You can add form validation routines to your server-side code, or you can add the validation routines to your client-side code.The advantage of writing validation logic in client-side code is that you can provide instant feedback to your users. For example, if a user neglects to enter a value in a required form field, you can instantly display an error message without requiring a roundtrip back to the server.People really like client-side validation. It looks great and creates a better overall user experience. The problem, however, is that it does not work with all browsers. Not all browsers support JavaScript, and different versions of browsers support different versions of JavaScript, so client-side validation is never guaranteed to work.For this reason, in the past, many developers decided to add all their form validation logic exclusively to server-side code. Because server-side code functions correctly with any browser, this course of action was safer.Fortunately, the Validation controls discussed in this chapter do not force you to make this difficult choice. The Validation controls automatically generate both client-side and server-side code. If a browser is capable of supporting JavaScript, client-side validation scripts are automatically sent to the browser. If a browser is incapable of supporting JavaScript, the validation routines are automatically implemented in server-side code.You should be warned, however, that client-side validation works only with Microsoft Internet Explorer version and higher. In particular, the client-side scripts discussed in this chapter do not work with any version of Netscape Navigator.Requiring Fields: The RequiredFieldValidator ControlYou use RequiredFieldValidator in a Web form to check whether a control has a value. Typically, you use this control with a TextBox control. However, nothing is wrong with using RequiredFieldValidator with other input controls such as RadioButtonList.Validating Expressions: The RegularExpressionValidator ControlYou can use RegularExpressionValidator to match the value entered into a form field to a regular expression. You can use this control to check whether a user has entered, for example, a valid e-mail address, telephone number, or username or password. Samples of how to use a regular expression to perform all these validation tasks are provided in the following sections.Comparing Values: The CompareValidator ControlThe CompareValidator control performs comparisons between the data entered into a form field and another value. The other value can be a fixed value, such as a particular number, or a value entered into another control.Summarizing Errors: The ValidationSummary ControlImagine that you have a form with 50 form fields. If you use only the Validation controls discussed in the previous sections of this chapter to display errors, seeing an error message on the page might be difficult. For example, you might have to scroll down to the 48th form field to find the error message.Fortunately, Microsoft includes a ValidationSummary control with the Validation controls. You can use this control to summarize all the errors at the top of a page, or wherever else you want.4. Advanced Control ProgrammingWorking with View StateBy default, almost all controls retain the values of their properties between form posts. For example, if you assign text to a Label control and submit the form, when the page is rendered again, the contents of the Label control are preserved.The magic of view state is that it does not depend on any special server or browser properties. In particular, it does not depend on cookies, session variables, or application variables. View state is implemented with a hidden form field called VIEWSTATE that is automatically created in every Web Forms Page.When used wisely, view state can have a dramatic and positive effect on the performance of your Web site. For example, if you display database data in a control that has view state enabled, you do not have to return to the database each time the page is posted back to the server. You can automatically preserve the data within the page's view state between form posts.Displaying and Hiding ContentImagine that you are creating a form with an optional section. For example, imagine that you are creating an online tax form, and you want to display or hide a section that contains questions that apply only to married tax filers.Or, imagine that you want to add an additional help button to the tax form. You might want to hide or display detailed instructions for completing form questions depending on a user's preferences.Finally, imagine that you want to break the tax form into multiple pages so that a person views only one part of the tax form at a time.In the following sections, you learn about the properties that you can use to hide and display controls in a form. You learn how to use the Visible and Enabled properties with individual controls and groups of controls to hide and display page content.Using the Visible and Enabled PropertiesEvery control, including both HTML and Web controls, has a Visible property that determines whether the control is rendered. When a control's Visible property has the value False, the control is not displayed on the page; the control is not processed for eitherpre-rendering or rendering.Web controls (but not every HTML control) have an additional property named Enabled. When Enabled has the value False and you are using Internet Explorer version or higher, the control appears ghosted and no longer functions. When used with other browsers, such as Netscape Navigator, the control might not appear ghosted, but it does not function.Disabling View StateIn certain circumstances, you might want to disable view state for an individual control or for an page as a whole. For example, you might have a control that contains a lot of data (imagine a RadioButtonList control with 1,000 options). You might not want to load the data into the hidden __VIEWSTATE form field if you are worried that the form data would significantly slow down the rendering of the page.Using Rich ControlsIn the following sections, you learn how to use three of the more feature-rich controls in the framework. You learn how to use the Calendar control to display interactive calendars, the AdRotator control to display rotating banner advertisements, and the HTMLInputFile control to accept file uploads.5 ConclusionThe advantages of using Struts to realize the website construction: It adopts JSPmarked mechanism to get the reusing codes and abstract codes. This method contributed to improve the reusability and flexibility of codes. When the technology space or the problem space varied, users have much more chances to reuse codes. Using open sou rce, everybody in the user’s room could check up codes. Struts make the designers and developers pay their attention to their own favorite aspects. Adopting separately control ideology to manage the problem space. The websites based on this pattern had perfectly robustness. The layer structures were clear. As to huge scale of system, Struts conducted to manage complicated system. The disadvantages of using Struts to realize the website construction: The applicable scope of Struts is limited. Struts are MVC solution based on web. So it must be achieved by HTML, JSP document and Servlet and use J2EE application program to support Struts. Struts need to support and Servlet standard Servlet container. Of course, isolating the problem scope, but strengthening the complicacy, so one must accept some training before they adopt Struts development.References1. Selfa, ., Carrillo, M., Del Rocío Boone, M.: A database and web application based onMVC architecture. In: International Conference on Electronics, Communications and Computers, pp. 48–49 (2006)2. Lin, ., Hu, .: Design and implementation of the internet service platform forrural house building technique criteria and management based on .NET MVC. Applied Mechanics and Materials, 1727–1731 (2011)3. Wang, ., Xi, M., Li, .: A network-friendly architecture for Multi-view VideoCoding (MVC). Advanced Materials Research, 678–681 (2010)4. Li, ., Ma, ., Feng, G., Ma, .: Research on Web Application of StrutsFramework Based on MVC Pattern. In: Shen, ., Li, J., Li, M., Ni, J., Wang, W. (eds.) APWeb Workshops 2006. LNCS, vol. 3842, pp. 1029–1032. Springer, Heidelberg (2006)Advanced AJAX Server Controls ,2009,177(5):97-102技术Adam Calderon Joel Rumerman摘要:页面的构建,验证和编程。
毕业设计(论文)外文资料和译文格式要求

东北大学东软信息学院外文资料和译文格式要求一、译文必须采用计算机输入、打印,幅面A4。
外文资料原文(复印或打印)在前,译文在后,于左侧装订。
二、具体要求1、至少翻译一篇内容与所选课题相关的外文文献。
2、译文汉字字数不少于4000字。
3、正文格式要求:宋体五号字。
附:外文资料和译文封面、空白页外文资料和译文专业:班级:姓名:学号:指导教师:2010年12月23日5.2.5. Read/Write Spin LocksRead/write spin locks have been introduced to increase the amount of concurrency inside the kernel. They allow several kernel control paths to simultaneously read the same data structure, as long as no kernel control path modifies it. If a kernel control path wishes to write to the structure, it must acquire the write version of the read/write lock, which grants exclusive access to the resource. Of course, allowing concurrent reads on data structures improves system performance.Figure 5-2 illustrates two critical regions (C1 and C2) protected by read/write locks. Kernel control paths R0 and R1 are reading the data structures in C1 at the same time, while W0 is waiting to acquire the lock for writing. Kernel control path W1 is writing the data structures inC2, while both R2 and W2 are waiting to acquire the lock for reading and writing, respectively.Figure 5-2. Read/write spin locksEach read/write spin lock is a rwlock_t structure; its lock field is a 32-bit field that encodes two distinct pieces of information:∙ A 24-bit counter denoting the number of kernel control paths currently reading the protected data structure. The two's complement value of this counter is stored in bits 023 of the field.∙An unlock flag that is set when no kernel control path is reading or writing, and clear otherwise. This unlock flag is stored in bit 24 of the field.Notice that the lock field stores the number 0x01000000 if the spin lock is idle (unlock flag set and no readers), the number 0x00000000 if it has been acquired for writing (unlock flag clear and no readers), and any number in the sequence 0x00ffffff, 0x00fffffe, and so on, if it has been acquired for reading by one, two, or more processes (unlock flag clear and the two's complement on 24 bits of the number of readers). As the spinlock_t structure, the rwlock_t structure also includes a break_lock field.The rwlock_init macro initializes the lock field of a read/write spin lock to 0x01000000 (unlocked) and the break_lock field to zero.5.2.5.1. Getting and releasing a lock for readingThe read_lock macro, applied to the address rwlp of a read/write spin lock, is similar to thespin_lock macro described in the previous section. If the kernel preemption option has been selected when the kernel was compiled, the macro performs the very same actions as those of spin_lock( ), with just one exception: to effectively acquire the read/write spin lock in step 2, the macro executes the _raw_read_trylock( ) function:int _raw_read_trylock(rwlock_t *lock){atomic_t *count = (atomic_t *)lock->lock;atomic_dec(count);if (atomic_read(count) >= 0)return 1;atomic_inc(count);return 0;}The lock fieldthe read/write lock counteris accessed by means of atomic operations. Notice, however, that the whole function does not act atomically on the counter: for instance, the counter might change after having tested its value with the if statement and before returning 1. Nevertheless, the function works properly: in fact, the function returns 1 only if the counter was not zero or negative before the decrement, because the counter is equal to 0x01000000 for no owner, 0x00ffffff for one reader, and 0x00000000 for one writer.If the kernel preemption option has not been selected when the kernel was compiled, theread_lock macro yields the following assembly language code:movl $rwlp->lock,%eaxlock; subl $1,(%eax)jns 1fcall _ _read_lock_failed1:where _ _read_lock_failed( ) is the following assembly language function:_ _read_lock_failed:lock; incl (%eax)1: pausecmpl $1,(%eax)js 1block; decl (%eax)js _ _read_lock_failedretThe read_lock macro atomically decreases the spin lock value by 1, thus increasing the number of readers. The spin lock is acquired if the decrement operation yields a nonnegative value; otherwise, the _ _read_lock_failed( ) function is invoked. The function atomically increases the lock field to undo the decrement operation performed by the read_lock macro, and then loops until the field becomes positive (greater than or equal to 1). Next, _ _read_lock_failed( ) tries to get the spin lock again (another kernel control path could acquire the spin lock for writing right after the cmpl instruction).Releasing the read lock is quite simple, because the read_unlock macro must simply increase the counter in the lock field with the assembly language instruction:lock; incl rwlp->lockto decrease the number of readers, and then invoke preempt_enable( ) to reenable kernel preemption.5.2.5.2. Getting and releasing a lock for writingThe write_lock macro is implemented in the same way as spin_lock( ) andread_lock( ). For instance, if kernel preemption is supported, the function disables kernel preemption and tries to grab the lock right away by invoking_raw_write_trylock( ). If this function returns 0, the lock was already taken, thus the macro reenables kernel preemption and starts a busy wait loop, as explained in the description of spin_lock( ) in the previous section.The _raw_write_trylock( ) function is shown below:int _raw_write_trylock(rwlock_t *lock){atomic_t *count = (atomic_t *)lock->lock;if (atomic_sub_and_test(0x01000000, count))return 1;atomic_add(0x01000000, count);return 0;}The _raw_write_trylock( ) function subtracts 0x01000000 from the read/write spin lock value, thus clearing the unlock flag (bit 24). If the subtraction operation yieldszero (no readers), the lock is acquired and the function returns 1; otherwise, the function atomically adds 0x01000000 to the spin lock value to undo the subtraction operation.Once again, releasing the write lock is much simpler because the write_unlock macro must simply set the unlock flag in the lock field with the assembly language instruction:lock; addl $0x01000000,rwlpand then invoke preempt_enable().5.2.6. SeqlocksWhen using read/write spin locks, requests issued by kernel control paths to perform a read_lock or a write_lock operation have the same priority: readers must wait until the writer has finished and, similarly, a writer must wait until all readers have finished.Seqlocks introduced in Linux 2.6 are similar to read/write spin locks, except that they give a much higher priority to writers: in fact a writer is allowed to proceed even when readers are active. The good part of this strategy is that a writer never waits (unless another writer is active); the bad part is that a reader may sometimes be forced to read the same data several times until it gets a valid copy.Each seqlock is a seqlock_t structure consisting of two fields: a lock field of type spinlock_t and an integer sequence field. This second field plays the role of a sequence counter. Each reader must read this sequence counter twice, before and after reading the data, and check whether the two values coincide. In the opposite case, a new writer has become active and has increased the sequence counter, thus implicitly telling the reader that the data just read is not valid.A seqlock_t variable is initialized to "unlocked" either by assigning to it the value SEQLOCK_UNLOCKED, or by executing the seqlock_init macro. Writers acquire and release a seqlock by invoking write_seqlock( ) and write_sequnlock( ). The first function acquires the spin lock in the seqlock_t data structure, then increases the sequence counter by one; the second function increases the sequence counter once more, then releases the spin lock. This ensures that when the writer is in the middle of writing, the counter is odd, and that when no writer is altering data, the counter is even. Readers implement a critical region as follows:unsigned int seq;do {seq = read_seqbegin(&seqlock);/* ... CRITICAL REGION ... */} while (read_seqretry(&seqlock, seq));read_seqbegin() returns the current sequence number of the seqlock; read_seqretry() returns 1 if either the value of the seq local variable is odd (a writer was updating the data structure when the read_seqbegin( ) function has been invoked), or if the value of seq does not match the current value of the seqlock's sequence counter (a writer started working while the reader was still executing the code in the critical region).Notice that when a reader enters a critical region, it does not need to disable kernel preemption; on the other hand, the writer automatically disables kernel preemption when entering the critical region, because it acquires the spin lock.Not every kind of data structure can be protected by a seqlock. As a general rule, the following conditions must hold:∙The data structure to be protected does not include pointers that are modified by the writers and dereferenced by the readers (otherwise, a writer couldchange the pointer under the nose of the readers)∙The code in the critical regions of the readers does not have side effects (otherwise, multiple reads would have different effects from a single read) Furthermore, the critical regions of the readers should be short and writers should seldom acquire the seqlock, otherwise repeated read accesses would cause a severe overhead. A typical usage of seqlocks in Linux 2.6 consists of protecting some data structures related to the system time handling (see Chapter 6).5.2.7. Read-Copy Update (RCU)Read-copy update (RCU) is yet another synchronization technique designed to protect data structures that are mostly accessed for reading by several CPUs. RCU allows many readers and many writers to proceed concurrently (an improvement over seqlocks, which allow only one writer to proceed). Moreover, RCU is lock-free, that is, it uses no lock or counter shared by all CPUs; this is a great advantage over read/write spin locks and seqlocks, which have a high overhead due to cache line-snooping and invalidation.How does RCU obtain the surprising result of synchronizing several CPUs without shared data structures? The key idea consists of limiting the scope of RCU as follows:1.Only data structures that are dynamically allocated and referenced by meansof pointers can be protected by RCU.2.No kernel control path can sleep inside a critical region protected by RCU.When a kernel control path wants to read an RCU-protected data structure, it executes the rcu_read_lock( ) macro, which is equivalent to preempt_disable( ). Next, the reader dereferences the pointer to the data structure and starts reading it. As stated above, the reader cannot sleep until it finishes reading the data structure; the end of the critical region is marked by the rcu_read_unlock( ) macro, which is equivalent to preempt_enable( ).Because the reader does very little to prevent race conditions, we could expect that the writer has to work a bit more. In fact, when a writer wants to update the data structure, it dereferences the pointer and makes a copy of the whole data structure. Next, the writer modifies the copy. Once finished, the writer changes the pointer to the data structure so as to make it point to the updated copy. Because changing the value of the pointer is an atomic operation, each reader or writer sees either the old copy or the new one: no corruption in the data structure may occur. However, a memory barrier is required to ensure that the updated pointer is seen by the other CPUs only after the data structure has been modified. Such a memory barrier is implicitly introduced if a spin lock is coupled with RCU to forbid the concurrent execution of writers.The real problem with the RCU technique, however, is that the old copy of the data structure cannot be freed right away when the writer updates the pointer. In fact, the readers that were accessing the data structure when the writer started its update could still be reading the old copy. The old copy can be freed only after all (potential) readers on the CPUs have executed the rcu_read_unlock( ) macro. The kernel requires every potential reader to execute that macro before:∙The CPU performs a process switch (see restriction 2 earlier).∙The CPU starts executing in User Mode.∙The CPU executes the idle loop (see the section "Kernel Threads" in Chapter 3).In each of these cases, we say that the CPU has gone through a quiescent state.The call_rcu( ) function is invoked by the writer to get rid of the old copy of the data structure. It receives as its parameters the address of an rcu_head descriptor (usually embedded inside the data structure to be freed) and the address of a callback function to be invoked when all CPUs have gone through a quiescent state. Once executed, the callback function usually frees the old copy of the data structure.The call_rcu( ) function stores in the rcu_head descriptor the address of the callback and its parameter, then inserts the descriptor in a per-CPU list of callbacks. Periodically, once every tick (see the section "Updating Local CPU Statistics" in Chapter 6), the kernel checks whether the local CPU has gone through a quiescent state. When all CPUs have gone through a quiescent state, a local taskletwhose descriptor is stored in the rcu_tasklet per-CPU variableexecutes all callbacks in the list.RCU is a new addition in Linux 2.6; it is used in the networking layer and in the Virtual Filesystem.5.2.8. SemaphoresWe have already introduced semaphores in the section "Synchronization and Critical Regions" in Chapter 1. Essentially, they implement a locking primitive that allows waiters to sleep until the desired resource becomes free.Actually, Linux offers two kinds of semaphores:∙Kernel semaphores, which are used by kernel control paths∙System V IPC semaphores, which are used by User Mode processesIn this section, we focus on kernel semaphores, while IPC semaphores are described in Chapter 19.A kernel semaphore is similar to a spin lock, in that it doesn't allow a kernel control path to proceed unless the lock is open. However, whenever a kernel control path tries to acquire a busy resource protected by a kernel semaphore, the corresponding process is suspended. It becomes runnable again when the resource is released. Therefore, kernel semaphores can be acquired only by functions that are allowed to sleep; interrupt handlers and deferrable functions cannot use them.A kernel semaphore is an object of type struct semaphore, containing the fields shown in the following list.countStores an atomic_t value. If it is greater than 0, the resource is free that is, itis currently available. If count is equal to 0, the semaphore is busy but noother process is waiting for the protected resource. Finally, if count isnegative, the resource is unavailable and at least one process is waiting for it.waitStores the address of a wait queue list that includes all sleeping processes that are currently waiting for the resource. Of course, if count is greater than orequal to 0, the wait queue is empty.sleepersStores a flag that indicates whether some processes are sleeping on thesemaphore. We'll see this field in operation soon.The init_MUTEX( ) and init_MUTEX_LOCKED( ) functions may be used to initialize a semaphore for exclusive access: they set the count field to 1 (free resource with exclusive access) and 0 (busy resource with exclusive access currently granted to the process that initializes the semaphore), respectively. The DECLARE_MUTEX and DECLARE_MUTEX_LOCKED macros do the same, but they also statically allocate the struct semaphore variable. Note that a semaphore could also be initialized with an arbitrary positive value n for count. In this case, at most n processes are allowed to concurrently access the resource.5.2.8.1. Getting and releasing semaphoresLet's start by discussing how to release a semaphore, which is much simpler than getting one. When a process wishes to release a kernel semaphore lock, it invokes the up( ) function. This function is essentially equivalent to the following assembly language fragment:movl $sem->count,%ecxlock; incl (%ecx)jg 1flea %ecx,%eaxpushl %edxpushl %ecxcall _ _uppopl %ecxpopl %edx1:where _ _up( ) is the following C function:__attribute__((regparm(3))) void _ _up(struct semaphore *sem){wake_up(&sem->wait);}The up( ) function increases the count field of the *sem semaphore, and then it checks whether its value is greater than 0. The increment of count and the setting of the flag tested by the following jump instruction must be atomically executed, or else another kernel control path could concurrently access the field value, with disastrousresults. If count is greater than 0, there was no process sleeping in the wait queue, so nothing has to be done. Otherwise, the _ _up( ) function is invoked so that one sleeping process is woken up. Notice that _ _up( ) receives its parameter from the eax register (see the description of the _ _switch_to( ) function in the section "Performing the Process Switch" in Chapter 3).Conversely, when a process wishes to acquire a kernel semaphore lock, it invokes the down( ) function. The implementation of down( ) is quite involved, but it is essentially equivalent to the following:down:movl $sem->count,%ecxlock; decl (%ecx);jns 1flea %ecx, %eaxpushl %edxpushl %ecxcall _ _downpopl %ecxpopl %edx1:where _ _down( ) is the following C function:__attribute__((regparm(3))) void _ _down(struct semaphore * sem){DECLARE_WAITQUEUE(wait, current);unsigned long flags;current->state = TASK_UNINTERRUPTIBLE;spin_lock_irqsave(&sem->wait.lock, flags);add_wait_queue_exclusive_locked(&sem->wait, &wait);sem->sleepers++;for (;;) {if (!atomic_add_negative(sem->sleepers-1, &sem->count)) {sem->sleepers = 0;break;}sem->sleepers = 1;spin_unlock_irqrestore(&sem->wait.lock, flags);schedule( );spin_lock_irqsave(&sem->wait.lock, flags);current->state = TASK_UNINTERRUPTIBLE;}remove_wait_queue_locked(&sem->wait, &wait);wake_up_locked(&sem->wait);spin_unlock_irqrestore(&sem->wait.lock, flags);current->state = TASK_RUNNING;}The down( ) function decreases the count field of the *sem semaphore, and then checks whether its value is negative. Again, the decrement and the test must be atomically executed. If count is greater than or equal to 0, the current process acquires the resource and the execution continues normally. Otherwise, count is negative, and the current process must be suspended. The contents of some registers are saved on the stack, and then _ _down( ) is invoked.Essentially, the _ _down( ) function changes the state of the current process from TASK_RUNNING to TASK_UNINTERRUPTIBLE, and it puts the process in the semaphore wait queue. Before accessing the fields of the semaphore structure, the function also gets the sem->wait.lock spin lock that protects the semaphore wait queue (see "How Processes Are Organized" in Chapter 3) and disables local interrupts. Usually, wait queue functions get and release the wait queue spin lock as necessary when inserting and deleting an element. The _ _down( ) function, however, uses the wait queue spin lock also to protect the other fields of the semaphore data structure, so that no process running on another CPU is able to read or modify them. To that end, _ _down( ) uses the "_locked" versions of the wait queue functions, which assume that the spin lock has been already acquired before their invocations.The main task of the _ _down( ) function is to suspend the current process until the semaphore is released. However, the way in which this is done is quite involved. To easily understand the code, keep in mind that the sleepers field of the semaphore is usually set to 0 if no process is sleeping in the wait queue of the semaphore, and it is set to 1 otherwise. Let's try to explain the code by considering a few typical cases. MUTEX semaphore open (count equal to 1, sleepers equal to 0)The down macro just sets the count field to 0 and jumps to the nextinstruction of the main program; therefore, the _ _down( ) function is notexecuted at all.MUTEX semaphore closed, no sleeping processes (count equal to 0, sleepers equal to 0)The down macro decreases count and invokes the _ _down( ) function withthe count field set to -1 and the sleepers field set to 0. In each iteration of theloop, the function checks whether the count field is negative. (Observe thatthe count field is not changed by atomic_add_negative( ) because sleepers isequal to 0 when the function is invoked.)∙If the count field is negative, the function invokes schedule( ) tosuspend the current process. The count field is still set to -1, and thesleepers field to 1. The process picks up its run subsequently insidethis loop and issues the test again.∙If the count field is not negative, the function sets sleepers to 0 and exits from the loop. It tries to wake up another process in thesemaphore wait queue (but in our scenario, the queue is now empty)and terminates holding the semaphore. On exit, both the count fieldand the sleepers field are set to 0, as required when the semaphore isclosed but no process is waiting for it.MUTEX semaphore closed, other sleeping processes (count equal to -1, sleepers equal to 1)The down macro decreases count and invokes the _ _down( ) function withcount set to -2 and sleepers set to 1. The function temporarily sets sleepers to 2, and then undoes the decrement performed by the down macro by addingthe value sleepers-1 to count. At the same time, the function checks whethercount is still negative (the semaphore could have been released by theholding process right before _ _down( ) entered the critical region).∙If the count field is negative, the function resets sleepers to 1 andinvokes schedule( ) to suspend the current process. The count field isstill set to -1, and the sleepers field to 1.∙If the count field is not negative, the function sets sleepers to 0, tries to wake up another process in the semaphore wait queue, and exitsholding the semaphore. On exit, the count field is set to 0 and thesleepers field to 0. The values of both fields look wrong, becausethere are other sleeping processes. However, consider that anotherprocess in the wait queue has been woken up. This process doesanother iteration of the loop; the atomic_add_negative( ) functionsubtracts 1 from count, restoring it to -1; moreover, before returningto sleep, the woken-up process resets sleepers to 1.So, the code properly works in all cases. Consider that the wake_up( ) function in _ _down( ) wakes up at most one process, because the sleeping processes in the wait queue are exclusive (see the section "How Processes Are Organized" in Chapter 3).Only exception handlers , and particularly system call service routines , can use the down( ) function. Interrupt handlers or deferrable functions must not invoke down( ),because this function suspends the process when the semaphore is busy. For this reason, Linux provides the down_trylock( ) function, which may be safely used by one of the previously mentioned asynchronous functions. It is identical to down( ) except when the resource is busy. In this case, the function returns immediately instead of putting the process to sleep.A slightly different function called down_interruptible( ) is also defined. It is widely used by device drivers, because it allows processes that receive a signal while being blocked on a semaphore to give up the "down" operation. If the sleeping process is woken up by a signal before getting the needed resource, the function increases the count field of the semaphore and returns the value -EINTR. On the other hand, if down_interruptible( ) runs to normal completion and gets the resource, it returns 0. The device driver may thus abort the I/O operation when the return value is -EINTR.Finally, because processes usually find semaphores in an open state, the semaphore functions are optimized for this case. In particular, the up( ) function does not execute jump instructions if the semaphore wait queue is empty; similarly, the down( ) function does not execute jump instructions if the semaphore is open. Much of the complexity of the semaphore implementation is precisely due to the effort of avoiding costly instructions in the main branch of the execution flow.5.2.9. Read/Write SemaphoresRead/write semaphores are similar to the read/write spin locks described earlier in the section "Read/Write Spin Locks," except that waiting processes are suspended instead of spinning until the semaphore becomes open again.Many kernel control paths may concurrently acquire a read/write semaphore for reading; however, every writer kernel control path must have exclusive access to the protected resource. Therefore, the semaphore can be acquired for writing only if no other kernel control path is holding it for either read or write access. Read/write semaphores improve the amount of concurrency inside the kernel and improve overall system performance.The kernel handles all processes waiting for a read/write semaphore in strict FIFO order. Each reader or writer that finds the semaphore closed is inserted in the last position of a semaphore's wait queue list. When the semaphore is released, the process in the first position of the wait queue list are checked. The first process is always awoken. If it is a writer, the other processes in the wait queue continue to sleep. If it is a reader, all readers at the start of the queue, up to the first writer, are also woken up and get the lock. However, readers that have been queued after a writer continue to sleep.Each read/write semaphore is described by a rw_semaphore structure that includes the following fields:countStores two 16-bit counters. The counter in the most significant word encodesin two's complement form the sum of the number of nonwaiting writers(either 0 or 1) and the number of waiting kernel control paths. The counter inthe less significant word encodes the total number of nonwaiting readers andwriters.wait_listPoints to a list of waiting processes. Each element in this list is arwsem_waiter structure, including a pointer to the descriptor of the sleepingprocess and a flag indicating whether the process wants the semaphore forreading or for writing.wait_lockA spin lock used to protect the wait queue list and the rw_semaphorestructure itself.The init_rwsem( ) function initializes an rw_semaphore structure by setting the count field to 0, the wait_lock spin lock to unlocked, and wait_list to the empty list. The down_read( ) and down_write( ) functions acquire the read/write semaphore for reading and writing, respectively. Similarly, the up_read( ) and up_write( ) functions release a read/write semaphore previously acquired for reading and for writing. The down_read_trylock( ) and down_write_trylock( ) functions are similar todown_read( ) and down_write( ), respectively, but they do not block the process if the semaphore is busy. Finally, the downgrade_write( ) function atomically transforms a write lock into a read lock. The implementation of these five functions is long, but easy to follow because it resembles the implementation of normal semaphores; therefore, we avoid describing them.5.2.10. CompletionsLinux 2.6 also makes use of another synchronization primitive similar to semaphores: completions . They have been introduced to solve a subtle race condition that occurs in multiprocessor systems when process A allocates a temporary semaphore variable, initializes it as closed MUTEX, passes its address to process B, and then invokes down( ) on it. Process A plans to destroy the semaphore as soon as it awakens. Later。
毕业设计(论文)外文资料及译文(模板

大连东软信息学院
毕业设计(论文)外文资料及译文
系所:
专业:
班级:
姓名:
学号:
大连东软信息学院
Dalian Neusoft University of Information
外文资料和译文格式要求
一、装订要求
1、外文资料原文(复印或打印)在前、译文在后、最后为指导教师评定成绩。
2、译文必须采用计算机输入、打印。
3、A4幅面打印,于左侧装订。
二、撰写要求
1、外文文献内容与所选课题相关。
2、本科学生译文汉字字数不少于4000字,高职学生译文汉字字数不少于2000字。
三、格式要求
1、译文字号:中文小四号宋体,英文小四号“Times New Roman”字型,全文统一,首行缩进2个中文字符,1.5倍行距。
2、译文页码:页码用阿拉伯数字连续编页,字体采用“Times New Roman”字体,字号小五,页底居中。
3、译文页眉:眉体使用单线,页眉说明五号宋体,居中“大连东软信息学院本科毕业设计(论文)译文”。
大连东软信息学院毕业设计(论文)译文
-1-。
最全毕业设计方案外文资料翻译

毕业设计外文资料翻译题目山东省统计学会官方网站的设计与实现学院XX专业XX班级XX学生XX学号XX指导教师XX二〇一〇年六月五日可扩展的开放源码内容管理系统和框架:一组生物信息学解决方案摘要这是一个为生物信息学家的学术或行业实验室环境提出的共同的挑战,它提供了一套基于B/S的解决方案。
近日,开源社区开始开发建设和维护Web应用程序的许多学科的工具。
这些内容管理系统<CMS)提供的一组信息学的许多基本需要,无论是小公司,在一个更大的组织或一个学术实验室小组。
这些管理软件开发,网站开发,文档开发,课程开发,数据集,协作和客户工具的帮助。
由于这些工具有不少是扩展的,他们可以开发,以支持诸如处理大型数据集或部署bioanalytic生物医学等研究工具的具体活动。
在这个开放源码的审查网站管理工具,内容管理系统的基本特征进行了讨论随着常用的开源软件。
此外,他们在生物医学研究中使用的一些实例。
关键词:内容管理系统,CMS,实验室信息管理系统,LIMS,网站设计,数据管理,开放源码软件引言一般而言,用内容管理系统<CMS)的软件工具来管理网页和网站。
我们的社会的对CMS工具的想法,他们往往认为,如维基的mediawiki。
事实上,社区驱动的数据库注释的使用已吸引了许多科学的兴趣。
但是,也有许多开源工具,交换内容,发展社区推动知识和维护网站。
这些系统提供了一个有用的工具和插件,可以解决几乎所有的管理任务繁多。
选择其他的许多此前已书面审查,在这里我们提供一个在内容管理系统如何可用于促进生物医学研究人员的最新审查工作的重点。
在CMS内容的界定比较松散,但是,大部分系统作为例子,考虑以下各项内容:传统的网页,维基,论坛,社交网络,工程管理,文档管理和组<表1)。
一个特别有用的流行的开源CMS的工具方面是他们的可扩展和模块化设计,新内容的能力的发展允许。
这种特性使网络编程知识群体与发展,而不必维持基本的网络架构,其群体定制应用。
毕业设计(论文)外文资料翻译(学生用)

南京理工大学紫金学院毕业设计(论文)外文资料翻译系:计算机专业:计算机科学与技术姓名:沈俊男学号: 060601239外文出处: E. Jimenez-Ruiz,R. Berlanga. The Management(用外文写)and Integration of Biomedical[M/OL].Castellon:Spanish Ministry of Education andScience project,2004[2005-09098]./ftp/cs/papers/0609/0609144.pdf附件: 1.外文资料翻译译文;2.外文原文。
注:请将该封面与附件装订成册。
附件1:外文资料翻译译文管理和集成的生物医学知识:应用于Health-e-Child项目摘要:这个Health-e-Child项目的目的是为欧洲儿科学发展集成保健平台。
为了实现一个关于儿童健康的综合观点,一个复杂的生物医学数据、信息和知识的整合是必需的。
本体论将用于正式定义这个领域的专业知识,将塑造医学知识管理系统的基础。
文中介绍了一种对生物医学知识的垂直整合的新颖的方法。
该方法将会主要使临床医生中心化,并使定义本体碎片成为可能,连接这些碎片(语义桥接器),丰富了本体碎片(观点)。
这个策略为规格和捕获的碎片,桥接器和观点概述了初步的例子证明从医院数据库、生物医学本体、生物医学公共数据库的生物医学信息的征收。
关键词:垂直的知识集成、近似查询、本体观点、语义桥接器1.1 医学数据集成问题数据来源的集成已经在数据库社区成为传统的研究课题。
一个综合数据库系统主要的目标是允许用户均匀的访问一个分布和一个异构数据库。
数据集成的关键因素是定义一个全局性的模式,但是值得指出的是,我们必须区分三种全局模式:数据库模式、概念模式和域本体模式。
首先介绍了数据类型的信息存储、本地查询;其二,概括了这些图式采用更富有表达力的数据模型,如统一建模语言(UML)(TAMBIS和SEMEDA都遵循这个模式)。
毕业设计外文翻译英文

Bid Compensation Decision Model for Projectswith Costly Bid PreparationS.Ping Ho,A.M.ASCE 1Abstract:For projects with high bid preparation cost,it is often suggested that the owner should consider paying bid compensation to the most highly ranked unsuccessful bidders to stimulate extra effort or inputs in bid preparation.Whereas the underlying idea of using bid compensation is intuitively sound,there is no theoretical basis or empirical evidence for such suggestion.Because costly bid preparation often implies a larger project scale,the issue of bid compensation strategy is important to practitioners and an interest of study.This paper aims to study the impacts of bid compensation and to develop appropriate bid compensation strategies.Game theory is applied to analyze the behavioral dynamics between competing bidders and project owners.A bid compensation model based on game theoretic analysis is developed in this study.The model provides equilibrium solutions under bid compensation,quantitative formula,and quali-tative implications for the formation of bid compensation strategies.DOI:10.1061/(ASCE )0733-9364(2005)131:2(151)CE Database subject headings:Bids;Project management;Contracts;Decision making;Design/build;Build/Operate/Transfer;Construction industry .IntroductionAn often seen suggestion in practice for projects with high bid preparation cost is that the owner should consider paying bid compensation,also called a stipend or honorarium,to the unsuc-cessful bidders.For example,according to the Design–build Manual of Practice Document Number 201by Design–Build In-stitute of America (DBIA )(1996a ),it is suggested that that “the owner should consider paying a stipend or honorarium to the unsuccessful proposers”because “excessive submittal require-ments without some compensation is abusive to the design–build industry and discourages quality teams from participating.”In another publication by DBIA (1995),it is also stated that “it is strongly recommended that honorariums be offered to the unsuc-cessful proposers”and that “the provision of reasonable compen-sation will encourage the more sought-after design–build teams to apply and,if short listed,to make an extra effort in the prepara-tion of their proposal.”Whereas bid preparation costs depend on project scale,delivery method,and other factors,the cost of pre-paring a proposal is often relatively high in some particular project delivery schemes,such as design–build or build–operate–transfer (BOT )contracting.Plus,costly bid preparation often im-plying a large project scale,the issue of bid compensation strat-egy should be important to practitioners and of great interest of study.Existing research on the procurement process in constructionhas addressed the selection of projects that are appropriate for certain project delivery methods (Molenaar and Songer 1998;Molenaar and Gransberg 2001),the design–build project procure-ment processes (Songer et al.1994;Gransberg and Senadheera 1999;Palaneeswaran and Kumaraswamy 2000),and the BOT project procurement process (United Nations Industrial Develop-ment Organization 1996).However,the bid compensation strat-egy for projects with a relatively high bid preparation cost has not been studied.Among the issues over the bidder’s response to the owner’s procurement or bid compensation strategy,it is in own-er’s interest to understand how the owner can stimulate high-quality inputs or extra effort from the bidder during bid prepara-tion.Whereas the argument for using bid compensation is intuitively sound,there is no theoretical basis or empirical evi-dence for such an argument.Therefore,it is crucial to study under what conditions the bid compensation is effective,and how much compensation is adequate with respect to different bidding situa-tions.This paper focuses on theoretically studying the impacts of bid compensation and tries to develop appropriate compensation strategies for projects with a costly bid preparation.Game theory will be applied to analyze the behavioral dynamics between com-peting bidders.Based on the game theoretic analysis and numeric trials,a bid compensation model is developed.The model pro-vides a quantitative framework,as well as qualitative implica-tions,on bid compensation strategies.Research Methodology:Game TheoryGame theory can be defined as “the study of mathematical models of conflict and cooperation between intelligent rational decision-makers”(Myerson 1991).Among economic theories,game theory has been successfully applied to many important issues such as negotiations,finance,and imperfect markets.Game theory has also been applied to construction management in two areas.Ho (2001)applied game theory to analyze the information asymme-try problem during the procurement of a BOT project and its1Assistant Professor,Dept.of Civil Engineering,National Taiwan Univ.,Taipei 10617,Taiwan.E-mail:spingho@.twNote.Discussion open until July 1,2005.Separate discussions must be submitted for individual papers.To extend the closing date by one month,a written request must be filed with the ASCE Managing Editor.The manuscript for this paper was submitted for review and possible publication on March 5,2003;approved on March 1,2004.This paper is part of the Journal of Construction Engineering and Management ,V ol.131,No.2,February 1,2005.©ASCE,ISSN 0733-9364/2005/2-151–159/$25.00.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .implication in project financing and government policy.Ho and Liu (2004)develop a game theoretic model for analyzing the behavioral dynamics of builders and owners in construction claims.In competitive bidding,the strategic interactions among competing bidders and that between bidders and owners are com-mon,and thus game theory is a natural tool to analyze the prob-lem of concern.A well-known example of a game is the “prisoner’s dilemma”shown in Fig.1.Two suspects are arrested and held in separate cells.If both of them confess,then they will be sentenced to jail for 6years.If neither confesses,each will be sentenced for only 1year.However,if one of them confesses and the other does not,then the honest one will be rewarded by being released (in jail for 0year )and the other will be punished for 9years in jail.Note that in each cell,the first number represents player No.1’s payoff and the second one represents player No.2’s.The prisoner’s dilemma is called a “static game,”in which they act simultaneously;i.e.,each player does not know the other player’s decision before the player makes the decision.If the payoff matrix shown in Fig.1is known to all players,then the payoff matrix is a “common knowledge”to all players and this game is called a game of “complete information.”Note that the players of a game are assumed to be rational;i.e.,to maximize their payoffs.To answer what each prisoner will play/behave in this game,we will introduce the concept of “Nash equilibrium ,”one of the most important concepts in game theory.Nash equilibrium is a set of actions that will be chosen by each player.In a Nash equilib-rium,each player’s strategy should be the best response to the other player’s strategy,and no player wants to deviate from the equilibrium solution.Thus,the equilibrium or solution is “strate-gically stable”or “self-enforcing”(Gibbons 1992).Conversely,a nonequilibrium solution is not stable since at least one of the players can be better off by deviating from the nonequilibrium solution.In the prisoner’s dilemma,only the (confess,confess )solution where both players choose to confess,satisfies the stabil-ity test or requirement of Nash equilibrium.Note that although the (not confess,not confess )solution seems better off for both players compared to Nash equilibrium;however,this solution is unstable since either player can obtain extra benefit by deviating from this solution.Interested readers can refer to Gibbons (1992),Fudenberg and Tirole (1992),and Myerson (1991).Bid Compensation ModelIn this section,the bid compensation model is developed on the basis of game theoretic analysis.The model could help the ownerform bid compensation strategies under various competition situ-ations and project characteristics.Illustrative examples with nu-merical results are given when necessary to show how the model can be used in various scenarios.Assumptions and Model SetupTo perform a game theoretic study,it is critical to make necessary simplifications so that one can focus on the issues of concern and obtain insightful results.Then,the setup of a model will follow.The assumptions made in this model are summarized as follows.Note that these assumptions can be relaxed in future studies for more general purposes.1.Average bidders:The bidders are equally good,in terms oftheir technical and managerial capabilities.Since the design–build and BOT focus on quality issues,the prequalification process imposed during procurement reduces the variation of the quality of bidders.As a result,it is not unreasonable to make the “average bidders”assumption.plete information:If all players consider each other tobe an average bidder as suggested in the first assumption,it is natural to assume that the payoffs of each player in each potential solution are known to all players.3.Bid compensation for the second best bidder:Since DBIA’s(1996b )manual,document number 103,suggests that “the stipend is paid only to the most highly ranked unsuccessful offerors to prevent proposals being submitted simply to ob-tain a stipend,”we shall assume that the bid compensation will be offered to the second best bidder.4.Two levels of efforts:It is assumed that there are two levelsof efforts in preparing a proposal,high and average,denoted by H and A ,respectively.The effort A is defined as the level of effort that does not incur extra cost to improve quality.Contrarily,the effort H is defined as the level of effort that will incur extra cost,denoted as E ,to improve the quality of a proposal,where the improvement is detectable by an effec-tive proposal evaluation system.Typically,the standard of quality would be transformed to the evaluation criteria and their respective weights specified in the Request for Pro-posal.5.Fixed amount of bid compensation,S :The fixed amount canbe expressed by a certain percentage of the average profit,denoted as P ,assumed during the procurement by an average bidder.6.Absorption of extra cost,E :For convenience,it is assumedthat E will not be included in the bid price so that the high effort bidder will win the contract under the price–quality competition,such as best-value approach.This assumption simplifies the tradeoff between quality improvement and bid price increase.Two-Bidder GameIn this game,there are only two qualified bidders.The possible payoffs for each bidder in the game are shown in a normal form in Fig.2.If both bidders choose “H ,”denoted by ͑H ,H ͒,both bidders will have a 50%probability of wining the contract,and at the same time,have another 50%probability of losing the con-tract but being rewarded with the bid compensation,S .As a re-sult,the expected payoffs for the bidders in ͑H ,H ͒solution are ͑S /2+P /2−E ,S /2+P /2−E ͒.Note that the computation of the expected payoff is based on the assumption of the average bidder.Similarly,if the bidders choose ͑A ,A ͒,the expected payoffswillFig.1.Prisoner’s dilemmaD o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .be ͑S /2+P /2,S /2+P /2͒.If the bidders choose ͑H ,A ͒,bidder No.1will have a 100%probability of winning the contract,and thus the expected payoffs are ͑P −E ,S ͒.Similarly,if the bidders choose ͑A ,H ͒,the expected payoffs will be ͑S ,P −E ͒.Payoffs of an n -bidder game can be obtained by the same reasoning.Nash EquilibriumSince the payoffs in each equilibrium are expressed as functions of S ,P ,and E ,instead of a particular number,the model will focus on the conditions for each possible Nash equilibrium of the game.Here,the approach to solving for Nash equilibrium is to find conditions that ensure the stability or self-enforcing require-ment of Nash equilibrium.This technique will be applied throughout this paper.First,check the payoffs of ͑H ,H ͒solution.For bidder No.1or 2not to deviate from this solution,we must haveS /2+P /2−E ϾS →S ϽP −2E͑1͒Therefore,condition (1)guarantees ͑H ,H ͒to be a Nash equilib-rium.Second,check the payoffs of ͑A ,A ͒solution.For bidder No.1or 2not to deviate from ͑A ,A ͒,condition (2)must be satisfiedS /2+P /2ϾP −E →S ϾP −2E͑2͒Thus,condition (2)guarantees ͑A ,A ͒to be a Nash equilibrium.Note that the condition “S =P −2E ”will be ignored since the con-dition can become (1)or (2)by adding or subtracting an infinitely small positive number.Thus,since S must satisfy either condition (1)or condition (2),either ͑H ,H ͒or ͑A ,A ͒must be a unique Nash equilibrium.Third,check the payoffs of ͑H ,A ͒solution.For bid-der No.1not to deviate from H to A ,we must have P −E ϾS /2+P /2;i.e.,S ϽP −2E .For bidder No.2not to deviate from A to H ,we must have S ϾS /2+P /2−E ;i.e.,S ϾP −2E .Since S cannot be greater than and less than P −2E at the same time,͑H ,A ͒solution cannot exist.Similarly,͑A ,H ͒solution cannot exist either.This also confirms the previous conclusion that either ͑H ,H ͒or ͑A ,A ͒must be a unique Nash equilibrium.Impacts of Bid CompensationBid compensation is designed to serve as an incentive to induce bidders to make high effort.Therefore,the concerns of bid com-pensation strategy should focus on whether S can induce high effort and how effective it is.According to the equilibrium solu-tions,the bid compensation decision should depend on the mag-nitude of P −2E or the relative magnitude of E compared to P .If E is relatively small such that P Ͼ2E ,then P −2E will be positive and condition (1)will be satisfied even when S =0.This means that bid compensation is not an incentive for high effort when the extra cost of high effort is relatively low.Moreover,surprisingly,S can be damaging when S is high enough such that S ϾP −2E .On the other hand,if E is relatively large so that P −2E is negative,then condition (2)will always be satisfied since S can-not be negative.In this case,͑A ,A ͒will be a unique Nash equi-librium.In other words,when E is relatively large,it is not in the bidder’s interest to incur extra cost for improving the quality of proposal,and therefore,S cannot provide any incentives for high effort.To summarize,when E is relatively low,it is in the bidder’s interest to make high effort even if there is no bid compensation.When E is relatively high,the bidder will be better off by making average effort.In other words,bid compensation cannot promote extra effort in a two-bidder game,and ironically,bid compensa-tion may discourage high effort if the compensation is too much.Thus,in the two-bidder procurement,the owner should not use bid compensation as an incentive to induce high effort.Three-Bidder GameNash EquilibriumFig.3shows all the combinations of actions and their respective payoffs in a three-bidder game.Similar to the two-bidder game,here the Nash equilibrium can be solved by ensuring the stability of the solution.For equilibrium ͑H ,H ,H ͒,condition (3)must be satisfied for stability requirementS /3+P /3−E Ͼ0→S Ͼ3E −P͑3͒For equilibrium ͑A ,A ,A ͒,condition (4)must be satisfied so that no one has any incentives to choose HS /3+P /3ϾP −E →S Ͼ2P −3E͑4͒In a three-bidder game,it is possible that S will satisfy conditions (3)and (4)at the same time.This is different from the two-bidder game,where S can only satisfy either condition (1)or (2).Thus,there will be two pure strategy Nash equilibria when S satisfies conditions (3)and (4).However,since the payoff of ͑A ,A ,A ͒,S /3+P /3,is greater than the payoff of ͑H ,H ,H ͒,S /3+P /3−E ,for all bidders,the bidder will choose ͑A ,A ,A ͒eventually,pro-vided that a consensus between bidders of making effort A can be reached.The process of reaching such consensus is called “cheap talk,”where the agreement is beneficial to all players,and no player will want to deviate from such an agreement.In the design–build or BOT procurement,it is reasonable to believe that cheap talk can occur.Therefore,as long as condition (4)is satis-fied,͑A ,A ,A ͒will be a unique Nash equilibrium.An important implication is that the cheap talk condition must not be satisfied for any equilibrium solution other than ͑A ,A ,A ͒.In other words,condition (5)must be satisfied for all equilibrium solution except ͑A ,A ,A͒Fig.2.Two-biddergameFig.3.Three-bidder gameD o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .S Ͻ2P −3E ͑5͒Following this result,for ͑H ,H ,H ͒to be unique,conditions (3)and (5)must be satisfied;i.e.,we must have3E −P ϽS Ͻ2P −3E͑6͒Note that by definition S is a non-negative number;thus,if one cannot find a non-negative number to satisfy the equilibrium con-dition,then the respective equilibrium does not exist and the equi-librium condition will be marked as “N/A”in the illustrative fig-ures and tables.Next,check the solution where two bidders make high efforts and one bidder makes average effort,e.g.,͑H ,H ,A ͒.The ex-pected payoffs for ͑H ,H ,A ͒are ͑S /2+P /2−E ,S /2+P /2−E ,0͒.For ͑H ,H ,A ͒to be a Nash equilibrium,S /3+P /3−E Ͻ0must be satisfied so that the bidder with average effort will not deviate from A to H ,S /2+P /2−E ϾS /2must be satisfied so that the bidder with high effort will not deviate from H to A ,and condi-tion (5)must be satisfied as argued previously.The three condi-tions can be rewritten asS Ͻmin ͓3E −P ,2P −3E ͔andP −2E Ͼ0͑7͒Note that because of the average bidder assumption,if ͑H ,H ,A ͒is a Nash equilibrium,then ͑H ,A ,H ͒and ͑A ,H ,H ͒will also be the Nash equilibria.The three Nash equilibria will constitute a so-called mixed strategy Nash equilibrium,denoted by 2H +1A ,where each bidder randomizes actions between H and A with certain probabilities.The concept of mixed strategy Nash equilib-rium shall be explained in more detail in next section.Similarly,we can obtain the requirements for solution 1H +2A ,condition (5)and S /2+P /2−E ϽS /2must be satisfied.The requirements can be reorganized asS Ͻ2P −3EandP −2E Ͻ0͑8͒Note that the conflicting relationship between “P −2E Ͼ0”in condition (7)and “P −2E Ͻ0”in condition (8)seems to show that the two types of Nash equilibria are exclusive.Nevertheless,the only difference between 2H +1A and 1H +2A is that the bidder in 2H +1A equilibrium has a higher probability of playing H ,whereas the bidder in 1H +2A also mixes actions H and A but with lower probability of playing H .From this perspective,the difference between 2H +1A and 1H +2A is not very distinctive.In other words,one should not consider,for example,2H +1A ,to be two bidders playing H and one bidder playing A ;instead,one should consider each bidder to be playing H with higher probabil-ity.Similarly,1H +2A means that the bidder has a lower probabil-ity of playing H ,compared to 2H +1A .Illustrative Example:Effectiveness of Bid Compensation The equilibrium conditions for a three-bidder game is numerically illustrated and shown in Table 1,where P is arbitrarily assumed as 10%for numerical computation purposes and E varies to rep-resent different costs for higher efforts.The “*”in Table 1indi-cates that the zero compensation is the best strategy;i.e.,bid compensation is ineffective in terms of stimulating extra effort.According to the numerical results,Table 1shows that bid com-pensation can promote higher effort only when E is within the range of P /3ϽE ϽP /2,where zero compensation is not neces-sarily the best strategy.The question is that whether it is benefi-cial to the owner by incurring the cost of bid compensation when P /3ϽE ϽP /2.The answer to this question lies in the concept and definition of the mix strategy Nash equilibrium,2H +1A ,as explained previously.Since 2H +1A indicates that each bidderwill play H with significantly higher probability,2H +1A may already be good enough,knowing that we only need one bidder out of three to actually play H .We shall elaborate on this concept later in a more general setting.As a result,if the 2H +1A equilib-rium is good enough,the use of bid compensation in a three-bidder game will not be recommended.Four-Bidder Game and n-Bidder GameNash Equilibrium of Four-Bidder GameThe equilibrium of the four-bidder procurement can also be ob-tained.As the number of bidders increases,the number of poten-tial equilibria increases as well.Due to the length limitation,we shall only show the major equilibria and their conditions,which are derived following the same technique applied previously.The condition for pure strategy equilibrium 4H ,is4E −P ϽS Ͻ3P −4E͑9͒The condition for another pure strategy equilibrium,4A ,isS Ͼ3P −4E͑10͒Other potential equilibria are mainly mixed strategies,such as 3H +1A ,2H +2A ,and 1H +3A ,where the numeric number asso-ciated with H or A represents the number of bidders with effort H or A in a equilibrium.The condition for the 3H +1A equilibrium is3E −P ϽS Ͻmin ͓4E −P ,3P −4E ͔͑11͒For the 2H +2A equilibrium the condition is6E −3P ϽS Ͻmin ͓3E −P ,3P −4E ͔͑12͒The condition for the 1H +3A equilibrium isS Ͻmin ͓6E −3P ,3P −4E ͔͑13͒Illustrative Example of Four-Bidder GameTable 2numerically illustrates the impacts of bid compensation on the four-bidder procurement under different relative magni-tudes of E .When E is very small,bid compensation is not needed for promoting effort H .However,when E grows gradually,bid compensation becomes more effective.As E grows to a larger magnitude,greater than P /2,the 4H equilibrium would become impossible,no matter how large S is.In fact,if S is too large,bidders will be encouraged to take effort A .When E is extremely large,e.g.,E Ͼ0.6P ,the best strategy is to set S =0.The “*”in Table 2also indicates the cases that bid compensation is ineffec-Table pensation Impacts on a Three-Bidder GameEquilibriumE ;P =10%3H 2H +1A 1H +2A 3A E ϽP /3e.g.,E =2%S Ͻ14%*N/A N/N 14%ϽS P /3ϽE ϽP /2e.g.,E =4%2%ϽS Ͻ8%S Ͻ2%N/A 8%ϽS P /2ϽE Ͻ͑2/3͒P e.g.,E =5.5%N/AN/AS Ͻ3.5%*3.5%ϽS͑2/3͒P ϽEe.g.,E =7%N/A N/A N/A Always*Note:*denotes that zero compensation is the best strategy;and N/A =the respective equilibrium does not exist.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .tive.To conclude,in a four-bidder procurement,bid compensation is not effective when E is relatively small or large.Again,similar to the three-bidder game,when bid compensation becomes more effective,it does not mean that offering bid compensation is the best strategy,since more variables need to be considered.Further analysis shall be performed later.Nash Equilibrium of n -Bidder GameIt is desirable to generalize our model to the n -bidder game,al-though only very limited qualified bidders will be involved in most design–build or BOT procurements,since for other project delivery methods it is possible to have many bidders.Interested readers can follow the numerical illustrations for three-and four-bidder games to obtain the numerical solutions of n -bidder game.Here,only analytical equilibrium solutions will be solved.For “nA ”to be the Nash equilibrium,we must have P −E ϽS /n +P /n for bidder A not to deviate.In other words,condition (14)must be satisfiedS Ͼ͑n −1͒P −nE͑14͒Note that condition (14)can be rewritten as S Ͼn ͑P −E ͒−P ,which implies that it is not likely for nA to be the Nash equilib-rium when there are many bidders,unless E is very close to or larger than P .Similar to previous analysis,for “nH ”to be the equilibrium,we must have S /n +P /n −E Ͼ0for stability requirement,and condition (15)for excluding the possibility of cheap talk or nA equilibrium.The condition for the nH equilibrium can be reorga-nized as condition (16).S Ͻ͑n −1͒P −nE ͑15͒nE −P ϽS Ͻ͑n −1͒P −nE͑16͒Note that if E ϽP /n ,condition (16)will always be satisfied and nH will be a unique equilibrium even when S =0.In other words,nH will not be the Nash equilibrium when there are many bidders,unless E is extremely small,i.e.,E ϽP /n .For “aH +͑n −a ͒A ,where 2Ͻa Ͻn ”to be the equilibrium so-lution,we must have S /a +P /a −E Ͼ0for bidder H not to devi-ate,S /͑a +1͒+P /͑a +1͒−E Ͻ0for bidder A not to deviate,and condition (15).These requirements can be rewritten asaE −P ϽS Ͻmin ͓͑a +1͒E −P ,͑n −1͒P −nE ͔͑17͒Similarly,for “2H +͑n −2͒A ,”the stability requirements for bidder H and A are S /͑n −1͒ϽS /2+P /2−E and S /3+P /3−E Ͻ0,re-spectively,and thus the equilibrium condition can be written as ͓͑n −1͒/͑n −3͔͒͑2E −P ͒ϽS Ͻmin ͓3E −P ,͑n −1͒P −nE ͔͑18͒For the “1H +͑n −1͒A ”equilibrium,we must haveS Ͻmin ͕͓͑n −1͒/͑n −3͔͒͑2E −P ͒,͑n −1͒P −nE ͖͑19͒An interesting question is:“What conditions would warrant that the only possible equilibrium of the game is either “1H +͑n −1͒A ”or nA ,no matter how large S is?”A logical response to the question is:when equilibria “aH +͑n −a ͒A ,where a Ͼ2”and equilibrium 2H +͑n −2͒A are not possible solutions.Thus,a suf-ficient condition here is that for any S Ͼ͓͑n −1͒/͑n −3͔͒͑2E −P ͒,the “S Ͻ͑n −1͒P −nE ”is not satisfied.This can be guaranteed if we have͑n −1͒P −nE Ͻ͓͑n −1͒/͑n −3͔͒͑2E −P ͒→E Ͼ͓͑n −1͒/͑n +1͔͒P͑20͒Conditions (19)and (20)show that when E is greater than ͓͑n −1͒/͑n +1͔͒P ,the only possible equilibrium of the game is either 1H +͑n −1͒A or nA ,no matter how large S is.Two important practical implications can be drawn from this finding.First,when n is small in a design–build contract,it is not unusual that E will be greater than ͓͑n −1͒/͑n +1͔͒P ,and in that case,bid compensa-tion cannot help to promote higher effort.For example,for a three-bidder procurement,bid compensation will not be effective when E is greater than ͑2/4͒P .Second,when the number of bidders increases,bid compensation will become more effective since it will be more unlikely that E is greater than ͓͑n −1͒/͑n +1͔͒P .The two implications confirm the previous analyses of two-,three-,and four-bidder game.After the game equilibria and the effective range of bid compensation have been solved,the next important task is to develop the bid compensation strategy with respect to various procurement situations.Table pensation Impacts on a Four-Bidder GameEquilibriumE ;P =10%4H 3H +1A 2H +2A 1H +3A 4A E ϽP /4e.g.,E =2%S Ͻ22%*N/A N/A N/A S Ͼ22%P /4ϽE ϽP /3e.g.,E =3%2%ϽS Ͻ18%S Ͻ2%N/A N/A S Ͼ18%P /3ϽE ϽP /2e.g.,E =4%6%ϽS Ͻ14%2%ϽS Ͻ6%S Ͻ2%N/A S Ͼ14%P /2ϽE Ͻ͑3/5͒P e.g.,E =5.5%N/A 6.5%ϽS Ͻ8%3%ϽS Ͻ6.5%S Ͻ3%S Ͼ8%͑3/5͒P ϽE Ͻ͑3/4͒P e.g.,E =6.5%N/AN/AN/AS Ͻ4%*S Ͼ4%͑3/4͒P ϽEe.g.,E =8%N/A N/A N/A N/AAlways*Note:*denotes that zero compensation is the best strategy;and N/A=respective equilibrium does not exist.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .。
Asp net技术 毕业论文外文翻译

技术的前身ASP技术,是在IIS 2.0上首次推出(Windows NT 3.51),当时与 ADO 1.0 一起推出,在IIS 3.0 (Windows NT 4.0)发扬光大,成为服务器端应用程序的热门开发工具,微软还特别为它量身打造了Visual 标识InterDev开发工具,在1994年到2000年之间,ASP技术已经成为微软推展Windows NT 4.0平台的关键技术之一,数以万计的ASP网站也是这个时候开始如雨后春笋般的出现在网络上。
它的简单以及高度可定制化的能力,也是它能迅速崛起的原因之一。
不过ASP的缺点也逐渐的浮现出来:意大利面型的程序开发方法,让维护的难度提高很多,尤其是大型的ASP应用程序。
直译式的VBScript或JScript语言,让效能有些许的受限。
延展性因为其基础架构扩充性不足而受限,虽然有COM元件可用,但开发一些特殊功能(像文件上传)时,没有来自内置的支持,需要寻求第三方软件商开发的元件。
1997年时,微软开始针对ASP的缺点(尤其是意大利面型的程序开发方法)准备开始一个新项目来开发,当时的主要领导人Scott Guthrie刚从杜克大学毕业,他和IIS团队的Mark Anders经理一起合作两个月,开发出了下一代ASP 技术的原型,这个原型在1997年的圣诞节时被发展出来,并给予一个名称:XSP,这个原型产品使用的是Java语言。
不过它马上就被纳入当时还在开发中的CLR平台,Scott Guthrie事后也认为将这个技术移植到当时的CLR平台,确实有很大的风险(huge risk),但当时的XSP团队却是以CLR开发应用的第一个团队。
为了将XSP移植到CLR中,XSP团队将XSP的内核程序全部以C#语言重新撰写,并且改名为ASP+,作为ASP技术的后继者,并且也会提供一个简单的移转方法给ASP开发人员。
ASP+首次的Beta版本以及应用在PDC 2000中亮相,由Bill Gates 主讲Keynote(即关键技术的概览),由富士通公司展示使用COBOL语言撰写ASP+应用程序,并且宣布它可以使用Visual 、C#、Perl与Python语言(后两者由ActiveState公司开发的互通工具支持)来开发。
毕业设计外文资料翻译译文

附件1:外文资料翻译译文包装对食品发展的影响一个消费者对某个产品的第一印象来说包装是至关重要的,包括沟通的可取性,可接受性,健康饮食形象等。
食品能够提供广泛的产品和包装组合,传达自己加工的形象感知给消费者,例如新鲜包装/准备,冷藏,冷冻,超高温无菌,消毒(灭菌),烘干产品。
食物的最重要的质量属性之一,是它的味道,其影响人类的感官知觉,即味觉和嗅觉。
味道可以很大程度作退化的处理和/或扩展存储。
其他质量属性,也可能受到影响,包括颜色,质地和营养成分。
食品质量不仅取决于原材料,添加剂,加工和包装的方法,而且其预期的货架寿命(保质期)过程中遇到的分布和储存条件的质量。
越来越多的竞争当中,食品生产商,零售商和供应商;和质量审核供应商有显着提高食品质量以及急剧增加包装食品的选择。
这些改进也得益于严格的冷藏链中的温度控制和越来越挑剔的消费者。
保质期的一个定义是:在食品加工和包装组合下,在食品的容器和条件,在销售点分布在特定系统的时间能保持令人满意的食味品质。
保质期,可以用来作为一个新鲜的概念,促进营销的工具。
延期或保质期长的产品,还提供产品的使用时间,方便以及减少浪费食物的风险,消费者和/或零售商。
包装产品的质量和保质期的主题是在第3章中详细讨论。
包装为消费者提供有关产品的重要信息,在许多情况下,使用的包装和/或产品,包括事实信息如重量,体积,配料,制造商的细节,营养价值,烹饪和开放的指示,除了法律准则的最小尺寸的文字和数字,有定义的各类产品。
消费者寻求更详细的产品信息,同时,许多标签已经成为多语种。
标签的可读性是为视障人士的问题,这很可能成为一个对越来越多的老年人口越来越重要的问题。
食物的选择和包装创新的一个主要驱动力是为了方便消费者的需求。
这里有许多方便的现代包装所提供的属性,这些措施包括易于接入和开放,处置和处理,产品的知名度,再密封性能,微波加热性,延长保质期等。
在英国和其他发达经济体显示出生率下降和快速增长的一个相对富裕的老人人口趋势,伴随着更加苛刻的年轻消费者,他们将要求和期望改进包装的功能,如方便包揭开(百货配送研究所,IGD)。
基于ASP开发Web应用程序论文-外文翻译+原文【免费】

ASP外文翻译+原文ENGLISHE:Develop Web application program using ASP the architecture that must first establish Web application. Now in application frequently with to have two: The architecture of C/S and the architecture of B/S.Client/server and customer end / server hold the architecture of C/S.The customer / server structure of two floor.Customer / server ( Client/Server ) model is a kind of good software architecture, it is the one of best application pattern of network. From technology, see that it is a logic concept, denote will a application many tasks of decomposing difference carry out , common completion is entire to apply the function of task. On each network main computer of web site, resource ( hardware, software and data ) divide into step, is not balanced, under customer / server structure, without the client computer of resource through sending request to the server that has resource , get resource request, so meet the resource distribution in network not balancedness. With this kind of structure, can synthesize various computers to cooperate with work, let it each can, realize the scale for the system of computer optimization ( Rightsizing ) with scale reduce to melt ( Downsizing ). Picture is as follows:It is most of to divide into computer network application into two, in which the resource and function that part supports many users to share , it is realized by server; Another part faces every user , is realized by client computer, also namely, client computer is usual to carry out proscenium function , realizes man-machine interaction through user interface , or is the application program of specific conducted user. And server usually carries out the function of backstage supporter , manages the outside request concerning seting up, accepting and replying user that shared. For a computer, it can have double function , is being certain and momentary to carve to act as server , and again becomes client computer in another time.Customer / server type computer divide into two kinds, one side who offers service is called as server , asks one side of service to be called as customer. To be able to offer service, server one side must have certain hardware and corresponding server software; Also, customer one side mustalso have certain hardware and corresponding customer software.There must be a agreement between server and customer, both sides communicate according to this agreement.Apply customer / server model in Internet service , the relation between customer and server is not immutable. Some Internet node offers service on the one hand , also gets service on the other hand from other node; It is even in one time dialogue course, mutual role also exchanges probably. As in carry out file transmission , if be called as one side who offers file server, is called as one side who gets file customer, when using get or mget order since another node takes file, can think that what self use and it is client computer , is using put or mput order to another node dispatch file can again think the machine that used self is server.Multilayer customer / server structureAlong with the development of enterprise application, recently, have again arisen a kind of new multilayer architecture, it applies customer end to divide into two minutes: Customer application and server apply. Customer application is the part of original customer application , is another and partial to have been transfered to server to apply. New customer application takes the responsibility for user interface and simple regular business logic and new server application resident core , changeable business logic. Therefore its structure has become new ( Client application + Server application )/Server structure. Following picture shows:This kind of structure has solved traditional Client/Server can expand problem, have reduced customer end business logic , and have reduced the requirement of customer end for hardware. At the same time because of a lot of business logic concentrations have gone to unitary application server on, the maintenance work of application system had been also concentrated together, have eliminated the problem in the traditional structure of Client/Server that software distributes. This kind of structure is called as the architecture of B/S.Browser/Server and browser / server hold the architecture of B/S. Onessence, Browser/Server is also a kind of structure of Client/Server, it is a kind of from the traditional two levels of structural development of Client/Server come to the three-layer structural special case of Client/Server that applied on Web.In the system of Browser/Server, user can pass through browser to a lot of servers that spread on network to send request. The structure of Browser/Server is maximum to have simplified the work of client computer, on client computer, need to install and deploy few customer end software only , server will bear more work, for database visit and apply program carry out will in server finish.Under the three-layer architecture of Browser/Server, express layer ( Presentatioon ) , function layer ( Business Logic ) , data layer ( Data Service ) have been cut the unit of 3 relative independences: It is the first layer of to express layer: Web browser.In expressing layer contain system show logic, locate in customer end. It's task is to suggest by Web browser to the certain a Web server on network that service is asked , after verifying for user identity, Web server delivers needed homepage with HTTP agreement to customer end, client computer accept the homepage file that passed , and show it in Web browser on.Second layer function layer: Have the Web server of the application function of program extension.In function layer contain the systematic handling of general affairs logic, locate in Web server end. It's task is the request concerning accepting user , need to be first conducted and corresponding to expand application program and database to carry out connection , passes through the waies such as SQL to database server to put forward data handling to apply for, then etc. database server the result of handling data submit to Web server, deliver again by Web server to return customer end.The number of plies of 3th according to layer: Database server.In data layer contain systematic data handling logic, locate in database server end. It's task is to accept the request that Web server controls for database, realization is inquired and modified for database , update etc. function, submit operation result to Web server.Careful analysis is been easy to see , the architecture of Browser/Server of three-layer is the handling of general affairs of the two levels of structure of Client/Server logic modular from the task of client computer in split , from the first floor of individual composition bear the pressure of its task and such client computer have alleviated greatly, distribute load balancedly and have given Web server, so from the structural change of Client/server of original two floor the structure of Browser/Server of three-layer. This kind of three-layer architecture following picture shows.This kind of structure not only client computer from heavy burden andthe requirement of performance that rises continuously for it in liberation come out , also defend technology people from heavy maintenance upgrading work in free oneself. Since client computer handles general affairs , logic partial minutes have given function server, make client computer right off " slender " a lot of, do not take the responsibility for handling complex calculation and data again visit etc. crucial general affairs, is responsible to show part, so, maintenance people do not rush about again for the maintenance work of program between every client computer, and put major energy in the program on function server update work. Between this kind of three-layer structural layer and layer, the mutually independent change of any first floor does not affect the function of other layer. It has changed the defect of the two levels of architecture of Client/Server of tradition from foundation, it is the transform with deep once in application systematic architecture.The contrast of two architecturesThe architecture of Browser/Server and the architecture ofClient/Server compare with all advantages that not only have the architecture of Client/Server and also have the architecture ofClinet/Server the unique advantage that place does not have: Open standard: The standard adopted by Client/Server only in department unification for but, it's application is often for special purpose.It is lower to develop and defend cost: It need to be implemented on all client computers that the application of Client/Server must develop the customer end software for special purpose, no matter installation and disposition escalate still, have wasted manpower and material resources maximumly. The application of Browser/Server need in customer end have general browser , defend and escalate to work in server end go on , need not carry out any change as customer holds , have reduced the cost of development and maintenance so greatly.It is simple to use , interface friendly: The interface of the user of Client/Server is decided by customer end software, interface and the method of its use are not identical each, per popularize a system of Client/Server ask user study from the beginning, is hard to use. The interface of the user of Browser/Server is unified on browser, browser is easy to use , interface friendly, must not study use again other software, the use of a Lao Yong Yi that has solved user problem.Customer end detumescence: The customer end of Client/Server has the function that shows and handles data , as the requirement of customer end is a client computer " it is fat " very high. The customer of Browser/Server holds the access that not takes the responsibility for database again and the etc. task of complex data calculation, need it only show , the powerful role that has played server fully is so large to have reduced the requirement for customer end, customer end become very " thin ".。
网络应用程序ASP中英文对照外文翻译文献

中英文资料外文翻译文献Moving from Classic ASP to ABSTRACT is Microsoft new offering for Web application development, innovation within have resulted in significant industry popularity for this product. Consequently there is an increased need for education. The Web Application Development is a third year undergraduate course. To meet the demands of both industry and students, we have changed the focus of this course from Classic ASP to . This paper reports this move. The significant features of and the motivations for this move are discussed. The process, the problems encountered, and some helpful online learning resources are described.Key wordsWeb Application Development, Classic ASP, , Move, 1. INTRODUCTION is not just a new version of ASP. It provides innovation for moving Windows applications to Web applications. Web services and the .NET framework have made the vision of the Web as the next generation computing platform a reality. With server controls, Web forms and “code-behind”, we can develop a Web application by using a complete object-oriented programming (OOP) model. This increases the popularity of in industry. The industry project is the final course of the Bachelor of Computing Systems (BCS) degree at UNITEC, in which students undertake a real-world project. We have observed a rapid growth of related industry projects in our school.The Web Application Development (WAD) paper is a third year undergraduate course. It was originally offered using ASP 2.0 and ColdFusion. To meet the demands from both industry and students, we have changed the course content to cover , Visual () and ColdFusion. This change commencedwith the first semester of 2003.This paper will examine the features of and explain why these are unique. The motivations for moving to are discussed by analyzing the current situation of related to industry projects in our school, analyzing the results of short surveys on students, and analyzing whether is a better tool for teaching. Problems encountered during the move are also discussed and some of the learning resources are presented. It is anticipated that these will be helpful for teachers who intend to introduce .2. WHAT MAKES SPECIAL?There are many articles on the Internet discussing the advantages of over Classic Active Server Pages (ASP), such as that introduces an integrated development environment (IDE), a single development library for all types of applications, compiled as well as strongly typed code, and a true OO approach to Web application development (Goodyear, 2002, Bloom, 2002).Traditionally, we have three versions of ASP (ASP 1.0, ASP 2.0 and ASP 3.0), which are called Classic ASP. Although each version provides certain new features to overcome the shortcomings of its predecessors, these versions of ASP follow the same working model and share many limitations. Their successor supports complete new working model while preserving the traditional working model and provides innovative techniques to overcome the limitations of Classic ASP.2.1. Architecture enhances and extends the Windows DNA (Windows Distributed interNet Application). The windows DNA specification is a methodology for building n-tier applications using Microsoft (DCOM/COM) technologies. Breaking applications into functional pieces and deploying these across a network is a strategy to make better use of organizational resources. This needs a well-planned architecture. In the past, usually it was the windows DNA. DCOM communication normally has problems with firewalls and proxy servers. This means Windows DNA usually onlyworks well within an intranet, not on the Internet. DCOM/ COM also need registry entries. makes the process of creating and integrating Web Services easier, which can be used in a similar manner to the Windows DNA. Here DCOM/COM is no longer involved. HTTP (as channels), SOAP (as formatters) and XML are used for communication and data-transfer between distributed components. This overcomes the problem of communicating across the Internet and across corporate firewalls without resorting to proprietary solutions that require additional communications ports to be opened to external access. In addition, URI (uniform resource identifier) and UDDI (Universal Description Discovery and Integration) are used for remote components references instead of registry entries.2.2. Development integrates seamlessly with IDE. includes built-in support for creating and modifying content. This unifies the ASP/VB programming models for the developers. Instead of opening multiple IDEs (as with Classic ASP platform), developers can open a single IDE and do all their work from a clean, consistent interface. is equipped with powerful debugging environment. This means that the powerful debugger for Windows applications is now available to debug Web applications as well. enables programmers to take advantage of the OOP model, for example, code sharing. Under OOP model, one of the most common ways to achieve code sharing is inheritance, which is not available in Classic ASP. Since complete OO features are supported in , developers can transfer their OO design smoothly into code, enabling a software company to keep their Windows application development styles, with which they are familiar, in Web application development; and also they can convert their Windows applications into Web applications without major modifications.’s improved state maintenance features enable us to provide users with Web applications that are richer and faster than Classis ASP (Olges,2002). supports advanced session state management. There are two major problems with session management in Classic ASP: session objects are stored in the Web server memory and session IDs are stored on the client computers as cookies. These prevent session management from being efficiently implemented. solves these problems in two ways: it provides a “cookieless” option for session objects so that a session ID can be passed via URL; it provides three different session modes (inprocess, state server, and SQL Server), so that a session object can either be stored on the Web server, a remote server or a database.3. THE MOTIVATIONS FOR MOVING3.1. The industry motivationI’ve checked almost all the industry projects in our school for three semesters on whether they are WAD related, if yes, then what tools they have used. Table 1 shows a brief summary of the results.For these three semesters, the total ASP/ projects are increasing, but slowly. However the Classic ASP projects are dropping quickly and the projects are increasing rapidly (in the speed of more than 12% per semester). This gives us an idea that is preferred over Classic ASP in industry especially given that is only officially first released in 2002. Our student’s feedbacks from their industry communication confirm this view. A huge number of articles on the Internet also support this view. This encourages us to drop Classic ASP and move to in our WAD course. Higher education has over years recognized that it is a service industry and has to revaluate their approach in the industry by placing greater emphasis on meeting the expectations and needs of their stakeholders (Nair, 2002). 3.2. The student motivationThe students demand . When students enroll in our WAD course, most of them are aiming to become a professional software developer. As a matter of fact, some of them already are software developers, or they were software developers and are seeking to return to the workplace. Techniques highly demanded in workplace are of great interest to them.A short survey has been given to past students and current students respectively. For the past students, among the 11 responses, 100% students still want to learn ; and if they are given choice, 82% students prefer to learn rather than Classic ASP, 18% students like to learn both. These answers are also supported by comments, such as “I would prefer to know the technology that the industry requires me to work with”, “I would like to work in future as a WAD professional andI think would be usefu l in this field.” For the current students, among the16 responses, 75% students prefer to learn rather than Classic ASP. However, 25% students answered no idea. This could be due to that they lack of knowledge of Classic ASP. This survey is done after 6 weeks of teaching.3.3. The pedagogical motivationPedagogically speaking, a good tool for industry is not necessarily a good tool for teaching. Is a better tool for teaching than Classic ASP? provides much richer language features than Classic ASP. We often have options to perform certain tasks. A key benefit of is that there exists a more gradual transition in programming models from simple to powerful, or from easy to difficult. Although supports OOP model, you don’t have to program by using that model. A Web form without “code-behind” will work perfectly. An web page in complete Classic ASP model will still work. Although is integrated with , we are not limited to use . A notepad and a FTP client with a pre-created Web application directory also allow us to develop a reasonably large application. With , we can either develop a large distributed application with numbers of Web services and consumers, or develop a single simple Web application. Therefore, provides sufficient room for us to organize course materials at a suitable level for the students. The challenge for a lecturer is how to settle in at the right balance of power vs. simplicity, or at the right balance of difficulty vs. ease. offers a more conventional approach to programming than does Classic ASP. It possesses all the features of a modern programming language. The Classic ASP programming style favors developers coming from HTML coding background, whereas is more suited to professional software developers. Given our entire WAD students have taken C/Delphi programming courses, and our aim is to output software professionals, is a better teaching tool for us. enhances the programming concepts the students learned from the previous courses and provides a good bridge to Advanced Distributed Computing and Advanced Object- Oriented Programming.4. THE PROCESSOur first step was to learn . After reading books and online tutorials, the next step is practical. We set an implementation server on the laptop in a stand-alone environment. The .NET Framework requires IIS 5 and the above; Windows 2000 or Windows XP professional will work with .NET. However, Windows XP home edition or Windows 98 won’t work. On the client side, we can either use or WebMatrix. Among these, only costs money. The .NET Framework is included inside the package. We also can download the .NET Frameworkfrom the Internet. After the .NET Framework is installed, the QuickStart Tutorial is set up. It is also found on the Internet. This tutorial is a good starting point for experienced developers. It is claimed that the readers “should be fluent in HTML and general Web development term inology. …… should be familiar with the concepts behind interactive Web pages, including forms, scripts, and data access.” More complicated examples can be found from Microsoft .NET Framework SDK Documentation or Microsoft Visual Studio .NET Documentation.The second step was to test the teaching environment. A teaching server was set up for the Intranet on campus. It is configured for the client computers in the teaching lab. is installed on the client computers. provides two ways to access the Web server: FrontPage server extensions and File share. The FrontPage server extension is used on our teaching server. Programming testing has been done on all the major aspects of WAD. Except a few special ones, most of the problems occurred during the testing were minor problems which, after the communication with our Web technician, were resolved.Teaching materials have been updated. The major changes have been made on the data interaction, form and controls, application/session management, and error handling. Given that has made XML very practical and the using of Web service much easier. A lecture on XML and Web service has been added. As a result, ColdFusion lectures are reduced. The assessment has been adjusted accordingly. 5. THE PROBLEMSWe have to admit that with is a much more complicated client server environment than the Classic ASP environment. This complexity comes from the configuration system and the integration between the client computers and the Web server.On server, each level of the application directory can have a configuration file. All these configuration files are optional except Machine.config. A developer has full control over those optional configuration files. Developers become more involved with the server settings via these files. One problem that happened to several students and myself on our home servers is the permission problem. We found our applications didn’t have permission to write to database/XML files. Microsoft (2003) provides three solutions to this problem. The simplest one is to change the Machine.config file and set the username attribute to SYSTEM in the <processModel> section.We observed that behave differently in a stand-alone environment, asingle user client server environment, and a multiple user client server environment. A few problems don’t occur in the first two environments occur frequently in the last environment. The major one is when we try to create a new project or open an existing project, we often get an error message, “The user name or password you entered is incorrect, or you do not have authorization to permit this operation”, even if our user name and password are perfectly correct. This problem seems to be caused by FrontPage server extensions. Regularly cleaning VSWebCache partially solved the problem. This approach is confirmed by Kiely (2003).Another problem is a debug problem. When we try to use Debug|Start or Debug|Start Without Debugging in the multiple user client server environment within , we often get error messages. “…… Unable to start debugging on the web server. ……”. However,we don’t have the same problem for Debug|Start Without Debugging in the single user client server environment. We don’t have any problem in a standalone environment. After adding users to the debugging group on the server, the problem still exists. The reason of this problem is not clear to the author.6. RESOURCESThere is a huge amount of helpful online learning resources related to . Here are a couple of them, which are particularly helpful to the author./aspxtreme/. Accessed April 17, 2003. This site provides many tutorials covering wide range concepts. They usually show you how to do a particular task step by step. Some of the examples have both C# and VB versions./resources/spcollections/aspnet/default.asp. Accessed April 17, 2003. This site provides many articles from intermediate level to highly technical level. These articles are mostly from online magazines and they discuss many interesting topics in ./aspnet/. Accessed May 5, 2003. This site provides free source code and tutorials for developers. We can find complete examples for some typical tasks./. Accessed May 5, 2003. This site provides wide range of tutorials for different levels of readers. This is my favorite site. I’ve been with it since Classic ASP. I found that whenever I meet a challenging problem, I always find a solution here./tutorialsindex.aspx. Accessed May 5, 2003. This site provides wide range of articles for different levels of readers. Articles are groupedaccording to topics, which is very helpful when we do research on a particular topic.7. CONCLUSIONMoving from Classic ASP to has proven to be a challenging and exciting process. The author has learned a lot in this process. From the responses to our six-week survey, 100% students feel our WAD course challenging. However, most of them still prefer to learn rather than Classic ASP. We feel confident about the move. The issue is how to organize the course and help the students meet the challenge. is certainly an outstanding tool for both teaching and development. As a new development platform, we do need some time to absorb all the new features.从经典ASP到摘要是微软公司基于网络应用程序新开发出的产品,这个产品的普及在的创新当中具有重大意义,因此在方面的教育有了很大的需求。
关于ASP的英文文献及其翻译
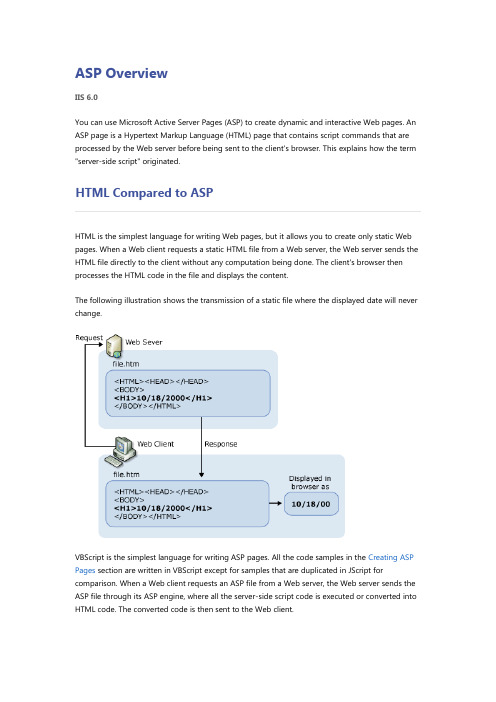
ASP OverviewIIS 6.0You can use Microsoft Active Server Pages (ASP) to create dynamic and interactive Web pages. An ASP page is a Hypertext Markup Language (HTML) page that contains script commands that are processed by the Web server before being sent to the client's browser. This explains how the term "server-side script" originated.HTML Compared to ASPHTML is the simplest language for writing Web pages, but it allows you to create only static Web pages. When a Web client requests a static HTML file from a Web server, the Web server sends the HTML file directly to the client without any computation being done. The client's browser then processes the HTML code in the file and displays the content.The following illustration shows the transmission of a static file where the displayed date will never change.VBScript is the simplest language for writing ASP pages. All the code samples in the Creating ASP Pages section are written in VBScript except for samples that are duplicated in JScript for comparison. When a Web client requests an ASP file from a Web server, the Web server sends the ASP file through its ASP engine, where all the server-side script code is executed or converted into HTML code. The converted code is then sent to the Web client.The following illustration shows the transmission of dynamically generated content where the displayed date reflects the date at the time of the request.If you are an HTML author, you will find that server-side scripts written in ASP are an easy way to begin creating more complex, real-world Web applications. If you have ever wanted to store HTML form information in a database, personalize Web sites according to visitor preferences, or use different HTML features based on the browser, you will find that ASP provides a compelling solution. For example, previously, to process user input on the Web server you would have had to learn a language such as Perl or C to build a conventional Common Gateway Interface (CGI) application. With ASP, however, you can collect HTML form information and pass it to a database using simple server-side scripts embedded directly in your HTML documents. If you are already familiar with scripting languages such as VBScript or JScript (JScript is the Microsoft implementation of the ECMA 262 language specification), you will have little trouble learning ASP.ASP ProcessingAn ASP page is requested the same way that an HTML page is requested. A request can optionally contain a querystring after a question mark (?), using the following syntax:Copyhttp://Server_name/MyASPFile.asp?var1=12&var2=BrownWhen the server receives a request for an ASP file, it processes server-side script code contained in the file to build the HTML Web page that is sent to the browser. In addition to server-side script code, ASP files can contain HTML (including related client-side scripts) as well as calls to COM components that perform a variety of tasks, such as connecting to a database or processing business logic.IIS processes an ASP file in the following order when a request is received from a client:1.If an ISAPI filter is installed on the Web site, the ISAPI filters is processed first. This is truefor all applications.2.If the ASP application contains a Global.asa file in the root directory, the Global.asa isprocessed. Global.asa files specify event scripts and declare objects that have session orapplication scope. They donot display content; instead they stores event information andobjects used globally by the ASP application.3.In the requested ASP file, IIS separates the script blocks from the static HTML code blocks,reserving the static code in the response body.4.IIS processes the script blocks. The script blocks might include transaction processing,database access calls, or calls to COM components in which case COM+ handles some ofthe processing.5.After the ASP page script blocks are processed, their output is injected into the responsebody with the static HTML code.6.The response is sent to the client.Caution:ASP and COM ComponentsWith ASP, you can combine HTML pages, script commands, and COM components to create interactive Web pages or powerful Web-based applications, which are easy to develop and modify.COM components dramatically extend the power of ASP. COM components are pieces of compiled code that can be called from ASP pages. COM components are secure, compact, and reusable objects that are compiled as DLLs. They can be written in Visual C++, Visual Basic, or other languages that support COM.翻译你可以使用微软动态服务器页面(ASP)创建动态的、交互的网页。
英文文献及中文翻译_ASP.NET概述ASP.NETOverview

英文文献及中文翻译 Overview is a unified Web development model that includes the services necessary for you to build enterprise-class Web applications with a minimum of is part of the .NET Framework, and when coding applications you have access to classes in the .NET Framework.You can code your applications in any language compatible with the common language runtime (CLR), including Microsoft Visual Basic and C#. These languages enable you to develop applications that benefit from the common language runtime, type safety, inheritance, and so on.If you want to try , you can install Visual Web Developer Express using the Microsoft Web Platform Installer, which is a free tool that makes it simple to download, install, and service components of the Microsoft Web Platform.These components include Visual Web Developer Express, Internet Information Services (IIS), SQL Server Express, and the .NET Framework. All of these are tools that you use to create Web applications. You can also use the Microsoft Web Platform Installer to install open-source and PHP Web applications.Visual Web DeveloperVisual Web Developer is a full-featured development environment for creating Web applications. Visual Web Developer provides an ideal environment in which to build Web sites and then publish them to a hosting site. Using the development tools in Visual Web Developer, you can develop Web pages on your own computer. Visual Web Developer includes a local Web server that provides all the features you need to test and debug Web pages, without requiring Internet Information Services (IIS) to be installed.Visual Web Developer provides an ideal environment in which to build Web sitesand then publish them to a hosting site. Using the development tools in Visual Web Developer, you can develop Web pages on your own computer. Visual Web Developer includes a local Web server that provides all the features you need to test and debug Web pages, without requiring Internet Information Services (IIS) to be installed.When your site is ready, you can publish it to the host computer using the built-in Copy Web tool, which transfers your files when you are ready to share them with others. Alternatively, you can precompile and deploy a Web site by using the Build Web Site command. The Build Web Sitecommand runs the compiler over the entire Web site (not just the code files) and produces a Web site layout that you can deploy to a production server.Finally, you can take advantage of the built-in support for File Transfer Protocol (FTP).Using the FTP capabilities of Visual Web Developer, you can connect directly to the host computer and then create and edit files on the server. Web Sites and Web Application ProjectsUsing Visual Studio tools, you can create different types of projects, which includes Web sites, Web applications, Web services, and AJAX server controls.There is a difference between Web site projects and Web application projects. Some features work only with Web application projects, such as MVC and certain tools for automating Web deployment. Other features, such as Dynamic Data, work with both Web sites and Web application projects.Page and Controls FrameworkThe page and controls framework is a programming framework that runs on a Web server to dynamically produce and render Web pages. Web pages can be requested from any browser or client device, and renders markup (such as HTML) to the requesting browser. As a rule, you can use the samepage for multiple browsers, because renders the appropriate markup for the browser making the request. However, you can design your Web page to target a specific browser and take advantage of the features of that browser. Web pages are completely object-oriented. Within Web pages you can work with HTML elements using properties, methods, and events. The page framework removes the implementation details of the separation of client and server inherent in Web-based applications by presenting a unified model for responding to client events in code that runs at the server. The framework also automatically maintains the state of a page and the controls on that page during the page processing life cycle.The page and controls framework also enables you to encapsulate common UI functionality in easy-to-use, reusable controls. Controls are written once, can be used in many pages, and are integrated into the Web page that they are placed in during rendering.The page and controls framework also provides features to control the overall look and feel of your Web site via themes and skins. You can define themes and skins and then apply them at a page level or at a control level.In addition to themes, you can define master pages that you use to create a consistent layout for the pages in your application. A single master page defines the layout and standard behavior that you want for all the pages (or a group of pages) in your application. You can then create individual content pages that contain the page-specific content you want to display. When users request the content pages, they merge with the master page to produce output that combines the layout of the master page with the content from the content page. The page framework also enables you to define the pattern for URLs that will be used in your site. This helps with search engine optimization (SEO) and makes URLs more user-friendly.The page and control framework is designed to generate HTML thatconforms to accessibility guidelines. CompilerAll code is compiled, which enables strong typing, performance optimizations, and early binding, among other benefits. Once the code has been compiled, the common language runtime further compiles code to native code, providing improved performance. includes a compiler that will compile all your application components including pages and controls into an assembly that the hosting environment can then use to service user requests.Security InfrastructureIn addition to the security features of .NET, provides an advanced security infrastructure for authenticating and authorizing user access as well as performing other security-related tasks. You can authenticate users using Windows authentication supplied by IIS, or you can manage authentication using your own user database using forms authentication and membership. Additionally, you can manage the authorization to the capabilities and information of your Web application using Windows groups or your own custom role database using roles. You can easily remove, add to, or replace these schemes depending upon the needs of your application. always runs with a particular Windows identity so you can secure your application using Windows capabilities such as NTFS Access Control Lists (ACLs),database permissions, and so on.State-Management Facilities provides intrinsic state management functionality that enables you to store information between page requests, such as customer information or the contents of a shopping cart. You can save and manage application-specific, session-specific, page-specific, user-specific, and developer-defined information. This information can beindependent of any controls on the page. offers distributed state facilities, which enable you to manage state information across multiple instances of the same application on one computer or on several computers. 概述是一个统一的Web开发模型,它包括您使用尽可能少的代码生成企业级Web应用程序所必需的各种服务。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
网络课堂:一个大型互动远程教学平台林,SW1,程,K L2,王,R3,周,H4和H5陈,S1cs_lswaa@t.hk2cs_cklaa@t.hk3cs_wrx@t.hk4cs_zhxaa@t.hk5gchan@t.hk香港科技大学计算机科学系摘要:传统上,为了与教员进行更好的交流互动,讲座一般在学生所处的教室进行。
这种模式对于有些学生并不是很方便和划算,例如对于那些正在工作的、行动不便的、生活在偏远地区的,或者类似在SARS期间被社会隔离的人来说。
伴随着宽带互联网连接和无线媒体(Wi-fi 和 3G)的普遍渗透,我们开发了一个平台,让讲座可以通过互联网以交互方式进行。
该项目被称为“网络课堂”,提供了一种类似于现今的传统教室,但学生们分布在互联网的教学体验。
学生可以在任何时间任何地点使用他们的 PC 或便携式计算机通过互联网和无线媒体向他们的导师提问题。
视频、音频、以及白板也流向实时的用户终端。
利用现有现成的计算产品和最先进的网络技术,该系统可扩展到数百名学生。
它具有成本效益,能够有效地突破地域限制让学生来听取讲座。
使用该系统的学生传来的最初反馈是积极和鼓舞人心的。
关键词:远距离学习,网络课堂,互动、教育、分布式系统、多媒体应用和通信网引言随着计算设备和计算机使用的巨大增长,人与人之间的地理距离已显著减少。
简单举几个目前正在使用的互联网软件的例子:网络会议,网络电话,ICQ 聊天等等。
利用这些,人们可以在世界的各个角落,与他人进行比以往任何时候都更经济、更有效地沟通。
近来,香港政府一直在努力推行“终身学习”的理念。
然而,在香港的工作时间和生活节奏,让人们几乎不可能在一个固定的时间,固定的地点进行学习。
在香港科技大学计算机科学系,我们已经开发了一个名为“网络课堂"的交互式远程学习平台。
该项目旨在为广大学生提供现场讲座。
它允许学生在任何时间任何地点通过任何一台计算机来参加课程。
我们在下图展示所开发的系统。
它由学生的分布组成网络。
教授可以通过互联网提供他/她的讲座录音和课件,也可以通过轮询与学生进行交流。
该平台有以下几个独特的功能和技术项目:网络模块:我们设计并实现了一个传输机制,以便容纳成千上万没有强大的服务器的学生和客户的需要。
我们的网络协议在最近召开的重大会议和研讨会上得以展示,并引起了广泛的关注。
2、音频模块:在该模块中音频能够被很好地传递给学生。
在传递过程中,我们使用了一个高度压缩的音频,并不会占用大量的网络带宽,使用的编码标准称为G.723。
3、视频模块:我们已经实现了最新的H.264视频压缩编码技术。
它在保证了视频的高质量的同时,对于网络和系统资源的使用显著减少了,也因此,这个软件的带宽的要求大大降低。
4、网络接口:这一部分的重点是支持一个网络接口。
有了这项功能,学生就可以在任何能找到一台计算机上网的地方学习。
为了进一步提高用户友好性,网络课堂项目还提供安装文件。
根据指导进行简单的鼠标点击使安装更方便。
完全无需编译或链接,而这在去年的项目里是必要的。
下面,我们来详细解释一下模块。
1、网络模块由于网络课堂属于实时应用,并且听课人的数量通常都是很大的,因此稳定的和可扩展的网络层显得极为重要。
网络的主要功能是将演讲材料,即,视频和音频,分发给所有参加讲座的学生。
这项技术被称为多播。
传统上,多播有两种方式:应用层组播(ALM)和IP组播。
应用层组播,组播是沿节点/用户逻辑树序列的单播来做的。
它是用来解决IP组播的适应性问题。
由于数据向一组ALM主机的传输是通过如TCP和UDP之类的单播协议来完成的,它支持互联网上的任何路由器。
然而,所有的数据传输是通过单播,冗余传输,从而导致带宽利用效率低下,这将成为层组播使用的主要问题。
相比之下,利用IP组播技术,数据只需发送一次,同一组内的每个主机都能收到它。
与多播通信相比,IP组播能够更有效的消除冗余传输,节省带宽。
在ALM技术和IP 组播技术的基础上,我们设计并实现了一个新的架构,将其命名为“岛组播(IM)”。
岛组播,即课堂上教师与学生,分成几个较小的多播能力的地区(或者“岛”)。
当所有这些层组播(ALM)协议在同一个岛上,就使用IP 组播。
岛组播(IM)是一个通用的应用层框架,它适用于任何层组播协议。
对于网络课堂项目,我们决定再次使用ALMI为岛间通信。
岛组播采用这种结构,会话中的成员可以是一个父节点的其他成员,这需要将所有的数据包从邻居节点传送到到其他所有的邻居。
这种对等结构使系统在多播期也能保证信息的高效传播。
这种结构的主要问题是数据传输在很大程度上取决于内的所有节点的可靠性。
如果一个内节点突然断开,那么所有的下游节点也将在一秒钟内从主树中断开。
为了解决这个问题,我们将“代理服务器”引入系统之中。
代理服务器必须高度可靠,并且有IM网络运营商建立。
这是一个简单的构件,提供许多其他成员。
系统中的代理服务器越多,那么它所提供的网络就就越稳定,越可靠。
音频模块微软举,在Windows平台上进行多媒体应用程序开发的一个公认的标准,用于在网络课堂的桌面版操作:重新编码,音频压缩,解压缩,传输和播放。
(图1和图2。
)。
音频传输实时流媒体技术应用于音频传输。
当一个人说,所有的用户应该能够听到。
音频传输是一对多的。
实时音频的时间敏感,需要低延迟。
同时实时音频可以忍受一些损失。
因此,播放音频的最合适的方法是使用传输层协议。
图1:音频流设计(教授方面)图2:音频流设计(学生方面)带宽是互联网上最有价值的资源,通过音频压缩带宽是该应用程序的主要目的。
这个应用程序是专为数以百计的学生同时使用而开发,所需的带宽是如此之大,以致于网络无法支持它。
因此,音频压缩是必不可少的。
在这个项目中我们采用G.723.1。
G.723.1语音压缩算法是一个标准的ITU。
G.723.1在5.3和6.3千位/秒的DUL编码速率。
该声码器信号处理30毫秒的帧和低失真。
该算法的输入/输出是16位线性PCM样品。
G.723.1语音声码器中的比特率提能够供任何当前ITU标准最高的压缩比,而不影响语音质量。
此外,我们的声码器的编码延迟是非常低的(小于0.5秒)。
3、视频模块有许多不同类型的视频压缩编码标准,如H.261,H.263,MPEG4。
他们是被一些国际机构开发的。
在这个项目中,新的视频压缩标准H.264标准提供了一个更大的压缩率,大大降低了网络资源的利用。
比较不同的视频编码标准下比特率的PSNR工作的实施是基于专家设计的标准H264 ITU下的软件JM 5.0(最新版本7.6)。
加快视频压缩,修改也将是基于JM 5.0现有的代码。
对原有的H.264编解码器各部分的时间消耗加快视频编解码器从在<时间定时器H>功能调查计算瓶颈的过程。
从下面的数字,可以看出整像素的帧间预测需要的计算能力。
加快整像素的帧间预测。
为了提高编码速度,国际搜索模式禁用其他16×16忽略低效的编码处理。
同时,一个新的算法应用于运动估计。
在许多快速搜索算法的运动估计,预测运动矢量场自适应搜索技术(PMVFAST)算法,现在基于前者MVFAST算法改进,实现最佳性能方面和加速比的PSNR值减少大多数搜索点,这些有非常小的概率,当前块最后引用MMX技术也被应用于加速各种耗时的计算如绝对差之和(SAD)和YUV到RGB的转换等。
原来的H.264编码器和解码器是使用文件输入和文件输出。
在这个项目中,H264编码器和解码器是处理文件输入和文件输出。
在这个项目中,H.264编解码器必须进行修改,使其能为网络摄像头和网络提供必要的接口。
随着JM软件用C实现,它必须在C和C++之间建立静态库来保持的编解码速度。
静态库的使用也可以更容易的修改和升级。
下面的图显示了在4阶段的改进速度的优化结果。
阶段1:原始阶段2:配置修改阶段3:运动阶段4:运动技术在压缩和解压缩速度,视频质量也在网络课堂项目的极大关注。
拍摄的图片说明了视频质量的测试:原foreman.qcif序列(左)和解码序列(右)原container.qcif序列(左)和解码序列(右)可以从第一个看到第一个图,因为在编码器进行量化,工头的脸模糊。
出于同样的原因,在湖的表面的波变得不明显。
然而,该框架在整体上和他们的质量是可以接受的。
这个项目给予高压缩率仍然是明确的。
4、网络接口学生可以参加现场讲座通过公共计算机或计算机操作系统比Windows更可能发生。
要解决这些问题,开发了一个Web界面。
Web接口包含一个主页,BBS 系统,部分音频和部分视频。
网页是由Dreamweaver MX,Flash MX开发的。
用户可以找到所有的一般信息的有关项目和文件。
主页BBS系统是在互联网上广泛使用的在线讨论。
所有的用户都可以通过发布和回答后互相沟通。
通过提供免费BBS系统源码的6K集团,我们使用ASP建立了自己的BBS系统。
BBS几种不同的实现可以考虑使用视频和音频部分。
但我们的软件使用特定的视频和音频标准(H. 264,G.723),因此很难用java写的匹配的解码器,我们选择了Windows Media系列Windows Media编码器9.0的视频和音频编码器和媒体流可以通过Windows媒体播放器轻松解码。
视频播放网页只有音频很长一段时间过去了,沟通问题在不同地区和国家之间都受到极大关注,特别是那些在地理上的障碍和距离使得传统的面对面教授是不可能的。
现代技术和互联网已经彻底改变了远程通讯,因此远程学习的概念已经能够实现。
网络课堂提供了很大的灵活性:任何人谁有权访问互联网都可以生活在远程教育中。
教授们可以进行讲座就像在传统的教室,有轻微的变化,利用功能如PRS,白板,视频和音频传输。
结语和传统的课程交付相比,网络课堂具有几乎无限的班级大小,以及在时间和地点上有更大的灵活性。
去年,非典的爆发导致停课。
“网络课堂”,学生可以安全的、有效的在家参加讲座,教学调度不需要中断。
今天的因特网是组播的“岛屿”,不能由组播路由器互连。
为了使全球多播组播功能有效,应在一个岛上使用组播功能,岛屿间的单播连接的。
在我们的项目中,我们使用了一个应用层组播框架,称为岛组播(IM),其中组播为两层组织:在上层岛间覆盖建立的同时,IP组播技术在较低的水平内岛应用。
连同IP 组播可扩展性增加。
这允许一个更大的潜在的学生,因此网络课堂提供传统教学的优势和几乎无限的可供选择的班级规模。
在音频部分,压缩算法G.723.1是用来转换成IP数据包的演讲。
G.723.1在提供比当前任何ITU标准都高的压缩比的前提下,尽管巨大的压缩,仍然保留非常高的声音质量。
在实践中,它几乎不可能在不同IP间检测声音的语音质量之间的差异。
我们可以实现延迟小(小于0.5秒)并且好的音频质量。
