Day 2 session 3e - Europe of Interconnector networks - Results of TradeWind
2024四级英语考试试卷

2024四级英语考试试卷Part I:Writing (30 minutes)Directions: For this part, you are allowed 30 minutes to write an essay on the topic "The Importance of Cultural Heritage Protection". You should write at least 120 words but no more than 180 words.Part II:Listening Comprehension (25 minutes)Section A.Directions: In this section, you will hear three news reports. At the end of each news report, you will hear two or three questions. Both the news report and the questions will be spoken only once. After you hear a question, you must choose the best answer from the four choices marked A), B), C) and D).News Report 1.Questions 1 and 2 will be based on the following news item.A new study has found that the number of endangered species in the world is increasing at an alarming rate. The research, which was conducted by a team of international scientists, surveyed over 10,000 species across the globe. It was discovered that factors such as habitat destruction, climate change, and illegal hunting are the main reasons for this increase.1. What is the main topic of this news report?A) The success of international scientific research.B) The increase in the number of endangered species.C) The methods of conducting a global survey.D) The importance of protecting habitats.2. Which of the following is NOT mentioned as a reason for the increase in endangered species?A) Habitat destruction.B) Climate change.C) Illegal hunting.D) Over - population.News Report 2.Questions 3 and 4 will be based on the following news item.In a major step towards sustainable transportation, a new type of electric bus has been launched in a large city. This bus is equipped with advanced battery technology that allows it to travel longer distances without recharging. The local government hopes that this will encourage more people to use public transportation and reduce the city's carbon footprint.3. What is special about the new electric bus?A) It has a very low cost.B) It is very small in size.C) It can travel long distances without recharging.D) It is made of recycled materials.4. What is the goal of the local government in launching this new bus?A) To make more money from public transportation.B) To attract more tourists to the city.C) To encourage people to use public transportation and reduce carbon footprint.D) To show off their advanced technology.News Report 3.Questions 5 to 7 will be based on the following news item.A famous university has announced a new scholarship program for international students. The program aims to attract talented students from all over the world to study in various fields such as science, technology, and engineering. The scholarship will cover tuition fees, accommodation, and living expenses for the selected students.5. Who is the scholarship program aimed at?A) Domestic students.B) International students.C) Students in science only.D) Students in engineering only.6. Which of the following is NOT covered by the scholarship?A) Tuition fees.B) Accommodation.C) Travel expenses.D) Living expenses.7. What fields are included in this scholarship program?A) Only science.B) Only technology.C) Only engineering.D) Science, technology, and engineering.Section B.Directions: In this section, you will hear two long conversations. At the end of each conversation, you will hear four questions. Both the conversation and the questions will be spoken only once. After you hear a question, you must choose the best answer from the four choices marked A), B), C) and D).Conversation 1.Questions 8 to 11 will be based on the following conversation.M: Hi, Lisa. How was your weekend?W: It was great. I went to a music concert.M: Oh, really? Who was performing?W: It was a local band. They play really good rock music.M: That sounds interesting. How did you find out about this concert?W: I saw an advertisement on the Internet.8. What did Lisa do last weekend?A) She went to a movie.B) She went to a music concert.C) She stayed at home.D) She went shopping.9. Who was performing at the concert?A) A famous singer.B) A foreign band.C) A local band.D) A group of dancers.10. How did Lisa know about the concert?A) From a friend.B) From a newspaper.C) From an advertisement on the Internet.D) From the radio.11. What kind of music does the band play?A) Pop music.B) Classical music.C) Rock music.D) Jazz music.Conversation 2.Questions 12 to 15 will be based on the following conversation.M: Have you started your project yet?W: Yes, I have. But I'm having some problems with it.M: What kind of problems?W: Well, I'm not sure about the research methods. I don't know if I should use questionnaires or interviews.M: Hmm, that's a difficult choice. Questionnaires can reach a large number of people, but interviews can get more in - depth information.W: Yes, that's exactly my dilemma. And also, I'm not sure how to analyze the data once I collect it.12. What is the woman's problem?A) She hasn't started her project yet.B) She is not sure about the research methods and data analysis.C) She doesn't have enough time for the project.D) She doesn't know what her project is about.13. What are the two research methods the woman is considering?A) Surveys and experiments.B) Questionnaires and interviews.C) Observations and tests.D) Case studies and focus groups.14. What is an advantage of questionnaires according to the man?A) They can get more in - depth information.B) They are easier to analyze.C) They can reach a large number of people.D) They are more accurate.15. What else is the woman not sure about?A) How to collect data.B) How to start the project.C) How to write the report.D) How to analyze the data.Section C.Directions: In this section, you will hear three passages. At the end of each passage, you will hear three questions. Both the passage and the questions will be spoken only once. After you hear a question, you must choose the best answer from the four choices marked A), B), C) and D).Passage 1.Questions 16 to 18 will be based on the following passage.The Internet has changed the way we communicate and access information. It has made it possible for people all over the world to connect with each other instantly. However, it also has some negative effects. For example, the spread of false information has become a major problem. People need to be more careful when using the Internet and verify the information they receive.16. What has the Internet changed?A) Only the way we communicate.B) Only the way we access information.C) The way we communicate and access information.D) The way we live our lives completely.17. What is a negative effect of the Internet?A) It is too expensive to use.B) It takes too much time.C) The spread of false information.D) It is difficult to learn how to use.18. What should people do when using the Internet?A) Use it as much as possible.B) Ignore all the information.C) Be more careful and verify information.D) Only use it for entertainment.Passage 2.Questions 19 to 21 will be based on the following passage.Reading is an important activity that can enrich our knowledge and imagination. It can take us to different worlds and introduce us to different cultures. However, in modern society, many people are spendingless time reading. There are many reasons for this, such as the popularity of electronic devices and the fast - paced lifestyle.19. What can reading do?A) Only enrich our knowledge.B) Only enrich our imagination.C) Enrich our knowledge and imagination.D) Make us more popular.20. What is the situation of reading in modern society?A) More people are reading than before.B) People are spending less time reading.C) Reading has become more popular.D) Reading is only for students.21. Which of the following is a reason for people spending less time reading?A) Lack of good books.B) The unpopularity of electronic devices.C) The slow - paced lifestyle.D) The popularity of electronic devices and fast - paced lifestyle.Passage 3.Questions 22 to 24 will be based on the following passage.Exercise is essential for our physical and mental health. It can helpus maintain a good body shape, improve our cardiovascular function, and relieve stress. There are many different types of exercise, such as running, swimming, and cycling. People should choose the type of exercise that suits them best.22. What is exercise essential for?A) Only physical health.B) Only mental health.C) Physical and mental health.D) To look more beautiful.23. Which of the following is NOT an advantage of exercise?A) Maintaining a good body shape.B) Improving cardiovascular function.C) Causing more stress.D) Relieving stress.24. What should people do regarding exercise?A) Do the same exercise every day.B) Choose the type of exercise that suits them best.C) Only do running.D) Avoid exercise if they are busy.Part III:Reading Comprehension (40 minutes)Section A.Directions: In this section, there is a passage with ten blanks. You are required to select one word for each blank from a list of choices given in a word bank following the passage. Read the passage through carefully before making your choices. Each choice in the word bank is identified by a letter. Please mark the corresponding letter for each item on Answer Sheet 2. You may not use any of the words in the word bank more than once.The development of modern technology has had a great impact on ourdaily lives. One of the most significant changes is in the way we communicate. With the _(25)_ of the Internet and mobile phones, we can now communicate with people all over the world instantly. This has made the world seem smaller and has brought people closer together.However, this also has some _(26)_ effects. For example, people may become too _(27)_ on electronic devices and neglect face - to - face communication. In addition, the _(28)_ of false information on the Internet has become a serious problem.Another area where technology has had a major impact is in transportation. New forms of transportation such as high - speed trains and electric cars are becoming more and more _(29)_. These new technologies are more environmentally friendly and can help reduce _(30)_ emissions.In the field of education, technology has also brought many changes. Online courses are now widely available, which allows people to study at their own _(31)_ and from anywhere in the world. However, some people worry that this may lead to a decrease in the quality of education as there may be less _(32)_ interaction between teachers and students.Overall, while modern technology has brought many benefits, we also need to be aware of its _(33)_ and take steps to address them.Word Bank:A) advent.B) addicted.C) adverse.D) availability.E) carbon.F) close.G) convenient.H) direct.I) disadvantages.J) emergence.K) environmental.L) pace.M) pollution.N) prevalent.O) spread.25. A) advent.26. C) adverse.27. B) addicted.28. O) spread.29. N) prevalent.30. E) carbon.31. L) pace.32. H) direct.33. I) disadvantages.Section B.Directions: In this section, you are going to read a passage with ten statements attached to it. Each statement contains information given in one of the paragraphs. Identify the paragraph from which the information is derived. You may choose a paragraph more than once. Each paragraph is marked with a letter. Answer the questions by marking the corresponding letter on Answer Sheet 2.The Future of Work.A) The world of work is changing rapidly. Technological advancements such as artificial intelligence, robotics, and automation are transforming the way we work. These changes are not only affecting the types of jobsthat are available but also the skills that are required for success in the workplace.B) One of the most significant changes is the increasing automation of routine tasks. Machines are now able to perform many jobs that were previously done by humans, such as data entry, manufacturing, and customerservice. This has led to concerns about job losses, especially inindustries that rely heavily on manual labor.C) However, while some jobs may be disappearing, new jobs are alsobeing created. For example, the development of artificial intelligence has led to the emergence of new fields such as machine learning and data analytics. These fields require highly skilled workers who can develop, manage, and interpret complex algorithms.D) Another trend in the future of work is the increasing importance of soft skills. Soft skills such as communication, teamwork, and problem - solving are becoming more and more essential in the workplace. This is because as machines take over routine tasks, humans will need to focus on tasks that require human interaction and creativity.E) The rise of the gig economy is also changing the nature of work. In the gig economy, people work on a freelance or contract basis, oftenthrough online platforms. This gives workers more flexibility and control over their work, but it also means that they may not have the same job security or benefits as traditional employees.F) Technology is also enabling more remote work. With the developmentof high - speed Internet and communication tools, more and more people are able to work from home or other locations outside of the traditional office. This can improve work - life balance for employees and also reduce costsfor employers.G) However, remote work also has its challenges. For example, it can be difficult to maintain team cohesion and communication when employees arenot physically in the same location. Employers need to find ways to overcome these challenges, such as through the use of video conferencingand project management tools.H) In order to succeed in the future of work, individuals need to be adaptable and continuously learn new skills. Lifelong learning will be essential as the skills required for work are constantly evolving. Educational institutions and employers also need to play a role in providing training and development opportunities for workers.I) The future of work is likely to be more globalized. With the increasing ease of communication and transportation, companies are more likely to hire workers from all over the world. This means that individuals will need to be able to work effectively in a multicultural environment.J) Overall, the future of work is full of opportunities and challenges. While technological advancements are changing the nature of work, they also offer the potential for new jobs, greater flexibility, and improved productivity.34. Machines are taking over many jobs that were previously done by humans. B.35. New fields like machine learning and data analytics are emerging due to artificial intelligence. C.36. Soft skills are becoming more important as machines do routine tasks. D.37. The gig economy gives workers more flexibility but less job security. E.38. Remote work can improve work - life balance but has challenges in communication. F.39. Lifelong learning is necessary for individuals to succeed in the future of work. H.40. Companies are more likely to hire globally in the future. I.41. The future of work has both opportunities and challenges. J.42. Automation is not only affecting job types but also required skills.A.43. Employers need to use tools to overcome remote work challenges. G.Section C.Directions: There are 2 passages in this section. Each passage is followed by some questions or unfinished statements. For each of them there are four choices marked A), B), C) and D). You should decide on the best choice and mark the corresponding letter on Answer Sheet 2.Passage 1.The concept of "green jobs" has become increasingly popular in recent years. Green jobs are those that contribute to environmental protection and sustainable development. These jobs can be found in a variety of sectors, such as renewable energy, energy efficiency, waste management, and sustainable agriculture.One of the main drivers of the growth of green jobs is the increasing concern about climate change. As countries around the world strive toreduce their carbon emissions, they are investing in renewable energy sources such as solar, wind, and hydro power. This has led to the creationof many jobs in the renewable energy sector, from research and developmentto installation and maintenance.In addition to renewable energy, energy efficiency is also an important area for green jobs. Improving the energy efficiency of buildings, for example, can reduce energy consumption and costs. Jobs in this area includeenergy auditors, who assess the energy use of buildings and recommend improvements, and insulation installers, who install energy - saving materials in buildings.Waste management is another sector with significant potential for green jobs. Recycling and composting are two important waste management methods that can reduce the amount of waste sent to landfills. Jobs in waste management include waste collectors, recyclers, and composting operators.Sustainable agriculture is also an emerging area for green jobs. Organic farming, for example, uses natural fertilizers and pesticides, which are better for the environment. Jobs in sustainable agriculture include farmers, agricultural technicians, and food processors who work with organic products.44. What are green jobs?A) Jobs that are only related to renewable energy.。
more information, you can contact the session organizers or the authors of the articles. A

IEEE DISTRIBUTED SYSTEMS ONLINE 1541-4922 © 2005 Published by the IEEE Computer SocietyVol. 10, No. 10; October 2005Cluster Computing and Grid 2005 Works in ProgressThis is the second in a two-part series () of works-in-progress articles taken from a special session, which was part of the Cluster Computing and Grid 2005 conference(/ccgrid2005), held in Cardiff, UK. The session was organized by Mark Baker (University of Portsmouth, UK) and Daniel S. Katz (Jet Propulsion Laboratory, US). For more information, you can contact the session organizers or the authors of the articles.A Pluggable Architecture for High-Performance Java MessagingMark Baker, University of PortsmouthAamir Shafi, University of PortsmouthBryan Carpenter, University of SouthamptonEfforts to build Java messaging systems based on the Message Passing Interface (MPI) standard have typically followed either the JNI (Java Native Interface) or the pure Java approach. Experience suggests there's no "one size fits all" approach because applications implemented on top of Java messaging systems can have different requirements. For some, the main concern might be portability, while for others it might be high bandwidth and low latency. Moreover, portability and high performance are often contradictory requirements. You can achieve highperformance by using specialized communication hardware but only at the cost of compromising the portability Java offers. Keeping both in mind, the key issue isn't to debate the JNI versus pure Java approaches, but to provide a flexible mechanism for applications to swap between communication protocols.To address this issue, we have implemented MPJ Express based on the Message Passing in Java (MPJ) API.1 MPJE follows a layered architecture that uses device drivers, which are analogous to Unix device drivers. The ability to swap devices at runtime helps mitigate the applications' contradictory requirements. In addition, we're implementing a runtime system that bootstraps MPJE processes over a collection of machines connected by a network. Though the runtime system isn't part of the MPI specifications, it's essential to spawn and manage MPJE processes across various platforms.MPJE's design is layered to allow incremental development and provide the capability to update and swap layers in or out as needed. Figure 1 shows a layered view of the messaging system. The high and base levels rely on the MPJ device2 and xdev level for actual communications and interaction with the underlying networking hardware. One device provides JNI wrappers to the native MPI implementations, and the other (xdev) provides access to Java sockets, shared memory, or specialized communication libraries. The wrapper implementation doesn't need xdev, because the native MPI is responsible for selecting and switching between different communication protocols. Figure 1 also shows three implementations of xdev: smpdev, the shared memory device; niodev, an implementation of xdev using the Java New I/O package; and gmdev, an implementation of xdev using JNI to interact with the Myrinet communications library.Figure 1. MPJ Express's layered design.MPJE's initial performance evaluation on Fast and Gigabit Ethernet shows comparable performance to mpiJava, which uses JNI wrappers to interact with a native MPI implementation. We released a beta version of MPJE in early September. You can find further details of MPJE on the project's Web site (/projects/mpj or email us.References1. B. Carpenter et. al, MPI for Java Position Document and Draft API Specification,tech. report JGF-TR-03, Java Grande Forum, Nov. 1998.2. S.B. Lim et. al, "A Device Level Communication Library for the HPJava ProgrammingLanguage." Proc. Iasted Int'l Conf. Parallel and Distributed Computing and Systems(PDCS 2003), ACTA Press, 2003.Mark Baker is a Reader in Distributed Systems at the University of Portsmouth, UK. Contact him at mark.baker@.Bryan Carpenter is a senior researcher at the Open Middleware Infrastructure Institute, University of Southampton, UK. Contact him at dbc@.Aamir Shafi is a PhD student in the Distributed Systems Group, University of Portsmouth, UK. Contact him at aamir.shafi@.Toward Intelligent, Adaptive, and Efficient Communication Services for Grid Computing Phillip M. Dickens, University of MaineWhat constitutes an intelligent, adaptive, highly efficient communication service for grid computing? An intelligent service can accurately assess the end-to-end system's state to determine how (and whether) to modify the data transfer's behavior. An intelligent controller could, for example, respond more aggressively to a network-related loss than to a loss caused by events outside the network domain. An adaptive communication service can either change its execution environment or adapt its behavior in response to changes in that environment. An efficient communication service can exploit the underlying network bandwidth when system conditions permit. It can also fairly share network resources in response to observed (or predicted) network contention.A necessary milestone on the path to such next-generation communication services is the development of a classification mechanism that can distinguish between various data-loss causes in cluster or Grid environments. We're developing such a mechanism based on packet-loss signatures, which show the distribution (or pattern) of packets that successfully traversed the end-to-end transmission path versus those that did not. These signatures are essentially largeselective-acknowledgment packets that the data receiver collects and, upon request, delivers to the data sender. We refer to them as packet-loss signatures because a growing set of experimental results shows that different data-loss causes have different signatures.1,2 The question then is how to quantify the differences between packet-loss signatures so that a classification mechanism can identify them.Our approach is to treat packet-loss signatures as time-series data and to apply techniques from symbolic dynamics to learn about the time series' dynamical structure. We quantify the structure in the sequence based on its complexity. We've learned that the complexity measures of packet-loss signatures have different statistical properties when the cause of such loss lies inside rather than outside the network domain. In fact, these statistical properties are different enough to let us construct, using Bayesian statistics, rigorous hypothesis tests regarding the cause of data loss.3 We're currently developing the infrastructure required to perform such hypothesis testing in real time.Next, we plan to develop and evaluate a set of responses tailored to particular data-loss causes. We'll explore, for example, data-receiver migration and user-specified limits on CPU utilization for data loss caused by contention for CPU resources.References1. P. Dickens and J. Larson, "Classifiers for Causes of Data Loss Using Packet-LossSignatures,"Proc. IEEE Symp. Cluster Computing and the Grid (CCGrid 04), IEEE CS Press, 2004.2. P. Dickens, J. Larson, and D. Nicol, "Diagnostics for Causes of Packet Loss in a HighPerformance Data Transfer System," /persagen/DLAbsToc.jsp?Proc. 18th Int'l Parallel and Distributed Processing Symp. (IPDPS 04), IEEE CS Press, 2004.3. P. Dickens and J. Peden, "Towards a Bayesian Statistical Model for the Causes of DataLoss,"Proc. 2005 Int'l Conf. High Performance Computing and Communications, LNCS 3726, Springer, 2005, pp. 755-767.Phillip M. Dickens is an assistant professor in the Department of Computer Science at the University of Maine. Contact him at dickens@.Grimoires: A Grid Registry with a Metadata-Oriented InterfaceSylvia C. Wong, School of Electronics and Computer Science, University of Southampton Victor Tan, School of Electronics and Computer Science, University of Southampton Weijian Fang, School of Electronics and Computer Science, University of Southampton Simon Miles, School of Electronics and Computer Science, University of Southampton Luc Moreau, School of Electronics and Computer Science, University of SouthamptonThe Grid is an open distributed system that brings together heterogeneous resources across administrative domains. Grid registries let service providers advertise their services, so users can use these registries to dynamically find available resources. However, existing service registry technologies, such as Universal Description, Discovery, and Integration (UDDI), provide only a partial solution.First of all, such technologies have limited support for publishing semantic information. In particular, services aren't the only entities that need to be classified for example, we would also want to define classifications for individual operations or their argument types. Second, only service operators can provide information about services, and in a large and disparate environment, it's impossible for operators to foresee all the information that users might use to find resources. Third, UDDI uses authentication techniques for security that aren't particularly suited for the large-scale nature of Grid systems.To address these problems, we're developing a registry called Grimoires() for the myGrid project () and the Open Middleware Infrastructure Institute (OMII, ) Grid software release. Figure 2 shows our registry's architecture, which we've implemented as a Web service. It has two major interfaces UDDI and metadata. The registry is UDDI v2 compliant, and you canaccess the UDDI interface using any UDDI client, such as UDDI4j (). To access the metadata functionalities, you need to use a Grimoires client.Figure 2. The Grimoires architecture. (UDDI is Universal Description, Discovery, and Integration.)Our registry has several unique features:l Registration of semantic descriptions. Our registry can publish and inquire overmetadata attachments. These attachments are extra pieces of data that provideinformation about existing entities in the registry. Currently, the registry supportsannotations to UDDI BusinessEntity, BusinessService, tModel, and BindingTemplate, and to WSDL (Web Services Description Language) operations and message parts.Thus, using Grimoires, users can annotate BusinessService with service ratings andfunctionality profiles and attach semantic types of operation arguments to WSDLmessage parts.l Multiple metadata attachments. Each entity can have an unlimited number ofattachments, and each piece of metadata can be updated without republishing the entity or other metadata attached to the same entity. This efficiently captures ephemeralinformation about services, which changes often.l Third party annotations. Both service operators and third parties can publishmetadata, so users with expert knowledge can enrich service descriptions in ways that the original publishers might not have conceived.l Inquiry with metadata. Grimoires supports multiple search patterns. It ranges from simple searches that return a list of metadata attached to the specified entity to morecomplex searches that return entities that match a certain criteria.l Signature-based authentication. UDDI uses a username and password credentialscheme. However, Grid environments typically use certificate-based authentication.OMII provides an implementation of SOAP message signing and verification thatconforms to Web Services security standards. By deploying Grimoires in the OMIIcontainer, the registry can authenticate users using X509 certificates. This makes iteasier to integrate Grimoires into existing Grid security infrastructures, and it provides an important building block certificate-based authentication for the single sign-on capabilities that many Grid applications require.For more information, please visit .Sylvia C. Wong is a research fellow in the Intelligence, Agents, Multimedia group at the School of Electronics and Computer Science, University of Southampton, UK. Contact her at sw2@.Victor Tan is a research fellow in the Intelligence, Agents, Multimedia group at the School of Electronics and Computer Science, University of Southampton, UK. Contact him atvhkt@.Weijian Fang is a research fellow in the Intelligence, Agents, Multimedia group at the School of Electronics and Computer Science, University of Southampton, UK. Contact him at wf@.Simon Miles is a research fellow in the Intelligence, Agents, Multimedia group at the School of Electronics and Computer Science, University of Southampton, UK. Contact him atsm@.Luc Moreau is a professor in the Intelligence, Agents, Multimedia group at the School of Electronics and Computer Science, University of Southampton, UK. Contact him atl.moreau@.Cite this article:Mark Baker, Bryan Carpenter, and Aamir Shafi, "Cluster Computing and Grid 2005 Works in Progress: A Pluggable Architecture for High-Performance Java Messaging," IEEE DistributedSystems Online, vol. 6, no. 10, 2005.Phillip M. Dickens, "Cluster Computing and Grid 2005 Works in Progress: Toward Intelligent, Adaptive, and Efficient Communication Services for Grid Computing," IEEE Distributed Systems Online, vol. 6, no. 10, 2005.Sylvia C. Wong, Victor Tan, Weijian Fang, Simon Miles, and Luc Moreau, "Cluster Computing and Grid 2005 Works in Progress: Grimoires: A Grid Registry with a Metadata-Oriented Interface," IEEE Distributed Systems Online, vol. 6, no. 10, 2005.。
计算机网络英文复习题

计算机⽹络英⽂复习题、英译汉(10分)1.TCP(Transmission Control Protocol) 传输控制协议2.IP(Internet Protocol) 互联⽹协议3.RFC(Requests for comments) 请求评议4.SMTP(Simple Mail Transfer Protocol) 简单邮件传输协议5.Congestion-control 拥塞控制6.Flow control 流控制7.UDP (User Datagram Protocol) ⽤户数据报协议8.FTP(File Transfer Protocol) ⽂件传输协议9.HTTP( Hyper-Text Transfer Protocol ) 超⽂本传输协议10.TDM 时分复⽤11.FDM 频分复⽤12.ISP(Internet Service Provider) 互联⽹服务提供商13.DSL(Digital Subscriber Line) 数字⽤户线路14.DNS(Domain Name System) 域名系统15.ARQ(Automatic Repeat Request) ⾃动重发请求16.ICMP(Internet Control Message Protocol) ⽹间控制报⽂协议17.AS(Autonomous Systems) ⾃制系统18.RIP(Routing Information Protocol)\ 路由信息协议19.OSPF(Open Shortest Path First) 开放最短路径优先20.BGP (Border Gateway Protocol) 边界⽹关协议21.HFC 光纤同轴电缆混合⽹22.CRC(Cyclic Redundancy Check) 循环冗余检验23.CSMA/CD 带冲突检测的载波侦听多路存取24.ARP 地址解析协议25.RARP 反向地址解析协议26.DHCP 动态主机配置协议27.RTT 循环时间28.IETF(P5)互联⽹⼯程任务组29.URL(P88)统⼀资源定位30.API应⽤程序编程接⼝31.MIME多⽤途互联⽹邮件扩展1. DSL divides the communication link between the home and the ISP into three nonoverlapping frequency bands, a upstream channel is in _A_________.A)50 kHz to 1MHz band B) 1MHz to 2MHz bandC)4 kHz to 50kHz band D) 0 to 4kHz band2. As a data packet moves from the upper to the lower layers, headers are A .A) Added; B) subtracted; C) rearranged; D) modified3. What is the main function of the network layer? DA) node-to-node delivery; B) process-to-process message deliveryC) synchronization; D) updating and maintenance of routingtables4. Which of the following is the default mask for the address 168.0.46.201? BA) 255.0.0.0; B) 255.255.0.0; C) 255.255.255.0; D) 255.255.255.2555.A router reads theaddress on a packet to determine the next hop. AA) IP ; B) MAC; C) source; D)ARP6 .Which device can’t isolates the departme ntal collision domains. AA) Hub; B) switch; C) router; D) A and B7. Input port of a router don’t perform ____D____ functions.A) the physical layer functions B) the data link layer functionsC) lookup and forwarding function D) network management8. HTTP has a mechanism that allows a cache to verify that its objects are up to date. The mechanism is DA) persistent connections B) cookies C) Web Caching D) conditional GET9. A protocol layer can be implemented in ___D_____.A) software B) hardware C) a combination of the software and hardware D) All of the above10. A protocol has three important factors, they are_A______.A)syntax, semantics, order B) syntax, semantics, layerC)syntax, semantics, packet D) syntax , layer, packet11. There are two broad classes of packet-switched networks: datagram networks and virtual-circuit networks. The virtual-circuit networks forward packets in their switches use ___D___.A) MAC addresses B) IP addressesC) e-mail addresses D) virtual-circuit numbers12. TCP service model doesn’t provide ___D_______service.A) reliable transport service B) flow control serviceC) congestion-control service D) guarantee a minimum transmission rate service.13. Usually elastic applications don’t include____B______.A) Electronic mail B) Internet telephony14. A user who uses a user agent on his local PC receives his mail sited in a mail server by using _B___ protocol.A)SMTP B) POP3C)SNMP D) FTP15. Considering sliding-window protocol, if the size of the transmitted window is N and the size of the receiving window is 1,the protocol is BA) stop-and-wait protocol B) Go-Back-N protocolC) selective Repeat protocol D) alternating-bit protocol16. which IP address is effective___B______.A) 202,131,45,61 B) 126.0.0.1C) 192.268.0.2 D) 290.25.135.1217. if IP address is 202.130.191.33, subnet mask is 255.255.255.0,then subnet prefix is__D_____A) 202.130.0.0 B) 202.0.0.0C) 202.130.191.33 D)202.130.191.018.The command Ping s implemented with __B______messagesA) DNS B) ICMPC) IGMP D) RIP19. Which layer-function is mostly implemented in an adapter? __A________A) physical layer and link layer B) network layer and transport layerC)physical layer and network layer D) transport layer and application layer20. If a user brings his computer from Chengdu to Peking, and accesses Internet again. Now, __B_____ of his computer needs to be changed.A) MAC address B) IP addressC) e-mail address D) user address1. .traceroute is implemented with __B____messages.A) DNS B) ICMPC) ARP D) RIP2.A router reads the A address on a packet to determine the next hop.A. IP ;B. MAC;C. source;D.ARP3. There are two broad classes of packet-switched networks: datagram networks andvirtual-circuit networks. The virtual-circuit networks forward packets in their switches use ___D___.A) MAC addresses B) IP addressesC) e-mail addresses D) virtual-circuit numbersA) device interfaces with same subnet part of IP addressB) can’t physically reach each other without intervening a router.C)all of the devices on a given subnet having the same subnet address.D)A portion of an interface’s IP address must be determined by the subnet to which it is connected.5. if IP address is 102.100.100.32, subnet mask is 255.255.240.0,then subnet prefix is___A___A) 102.100.96.0 B) 102.100.0.0C) 102.100.48.0 D) 102.100.112.06 If a user brings his computer from chengdu to beijing, and accesses Internet again. Now,___B__ of his computer needs to be changed.A) MAC address B) IP addressC) e-mail address D) user address7.I nput port of a router don’t perform ____D___ functions.A) the physical layer functions B) the data link layer functionsC) lookup and forwarding function D) network management8.switching fabric is at the heart of a router, switching can be accomplished in a number of ways, donit include_D_A)Switching via memory B)Switching via crossbarC)Switching via a bus D) Switching via buffer9.if a host wants to emit a datagram to all hosts on the same subnet, then the datagram’s destination IP address is ___B__A)255.255.255.0 B) 255.255.255.255C)255.255.255.254 D) 127.0.0.110.The advantage of Circuit switching does not include________.A) small transmission delay B)small Processing costC) high link utilization D)no limited to format of message1.an ARP query sent to __A__A) local network B) all over the Internet.2. .packet-switching technologies that use virtual circuitsinclude__B___:A) X.25, ATM, IP B) X.25, ATM, frame relay.C) IPX, IP, ATM D) IPX, IP, TCP3. In Internet, _D_ protocol is used to report error and provide the information forun-normal cases.A) IP B) TCP C)UDP D) ICMP1.A is a Circuit-switched network.B. Datagram networkC. InternetD. virtual circuit network2.The store-and-forward delay is DA. processing delayB. queuing delayC. propagation delayD. transmission delay3.Which is not the function of connection-oriented service? DA. flow controlB. congestion controlC. error correctionD. reliabledata transfer4.The IP protocol lies in CA. application layerB. transport layerC. network layerD. link layer5.Which of the following is the PDU for application layer __B___A.datagram;B. message;C. frame;D.segment6.bandwidth is described in _B__A) Bytes per second B) Bits per secondC) megabits per millisecond D) centimeters7.A user who uses a user agent on his local PC receives his mail sited in a mail server by using __A__ protocol.A)SMTP B) POP3C)SNMP D) FTP8.As a data packet moves from the lower to the upper layers, headers are B.A)Added; B. subtracted; C. rearranged; D. modified三、填空题(每空1分,共22分 (注意:所有填空题不能写中⽂,否则中⽂答案对的情况1. link-layer address is variously called a LAN address, a MAC address, or a physical address.2 In the layered architecture of computer networking, n layer is the user of n-1 layer and the service provider of n+1 layer.A) n B) n+3 C) n+1 D) n-1四、判断题(每⼩题1分,共10分)1.√The services of TCP’s reliable data transfer founded on the services of theunreliable data transfer.2.√Any protocol that performs handshaking between the communication entitiesbefore transferring data is a connection-oriented service.3.× HOL blocking occur in output ports of router.4.√Socket is globally unique.5.√SMTP require multimedia data to be ASCII encoded before transfer.6.×The transmission delay is a function of the distance between the two routers.7.×IP address is associated with the host or router. SO one device only have one IPaddress.8. √In packet-switched networks, a session’s messages use the resources on demand, and Internet makes its best effort to deliver packets in a timely manner.9. ×UDP is a kind of unreliable transmission layer protocol, so there is not any checksum field in UDP datagram header.10.√Forwarding table is configured by both Intra and Inter-AS routing algorithmIP is a kind of reliable transmission protocol. F8.Forwarding table is configured by both Intra and Inter-AS routing algorithm.T9.Distance vector routing protocol use lsa to advertise the network which router10.RIP and OSPF are Intra-AS routing protocols T11.Packet switching is suitable for real-time services, and offers better sharing ofbandwidth than circuit switching F五、计算题(28 points)1.C onsider the following network. With the indicated link costs, use Dijkstra’s shortest-path algorithm to compute the shortest path from X to all network nodes.2 Given: an organization has been assigned the network number 198.1.1.0/24 and it needs todefine six subnets. The largest subnet is required to support 25 hosts. Please:●Defining the subnet mask; (2分) 27bits or 255.255.255.224●Defining each of the subnet numbers; which are starting from 0# (4分)198.1.1.0/27 198.1.1.32/27 198.1.1.64/27 198.1.1.96/27 198.1.1.128/27 198.1.1.160/27 198.1.1.192/27 198.1.1.224/27●Defining the subnet 2#’s broadcast address.(2分) 198.1.1.95/27Defining host addresses scope for subnet 2#. (2分) 198.1.1.65/27--198.1.1.94/273. Consider sending a 3,000-byte datagram into a link that has an MTU of 1500bytes.Suppose the original datagram is stamped with the identification number 422 .Assuming a 20-byte IP header,How many fragments are generated? What are their characteristics?(10分)。
Eurex_NTA_Workshop_Part3_Tech

• Reports from new trading architecture:
– – – – – – – – –
V 1.10
Daily order maintenance, Cross and quote requests, Futures price movement summary, User security maintenance, … Trade report, EurexOTC trade maintenance report, Position report, …
Eurex Exchange’s New Trading Architecture
The next generation in derivatives trading Part 3 – Technical Characteristics
May 2012
Eurex Exchange’s New Trading Architecture
New Situation Participant
EurexOTC
... ...
Current Situation
Current system
Participant
... ...
... ...
... ...
On-exchange
New trading architecture
... ...
MISS
Current system
V 1.10
2
Eurex Exchange’s New Trading Architecture
May 2012
New interfaces
Interface landscape of Eurex Exchange’s new trading architecture
全国大学英语CET四级考试试题及解答参考(2025年)

2025年全国大学英语CET四级考试复习试题及解答参考一、写作(15分)Part I Writing (30 points)Directions: For this part, you are allowed 30 minutes to write a short essay on the topic “The Impact of Artificial Intelligence on Daily Life.” You should start your essay with a brief introduction to the topic, then give specific examples to illustrate your point, and finally, provide a conclusion with your personal view. Your essay should be about 120 to 150 words but no less than 100 words.Writing Sample:The advent of artificial intelligence (AI) has revolutionized our daily lives in numerous ways. From smart homes to advanced medical diagnosis, AI has become an integral part of modern society.In smart homes, AI systems like voice assistants and smart security cameras enhance our convenience and safety. These systems learn from our habits and preferences, making our homes more comfortable and efficient. Moreover, in the healthcare sector, AI algorithms are being used to analyze medical images and identify potential diseases at an early stage, which can significantly improvepatient outcomes.However, the rise of AI also brings challenges. For example, job displacement is a major concern, as AI can perform certain tasks more efficiently than humans. Additionally, there are ethical questions about privacy, data security, and the potential misuse of AI technology.In conclusion, while AI has brought substantial benefits to our daily lives, we must also address its challenges to ensure a balanced and ethical integration of AI into our society.Writing Analysis:•Introduction: The essay starts with a clear introduction to the topic of AI and its impact on daily life, providing a broad perspective.•Body Paragraphs: The body of the essay presents two distinct impacts of AI:•The positive impact of AI in smart homes and healthcare.•The negative impacts of job displacement and ethical concerns.•Conclusion: The essay concludes with a balanced view, acknowledging both the benefits and challenges of AI, and emphasizing the need for ethical considerations.•Structure and Coherence: The essay has a clear structure and is well-organized, making the flow of ideas easy to follow.•Length: The essay meets the required word count, with 120 words, demonstrating the writer’s ability to convey the main points concisely.二、听力理解-短篇新闻(选择题,共7分)第一题News:In recent years, global attention has been drawn to the rapid development of electric vehicles (EVs). According to a recent report by the International Energy Agency (IEA), the number of electric vehicles on the roads worldwide reached 13 million in 2021, up from just 2 million in 2015. The report also indicates that by 2030, the number of electric vehicles is expected to surpass 145 million.Question 1:What has the number of electric vehicles on the roads reached as of 2021 according to the recent report by the IEA?A) 1 millionB) 13 millionC) 2 millionAnswer: BQuestion 2:How many years is it mentioned from 2015 to 2021 in the report?A) 5 yearsB) 6 yearsC) 7 yearsAnswer: BQuestion 3:What is the expected number of electric vehicles by 2030 according to the report?A) 13 millionB) 2 millionC) 145 millionAnswer: C第二题News Item 1:A new study reveals that the global use of electric scooters has increased significantly in recent years. These scooters are becoming a popular form of transportation in cities around the world. However, the study also highlights the environmental and safety concerns associated with the rapid growth in electric scooter usage.Cities are faced with the challenge of managing the increased demand for parking spaces, as well as the potential risks of accidents involving these scooters. Improved infrastructure and regulations are being considered to address these issues.Questions:1、What is the primary topic of the news item?A. The decline of traditional scootersB. The environmental impact of electric scootersC. The safety concerns of using electric scootersD. The rise in global use of electric scooters2、“These scooters are becoming a popular form of transportation in cities around the world.” Which of the following is true regarding the use of electric scooters?A. They are only popular in developed countries.B. They have no environmental impact.C. They are causing a decrease in car usage.D. They have become a common mode of transportation globally.3、“Improved infrastructure and regulations are being considered to address these issues.” What is the implied issue that needs to be addressed?A. The overuse of public transportation.B. The need for more parking spaces for cars.C. The decline in bicycle usage.D. The potential safety risks and management challenges posed by electric scooters.Answers:1.D2.D3.D三、听力理解-长对话(选择题,共8分)First QuestionConversationA: Hey, Sarah! Did you finish listening to the podcast this morning?B: Yeah, I did. It was quite fascinating. Have you checked the transcript on their webpage?A: Not yet. I plan to review what we heard today after work. By the way, I was thinking it would be nice to form a study circle this semester.B: That sounds like a good idea. Could you host a meeting this weekend?A: Sure, I can. I’ll prepare some questio ns for us to discuss, and you can bring in your notes. It’ll make our learning more productive.B: Great! Should we stick to the topics in the podcast or choose something else?A: Let’s talk about the topics in the podcast first. That way, it’ll help us understand the context better.B: Sounds perfect. I have a couple of questions for you. How long have you been listening to podcasts?A: Since about a year now. I find it’s a great way to learn English while doing something productive.B: I agree. What’s your favorite podcast?A: Hmm, I really like “The Economist Briefing.” It covers current events and history, which are topics I find interesting.B: Nice choice. I’m a fan of “TED Talks Daily.” It’s a bit different from “The Economist Briefing” but still educational.A: That’s true. We can switch up the topics as we like. What are youstudying?B: I’m majoring in international relations. The podcast really helps me get more insights into what I’m studying.A: That’s awesome. What about yo ur plans for the future?B: I hope to travel around Europe for my study abroad program next year, so I’m trying to learn more European languages. It would be a great opportunity to practice my English as well.A: That sounds exciting! This weekend, let’s m eet for an hour at my place, okay?B: Sure, that works for me.Q1. What is one reason Sarah likes listening to this podcast?a)To practice her English.b)To pass CET-4.c)To prepare for a trip.d)To learn her major subject.Answer: aQ2. How long has the speaker been listening to podcasts?a)One yearb)Two yearsc)Three yearsd)Half a yearAnswer: aQ3. Who does the speaker admire for choosing “TED Talks Daily”?a)Sarahb) A friendc) A professord)Another studentAnswer: aQ4. What will they do this weekend?a)Meet for an hour at the speaker’s place.b)Join a club activity.c)Go to a coffee shop.d)Attend a lecture on English.Answer: aQuestion 2:Why does Liu feel a bit nervous about the exam?A) He is preparing for it for too long.B) He hasn’t studied hard enough.C) His friends are also enrolled in CET-4 course classes.D) He needs to take a break soon.Answer: AQuestion 3:What advice does Amy give to Liu?A) Enroll in a CET-4 course class.B) Review the past papers.C) Study every day.D) Take a break.Answer: BQuestion 4:What can be inferred about Liu from the conversation?A) He is confident about the exam.B) He has been preparing for the exam for a long time.C) He is ready for the upcoming exam.D) He doesn’t like studying hard.Answer: B四、听力理解-听力篇章(选择题,共20分)第一题Directions: In this section, you will hear a passage. Listen carefully and answer the questions that follow.Passage:In today’s fast-paced digital world, it has become increasingly important for businesses to adopt technologies that improve their efficiency and customer satisfaction. The rise of artificial intelligence (AI) and machine learning (ML) has led to significant advancements in the field of business operations. Companies are now exploring various ways to integrate these technologies to enhance their processes.1、What aspect of business operations has seen significant advancements dueto AI and ML integration?A) Customer serviceB) LogisticsC) Financial managementD) A2、Why is the adoption of AI and ML technologies regarded as important for businesses?A) To reduce operational costsB) To improve customer satisfactionC) To increase operational efficiencyD) C3、Which of the following is NOT an example of how businesses can integrate AI and ML?A) Enhancing predictive analyticsB) Automating routine tasksC) Increasing manual data entryD) C第二题Passage 1The globalization of the economy has brought about significant changes in the world, and one area that has been heavily affected is the sports industry. In this essay, we will explore how globalization has impacted the sports industry,focusing on the growth of international sports events and the role of sports in global culture.1、Why is globalization having a profound impact on the sports industry?A) Because it allows sports to be practiced anywhere in the world.B) Because it has led to the growth of international sports events.C) Because it has changed the way people culture around the world.D) Because it has increased the salaries of professional athletes.2、Which of the following is not mentioned as a change brought about by globalization in the sports industry?A) The increase in cross-cultural interactions.B) The decline in local sports teams.C) The rise of regional sports leagues.D) The increase in global fan bases for various sports.3、What is the main argument made by the essay about the role of sports in global culture?A) Sports have a单一 focus on winning and losing.B) Sports help to foster national pride and identity.C) Sports have become a way for countries to cooperatively compete.D) Sports have lost their relevance due to increased commercialization.Answer Key:1、B2、BThird Question: Listening Comprehension - Listening PassagePassage:Welcome to our final research trip to India. We are in a small village in the state of Kerala, known for its rich cultural heritage and scenic beauty. The village, named Paravoor, has a population of approximately 15,000. Today, we focus on the local economy, which is largely dependent on farming, tourism, and small-scale industries. Currently, the village is facing several challenges, including water scarcity and lack of proper infrastructure. The government plans to implement a new irrigation project, which will provide a significant boost to the agricultural sector. In addition, the village is promoting eco-tourism to diversify its economic base. However, these initiatives require support and investment from both the government and the local community.1、Which of the following is NOT a challenge facing Paravoor Village?A、Water scarcityB、Lack of proper infrastructureC、Dependence on large-scale industriesD、C、2、What is the villagers’ plan to diversify their economic base?A、Developing new industriesB、Promoting eco-tourismC、Increasing agricultural production3、Which of the following is a potential benefit of the new irrigation project?A、It will help diversify the local economy.B、It will improve the infrastructure.C、It will provide water to the entire state.D、C、五、阅读理解-词汇理解(填空题,共5分)第一题Reading PassageAlice, receiving a ring, was extremely pleased. Her father promptly asked, “Have you made up your mind, my dear?” “Not quite,” said Alice ominously, stepping out of her ring. “But I will do so directly,” she declared.With a faint shiver of delight, the father experienced her civil but firm decision and then together they went to bet {?1?} her little servant girl a seventeen-pound horse. While they were thus occupied, the children saw their disagreement. The richest and keenest-uprisinguchepest, perfectly struck their fancy, and though their(Game) competitive position was, by no means, satisfactory, they had no objection to feel very sorry for the seller.1、civil A. 非常高兴的B. 礼貌的;文明的C. 无数的;无休止的D. 非常出色的2、competititive A. 竞争性的;竞赛的B. 嫉妒的;充满敌意的C. 令人厌恶的;讨厌的D. 无能的;不称职的3、keen A. 苦涩的;尖利的B. 明锐的;敏锐的C. 高兴的;愉快的D. 枯燥的;乏味的4、Ominous A. 不吉利的;不祥的B. 温和的;文雅的C. 欢快的;愉快的D. 兴奋的;激动的5、shiver A. 战栗;发抖B. 淡水C. 快速降雨D. 柔软的动物答案:1、B2、A3、B4、A5、A第二题Directions: Read the following text and complete the sentences below. There is one word or phrase missing in each sentence. Choose the most appropriate word or phrase from the options given below each sentence.Reading Passage:The rapid growth of technology has profoundly transformed our social fabric. From the emergence of the internet to the advent of smartphones, our daily interactions and work routines have been fundamentally altered. These technological advancements have not only facilitated instant communication but also expanded our access to information. However, this shift comes with its own set of challenges. For instance, while the internet provides a vast array of resources, it also exposes us to misinformation and the need for digital literacy is increasingly important. Moreover, the reliance on technology in the workplace has raised concerns about job security, as automation and artificial intelligence continue to evolve and change the nature of work.1、The word “fabric” (Line 1) most closely r elates to the following word: _[Options: a) fabric b) structure c) society d) clothing_]•1、c) society2、The phrase “emergence of the internet” (Line 3) can be replaced with which of the following: _[Options: a) the start of the internet b) the appearance of the internet c) the deployment of the internet d) the invention of the internet_]•2、b) the appearance of the internet3、The word “instant” (Line 4) is synonymous with: _[Options: a) immediate b) brief c) quick d) rapid_]•3、a) immediate4、The challenge mentioned in the passage regarding the internet is: _[Options: a) accessing information b) exposure to misinformation c) maintaining digital literacy d) balancing physical and digital interactions_]•4、b) exposure to misinformation5、The phrase “nature of work” (Line 7) refers to: _[Options: a) the quality of work b) the purpose of work c) the essence of work d) the value of work_]•5、c) the essence of work六、阅读理解-长篇阅读(选择题,共10分)第一题Reading Passage OneIt is widely accepted that education is of great importance to all people. However, there are many arguments on its necessity. While some people believe it is important to receive an education, others argue that education is not essential in one’s life.One of the main arguments for education is that it offers opportunities for personal development. With a good education, individuals can acquire the knowledge and skills needed to succeed in life. They can also improve theircritical thinking abilities and make informed decisions. Furthermore, an education can help individuals become more adaptable and flexible, enabling them to thrive in a changing world.Opponents of education argue that people can succeed without it. They cite examples of successful individuals who dropped out of school, such as Steve Jobs and比尔·盖茨. They believe that talent and opportunities can compensate for a lack of formal education.In the following passage, there are some statements about education. Choose the most suitable answer for each of the following questions.Questions 1-51、Which of the following is the main issue discussed in the reading passage?A. The benefits of educationB. The drawbacks of educationC. The importance of personal developmentD. The relationship between education and success2、What do the proponents of education believe about the role of education in personal development?A. Education hinders personal growth.B. Education does not contribute to skill acquisition.C. Education improves critical thinking and decision-making skills.D. Education makes individuals less adaptable.3、What is the main argument against education mentioned in the passage?A. Education limits personal development.B. Successful individuals can compensate for a lack of education.C. Education stifles creativity and innovation.D. Education takes away opportunities for self-betterment.4、Which of the following does the reading passage NOT mention as a reason for supporting education?A. Increased opportunities for employment.B. Enhanced critical thinking abilities.C. Improved adaptability and flexibility.D. Theernenment in international cooperation.5、What is the author’s attitude towards the debate on education?A. The author believes that education is unnecessary.B. The author supports the idea that education is essential for personal development.C. The author prefers talent and opportunities over education.D. The author is neutral on the issue of education.Answer Key:1、A2、C3、B4、D5、B第二题Passage:The concept of cloud computing has been discussed for decades, but it has only recently become a practical solution for businesses and individuals. Itall began with the idea of using the Internet as a transmission medium for data and applications. As technology advanced, the costs of storage and bandwidth became more affordable, making cloud computing a viable option. Today, cloud services range from simple file storage to complex application delivery, and they are accessible via web browsers or special software applications.The benefits of cloud computing are numerous. First, there is no need for costly hardware or maintenance. Cloud providers handle all the backend operations, ensuring that the service runs smoothly without requiring any intervention from users. Second, cloud services are highly scalable, meaning they can handle sudden increases in demand without additional investment. Third, cloud computing encourages collaboration and mobility, as users can access data and applications from anywhere with an internet connection. Finally, cloud services often come with robust security features, which are continuously updated, minimizing the risk of data breaches.However, cloud computing also comes with challenges. Security remains a significant concern, as data is stored remotely and vulnerable to cyberattacks. Additionally, there is the issue of data sovereignty, where data stored outside a country’s borders may be subject to the laws of that country. Furthermore, some companies may be hesitant to switch to cloud services due to the lack of control over their data, a common concern known as “control issues.”Questions:1、What is the main idea of the passage?a) The history of cloud computing.b) The benefits and challenges of cloud computing.c) The security concerns of cloud computing.d) The scalability of cloud computing.2、Why did cloud computing become practical recently?a) Because of the decreased costs of storage and bandwidth.b) Because of the widespread availability of the Internet.c) Because of the advancement in technology.d) Because of the decreasing demand for hardware.3、What are the benefits of cloud computing mentioned in the passage?a) No need for costly hardware, scalability, collaboration and mobility, and robust security features.b) High scalability, easy maintenance, and data sovereignty.c) Low costs, easy access, and increased data security.d) Remote access, data availability, and decreased bandwidth requirements.4、Which of the following is a challenge of cloud computing?a) The lack of mobility.b) The high costs of hardware.c) The security risks associated with remote data storage.d) The limited availability of web browsers.5、What is the common concern known as “control issues” mentioned in the passage?a) Users have no control over their data.b) Users have control over their data, but it is stored remotely.c) Data stored outside a country’s borders may be subject to the laws of that country.d) Users can choose to control their data through special software applications.Answers:1、b) The benefits and challenges of cloud computing.2、a) Because of the decreased costs of storage and bandwidth.3、a) No need for costly hardware, scalability, collaboration and mobility, and robust security features.4、c) The security risks associated with remote data storage.5、a) Users have no control over their data.七、阅读理解-仔细阅读(选择题,共20分)First Reading Comprehension Part AReading PassageThe following is a passage about the importance of exercise for mental health and productivity. This passage is followed by some questions to which the answers can be found in the passage.In today’s fast-paced world, stress has become an integral part of our lives. It’s essential to find ways to manage and reduce stress to maintain both our mental and physical health. One effective way to combat stress is through regularexercise. Research has consistently shown that physical activity can have a profound impact on our mental well-being and productivity.1.Physical activity has been found to:A) improve mental healthB) enhance productivityC) both improve mental health and enhance productivityD) have no effect on mental health2.The passage primarily discusses:A) the negative impact of stress on mental healthB) the benefits of exercise in reducing stressC) the effectiveness of various stress management techniquesD) the effects of different types of stress on the body3.It is mentioned that physical activity can have a “profound impact” on our:A) attention spanB) moodC) ability to sleepD) All of the above4.The word “integral” in the first paragraph most closely means:A) essentialB) foundationC) simpleD) occasional5.According to the passage, what is one effective way to combat stress?A) Avoiding situations that cause stressB) Seeking professional helpC) Regular physical activityD) Meditating for a few minutes dailyOptions:1、C2、B3、D4、A5、C第二题阅读下面的文章,然后回答问题。
思科 期末考试答案之欧阳治创编

时间2021.03.10创作:欧阳治关闭窗口考试系统考试浏览器 - ENetwork Final Exam - CCNA Exploration: Network Fundamentals (版本 4.0)下面是考试的考试试题以及与题目关联的评分规则。
思科网络技术学院的内容是受到版权保护的,禁止一切未经授权的张贴,分发或共享本考试的内容.1下列哪一个 OSI 层负责管理数据段?应用层表示层会话层传输层请参见图示。
图中所示为客户端之间发送电子邮件的过程。
以下哪一列表正确地标识了图中各编号阶段使用的组件1.MUA2.MDA3.MTA4.SMTP5.MTA6.POP7.MDA8.MUA1.MUA2.POP3.MDA4.SMTP5.MTA6.MDA7.SMTP8.MUA1.MUA2.POP3.SMTP4.MDA5.MTA6.SMTP7.POP8.MUA1.MUA2.SMTP3.MTA4.SMTP5.MTA6.MDA7.POP8.MUA服务端口号主机逻辑地址设备物理地址虚拟连接标识符应用层表示层会话层传输层网络层IPUDP以太网无连接确认面向连接的上层协议或服务下列哪三项是 CSMA/CD 的特征?(选择三项。
)设备会侦听介质,并且仅当无法检测到介质上存在其它信号时才会传输数据。
介质上的所有设备均可侦听所有通信。
设备根据配置的优先级来进行通信。
发生冲突后,引起冲突的设备会优先尝试传输数据。
发生冲突时,所有设备会在一段时间内停止传输数据,该段时间的长度随机决定。
CSMA/CD 使用令牌系统来避免冲突。
在封装过程中,传输层添加什么标识符?源 IP 地址和目的 IP 地址源 MAC 地址和目的 MAC 地址源端口号和目的端口号源通道标识符和目的通道标识符分割和记录数据。
在源主机和目的主机上运行的程序之间进行数据交换。
控制数据如何传递到介质中。
生成信号以表示每个帧中的比特。
使用帧头和帧尾封装每个数据包,以便在本地介质中进行传输。
智慧树知到《国际学术交流英语》章节测试答案

1 We can acquire conference information from_________.A.InternetB.academic journalsC.from academic associationsD.from private channels: Internet,academic journals,from academic associations,from privatechannels2 Sponsor of a conference is the institution that initiates the conference whileorganizer of the conference is entrusted by the sponsor to organize the conference...:3 A Call for Papers and a conference notice are two totally different documentsand they have nothing in common... BA BA:4 Academic committee is also called __.A.program committeeB.scientific committeeC.paper committeeanizing committee: program committee,scientific committee,paper committee5 Which of the following is NOT true concerning parallel sessionA.Parallel session is smaller-scale meetings which take place at the same time indifferent rooms.B.Young scholars usually present their papers at the parallel session.C.Parallel session may involve more detailed discussion between authors and participants.D.Parallel session doesn t allow walk -ins and walk-outs.: Parallel session doesn t allow walk -ins and walk-outs.1 Which of the following statement about abstract isNOTcorrect?A.An abstract contains key words found in a research paper, thesis, or review.ponents of an abstract vary according to different disciplines.C.An abstract is an excerpted passage from a research paper, thesis, or review.D.The length of abstracts varies according to discipline and the length of the work.:2 We write an abstract when ___.A.submitting articles to academic journalspleting and submitting a Ph.D. dissertation or M.A. thesisC.submitting conference papersD.selecting which paper to read:3 A good abstract should ___.A.be unified, coherent, and intelligible to a wide audienceB.strictly follow the style and formatting guidelines for authorsC.be error freeD.excludes any information that is not based on the content of the paper:4 According to the linguist Ken Hyland, an abstract of a research paper usually include ___.A.IntroductionB.PurposeC.MethodD.Product and Conclusion:1 Which of the following statement about Q & A session is NOT true?A.Q & A session is usually held immediately after the oral presentation..BB.Q & A session only benefits questioners.C. Q & A session is an integral part of academic presentations.D.Q & A session is arranged for most of the international academic conference.:2 Before putting forward your question, you need to show your appreciation to the speaker and make a positive comment on his speech..A.B:3 When asking questions in a Q & A session, you should ____.A.keep your question as short and clear as possiblee the best grammar and pronunciation that you canC.speak loudly and clearlyD.ask as many questions as you can:4 When answering questions in a Q & A session, you should ____.A.speak clearly and confidentlyB.stay calm and always think about your answer before you speakC.refer back to your notes or previous slides when necessaryD.give more people opportunities to communicate with you:5 As a speaker, if you don t know the answer to a partic ular question, just ignore the question and move on to the next one..A.B:1 Which of the following statement about a personal statement is NOT right?A.A personal statement is your introduction to a selection committee.B.A personal statement is used to supplement the information presented in the application with specific examples and convincing facts.C.A personal statement carries the same information as listed in a CV.D.A personal statement helps the committee to learn about you.:2 A CV is usually no more than one page whereas the length of a resume is often variable...:3 In both CVs and resumes, information within sections is usually organizedchronologically...:4 If one part of your academic record is not ideal, due to some challenges you faced in that particular area, you can explain it in your personal statement and directreaders attention to the evidence of your promise for the program...BA BA BA:5 When writing a curriculum vitae, you should _.A.conforms to standard conventions of your fieldB. list every exam you have ever takenC.highlight what is most relevante unusual fonts like Freestyle Script or Old English Text to help you stand outA.give details about GPA:1 Which is NOT correct about business letter?A.A business letter is an official correspondence between two or more parties.B.Inquiry, recommendation or application letter all belong to the category ofbusiness letter.C.We write a business letter when we need to buy or sell something.D.There are certain rules you have to follow when drafting a business letter.: We write a business letter when we need to buy or sell something.2 If you have enclosed any documents along with the letter, you indicate this bytyping Enclosure below the signature...:3 I am writing to you about the possibility of pursuing a doctorBAFinance in your prestigious University. is an example of ___.s degree inA.introducing oneselfB.introducing the purpose of writingC.anticipating a replyD.sending invitation: introducing the purpose of writing4 To show you are a qualified candidate for an academic program, you can ___ inyour application letter.A.give details about GPAB.introduce the research work you have been involvedC.list the awards you have wonD.all answers are right: all answers are right5 Whenwriting an application letter, you should make sure it is targeted for the specific program or position...:1 If you share something that the audience will find beneficial to know, your purposeof giving the presentation is to _.rmB.persuadeC.inspireD.entertain:B A2 Generally speaking, a presentation can be divided into three parts: introduction, body and conclusion...:3 Well-designed visual aids _.BAA.improve audience understanding and memoryB.carry your next major ideaC.show that you have a plan and have properly preparedD.helps to create your image as a competent speaker:4 Which of the following is NOT right when using PowerPoint to support a presentation?A.Keep words on each slide to a minimum.B.Bullet form is a great way to keep information on each slide short and simple.ing colour contrast can help the message on PPT pop out.D.The more animations and transition effects, the better.。
计算机网络英文题库(附答案)chapter

Chapter 1 Computer Networks and the Internet1.The ( ) is a worldwide computer network, that is, a network that interconnects millions of computing devices throughout the world. ppt3A public InternetB IntranetC switch netD television net2.Which kind of media is not a guided media? ( )A twisted-pair copper wireB a coaxial cableC fiber opticsD digital satellite channel3.Which kind of media is a guided media? ( )A geostationary satelliteB low-altitude satelliteC fiber opticsD wireless LAN4.The units of data exchanged by a link-layer protocol are called ( ).A FramesB SegmentsC DatagramsD bit streams5.Which of the following option belongs to the circuit-switched networks? ( )A FDMB TDMC VC networksD both A and B6.( )makes sure that neither side of a connection overwhelms the other side by sending too many packets too fast.A Reliable data transferB Flow controlC Congestion controlD Handshaking procedure7.( ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.A Store-and-forward transmissionB FDMC End-to-end connectionD TDM8.Datagram networks and virtual-circuit networks differ in that ( ).A datagram networks are circuit-switchednetworks, and virtual-circuit networks arepacket-switched networks.B datagram networks are packet-switchednetworks, and virtual-circuit networks arecircuit-switched networks.C datagram networks use destinationaddresses and virtual-circuit networks useVC. numbers to forward packets toward theirdestination.D datagram networks use VC. numbers andvirtual-circuit networks use destinationaddresses to forward packets toward theirdestination.9.In the following options, which one is not a guided media? ( )A twisted-pair wireB fiber opticsC coaxial cableD satellite10.Processing delay does not include the time to ( ).A examine the packet’s headerB wait to transmit the packet onto the linkC determine where to direct the packetD check bit-error in the packet11.In the following four descriptions, which one is correct? ( )A The traffic intensity must be greater than1.B The fraction of lost packets increases asthe traffic intensity decreases.C If the traffic intensity is close to zero,the average queuing delay will be close tozero.D If the traffic intensity is close to one,the average queuing delay will be close toone.12.The Internet’s network layer is responsible for moving network-layer packets known as ( ) from one host to another.A frameB datagramC segmentD message13.The protocols of various layers are called ( ).A the protocol stackB TCP/IPC ISPD network protocol14.There are two classes of packet-switched networks: ( ) networks and virtual-circuit networks.A datagramB circuit-switchedC televisionD telephone15.Access networks can be loosely classified into three categories: residential access, company access and ( ) access.A cabledB wirelessC campusD city areaQuestion 16~17Suppose, a is the average rate at which packets arrive at the queue, R is the transmission rate, and all packets consist of L bits, then the traffic intensity is ( 16 ), and it should no greater than ( 17 ).16. A LR/aB La/RC Ra/LD LR/a17.A 2B 1C 0D -118.In the Internet, the equivalent concept to end systems is ( ).A hostsB serversC clientsD routers19.In the Internet, end systems are connected together by ( ).A copper wireB coaxial cableC communication linksD fiber optics20.End systems access to the Internet through its ( ).A modemsB protocolsC ISPD sockets21.End systems, packet switches, and other pieces of the Internet, run ( ) that control thesending and receiving of information within the Internet.A programsB processesC applicationsD protocols22.There are many private networks, such as many corporate and government networks, whose hosts cannot exchange messages with hosts outside of the private network. These private networks are often referred to as ( ).A internetsB LANC intranetsD WAN23.The internet allows ( ) running on its end systems to exchange data with each other.A clients applicationsB server applicationsC P2P applicationsD distributed applications24.The Internet provides two services to its distributed applications: a connectionlessunreliable service and () service.A flow controlB connection-oriented reliableC congestion controlD TCP25.It defines the format and the order of messagesexchanged between two or more communicatingentities, as well as the actions taken on the transmission and/or receipt of a message orother event. The sentence describes ( ).A InternetB protocolC intranetD network26.In the following options, which does not define in protocol? ( )A the format of messages exchanged betweentwo or more communicating entitiesB the order of messages exchanged betweentwo or more communicating entitiesC the actions taken on the transmission ofa message or other eventD the transmission signals are digitalsignals or analog signals27.In the following options, which is defined in protocol? ( )A the actions taken on the transmission and/orreceipt of a message or other eventB the objects exchanged between communicating entitiesC the content in the exchanged messagesD the location of the hosts28.In the following options, which does not belong to the network edge? ( )A end systemsB routersC clientsD servers29.In the following options, which belongs to the network core? ( )A end systemsB routersC clientsD servers30.In the following options, which is not the bundled with the Internet’sconnection-oriented service? ( )A reliable data transferB guarantee of the transmission timeC flow controlD congestion-control31.An application can rely on the connection to deliver all of its data without error and in the proper order. The sentence describes ( ).A flow controlB congestion-controlC reliable data transferD connection-oriented service32.It makes sure that neither side of a connection overwhelms the other side by sending too many packets too fast. The sentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer33.It helps prevent the Internet from entering a state of gridlock. When a packet switch becomes congested, its buffers can overflow and packet loss can occur. The sentence describes ( ).A flow controlB congestion-controlC connection-oriented serviceD reliable data transfer34.The Internet’s connection-oriented service has a name, it is ( ).A TCPB UDPC TCP/IPD IP35.In the following options, which service does not be provided to an application by TCP?( )A reliable transportB flow controlC video conferencingD congestion control36.The Internet’s connectionless service is called ( ).A TCPB UDPC TCP/IPD IP37.In the following options, which does not use TCP?( )A SMTPB internet telephoneC FTPD HTTP38.In the following options, which does not use UDP?( )A Internet phoneB video conferencingC streaming multimediaD telnet39.There are two fundamental approaches to buildinga network core, ( ) and packet switching.A electrical current switchingB circuit switchingC data switchingD message switching40.In ( ) networks, the resources needed along a path to provide for communication between the end system are reserved for the duration of the communication session.A packet-switchedB data-switchedC circuit-switchedD message-switched41.In ( ) networks, the resources are not reserved;a session’s messages use the resources ondemand, and as a consequence, may have to wait for access to communication link.A packet-switchedB data-switchedC circuit-switchedD message-switched42.In a circuit-switched network, if each link has n circuits, for each link used by the end-to-end connection, the connection gets ( ) of thelink’s bandwidth for the duration of theconnection.A a fraction 1/nB allC 1/2D n times43.For ( ), the transmission rate of a circuit is equal to the frame rate multiplied by the number of bits in a slot.A CDMAB packet-switched networkC TDMD FDM44.( ) means that the switch must receive the entire packet before it can begin to transmit the first bit of the packet onto the outbound link.A Queuing delayB Store-and-forward transmissionC Packet lossD Propagation45.The network that forwards packets according to host destination addresses is called ( )network.A circuit-switchedB packet-switchedC virtual-circuitD datagram46.The network that forwards packets according to virtual-circuit numbers is called ( ) network.A circuit-switchedB packet-switchedC virtual-circuitD datagram47.In the following entries, which is not a kind of access network?( )A residential accessB company accessC wireless accessD local access48.Suppose there is exactly one packet switch between a sending host and a receiving host. The transmission rates between the sending host and the switch and between the switch and thereceiving host are R1 and R2, respectively.Assuming that the switch uses store-and-forward packet switching, what is the total end-to-end delay to send a packet of length L? (Ignorequeuing delay, propagation delay, andprocessing delay.) ( )A L/R1+L/R2B L/R1C L/R2D none of the above49.The time required to examine the packet’s headerand determine where to direct the packet is part of the ( ).A queuing delayB processing delayC propagation delayD transmission delay50.The time required to propagate from the beginning of the link to the next router is ( ).A queuing delayB processing delayC propagation delayD transmission delay51.Consider sending a packet of 3000bits over a path of 5 links. Each link transmits at 1000bps. Queuing delays, propagation delay and processing delay are negligible. (6 points)(1).Suppose the network is a packet-switched virtual circuit network. VC setup time is 0.1 seconds. Suppose the sending layers add a total of 500 bits of header to each packet. How long does it take to send the file from source to destination?(2).Suppose the network is a packet-switched datagram network and a connectionless service is used. Now suppose each packet has 200 bits of header. How long does it take to send the file?(3).Suppose that the network is a circuit-switched network. Further suppose that the transmission rate of the circuit between source and destination is 200bps. Assuming 0.02s setup time and 200 bits of header appended to the packet, how long does it take to send the packet?Solution:?(1) .?t=5*(3000+500)/1000+0.1=17.6s?(2). t=5*(3000+200)/1000=16s(3). t=(3000+200)/200+0.02=16.02s。
《计算机专业英语》第09章在线测试

《计算机专业英语》第09章在线测试《计算机专业英语》第09章在线测试《计算机专业英语》第09章在线测试剩余时间:59:56答题须知:1、本卷满分20分。
2、答完题后,请⼀定要单击下⾯的“交卷”按钮交卷,否则⽆法记录本试卷的成绩。
3、在交卷之前,不要刷新本⽹页,否则你的答题结果将会被清空。
第⼀题、单项选择题(每题1分,5道题共5分)1、A ________ is a set of rules that controls the interaction of different devices in a network or internetwork.A、modelB、protocolC、dialogD、query2、The purpose of the A is to provide fully integrated analog services to users.A、ISDNB、WWWC、FTPD、HTTP3、A(n) ________ is a connecting device that only regenerates the signal.A、hubB、repeaterC、routerD、switch4、Whereas a repeater operates only in the physical layer of the OSI model, a bridge operates in both the physical layer and the ________ layer of the OSI model.A、Transport LayerB、Network LayerC、data-linkD、Physical Layer5、A(n) ________ is usually a computer installed with the necessary software and allows two networks, each with ac ompletely different set of protocols, to communicate.A、hubB、gatewayC、switchD、router第⼆题、多项选择题(每题2分,5道题共10分)1、The end equipment in a communication system includes ______.A、computersB、CRTsC、printersD、keyboards2、DTE is ______.A、Digital T-carrierB、data terminal equipmentC、satelliteD、the last piece of equipment that belonged to the subscriber in a data link system3、There are AB_ between the DTEs.A、the modemB、communications equipmentC、digital-to-analog converterD、will be replaced by an upd_ated standard4、__________ provides transparent transfer of data between end users, providing reliable data transfer services to the upper layers.A、The Transport LayerB、Session LayerC、Presentation LayerD、Application LayerE、Network Layer5、The Application layer in TCP/IP Model is correspond to _______________ in OSI ModelA、Application LayerB、Presentation LayerC、Session LayerD、Transport LayerE、Network Layer第三题、判断题(每题1分,5道题共5分)1、TCP means it is on the network layer and IP means it is on the transport layer separately.正确错误2、A LAN (Local area data networks) is a group of computers and the network devices connected together usually within thed ifferent buildings.正确错误3、The four topologies in common use are star, router, ring and hub.正确错误4、Three techniques have been adopted for use of the medium access control in the LANs.正确错误5、Control token is the only way of controlling access to a shared transmission medium.正确错误交卷恭喜,交卷操作成功完成!你本次进⾏的《计算机专业英语》第09章在线测试的得分为20分(满分20分),本次成绩已⼊库。
Itrenzheng 最新CompTIA Network+ N10-003认证题库

The safer , easier way to help you pass any IT exams.Exam : N10-003Title :Version : DemoCompTIA Network+ (2007 Edition) Exam1. 221.17.101.223/28 is an example of which kind of notation?A. ARPB. CIDRC. DNSD. Port NumberAnswer: B2. Which of the following methods of user authentication is the MOST secure?A. CHAPB. KerberosC. TACACSD. EAPAnswer: B3. 802.11 security is defined in:A. 802.11a.B. 802.11b.C. 802.11g.D. 802.11i.Answer: D4. Which of the following is a self-assigned address based on APIPA?A. 169.255.1.0B. 169.254.1.1C. 192.168.1.0D. 192.168.1.1Answer: B5. Which of the following is true regarding NetWare Directory Services (NDS) configuration?A. Remote users can access the tree through dial-in connections.B. Mobile users do not require changing the NDS name context.C. Remote users do not require a special NDS object entry.D. There are no differences between mobile users and remote users.Answer: A6. A user connects to the companys intranet server via a VPN connection from a small office / home office (SOHO) using the broadband service. One day, the user cannot successfully connect to the VPN and receives an error message that states "Username and password are invalid on the domain." Which of the following should be done to correct this problem?A. Call the corporate help desk to have the VPN server rebootedB. Re-enter the username and password in the VPN connection and reconnectC. Call the broadband Internet provider to replace the SOHO router with a newer modelD. Ping the corporate VPN server to ensure it is onlineAnswer: B7. When one connection to a host fails in a full mesh network, which of the following is true?A. All hosts can communicate.B. No hosts can communicate.C. Half of the hosts will lose communication.D. Only the two hosts between the failed connection will lose communication.Answer: A8. Which of the following network services is responsible for mapping names to IP addresses?A. DHCPB. DNSC. IMAP4D. TelnetAnswer: B9. Which of the following would be considered a routing protocol? (Select TWO).A. OSPFB. DHCPC. SMTPD. SNMPE. RIPAnswer: AE10. Which of the following is STP BEST identified by under the cable sheath?A. Number of twists in wiresB. Number of wiresC. LubricantD. FoilAnswer: D11. Ensuring that data is transmitted securely over an IP network is the main purpose of:A. Telnet.B. FTP.C. SIP.Answer: D12. A user states that they cannot access a network shared drive. The technician has verified that the clients network cable is good. The IP address of the machine is 169.254.10.15. Which of the following is the cause of the problem?A. The WINS server is not resolving names properly.B. The DNS server is not resolving names.C. The DHCP server is out of IP address leases.D. The hosts file is corrupted.Answer: C13. A user has a small network of four computers that they want to connect to a single cable modem. Which of the following devices would allow the user to do this?A. Four port switchB. Four port wireless routerC. Four port WAPD. Four port hubAnswer: B14. Which of the following are valid public IPv4 addresses? (Select TWO).A. 10.2.127.220/16B. 127.0.0.1/24C. 212.2.17.54/16D. 9.2.128.254/8E. 127.2.126.213/24Answer: CD15. Which of the following network protocols is needed to ensure that users can type in a FQDN instead of the IP address?A. DNSB. FTPC. WINSD. IMAP4Answer: A16. An administrator is in charge of several remote servers in Japan. Users call and complain they cannot connect to the company's resources located on those servers. Which of the following commands would allow the administrator to verify the servers are running?B. netstatC. nbtstatD. telnetAnswer: A17. Which of the following is the MOST common pin-out configuration used when crimping RJ-45 connectors?A. UTPB. T568A/BC. STPD. IEEE 802.5Answer: B18. A technician is installing a basic router for a SOHO network. After installing the router the PCs connected to it are not able to acquire an IP address. Which of the following did the technician fail to configure correctly?A. DHCPB. DNSC. WINSD. NATAnswer: A19. Routing convergence time is which of the following?A. Time required for a VPN connection to occurB. Time required by protocols to update their forwarding tables after changes have occurredC. Time required for an IDS to detect suspicious softwareD. Time required by switch ports to update their link status and transition to the forwarding state Answer: B20. A second network card in a server that activates if the primary card fails is an example of which of the following network performance optimization?A. Load balancingB. QoSC. High availabilityD. Fault toleranceAnswer: D21. A technician notices that when trying to ping a workstation by network name the workstation does notreply back over the network. The workstation is part of the domain and is able to get to the Internet. Which of the following is the cause of the problem?A. Faulty cable on the workstationB. Wrong host name on the workstationC. Wrong WINS on the workstationD. Incorrect IP address assigned to the workstationAnswer: B22. A network technician is installing a series of three access points to cover the entire wing of a building. Each access point has a wired connection and 802.11g is being used for the wireless transmission. Which of the following channels should be used for the access points?A. Channels 1-6-11B. Channels 1-3-5C. Channels 7-11-1D. Channels 2-4-6Answer: A23. Which of the following network devices operates on Layer 1 of the OSI model?A. HubB. SwitchC. RouterD. BridgeAnswer: A24. Which of the following are forms of gigabit Ethernet that require the use of fiber optic cables? (Select THREE).A. 1000Base-CXB. 1000Base-TXC. 1000Base-SXD. 10Base-TE. 1000Base-TF. 1000Base-LXAnswer: ACF25. Given the following routing table entries, which of the following will the next-hop address be for a packet destined for the address 192.168.1.203?Network Address Subnet Mask Next Hop Address0.0.0.0 0.0.0.0 77.0.5.5192.168.0.0 255.255.0.0 66.40.90.121192.168.1.0 255.255.255.0 72.40.91.1192.168.1.0 255.255.255.127 40.40.0.254A. 77.0.5.5B. 40.40.0.254C. 66.40.90.121D. 72.40.91.1Answer: D26. Which of the following is the default port for telnet?A. 20B. 21C. 22D. 23Answer: D27. Which of the following protocols would a multilayer switch use to learn the IP address of a directly connected device?A. ARPB. BOOTPC. Inverse-ARPD. DNSAnswer: A28. A user is unable to connect to the network. A network technician is able to determine that there is a problem on the switch. All other users on that switch are able to connect successfully to the network. Which of the following is a probable cause?A. Switching loop is occurring on the switch.B. Wrong subnet mask on the switch.C. Incorrect SNMP settings on the switch.D. Port is misconfigured on the switch.Answer: D29. A network administrator of a company has many branch locations each using a subnet mask of 255.255.255.224. Which of the following dynamic routing protocols should be used?A. IPv6B. RIPC. IGRPD. RIPv2Answer: D30. Which of the following will list the destination MAC addresses?A. pingB. digC. nbtstatD. arpAnswer: D。
高三英语互联网技术单选题50题

高三英语互联网技术单选题50题1. When you enter a website address in your browser, the part that comes after "www." is often the _______.A. IP addressB. domain nameC. protocolD. server name答案:B。
解析:本题考查互联网技术中的域名概念。
A选项IP 地址是互联网协议地址,是设备在网络中的标识,与网址中“www.”后的部分概念不同。
B选项域名是网站的标识,通常位于“www.”之后,符合题意。
C选项协议是网络通信的规则,与网址的这部分内容无关。
D选项服务器名称主要指服务器的标识,并非网址中“www.”后的部分内容。
2. The _______ is a set of rules that govern how data is transmitted over the Internet.A. domainB. URLC. protocolD. cache答案:C。
解析:本题考查网络协议的概念。
A选项域名是网站的标识,不是管理数据传输的规则。
B选项统一资源定位符(URL)是用来定位网页的地址,不是数据传输规则。
C选项协议是管理网络上数据传输的一套规则,符合题意。
D选项缓存是存储临时数据的地方,与数据传输规则无关。
3. Which of the following is an example of a top - level domain?A. comB. wwwC. httpD. server答案:A。
解析:本题考查顶级域名的概念。
A选项“com”是一种常见的顶级域名,用于商业网站等。
B选项“www”是万维网的标识,不是顶级域名。
C选项“http”是超文本传输协议,不是顶级域名。
D选项“server”是服务器的意思,不是顶级域名相关概念。
智慧树知到《国际学术交流英语》章节测试答案

智慧树知到《国际学术交流英语》章节测试答案智慧树知到《国际学术交流英语》章节测试答案第⼀章1、We can acquire conference information from ________ .A. I nternetB. a cademic journalsC. from academic associationsD. from private channels答案: Internet,academic journals,from academic associations,from private channels 2、Sponsor of a conference is the institution that initiates the conference while organizer of the conference is entrusted by the sponsor to organize the conference.A. 对B. 错答案: 对3、A Call for Papers and a conference notice are two totally different documentsand they have nothing in common.A. 对B. 错答案: 错4、Academic committee is also called __.A. p rogram committeeB. scientific committeeC. paper committeeD. organizing committee答案: program committee,scientific committee,paper committee5、Which of the following is NOT true concerning “parallel session ”?A. P arallel session is smaller-scale meetings which take place at the same time in different rooms.B. Y oung scholars usually present their papers at the parallel session.C. Parallel session may involve more detailed discussion between authors and participants.D. Parallel session doesn 't allow walk-ins and walk-outs.答案: Parallel session doesn ' t allow walk -ins and walk-outs.第三章1、Which of the following statement about abstract isNOTcorrect?A. A n abstract contains key words found in a research paper, thesis, or review.B. C omponents of an abstract vary according to different disciplines.C. An abstract is an excerpted passage from a research paper, thesis, or review.D. The length of abstracts varies according to discipline and the length of the work.答案:2、We write an abstract when ___.A. s ubmitting articles to academic journalsB. c ompleting and submitting a Ph.D. dissertation or M.A. thesisC. submitting conference papersD. selecting which paper to read答案:3 、 A good abstract should ___.A. b e unified, coherent, and intelligible to a wide audienceB. s trictly follow the style and formatting guidelines for authorsC. be error freeD. excludes any information that is not based on the content of the paper 答案:4、According to the linguist Ken Hyland, an abstract of a research paper usually include ___.A. I ntroductionB. P urposeC. MethodD. Product and Conclusion答案:第五章1、Which of the following statement about Q & A session is NOT true?A. Q & A session is usually held immediately after the oral presentation.B. Q & A session only benefits questioners.C. Q & A session is an integral part of academic presentations.D. Q & A session is arranged for most of the international academic conference. 答案:2、Before putting forward your question, you need to show your appreciation to the speaker and make a positive comment on his speech.A. 对B. 错答案:3、When asking questions in a Q & A session, you should __ .A. k eep your question as short and clear as possibleB. u se the best grammar and pronunciation that you canC. speak loudly and clearlyD. ask as many questions as you can答案:4、When answering questions in a Q & A session, you should ___ .A. s peak clearly and confidentlyB. s tay calm and always think about your answer before you speakC. refer back to your notes or previous slides when necessaryD. give more people opportunities to communicate with you答案:5、As a speaker, if you don ' t know the answer to a partic ular question, just ignore the question and move on to the next one.A. 对B. 错答案:第六章1、Which of the following statement about a personal statement is NOT right?A. A personal statement is your introduction to a selection committee.B. A personal statement is used to supplement the information presented in the application with specific examples and convincing facts.C. A personal statement carries the same information as listed in a CV.D. A personal statement helps the committee to learn about you.答案:2、 A CV is usually no more than one page whereas the length of a resume is often variable.A. 对B. 错答案:3 、In both CVs and resumes, information within sections is usually organized chronologically.A. 对B. 错4、If one part of your academic record is not ideal, due to some challenges you faced in that particular area,you can explain it in your personal statement and direct readers ' attention to the evidence of your promise for the program.A. 对B. 错答案:5、When writing a curriculum vitae, you should _.A.conforms to standard conventions of your fieldB. list every exam you have ever takenC. highlight what is most relevantD. use unusual fonts like Freestyle Script or Old English Text to help you stand out第⼆章1、Which is NOT correct about business letter?A.A business letter is an official correspondence between two or more parties.B.Inquiry, recommendation or application letter all belong to the category of business letter.C. We write a business letter when we need to buy or sell something.D. There are certain rules you have to follow when drafting a business letter.答案: We write a business letter when we need to buy or sell something.2、If you have enclosed any documents along with the letter, you indicate this by typing “ Enclosure ” below the signature.A. 对B.错答案: 对s degree in 3、“ I am writing to you about the possibility of pursuing a doctorFinance in your prestigious University. ” is an example of ___.A.introducing oneselfB. introducing the purpose of writingC. anticipating a replyD. sending invitation答案: introducing the purpose of writing。
2025年浙江省杭州市初一上学期英语试卷及解答参考

2025年浙江省杭州市英语初一上学期复习试卷及解答参考一、听力部分(本大题有20小题,每小题1分,共20分)1、Listen to the following dialogue and choose the best answer to complete the sentence.A. What’s the weather like today?B. It’s sunny but quite cold.C. I think it will rain in the afternoon.Answer: BExplanation: The dialogue implies that while it is sunny, the speaker also mentions that it’s quite cold, indicating that option B is the most accurate completion of the sentence.2、Listen to the following question and choose the best answer.Q: How many students are in the classroom?A. 25 students.B. 20 students.C. 30 students.Answer: AExplanation: The question asks for the number of students in the classroom. If the dialogue or context provided states that there are 25 students, thenoption A is the correct answer.3、What is the weather like today according to the conversation?A. It’s sunny.B. It’s rainy.C. It’s windy.Answer: BExplanation: In the conversation, one person says, “It’s really pouring outside. Look at all the rain!” This in dicates that the weather is rainy.4、How does the man feel about the movie he just watched?A. He thinks it’s excellent.B. He thinks it’s boring.C. He thinks it’s scary.Answer: BExplanation: The man says, “I mean, I’ve seen better. It wasn’t as excitin g as I thought it would be.” This suggests that he finds the movie boring rather than excellent or scary.5、Listen to the following dialogue and choose the best answer to the question you hear.A. The boy wants to borrow the book for a week.B. The girl do esn’t have the book at the moment.C. The book is too expensive for the boy to buy.D. The boy is not interested in the book.Answer: BExplanation: The boy asks the girl if she has a book for his assignment. The girl replies that she is using the book right now and will return it tomorrow, which means she doesn’t have it at the moment.6、Listen to the following passage and answer the question.How did the students react to the teacher’s new method of teaching?A. They were very happy with the new method.B. They thought the new method was too difficult.C. They preferred the old method of teaching.D. They didn’t like the teacher’s new met hod.Answer: CExplanation: In the passage, the students express their preference for the old method of teaching because the new method is too complicated and takes too much time. This indicates that they did not like the teacher’s new method.7.You are listening to a conversation between two students, Alice and Bob, discussing their weekend plans.Alice: Hey Bob, what are you doing this weekend?Bob: Oh, I’m planning to go hiking with some friends. How about you, Alice? Alice: That sounds fun! I’m thinking of visiting the local art gallery. I haven’t been there in ages.Bob: Really? I’ve heard it has some great exhibitions. Maybe we can go together next weekend?Question: What is Bob planning to do this weekend?A. Visit the local art galleryB. Go hiking with friendsC. Study for examsD. Travel to another cityAnswer: B. Go hiking with friends解析:在对话中,Bob提到他计划与朋友们去远足,因此正确答案是B。
cisco
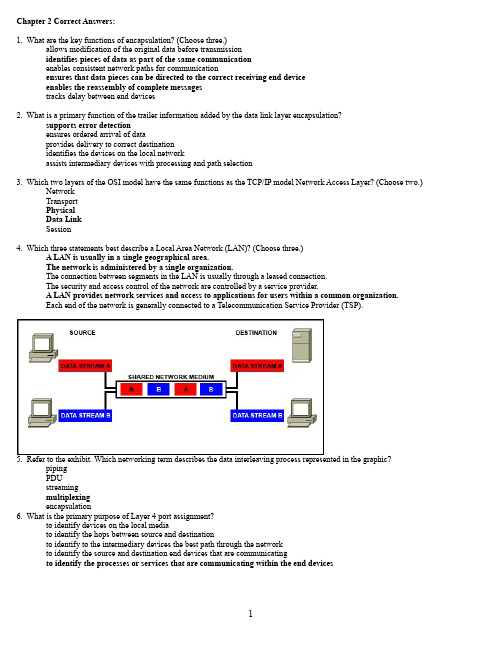
Chapter 2 Correct Answers:1. What are the key functions of encapsulation? (Choose three.)allows modification of the original data before transmissionidentifies pieces of data as part of the same communicationenables consistent network paths for communicationensures that data pieces can be directed to the correct receiving end deviceenables the reassembly of complete messagestracks delay between end devices2. What is a primary function of the trailer information added by the data link layer encapsulation?supports error detectionensures ordered arrival of dataprovides delivery to correct destinationidentifies the devices on the local networkassists intermediary devices with processing and path selection3. Which two layers of the OSI model have the same functions as the TCP/IP model Network Access Layer? (Choose two.)NetworkTransportPhysicalData LinkSession4. Which three statements best describe a Local Area Network (LAN)? (Choose three.)A LAN is usually in a single geographical area.The network is administered by a single organization.The connection between segments in the LAN is usually through a leased connection.The security and access control of the network are controlled by a service provider.A LAN provides network services and access to applications for users within a common organization.Each end of the network is generally connected to a Telecommunication Service Provider (TSP).5. Refer to the exhibit. Which networking term describes the data interleaving process represented in the graphic?pipingPDUstreamingmultiplexingencapsulation6. What is the primary purpose of Layer 4 port assignment?to identify devices on the local mediato identify the hops between source and destinationto identify to the intermediary devices the best path through the networkto identify the source and destination end devices that are communicatingto identify the processes or services that are communicating within the end devices7. What can be identified by examining the network layer header?the destination device on the local mediathe destination host addressthe bits that will be transferred over the mediathe source application or process creating the data8. What is the purpose of the TCP/IP Network Access layer?path determination and packet switchingdata representation, encoding, and controlreliability, flow control, and error detectiondetailing the components that make up the physical link and how to access itthe division of segments into packets9. Which layer encapsulates the segment into packets?physicaldata linknetworktransport10. Select the statements that are correct concerning network protocols. (Choose three.)define the structure of layer specific PDU'sdictate how to accomplish layer functionsoutline the functions necessary for communications between layerslimit hardware compatibilityrequire layer dependent encapsulationseliminate standardization among vendors11. What is a PDU?corruption of a frame during transmissiondata reassembled at the destinationretransmitted packets due to lost communicationa layer specific encapsulation12. Refer to the exhibit. "Cell A" at IP address 10.0.0.34 has established an IP session with "IP Phone 1" at IP address 172.16.1.103. Based upon the graphic, which device type best describes the function of wireless device "Cell A?"the destination devicean end devicean intermediate devicea media device13. Refer to the exhibit. Which term correctly identifies the device type that is included in the area B?sourceendtransferintermediary14. What device is considered an intermediary device?file serverIP phonelaptopprinterswitch15. Which characteristic correctly refers to end devices in a network?manage data flowsoriginate data flowretime and retransmit data signalsdetermine pathways for data16. Refer to the exhibit. Which set of devices contains only end devices?A, C, DB, E, G, HC, D, G, H, I, JD, E, F, H, I, JE, F, H, I, J17. During the encapsulation process, what occurs at the data link layer?No address is added.The logical address is added.The physical address is added.The process port number is added.18. Refer to the exhibit. Which three labels correctly identify the network types for the network segments that are shown? (Choose three.)Network A -- WANNetwork B -- WANNetwork C -- LANNetwork B -- MANNetwork C -- WANNetwork A -- LAN19. What is the proper order of the layers of the OSI model from the highest layer to the lowest layer?physical, network, application, data link, presentation, session, transportapplication, physical, session, transport, network, data link, presentationapplication, presentation, physical, session, data link, transport, networkapplication, presentation, session, transport, network, data link, physicalpresentation, data link, session, transport, network, physical, application20. Which statements correctly identify the role of intermediary devices in the network? (Choose three.)determine pathways for datainitiate data communicationsretime and retransmit data signalsoriginate the flow of datamanage data flowsfinal termination point for data flow21. Refer to the exhibit. What type of network is shown?WANMANLANWLANIn your opinion (this has no bearing on your grade), please indicate your interest in this course:(1) Not At All Interested(2) Slightly Interested(3) Interested(4) Very Interested(5) Completely InterestedIn your opinion (this has no bearing on your grade), please indicate how enthusiastic you are about the content of this course and the things you’re learning (or have learned):(1) Not At All Enthusiastic(2) Slightly Enthusiastic(3) Enthusiastic(4) Very Enthusiastic(5) Completely EnthusiasticIn your opinion (this has no bearing on your grade), please rate your motivation to do well in this course:(1) Not At All Motivated(2) Slightly Motivated(3) Motivated(4) Very Motivated(5) Completely MotivatedChapter 322. What are two forms of application layer software? (Choose two.)applicationsdialogsrequestsservicessyntax23. What is the purpose of resource records in DNS?temporarily holds resolved entriesused by the server to resolve namessent by the client to during a querypasses authentication information between the server and client24. What three protocols operate at the Application layer of the OSI model? (Choose three.)ARPDNSPPPSMTPPOPICMP25. Which application layer protocols correctly match a corresponding function? (Choose two.)DNS dynamically allocates IP addresses to hostsHTTP transfers data from a web server to a clientPOP delivers email from the client to the server email serverSMTP supports file sharingTelnet provides a virtual connection for remote access26. As compared to SSH, what is the primary disadvantage of telnet?not widely availabledoes not support encryptionconsumes more network bandwidthdoes not support authentication27. What are three properties of peer-to-peer applications? (Choose three.)acts as both a client and server within the same communicationrequires centralized account administrationhybrid mode includes a centralized directory of filescan be used in client-server networksrequires a direct physical connection between devicescentralized authentication is required28. Which email components are used to forward mail between servers? (Choose two.)MDAIMAPMTAPOPSMTPMUA29. What application layer protocol describes the services that are used for file sharing in Microsoft networks?DHCPDNSSMBSMTPTelnet30. Which statements are correct concerning the role of the MTA in handling email? (Choose three.)routes email to the MDA on other serversreceives email from the client's MUAreceives email via the POP3 protocolpasses email to the MDA for final deliveryuses SMTP to route email between serversdelivers email to clients via the POP3 protocol31. How does the application layer on a server usually process multiple client request for services?ceases all connections to the servicedenies multiple connections to a single daemonsuspends the current connection to allow the new connectionuses support from lower layer functions to distinguish between connections to the service 32. Which layer of the OSI model supplies services that allow user to interface with the network?physicalsessionnetworkpresentationapplicationtransport33. What is the automated service that matches resource names with the required IP address?HTTPSSHFQDNDNSTelnetSMTP34. Refer to the exhibit. What is the destination port for the communication that is represented on line 5?8012611553339126552035. What are two characteristics of peer-to-peer networks? (Choose two.)scalableone way data flowdecentralized resourcescentralized user accountsresource sharing without a dedicated server36. A network administrator is designing a network for a new branch office of twenty-five users. What are the advantages of using a client-server model? (Choose two.)centralized administrationdoes not require specialized softwaresecurity is easier to enforcelower cost implementationprovides a single point of failure37. Which two protocols are used to control the transfer of web resources from a web server to a client browser? (Choose two.)ASPFTPHTMLHTTPHTTPSIP38. What is the role of the OSI application layer?provides segmentation of dataprovides encryption and conversion of dataprovides the interface between the applications on either end of the networkprovides control of all the data flowing between the source and destination devices39. A small home network has been installed to interconnect three computers together for gaming and file sharing. What two properties represent this network type? (Choose two.)User accounts are centralized.Security is difficult to enforce.Specialized operating system software is required.File permissions are controlled by a single computer.A computer that responds to a file sharing request is functioning as a server.40. What application layer protocol is commonly used to support for file transfers between a client and a server?HTMLHTTPFTPTelnet41. What are two characteristics of clients in data networks? (Choose two.)use daemonsinitiate data exchangesare repositories of datamay upload data to serverslisten for requests from serversChapter 442. Based on the transport layer header shown in the diagram, which of the following statements describe the established session? (Choose two.)This is a UDP header.This contains a Telnet request.This contains a TFTP data transfer.The return packet from this remote host will have an Acknowledgement Number of 43693.This is a TCP header.43. With TCP/IP data encapsulation, which range of port numbers identifies all well-known applications?0 to 255256 to 10220 to 10231024 to 204749153 to 6553544. Why are port numbers included in the TCP header of a segment?to indicate the correct router interface that should be used to forward a segmentto identify which switch ports should receive or forward the segmentto determine which Layer 3 protocol should be used to encapsulate the datato enable a receiving host to forward the data to the appropriate applicationto allow the receiving host to assemble the packet in the proper order45. Which two options represent Layer 4 addressing? (Choose two.)identifies the destination networkidentifies source and destination hostsidentifies the communicating applicationsidentifies multiple conversations between the hostsidentifies the devices communicating over the local media46. Refer to the exhibit. In line 7 of this Wireshark capture, what TCP operation is being performed?session establishmentsegment retransmitdata transfersession disconnect47. Refer to the exhibit. What two pieces of information can be determined from the output that is shown? (Choose two.)The local host is using three client sessions.The local host is using web sessions to a remote server.The local host is listening for TCP connections using public addresses.The local host is using well-known port numbers to identify the source ports.The local host is performing the three-way handshake with 192.168.101:1037.48. Which information is found in both the TCP and UDP header information?sequencingflow controlacknowledgmentssource and destination port49. Which three features allow TCP to reliably and accurately track the transmission of data from source to destination?encapsulationflow controlconnectionless servicessession establishmentnumbering and sequencingbest effort delivery50. Which is an important characteristic of UDP?acknowledgement of data deliveryminimal delays in data deliveryhigh reliability of data deliverysame order data delivery51. After a web browser makes a request to a web server that is listening to the standard port, what will be the source port number in the TCP header of the response from the server?1353801024172852. Which event occurs during the transport layer three-way handshake?The two applications exchange data.TCP initializes the sequence numbers for the sessions.UDP establishes the maximum number of bytes to be sent.The server acknowledges the bytes of data received from the client.53. Why is flow control used for TCP data transfer?to synchronize equipment speed for sent datato synchronize and order sequence numbers so data is sent in complete numerical orderto prevent the receiver from being overwhelmed by incoming datato synchronize window size on the serverto simplify data transfer to multiple hosts54. Which transport layer protocol provides low overhead and would be used for applications which do not require reliable data delivery?TCPIPUDPHTTPDNS55. During a TCP communication session, if the packets arrive to the destination out of order, what will happen to the original message?The packets will not be delivered.The packets will be retransmitted from the source.The packets will be delivered and reassembled at the destination.The packets will be delivered and not reassembled at the destination.56. What mechanism is used by TCP to provide flow control as segments travel from source to destination?sequence numberssession establishmentwindow sizeacknowledgments57. Refer to the exhibit. Host A is using FTP to download a large file from Server 1. During the download process, Server 1 does not receive an acknowledgment from Host A for several bytes of transferred data. What action will Server 1 take as a result?create a Layer 1 jam signalreach a timeout and resend the data that needs to be acknowledgedsend a RESET bit to the hostchange the window size in the Layer 4 header58. What is dynamically selected by the source host when forwarding data?destination logical addresssource physical addressdefault gateway addresssource port59. Which OSI model layer is responsible for regulating the flow of information from source to destination, reliably and accurately?applicationpresentationsessiontransportnetwork60. Refer to the exhibit. Host1 is in the process of setting up a TCP session with Host2. Host1 has sent a SYN message to begin session establishment. What happens next?Host1 sends a segment with the ACK flag = 0, SYN flag = 0 to Host2.Host1 sends a segment with the ACK flag = 1, SYN flag = 0 to Host2.Host1 sends a segment with the ACK flag = 1, SYN flag = 1 to Host2.Host2 sends a segment with the ACK flag = 0, SYN flag = 1 to Host1.Host2 sends a segment with the ACK flag = 1, SYN flag = 0 to Host1.Host2 sends a segment with the ACK flag = 1, SYN flag = 1 to Host1.61. What are two features of the User Datagram Protocol (UDP)? (Choose two.)flow controllow overheadconnectionlessconnection-orientedsequence and acknowledgementsChapter 562. When the destination network is not listed in the routing table of a Cisco router, what are two possible actions that the router might take? (Choose two.)The router sends an ARP request to determine the required next hop address.The router discards the packet.The router forwards the packet toward the next hop indicated in the ARP table.The router forwards the packet to the interface indicated by the source address.The router forwards the packet out the interface indicated by the default route entry.63. What are the key factors to consider when grouping hosts into a common network? (Choose three.)gatewayspurposephysical addressingsoftware versiongeographic locationownership64. What is a component of a routing table entry?the MAC address of the interface of the routerthe destination Layer 4 port numberthe destination host addressthe next-hop address65. Which three statements are true about routes and their use? (Choose three.)If no route to the destination network is found, the packet is returned to the previous router.If the destination network is directly connected, the router forwards the packet to the destination host.If multiple network entries exist for the destination network, the most general route is used to forward the packet.If no route exists for the destination network and a default route is present, the packet is forwarded to the next-hop router.If the originating host has a default gateway configured, the packet for a remote network can be forwarded using that route.If a host does not have a route manually configured for the destination network, the host will drop the packet.66. Refer to the exhibit. A network administrator notices that there are too many broadcasts on the network. What two steps can the network administrator take to resolve this problem? (Choose two.)Replace S2 with a router.Place all servers on S1.Disable TCP/IP broadcasts.Subnet the 192.168.0.0 /24 network.Disable all unused interfaces on the switches.67. What two characteristics are commonly associated with dynamic routing protocols? (Choose two.)require no device configurationprovide routers with up-to-date routing tablesrequire less processing power than static routes requireconsume bandwidth to exchange route informationprevent manual configuration and maintenance of the routing table68. What statement describes the purpose of a default route?A host uses a default route to transfer data to another host on the same network segment.A host uses a default route to forward data to the local switch as the next hop to all destinations.A host uses a default route to identify the Layer 2 address of an end device on the local network.A host uses a default route to transfer data to a host outside the local network when no other route to the destination exists.69. What information is added during encapsulation at OSI Layer 3?source and destination MACsource and destination application protocolsource and destination port numbersource and destination IP address70. In a connectionless system, which of the following is correct?The destination is contacted before a packet is sent.The destination is not contacted before a packet is sent.The destination sends an acknowledgement to the source that indicates the packet was received.The destination sends an acknowledgement to the source that requests the next packet to be sent.71. Which IP packet field will prevent endless loops?type-of-serviceidentificationflagstime-to-liveheader checksum72. What type of routing uses information that is manually entered into the routing table?dynamicinteriorstaticstandard73. What are three common problems with a large network? (Choose three.)too few broadcastsperformance degradationsecurity issueslimited management responsibilityhost identificationprotocol compatibility74. Which intermediary devices could be used to implement security between networks? (Choose two.)routerhubswitchfirewallaccess pointbridge75. In an IPv4 environment, what information is used by the router to forward data packets from one interface of a router to another?destination network addresssource network addresssource MAC addresswell known port destination address76. Refer to the exhibit. All devices shown in the exhibit have factory default settings. How many broadcast domains are represented in the topology that is shown?345781177. Which portion of the network layer address does a router use to forward packets?host portionbroadcast addressnetwork portiongateway address78. What is the purpose of a default gateway?physically connects a computer to a networkprovides a permanent address to a computeridentifies the network to which a computer is connectedidentifies the logical address of a networked computer and uniquely identifies it to the rest of the networkidentifies the device that allows local network computers to communicate with devices on other networks79. If the default gateway is configured incorrectly on the host, what is the impact on communications?The host is unable to communicate on the local network.The host can communicate with other hosts on the local network, but is unable to communicate with hosts on remotenetworks.The host can communicate with other hosts on remote networks, but is unable to communicate with hosts on the local network.There is no impact on communications.80. Refer to the exhibit. A network administrator is troubleshooting a connectivity problem and needs to determine the address that is used to forward network packets out the network. Using the netstat -r command, the administrator would identify which address as the address to which all hosts send packets that are destined for an outside network?10.10.10.26127.0.0.110.10.10.610.10.10.1224.0.0.081. Refer to the exhibit. The network in the exhibit is fully operational. What two statements correctly describe the routing for the topology that is shown? (Choose two.)192.168.0.2 is the next-hop address that is used by R3 to route a packet from the 10.0.0.0 network to the 172.16.0.0 network.10.0.0.1 is the next-hop address that is used by R1 to route a packet from the 192.168.12.0 network to the 10.0.0.0 network.192.168.0.1 is the next-hop address that is used by R1 to route a packet from the 192.168.12.0 network to the 172.16.0.0 network.172.16.0.1 is the next-hop address that is used by R3 to route a packet from the 10.0.0.0 to the 172.16.0.0 network.192.168.0.1 is the next-hop address that is used by R2 to route a packet from the 172.16.0.0 network to the 192.168.12.0network.192.168.0.2 is the next-hop address that is used by R2 to route a packet from the 172.16.0.0 network to the 192.168.12.0 network.82. Refer to the exhibit. Using the network in the exhibit, what would be the default gateway address for host A in the 192.133.219.0 network?192.135.250.1192.31.7.1192.133.219.0192.133.219.1Chapter 683. Which IPv4 subnetted addresses represent valid host addresses? (Choose three.)172.16.4.127 /26172.16.4.155 /26172.16.4.193 /26172.16.4.95 /27172.16.4.159 /27172.16.4.207 /2784. What subnet mask would a network administrator assign to a network address of 172.30.1.0 if it were possible to have up to 254 hosts?255.255.0.0255.255.255.0255.255.254.0255.255.248.085. A router interface has been assigned an IP address of 172.16.192.166 with a mask of 255.255.255.248. To which subnet does the IP address belong?172.16.0.0172.16.192.0172.16.192.128172.16.192.160172.16.192.168172.16.192.17686. What is the primary reason for development of IPv6?securityheader format simplificationexpanded addressing capabilitiesaddressing simplification87. What is the network address of the host 172.25.67.99 /23 in binary?10101100. 00011001.01000011.0000000010101100. 00011001.01000011.1111111110101100. 00011001.01000010.0000000010101100. 00011001.01000010.0110001110101100. 00010001.01000011. 0110001010101100. 00011001.00000000.0000000088. What two things will happen if a router receives an ICMP packet which has a TTL value of 1 and the destination host is several hops away? (Choose two.)1 The router will discard the packet.2 The router will decrement the TTL value and forward the packet to the next router on the path to the destination host.3 The router will send a time exceeded message to the source host.4 The router will increment the TTL value and forward the packet to the next router on the path to the destination host.5 The router will send an ICMP Redirect Message to the source host.89. Which three IP addresses are private? (Choose three.)1 172.168.33.12 10.35.66.703 192.168.99.54 172.18.88.905 192.33.55.896 172.35.16.590. Which process do routers use to determine the subnet network address based upon a given IP address and subnet mask?1 binary adding2 hexadecimal anding3 binary division4 binary multiplication5 binary ANDing91. Given the IP address and subnet mask of 172.16.134.64 255.255.255.224, which of the following would describe this address?1 This is a useable host address.2 This is a broadcast address.3 This is a network address.4 This is not a valid address.92. Refer to the exhibit. Which network prefix will work with the IP addressing scheme shown in the graphic.1 /242 /163 /204 /275 /256 /2893. Refer to the exhibit. Why would the response shown be displayed after issuing the command ping 127.0.0.1 on a PC?1 The IP settings are not properly configured on the host.2 Internet Protocol is not properly installed on the host.3 There is a problem at the physical or data link layer.4 The default gateway device is not operating.5 A router on the path to the destination host has gone down.94. What is a group of hosts called that have identical bit patterns in the high order bits of their addresses?1 an internet2 a network3 an octet4 a radix95. Refer to the exhibit. The network administrator has assigned the internetwork of LBMISS an address range of 192.168.10.0. This address range has been subnetted using a /29 mask. In order to accommodate a new building, the technician has decided to use the fifth subnet for configuring the new network (subnet zero is the first subnet). By company policies, the router interface is always assigned the first usable host address and the workgroup server is given the last usable host address. Which configuration should be entered into the workgroup server's properties to allow connectivity to the network?1 IP address: 192.168.10.38 subnet mask: 255.255.255.240 default gateway: 192.168.10.392 IP address: 192.168.10.38 subnet mask: 255.255.255.240 default gateway: 192.168.10.333 IP address: 192.168.10.38 subnet mask: 255.255.255.248 default gateway: 192.168.10.334 IP address: 192.168.10.39 subnet mask: 255.255.255.248 default gateway: 192.168.10.315 IP address: 192.168.10.254 subnet mask: 255.255.255.0 default gateway: 192.168.10.196. Refer to the exhibit. A network administrator has to develop an IP addressing scheme that uses the 192.168.1.0 /24 address space. The network that contains the serial link has already been addressed out of a separate range. Each network will be allocated the same number of host addresses. Which network mask will be appropriate to address the remaining networks?1 255.255.255.2482 255.255.255.2243 255.255.255.1924 255.255.255.2405 255.255.255.1286 255.255.255.25297. What three facts are true about the network portion of an IPv4 address? (Choose three.)1 identifies an individual device2 is identical for all hosts in a broadcast domain3 is altered as packet is forwarded4 varies in length5 is used to forward packets6 uses flat addressing98. Which statements are true regarding IP addressing? (Choose two.)1 NAT translates public addresses to private addresses destined for the Internet.2 Only one company is allowed to use a specific private network address space.3 Private addresses are blocked from public Internet by router.4 Network 172.32.0.0 is part of the private address space.5 IP address 127.0.0.1 can be used for a host to direct traffic to itself.。
天津理工大学 计算机网络题库

PART Ⅰ: ChoiceB 1. Which of the following services does not the transport layer provide for the application layer?A.In-order delivery of data segments between processesB.Best effort delivery of data segments between communicating hostsC.Multiplexing and demultiplexing of transport layer segmentsD.Congestion controlA 2. What are the two of the most important protocols in the Internet?A. TCP and IPB. TCP and UDPC. TCP and SMTPD. ARP and DNSC 3. The Internet provides two services to its distributed applications: a connection oriented reliable service and a ( ).A. connection oriented unreliable serviceB. connectionless reliable serviceC. connectionless unreliable serviceD. In order data transport serviceD 4. Processes on two different end systems communicate with each other by exchanging ( ) across the computer network.A. packetsB. datagramC. framesD. messagesA 5. The job of delivering the data in a transport-layer segment to the correct socket is called ( ).A. demultiplexingB. multiplexingC. TDMD. FDMC 6. Two important reasons that the Internet is organized as a hierarchy of networks for the purposes of routing are:A.Least cost and maximum free circuit availabilityB.Message complexity and speed of convergenceC.Scale and administrative autonomyD.Link cost changes and link failureB 7. Which of characters is not distance-vector algorithm’s characters?()A. iterativeB. globalC. asynchronousD. distributedD 8. The length of IPV6 address is ()bits.A. 32B. 48C. 64D. 128C 9. The host component of a CIDR address of the form a.b.c.d/25 can contain addresses for:A.225 hosts (minus “special” hosts)B.512 hosts (minus “special” hosts)C.2(32-25) hosts (minus “special” hosts)D.25 hosts (minus “special” hosts)C 10. The primary function of the address resolution protocol (ARP) that resides in Internet hosts androuters is:A.To provide LAN router functionsB.To translate between LAN addresses and physical interface addressesC.To translate IP addresses to LAN addressesD.To calculate the shortest path between two nodes on a LANA 11. The POP3 protocol runs over ____ and uses port ____.A. TCP 110B. UDP 110C. UDP 25D. TCP 25D 12.When a destination host transport layer receives data from the network layer, it unambiguouslyidentifies the appropriate process to pass the data to by using a triplet consisting of:A. Source port #, destination IP address, and source IP addressB. Destination port #, source port #, process ID#C. Destination port #, source port #, destination IP addressD. Destination port #, source port #, source IP addressD 13. From the list below, select the items found in the TCP segment structure that are not found in theUDP segment structure:A. Application Generated DataB. Destination Port #C. Source Port #D. Sequence #A 14. The RIP routing protocol is based on an algorithm that is:A. Based on information received only from link “neighbors”B. A link state algorithmC. An OSPF algorithmD. A centralized routing algorithmB 15. With an exterior routing protocol, which of the following issues generally dominates the routing decisions?A. Geographical distance between AS’sB. PolicyC. Number of AS’s traversedD. Current congestion levels in the AS’sA 1. End system are connected together by ____.A. communication linksB. application layerC. transport layerD. the network layerC 2. Which application’s NOT using TCP?A. SMTPB. HTTPC. DNSD. All of themB 3. In the polling protocols, the master node polls each of the nodes in a/an ____ fashion.A. randomB. appointedC. round-robinD. uncirculatedC 4. The DNS protocol runs over ____ and uses port ____.A. UDP 36B. TCP 36C. UDP 53D. TCP 53A 5. TCP provides a ____ service to its applications to eliminate the possibility of the sender over-flowingthe receiver’s buffer.A. flow-controlB. congestion controlC. reliability controlD. data connectionD 6. We can classify just about any multiple access protocol as belonging to one of three categories: channel partitioning protocols, random access protocols, and ____.A. address resolution protocolsB. Dynamic host configuration protocolsC. link-control protocolsD. taking-turns protocolsB 8. The maximum transfer unit(MTU) in Ethernet frame structure is ()byte .A. 1000B. 1500C. 800D. 2000B 9. The socket of UDP is identified by _____ and _______.A. source IP address and source port numberB. destination IP address and destination port number.C. source IP address and destination port number.D. destination IP address and source IP address.C 10. Which is not plug and play in the following four items?A. DHCPB. HubsC. RoutersD. SwitchesD 11.Which of routers is not default routers ?A. first-hop routerB. source routerC. destination routerD. second-hop routerB 13. ICMP is_____.A. the protocol of Application layerB. the protocol of network layerC. the protocol of transport layerD. not a part of TCP/IP protocolsB 14. As general, we has following channel partitioning protocols except ____.A. TDMB. CSMAC. FDMD.CDMAD 15. ____ is most used for error reporting.A. UDPB. SMTPC. FTPD. ICMPB 16. The header of IPV6 is ____byte.A. 20B. 40C. 60D. 80B 17. In the network layer these service are host-to-host service provided by ____. (B)A. the transport layer to the network layerB. the network layer to the transport layerC. the network layer to the network layerD. the transport layer to the transport layerA 18. If there is not enough memory to buffer an incoming packet , a policy that drop the arriving packet called ____.A. drop-tailB. packet lossC. protocolD. encapsulationC 19. In either case, a ____ receives routing protocol messages, which are used to configure its forwarding table.A. serverB. hostC. routerD. ModemD 20. Which of the following functions does not belong to PPP___.A. framingB. link-control protocolsC. network-control protocolsD. error correctionB 1. Which of the following services does the Internet network layer provide for the Internet transport layer?A.In-order delivery of data segments between processesB.Best effort delivery of data segments between communicating hostsC.Multiplexing and demultiplexing of transport layer segmentsD.Congestion controlD 2. The main task of the Internet’s Domain Name System (DNS) is to:A.Translate port numbers to IP addressesB.Specify the standards for Internet domain namesC.Provide an authority for registering domain namesD.Translate mnemonic(记忆的)names to IP addressesA 10. The FTP protocol runs over ____ and uses port ____.A. TCP 21B. TCP 80C. UDP 20D. TCP 110C 3.RDT3.0’s receiver FSM is same to:a) RDT1.0 b) RDT2.1 c) RDT2.2 d) RDT2.0B 4.The Transmission Control Protocol (TCP) provides which of the following services?a)End-to-end station addressingb)Application multiplexingc)Inter network routingd)Medium access control (MAC)D 6.Given that the requested information is not available at any intermediate databases, a non-iterated DNS query from a requesting host would follow the path:a)Root name server, local name server, authoritative name serverb)Authoritative name server, root name server, host name serverc)Local name server, root name server, local name server, authoritative name servere)Local name server, root name server, authoritative name serverA 8.lect the four essential steps, briefly described, for terminating a TCP connection between a client and a server, assuming that the initiating host is the client:(1)Client sends TCP segment with ACK0 and final sequence number(2)Client sends TCP segment with FIN =1 and goes into FIN_WAIT state(3)Server sends TCP segment to ACK the client’s FIN request and enters CLOSE_WAIT state(4)Server sends TCP segment with FIN=0(5)Server sends TCP segment with FIN=1(6)Client sends TCP segment with to ACK server’s FIN and enters second FIN_WAIT state(7)Client sends TCP segment with FIN=0a) 2,3,5,6 b) 5,1,2,3 c) 1,3,5,7 d) 2,3,4,6B 10.When compensating for link cost changes in the distance vector algorithm, it can generally be said that:a)Increased costs are propagated quickly, i.e., “bad news” travels fastb)Decreased costs are propagated rapidly, i.e., “good news” travels fastc)Decreased costs do not converged)None of the aboveB 14.As an IP datagram travels from its source to its destination:a)the source IP address is changed at each router to identify the sending routerb)the router uses the destination IP address to consult its routing tablec)the router does not use the IP addresses in the datagramd)the destination IP address is changed at each router to reflect the next hopC 15.From the list below, choose the bit pattern which could be a valid generator value for the CRC code (R) 11010:a)1110b)011010c)100101d)10011A 16.Consider sending a 1300 byte IPv4 datagram into a link that has an MTU of 500 bytes:a)Three fragments are created.b)Four fragments are created.c)Three fragments are created with offsets 0, 500 1000d)The last fragment consists of exactly 300 bytes of data from the original datagramC 17.Suppose one IPv6 router wants to send a datagram to another IPv6 router, but the two are connected together via an intervening IPv4 router. If the two routers use tunneling, then:a)The sending IPv6 router creates an IPv4 datagram and puts it in the data field of an IPv6datagram.b)The sending IPv6 router creates one or more IPv6 fragments, none of which is larger than themaximum size of an IPv4 datagram.c)The sending IPv6 router creates an IPv6 datagram and puts it in the data field of an IPv4datagram.d)The sending IPv6 router creates an IPv6 datagram and intervening IPv4 router will reject theIPv6 datagramD 18.Which of the following was an important consideration in the design of IPv6a)fixed length 40-byte header and specified options to decrease processing time at IPv6 nodesb)128-bit addresses to extend the address spacec)different types of service (flows) definedd)all of the aboveD 19.A network bridge table is used to perform the following:a)Mapping MAC addresses to bridge port numbersb)Forwarding frames directly to outbound ports for MAC addresses it handlesc)Filtering (discarding) frames that are not destined for MAC addresses it handlesd)All of the abovePART Ⅱ: True / False (1 points per question – total:20 points)1. The DNS server can update the records. (T)2. The TCP connection is a direct virtual pipe between the client’s socket and the server’s connection socket. (T)3. SMTP protocol connect the sender’s mail server and receiver’s mail server (T)4. Whereas a transport-layer protocol provides logical communication between processes running on different hosts, a network-layer protocol provides logical communication between hosts. (T)5. UDP and TCP also provide integrity checking by including right-detection fields in their headers. (F)6. If the application developer chooses UDP instead of TCP, then the application is not directly talking with IP. ( F )7. When we develop a new application, we must assign the application a port number. ( T )8. Real-tine applications, like Internet phone and video conferencing, react very poorly to TCP’s congestion control. ( T )9. The sender knows that a received ACK or NAK packet was generated in response to its most recently transmitted data packet. (T)10. To simplify terminology, when in an Internet context, we refer to the 4-PDU as a unit. (F)11. DV algorithm is essentially the only routing algorithm used in practice today in the Internet。
CCIE实验考试经典题库

C C I E实验考试经典题库(总10页)--本页仅作为文档封面,使用时请直接删除即可----内页可以根据需求调整合适字体及大小--CCIE实验考试经典题库1- Day Format Version2- Policy Routing Frame relay OSPFLab#1Network Learning, Inc. R&S CCIE Practice Lab 1 1-day VersionAt the end of this lab verify connectivity to all ports. You should be able to ping every interface form any router. (don’t worry about being able to ping a local frame-relay interface. Please disregard this statement if you are asked to filter packets, routers or other specific tasks.)1. Initial Configuration – 5 pts (30 minutes)a. Use the pre-configuration files to apply proper IP addresses to the router interfaces. Add IP addresses as needed as shown on the network diagram.b. Configure router R7 as a frame-relay switch. Refer to the diagram for interface connections to other routers connected to router R7.c. Connect routers R1,R2, R3, and R5 over the frame-relay cloud. Configure router R1’s S0 interface as a sub-interface. Configure R2,R3, and R5 without using sub-interfaces. Use only one frame-relay PVC on routers R2, R3, and R5. The recommended DLCI numbers 102, 201,103,301,105, and 501 are indicated on the lab diagram.d. Routers R1, R2, R3, and R5 should share network on their frame-relay interfaces.e. Router R1 should have network with an 8-bit subnet mask on its Ethernet interface( The mask should be )f. Make sure all the Ethernet interfaces are in their own broadcast domain if you are using an Ethernet switch for your Ethernet connections.2. OSPF Configuration –25pts (2 hours 30 minutes)a. configure OSPF area 0 on the frame-relay interfaces between R1, R2, R3, and R5.b. Configure router R1’s interface Ethernet 0 for OSPF area 1c. Configure router R2’s interface E0 for OSPF area 10d. Configure router R3’s interface S 1 and all of router R4’s interface for OSPF area 3.e. Configure router R5’s interface E 0 for OSPF area 4.f. Create two loopback interface on R4 and put both of the associated subnets on these interfaces in OSPF area 44.g. Summarize the (2) loopback interface you just created on router R4 so they appear as one route to the rest of the OSPF routers in your network..h. Here is the tricky part. You can’t use the command ip ospf network xxxx anywhere in your router configurations.i. Redistribute the default route on router R2 as type-1 with a metric of 100. This route is already part of the initial configurations we provided for you.j. Also, one of the problems in this lab can be solved with multiple frame map ip statements, but that is not the solution we want you to use, Solve the problem with routing, not layer 3 to layer 2 mapping via additional frame map statements!!!(Yes, this is a tricky issue)You have completed lab 1. compare your configurations to the ones we provided. Often there is more than one complete a task so your configurations may be different than ours. If your configuration are different than ours make sure you understand how to complete the lab with our configurations too.Lab 2At the end of this lab verify connectivity to all ports. You should be able to ping every interface from and router. (Don’t worry about being able to ping a local frame-relay interface. Please disregard this statement if you are asked to filter packets. Routes or other specific tasks.)1. Initial Configuration – 5 pts (30 mins)a. Use the pre-configuration files to apply proper IP addresses to the router interfaces. Add IP addresses as needed as shown on the network diagram. You may have to add additional IP addresses to complete some tasks.b. Connect routers R1, R2, R3, and R5 over the frame-relay cloud. Configure router R1 using sub-interfaces. Configure routers R2, R3, and R5 without using sub-interface.c. Use only one frame-relay PVC on routers R2, R3, and R5, The recommended DLCI numbers 102,201,103, 301,105, and 501 for the frame-relay PVC’s are indicated on the network diagram.d. Routers R1,R3,and R5 should share network on their frame-relay interfacese. Routers R1 and R2 should share network on their frame-relay interfaces.f. Router R1 should have network with an 8-bit subnet mask on its Ethernet interface( The mask should be )g. Router R2 should have network with a 24-bit mask on its Ethernet interface.h. Router R3 should have network with an 8-bit subnet mask on its token-ring interface ( The mask should be )2. OSPF configuration –30 pts (2 Hours 30 minutes)a. configure OSPF area 0 on the frame-relay interfaces between routers R1, R3 and Router R5.b. Place router R1’s Ethernet in OSPF area 1. place router R5’s interface E0 in OSPF area 0.c. Setup a default static route (default gateway) from R3 to R4. Redistribute this default static route into OSPF with a metric-type of 1 and a metric of 500.d. Configure router R3’s serial 1 interface as /24 and router R4’s serial 0 interface as /24.e. Configure router R4’s E0 interface as /24.f. Configure a default gateway on router R4 to route all packets for which it has no routes to router R3.g. Configure two loopback interfaces on router R3 with networks that could have at most 254 hosts and put them both in the same OSPF area, but different from OSPF area 0. Summarize this route into OSPF so that the two subnets appear as one route.h. Configure router R2 for EIGRP and put all interface in the routing process.i. Configure router R1 with EIGRP and redistribute with OSPF. Set themetric type to type-1 when you redistribute from EIGRP to OSPF. Also, redistribute OSPFinto EIGRP.j. Configure router R1 so that it only listens to EIGRP updates on E0 and . k. Configure router R6 for OSPF with a different process ID than used thus far. Do not configure R6’s E0 for OSPF.l. Configure router R8 to be in the same OSPF area as router R6. put router R8’s interface E0&Lo0 into the OSPF routing process. Configure router R6 so that its S1 interface speed is correctly reflected in the OSPF metrics without using the “ip ospf cost xxx” command.m. Configure OSPF message-digest authentication between routers R6 & R8.n. Change the OSPF hello interval between routers R6 & R8 to 45 seconds.o. Configure router R8 suing the “ip ospf cost” command such that the speedof the link for interface S0 is correctly reflected in the OSPF metrics.p. Change the OSPF transmit interval delay to 10 seconds between routes R6 & R8. q. Add a default route to router R2 that points to . configure one static route on router R2 so that full connectivity to R4’s interface E0 is available. You will notice that the default gateway of router R2 has a lower administrative cost than the one learned via router R1. as a result, the other default route never makes it in the routing table for router R2.r. You will notice that R2 can’t ping the serial interfaces between routers R3 & R4. fix this problem by only making changes to router R3 without static routes.3. BGP configuration -15 pts (1 hour)a. Configure router R4 in BGP autonomous system 1.b. Create a static route to null0 router R4 and redistribute into BGP.c. Create a loopback interface on R4 and add its network to BGPd. When adding the first loopback to BGP use a class A address with a 24-bit mask. The network that was added to BGP from the first loopback address should appear inthe routing table of other routers as “ B …”e. Create another loopback on router R4 with a class A address and put this network into RIP and redistribute RIP into BGP.f. Configure router R3 in BGP autonomous system 1 and use interface loopback0 as the update source.g. Configure routers R1, R2, and R5 in BGP autonomous system 2, only use one neighbor remote-as 2 command on routers R2, R3. &R5 for autonomous system 2.h. Place routers R6 and R8 in BGP autonomous system 3.i. Configure BGP authentication between router R6 & R8.j. Configure a loopback interface on router R8 and enable RIP for this network. Redistribute this RIP network into OSPF.k. Redistribute the OSPF routing process that contains routers R6 and R8 into BGP.l. You are not allowed to add any static routes to router R8 during this exercise.m. Configure router R6 such that all BGP routes learned from router R5 have a local preference of 300.n. Filter on router R5 such that the BGP route to null0 defined on router R4 isn’t seen on routers R6 &R8.o. Hint the object of this BGP section is to provide end-to-end connectivity between all routers and interfaces. In this exercise you are not allowed to configure IGP or two-way static route connectivity between routers R5 & R6, BGP should be providing the necessary routing information. You are allowed to setup a default route on router R6 to point to router R5.Now that you have completed lab 2 check., the routing tables on all routers. Do they make sense Ping all interfaces from all routers. Can you ping everywhere Do the appropriate routers see the static route to null0 on R4 via BGP Go to every router and ping every interface. If you can’t ping everything you are not done yes.You have completed lab 2. Compare your configuration to ones we provided. Often there is more than one to complete a task so your configurations may be different than ours. If your configurations are different than ours make sure you understand how to complete the lab with our configurations tooLab 3At the end of this lab verify connectivity to all ports. You should be able to ping every interface from any router. (Don’t worry about being able to ping a local frame-relay interface. Please disregard this statement if you are asked to filter packets. Routes or other specific tasks.)1. Initial configuration -5 pts (30 mins)a. Use the pre-configuration files to apply proper IP addresses to the router interfaces. Add IP addresses as needed as shown on the network diagram. You may have to add additional IP addresses to complete some tasks.b. Configure lab 3 network using networkc. Create a loopback interface on router R2 with /24.d. Connect routers R1,R2, R3, and R5 over frame-relay cloud.e. Configure router R1 using sub-interfaces.f. Configure router R2 without using sub-interfaces or frame-relay map commands.g. Put routers R1 &R2 frame-relay interfaces on one subnet and routers R1, R3, and R5 on a different subnet.2. OSPF & Other IP Routing Configuration -35 pts ( 2 h)a. Configure OSPF with the frame-relay cloud in OSPF area 0b. Configure the R3-R4 serial connection to be in area 1.c. Set the ring-speed on router R3 to 16 Mbps.d. Configure the loopback interface on router R2 in a different OSPF area.e. Configure the LAN interfaces on routers R1, R2,and R3 to be in different OSPF areas.f. Configure two loopbacks on router R3 using subnets that will contain at most 30 host IP addresses.g. Configure two loopback interfaces on router R1 using subnets that will contain at most 14 host IP addresses.h. Summarize the two loopback interfaces on routers R1 and R3 such that router R2 only sees one route from each.i. Configure the Ethernet interface E0 on router R4 to be in OSPF area 40. j. Configure the R5, R6, and R8 Ethernet 0 interface to use EIGRP.k. Configure R8’s interface loop5 as /24 and add it to RIPl. Redistribute routes between all protocols such that router R1 can ping any interface.m. Configure 2 loopbacks interfaces on router R8 with /24 & /24. add there to RIP and redistribute RIP to EIGRP. Summarize such that all routers only see one route to the loopback interfaces. Test connectivity to loopback interface via ping.n. Filter such that router R6 can ping the loopbacks on router R1, but not the Ethernet interface on router R1. the route for the Ethernet on router R1 should still be visible and all other traffic such as telnet should still pass unfiltered.o. Filter on router R5 such that routers R1 R2, R3, and R4, don’t see the route to router R8’s interface loopback 5.p. Create three loopback interfaces on router R8 and use /24 for loopback 2,q. /24 for loopback 3, and for loopback 4. now summarize the three loopback networks into one route. When done router R1 should see only one route for these three loopback interfaces ana should be able to ping all three of them. Hint, the route may not look like what you think.3. NTP & Access-list & Other Tasks -15 pts (30 mins)a. configure NTP between routers R2 &R3. make R2 the time source. Set the correct time and date on router on router R2. Set the time-zone on routers R2 & R3, Verify that router R3 has synced with router R2 via NTP.b. Configure queuing on router R3’s S0 interface such that telnet, IP, IPX, and everything else use 25% of the bandwidth each. Configure the queuing such that none of the traffic defined at 25% above uses more than 1000 bytes per time slice. You are allowed to exceed 1000 bytes per time slice only if there is part of a remaining individual packet that needs to be emptied from the queue.c. Configure the frame-relay interface on router R2’s interface So such that IP is discard eligible on the frame.d. Create the following 6 static routes on router R6; suing the Cisco IOS command IP route null 0. use the number 1,2,3,4,5 and 6 for the variable X. redistribute the static routes such that they are seen by all the other routers. Now filter on router R5 using any method that use an access list so that only the even routes . X=2,4,and 6) are seen past router R5 towards the OSPF network. Your access-list can only have two lines in it, not seven for this exercise. All the routes must still be seen in router R5’s routing table.4. IPX Configuration – 20 pts (1h)a. Configure all interface(including loopbacks ) for IPXb. Configure IPX EIGRP on the NBMA frame-relay networkc. Configure IPX RIP/SAP everywhere else.d. Configure two static SAPs on router R3. Filter on router R5 such that routers R6 and R8 only see one of the SAPs.e. Disable IPX on the between routers R3 &R4 all routes should still be seen by all routers running IPX.f. Change the frequency of the RIP updates across the R3-R4 serial connection to once every 2 minutes.g. Configure router R1’s Ethernet with IPX and raw frame types.h. Configure routers R3 and R4 to pass IPX NETBIOS type-20 broadcasts between their LAN interfaces.5. DLSW Configuration – 10 pts (45 mins)a. Configure DLSw between router R3’s interface token-ring 0 and router R4’s interface Ethernet 0.b. Place router R2’s interface Ethernet 0 into the DLSw network. Make sure there is connectivity between all LAN interfaces.c. Configure a filter that blocks NETBIOS packets with destination name‘CCIERING1” from leaving router R3’s interface To0.d. Setup a filter that would permit only SNA traffic between routers R3 & R4.6. BGP Configuration – 15 pts (1h)a. Configure BGP on router R4 using AS number 1. configure BGP on routers R1,R2, R3 and R5 using AS number 2. You can only use one neighbor .. remote-as 2 command on routers R2 and R5.b. Configure two static routes to /24 and /24 using the command ip route null0 on router R4, Redistribute the second route into BGP using the route-map command.c. Make sure that router R5 can see the route.d. Setup router R8 with BGP in AS number 3. on router R8 use the loopback interface Lo0 as the source for its BGP connection to AS2. make sure router R8 can see the specific route, and not the aggregateYou have completed lab 3. compare your configurations to the ones we provided. Often there si more than one to complete a task so your configuration may be different than ours. If your configuration are different than ours make sure you understand how to complete the lab with our configurations too.LAB4At the end of this lab verify connectivity to all ports. You should be able to ping every interface from any router. (Don’t worry about being able to ping a local frame-relay interface. Please disregard this statement if you are asked to filter packets. Routes or other specific tasks.)1. Initial configuration -10pts (30 mins)a. Use the pre-configuration files to apply proper IP addresses to the router interfaces. Add IP addresses as needed as shown on the network diagram. You may have to add additional IP addresses to complete some tasks.b. Connect routers R1,R2,R3, and R5 over the frame-relay. Configure router R1 using sub-interfaces. Configure routers , and R5 without using sub-interfaces.c. Use only frame-relay PVC on routers R2, R3 and R5. The recommended DLCI numbers , and 501 are indicated on the network diagram.d. Routers R1, R3 and R5 should share network on their frame-relay interfaces.e. Routers R1 and R2 should share network on their frame-relay interfaces.f. Router R1 should have network with a 9-bit subnet mask on its Ethernet interface.(the mask should be ) sue subnet-zero here.g. Router R2 should have network with a 24-bit mask on its Ethernet interface.h. Router R3 should have network with an 8-bit subnet mask on its token-ring interface. (the mask should be )i. Use network between routers R5 &R6.2. OSPF & Other IP routing configuration –35 pts (1hous 30 mins)a. Configure OSPF area 0 on the frame-relay interfaces between routers R1,R3, and R5.b. Place router R1’s Ethernet in OSPF area 1. Place router R3’s interface To0 in OSPF area 2.c. Place router R3’s interface serial 0, and all of router R4 in OSPF area 3. make OSPF area 3 a totally-stubby area.d. Place R5 and R6 Ethernet interface in OSPF area 4. Make this OSPF area a NSSA (not-so-stubby-area) Make the default cost 20.e. Configure router R6’s interface serial 0 and router R8’s interfaces S0,E0,and loop 0 for EIGRP.f. Place router R2’s interface serial 0 and router R1’s in OSPF area 5.g. Redistribute all routes so that you can see all routes and ping from everywhere.h. Summarize the routers for router R8’s interface E0, Loop0, and S0 that were redistributed into OSPF by router R6 on router R5 so that all of router R8’s networks appear as one route to the rest of the OSPF routers except R6.i. When you redistribute EIGRP into OSPF make these routes appear as type-1 external routes.j. Configure router R2 such that it propagates a default route the other OSPF routers.k. Create a second loopback interface on router R2 with an address of /24. make sure you can ping the second loopback interface on router R2 from other the routers.l. Create two loopbacks on router R3 with networks that could contain at most 30 hosts. Place the loopbacks on router R3 in one area and summarize such that one route appears for both loopacks.m. Place the Ethernet interface on router R2 in area 10.n. Configure simple password authentication in OSPF area 4.o. Use the ip ospf priority command on router R5 to make it become the DR for OSPF area 4.p. Change the cost on router R5’s interface E0 using an IP OSPF command to make it appear as 100Mbps as it relates to OSPF metrics.q. Change the cost on R6’s E0 without using an IP OSPF command to make it appear as 100Mbps as it relates to OSPF metics.3. BGP Configuration –15pts (1h)a. Place router R4 in BGP AS 1 and router R3 in BGP AS 2. Create two static routes to null0 using a class A address with a 24-bit mask on R4 and inject into BGP such that router R3 can see it. Use loopbacks as the update source on both routers R3 and R4. Create loopback interface as necessary.b. Filter one of the static routes with a route-map statement on router R4.c. Configure BGP on router R4 such that the sub-netted class A route is seen. For example, the BGP route on router R3 could be not .d. Configure a second loopback interface on router R4 at /24 and enable RIP on this router for this network. Inject this route and the previous one with a metric of 5.e. Configure router R2, R1, and R5 in BGP AS3. use only one neighbor remote-as x statement on routers R2 and R5.f. Create a static route on router R2 (ip route null0) inject this route into BGP. Make sure the other routers running BGP can see this route.g. Also make sure all routers can ping .you have completed lab 4 compare your configurations to the ones we provided. Often thereis more than one to complete a task so your configuration may be different than ours. If your configuration are different than ours make sure you understand how to complete the lab with our configurations tooLab5At the end of this lab verify connectivity to all ports. You should be able to ping every interface from any router. (Don’t worry about being able to ping a local frame-relay interface. Please disregard this statement if you are asked to filter packets. Routes or other specific tasks.)1. Initial configuration & OSPF -35pts (2 h)a. Use the pre-configuration files to apply proper IP addresses to the router interfaces. Add IP addresses as needed as shown on the network diagram. You may have to add additional IP addresses to complete some tasks.b. Configure router R2’s Ethernet interfaces with IP address /24 and routerR2’s default route to .c. Use a 24-bit mask unless told to use otherwise.d. Create a loopback interface on router R2 with /24.e. Connect router R3, R4, R5, and R6 over frame-relay. Configure router R5 using sub-interfaces.f. Connect routers R3, R4, R5 and R6 over frame-relay. Configure router R5 and router R4 on a different subnet.g. Configure OSPF on router R3’s interface S1, router R6’s interface S1, and router R5’s sub-interface for OSPF area 10, place R5’s and R2’s Ethernet interface in OSPF area 0.h. Configure the connection between router R5’s interface and router R4 for IGRP.i. Configure router R6’s Ethernet E0 as OSPF area 6. configure router R3’s token-ring interface To0 as OSPF area 3. configure two loopback interfaces on router R3 with networks that contain at most 30 hosts and put both loopbacks in the same area as the token-ring interface. Summarize the loopback subnets and router R3’s interface To0 to appear as one route to OSPF.j. Make the default route on R2 appear in he routing table of all the other routers.k. Configure routers R1, R2’s S1, and router R8’s Ethernet interface E0 for EIGRP. Configure router R8’s interface To0 for RIP.l. Redistribute all routers between all routing protocols such that all routes are visible in all routers and every router can ping each other’s IP interfaces (even the loopback on R2) as shown on the lab diagram lab 5a.m. Make sure that all OSPF external routes appear as type-1, verify your routes. Are the routes appearing in the correctly routing protocol?n. Configure router R5 such that the only route on R6 for the 137. network appears exactly as follows; O [110/65] via , 00:51:03, serial 1. Hint pay attention to the underlined value 65.o. Configure routers R3 & R4 to resolve dns names using DNS servers &.2. OSPF Demand Circuit –15 pts (1 hour)a. Use network /24 for the ISDN interfaces on routers R5 &R6 and ass them to OSPF. Configure routers R5 & R6 to use the ISDN interfaces for restoral[ 恢复]. The ISDN link should only come up when you administratively shutdown the serial 4 interface onrouter R7, and there is interesting traffic trying to get between routers R5 & R6 . use ping as the interesting traffic to test. Make sure you test from router R6 and from router R5. See the router ports/configuration into online for the phone #’s, spids, and switch type if you are using our remote racks. Configure the ISDN link so that it will shutdown 45 seconds after an inbound or outbound ping packet. Both routers should shave full OSPF routes when the frame link is functional or not.You are required to use OSPF demand-circuit as your solution here, after the initial ISDN call to synchronize OSPF, your ISDN interfaces should stay down unless you break the frame connection between R5 and R6 and there is interesting traffic.Now go to router R7 and shut down interface S4, your ISDN connection should kick in and provide a backup path for router R6 to reach the rest of the network, but only when thereis data to send. OSPF router updates should not keep the ISDN up. Pretend [假装]your ISDN line is charged at $5 per minute and it comes out of your check.At this point when router R7’s interfaces S4 (your frame connection) is still down. Router R5 should have the following displays for:”show ip route”, “show ip ospf int bri0”, and “show dialer”Notice that the ISDN connection is down and router R5 has a routing table with OSPF entries using interface BRI0 to get to router R6’s Ethernet network, and is suppressing OSPFhellos for 1 neighbor. Also pay attention to the OSPF dead time on R5’s BRI0 interface. Output from router R5R5# show ip routeCodes: C- connected, S-static I- IGRP, R-RIP, M-mobile, B-BGP, D-EIGRP, EX-EIGRP external, O-OSPF, IA-OSPF inter area, N1-OSPF NSSA external type 1, N2- OSPF NSSA external type2, E1- OSPF external type 1, E2- OSPF external type 2 E- EGP i- IS-IS, L1- IS-IS lever-1, L2-IS-IS level-2, *- candidate default, U- per-user static route, o- ODRGateway of last resort is to network/24 is subnetted, 1 subnetsC is directly connected, Ethernet 0/16 is variably subnetted, 7 subnets, 2 masksO IA /24 [110/65] via , 00:09:03, serialI /24 [100/8576] via , 00:01:11, serialO IA /24 [110/1572] via . 00:09:03, BRI0C /24 is directly connected, BRI0C /24 is directly connected, serialO /24 [110/64] via , 00:09:13, serialC /24 is directly connected, serialO E1 . 24 [110/21] via . 00:09:03, Ethernet 0O E1 . 24 [110/21] via . 00:09:03, Ethernet 0O E1 . 24 [110/21] via . 00:09:03, Ethernet 0O*E1 /0 [110/21] via . 00:09:03, Ethernet 0R5#show ip ospf int bri0BRI0 is up, line protocol is up (spoofing)Internet address /24, Area 10Process ID 1, router ID , Network type POINT_TO_POINT, Cost 1562Run as demand circuitDoNotAge LSA allowed.Transmit Delay is 1 sec, State POINT_TO_POINT,Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5Hello due in 00:00:06Neighbor Count is 1, Adjacent neighbor count is 1Adjacent with neighbor (Hello suppressed)Suppress hello for 1 neighbor(s)R5#show dialerBRI0 – dialer type =ISDNDial string Successes Failures Last called Last status 4930622 1 0 00:08:45 succ essful0 incoming call(s) have been screened0 incoming call(s) rejected for callbackBRI0:1 – dialer type =ISDNIdle time(45 secs), Fast idle timer (20 secs)Wait for carrier (30 secs), Re-enable (15 secs)Dialer state is idleBRI0:2 – dialer type =ISDNIdle time(45 secs), Fast idle timer (20 secs)Wait for carrier (30 secs), Re-enable (15 secs)Dialer state is idleR5#Now go back to router R7 and bring up router R7’s interface S4 again.3. IPX configuration –15 pts (1 hour)a. Configure all the active interfaces, including loopbacks, on routers R1, R2, R3, R5, R6, and R8 for IPX.b. Configure router R8 and the LAN interfaces on routers R3, R4, R5 and R6 for IPX RIP.c. Configure router R1 & R2 for IPX NLSP.d. Configure the serial interfaces on the rest of the routers for IPXEIGRP( not routers R1& R2 these oly use NLSP), Also make the Ethernet interface on router R2 IPX EIGRP only.e. Configure the BRI0 interfaces on routers R5 & R6 as IPX RIP.f. After this point you should be able to see all the IPX networks in all the Routers routing table. Test connectivity with IPX ping.g. Create two static SAPS on router R6.h. Filter IPX SAPs such that routers R2, R1, and R8 only see one of the SAPs.i. Filter on router R2 such that the IPX network on router R8’s interface E0 is no seen by any of the frame-relay connected routers and router R5.。
CWP2011 Conference Guide
Notice for Conference AttendeeGeneral InformationDate VenueOct19-21, 2011 New China International Exhibition Center (New CIEC)Address: No. 88 Yuxiang Road, Tianzhu, Shunyi District, BeijingConference RegistrationConference onsite Registration will be open from October 18-20, on south registration hall, CIEC (new venue).For Pre-Registered AttendeePlease go to the ‘Confirmed Attendee’ counter’ , conference registration desk, south registration hall to collect conference admission badge and all the conference materials by business card and your conference ID number (send to your e-mail box after your registration fee is paid).For Onsite Register AttendeePlease go to the ‘Onsite Registration’ counter, conference registration desk, south registration hall, make payment onsite and then pick up conference admission badge and all the conference materials.*Credit Card / Local Check / Cash is acceptable when on-site paymentWhat’s inside the Conference Bag?Conference Guide, Exhibition Catalogue, Paper Disk and invitation card for conference welcome banquet etc.About Lunch CouponConference attendee will get a lunch coupon card together with the conference admission badge. The coupon is a contactless smart card with the right allowance for conference lunch. Please be noted to well keep the card and show it to the staff when having lunch.Welcome BanquetAll Conference Attendee is invited to CWP2011 Conference Welcome Banquet, which will be held on 18:00‐20:00, CROWN PLAZA, October 19. The invitation card is in your conference bag. Detailed information could be found on the card and please bring it with you when go to the banquet.Simultaneous interpretation ServiceSimultaneous interpretation Service is available for all the conference session (Side events not included). You can pick up earphone on meeting room entrance and do not forget to turn it back.Traffic to Conference VenueMetroMetro Route No.15 and take off at the shop New CIECDriving DirectionTake Jingcheng Expressway ‐ Exit from Houshayu toll booth ‐ Drive onto Huosha Rd. ‐ Reach Luoma Roundabout ‐ go south for Yu Xiang Rd ‐ New CIEC is on your left side.Shuttle bus TimetableRoute: between Exit F, Metro Station “Shaoyaoju” and South Square, CIEC (new venue)PPT CollectionAttendees will receive an e‐mail within 20 working days from the event organizer after CWP2010 , which will include links to download of conference PPT of all speeches (excluding the speeches the speakers refuse to public).Help‐Yourself CounterA Help‐Yourself counter is installed in each CWP2010 conference room. You may help yourself with drinking water, stationary and the others you may need.WiFi and InternetWiFi network will cover Meeting room W201 and most of the meeting rooms on first floor. Also, you can go to Internet access area both in east and west show halls.。
Texas HHAeXchange Onboarding和培训资源说明书

An Important Message fromThe Texas Health and Human Services Commission (HHSC)HHAeXchange Onboarding and TrainingResources AvailableBackground:As a reminder, EVV program providers and financial management services agencies (FMSAs) transitioning to HHAeXchange must complete onboarding and system user training.1.HHAeXchange will issue user credentials for their Learning ManagementSystem (LMS) portal within three business days of submission ofthe HHAeXchange Provider Onboarding Form.2.HHAeXchange will issue system user credentials for the HHAeXchange Portalafter the program provider or FMSA has completed the EVV system training on the HHAeXchange LMS training portal. Please allow five business days to receive your login credentials.Key Details:HHAeXchange Training ResourcesOpen Hours Webinar SessionsProgram providers, financial management services agencies (FMSAs), CDS employers and CDS employees can attend HHAeXchange Open Hours webinar sessions to ask questions or see methods demonstrated. The webinar sessions will be available Monday through Friday until Nov. 3.The webinar sessions do not require registration, so attendees can drop in and out between the selected hours.Program providers and FMSAs join here.The webinar sessions will cover the following topics:•Monday, Wednesday, Friday: 9–11 a.m.•And a last session on Friday, Nov. 3 from 1–3 p.m.o Administrativeo Service Provider Managemento Member Managemento Schedulingo EVV Clock In and Clock Out/EVV Visit Managemento Manual Visit Managemento Call Dashboard•Tuesday, Thursday: 9–11 a.m.o BillingFMSAs, CDS employers and CDS employees join here.The webinars will cover the following topics:•Friday: 9–11 a.m.o Services Portalo EVV Clock In and Clock Out/EVV Visit ManagementFor more information, visit HHAeXchange Texas Open Hours.One-On-One SessionsEVV users may schedule a one-on-one session with an HHAeXchange expert for additional help and training. Click here to book a one-on-one session.Resources:For more information or questions about HHAeXchange training, email HHAeXchange.For general EVV questions or questions about EVV Policy, email HHSC EVV Operations.。
金边_精品文档
七年级下册英语试卷Part 1: ListeningSection A: Short ConversationsDirections: In this section, you will listen to 5 short conversations. At the end of each conversation, a question will be asked about what was said. Both the conversation and the question will be spoken only once. After each question, there will be a pause. During the pause, you must read the four choices marked A, B, C, and D, and decide which is the best answer. Then mark the corresponding letter on the Answer Sheet with a single line through the center.1. M: Have you finished your history project yet?W: Almost. I just need to add some pictures and then it will be done.Q: What does the woman need to add to her history project?2. M: How was the movie you saw last night?W: It was excellent! I highly recommend it.Q: What does the woman think of the movie she saw?3. M: Excuse me, when does the next bus to the city center leave?W: I’m not sure, but I think the timetable is posted over there.Q: Where can the man find the information he needs?4. M: I heard our school’s basketball team won the championship!W: Yes, they played really well. I’m proud of them.Q: What does the woman think of the school’s basketball team?5. M: Would you like to come to my birthday party this Saturday?W: I’d love to, but I have to attend my piano lesson that day.Q: Why can’t the woman go to the man’s birthday party?Section B: PassagesDirections: In this section, you will hear 2 short passages. At the end of each passage, you will hear some questions. Both the passage and the questions will be spoken only once. After you hear a question, you must choose the best answer from the four choices marked A, B, C, and D. Then mark the corresponding letter on the Answer Sheet with a single line through the center.Passage 1In many countries, students often take the school bus to get to school. However, the situation is different in Japan. Most students in Japan walk or ride bicycles to school. Some take public transportation when they live far away from school. In Japan, students are responsible for cleaning their own classrooms and school buildings. After school, they take turns sweeping the floors and cleaning the chalkboard. This not only instills a sense of responsibility, but also teaches them valuable life skills.Q1: How do most students in Japan travel to school?Q2: What do Japanese students do after school?Q3: What do Japanese students learn from cleaning their school?Passage 2Dear students,We are organizing a school trip to the Science Museum next month. The trip will take place on April 15th and we will be leaving on buses at 8:30 a.m. from the school gate. Please remember to bring your student ID card and a packed lunch. We will spend the whole day at the museum, where you can explore various exhibits and participate in educational activities. We will return to the school at 4:30 p.m. Don'tforget to bring comfortable shoes and dress appropriately for the weather. We hope you all can join us for this exciting trip!Thank you,The TeachersQ4: When will the school trip to the Science Museum take place?Q5: What time will the buses leave from the school gate?Q6: What should the students bring for the trip?Part 2: ReadingSection A: Multiple ChoiceDirections: In this section, you will read 10 short passages. Each passage is followed by several questions about it. Read the passages and the questions carefully. Choose the best answer to each question based on the information given in the passage. Then mark the corresponding letter on the Answer Sheet with a single line through the center.Passage 1Snowboarding is a popular winter sport. It was developed in the United States in the 1960s and became an Olympic sport in 1998. Unlike skiing, snowboarding involves using a singleboard to slide down snowy slopes. People wear special boots and straps to keep their feet attached to the board. Snowboarding has its own set of tricks and techniques, such as carving, jumping, and grinding. It requires both balance and coordination.Q1: When did snowboarding become an Olympic sport?Q2: How is snowboarding different from skiing?Q3: What skills are required for snowboarding?Passage 2The internet is a global network that connects millions of computers worldwide. It allows people to share information, communicate with others, and access various services. With the internet, people can check emails, read news, watch videos, and listen to music from different parts of the world. They can also shop online, play games, and even take online courses. The internet has made our lives more convenient and efficient.Q4: What is the internet?Q5: What can people do with the internet?Q6: How has the internet impacted our lives?Section B: Cloze TestDirections: In this section, there are 10 blanks in the following passage. For each blank, there are four choices marked A, B, C, and D. Choose the best answer to fit in the blank and mark the corresponding letter on the Answer Sheet with a single line through the center.Many people enjoy traveling and exploring new places. However, when it comes to packing, they often find it 7 . Here are some tips to make packing easier. First, make a 8 list of the things you will need. Then, lay out all the items you plan to bring on the bed or 9 . Check the weather forecast for your destination and choose clothes accordingly. Remember to pack 10 outfits and versatile pieces that can be mixed and matched. Don't forget to pack extra underwear and socks, as well as toiletries and any necessary medications. Roll clothes instead of folding them to save space in your suitcase. Finally, make sure to label your luggage with your contact information in case it gets 11 . By following these packing tips, your travel experience will be more enjoyable and stress-free.Q7: A. simple B. hard C. exciting D. boringQ8: A. comprehensive B. basic C. quick D. detailedQ9: A. sofa B. floor C. chair D. tableQ10: A. fancy B. casual C. bright D. tightQ11: A. lost B. forgotten C. damaged D. stolenPart 3: WritingDirections: In this section, you will write a composition. You must write at least 80 words for each blank. Use the information given in the table to write your composition. Your composition should be based on the following points:Title: My Favorite Season- Introduction: briefly introduce the topic and state your favorite season- Body: describe the weather, activities, and reasons why you like your favorite season- Conclusion: summarize your favorite season and express your preferenceTitle: My Favorite SeasonIntroduction:Seasons come and go, bringing different kinds of weather and activities. Among the four seasons, my favorite season is summer.Body:The weather in summer is hot and sunny. The days are long and the nights are relatively short. It is the perfect time to go swimming and enjoy water sports. Many people go to the beach or have barbecues in the park. I also love the abundance of fruits and vegetables in summer. The vibrant colors and refreshing flavors make the season even more enjoyable.Conclusion:In conclusion, summer is my favorite season because of the warm weather, fun activities, and delicious food. I look forward to summer every year and cannot imagine a year without it.(Note: The composition should include the information above, but you are welcome to add more details or examples to support your points.)。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
European electrical transmission system export capability for increasing wind power penetrationShiva Beharrysingh, Frans Van HulleEuropean Wind Energy AssociationInternational Workshop on large scale integration, Bremen 14-15 October 2009WHAT IS THE EUROPEAN WIND ENERGY ASSOCIATION?EWEA is the voice of the wind industry, actively promoting the utilisation of wind power in Europe and worldwide. Resources are focussed on lobbying, communication and policy activities, and responding to enquiries from our member organisations.More than 600 members from almost 60 countries• • • • • • • • • Manufacturers covering 90% of the world wind power market Component suppliers Research institutes National wind and renewables associations Developers Electricity providers Finance and insurance companies Consultants ContractorsBeharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 20092 of 16Contents • Brief on TradeWind and its model • More detailed UCTE network model: advantages, generation type allocation, wind injection dispersion • Analysis and discussion of results for regional markets: significant interconnectors, constrained wind energy • Discussion and conclusionsBeharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 20093 of 16TradeWind and its modelwww• TradeWind (2006-2009): recommendations for stronger interconnection and markets to support large scale integration, a.o. identified 42 interconnector upgrades • Wind power capacities scenarios until 2030 (L-M-H) • Regional wind power production from time series (Reanalysis) of year 2004 – combined with specific Equivalent (regional) Power Curves • Network model: 3 system models (UCTE, Nordel, GB+IRL) merged at HVDC interconnections. Based on simplified UCTE by University of Edinburgh • Optimal power flow: PSST tool SINTEF calculating sensitivities (€/MW) of total generation costs on power line capacities (thermal and NTC).tra dewin d.euBeharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 20094 of 16Main findings of TradeWind• Significant effects of wind power on crossborder flows and congestions after 2015, • Reinforcing the 42 identified interconnectors will bring high economic value (reduction of operational cost of generation) • Wind power capacity value significantly increased by better interconnection (14% in 2020) • A dedicated meshed offshore grid has significant economic value • Economic benefits of faster and larger market are significant: intraday rescheduling of reserves (250 M€/year) and of power exchange (1-2 Billion €/year)Beharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 2009 5 of 16Modeling UCTE networkUCTE 2008 Winter&Summer Research ModelCom put ati on 6h al tim ver sus e: 2hApprox. UCTE bus total generator buses load buses total branches lines transformers hvdc lines constrained branches of that, between countries of that, internal to countries 1381 568 984 2211 2211 0 12 224 159 65Detailed UCTE 4339 943 2317 7292 6201 1091 12 5677 181 5496 6 of 16Beharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 2009Detailed UCTE network model: advantages• Full list of nodes, allowing precise location of nuclear, and hydro – more flexible generation allocation algorithm and availability of wind injection points • Actual network topology and voltage: more accurate power flows and selection of more realistic wind injection points • Load centres identified with demand on 16-01-2008 • More informed assignment of generation types based on power outputs (at 16-01-2008 snapshot) • Last but not least: thermal ratings of internal transmission circuitsAll of this supported the implementation of generation type allocation algorithms which was necessary because of the lack of specific detailed publicly available information from system operators. Beharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 2009 7 of 16Analysis of regional energy markets in 2020: approach• Significance of wind production in the regional market • Quantification of constrained wind • Identification of significant interconnectors:– Significant to the market: based on power flow duration and congestion sensitivity sum – Significant for wind power trade: based on comparison of congestion hours LOW and HIGH wind scenario 2020Congestion sensitivity of power line: change in generation cost as consequence of increasing its capacity with one unit (€/MW)Beharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 2009 8 of 16Results for Central West Market (FR-DE-Benelux) for 2020 • Prominent WE producers: DE / FR / NL • Constrained / discarded wind100 90 25% 20% 15% 10% 5% 0% 80 70 60 50 40 30 20 10 0BEDEFRLUNLActual wind energy production, TWh Percentage constrainedConstrained wind energy, TWhBeharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 2009Percentage constrained, %Wind energy, TWh9 of 16Central West region: significant interconnectors • Significant for market: DE-NL, DE-FR, NL-BEBeharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 200910 of 16Central West region: significant interconnectors • Significant for wind power trade: DE-NL, NL-BE (NTC) and BE-FRCongestion hours (power line) between high and low wind capacity scenarios (Central-West market)NTC congestion sensitivities (2020 high and low scenarios - Central-West market)S e n s it iv it y ( E u ro /M W * y e a r) 6.E+05 5.E+05 4.E+05 3.E+05 2.E+05 1.E+05 0.E+00 DE-NL DE-LU DE-FR DE-CH DE-AT NL-BE BE-LU BE-FR FR-CH 2020-lo 2020-hiFR-CH BE-FR BE-LU NL-BE DE-AT DE-CH DE-FR DE-LU DE-NL-10000 -8000 -6000 -4000 -2000 0 2000 4000 6000 8000 10000Congestion hoursBeharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 200911 of 16Summary of findings for each regional marketRegional Market Central West Northern UK/IR Central South West Central East North SeaSignificant exporters Significant importers or transit paths BE, NL Major wind energy producers DE, FR DE, SE, DK, PL, NO. FR, GB Significant wind penetrations DE, NL Highest wind energy constrained DE, NLFR, DESE, DE, NOSF, PLDE, DK, SEDEFRGBIR, GB, FRFR, SI, AT ES mixed DE, BEIT FR CZ, SK, AT NLDE, FR ES, FR, PT DE, AT, PL DE, GBDE, GR, AT ES, PT DE, AT, PL DK, DE, GB, NLDE, IT PT DE, SK DE, NLBeharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 200912 of 16Summary significant interconnectorsRegional Market Central West Northern UK/IR Central South West Central East North Sea Significant interconnectors DE-FR, FR-CH, DE-NL, DE-CH, NL-BE DE-NO, DE-PL, SE-PL. NL-GB, FR-GB, GB-IR FR-CH, FR-IT, IT-SI, AT-SI, DE-CH, DE-FR, IT-GR FR-ES AT-SI, AT-HU, SK-PL, AT-CZ, DE-PL NL-GB, DE-NL, NL-NO and DE-NO Significant interconnectors to the wind energy trade DE-NL, NL-BE, BE-FR DE-DK, SE-PL NL-GB FR-CH, IT-SI, FR-IT DE-AT DE-DK, NL-GB, NL-BE, DE-NL13 of 16Beharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 2009Identified regions with constrained (discarded) wind energyCountry RO DE ES SK PT ES DE IT DE FR ES ES DE NL Region Muntenia North Sea (far) Aragón - North West Center Comunidad Valenciana - South North Sea (close) Sud West (North) Area 2 Aragón - Centre Castilla-La Mancha West (South) Coastal (close) 14 of 16Position coordinates of regions are given in the paperBeharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 2009Conclusions • TradeWind is a very valuable point of departure for analysing transmission and market adequacy for large wind penetration • Additional analysis for 2020 with more detailed network model, including local congestions and transmission limits:– identification of interconnectors critical both to regional market and to wind energy trade – Pinpointing regions needing transmission upgrades to avoid discarded wind energy• Recommendation to look more in detail at constrained regions in follow-up studies, as well as to eastern EU countriesBeharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 2009 15 of 16The case for follow-up studies … directions for onshore Global cumulative wind power capacity grid?1990-2007 (MW)Source: EWEA 2009EWEA 2009Beharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 200916 of 16Thank you very much for your attentionRENEWABLE ENERGY HOUSE 63-65 RUE D’ARLON Beharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 2009 B-1040 BRUSSELST: +32 2 546 1940 F: +32 2 546 1944 E: ewea@ 17 of 1620 – 23 April 2010, Warsaw, Poland Abstracts submission open till 12 October Beharrysingh & Van Hulle Wind Integration Workshop 14-15 Oct 200918 of 16。
