数据库ch12_application achitecture and access interface
空间数据建库标准体系

ISO/TC211地理信息标准(二)
15)元数据(Metadata)
16)空间信息定位服务 (Positioning Service)
17)地理信息描述 (Portrayal)
18)编码(Encoding)
19)服务(Service)
20)功能标准(Functional standards)
ISO/TC211地理信息标准(一)
1)参考模型(Reference Model)
9)应用模式规则(Rules for Application Schema)
2)综述(Overview)
10)要素分类方法(Feature
3)概念化模式语言
cataloguing methodology)
目前,ISO/TC 211的积极成员(P成员)有31个,观察员(O成员)有 30个,并和许多有关国际组织密切合作。我国从1994年该组织成立起 即参与工作,1995年起成为积极成员。国内的技术归口主管部门为国 家测绘局,国家基础地理信息中心承担ISO/TC 211国内技术归口办公 室工作,主要任务是负责组织国内专家参与ISO/TC 211国际标准制定, 组团参加ISO/TC 211的全体会议和工作组会议,代表中国对该组织制 定的标准、技术规范等提出修改意见并投票等。
3)信息团体模型
信息团体模型的目的是建立一种途径,使 得信息团体或用户维护对数据进行分类和 共享所遵循的定义;实现一种有效的、更 为精确的方式,使不同信息团体之间可以 共享数据。
OpenGIS 标准
综述、要素几何、空间参考系、定位几何 结构、存储功能和插值、要素、覆盖类型 及其子类型、地球影像、要素关系、质量、 要素集、元数据、OpenGIS服务体系结构、 目录服务、语义和信息团体、图像使用服 务、图像坐标转换服务、用于COM/OLE的简 单要素规范、用于CORBA 的简单要素规范、 用于SQL的简单要素规范、地理信息标记语 言、网络地图模型等
ch12数据库系统概念(第6版)第十二章查询处理

指定详细的计算策略的带注释的表达式被称作 执 行计划。
例如, 用 salary 上的索引来寻找薪水 < 75000 的教师。 或者可以执行完整的关系扫描,并且丢弃薪水 75000 的教在所有等价的执行计划中选择代价最低 的一个。
使用数据库目录中的统计信息来估计代价 例如每个关系中的元组数目, 元组的大小, 等等 。
文件扫描 A1 算法(线性搜索)。 扫描每个文件块并且测试所 有的记录是否满足选择条件.
成本估计 = br 个块访问 + 1 次搜索 br 表示包含关系r中的记录的块的数量 如果是码属性上的选择, 找到记录的时候可以终止 成本 = (br /2) 次块访问 + 1 次搜索 可以使用线性搜索,而不管
选择运算
注: 二分法搜索通常没有意义,因为数据不是连续 存储的
除非存在索引, 且二分法搜索比起索引搜索需要进行更多次搜索
选择条件, 或者 文件中记录的顺序, 或者 索引是否可用
利用索引的选择
索引扫描 – 使用索引的搜索算法
选择条件必须在索引的搜索码上.
A2 (主索引, 主码属性等值比较)。 检索到满足对 应等值条件的一条记录 A3 (主索引, 非码属性等值比较) 检索到多条记录 。
可能非常昂贵!各记录可能位于不同的块上 对每条检索到的记录都有一次块存取
涉及比较的选择
可以实现形如 AV (r) 或者 A V(r) 的选择,通过
A5 (主索引, 比较)。(关系在A上排序)
线性文件扫描, 或者通过以下方式来使用索引:
A6 (辅助索引, 比较)。
对 A V(r) 用索引找到第一个 v 的元组,并且从这里开始 顺序扫描关系 对 AV (r) 只要顺序扫描关系,直到 > v的第一个元组; 不使 用索引 对 A V(r) 用索引找到第一个 v 的条目,并且从这里开始 顺序扫描索引,以寻找指向记录的指针. 对r AV (r) 只要扫描索引的叶页面,寻找指向记录的指针, 直到第一个> v 的条目 无论哪种情况, 检索那些被指向的记录, 都 每个记录需要一次 I/O 线性文件扫描代价可能更低(优)
Application Architecture

8 Application Architecture8.1 IntroductionThis chapter describes an abstract architecture for OPC UA applications with different layers having defined responsibilities regarding OPC UA functionality. Afterward the deliverables of the OPC Foundation and their features are listed and it is pointed out how these are reflected in the abstract architecture.8.2 Architectural OverviewWhen you intend to develop an application based on OPC UA you first have to think about what it should do by specifying the requirements and the functionality. Having that in mind you normally start designing the architecture of your applica-tion. Thereby certain design goals (e.g., portability, performance, or security) have to be agreed upon before first architectural concepts are developed. In this chapter, we will take a look at OPC UA from the design perspective and introduce a poten-tial application scenario. We expect that this scenario will be applied by many application vendors. The main design goal thereby is the reuse of components and artifacts.In this scenario, we assume that we have to develop an OPC UA client and a server. Both client and server will have application logic covering functionality tailored to concrete use cases. For example, the server has to access special data sources (e.g., data bases, devices, or other applications) or the client has to be integ-application logic covering common functionality like managing connections, cre-ating and processing OPC UA messages as well as securing them. Since we defined reuse as our main design goal it would make sense to separate use-case-specific and common functionality when designing the architecture. The common part can tions and processing Service messages and lower level functions like encoding, securing, and transmitting messages. The part providing the higher level functions can be considered as a Software Development Kit (SDK) and the part with the lower level functions can be represented by a protocol stack. The client and server applications are layered on top of the SDK. Based on these blocks we come to a very high level architecture shown in Fig. 8.1.The above-described software layers are named as Application, SDK, and Stack and are described in more details in the following sections.255DOI: 10.1007/978-3-540-68899-0_8,be further divided into two parts: the higher level functions like managing connec-W. Mahnke et al., OPC Unified Architecture ,rated into another application (e.g., in a MES application). But they will also have © Springer-Verlag Berlin Heidelberg 2009Fig. 8.1 Architectural overview8.3 StackAs mentioned in Sect. 8.2, the Stack is a common part covering lower level func-tionality. In this section, we want to structure the Stack further into different partsleading to a more detailed architectural view like the one shown in Fig. 8.2.Fig. 8.2 Stack overview8.3.1InterfacesFirst of all, the layers above need somehow to access the Stack in order to send and receive messages. Both client and server can use the same stack since it pro-vides a lot of functionality that can be used for both sides such as encoding and securing messages. However, there are also functions specific to each side. For8 Application Architecture256example the client is only sending requests and processing responses, whereas the server processes requests and sends responses. Therefore an access layer (i.e., interface) is needed for both the client- and the server-side (Client and Server API in the figure). They could, for example, offer methods for configuring the Stack, for managing the connection establishment, for sending OPC UA Service mes-sages, and for notifying the layers above when messages are received.The encoding and the decoding of messages are processed in the Encoding Layer. Once data structures representing Service messages are provided from the API layer they are serialized according to the special rules defined by OPC UA and passed to the layer beneath for further processing. Service messages received from the Security Layer are deserialized and passed as arguments of callback functions registered by the upper layer.8.3.3Security LayerEncoded Service messages passed by the Encoding Layer to the Security Layer are then secured. Secured in this context means that depending on the configura-encrypted or only signed. In scenarios in which applications are running in iso-lated environments there must also be the possibility to disable message security by configuration. In addition, special security headers and footers are appended providing information for the receiver on how to decrypt the message and how to verify the signature of the message. The Security Layer of the receiver has to check the security headers and footers of incoming messages to know how they were secured. Depending on that messages are first decrypted and afterward the signature of the message is verified or only the signature is verified or none of these activities are done (in the case the message was not secured).8.3.4Transport LayerThe Transport Layer is responsible for transmitting and receiving messages as well as for dealing with errors at Network Layer. Before transmitting messages special transport headers are appended containing special information for example about the type and the length of the message. The Transport Layer of the receiver verifies whether it is well-formed meaning whether the type can be identified or whether the message is not too long 1 before forwarding it to the Security Layer.1In UA TCP, the maximum message lengths are negotiated and verified at Transport Level. 2578.3 Stack 8.3.2Encoding Layertion of the Secure Channel (Sect. 7.5.2.1) outgoing messages are signed and8.3.5Platform Layer The reuse factor of the Stack can be increased by adding an additional layer to this model – the Platform Layer. The basic idea thereby is that all other layers of the Stack are developed in platform-neutral manner. Only the Platform Layer contains for managing sockets, threads, or cryptographic operations (e.g., encrypting and signing messages). This means that only the Platform Layer has to be changed in order to port the Stack to another platform, the other parts of the code can be reused.8.4 Software Development ToolkitOn top of the Stack, the SDK Layer is located covering the higher level function-ality. This layer can be in general composed of three parts which are illustrated in Fig. 8.3.Fig. 8.3 SDK overview8.4.1UA-Specific FunctionalityThe UA-specific part represents the implementation of the concepts and the Services specified in OPC UA. Note, that all the different aspects (like Sessions, Events, or Nodes) depicted in Fig. 8.3 have to be addressed by both the client and the server.8 Application Architecture258However, the semantic of these aspects for client and server is different (e.g., Client creates a Session request and server processes the client’s Session request).One important aspect is the management of OPC UA Sessions. As we learned the connection establishment of OPC UA includes creating a Secure Channel, establishing a Session, and activating the Session. The SecureChannel Services should be implemented in the Stack Layer to reduce the complexity in the SDK. Therefore, the Secure Channels should also be managed in that layer. The Session Services (i.e., CreateSession, ActivateSession, and CloseSession) are implemented in the present model in the SDK Layer. However, managing OPC UA Sessions does not only mean processing the Service requests and responses. There has also to be special logic behind like associating Sessions with the Secure Channel that secures the exchanged messages for that context. In addition, Sessions are run on behalf of users that have to be authenticated and authorized. Furthermore there are special Session parameters that have to be taken care of like the lifetime of the session or used locales. Such tasks are handled by a management class which can be called as a Session Manager.Another important aspect is working with Nodes. Nodes are very essential to OPC UA and are used for organizing Address Spaces as well as for providing attribute values. Address Spaces in OPC UA reside on the server-side allowing clients to access and manipulate them via the NodeManagement and Attribute Service Sets. This means that on the server-side there has to be entities managing the Nodes (e.g., Node Manager) of the Address Space (i.e., Nodes and References) and the manipulation of the values contained in the Nodes (e.g., I/O Manager). Other concepts and Services like Subscriptions, Events, and History can be approached in a similar way.OPC UA defines certain diagnostics information for Services and exposes it in the Address Space. It contains for example information about how often Services have been called. Managing this information is also a task for the SDK Layer since is also manages the Services of which the upper layer may not be aware of.8.4.2Common FunctionalityThe second part of the SDK Layer covers more general functionality that has to be implemented by clients and servers.OPC UA exchanges certificates in order to establish secure connections. Before using them it has to be verified whether a received certificate can be trusted or not. OPC UA specifies what part of a certificate has to be validated to be trusted, how-ever, it does not state how it has to be validated. Therefore common functionality has to be provided allowing the applications to validate certificates and accessing their associated certificate stores. An alternative to implementing that function-ality in the SDK is using the Stack for that purpose. Since the Stack is a common component that should be used for large range of applications it is assumed that all applications use the same way of validating certificates. In heterogeneous 2598.4 Software Development Toolkitenvironments, it sometimes can make more sense to implement that in SDK or even in the Application Layer when different sources for gathering certificates or certificate-related information (e.g., certificate revocation lists, private keys, or validation rules) have to be consumed.Other important topics that belong to the common part are application configu-ration and logging.8.4.3InterfacesThe last part of the SDK discussed in this context represents the interfaces to the Application Layer. Client interfaces are needed for sending requests to the server and for receiving responses from it (i.e., callback interfaces). On the server side some interfaces for initializing and configuring the SDK should be provided as well as for integrating underlying systems acting as data providers.8.5 ApplicationThe Application Layer includes in principle two kinds of applications: clients and servers. The way how the architectures of these applications look like differs very much depending on the concrete scenario.8.5.1ClientOne example for an OPC UA client application is a generic browser used for exploring and manipulating the Address Space provided by a server. The main tasks of the client is visualizing data provided by the SDK Layer and translating user interactions into calls to the SDK’s API. The design of such an application from the functionality point of view can be quite simple which is shown in Fig. 8.4.Fig. 8.4 Example of a high-level client architecture8 Application Architecture2608.5.2ServerIn principle there are two kinds of server applications: one managing the whole address space in the main memory and another one accessing underlying systems for gathering Address Space information.In the first case, the Address Space is stored in a special data source (e.g., data-base or XML file) and completely loaded into the main memory when the server starts up. This provides a fast access to information contained in the Address Space requested by clients.In the second case, an OPC UA server facades an underlying system like a device, controller or DCS. In the last case, typically several sources are accessed, like a configuration database and several controllers. It is expected that many sys-tem vendors will first head such an approach in order to smoothly migrate existing applications to OPC UA. The main responsibilities of this layer are reading and writing data from the underlying system. A SDK could for example provide spe-cial callback interfaces for exchanging data in a simple way to reduce the complexity of the server implementation on top of the SDK. An example of that architecture is given in Fig. 8.5.Fig. 8.5 Example of a high-level server architecture8.6 Deliverables Provided by the OPC FoundationThe OPC Foundation provides a set of deliverables that can make your life easier when developing OPC UA applications. Some of the deliverables follow the archi-tecture described in Sect. 8.5. All of them are available in the so-called UA SDK. It contains thereby various Stacks, libraries, and sample applications.2618.6 Deliverables Provided by the OPC Foundation8.6.1 StacksBoth an ANSI-C-based and a C#-based Stack is provided with the UA SDK.A Java-based Stack was under development at the time when this book was writ-ten. It is recommended to use the UA stacks provided by the OPC Foundation in order to ensure interoperability between applications implemented in different development environments.The ANSI-C Stack is implemented according to the architecture depicted in Conversation for the Security Layer, and UA TCP for the Transport. For securing messages and validating certificates, the OpenSSL crypto library is applied and integrated in the platform-specific part of the Stack.Alternatively there is also a .NET Stack written in C# which does not have a Platform Layer. Therefore the architecture is different to the one shown above. For the Encoding Layer it supports UA Binary and XML, UA-SecureConversation and WS-SecureConversation as Security Layer protocols, and the transport protocols UA TCP and SOAP/HTTP. However, only the following combinations of the pro-tocols (also named as Stack profiles or mappings schemes; see Chap. 6 for more details) can be used:•HTTP/SOAP, WS-SecureConversation, UA Binary •HTTP/SOAP, WS-SecureConversation, XML •HTTP/SOAP, WS-SecureConversation, UA Binary, and XML 8.6.2 SDKsThere are two C#-based libraries contained in the UA SDK: a client library and a server library. These libraries can be considered as the SDK Layer described ear-lier. Both are providing the base functionality for handling the UA protocol and for processing common tasks regarding logging, security, and configuration. The server library provides special interfaces that can be used to integrate underlying systems for example in order to read or write certain values. The client library implements a NodeCache for buffering Nodes and References. In addition to the client and server libraries, the SDK also provides a C#-based discovery server used by clients for identifying running endpoints of the server they can connect to. C++-based UA SDKs for clients and servers were developed by a group of early adopter companies and are available as commercial libraries from Unified Automation. They are using the ANSI-C stack and are providing platform layers for different operating systems. Similar to the .NET UA SDK, the C++ SDKs are implementing common UA functionality to reduce the development effort for UA applications and are defining interfaces to integrate the application-specific infor-mation with the SDK.8 Application Architecture262• UA TCP, UA-SecureConversation, UA Binary.Fig. 8.2. It supports UA Binary encoding for the Encoding Layer, UA-Secure-8.6.3 ApplicationsThe OPC Foundation’s UA SDK provides both a sample client and server application written in C#. The client application is a generic OPC UA browser offering the base OPC UA functionality like browsing the Address Space, reading and writing Node attributes, subscribing for data changes and Events, and also more sophisti-cated concepts like calling Methods or using Views. Therefore, it is a powerful tool for learning and exploring the concepts of OPC UA. The server uses an in-memory Address Space including standard Nodes as well as an example describing a boiler and its components.8.7 Summary8.7.1 Key MessagesThis chapter describes how the architecture of an OPC UA application typically looks like. The main design goal is thereby the reuse of artifacts (e.g., code and components). Therefore the following layers with certain responsibilities are defined: Application Layer, SDK Layer, and Stack Layer.The Stack is responsible for the lower level functions like encoding and decod-ing messages, securing messages, as well as sending and receiving messages. In addition to that, it has a Platform Layer containing only platform-specific code whereas the other layers are written in platform neutral manner. This facilitates the portability of the Stack to other platforms.The SDK contains higher level functionality covering UA-specific functions and common functions. The UA-specific part implements the OPC UA concepts and Services whereas the common part deals for example with configurations and logging. Additionally the server-side of the SDK provides interfaces in order to integrate other systems used as data providers.The Application Layer covers the use-case-specific part of the functionality. Clients could, for example, process data received from the SDK in a special way in order expose it to the user. Servers could access underlying systems in order to expose its information via OPC UA to clients.The OPC Foundation offers a set of OPC UA standard deliverables that system vendors can reuse. Some of the components already implement similar architec-ture as described in this chapter.8.7.2 Where to Find More Information?More information about the OPC UA standard deliverables can be found on the OPC Foundation Web site (/). More information 2638.7 Summary2648 Application Architectureabout the C++ SDKs can be found at the Unified Automation Web site (http:// ). Finally, the Web site of the OPC programmers’ connection (/) provides a section with SDKs that can a useful source when intending to implement OPC UA applications.8.7.3 What’s Next?In Chap. 8 – System Architecture – different variants of OPC UA client–server concepts are introduced like chained or aggregating server. In addition, some related concepts regarding redundancy, discovery, and auditing are introduced.。
Oracle数据库12c R2:管理员新特性(第2部分)教程说明书

Oracle University |Contact Us: 20 (0)2 35350254 Oracle Database 12c R2: New Features for Administrators Part 2 Ed 1Duration: 5 DaysWhat you will learnThroughout the lessons of the Oracle Database 12c R2: New Features for Administrators Part 2 course constituted by five modules; the Securing Data module, the Making Data Available module, the Partitioning Data module, the Managing Information Lifecycle module and the Monitoring DB Operations and Managing Performance module, students receive a good knowledge of the Oracle Database 12c Release 2 new and enhanced features in different areas of database administration like Unified Auditing, Transparent Data Encryption (TDE) and other areas of security, Recovery Manager, online operations, Oracle Data Pump, SQL*Loader, new partitioning methods, Automatic Data Optimization, In-Memory Column Store, Full Database In-Memory Caching, and Automatic Big Table Caching.Learn To:Gain an understanding of the new and enhanced features of Oracle Database 12c Release 2 (12.2.0.1) amongst different areas such as security, availability, partitioning, performance, and Information Lifecycle Management (ILM).Benefits To YouBenefit from getting a thorough understanding of the following lessons:The lessons of the Securing Data module cover enhancements in auditing like role based conditional auditing, in privilege administration like new system administrative privilege for RAC, in Privilege Analysis and Data Redaction, in Transparent Sensitive Data Protection with new types of policies for FGA and TDE, and finally also in Transparent Data Encryption (TDE).The lessons of the Making Data Available module cover enhanced features in RMAN like table recovery, transport data across platforms, enhancements related to online operations, and finally ongoing enhancements with Oracle Data Pump, SQL*Loader and external tables.The lesson of the Partitioning Data module covers enhancements and new partitioning methods.The lessons of the Managing Information Lifecycle module introduce Heat Map and Automatic Data Optimization with heat map statistics tracking and ADO policies. The lessons also cover Temporal functionalities such as temporal history and temporal validity. In-Database Archiving provides a new feature, the Row-archival.The lessons of the Monitoring DB Operations and Managing Performance module explain the new features to improve the performance of the databases with SQL Performance Analyzer, DB Replay and SQL Plan Management, and to improve query execution with the Optimizer Statistics Advisor, JOIN processing. You will also learn about In-Memory Database option.A Live Virtual Class (LVC) is exclusively for registered students; unregistered individuals may not view an LVC at anytime. Registered students must view the class from the country listed in the registration form. Unauthorized recording, copying, or transmission of LVC content may not be made.AudienceDatabase AdministratorsEnd UsersSystem AdministratorRelated TrainingRequired PrerequisitesKnowledge of Oracle Database 11g R2Knowledge of Oracle Multitenant Container Database architectureSuggested PrerequisitesOracle Database 12c R2: New Features for Administrators Part 1 Ed 1Oracle Enterprise Manager Cloud Control 13c: Install & Upgrade Ed 1Oracle Enterprise Manager Cloud Control 13c: Install & Upgrade Ed 2Course ObjectivesManage security by using Unified AuditingManage security by using privileges and profilesManage security by using Privilege AnalysisManage security by using Data RedactionManage security by using Transparent Data EncryptionManage security by using Transparent Sensitive Data EncryptionDescribe the new RMAN enhancementsManage data availability by using new features of Oracle Data Pump, SQL*Loader and external tablesManage data availability by performing online operationsManage data partitioningManage Information Lifecycle by using ADOManage Information Lifecycle by using In-Database Archiving and Temporal featuresDescribe database operationsConfigure and use In-Memory Column StoreUse In-Memory CachingUse Real Application Testing enhancementsCourse TopicsIntroductionGlobal objectives of the courseLessons grouped by modulesSchedule of the weekAuditing Using Unified AuditQuick review of 11g R2 audit trail implementationOverview of the Unified Audit TrailCreating and enabling audit policies for all users to whom the role is granted directlyCapturing VPD (Virtual Private Database) generated predicatesControlling Data Access Using Privileges and ProfilesNew 12.2 administrative privilegesPassword file enhancementsEnhance the security of administrative usersEnforce the associated profile’s password limitsUsing mandatory INHERIT PRIVILEGES privilege to execute invoker's rights procedureUsing mandatory INHERIT PRIVILEGES privilege to select from BEQUEATH current_user views Using new INHERIT (ANY) REMOTE PRIVILEGES privilegeControlling Data Access Using Privilege AnalysisOverview of database privilege analysisGranting the CAPTURE_ADMIN role to enable management of privilege capturesCreating and starting/stopping privilege captures and runsViewing privilege analysis resultQuerying DBA_PRIV_CAPTURESRedacting DataOverview of Oracle Data RedactionTypes of Data Redaction PoliciesNew redaction format library in EM GUIRedaction policy expressionRedacting with Nullify redaction functionEncrypting DataEncrypt / decrypt / rekey tablespaces onlineConfigure automatic tablespace encryptionControlling Data Access Using Transparent Sensitive Data ProtectionConfigure and use TSDP with VPDConfigure and use TSDP with Data RedactionConfigure and use TSDP with Unified AuditingConfigure and use TSDP with Fine-Grained Auditing (FGA)Configure and use TSDP with Transparent Data Encryption (TDE)Making Data Available by Using RMAN FeaturesRMAN enhancementsTransport Data Across PlatformsTable recoveryAutomate the manual recovery process by using Recover Database Until Available RedoREPAIR FAILURE command extentedMaking Data Available by Using Oracle Data Pump, SQL*Loader and External TablesOracle Data Pump enhancementsSQL*Loader enhancementsQuerying against external tables and overriding external table clausesMaking Data Available by Performing Online OperationsDescribe online redefinition supportsMove and compress table partitions ONLINEPartitioning DataEnable reference partitioning with interval partitioned parent tablesIncorporate the CASCADE option for TRUNCATE PARTITION and EXCHANGE [SUB]PARTITION operations Convert partitioning Range to Interval and vice-versaConvert subpartitioning Range to Interval and vice-versaSimplify the maintenance of (sub) partitioned tablesComposite partitioningManaging Information Lifecycle Using ADOData classification in 12c : tablespace, group, object, row levelsConfigure heat mapAutomatic movement and compressionCompression levels and typesPolicy declarationCustomized automated action execution with user-defined functionExecution in scheduled maintenance windows and by MMONCustomized schedule with DBMS_ILM packageManaging Information Lifecycle Using In-Database Archiving and TemporalChallenges of old data in tables and 11g solutionsIn-database archiving new solutionsUse ROW ARCHIVAL clause to enable row lifecycle state for applicationsSet ROW ARCHIVAL VISIBILITY for session level visibility controlUse predicate on ORA_ARCHIVE_STATE columnTemporal Validity versus Temporal History (Transaction Time of FDA)Set a Temporal Validity by using PERIOD FOR clause of CREATE / ALTER TABLENew SQL temporal data typeMonitoring DB Operations and PerformanceOverviewUse casesCurrent ToolsDefine a DB operationMonitoring: Bracketing an OperationMonitoring the Progress of OperationsDB Operation TuningDB Operation Active ReportConfiguring In-Memory Column StoreIn-Memory Database option goals and benefitsRow format and columnar formatNew SGA componentDeploymentCompression and priority in-memory segments attributesDictionary tables, added columns, IM statistics and IM AdvisorIM FastStartInteraction with other productsUsing In-Memory Column StoreCaching results of frequently evaluated expressions and virtual columnsOptimizing joined columns by creating join groupsImproving Performance Using In-Memory CachingSetting up Full Database In-Memory CachingExplaining the two buffer replacement algorithms of Automatic Big Table CachingConfiguring Automatic Big Table Caching with DB_BIG_TABLE_CACHE_PERCENT_TARGET initialization parameter Using Automatic Big Table CachingImproving SQL PerformanceStatistics gathering performance improvements: Optimizer Statistics AdvisorAdaptive Execution PlanBenefit from automatic dynamic samplingUsing Real Application Testing EnhancementsSQL Performance Analyzer enhancementsSQL Plan Management enhancementsDatabase Replay enhancementsImproving Performance Using Other FeaturesManage session PGA limitMultiple indexes on the same set of columnsDescribe Advanced Row Compression and Avanced Index Compression HIGH levelReduce Cursor Invalidations for DDLsDefine real-time materialized views with on query computation and ON STATEMENT refresh materialized views Using multi-process multi-threaded Oracle architectureDescribe Database Smart Flash Cache enhancementsUse temporary undo for your temporary tables。
四川大学硕士博士研究生论文排版格式要求及范文

密级:工程硕士专业学位论文(设计)题目作者完成日期培养单位四川大学指导教师指导教师工程领域软件工程授予学位日期 2007年12月日工商电子政务的实践与研究软件工程领域研究生关冀指导老师李志蜀唐楷泉网络和数据库是推行电子政务应用的重要手段,电子政务对于推动我国经济向着健康、稳定……关键词:电子政务网络数据Industrial And C omercial “E-Government” SystemSoftware EngineeringGraduate Student:Guan Ji Adviser: Li ZhiShu Tang KaiQuanComputer network and database are important theory in pushing ahead “e-government”,……Key Words: E-Government Network Database四川大学工程硕士学位论文工商电子政务实践与研究目录1 综述 (2)1.1 系统编写目的 (2)1.2 系统建设背景 (2)1.3 系统需求概述 (2)2 系统设计 (3)2.1 系统设计原则 (3)2.1.1 可靠性 (3)2.1.2 安全性 (3)2.2.3 网络各功能层的设计 (4)结论 (5)参考文献 (6)作者在读期间科研成果简介 (7)声明 (8)致谢 (9)附录 (10)1 综述改革开放以来,我国国民经济正逐步向着健康、……1.1系统编写目的本方案是为《成都市企业信用信息系统建设》项目所设计……1.2系统建设背景信息技术的飞速发展正引发着一场深刻的生产和生活方式的变革[1],极大地推动着……3+4+5+6+2=20 (1-1)1.3系统需求概述[2]为了贯彻落实国务院关于建立健全社会信用制度的精神,进一步促进成都市经济的高速……2 系统设计2.1系统设计原则2.1.1可靠性本系统用户群比较复杂,既有政府部门和各系统机构内的操作层、管理层和业务……2.1.2安全性针对成都市信用信息化网络系统的特点,系统设计从底层物理层安全到应用层安全进行了周密的考虑,主要分为以下三个方面:……2.1.2.1服务器部分为用户提供投资保护和更优化的系统能力。
国家计算机三级(数据库技术)67_真题-无答案

国家计算机三级(数据库技术)67(总分100,考试时间120分钟)选择题(每题1分,共60分)1. 下列哪些条目是数据库管理系统DBMS运行所依据的信息? I.数据完整性定义II.安全保密定义III.模式、内模式和外模式定义IV.数据库开放性定义V.用户界面形式定义A. 仅I、III和IVB. 仅I、II和IIIC. 仅II、III和VD. 都是2. 设计磁盘调度算法时应考虑的两个基本因素是______。
A. 公平性和高效性B. 独立性和可靠性C. 有效性和安全性D. 以上都不对3. 信息认证是信息安全的一个重要方面,下列哪一项不属于实施信息认证的方法?A. 身份识别B. 密钥管理C. 数字签名D. 消息认证4. 在关系代数中,自然连接的运算符号为______。
A. πB. ×C. σD. ∞5. 在现在的数据库系统开发中,常采用高级语言或第四代(4GL)语言进行开发,这是为了A. 代码的可重用性B. 系统的可维护性C. 降低开发和维护费用D. 用户界面的友好性6. 下列叙述错误的是( )。
A. SYBASE企业级数据库服务器支持Java、支持扩展标记语言、支持Microsoft的DTCB. SYBASE企业级数据库服务器支持1种类型的锁机制来保证系统的并发性和性能C. SYBASE在核心层实现了存储过程和触发器的可编程能力D. SYBASE支持服务器间的失败转移和客户端透明地自动失败转移等7. 如果要在关系R中插入一个元组,下面______元组不能插入。
A. (a2,b5,7)B. (a6,b5,3)C. (a7,b7,8)D. (a8,b4,1)8. 下面关于数据库系统基于日志的恢复的叙述中,哪一个是正确的?A. 利用更新日志记录中的改前值可以进行UNDO,利用更新日志记录中的改前值可以进行REDOB. 利用更新日志记录中的改前值可以进行UNDO,利用更新日志记录中的改后值可以进行REDOC. 利用更新日志记录中的改后值可以进行UNDO,利用更新日志记录中的改前值可以进行REDOD. 利用更新日志记录中的改后值可以进行UNDO,利用更新日志记录中的改后值可以进行REDO9. 设某散列表的当前状态如下:一共有20个位置,在第0、3、4、6、13、14、17、19的位置存放着各结点的值,则该散列表的负载因子约为______。
信息化五级架构标准

信息化五级架构标准In today's digital age, the five-level architecture standard for information technology is crucial for the development and implementation of complex IT systems. 近年来,信息技术的发展日新月异,信息化五级架构标准对于复杂IT系统的开发和实施至关重要。
This standard provides a clear framework for organizing and managing IT resources effectively, ensuring optimal performance, security, and scalability. 这一标准为有效组织和管理IT资源提供了清晰的框架,确保了最佳的性能、安全性和可扩展性。
By adhering to the five-level architecture standard, organizations can streamline operations, enhance productivity, and adapt to changing technological landscapes. 遵循五级架构标准,组织可以简化运营,提高生产力,并适应不断变化的技术环境。
The first level of the five-level architecture standard is infrastructure, which encompasses the physical components necessary to support IT operations. 五级架构标准的第一级是基础设施,包括支持IT运营所需的物理组件。
This level includes servers, storage devices, networks, and other hardware essential for data processing and communication. 这一级别包括服务器、存储设备、网络和其他对数据处理和通信至关重要的硬件。
中级数据库系统工程师上午试题-13_真题-无答案

中级数据库系统工程师上午试题-13(总分75,考试时间90分钟)单项选择题1. 幻影现象属于哪类数据不一致, (58) 。
A.丢失修改 B.不可重复读C.读脏数据 D.事务故障2. HTML<body>元素中, (68) 属性用于定义超链接被鼠标点击后所显示的颜色。
A.alink B.background C.bgcolor D.vlink3. 在数据库的关系表中,同一列中的分量来自 (36) ;不同的列中的分量来自 (36) 。
A) 同一个域同一个域 B) 同一个域可能同一个域C) 同一个域不同域 D) 不同域同一个域4. 王某是一名程序员,每当软件开发完成后均按公司规定完成软件文档,并上交公司存档,自己没有留存。
因撰写论文的需要,王某向公司要求将软件文档原本借出复印,但遭到公司拒绝,理由是该软件文档属于职务作品,著作权归公司。
以下叙述中,正确的是______。
A.该软件文档属于职务作品,著作权归公司B.该软件文档不属于职务作品,程序员享有著作权C.该软件文档属于职务作品,但程序员享有复制权D.该软件文档不属于职务作品,著作权由公司和程序员共同享有5. 以下关于DB,DBS和DBMS三者之间的的关系正确的是 (48) 。
A) DB包括DBS和DBMS B) DBS包括DB和DBMSC) DBMS包括DB和DBS D) DB,DBS和DBMS三者是并列关系6. 采用全双工通信方式,数据传输的方向性结构为 (50) 。
7. 银行系统采用分布式数据库系统,对本地储户的存储业务能够在本地正常进行,而不依赖于其他场地数据库,称为分布式数据库的______。
A.共享性 B.自治性 C.可用性 D.分布性8. CPU与I/O设备间的接口是 (16) ,它接收从CPU发来的命令,然后去控制I/O设备工作,从而使处理机从繁杂的设备控制事务中解脱出来。
9. 针对E-R图中的组合属性(如地址由省、市、街道、门牌号等组成),在面向对象数据库中用 (62) 来实现。
蛋白质结构预测网址

蛋白质结构预测网址物理性质预测:Compute PI/MW http://expaxy.hcuge.ch/ch2d/pi-tool.html Peptidemass http://expaxy.hcuge.ch/sprot/peptide-mass.html TGREASE ftp:///pub/fasta/SAPS http://ulrec3.unil.ch/software/SAPS_form.html基于组成的蛋白质识别预测AACompIdenthttp://expaxy.hcuge.ch/ch2d/aacompi.htmlAACompSimhttp://expaxy.hcuge.ch/ch2d/aacsim.html PROPSEARCHhttp://www.embl-heidelberg.de/prs.html二级结构和折叠类预测nnpredict /~nomi/nnpredict Predictproteinhttp://www.embl-heidelberg.de/predictprotein/SOPMAhttp://www.ibcp.fr/predict.htmlSSPRED http://www.embl-heidelberg.de/sspred/ssprd_info.html特殊结构或结构预测COILS http://ulrec3.unil.ch/software/COILS_form.htmlMacStripe /matsudaira/macstripe.html与核酸序列一样,蛋白质序列的检索往往是进行相关分析的第一步,由于数据库和网络技校术的发展,蛋白序列的检索是十分方便,将蛋白质序列数据库下载到本地检索和通过国际互联网进行检索均是可行的。
由NCBI检索蛋白质序列可联网到:“:80/entrz/query.fcgi?db=protein”进行检索。
利用SRS系统从EMBL检索蛋白质序列联网到:/”,可利用EMBL的SRS系统进行蛋白质序列的检索。
01_RNxxxx1EN14N00_Flexi_BSC_Architecture_and_Functionality_rev

Flexi BSC
3000 TRX one cabinet configuration (S14)
• Flexi BSC product family is a general term for all versions upgradeable to Flexi BSC configuration • Flexi BSC as product name is specific for the 3000 TRX one cabinet product/configuration
• IP based SS7 (SIGTRAN) links • 64/128/256/512kbit/s, 1Mbit/s or
2Mbit/s links
支持从所有的BSC3I升级 到FLEXI
Flexi BSC in Brief
General Evolution of BSC Products
• Describe the architecture and mechanics Flexi BSC • Describe the changes of Flexi BSC compared with BCS3i
660/1000/2000 and BSC2i
• Explain the functionality of the new units and plug in units in Flexi
• Redundancy, fault management and overload protection on top
Application Note AC147说明书

Application Note AC147February 20141© 2014 Microsemi CorporationUsing the BUFD and INVD Delay MacrosTable of ContentsIntroductionChip designers often find themselves in a situation where the board layout has been completed before the chip is designed. The FPGA they are targeting must satisfy an external input phase relationship -usually between clock and data inputs. Maintaining this phase relationship for signals going off-chip enables them to meet external setup and hold requirements. BUFD and INVD are special delay macros that give designers more control in the timing behavior of their designs.BUFD is a special version of the buffer (BUFF), which will not be removed by Microsemi’s designer software in its optimization steps. This macro will always be retained and its delay preserved after the compile and layout steps. Similarly, INVD is a special version of the inverter (INV), which is preserved after compilation and layout.The suggested uses of BUFD and INVD are as follows:•Maintain the phase relationship between clock and data input signals when sending signals derived from them these signals off-chip. This application enables them to meet external setup and hold requirements.•Maintain the phase relationship of clock and data input signals in designs with high-fanout clock signals.Maintaining Phase RelationshipsAs shown in Figure 1, a certain phase relationship exists between the clock and data signals (generally,the data signal lags the clock signal). Employing BUFD is recommended to maintain this phase relationship. All Microsemi antifuse device families have a restriction that a CLKBUF cannot be connected directly to an OUTBUF, so Designer software will automatically insert a BUFF module (inst3 in Figure 1). This will introduce a delay that may cause the data signal to arrive ahead of the sys_clk signal going off-chip. To prevent this, the user can insert a BUFD macro in his netlist. The BUFD, unlike a regular BUFF, is assigned the ALSPRESERVE property. This ensures that the BUFD will not be optimized away during the compilation step and hence can offset the delay caused by automatic insertion of the BUFF in the sys_clk path. This technique maintains the phase relationship of the data andclock inputs when going off-chip and the external setup and hold requirements can be met.Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1Maintaining Phase Relationships . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1Usage Models . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3HDL Design Flow . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3Schematic Capture Design Flow . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4Delay Values . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4List of Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4Using the BUFD and INVD Delay Macros2In Figure2, the clock signal coming from the CLKBUF has a high fanout. This means increased capacitive loading and hence increased delay. In contrast, the data signal has a fanout of only one. The clock network’s high fanout may allow the data input to (undesirably) lead the clock signal. Again, introducing one or more BUFD macros (inst1) in the data signal path provides enough delay to offset the delay of the high-fanout clock net.Figure 1 • Control of Phase Relationship between Data and System Clock using BUFDUsage Models3If inversion of the signal is required in addition to delay, the INVD macro is available. Again, the ALSPRESERVE property is assigned to this macro to avoid elimination during optimization steps.Usage ModelsHDL Design FlowNone of the synthesis tools that support Microsemi technologies will infer the INVD or BUFD macros in the synthesized netlist. Simulation library models of INVD and BUFD, similar to their INVD and BUFF counterparts, are available from Microsemi in both VHDL and Verilog. The manual process for buffer insertion is as follows:1.Import the synthesized netlist into Designer. Run compile and layout.2.Invoke Timer from Designer to check the timing/phase relationships for the signals of interest.ing a text editor, manually modify the netlist and insert BUFD and/or INVD macros into thedesired paths.4.Import the modified netlist into Designer. Again run compile and layout.5.Invoke Timer again to review the delays for the signals of step 2.If necessary, repeat steps 3 through 5 until the design timing requirements are met.Figure 2 • Control of Phase Relationship in Designs with High Clock FanoutsUsing the BUFD and INVD Delay Macros4Schematic Capture Design FlowINVDs and BUFDs are available for the following Microsemi-supported schematic capture tools:•ConceptHDL PE13.5 and PE13.6•Mentor Graphics c.4 and D.1•Workview Office 7.5•Powerview 6.1•ePD 1.0•ePD 1.1 TypicalTo avoid inadvertent instantiation of INVD or BUFD where INV or BUFF is intended, the graphicalsymbols for INVD and BUFD have warning labels "Special Use Only." The flow for buffer insertion is as follows:1.Generate an EDIF netlist with the schematic tool.2.Import the EDIF netlist into Designer. Run compile and layout.3.Invoke Timer from Designer to check the timing/phase relationships for the signals of interest.4.Edit the schematics to insert BUFD and/or INVD macros into the desired paths.5.Check and save your schematics. Generate an EDIF netlist from the modified schematics.6.Import the modified netlist into Designer. Again run compile and layout.7.Invoke Timer again to review the delays for the signals of step 3.8.If necessary, repeat steps 4 through 7 until the design timing requirements are met.Delay ValuesTable 1 shows the rising (R) and falling (F) delays for INVD and BUFD in different Microsemi families.These values are obtained using the fastest speed grade for the device using typical temperature,voltage, and process corners as well as optimized placement. Actual delay numbers may vary with the device, speed grade, and actual placement.List of ChangesThe following table lists critical changes that were made in the current version of the document.Table 1 • BUFD/INVD Delay for Various Microsemi Technology FamiliesACT1ACT2ACT33200DX 42Mx SX eX RTAX-S Units BUFD R 3.9 4.3 2.6 4.2 1.80.7 1.1 4.5ns F 3.7 3.5 2.5 3.4 1.60.7 1.1 4.6ns INVD R 3.8 4.3 2.4 3.9 1.80.7 1.1 6.5ns F3.6 3.6 2.2 3.2 1.60.7 1.1 6.1nsSpeed Grade-3-1-3-3-3-3STD-1Revision ChangesPage Revision 1(February 2014)Table 1 is updated to include RTAX-S values (SAR 47788).45192673-1/02.14© 2014 Microsemi Corporation. All rights reserved. Microsemi and the Microsemi logo are trademarks of Microsemi Corporation. All other trademarks and service marks are the property of their respective owners.Microsemi Corporation (NASDAQ: MSCC) offers a comprehensive portfolio of semiconductor solutions for: aerospace, defense and security; enterprise and communications; and industrial and alternative energy markets. Products include high-performance, high-reliability analog and RF devices, mixed signal and RF integrated circuits, customizable SoCs, FPGAs, and complete subsystems. Microsemi is headquartered in Aliso Viejo, Calif. Learn more at .Microsemi Corporate HeadquartersOne Enterprise, Aliso Viejo CA 92656 USA Within the USA: +1 (949) 380-6100Sales: +1 (949) 380-6136Fax: +1 (949) 215-4996。
华为LTE专业术语

0-91U机柜的高度通常以U(Unit)为单位,1U=44.45mm。
3GPP第三代移动通信标准化伙伴项目(3rd Generation Partnership Project),成立于1998年,由许多国家和地区的电信标准化组织共同组成,是一个具有广泛代表性的国际标准化组织,是3G技术的重要制定者。
目前,该组织负责制定WCDMA和TD-SCDMA通信标准,并先后推行了3GPP R99、R4、R5、R6、R7等逐级演进的WCDMA通信标准。
3GPP2第三代移动通信标准化伙伴项目2(3rd Generation Partnership Project 2)。
目前,该组织负责制定CDMA2000通信标准,并先后推行了3GPP2 IS-95A、IS-95B、CDMA2000 1X、CDMA2000 1X EV-DO、CDMA2000 1X EV-DV等逐级演进的CDMA2000通信标准。
A-EAA-RACF接入网资源接纳控制功能(Access-Resource and Admission Control Function)。
AAA认证、授权和计费(Authentication, Authorization and Accounting)。
一个用于配置认证、授权和计费的机制。
认证是指对用户的身份与可使用的网络服务进行确认;授权是指依据认证结果开放网络服务给用户;计费是指记录用户对各种网络服务的用量并提供给计费系统。
AC交流电(Alternating Current)。
ACF鉴权控制功能(Authentication & Authorization Control Function),完成用户的认证,授权、计费消息的处理。
EAP-SIM/EAP-AKA鉴权时,并完成从HLR获取用户鉴权数据和用户WLAN业务签约信息的处理。
ACL访问控制列表(Access Control List)。
ADD自动设备检测(Automatic Device Detection)。
计算机编程常用术语英语词汇汇总

计算机编程及常用术语英语词汇大全cover覆盖、涵盖create/creation创建、生成crosstab query交叉表查询(for database)CRTP (curiously recurring template pattern)CTS (common type system)通用类型系统cube多维数据集(for database)cursor光标cursor游标(for database)custom定制、自定义data数据data connection数据连接(for database)Data Control Language (DCL)数据控制语言(DCL) (for database)Data Definition Language (DDL)数据定义语言(DDL) (for database)data dictionary数据字典(for database)data dictionary view数据字典视图(for database)data file数据文件(for database)data integrity数据完整性(for database)data manipulation language (DML)数据操作语言(DML) (for database)data mart数据集市(for database)data pump数据抽取(for database)data scrubbing数据清理(for database)data source数据源(for database)Data source name (DSN)数据源名称(DSN) (for database) data warehouse数据仓库(for database)dataset数据集(for database)database 数据库(for database)database catalog数据库目录(for database)database diagram数据关系图(for database)database file数据库文件(for database)database object数据库对象(for database)database owner数据库所有者(for database)database project数据库工程(for database)database role数据库角色(for database)database schema数据库模式、数据库架构(for database) database scrīpt数据库脚本(for database)data-bound数据绑定(for database)data-aware control数据感知控件(for database)data member数据成员、成员变量dataset数据集(for database)data source数据源(for database)data structure数据结构data table数据表(for database)datagram数据报文DBMS (database management system)数据库管理系统(for database) DCOM (distributed COM)分布式COMdead lock死锁(for database)deallocate归还debug调试debugger调试器decay退化decision support决策支持declaration声明declarative referential integrity (DRI)声明引用完整性(DRI) (for database) deduction推导DEFAULT constraint默认约束(for database)default database默认数据库(for database)default instance默认实例(for database)default result set默认结果集(for database)default缺省、默认值defer推迟definition定义delegate委托delegation委托dependent namedeploy部署dereference解引用dereference operator (提领)运算子derived class派生类design by contract契约式设计design pattern 设计模式destroy销毁destructor(dtor)析构函数、析构器device设备DHTML (dynamic HyperText Markup Language)动态超文本标记语言dialog对话框digest摘要digital数字的DIME (Direct Internet Message Encapsulation)直接Internet消息封装directive (编译)指示符directory目录dirty pages脏页(for database)dirty read脏读(for database)disassembler反汇编器DISCO (Discovery of Web Services)Web Services的查找disk盘dispatch调度、分派、派发(我喜欢“调度”)DISPID (Dispatch Identifier)分派标识符distributed computing分布式计算distributed query分布式查询(for database)DNA (Distributed interNet Application)分布式网间应用程序document文档DOM (Document Object Model)文档对象模型dot operator (圆)点操作符driver驱动(程序)DTD (document type definition)文档类型定义double-byte character set (DBCS)双字节字符集(DBCS)dump转储dump file转储文件dynamic cursor动态游标(for database)dynamic filter动态筛选(for database)dynamic locking动态锁定(for database)dynamic recovery动态恢复(for database)dynamic snapshot动态快照(for database)dynamic SQL statements动态SQL语句(for database) dynamic assembly动态装配件、动态配件dynamic binding动态绑定EAI (enterprise application integration)企业应用程序集成(整合) EBCO (empty base class optimization)空基类优化(机制)e-business电子商务EDI (Dlectronic Data Interchange)电子数据交换efficiency效率efficient高效end-to-end authentication端对端身份验证end user最终用户engine引擎entity实体encapsulation封装enclosing class外围类别(与巢状类别nested class有关) enum (enumeration)枚举enumerators枚举成员、枚举器equal相等equality相等性equality operator等号操作符error log错误日志(for database)escape code转义码escape character转义符、转义字符exclusive lock排它锁(for database)explicit transaction显式事务(for database)evaluate评估event事件event driven事件驱动的event handler事件处理器evidence证据exception异常exception declaration异常声明exception handling异常处理、异常处理机制exception-safe异常安全的exception specification异常规范exit退出explicit显式explicit specialization显式特化export导出expression表达式facility设施、设备fat client胖客户端feature特性、特征fetch提取field字段(java)field字段(for database)field length字段长度(for database)file文件filter筛选(for database)finalization终结firewall防火墙finalizer终结器firmware固件flag标记flash memory闪存flush刷新font字体foreign key (FK)外键(FK) (for database)form窗体formal parameter形参forward declaration前置声明forward-only只向前的forward-only cursor只向前游标(for database) fragmentation碎片(for database)framework框架full specialization完全特化function函数function call operator (即operator ())函数调用操作符function object函数对象function overloaded resolution函数重载决议functionality功能function template函数模板functor仿函数GAC (global assembly cache)全局装配件缓存、全局配件缓存GC (Garbage collection)垃圾回收(机制)、垃圾收集(机制) game游戏generate生成generic泛化的、一般化的、通用的generic algorithm通用算法genericity泛型getter (相对于setter)取值函数global全局的global object全局对象global scope resolution operator全局范围解析操作符grant授权(for database)granularity粒度group组、群group box分组框GUI图形界面GUID (Globally Unique Identifier)全球唯一标识符hand shaking握手handle句柄handler处理器hard-coded硬编码的hard-copy截屏图hard disk硬盘hardware硬件hash table散列表、哈希表header file头文件heap堆help file帮助文件hierarchy层次结构、继承体系hierarchical data阶层式数据、层次式数据hook钩子Host (application)宿主(应用程序)hot key热键hyperlink超链接HTML (HyperText Markup Language)超文本标记语言HTTP pipeline HTTP管道HTTP (HyperText Transfer Protocol)超文本传输协议icon图标IDE (Integrated Development Environment)集成开发环境IDL (Interface Definition Language)接口定义语言identifier标识符idle time空闲时间if and only if当且仅当IL (Intermediate Language)中间语言、中介语言image图象IME输入法immediate base直接基类immediate derived直接派生类immediate updating即时更新(for database) implicit transaction隐式事务(for database) incremental update增量更新(for database) index索引(for database)implement实现implementation实现、实现品implicit隐式import导入increment operator增加操作符infinite loop无限循环infinite recursive无限递归information信息infrastructure基础设施inheritance继承、继承机制inline内联inline expansion内联展开initialization初始化initialization list初始化列表、初始值列表initialize初始化inner join内联接(for database)in-place active现场激活instance实例instantiated具现化、实体化(常应用于template) instantiation具现体、具现化实体(常应用于template) integrate集成、整合integrity完整性、一致性aggregation聚合、聚集algorithm算法alias别名align排列、对齐allocate分配、配置allocator分配器、配置器angle bracket尖括号annotation注解、评注API (Application Programming Interface)应用(程序)编程接口app domain (application domain)应用域application应用、应用程序application framework应用程序框架appearance外观append附加architecture架构、体系结构archive file归档文件、存档文件argument引数(传给函式的值)。
计算机常用日语词汇

ごみ箱 回收站
さ行
作成 建立 素材 (做主页用的)素材
辞書 词库 周辺装置 外围设备
出力 输出 情報 信息
情報化社会 信息化社会 情報家電 信息家电(如电脑)
新規 新建 設定 设置
専用回線 专线 外付け 外置
た行
帯域幅 带宽
あいまい検索=模糊匹配检索
アウトソーシング=外包=outsourcing
アウトプット=输出=output
アウトプットインフォメーション=输出信息=output information
アウトプットエリア=输出区=output area
アウトプットオーダー=输出指令=output order
リターン?キー 回车键 リンク 链接
ルート?ディレクトリ 根目录 レーザー?プリンタ 激光打印机
レス (接在别人话题后面的)留言 ログ (过去的)记录
ログアウト 退出 ログオン 进入
ワ行
ワークステーション 工作站 ワードパッド 写字板
ワードプロセッサ 文字处理机 ワープロソフト 字处理软件
別館 (个人主页的)非主要内容
返事 答复、回信等
変数 参数
変換 转换
放熱板 散热板
本館 (个人主页的)主要内容
ま行
申し込み 申请注册 文字列 字符串
や行
容量 容量
あ行
IPアドレス IP地址
アドレス帳 地址簿
(E)メール 电子邮件
Eコマース 电子商务
マ行
マイクロ?プロセッサ 微处理器
マイコンピュータ 我的电脑
マウス 鼠标
CH9121网络和UART透明传输芯片说明书
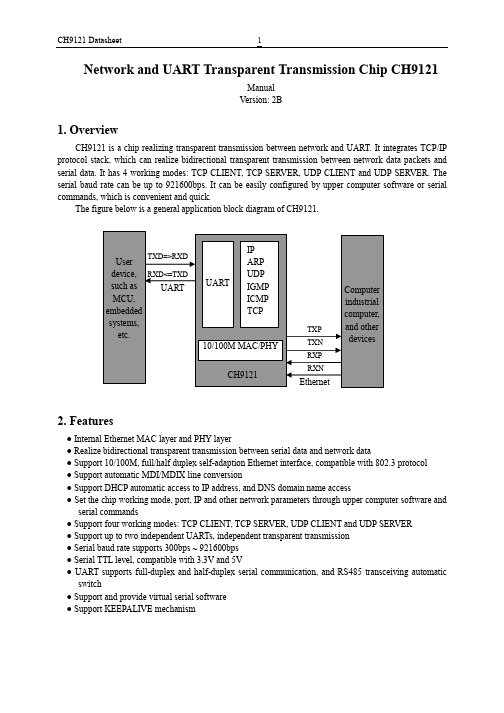
Network and UART Transparent Transmission Chip CH9121ManualVersion: 2B1.OverviewCH9121 is a chip realizing transparent transmission between network and UART. It integrates TCP/IP protocol stack, which can realize bidirectional transparent transmission between network data packets and serial data. It has 4 working modes: TCP CLIENT, TCP SERVER, UDP CLIENT and UDP SERVER. The serial baud rate can be up to 921600bps. It can be easily configured by upper computer software or serial commands, which is convenient and quick.The figure below is a general application block diagram of CH9121.2.Features●Internal Ethernet MAC layer and PHY layer●Realize bidirectional transparent transmission between serial data and network data●Support 10/100M, full/half duplex self-adaption Ethernet interface, compatible with 802.3 protocol●Support automatic MDI/MDIX line conversion●Support DHCP automatic access to IP address, and DNS domain name access●Set the chip working mode, port, IP and other network parameters through upper computer software andserial commands●Support four working modes: TCP CLIENT, TCP SERVER, UDP CLIENT and UDP SERVER●Support up to two independent UARTs, independent transparent transmission●Serial baud rate supports 300bps ~ 921600bps●Serial TTL level, compatible with 3.3V and 5V●UART supports full-duplex and half-duplex serial communication, and RS485 transceiving automaticswitch●Support and provide virtual serial software●Support KEEPALIVE mechanism3.PackageChipPackageName DescriptionCH9121 LQFP64M LQFP package; 64 pins; package body 10 x10mm 4.PinsCH9121 Pin No.PinNamePin Type Pin description2, 12, 17, 21, 29, 40, 42, 45, 63 VCC33 Power3.3V positive power input, require an external 0.1uF powerdecoupling capacitor6, 19, 28, 43, 54, 64 VCC18 Power1.8V positive power input, require an external 0.1uF powerdecoupling capacitor3, 9, 13, 18, 20,37, 41, 44, 48GND Power Common ground14, 15, 16, 22,23, 24, 25, 26,27, 34, 35, 38,39, 47, 49, 50,61, 62NC - Reserved, suspended1 RSETE Input Connected with an external 18K resistor to ground4 RXP EthernetsignalEthernet RXP signal5 RXN Ethernet Ethernet RXN signalsignal7 TXP EthernetsignalEthernet TXP signal8 TXN EthernetsignalEthernet TXN signal10 XI Input Input of the crystal oscillator, requires an external 30MHzcrystal11 XO Output Inverted output of crystal oscillator, requires an external 30MHzcrystal30 TCPCS1 Output In TCP client mode, connection status indicator of port 1, activeat low level31 RUN Output CH9121 running status indicator pin, multiplexed as ISPupgrade pin32 CFGEN Input Network configuration enable pin, detects when power-up, configuration disabled when at low level33 TCPCS2 Output In TCP client mode, connection status indicator of port 2, activeat low level36 RSTI Input External reset input, active at low level, built-in pull-up resistor 46 DIR2 Output Used to control RS485 receiving/transmitting switch of UART251 DIR1 Output Used to control RS485 receiving/transmitting switch of UART152 ACT# Output Ethernet connection communication indicator LED drive pin53 LINK# Output PHY connection indicator LED, active low55 RXD2 Input Serial data input of UART2, built-in pull-up resistor(Off by default)56 TXD2 Output Serial data output of UART2 (Off by default)57 RXD1 Input Serial data input of UART1, built-in pull-up resistor(On by default)58 TXD1 Output Serial data output of UART1 (On by default)59 RESET InputRestore factory settings, chip power-on detection, active at low level60 CFG0 InputUART configuration mode set pin, built in pull-up. If low level is detected, enter UART configuration mode. Exit the mode if high level is detected5.Function5.1. Function DescriptionCH9121 is a chip for transparent transmission between network and UART, and realizes bidirectional transparent transmission of serial data and network data. It supports 4 working modes (TCP CLEINT/SERVER, UDP CLIENT/SERVER), and the serial baud rate supported ranges from 300bps to 921600bps. Before use, the network parameters and UART parameters of the chip shall be configured by upper computer software NetModuleConfig.exe or serial commands. After the configuration is completed, CH9121 will save the configuration parameters to the internal storage space. And after the chip is reset, CH9121 will work according to the saved configuration value.The basic parameters of CH9121 include: name, MAC address display, dynamic access IP address setting, manual IP address setting (including CH9121 IP address, subnet mask, default gateway), and UART negotiation configuration.The name is mainly for the convenience of CH9121 module management within the LAN, with the length of not more than 20 bytes. The MAC address field shows the MAC address of the currently selectedmodule. There are two ways for CH9121 to set network parameters. 1) DHCP, that is, it automatically obtains network parameters from the gateway device with DHCP SERVER function; 2) manual setting. UART negotiation configuration function is to enter serial configuration mode by handshaking through the UART, which is disabled by default.CH9121 port parameters include: network mode, local port, target IP/domain name, destination port, serial baud rate/data bit/stop bit/parity check bit, network cable disconnection processing, RX packet length, RX packet timeout interval, network connection operation.The network mode (TCP SERVER/CLIENT, UDP SERVER/CLIENT), destination IP address, and local/destination port are the basic parameters of network communication. The destination IP address can also be accessed by domain name. The serial baud rate ranges from 300bps to 921600bps (the baud rate error of the serial port transmitting signal is less than 0.3%, and the allowable baud rate error of the serial port receiving signal is not less than 2%). It supports 5/6/7/8 data bits, 1/2 stop bits, odd/even/no parity check, blank 0, and mark 1 check mode. The network cable disconnection processing means that when the network cable is disconnected, CH9121 actively closes the connection or does not take any action. The length range of RX packet is 1-1024, which means that when the length of CH9121 UART receiving data reaches the set length, CH9121 will immediately packet the serial data and send it out via network. The timeout time setting range is 0-200, and the timeout unit is about 5ms. For example, when the timeout is 1, the data length of the serial port receiving buffer does not reach the length of the RX packet, and the serial port does not receive a new one in more than 5ms, the serial port timeout will occur. After the serial port timeout occurs, CH9121 will send the data received by the serial port over the network. When the timeout time is set to 0, the internal hardware timeout mechanism will be enabled (no new data is received after 4 data times), which is suitable for occasions where real-time requirements are high and large quantities of data are sent and received. Clear serial port buffer setting refers to how the data received by the serial port is processed before the network connection is established, the data is cleared (discarded) or retained after TCP connection.5.2. Default ConfigurationWhen CH9121 leaves factory, port 2 is closed and port 1 works in TCP CLIENT mode by default. The default parameters related to the network are as follows:(1)Device IP: 192.168.1.200(2)Subnet mask: 255.255.255.0(3)Default gateway: 192.168.1.1(4)Module port: 2000(5)Destination IP: 192.168.1.100(6)Destination port: 1000(7)Number of reconnection: unlimitedUART related default parameters are:(1)Baud rate: 9600(2)Timeout: 0(3)Data bit: 8. Stop bit: 1. Parity check bit: No(4)Clear UART buffer: Never6.Parameters6.1. Absolute Maximum ValueCritical value or exceeding the absolute maximum value may cause the chip to work abnormally or even be damaged.Name Parameter description Min. Max. UnitTA Ambient temperature during operation VCC33=3.3VVCC18=1.8V-40 85 ℃TS Ambient temperature during storage -55 125 ℃VCC33 Supply voltage (VCC33 connects to power, GND to ground) -0.4 4.2 V VCC18 Supply voltage (VCC18 connects to power, GND to ground) -0.4 2.3 V VIO Voltage on input or output pins -0.4 VCC33+0.4 V VIO5 Voltage on input or output pins that support 5V withstand voltage -0.4 5.4 V6.2. Electrical ParametersTest Conditions: TA=25℃, VCC33=3.3V, VCC18=1.8VName Parameter description Min. Typ. Max. UnitVCCxx Supply voltage VCC33 2.7 3.3 3.6V VCC18 1.65 1.8 1.95ICC Total supply current duringoperationVCC33=3.3V 160 190 mAVIL Low level input voltage -0.4 0.7 V VIH High level input voltage 2.0 VCC33+0.4 V VOL Low level output voltage (4mA draw current) 0.4 V VOH High level output voltage (4mA output current) VCC33-0.4 VIUP Input current at the input terminal with built-inpull-up resistor20 40 100 uAIDN Input current at the input terminal with built-inpull-down resistor-20 -40 -100 uAVR Voltage threshold when power-on reset 1.4 1.5 2.5 V7.Applications7.1 Hardware Circuit DesignNote: Due to space limitations, the circuit of the power supply and decoupling capacitors near the 3.3V and 1.8V pins is omitted in the figure, which must be added when designing the circuit. The detailed circuit reference file: CH9121PCB (please download in our official website).U1 is the main control chip CH9121. TXD1 and RXD1 are compatible with 3.3V and 5V level, and the RS485 control pin DIR can be suspended if not used.P1 is RJ45 port, with built-in network transformer, used to connect network equipments such as switches and router. It contains two pairs of Ethernet differential signals.When actually making a PCB, R5-R8, C6, and C7 should be as close as possible to the 5th pin of P1. The 0.1 uF decoupling capacitors for 3.3V and 1.8V pins are omitted in the figure. TXOP (RXIP) and TXON. (RXIN) are differential signals. When wiring, they should be wired close to parallel, and try to provide ground wire or copper coating on both sides to reduce external interference. The length of relevant signals of crystals XI and XO should be shortened as much as possible. In order to reduce the interference of high-frequency clock for the outside, the baselines should be surrounded or copper should be clad around relevant components.。
Oracle 12c数据库基础教程-Oracle 12c数据库办公事务管理系统(Visual C#)

RoomName VARCHAR2(50) , RoomSize NUMBER, Resources VARCHAR2(500) );
表Information的结构
编 号 字段名称 数据结构
说明 培训编号 创建日期 培训主题 当前状态,包括创建、发布、培训开始、培 训结束 培训类型,0表示内部培训、1表示外部培训 培训地点 培训讲师 培训开始日期 培训结束日期 报名开始日期 报名结束日期 参加人 是否免费,0表示免费、1表示不免费 培训费/人 培训介绍 参加人员姓名列表
创建表Training的脚本
创建表Information的脚本
CREATE TABLE C##rmation ( InfoNo VARCHAR2(20) NOT NULL , InfoName VARCHAR2(100), InfoType VARCHAR2(50) , ICount NUMBER, IPrice NUMBER, Detail VARCHAR2(2000), CreateDate VARCHAR2(50) );
表InfoLend的结构
编号 1 2 3 4 5
6
字段名称 Id InfoNo LendDate EmpName LendCount
Flag
数据结构 NUMBER VARCHAR2 (20) VARCHAR2 (50) VARCHAR2(40) NUMBER
NUMBER
说明 借阅号 资料编号 借阅日期 借阅员工姓名 借阅数量 标记,0表示借阅,1表示借阅确认,2表示 归还,3表示归还确认
4.用户管理。
p 修改密码。 p 切换用户。
Oracle Developer Studio 12.5 发行版功能介绍说明书

6 调试工具 ......................................................................................................... 33 关于 dbx 调试器 .......................................................................................... 33 新增和更改的 dbx 功能 ................................................................................ 33
蛋白质数据库介绍

SWISS-PROT或TrEMBL /sprotPIRMIPSJIPID已经和ExPASy 三、蛋白质二级结构预测网站(数据库)4始建于基于对蛋白质家族中同源序列多重序列比对得到的保守区域,这些区域通常与生物学功能相关。
数据库包括两个数据库文件:数据文件Prosite5蛋白质二级结构构象参数数据库DSSP6蛋白质家族数据库FSSP7同源蛋白质数据库HSSP在前面已经述说过了。
第二节、蛋白质序列分析方法一、多序列比对双序列比对是序列分析的基础。
序列之间的关系,生物学模式方面起着相当重要的作用。
多序列比对有时用来区分一组序列之间的差异,但其主要用于描述一组序列之间的相似性关系,法建立在某个数学或生物学模型之上。
因此,正如我们不能对双序列比对的结果得出果也没有绝对正确和绝对错误之分,相似性关系以及它们的生物学特征。
我们称比对前序列中残基的位置为绝对位置。
置Ⅰ相对位置。
显然,同一列中所有残基的相对位置相同,而每个残基的绝对位置不同,因为它们来自不同的序列。
绝对位置是序列本身固有的属性,也就比对过程赋予它的属性。
算法复杂性多序列比对的计算量相当可观,时间和内存空间与这两个序列的长度有关,或者说正比于这两个序列长度的乘积,用(的两维空间扩展到三维,即在原有二维平面上增加一条坐标轴。
这样算法复杂性就变成了(例如,如果用某种颜色表示一组高度保守的残基,则某个序列的某一位点发生突变时,则由于颜色不同,就可以很快找出。
颜色的选择可以根据主观愿望和喜好,但最好和常规方法一致。
用来构筑三维模型的按时氨基酸残基组件和三维分子图形软件所用的颜色分类方法,比较容易为大家接受(表2)。
多序列比对程序的另一个重要用途是定量估计序列间的关系,关系。
关系。
相似性值低于预料值,那么有可能是序列间亲缘关系较远,也可能是比对中有错误之处2同步法实质是把给定的所有序列同时进行比对,而不是两两比对或分组进行比对。
其基本思想是将一个二维的动态规划矩阵扩展到三维或多维。
免费期刊全文数据库(FreeFull-textJournalDatabase)
免费期刊全文数据库(Free Full-text Journal Database)Free journal full text database (with a spare) 2010-04-04 00:32 (| classification: default classification)Hong Kong University Science & Technology library, Dspace t.hk/dspaceIncluding Hong Kong University Science & Technology academic papers, dissertations, research reports and other content, free access to the full text.Openj-gate/Provides 4350 Open Access Journals of millions of Journal Full-text documents.International and regional digital collections, University of California/escholarship/University of California international and regional digital collection research project. EScholarshipRepository mainly provides published journal papers, unpublished research manuscripts, conference documents, and other more than 10 thousand articles linking publications. They can be read free of charge.University of Cambridge Institutional Repository/By Cambridge, University, Library and University Computing Service maintenance, University of Cambridge provides related journals, academic papers, dissertations and other electronic resources.Joint journal libraries in developing countries.br/Electronic publication services nonprofit, provided from developing countries (such as Brazil, Cuba, India, Indonesia, Kenya, South Africa, Uganda, Zimbabwe, etc.) the variety of open access journals.Michigan University Papers Library/index.jspMore than 20 thousand papers, technical reports, comments and other articles were published in the proceedings of the University of michigan. Related articles including art, biology, social science, resources and environment, and other dissertations. Full text can be opened with OPEN.JfGCERN Document ServerHttp://cdsweb.cern.ch/The main coverage of Physics (particle) and related disciplines, to provide more than 360000 full text literature, including pre printed literature, journal papers, books, pictures, dissertations and so on.KLArXiv/ArXiv is a non-profit educational institution in Cornell University, providing 16 free electronic journals for physics, mathematics, nonlinear science, computer science and quantitative biology.NASA Technical Reports Server/? Method=browse?It is mainly about the scientific and technical reports and conference papers on aerospace research.National, Service, Center, for, Environmental, Publications/ncepihom/National Service Center for Environmental Publicationsprovides the U.S. Environmental Protection Agency (EPA) publications. EPA, National, Publications, Catalog can be retrieved by EPA publication number or title.Energy Citations Database/energycitations/Provides a summary of the energy technology information from the US Department of energy. Subject areas: Materials Science, environmental science, computers, energy and physics. Literature types include journal papers, dissertations, research reports and patents.Online free full text journal FullText/ offers free full-text access to more than 7000 academic journals.Open J-Gate open access journal portal/Provides free access and full text links to nearly 4000 journals based on open access, including schools, research institutes, and industry journals, with over 1500 academic journals reviewed by peer review (Peer-Reviewed)PMC (PubMed, Centeral)/The United States NCBI (National Biotechnology Information Center) established digital life sciences journal literature collection, S now offers more than 50 kinds of biomedical journals free full textDOAJ (Directory, of, Open, Access, Journals)/Free full text academic journals. There are currently 2752 periodicals, 830 of which can be searched in full text. There are currently 140307 articles.HighWire PressThe HighWire library, a branch of the Stanford University library, has the largest free journal database, offering 916 free journals and 1149216 full text onlineUniversity, of, Tennessee, Knoxville/utj/jei-home.phpThe Journal of economics at the University of Tennessee includes free periodicals in 12 phases for three years from 2000 to 2002.The, Electronic, Library, of, Mathematics/journals/The European Mathematical Society electronic library provides resources such as periodicals, conferences, essays, monographs, lectures, and software. And provides full page browsing of periodicals and electronic books. Non electronic books provide foreword, abstract, catalogue, book review and so on. In particular, the classical papers in Hamilton and Riemann can be retrieved from the classics. /The U.S. "science" website content to research and development report, all the information are free to use, also do not have to register, but through some information of these links is to restrict the use or the use of the conditional.ERIC Education Resource Information Center/Funded by the U.S. Department of education website series and the world's largest educational resources database, including various documents and education research and practice in these aspects, the more than one million articles, included 980 kinds of education and education related journals and the titles and abstracts. Some resources can be found in full textPLoS Public Library of Science/PLOS is a support by many Nobel prize winners and charitable non-profit academic organization, the latest scientific research achievements around the world and to promote the medical field, make it become a kind of public resources, scientists, doctors, patients and students can understand the latest research developments through such a being restricted platform. PLoS publishes 8 journals in the field of life science and medicine for free access to the full text.Journal of Statistical Software/The Journal of statistical software, published by the American Statistical Society, provides 20 volumes from 1996 to the present. You can get full text free of charge.Social Science Research Network/Social Science (economic) research papers database, part of the full text.Max Planck SocietyThe German Society of Cape Planck founded 3 open access magazines:(1) Living, Reviews, in, Relativity, ISSN, 1433-8351/(2) Living, Reviews, in, Solar, Physics, ISSN, 1614-4961/(3) Living, Reviews, in, European, Governance, ISSN:,1813-856X/Networked, Computer, Science, Technical, Reference, Library (NCSTRL)/The network computer reference library, the Andrew W. Mellon foundation, combined with information network, digital library alliance, the United States National Science Foundation support,An open computer science research report and library on the internet. Provide advanced search and simple search, the original format required to download the corresponding reader software.World Bank reportThere are 27000 bank reports_____________________________The full-text database of free dissertations abroad zz, 06 2009, 03:44 p.m. on Tuesday, 09/m/user_content.aspx? Id=236806?Resource descriptionWorcester Polytechnic Institute/Pubs/ETD/Wooster Institute of Technology: including more than 670 dissertations, including more than 550 full text, master's thesis 4. Covers biology, electronics, computers, materials, physics, mechanics, and so on.The University of Nottingham/University of Nottingham papers database. Contains 131 free articles, covering medical, art, education, law, engineeringand other disciplines.Australian Digital Theses Program.auThe Australian digital papers programme was initiated by the Australian Association of University librarians. More than 40 universities and colleges in Australia, including 15440 theses, cover all subjects.University of South Florida/cgi-bin/ETD-db/ETD-...D-search/search989 electronic version because the south of University of Florida, covering geography, medicine, electronics and other disciplines. Most of them can get full text online free of charge.Virginia Commonwealth University/ETD-db/ETD-search/search768 because the Virginia public assets of University, including chemistry, biology, medicine, accounting, engineering, art, language, education and other disciplines. 614 of these articles can be obtained online free of charge.The, Pennsylvania, State, University's, electronic, Theses,and, Dissertations, Archives/ETD-db/ETD-search/searchThe proceedings of the University of Pennsylvania electronic library contains 1848 articles covering materials science, education, engineering, law, medicine, aviation, economics, chemistry, architecture, and other disciplines. Available online free of charge.North Carolina State University/ETD-db/ETD-search/search3937 free because the North Carolina State University, including chemistry, physics, electronic and electrical, nuclear energy, machinery, materials, food, forestry, soil and other disciplines.University of Pretoria: Electronic, Theses, and, DissertationsHttp://upetd.up.ac.za/Pretoria University of electronic theses, containing more than 3000 articles covering electronic doctoral, sociology, food, architecture, economy, information, education, management, biochemistry, psychology, law and other disciplines, including 2876 articles free access to full text.Ohio State University/etd/search.cgiElectronic Theses of Ohio State University. Including 12677 records, index updates in a timely manner, but also online translation into Chinese, covering mechanical, electronic, management, philosophy, chemistry, environmental science, materials, mathematics, physics and other disciplines, can be free access.University, of, Tennessee, Knoxville/cgi/b/... =etd-bib; page=indexElectronic Theses of University of Tennessee. With more than 1500 free papers, 86 branches covering science, engineering, agriculture and other disciplines.The, Institute, for, Systems, Research/ARCHIVE/Institute of systems research ISR Technical Research Report library.Nearly 3000 studies were reported from 1985 to 2007. It covers network security, mobile and network sensing, signal processing, system control, aviation management and so on.M.I.T., Theses, and, E-Theses, Online/F? Func=find-b-0?Australian .au/。
数据库复习例题

第一章一、填空题1. 数据库是长期存储在计算机内、具有__组织_____的、可以___共享______的数据集合。
2. 数据独立性是指__用户的应用程序______和__数据库中的数据_______是相互独立的。
3. 外模式是_逻辑_模式的子集。
4. 数据库的两级映象技术是指__外模式与模式之间的映象_______________和___模式与内模式之间的映象______________。
5. 数据库管理系统的主要功能包括__数据操纵功能___、____数据库定义功能___________、数据库建立和维护功能及数据库的运行管理6. 当数据的物理存储改变时,应用程序不变,而由DBMS处理这种改变,这是指数据的___物理独立性_____________。
7. 以子模式为框架的数据库是__用户数据库___________;以模式为框架的数据库是_概念数据库_________;以物理模式为框架的数据库是___物理数据库__________。
二、选择题1. 模式和内模式〔A〕A、只能有一个B、最多只能有一个C、至少两个D、可以有多个2. 数据库技术采用分级方法将数据库的构造划分成多个层次,是为了提高数据库的〔B〕A、数据标准性和数据独立性B、逻辑独立性和物理独立性C、管理标准性和物理独立性D、数据的共享和数据独立性3. 在数据管理技术的开展过程中,经历了人工管理阶段、文件系统阶段和数据库系统阶段。
在这几个阶段中,数据独立性最高的是哪一阶段〔A〕A、数据库系统B、文件系统C、人工管理D、数据项管理4. 下述关于数据库系统的正确表达是〔B〕A、数据库中只存在数据项之间的联系B、数据库的数据项之间和记录之间都存在联系C、数据库的数据项之间无联系,记录之间存在联系D、数据库的数据项之间和记录之间都不存在联系5. 在数据库系统中,通常用三级模式来描述数据库,其中〔B〕是对数据的整个的逻辑构造的描述。
A、外模式B、逻辑模式C、内模式D、逻辑构造6. 数据库的三级模式之间存在的映象关系正确的选项是〔B〕A、外模式/内模式B、外模式/模式C、外模式/外模式D、模式/模式7. 在数据库中存储的是〔C〕A、数据B、数据模型C、数据及数据间的联系D、信息8. 下面哪个不是数据库系统必须提供的数据控制功能(B).A.平安性B.可移植性C.完整性D.并发控制9. DBMS提供的DML有两种使用方式,其中一种是将DML嵌入到某一高级语言中,此高级语言称为〔B〕A、查询语言B、宿主语言C、自含语言D、会话语言10. 对于数据库系统,负责定义数据库内容,决定存储构造和存取策略及平安性授权工作的是〔C〕A、应用程序开发人员B、终端用户C、数据库管理员D、数据库管理系统的软件设计人员三、简答题1. 数据有哪些特征(4分)?数据有型与值之分、数据受数据类型和取值范围的约束、数据有定性表示和定量表示之分、数据应具有载体和多种表现形式。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
第12章数据库应用结构与数据访问接口
•12.1 数据库应用结构
•12.2 数据访问接口
12.1 数据库应用结构
•12.1.1 集中式应用结构•12.1.2 文件服务器结构•12.1.3 客户/服务器结构•12.1.4 互联网应用结构
数据库应用结构•集中式应用结构
应用程序数据库大型机
按键信息
终端字符
终端1
终端N
终端2
客户端
图12-1大型机结构的数据库访问
数据库应用结构
•文件服务器结构
应用程序
数据库
网络文件服务器
文件
文件请求
工作站1工作站N
工作站2
客户端
图12-2 文件服务器结构的数据库访问
应用程序应用程序
数据库应用结构
•客户/服务器结构
应用程序数据库
服务器
请求结果
工作站1工作站N
工作站2
客户端
图12-3 客户/服务器结构的数据库访问
应用程序
应用程序
数据库应用结构
•互联网应用结构
客户端
应用程序
数据库
数据库服务器
请求
页面
个人机1个人机N
个人机2图12-4互联网计算环境下的数据库访问
请求
结果
Web 服务器
浏览器
浏览器浏览器
12.2 数据访问接口
•12.2.1 ODBC
•12.2.2 OLE DB和ADO
•12.2.3 ADO为OLE DB带来了什么?
数据访问接口
•ODBC
1.ODBC提出的背景
在ODBC概念提出之前,应用程序访问数据库时是使用数据库系统提供的专用接口来进行开发。
一个专用接口只能访问一种类型的数据库,不同的数据库管理系统提供的接口是各不相同的,因此,在一个数据库应用程序中很难同时访问多个不同数据库管理系统中的数据,而这在实际应用中通常是需要的。
数据访问接口
•ODBC(开放数据库互连,Open DataBase Connectivity)是Microsoft公司开发的一套开放的数据库系统应用程序接口规范,它为应用程序提供了一套高层调用接口规范和基于动态链接库的运行支撑环境。
这样就使数据库应用程序具有很好的适应性和可移植性,并且具备同时访问多种数据库管理系统的能力。
•ODBC驱动程序有些类似于Windows下的打印机驱动程序,对用户来说,驱动程序屏蔽掉了不同对象间的差异,使用ODBC编写的数据库应用程序就像Windows下的打印程序能够在不同的打印机上打印一样,可以运行于不同的数据库环境下。
数据访问接口
DBMS1.SQL(专用)
DBMSm.SQL(专用)
…ODBC AP1
ODBC APn
ODBC ODBC API Driver
DBMS 1DBMS m
DB1DBm
ODBC.SQL(通用)
驱动程序管理器
SQL Server
驱动程序Oracle 驱动程序
SQL Server 数据源Oracle 数据源
图12-5 ODBC 体系结构
数据访问接口
3.建立ODBC数据源
可以通过Windows的控制面板建立ODBC数据源。
建立步骤为:
(1)打开控制面板。
如果使用的是Windows98,则直接双击控制面板上的“ODBC数据源”;如果使用的是Windows2000,则双击控制面板上的“管理工具”,然后再双击管理工具上的“数据源(ODBC)”。
打开“ODBC数据源管理器”窗口。
(2)ODBC数据源共有三种类型:用户数据源(用户DSN),系统数据源(系统DSN)和文件数据源(文件DSN)。
数据访问接口
•OLE DB和ADO
人们所采用的信息管理系统多种多样,有文件系统、数据库系统等,它们的数据格式也各不相同,有文本格式、电子表格格式及在Internet上使用的电子邮件格式和HTML格式等。
这就意味着如果要同时访问这些不同管理系统中的数据就必须使用多种数据访问方法,为此,Microsoft提出了一致的数据访问(Universal Data Access)策略,此策略是在广泛的不同应用程序(从传统的C/S到Web)中保证开放和集成,并提供对所有的数据类型(关系的和非关系的,甚至是非结构的)的基于标准的访问方法。
数据访问接口
一致的数据访问策略是基于OLE DB(Object Linked and Embed Database)来访问所有类型的数据,并通过ADO(ActiveX Data Object)来提供应用程序开发者使用的编程模型。
数据访问接口
OLE DB定义了三种类型的数据访问组件:
l数据提供者:包含数据并将数据输出到其他组件中去。
l数据消费者:使用包含在数据提供者中的数据。
l服务组件:处理和传输数据。
例如,如果使用OLE DB访问SQL Server数据,并且是用C++显示获得的数据,则SQL Server就是数据提供者,C++的接口应用程序就是数据的消费者,临时表引擎中保留的一系列记录就是一个服务组件。
数据访问接口一致的数据访问策略的体系结构前端应用程序ADO
OLE DB
提供者
提供者提供者提供者
VSAM/ISAM E-mail 消息目录服务ODBC
提供者文件系统关系数
据库
数据访问接口
ADO 对象模型Connection Error
Command Parameter
Recordset
Field
Property
Property
Property
Property
数据访问接口
l Connection对象:包含了与数据源连接的信息。
l Command对象:包含了与一个命令相关的信息。
l Recordset对象:包含了从数据源得到的记录集。
l Field对象:包含了记录集中的某个记录的字段信息。
l Property对象:ADO对象的属性。
l Parameter对象:与命令对象相关的参数。
l Error对象:包含了由数据源产生的Errors集合中的扩展的错误信息。
由于一个单独的语句会产生一个和多个错误,因此Errors集合可以同时包括一个和多个Error对象。
小结
到目前为止,数据库的应用结构经历了四种变化,从最开始的集中式,到文件服务器方式,再到现在应用范围非常广泛的客户/服务器方式,最终到目前日益兴起的互联网方式的多层结构,每一种结构的变化都更加合理地均衡了客户端和服务器端的处理逻辑和负载。
数据库应用结构是由数据库管理系统对数据的处理方式决定的,而不是由操作系统和硬件结构决定的。
数据库的数据访问接口分为专用接口和通用接口两种。
专用接口是每个数据库管理系统自己提供的专门用于访问自己的数据的接口,通用接口的思想是由Microsoft提出的,通过这些通用接口,用户可以访问不同的数据库管理系统,而不必再关心这些接口之间的差异,这极大的简化和方便了用户对数据库的访问。
通用接口中常用的有ODBC和OLE DB两种。
ADO是建立在OLE DB基础之上的高层封装,其目的是为了简化用户使用OLE DB低层接口时访问数据库的复杂性。
