rfc3149.MGCP Business Phone Packages
imap rfc标准

Internet Message Access Protocol (IMAP) is an email retrieval protocol. It stores email messages on a mail server and enables the recipient to view and manipulate them as though they were stored locally on their device. IMAP was developed in the late 1980s and has since become one of the most widely used email retrieval protocols.The IMAP standard is defined in RFC 3501, which was published in 2003. This document provides a detailed description of the protocol's functionality, including its data formats, commands, and responses. The standard specifies how IMAP clients and servers should communicate with each other to enable the retrieval and manipulation of email messages.One of the key features of IMAP is its support for multiple clients accessing the same mailbox simultaneously. This is achieved through the use of a "shared" storage model, where all clients see the same set of messages and folders stored on the server. This allows users to access their email from different devices without having to worry about synchronizing their messages manually.Another important aspect of IMAP is its support for message organization and management. Clients can create, delete, and rename folders, as well as move messages between folders. They can also search for specific messages based on various criteria, such as sender, subject, or date.IMAP also provides a range of features for managing individual messages. Clients can mark messages as read or unread, flag them for follow-up, and even move them to a specific folder. They can also reply to messages, forward them to others, and generate replies or forwards with attachments.Overall, the IMAP standard provides a powerful and flexible framework for managing email messages. Its support for shared storage, message organization, and advanced message management features make it a popular choice for both personal and business email users.。
EIS功能配置说明

EIS 系统功能配置说明(仅供内部使用)文 档 作 者: ______________ 日期:____/____/____ 开发/测试经理: ______________ 日期:____/____/____ 产 品 经 理: ______________ 日期:____/____/____ 文 档 管 理 办: ______________日期:____/____/____深圳市众方信息科技有限公司版权所有 不得复制深圳市众方信息科技有限公司产品名称 产品版本密级EIS内部公开 文档编号:共 38 页修订记录目录1引言 (5)2升级 (5)2.1平台升级说明 (5)2.1.1升级 (5)2.1.2备份数据库 (6)2.2终端升级说明 (6)2.2.1通过平台升级终端 (6)2.2.2在终端上直接升级 (7)2.2.3通过provision加载 (7)3功能配置和查看 (7)3.1平台功能配置 (7)3.1.1更改IP地址 (7)3.1.2Freelink配置 (9)3.1.3修改MGCPSIP注册端口 (9)3.1.4pra配置 (9)3.1.5SIP中继配置 (10)3.1.6呼出呼入路由配置 (11)3.1.7计费服务器配置 (12)3.1.8全局O口配置方法 (12)3.1.9号码替换配置 (12)3.1.10RS路由配置(业务不对外) (12)3.1.11H323配置 (15)3.1.12标准中继对接 (16)3.1.13虚拟业务配置 (16)3.1.14虚拟小交业务配置 (26)3.1.15P2P配置(功能不对外) (26)3.1.16计费管理(半实时计费) (27)3.1.17ADA常用命令 (28)3.1.18信息查看 (31)3.1.19数据库操作命令 (32)3.2终端配置 (33)3.2.1注册配置 (33)3.2.2路由配置 (36)4问题定位跟踪 (36)4.1.1cc跟踪 (36)4.1.2sip跟踪 (37)4.1.3计费跟踪 (37)4.1.4mgcp跟踪 (37)4.1.5H323跟踪 (38)4.1.6pra跟踪 (38)4.1.7新信令跟踪(trace) (38)4.1.8版本单通定位手段(适用于EIGA和EIGB) (38)5其它 (38)EIS系统功能配置说明1引言此文档主要是针对现在EIS系列产品的功能使用的说明书,阐述了如何对平台和终端进行升级、配置和问题定位。
consul rpc error making call eof

consul rpc error making call eof
1. **网络问题**:网络连接不稳定或中断可能导致 RPC 调用失败。
确保 Consul 节点之间的网络连接正常,可以尝试通过 `ping` 命令测试网络连通性。
2. ** consul agent 未运行**:Consul 的 `agent` 是在 Consul 集群的每个成员上长期运行的守护进程,通过命令 `consul agent` 启动运行。
请确保所有节点上的 `agent` 都在运行。
3. **证书问题**:如果 Consul 使用了 TLS 证书进行安全服务通信,但证书配置不正确或过期,可能会导致 RPC 调用错误。
请确保证书有效并正确配置。
4. **服务注册问题**:如果服务没有正确注册或发现,可能会导致 RPC 调用错误。
确保服务在 Consul 中正确注册,并能够被发现。
5. ** consul 配置问题**:Consul 的配置不正确也可能导致 RPC 调用错误。
请检查Consul 的配置文件(如 `consul.json`),确保配置正确。
6. **资源限制**:如果 Consul 节点的资源(如内存、CPU 等)使用过高,可能会导致 RPC 调用错误。
可以监控节点的资源使用情况,并根据需要进行调整。
如果以上方法都不能解决问题,建议查看 Consul 的日志文件以获取更详细的错误信息,从而更好地了解问题所在,并采取相应的措施解决问题。
学习网络常用的RFC文档的名称

学习网络常用的RFC文档的名称双语RFC --RFC中英文对照版rfc1050中文版-远程过程调用协议规范rfc1055中文版-在串行线路上传输IP数据报的非标准协议rfc1057中文版-RFC:远程过程调用协议说明第二版rfc1058中文版-路由信息协议(Routing Information Protocol)rfc1073中文版-RFC1073 Telnet窗口尺寸选项rfc1075中文版-远距离矢量多播选路协议rfc1088中文版-在NetBIOS网络上传输IP数据报的标准rfc1090中文版-SMTP在X.25上rfc1091中文版-TELNET终端类型选项rfc1094中文版-RFC1094 网络文件系统协议rfc1096中文版-Telnet X显示定位选项rfc1097中文版-Telnet潜意识-信息选项rfc1112中文版-主机扩展用于IP多点传送rfc1113中文版-Internet电子邮件保密增强:Part1-消息编码和鉴别过程rfc1132中文版-802.2分组在IPX网络上传输的标准rfc1144中文版-低速串行链路上的TCP/IP头部压缩rfc1155中文版-基于TCP/IP网络的管理结构和标记rfc1191中文版-RFC1191 路径MTU发现rfc1332中文版-RFC1332 端对端协议网间协议控制协议(IPCP)rfc1333中文版-PPP 链路质量监控rfc1334中文版-PPP 身份验证协议rfc1387中文版-RIP(版本2)协议分析rfc1388中文版-RIP协议版本2rfc1433中文版-直接ARPrfc1445中文版-SNMPv2的管理模型rfc1582中文版-扩展RIP以支持按需链路rfc1618中文版-ISDN上的PPP(点对点)协议rfc1661中文版-RFC1661 PPP协议rfc1723中文版-路由信息协议(版本2)rfc1738中文版-统一资源定位器(URL)rfc1769中文版-简单网络时间协议( SNTP)rfc1771中文版-边界网关协议版本4(BGP-4)rfc1827中文版-IP封装安全载荷(ESP)rfc1883中文版-Internet协议,版本6(IPv6)说明书rfc1939中文版-POP3协议rfc1945中文版-超文本传输协议 -- HTTP/1.0rfc1994中文版-PPP挑战握手认证协议(CHAP)rfc1997中文版-RFC1997 BGP团体属性rfc2002中文版-IP移动性支持rfc204中文版-利用报路rfc2105中文版-Cisco 系统的标签交换体系结构纵览rfc2281中文版-Cisco热备份路由协议()rfc2283中文版-BGP-4的多协议扩展rfc2326中文版-实时流协议(RTSP)rfc2328中文版-OSPF版本2rfc2516中文版-在以太网上传输PPP的方法(PPPoE)rfc2526中文版-IPv6保留的子网任意传送地址rfc2547中文版-BGP/MPLS VPNsrfc2616中文版-超文本传输协议——HTTP/1.1rfc2702中文版-基于MPLS的流量工程要求rfc2706中文版-RFC2706—电子商务域名标准rfc2756中文版-超文本缓存协议(HTCP/0.0)rfc2764中文版-IP VPN的框架体系rfc2773中文版-使用KEA和SKIPJACK加密rfc2774中文版-HTTP扩展框架rfc2781中文版-UTF-16, 一种ISO 10646的编码方式rfc2784中文版-通用路由封装rfc2793中文版-用于文本交谈的RTP负载rfc2796中文版-BGP路由反射rfc2917中文版-核心 MPLSIP VPN 体系结构rfc2918中文版-BGP-4(边界网关协议)的路由刷新功能rfc2923中文版-TCP的路径MTU发现问题rfc3003中文版-Audio/mpeg 媒体类型rfc3005中文版-IETF 讨论列表许可证rfc3007中文版-安全的域名系统动态更新rfc3018中文版-统一内存空间协议规范rfc3022中文版-传统IP网络地址转换(传统NAT)rfc3032中文版-RFC3032 MPLS标记栈编码rfc3033中文版-用于Internet协议的信息域和协议标识符在Q.2941类属标识符和Q.2957 User-to-user信令中的分配rfc3034中文版-标签转换在帧中继网络说明书中的使用rfc3037中文版-RFC3037 标记分配协议的适用范围(RFC3037 LDP Applicability)rfc3058中文版-IDEA加密算法在CMS上的使用rfc3059中文版-服务定位协议的属性列表扩展rfc3061中文版-对象标识符的一种URN姓名空间rfc3062中文版-LDAP口令修改扩展操作rfc3063中文版-MPLS(多协议标签交换)环路预防机制rfc3066中文版-语言鉴定标签rfc3067中文版-事件对象描述和转换格式要求rfc3069中文版-VLAN聚合实现IP地址有效分配rfc3070中文版-基于帧中继的第二层隧道协议rfc3072中文版-结构化数据交换格式rfc3074中文版-DHCP 负载平衡算法rfc3078中文版-RFC3078微软点到点加密(MPPE)协议rfc3081中文版-将区块扩展交换协议(BEEP)核心映射到传输控制协议(TCP)rfc3083中文版-遵循DOCSIS的Cable Modem和CMTS的PBI 的管理信息数据库rfc3085中文版-新闻型标记语言(NewsML)资源的URN名字空间rfc3090中文版-域名系统在区域状况下的安全扩展声明rfc3091中文版-Pi数字生成协议rfc3093中文版-防火墙增强协议rfc3550中文版-RTP:实时应用程序传输协议rfc457中文版-TIPUGrfc697中文版-FTP的CWD命令rfc698中文版-TELNET扩展ASCII选项rfc775中文版-面向目录的 FTP 命令rfc779中文版-TELNET的SEND-LOCATION选项rfc792中文版-RFC792- Internet控制信息协议(ICMP)rfc821中文版-RFC821 简单邮件传输协议(SMTP)rfc826中文版-以太网地址转换协议或转换网络协议地址为48比特以太网地址用于在以太网硬件上传输rfc854中文版-TELNET协议规范rfc855中文版-TELNET选项规范rfc856中文版-RFC856 TELNET二进制传输rfc857中文版-RFC 857 TELNET ECHO选项rfc858中文版-RFC 858 TELNET SUPPRESS GO AHEAD选项rfc859中文版-RFC 859 TELNET的STATUS选项rfc860中文版-RFC 860 TELNET TIMING MARK选项rfc861中文版-RFC 861 TELNET扩展选项-LISTrfc862中文版-RFC 862 Echo 协议rfc868中文版-RFC868 时间协议rfc894中文版-IP 数据包通过以太网网络传输标准rfc903中文版-反向地址转换协议rfc930中文版-Telnet终端类型选项(RFC930——T elnet Terminal Type Option)rfc932中文版-子网地址分配方案rfc937中文版-邮局协议 (版本2)rfc948中文版-IP数据报通过IEEE802.3网络传输的两种方法rfc949中文版-FTP 未公开的独特命令rfc951中文版-引导协议(BOOTP)rfc962中文版-TCP-4 的最初rfc974中文版-邮件路由与域名系统rfc975中文版-自治联邦。
rfc 1421标准 -回复

rfc 1421标准-回复rfc 1421标准是关于加密通信协议的一项RFC(Request for Comments,即请求评论)标准。
该标准定义了一种简单的加密连接协议,用于保护网络通信中的敏感数据。
本文将一步一步地回答关于rfc 1421标准的问题。
第一步:了解rfc 1421标准的背景和意义rfc 1421标准是由互联网工程任务组(IETF)于1993年发布的。
当时,互联网开始大规模发展,网络安全问题也越来越突出。
为了保护通信过程中敏感信息的安全性,需要采用一种有效且经过验证的加密通信协议。
rfc 1421标准的出现填补了这一需求。
第二步:了解rfc 1421标准的基本原理和概念rfc 1421标准基于加密算法和公钥基础设施(PKI),旨在建立安全的通信连接。
它使用了一种称为“加密消息语法”(CMS)的数据格式来对敏感数据进行编码和解码。
CMS通过利用公钥和私钥对数据进行加密和解密,确保通信内容的机密性。
第三步:掌握rfc 1421标准的主要特征和功能rfc 1421标准提供了一套完整的加密通信方案,包括数字签名、数据完整性验证和消息机密性。
它允许发送者使用公钥对数据进行加密,并使用私钥对接收者进行身份验证。
同时,还支持对消息进行数字签名,确保数据的完整性和真实性。
第四步:学习rfc 1421标准的具体应用和实现方式根据rfc 1421标准,加密通信协议可以在各个网络层次中实现,例如运输层安全协议(TLS)和安全套接字层(SSL)。
同时,它还提供了一些基本的加密算法和协议,例如RSA、Diffie-Hellman和MD5。
第五步:了解rfc 1421标准的发展和衍生版本随着时间的推移,rfc 1421标准也得到了不断改进和扩展。
RFC 2311、RFC 2312和RFC 2630等相关标准对其中的一些缺陷进行了修复,并提出了新的建议和要求。
这些改进使rfc 1421标准在实际应用中更加可靠和安全。
RFC技术介绍

1使用RFC的意义RFC是实现接口的主要方式之一,不但是一种函数,更是一种数据通信协议,类TCP/IP。
RFC不仅是一个函数,也是一个数据通信协议,SAP显然是吃定大集团的管理应用,在大集团通常分散了若干Sap应用,可通过RFC协议进行连接,Tcode:SM59 ,典型应用在如下的几个方面:(1)MDM:总部MDM做整个集团的主数据编码规划,通过XI+RFC连接自动分发到各分散服务器。
(2)BI数据仓库系统通过RFC从分散的R/3应用服务器中抽取数据,做报表分析和数据挖掘。
(3)SLM(SoLution Management),SLM通过RFC连接各企业,在SLM统一登录,R/3那边设置好RFC用户可自动登录,当然SLM还提供了完善的问题处理流程跟踪。
2 SAP RFC几种模式(1)sRFC(synchronous RFC)是RFC的第一个版本,它要求连接的双方是同步的工作方式,即都是在可用状态才能够实现成功调用。
(2)aRFC(asynchronous RFC)这种RFC可以实现异步的RFC调用方式,它可以进行多个并发调用,并且不要求被调用系统的可用状态。
发出调用系统会一直尝试直到获得被调用系统的应答。
它通常用于当你需要提高系统并行调用多个RFC的效率,相对于强制等待程序的结果,它的效率更高。
(3)tRFC(transactional RFC)是对aRFC进行相关技术改进后的一个RFC版本,其于ARFC相同点是实现异步调用,其优点是可以将多个调用进行LUW分组处理,并只执行一次运行。
现在aRFC基本上已经停用。
(4)qRFC(queue(d) RFC)是tRFC的一个增强版本,它保证了所传输数据的处理次序。
(5)pRFC(Parallel RFC)是一种特殊的RFC,它是aRFC的一种扩展类型。
因为它改善了系统的性能,在执行大量的aRFC时。
SAP 使用它在MRP里面提高速度。
但是它只能执行在同一个系统和同一个client里。
IPMSG飞鸽传书
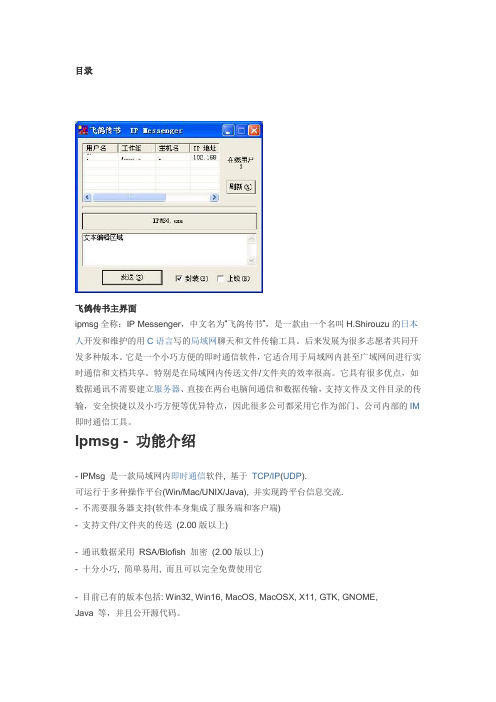
目录飞鸽传书主界面ipmsg全称:IP Messenger,中文名为“飞鸽传书”,是一款由一个名叫H.Shirouzu的日本人开发和维护的用C语言写的局域网聊天和文件传输工具。
后来发展为很多志愿者共同开发多种版本。
它是一个小巧方便的即时通信软件,它适合用于局域网内甚至广域网间进行实时通信和文档共享。
特别是在局域网内传送文件/文件夹的效率很高。
它具有很多优点,如数据通讯不需要建立服务器、直接在两台电脑间通信和数据传输,支持文件及文件目录的传输,安全快捷以及小巧方便等优异特点,因此很多公司都采用它作为部门、公司内部的IM 即时通信工具。
Ipmsg - 功能介绍- IPMsg 是一款局域网内即时通信软件, 基于TCP/IP(UDP).可运行于多种操作平台(Win/Mac/UNIX/Java), 并实现跨平台信息交流.- 不需要服务器支持(软件本身集成了服务端和客户端)- 支持文件/文件夹的传送(2.00版以上)- 通讯数据采用RSA/Blofish 加密(2.00版以上)- 十分小巧, 简单易用, 而且可以完全免费使用它- 目前已有的版本包括: Win32, Win16, MacOS, MacOSX, X11, GTK, GNOME,Java 等,并且公开源代码。
Ipmsg - 源码简介IP Messenger在程序结构方面采用了Windows SDK处理结构,通信方面采用了TCP/UDP通信方式,在文件传输处理方面采用文件映射技术,等等。
通过分析IP Messenger 的运行、工作原理,可以提高并加深对Windows处理流程的理解,提高SOCKET编程技术等,因此特对其源码进行分析,以抛砖引玉,共同提高大家的编程技术。
1、IP Messenger源代码的下载在写这篇文章时,IP Messenger的最新版本是2.06,因此大家在下载时尽量选择最新版本下载。
IP Messenger源代码的下载地址是/,在网站的右上角,点击English page,网站转换到英文界面,网站有英文版以及其它语言的版本,当然还有中文版的链接(/IPMsg/),建议大家尽量下载原版的英文版源代码,以利于学习。
rfc相关设置及使用

rfc相关设置及使用RFC(Request for Comments)是一种用于定义互联网协议、标准和相关问题的文档。
RFC的格式由互联网工程任务组(IETF)统一规定,它们记录了网络技术的发展和演进过程。
在本文中,我们将介绍RFC相关的设置和使用。
1. 了解RFC的作用和历史:RFC是由IETF组织制定的一种标准化文档,它记录了互联网协议的设计、开发和演化过程。
RFC起源于20世纪60年代的ARPANET,是一种社区驱动的文档,通过共享和讨论来推动互联网技术的发展。
RFC文档旨在提供指南、建议和最佳实践,帮助网络技术人员解决问题。
2. 寻找和阅读RFC文档:RFC文档可以在互联网上免费获取,IETF的官方网站和其他资源库都有存档。
这些文档按照顺序编号,并且以RFC开头,比如RFC 791定义了IPv4协议。
通过搜索引擎或在IETF网站上使用关键词搜索,可以找到特定主题的RFC文档。
阅读RFC文档时,应该注意文档的状态,有一些可能已经被更新或废弃。
3. 使用RFC文档:RFC文档在网络技术的发展过程中起着重要的指导作用。
它们提供了协议规范、算法实现、安全性和隐私等方面的建议。
网络管理员、网络工程师和开发人员可以使用RFC文档来了解和理解特定协议或标准的设计原理和要求。
此外,RFC文档还常用于进行互联网协议的实现、编程和配置。
4. 参与RFC的制定过程:RFC并不是静止的文件,而是一个持续演进的过程。
任何人都可以参与到RFC的制定过程中。
要参与RFC的制定,可以加入IETF并参与相关的工作组或邮件列表。
通过这种方式,个人可以提出改进建议,参与讨论和标准化的制定。
5. 遵循RFC的指导原则:在网络技术领域,遵循RFC的指导原则是至关重要的。
这些指导原则包括设计原则、协议分层、安全性和互操作性等要求。
遵循RFC的指导原则可以确保网络协议的正确性、稳定性和可靠性,同时也可以促进网络技术的发展和创新。
总结起来,RFC在互联网技术领域起着重要的作用,它们记录了互联网协议的发展历程和指导原则。
rfc 3174标准

rfc 3174标准RFC 3174标准介绍RFC(Request for Comments)3174是一项用于计算机网络中数据完整性校验的标准。
该标准定义了一种安全散列算法,即SHA-1(Secure Hash Algorithm 1)算法,用于验证数据在传输过程中是否被篡改。
SHA-1算法是美国国家安全局(NSA)设计的一种加密散列函数。
它将任意大小的数据块映射为一个固定长度的哈希值,通常为160位。
哈希值是一个数字指纹,用于唯一标识原始数据。
SHA-1算法使用了一系列复杂的位操作和逻辑函数来执行数据转换,以确保数据和哈希值之间的关联性。
RFC 3174标准的主要目的是提供一种机制来验证数据的完整性,以解决数据篡改的问题。
在现代互联网中,数据传输时存在被黑客篡改的风险。
如果数据在传输过程中被篡改,接收方将无法确定数据是否真实,从而产生安全隐患。
通过使用SHA-1算法,发送方可以将数据进行哈希运算并生成哈希值,然后将哈希值附加到数据中一起传输。
接收方可以使用相同的算法对接收到的数据进行计算,并将计算出的哈希值与附加的哈希值进行比较。
如果两个哈希值匹配,即可确认数据的完整性,并且可以安全地使用接收到的数据。
SHA-1算法具有以下特点,使其成为数据完整性校验的理想选择:1. 不可逆性:SHA-1算法将数据转换为固定长度的哈希值,不同的数据将生成不同的哈希值。
但是,无法通过哈希值推导出原始数据,使得黑客无法从哈希值中了解任何有关原始数据的信息。
2. 高度敏感性:SHA-1算法对数据的任何改动都会导致不同的哈希值。
即使是对原始数据进行微小的修改,也会显著改变哈希值,从而保证了数据完整性的检测。
3. 速度较快:SHA-1算法的计算速度较快,适用于大规模数据的处理。
这样可以确保数据的完整性校验不会成为传输过程中的瓶颈。
尽管SHA-1算法在数据完整性校验方面表现出色,但是随着计算能力的增强和密码破解技术的不断发展,SHA-1算法已经不再被认为是安全的加密散列函数。
RFC逻辑定律

RFC逻辑定律SAP 高级应用开发 - RFCRFC Remote function Call 远程功能调用, 是SAP系统之间以及非SAP系统之间程序通信的基本接口技术. 例如BAPI , ALE都是基于RFC实现的RFC连接类型:1.类型2: R/2连接2.类型3: ABAP连接或R/3连接,指定主机名和通信服务3.类型I:内部连接,与当前系统连接到同一ABAP系统中,预定义无法修改,与SM51中所显示的应用服务器名相同4.类型L:逻辑目标,通常工作流系统指定过程中配置的RFC目标即为该类型的逻辑目标5.类型X:指定安装了特殊的ABAP设备驱动程序的系统,必须制定ABAP设备驱动程序名6.类型S:通过SNA或APPC启动的外部程序连接7.类型M:通过CMC到ABAP系统的异步RFC连接8.类型T:通过TCP/IP并使用RFC库或SAP连接器的外部程序连接;分为启动(指定主机名、程序路径名)和注册(RFC服务器程序)两种连接模式。
9.类型G:定义外部系统到本地HTTP连接10.类型H:定义ABAP系统到本地的HTTP连接远程调用RFM:1.远程目标可以是文字或变量,其值为SAP系统中一直的远程目标系统。
2.若远程系统是当前系统中的SAP应用服务器,也可以直接指定应用服务器名称,则SM59中的I类型目标3.SM59定义的RFC目标是区分大小写的。
DESTINATION附加项中目标变量的值必须与其完全一致通过CALL FUNCTION语句进行远程功能调用时,可形成不同的调用模式:1. CALL FUNCTION DESTINATION 以同步RFC方式实现RFM 调用,若后面无其他附加项,则形成同步RFC调用,调用程序等待远程调用结果以继续执行2. CALL FUNCTION STARTING NEW TASK 以异步RFC方式实现RFM调用,调用程序不等待远程调用结果继续执行,结果将在回调子程序(callback subroutine)中接收3. CALL FUNCTION IN BACKROUND TASK 以事务性RFC方式实现RFM调用,远程功能暂不开始执行,等待COMMIT WORK 语句出现时,一次性执行一个或多个远程功能远程功能调用时,仅允许通过值传递参数,不能进行引用传递,因为在RFC过程中,可以传递参数,并返回结果,但不能改变调用程序的上下文对表类型参数,在本地普通功能调用中默认为引用传递,不需要创建内表的本地副本,但RFC不支持引用传递机制,将进行隐式的值传递调用,必须在RFC客户和RFC服务器之间交换整个表,只传输实际表格,如果没有指定表参数,则在被调用功能中使用空表RFC 创建连接类型时:1.LOAD BALANCING选择NO:指定TARGET HOST,SYSTEM NUMBER2. LOAD BALANCING选择YES,要指定TARGET SYSTEM (SM51),MESSAGE SERVER(RZ03),GROUP(SMLG)除去SM59定义的远程目标之外,SAP提供两个预定义目标,可以再CALL FUNCTION 语句的DESTINATION附加附件中使用:l目标NONE,将运行当前程序的应用服务器作为目标系统,调用过程将通过RFC接口实现,并拥有RFC上下文,应用于任意调用类型l目标BACK,用于被远程调用的RFM内部的CALL FUNCTION 语句中的目标制定,通过已建立的RFC连接反过来调用该模块的调用者或已载入的其他功能模块SAP ABAP 系统间的RFC实现(通过RFM实现)远程调用RFM:1.远程目标可以是文字或变量,其值为SAP系统中一直的远程目标系统。
5g短信messageid生成规则 -回复

5g短信messageid生成规则-回复1. 使用时间戳:将当前时间转换为毫秒数作为MessageID的一部分,确保唯一性。
2. 结合设备ID:在时间戳的基础上,添加设备ID,以确保不同设备生成的MessageID不同。
3. 添加序列号:使用一个自增的序列号作为MessageID的一部分,以保证在同一设备下,每条短信生成的MessageID都是唯一的。
4. 引入随机数:添加一个随机数作为MessageID的一部分,以增加生成的MessageID的随机性和唯一性。
5. 添加业务标识:在MessageID中加入一些业务相关的标识,如用户ID 或业务类型,以便后续处理和查询。
6. 使用分段编码:将MessageID分成几个部分,每个部分使用特定的编码方式,如Base64、MD5等,在生成时进行拼接,以便在后续处理中能够解析出各个部分的含义。
7. 结合用户手机号:将用户手机号作为MessageID的一部分,确保同一手机号生成的MessageID不同,方便后续按照手机号进行查询和处理。
8. 添加运营商标识:在MessageID中添加运营商的标识,以便后续查询和统计不同运营商的短信发送情况。
9. 使用哈希算法:对一些特定的信息(如设备ID、手机号等)进行哈希运算,生成一个固定长度的哈希值作为MessageID的一部分,保证唯一性和随机性。
10. 结合地区编码:在MessageID中加入地区编码,以便后续根据地区进行分析和查询。
11. 添加消息类型标识:在MessageID中添加消息的类型标识,如短信、彩信、语音等,方便后续根据类型进行分类和处理。
12. 使用CRC校验码:对一些特定的信息进行CRC校验生成一个固定长度的校验码作为MessageID的一部分,以确保消息的完整性和唯一性。
13. 添加业务流水号:将业务流水号作为MessageID的一部分,确保同一业务的相关消息生成的MessageID是唯一的。
14. 引入分布式ID生成算法:使用分布式ID生成算法,如Snowflake 算法,生成全局唯一的ID作为MessageID,确保全局唯一性。
mosh协议对应的rfc

mosh协议对应的rfcEnglish Response:The Mosh (Mobile Shell) protocol is an open networking protocol designed for interactive remote terminal sessions over unreliable networks. It is a more modern alternative to SSH, offering several advantages such as:No need for a persistent connection: Mosh establishes a persistent connection between the client and server, but it does not require a constant network connection. This means that the session can survive temporary network outages without losing any data.Low latency: Mosh uses a prediction algorithm to reduce latency, making it ideal for even high-latency connections.Encryption: Mosh supports encryption to protect the data transmitted between the client and server.The Mosh protocol is still under development, but it has been actively maintained since 2010. It is available as a free and open-source software package for Windows, macOS, Linux, and other platforms.The main RFCs related to the Mosh protocol are:RFC 8329: Mosh: An Encrypted Remote Shell Protocol.RFC 8330: Mosh: A Server for the Mosh Encrypted Remote Shell Protocol.Chinese Response:Mosh(Mobile Shell)协议是一种开放的网络协议,专为通过不可靠网络进行交互式远程终端会话而设计。
rfc相关设置及使用

rfc相关设置及使用摘要:一、RFC简介1.RFC的含义2.RFC的作用二、RFC相关设置1.RFC文件的存放位置2.RFC文件的命名规则3.RFC文件的权限设置三、RFC的使用方法1.RFC文件的查看2.RFC文件的编辑3.RFC文件的导入导出四、RFC的高级应用1.RFC模板的使用2.RFC文件的版本控制3.RFC与其他软件的协同工作正文:RFC(Request for Comments)是一种广泛应用于计算机领域的文档格式,它主要用于记录和共享各种计算机网络协议和技术规范。
作为一个重要的知识库,RFC对于网络工程师、程序员等IT从业者来说具有很高的参考价值。
本文将为您详细介绍RFC的相关设置及使用方法。
首先,我们需要了解RFC的基本概念。
RFC(Request for Comments)意为“请求评论”,是一种用于记录和共享计算机网络协议和技术规范的文档格式。
它起源于20世纪60年代的美国,如今已成为互联网领域最重要的知识库之一。
RFC文件通常由网络工程师、程序员等IT从业者编写,并经过专家评审和公开讨论,以确保其内容的准确性和可靠性。
接下来,我们来了解RFC相关设置。
RFC文件的存放位置通常在系统的“/etc/rfc”目录下。
文件的命名规则一般采用“RFC”加数字的形式,如“RFC1925”。
此外,文件的权限设置也很重要,一般来说,RFC文件应具有可读、可写和可执行的权限,以便于用户查看、编辑和执行。
在了解RFC的相关设置后,我们来学习RFC的使用方法。
首先,可以通过命令行或图形界面查看RFC文件的内容。
编辑RFC文件时,可以使用文本编辑器或专门的RFC编辑工具。
此外,RFC文件还可以导入导出,方便与其他软件协同工作。
在掌握RFC的基本使用方法后,我们可以进一步探索RFC的高级应用。
RFC模板可以帮助用户快速创建和编辑RFC文件。
此外,RFC文件还支持版本控制,可以方便地追踪文件的变更历史。
IDOC配置步骤
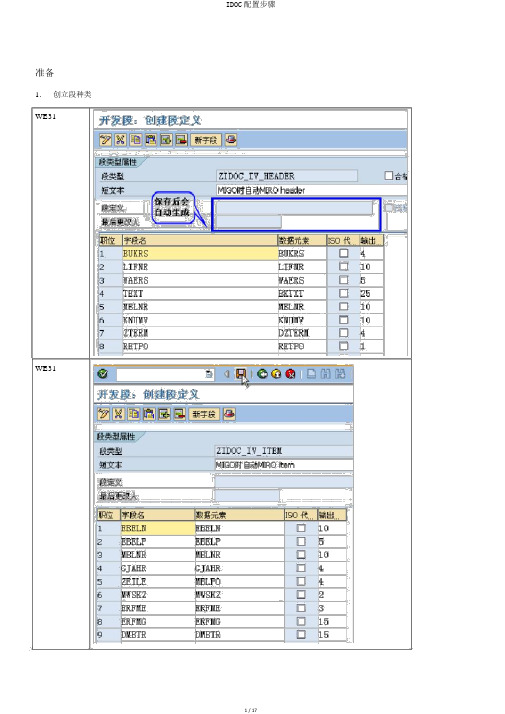
准备
1.创立段种类WE31
WE31
2.创立基本凭据种类WE30
3.创立逻辑信息种类WE81
4.将逻辑信息种类与基本凭据种类绑定
WE82
出站设置
1. 配置 RFC目的地(假如出站的系统与入站的系统同样,则这步能够省略,一般系统中BASIS 都已经配置好
了 RFC链接)
SM59
2.设置端口
WE21
3.设置合作伙伴参数
定义逻辑系统
SALE
设置合作伙伴(SAVE后增添出站参数)
WE20
入站准备
1.将函数与信息种类关系WE57
2.设置入站函数特征BD51
3.定义履行代码WE42
入站设置
1.设置合作伙伴( SCC4中查找公司逻辑系统)
WE20合作伙伴编号写的是公司逻辑系统号,能够经过SCC4来查找。
比如本需求中是直接连结自己的R3 系统,此时找到目前R3 系统的逻辑系统编号即可
TCODE: WE02、 BD87能够查察IDOC的履行状况列如: WE02查 IDOC履行状况
(1) IDOC配置问题
合作伙伴没有激活:
( 2)传输数据问题
原由是 FK01 下没有成立对应的科目
TCODE: WE19能够从头运转IDOC。
rfc 规则 -回复

rfc 规则-回复什么是RFC规则?RFC规则(Request for Comments) 是一种用于文档化Internet标准、协议、过程等的机制。
RFC最早由互联网工程任务组(IETF) 创建,现已发展成为面向整个互联网技术社区的一种通用标准。
RFC规则的主要作用是促进协议和标准的发展和交流,以确保互联网的统一性和互操作性。
目前,RFC规则成为了推动各类互联网标准化工作必不可少的一环,对于新标准和协议的提出、讨论、修改和最终认可都有着重要的影响。
那么,RFC规则是如何产生和演化的呢?如何确保规则的严谨性和有效性?接下来,我们将详细介绍RFC规则的产生和发展过程。
1. RFC的起源和发展RFC的起源可以追溯到20世纪60年代末,当时美国国防部高级研究计划局(ARPA) 正在进行一个名为ARPANET的项目,旨在构建一个分布式的计算机网络。
为了促进网络上各种标准和协议的制定和发展,ARPANET 的相关负责人制定了一个名为"Request for Comments"的机制,用于发布网络协议的设计和实现文档,并邀请来自世界各地的技术专家提出反馈和建议。
由于RFC规则的成功应用于ARPANET项目,它也被采纳为一种通用的标准化规范机制。
随着互联网的快速发展,RFC规则也逐渐成为促进互联网技术标准化的主要途径。
2. RFC的书写和提交RFC规则的书写和提交是一个开放的过程,任何人都可以通过填写RFC 表单来提交自己的标准、协议、技术报告或其他相关文档。
RFC规则要求提交的文档需经过严格的审查和讨论,确保其内容准确、一致、易于理解,并有利于互联网的发展。
一篇RFC规则文档通常包括以下几个部分:- 文档的标识和版本信息- 文档的摘要和目的- 相关术语和定义- 提出的标准或协议的描述和技术细节- 安全性、互操作性和性能等方面的考虑- 影响和建议的总结- 参考资料和相关链接提交的文档经过初步审查后,将被分配一个RFC编号,并发布在互联网上供公众查阅和讨论。
MGCP协议RFC2705-软交换分组协议基础

资料编码产品名称 NGN使用对象工程师产品版本编写部门固网技术支持部资料版本 V2.0软交换分组协议基础MGCP协议拟制:刘志强日期: 2002年07月15日审核:日期:审核:日期:批准:日期:目录第1章 MGCP协议介绍 (3)第2章 MGCP协议常见名词解释 (5)2.1 端点的命名 (5)2.2 连接的命名 (6)2.3 呼叫的命名 (6)2.4 事务标识和三次握手 (6)2.5 事件、信号与包 (7)2.6 号码分析表 (8)第3章 MGCP命令解释与说明命令 (10)3.1 命令的格式 (10)3.1.1 命令行 (10)3.1.2 参数行 (11)3.2 MGCP命令介绍 (12)3.2.1 通知请求(RQNT) (12)3.2.2 通知命令(NTFY) (13)3.2.3 创建连接命令(CRCX) (13)3.2.4 修改连接命令(MDCX) (14)3.2.5 由呼叫代理发起的删除连接命令(DLCX) (15)3.2.6 由网关发起的删除连接命令(DLCX) (15)3.2.7 审计端点命令(AUEP) (16)3.2.8 审计连接命令(AUCX) (16)3.2.9 重启命令(RSIP) (17)3.3 命令示例 (17)3.3.1 MGCP命令编码的示例 (17)3.3.2 响应格式 (18)第4章 MGCP接续流程分析 (20)4.1 成功呼叫流程 (20)4.2 不成功呼叫流程 (22)第5章 MGCP在组网中的实际应用 (1)5.1 MGCP在NGN组网中的应用: (1)5.2 MGCP在SoftX3000产品中的应用: (2)5.2.1 协议栈 (3)5.2.2 功能实现 (4)关键词和缩略语:MG --媒体网关MGCP--媒体网关控制协议CA--呼叫代理MGC--媒体网关控制器Endpoint--端点Connection--连接摘要:本文对网关控制协议(MGCP)做了简单的介绍,包括MGCP协议的概念、原理及在NGN组网中的应用。
RFC协议标准

标准参考文档链路层协议PPP(Point-to-Point Protocol):RFC 1332: The PPP Internet Protocol Control Protocol (IPCP)RFC 1334: PPP Authentication ProtocolsRFC 1552: The PPP Internetworking Packet Exchange Control Protocol (IPXCP) RFC 1570: PPP LCP Extensions(实现了其中的callback选项)RFC 1661: The Point-to-Point Protocol (PPP)RFC 1877: PPP Internet Protocol Control Protocol Extensions for Name Server AddressesRFC 1990: The PPP Multilink Protocol (MP)RFC 1994: PPP Challenge Handshake Authentication Protocol (CHAP)RFC 2509: IP Header Compression over PPPRFC 1962: The PPP Compression Control Protocol (CCP)RFC 1974: PPP Stac LZS Compression ProtocoldX25、LAPB(Link Access Protocol Balanced):RFC1613:Cisco Systems X.25 over TCP(XOT)RFC1598:PPP in X.25RFC1461:SNMP MIB extension for MultiProtocol Interconnect over X.25RFC1382: SNMP MIB Extension for the X.25 Packet LayerRFC1381: SNMP MIB Extension for X.25 LAPBRFC1356: Multiprotocol Interconnect on X.25 and ISDN in the Packet ModeRFC1236: IP to X.121 Address Mapping for DDNRFC1226: Internet Protocol Encapsulation of AX.25 FramesRFC1090: SMTP on X.25RFC1086: ISO-TP0 bridge between TCP and X.25RFC874: Critique of X.25RFC1236: IP to X.121 Address Mapping for DDNRFC1133: Routing between the NSFNET and the DDNCisco-HDLC:Cisco-HDLC是CISCO自己设计的一个协议,没有可参考的标准Frame Relay:RFC1294/1490: Multiprotocol Interconnect over Frame RelayRFC1293: Inverse Address Resolution Protocol(INARP)RFC1315: Management Information Base for Frame Relay DTEsITU-T Q933附录A:帧中继本地管理接口(LMI)协议ANSI T1.617附录D:帧中继本地管理接口(LMI)协议ISDN(Integrated Services Digital Network):ITU-T Q.931建议(网络层)ITU-T Q.921建议(链路层)IP层协议RFC791: Internet Protocol. (IP)RFC792: Internet Control Message Protocol (ICMP)RFC793: TRANSMISSION CONTROL PROTOCOL (TCP)RFC896: Congestion Control in IP/TCP InternetworksRFC768: User Datagram Protocol (UDP)RFC 826: An Ethernet Address Resolution Protocol (ARP)Socket: Unix标准路由协议RIP(Routing Information Protocol):RFC1058: Routing Information ProtocolRFC1723: RIP Version 2RFC2082: RIP-2 MD5 AuthenticationOSPF(Open Shortest Path First):RFC2328: OSPF Version 2RFC1793: Extending OSPF to Support Demand CircuitsIGRP(Interior Gateway Routing Protocol):IGRP协议无标准RFC,与CISCO保持兼容BGP(Border Gateway Protocol):RFC1771: A Border Gateway Protocol 4(BGP-4)RFC1772: Application of the Border Gateway Protocol in the Internet (BGP-4) RFC1965: Autonomous System Confederations for BGPRFC1966: BGP Route Reflection -- An alternative to full mesh IBGPRFC1997: BGP Community AttributeRFC2439: BGP Route Flap Damping网络安全RADIUS(Remote Authentication Dial In User Service):RFC2138: Remote Authentication Dial In User Service (RADIUS)RFC2139: RADIUS AccountingGRE(Generic Routing Encapsulation):RFC1701: Generic Roouting Encapsulation (老版本)RFC1702: Generic Routing Encapsulation over IPv4 networksRFC2784: Generic Roouting Encapsulation (新版本)RFC2667: IP Tunnel MIBIPSEC(IP Security):RFC1825: Security Architechure for the Internet Protocol (老版本)RFC2401: Security Architechure for the Internet Protocol (新版本)AH(Authentication Header)协议:RFC2402: IP Authentication HeaderRFC1321: The MD5 Message-Digest AlgorithmRFC2104: HMAC: Keyed-Hashing for Message AuthenticationRFC2085: IP Authentication with Replay PreventionRFC2403: The Use of HMAC-MD5-96 within ESP and AHRFC2404: The Use of HMAC-SHA-1-96 within ESP and AHESP(Encapsulating Security Payload):RFC2406: IP Encapsulating Security Payload (ESP)RFC2405: The ESP DES-CBC Cipher Algorithm With Explicit IVIKE(Internet Key Exchange):RFC2408:Internet Security Association and Key Management Protocol (ISAKMP) RFC2409:The Internet Key Exchange (IKE)RFC2407:The Internet IP Security Domain of Interpretation for ISAKMP (IPSEC DOI)L2TP(Layer 2 Tunnel Protocol):RFC2661:Layer 2 Tunnel ProtocolNAT(Network Address Translator):RFC1631:The IP Network Address Translator (NAT)RFC2663:IP Network Address Translator (NAT) Terminology and Considerations 网络管理SNMP(Simple Network Management Protocol):RFC 1157: Simple Network Management Protocol (SNMP)。
slmp协议手册

slmp协议手册SLMP(Seamless Message Protocol)协议是一种工业自动化领域常用的通信协议,用于在不同设备之间传输数据和命令。
它采用了简单、轻量级的设计,旨在提供高效、可靠的通信。
首先,SLMP协议的核心目标是实现不同品牌、不同类型的设备之间的无缝通信。
在工业自动化领域,不同设备之间的互联性是非常重要的,因为不同设备负责不同的任务,需要相互配合才能实现自动化流程。
而SLMP协议通过定义统一的数据传输格式和通信规则,使得不同设备可以以统一的方式进行通信,降低了集成的难度和成本。
SLMP协议的设计理念是简单、轻量级。
它采用了基于报文的通信方式,通过定义不同类型的报文来实现数据的传输和命令的执行。
报文的结构非常简单,通常包含报文头、报文体和报文尾等几个部分。
报文头用于标识报文的类型和长度等信息,报文体用于存储具体的数据或命令,而报文尾则用于校验报文的完整性。
这种简单的设计不仅提高了协议的可读性和可理解性,也降低了协议的复杂度和开销。
SLMP协议支持多种类型的数据传输,包括实时数据、历史数据、报警数据等。
不同类型的数据可以通过不同类型的报文进行传输,从而满足不同应用场景的需求。
同时,SLMP协议还支持多种通信方式,包括以太网、串口、无线等。
这些通信方式可以根据具体的设备和应用场景进行选择,并通过相应的协议转换器实现互联。
SLMP协议还具有高效、可靠的特点。
它采用了基于事件驱动的通信模式,即设备之间通过事件来触发数据的传输。
这种通信模式既可以降低通信的开销,又可以提高通信的实时性。
同时,SLMP协议还支持数据的压缩和加密等功能,以提高通信的效率和安全性。
在实际应用中,SLMP协议已经被广泛应用于工业自动化领域。
它可以用于各种类型的设备之间的通信,包括传感器、执行器、控制器等。
通过SLMP协议,这些设备可以实现数据的共享和交换,从而实现更高级别的自动化控制和集成。
同时,SLMP协议还可以与其他通信协议结合使用,例如Modbus、OPC等,以满足不同应用场景的需求。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Network Working Group A. Srinath Request for Comments: 3149 G. Levendel Category: Informational K. Fritz Sylantro Systems R. Kalyanaram Wipro Systems September 2001 MGCP Business Phone PackagesStatus of this MemoThis memo provides information for the Internet community. It doesnot specify an Internet standard of any kind. Distribution of thismemo is unlimited.Copyright NoticeCopyright (C) The Internet Society (2001). All Rights Reserved.AbstractThis document describes a collection of MGCP (Media Gateway ControlProtocol) packages that can be used to take advantage of the feature keys and displays on digital business phones and IP-Phones.IESG NoteThis document is being published for the information of thecommunity. It describes a non-IETF protocol that is currently being deployed in a number of products. Implementers should be aware that the IETF Megaco working group and the ITU-T Study Group 16 haveproduced a standards track RFC "Megaco Protocol Version 1.0" (RFC3015, also published as ITU recommendation H.248) which addresses the same problem space and are developing extensions to that protocol for functions of this type.Table of Contents1. Introduction. . . . . . . . . . . . . . . . . . . . . . . . 31.1 General Information. . . . . . . . . . . . . . . . . . 41.2 Objectives . . . . . . . . . . . . . . . . . . . . . . 52. MGCP Packages for Business Phones . . . . . . . . . . . . . 52.1 Feature Key Package. . . . . . . . . . . . . . . . . . 62.2 Business Phone Package . . . . . . . . . . . . . . . . 92.3 Display XML Package. . . . . . . . . . . . . . . . . . 9 Srinath, et al. Informational [Page 1]3. Endpoint Naming and Phone Type Determination. . . . . . . .104. Functions that should be Locally Implemented. . . . . . . .114.1 Volume Control . . . . . . . . . . . . . . . . . . . .114.2 Audio Path . . . . . . . . . . . . . . . . . . . . . .114.3 Microphone mute button and light . . . . . . . . . . .115. XML Package Support . . . . . . . . . . . . . . . . . . . .125.1 XML Documents. . . . . . . . . . . . . . . . . . . . .125.2 XML Requests . . . . . . . . . . . . . . . . . . . . .135.3 XML Request History. . . . . . . . . . . . . . . . . .155.4 XML Events . . . . . . . . . . . . . . . . . . . . . .155.5 XML Tags . . . . . . . . . . . . . . . . . . . . . . .155.5.1 XML Tag. . . . . . . . . . . . . . . . . . . . . . .175.5.2 Card Tag . . . . . . . . . . . . . . . . . . . . . .185.5.3 P Tag. . . . . . . . . . . . . . . . . . . . . . . .185.5.4 Select Tag . . . . . . . . . . . . . . . . . . . . .185.5.5 Option Tag . . . . . . . . . . . . . . . . . . . . .195.5.6 Input Tag. . . . . . . . . . . . . . . . . . . . . .205.5.7 Echo Tag . . . . . . . . . . . . . . . . . . . . . .205.5.8 Calltimer Tag. . . . . . . . . . . . . . . . . . . .215.5.9 Time Tag . . . . . . . . . . . . . . . . . . . . . .215.5.10 Timer Tag . . . . . . . . . . . . . . . . . . . . .215.5.11 Do Tag. . . . . . . . . . . . . . . . . . . . . . .225.5.12 Go Tag. . . . . . . . . . . . . . . . . . . . . . .225.5.13 Prev Tag. . . . . . . . . . . . . . . . . . . . . .236. Security Considerations . . . . . . . . . . . . . . . . . .237. Acknowledgements. . . . . . . . . . . . . . . . . . . . . .238. References. . . . . . . . . . . . . . . . . . . . . . . . .239. Authors’ Addresses. . . . . . . . . . . . . . . . . . . . .24Appendix A: BNF description of XML grammar . . . . . . . . . .25Appendix B: Sample XML Documents, Renderings and Events. . . .27B.1 Sample Deck 1 (Itemized List Box). . . . . . . . . . .27B.2 Sample Deck 2 (Enumerated List Box). . . . . . . . . .28B.3 Sample Deck 3 (Text Box) . . . . . . . . . . . . . . .29B.4 Sample Deck 4 (Echo Box) . . . . . . . . . . . . . . .30B.5 Sample Deck 5 (Input Box). . . . . . . . . . . . . . .31B.6 Sample Deck 6 (Timers) . . . . . . . . . . . . . . . .32Appendix C: Example usage of MGCP extension packages . . . . .33C.1 Setting Labels on Phone. . . . . . . . . . . . . . . .33C.2 Activating a Feature on a Feature Key. . . . . . . . .33C.3 Generating a Call using Feature Key as a Line Key. . .35C.4 Determining Make and Model of a Phone. . . . . . . . .38Appendix D: BNF Description of X-UA Parameter. . . . . . . . .39Full Copyright Statement . . . . . . . . . . . . . . . . . . .41 Srinath, et al. Informational [Page 2]1. IntroductionThe Media Gateway Control Protocol (MGCP) Version 1.0 defines aprotocol for controlling Voice over IP Telephony Gateways fromexternal call control elements. As defined, it supports externalcall control elements called Media Gateway Controllers and assumesthat these Gateways can support collections of endpoints. Theendpoint type known as an "analog line" can be used as a clientinterface to provide service to a basic analog telephone unit. Thepackages that are currently defined to handle events and signalsallow for only a basic level of audio connection and signaling tosuch endpoints. To handle more advanced capabilities commonly found on business phones such as feature keys, speaker phones and displays, it is necessary to define additional packages as extensions to theMGCP protocol.These packages, when used in conjunction with the packages currently defined in RFC 2705 (Media Gateway Control Protocol Version 1.0) [1], allow an MGCP Call Agent to control business phone endpoints.The MGCP extension packages defined here are as follows:- Feature Key Packageo Groups events and signals associated with the additionalkeys available on business phones that are non-DTMF and not locally-implemented. These include:- Feature Key event to allow mapping of key numbers tofeatures.- Key State signal to indicate the state of feature keys.- Set Label signal to display a label on the LCD next to a feature key.- Business Phone Packageo Groups signals that are not related to feature keys,including:- Force Off-hook and Force On-hook signals to allowapplication integration with speaker phone capabilities. - Beep signal to play a beep on the phone.- Display XML Packageo Used to convey XML [2] script data to and from the phone to control the display and assign functions to the displaysoft-keys for event reporting. These include:Srinath, et al. Informational [Page 3]- XML event to report user input or selection.- XML signal to render text to the LCD display.An MGCP experimental parameter is also defined here:- User Agent Parametero Used to determine the make and model of a phone1.1 General InformationA generic business phone typically includes a number of features that provide access to additional functionality useful in a businessenvironment. Beyond the basic handset and dial pad, a business phone may optionally include a number of fixed buttons, line keys andprogrammable feature keys, along with an LCD display and soft-keys.Specific examples of items that may be included on a business phoneare:- Speaker phone microphone and speaker- Speaker phone button and light- Messages button and light- Redial button- Volume up and down buttons- Hold button and light- Transfer button and light- Forward button and light- Conference button and light- Microphone mute button and light- Multiple feature keys with lights- Multi-line LCD Display- Multiple soft-keys next to the LCD display- Navigation keysExamples of fixed buttons functionality are ’hold’, ’transfer’,’redial’, ’conference’, ’call-logs’, ’directories’, and ’messages’.Fixed buttons may vary from phone to phone. While the packagesdescribed here would allow these to be reported to a Call Agent, the Call Agent would also need to determine which feature key numbercorresponds to a particular pre-assigned function.Since MGCP assumes a call control architecture where the call control "intelligence" is outside the Gateways and handled by external callcontrol elements, the programming of the feature keys would beresident in the Call Agent. If the user were to press the ’hold’button, the phone would simply report the key number, and the burden Srinath, et al. Informational [Page 4]of recognizing that this feature key is assigned to the ’hold’function, and providing such functionality, is left to the CallAgent.1.2 ObjectivesThe high level objectives that were considered in generating thepackages described here are:- Provide a minimum set of extension packages to the MGCP Version1.0 protocol to allow applications to take advantage of genericbusiness phone capabilities.- Provide event and control extensions at a sufficiently low levelfor an application to implement generic business phone functionswithout generating excessive or redundant data traffic. (e.g.,sending feature key information on both press and release would be a "don’t care" for a Call Agent. All it cares about is that thekey was pressed.)- Provide a mechanism to interface with LCD displays and allow theflexibility to accommodate a variety of application needs and the different types of displays available.2. MGCP Packages for Business PhonesThe following packages should be implemented for business phones.The G,D,L, and H packages are defined in RFC 2705 [1]. Packages KY, BP and XML are defined in this specification.______________________________________________________| Package | Name | Defined ||______________________________|_________|_____________|| Generic Media Package | G |in RFC 2705 || DTMF package | D |in RFC 2705 || Line Package | L |in RFC 2705 || Handset Package | H |in RFC 2705 || Feature Key Package | KY |in this spec || Business Phone Package | BP |in this spec || Display XML Package | XML |in this spec ||______________________________|_________|_____________|In the tables of events for each package, there are five columns:Symbol: the unique symbol used for the eventDefinition: a short description of the eventSrinath, et al. Informational [Page 5]R: an x appears in this column if the event can be requested by theCall Agent.S: if nothing appears in this column for an event, then the eventcannot be signalled on command by the Call Agent. Otherwise, the following symbols identify the type of signal:OO On/Off signal. The signal is turned on until requested by the Call Agent to turn it off, and vice versa.TO Timeout signal. The signal lasts for a given duration unlessit is superseded by a new signal.BR Brief signal. The event has a short, known duration.Duration: specifies the duration of TO signals.2.1 Feature Key PackagePackage Name: KYThe Feature Key Package groups events and signals that are associated with the additional keys that are available on business phones.____________________________________________________________________| Symbol | Definition | R | S Duration ||__________|____________________________|_____|______________________|| fk1-fk99 | Feature Key | x | || ks | Key State | | OO || ls | Set Label | | OO ||__________|____________________________|_____|______________________|Feature Key (fk1-fk99)These events map to all the keys on the phone that are not DTMFkeys or locally implemented functions (such as volume). Themapping of fk number to key is expected to vary between phones.Note: Some have suggested parameterizing the fk event, i.e.,sending an RQNT with "R: KY/fk" and an NTFY with "O: KY/fk(1)",but this is problematic; It is desirable to request only the keys that can be pressed in a given state, to eliminate the chance that a mis-pressed button will cancel a timeout signal, as well as toreduce message traffic. This is not possible within the confines of MGCP, as requested events cannot be parameterized.Srinath, et al. Informational [Page 6]Key State (ks)This signal is used to indicate the state of a feature key. Itshould be ignored by phones without this capability.This signal has two parameters: key number and state. The keynumber maps directly to the feature key number. The state is ahigh level description of the state of the key. This allowsdifferent phones to implement different indications of state. For example, Phone A may have a multi-color LED associated withfeature keys that can blink at different cadences. Phone B might have an LCD beside the keys that can display text or icons. It is up to each phone vendor to determine how to present the stateindication.The following states are used:______________________| State | Definition ||_______|______________|| en | enabled || db | disabled || id | idle || dt | dial tone || cn | connected || dc | disconnected || rg | ringing || rb | ringback || ho | holding || he | held ||_______|______________|For example: an RQNT with "S: KY/ks(5,en)" will cause an indicator corresponding to fk5 to indicate that it is enabled. An RQNT with "S: KY/ks(2,rg)" will cause an indicator corresponding to fk2 toindicate that it is ringing."en" stateThe associated feature is enabled. Used for keys that turn afeature on or off, such as "Do Not Disturb.""db" stateThe associated feature is disabled. Used for keys that turn afeature on or off, such as "Do Not Disturb."Srinath, et al. Informational [Page 7]"id" stateThe specified line appearance is in the idle state, available for a call."dt" stateThe specified line appearance is providing dial-tone."cn" stateThe specified line appearance is actively in a call, in theconnected state."dc" stateThe specified line appearance is disconnected, but thecorresponding line is still active (the user is still offhook)."rg" stateThe specified line appearance is terminating an incoming call, in the ringing state."rb" stateThe specified line appearance is originating an outgoing call, in the ringing-back state."ho" stateThe specified line appearance is in the holding state, with thefar end held."he" stateThe specified line appearance is in the held state, with the farend holding.Set Label (ls)This signal is used to set the label on a key. This is used forphones that have an LCD next to the feature keys. It should beignored by phones without this capability.This signal has 2 parameters: key number and label. The keynumber maps directly to the feature key number. The label is free form text, restricted to the capabilities of the phone.Srinath, et al. Informational [Page 8]For example, an RQNT with "S: KY/ls(1,2200)" sets the label nextto the fk1 feature key to the string "2200" (a phone extension). 2.2 Business Phone PackagePackage Name: BPThe Business Phone Package groups signals other than those related to feature keys and displays.____________________________________________________________________| Symbol | Definition | R | S Duration ||__________|____________________________|_____|______________________|| hd | Force Offhook | | OO || hu | Force Onhook | | OO || beep | Beep | | BR ||__________|____________________________|_____|______________________|Force Offhook (hd)This signal is used to force the phone offhook. If the phone has a speaker phone, it should be activated. This signal can benegated by the user by hanging up.This can be used if a feature key causes a call to be initiated.See the sample call flow in Appendix C.This can also be used for application integration. For example, a user could select a number in an application on their PC, and the phone would be forced offhook and a call initiated.Force Onhook (hu)This signal forces the phone onhook. This can be used when thefar-end disconnects, or if a feature key causes a call to beterminated.Beep (beep)Play a beep on the phone.2.3 Display XML PackagePackage Name: XMLThe XML Package contains one event/signal that is used to convey XML data to and from the phone.Srinath, et al. Informational [Page 9]_____________________________________________________________________| Symbol | Definition | R | S Duration ||__________|____________________________|_____|______________________|| xml | XML Data | x | OO ||__________|____________________________|_____|______________________|XML Data (xml)As an event, if this event is requested in an RQNT with "R:XML/xml", any posts of data from an XML script are returned in an NTFY with "O: XML/xml(post data here)".As a signal, the parameterized data indicates a URL to an XMLscript (possibly local), as well as substitution values thatdepend on the XML script selected. See section 5 for moreinformation.3. Endpoint Naming and Phone Type DeterminationBecause the display state can be asynchronous from the signalingstate of the phone, it is desirable to address the display as aseparate MGCP endpoint.For example, suppose a call is presented to the phone, and a display is presented that gives the user the option of redirecting the caller immediately to voice-mail. Selecting the option via the displaywould cause an XML post to occur, cancelling any timeout signals (the ringing).In order to simplify the handling of such scenarios, it is expectedthat the related display have a different MGCP endpoint name, created by inserting a prefix before the phone endpoint name. The prefixused shall be "disp/".For example, if the phone endpoint has the name"ep1@", the display endpoint would be named"disp/ep1@".The Call Agent must be able to determine which feature key numbercorresponds to a particular pre-assigned function. For example, one phone may have the pre-assigned functions of ’redial’ and ’hold’mapped to feature keys numbered fk1 and fk23, respectively. Anotherphone may not report fk23 at all, and have the pre-assigned function of ’transfer’ mapped to fk1. Also, since the programming of feature keys would be resident in the Call Agent, a user-interface that Srinath, et al. Informational [Page 10]allows the programming of these keys must know the keys supported on the phone, in order for the Call Agent to request the appropriatefeature keys.Determination of such basic capabilities must occur at the momentwhen the phone sends its first RSIP message to a Call Agent. Whileit might be possible to define packages with events and signals that allow for an exhaustive discovery of the layout of a particularphone, a simpler and more reasonable approach would be for the CallAgent to discover the make and model of the phone, and thus determine the capabilities of the phone. To this end, an experimentalparameter, "X-UA" has been introduced for use in the Requested-Infofield (F:) of the AUEP method. The response to the "X-UA" isexpected to be a string that uniquely identifies the make and modelof the phone. Note that per RFC 2705, a Gateway must ignoreexperimental parameters prefixed as "X-" that it cannot support,versus respond with an error code such as 511 (Unrecognizedextension). See the sample call flow in Appendix C.4. Functions that should be Locally ImplementedSome functions should be implemented locally on the Gateway. Theseare listed in the following sections.4.1 Volume ControlVolume for ringing, handset, and speaker phone should be implemented locally on the Gateway.4.2 Audio PathIf the phone includes a speaker phone, activating the speaker phonefrom the idle state should generate an offhook (L/hd) event. Theuser should then be able to switch to handset mode by lifting thehandset, and be able to switch back to speaker phone mode without any interaction with the Call Agent. De-activating the speaker phonewith the handset on-hook should generate an onhook (L/hu) event.4.3 Microphone mute button and lightIf the phone includes a microphone mute button and (optionally) anassociated indicator (e.g., light), the functionality of these items should be implemented locally on the Gateway.Srinath, et al. Informational [Page 11]5. XML Package SupportNot all business phones have the same display and keypadcapabilities. To support these varying devices in a consistentmanner, this section outlines an XML framework that is used to drive the phone. In this framework, the Call Agent pushes XML requests to the Gateway using MGCP signals. These XML requests indicate the XML document that is to be rendered on the phone.When a user inputs data or makes a selection from a display, theGateway "posts" an XML request to the Call Agent using MGCP events. 5.1 XML DocumentsWhen an XML signal request is sent to an endpoint, it indicates theXML documents that the endpoint must process. These documentscontain tags that are a subset of the Wireless Markup Language (WML) [3] plus some non-WML additions. These tags specify items to bedisplayed as well as XML events that may be reported as the result of user input.Each XML document, known as a card, defines a user interaction. Agroup of cards is called a deck. One or more decks define anapplication. The cards define soft key behavior as well as displaybehavior, and are mapped to components that implement the behavior of a basic graphical user interface on the display phone. Based on the available requirements, the components needed are:- Input box:allows user input, including editing capabilities, via thekeypad.- Enumerated list box:allows the user to select one of a list of items.- Itemized list box:allows the user to select an item using a soft key.- Text box:displays read-only text to the user.- Echo box:displays but does not process user input.Srinath, et al. Informational [Page 12]A card may have the following properties.1. Timed content (e.g., card expiration)2. Static content (e.g., text)3. Dynamic content (e.g., call timers/time)Additionally, cards may also contain variables to be substituted for values that are specified in an XML request. See section 5.2 fordetails on variable substitution.There are cases where the XML scripts handling the display need touse keys that are also used by the phone. For example, the displaycould present an enumerated list, where a particular item is selected by pressing the associated number on the dial pad. All user keypresses must be routed through the XML component layer. The display layer either consumes the key presses or passes them on to the phone layer for consumption.The code handling key presses should thus present a key press to the display code first. If the display code does not "use" the keypress, then the key press should be presented to the phone code.This gives precedence to the XML scripts for key presses.5.2 XML RequestsThe XML framework uses MGCP as its transport for making requests tothe display phone. MGCP is also used to receive asynchronous events from the display phone (e.g., an item has been selected, or the user has entered text).An XML request is made to an endpoint using the XML/xml signal. The signal has the following format:S: XML/xml(<url>?<card>?$<variable1>=<value1>?$<variable2>=<value2>)The first component of the signal parameter is a URL to the deck. If no scheme is indicated, the deck is assumed to be local to the phone. Here are some examples:ftp:///deck1?card1?$var1=val1/deck1?card1?$var1=val1file://deck1?card1?$var1=val1deck1?card1?$var1=val1A card identifier and a list of variable/value pairs follow the URL. The card identifier indicates the card within the deck to display. Srinath, et al. Informational [Page 13]The variable/value pairs are substituted into the deck before it isrendered to the display. This means that the variables are deck-scoped, and variables not defined in the requested card must bepopulated in other cards in the same deck if defined therein.For example, a deck may contain the following cards:<card id="one"><p>$line1</p><timer value="2"/><do type="ontimer"><go href="#two"/></do></card><card id="two"><p>$line2</p></card>And an XML request may look like:S: XML/xml(deck?one?$line1=abc$line2=xyz)After variable substitution, the deck will look like:<card id="one"><p>abc</p></card><card id="two"><p>$line2</p></card>Once variable substitution is complete, the card is rendered. If aparameter variable does not exist anywhere in the deck it should beignored.When card two is invoked from card1 in response to the timeoutaction, card two’s variables are substituted with the variablesvalues passed as a request to card one. Card two will look like:<card id="two"><p>xyz</p></card>Srinath, et al. Informational [Page 14]5.3 XML Request HistoryIn order to support navigation through a request history such as when a user cancels a card, the XML layer must maintain a last-in-first-out history of requests made for the endpoint. (See the <prev> tagdefinition in section 5.5.13.)5.4 XML EventsWhenever the XML layer determines that an event has occurred, itreports the event using the MGCP observed event field:O:XML/xml(post?<deck>?<card>?<variable1>=<value1>?<variable2>=<value2>) Here, the event parameter contains the deck and card that generatedthe event, as well as data that is to be processed by the Call Agent. The data being posted is in the form of a list of variable/valuepairs.In order for the Gateway to properly generate the XML event, it isnecessary for the Call Agent to request the event using the requested events field:R: XML/xmlThis requested event should be combined with the signal request in an RQNT.5.5 XML TagsAny XML implementation must at a minimum support the XML tags listed in the table that follows. All tags have a terminator tag of theform </tag> to indicate the end of the tag. See the XML grammar inAppendix A.Srinath, et al. Informational [Page 15]_____________________________________________________________________| Name | Usage | |_______________|_____________________________________________________| | <xml> | Marks the beginning of a deck. | |_______________|_____________________________________________________| | <card> | Marks the beginning of a card. | |_______________|_____________________________________________________| | <p> | Marks the beginning of a paragraph. | |_______________|_____________________________________________________| | <select> | Defines a list of items that may be selected (an | | | enumerated or itemized list box). | |_______________|_____________________________________________________| | <option> | Used in conjunction with the <select> tag to | | | specify an individual item that may be selected. | |_______________|_____________________________________________________| | <input> | Marks the beginning of user input (an input box). | |_______________|_____________________________________________________| | <echo> | Marks the beginning of an echo box. | |_______________|_____________________________________________________| | <calltimer> | Call Timer. An incremental timer usually used to | | | maintain the duration of a call. | |_______________|_____________________________________________________| | <timer> | Card timer. Allows an event to be generated when | | | the timer expires. | |_______________|_____________________________________________________| | <time> | A tag indicating the current time. | |_______________|_____________________________________________________| | <do> | Event consumer. | |_______________|_____________________________________________________| | <go> | Used in conjunction with the <do> tag to indicate | | | a new page to be displayed. | |_______________|_____________________________________________________| | <prev> | Used in conjunction with the <do> tag to indicate | | | that the previous card in the history should be | | | displayed. | |_______________|_____________________________________________________| Srinath, et al. Informational [Page 16]。
