第六章--黎明--访问控制列表 (一)--2014-03-10
教案

实现网络安全隔离
------配置标准访问控制列表
象山职业高级中学林欢欢
【课题】:实现网络安全隔离——配置标准访问控制列表
【学情分析】:
学生经过了《中小型网络构建与管理》半个多学期的学习,对网络基本配置比较熟悉。
已经学习过静态路由、动态路由的知识,并进行过多次的练习。
【教学目标】:
知识与技能目标:掌握访问控制列表的基本概念,会配置标准访问控制列表
过程与方法目标:通过操作指导培养学生自学能力。
通过找错排错培养学生独立思考能力及控索精神。
情感态度与价值观目标:学生亲手创建访问控制列表,培养学生的网络安全意识。
【教学重点】:标准访问控制列表的创建
【教学难点】:访问控制列表的概念理解
通过操作指导和课堂讲解,使学生能够掌握重点及难点
【教学准备】:
多媒体机房、cisco packet模拟器软件、投影仪等
【课时】:
1课时。
第八讲 访问控制列表

➢使用最多的是希望控制的IP地址和通配符掩码
➢IP地址可以是子网、一组地址或单一节点地址
➢路由器使用通配符掩码来决定检查地址的哪些
位
IP地址 通配符掩码
Lab-A(config)#access-list 1 deny 192.5.5.10 0.0.0.0
第16页
通配符掩码
➢通配符掩码指定了路由器在匹配地址时检查哪些 位忽略哪些位
– 掩码为255.255.255.192的192.5.5.64子网的控制第IP21页地址
通配符掩码练习
– 掩码为255.255.128.0的172.16.128.0子网的控制IP 地址和通配符掩码?
– 答案: 172.16.128.0 0.0.127.255 – 掩码为255.255.252.0的172.16.16.0子网的控制IP地
第27页
host命令
– 众多情况下,网络管理员需要在ACL处 理单独节点的情况,可以使用两种命令:
– Lab-A(config)#access-list 1 permit 192.5.5.10 0.0.0.0
将最严格的语句放在列表顶部, 最不严格的语句 放在列表底部 • 如果ACL中没有找到匹配项, 则执行隐性拒绝语 句 • 每个接口的每个方向只能应用一个IP ACL。
第11页
ACL分类
• 标准访问控制列表: 只对数据包中源地址 进行检查。
• 扩展访问控制列表: 即检查源地址,也检 查目标地址,以及数据包的上层协议。
– 为了控制网络中一部分节点往往需要在二 进制方式下进行计算
– 例如:学生使用192.5.5.1到192.5.5.127地址 范围,教师使用192.5.5.128到192.5.5.254地 址范围。这些地址处在相同的网络中 192.5.5.0/24
信息安全题库(最完整的)

信息安全培训题库单选题1.UNIX中,可以使用下面哪一个代替Telnet,因为它能完成同样的事情并且更安全?A.RHOST B.SSH C.FTP D.RLOGONB2.root是UNIX系统中最为特殊的一个账户,它具有最大的系统权限:下面说法错误的是:A.应严格限制使用root特权的人数。
B.不要作为root或以自己的登录户头运行其他用户的程序,首先用su命令进入用户的户头。
C.决不要把当前工作目录排在PATH路径表的前边,那样容易招引特洛伊木马。
当系统管理员用su命令进入root时,他的PATH将会改变,就让PATH保持这样,以避免特洛伊木马的侵入。
D.不同的机器采用相同的root口令。
D3.下列那种说法是错误的?A.Windows 2000 server系统的系统日志是默认打开的。
B.Windows 2000 server系统的应用程序日志是默认打开的。
C.Windows 2000 server系统的安全日志是默认打开的。
D.Windows 2000 server系统的审核机制是默认关闭的。
D4.no ip bootp server 命令的目的是:A.禁止代理ARPB.禁止作为启动服务器C.禁止远程配置D.禁止IP源路由B5.一般网络设备上的SNMP默认可写团体字符串是:A.PUBLICB.CISCOC.DEFAULTD.PRIV ATED6.在以下OSI七层模型中,synflooding攻击发生在哪层:A.数据链路层B.网络层C.传输层D.应用层C7.对局域网的安全管理包括:A.良好的网络拓扑规划B.对网络设备进行基本安全配置C.合理的划分VLAND.All of aboveD8.ARP欺骗工作在:A.数据链路层B.网络层C.传输层D.应用层A9.路由器的Login Banner信息中不应包括:A.该路由器的名字B.该路由器的型号C.该路由器的所有者的信息D.ALL OF ABOVED10.设置IP地址MAC绑定的目的:A.防止泄露网络拓扑B.防止非法接入C.加强认证D.防止DOS攻击B11.为什么要对于动态路由协议采用认证机制?A.保证路由信息完整性B.保证路由信息机密性C.保证网络路由的健壮D.防止路由回路A12.在CISCO设备的接口上防止SMURF攻击的命令:A.Router(Config-if)# no ip directed-broadcastB.Router(Config-if)# no ip proxy-arpC.Router(Config-if)# no ip redirectsD.Router(Config-if)# no ip mask-replyA13.在CISCO设备中防止交换机端口被广播风暴淹没的命令是:A.Switch(config-if)#storm-control broadcast levelB.Switch(config-if)#storm-control multicast levelC.Switch(config-if)#dot1x port-control autoD.Switch(config-if)#switchport mode accessA14.下面哪类命令是CISCO限制接口流量的?A.RATE-LIMITB.privilegeC.AAAD.LOOPBACKA15.802.1X认证是基于:A.路由协议B.端口C. VTPD.VLANB16.以下哪种入侵检测系统是通过监控网段中的通讯信息来检测入侵行为的?A.网络入侵检测B.主机入侵检测C.文件完整性检验D.蜜罐与信元填充A17.以下哪一项不是入侵检测系统的主要功能?A.有效识别各种入侵手段及方法B.严密监控内部人员的操作行为C.实时报警、响应D.网络访问控制D18.与OSI参考模型的网络层相对应的与TCP/IP协议中层次是:A. B. TCP C. UDP D. IPD19.Ping of Death 攻击的原理是A. IP标准中数据包的最大长度限制是65536B. 攻击者发送多个分片,总长度大于65536C. 操作系统平台未对分片进行参数检查D. IPv4协议的安全机制不够充分C20.防火墙策略配置的原则包括:A. 将涉及常用的服务的策略配置在所有策略的顶端B. 策略应双向配置C. 利用内置的对动态端口的支持选项D.ALL OF ABOVED21.下面哪一种不是防火墙的接口安全选项A.防代理服务B.防IP碎片C.防IP源路由D.防地址欺骗A22.下列说法错误的是:A.防火墙不能防范不经过防火墙的攻击B.防火墙不能防范基于特殊端口的蠕虫C.防火墙不能防止数据驱动式的攻击B23.下列哪个是能执行系统命令的存储过程A. Xp_subdirsB. Xp_makecabC. Xp_cmdshellD. Xp_regreadC24.“Select * from admin where username=‘admin’and password=‘”&request(“pass”) & “’”如何通过验证A. ‘1’ or ‘1’=‘1’B. 1 or 1 = 1C. 1’ or ‘1’=‘1D. ‘1’=‘1’C25.“Select * from News where new_id=”& replace(request(“newid”,”’”,””)”是否存在注入?A. 是B. 否A26.从数据来源看,入侵检测系统主要分为哪两类A、网络型、控制型B、主机型、混合型C、网络型、主机型D、主机型、诱捕型C27.TCP/IP协议的4层概念模型是( 单选)A、应用层、传输层、网络层和网络接口层B、应用层、传输层、网络层和物理层C、应用层、数据链路层、网络层和网络接口层D、会话层、数据链路层、网络层和网络接口层(A)28.在UNIX系统中,当用ls命令列出文件属性时,如果显示-rwx rwx rwx,意思是()A、前三位rwx表示文件属主的访问权限;中间三位rwx表示文件同组用户的访问权限;后三位rwx表示其他用户的访问权限B、前三位rwx表示文件同组用户的访问权限;中间三位rwx表示文件属主的访问权限;后三位rwx表示其他用户的访问权限C、前三位rwx:表示文件同域用户的访问权限;中间三位rwx表示文件属主的访问权限;后三位rwx:表示其他用户的访问权限D、前三位rwx表示文件属主的访问权限;第二个rwx表示文件同组用户的访问权限;后三位rwx表示同域用户的访问权限(A)29.UNIX中,默认的共享文件系统在哪个位置()A、/sbin/B、/use/local/C、/export/D、/usr/(C)30.通过以下哪个命令可以查看本机端口和外部连接状况( )A、netstat –anB、netconn -anC、netport -aD、netstat -allA31.LINUX中,什么命令可以控制口令的存活时间?()A、chageB、passwdC、chmodD、umask(A)32.UNIX系统中存放每个用户的信息的文件是()A、/sys/passwdB、/sys/passwordC、/etc/passwordD、/etc/passwd(D)33.linux系统中如何禁止按Control-Alt-Delete关闭计算机(单选)A、把系统中“/sys/inittab”文件中的对应一行注释掉B、把系统中“/sysconf/inittab”文件中的对应一行注释掉C、把系统中“/sysnet/inittab”文件中的对应一行注释掉D、把系统中“/sysconf/init”文件中的对应一行注释掉(B)34.由于ICMP消息没有目的端口和源端口,而只有消息类型代码。
访问控制列表

l number acl-number:定义一个数字型的ACL。
l acl-number:访问控制规则序号。1000~1999是基于接口的访问控制列表,2000~2999范围的数字型访问控制列表是基本的访问控制列表,3000~3999范围的数字型访问控制列表是高级的访问控制列表,4000~4999是基于MAC地址的访问控制列表。
[Quidway-acl-adv-3000]
进入了ACL视图之后,就可以配置ACL的规则了。对于不同的ACL,其规则是不一样的,具体的各种ACL的规则的配置方法将在后面小节分别介绍。
5.1.5 基本访问控制列表
基本访问控制列表只能使用源地址信息,做为定义访问控制列表的规则的元素。通过上面小节介绍的acl命令,可以创建一个基本的访问控制列表,同时进入基本访问控制列表视图,在基本访问控制列表视图下,可以创建基本访问控制列表的规则。
undo rule rule-id [ comment text ] [ source ] [ time-range ] [ logging ] [ fragment ] [ vpn-instance vpn-instance-name ]
参数说明:
l rule-id:ACL规则编号,必须是一个已经存在的ACL规则编号。如果后面不指定参数,则将这个ACL规则完全删除。否则只是删除对应ACL规则的部分信息。
参数说明:
l rule-id:可选参数,ACL规则编号,范围为0~65534。当指定了编号,如果与编号对应的ACL规则已经存在,则会部分覆盖旧的规格,相当于编辑一个已经存在的ACL的规则。故建议用户在编辑一个已存在编号的规则前,先将旧的规则删除,再创建新的规则,否则配置结果可能与预期的效果不同。如果与编号对应的ACL规则不存在,则使用指定的编号创建一个新的规则。如果不指定编号,表示增加一个新规则,系统自动会为这个ACL规则分配一个编号,并增加新规则。
访问控制列表

• 设备从某接口向外发送数据时进行安全规则过滤
• 一个接口在一个方向只能应用一组访问控制列表
IN F1/0
OUT F1/1
访问列表的入栈应用
查找路由表 进行选路转发 是否应用 访问列表 ?
Y N
是否送方
平顶山学院
平顶山学院
软件学院
反掩码(通配符) 反掩码(通配符)
128 64 32 16 8 4 2 1
0 0 0 1
0 0 0 1
0 1 0 1
0 1 0 1
0 1 1 1
0 1 1 1
0 1 1 1
0 1 1 1
0表示检查相应的地址比特 表示检查相应的地址比特 1表示不检查相应的地址比特 表示不检查相应的地址比特
• 规则匹配原则
– 从头到尾,自顶向下的匹配方式 – 匹配成功马上停止 – 立刻使用该规则的“允许/拒绝……”
9.3.5访问列表规则的定义
• 标准访问列表
– 根据数据包源IP地址进行规则定义
• 扩展访问列表
– 根据数据包中源IP、目的IP、源端口、目的端 口、协议进行规则定义
IP标准访问列表 标准访问列表
平顶山学院 软件学院
标准访问列表配置实例(二)
• 需求:
– 你是某校园网络管理员,领导要你对网络的数据 流量进行控制,要求校长可以访问财务的主机,但 教师机不可以访问。
• 配置:
– ip access-list standard abc – permit host 192.168.2.8 – deny 192.168.2.0 0.0.0.255 F0/2 – ip access-group abc in
F0/1 财务 192.168.1.0 F0/6 F0/8 F0/10 教师 192.168.2.0
综合安防管理平台操作手册

iSecure Center综合安防管理平台操作手册前言本部分内容的目的是确保用户通过本手册能够正确使用产品,以避免操作中的危险或财产损失。
在使用此产品之前,请认真阅读产品手册并妥善保存以备日后参考。
适用产品本手册适用于iSecure Center客户端。
本手册描述了iSecure Center客户端,指导您完成相关配置与操作。
符号约定对于文档中出现的符号,说明如下所示。
符号说明说明说明类文字,表示对正文的补充和解释。
注意注意类文字,表示提醒用户一些重要的操作或者防范潜在的伤害和财产损失危险。
如果不加避免,有可能造成伤害事故、设备损坏或业务中断。
危险危险类文字,表示有高度潜在风险,如果不加避免,有可能造成人员伤亡的重大危险。
目录第 1 章法律声明ii第 1 章前言ii1.1 适用产品ii1.2 符号约定ii第 1 章概述61.1 简介61.2 运行环境要求61.3 登录7第 2 章事件联动82.1 实时事件监控82.2 查询事件10第 3 章图上监控113.1 资源点操作113.2 地图操作133.3 图上报警143.3.1 查看实时报警143.3.2 查询历史事件153.4 轨迹回放16第 4 章人脸监控194.1 实时识别194.2 陌生人识别194.3 重点人员识别204.4 高频人员识别204.5 以脸搜脸204.6 查询抓拍历史记录21第 5 章视频监控235.1 实时预览235.1.1 开始预览235.1.2 手动抓图245.1.3 管理视图245.1.4 云台控制255.1.4.1 设置预置点265.1.4.2 设置巡航265.1.4.3 设置轨迹275.1.5 轮巡预览285.1.6 辅屏预览285.1.7 广播285.1.8 自定义预览工具栏295.2 远程回放315.2.1 回放视频文件315.2.1.1 常规回放315.2.1.2 同步回放325.2.2 添加标签335.2.3 下载录像文件335.2.4 自定义回放工具栏345.3 预览和回放设置355.4 全景监控375.4.1 开启全景预览375.4.2 全景视频参数设置38第 6 章电视墙396.1 资源管理396.1.1 添加电视墙396.1.2 添加解码设备406.1.2.1 添加在线解码设备40 6.1.2.2 通过IP地址添加设备41 6.1.3 关联解码通道436.2 电视墙配置436.2.1 配置取流模式436.2.2 拼接电视墙446.2.3 配置虚拟LED456.3 解码上墙466.3.1 预览上墙476.3.1.1 监控点预览上墙476.3.1.2 场景上墙496.3.1.3 模拟信号源上墙506.3.2 回放上墙526.3.3 桌面上墙536.3.4 开窗和漫游536.4 场景管理556.4.1 添加场景566.4.2 设置监控点轮巡576.4.3 设置场景切换计划576.5 配置电视墙参数58第 7 章门禁管理607.1 控制门状态607.2 收藏夹管理617.2.1 添加收藏夹617.2.2 添加门禁点到收藏夹61 7.3 查看门禁事件62第 8 章停车场638.1 控制道闸638.2 查看过车记录638.3 查看道闸控制记录648.4 查看车位占用情况648.5 查看一户多车车辆在场状态64 第 9 章行车监控669.1 实时定位669.2 行车轨迹回放679.3 事件查询68第 10 章园区卡口69第 11 章入侵报警7111.1 控制子系统7111.2 控制防区7111.3 查看事件日志72第 12 章常规配置73第 1 章概述本客户端是平台配套的控制客户端,适用于监控中心、值班室、指挥调度室等场合。
EKP管理员手册_系统初始配置
蓝凌标准产品EKP系统管理员手册系统初始配置页脚内容0文档控制/Document Control文档属性模板修改记录页脚内容1文档修改记录审阅记录页脚内容2分发页脚内容3目录第一章应用系统初始过程讲解 (9)第二章ADMIN.DO的设置 (10)第三章导入初始化数据 (10)3.1 系统初始化 (10)3.2 数据初始化 (13)3.2.1 导入系统基础数据 (13)3.2.2 数据导入导出 (15)3.2.2.1 导入初始化内容包 (15)3.2.2.2 不同系统间的数据导出导入 (18)第四章设置组织架构 (21)4.1.1 从其它系统同步导入 (22)4.1.2 数据导入方式创建 (23)4.1.2.1 设置导入模板 (23)4.1.2.2 下载模板 (26)4.1.2.3 导入信息 (26)页脚内容44.1.3 直接在系统中创建 (27)4.1.3.1 机构管理 (27)4.1.3.2 部门管理 (28)4.1.3.3 岗位管理 (28)4.1.3.4 员工管理 (28)第五章集团分级授权部署 (29)第六章设置系统门户 (29)第七章设置应用模块权限 (30)7.1.1 导入系统权限 (30)7.1.2 系统重要角色说明 (31)7.1.3 分配权限 (32)7.1.3.1 创建角色分配文档 (32)7.1.3.2 在角色文档中指定用户 (33)7.1.4 权限分配查询 (35)7.1.4.1 按员工查询 (35)7.1.4.2 按角色查询 (36)第八章设置系统其他必要信息 (37)页脚内容58.1.1 全系统搜索 (37)8.1.2 统一分类管理 (39)8.1.2.1 辅类别设置 (39)8.1.2.2 分类设置 (40)8.1.3 流程服务 (40)8.1.3.1 基础设置 (40)8.1.3.2 操作方式设置 (42)8.1.3.3 默认审批语设置 (45)8.1.4 订阅管理 (47)8.1.5 个人设置内容维护 (48)8.1.6 个人收藏夹 (49)8.1.7 关联管理 (50)8.1.8 排班管理 (54)第九章系统升级向导 (56)9.1 代码升级部署 (56)9.2 配置ADMIN.DO (56)9.3 系统升级向导 (56)页脚内容6第十章系统配置(管理员工具箱) (60)10.1 数据库检测 (60)10.1.1 一键检测:按整个应用进行检测 (63)10.1.1.1 一键检测 (63)10.1.1.2 开始修复 (64)10.1.1.3 重新检测 (66)10.1.2 高级选项:按应用模块进行检测 (67)10.1.2.1 开始检测 (67)10.1.2.2 开始修复 (69)10.1.2.3 重新检测 (69)10.2 常用工具集 (69)10.2.1 查看数据字典 (70)10.2.2 查看模块信息 (72)10.2.3 修改log4j级别 (72)10.2.4 重新加载数据字段 (73)10.2.5 重新创建索引 (73)10.2.6 重新生成自定义表单JSP (74)页脚内容710.3 群集信息 (75)10.4 W EB服务管理 (75)10.5 数据源 (76)10.6 日志管理 (77)10.7 在线统计 (78)10.8 产品许可证 (80)页脚内容8第一章应用系统初始过程讲解【概述】描述系统服务器启动后,用管理员账号登录系统该做哪些事情和创建哪些数据。
欧陆风云秘籍

神风之后.请用~呼出控制台.神风之前请用ALT+1 6 8 呼出控制台然后输入.event IDcash 5000金stability 加稳定prestige 加威望spy 得到5个间谍diplomat 得到5个外交官missionary 得到5传教士merchant 得到5商人colonist 得到5殖民者1051 首都加入神圣罗马帝国3071-3079 殖民事件(强化殖民率)3081-3082 叛军3091-3093 叛军3094 叛军占领国土3095-3096 部队改革事件4001 科技体制改拉丁人4002 科技体制改东方宗教4003 科技体制改拉丁人4011 改革,投资成本各项+24021 选稳定或声望4022 科学进展+选稳定或声望4023 陆军投资+选稳定或声望4024 海军投资+选稳定或声望4025 降低支出+选稳定或声望4026 贸易投资+选稳定或声望4027 传教士+选稳定或声望4028 行政投资+选稳定或声望4029 移民队+选稳定或声望4030 情报员+选稳定或声望4031外交+选稳定或声望4032商人+选稳定或声望4033税收增加+选稳定或声望4034人身解放+选稳定或声望4035质量至上+选稳定或声望4036开扩创新+选稳定或声望4041-4042 国家改革事件(还算良性)5001 天主教5002 新教5003 伊斯兰教逊尼派5004 伊斯兰教什叶派5005-5007 叛军或减少税收5008 1声望或50钱5009 1声望或100钱5010 2声望或200钱5011 2声望或300钱5012 2声望或500钱5013 +1000金钱VS+2声望5014 失去声望+5军事传统+5海洋传统5015 +10军事传统VS+1稳定+2声望5016-5018 不吉利啊(丢钱或丢声望) 5019-5021 好年景5022 +5远洋收入+3移民队5023 +3商人团5024 +3外交官5025 声望或名誉二选一5026 人口丢失或者发生瘟疫5027 10陆军传统5028 12陆军传统5029 15陆军传统5030 20陆军传统5031 投入1000金钱到陆军25陆军传统5032 10陆军传统5033 12陆军传统5034 15陆军传统5035 20陆军传统5036 投入2500金钱到海军25陆军传统5037 首都基础收入增加或后备兵员增加5038 首都基础收入增加或后备兵员增加5039 首都基础收入增加或后备兵员增加5040 稳定,陆军+100,+50钱5041 政府投资+2005042 政府投资+4005043 政府投资+10005044 政府投资+25005045-5048 不吉利啊(丢钱)5051 人身解放+15052-5053 不吉利啊(丢钱或丢声望) 5054 加名誉15055 +3通货膨胀5056 获得宣战理由或+60关系5057 首都+2要塞5058 贵族政治+15059 贸易震荡或丢50钱5060 稳定少15061 因循守旧+15062 首都人口增长+10或开拓创新+1 5063-5064 不吉利啊5065 金钱政治+15066-5069 税收减少5070 贸易收入+%505071 税收减少5072 税收增加5073 税收基数+15074 增加预备兵员5075-5081 地方分权+15082 金钱政治+15083 进攻战略+1质量至上+15084 质量至上+15085 声望+55086 因循守旧+1或开拓创新+1 5087 获得核心省份5088 得到宣战理由(我得到的是波兰) 5089 中央集权+15090-5092 丢50钱5092 重商主义+25093-5095 得到宣战理由5096 和一国家改善关系5097 人身拘束或人身解放+15098 +1稳定5099 重商主义或自由贸易+16000 -20大洋传统+10陆地传统6001 -20陆地传统+10大洋传统6002 进攻战略或防御战略+16003 中央集权或地方分权6004 2情报员6005 7叛军6006 7叛军6007 割地或宣战6011-6015 提高国家稳定性。
Solaris系统管理员手册

S o l a r i s系统管理员手册目录第 1 章、前言..........................................................................................................................1.1 认识超级用户状态....................................................................................................1.1.1 成为超级用户〔 su〕........................................................................................1.1.2 退出超级用户状态...........................................................................................1.1.3 以 root 注册.......................................................................................................1.2 与用户通讯.................................................................................................................1.2.1 在注册时显示系统专用信息...........................................................................1.2.2 将信息发送给单个用户...................................................................................发送一个短信息给一个单独的用户..................................................................将作为一个文件的信息发给个别用户..............................................................1.2.3 将信息发送给一个系统或网络中的所适用户...............................................1.2.4 经过电子邮件发送信息...................................................................................1.3 启动和关闭系统.........................................................................................................1.3.1 选择 init 状态....................................................................................................查察系统运行级..................................................................................................使用掉电状态,运行级0...................................................................................使用系统管理员状态,运行级1.......................................................................使用多用户状态,运行级2...............................................................................使用远程资源共享状态,运行级3...................................................................使用取代多用户状态,运行级4.......................................................................使用交互重引导状态,运行级5.......................................................................使用重引导状态,运行级6...............................................................................使用单用户状态,运行级s 或 S.......................................................................改变运行级..........................................................................................................1.3.2 选择所用的关闭命令.....................................................................................................................................................................................................................和 init ...............................................................................................................................................................................................................................................................................................................................................................................1.3.3 引导系统 ..........................................................................................................引导到多用户状态 ..............................................................................................引导到单用户状态 ..............................................................................................交互式引导 ..........................................................................................................查察引导信息 ......................................................................................................增加新的硬件后引导系统..................................................................................退回引导进度 ......................................................................................................1.3.4 关闭系统 ...........................................................................................................关闭一个多用户系统 ..........................................................................................关闭系统:可选方式 ..........................................................................................1.4 监察进度 .....................................................................................................................1.4.1 ps 命令报告的内容 ...........................................................................................1.4.3 杀死进度 ...........................................................................................................1.5 根本管理工具 .............................................................................................................1.5.1 经常使用的命令...............................................................................................在文件系统中搬动 ..............................................................................................查察在文件系统中所处的地址..........................................................................改变目录 ..............................................................................................................查察文件的相关信息 ..........................................................................................显示文件信息 ......................................................................................................查找一个文件 ......................................................................................................查察一个文件的种类 ..........................................................................................查察文件中的信息 ..............................................................................................查找文件中的字符串 ..........................................................................................查察文件 ..............................................................................................................阅读文件 ..............................................................................................................查察文件尾 ..........................................................................................................查察文件头 ..........................................................................................................改变文件的全部权和赞同权..............................................................................改变文件组 ..........................................................................................................设置或显示系统环境 ..........................................................................................定义 Bourne 和 Korn shell 环境变量 .................................................................定义 C shell 环境变量 ........................................................................................显示环境变量的设置 ..........................................................................................使用 PATH 变量 .................................................................................................设置 Bourne 和 Korn shell 路径 .........................................................................设置 C shell 路径 ................................................................................................1.5.2 使用管理工具 ...................................................................................................第 2 章、根本 OS 命令 ...........................................................................................................2.1 查找用户信息 .............................................................................................................2.1.1 确定系统中有谁注册.......................................................................................使用 who 命令 .....................................................................................................使用 finger 命令 ..................................................................................................使用 rusers - 1 命令 ..........................................................................................使用 whodo 命令 .................................................................................................2.1.2 检查用户的用户号和组号(id 命令 ) .................................................................2.2 查寻环境信息 .............................................................................................................2.3 创立和编写文件 .........................................................................................................2.3.1 使用 cat 命令 .....................................................................................................2.3.2 使用 touch 命令 ................................................................................................2.3.3 文件拷贝〔 cp〕或更名〔 mv〕 ......................................................................2.3.4 文本编写器的使用...........................................................................................2.3.5 vi 的使用 ...........................................................................................................2.4 命令组合及输出重新定向.........................................................................................2.4.1 在同一命令行里键入多个命令.......................................................................2.4.2 输出重新定向 (<>) ............................................................................................2.4.3 组合命令 (|) ........................................................................................................2.5.1 显示手册〔 man〕 ............................................................................................2.5.2 找命令节号〔 whatis、man〕 ..........................................................................2.6 查阅磁盘信息 .............................................................................................................2.6.1 显示磁盘空间的信息〔 df -k〕 ....................................................................2.6.2 鉴识某文件系统可否为当地文件系统〔df〕 ................................................2.6.3 找出某各种类已安装的文件系统〔df -F 〕....................................................第 3 章、设备管理 ..................................................................................................................3.1 磁带的使用 .................................................................................................................3.1.1 磁带设备的命名习惯.......................................................................................使用缺省密度规定驱动器号..............................................................................为磁带机指定密度 ..............................................................................................指定 "不倒带 "选项 ..............................................................................................不同样磁带控制器和介质的设备名缩写..............................................................英寸卷绕式非 SCSI 内接 (Rack mounted)磁带机 .............................................英寸 SCSI 盒式和 1/2 英寸前部装入的卷绕式磁带机....................................螺线扫描磁带机 ..................................................................................................3.1.2 读写磁带的命令...............................................................................................拉紧磁带 ..............................................................................................................倒带 ......................................................................................................................列出磁带机状态 ..................................................................................................3.2 磁带与软盘操作 ........................................................................................................3.2.1 tar 命令 ..............................................................................................................向磁带写文件 (tar) ...............................................................................................列出磁带上的文件 (tar) .......................................................................................向磁带上增加文件 (tar) .......................................................................................从磁带中析取文件 (tar) .......................................................................................命令 ............................................................................................................................将某目录下的全部文件拷入磁带(cpio) ............................................................列出磁带上的文件 (cpio) ....................................................................................析取磁带上全部文件 (cpio) ................................................................................自磁带中析取个别文件 (cpio) ............................................................................软盘的使用 ..........................................................................................................3.2.3 软驱设备名 .......................................................................................................文件系统的软盘........................................................................................................格式化 ufs 软盘 ...................................................................................................自软驱中取出软盘 ..............................................................................................将 ufs 文件拷入单张格式化过软盘...................................................................列出软盘上的文件 ..............................................................................................向一个格式化好的软盘上附加文件(tar) ...........................................................从软盘上拷出文件 (tar) .......................................................................................自软盘上拷出 bar 格式的文件 (cpio) .................................................................3.2.5 使用多张软盘存档...........................................................................................在软盘上创立一个ufs 文件系统 (newfs /dev/rdiskette)....................................文件系统的软盘........................................................................................................格式化 pcfs(DOS)文件系统软盘 .......................................................................卸掉 pcfs 软盘 .....................................................................................................3.3 硬盘命名管理 .............................................................................................................3.3.1 硬盘命名习惯 ...................................................................................................带有总线控制器的硬盘的使用..........................................................................带有直接驱动器的硬盘的使用..........................................................................3.3.2 检查硬盘使用情况...........................................................................................3.3.3 检查硬盘信息 (Prtvtoc) .....................................................................................将文件存档 ..........................................................................................................将硬盘上文件拷出 ..............................................................................................修复坏块 ..............................................................................................................重新格式化硬盘 ..................................................................................................换下旧硬盘 ..........................................................................................................参加错误表对硬盘进行格式化、分区及标志..................................................重建文件系统 (newfs)..........................................................................................在临时安装点安装文件系统(mount) .................................................................向文件系统转储文件 (ufsrestore) .......................................................................自临时装入点拆卸文件系统(umount)其方法以下 : ..........................................检查文件系统的不一致性(fsck) ........................................................................对恢复文件系统做0 级备份 ..............................................................................在永久安装点安装文件系统(mount) .................................................................第 4 章、文件系统管理 ..........................................................................................................4.1 文件系统种类 .............................................................................................................4.1.1 磁盘文件系统 ...................................................................................................4.1.2 网络文件系统 ...................................................................................................4.1.3 伪文件系统 .......................................................................................................临时文件系统 (tmpfs) ..........................................................................................循环文件系统 (lofs) .............................................................................................进度文件系统 (procfs) .........................................................................................其他伪文件系统 ..................................................................................................缺省的文件系统 .......................................................................................4.3 虚假文件系统表 (/etc/vfstab) ......................................................................................4.3.1 文件系统表项的建立......................................................................................4.4 文件管理命令 .............................................................................................................4.4.1 一般命令语法规那么...........................................................................................4.4.2 一般文件系统命令和特别文件系统命令手册...............................................4.4.3 利用文件系统命令确定文件系统种类...........................................................4.4.4 文件系统种类 ...................................................................................................4.5 怎样使文件系统有效..........................................................................................4.5.1 安装与拆卸 .......................................................................................................安装与拆卸文件系统命令..................................................................................查找已安装的文件系统......................................................................................安装 /etc/vfstab 文件中的全部文件系统............................................................安装特定种类的文件系统..................................................................................安装单个文件系统〔 mount〕 ...........................................................................拆卸全部的远程文件系统〔umountall -F nfs〕 ...............................................拆卸个其他文件系统 (umount) ...........................................................................自动安装程序 ...................................................................................................共享效劳器文件 ...............................................................................................检查文件系统的数据一致性 (fsck) ............................................................................决定文件系统可否需检测 ...............................................................................以交互方式检测文件系统 ...............................................................................备份和恢复文件系统 .................................................................................................用 QIC-150 盒式磁带备份文件系统 (ufsdump)...............................................实现增量备份 ......................................................................................................恢复备份文件系统 ...........................................................................................决定使用哪一备份带 ..........................................................................................恢复全部备份 ......................................................................................................交互式恢复文件 ..................................................................................................从备份带中恢复单个文件 ( ufsrestore) ..............................................................第 5 章、管理网络效劳 ..........................................................................................................检查远程系统状态 .....................................................................................................确定一个远程系统已运行了多长时间 ...........................................................确定一个远程系统可否在运行 (ping\rup\rpcinfo-p) .......................................注册到一个远程系统 (rlogin) .....................................................................................系统之间传达文件 (rcp、ftp) .....................................................................................使用 RCP 命令 ..................................................................................................使用文件传达程序 (ftp) ....................................................................................第 6 章、管理用户帐号和用户组 ..........................................................................................6.1 增加和管理用户帐号 .................................................................................................6.1.1 增加用户帐号 ...................................................................................................编写 Passwd数据库 ............................................................................................定义用户组 ..........................................................................................................建立主目录 (home director).................................................................................自动安装目录 ......................................................................................................用 nfs 安装主目录 ...............................................................................................定义初化文件 ......................................................................................................建立用户的邮件帐号 ..........................................................................................建立口令 ..............................................................................................................6.1.2 管理用户帐号 ...................................................................................................改正用户帐号 ......................................................................................................取消用户帐号 ......................................................................................................冻结用户帐号 ......................................................................................................6.2 设置和管理用户组 .....................................................................................................6.2.1 设置 Group 数据库中的域值...........................................................................设置组名 (Group Name)域 ..................................................................................设置 Group ID 域 ................................................................................................设置成员表域 ......................................................................................................6.2.2 建立缺省的 UNIX 用户组 ...............................................................................6.2.3 建立新的组 .......................................................................................................6.2.4 改正或删除用户组...........................................................................................改正某个组 ..........................................................................................................删除某个组 ..........................................................................................................第 7 章、 UNIX 的 shell 命令 .................................................................................................7.1 各种 shell 的公共命令 ...............................................................................................设置某种缺省 shell ...........................................................................................在命令行中改变 shell 种类 (sh,csh,ksh).....................................................从 shell 讲解器中退出 (exit) .............................................................................去除一个 shell 窗口 (clear) ...............................................................................7.2 标准 shell ....................................................................................................................标准 shell 的初始文件 ......................................................................................定义标准 shell 的环境变量 ..............................................................................7.3 C shell..........................................................................................................................的初始文件 ................................................................................................................环境变量的定义 ........................................................................................................建立 C shell 的别名 ..........................................................................................设置 C shell 的历史功能 ..................................................................................使用 C shell 历史功能 ......................................................................................设置 C shell 的退格键 (stty erase).....................................................................新命令的嵌入 ...................................................................................................历史命令的编写........................................................................................................7.4 Korn shell ....................................................................................................................的初始化文件 ............................................................................................................的选择项 ....................................................................................................................创立 Korn shell 的别名 .....................................................................................用 Korn shell 的联机编写器编写命令 .............................................................设置 Korn shell 的历史 .....................................................................................显示 Korn shell 的历史命令 .............................................................................使用 Korn shell 的历史命令 .............................................................................编写 Korn shell 的历史命令 .............................................................................第 8 章、管理系统 ..................................................................................................................8.1 显示系统专有信息 .....................................................................................................确定主机 ID 号〔 sysdef -h〕 ...........................................................................确定硬件种类 (uname -m).................................................................................确定办理机种类 (uname -p)..............................................................................确定 OS 版本号〔 uname -r〕 ..........................................................................显示系统配置信息 (prtconf) .............................................................................确定系统已经运行了多长时间 .......................................................................确定系统的日期和时间〔 date〕 .....................................................................设置系统的日期和时间 ...................................................................................改变系统的时区〔 /etc/TIMEZONE 〕 ............................................................8.2 配置附加的交换空间〔 mkfile ,swap〕 ..................................................................8.3 创立一个当地邮件别名〔 /etc/mail/aliases〕 ...........................................................第 9 章、文件存取问题解析 ..................................................................................................9.1 诊断与查找路径相关的问题 ....................................................................................显示当前查找路径 ...........................................................................................为 Bourne 和 Korn shells 设置路径 .................................................................和 Korn shell 的初始化文件 ......................................................................................。
About Flash................................................................................

Production of multimedia content using FlashDepartment of Electronics and Computer Science, University of Southampton1. AbstractMacromedia Flash is one of the most powerful web authoring tools available to web designers today and is used to produce animated and still graphics. However, because of the poor use of Flash animations on the Internet, Flash has acquired a reputation for poor usability. Macromedia itself Macromedia itself and other individuals have produced tools and documentation to help designers make the most out of Flash have now published many usability tips. If these are followed, good multimedia content can be produced which is usable to others.ContentsKeywords ............................................................................................. 1 Introduction .......................................................................................... 1 Background .......................................................................................... 2 Research.............................................................................................. 2 About Flash ..................................................................................... 3 Flash Usability ................................................................................. 3 Alternatives to Flash........................................................................ 4 My Film ............................................................................................ 4 Conclusions.......................................................................................... 9 References......................................................................................... 102. KeywordsMacromedia Flash, Multimedia Content Creation, Animation Graphics, Sound, Video,3. IntroductionThe aim of this paper is to look at multimedia content produced by Macromedia Flash. Flash has become very popular over the past few years; 474 million Internet users use it today. In this paper I research into how Flash is used by developers today and why to give a background into the use of Flash. The advantages and disadvantages of Flash as a multimedia content creation tool are discussed to help developers to decide if Flash is a suitable tool for their project. A number of usability tips for Flash have been put together by a number of individuals, which it is recommended to follow if a usable Flash application is to1be made. I will research into these and outline them. I will also research briefly into alternatives to Flash. To fully understand how to create multimedia applications with Flash, I made a small movie of my own in Flash. I will describe the nature of my film and how it was created. Finally, I will evaluate my film and report my findings and give a summary of my experiences using Macromedia Flash.4. BackgroundFlash was first introduced in 1996 and was known as FutureSplash Animator and run by a company called FutureWave. It was used to play back animation on web browsers through Java. The company decided to sell off their technology due to financial difficulties, they tried Adobe who turned them down, but were soon bought by Macromedia. FutureSplash Animator became Macromedia Flash 1.0. There are 2 main components to the Flash software, which are: • Flash Editor – which is used to create the graphics and animation that make up the end movie • Plug-in or Flash Player – which is used by web-browsers to display the Flash movie Flash can be used to create movies, which incorporate graphics, sound and animation. These movies are generally placed on web sites on the Internet. The main reason web designers use Flash is because it provides a good online user interface, allowing visitors to interact with a web site. Also, animation is known to have a tremendous effect on human peripheral vision and therefore is a good way to relay information to people. Unfortunately, bad use of Flash on web sites has left Flash with a tarnished reputation. Most people either love it or hate it. Even though Flash is very popular on the Internet, many people find the Flash content unusable and annoying. The main arguments for Flash content being unusable are as follows: • The majority of Flash content is unnecessary and gratuitous • Content is usually built once and then not updated regularly • Content usually follows the established standards for Web content5. ResearchFirstly, it is important to look at reasons why and why not to use Flash as a way of conveying information on the Internet. These reasons are outlined below. Advantages of using Flash: • Flash films are browser independent; therefore they can be viewed with any browser, so is not limited. • Designers are able to control colours, fonts and resolution quality, and so can make their films to their needs. • As vector graphics are used, films can be scaled without it affecting the image resolution and objects will be smaller than their bitmap equivalents.2• •Animated and interactive films can be produced with sound, which will be more appealing to visitors, and get information across more easily. Flash software is very powerful, well supported and updated frequently.Disadvantages of using Flash: • Flash is quite a hard piece of software to learn, it may take developers a significant amount of time to learn to use the flash development environment • A plug-in is required to view Flash films, so not all machines will be able to view Flash films. • Flash does not have a user-friendly interface and it not intuitive for designers, and therefore might take designers longer to produce multimedia content. • Printing Flash movies results in poor text quality. • Search engines are unable to read Flash movies, so they do not show up. • It takes longer to create a Flash website than the usual HTML ones.About Flash Flash files have the .SWF extension. These files combine code, media and data into a format that is compact. These are loaded using a steaming model, where the first few frames become available to view once. The files are also cached, so that they can be retrieved again locally, saving time. Video and audio are streamed, which means that MP3 content can be dynamically loaded and player, and that full-motion films can be added. The Sorenson Spark Codec is used for high quality playback with low bandwidth. Flash uses a compressing/decompressing model to help lower network costs. Developers can compress their code when publishing the movie, and when a user wants to run this, it is decompressed on the user’s machine at runtime. Flash Usability One of the main problems with Flash is that it is known to have poor usability. Some usability tips have been produced by individuals. Macromedia’s Flash Usability tips: [/software/flash/productinfo/usability/tips/] • Remember user goals • Remember site goals • Avoid unnecessary intros • Provide logical navigation and interactivity • Design for consistency • Don’t overuse animation • Use sound sparingly • Target low-bandwidth users • Design for accessibility • Test for usability3Alternatives to Flash Flash is not the only development tool available to create multimedia content. A brief discussion of alternatives is presented below. Synchronized Multimedia Integration Language (SMIL) – this is a mark-up language (XML) which is used to write interactive multimedia content. Developers can define the temporal behaviour of their content and the layout of this on screen. Video and audio can be streamed with together with other media types. Scalable Vector Graphics (SVG) – this is a language used to describe two dimensional vector based graphics. It allows for images, text and vector and vector graphic shapes. The Document Object Model (DOM) includes full XML DOM, which allows for effective vector animation via scripting. My Film I used Macromedia Flash to create a small animated film which is to be placed on my university website. I had only ever encountered these types of films on the Internet, but never made one of my own. I also had never used Flash before, so it was a new experience. My film is titled “How to Turn a Geek into a Super Stud”, and shows through animated and still graphics how you can make a geek into a super stud! It can be viewed at /~mkg100 There are some important concepts that need to be understood before starting with Flash, these are described below. • SYMBOLS – these are graphics that have been created by using the drawing tools, and can be used over and over again within the film. • LAYERS – these can be thought of as transparent sheets that are placed on top of each other. Objects can be drawn on one layer without affecting objects in other layers. • FRAMES – displays the contents of I second of the film; a film is made of a series of frames. • KEYFRAMES – these are frames where changes in animation occur. The first frame in a frame is automatically a keyframe. • TIMELINE – shows the frames in all the layers of the film, and what events are occurring in the frames. The film starts of with the opening screen which shows the title, with a moving flashy yellow border, and a button, which when pressed will start the main part of the film. These three objects are placed in their own layers (I made a new layer for each). To place the title on screen, I created a layer called text (Insert ! Layer) and had to use the Text tool from the drawing tools, which works pretty much the same way as the ones found in other programs. You just have to enter the required text into the4box, and change the font size, type and alignment, as you so please. I also inserted a keyframe at frame 25 (Insert ! Keyframe), as this is the last frame that the text appears in. To insert the keyframe, you have to have that particular frame selected from the timeline. I created a new layer for the yellow flashy border, which was created by using keyframes and motion tweening. Motion tweening is used to change the size of objects or rotate them in an animated manner. I placed a keyframe every 5 frames, up to frame 25, and changed the size of the border in each one by transforming the shape (Window ! Inspectors ! Transform), or you could use the re-size option in the drawing tools to change the size. I then inserted the motion tween in each keyframe (Insert ! Create Motion Tween), which makes the border move from one size to the other. These 25 frames run continuously until the arrow button is pressed. This was achieved by selecting frame 25 in this layer and modifying the frame properties (Modify ! Frame ! Actions tab). I added a ‘Go to’ action and specified the frame to ‘go to and play’ scene 1, frame 1; the beginning of the film. The red arrow was also created in another layer, using the drawing tools, and was then turned into a button (Insert ! Convert to Symbol ! Button). When the cursor is placed over the button, the arrow increases in size. To do this you have to select the arrow button and then edit the object (Edit ! Edit Selected). This brings up a new scene with just the button in it. The timeline at the top of the screen has frames for ‘up’, ‘down’, ‘over’ and ‘hit’. You need to edit the button design in each frame depending on what you want the button to do when the corresponding actions occur. In this case, in the ‘over’ frame I drew an enlarged arrow by using the re-size tool. When the arrow button is pressed, the film jumps to the next screen, which starts in frame 30. The button performs this action by editing the buttons properties (Modify ! Instance ! Actions tab). I added a ‘Go to’ action and specified the frame ‘go to and play’ at as frame 30. Again I added a keyframe at frame 25, as this is the last frame for the arrow. There is another layer in this screen, which displays the background. In this instance the layer is empty as the background is white. The next scene shows the geek and ‘Mandy’s Geek Transformer’ machine, which starts from frame 30. The background is now a sea blue colour, which I created by drawing a large box with the drawing tools to fill the screen. The background layer must be the layer at the bottom so that all the other objects can be place on top of it. I created a new layer for the geek and placed a keyframe at frame 30. In this frame I used the drawing tools to create the geek. I then used drawing tools to create the speech bubble and then added a text box inside this to add the words. I also wanted some to be played at this frame; the geek saying “hello, my names Colin”. I had recorded some voices earlier with my microphone onto my5computer. I then imported this sound into Flash (File ! Import ! select sound file). I wanted the sound to be played at frame 30, so created a new layer for this sound. I then edited the frame properties to play the required sound file (Modify ! Frame ! Sound tab ! select file from drop down box) at this frame. Then I added another keyframe at frame 45, as this is the frame in which the transformer machine enters the film. I wanted the film to stop here until the button on the machine is pressed. Therefore, I set an action to frame 45 in the geek layer called ‘Stop’. This causes the film to stop at that frame until another event is triggered; in this case, the red button on the machine is selected. The machine is also drawn in a new layer and is created with the drawing tools. The title is drawn using the text facility. The red circle on the machine is a button whose action is to ‘go to and play’ at frame 50. At frame 50, I placed keyframes in the geek layer and the machine layer, as I wanted the objects in this layer to be displayed on screen but I deleted the geek’s speech bubble, as it was no longer required. I then created another layer, which starts at frame 50. This layer contains the rays that shoot out of the machine when the button is pressed and the ‘zap’ graphic. I drew the rays and zap with the drawing tools and then inserted another keyframe in this layer 3 frames down, frame 53, and used the re-size tool to reduce the size of the rays. I then used motion tweening to make the ray’s change in size on an animated way. I repeated this until frame 71, increasing and decreasing the size of the rays each time, with motion tweening between each. This was to give a shooting rays effect. I moved the ‘zap’ graphic in each of these keyframes as well with the aid of the arrow tool from the drawing tools. During the zapping, the geek shouts “Nooo!” which occurs from frame 50 to frame 82. Again I used the drawing tools to create this.After the zapping has finished the film has reached frame 83. The layer that contains the machine is no longer needed, so there are no frames for this layer anymore. In the geek layer, the geek has a speech bubble beside him, which was made by the drawing tools. The only layers active at this point are the one with the geek in it and the background.6Now the geek transformation begins!In this scene, which starts at frame 98, I entered a keyframe and deleted the glasses from the geek and added a text box, both changes were made to the geek layer. I also drew some new eyes with the drawing tools and placed them over the old eye. I left this scene and all the others after this on for 15 frames in order to give people time read the text and note the difference in the geek.This scene starts at frame 113, where I placed a keyframe. I deleted the spots from the geeks face and entered new text into the text box.Another keyframe was placed at frame 128 in the geek layer. I drew another mouth using the drawing tools and placed it over the old one. I also edited the text in the text box.I placed another keyframe at frame 143 in the geek layer. I deleted the excess hair from the nose and ears with the aid of the eraser tool from the drawing tools. I then re-drew the hair using the paintbrush tool. Again, I edited the text.7This keyframe was added at frame 158 in the geek layer. I used the drawing tools to change the shape of the face and changed the text.A keyframe was inserted at frame at 173, and again drawing tools were used to change the shape of the body.This keyframe is at frame 188 and I used the fill tool to change the colours of the clothes.This is the last scene and the keyframe was inserted at frame 203 and I used the text tool to edit the text. I also created a button using the drawing tool to draw it. I then added an action to the button, which is ‘go to and play’ frame 1, which is the beginning of the film. I also added some sound to this frame, which says “hey baby!”, by changing the frame properties.8This concludes my film. The final step is to convert the Flash file into a movie so that is can be viewed in Flash players (File ! Export Movie ! specify file name and Save).6. ConclusionsI found Macromedia Flash a very powerful tool. It allowed me to draw pictures and make simple animations quite easily. I found Flash relatively easy to use when drawing basic pictures and animations, but it started to get very complicated when I attempted to produce more advanced animations. In my film, where the rays bombard the geek, I tried to animate the geek so that it looked like he was getting electrocuted. Unfortunately I was unable to do this. When I animated the geek Flash automatically turned the geek into a symbol, which meant that I was unable to change the appearance of the geek after this. This meant that I could not finish my film as the last part of the film is concerned with editing the appearance of the geek. I therefore decided that it would be more beneficial to not have the animated geek, but to have the appearance of the geek change. Flash has a large variety of tools, but there are far too many to learn. It would take a tremendous amount of time to fully learn all the tools and functions available. Also, as there are lots of things that Flash can do, it is hard to know exactly what can be done, as lots of time would be required to learn everything. It can also get very confusing knowing what does what. There are a number of tutorials that are available in the Flash software, which cover: • Basic drawing • Concepts • Buttons • Simple animation • Streaming audio These tutorials are extremely useful as you can learn enough to make a simple film and are very easy to follow. There are step-by-step instructions on how to make objects and lots of screen dumps so you can check if you are doing the right thing. Flash also has a good Help, where you can search on keywords. The concept of layers in Flash is extremely useful as it helps to organise objects. You can also colour code the layers, which helps to show which objects belong to which layer, especially when there are a lot of objects. It is also possible to lock layers, which is useful when you do not want to accidentally change objects, Making simple animations is quite straight forward, especially since there is a whole tutorial on it. But it is a lot harder to make complex animations, as there is no extra help. I found Flash quite easy to use, but to fully master it would take a lot of time and energy. It is very good for making multimedia content, as it allows you to incorporate graphics with animation and sound without any programming knowledge. It can annoying sometimes as it can quite awkward to draw objects as you want and it could benefit from more advanced drawing tools. Also, more help is needed on how to produce animations.97. References1. /alertbox/9512.html (last accessed 13/12/02) 2. http://www/iboost/com/build/design/articles/pageview/603.htm (last accessed 13/12/02) 3. /acrlnec/sigs/itig/tc_july_aug2000.htm (last accessed 13/12/02) 4. /software/flash/productinfo/usability/tips/ (last accessed 13/12/02) 5. /macromedia/events/john_gay/page04.html# (last accessed 13/12/02) 6. /approach/ (last accessed 13/12/02) 7. Allaire.J, Macromedia Flash MX – A next - generation rich client 8. /archives/2000/10/desirevu2/ (last accessed 13/12/02) 9. /TR/smil20/ (last accessed 13/12/02) 10. /Graphics/SVG/Overview.htm8 (last accessed 13/12/02)10。
(实例教程)Cisco-PT

(实例教程)Cisco-PT网路设备模拟器Packet Tracer教程第一章认识Packet Tracer软件 (3)第二章交换机的基本配置与管理 (5)第三章交换机的端口配置与管理 (9)第四章交换机的Telnet远程登陆配置 . 13 第五章交换机的端口聚合配置 (20)第六章交换机划分Vlan配置 (27)第七章三层交换机基本配置 (33)第八章利用三层交换机实现VLAN间路由 (36)第九章快速生成树配置 (43)第十章路由器的基本配置 (48)第十一章路由器单臂路由配置 (55)第十二章路由器静态路由配置 (59)第十三章路由器RIP动态路由配置 (65)第十四章路由器OSPF动态路由配置.. 72 第十五章路由器综合路由配置 (78)第十六章标准IP访问控制列表配置 (84)第十七章扩展IP访问控制列表配置 (91)第十八章网络地址转换NAT配置 (97)第十九章网络端口地址转换NAPT配置 (103)第一章认识Packet Tracer软件Packet Tracher介绍●Packet Tracer是Cisco公司针对CCNA认证开发的一个用来设计、配置和故障排除网络的模拟软件。
●Packer Tracer模拟器软件比Boson功能强大,比Dynamips操作简单,非常适合网络设备初学者使用。
学习任务1、安装Packer Tracer;PC2 ping Gateway Timeout第二章交换机的基本配置与管理实验目标●掌握交换机基本信息的配置管理。
实验背景●某公司新进一批交换机,在投入网络以后要进行初始配置与管理,你作为网络管理员,对交换机进行基本的配置与管理。
技术原理●交换机的管理方式基本分为两种:带内管理和带外管理。
●通过交换机的Console端口管理交换机属于带外管理;这种管理方式不占用交换机的网络端口,第一次配置交换机必须利用Console端口进行配置。
●通过Telnet、拨号等方式属于带内管理。
明御运维审计与册风险控制系统用户手册

资料范本本资料为word版本,可以直接编辑和打印,感谢您的下载明御运维审计与册风险控制系统用户手册地点:__________________时间:__________________说明:本资料适用于约定双方经过谈判,协商而共同承认,共同遵守的责任与义务,仅供参考,文档可直接下载或修改,不需要的部分可直接删除,使用时请详细阅读内容明御®运维审计与风险控制系统杭州安恒信息技术有限公司目录 TOC \o "1-3" \h \z \uHYPERLINK \l "_Toc374114606" 明御®运维审计与风险控制系统PAGEREF _Toc374114606 \h 1HYPERLINK \l "_Toc374114607" 目录PAGEREF _Toc374114607 \h 2 HYPERLINK \l "_Toc374114608" 前言PAGEREF _Toc374114608 \h 1 HYPERLINK \l "_Toc374114609" 章节概要 PAGEREF _Toc374114609 \h 1 HYPERLINK \l "_Toc374114610" 适用范围和先决条件PAGEREF_Toc374114610 \h 2HYPERLINK \l "_Toc374114611" 支持信息 PAGEREF _Toc374114611 \h 2 HYPERLINK \l "_Toc374114612" 第一章产品简介PAGEREF_Toc374114612 \h 4HYPERLINK \l "_Toc374114613" 1.1 产品概要PAGEREF_Toc374114613 \h 4HYPERLINK \l "_Toc374114614" 1.2 应用场景PAGEREF_Toc374114614 \h 5HYPERLINK \l "_Toc374114615" 第二章概念阐述PAGEREF_Toc374114615 \h 7HYPERLINK \l "_Toc374114616" 2.1 架构原理PAGEREF_Toc374114616 \h 7HYPERLINK \l "_Toc374114617" 2.2 权限模型PAGEREF_Toc374114617 \h 8HYPERLINK \l "_Toc374114618" 2.3 部署模式PAGEREF_Toc374114618 \h 10HYPERLINK \l "_Toc374114619" 2.4 支持的协议和客户端PAGEREF _Toc374114619 \h 11HYPERLINK \l "_Toc374114620" 第三章系统基本信息PAGEREF _Toc374114620 \h 13HYPERLINK \l "_Toc374114621" 3.1 出厂默认信息PAGEREF _Toc374114621 \h 13HYPERLINK \l "_Toc374114622" 第四章产品部署PAGEREF_Toc374114622 \h 14HYPERLINK \l "_Toc374114623" 4.1 外观示意图PAGEREF_Toc374114623 \h 14HYPERLINK \l "_Toc374114624" 4.1.1 前段面板PAGEREF_Toc374114624 \h 14HYPERLINK \l "_Toc374114625" 4.2 连接线缆PAGEREF_Toc374114625 \h 16HYPERLINK \l "_Toc374114626" 4.2.1 连接电源线PAGEREF_Toc374114626 \h 16HYPERLINK \l "_Toc374114627" 4.2.2 连接数据口线PAGEREF _Toc374114627 \h 16HYPERLINK \l "_Toc374114628" 4.3 配置IP PAGEREF_Toc374114628 \h 16HYPERLINK \l "_Toc374114629" 第五章登录PAGEREF _Toc374114629 \h 19HYPERLINK \l "_Toc374114630" 5.1 登录系统PAGEREF_Toc374114630 \h 19HYPERLINK \l "_Toc374114631" 第六章用户和用户组PAGEREF _Toc374114631 \h 20_Toc374114632 \h 20HYPERLINK \l "_Toc374114633" 6.1.1 新建用户PAGEREF_Toc374114633 \h 20HYPERLINK \l "_Toc374114634" 6.1.2 编辑用户PAGEREF_Toc374114634 \h 23HYPERLINK \l "_Toc374114635" 6.1.3 删除用户PAGEREF_Toc374114635 \h 25HYPERLINK \l "_Toc374114636" 6.1.4 导入用户PAGEREF_Toc374114636 \h 25HYPERLINK \l "_Toc374114637" 6.1.5 导出用户PAGEREF_Toc374114637 \h 27HYPERLINK \l "_Toc374114638" 6.1.6 搜索用户PAGEREF_Toc374114638 \h 27HYPERLINK \l "_Toc374114639" 6.1.7 激活/锁定用户PAGEREF _Toc374114639 \h 28HYPERLINK \l "_Toc374114640" 6.1.8 批量为用户修改用户组PAGEREF _Toc374114640 \h 28HYPERLINK \l "_Toc374114641" 6.2 AD用户管理PAGEREF_Toc374114641 \h 29HYPERLINK \l "_Toc374114642" 6.3 LDAP用户管理PAGEREF _Toc374114642 \h 29HYPERLINK \l "_Toc374114643" 6.4 RADIUS用户管理PAGEREF _Toc374114643 \h 29HYPERLINK \l "_Toc374114644" 6.5 用户组管理PAGEREF_Toc374114644 \h 30_Toc374114645 \h 30HYPERLINK \l "_Toc374114646" 6.5.2 编辑用户组PAGEREF_Toc374114646 \h 31HYPERLINK \l "_Toc374114647" 6.5.3 删除用户组PAGEREF_Toc374114647 \h 32HYPERLINK \l "_Toc374114648" 6.5.4 搜索用户组PAGEREF_Toc374114648 \h 32HYPERLINK \l "_Toc374114649" 6.5.5 添加用户组成员PAGEREF _Toc374114649 \h 33HYPERLINK \l "_Toc374114650" 6.5.6 删除用户组成员PAGEREF _Toc374114650 \h 34HYPERLINK \l "_Toc374114651" 6.5.7 搜索用户组成员PAGEREF _Toc374114651 \h 35HYPERLINK \l "_Toc374114652" 第七章资产PAGEREF _Toc374114652 \h 36HYPERLINK \l "_Toc374114653" 7.1 主机管理PAGEREF_Toc374114653 \h 36HYPERLINK \l "_Toc374114654" 7.1.1 添加主机PAGEREF_Toc374114654 \h 36HYPERLINK \l "_Toc374114655" 7.1.2 编辑主机PAGEREF_Toc374114655 \h 38HYPERLINK \l "_Toc374114656" 7.1.3 删除主机PAGEREF_Toc374114656 \h 39HYPERLINK \l "_Toc374114657" 7.1.4 导入主机PAGEREF_Toc374114657 \h 40HYPERLINK \l "_Toc374114658" 7.1.5 搜索主机PAGEREF_Toc374114658 \h 42HYPERLINK \l "_Toc374114659" 7.1.6 启用/禁用主机PAGEREF _Toc374114659 \h 42HYPERLINK \l "_Toc374114660" 7.1.7 添加主机标签PAGEREF _Toc374114660 \h 43HYPERLINK \l "_Toc374114661" 7.1.8 删除主机标签PAGEREF _Toc374114661 \h 44HYPERLINK \l "_Toc374114662" 7.1.9 批量为主机修改标签PAGEREF _Toc374114662 \h 45HYPERLINK \l "_Toc374114663" 7.2 帐户管理PAGEREF_Toc374114663 \h 45HYPERLINK \l "_Toc374114664" 7.2.1 添加主机帐户PAGEREF _Toc374114664 \h 46HYPERLINK \l "_Toc374114665" 7.2.2 编辑主机帐户PAGEREF _Toc374114665 \h 48HYPERLINK \l "_Toc374114666" 7.2.3 删除主机帐户PAGEREF _Toc374114666 \h 50HYPERLINK \l "_Toc374114667" 7.2.4 导入主机账户PAGEREF _Toc374114667 \h 51HYPERLINK \l "_Toc374114668" 7.2.5 导出主机账户PAGEREF _Toc374114668 \h 52HYPERLINK \l "_Toc374114669" 7.2.6 搜索主机帐户PAGEREF _Toc374114669 \h 53HYPERLINK \l "_Toc374114670" 7.2.7 添加主机账户标签PAGEREF _Toc374114670 \h 53HYPERLINK \l "_Toc374114671" 7.2.8 删除主机账户标签PAGEREF _Toc374114671 \h 54HYPERLINK \l "_Toc374114672" 7.3 应用托管PAGEREF_Toc374114672 \h 55HYPERLINK \l "_Toc374114673" 7.3.1 查看应用托管PAGEREF _Toc374114673 \h 55HYPERLINK \l "_Toc374114674" 7.3.2 导出应用托管PAGEREF _Toc374114674 \h 56HYPERLINK \l "_Toc374114675" 7.3.3 添加应用托管PAGEREF _Toc374114675 \h 58HYPERLINK \l "_Toc374114676" 7.3.4 删除应用托管PAGEREF _Toc374114676 \h 60HYPERLINK \l "_Toc374114677" 7.3.5 应用托管搜索PAGEREF _Toc374114677 \h 61HYPERLINK \l "_Toc374114678" 7.4 密码托管PAGEREF_Toc374114678 \h 61HYPERLINK \l "_Toc374114679" 7.4.1 新建任务PAGEREF_Toc374114679 \h 61HYPERLINK \l "_Toc374114680" 7.4.2 开始/暂停任务PAGEREF _Toc374114680 \h 63HYPERLINK \l "_Toc374114681" 7.4.3 删除任务PAGEREF_Toc374114681 \h 64HYPERLINK \l "_Toc374114682" 7.4.4 已托管密码PAGEREF_Toc374114682 \h 65HYPERLINK \l "_Toc374114683" 7.4.5 手动改密PAGEREF_Toc374114683 \h 67HYPERLINK \l "_Toc374114684" 7.4.6 邮件方式发送托管密码PAGEREF _Toc374114684 \h 68HYPERLINK \l "_Toc374114685" 7.4.7 ftp方式发送托管密码PAGEREF _Toc374114685 \h 70HYPERLINK \l "_Toc374114686" 第八章策略PAGEREF _Toc374114686 \h 72HYPERLINK \l "_Toc374114687" 8.1 访问规则PAGEREF_Toc374114687 \h 72HYPERLINK \l "_Toc374114688" 8.1.1 查看访问规则PAGEREF _Toc374114688 \h 72HYPERLINK \l "_Toc374114689" 8.1.2 添加访问规则PAGEREF _Toc374114689 \h 73HYPERLINK \l "_Toc374114690" 8.1.3 编辑访问规则PAGEREF _Toc374114690 \h 74HYPERLINK \l "_Toc374114691" 8.1.4 删除访问规则PAGEREF _Toc374114691 \h 76HYPERLINK \l "_Toc374114692" 8.1.5 启用/禁用访问规则 PAGEREF _Toc374114692 \h 76HYPERLINK \l "_Toc374114693" 8.1.6 搜索访问规则PAGEREF _Toc374114693 \h 77HYPERLINK \l "_Toc374114694" 8.2 行为规则PAGEREF_Toc374114694 \h 78HYPERLINK \l "_Toc374114695" 8.2.1 查看行为规则PAGEREF _Toc374114695 \h 78HYPERLINK \l "_Toc374114696" 8.2.2 添加行为规则PAGEREF _Toc374114696 \h 79_Toc374114697 \h 81HYPERLINK \l "_Toc374114698" 8.2.4 删除行为规则PAGEREF _Toc374114698 \h 82HYPERLINK \l "_Toc374114699" 8.2.5 启用/禁用行为规则 PAGEREF _Toc374114699 \h 83HYPERLINK \l "_Toc374114700" 8.2.6 搜索行为规则PAGEREF _Toc374114700 \h 84HYPERLINK \l "_Toc374114701" 8.2.7 查看行为规则命令PAGEREF _Toc374114701 \h 85HYPERLINK \l "_Toc374114702" 8.2.8 添加行为规则命令PAGEREF _Toc374114702 \h 86HYPERLINK \l "_Toc374114703" 8.2.9 删除行为规则命令PAGEREF _Toc374114703 \h 87HYPERLINK \l "_Toc374114704" 8.2.10 搜索行为规则命令PAGEREF _Toc374114704 \h 88HYPERLINK \l "_Toc374114705" 8.2.11 查看行为规则命令组PAGEREF _Toc374114705 \h 89HYPERLINK \l "_Toc374114706" 8.2.12 添加行为规则命令组PAGEREF _Toc374114706 \h 91HYPERLINK \l "_Toc374114707" 8.2.13 删除行为规则命令组PAGEREF _Toc374114707 \h 92HYPERLINK \l "_Toc374114708" 8.2.14 搜素行为规则命令组PAGEREF _Toc374114708 \h 93HYPERLINK \l "_Toc374114709" 8.3 审计规则PAGEREF_Toc374114709 \h 94_Toc374114710 \h 95HYPERLINK \l "_Toc374114711" 8.3.2 添加审计规则PAGEREF _Toc374114711 \h 95HYPERLINK \l "_Toc374114712" 8.3.3 编辑审计规则PAGEREF _Toc374114712 \h 97HYPERLINK \l "_Toc374114713" 8.3.4 删除审计规则PAGEREF _Toc374114713 \h 98HYPERLINK \l "_Toc374114714" 8.3.5 启用/禁用审计规则 PAGEREF _Toc374114714 \h 99HYPERLINK \l "_Toc374114715" 8.3.6 搜索审计规则PAGEREF _Toc374114715 \h 100HYPERLINK \l "_Toc374114716" 8.4 策略日志PAGEREF_Toc374114716 \h 100HYPERLINK \l "_Toc374114717" 8.4.1 查看访问规则日志PAGEREF _Toc374114717 \h 100HYPERLINK \l "_Toc374114718" 8.4.2 搜索访问规则日志PAGEREF _Toc374114718 \h 101HYPERLINK \l "_Toc374114719" 8.4.3 查看行为规则日志PAGEREF _Toc374114719 \h 102HYPERLINK \l "_Toc374114720" 8.4.4 搜索行为规则日志PAGEREF _Toc374114720 \h 103HYPERLINK \l "_Toc374114721" 8.4.5 查看审计规则日志PAGEREF _Toc374114721 \h 104HYPERLINK \l "_Toc374114722" 8.4.6 搜索审计规则日志PAGEREF _Toc374114722 \h 105HYPERLINK \l "_Toc374114723" 8.5 策略配置PAGEREF_Toc374114723 \h 106HYPERLINK \l "_Toc374114724" 8.5.1 查看策略配置PAGEREF _Toc374114724 \h 106HYPERLINK \l "_Toc374114725" 8.5.2 启用/禁用规则PAGEREF _Toc374114725 \h 106HYPERLINK \l "_Toc374114726" 第九章审计PAGEREF _Toc374114726 \h 108HYPERLINK \l "_Toc374114727" 9.1 会话审计PAGEREF_Toc374114727 \h 108HYPERLINK \l "_Toc374114728" 9.1.1 查看会话PAGEREF_Toc374114728 \h 108HYPERLINK \l "_Toc374114729" 9.1.2 审计会话PAGEREF_Toc374114729 \h 109HYPERLINK \l "_Toc374114730" 9.1.3 搜索会话PAGEREF_Toc374114730 \h 111HYPERLINK \l "_Toc374114731" 9.1.4 查看事件PAGEREF_Toc374114731 \h 111HYPERLINK \l "_Toc374114732" 9.1.5 审计事件PAGEREF_Toc374114732 \h 112HYPERLINK \l "_Toc374114733" 9.1.6 搜索事件PAGEREF_Toc374114733 \h 114HYPERLINK \l "_Toc374114734" 9.2 会话报表PAGEREF_Toc374114734 \h 114HYPERLINK \l "_Toc374114735" 9.2.1 主机标签PAGEREF_Toc374114735 \h 114HYPERLINK \l "_Toc374114736" 9.2.2 主机协议PAGEREF_Toc374114736 \h 115HYPERLINK \l "_Toc374114737" 9.2.3 会话数量趋势PAGEREF _Toc374114737 \h 117HYPERLINK \l "_Toc374114738" 9.2.4 主机会话数量PAGEREF _Toc374114738 \h 118HYPERLINK \l "_Toc374114739" 9.2.5 用户会话数量PAGEREF _Toc374114739 \h 119HYPERLINK \l "_Toc374114740" 9.2.6 主机会话源IP PAGEREF _Toc374114740 \h 120HYPERLINK \l "_Toc374114741" 9.2.7 用户会话源IP PAGEREF _Toc374114741 \h 121HYPERLINK \l "_Toc374114742" 9.2.8 访问告警等级PAGEREF _Toc374114742 \h 122HYPERLINK \l "_Toc374114743" 9.2.9 行为告警等级PAGEREF _Toc374114743 \h 123HYPERLINK \l "_Toc374114744" 9.2.10 审计告警等级PAGEREF _Toc374114744 \h 124HYPERLINK \l "_Toc374114745" 9.2.11 主机访问告警PAGEREF _Toc374114745 \h 125HYPERLINK \l "_Toc374114746" 9.2.12 主机行为告警PAGEREF _Toc374114746 \h 126HYPERLINK \l "_Toc374114747" 9.2.13 主机审计告警PAGEREF _Toc374114747 \h 127HYPERLINK \l "_Toc374114748" 9.2.14 用户访问告警PAGEREF _Toc374114748 \h 128HYPERLINK \l "_Toc374114749" 9.2.15 用户行为告警PAGEREF _Toc374114749 \h 129HYPERLINK \l "_Toc374114750" 9.2.16 用户审计告警PAGEREF _Toc374114750 \h 130HYPERLINK \l "_Toc374114751" 9.2.17 源IP访问告警PAGEREF _Toc374114751 \h 131HYPERLINK \l "_Toc374114752" 9.2.18 源IP行为告警PAGEREF _Toc374114752 \h 132HYPERLINK \l "_Toc374114753" 9.2.19 源IP审计告警PAGEREF _Toc374114753 \h 133HYPERLINK \l "_Toc374114754" 9.2.20 导出会话报表PAGEREF _Toc374114754 \h 134HYPERLINK \l "_Toc374114755" 第十章系统PAGEREF _Toc374114755 \h 135HYPERLINK \l "_Toc374114756" 10.1 安全配置PAGEREF_Toc374114756 \h 135HYPERLINK \l "_Toc374114757" 10.1.1 用户锁定配置PAGEREF _Toc374114757 \h 135HYPERLINK \l "_Toc374114758" 10.1.2 密码策略配置PAGEREF _Toc374114758 \h 136HYPERLINK \l "_Toc374114759" 10.1.3 登录配置PAGEREF_Toc374114759 \h 138HYPERLINK \l "_Toc374114760" 10.1.4 双因素认证PAGEREF_Toc374114760 \h 139HYPERLINK \l "_Toc374114761" 10.1.5 管理员登录配置PAGEREF _Toc374114761 \h 140HYPERLINK \l "_Toc374114762" 10.2 网络配置PAGEREF_Toc374114762 \h 142HYPERLINK \l "_Toc374114763" 10.2.1 查看网络配置PAGEREF _Toc374114763 \h 142HYPERLINK \l "_Toc374114764" 10.2.2 接口配置PAGEREF_Toc374114764 \h 143HYPERLINK \l "_Toc374114765" 10.2.3 DNS配置PAGEREF_Toc374114765 \h 144HYPERLINK \l "_Toc374114766" 10.2.4 协议端口配置PAGEREF _Toc374114766 \h 146HYPERLINK \l "_Toc374114767" 10.2.5 Web端口配置PAGEREF_Toc374114767 \h 148HYPERLINK \l "_Toc374114768" 10.3 SNMP配置PAGEREF_Toc374114768 \h 149HYPERLINK \l "_Toc374114769" 10.4 告警配置PAGEREF_Toc374114769 \h 151HYPERLINK \l "_Toc374114770" 10.4.1 邮件告警PAGEREF_Toc374114770 \h 151HYPERLINK \l "_Toc374114771" 10.4.2 Syslog告警PAGEREF_Toc374114771 \h 153HYPERLINK \l "_Toc374114772" 10.4.3 选择等级PAGEREF_Toc374114772 \h 155HYPERLINK \l "_Toc374114773" 10.5 认证配置PAGEREF_Toc374114773 \h 157HYPERLINK \l "_Toc374114774" 10.5.1 启用/禁用认证PAGEREF _Toc374114774 \h 157HYPERLINK \l "_Toc374114775" 10.5.2 LDAP认证配置PAGEREF _Toc374114775 \h 158HYPERLINK \l "_Toc374114776" 10.5.3 同步LDAP用户PAGEREF _Toc374114776 \h 160HYPERLINK \l "_Toc374114777" 10.5.4 AD认证配置PAGEREF_Toc374114777 \h 161HYPERLINK \l "_Toc374114778" 10.5.5 同步AD用户 PAGEREF_Toc374114778 \h 163HYPERLINK \l "_Toc374114779" 10.5.6 RADIUS认证配置PAGEREF _Toc374114779 \h 164HYPERLINK \l "_Toc374114780" 10.6 系统日志配置PAGEREF _Toc374114780 \h 166HYPERLINK \l "_Toc374114781" 10.7 系统报表PAGEREF_Toc374114781 \h 168HYPERLINK \l "_Toc374114782" 10.7.1 系统状态信息PAGEREF _Toc374114782 \h 168HYPERLINK \l "_Toc374114783" 10.7.2 操作重要性PAGEREF_Toc374114783 \h 169HYPERLINK \l "_Toc374114784" 10.7.3 用户控制PAGEREF_Toc374114784 \h 171HYPERLINK \l "_Toc374114785" 10.7.4 主机控制PAGEREF_Toc374114785 \h 172HYPERLINK \l "_Toc374114786" 10.7.5 会话控制PAGEREF_Toc374114786 \h 174HYPERLINK \l "_Toc374114787" 10.7.6 用户与资产操作PAGEREF _Toc374114787 \h 175HYPERLINK \l "_Toc374114788" 10.7.7 用户源IP PAGEREF_Toc374114788 \h 176HYPERLINK \l "_Toc374114789" 10.7.8 异常用户PAGEREF_Toc374114789 \h 178HYPERLINK \l "_Toc374114790" 10.7.9 异常IP PAGEREF_Toc374114790 \h 180HYPERLINK \l "_Toc374114791" 10.7.10 导出系统报表PAGEREF _Toc374114791 \h 181HYPERLINK \l "_Toc374114792" 10.8 系统日志PAGEREF_Toc374114792 \h 182HYPERLINK \l "_Toc374114793" 10.8.1 查看系统日志PAGEREF _Toc374114793 \h 182HYPERLINK \l "_Toc374114794" 10.8.2 搜索系统日志PAGEREF _Toc374114794 \h 183HYPERLINK \l "_Toc374114795" 10.9 数据维护PAGEREF_Toc374114795 \h 184HYPERLINK \l "_Toc374114796" 10.9.1 数据自动删除PAGEREF _Toc374114796 \h 184HYPERLINK \l "_Toc374114797" 10.9.2 数据手动删除PAGEREF _Toc374114797 \h 185HYPERLINK \l "_Toc374114798" 10.9.3 日志备份PAGEREF_Toc374114798 \h 186HYPERLINK \l "_Toc374114799" 10.9.4 新建会话备份任务PAGEREF _Toc374114799 \h 188HYPERLINK \l "_Toc374114800" 10.9.5 开始/暂停会话备份任务PAGEREF _Toc374114800 \h 190HYPERLINK \l "_Toc374114801" 10.9.6 删除会话备份任务PAGEREF _Toc374114801 \h 191HYPERLINK \l "_Toc374114802" 10.10 系统维护PAGEREF_Toc374114802 \h 192HYPERLINK \l "_Toc374114803" 10.10.1 系统状态PAGEREF_Toc374114803 \h 192HYPERLINK \l "_Toc374114804" 10.10.2 许可证管理-查看许可证PAGEREF _Toc374114804 \h 193HYPERLINK \l "_Toc374114805" 10.10.3 许可证管理-导出系统认证PAGEREF _Toc374114805 \h 194HYPERLINK \l "_Toc374114806" 10.10.4 许可证管理-导出许可证PAGEREF _Toc374114806 \h 196HYPERLINK \l "_Toc374114807" 10.10.5 许可证管理-导入许可证PAGEREF _Toc374114807 \h 198HYPERLINK \l "_Toc374114808" 10.10.6 系统管理-时间同步 PAGEREF _Toc374114808 \h 200HYPERLINK \l "_Toc374114809" 10.10.7 系统管理-系统升级 PAGEREF _Toc374114809 \h 201HYPERLINK \l "_Toc374114810" 10.10.8 系统管理-重启及恢复PAGEREF _Toc374114810 \h 203HYPERLINK \l "_Toc374114811" 10.10.9 系统配置备份与还原PAGEREF _Toc374114811 \h 204HYPERLINK \l "_Toc374114812" 10.10.10 磁盘管理-查看磁盘信息PAGEREF _Toc374114812 \h 206HYPERLINK \l "_Toc374114813" 10.10.11 磁盘管理-磁盘检测 PAGEREF _Toc374114813 \h 207HYPERLINK \l "_Toc374114814" 10.10.12 磁盘管理-磁盘同步 PAGEREF _Toc374114814 \h 208HYPERLINK \l "_Toc374114815" 10.10.13 调试日志PAGEREF_Toc374114815 \h 209HYPERLINK \l "_Toc374114816" 10.10.14 系统警报PAGEREF_Toc374114816 \h 210HYPERLINK \l "_Toc374114817" 10.10.15 网络诊断连通性测试PAGEREF _Toc374114817 \h 212HYPERLINK \l "_Toc374114818" 10.10.16 网络诊断TCPDump抓包PAGEREF _Toc374114818 \h 213HYPERLINK \l "_Toc374114819" 10.10.17 系统诊断PAGEREF_Toc374114819 \h 215HYPERLINK \l "_Toc374114820" 第十一章运维PAGEREF _Toc374114820 \h 217HYPERLINK \l "_Toc374114821" 11.1 会话管理PAGEREF_Toc374114821 \h 217HYPERLINK \l "_Toc374114822" 11.1.1 查看会话PAGEREF_Toc374114822 \h 217HYPERLINK \l "_Toc374114823" 11.1.2 会话监控PAGEREF_Toc374114823 \h 218HYPERLINK \l "_Toc374114824" 11.1.3 阻断会话PAGEREF_Toc374114824 \h 220HYPERLINK \l "_Toc374114825" 11.1.4 事件监控PAGEREF_Toc374114825 \h 221HYPERLINK \l "_Toc374114826" 11.2 应用中心PAGEREF_Toc374114826 \h 223HYPERLINK \l "_Toc374114827" 11.2.1 查看应用托管PAGEREF _Toc374114827 \h 223HYPERLINK \l "_Toc374114828" 11.2.2 搜索应用托管PAGEREF _Toc374114828 \h 223HYPERLINK \l "_Toc374114829" 11.2.3 下载单点登录器PAGEREF _Toc374114829 \h 224HYPERLINK \l "_Toc374114830" 11.2.4 应用托管单点登录PAGEREF _Toc374114830 \h 224HYPERLINK \l "_Toc374114831" 11.3 主机运维PAGEREF_Toc374114831 \h 226HYPERLINK \l "_Toc374114832" 11.3.1 查看运维主机PAGEREF _Toc374114832 \h 226HYPERLINK \l "_Toc374114833" 11.3.2 添加运维主机标签PAGEREF _Toc374114833 \h 226HYPERLINK \l "_Toc374114834" 11.3.3 修改运维主机标签PAGEREF _Toc374114834 \h 228HYPERLINK \l "_Toc374114835" 11.3.4 删除运维主机标签PAGEREF _Toc374114835 \h 229HYPERLINK \l "_Toc374114836" 11.3.5 下载单点登录器PAGEREF _Toc374114836 \h 230HYPERLINK \l "_Toc374114837" 11.3.6 下载第三方客户端PAGEREF _Toc374114837 \h 230HYPERLINK \l "_Toc374114838" 11.3.7 单点登录全局配置PAGEREF _Toc374114838 \h 231HYPERLINK \l "_Toc374114839" 11.3.8 单点登录细粒配置PAGEREF _Toc374114839 \h 232HYPERLINK \l "_Toc374114840" 11.3.9 主机运维单点登录PAGEREF _Toc374114840 \h 233HYPERLINK \l "_Toc374114841" 11.3.10 主机运维快速登录PAGEREF _Toc374114841 \h 235HYPERLINK \l "_Toc374114842" 11.4 命令审批PAGEREF_Toc374114842 \h 236HYPERLINK \l "_Toc374114843" 11.4.1 开启命令审批功能PAGEREF _Toc374114843 \h 237HYPERLINK \l "_Toc374114844" 11.4.2 命令审批PAGEREF_Toc374114844 \h 238HYPERLINK \l "_Toc374114845" 第十二章运维授权PAGEREF_Toc374114845 \h 241HYPERLINK \l "_Toc374114846" 12.1 用户授权账户PAGEREF _Toc374114846 \h 241HYPERLINK \l "_Toc374114847" 12.1.1 查看用户授权账户PAGEREF _Toc374114847 \h 241HYPERLINK \l "_Toc374114848" 12.1.2 添加用户授权账户PAGEREF _Toc374114848 \h 242HYPERLINK \l "_Toc374114849" 12.1.3 删除用户授权账户PAGEREF _Toc374114849 \h 243HYPERLINK \l "_Toc374114850" 12.1.4 搜索用户授权账户PAGEREF _Toc374114850 \h 245HYPERLINK \l "_Toc374114851" 12.2 用户组授权账户PAGEREF _Toc374114851 \h 246HYPERLINK \l "_Toc374114852" 12.2.1 查看用户组授权账户PAGEREF _Toc374114852 \h 246HYPERLINK \l "_Toc374114853" 12.2.2 添加用户组授权账户PAGEREF _Toc374114853 \h 248HYPERLINK \l "_Toc374114854" 12.2.3 删除用户组授权账户PAGEREF _Toc374114854 \h 249HYPERLINK \l "_Toc374114855" 12.2.4 搜索用户组授权账户PAGEREF _Toc374114855 \h 250HYPERLINK \l "_Toc374114856" 12.3 账户授权用户/用户组PAGEREF _Toc374114856 \h 252HYPERLINK \l "_Toc374114857" 12.3.1 查看账户授权用户PAGEREF _Toc374114857 \h 252HYPERLINK \l "_Toc374114858" 12.3.2 添加账户授权用户PAGEREF _Toc374114858 \h 253HYPERLINK \l "_Toc374114859" 12.3.3 删除账户授权用户PAGEREF _Toc374114859 \h 254HYPERLINK \l "_Toc374114860" 12.3.4 搜索账户授权用户PAGEREF _Toc374114860 \h 256HYPERLINK \l "_Toc374114861" 12.3.5 查看账户授权用户组PAGEREF _Toc374114861 \h 257HYPERLINK \l "_Toc374114862" 12.3.6 添加账户授权用户组PAGEREF _Toc374114862 \h 258HYPERLINK \l "_Toc374114863" 12.3.7 删除账户授权用户组PAGEREF _Toc374114863 \h 260HYPERLINK \l "_Toc374114864" 12.3.8 搜索账户授权用户组PAGEREF _Toc374114864 \h 261HYPERLINK \l "_Toc374114865" 12.4 应用托管授权用户/用户组PAGEREF _Toc374114865 \h 262HYPERLINK \l "_Toc374114866" 12.4.1 应用托管授权用户PAGEREF _Toc374114866 \h 262HYPERLINK \l "_Toc374114867" 12.4.2 应用托管授权用户组PAGEREF _Toc374114867 \h 263HYPERLINK \l "_Toc374114868" 12.5 账户未授权登录PAGEREF _Toc374114868 \h 264HYPERLINK \l "_Toc374114869" 12.5.1 运维授权配置PAGEREF _Toc374114869 \h 264HYPERLINK \l "_Toc374114870" 12.5.2 未授权登录PAGEREF_Toc374114870 \h 266HYPERLINK \l "_Toc374114871" 12.5.3 授权审核PAGEREF_Toc374114871 \h 268前言章节概要第一章产品简介介绍明御®运维审计与风险控制系统(DAS-USM)的主要功能和目的。
ZDC(智达康) ZG-5000-HB500-64 用户手册

ZG-5000-HB500-64用户手册版权说明本公司的用户手册并无任何明确或隐含的保证,包括为了特殊目的进行销售或安装的保证。
本公司有对手册进行更改或修订之权力,若有更改恕不另行通知。
未经本公司的书面许可不得对本手册的任何内容进行复制。
关于本手册使用本手册的目的是为了安装及使用无线接入点。
本手册包括配置过程及方法协助客户解决不可预见的问题。
为了突出一些需要注意的内容,本手册用了以下特殊文字及样式来表示:表示将有潜在的危险操作会对设备的硬件造成损害或使数据全部丢失或使设备不能正常使用。
表示有重要的信息提醒您以便更好的使用设备。
粗体:表示有重要的功能或者设置步骤需要您注意。
目录第一章产品介绍 (1)产品简介 (1)LED与接口定义 (1)第二章设备安装 (3)安装准备 (3)第三章安全注意事项 (4)安装注意事项 (4)管理注意事项 (4)第四章基本配置 (5)设备的缺省配置 (5)通过Web管理界面配置设备 (6)修改基本设置 (8)修改无线参数 (10)第五章高级功能配置 (17)RADIUS 服务器 (17)V AP(虚拟多AP)设定 (19)Bridge模式下的安全设定 (24)启用 802.1Q VLAN (25)无线端访问控制 (26)配置为路由器 (27)高级设置 (28)速率加速功能 (30)管理代理 (31)Smart WDS功能 (32)第六章设备管理 (33)查看设备的基本信息 (33)查看关联的STA列表 (33)查看周围AP/STA (34)查看统计信息 (35)更改管理密码 (35)升级软件 (36)配置文件的备份和恢复 (37)恢复缺省值的方法 (38)使用管理控制功能 (39)重新启动设备 (39)远程管理 (40)查看系统日志 (44)第七章典型应用介绍 (45)无线覆盖应用 (45)无线桥接应用 (45)无线路由及DHCP服务器 (48)PPPoE应用 (50)第八章故障排除 (52)第九章技术支持 (54)附录A. 国家/区域及信道 (55)图目录图 1 产品外观 (1)图 2 安全警报 (7)图 3 登录 (7)图 4 基本信息 (8)图 5 基本设置 (9)图 6 无线设定 (11)图 7 802.1x认证体系 (17)图 8 RADIUS 服务器 (18)图 9 V AP设定 (20)图 10 安全设定 (21)图 11 Bridge模式下安全设定 (25)图 12 VLAN设定 (25)图 13 访问控制列表 (27)图 14 路由模式 (28)图 15 高级设置 (29)图 16 管理代理 (31)图 17 Smart WDS (32)图 18 基本信息 (33)图 19 STA列表 (34)图 20 邻近AP/STA列表 (34)图 21 统计信息 (35)图 22 更改密码 (36)图 23 更新软件 (36)图 24 备份恢复设定 (38)图 25 管理控制 (39)图 26 重启AP (40)图 27 远程管理设定 (41)第三章 安全注意事项使用该设备之前,请您仔细阅读安装和管理注意事项,否则您的某些操作可能会对设备造成损坏!安装注意事项1.请不要把设备或天线安装在电力线、电灯、电网附近或任何有可能接触强电电网的地方,否则可能造成设备工作不正常!2.如果是室外设备(设备GND口接地、电源适配器接地),请您保证无线接入点接地状况良好,否则可能因静电而影响设备正常工作;若安装在室外,极有可能受雷击而损害设备。
access-list(访问控制列表)总结

access-list(访问控制列表)总结ACL的作用ACL可以限制网络流量、提高网络性能。
例如,ACL可以根据数据包的协议,指定数据包的优先级。
ACL提供对通信流量的控制手段。
例如,ACL可以限定或简化路由更新信息的长度,从而限制通过路由器某一网段的通信流量。
ACL是提供网络安全访问的基本手段。
如图1所示,ACL允许主机A访问人力资源网络,而拒绝主机B 访问。
ACL可以在路由器端口处决定哪种类型的通信流量被转发或被阻塞。
例如,用户可以允许E-mail通信流量被路由,拒绝所有的Telnet通信流量。
ACL的配置ACL的配置分为两个步骤:第一步:在全局配置模式下,使用下列命令创建ACL:Router (config)# access-list access-list-number {permit | deny } {test-conditions}其中,access-list-number为ACL的表号。
人们使用较频繁的表号是标准的IP ACL(1—99)和扩展的IP ACL(100-199)。
第二步:在接口配置模式下,使用access-group命令ACL应用到某一接口上:Router (config-if)# {protocol} access-group access-list-number {in | out }其中,in和out参数可以控制接口中不同方向的数据包,如果不配置该参数,缺省为out。
ACL在一个接口可以进行双向控制,即配置两条命令,一条为in,一条为out,两条命令执行的ACL表号可以相同,也可以不同。
但是,在一个接口的一个方向上,只能有一个ACL控制。
值得注意的是,在进行ACL配置时,网管员一定要先在全局状态配置ACL表,再在具体接口上进行配置,否则会造成网络的安全隐患。
访问控制列表使用目的:1、限制网络流量、提高网络性能。
例如队列技术,不仅限制了网络流量,而且减少了拥塞2、提供对通信流量的控制手段。
信息安全系统概论-访问控制

信息安全概论-访问控制什么是访问控制Access Control主体(subject):访问的发起者发起者是试图访问某个目标的用户或者是用户行为的代理。
必须控制它对客体的访问。
主体通常为进程,程序或用户。
客体(Object):接收其他实体访问的被动实体。
可供访问的各种软硬件资源。
控制策略主体对客体的访问规则集,这个规则集直接定义了主体可以的作用行为和客体对主体的约束条件。
是主体对客体的操作行为集和约束条件集。
体现为一种授权行为。
记录谁可以访问谁。
访问控制策略任何访问控制策略最终可被模型化为访问矩阵形式。
每一行:用户每一列:目标矩阵元素:相应的用户对目标的访问许可。
访问控制关系图多级信息安全系统将敏感信息与通常资源分开隔离的系统。
通常存在两种有层次安全级别。
目标按敏感性划分为不同密级:绝密top secret、秘密secret、机密confidential、限制restricted、无密级unclassified。
无层次安全级别。
访问控制过程首先对合法用户进行验证。
(认证)然后对选用控制策略。
(控制策略的具体实现)最后对非法用户或越权操作进行审计。
(审计)认证包括主体对客体的识别认证与客体对主体的检验认证。
身份认证。
控制策略具体实现规则集设定方法。
允许授权用户、限制非法用户。
保护敏感信息。
禁止越权访问。
审计操作日志。
记录用户对系统的关键操作。
威慑。
访问控制在安全操作系统领域中,访问控制一般都涉及自主访问控制(Discretionary Access Control,DAC)强制访问控制(Mandatory Access Control,MAC)两种形式安全模型安全模型就是对安全策略所表达的安全需求的简单、抽象和无歧义的描述,它为安全策略和它的实现机制之间的关联提供了一种框架。
安全模型描述了对某个安全策略需要用哪种机制来满足;而模型的实现则描述了如何把特定的机制应用于系统中,从而实现某一特定安全策略所需的安全保护。
第七章--黎明--TMG防火墙策略配置 一--2014-01-13
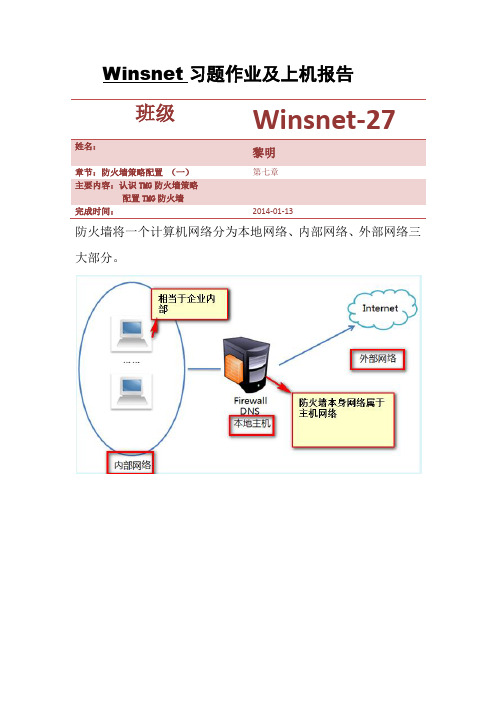
Winsnet习题作业及上机报告班级章节:防火墙策略配置(一)第七章主要内容:认识TMG防火墙策略配置TMG防火墙完成时间:2014-01-13防火墙将一个计算机网络分为本地网络、内部网络、外部网络三大部分。
边缘防火墙,双宿主防火墙网络。
3向外围网络,三宿主防火墙网络。
后端防火墙,相当于背靠背防火墙。
单一网络适配器,用于布署TMG缓存代理访问服务器。
实验:配置TMG防火墙网络第一步:配置TMG防火墙网络的IP地址参数。
第二步,单击TMG管理控制台的服务器节点,选择任务栏中的“入门配置向导”。
单击向导中的“配置网络设置”,用于重新定义防火墙体系结构及网络体、网络规则。
第三步:在配置向导中,选择网络模板是边缘防火墙模板。
第四步:选择内部网络接口的IP地址172.16.1.254,防火墙将根据IP、子网掩码计算出相对应的内部网络地址段172.16.1.1—255。
第五步:选择外部网络连接的IP地址192.168.2.254。
第六步:完成定义边缘防火墙模块后,显示当前TMG防火墙包含的网络体有内部、外部、本地主机。
第七步:单击“内部”网络体属性,查看地址,TMG所保护的内部网络段是172.16.0.0/255.255.0.0上面,简单配置边缘模板TMG防火墙完成!!!实验:创建TMG防火墙策略元素。
防火墙策略由防火墙策略元素构成,所以元素是组成防火墙规则的最基本参数。
构成防火墙规则的策略元素包括协议、用户、内容类型、计划、网络对象。
第一步:打开TMG防火墙策略元素管理面板第二步:在TMG防火墙中,默认微软已经建立了常用的通讯协议,如http、https、dhcp、dns、ping协议。
但对于部分不常用的协议,管理员需要手工建立,如腾讯QQ的通讯传输协议。
第三步:定义协议的参数,协议类型“UDP”,方向“发送接受”,端口范围从、到8000第四步:配置协议的辅助连接。
目前的网络协议,除FTP协议,同时使用tcp21、tcp20传输数据及指令,大部分协议都没有辅助连接。
XXXXXXXXXXXXXXXXXXXX系统操作手册【模板】

XXXXXXXXXXXXXXXXXXXX系统操作手册-------TRICONEX目录1.TriStation 1131操作手册 (2)2.Triconex SOE 操作手册 (8)3.Enhanced Diagnostic 诊断软件操作手册 (11)4.DDE Server 操作手册 (15)5.InTouth 操作手册 (18)6.特殊操作注释 (24)第一章TriStation 1131操作手册1.1 1131编程变量前缀,所有程序均按照此前缀编写逻辑1.2 登录到1131软件,打开软件界面在程序文件夹中双击图标,弹出:输入用户名(MANAGER)和密码(password)打开程序,在左面的菜单栏中如图所示:选择控制器画面,然后选择控制器双击连接,选择单击控制器连接,以使软件与控制器连接。
1.3 进入逻辑程序选择OK,双击右侧打开程序要看其中某一个逻辑可以双击打开需要选择的逻辑,然后选择连接并打开。
每个逻辑的都注有说明用来解释该逻辑功能,如图所示:1.4 进入逻辑块在进入到需要的程序块后,可以通过以下方式进入到每一逻辑块的每一页程序,选择可以直接看该逻辑中的某一页程序选择参数设置A组,然后按进入程序(或双击)。
1.5 在线情况修改报警值,连锁值在这个逻辑中可以修改报警联锁值,a. 双击修改报警值位号b. 选择“Disable”,然后写入新的报警联锁值(555),然后按Confirm , 新联锁值改为,然后选择Enable,修改结束。
1.6 在程序中查找逻辑中位号a. 如果不知道变量在具体哪个程序中,可以在程序文件中进行完全搜索:选择菜单栏上的,选择然后输入位号,然后点Find,搜索后,如下图:发现要找的LT_26121在程序中,然后在右侧边栏中找到相应程序并双击,如图:,就找到了相应变量。
b. 如果知道变量在具体哪个程序中,可以打开该程序,然后快捷键ctrl+F,如下图:然后选择Find First查找到第一个位置,然后选择Find Next向后查找,直到全部搜索结束。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Winsnet习题作业及上机报告
班级
章节:访问控制列表一第六章
主要内容:访问控制列表分类
配置标准访问控制列表
完成时间:2014-03-10
访问控制列表分类:严格意义上只有标准和扩展。
1.标准访问控制列表1-99
2.扩展访问控制列表100-199
3.命名访问控制列表
4.时间访问控制列表
命名访问控制列表可以解决编号取值范围不足的缺陷。
访问控制列表,实施对目标的访问限制
路由器对ACL和路由表的应用顺序,先应用ACL再查看路由表。
二层交换机MAC
三层路由器IP 访问控制列表相当于路由器“包过滤”防火墙四层服务器端口
策略路由:符合转发,不符合不转发。
访问控制列表利用4个元素定义规则。
源地址目标地址源端口目标端口
标准:源地址1-99
扩展:源地址、目标地址、源端口、目标端口。
访问控制器的应用:看到拒绝,选择离源IP最近的端口应用规则。
访问控制列表:一组判断语句的集合,规则策略的集合应用在接口。
先在全局模式定义,然后在接口应用。
如果接口上没有访问控制列表,则路由。
如果接口上有访问控制列表,则检测访问规则,依次往下判断。
第一条不匹配、则看第二条,依次往下判断,当有一条匹配,则应用,如果到最后没有一条匹配,则丢失数据包。
全局模式:
access-list 1 permit 172.16.0.0 0.0.255.255(反向掩码)
访问控制列表1允许172.16开头的IP地址通讯。
隐含的拒绝语句:
ccess-list 1 deny 0.0.0.0 255.255.255.255
关键字:host 主机
any 所有
access-list 1 permit 172.16.10.20 0.0.255.255
或access-list 1 permit host 172.16.10.20
将ACL应用于接口:
接口模式:ip access-group 1 in或out
配置ACL时顺序是很重要的。
实验:配置标准访问控制列表。
上图:禁止计算机PC 1与PC 2进行通信。
步骤:
1.配置3台路由器的ip地址,并配置静态路由条目。
2.定义ACL,并在接口应用ACL
3.验证
第一步:路由器1的接口IP地址配置。
第二步:配置路由器1的静态路由。
到达192.168.3.0/24和192.168.4.0/24网络下一跳地址是192.168.2.2.
第三步:配置路由器2、路由器3的接口IP地址。
第四步:配置路由器2、3的静态路由。
第五步:测试从计算机192.168.1.10到计算机192.168.4.10的连通性。
第六步:配置R1路由器的访问控制列表条目,在接口f0/0上应用访问控制列表,方向是in。
第七步:使用show access-list命令,查看访问控制列表配置。
第八步:测试从计算机192.168.1.10到计算机192.168.4.10的连通性。
问题:标准访问控制列表与扩展访问控制列表的区别?
答:标准ACL仅检查数据包的源地址部分,而扩展ACL的测试条件可检查数据包的源地址,也可以检查数据包的目标等多个层次。
