基于W2K的CiscoACS 2.6
思科设备型号大全

思科设备型号大全思科设备型号大全cisco路由的命名规则都是以CISCO开头比如:cisco1721,cisco2621,cisco3662,cisco3745。
这些都是路由器。
比如:cisco2621其中cisco:是品牌,后面的前两位数字是系列号,这款产品属于2600系列,后两位是具体的型号。
其中cisco路由器有以下几个系列:cisco2500系列:cisco2501、cisco2502、一直到cisco2514,这些都是国内能见到的设备,再往上就是国外的了,国内很少见到。
cisco1700:1720、1721、1751、1760cisco1800:1821、1841cisco2600系列:2610、2611、2620、2621、2651cisco2600XM系列:2610XM、2611XM、2620XM、2621XM cisco3600:3620、3640、3660cisco3700:3725、3745cisco3800:3825、3845cisco7200:7204、7206、7204VXR、7206VXR这些都是机箱,使用当中需要引擎的支持(NPE-225、NPE-300、NPE-400、NPE-G1、最新的是NPE-G2)和业务模块的支持东西很多了,这就不写了。
cisco7500:7507、7513 同样也需要引擎的支持(RSP2、RSP4、RSP8、RSP16)和业务模块的支持,7200上的业务模块都能在75上使用,需要一块VIP卡的支持。
在上面就是12000系列:12008,12016这些是目前最高端的。
同样也需要引擎和业务模块的支持。
交换:交换机的命名一般是WS开头这个是固定的,再下一个字母有两种一个是C一个是X,C代表固化交换机或者机箱,X代表的是模块。
比如看到WS- C3750-24TS-S这个型号的时候我们应该知道他是CISCO交换机固化交换机3750系列,24个以太网口,TS表示是以太口+SFP口后面的S表示是标准版的,相映的型号就是E的,属于增强型或者叫企业版。
Cisco Secure ACS认证系统

1.1.1 Cisco Secure ACS认证系统Cisco Secure ACS是思科网络准入控制(NAC)架构的重要组件。
思科NAC是思科系统公司®赞助的业界计划,使用网络基础设施迫使企图访问网络计算资源的所有设备遵守安全策略,进而防止病毒和蠕虫造成损失。
通过NAC,客户只允许遵守安全策略的可信的端点设备访问网络(如PC、服务器和个人数字助理等),并可限制违规设备的访问。
思科NAC是思科自防御网络计划的一部分,为在第二层和第三层网络上实现网络准入控制奠定了基础。
我们计划进一步扩展端点和网络安全性的互操作性,以便将动态的事故抑制功能包含在内。
这个创新将允许遵守安全策略的系统组件报告攻击期间因恶意系统或受感染的系统导致的资源误用。
因此,用户可将受感染的系统与其他网络部分动态隔离开,从而大大减少病毒、蠕虫及混合攻击的传播。
AAA管理系统Cisco Secure ACS是功能强大的访问控制服务器,为正在增加其WAN或LAN连接的机构提供了许多高性能和可扩展性特性。
表1列出了Cisco Secure ACS的主要优势。
Cisco Secure ACS的主要优势Cisco Secure ACS 4.0提供以下全新特性和优势:Cisco NAC 支持— Cisco Secure ACS 4.0用作NAC部署中的策略决策点。
使用可配置的策略,它能评估Cisco Trust Agent 提交的证书、决定主机状态、并向网络访问设备发送逐用户的授权信息:ACL、基于策略的ACL或专用的VLAN分配。
评估主机证书可执行许多特定策略,如操作系统补丁级别和防病毒DAT文件版本等。
Cisco Secure ACS记录策略评估结果以供监控系统使用。
Cisco Secure ACS 4.0还允许第三方审查供应商对没有采用适当代理技术的主机进行审查,然后再决定是否准许它访问网络。
您可通过作为Cisco Secure ACS转发证书目的地的外部策略服务器扩展Cisco Secure ACS策略。
Cisco_ACS_RSA
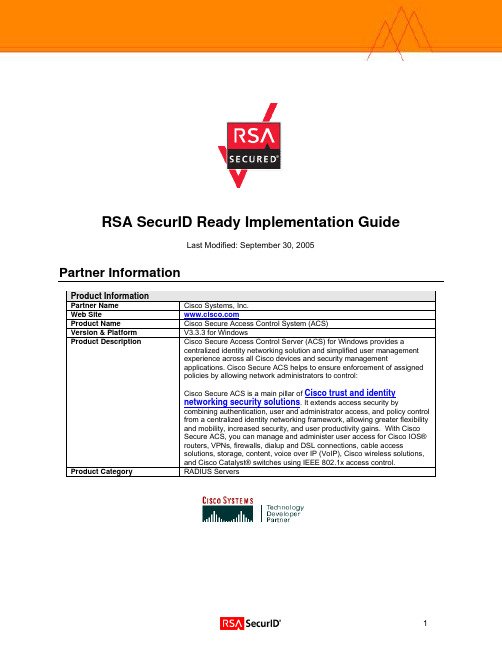
RSA SecurID Ready Implementation GuideLast Modified: September 30, 2005Partner InformationProduct InformationPartner Name Cisco Systems, Inc.Web Site Product Name Cisco Secure Access Control System (ACS)Version & Platform V3.3.3 for WindowsProduct Description Cisco Secure Access Control Server (ACS) for Windows provides acentralized identity networking solution and simplified user managementexperience across all Cisco devices and security managementapplications. Cisco Secure ACS helps to ensure enforcement of assignedpolicies by allowing network administrators to control:Cisco Secure ACS is a main pillar of Cisco trust and identitynetworking security solutions. It extends access security bycombining authentication, user and administrator access, and policy controlfrom a centralized identity networking framework, allowing greater flexibilityand mobility, increased security, and user productivity gains. With CiscoSecure ACS, you can manage and administer user access for Cisco IOS®routers, VPNs, firewalls, dialup and DSL connections, cable accesssolutions, storage, content, voice over IP (VoIP), Cisco wireless solutions,and Cisco Catalyst® switches using IEEE 802.1x access control.Product Category RADIUS ServersSolution SummaryPartner Integration OverviewAuthentication Methods Supported Native RSA SecurID AuthenticationList Library Version Used Version #5.0.3RSA Authentication Manager Name Locking YesRSA Authentication Manager Replica Support Full Replica SupportSecondary RADIUS Server Support NoLocation of Node Secret on Agent In RegistryRSA Authentication Agent Host Type Net OSRSA SecurID User Specification Designated Users, All Users, RSA SecurID as Default RSA SecurID Protection of Administrative Users NoRSA Software Token API Integration NoUse of Cached Domain Credentials NoProduct RequirementsPartner Product Requirements: Cisco Secure ACSCPU x86 550MHz or fasterMemory 256MBStorage 250MB of Hard Disk space. More disk space requiredfor configurations also running a Database.Operating SystemPlatform Required PatchesMicrosoft Windows 2000 Server Service Pack 4 or greaterMicrosoft Windows 2000 Advanced Server Service Pack 4 or greaterMicrosoft Windows 2003 Server All Service Levels SupportedMicrosoft Windows 2003 Enterprise Server All Service Levels SupportedAdditional Software RequirementsPatches Application AdditionalMicrosoft Internet Explorer 6.0 Service Pack 2Sun Java Plug-in 1.4.2-04 or Microsoft Java VirtualMachineNetscape Communicator 7.1 Sun Java Plug-in 1.4.2-04Note: Both Java and JavaScript must be enabled in the browsers used toadminister Cisco Secure ACSAgent Host ConfigurationTo facilitate communication between the Cisco Secure ACS and the RSA Authentication Manager / RSA SecurID Appliance, an Agent Host record must be added to the RSA Authentication Manager database. The Agent Host record identifies the Cisco Secure ACS within its database and contains information about communication and encryption.To create the Agent Host record, you will need the following information.• Hostname•IP Addresses for all network interfacesWhen adding the Agent Host Record, you should configure the Cisco Secure ACS as Net OS. This setting is used by the RSA Authentication Manager to determine how communication with the Cisco Secure ACS will occur.Note: Hostnames within the RSA Authentication Manager / RSA SecurIDAppliance must resolve to valid IP addresses on the local network.Please refer to the appropriate RSA Security documentation for additional information about Creating, Modifying and Managing Agent Host records.Partner Authentication Agent ConfigurationBefore You BeginThis section provides instructions for integrating the partners’ product with RSA SecurID Authentication. This document is not intended to suggest optimum installations or configurations.It is assumed that the reader has both working knowledge of all products involved, and the ability to perform the tasks outlined in this section. Administrators should have access to the product documentation for all products in order to install the required components.All vendor products/components must be installed and working prior to the integration. Perform the necessary tests to confirm that this is true before proceeding.Documenting the SolutionActivating RSA SecurID authentication:Cisco Secure ACS supports RSA SecurID authentication of users. To configure Cisco Secure ACS 3.3.3 to authenticate users with Authentication Manger 6.1, follow these steps:1. Install the Authentication Agent 5.5 for Windows on the same system as the Cisco Secure ACSserver. Verify connectivity by running the Test Authentication function of the AuthenticationAgent.2. In the navigation bar, click .3. Click Database Configuration.4. Click RSA SecurID Token Server.5. Click Create New Configuration.6. Enter a name, then click Submit.7. Click Configure.Note: Cisco Secure ACS displays the name of the token server and thepath to the authenticator DLL. This information confirms thatCisco Secure ACS can contact the RSA Authentication Agent. You can addthe RSA SecurID external user database to your Unknown User Policy orassign specific user accounts to use this database for authentication.Adding/Configuring RSA SecurID Authentication to your Unknown User Policy:1. Click .2. Click Unknown User Policy. Select Check the following external user databases, highlightRSA SecurID Token Server and move it to the Selected Databases box. Click Submit.Adding/Configuring RSA SecurID Authentication for specific user accounts:1. Click from the main ACS Admin GUI. Type in the user name and click Add.2. Under User Setup > Password Authentication, choose RSA SecurID Token Server. ClickSubmit.Certification ChecklistDate Tested: September 29, 2005Certification EnvironmentProduct Name Version Information Operating SystemRSA Authentication Manager 6.1 Windows 2003 Enterprise ServerRSA Authentication Agent 5.5 Windows 2000 Service Pack 4RSA Software Token 3.0.3 [008] Windows 2000 Service Pack 4Cisco Secure ACS 3.3.3 Windows XP Service Pack 2Mandatory FunctionalityRSA Native Protocol RADIUS ProtocolNew PIN ModeForce Authentication After New PIN Force Authentication After New PIN N/ASystem Generated PIN System Generated PIN N/AUser Defined (4-8 Alphanumeric) User Defined (4-8 Alphanumeric) N/AUser Defined (5-7 Numeric) User Defined (5-7 Numeric) N/AUser Selectable User Selectable N/ADeny 4 and 8 Digit PIN Deny 4 and 8 Digit PIN N/ADeny Alphanumeric PIN Deny Alphanumeric PIN N/APASSCODE16 Digit PASSCODE 16 Digit PASSCODE N/A4 Digit Password 4 Digit Password N/ANext Tokencode ModeNext Tokencode Mode Next Tokencode Mode N/ALoad Balancing / Reliability TestingFailover (3-10 Replicas) Failover N/A Name Locking Enabled Name Locking EnabledNo RSA Authentication Manager No RSA Authentication Manager N/AAdditional FunctionalityRSA Software Token API FunctionalitySystem Generated PIN N/A System Generated PIN N/AUser Defined (8 Digit Numeric) N/A User Defined (8 Digit Numeric) N/AUser Selectable N/A User Selectable N/ANext Tokencode Mode N/A Next Tokencode Mode N/ADomain Credential FunctionalityDetermine Cached Credential State N/A Determine Cached Credential StateSet Domain Credential N/A Set Domain CredentialRetrieve Domain Credential N/A Retrieve Domain CredentialBSD / SWA = Pass = Fail N/A = Non-Available Function11。
思科acs使用指南

思科acs使用指南English:CISCO ACS (Access Control System) is a powerful and comprehensive network access control solution that is widely used in enterprises and organizations of all sizes. It provides a secure and efficient way to authenticate, authorize, and account for users and devices trying to connect to a network.CISCO ACS offers a range of features that make it a versatile and valuable tool for network administrators. Firstly, it supports a wide variety of authentication methods, including local database, LDAP, RADIUS, and TACACS+. This flexibility allows organizations to choose the most suitable authentication method for their needs. Additionally, it supports multiple authorization and accounting protocols, ensuring compatibility with different network devices and services.Another key feature of CISCO ACS is its central management and administration capabilities. With a user-friendly web-based interface, administrators can easily configure and manage user access policies,authentication methods, and network devices. This centralized management streamlines the process of managing user access privileges and ensures consistency across the network.Furthermore, CISCO ACS provides robust auditing and reporting features. It keeps detailed logs of all authentication and access events, allowing administrators to track and investigate any suspicious activities. The reporting functionality allows administrators to generate reports on user access patterns, device usage, and other important network statistics. These reports are invaluable for network troubleshooting, capacity planning, and compliance monitoring.Additionally, CISCO ACS integrates seamlessly with other network security solutions. It can be integrated with CISCO Identity Services Engine (ISE) for advanced posture assessment and endpoint profiling. It can also be integrated with CISCO Adaptive Security Appliance (ASA) for advanced firewall and VPN capabilities. These integrations enhance the overall security and control of the network.In conclusion, CISCO ACS is a highly capable network access control solution that provides a secure and efficient way to authenticate, authorize, and account for users and devices. Its extensive features, centralized management, auditing capabilities, and integration options make it a valuable tool for network administrators in ensuring the security and compliance of their networks.中文翻译:思科ACS(Access Control System)是一种功能强大且综合的网络访问控制解决方案,在各类企业和组织中广泛应用。
cisco_acs使用

简易使用手册1.ACS 基本配置1.1设置ACS 管理员帐号Step 1>点击ACS 界面左边的Administration control 按钮,然后点击Administrator control 界面中的Add AdministratorStep 2>点击Add administrator 后出现此账户的诸多选项,逐一填写后点击Submit这里是填写管理员的密码下面的页面选项是管理员的属性选项,这里控制这个账号管理员可以拥有的权限,如果这个账号需要某个权限必须在对于权限前打对勾这个选项是控制这个管理员可以管理那个user group 的选项。
如果不选择默认是不可以管理任何组的,所以这里必须选择这个管理员可以控制的组。
控制ACS 的访问策略和HTTP 设置ACS 连接策略(idle timeout ) 管理员账号安全策略(账号长度,存活时间等)Step3>设置了管理员后就可以通过web界面登录到ACS服务器对ACS进行配置1.2 ACS网络设置(添加Tacacs+ 客户端)Step1>点击ACS界面的Network Configuration按钮,出现网络配置界面,然后点击Add Entry,这里需要注意cisco acs软件在默认情况下没有打开Network Device Groups(NDG)功能的。
如果要启用NDG功能你必须在interface Configuration中打开这个功能。
见下图:ACS高级功能设置interface Configuration这个选项控制是否打开NDG功能Step2>填写设备组的名称以及key这里需要注意,见后面注释。
注一:在这里如果填写了KEY值,那么在认证时候属于这个组的设备的KEY就全部匹配这里配置的KEY了。
而不是匹配在设备添加时候填写的KEY。
也就是说NDG的KEY的权限比在属于组的设备的KEY优先级高。
如果在认证日志里发现“Key Mismatch”的情况,首先检查设备和你配置的KEY是否一致,然后可以检查这个设备所属的组是否配置了KEY。
Cisco Secure ACS 购买指南说明书

Ordering GuideCisco Secure ACSThis document provides guidance on how to order Cisco Secure Access Control System (ACS) family products. It includes information on upgrade scenarios as well as information on software and hardware service offerings.OverviewCisco® ACS is designed to address both current and future corporate network access policy challenges. The world’s most trusted enterprise access and policy platform, it is used by more than 40,000 enterprises worldwide.The Cisco Secure ACS family includes:●Cisco Secure ACS: The Cisco flagship access and policy system, Cisco Secure ACSsupports up to hundreds of thousands of users and tens of thousands of network devices and is ideal for medium or large enterprises.●Cisco Secure ACS View: A dedicated reporting and monitoring device designed tocomplement Cisco Secure ACS, View helps ensure the highest level of network accesscontrol and compliance.●Cisco Secure ACS Express: Ideal for small and medium-sized businesses (SMBs) ormedium/small enterprises, ACS Express is an easy-to-deploy device with built-in reporting and monitoring. It supports up to 50 devices and 350 users.Cisco Secure ACSCisco Secure ACS is available as software for Windows servers (ACS for Windows) and as a dedicated appliance (ACS Solution Engine). Product part numbers are shown in Table 1. For guidelines on Cisco Secure ACS deployment, see the deployment guide at/en/US/products/sw/secursw/ps2086/prod_white_papers_list.html.Table 1. Cisco Secure ACS New Order Part NumbersPart Number DescriptionCSACS-4.2-WIN-K9 Cisco Secure ACS 4.2 for WindowsCSACSE-1113-K9 Cisco ACS Solution Engine – Cisco 1113 hardware with ACS version 4.2 preinstalledFor ACS for Windows, Software Application Support (SAS) is available. SAS entitles customers to maintenance and minor updates, plus access to online resources and support services.For ACS Solution Engine, SAS is required for software coverage and SMARTnet® is required for hardware coverage. SMARTnet has various service options to provide the hardware replacement coverage desired. For more information on SAS and SMARTnet, please visit/en/US/products/svcs/ps3034/ps2827/serv_category_home.html.Software upgrades are available for current ACS for Windows and ACS Solution Engine customers. Customers that have SAS contracts are entitled to minor upgrades. For example, a customer with SAS running ACS version 4.0 software would be entitled to ACS 4.1 and 4.2 upgrades. Customers that do not have SAS contracts can purchase minor upgrades. Part numbers for minor upgrades are identified by the “MR” designation.Customers that have SAS contracts can obtain upgrade kits using the Product Upgrade Tool (requires login) at /upgrade.SAS contracts do not cover major upgrades and these upgrades must always be purchased. For example, customers running ACS for Windows version 3.3 software that want to upgrade to ACS version 4.2 must purchase the upgrade part number CSACS-4.2-WINUP-K9.Upgrade part numbers are shown in Table 2. Note that there are different part numbers for ACS for Windows and ACS Solution Engine software upgrades.Table 2. Cisco Secure ACS Upgrade Part NumbersPart Number DescriptionCSACS4.2-WIN-MR-K9 ACS for Windows minor upgrade for customers with ACS for Windows versions 4.0 or 4.1 CSACS-4.2-WINUP-K9 ACS for Windows major upgrade for customers with ACS for Windows versions earlier than 4.0 CSACSE4.2-SW-MR-K9 ACS Solution Engine minor upgrade for customers with versions 4.0 or 4.1 (1112 or 1113hardware required)CSACSE-4.2-SWUP-K9 ACS Solution major upgrade for customers with versions earlier than 4.0 (1112 or 1113hardware required)CSACSE-1113-UP-K9 ACS Solution Engine hardware and software upgrade – for customers with 1111 or 1112hardware; includes Cisco 1113 hardware with ACS version 4.2 installedImportant: ACS Solution Engine version 4.2 is only supported on Cisco 1112 and 1113 hardware. Customers with Cisco 1111 hardware should consider upgrading to 1113 by purchasing CSACSE-1113-UP-K9. Trade-in credit may also be available through the Cisco Technology Migration Program (TMP).Cisco Secure ACS ViewCisco Secure ACS View collects and correlates data from multiple Cisco Secure ACS servers and logs to provide aggregate views of system activity as well as detailed information at the transaction level for both network access and device administration. Cisco Secure ACS View provides essential information for network monitoring and planning, access problem detection and troubleshooting, and entitlement and compliance reporting.Cisco Secure ACS View is recommended for all ACS 4.2 deployments. For guidelines on Cisco Secure ACS View deployment, see the deployment guide at/en/US/products/ps9302/prod_white_papers_list.html.Cisco Secure ACS View part numbers are shown in Table 3.Table 3. Cisco Secure ACS View Part NumbersPart Number DescriptionCSACS4.0-VIEW-K9 Cisco Secure ACS View appliance with ACS View 4.0 software and license for managing twoACS servers (version 4.1.4 or 4.2 required). ACS View does not support ACS Express.CSACS4.0-VIEWLIC License for managing an additional ACS server with Cisco Secure ACS View 4.0.For the ACS View appliance, an SAS contract is required for software coverage and SMARTnet isrequired for hardware coverage. SAS entitles customers to maintenance and minor updates, plusaccess to online resources and support services.Cisco Secure ACS ExpressCisco Secure ACS Express offers a comprehensive yet simplified feature set, a user-friendlygraphical user interface, and an attractive price point that allows placement of this product insituations where Cisco Secure ACS for Windows or Cisco Secure ACS Solution Engine may notbe suitable.Cisco Secure ACS Express part numbers are shown in Table 4.Table 4. Cisco Secure ACS Express Part NumbersPart Number DescriptionCSACS-5.0-EXP-K9 Cisco Secure ACS Express 5.0 applianceFor ACS Express, an SAS contract is required for software coverage and SMARTnet is requiredfor hardware coverage. SAS entitles customers to maintenance and minor updates, plus access toonline resources and support services.For More InformationPlease check the Cisco Secure ACS homepage at /go/acs for the latestinformation about Cisco Secure ACS.For more information contact the ACS marketing team at *****************, or contact youraccount representative.Printed in USA C07-500695-00 10/08。
CISCO低端路由器产品介绍

产品与解决方案介绍
思科顺应和引领行业发展 —20年的创新历程
Cisco 2500系列
第一个集成、全功 AGS多协议 能的中小企业及分 支办公室路由器 路由器 思科永远地改变了 网络连接与互联网
第一百万台 2500系列路 由器发货!
Cisco 2600 系列面世
Cisco 1600 系列面世
小企业
SB100
C2600XM C850/870 C1700 C800 SOHO
适用于大中小型各类企业/运营商用户 —思科多业务集成路由器产品线
市场定位 大企业 中型企业 小企业
3800 Series 2800 Series 高密度及高新性能 提供并发多业务 内置的高级话音、视频、数据及安全服务 高性能集成安全与数据 安全的宽带和无线连接
适用于小型机构的全新Cisco 800 系列集成多 业务路由器
• 为小型机构中的宽带接入提供了出色性能
• 先进的安全特性包括:
• • • • 状态化检测防火墙 IPSec VPN (3DES 或 AES) 入侵防御系统 (IPS) 通过网络准入控制(NAC) 和安全接入策略的实施,来提供防病毒支持
中型网络的旗 舰产品面世
3700 系列
集成多业务 路由器 ISR
1986
1994
1996
1998
1999
Cisco 1700 系列面世
2002
获得创新“先锋 奖”的集中化应 急IP话音通信
2004
CRS-1
领导业务集成
Cisco 3600 系列面世 4000系列 第一个集成话 音模块面世 业界第一款 模块化路由器 Cisco IOS 防火墙第 提出QoS以 一个集成 便于管理网 的防火墙 话音解决方案相匹配的 性能和密度 –面向高密度模拟/BRI的新扩展话音模块
CISCO ACS简单介绍

Cisco ACS配置手册
• 共享配置組建
Cisco ACS配置手册
• 網絡配置
Cisco ACS配置手册
• 系統配置
Cisco ACS配置手册
• 接口配置
CisHale Waihona Puke o ACS配置手册• 管理控制
Cisco ACS配置手册
• 報告和活動
設備端配置
• 啟用AAA,并添加本地帳戶 • aaa new-model • username xxx privilege 15 password yyy
ACS 4.X應用
摘要
• 本次分享課程從實用角度出發,介紹 CISCO ACS服務器安裝配置和管理。 • 主要內容包括:ACS工作原理;安装ACS 服務器;ACS配置;ACS用戶帳戶管理。 • 本次課程時長一个小时。
內容
• • • • ACS工作原理 ACS服務器安装 ACS在交換機上配置 ACS用戶帳戶管理
設備端配置
• • • • • • • • • 记录用户行为审计 aaa accounting send stop-record authentication failure aaa accounting exec default start-stop group tacacs+ aaa accounting commands 1 default start-stop group tacacs+ aaa accounting commands 5 default start-stop group tacacs+ aaa accounting commands 10 default start-stop group tacacs+ aaa accounting commands 15 default start-stop group tacacs+ aaa accounting network default start-stop group tacacs+ aaa accounting connection default start-stop group tacacs+
ciscoacs替代方案

Cisco ACS替代方案1. 简介Cisco ACS(Cisco Secure Access Control System)是思科公司提供的一种用于网络访问控制和身份验证的解决方案。
然而,随着网络技术的发展和安全需求的不断增加,许多组织和企业正在寻找更先进和功能更强大的替代方案。
本文将介绍一些替代Cisco ACS的方案,以满足不同组织的需求。
2. RADIUS服务器RADIUS(Remote Authentication Dial-In User Service)是一种网络协议,用于提供用户身份验证、授权和账号计费服务。
许多厂商提供了自己的RADIUS服务器产品,可以作为Cisco ACS的替代方案。
常见的RADIUS服务器包括:•FreeRADIUS: 免费且开源的RADIUS服务器,具有强大的扩展性和灵活性。
•Microsoft NPS: 在Windows Server操作系统上提供的RADIUS服务器,方便与Active Directory集成。
•Radisys NPS: 提供高性能和可靠性的RADIUS服务器,适用于大规模网络环境。
这些RADIUS服务器可以提供与Cisco ACS类似的身份验证、授权和账号计费功能,同时支持多种身份认证协议和网络设备。
3. AAA服务器AAA(Authentication, Authorization, and Accounting)服务器是一种用于网络访问控制和身份验证的综合解决方案。
它可以替代Cisco ACS,并提供更多功能和灵活性。
以下是一些常见的AAA服务器:•ClearPass: Aruba Networks提供的AAA服务器,支持广泛的网络设备和认证协议,具有强大的访问控制和身份验证功能。
•ISE(Identity Services Engine): Cisco自家的AAA服务器,集成了对网络访问控制、终端安全和身份认证的全面支持。
•FreeRADIUS + daloRADIUS: 使用FreeRADIUS作为认证和授权服务器,并结合daloRADIUS作为用户界面和管理工具,提供灵活的AAA解决方案。
用Shorewall取代Cisco 2621

0. r b 2 t . z 。然 后 使 用 如 下 命 令 a
进 行 解压 安 装 :
务 器 替 代 Cic 6 l 由 器 , so 2 2 路
性 能 得 到 了 很 大 的 提 升 。 面 下
2.
n t e
/ t / ho e J n e f c s e c s r wa 1 t r a e /i
e h0 t de e t tc
ic n g fo f i
3 4
nem a k 25 . 5. 5 2 0 t s 5 25 2 5.4
此 时 这 台 服 务 器 就 可 以 完 全 替 代 Cic 2 2 。 者 经 so 6 笔 1
的过程 。
Fa t he e /0 s Et m t 0
i p r u e 1 2. 6 0. 2 5. o t 9 1 8. O 5 2 5. 0 5 0. 1 2. 68. 1 9 1 9.
# . 8 a1破 伽 t l.
安 装 好 Sho e a 1后 对 rw 1 S r 1进 行 配 置 ,大 部 分 ho wa 1
学 校 网络 拓 扑
由上 面 的 配 置 不 难 看 出 ,
配 置 文 件 不 用 修 改 , 用 默 认 使
学 校 网 络 的 拓 扑 结 构 如 图
1 示 。 所
原 Cic 2 2 s o 6 l配 置 参 数
如 下 :
i e f ̄ ntra
n lt h } 吼 0 s默 瑚 /0
.
n O
 ̄
-br a c s o d a t
思科Cisco WPA2-PSK开放式身份验证 使用说明书

WPA2-PSK 和开放式身份验证(以思科 5760 WLC 配置为例)目录简介先决条件要求使用的组件配置网络图使用 CLI 进行 WPA2-PSK 配置使用 GUI 进行 WPA2-PSK 配置使用 CLI 进行开放式身份验证配置使用 GUI 进行开放式身份验证配置验证故障排除简介本文档介绍在无线局域网 (WLAN) 中使用 Wi-FiProtected Access 2 (WPA2) 的优势。
本文档提供两个在 WLAN 上实施 WPA2 的配置示例:配置 WPA2 预共享密钥 (PSK)q开放式身份验证配置q先决条件要求Cisco 建议您了解以下主题:无线保护访问 (WPA)qWLAN 安全解决方案q使用的组件本文档中的信息基于以下软件和硬件版本:思科 5700 系列无线局域网控制器 (WLC) 与思科 IOS® XE 软件版本 3.3 qCisco Aironet 3600 系列轻型接入点qMicrosoft Windows 7 本地无线请求方q本文档中的信息都是基于特定实验室环境中的设备编写的。
本文档中使用的所有设备最初均采用原始(默认)配置。
如果您使用的是真实网络,请确保您已经了解所有命令的潜在影响。
配置注意:使用命令查找工具(仅限注册用户)可获取有关本部分所使用命令的详细信息。
网络图此图显示了网络图:图 1. 网络图使用 CLI 进行 WPA2-PSK 配置本示例描述了使用命令行界面 (CLI) 为用于客户端的 VLAN 配置 DHCP 探听的过程。
VLAN20用于客户端,池配置在同一WLC上。
Cisco 5700 WLC的TenGigabitEthernet1/0/1连接到上行链路交换机。
如果在 WLC 之外的服务器上或外部 DHCP 服务器上配置了 DHCP 服务器,则必须信任 DHCP 探听和中继信息。
ip device trackingip dhcp snooping vlan 12,20,30,40ip dhcp snooping!ip dhcp pool vlan20network 20.20.20.0 255.255.255.0default-router 20.20.20.1interface Vlan20ip address 20.20.20.1 255.255.255.0interface TenGigabitEthernet1/0/1switchport trunk native vlan 12switchport mode trunkip dhcp relay information trustedip dhcp snooping trustwlan wpa2psk 1 wpa2pskclient vlan 20no security wpa akm dot1xsecurity wpa akm psk set-key ascii 0 Cisco123no shutdown注意:如果您的配置在 PSK 密码中包含空格,请使用“密码 PSK”格式。
acsae_wp

Deploying Cisco Secure ACS for Windowsin a Cisco Aironet EnvironmentIntroductionCisco Secure ACS for Windows has longsupported the centralization of accesscontrol and accounting for dial-up accessservers, virtual private networks (VPNs),firewalls, and voice over IP (VoIP)solutions. Starting with Cisco Secure ACSv2.6 for Windows 2000/NT Servers, itsupports standards-based IEEE 802.1X authentication of Cisco Aironet ® 1200,1100, 350 and 340 Series Access Points.Starting with Cisco Secure ACS v3.1 forWindows, support is now available forthree IEEE 802.1X ExtensibleAuthentication Protocol (EAP) typessupported by the Cisco Wireless SecuritySuite:•EAP Cisco Wireless (Cisco LEAP)•Extensible AuthenticationProtocol-Transport Layer Security(EAP-TLS)•Protected Extensible AuthenticationProtocol (PEAP)Cisco Secure ACS v3.1 also supportsconcurrent operation of any combination ofthese three EAP types.Deployment OverviewYou should consider several factors whenyou are deploying an access control server(ACS) to support wireless networks. Eachfactor may not be critical in isolation butwhen combined in the completedeployment,the combination may seriously affect the performance of the wireless LAN (WLAN) and ACS service. Points to consider include:•Location and number of access points •Location and number of Cisco Secure ACSs within the network •Authentication types to be used •Types of databases to be used and replication and synchronization strategies •Number of users in each database and the expected access rate •Need for central or dispersed access control •Authentication timeouts •Cisco Secure ACS redundancy After you have reviewed these factors for your intended design and compared them to the guidelines discussed in this paper, you can design a logical and efficient Cisco Secure ACS deployment for wireless access control.Performance Stress testing was performed on Cisco Secure ACS v3.1 to determine the maximum number of authentication requests the Cisco Secure ACS can serve per second.The results were generated using an authentication, authorization, and accounting (AAA) client simulator created internally.The hardware for testing the ACS system was configured as follows:Cisco Secure ACSHP Kayak 1.6 GHz, 256 MB RAMCisco Secure ACS v3.1 Internal database with 100,000 users in the database300 access pointsThe following test results for LEAP, PEAP and EAP-TLS authentications are raw authentication rates. They do not include network latency, reliability, or user distribution factors.•Sustained LEAP—90 authentications per second•Sustained EAP-TLS—32 authentications per second•Sustained PEAP—32 authentications per secondA significant factor in ACS authentication performance is the Remote Authentication Dial-In User Service(RADIUS) logging level. A high logging level may cause up to a 50 percent degradation of authentication performance.Note:EAP-TLS testing was performed with "Certificate name comparison" only. Certificate name comparison uses Cisco Secure ACS to verify user identity by comparing the username to the name in the end-user client certificate. Certificate binary comparison uses Cisco Secure ACS to verify user identity by doing a binary comparison with the user certificate.ScalabilityNumber of UsersThe following recommendations provide guidelines on how to scale the Cisco Secure ACS for a Cisco Aironet wireless ing the minimum recommended hardware for the Cisco Secure ACS(Pentium III processor, 550 MHz or faster, and 256 megabytes of RAM), it can support 80,000 users in the internal database. Laboratory tests indicate that this number can be increased with the addition of more RAM. Testing shows that with RAM increased to one gigabyte,the Cisco Secure ACS can support300,000internal users with performance similar to the standard system supporting 50,000 users. However, the increased database size will affect replication, as discussed in a later section of this document.The number of Cisco Secure ACSs required to support a specific size of user database depends on several factors including network topology, number of access points, network latency, expected number of users per access point, etc. Table 1 lists these performance factors.Table 1ACS Performance FactorsNumber of ACS deployments required for a given user base N acsMaximum number of authentications per second a single ACS is able to process M apsNumber of access points connected to the same ACS N apNumber of users per access point N usersNumber of retries configured on each access point N retryTimeout of the retry (in seconds)T retryRekeying interval (RADIUS attribute 27)T rekeyAverage length of user session T sessionAverage length of roaming user session T roamPercentage of roaming users P roamPacket rate PTotal number of access points N tapSafe work load W safeTotal number of users in the environment N tuserLogging levelNetwork latencyIn general, the minimum number of Cisco Secure ACSs required to support a given size of user database can be calculated with the following formula:(N tuser / (T rekey * 60)) / (M aps *W safe) =N acsWhere:•N acs is the number of Cisco Secure ACSs required•N tuser is total number of users in the environment•T rekey is the rekeying interval in minutes (RADIUS attribute 27)1•M aps is the number of authentication transactions per second•W safe is a "safe" workload for the ACS indicated as a percent fraction of the total ACS transaction capability In our case study,we can expect an initial user base of10,000LEAP users.Testing has shown that we can expect to have a transaction rate of90transactions per second(tps)(Maps in the formula)for authentication only.Assuming a "safe" working load2 of 40 percent, we can calculate the number of Cisco Secure ACSs required:N acs = (1000/(15*60)) / (90*0.40)N acs = 0.311.See Product Bulletin No. 1515:Cisco Wireless LAN Security Bulletin for guidance on determining the correct rekeying interval for a given environment.2.Thefigure for the"safe"working load is derived using several assumptions:(1)provide the ability of any ACS to handle the load from the failover from another ACS;(2)provide the ability to handle"spikes"in authentication load,such as employees arrivingfirst on shift;(3)provide an additional "spare"amount for handling new users.This value is arbitrary in this example.To determine this value,the percentage should include the number of failover ACSs that might be used (100% / # ACS), less some room for new users. The example shows (100%/2)-20% = 40% or 0.40.Adding5,000EAP-TLS users,using the test results of32tps for EAP-TLS and keeping the other parameters the same, we get the following ACS requirements for EAP-TLS:N acs = (5000/(15*60)) / (32*0.40)N acs = 0.43Add these two results together and 0.74 (or 1 rounded) ACS is required to support this user base. To put this in different terms,using the same ratio of2to1for LEAP to EAP-TLS,a single Cisco Secure ACS can support21,000 users in a single LAN environment, as shown below.(14000/(15*60)) / (90*0.40) = 0.43(7000/(15*60))/(32*0.40) = 0.61Total (21000 users per) = 1.04The higher the safe work load, the higher number of supported users per ACS.It's important to note, however, that a value of 40 percent for the "safe" working load may not be adequate if all contingencies occur simultaneously.In the event of a large user base(100,000+),the calculations remain the same.Databases of this size incur other side effects.As mentioned earlier,increased memory helps alleviate performance issues related to database access.Other size-related issues will be discussed later in this document.Note:The calculations for Nacs assume a uniform user density. The deployment designer needs to apply thesecalculations on a"per location"basis to get a more accuratefigure.There will likely be localized"hot spots"where traffic could be many times higher than other areas.In the case study scenario of 300,000 users, the calculations for the mixed environment for LEAP is: Nacs = (150000/(15*60))/(90*0.40)Nacs = 4.63and for EAP-TLS:Nacs = (150000/(15*60))/ (32*0.40)Nacs = 13.02The combined number is18Cisco Secure ACSs(rounded off).This number assumes a balanced deployment of LEAP and EAP-TLS.The40percent"safe"workload providesflexibility in thefigures and allows for some growth before adding new servers is required. Similar calculations can be factored in for PEAP.Additional adjustments to the number of Cisco Secure ACSs can be made by implementing features such as the Temporal Key Integrity Protocol (TKIP)3. Using TKIP, the Wired Equivalent Privacy (WEP) rekey timeout interval may be expanded to a maximum of 4 hours and 15 minutes without adversely affecting security (based on currentIP defends against an attack on WEP in which the intruder uses the unencrypted initialization vector in encrypted packets to calculate the WEP key. TKIP removes the predictability that an intruder relies on to determine the WEP key by exploiting initialization vectors. See Chapter 4 of the Cisco Aironet Access Point Software Configuration Guide for more details.key vulnerability metrics).With a longer rekey timeout interval,fewer Cisco Secure ACSs are required for the same number of ing the original factors for LEAP(above),but using a WEP key timeout of4hours(240minutes) we get the following:Nacs = (150000/(1240*60))/(90*0.40)Nacs = 0.056Number of Access PointsTo determine the number of access points that a Cisco Secure ACS can manage,start with the assumption that each access point manages about ten WLAN users, then divide that number into the total number of users that can be supported by a Cisco Secure ACS–21,000.With this formula we have21,000divided by10or2100access points that can be supported by one Cisco Secure ACS.This is the minimum number of access points that can be supported because not all access points will be supporting the maximum number of users at any one time.Number of Network Access ServersA Cisco Secure ACS can support up5000discrete4network access servers(NASs).This number can be increased by the use of the multi-NAS capability of an ACS.Multi-NAS is a concept that allows one or more addresses to be configured for a given NAS ing multi-NAS, the Cisco Secure ACS can support a theoretical maximum of 255 multiplied by 5000 discrete NAS equaling 1.275 million devices.However,a configuration of1.275million devices per Cisco Secure ACS is clearly not realistic.For each octet in the NAS IP address, there are three options:–Number (ie: a specified number, such as 10.3.157.98)–Numeric Range (ie: specified low and high numbers of the range in the octet, separated by a hypen, such as10.3.157.10 – 50.–Wildcard – An asterisk (*) is used to match all numbers in that octet, such as 10.3.157*.LAN Versus WAN DeploymentThe values calculated above do not take into account the network topology, particularly WAN latency and dependability. Depending on how critical wireless connectivity is to the organization (for example, maintaining connectivity for wireless cash registers in a store is very critical),we recommend that each wired LAN have at least one dedicated ACS. This can be mitigated by either using short, reliable WAN connections, or administratively reducing the degree critical connectivity for these remote devices; for example, meeting rooms where connection reliability is a convenience.A building may have400potential users and there may be a cluster of four buildings on the same subnet.One ACS assigned to this subnet will service1600users(about one tenth of the number of current users).Other buildings could be on adjacent subnets with reliable WAN connections.Cisco Secure ACSs on adjacent subnets could then be used as secondary systems for backup.In the event that the WAN connections between buildings in this cluster are short, reliable, and pose no issue of network latency, all of these buildings an all the users can be serviced with two Cisco Secure ACSs. At 40 percent workload, one Cisco Secure ACS would take half of the access points as the primary server, and the other Cisco4.A discrete NAS is a NAS entry configured with a single, non-wildcarded IP address.Secure ACS would take the remaining access points. Each Cisco Secure ACS would provide backup for the other.Again,at 40percent load,a failure of one Cisco Secure ACS would only create an 80percent load on the other Cisco Secure ACS for the duration of the outage.In the case where the WAN is not suitable for authentication connections,we recommend using two or more Cisco Secure ACSs on the LAN in a primary or secondary mode or load balanced.In the above case study,the 15,000LEAP/EAP-TLS users will be distributed throughout customer's global network.The number of users at local sites will range from hundreds at the corporate headquarters to less than ten at remote offices. This poses some issues. Figure 1 illustrates one possible solution.In a given geographical or organizational region,the total number of users may or may not reach a critical level for a Cisco Secure ACS. Small offices would not qualify for separate installations of Cisco Secure ACSs and a regional office may have sufficient reserve capacity. In this case, the small offices can authenticate users across the WAN to the larger regional office. Once again, we should determine that this does not pose a risk to the users in the remote offices. Critical connectivity needs to be assessed against the reliability and throughput to the central Cisco Secure ACS.Figure 1 Cisco Secure ACS Placement in Regional Settings XXXXXXXXXXXXXXXXXXXXXXXXXInternet SmallRemoteOffice SmallRemoteOffice RegionalOfficeCorporate RegionCorporate headquartersCisco AironetCisco Secure ACS XXXXX XXXXX A AA A XXXXXXXXXX XXXXXLoad-Balancing and FailoverA network load-balancing device such as the Cisco Content Services Switch (CSS) or Cisco LocalDirector content switch can be employed to balance authentication requests between Cisco Secure ACSs. Cisco uses LocalDirector content switches for load balancing and failover for its wireless installation using Cisco Secure ACSs.However,the use of certain features such as accounting may render this approach impractical.It is better to use a simpler method to balance RADIUS traffic between Cisco Secure ACSs.By convention,most RADIUS clients perform their own failover by maintaining a list of approved RADIUS servers. In the case of the Cisco Aironet access point, this list may contain as many as four RADIUS servers. If you set up more than one server for the same service, the first server in the list is the primary server for that service, and the other servers are used, in the order listed, when the previous server times out. If a backup server responds after the primary server fails, the access point continues to use the backup server for new transactions. Figure 2 shows the configuration window for RADIUS server configuration on the Cisco Aironet access point. Each access point must be configured to apply this failover capability.Note:Though the example shows failover between sites,the best deployment would include local failover systems on the same LAN. This provides fast, reliable, authentication for the local network. Load balancing can be accomplished in the same manner.Figure 2 RADIUS Server Configuration on the Cisco Aironet Access PointLoad balancing on the Cisco Secure ACS is similarly simple.Divide the access points into the same number of groups that there are Cisco Secure ACSs within the local WAN. Point the primary RADIUS server configuration of each access point of each group to the nearest ACS. Point the secondary RADIUS server configuration to the next Cisco Secure ACS, and so on. Figure 3 shows this deployment.Figure 3 Failover and Load Balancing of ACSsDatabase ReplicationDatabase replication replicates selected database information such as user and group information, from a primary Cisco Secure ACS to one or more Cisco Secure ACS backups or clients.Many aspects of system configuration (AAA client tables, groups/profiles, proxy settings, etc.) may be backed up to a secondary using replication. Replication enables the automatic creation of mirror Cisco Secure ACSs. These mirror systems can be used to provide backup redundancy servers,to increase fault-tolerance if the primary system fails.Because of this,the replicated data can be configured. The following aspects of replication are configurable with Cisco Secure ACS:CorporateWANCisco AironetCisco Secure ACSPrimary RADIUS ConnectionSecondary RADIUS Connection XXXXX AA XXXXXXXXXXAA AXXXXXXXXXX XXXXX XXXXX XXXXXXXXXX•Configuration components for replication—What is replicated•Replication scheduling—When replication takes place•Replication frequency—How often systems are replicated•Replication partners—Which systems are replicated•Client configuration—How the client is to be configured•Reports and event (error) handling—What information to include in the logsSome information cannot be replicated(such as IP pool definitions,Cisco Secure ACS certificate and private keyfiles). Database replication does not cover the configuration of external authentication sources. This part of theconfiguration is not covered because the Cisco Secure ACS functionality relies on the installation of a number of communication dynamic link libraries (DLLs) – installation of these DLLs is determined manually by the system administrator for each case. Database Replication cannot rely on the necessary DLLs being present. Replication of these parts of the Cisco Secure ACS configuration must be done manually.Caveats•Any component designated to be replicated to or from another component will be completely overwritten in favor of the replicated component; that is, the replication may be characterized as being destructive master/slave. For example,if the Receive checkbox is selected for user and group database,any user records in the database prior to the replication will be lost when the other Cisco Secure ACS's user database is received.•Database replication only achieves database synchronization by transforming the slave database into a copy of the master. The data flow in replication is one way and the data on the secondary is overwritten, as described above.•During the replication process,the authentication service is halted briefly on each of the devices(although not at the same time).On the sender AAA server,service is halted only once at the beginning while the appropriatefiles and registry information are collated and prepared for sending.On the receiver AAA server,service is halted when the incoming file and registry set is restored. Service is normal while the replication set is being transmitted between servers.Database Replication Test ResultsA sample of the database replication test results is documented in Table2.Four servers participated in the replication tests.Thefirst three systems("system1,""system2,"and"system3")were co-located in San Jose,California.The fourth system,"remote-server,"was located in Netanya,Israel5."System1"was the primary sever."System1"was replicated to "remote-server" and to "system 2". "System 2" was configured to perform "cascade"6replication to "system 3". The user database consisted of 100,000 users in 500 user groups, and 5000 AAA clients (NASs). This scenario is represented in Figure 4.The test results indicate that replication of a large internal database on the LAN takes from1.5to2.0minutes,while replication of the same database across a long WAN connection takes from5to5.5minutes.This indicates that when replicating over long distances, care must be made to design a system that minimizes the replication timeouts that5.The link between San Jose and Netanya is carried over a private, high-speed, dedicated circuit that passes through the United Kingdom.6.“Cascade”replication is where a secondary ACS server receives database replication from a primary ACS server and acts as a primary ACS server to replicate to other secondary ACS servers upon completion of its replication cycle with its primary.occur during replication.In the case of the long WAN coverage,either system is actually"down"7only a short time. Most of the 5 plus minutes is taken up with "transport" time, which does not affect an ACS's ability to perform authentication.Table 2Table 2 Database Replication Test ResultsDate Time Message Seconds System 19/20/2002 13:40:22 Outbound replication cycle starting...9/20/2002 13:45:36 Replication to ACS 'remote-server' was successful3149/20/2002 13:45:36 Outbound replication cycle completed9/20/2002 13:53:06 Outbound replication cycle starting...9/20/2002 13:58:34 Replication to ACS 'remote-server' was successful3289/20/2002 13:59:52 Replication to ACS 'System-2' was successful789/20/2002 13:59:52 Outbound replication cycle completedSystem 29/20/2002 13:59:02 Inbound database replication from ACS 'System 1' started9/20/2002 14:00:15 Inbound database replication from ACS 'System 1' completed739/20/2002 14:00:15 Outbound replication cycle starting...9/20/2002 14:01:57 Replication to ACS 'System 3' was successful1029/20/2002 14:01:57 Outbound replication cycle completedSystem 39/20/2002 14:00:48 Inbound database replication from ACS 'System 2' started9/20/2002 14:02:06 Inbound database replication from ACS 'System 2' completed78Note:Note: the link speed will affect the complete replication time. However, as stated above, the server is only unavailable while manipulating the database,not during transport.As a result,the transport time does not affect the availability of the server for authentication.Replication DesignBecause database replication in a Cisco Secure ACS is a"top down"approach,using the cascade method minimizes replication-induced downtime on the master server. If the master server is not used for authentication services, but for database maintenance only, the cascade method may not be as critical. However, when traveling across time zones, particularly international time zones, it may be necessary to consider using the cascade method going to remote secondaries.In this case,consider using At specific times versus Automatically triggered cascade(see Figure 5). This will allow "local" replication to take place during a time that will minimize the impact on user7.The server is"down"for authentication only during database changes.For the primary server,this occurs while reading the database and creation of thefile used to transport the replicated data.For the secondary server,this occurs while reading the receivedfile and writing to the database.This means that neither server is unavailable at the same time as the other.authentication.During these long distance replications,replicating to the backup or secondary server first also helpsreduce this impact.Figure 6shows a hypothetical deployment for replication where each region has both a primaryand a secondary Cisco Secure ACS deployed. In the scenario, replication is made to the secondary servers to avoidreplication downtime to the primary.Figure 4 Cisco Secure ACS Database Replication Scenario ISRAELMASTERsystem 1MASTER/SECONDARYsystem 2SECONDARYsystem 2AA AASECONDARY remote-systemCALIFORNIAFigure 5 Cisco Secure ACS for Windows Database Replication SchedulingFigure 6 Cisco Secure ACS for Windows Database Replication Scheduling AA A A A A AA Secondary (Region 3)Primary (Region 3)Secondary (Region 4)Primary (Region 4)Secondary (Region 2)Primary (Region 2)Secondary (Region 1)Master Primary (Region 1)An alternative to database replication is the use of Relational Database Management System (RDBMS) synchronization.The RDBMS Synchronization feature enables the updating of the Cisco Secure ACS user database with information from an Open Database Connectivity(ODBC)-compliant data source.The ODBC-compliant data source can be the RDBMS database of a third-party application.It can also be an intermediatefile or database that a third-party system updates. Regardless of where the file or database resides, Cisco Secure ACS reads the file or database via the ODBC connection. RDBMS synchronization supports addition, modification, and deletion for all data items it can access.More information about RDBMS synchronization is available at:/univercd/cc/td/doc/product/access/acs_soft/csacs4nt/acs31/acsuser/s.htm#xtocid26Design Implementation at Cisco—An ExampleCisco uses its own technology within its corporate network whenever possible. In the case of wireless technology, Cisco employs Cisco Aironet access points using the Cisco Wireless Security Suite to implement Cisco LEAP and pre-standard TKIP for secure authentication and encryption of all WLAN communication.Cisco Secure ACS is used to provide the RADIUS services required for LEAP. To provide some background and an example of a functioning Cisco Secure ACS deployment with Aironet wireless products, a brief discussion follows of how Cisco has implemented Cisco Secure ACS and Aironet products in its network.At the Cisco main campus in San Jose,CA buildings are grouped into three segments.Each segment consists of6to 19buildings and all the buildings in the segment are on a common LAN.Each building has six to eight WLAN access points per floor and all the access points in each building are on their own dedicated VLAN. All inter-building and inter-segment network connections use one-gigabyte fiber optic technology. Other Cisco campuses are similarly configured(Figure7).All wireless connections are designated as secondary network access.Primary network access is through switch ports over wired Ethernet.Cisco Secure ACS is used to provide LEAP authentication for the access points, and is configured to use Microsoft Active Directory for external database authentication. One Cisco Secure ACS is deployed for each segment of 6 to 19 buildings. A Cisco LocalDirector content switch is placed before each Cisco Secure ACS for load balancing and failover. All Aironet access points are configured with one RADIUS server and the LocalDirector content switch is used for failover.The LocalDirector is used because of the way the deployed version of access point software handles RADIUS failover8. As a result, Cisco is not currently using accounting on its wireless network.8.Earlier versions of the access point software had a problem with RADIUS failover. If failover occurred, the access point would not check to determine if the primary server was back online. It would remain on the secondary until it was manually reset or the secondary failed, forcing the access point to fail over to the next configured RADIUS server.This is not an issue with the current version of Aironet access point software.Cisco IT is studying the possibility of using the RADIUS client(access point)providing standard RADIUS fail over services(as in IOS)and utilizing accounting.Figure 7 Cisco Systems Wireless DeploymentFor small remote offices, the Cisco Wireless Security Suite provides LEAP and pre-standard TKIP across the WANto the nearest major campus. Once again, because Cisco's current strategy is for wireless access to be a secondarymeans of network access, this does not cause a serious problem in the event of a WAN failure.Recommendations for Cisco Secure ACS Installations with WLANsThe following recommendations are made based on the current test data.1.If wireless network access is designed to be a secondary means of accessing the network, a configuration usinggeographically remote Cisco Secure ACSs as secondary systems for failover authentication is acceptable. Inaddition,as with the Cisco scenario,remote Cisco Secure ACSs can be successfully used for small remote offices.2.If wireless network access is designed to be the primary means of accessing the network (critical application),itis recommended that a primary Cisco Secure ACS be placed in each LAN, with consideration of a secondaryCisco Secure ACS at the same location.3.If a customer will be using the Cisco Secure ACS internal database for user configuration, replication becomescritical factor. There may be issues with how to replicate certain information from the master to the secondary/masters and out to the rest of the network. In some circumstances the customer needs to replicate user andnetwork data,while in others only user information is to be replicated.Because of the flat nature of the replication InternetCisco AironetCisco Secure ACSCisco LocalDirector Segment 3Segment 1Segment 2Remote OfficeXXXXX XXXXX XXXXXXXXXXXXXXXXXXXXA XXXXXXXXXXXXXXX XXXXXXXXXX XXXXXXXXXXXXXXXAAA。
Cisco+ACS安装与应用详解

Cisco ACS安装与应用详解目 录(v2.0)准备工作 (3)1.安装操作系统(win2003)2.安装JA V A EDK3.安装IIS4.安装证书服务器第一章:CiscoSecure ACS v3.3的安装和配置 (7)第一部分:安装ACS v3.31.安装ACS v3.32.创建ACS管理员帐户第二部分:配置ACS相关选项1.Interface Configurationa. User Data Configurationb. TACACS+ (Cisco IOS)c. Advanced Options2. System Configurationa.Service Controlb.loggingc.Date Format Controld.Local Password Managemente.CiscoSecure Database Replicationf.ACS Backupg.ACS Restoreh.ACS Service Managementi.ACS Certificate Setupj.Global Authentication Setup第三部分:安装ACS 证书1. Generate Self-Signed Certificate2. Install ACS Certificate3. ACS Certification Authority Setup4. Edit Certificate Trust List5. Use HTTPS Transport for Administration Access第二章:CiscoSecure ACS v3.3的应用范例 (14)第一部分:Network Configuration第二部分:User Setup第三部分:Group Setup第四部分:SharedProfile Components第三章:在交换机上配置AAA认证、授权、记账 (22)1.现在交换机上创建本地用户2.开启AAA服务3.在接口上激活配置第四章:Cisco User Changeable Password安装与配置 (24)第一部分:.新建站点第二部分:.创建站点虚拟目录第三部分:.申请、颁发、安装站点(IIS)证书第四部分:.安装UCP准备工作本文所有内容都是在windows2003操作系统上完成的,对于其他操作系统的操作如果有不同的地方,请自行参考解决!本文稍后介绍的软件或服务版本要求:Internet Explorer 6.0 SP1 或更新版本Internet Information Service 6.0(win2003)CiscoSecure ACS v3.3Cicso User Changeable Password v3.3安装Cisco ACS前的准备工作:1.安装操作系统win20003,打全补丁;2.安装java EDK,安装后尽量更新到最新版本;3.安装IIS。
Cisco Secure ACS 解决方案

思科安全访问控制解决方案引擎Cisco Secure ACS解决方案引擎是一款高度安全、独立于OS的专用平台,提供了高度可管理的访问控制解决方案,进一步缩短了设置和排障时间。
它提供了即插即用部署,一个高度可靠的验证、授权和记帐(AAA)解决方案,且能更好地保护总拥有成本(TCO)。
每个Cisco Secure ACS 解决方案引擎都配有一个Cisco Secure ACS远程代理,支持远程登录和Windows验证。
适用场合销售该产品当客户需要以下这些特性时思科安全访问控制解决方案引擎z需专用、增强安全、针对特定应用的设备包z凭借Cisco Secure ACS服务的整体可靠性和安全性,简化日常管理z为不愿意在Windows OS上安装或管理Cisco Secure ACS的Cisco Secure ACS UNIX客户提供的合适替代品关键特性z仅运行Cisco Secure ACS服务,以防止任何基于设备的OS更改、添加或配置修改z提供了一个串行控制台接口,以用于初始配置、随后对IP连接的管理、接入Cisco Secure ACS HTML接口,以及升级和恢复过程的应用z解决方案引擎专用管理工具提供了通用设备管理功能,包括备份、恢复、软件升级、监控、维护和排障功能z提供了针对Windows域的验证和远程用户帐户记录功能z分组过滤服务,可阻塞除必要的Cisco Secure ACS专用TCP和用户数据报协议端口外所有端口上的流量z预先安装的独立思科安全代理有助于保护Cisco Secure ACS解决方案引擎免遭“零日”攻击z内置NTP功能可保持网络时间同步及与其他Cisco Secure ACS设备或网络设备的一致性产品特性特性思科安全访问控制解决方案引擎1处理器速度Pentium IV,3.2GHz内存1GB RAM硬盘80GB磁盘空间接口2个内置10/100以太网控制器和1个软驱1专用于Cisco ACS解决方案引擎。
ciscoacs替代方案

ciscoacs替代方案随着网络安全的日益重要,越来越多的组织开始寻求替代思科ACS (Access Control Server)的解决方案。
ACS是一款广泛使用的网络访问控制和安全认证系统,然而,它的高成本、复杂性和性能限制使得许多企业寻求更好的替代方案。
在本文中,我们将探讨替代ACS的一些可行方案,并分析它们的优点和限制。
一、Radius服务器Radius是一种基于客户/服务器模型的认证协议,广泛用于网络访问控制。
它通过认证中心进行身份验证和授权,可以与多种网络设备和应用程序集成。
相对于ACS而言,Radius服务器的成本较低,配置较为简单,适用于小型和中型企业。
然而,该解决方案的性能可能不如ACS,且功能相对有限。
二、TACACS+服务器TACACS+(Terminal Access Controller Access Control System Plus)是一种用于网络管理和认证的协议。
与Radius不同,TACACS+基于分离的认证、授权和账务(AAA)过程,提供更高级的访问控制和灵活性。
TACACS+服务器与各种网络设备兼容,并且可以用于实现细粒度的访问控制。
然而,相对于ACS而言,TACACS+的部署和配置可能更加复杂,需要更多的技术知识。
三、FreeRADIUSFreeRADIUS是一个开源的Radius服务器,具有广泛的功能和可定制性。
它可以作为ACS的替代方案,提供强大的认证和授权功能,支持多种网络设备。
FreeRADIUS的优点是免费、开源且具有活跃的社区支持,可以适应各种企业需求。
然而,相对于ACS而言,FreeRADIUS的部署和配置可能需要更多的技术知识和精力。
四、ISE(Identity Services Engine)ISE是思科推出的一种全面的网络访问控制解决方案,可以替代ACS并提供更多功能。
ISE集成了Radius、TACACS+以及其他安全特性,可以为企业提供集中化的身份验证、访问控制和安全策略管理。
思科ACS网络设备安全管理方案

对于非专业人员来说,配置和管理可能具有一定 的难度。
兼容性问题
可能与某些老旧设备或软件存在兼容性问题。
03
思科ACS网络设备安全管理方 案
设备物理安全
设备放置
确保网络设备放置在安全的环境中,避免未经授权的人员接触。
访问控制
实施严格的访问控制措施,如门禁系统、监控摄像头等,以防止未 经授权的进入。
03
灵活性
04
支持多种接口类型和协议,满足 不同网络架构的需求。
安全性
提供多层安全防护,有效抵御各 类网络威胁。
ACS网络设备的应用场景
数据中心
适用于大型数据中心的网络出口安全防护,确保数据 传输的安全性。
企业网络
适用于企业总部和分支机构的网络安全防护,保障关 键业务的安全运行。
云服务提供商
为云服务提供安全的网络环境,保护租户数据的安全 性。
思科ACS网络设备安全管理 方案
汇报人: 2024-01-09
Hale Waihona Puke 录• 引言 • 思科ACS网络设备概述 • 思科ACS网络设备安全管理方
案 • 实施步骤和注意事项 • 案例分析和实际应用
01
引言
背景介绍
01
随着网络技术的快速发展,网络设备的安全管理变得日益重要 。
02
思科作为全球领先的网络设备供应商,其产品广泛应用于各行
各业。
由于网络设备的安全漏洞可能引发严重的安全事件,因此需要
03
采取有效的安全管理方案来保障网络设备的安全性。
目的和意义
本文旨在介绍思科ACS网络设 备的安全管理方案,以提高网
络设备的安全性。
通过实施有效的安全管理措 施,可以降低网络设备遭受 攻击的风险,保护企业的信
通过RADIUS服务器和无线控制器动态分配VLAN

通过RADIUS服务器和无线控制器动态分配VLAN介绍本文介绍如何在RADIUS认证服务器和无线控制器(WLC)上配置VLAN动态指定.配置条件必要条件在配置前,请先确定掌握以下知识点:(1) LAP的基本知识(2) AAA服务器的基本知识(3) 无线网络相关安全知识(4) LAP的协议LWAPP涉及更多LWAPP协议的相关知识,请参考以下网址/en/US/prod/collateral/wireless/ps5678/ps6306/prod_white_paper0900aecd802c18ee.html使用说明本文涉及的信息基于以下软件及硬件版本:(1) 使用固件4.0 的思科2006WLC(2) 1000系列的LAP(3) 使用固件2.6的思科802.11a/b/g的无线客户端(4) 软件版本2.6.0.1的思科无线客户软件(ADU)(5) 软件版本3.2的思科准入控制软件ACS(6) 思科2950交换机文档中描述的是在实验环境,所有设备都是初始配置,请先确定各命令的意义,再做配置。
规定请参考以下网址,获得更多信息/en/US/tech/tk801/tk36/technologies_tech_note09186a0080121a c5.shtml知识点在大多数的无线环境下,每一个无线网络都有静态的策略应用到相应的SSID上,但它具有限制性,因为每个客户端通过不同的SSID关联后,应继承相应SSID的策略.在思科的无线网络中,支持具有身份认证的特性,容许通告唯一的SSID,和具有不同认证身份的客户端拥有相应权限.通过RADIUS认证服务器对不同的客户端的验证,指定动态VLAN,RADIUS服务器可以是思科的ACS.动态VLAN指定可以用在,当一个客户端在园区内移动时,仍然保持同样的VLAN接入.因此,当一个客户端通过LAP认证到WLC时,LAP可以把相应的认证数据发送到认证服务器做检测,一旦认证成功后,认证服务器会将相应的属性(比如VLAN ID)发送给客户端,不用关心SSID的设置。
基于ODBC的CiscoSecure ACS认证数据库的设计与实现

基于ODBC的CiscoSecure ACS认证数据库的设计与实现殷民;舒坚;杨晓东;樊鑫
【期刊名称】《微计算机信息》
【年(卷),期】2006(022)021
【摘要】随着宽带网络的高速发展,宽带用户的管理显得日益重要,用户认证作为宽带用户管理的重要内容成为人们研究的重点.本文介绍了Cisco公司开发的CiscoSecure ACS认证系统,对其中基于ODBC的数据库认证方法进行了分析,并在实例中使用该方法设计、实现了系统的认证功能,验证了这种认证方法在工程中的有效性.
【总页数】3页(P224-226)
【作者】殷民;舒坚;杨晓东;樊鑫
【作者单位】330063,南昌航空工业学院软件学院;330063,南昌航空工业学院软件学院;330002,江西广电网络传输有限公司;330063,南昌航空工业学院软件学院【正文语种】中文
【中图分类】TP3
【相关文献】
1.数据库网络访问接口安全ODBC的设计与实现 [J], 马耀华;柏文阳;徐洁磐
2.基于JDBC-ODBC的数据库访问方法的设计与实现 [J], 李贤华;彭真
3.基于ODBC的CiscoSecure ACS认证数据库的设计与实现 [J], 殷民;舒坚;杨晓东;樊鑫
4.基于Spring和AOP的数据库认证日志的设计与实现 [J], 陈焕英; 马静婕
5.基于ODBC技术实现iFix组态软件与关系数据库通讯接口 [J], 龚伟平
因版权原因,仅展示原文概要,查看原文内容请购买。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
!"# RADIUS
!"
RADIUS
Cisco Secure ACS ! 3; !"IPsec PPTP !"#$%&'
! TACACS+
!"#!$% VPN
!
!" Cisco Secure ACS V.2.6 for Windows 2000 & NT !"# !"#$%&'( !"#$%& Cisco Secure ACS V.2.6 !"#$%&'()*
•
!"#$%& Cisco Secure ACS !"#$%& !"#$ !"
!"#$%&'()* !"#$%& IEEE 802.1x !" ACS
!"!#$%&'() Cisco Aironet 350 '()*+,!"#$ !"#$% (EAP) !"# !' !"##
• tory / •
!"#$%
Cisco Secure ACS V.2.6 for Windows 2000 & NT Cisco Secure ACS V.1.0/V.2.X for Windows NT V.2.6 Windows 2000 NT Cisco Secure !"#
!
!"#$%&'( Cisco Secure ACS for Winows 2000 & NT !"# ! ACS2000 ! !"#/go/acs
•
Cisco IOS
! VPN
!"#$%& !
!"#$%#&'()(*+ ( M u l t i c h a s s i s Multilink Point-to-Point Protocol) !" • Cisco IOS
'()*+
!"#$
RSA SecurID Axent !"# !"#$ !" !"#$%&' !
!"
CrytoCard
1 Cisco Secure !
!"#$ V.2.6
!" !
CSNT-2.6 CSNT-2.6-UG CON-SAS-CSNT
•
!"#$
! "#
!"#$%&
• Windows 2000 Windows NT ! 350MHz 4.0 ! !" !"#$%&'( !"#$% !"#$%Pentium • Windows 2000 !" 6.0 !"#$% !&' ! NT
Windows 2000 NT Cisco Secure !"#$(ACS) V.2.6
ACS Internet ! !"#$% ! !"#$ !" !"#$% NT
• • • •
!"#$%&$'()*
!"#$%&'%()*+,!"#$%&'()*+ !"#$%& !"#$ Cisco IOS® !"#$%& TACACS+ !"#$%& !"#$%&' ! Catalyst® !"
!(
)
!"#$%
!"# SS ! NU ~NV !WNMMMQR WEUSNMFSUMOPPRR WEUSNMFSUMPUPMO
!"#$ OPP ! QP !WRNMSOM WEUSOMFPUTTMMMM WEUSOMFPUTTMMTT
! "# OOO ! PO PP !WOMMMON WEUSONFRPVSSNSN WEUSONFRPVSSTRM
!"#$ PMU ! OP !WSNMMNT WEUSOUFSROUUUU WEUSOUFSROUVVV
Lit-CH0104T08A
2001
!"#
!
!"#$%&'()*+,-.(
•
!"
ACS
Cisco IOS !"#$%& Cisco
!"# AAA !"#$%&' TACACS+) •
!
Windows 2000 NAS NT !"#$%&'()* ! !" !"#$%&' ! Cisco IOS 11.2 RADIUS
(NAS)(Cisco IOS •
!"#$%&'()$*+,!"#$%&'((AAA) ACS V.2.6 ! "# !"#$%& RADIUS
!"#$%&'()*+, !"#$% !"#$ !" !"#$% ACS !"#$%
•
!"Cisco Secure !"#$%&'() !"#$ !"
!"#$%&'( !"#$%&'
• 128MB RAM • 150MB !" • 256 !" !"#$% !"#$%&' !" 800(600 !"#$%&'(
•
!"#$
Cisco Secure ACS !"#$%&'( !"
&
!"#$% !"#
!"#$%& WAN
!"#$% !
!"#$%&'()*+ (AAA)
!"#$%&'()*+,-(.
Web ! !"#$ ACS
Cisco Secure ACS VPN !"IP
!"#$%& (VoIP) 2.6 !
!"#$%&'()*
!
!"#$%(LDAP)
!"#$%&'()*+,-./01 !"#$%&'()*+,-./01 !"#$ N e t s c a p e Microsoft Windows 2000 Active DirecNT !"#$ !"#$%& !"#$%&'()*+ Windows Windows Novell
"#$%&'()*+,-. !"#$%&'() VPN
!"#$%&'() !"#$ !"#$%(
!"#$%& ) Cisco Cisco Secure Cisco Secure ACS !"#$%& TACACS+
!" Windows 2000
!"#$%&'(
!"#$(ACS) V.2.6 !"#$%&!' !" RADIUS !"#$ !"
