A_Dynamic_Theory_of_Resource_Wars1
CISP考试认证(习题卷9)

CISP考试认证(习题卷9)说明:答案和解析在试卷最后第1部分:单项选择题,共94题,每题只有一个正确答案,多选或少选均不得分。
1.[单选题]在IIS上,除了修改HTTP 500的错误页面信息外,另外一种屏蔽HTTP 500错误信息的方式是( )A)自定义脚本错误信息B)修改ISAPIC)修改WEB目录权限D)修改ASP执行权限2.[单选题]如果将允许使用中继链路的 VLAN 范围设置为默认值,表示允许哪些 VLANA)允许所有 VLAN 使用中继链路B)只允许 VLAN1 使用中继链路C)只允许本征 VLAN 使用中继链路D)交换机将通过 VTP 来协商允许使用中继链路的 VLAN3.[单选题]为增强Web 应用程序的安全性,某软件开发经理决定加强Web 软件安全开发培训,下面哪项内容不在考虑范围内A)关于网站身份鉴别技术方面安全知识的培训B)针对OpenSSL 心脏出血漏洞方面安全知识的培训C)针对SQL 注入漏洞的安全编程培训D)关于ARM 系统漏洞挖掘方面安全知识的培训4.[单选题]下列哪些措施不是有效的缓冲区溢出的防护措施?A)使用标准的C 语言字符串库进行操作B)严格验证输入字符串长度C)过滤不合规则的字符D)使用第三方安全的字符串库操作5.[单选题]由于IT的发展,灾难恢复计划在大型组织中的应用也发生了变化。
如果新计划没有被测试下面哪项是最主要的风险A)灾难性的断电B)资源的高消耗C)"恢复的总成本不能被最小化"D)用户和恢复团队在实施计划时可能面临服务器问题6.[单选题]在信息系统中, 访问控制是最重要的安全功能之一。
访问控制模型将所有实体分为主体和客体两大失,通过对主体身份的识别来限制其对客体的访问权限。
下列选项中, 对主体客体和访问权阳的述中正确的是A)对文件进行操作的用户是一种主体B)用户调度并运行的某个进程是一种客体C)主体与客体的关系是固定的, 不能互换D)一个主体为了完成任务, 可以创建另外的客体, 并使这些子客体独立运行7.[单选题]CISP职业道德包括诚实守信,遵纪守法,主要有()、()、()A)不通过计算机网络系统进行造谣、欺诈、诽谤、弄虚作假等违反诚信原则的行为;不利用个人的信息安全技术能力实施或组织各种违法犯罪行为,不在公共网络传播反动、暴力、黄色、低俗信息及非法软件。
Error and attack tolerance of complex networks

a r X i v :c o n d -m a t /0008064v 1 [c o n d -m a t .d i s -n n ] 3 A u g 2000Error and attack tolerance of complex networksR´e ka Albert,Hawoong Jeong,Albert-L´a szl´o Barab´a siDepartment of Physics,University of Notre Dame,Notre Dame,IN 46556Many complex systems display a surprising degree of tolerance against er-rors.For example,relatively simple organisms grow,persist and reproduce de-spite drastic pharmaceutical or environmental interventions,an error tolerance attributed to the robustness of the underlying metabolic network [1].Complex communication networks [2]display a surprising degree of robustness:while key components regularly malfunction,local failures rarely lead to the loss of the global information-carrying ability of the network.The stability of these and other complex systems is often attributed to the redundant wiring of the func-tional web defined by the systems’components.In this paper we demonstrate that error tolerance is not shared by all redundant systems,but it is displayed only by a class of inhomogeneously wired networks,called scale-free networks.We find that scale-free networks,describing a number of systems,such as the World Wide Web (www)[3–5],Internet [6],social networks [7]or a cell [8],display an unexpected degree of robustness,the ability of their nodes to com-municate being unaffected by even unrealistically high failure rates.However,error tolerance comes at a high price:these networks are extremely vulnerable to attacks,i.e.to the selection and removal of a few nodes that play the mostimportant role in assuring the network’s connectivity.Such error tolerance and attack vulnerability are generic properties of communication networks,such as the Internet or the www,with complex implications on assuring information readiness.The increasing availability of topological data on large networks,aided by the computer-ization of data acquisition,has lead to major advances in our understanding of the generic aspects of network structure and development[9–16].The existing empirical and theoretical results indicate that complex networks can be divided into two major classes based on their connectivity distribution P(k),giving the probability that a node in the network is connected to k other nodes.Thefirst class of networks is characterized by a P(k)that is peaked at an average k and decays exponentially for large k.The most investigated examples of such exponential networks are the random graph model of Erd˝o s and R´e nyi[9,10]and the small-world model of Watts and Strogatz[11],both leading to a fairly homogeneous network,in which each node has approximately the same number of links,k≃ k .In contrast,results on the world-wide web(www)[3–5],Internet[6]and other large networks[17–19]indicate that many systems belong to a class of inhomogeneous networks,referred to as scale-free networks,for which P(k)decays as a power-law,i.e.P(k)∼k−γ,free of a characteristic scale.While the probability that a node has a very large number of connections(k>> k ) is practically prohibited in exponential networks,highly connected nodes are statistically significant in scale-free networks(see Fig.1).We start by investigating the robustness of the two basic network models,the Erd˝o s-R´e nyi(ER)model[9,10]that produces a network with an exponential tail,and the scale-free model[17]with a power-law tail.In the ER model wefirst define the N nodes,and then connect each pair of nodes with probability p.This algorithm generates a homogeneous net-work(Fig.1),whose connectivity follows a Poisson distribution peaked at k and decaying exponentially for k>> k .The inhomogeneous connectivity distribution of many real networks is reproduced by the scale-free model[17,18]that incorporates two ingredients common to real networks: growth and preferential attachment.The model starts with m0nodes.At every timestep t a new node is introduced,which is connected to m of the the already existing nodes.The probabilityΠi that the new node is connected to node i depends on the connectivity k i ofthat node,such thatΠi=k i/jk j.For large t the connectivity distribution is a power-lawfollowing P(k)=2m2/k3.The interconnectedness of a network is described by its diameter d,defined as the av-erage length of the shortest paths between any two nodes in the network.The diameter characterizes the ability of two nodes to communicate with each other:the smaller d is,the shorter is the expected path between works with a very large number of nodes can have a rather small diameter;for example the diameter of the www,with over800million nodes[20],is around19[3],while social networks with over six billion individuals are be-lieved to have a diameter of around six[21].To properly compare the two network models we generated networks that have the same number of nodes and links such that P(k)follows a Poisson distribution for the exponential,and a power-law for the scale-free network.Error tolerance—To address the networks’error tolerance,we study the changes in the diameter when a small fraction f of the nodes is removed.The malfunctioning(absence)of a node in general increases the distance between the remaining nodes,since it can eliminate some paths that contribute to the system’s interconnectedness.Indeed,for the exponential network the diameter increases monotonically with f(Fig.2a),thus,despite its redundant wiring(Fig.1),it is increasingly difficult for the remaining nodes to communicate with each other.This behavior is rooted in the homogeneity of the network:since all nodes have approximately the same number of links,they all contribute equally to the network’s diameter,thus the removal of each node causes the same amount of damage.In contrast,we observe a drastically different and surprising behavior for the scale-free network(Fig.2a): the diameter remains unchanged under an increasing level of errors.Thus even when as high as5%of the nodes fail,the communication between the remaining nodes in the network is unaffected.This robustness of scale-free networks is rooted in their extremely inhomogeneous connectivity distribution:since the power-law distribution implies that the majority of nodes have only a few links,nodes with small connectivity will be selected with much higher probability,and the removal of these”small”nodes does not alter the path structure of the remaining nodes,thus has no impact on the overall network topology.Attack survivability—An informed agent that attempts to deliberately damage a net-work,such as designing a drug to kill a bacterium,will not eliminate the nodes randomly,but will rather target the most connected nodes.To simulate an attack wefirst remove the most connected node,and continue selecting and removing nodes in the decreasing order of their connectivity k.Measuring the diameter of an exponential network under attack,wefind that,due to the homogeneity of the network,there is no substantial difference whether the nodes are selected randomly or in decreasing order of connectivity(Fig.2a).On the other hand,a drastically different behavior is observed for scale-free networks:when the most connected nodes are eliminated,the diameter of the scale-free network increases rapidly, doubling its original value if5%of the nodes are removed.This vulnerability to attacks is rooted in the inhomogeneity of the connectivity distribution:the connectivity is ensured by a few highly connected nodes(Fig.1b),whose removal drastically alters the network’s topology,and decreases the ability of the remaining nodes to communicate with each other.Network fragmentation—When nodes are removed from a network,clusters of nodes, whose links to the system disappear,can get cut offfrom the main cluster.To better understand the impact of failures and attacks on the network structure,we next investigate this fragmentation process.We measure the size of the largest cluster,S,shown as a fraction of the total system size,when a fraction f of the nodes are removed either randomly or in an attack mode.Wefind that for the exponential network,as we increase f,S displays a threshold-like behavior such that for f>f c≃0.28we have S≃0.A similar behavior is observed when we monitor the average size s of the isolated clusters(i.e.all the clusters except the largest one),finding that s increases rapidly until s ≃2at f c,after which it decreases to s =1.These results indicate the following breakdown scenario(Fig.4):For small f,only single nodes break apart, s ≃1,but as f increases,the size of the fragments that fall offthe main cluster increases,displaying a singular behavior at f c.At f c the system practically falls apart,the main cluster breaking into small pieces,leading to S≃0,and the size of the fragments, s ,peaks.As we continue to remove nodes(f>f c),we fragment these isolated clusters,leading to a decreasing s .Since the ER model is equivalent to theinfinite dimensional percolation[22],the observed threshold behavior is qualitatively similar to the percolation critical point.However,the response of a scale-free network to attacks and failures is rather different (Fig.3b).For random failures no threshold for fragmentation is observed,rather the size of the largest cluster slowly decreases.The fact that s ≃1for most f indicates that the network is deflated by nodes breaking offone by one,the increasing error level leading to the isolation of single nodes only,not clusters of nodes.Thus,in contrast with the catastrophic fragmentation of the exponential network at f c,the scale-free network stays together as a large cluster for very high values of f,providing additional evidence of the topological stability of these networks under random failures.This behavior is consistent with the existence of an extremely delayed critical point(Fig.3),the network falling apart only after the main cluster has been completely deflated.On the other hand,the response to attack of the scale-free network is similar(but swifter)to the response to attack and failure of the exponential network(Fig.3b):at a critical threshold f sf c≃0.18,smaller than the value f e c≃0.28observed for the exponential network,the system breaks apart,forming many isolated clusters(Fig.4).While great efforts are being made to design error tolerant and low yield components for communication systems,little is known about the effect of the errors and attacks on the large-scale connectivity of the network.To demonstrate the impact of our model based studies to these systems,next we investigate the error and attack tolerance of two networks of increasing economic and strategic importance:the Internet and the www.Recently Faloutsos et al.[6]investigated the topological properties of the Internet at the router and inter-domain level,finding that the connectivity distribution follows a power-law, P(k)∼k−2.48.Consequently,we expect that it should display the error tolerance and attack vulnerability predicted by our study.To test this,we used the latest survey of the Internet topology,giving the network at the inter-domain(autonomous system)level.Indeed,wefind that the diameter of the Internet is unaffected by the random removal of as high as2.5%of the nodes(an order of magnitude larger than the failure rate(0.33%)of the Internet routers[23]),while if the same percentage of the most connected nodes are eliminated(attack),d more than triples(Fig.2b).Similarly,the large connected cluster persists for high rates of random node removal,but if nodes are removed in the attack mode,the size of the fragments that break offincreases rapidly,the critical point appearing at f I c≃0.03(Fig.3b).The www forms a huge directed graph whose nodes are documents and edges are the URL hyperlinks that point from one document to another,its topology determining the search engines’ability to locate information on it.The www is also a scale-free network:the probabilities P out(k)and P in(k)that a document has k outgoing and incoming links follow a power-law over several orders of magnitude,i.e.P(k)∼k−γ,withγin=2.1andγout=2.45 [3,4,24].Since no complete topological map of the www is available,we limited our study to a subset of the web containing325,729nodes and1,469,680links( k =4.59)[3].Despite the directedness of the links,the response of the system is similar to the undirected networks we investigated earlier:after a slight initial increase,d remains constant in the case of random failures,while it increases for attacks(see Fig.2c).The network survives as a large cluster under high rates of failure,but the behavior of s indicates that under attack the system abruptly falls apart at f w c=0.067(Fig.3c).In summary,wefind that scale-free networks display a surprisingly high degree of toler-ance against random failures,a property not shared by their exponential counterparts.This robustness is probably the basis of the error tolerance of many complex systems,ranging from cells[8]to distributed communication systems.It also explains why,despite frequent router problems[23],we rarely experience global network outages or,despite the temporary unavailability of many webpages,our ability to surf and locate information on the web is unaffected.However,the error tolerance comes at the expense of attack survivability:the diameter of these networks increases rapidly and they break into many isolated fragments when the most connected nodes are targeted.Such decreased attack survivability is useful for drug design[8],but it is less encouraging for communication systems,such as the Internet or the www.While the general wisdom is that attacks on networks with distributed resource management are less successful,our results indicate that the topological weaknesses of thecurrent communication networks,rooted in their inhomogeneous connectivity distribution, have serious effects on their attack survivability,that could be exploited by those seeking to damage these systems.REFERENCES[1]Hartwell,L.H.,Hopfield,J.J.,Leibler,S.&Murray,A.W.,From molecular to modularcell biology,Nature402,C47-C52(1999).[2]Claffy,K.,Monk,T.E.&McRobb,D.Internet tomography,Nature web matters,7January1999,</webmatters/tomog/tomog.html>.[3]Albert,R.,Jeong,H.&Barab´a si,A.-L.Diameter of the World-Wide Web,Nature401,130-131(1999).[4]Kumar,R.,Raghavan,P.,Rajalopagan,S.&Tomkins,A.Extracting large-scale knowl-edge bases from the web,Proc.25th VLDB Conf.,Edinburgh,1999.[5]Huberman,B.A.&Adamic,L.A.Growth dynamics of the World-Wide Web,Nature401,131(1999).[6]Faloutsos,M.,Faloutsos,P.&Faloutsos,C.On Power-Law Relationships of the InternetTopology,ACM SIGCOMM’99,mun.Rev.29,251-263(1999).[7]Wasserman,S.&Faust,K.Social Network Analysis(Cambridge University Press,Cam-bridge,1994).[8]Jeong,H.,Tombor,B.,Albert,R.,Oltvai,Z.&Barab´a si,A.-L.The large-scale organi-zation of metabolic networks.(preprint).[9]Erd˝o s,P.&R´e nyi,A.On the evolution of random graphs.Publ.Math.Inst.Hung.Acad.Sci.5,17-60(1960).[10]Bollob´a s,B.Random Graphs(Academic Press,London,1985).[11]Watts,D.J.&Strogatz,S.H.Collective dynamics of’small-world’networks.Nature393,440-442(1998).[12]Zegura,E.W.,Calvert,K.L.&Donahoo,M.J.A Quantitative Comparison of Graph-based Models for Internet Topology.IEEE/ACM Transactions on Networking5,770-787 (1997).[13]Cohen,J.E.,Briand,F.&Newman,munity food webs:data and theory(Springer-Verlag,Berlin1990).[14]Maritan,A.,Colaiori,F.,Flammini,A.,Cieplak,M.,&Banavar,J.Universality Classesof Optimal Channel Networks.Science272,984-986(1996).[15]Banavar,J.R.,Maritan,A.&Rinaldo,A.Size and form in efficient transportationnetworks.Nature399,130-132(1999).[16]Barth´e l´e my,M.&Amaral,L.A.N.Small-World Networks:Evidence for a CrossoverPicture.Phys.Rev.Lett.82,3180-3183(1999).[17]Barab´a si,A.-L.&Albert,R.Emergence of Scaling in Random Networks.Science286,509-511(1999).[18]Barab´a si,A.-L.,Albert,R.&Jeong,H.Mean-field theory for scale-free random net-works.Physica272A,173-187(1999).[19]Redner,S.,How popular is your paper?An empirical study of the citation distribution.Euro.Phys.J.B4,131-134(1998).[20]Lawrence,S.&Giles,C.L.Accessibility of information on the web.Nature400,107-109(1999).[21]gram,The Small-World Problem.Psychol.Today2,60-67(1967).[22]Bunde,A.&Havlin S.(editors)Fractals and Disordered Systems(Springer,New York,1996).[23]Paxson,V.End-to-End Routing Behavior in the Internet.IEEE/ACM Transactions onNetworking5,601-618(1997).[24]Adamic,L.A.The Small World Web.Lect.Notes Comput.Sci1696,443-452(1999).FIGURESFIG.1.Visual illustration of the difference between an exponential and a scale-free network. The exponential network a is rather homogeneous,i.e.most nodes have approximately the same number of links.In contrast,the scale-free network b is extremely inhomogeneous:while the ma-jority of the nodes have one or two links,a few nodes have a large number of links,guaranteeing that the system is fully connected.We colored with red thefive nodes with the highest number of links, and with green theirfirst neighbors.While in the exponential network only27%of the nodes are reached by thefive most connected nodes,in the scale-free network more than60%are,demonstrat-ing the key role the connected nodes play in the scale-free network.Note that both networks contain 130nodes and215links( k =3.3).The network visualization was done using the Pajek program for large network analysis<http://vlado.fmf.uni-lj.si/pub/networks/pajek/pajekman.htm>.0.000.010.021015200.000.010.020510150.000.020.044681012abcfdInternetwwwAttackFailureAttackFailureSFE AttackFailure FIG.2.Changes in the diameter of the network as a function of the fraction of the removed nodes.a ,Comparison between the exponential (E)and scale-free (SF)network models,each containing N =10,000nodes and 20,000links (i.e. k =4).The blue symbols correspond to the diameter of the exponential (triangles)and the scale-free (squares)network when a fraction f of the nodes are removed randomly (error tolerance).Red symbols show the response of the exponential (diamonds)and the scale-free (circles)networks to attacks,when the most connected nodes are removed.We determined the f dependence of the diameter for different system sizes (N =1,000,5,000,20,000)and found that the obtained curves,apart from a logarithmic size correction,overlap with those shown in a ,indicating that the results are independent of the size of the system.Note that the diameter of the unperturbed (f =0)scale-free network is smaller than that of the exponential network,indicating that scale-free networks use more efficiently the links available to them,generating a more interconnected web.b ,The changes in the diameter of the Internet under random failures (squares)or attacks (circles).We used the topological map of the Internet,containing 6,209nodes and 12,200links ( k =3.4),collected by the National Laboratory for Applied Network Research </Routing/rawdata/>.c ,Error (squares)and attack (circles)survivability of the world-wide web,measured on a sample containing 325,729nodes and 1,498,353links [3],such that k =4.59.012301<s > a n d S0.00.20.40120.00.20.401210-110101102f<work fragmentation under random failures and attacks.The relative size of the largest cluster S (open symbols)and the average size of the isolated clusters s (filled symbols)in function of the fraction of removed nodes f for the same systems as in Fig.2.The size S is defined as the fraction of nodes contained in the largest cluster (i.e.S =1for f =0).a ,Fragmentation of the exponential network under random failures (squares)and attacks (circles).b ,Fragmentation of the scale-free network under random failures (blue squares)and attacks (red circles).The inset shows the error tolerance curves for the whole range of f ,indicating that the main cluster falls apart only after it has been completely deflated.Note that the behavior of the scale-free network under errors is consistent with an extremely delayed percolation transition:at unrealistically high error rates (f max ≃0.75)we do observe a very small peak in s ( s max ≃1.06)even in the case of random failures,indicating the existence of a critical point.For a and b we repeated the analysis for systems of sizes N =1,000,5,000,and 20,000,finding that the obtained S and s curves overlap with the one shown here,indicating that the overall clustering scenario and the value of the critical point is independent of the size of the system.Fragmentation of the Internet (c )and www (d ),using the topological data described in Fig.2.The symbols are the same as in b .Note that s in d in the case of attack is shown on a different scale,drawn in the right side of the frame.While for small f we have s ≃1.5,at f w c=0.067the average fragment size abruptly increases,peaking at s max ≃60,then decays rapidly.For the attack curve in d we ordered the nodes in function of the number of outgoing links,k out .Note that while the three studied networks,the scale-free model,the Internet and the www have different γ, k and clustering coefficient [11],their response to attacks and errors is identical.Indeed,we find that the difference between these quantities changes only f c and the magnitude of d ,S and s ,but not the nature of the response of these networks to perturbations.f≈0.05f≈0.18f≈0.45 FIG.4.Summary of the response of a network to failures or attacks.The insets show the cluster size distribution for various values of f when a scale-free network of parameters given in Fig.3b is subject to random failures(a-c)or attacks(d-f).Upper panel:Exponential networks under random failures and attacks and scale-free networks under attacks behave similarly:for small f clusters of different sizes break down,while there is still a large cluster.This is supported by the cluster size distribution:while we see a few fragments of sizes between1and16,there is a large cluster of size9,000(the size of the original system being10,000).At a critical f c(see Fig.3)the network breaks into small fragments between sizes1and100(b)and the large cluster disappears. At even higher f(c)the clusters are further fragmented into single nodes or clusters of size two. Lower panel:Scale-free networks follow a different scenario under random failures:The size of the largest cluster decreases slowly asfirst single nodes,then small clusters break off.Indeed,at f=0.05only single and double nodes break off(d).At f=0.18,when under attack the network is fragmented(b),under failures the large cluster of size8,000coexists with isolated clusters of size1through5(e).Even for unrealistically high error rate of f=0.45the large cluster persists, the size of the broken-offfragments not exceeding11(f).。
2022年全国大学生网络安全知识竞赛试题(单选题)

2022年全国大学生网络平安知识竞赛试题〔单项选择题〕1[单项选择题] GSM的鉴权三元组不包括RANDKcKiRES2[单项选择题] hp-ux系统中who命令通过读取_____文件,显示当前登录的用户信息/var/adm/wtmp/var/adm/btmp/etc/utmp/var/adm/utmp3[单项选择题] 关于Cisco路由器的时间戳设置,在没有启用NTP效劳的情况下,以下配置正确的选项是service timestamp log datetime localtimeservice timestamp log datetimeservice timestamp log uptimeservice timestamp log uptime localtime4[单项选择题] 在cisco网络设备中,以下命令都可以对口令进行加密,其中最平安的是:enable password ***enable secret ***username *** password ***password 7 ***5[单项选择题] 要限制用户连接vty,只允许IP1.1.1.1 可以连接,下面哪一个配置适用:access-list 1 permit 1.1.1.1 line vty 0 4 access-class 1 inaccess-list 1 permit 1.1.1.1 255.255.255.255 line vty 0 4 access-class 1 inaccess-list 1 pe 0.0.0.0 line vty 66 70 access-class 1 inaccess-list 1 permit 1.1.1.1 line vty 0 4 access-group 1 in6[单项选择题] 有三种根本的鉴别的方式: 你知道什么,你有什么,以及:你需要什么你看到什么你是什么你做什么7[单项选择题] SQL SERVER数据库本身能否审核登录失败和成功的记录信息?不可以只可以审核登录成功信息可以审核登录失败信息可以审核成功和失败的信息8[单项选择题] Tomcat中的tomcat-users.xml配置文件格式为:,其中password域〔〕明文保存使用MD5加密算法保存使用SHA-1加密算法保存使用DES加密算法保存2022年全国大学生网络平安知识竞赛9[单项选择题] 网站论坛等系统中经常替代HTML代码的一种平安代码简称为?UBB〔Ultimate Bulletin Board〕XMLDHTMLJavaScript10[单项选择题] 一台需要与Internet互通的效劳器放在哪个位置最平安〔〕内网外网DMZ和防火墙在同一台计算机上11[单项选择题] 默认配置喜爱,IIS的日志被存储在〔〕目录中%systemroot%/system32/logfiles/w3svc%systemroot%/logfiles/w3svc%systemroot%/logs/w3svc%systemroot%/logfiles/w3svc12[单项选择题] 重启IIS的命令是iisrestartiisresetiisrebootiisshutdown13[单项选择题] 用于查看/var/log/wtmp日志的命令是lastlastloglastwtmplastmp14[单项选择题],可以使用哪个命令或工具openfilesdirlistfilelist15[单项选择题] 下面对Oracle的密码规那么描述,哪个是错误的?Oracle 密码必须由英文字母,数字,#,下划线(_),美元字符($)构成,密码的最大长度为 30 字符;并不能以〞$〞,〞#〞,〞_〞或任何数字开头;密码不能包含像〞SELECT〞,〞DELETE〞,〞CREATE〞这类的 Oracle/SQL 关键字。
1Strategic Entrepreneurship_ Creating Value for Individuals, Organizations, and society

A R T I C L E S Strategic Entrepreneurship:Creating Value for Individuals,Organizations,and Societyby Michael A.Hitt,R.Duane Ireland,David G.Sirmon,and Cheryl A.TrahmsExecutive OverviewThe foci of strategic entrepreneurship(SE)are broad and rich,building on research from multiple disciplines such as economics,psychology,and sociology,along with other subdisciplines in management including organizational behavior and organization theory.Herein,we examine the contributions of strategic management and entrepreneurship to SE.Building on a previous model of SE,we develop an input-process-output model to extend our understanding of the SE construct.We examine the resource inputs into SE,such as individual knowledge and skills.In addition,we explore the resource orchestration processes that are important for SE and the outcomes,including creating value for customers,building wealth for stockholders,and creating benefits for other stakeholders,especially for society at large. Individual entrepreneurs also benefit through financial wealth,but other outcomes such as personal satisfaction and fulfillment of personal needs(e.g.,self-actualization)may be of equal or even greater importance.Therefore,we incorporate in the model of SE multilevel outcomes that motivate entrepre-neurs.A n important scholarly question with signifi-cant practical relevance in the current and projected economic environments is how firms can create value,an end goal of both stra-tegic management and entrepreneurship(Bruyat &Julien,2001;Meyer,1991).In particular,how do firms create and sustain a competitive advan-tage while simultaneously identifying and exploit-ing new opportunities?This is the primary ques-tion on which strategic entrepreneurship(SE)is based,placing it at the nexus of strategic man-agement and entrepreneurship.Thus,SE is con-cerned with advantage-seeking and opportuni-ty-seeking behaviors resulting in value for individuals,organizations,and/or society.This means that SE involves actions taken to exploit current advantages while concurrently exploring new opportunities that sustain an entity’s ability to create value across time.The need to under-stand how new ventures can achieve and sustain success by exploiting one or more competitive advantages and how large established firms can become more entrepreneurial provides incentives to theoretically explain and empirically explore the SE construct.Work on SE began in earnest early in the21st century(Hitt,Ireland,Camp,&Sexton,2001; Ireland,Hitt,Camp,&Sexton,2001).Ireland,*Michael A.Hitt(mhitt@)is Distinguished Professor,Joe B.Foster’56Chair in Business Leadership,Management Department,Mays School of Business,Texas A&M University.R.Duane Ireland(direland@)is Distinguished Professor,Conn Chair in New Ventures Leadership,Management Depart-ment,Mays School of Business,Texas A&M University.David G.Sirmon(dsirmon@)is Pamela M.and Barent W.Cater’77Faculty Research Fellow and Assistant Professor, Management Department,Mays School of Business,Texas A&M University.Cheryl A.Trahms(ctrahms@)is a Ph.D.Student and Research Assistant,Management Department,Mays School of Business,Texas A&M University.Copyright by the Academy of Management;all rights reserved.Contents may not be copied,e-mailed,posted to a listserv,or otherwise transmitted without the copyright holder’s express written ers may print,download,or e-mail articles for individual use only.Hitt,and Sirmon(2003)developed an initial model of SE with four key dimensions:(1)the entrepreneurial mindset,culture,and leadership, (2)the strategic management of organizational resources,(3)application of creativity,and(4) development of innovation.Based on additional research and critical examination of the SE con-struct,Kyrgidou and Hughes(2010)suggested that this model lacked the robustness required to capture the gestalt of SE.Supporting this assertion is recent evidence suggesting that SE is broader in scope,multilevel,and more dynamic(Chiles, Bluedorn,&Gupta,2007;Hitt,Beamish,Jackson, &Mathieu,2007;Rindova,Barry,&Ketchen, 2009)than was originally conceptualized.To contribute to the continuing development of this young and dynamic field of inquiry requires a richer model of SE.Thus,we extend the original SE model to incorporate a multilevel and broader domain(see Shepherd,2011).The enhanced model of strategic entrepreneurship presented herein integrates environmental influences,ex-plains how resources are managed in the process of SE to create value across time,and describes sev-eral different outcomes,thereby providing a more complete view of SE.The new model,discussions of resource orches-tration,and unique outcomes of SE produce a number of valuable and important questions warranting scholarly examination to advance our knowledge about SE and its application in orga-nizations.Integration of the Relevant Research S trategic management and entrepreneurship are separate disciplines offering unique opportuni-ties for scholarly inquiry as well as insights that inform managerial and entrepreneurial practice (Schendel&Hitt,2007).As a foundation for SE, we briefly summarize relevant research in these two domains.Strategic ManagementCreating competitive advantages and wealth are at the core of strategic management(Chen, Fairchild,Freeman,Harris,&Venkataraman, 2010).Andrews(1971)defined corporate strategy as a pattern of organizational decisions that evolves with the purpose of achieving an array of objectives that are important to a firm’s stakehold-ers.Hitt,Ireland,and Hoskisson(2011,p.6) defined strategic management as“the full set of commitments,decisions,and actions required for a firm to achieve strategic competitiveness and earn above-average returns.”With a strong focus on outcomes,Makadok and Coff(2002)sug-gested that strategic management’s purpose is to positively influence the firm’s ability to gener-ate profits.Strategic management scholars seek to under-stand the causes of performance differentials across firms(Ireland et al.,2003;Schendel& Hofer,1978).Effective competitive positioning is a primary factor influencing a firm’s ability to create value and wealth for stakeholders and the broader society(Ketchen,Ireland,&Snow,2007; Porter,1980).Similarly,the firm’s idiosyncratic stock of resources influences efforts to achieve these outcomes(Barney,1991).Learning how to acquire,bundle,and leverage the firm’s idiosyn-cratic resources is critical to achieving a compet-itive advantage and creating value(Chen,1996; Sirmon,Hitt,&Ireland,2007). EntrepreneurshipEntrepreneurship is a developing discipline that has begun to blossom in recent years,yet there is a lack of agreement on precisely what constitutes entrepreneurship(Rauch,Wiklund,Lumpkin,& Frese,2009).One definition frames the activities required for entrepreneurship to be engaged.In this context,Davidsson(2005,p.80)offered what he labeled as three partly overlapping views of entrepreneurial activities:“(1)entrepreneurship is starting and running one’s own firm;(2)entrepre-neurship is the creation of new organizations;and (3)entrepreneurship is...the creation of new-to-the-market economic activity.”Criticizing the tendency for scholars to define the entrepreneur-ship domain strictly in terms of the entrepreneur and what he or she does,Shane and Venkatara-man(2000,p.218)offered a more expansive definition,saying that the“field of entrepreneur-ship[is]the scholarly examination of how,by whom,and with what effects opportunities to create future goods and services are discovered,evaluated,and exploited.”Thus,Shane and Ven-kataraman argued that entrepreneurship involves sources of opportunities;the processes of discovery, evaluation,and exploitation of opportunities;and the set of individuals who discover,evaluate,and exploit opportunities.Consistent with the Shane and Venkataraman definition,Hitt et al.(2001,p. 480)defined entrepreneurship as“the identifica-tion and exploitation of previously unexploited opportunities.”Ireland et al.(2001,p.51)ex-panded this definition primarily to include a focus on wealth creation as an outcome of entrepreneur-ship:“We define entrepreneurship as a context-specific social process through which individuals and teams create wealth by bringing together unique packages of resources to exploit market-place opportunities.”However,to generate wealth first requires cre-ating value.Entrepreneurs create value by lever-aging innovation to exploit new opportunities and to create new product-market domains(Miles, 2005).More specifically,“value creation is the act of obtaining rents(widely defined as financial, social,or personal)that exceed the total costs (which may or may not include average rates of return for a particular industry)associated with that acquisition”(Bamford,2005,p.48).There-fore,generating wealth through value creation is entrepreneurship’s central function(Knight, 1921).Strategic EntrepreneurshipAs our discussion shows,strategic management and entrepreneurship are concerned with creating value and wealth.In the main,entrepreneurship contributes to a firm’s efforts to create value and subsequently wealth primarily by identifying op-portunities that can be exploited in a marketplace, while strategic management contributes to value-and wealth-creation efforts primarily by forming the competitive advantages that are the founda-tion on which a firm competes in a marketplace. Therefore,entrepreneurship involves identifying and exploiting opportunities,and strategic man-agement involves creating and sustaining one or more competitive advantages as the path through which opportunities are exploited.Thus,both strategic management and entrepreneurship“are concerned about growth,creating value for cus-tomers,and subsequently creating wealth for own-ers”(Hitt&Ireland,2005,p.228).A significant amount of scholarship focuses on the need for firm outcomes to create wealth only or primarily for shareholders.SE expands the scope to which a firm’s wealth-creating outcomes can apply to mul-tiple stakeholders,including society at large (Schendel&Hitt,2007).SE allows those leading and managing firms to simultaneously address the dual challenges of ex-ploiting current competitive advantages(the pur-view of strategic management)while exploring for opportunities(the purview of entrepreneurship) for which future competitive advantages can be developed and used as the path to value and wealth creation.Because“concentrating on either strategy or entrepreneurship to the exclusion of the other enhances the probability of firm ineffec-tiveness or even failure”(Ketchen et al.,2007,p. 372),SE involves both entrepreneurship’s oppor-tunity-seeking behaviors and strategic manage-ment’s advantage-seeking behaviors and is useful for all organizations,including family-oriented firms(Sirmon&Hitt,2003;Webb,Ketchen,& Ireland,2010).Relatively speaking,successfully using SE challenges large,established firms to learn how to become more entrepreneurial and challenges smaller entrepreneurial ventures to learn how to become more strategic.An Input-Process-Output Model of StrategicEntrepreneurshipH ere,we build on the initial model of SE(Ire-land et al.,2003)and draw insights from pre-vious research to present a multilevel input-process-output model for the purpose of providing a richer understanding of the SE construct.The SE model we advance incorporates environmen-tal,organizational,and individual foci into the dynamic process of simultaneous opportunity-and advantage-seeking behaviors.When used effec-tively,these behaviors create value for societies, organizations,and individuals.The SE model presented in Figure1identifies three dimensions:resource/factor inputs,resource orchestration processes,and outputs.The first di-mension specifies the resources/factors serving as the SE process inputs at different levels,including environmental factors,organizational factors,and individual resources.Second,we examine the SE-related actions or processes in the firm,specifically focusing on the orchestration of its resources and the entrepreneurial actions that are used to pro-tect and exploit current resources while simulta-neously exploring for new resources with value-creating potential.These actions occur primarily at the firm st,we examine outcomes, which vary across levels.Specifically,we focus on the creation of value for society,organizations, and individuals.These benefits include societal enhancements,wealth,knowledge,and opportu-nity.First,we discuss the inputs of the extended SE model.Inputs:Resources/FactorsEnvironmental FactorsThe firm’s external environment affects its ability and the ability of individuals to discover or create opportunities and,subsequently,their ability to exploit those opportunities as a foundation for competitive success.The relationship between the external environment and the firm affects perfor-mance(Keats&Hitt,1988)and long-term sur-vival(Dess&Beard,1984).In addition to the perspectives associated with traditional organiza-tional theories such as ecological theory(Hannan &Freeman,1984,1989)and evolutionary theory (Winter,2005),an entrepreneurial perspective of this relationship proposes that an organization and those within it influence the environment (Smith&Cao,2007).Munificence,dynamism (and the uncertainty resulting from it),and inter-connectedness are important environmental fac-tors for SE.Environmental munificence facilitates acquir-ing resources and identifying opportunities as well as the ability to exploit the resources and oppor-tunities to create competitive ani-zations seek out environmental munificence, which refers to the level of resources in a partic-ular environment that can support sustained growth,stability,and survival(Dess&Beard, 1984).Munificence allows firms to acquire re-sources such as raw materials,financial capital, labor,and customers(Aldrich,1979;Castrogio-vanni,1991)and intangible assets such as anFigure1Input-Process-Output Model of SEindustry’s or geographic region’s tacit knowledge (Agarwal,Audretsch,&Sarkar,2007).The munificence of an environment(e.g.,geo-graphic region)is context-specific for the firm. Moreover,entrepreneurially minded individuals gain access to resources in the environment to generate competitive advantage and create value by engaging in entrepreneurial bricolage.Baker and Nelson(2005)identified three characteristics that affect how perceptions of resources influence the successful interaction between a firm and its environment.First,firms are idiosyncratic in what they perceive to be value-creating resources.Sec-ond,firms tend to gain differential benefits from resources based on their leaders’creative judg-ments and actions.Third,because of the nature of the first two attributes,firms can capitalize on resources that other organizations deem to have less value-creating potential.Thus,even resource-constrained environments can be perceived as munificent by some firms.An example is the intangible assets that leak into the environment when firms fail to commercialize knowledge they hold(Agarwal et al.,2007).As knowledge is rarely idiosyncratic to one organization,it is diffi-cult to avoid leakage and protect against appro-priation by competitors.This knowledge spillover allows individuals and firms to appropriate knowl-edge that can be used to create firm capabilities. These capabilities are then used to gain a compet-itive advantage that subsequently leads to perfor-mance gains(DeCarolis&Deeds,1999;Grant, 1996),resulting in the economic growth of a region and the expansion of an industry(Agarwal et al.,2007).The environment many firms face is inherently dynamic,thereby producing uncertainty(Barnard, 1938).Uncertainty(and the willingness to bear uncertainty)(McMullen&Shepherd,2006)si-multaneously poses threats and reveals opportuni-ties.Because of uncertainty,the quality of infor-mation available to firms and individuals is limited,reducing their ability to assess present and future environmental states.In addition,an in-ability to access robust information about condi-tions in the external environment creates ambi-guity during the strategic decision-making process (e.g.,decision makers lack adequate knowledge for identifying and exploiting new opportunities). However,research has shown that environmental dynamism has a positive relationship with new venture creation(Aldrich,2000)and innovation through the stimulation of exploration(Wang& Li,2008).Gaglio and Katz(2001)suggest that individuals who act entrepreneurially seek opportunities in dynamic markets,using their knowledge stocks and ability to perceive and deal with uncertainty. The ability to operate under conditions of uncer-tainty may also be based on an individual’s moti-vation and risk propensity(Baum&Locke,2004). Alternatively,radical innovations produced by entrepreneurial firms often serve as a catalyst for or at least contribute to more dynamic and poten-tially more munificent environments.In dynamic environments,some firms use rela-tionships to gain access to needed resources from partners and then bundle them to exploit oppor-tunities.In addition,firms may use cooperative strategies such as alliances to build capabilities that facilitate the building of a competitive ad-vantage.Theories of interconnectedness includ-ing networks and social capital explain the paths firms follow to build capabilities in this manner.Building on organizational learning,resource-based,and real options theories,Ketchen et al. (2007)argued that collaborative innovation,in which large and small firms share ideas,knowl-edge,expertise,and opportunities,supports SE. Small firms are able to use creativity to create unique innovation while minimizing the liabilities associated with their small size and newness.Al-ternatively,because of slack resources,large firms are able to explore opportunities outside their traditional domain and leverage existing business practices in doing so.Organizational ResourcesCulture and top leadership are perhaps the re-sources that are the most idiosyncratic to a specific organization.Effective leadership is required to develop and grow new ventures and to entrepre-neurially lead established corporations.Leaders understand the importance of developing and sup-porting a culture through which the entrepreneur-ial actions necessary to achieve profitable growthare established(Kuratko,Ireland,Covin,&Horns-by,2005).“[An]entrepreneurial culture is one in which new ideas and creativity are expected,risk taking is encouraged,failure is tolerated,learning is promoted,product,process and administrative innovations are championed,and continuous change is viewed as a conveyor of opportunities”(Ireland et al.,2003,p.970).Thus,entrepreneur-ial leadership is the ability to influence others to emphasize opportunity-seeking and advantage-seeking behaviors(Covin&Slevin,2002).Entrepreneurial leaders create visionary scenar-ios that can be used to assemble and mobilize a supporting group in the firm that is committed to opportunity discovery and exploitation(Gupta, Macmillan,&Surie,2004).The leader and the organizational culture are interdependent;they are symbiotic,with the leader’s judgments affect-ing the organizational culture and cultural attri-butes influencing a leader’s future decisions and actions.In this manner,an“entrepreneurial loop”occurs between a leader’s ability to identify an opportunity and the attributes of organizational culture that positively influence pursuing it (Shepherd,Patzelt,&Haynie,2009).Individual ResourcesFinancial capital(a tangible resource)and social and human capital(intangible resources)are nec-essary to engage in SE(Ireland et al.,2003). Alone,financial capital is relatively less important than social and human capital for achieving,and especially for sustaining,a competitive advantage; however,financial capital is often crucial for ac-quiring or creating the resources necessary to ex-ploit opportunities.For example,new ventures and firms with stronger financial positions in early developmental stages are more likely to survive, grow,and experience higher performance(Chad-dad&Reuer,2009).In addition,established firms with strong financial resources have slack,which can facilitate the development of innovations (Kim,Kim,&Lee,2008).The firm’s social capital is the sum of its inter-nal social capital(relationships between individ-uals)and its external social capital(relationships between external organizations and individuals in the focal firm).It facilitates actions taken to ac-cess additional resources and to build and leverage capabilities to achieve a competitive advantage (Hitt,Lee,&Yucel,2002).Thus,specific social skills influence individuals’ability not only to acquire knowledge and resources,but to create and/or identify opportunities.Baron and Mark-man(2000,2003)suggest that social skills—for example,reputation and expansion of social networks—play a significant role in the success of individuals and their new ventures by attract-ing resources such as financial capital and key employees.In a specific context,evidence indicates that an entrepreneur’s social skills and social networks influence outcomes for both new ventures and established organizations(Baron&Tang,2009; Batjargal et al.,2009).Additional evidence indi-cates that within the firm,individuals with well-developed social skills who recognize or create opportunities can gain acceptance for projects that require cross-divisional resources through so-cial networks(Kleinbaum&Tushman,2007). Actions taken to exploit an opportunity encour-age others in the organization to collaborate, which in turn facilitates a social structure and culture conducive to subsequent opportunity-seeking behaviors.Human capital is the set of individuals’capa-bilities,knowledge,and experience related to a task and the ability to increase the“capital”through learning(Dess&Lumpkin,2001).Chandler (1962)wrote that of all resources available to firms,human resources are perhaps the most im-portant;thus,idiosyncratic human capital can be central to a new venture’s survival(Baker,Miner, &Easley,2003)and an established firm’s success. Tacit knowledge is particularly important in iden-tifying entrepreneurial opportunities(McGrath& MacMillan,2000)and in achieving a competitive advantage(Coff,2002).Individuals’knowledge, skills,and abilities,along with their motivation and passion to perform,are important for a firm to exploit an opportunity and achieve an advantage as the sources of its long-term success.The entrepreneurial mindset,composed of alertness,real option reasoning,and opportunity recognition,facilitates rapid sensing to identify and exploit opportunities,even those that arehighly uncertain(McGrath&MacMillan,2000). Entrepreneurial alertness entails the ability to no-tice opportunities that have been hitherto over-looked and to do so without searching for them (Kirzner,1979).However,being alert is a neces-sary but insufficient condition to effectively en-gaging in SE.In the SE framework,an individual must respond to numerous economic changes and innovations in a dynamic(and uncertain)envi-ronment.To make decisions,one needs a frame-work that helps to identify decision criteria,the available resources,and the value creation goals (Gaglio,2004).Entrepreneurial cognition,or the knowledge structures driving assessments of op-portunities(Holcomb,Ireland,Holmes,&Hitt, 2009),helps to differentiate the degree of risk involved with various opportunities(Baron,2007) and thus to select the most appropriate one for the new venture(or established organization).Real options logic suggests that real assets pos-sess the same characteristics as financial options (Barney,2002).This set of characteristics facili-tates individuals’willingness to engage in risky (yet carefully evaluated)entrepreneurial activity through opportunity-seeking behavior.Real op-tions have the potential to positively or negatively influence opportunity-and advantage-seeking be-haviors.The nature of factors in the external environment at a point in time(e.g.,bankruptcy laws)determines the maximum potential down-side loss associated with a firm’s risky investments, while the upside potential of these investments is commonly high.An entrepreneur-friendly bank-ruptcy law(i.e.,one that allows reasonable conditions for continuing the new venture by allowing the restructuring of debt)encourages en-trepreneurial activity and economic development (Lee,Peng,&Barney,2007).Alternatively, strong bankruptcy laws(e.g.,ones that make it difficult to continue the new venture after declar-ing bankruptcy)deter individual and firm risk-taking behaviors.Goal setting is significantly influenced by an individual’s psychological factors.For example, passion,which in an entrepreneurial context is reflected in the entrepreneur’s devotion and en-thusiasm for a proposed business venture(Chen, Yoa,&Kotha,2009),accounts for behaviors such as unconventional risk taking,focused intensity, and belief in a dream(Cardon,Wincent,Singh, &Drnovsek,2009).Entrepreneurial leaders’ex-pression of passion for the new venture can moti-vate employees to create new ideas,take risks,and develop personal pride in the firm’s goals.There-fore,passion contributes to entrepreneurial suc-cess because of the commitment and effort gener-ated(Baum&Locke,2004).Passion and the commitment it engenders contribute to entrepre-neurial self-efficacy.Cassar and Freidman(2009) found that entrepreneurial self-efficacy has a sig-nificant influence on the commitment of both personal time and capital to discover(or create) and exploit entrepreneurial opportunities.For en-trepreneurial leaders,high self-efficacy often con-tributes to enhanced revenue and employment growth in the firm(Baum&Locke,2004).Pas-sion and entrepreneurial self-efficacy motivate en-trepreneurs to pursue and realize strategic and entrepreneurial goals that are central to SE.Alvarez and Barney(2007)argued that there are two theories of entrepreneurial action:discov-ery of existing opportunities and creation of new opportunities.Thus,opportunity-seeking behav-ior could involve being alert to existing opportu-nities or creating new opportunities.The tradi-tional perspective of the entrepreneurship process, focused on the discovery of an opportunity(Eck-hard&Shane,2003),relies on a notion of cau-sation.Two individuals may have the same char-acteristics and resources;however,environmental variation may lead only one of the two to identify and exploit a particular opportunity(Alvarez& Barney,2010).Identifying existing opportunities requires the entrepreneurial mindset.However,creating opportunities involves dif-ferent types of entrepreneurial actions:effectua-tion and creativity.Effectuation is based on the notion that firm growth relies on dynamic and interactive judgments in which the future is un-predictable yet controllable through human ac-tion,and the belief that the environment can be enacted through choice(Sarasvathy,2008).Thus, cognitive ability to effectuate is used to create opportunities in the environment and to achieve short-term competitive advantages.Creativity af-fects the quality and quantity of innovations,change”)increased investment by millions of dol-lars.Beyond capital investment,Zott and Huy (2007)found that entrepreneurs’“symbolic ac-tions”speak loudly to a wide array of resource providers.More specifically,they found that dem-onstrating personal credibility,professional orga-nization,achievement,and relational aptitude not only resulted in higher levels of capital invest-ment,but also helped entrepreneurs attract tal-ented human capital and assemble a sufficient customer base.Firms may also find it necessary to build re-sources internally(accumulate)as well as divest them.Divestment is an understudied phenome-non;however,it is critical in managing resources. Recent research indicates that reducing weak-nesses may be more important for increasing per-formance than increasing a firm’s strengths(Sir-mon et al.,2010).In addition,Morrow,Sirmon, Hitt,and Holcomb(2007)provided evidence that divestment can be especially useful when firms attempt to recover from a performance crisis.Pre-sumably,the divested resources create a weakness that when released removes a negative influence on firm performance(Shimizu&Hitt,2005). Accumulating resources(knowledge,skills,repu-tation,etc.)often complements acquiring re-sources,thereby allowing firms to create unique resource portfolios.BundlingBundling resources to form capabilities requires intentional actions.Often,capabilities are formed within functions such as manufacturing and mar-keting.Bundling requires knowledge while pro-viding a rich learning context,especially tacit learning.For example,Kor and Leblebici(2005) found that bundling senior partners with less ex-perienced associates in law firms positively affects performance.These results support Hitt,Bierman, Shimizu,and Kochhar’s(2001)suggestion that bundling choices strongly affect the development of tacit knowledge.Thus,the choices leaders make regarding the bundling of resources to sta-bilize,enrich,or pioneer new capabilities are im-portant to achieving and sustaining a competitive advantage(Lu,Zhou,Bruton,&Li,2010).LeveragingLeveraging actions move the firm from the poten-tial to create value to realizing value by deploying the capabilities to achieve competitive advan-tages.Leaders mobilize,coordinate,and deploy specific capabilities in particular market contexts by choosing and implementing a particular strat-egy.Of equal importance to choosing the strategy to follow is synchronizing the actions necessary for leveraging.Recent empirical work demonstrates that resource investment deviating from industry norms negatively affects performance,unless that deviation is synchronized with an appropriate le-veraging strategy(Sirmon&Hitt,2009).When matched to the appropriate strategy,greater in-vestment deviations(in either direction from in-vestment norms)lead to higher performance.Sup-porting these conclusions,Holcomb,Holmes,and Connelly’s(2009)results showed that synchroni-zation across the resource management processes is vital to developing a competitive advantage.For synchronization to occur,leaders require sufficient information pertaining to the firm’s ex-ternal environment and internal organization as well as the ability to effectively process that in-formation.Sleptsov and Anand’s(2008)research suggested that having one without the other, or—as is more likely the case—when such infor-mation is not balanced,performance is negatively affected.Thus,feedback loops exist among struc-turing,bundling,and leveraging actions(Sirmon et al.,2007).Although we discuss these actions sequentially,in practice leaders can,and likely do, perform them in an iterative process.The choice of sequencing or iteration among these actions may be based on the specific oppor-tunity being considered.For instance,Choi and Shepherd(2004)found that the decision to ex-ploit an opportunity was influenced by several factors,including knowledge of the customer, knowledge of the underlying technology offered, level of stakeholder support,and overall manage-rial experience.Moreover,an opportunity’s at-tractiveness enhanced the effect of all of these factors,especially managerial experience.Thus, when potential entrepreneurs have a high level of stakeholder support that addresses much of their。
牛顿-拉夫逊潮流计算中检测雅可比矩阵奇异性和网络孤岛的新方法

由 ( 式可得:I 【 0由于 D是对角矩 3 ) = 阵, , 因此 至少有一对角元 素为 0 。 因为 U= UL D D ,VL 设该潮流计算 是 n 节点 系统 。 所以( ) 2) 2 或( 工 a b弋有一个成立 , U 中有一 H子矩阵奇异 ,那 么 H矩阵各 个列向量线 性相 即 n 一1 零行 或 中有一零列 。 u 中行为零 , 是行相关 隋况 ;丰中列 为 关 , : 这 L 即 - = ( 不全为 0 q 0 ) 零, 这是列相关 隋况。 其 中: 是 H矩 阵的列 向量 ,1是相关 系 c T A矩 阵奇异 , 那么 A矩 阵行 向量 、 向量线 列 数 。由潮流雅可 比矩阵元素计算可知 : 性相关 , 即: 对 同一节点 , 素和 J 素的计 算具 有完 H元 元 全相似 的表达式 ,因此 ,矩 阵的各个列 向量也 J (a 4) 应满足( , 即:
中国新技术新产 品
一7
!
C ia N w T c n l ge n r d cs h n e e h oo isa d P o u t
高 新 技 术
新型停 水 自动关 闭阀结构 、 点及操作要 点 特
张金龙 曹 艳
( 西安航 空技 术高等专科学校机械 工程 系, 陕西 西安 7 0 7 ) 10 7
中图分 类 号 : 4 . 文献标 识 码 : G6 45 A
。
I 言 。在 日常生 活 中 , 前 由于停 水时 忘记 关 闭 阀门 , 水 时 也没 能及 时 关 闭 阀门 , 来 造成 水 资源 浪 费甚 至形 成安 全 隐 患 的情况 屡 见不 鲜 。 着全 民节 水 概念 不 断深入 人 心 , 一 问 随 这 题 引起 各方 关 注 。 因此 急 需设 计 一 款可 以在 停 水 时 自动关 闭 的水 阀 ,它 能够 在停 水 后 即 使 人们 忘记 关 闭 水 龙 头 也 能实 现 自动 关 闭 , 而再 次 来水 时 不 至于 出 现水 患 的情 况 ,能够 有 效 的节 约水 资源 。 要 实 现 自动 关 闭 功 能首 先 要 有 动 力 , 这 方 面可 以借 助 磁性 元件 的磁 力 、弹性 元 件 的 弹力 、 力 等外 力 , 时考 虑供 水 和停 水 时 的 重 同 水 压变 化 , 通过 联 动机 构实 现 。 2停 水 自动关 闭 阀 的结 构 及 特点 。利用 水 压 、 力 等 力 学 特 性 , 过 一 系 列 的实 验 、 重 经 改 进 , 发 出一 种 简单 、 行 的带 有 停水 自锁 研 可 机 构 的水 阀 。 款 水 阀为纯 机 械构 造 , 阀体 这 以 为 主体 框 架 , 有 阀 芯 、 封 圈 、 心 轮 以及 配 密 偏 手柄 , 无弹 性元 件 , 作状 况 不 受环 境 和时 间 工 的 限制 , 构 简 单 , 价 低 廉 并 方 便拆 换 , 结 造 整 体 可靠 性 高 。 停 水 自动关 闭 阀结 构 原 理 如 图 1 示 , 所 实 物 如 图 2所示 。序号 l 水 阀 的偏 心轮 , 为 2 为 0 型密 封 圈 , 为 V型 密封 圈 , 阀体 , 3 4为 5 为 阀芯 , 销 轴 , 手 柄 。 阀体 4是 主 框 6为 7为 架 , 来装 配其 它 元 件 , 进 水 口和 出 水 口; 用 有 阀芯 5的顶 端 与末 端分 别 装有 V 型密 封 圈 3 和 0 型 密 封 圈 2v 型 密 封 圈 3利 用 其 锥 面 , 与 阀体 4内部 锥 面 配合 实 现 停 水 时 密 封 , 而 0型密 封 圈 2与 阀体 4内壁 的接 触 实 现来 水 时对 水 阀末 端 的密 封 ,在 阀 芯 5的 中部 开两
3GPP TS 36.331 V13.2.0 (2016-06)

3GPP TS 36.331 V13.2.0 (2016-06)Technical Specification3rd Generation Partnership Project;Technical Specification Group Radio Access Network;Evolved Universal Terrestrial Radio Access (E-UTRA);Radio Resource Control (RRC);Protocol specification(Release 13)The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented.This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organizational Partners' Publications Offices.KeywordsUMTS, radio3GPPPostal address3GPP support office address650 Route des Lucioles - Sophia AntipolisValbonne - FRANCETel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16InternetCopyright NotificationNo part may be reproduced except as authorized by written permission.The copyright and the foregoing restriction extend to reproduction in all media.© 2016, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC).All rights reserved.UMTS™ is a Trade Mark of ETSI registered for the benefit of its members3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational PartnersLTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM AssociationBluetooth® is a Trade Mark of the Bluetooth SIG registered for the benefit of its membersContentsForeword (18)1Scope (19)2References (19)3Definitions, symbols and abbreviations (22)3.1Definitions (22)3.2Abbreviations (24)4General (27)4.1Introduction (27)4.2Architecture (28)4.2.1UE states and state transitions including inter RAT (28)4.2.2Signalling radio bearers (29)4.3Services (30)4.3.1Services provided to upper layers (30)4.3.2Services expected from lower layers (30)4.4Functions (30)5Procedures (32)5.1General (32)5.1.1Introduction (32)5.1.2General requirements (32)5.2System information (33)5.2.1Introduction (33)5.2.1.1General (33)5.2.1.2Scheduling (34)5.2.1.2a Scheduling for NB-IoT (34)5.2.1.3System information validity and notification of changes (35)5.2.1.4Indication of ETWS notification (36)5.2.1.5Indication of CMAS notification (37)5.2.1.6Notification of EAB parameters change (37)5.2.1.7Access Barring parameters change in NB-IoT (37)5.2.2System information acquisition (38)5.2.2.1General (38)5.2.2.2Initiation (38)5.2.2.3System information required by the UE (38)5.2.2.4System information acquisition by the UE (39)5.2.2.5Essential system information missing (42)5.2.2.6Actions upon reception of the MasterInformationBlock message (42)5.2.2.7Actions upon reception of the SystemInformationBlockType1 message (42)5.2.2.8Actions upon reception of SystemInformation messages (44)5.2.2.9Actions upon reception of SystemInformationBlockType2 (44)5.2.2.10Actions upon reception of SystemInformationBlockType3 (45)5.2.2.11Actions upon reception of SystemInformationBlockType4 (45)5.2.2.12Actions upon reception of SystemInformationBlockType5 (45)5.2.2.13Actions upon reception of SystemInformationBlockType6 (45)5.2.2.14Actions upon reception of SystemInformationBlockType7 (45)5.2.2.15Actions upon reception of SystemInformationBlockType8 (45)5.2.2.16Actions upon reception of SystemInformationBlockType9 (46)5.2.2.17Actions upon reception of SystemInformationBlockType10 (46)5.2.2.18Actions upon reception of SystemInformationBlockType11 (46)5.2.2.19Actions upon reception of SystemInformationBlockType12 (47)5.2.2.20Actions upon reception of SystemInformationBlockType13 (48)5.2.2.21Actions upon reception of SystemInformationBlockType14 (48)5.2.2.22Actions upon reception of SystemInformationBlockType15 (48)5.2.2.23Actions upon reception of SystemInformationBlockType16 (48)5.2.2.24Actions upon reception of SystemInformationBlockType17 (48)5.2.2.25Actions upon reception of SystemInformationBlockType18 (48)5.2.2.26Actions upon reception of SystemInformationBlockType19 (49)5.2.3Acquisition of an SI message (49)5.2.3a Acquisition of an SI message by BL UE or UE in CE or a NB-IoT UE (50)5.3Connection control (50)5.3.1Introduction (50)5.3.1.1RRC connection control (50)5.3.1.2Security (52)5.3.1.2a RN security (53)5.3.1.3Connected mode mobility (53)5.3.1.4Connection control in NB-IoT (54)5.3.2Paging (55)5.3.2.1General (55)5.3.2.2Initiation (55)5.3.2.3Reception of the Paging message by the UE (55)5.3.3RRC connection establishment (56)5.3.3.1General (56)5.3.3.1a Conditions for establishing RRC Connection for sidelink communication/ discovery (58)5.3.3.2Initiation (59)5.3.3.3Actions related to transmission of RRCConnectionRequest message (63)5.3.3.3a Actions related to transmission of RRCConnectionResumeRequest message (64)5.3.3.4Reception of the RRCConnectionSetup by the UE (64)5.3.3.4a Reception of the RRCConnectionResume by the UE (66)5.3.3.5Cell re-selection while T300, T302, T303, T305, T306, or T308 is running (68)5.3.3.6T300 expiry (68)5.3.3.7T302, T303, T305, T306, or T308 expiry or stop (69)5.3.3.8Reception of the RRCConnectionReject by the UE (70)5.3.3.9Abortion of RRC connection establishment (71)5.3.3.10Handling of SSAC related parameters (71)5.3.3.11Access barring check (72)5.3.3.12EAB check (73)5.3.3.13Access barring check for ACDC (73)5.3.3.14Access Barring check for NB-IoT (74)5.3.4Initial security activation (75)5.3.4.1General (75)5.3.4.2Initiation (76)5.3.4.3Reception of the SecurityModeCommand by the UE (76)5.3.5RRC connection reconfiguration (77)5.3.5.1General (77)5.3.5.2Initiation (77)5.3.5.3Reception of an RRCConnectionReconfiguration not including the mobilityControlInfo by theUE (77)5.3.5.4Reception of an RRCConnectionReconfiguration including the mobilityControlInfo by the UE(handover) (79)5.3.5.5Reconfiguration failure (83)5.3.5.6T304 expiry (handover failure) (83)5.3.5.7Void (84)5.3.5.7a T307 expiry (SCG change failure) (84)5.3.5.8Radio Configuration involving full configuration option (84)5.3.6Counter check (86)5.3.6.1General (86)5.3.6.2Initiation (86)5.3.6.3Reception of the CounterCheck message by the UE (86)5.3.7RRC connection re-establishment (87)5.3.7.1General (87)5.3.7.2Initiation (87)5.3.7.3Actions following cell selection while T311 is running (88)5.3.7.4Actions related to transmission of RRCConnectionReestablishmentRequest message (89)5.3.7.5Reception of the RRCConnectionReestablishment by the UE (89)5.3.7.6T311 expiry (91)5.3.7.7T301 expiry or selected cell no longer suitable (91)5.3.7.8Reception of RRCConnectionReestablishmentReject by the UE (91)5.3.8RRC connection release (92)5.3.8.1General (92)5.3.8.2Initiation (92)5.3.8.3Reception of the RRCConnectionRelease by the UE (92)5.3.8.4T320 expiry (93)5.3.9RRC connection release requested by upper layers (93)5.3.9.1General (93)5.3.9.2Initiation (93)5.3.10Radio resource configuration (93)5.3.10.0General (93)5.3.10.1SRB addition/ modification (94)5.3.10.2DRB release (95)5.3.10.3DRB addition/ modification (95)5.3.10.3a1DC specific DRB addition or reconfiguration (96)5.3.10.3a2LWA specific DRB addition or reconfiguration (98)5.3.10.3a3LWIP specific DRB addition or reconfiguration (98)5.3.10.3a SCell release (99)5.3.10.3b SCell addition/ modification (99)5.3.10.3c PSCell addition or modification (99)5.3.10.4MAC main reconfiguration (99)5.3.10.5Semi-persistent scheduling reconfiguration (100)5.3.10.6Physical channel reconfiguration (100)5.3.10.7Radio Link Failure Timers and Constants reconfiguration (101)5.3.10.8Time domain measurement resource restriction for serving cell (101)5.3.10.9Other configuration (102)5.3.10.10SCG reconfiguration (103)5.3.10.11SCG dedicated resource configuration (104)5.3.10.12Reconfiguration SCG or split DRB by drb-ToAddModList (105)5.3.10.13Neighbour cell information reconfiguration (105)5.3.10.14Void (105)5.3.10.15Sidelink dedicated configuration (105)5.3.10.16T370 expiry (106)5.3.11Radio link failure related actions (107)5.3.11.1Detection of physical layer problems in RRC_CONNECTED (107)5.3.11.2Recovery of physical layer problems (107)5.3.11.3Detection of radio link failure (107)5.3.12UE actions upon leaving RRC_CONNECTED (109)5.3.13UE actions upon PUCCH/ SRS release request (110)5.3.14Proximity indication (110)5.3.14.1General (110)5.3.14.2Initiation (111)5.3.14.3Actions related to transmission of ProximityIndication message (111)5.3.15Void (111)5.4Inter-RAT mobility (111)5.4.1Introduction (111)5.4.2Handover to E-UTRA (112)5.4.2.1General (112)5.4.2.2Initiation (112)5.4.2.3Reception of the RRCConnectionReconfiguration by the UE (112)5.4.2.4Reconfiguration failure (114)5.4.2.5T304 expiry (handover to E-UTRA failure) (114)5.4.3Mobility from E-UTRA (114)5.4.3.1General (114)5.4.3.2Initiation (115)5.4.3.3Reception of the MobilityFromEUTRACommand by the UE (115)5.4.3.4Successful completion of the mobility from E-UTRA (116)5.4.3.5Mobility from E-UTRA failure (117)5.4.4Handover from E-UTRA preparation request (CDMA2000) (117)5.4.4.1General (117)5.4.4.2Initiation (118)5.4.4.3Reception of the HandoverFromEUTRAPreparationRequest by the UE (118)5.4.5UL handover preparation transfer (CDMA2000) (118)5.4.5.1General (118)5.4.5.2Initiation (118)5.4.5.3Actions related to transmission of the ULHandoverPreparationTransfer message (119)5.4.5.4Failure to deliver the ULHandoverPreparationTransfer message (119)5.4.6Inter-RAT cell change order to E-UTRAN (119)5.4.6.1General (119)5.4.6.2Initiation (119)5.4.6.3UE fails to complete an inter-RAT cell change order (119)5.5Measurements (120)5.5.1Introduction (120)5.5.2Measurement configuration (121)5.5.2.1General (121)5.5.2.2Measurement identity removal (122)5.5.2.2a Measurement identity autonomous removal (122)5.5.2.3Measurement identity addition/ modification (123)5.5.2.4Measurement object removal (124)5.5.2.5Measurement object addition/ modification (124)5.5.2.6Reporting configuration removal (126)5.5.2.7Reporting configuration addition/ modification (127)5.5.2.8Quantity configuration (127)5.5.2.9Measurement gap configuration (127)5.5.2.10Discovery signals measurement timing configuration (128)5.5.2.11RSSI measurement timing configuration (128)5.5.3Performing measurements (128)5.5.3.1General (128)5.5.3.2Layer 3 filtering (131)5.5.4Measurement report triggering (131)5.5.4.1General (131)5.5.4.2Event A1 (Serving becomes better than threshold) (135)5.5.4.3Event A2 (Serving becomes worse than threshold) (136)5.5.4.4Event A3 (Neighbour becomes offset better than PCell/ PSCell) (136)5.5.4.5Event A4 (Neighbour becomes better than threshold) (137)5.5.4.6Event A5 (PCell/ PSCell becomes worse than threshold1 and neighbour becomes better thanthreshold2) (138)5.5.4.6a Event A6 (Neighbour becomes offset better than SCell) (139)5.5.4.7Event B1 (Inter RAT neighbour becomes better than threshold) (139)5.5.4.8Event B2 (PCell becomes worse than threshold1 and inter RAT neighbour becomes better thanthreshold2) (140)5.5.4.9Event C1 (CSI-RS resource becomes better than threshold) (141)5.5.4.10Event C2 (CSI-RS resource becomes offset better than reference CSI-RS resource) (141)5.5.4.11Event W1 (WLAN becomes better than a threshold) (142)5.5.4.12Event W2 (All WLAN inside WLAN mobility set becomes worse than threshold1 and a WLANoutside WLAN mobility set becomes better than threshold2) (142)5.5.4.13Event W3 (All WLAN inside WLAN mobility set becomes worse than a threshold) (143)5.5.5Measurement reporting (144)5.5.6Measurement related actions (148)5.5.6.1Actions upon handover and re-establishment (148)5.5.6.2Speed dependant scaling of measurement related parameters (149)5.5.7Inter-frequency RSTD measurement indication (149)5.5.7.1General (149)5.5.7.2Initiation (150)5.5.7.3Actions related to transmission of InterFreqRSTDMeasurementIndication message (150)5.6Other (150)5.6.0General (150)5.6.1DL information transfer (151)5.6.1.1General (151)5.6.1.2Initiation (151)5.6.1.3Reception of the DLInformationTransfer by the UE (151)5.6.2UL information transfer (151)5.6.2.1General (151)5.6.2.2Initiation (151)5.6.2.3Actions related to transmission of ULInformationTransfer message (152)5.6.2.4Failure to deliver ULInformationTransfer message (152)5.6.3UE capability transfer (152)5.6.3.1General (152)5.6.3.2Initiation (153)5.6.3.3Reception of the UECapabilityEnquiry by the UE (153)5.6.4CSFB to 1x Parameter transfer (157)5.6.4.1General (157)5.6.4.2Initiation (157)5.6.4.3Actions related to transmission of CSFBParametersRequestCDMA2000 message (157)5.6.4.4Reception of the CSFBParametersResponseCDMA2000 message (157)5.6.5UE Information (158)5.6.5.1General (158)5.6.5.2Initiation (158)5.6.5.3Reception of the UEInformationRequest message (158)5.6.6 Logged Measurement Configuration (159)5.6.6.1General (159)5.6.6.2Initiation (160)5.6.6.3Reception of the LoggedMeasurementConfiguration by the UE (160)5.6.6.4T330 expiry (160)5.6.7 Release of Logged Measurement Configuration (160)5.6.7.1General (160)5.6.7.2Initiation (160)5.6.8 Measurements logging (161)5.6.8.1General (161)5.6.8.2Initiation (161)5.6.9In-device coexistence indication (163)5.6.9.1General (163)5.6.9.2Initiation (164)5.6.9.3Actions related to transmission of InDeviceCoexIndication message (164)5.6.10UE Assistance Information (165)5.6.10.1General (165)5.6.10.2Initiation (166)5.6.10.3Actions related to transmission of UEAssistanceInformation message (166)5.6.11 Mobility history information (166)5.6.11.1General (166)5.6.11.2Initiation (166)5.6.12RAN-assisted WLAN interworking (167)5.6.12.1General (167)5.6.12.2Dedicated WLAN offload configuration (167)5.6.12.3WLAN offload RAN evaluation (167)5.6.12.4T350 expiry or stop (167)5.6.12.5Cell selection/ re-selection while T350 is running (168)5.6.13SCG failure information (168)5.6.13.1General (168)5.6.13.2Initiation (168)5.6.13.3Actions related to transmission of SCGFailureInformation message (168)5.6.14LTE-WLAN Aggregation (169)5.6.14.1Introduction (169)5.6.14.2Reception of LWA configuration (169)5.6.14.3Release of LWA configuration (170)5.6.15WLAN connection management (170)5.6.15.1Introduction (170)5.6.15.2WLAN connection status reporting (170)5.6.15.2.1General (170)5.6.15.2.2Initiation (171)5.6.15.2.3Actions related to transmission of WLANConnectionStatusReport message (171)5.6.15.3T351 Expiry (WLAN connection attempt timeout) (171)5.6.15.4WLAN status monitoring (171)5.6.16RAN controlled LTE-WLAN interworking (172)5.6.16.1General (172)5.6.16.2WLAN traffic steering command (172)5.6.17LTE-WLAN aggregation with IPsec tunnel (173)5.6.17.1General (173)5.7Generic error handling (174)5.7.1General (174)5.7.2ASN.1 violation or encoding error (174)5.7.3Field set to a not comprehended value (174)5.7.4Mandatory field missing (174)5.7.5Not comprehended field (176)5.8MBMS (176)5.8.1Introduction (176)5.8.1.1General (176)5.8.1.2Scheduling (176)5.8.1.3MCCH information validity and notification of changes (176)5.8.2MCCH information acquisition (178)5.8.2.1General (178)5.8.2.2Initiation (178)5.8.2.3MCCH information acquisition by the UE (178)5.8.2.4Actions upon reception of the MBSFNAreaConfiguration message (178)5.8.2.5Actions upon reception of the MBMSCountingRequest message (179)5.8.3MBMS PTM radio bearer configuration (179)5.8.3.1General (179)5.8.3.2Initiation (179)5.8.3.3MRB establishment (179)5.8.3.4MRB release (179)5.8.4MBMS Counting Procedure (179)5.8.4.1General (179)5.8.4.2Initiation (180)5.8.4.3Reception of the MBMSCountingRequest message by the UE (180)5.8.5MBMS interest indication (181)5.8.5.1General (181)5.8.5.2Initiation (181)5.8.5.3Determine MBMS frequencies of interest (182)5.8.5.4Actions related to transmission of MBMSInterestIndication message (183)5.8a SC-PTM (183)5.8a.1Introduction (183)5.8a.1.1General (183)5.8a.1.2SC-MCCH scheduling (183)5.8a.1.3SC-MCCH information validity and notification of changes (183)5.8a.1.4Procedures (184)5.8a.2SC-MCCH information acquisition (184)5.8a.2.1General (184)5.8a.2.2Initiation (184)5.8a.2.3SC-MCCH information acquisition by the UE (184)5.8a.2.4Actions upon reception of the SCPTMConfiguration message (185)5.8a.3SC-PTM radio bearer configuration (185)5.8a.3.1General (185)5.8a.3.2Initiation (185)5.8a.3.3SC-MRB establishment (185)5.8a.3.4SC-MRB release (185)5.9RN procedures (186)5.9.1RN reconfiguration (186)5.9.1.1General (186)5.9.1.2Initiation (186)5.9.1.3Reception of the RNReconfiguration by the RN (186)5.10Sidelink (186)5.10.1Introduction (186)5.10.1a Conditions for sidelink communication operation (187)5.10.2Sidelink UE information (188)5.10.2.1General (188)5.10.2.2Initiation (189)5.10.2.3Actions related to transmission of SidelinkUEInformation message (193)5.10.3Sidelink communication monitoring (195)5.10.6Sidelink discovery announcement (198)5.10.6a Sidelink discovery announcement pool selection (201)5.10.6b Sidelink discovery announcement reference carrier selection (201)5.10.7Sidelink synchronisation information transmission (202)5.10.7.1General (202)5.10.7.2Initiation (203)5.10.7.3Transmission of SLSS (204)5.10.7.4Transmission of MasterInformationBlock-SL message (205)5.10.7.5Void (206)5.10.8Sidelink synchronisation reference (206)5.10.8.1General (206)5.10.8.2Selection and reselection of synchronisation reference UE (SyncRef UE) (206)5.10.9Sidelink common control information (207)5.10.9.1General (207)5.10.9.2Actions related to reception of MasterInformationBlock-SL message (207)5.10.10Sidelink relay UE operation (207)5.10.10.1General (207)5.10.10.2AS-conditions for relay related sidelink communication transmission by sidelink relay UE (207)5.10.10.3AS-conditions for relay PS related sidelink discovery transmission by sidelink relay UE (208)5.10.10.4Sidelink relay UE threshold conditions (208)5.10.11Sidelink remote UE operation (208)5.10.11.1General (208)5.10.11.2AS-conditions for relay related sidelink communication transmission by sidelink remote UE (208)5.10.11.3AS-conditions for relay PS related sidelink discovery transmission by sidelink remote UE (209)5.10.11.4Selection and reselection of sidelink relay UE (209)5.10.11.5Sidelink remote UE threshold conditions (210)6Protocol data units, formats and parameters (tabular & ASN.1) (210)6.1General (210)6.2RRC messages (212)6.2.1General message structure (212)–EUTRA-RRC-Definitions (212)–BCCH-BCH-Message (212)–BCCH-DL-SCH-Message (212)–BCCH-DL-SCH-Message-BR (213)–MCCH-Message (213)–PCCH-Message (213)–DL-CCCH-Message (214)–DL-DCCH-Message (214)–UL-CCCH-Message (214)–UL-DCCH-Message (215)–SC-MCCH-Message (215)6.2.2Message definitions (216)–CounterCheck (216)–CounterCheckResponse (217)–CSFBParametersRequestCDMA2000 (217)–CSFBParametersResponseCDMA2000 (218)–DLInformationTransfer (218)–HandoverFromEUTRAPreparationRequest (CDMA2000) (219)–InDeviceCoexIndication (220)–InterFreqRSTDMeasurementIndication (222)–LoggedMeasurementConfiguration (223)–MasterInformationBlock (225)–MBMSCountingRequest (226)–MBMSCountingResponse (226)–MBMSInterestIndication (227)–MBSFNAreaConfiguration (228)–MeasurementReport (228)–MobilityFromEUTRACommand (229)–Paging (232)–ProximityIndication (233)–RNReconfiguration (234)–RNReconfigurationComplete (234)–RRCConnectionReconfiguration (235)–RRCConnectionReconfigurationComplete (240)–RRCConnectionReestablishment (241)–RRCConnectionReestablishmentComplete (241)–RRCConnectionReestablishmentReject (242)–RRCConnectionReestablishmentRequest (243)–RRCConnectionReject (243)–RRCConnectionRelease (244)–RRCConnectionResume (248)–RRCConnectionResumeComplete (249)–RRCConnectionResumeRequest (250)–RRCConnectionRequest (250)–RRCConnectionSetup (251)–RRCConnectionSetupComplete (252)–SCGFailureInformation (253)–SCPTMConfiguration (254)–SecurityModeCommand (255)–SecurityModeComplete (255)–SecurityModeFailure (256)–SidelinkUEInformation (256)–SystemInformation (258)–SystemInformationBlockType1 (259)–UEAssistanceInformation (264)–UECapabilityEnquiry (265)–UECapabilityInformation (266)–UEInformationRequest (267)–UEInformationResponse (267)–ULHandoverPreparationTransfer (CDMA2000) (273)–ULInformationTransfer (274)–WLANConnectionStatusReport (274)6.3RRC information elements (275)6.3.1System information blocks (275)–SystemInformationBlockType2 (275)–SystemInformationBlockType3 (279)–SystemInformationBlockType4 (282)–SystemInformationBlockType5 (283)–SystemInformationBlockType6 (287)–SystemInformationBlockType7 (289)–SystemInformationBlockType8 (290)–SystemInformationBlockType9 (295)–SystemInformationBlockType10 (295)–SystemInformationBlockType11 (296)–SystemInformationBlockType12 (297)–SystemInformationBlockType13 (297)–SystemInformationBlockType14 (298)–SystemInformationBlockType15 (298)–SystemInformationBlockType16 (299)–SystemInformationBlockType17 (300)–SystemInformationBlockType18 (301)–SystemInformationBlockType19 (301)–SystemInformationBlockType20 (304)6.3.2Radio resource control information elements (304)–AntennaInfo (304)–AntennaInfoUL (306)–CQI-ReportConfig (307)–CQI-ReportPeriodicProcExtId (314)–CrossCarrierSchedulingConfig (314)–CSI-IM-Config (315)–CSI-IM-ConfigId (315)–CSI-RS-Config (317)–CSI-RS-ConfigEMIMO (318)–CSI-RS-ConfigNZP (319)–CSI-RS-ConfigNZPId (320)–CSI-RS-ConfigZP (321)–CSI-RS-ConfigZPId (321)–DMRS-Config (321)–DRB-Identity (322)–EPDCCH-Config (322)–EIMTA-MainConfig (324)–LogicalChannelConfig (325)–LWA-Configuration (326)–LWIP-Configuration (326)–RCLWI-Configuration (327)–MAC-MainConfig (327)–P-C-AndCBSR (332)–PDCCH-ConfigSCell (333)–PDCP-Config (334)–PDSCH-Config (337)–PDSCH-RE-MappingQCL-ConfigId (339)–PHICH-Config (339)–PhysicalConfigDedicated (339)–P-Max (344)–PRACH-Config (344)–PresenceAntennaPort1 (346)–PUCCH-Config (347)–PUSCH-Config (351)–RACH-ConfigCommon (355)–RACH-ConfigDedicated (357)–RadioResourceConfigCommon (358)–RadioResourceConfigDedicated (362)–RLC-Config (367)–RLF-TimersAndConstants (369)–RN-SubframeConfig (370)–SchedulingRequestConfig (371)–SoundingRS-UL-Config (372)–SPS-Config (375)–TDD-Config (376)–TimeAlignmentTimer (377)–TPC-PDCCH-Config (377)–TunnelConfigLWIP (378)–UplinkPowerControl (379)–WLAN-Id-List (382)–WLAN-MobilityConfig (382)6.3.3Security control information elements (382)–NextHopChainingCount (382)–SecurityAlgorithmConfig (383)–ShortMAC-I (383)6.3.4Mobility control information elements (383)–AdditionalSpectrumEmission (383)–ARFCN-ValueCDMA2000 (383)–ARFCN-ValueEUTRA (384)–ARFCN-ValueGERAN (384)–ARFCN-ValueUTRA (384)–BandclassCDMA2000 (384)–BandIndicatorGERAN (385)–CarrierFreqCDMA2000 (385)–CarrierFreqGERAN (385)–CellIndexList (387)–CellReselectionPriority (387)–CellSelectionInfoCE (387)–CellReselectionSubPriority (388)–CSFB-RegistrationParam1XRTT (388)–CellGlobalIdEUTRA (389)–CellGlobalIdUTRA (389)–CellGlobalIdGERAN (390)–CellGlobalIdCDMA2000 (390)–CellSelectionInfoNFreq (391)–CSG-Identity (391)–FreqBandIndicator (391)–MobilityControlInfo (391)–MobilityParametersCDMA2000 (1xRTT) (393)–MobilityStateParameters (394)–MultiBandInfoList (394)–NS-PmaxList (394)–PhysCellId (395)–PhysCellIdRange (395)–PhysCellIdRangeUTRA-FDDList (395)–PhysCellIdCDMA2000 (396)–PhysCellIdGERAN (396)–PhysCellIdUTRA-FDD (396)–PhysCellIdUTRA-TDD (396)–PLMN-Identity (397)–PLMN-IdentityList3 (397)–PreRegistrationInfoHRPD (397)–Q-QualMin (398)–Q-RxLevMin (398)–Q-OffsetRange (398)–Q-OffsetRangeInterRAT (399)–ReselectionThreshold (399)–ReselectionThresholdQ (399)–SCellIndex (399)–ServCellIndex (400)–SpeedStateScaleFactors (400)–SystemInfoListGERAN (400)–SystemTimeInfoCDMA2000 (401)–TrackingAreaCode (401)–T-Reselection (402)–T-ReselectionEUTRA-CE (402)6.3.5Measurement information elements (402)–AllowedMeasBandwidth (402)–CSI-RSRP-Range (402)–Hysteresis (402)–LocationInfo (403)–MBSFN-RSRQ-Range (403)–MeasConfig (404)–MeasDS-Config (405)–MeasGapConfig (406)–MeasId (407)–MeasIdToAddModList (407)–MeasObjectCDMA2000 (408)–MeasObjectEUTRA (408)–MeasObjectGERAN (412)–MeasObjectId (412)–MeasObjectToAddModList (412)–MeasObjectUTRA (413)–ReportConfigEUTRA (422)–ReportConfigId (425)–ReportConfigInterRAT (425)–ReportConfigToAddModList (428)–ReportInterval (429)–RSRP-Range (429)–RSRQ-Range (430)–RSRQ-Type (430)–RS-SINR-Range (430)–RSSI-Range-r13 (431)–TimeToTrigger (431)–UL-DelayConfig (431)–WLAN-CarrierInfo (431)–WLAN-RSSI-Range (432)–WLAN-Status (432)6.3.6Other information elements (433)–AbsoluteTimeInfo (433)–AreaConfiguration (433)–C-RNTI (433)–DedicatedInfoCDMA2000 (434)–DedicatedInfoNAS (434)–FilterCoefficient (434)–LoggingDuration (434)–LoggingInterval (435)–MeasSubframePattern (435)–MMEC (435)–NeighCellConfig (435)–OtherConfig (436)–RAND-CDMA2000 (1xRTT) (437)–RAT-Type (437)–ResumeIdentity (437)–RRC-TransactionIdentifier (438)–S-TMSI (438)–TraceReference (438)–UE-CapabilityRAT-ContainerList (438)–UE-EUTRA-Capability (439)–UE-RadioPagingInfo (469)–UE-TimersAndConstants (469)–VisitedCellInfoList (470)–WLAN-OffloadConfig (470)6.3.7MBMS information elements (472)–MBMS-NotificationConfig (472)–MBMS-ServiceList (473)–MBSFN-AreaId (473)–MBSFN-AreaInfoList (473)–MBSFN-SubframeConfig (474)–PMCH-InfoList (475)6.3.7a SC-PTM information elements (476)–SC-MTCH-InfoList (476)–SCPTM-NeighbourCellList (478)6.3.8Sidelink information elements (478)–SL-CommConfig (478)–SL-CommResourcePool (479)–SL-CP-Len (480)–SL-DiscConfig (481)–SL-DiscResourcePool (483)–SL-DiscTxPowerInfo (485)–SL-GapConfig (485)。
战争的讨价还价理论_探索战争的理性主义解释

詹姆斯 ·费伦 (James Fearon)在 1995年发表的 《战争的理性主义解释 》⑤一文中提出了这样一个理 论问题 :由于战争是高成本的 ,原则上事先 ( ex ant) 一直存在着一个可供达成协议的讨价还价范围 ,这 种协议不仅能够反映战后的结果 ,而且还能避免战 争的成本 。从成本 - 收益权衡的角度看 ,战争双方 在战前通过讨价还价达成一个反映战后结果的协议 要优于战争方案 ,按费伦的话说 ,战争一直是事后无 效的 ( ex post inefficient) 。因此 , 这 里的 理论困 惑 是 :为什么理性的国家不能在战前通过讨价还价来 达成一个优于战争的和平方案 ? 对此 ,费伦提出了 三条理性主义解释 , 即信息不对称 ( information a2
与经济学相同 ,国际政治学也可以被视为稀缺 资源如何在国家之间分配的科学 。在国际体系中 , 国家行为的出发点是维护本国的利益 ,但是由于资 源的稀缺性 ,国家之间的利益经常是冲突的 ,任何国 家都无法在国际政治的真空中去追求无限的国家利 益 ,这里必然存在一个协调 、谈判 、妥协的过程 。国 家间关系无外乎合作和冲突 (包括战争 )两种形式 , 这两种形式都可被视为讨价还价问题 :前者意味着 国家之间的讨价还价取得成功 ,后者意味着国家之 间的讨价还价以失败而告终 。
把国家间合作视为讨价还价过程 ,这一点并不 难理解 ,在国际合作的背景下 ,国家之间存在某种共 同利益的竞争 ,从而呈现非零和博弈状态 。但是 ,把
— 14 —
战争视为讨价还价问题 ,则似乎有违常识 。按照惯 常的理解 ,国家之间发生战争是因为两国的竞争是 零和博弈 ,一方的所得必是另一方的所失 ,因此 ,不 存在讨价还价的空间 ( bargaining space) ,只能在战 场上一决雌雄 。这种观点的缺陷在于它没有认识 到 ,战争的高成本和高风险使得冲突双方在避免战 争上有着共同的利益 ,双方并非是零和关系 。事实 上 ,在国际政治中 ,国家间关系几乎不存在绝对的零 和博弈 。既然是非零和博弈 ,原则上必然存在讨价 还价的可能性 。战争之所以发生 ,不是因为没有讨 价还价的空间 ,而是由于国家之间存在种种阻碍谈 判的因素而无法达成和平协议 。把战争视为讨价还 价问题的讨价还价理论 ,其理论主旨正是解释哪些 因素阻碍了国家之间达成一种优于战争方案的和平 方案 。
[翻译]红队战术:结合直接系统调用和sRDI来绕过AVEDR
![[翻译]红队战术:结合直接系统调用和sRDI来绕过AVEDR](https://img.taocdn.com/s3/m/31b80febfbb069dc5022aaea998fcc22bcd143b6.png)
[翻译]红队战术:结合直接系统调⽤和sRDI来绕过AVEDR0x00 简介在本⽂我们将介绍如何使⽤直接系统调⽤(Direct System Calls)以及配合sRDI注⼊来绕过R3层的⾏为监控。
随着安全技术的防御能⼒逐渐增强,另⼀⽅⾯,攻击技术也在不断发展,作为⼀个Red Team需要研究更先进的技术来绕过当下⽐较流⾏的防御和检测机制。
近期⼀篇恶意代码的研究报告声称,使⽤"直接系统调⽤"技术来绕过安全软件⽤户层Hook的恶意样本正在与⽇俱增。
作为⼀名ReadTeamer,要与时俱进!!现在轮到我们也来更新⼀波shellcode攻击代码了。
我们将接下来将使⽤这种技术证明,在不触碰磁盘的情况下绕过AV/EDR监控的⽤户层Hook,使⽤Cobalt Strike来dump LSASS.exe进程内存。
0x01 什么是直接系统调⽤?为了弄清楚直接系统调⽤的真正含义,⾸先我们需要先深⼊Windows操作系统底层架构。
如果你使⽤过MS-DOS年代Windows系统,也许你会记得,⼀个简单的程序崩溃可以引起整个操作系统瘫痪。
这是因为操作系统在实模式(Real Mode)运⾏,处理器在实模式下运⾏时,不会有内存隔离的概念(没有严格限制或者声明,哪些内存区域是可以访问,哪些不能访问)。
也就意味者,如果你写的程序出现了bug导致内存破坏(Memory Currption)会导致整个操作系统停⽌运⾏。
⼀直到后来出现了可以⽀持保护模式的新处理器和操作系统,这⼀现象才被改变。
为了防⽌⼀个进程崩溃导致操作系统也跟着崩溃,在保护模式下引⼊了许多安全措施,通过虚拟内存(Virtual Memory)和权限级别(Privilege Levels),和⼀个叫Rings的概念,来隔离运⾏的不同进程之间,以及进程和操作系统之间的内存访问。
Rings⼀共有4层,Ring0 ~ Ring3分别对应4个特权级别。
Windows操作系统中实际只使⽤了两个特权级别:⼀个是Ring3层,平时我们所见到的应⽤程序运⾏在这⼀层,所以叫它⽤户层,也叫User-Mode。
加速器驱动的陶瓷快堆的中子物理进展

2017·201·state within10s respectively.It can be seen that the variation law and range of simulation results are in good agreement with the experimental results,which show that the IQS/MC program is reliable in simulating dynamic behavior of source jerk of sub-critical zero power reactor.Fig.1(color online)The comparison of simulation results and experiment results of three schemes in the process of source jerk.Reactivity insertion processFigure2shows the comparison curves between the experimental value and the simulated value of the relative change behavior of neutronflux at the detector channel during the process of the single safety rod falling and double safety rod falling at different subcritical levels,and the neutronflux under stable state is seen as the reference value of relative neutronflux.In thisfigure,the sawtooth curve is the experimental data recorded at the detector channel, and the smooth curve is the simulated data calculated by IQS/MC program.As can be seen from the Fig.2,the power is rapidly reduced when safety rod is falling and then the power is slowly attenuated to a stable level under the action of delayed neutrons.At the same time,the deeper the subcritical degree is,the lower the attenuation amplitude of relative count is.We can alsofind that the simulated data is consistent with the experimental data on the changing trends.Fig.2(color online)The comparison of IQS/MC simulation and experiment under SC1to SC3layout schemes in the process of single safety rod falling process(left)and double safety rods falling process(right).5-20Progress of Neutron Simulation in Accelerator-drivenCeramic Fast ReactorYan Xuesong,Zhang Xunchao,Zhang Yaling and Yang LeiIn an attempt to allow nuclear power to reach high resource utilization,sufficient nuclear safety,nuclear prolifera-tion resistance and lowerfinancial risk,the concept of accelerator-driven ceramic fast reactor(ADCFR)is proposed. The ADCFR could converted loaded nuclear fertile material tofissile fuel and burns it over a40-year core life without fuel shuffling or supplementation.Figure.1(a)is schematic of accelerator-driven ceramic fast reactor.AD-CFR consists of a high-power superconducting linear accelerator[1],a spallation target[2]and an ceramic-coolant·202·2017fast reactor.This system is constructed based on the accelerator-driven system (ADS)[3]and belongs the burner system in Accelerator-Driven Advanced Nuclear Energy System (ADANES)[4,5].Fig.1(color online)(a)Schematic of accelerator-driven ceramic fast reactor.(b)Schematic radial cross-section of the ADCFR.Figure 1(b)shows a schematic cross-section of the reactor core.The red component of the reactor is a spallation target.There are 7layers of fuels wrapped outside the spallation target,expressed in 6different colors(except for red and dark blue).The dark blue outside the fuel is the reflection component and the shieldingcomponent.Fig.2(color online)Time-dependent distribution of theideal K efffor ZrO 2and Al 2O 3ceramic materials.To study the operation time of the core and the perfor-mance of the nuclear fuel breeding,we have chosen thecomplete ceramic reactor to carry out the simulation.The reactor core consists of ZrO 2and Al 2O 3ceramic ma-terials,which include the coolant,nuclear fuels,struc-tural materials,reflective materials,and absorption-control materials.Figure.2shows the ideal effectivemultiplication factor (K eff)as a function of full-poweroperation-time (∼35a).Initially,the CFR can operateunder sub-critical conditions due to the external neu-tron source.K effis initially set to 0.98.Nearly 5alater,K effreaches around ∼1.0,which means it can be-gin to operate under a critical mode because of excessreactivity,without the need to be sustained by an ex-ternal neutron-source.After 15a,K effwould reach its maximum,and then it gradually decreased over morethan 20a.The total operation time is over 30a.The CFR has increased inherent safety,excellent breeding performance,efficient power generation.If CFR would be combined with simple high dry reprocessing,a fully closed nuclear-energy system might become feasible.It is belong to ADANES,which would be an ideal clean nuclear fission energy system.References[1]H.A.Abderrahim,J.Galambos,Y.Gohar,et al.,DOE white paper on ADS,(2010).[2]G.S.Bauer,J Nucl.Mat.,398(2010)19.[3]C.Rubbia,J.Aleixandre,S.Andriamonje,ENEA Report,(2001).[4]L.Yang,W.L.Zhan,Sci.China Technol.Sci.,(2017);in press.[5]X.S.Yan,L.Yang,X.C.Zhang,Energies,10(2017)944.。
International-Human-Resource-Management国际人力资源管理 (1

Corporations
• HRM typically refers to those activities undertaken by an organisation to utilize human resources effectively,
Boxhall and Purcell give a broader definition as ‘human resources management includes the firm’s work system and its employment practices. It embraces both individual and collective aspects of people management’
• HR planning • Staffing (recruitment, selection, placement) • Performance management • Training and development • Compensation (remuneration) and benefits • Industrial relations
International Organisational structure
Chief executive/Headquarters
Production
Marketing
Finance
Personnel
International division
International geographic structure
What changes when HRM goes international?
电力系统潮流计算软件设计外文原文及中文翻译

电力系统潮流计算软件设计外文原文及中文翻译外文原文及中文翻译Modelling and Analysis of Electric Power SystemsPower Flow Analysis Fault AnalysisPower Systems Dynamics and StabilityPrefaceIn the lectures three main topics are covered,i.e.Power flow an analysisFault current calculationsPower systems dynamics and stabilityIn Part I of these notes the two first items are covered,while Part II givesAn introduction to dynamics and stability in power systems. In appendices brief overviews of phase-shifting transformers and power system protections are given.The notes start with a derivation and discussion of the models of the most common power system components to be used in the power flow analysis.A derivation of the power ?ow equations based on physical considerations is then given.The resulting non-linear equations are for realistic power systems of very large dimension and they have to be solved numerically.The most commonly used techniques for solving these equations are reviewed.The role of power flow analysis in power system planning,operation,and analysis is discussed.The next topic covered in these lecture notes is fault current calculations in power systems.A systematic approach to calculate fault currents in meshed,large power systems will be derived.The needed models will be given and the assumptions made when formulating these models discussed.It will be demonstrated thatalgebraic models can be used to calculate the dimensioning fault currents in a power system,and the mathematical analysis has similarities with the power ?ow analysis,soitis natural to put these two items in Part I of the notes.In Part II the dynamic behaviour of the power system during and after disturbances(faults) will be studied.The concept of power system stability isde?ned,and different types of pow er system in stabilities are discussed.While the phenomena in Part I could be studied by algebraic equations,the description of the power system dynamics requires models based on differential equations.These lecture notes provide only a basic introduction to the topics above.To facilitate for readers who want to get a deeper knowledge of and insight into these problems,bibliographies are given in the text.Part IStatic Analysis1 IntroductionThis chapter gives a motivation why an algebraic model can be used to de scribe the power system in steady state.It is also motivated why an algebraic approach can be used to calculate fault currents in a power system.A power system is predominantly in steady state operation or in a state that could with sufficient accuracy be regarded as steady state.In a power system there are always small load changes,switching actions,and other transients occurring so that in a strict mathematical sense most of the variables are varying with thetime.However,these variations are most of the time so small that an algebraic,i.e.not time varying model of the power systemis justified.A short circuit in a power system is clearly not a steady state condition.Such an event can start a variety of different dynamic phenomena in the system,and to study these dynamic models are needed.However,when it comes to calculate the fault current sin the system,steady state(static) model swith appropriate parameter values can be used.A fault current consists of two components,a transient part,and a steady state part,but since the transient part can be estimated from the steady state one,fault current analysis is commonly restricted to the calculation of the steady state fault currents.1.1 Power Flow AnalysisIt is of utmost importance to be able to calculate the voltages and currents that different parts of the power system are exposed to.This is essential not only in order to design the different power system components such asgenerators,lines,transformers,shunt elements,etc.so that these can withstand the stresses they are exposed to during steady state operation without any risk of damages.Furthermore,for an economical operation of the system the losses should be kept at a low value taking various constraint into account,and the risk that the system enters into unstable modes of operation must be supervised.In order to do this in a satisfactory way the state of the system,i.e.all(complex) voltages of all nodes in the system,must be known.With these known,all currents,and hence all active and reactive power flows can be calculated,and other relevant quantities can be calculated in the system.Generally the power ?ow,or load ?ow,problem is formulated as a nonlinear set of equationsf (x, u, p)=0(1.1)wheref is an n-dimensional(non-linear)functionx is an n-dimensional vector containing the state variables,or states,ascomponents.These are the unknown voltage magnitudes and voltage angles of nodes in the systemu is a vector with(known) control outputs,e.g.voltages at generators with voltage controlp is a vector with the parameters of the network components,e.g.line reactances and resistancesThe power flow problem consists in formulating the equations f in eq.(1.1) and then solving these with respect to x.This will be the subject dealt with in the first part of these lectures.A necessary condition for eq.(1.1) to have a physically meaningful solution is that f and x have the same dimension,i.e.that we have the same number of unknowns as equations.But in the general case there is no unique solution,and there are also cases when no solution exists.If the states x are known,all other system quantities of interest can be calculated from these and the known quantities,i.e. u and p.System quantities of interest are active and reactive power flows through lines and transformers,reactive power generation from synchronous machines,active and reactive power consumption by voltage dependent loads, etc.As mentioned above,the functions f are non-linear,which makes the equations harder to solve.For the solution of the equations,the linearizationy X Xf ?= (1.2)is quite often used and solved.These equations give also very useful information about the system.The Jacobian matrix Xf ?? whose elements are given by j iij X f X f ??=??)((1.3)can be used form any useful computations,and it is an important indicator of the system conditions.This will also be elaborate on.1.2 Fault Current AnalysisIn the lectures Elektrische Energiesysteme it was studied how to calculate fault currents,e.g.short circuit currents,for simple systems.This analysis will now be extended to deal with realistic systems including several generators,lines,loads,and other system components.Generators(synchronous machines) are important system components when calculating fault currents and their model will be elaborated on and discussed.1.3 LiteratureThe material presented in these lectures constitutes only an introduction to thesubject.Further studies can be recommended in the following text books:1. Power Systems Analysis,second edition,by Artur R.Bergen and VijayVittal.(Prentice Hall Inc.,2000,ISBN0-13-691990-1,619pages)2. Computational Methods for Large Sparse Power Systems,An object oriented approach,by S.A.Soma,S.A.Khaparde,Shubba Pandit(Kluwer Academic Publishers, 2002, ISBN0-7923-7591-2, 333pages)2 Net work ModelsIn this chapter models of the most common net work elements suitable for power flow analysis are derived.These models will be used in the subsequent chapters when formulating the power flow problem.All analysis in the engineering sciences starts with the formulation of appropriate models.A model,and in power system analysis we almost invariably then mean a mathematical model,is a set of equations or relations,which appropriately describes the interactions between different quantities in the time frame studied and with the desired accuracy of a physical or engineered component or system.Hence,depending on the purpose of the analysis different models of the same physical system or components might be valid.It is recalled that the general model of a transmission line was given by the telegraph equation,which is a partial differential equation, and by assuming stationary sinusoidal conditions the long line equations, ordinary differential equations,were obtained.By solving these equations and restricting the interest to the conditions at the ends of the lines,the lumped-circuit line models (π-models) were obtained,which is an algebraic model.This gives us three different models each valid for different purposes.In principle,the complete telegraph equations could be used when studying the steady state conditions at the network nodes.The solution would then include the initial switching transients along the lines,and the steady state solution would then be the solution after the transients have decayed. However, such a solution would contain a lot more information than wanted and,furthermore,it would require a lot of computational effort.An algebraic formulation with the lumped-circuit line model would give the same result with a much simpler model ata lower computational cost.In the above example it is quite obvious which model is the appropriate one,but in many engineering studies these lection of the“correct”model is often the most difficult part of the study.It is good engineering practice to use as simple models as possible, but of course not too simple.If too complicated models are used, the analysis and computations would be unnecessarily cumbersome.Furthermore,generally more complicated models need more parameters for their definition,and to get reliable values of these requires often extensive work.i i+diu+du C ’dx G ’dxR ’dx L ’dx u dxFigure2.1. Equivalent circuit of a line element of length dx In the subsequent sections algebraic models of the most common power system components suitable for power flow calculations will be derived.If not explicitly stated,symmetrical three-phase conditions are assumed in the following.2.1 Lines and CablesThe equ ivalent π-model of a transmission line section was derived in the lectures Elektrische Energie System, 35-505.The general distributed model is characterized by the series parametersR′=series resistance/km per phase(?/km)X′=series reactance/km per phase(?/km)and the shunt parametersB′=shunt susceptance/km per phase(siemens/km)G′=shunt conductance/km per phase(siemens/km )As depicted in Figure2.1.The parameters above are specific for the line or cable configuration and are dependent onconductors and geometrical arrangements.From the circuit in Figure2.1the telegraph equation is derived,and from this the lumped-circuit line model for symmetrical steady state conditions,Figure2.2.This model is frequently referred to as the π-model,and it is characterized by the parameters)(Ω=+=impedance series jX R km km km Z )(siemens admittance shuntjB G Y sh km sh km sh km =+= I mk Z km y sh km y sh mkI kmkmFigure2.2. Lumped-circuit model(π-model)of a transmission line betweennodes k and m.Note. In the following most analysis will be made in the p.u.system.Forimpedances and admittances,capital letters indicate that the quantity is expressed in ohms or siemens,and lower case letters that they are expressed in p.u.Note.In these lecture notes complex quantities are not explicitly marked asunder lined.This means that instead of writing km Z we will write km Z when this quantity is complex. However,it should be clear from the context if a quantity is real or complex.Furthermore,we will not always use specific type settings for vectors.Quite often vectors will be denoted by bold face type setting,but not always.It should also be clear from the context if a quantity is a vector or a scalar.When formulating the net work equations the nodeadmittance matrix will be used and the series admittance of the line model is neededkm km 1-km km jb g z y +== (2.1)With22km r g km km kmx r +=(2.2)and 22km x -b km km kmx r += (2.3)For actual transmission lines the series reactance km x and the series resistance km r are both positive,and consequently km g is positive and km b is negative.The shunt susceptance sh y km and the shunt conductance sh g km are both positive for real line sections.In many cases the value of sh g km is so small that it could be neglected.The complex currents km I and mk I in Figure2.2 can be expressed as functions of the complex voltages at the branch terminal nodes k and m:k sh km m k km km E y E E y I +-=)( (2.4)m k m mk )(E y E E y I sh km km +-=(2.5)Where the complex voltages arek j k k e θU E = (2.6)k j k k e θU E =(2.7) This can also be written in matrix form as))(()(m k sh km km km km sh km km mk km E E y y y -y -y y I I ++=(2.8) As seen the matrix on the right hand side of eq.(2.8)is symmetric and thediagonal elements are equal.This reflects that the lines andcables are symmetrical elements.2.2 TransformersWe will start with a simplified model of a transformer where we neglect the magnetizing current and the no-load losses .In this case the transformer can be modelled by an ideal transformer with turns ratio km t in series with a series impedance km z which represents resistive(load-dependent)losses and the leakage reactance,see Figure2.3.Depending on if km t is real ornon-real(complex)the transformer is in-phase or phase-shifting.p k mU m ej θm I km I mkU kej θk U p e j θp Z km 1:t km p k mU m ej θm I km I mkU kej θk U p e j θp Z km t km :1Figure2.3. Transformer model with complex ratio kmj km km e a t ?=(km -j 1-km km e a t ?=) mp k U m ej θm I km I mk U kej θk U p e j θp Z km a km :1Figure2.4. In-phase transformer model 2.2.1In-Phase TransformersFigure2.4shows an in-phase transformer model indicating the voltage at the internal –non-physical –node p.In this model the ideal voltage magnitude ratio(turns ratio)iskm k p(2.9) Since θk = θp ,this is also the ratio between the complex voltages at nodes k and p, km j k j p k pa e U e U E E k p ==θθ(2.10)There are no power losses(neither active nor reactive)in the idealtransformer(the k-p part of the model),which yields0I E I E *mk p *km k =+(2.11) Then applying eqs.(2.9)and(2.10)giveskm mk km mk km -a I I -I I ==(2.12)A B Ck m I mk I kmFigure2.5. Equivalent π-model for in-phase transformerwhich means that the complex currents km I and mk I are out of phase by 180since km a ∈ R.Figure2.5 represents the equivalent π-model for thein-phase transformer in Figure2.4.Parameters A, B,and C of this model can be obtained by identifying the coefficients of the expressions for the complex currents km I and mk I associated with the models of Figures2.4 and 2.5.Figure2.4 givesm km km k km 2km p m km km km E y a E y a E -E y -a I )()()(+==(2.13)m km k km km p m km mk E y E y a -E -E y I )()()(+== (2.14)or in matrix form ))(()(m k km km km km km km2km mk km E E y y a -y a -y a I I =As seen the matrix on the right hand side of eq.(2.15) is symmetric,but thediagonal elements are not equal when 1a 2km ≠.Figure2.5 provides now the following:m k km E A -E A -I )()(+=(2.16)m k mk E C A E A -I )()(++=(2.17)or in matrix form))(()(m k mk km E E C A A -A -B A I I ++= (2.18)Identifying the matrix elements from the matrices in eqs.(2.15) and (2.18) yieldskm km y a A = (2.19)km km km y 1-a a B )(= (2.20)km km )y a -(1C =(2.21) 2.2.2 Phase-Shifting TransformersPhase-shifting transformers,such as the one represented in Figure2.6,are used to control active power flows;the control variable is the phase angle and the controlled quantity can be,among other possibilities,the active power flow in the branch where the shifter is placed.In Appendix A the physical design of phase-shifting transformer is described. A phase-shifting transformer affects both the phase and magnitude of the complex voltages k E and p E ,without changing their ratio,i.e., km j km km k p e a t E E ?== (2.22)Thus, km k p ?θθ+=and k km p U a U =,using eqs. (2.11) and (2.22)km j -km *km mkkm e -a -t I I ?==I km m U m ej θm I mk pkU k ej θk Z km 1:a kme j φkmkm k p ?θθ+=k km p U a U = Figure2.6. Phase-shifting transformer with km j km km e a t ?=As with in-phase transformers,the complex currentskm I and mk I can be expressed in terms of complex voltages at the phase-shifting transformer terminals:m km *km k km 2km p m km *km km E y t -E y a E -E y -t I )()()(+== (2.24)m km k km km p m km mk E y E y t -E -E y I )()()(+==(2.25)Or in matrix form))(()(m k km km km km *km km 2km mk km E E y y t -y t -y a I I =(2.26) As seen this matrix is not symmetric if km t is non-real,and the diagonal matrixelements are not equal if 1a 2km ≠.There is no way to determine parameters A, B,and Cof the equivalent π-model from these equations,since the coefficient km *km y t - ofEm in eq.(2.24)differs from km km y t -in eq.(2.25),as long as there is non zero phase shift,i.e. km t ?R.A phase-shifting transformer can thus not be represented by a π-model.2.2.3Unified Branch ModelThe expressions for the complex currents km I and mk I for both transformersand shifters derived above depend on the side where the tap is located;i.e., they are not symmetrical.It is how ever possible to develop unified complex expressions which can be used for lines,transformers,and phase-shifters, regardless of the side on which the tap is located(or even in the case when there are taps on both sides of thedevice).Consider initially the model in Figure2.8 in which shunt elements have beentemporarily ignored and km j km km e a t ?= and m k j mk mk e a t ?=。
RBV回顾(资源基础理论的系统梳理)

(一)理论溯源:理论发展(2)
3.Barney, J.B. 1986. “Strategic Factor Markets: Expectations, Luck, and Business Strategy.” Management Science 32:1231-1241. 引入“战略性要素市场”:企业获取或培育其实施产品市场 战略所需资源的场所。“The ability to create imperfectly competitive product markets also depends on the cost of implementing the strategy” 如果战略要素 市场是完全竞争的,那么,在这些市场中对资源的获取 将会反映该资源用于实施产品市场战略时所能够创造的 绩效。如果战略性要素市场总是完全竞争的,企业则不 可能获得经济租。 (对 Porter研究的质疑) 获取经济租之所需资源两种途径:(1) Fortune and luck; (2)More accurate expectations(unusual insights about the future value of the resources) 企业已控资源比其他类型的资源更可能成为经济租来源。
解释企业为何存在,并聚焦于企业获取经济租的能力。探究了企业的寻租和配 租特性。将寻租理论、交易成本理论及随后出现的治理理论联系起来,致 力于发展一种企业的基于资源或基于知识的理论。将企业定义为一串生产 性资源束,且这些资源的价值将会依其应用情境变化而变化。他强调,这 些资源的可模仿性取决于它们被“隔绝机制”所保护的程度。甚至还提出 了一系列的隔绝机制并开始探讨那些能够增强不可模仿性的资源属性。
1.理论基础:特质能力理论(1)
物流2010级管理学双语期末试卷B
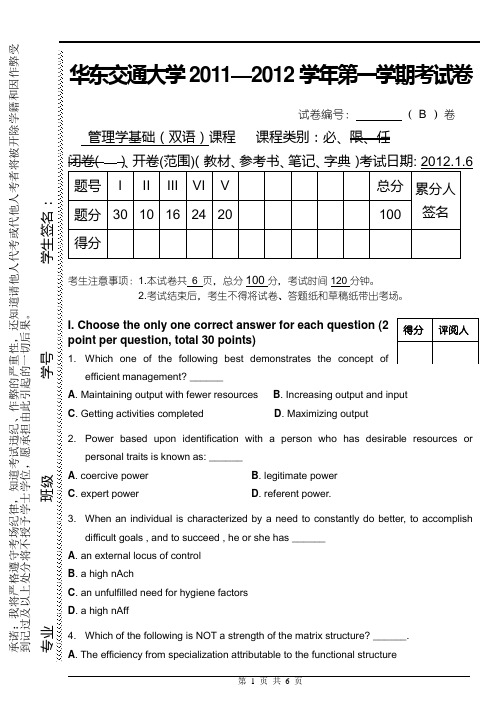
华东交通大学2011—2012学年第一学期考试卷试卷编号: ( B )卷管理学基础(双语)课程 课程类别:必、限、任闭卷( )、考生注意事项:1.本试卷共 6 页,总分100分,考试时间120分钟。
2.考试结束后,考生不得将试卷、答题纸和草稿纸带出考场。
I. Choose the only one correct answer for each question (2 point per question, total 30 points)1. Which one of the following best demonstrates the concept ofefficient management? ______A . Maintaining output with fewer resourcesB . Increasing output and inputC . Getting activities completedD . Maximizing output2. Power based upon identification with a person who has desirable resources orpersonal traits is known as: ______ A . coercive power B. legitimate power C . expert powerD . referent power.3. When an individual is characterized by a need to constantly do better, to accomplishdifficult goals , and to succeed , he or she has ______ A . an external locus of control B . a high nAchC . an unfulfilled need for hygiene factorsD . a high nAff4. Which of the following is NOT a strength of the matrix structure? ______. A . The efficiency from specialization attributable to the functional structure B . The accountability of the divisional structureC. Minimizes ambiguity in reporting relationshipD. Elimination of the duplication of resources and facilities5. If the environment in which the organization functions is relatively stable, whichstructure will be most effective?__________A. strategic organizationB. mechanistic organizationC. organic organizationD. adhocracy6. An organization must contain all except which of the following characteristics______A. purposeB. peopleC. structureD. product7. According to the leadership grid, which leadership style occurs when efficiency inoperations is the dominant orientation?____________A. team managementB. country club managementC. impoverished managementD. task management8. Which of the following statements is INCONSISTENT with the relationship betweenstrategy and structure?__________A. change in structure will result in a change in strategy.B. change in strategy is followed by a change in structure.C. Strategy is a major influence on structure.D. None of the above is inconsistent with the relationship between strategy and structure.9. A large discount store, like Wal-Mart, whose primary goal is to have the lowest pricesin the industry, is using which of the following strategies to maintain a competitive advantage?__________A. cost-leadership strategyB. differentiation strategyC. focus strategyD. retrenchment strategy10. The degree to which an individual believes that working at a particular level willgenerate a desired outcome is defined by the expectancy theory as______A. value or valenceB. attractivenessC. performance-reward linkageD. effort-performance linkage11. If a leader describes his or her least-preferred coworker in relatively unfavorable terms,according to Fielder, ______A. The leader would be classified as relationship-orientedB. The leader would be classified as task-orientedC. The leader would be classified as authoritarianD. None of the above12. In the job characteristics model (JCM), the links between the job dimensions and theoutcomes are moderated or adjusted by the strength of the _____ need.A. securityB. powerC. growthD. affiliation13. According to Maslow, when does a need stop motivating? ______A. When the situation changesB. When it is substantially satisfiedC. When the person returns to a lower-level needD.Never14. Information about opportunities and threats comes from______A. An analysis of the organization’s internal resourcesB. A department by department study of the organizationC. Scanning the external environmentsD. None of the above15. Bounded rationality differs from the rational model in that decision makers:A. act irrationallyB. focus on easy-to-find choicesC. seek advice from employeesD. act outside the boundaries set by their organizations.1._________2.________3.________ 4________ 5.________6._________7.________8.________9.________ 10.________1. The four contemporary functions of management are planning, organizing, leading, and controlling.2.The primary issue that aroused Taylor to create a more scientific approach to management was worker effectiveness3.The 14 principles of management are associated with Fayol.4.In the omnipotent view of management, much of an organizat ion’s success or failure is due to forces outside management’s control.5.Goals are the foundation of organizational planning.6.The most outspoken advocate of the classical view of organizational socialresponsibility is Milton Friedman.7.The BCG matrix evaluates SBUs to identify which SBUs offer high potential and which drain organizational resources.8.People will do better when they get feedback on how well they’re progressing toward their goals.9.Job enlargement increases job depth.10.Managers and leaders are the same.III.名词解释(每题4分,共16分)2. Overall Cost-leadership Strategy3. Related Diversification4. escalation of commitmentIV、简答题(每题8分,共24分)1. 什么是非正式组织,了解非正式组织有何意义?2.矩阵式组织结构有哪些优点和缺点?3. 简述战略管理基本流程的内容。
战争的讨价还价理论_探索战争的理性主义解释

詹姆斯 ·费伦 (James Fearon)在 1995年发表的 《战争的理性主义解释 》⑤一文中提出了这样一个理 论问题 :由于战争是高成本的 ,原则上事先 ( ex ant) 一直存在着一个可供达成协议的讨价还价范围 ,这 种协议不仅能够反映战后的结果 ,而且还能避免战 争的成本 。从成本 - 收益权衡的角度看 ,战争双方 在战前通过讨价还价达成一个反映战后结果的协议 要优于战争方案 ,按费伦的话说 ,战争一直是事后无 效的 ( ex post inefficient) 。因此 , 这 里的 理论困 惑 是 :为什么理性的国家不能在战前通过讨价还价来 达成一个优于战争的和平方案 ? 对此 ,费伦提出了 三条理性主义解释 , 即信息不对称 ( information a2
① [德 ]克劳塞维茨著 ,中国人民解放军军事科学院译 :《战争 论 》,北京 :商务印书馆 , 1997年版 。
2009年第 2期
战争视为讨价还价问题 ,但《战争论 》中的核心思想 却是当代学者建立战争的讨价还价理论时的思想基 础 ,以至于他们均把克劳塞维茨视为战争的讨价还 价理论的鼻祖 。
托马斯 ·谢林 ( Thom as Schelling) 可能是二战 后国际政治学中第一个明确地把战争视为讨价还价 问题的学者 ,他的研究领域横跨国际政治学和经济 学两大领域 ,他本人则为经济学中的讨价还价理论 做出了杰出贡献 。在 1960年出版的《冲突的战略 》 中 ,谢林把冲突视为一个讨价还价的过程 ,他指出冲 突双方利益完全对立的纯粹冲突状态是非常罕见 的 ,纯粹冲突通常只会在大规模毁灭性战争中出现 , 而在一般战争中很少发生 。双方除了冲突的利益之 外还存在某种共同利益 (如避免战争及其高昂成 本 ) ,这种共同利益界定了在冲突中的“取胜 ”之道 , 即胜利只能通过冲突双方的讨价还价 、互谅以及避 免采取互损行为得以实现 。① 20世纪 70年代至 80 年代 ,用讨价还价方式研究战争的成果逐渐增多 。 杰弗里 ·布莱 尼 ( Geoffrey B lainey) 在《战 争的 原 因 》②中以讨价还价理论的视角指出 ,战争发生是因 为冲突双方不能就彼此的实力和开战决心 ( resolve) 达成共识 ,每一方往往都会夸大自身的实力和决心 而低估对方的实力和决心 ,从而在对战争前景盲目 乐观的情况下发动战争 。换言之 ,如果战前双方能 够就实力和决心达成一致的话 ,双方将会选择谈判 方式来解决争端 。这一时期 ,不仅有学者用讨价还 价视角研究战争的发生 ,还有一些学者以讨价还价 的方式研究战争的结束 。在后者看来 ,要研究战争 发生的原因 , 就 必须 解释 战争 结束 的原因 。 1979 年 ,唐纳德 ·威特曼 (Donald W ittman) 建立了一个 关于战争结束的讨价还价模型 ,他把战争的结束视 为战争双方理性估计的过程 ,指出除非双方都认识 到谈判能更好地改进它们的福利 ,否则战争将继续 下去 。③ 保罗 ·皮勒 ( Paul Pillar)同样把战争的结 束视为一种讨价还价的过程 ,通过分析 1800~1980 年间的 142场战争 ,他解释了战场的较量如何影响 战争期间的谈判进程并最终促使双方达成一个用以 结束战争的和平协议 。④
SOC网络安全题目300题

SOC 单项选择题120题多选60题判断90题简答30小题合计300题一.单项选择题(共120小题)1.在网页上点击一个链接是使用哪种方式提交的请求?A.GETB。
POSTC.HEADD.RACE正确答案:A;2。
对于单次SQL注入最可能会用到下列哪组字符?A。
双引号B。
单引号C。
#D.—正确答案:B;3.仅根据扩展名判断,以下哪个文件不是动态页面?A.index.aspxB.test.jspC。
news。
doD。
web.xml正确答案:D;36835 8FE3 迣631839 7C5F 籟22269 56FD 国24417 5F61 彡`33178 819A 膚4.关于XSS的说法以下哪项是正确的?A.XSS全称为Cascading Style SheetB.通过XSS无法修改显示的页面内容C。
通过XSS有可能取得被攻击客户端的CookieD。
XSS是一种利用客户端漏洞实施的攻击正确答案:C;5。
在应用程序中接收到如下内容,请选出对其可信任程度描述正确的一项。
A。
来自设置为不可编辑的输入框的内容可信任B。
来自设置为隐藏域的内容可信任C。
来自客户端提交Cookie的内容可信任D。
来自客户端提交的Agent域的内容可信任E。
以上内容均不可信正确答案:E;6。
HTTP中如提交多个参数通过下列哪个符号进行分隔?A。
;D。
+i22100 5654 噔!X30946 78E2 磢(l22993 59D1 姑正确答案:C;7。
通过以下哪种方法可最为有效地避免在中括号参数处产生SQL注入?select * from users where age<[18]and male=1;A。
过滤输入中的单引号B。
过滤输入中的分号.-—及#;过滤输入中的空格.TAB(\t)C.如输入参数非正整数则认为非法,不再进行SQL查询D。
过滤关键字and、or正确答案:D;8。
端口扫描使用的最常见协议是A.TCPB。
UDPC。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
of the 20 major wars hadsignificant economiccauses, often related toconflict over resources. He emphasized“the rise of industrialism has led to the struggle for ... raw materials.” For example, in the War of the Pacific (1879–1884), Chile fought against a defensive alliance of Bolivia and Peru for the control of guanomineral deposits. The war was precipitated by the rise in the value of the deposits due to their extensive use in agriculture. Chile’s victory increased the size of its treasury by 900%. Westing (1986) argues that many of the wars in the twentieth century had an important resource dimension. As examples he cites the Algerian War of Independence (1954–1962), the Six Day War (1967), and the Chaco War (1932–1935).2 More recently, Saddam Hussein’s invasion of Kuwait in 1990 was a result of the dispute over the Rumaila oil field. In Resource Wars (2001), Klare argues that following the end of the Cold War, control of valuable natural resources has become increasingly important, and these resources will become a primary motivation for wars in the future. The famous Carter Doctrine, which states “Any attempt by any outside force to gain control of the Persian Gulf ... will be repelled by any means necessary, including military force,” is just one facet of this perspective.3 This article develops an economic theory of resource wars and clarifies the conditions under which such wars can be prevented. We consider the dynamicinteractions between a resource-rich and a resource-poor country, which enable us to capture the effect of the increasing scarcity of finite resources. Our approach combines the classic Hotelling (1931) model of exhaustible resources with a dynamic “guns and butter” model of armament and war along the lines of Powell (1993). A key friction in our model is the presence of
Downloaded from / at Shaoxing University on April 19, 2012
I. INTRODUCTION Control over natural resources has been one of the key determinants of wars.1 An early study of causes of modern wars during the 1878 to 1918 period by Bakeless (1921) argued that 14
c The Author(s) 2012. Published by Oxford University Press, on the behalf of President and Fellows of Harvard College. All rights reserved. For Permissions, please email: journals. permissions@. The Quarterly Journal of Economics (2012) 127, 283–331. doi:10.1093/qje/qjr048. Advance Access publication on January 6, 2012.
A DYNAMIC THEORY OF RESOURCE WARS∗ DARON ACEMOGLU MIKHAIL GOLOSOV ALEH TSYVINSKI PIERRE YARED
We develop a dynamic theory of resource wars and study the conditions under which such wars can be prevented. Our focus is on the interaction between the scarcity of resources and the incentives for war in the presence of limited commitment. We show that a key parameter determining the incentives for war is the elasticity of demand. Our first result identifies a novel externality that can precipitate war: price-taking firms fail to internalize the impact of their extraction on military action. In the case of inelastic resource demand, war incentives increase over time andwar may become inevitable. Our secondresult shows that in some situations, regulation of prices and quantities by the resource-rich country can prevent war, and when this is the case, there will also be slower resource extraction than the Hotelling benchmark (with inelastic demand). Our third result is that because of limited commitment and its implications for armament incentives, regulation of prices and quantities might actually precipitate war even in some circumstances where wars would not have arisen under competitive markets. JEL Codes: F10, F51, H56, Q32.
