CH9_Network
American Dreams in China

80AUDIO-VISUALWORLDAmerican Dreams in China《中国合伙人》Zh4nggu5 H9hu6r9nDirectorPeter ChanProducersZhao Haicheng, Tian PujunWritersZhou Zhiyong, Zhang Ji, Lin AihuaI f Aaron Sorkin penned Chinesemovies glamorizing the rise and fall ofentrepreneurs in the 90s, then AmericanDreams in China surely would have beenthe jewel in his crown. In just 10 days,Dreams became the largest current-grossingblockbuster in China, generating nearly 51million USD—leading to its surreptitiously-mentioned subtitle: “The Chinese SocialNetwork”. Alas, Sorkin had no role in thecreation of Dreams; instead, Hong Kongcelebrity-director Peter Chan pays just alittle more than a comfortable homage toSorkin’s Zuckerberg biopic. Dreams is looselybased around the back story of the foundersof New Orient Education & TechnologyGroup, an English-language firm that IPO’din the US in 2006. New Orient is re-titledNew Dream, and the three protagonists—Meng Xiaojun, Cheng Dongqing and WangYang—are respectively played by veteranactors Deng Chao, Huang Xiaoming andTong Dawei. Dreams then becomes a storyabout what young Chinese men are willingto do to achieve success and the lechery,hardship, and seduction that comes with it.All three men meet as young, enterprisingcollege students in the 1990s, with the samedreams as their peers: getting to America.Their college-boy antics (forcible fondles,back room hookups, nervous glances atbeautiful girls, etc.) begin to lead theminexorably toward their greater purpose ofa life in America. The format of the movieflits to and from scenes of a private office,where they are being accused of intellectualthievery, to the happy-go-lucky days oftheir youth and the stories that shapedtheir development into the forlorn and wisecharacters who sit at the glass table, a laSorkin.But what’s interesting, or surprising, in thismovie isn’t the smarmy dialogue (Sorkin’spointy one-liners have been converted totruth-y lectures on success and life). It isn’teven the relationships between these threeup-and-coming young Chinese men that81lead them to betray , support, and reject each other. What Dreams does well is dramatize and portray the ethos of China’s youth in the 90s—an invocation of the optimism,knavery , and seduction that surround their struggle to reach America. Times Square gleams like a modern Zion and each protagonist looks longingly to the sky each time the word “America” is mentioned. Back in a college book club led by Meng, he asks his peers to describe their generation using a single word. In the end, he offers his own view:The most important mission of our generation is to change. Change everyone and everything around us. The only constant is our courage at this moment. If we can do it, we will change the whole world.W6men zh- y!—d3i r9n, zu# zh7ngy3o de sh# g2ibi3n. G2ibi3n sh8nbi`n m0i g- r9n, g2ibi3n sh8nbi`n m0i ji3n sh#. W9iy~ b%bi3n de ji&sh# c@—sh! c@k- de y6ngq#. R%gu6 w6men n9ng zu7d3o zh- y# —di2n, w6men ji`ng g2ibi3n sh#ji-.我们这一代人,最重要的是改变。
LaCie 2big Network 说明书

ch9内存管理基础(自己摘抄的笔记)

ch9内存管理基础(⾃⼰摘抄的笔记)静态链接、静态装⼊的缺点是既浪费硬盘空间,也浪费内存空间部分装⼊的依据是程序局部性特性组织合理的存储结构,依据是访问速度匹配关系、容量要求和价格。
(易失性)操作系统对寄存器,Cache没有话语权,(对操作系统是透明的),只能⽤,不能⽀配存储管理⽬的充分利⽤内存尽可能⽅便⽤户使⽤存储保护与安全共享与通信实现的性能和代价解决程序空间⽐实际内存空间⼤的问题存储管理任务存储分配和回收存储共享存储保护存储器扩充存储管理⽅案连续分配⽅式单⼀连续存储管理分区存储管理离散分配⽅式分页存储管理(分配单位是页)段式存储管理(分配单位是段)段页式存储管理虚拟存储器连续分配⽅式基本思想Main memory usually into two partitions:Resident(常驻) operating system, usually held in low memory with interrupt vector.User processes then held in high memory单⼀连续存储管理:基本思想整个内存空间分成系统区和⽤户区,系统区给操作系统使⽤,⽤户区给⽤户使⽤。
适⽤场合最简单,适⽤于单⽤户、单任务的OS优点易于管理缺点对要求内存空间少的程序,造成内存浪费;程序全部装⼊,很少使⽤的程序部分也占⽤内存。
系统特点1.容易记住的状态,不是全部空闲就是全部已分配;2.当作业被调度时就获得全部空间;3.全部主都分配给⼀个作业;4.作业运⾏完后,全部主存空间⼜恢复成空闲(以上所指的全部主存空间是全部⽤户区空间)对于连续区分配⽽⾔,虽然这种管理⽅案不需要专门的硬件,但是应有硬件保护机构,以确保不⾄于偶然或⽆意地⼲扰系统区中的信息,解决的⽅法有两个:1.使⽤界限的⽅法。
界限寄存器中存放的起始地址和终⽌地址,作业运⾏时,检查访问指令或数据的地址,若不在界限寄存器所框住的范围内,则发⽣越界中断。
阅听人研究

閱聽人研究(Audience Research)─A Journey of Fans, Free labor and New Media─2010,Fall授課時地:二16:10~19:00 社科院R225授課教師:簡妙如(mjjian@,研究室301,分機:32563)課程宗旨在新媒介科技匯流的時代,老媒體與新媒體,在地媒體與跨國、虛擬媒體,被動接收與自主生產閱聽人…,重新架接了我們的閱聽人經驗。
閱聽人被今日的媒介網絡再媒介化(remediate),我們又要如何架接過去的閱聽人理論,來解釋一波波方興未艾的媒介閱聽/消費/生產的新經驗?本學期課程由「迷」的理論及研究作為出發,但也銜接新媒體及社群媒體時代對於閱聽人數位素養,閱聽人作為公民,以及「使用者創造內容」(user-generated content)、迷勞動及免費勞動的討論。
除了探訪不同的理論思考角度,也協助同學發展可能的研究問題。
課堂要求1.課堂參與:每週需閱讀指定文獻章節,並於課堂與同學及老師討論。
2.兩次心得回應:課堂分為期中及期末兩階段,每階段同學需選擇當期範圍內的主題文章至少兩篇,撰寫讀書心得。
心得需涵括理論論點的討論,以及自己對於相關研究領域或文化現象的觀察、疑問或心得。
每次約1000~2000字。
3.期末報告—自組workshop「我們的閱聽人田野及研究…」閱聽人研究怎麼做?要做什麼?你是否厭倦了孤獨的苦思與瓶項?請選擇一個閱聽人/迷常會出現的場景,進行田野調查。
它可能是演唱會、網路討論區、動漫迷的cosplay…,請依自己的興趣及可及性,進入田野作觀察及紀錄。
在田野期間,請和班上同學共同討論、發展,並據以組織一個彼此有扣連、有呼應的閱聽人研究議題。
作業分兩階段:i期中報告:田野workshop。
每人根據自己的田野調查,提出初步觀察結果及研究構想,全班並進行panel主題的發想與深化。
田野報告需繳交3000字書面,並進行討論。
凌鸥创芯 LKS32MC08X 电机控制处理器数据手册说明书

南京凌鸥创芯电子有限公司LKS32MC08X Datasheet© 2020, 版权归凌鸥创芯所有机密文件,未经许可不得扩散1概述1.1功能简述LKS32MC08X系列MCU是32位内核的面向电机控制应用的专用处理器,集成了常用电机控制系统所需要的所有模块。
⚫性能➢96MHz 32位Cortex-M0内核➢集成自主指令集电机控制专用DSP➢超低功耗休眠模式,低功耗休眠电流10uA➢工业级工作温度范围➢超强抗静电和群脉冲能力⚫工作范围➢ 2.2V~5.5V电源供电,内部集成1个LDO,为数字部分电路供电➢工作温度: -40~105℃,LKS32MC085工作温度: -40~125℃⚫时钟➢内置4MHz高精度RC时钟,-40~105℃范围内精度在±1%之内➢内置低速32KHz 低速时钟,供低功耗模式使用➢可外挂4MHz外部晶振➢内部PLL可提供最高96MHz时钟⚫外设模块➢两路UART➢一路SPI,支持主从模式➢一路IIC,支持主从模式➢一路CAN(部分型号不带CAN)➢2个通用16位Timer,支持捕捉和边沿对齐PWM功能➢2个通用32位Timer,支持捕捉和边沿对齐PWM功能;支持正交编码输入,CW/CCW输入,脉冲+符号输入➢电机控制专用PWM模块,支持8路PWM输出,独立死区控制➢Hall信号专用接口,支持测速、去抖功能➢硬件看门狗➢最多4组16bit GPIO。
P0.0/P0.1/P1.0/P1.1 4个GPIO可以作为系统的唤醒源。
P0.15 ~ P0.0 共16个GPIO可以用作外部中断源输入。
⚫模拟模块➢集成1路12bit SAR ADC,同步双采样,3Msps采样及转换速率,最多支持13通道➢集成4路运算放大器,可设置为差分PGA模式➢集成两路比较器,可设置滞回模式➢集成12bit DAC 数模转换器➢内置±2℃温度传感器➢内置1.2V 0.5%精度电压基准源➢内置1路低功耗LDO和电源监测电路➢集成高精度、低温飘高频RC时钟➢集成晶体起振电路1.2性能优势➢高可靠性、高集成度、最终产品体积小、节约BOM成本;➢内部集成4路高速运放和两路比较器,可满足单电阻/双电阻/三电阻电流采样拓扑架构的不同需求;➢内部高速运放集成高压保护电路,可以允许高电压共模信号直接输入芯片,可以用最简单的电路拓扑实现MOSFET电阻直接电流采样模式;➢应用专利技术使ADC和高速运放达到最佳配合,可处理更宽的电流动态范围,同时兼顾高速小电流和低速大电流的采样精度;➢整体控制电路简洁高效,抗干扰能力强,稳定可靠;➢单电源2.2V~5.5V供电,确保了系统供电的通用性;适用于有感BLDC/无感BLDC/有感FOC/无感FOC及步进电机、永磁同步、异步电机等控制系统。
千兆光猫用户手册说明书

The CODA-5519is a powerful router that will be used as the heart of your wireless home.It will offer strong Wi-Fi that will covers most houses.The CODA-5519has the capability to receive 5Gbps bi-directional based on 2OFDM +32QAM downstream channels and with 2OFDMA +8upstream channels over its DOCSIS 3.1interface.The integrated Wi-Fi 4x42.4GHz 802.11ax and 4x45GHz 802.11ax dual band MU-MIMO Access Point significantly improves customer experience extending range and coverage with blazing speeds.For wired clients,2.5G plus two Gigabit Ethernet ports offer ultra-fast connection.It can be paired with Hitron extenders/mesh pods for extra coverage.•DOCSIS 3.1 2x2 multi-carrier OFDM •DOCSIS 3.0 32x8 channel bonding•4x4 2.4GHz 802.11ax and 4x4 5GHz 802.11ax dual band concurrent MU-MIMO internal antennas •16 SSIDs (8SSIDs per radio)•Individual configuration for each SSID (security, bridging, routing, firewall and Wi-Fi parameters)•Extensive operator control via configuration file and SNMP•Integrated DLNA Media Server with support for video, audio and image servingDOCSIS 3.1 Wi-Fi 6 and eMTA GatewayIntel® Puma™ 7 OFDM 2x2 w / fixed upstream, 4x4 dual band Wi-Fi w/ concurrent 802.11ax 2.4Ghz + 5GHz, MoCA 2.0 channel bonding and voice HIGH PERFORMANCE INTERNET AND WIRELESS ACCESSThe CODA-5519supports pre-configured and pre-enabled Wi-Fi security via Wi-Fi Protected Setup (WPS),allowing the end-user to rapidly set up a secure wireless network without manual configuration.Hitron's AutoSync software provides secure automated setup of extenders in the customer's home or business.It comes with MyHitron (end user management mobile application).MSO can also get extra management and analytics via HitronCloud/OptiMy CSR interface from the support center.SECURE WIRELESS NETWORKING CONTROLLED AT THE TIP OF YOUR FINGERSKEY FEATURES•IPv6 routing•MoCA 2.0 channel bonding•TR-069 and HNAP for easy setup and remote management•Enhanced management and stability for low total cost of ownership•One 2.5G and Two 1G Ethernet ports •Hitron Ecosystem Support (OptiMy, HitronCloud, MyHitron)•2 HD voice ports with SIP or MGCP supportTVStreamer Smartphone TabletThermostatHome Security LaptopCODA-5519Printer PCMoCA ExtenderPhonesWi-Fi1G Ethernet Analog2.5G Ethernet Coax PodLaptop Gaming ConsoleConnectivity•RF F-Type 75Ωfemale connector•2x RJ-45 Ethernet port 10/100/1000Mbps•1x RJ-45 Ethernet port 10/100/1000/2500Mbps•USB 3.0 type A connector with host interface•2x RJ-11 HD voice ports•EBBU jackManagement•Protocol support: TR-069, TFTP, SSHv2, SNMP v2C, v3•Web-based GUI control, configuration and management •Power-on self diagnostic•Hitron proprietary MIBs for extended support onDOCSIS, router management, Wi-Fi managementand MoCA management•app support•and back end supportReception-Demodulation•DOCSIS 3.1/3.0/2.0•DOCSIS 3.1 demodulation: Multi-carrier OFDM 16 to 4096QAM •DOCSIS 3.1 data rate: Up to 5Gps with 2 OFDM 192MHz downstream channels +32 QAM•DOCSIS 3.0 demodulation: 64QAM, 256QAM•DOCSIS 3.0 data rate: Up to 1.2Gbps with 32 bonded downstream channels•Frequency (edge-to-edge): 108-1218MHz and 258-1218 •Channel Bandwidth: 6MHz•Signal level: -15dBmV to 15dBmVTransmitter-Modulation•DOCSIS 3.1/3.0/2.0•DOCSIS 3.1 modulation: Multi-carrier OFDMA BPSK to 4096QAM •DOCSIS 3.1 data rate: Up to 700Mbps with OFDMA 96MHz upstream channels•DOCSIS 3.0 modulation: QPSK, 8QAM, 16QAM, 32QAM, 64QAM, and 128QAM (SCDMA only)•DOCSIS 3.0 data rate: Up to 320Mbps with 8 bonded upstream channels•Frequency: Fixed 5-85MHz•Upstream transmit signal level: +11 to 65dBmVMoCA 2.0 Reception / Transmitter-Modulation •Demodulation/ Modulation: BPSK, QPSK, 8QAM, 16QAM,32QAM, 64QAM, 128QAM, 256QAM, 512QAM, 1024QAM •PHY data rate: 700Mbps (baseline Mode) / 1400Mbps (bonding channel)•Throughput: 400+Mbps (baseline mode) / 500+Mbps (turbo mode, point to point) / 800Mbps (bonding channel)•Frequency (center frequencies): 1400-1625MHz•Channel bandwidth: 100MHz (baseline mode) / 225MHz (bonding channel)Voice•Protocol support: SIP or MGCP•2x 8kHz each HD voice•Audio codecs: G.711 (a-law and mu-law), G.722 (HD codec), G.723.1, G.726, G.728, and G.729Routing Support•Protocol support: IGMP v3 for IPTV service capability•MAC address filtering (IPv4/IPv6)•IP source/destination address filtering (IPv4/IPv6)•DHCP, TFTP and ToD clients (IPv4/IPv6)•DHCP server supports RFC 1541 (IPv4)•DHCPv6 obtains prefix from DHCPv6 server through prefix delegation•Firewall with stateful inspection (IPv4/IPv6)•Hacker intrusion prevention and detection•Application content filtering (IPv4/IPv6)•Complete NAT software implemented as per RFC 1631 with port and address mapping (IPv4)•DSLite support for IPv4 in-home support with IPv6 MSO backbone •6RD support for quick IPv6 deployment over IPv4 backbone •RIPv2 for static IP supportWireless•802.11a/b/g/n/ac/ax•4T4R 2.4GHz 11ax and 4T4R 5GHz 11ax dual band concurrent MU-MIMO with 1Gbps+4.8Gbps PHY rate•20/40/80/160MHz channel bandwidth•Up to 8 SSIDs for each frequency•Security: WPA-PSK/WPA2-PSK (TKIP/AES), WPA3, WAPI •QoS: WMM/WMM-PS•WPS (Wi-Fi Protected Setup) PBC, PIN•Airtime Fairness (ATF), Band Steering (BS)•Dynamic Frequency Selection (DFS)•Wi-Fi output power range: Max permitted by FCC/IC Electrical•Input power: 12VDC, 4A•Power adaptor: 100-240VAC, 50/60Hz•Power consumption: 4.92 (power saving), 22W (typ.), 38W (Max)•Support power outage for 24 hours on Hitron external battery •Surge protection: RF input sustains at least 4KVEthernet RJ-45 sustains at least 4KV Mechanical•Factory default reset button•WPS button•Dimensions: 74.3mm (W) x 251.5mm (H) x 230.8mm (D)•Weight: Weight: 1850 ±10gEnvironmental•Operating temperature: 0°C (32°F) ~ 40°C (104°F)•Operating humidity: 10% ~ 90% (Non-condensing)•Storage temperature: -40°C (-40°F) ~ 60°C (140°F) Compliance Certificates•RoHS compliant•FCC, IC, ULSPECIFICATIONS。
DrayTek VigorAP 960C 802.11ax Ceiling-mount Access

VigorAP 960C802.11ax Ceiling-mount AccessPointQuick Start GuideVersion: 1.2Firmware Version: V1.4.5(For future update, please visit DrayTek web site)Date: Dec. 21, 2022Intellectual Property Rights (IPR) InformationCopyrights © All rights reserved. This publication contains information that is protected by copyright. No part may be reproduced, transmitted, transcribed, stored ina retrieval system, or translated into any language without written permissionfrom the copyright holders.Trademarks The following trademarks are used in this document:●Microsoft is a registered trademark of Microsoft Corp.●Windows, Windows 8, 10, 11 and Explorer are trademarks of MicrosoftCorp.●Apple and Mac OS are registered trademarks of Apple Inc.●Other products may be trademarks or registered trademarks of theirrespective manufacturers.Safety Instructions and ApprovalSafety Instructions ●Read the installation guide thoroughly before you set up the device.●The device is a complicated electronic unit that may be repaired only beauthorized and qualified personnel. Do not try to open or repair thedevice yourself.●Do not place the device in a damp or humid place, e.g. a bathroom.●Do not stack the devices.●The device should be used in a sheltered area, within a temperaturerange of 0 to +40 Celsius.●Do not expose the device to direct sunlight or other heat sources. Thehousing and electronic components may be damaged by direct sunlight or heat sources.●Do not deploy the cable for LAN connection outdoor to preventelectronic shock hazards.●Keep the package out of reach of children.●When you want to dispose of the device, please follow local regulationson conservation of the environment.Warranty We warrant to the original end user (purchaser) that the device will be free from any defects in workmanship or materials for a period of two (2) yearsfrom the date of purchase from the dealer. Please keep your purchase receiptin a safe place as it serves as proof of date of purchase. During the warrantyperiod, and upon proof of purchase, should the product have indications offailure due to faulty workmanship and/or materials, we will, at our discretion,repair or replace the defective products or components, without charge foreither parts or labor, to whatever extent we deem necessary tore-store theproduct to proper operating condition. Any replacement will consist of a newor re-manufactured functionally equivalent product of equal value, and willbe offered solely at our discretion. This warranty will not apply if the productis modified, misused, tampered with, damaged by an act of God, or subjectedto abnormal working conditions. The warranty does not cover the bundled orlicensed software of other vendors. Defects which do not significantly affectthe usability of the product will not be covered by the warranty. We reservethe right to revise the manual and online documentation and to make changesfrom time to time in the contents hereof without obligation to notify anyperson of such revision or changes.Declaration of ConformityHereby, DrayTek Corporation declares that the radio equipment type VigorAP 960C is in compliance with Directive 2014/53/EU.The full text of the EU declaration of conformity is available at the following internet address: https:///VigorAP 960C/Document/CE/Manufacturer: DrayTek Corp.Address: No.26, Fushing Rd., Hukou, Hsinchu Industrial Park, Hsinchu 303, Taiwan Product: VigorAP 960CFrequency Information for Europe area:2.4GHz WLAN 2400MHz - 2483MHz, max. TX power: 19.95dBm5GHz WLAN 5150MHz - 5350MHz, max. TX power: 22.84dBm5470MHz - 5725MHz, max. TX power: 28.14dBmRequirements in AT/BE/BG/CZ/DZ/DK/EE/FR/DE/IS/IE/IT/EL/ES/CY/LV/LI/LT/ LU/HU/MT/NL/NO/PL/PT/RO/SI/SK/TR/FI/SE/CH/HR.5150MHz~5350MHz is for indoor use only.This product is designed for 2.4GHz and 5GHz WLAN network throughout the EC region.Declaration of ConformityHereby, DrayTek Corporation declares that the radio equipment type VigorAP 960C is in compliance with Regulation SI 2017 No. 1206.Manufacturer: DrayTek Corp.Address: No.26, Fushing Rd., Hukou, Hsinchu Industrial Park, Hsinchu 303, Taiwan Product: VigorAP 960CImporter: CMS Distribution Ltd: Bohola Road, Kiltimagh, Co Mayo, IrelandFrequency Information for UK area:2.4GHz WLAN 2400MHz - 2483MHz, max. TX power: 19.95dBm5GHz WLAN 5150MHz - 5350MHz, max. TX power: 22.84dBm5470MHz - 5725MHz, max. TX power: 28.14dBmRequirements in UK. 5150MHz~5350MHz is for indoor use only.This product is designed 2.4GHz and 5GHz WLAN network use in the UK & Ireland.Regulatory InformationFederal Communication Commission Interference StatementThis equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to radio communications. However, there is no guarantee that interference will not occur in a particular installation. If this equipment does cause harmfulinterference to radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one of the following measures:● Reorient or relocate the receiving antenna.● Increase the separation between the equipment and receiver.● Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.●Consult the dealer or an experienced radio/TV technician for help.This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions:(1) This device may not cause harmful interference, and(2) This device may accept any interference received, including interference that may cause undesired operation.Company nameABP International Inc.Address 13988 Diplomat Drive Suite 180 Dallas TX 75234 ZIP Code 75234E-mail*******************USA Local Representative Contact PersonMr. Robert MesserTel. 19728311600Caution ● Any changes or modifications not expressly approved by the grantee of this device could void the user's authority to operate the equipment.● Any changes or modifications not expressly approved by the party responsible for compliance could void the user's authority to operate this equipment.● This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter.●Radiation Exposure Statement: This equipment complies with FCC radiation exposure limits set forth for an uncontrolled environment. This equipment should be installed and operated with minimum distance 20cm between the radiator & your body.External Power Supply ErP Information1 2A Manufacturer DVE DVEB Address No.5, Baogao Rd, XindianDist, New Taipei City(23144), TaiwanNo.5, Baogao Rd, XindianDist, New Taipei City(23144), Taiwan DSA-12PF09-12 FUK DSA-18PFR-12 FUKC Model identifierDSA-12PF09-12 FEU DSA-18PFR-12 FEU D Input voltage 100~240V 100~240VInput AC frequency 50/60Hz 50/60HzEOutput voltage DC 12.0V 12.0VF Output current 1.0A 1.5AG Output power 12.0W 18.0WH Average active efficiency 83.3% 85.5%I Efficiency at low load 10% 80.8% 83.7%J No-load power consumption 0.06W 0.07W*The external power supply used for each product will be model dependent.For more update, please visit .T a b l e o f C o n t e n t s1. Package Content (1)2. Panel Explanation (2)3. Installation (3)3.1 Ceiling-mount Installation (Wooden Ceiling) (3)3.2 Ceiling-mount Installation (Plasterboard Ceiling) (4)3.3 Suspended Ceiling (Lightweight Steel Frame) Installation (5)3.4 Wall-Mounted Installation (7)4. Connection and Configuration (8)4.1 Notifications for Hardware Connection (8)4.2 Connect to a Vigor Router using AP Management (9)4.3 Web Configurations (10)5. Customer Service (14)Be a Registered Owner (14)Firmware & Tools Updates (14)1.P a c k a g e C o n t e n tTake a look at the package content. If there is anything missed or damaged, please contact DrayTek or dealer immediately.VigorAP 960C Main Unit Ceiling mount bracket & Quick StartGuideT-Rail Mounting Kits(Used for suspended ceiling)Fixings and Screws(for ceiling mounting) RJ-45 Cable (Ethernet)Screw set (for wall mounting) The type of the power adapter depends on the country that the AP will be installed:UK-type Power Adapter EU-type Power AdapterUSA/Taiwan-type Power Adapter AU/NZ-type Power AdapterThe maximum power consumption is 11 Watt.2. P a n e l E x p l a n a t i o nLED Status ExplanationOn The system is in boot-loader mode. OffThe system is not ready or fails.Blue LEDBlinking The system is in AP mode and work normally.Green LED BlinkingThe system is in Mesh mode or Range Extender modeand works normally.Orange LED Blinking The system is in TFTP mode. Off Off VigorAP is turned off or not functioning. Interface Explanation Ethernet Port Connects to LAN or router.Supports PoE power & Gigabit (1000BaseT).Power Jack (DC IN) Connecter for a power adapter. Hole Explanation Factory Reset Restores the unit back to factory default settings.To use, insert a small item such as an unbent paperclip into the hole. You will feel the button inside depress gently. Hold it for 5 seconds. The VigorAP will restart with the factory default configuration and the LED will blink blue.Note● For the sake of security, make the accessory kit away fromchildren.● Remove the protective film from the access point before useto ensure ventilation.LEDFactory ResetEthernet PortPower Jack (DC IN)3. I n s t a l l a t i o nVigorAP can be installed under certain locations: wooden ceiling, plasterboard ceilings, light-weighted steel frame and wall.3.1 C e i l i n g -m o u n t I n s t a l l a t i o n (W o o d e n C e i l i n g )1. Place the bracket under the wooden ceiling and fasten two screws firmly (asshown in Figure below, Step 1). 2. When the bracket is in place, fasten two screws firmly (as shown in Figurebelow, Step 2) on the bottom of VigorAP. 3. Make the device just below the bracket. Put the screws installed in Step 2 onthe holes of the bracket (as shown in Figure below, Step 3). 4. Gently rotate the device to make screws slide into the notches of thebracket and move forward till it is firmly fixed.Step 1Step 2BracketStep 33.2 C e i l i n g -m o u n t I n s t a l l a t i o n (P l a s t e r b o a r d C e i l i n g )1. Place the bracket under the plasterboard ceiling and fasten two turnbuckles firmly (as shown in Figure below, Step 1).2. Make the screws pass through the bracket and insert into the turnbuckles (asshown in Figure below, Step 2). Fasten them to offer more powerful supporting force.3. When the bracket is in place, fasten two screws firmly (as shown in Figurebelow, Step 3) on the bottom of VigorAP.4. Make the device just below the bracket. Put the screws installed in Step 3 onthe screw holes of the bracket (as shown in Figure below, Step 4).5. Gently rotate the device to make screws slide into the notches of thebracket and move forward till it is firmly fixed.BracketStep 1Step 2Step 3Step 43.3 S u s p e n d e d C e i l i n g (L i g h t w e i g h t S t e e l F r a m e )I n s t a l l a t i o nYou cannot screw into ceiling tiles as they are weak and not suitable for bearing loads. Your VigorAP is supplied with mounts (T-Rail brackets) which attach directly to the metal grid (‘T-Rail’) of your suspended ceiling.1. Choose one set of T-Rail mounting kits from the bundled package.2. Put the T-Rail brackets on the holes of the bottom side of the device. Fastenthem with suitable screws.3. If a larger gap is required between the ceiling and the VigorAP, use theextension pieces to extend the height of the brackets.T-Rail BracketExtension PieceT-Rail BracketExtension Piece4.Attach the T-Rail brackets to the ceiling frame.NoteWarning: The screw set shown below is for wall mounting only. Do not use such set for ceiling mounting due to the danger offalling.3.4 W a l l -M o u n t e d I n s t a l l a t i o nFor wall-mounting, the VigorAP has keyhole type mounting slots on the underside. You can fit the AP at any axis (i.e. 12, 3, 6 or 9 O’Clock) to allow for cable entry from the most convenient location if you are using side entry – note the position of the side entry cable cutout.1. A template is provided on the VigorAP’s packaging box to enable you tospace the screws correctly on the wall.2. Place the template on the wall and drill the holes according to therecommended instruction.3. Fit screws into the wall using the appropriate type of wall plug (as shown inthe ceiling section) but do not use the ceiling bracket – the VigorAP hangs directly onto the screws.Wall (wooden, concrete, plasterboard or others)4.C o n n e c t i o n a n d C o n f i g u r a t i o n4.1N o t i f i c a t i o n s f o r H a r d w a r e C o n n e c t i o n●If required, remove the protective cap of VigorAP to create extra spacefor the cables to pass through.●Connect VigorAP to Vigor router (via LAN port) with Ethernet cable.●Connect VigorAP to PoE switch (via LAN port) with Ethernet cable. Forconnecting with PoE switch, do not connect the power adapter. VigorAPwill get the power from the switch directly.4.2C o n n e c t t o a V i g o r R o u t e r u s i n g A P M a n a g e m e n tYour VigorAP can be used with Vigor routers which support AP management (such as the Vigor2865 or Vigor2927 series). AP Management enables you to monitor and manage multiple DrayTek APs from a single interface.1.Connect one end of the power adapter to power port of VigorAP, and theother side into a wall outlet.2.Access into the web user interface of Vigor router. Here we take Vigor2865as an example. Open Central Management>>AP>>Status.3.Locate VigorAP 960C. Click the IP address assigned by Vigor router to accessinto web user interface of VigorAP 960C.4.After typing username and password (admin/admin), the main screen will bedisplayed.4.3W e b C o n f i g u r a t i o n sThis section will guide you to install the AP and make configuration for VigorAP.C o n n e c t e d A s a M e s h N o d e(i n M e s h N e t w o r k)❶Install VigorAP on to the ceiling.❷As a mesh node, settings related to VigorAP 960C must be configured by a remote Mesh Root (e.g., VigorAP 903) within the mesh network.The user must detect VigorAP 960C via a Mesh Root to add it as a meshnode.C o n n e c t e d A s a n A c c e s s P o i n tAs an access point, VigorAP 960C must be connected to a router and configured in AP (Access Point) / Range Extender mode.❶Install VigorAP on to the ceiling.❷Use a twisted-pair cable with RJ-45 plugs at both ends, and plug into Ethernet device (e.g., Vigor router) and Ethernet port of VigorAP.❸ There are two methods to configure VigorAP.Method 1:(a) First, open a web browser on your PC and type https://192.168.1.2. Apop-up window will open to ask for username and password.Note You may either simply set up your computer to get IPdynamically from the router or set up the IP address of thecomputer to be in the same subnet as the IP address ofVigorAP 960C.● If there is no DHCP server on the network, then VigorAP960C will have an IP address of 192.168.1.2.● If there is DHCP available on the network, then VigorAP960C will receive its IP address via the DHCP server.● If you connect to VigorAP by wireless LAN, you could tryto access the web user interface through .(b) After clicking Login, Quick Start Wizard for configuring wirelesssettings will appear as follows.(c)Follow the on-screen steps to finish the network connection.Method 2:(a)Use a mobile phone to scan the QR code named with DrayTek WirelessApp to download DrayTek Wireless APP.(b)After downloading, run the APP.(c)From the home page, click the Connect icon to access the Connectpage. Next, press the QR code icon next to Scan QR Code on yourphone screen to open the camera.Scan the QR code named with Connect SSID to access the web user interface (configuration wizard) of VigorAP 960C. (For iOS users, the SSID and the password will be shown first. Simply click the Connect button to access the web user interface of VigorAP.)5.C u s t o m e r S e r v i c eIf the device cannot work correctly after trying many efforts, please contact your dealer/DrayTek for further help right away. For any questions, please feel freetosende-mailto“*******************”.B e a R e g i s t e r e d O w n e rWeb registration is preferred. You can register your Vigor router viahttps://..F i r m w a r e&T o o l s U p d a t e sDue to the continuous evolution of DrayTek technology, all routers will beregularly upgraded. Please consult the DrayTek web site for more information on newest firmware, tools and documents.https://GPL Notice This DrayTek product uses software partially or completely licensedunder the terms of the GNU GENERAL PUBLIC LICENSE. The author ofthe software does not provide any warranty. A Limited Warranty isoffered on DrayTek products. This Limited Warranty does not coverany software applications or programs.To download source codes please visit:GNU GENERAL PUBLIC LICENSE:https:///licenses/gpl-2.0Version 2, June 1991For any question, please feel free to contact DrayTek technical*************************************************.14。
生物医学仪器简介

心电图设备
小 型 化 的 同 步 12 导 联 自 动 心 电 图 仪
技术发展事例(2/6)
用于医学的分析仪器,主要沿袭了现代 化学分析仪的方法和手段,如谱分析方 法,电化学方法、各种分离技术等,对 人体成份进行离体分析,直接针对活体 内成份的测量,是医学分析仪器的特殊 处和极重要的方面,20世纪末得益于生 物工程技术和电子技术的发展,使医用 分析仪器在大规模测量和小型化、快速 分析等方面均取得了重大进展。
双探头SPECT,专门用于 心脏 SPECT检查
《生物医学仪器及应用》教材
• 王保华,生物医学测量与仪器, 复旦大学出版社,2003年6月, ¥38
教材目录
Ch1 绪论 Ch2 生物电测量及仪器 Ch3 生理参数测量及仪器 Ch4 生化参数检测及仪器 Ch5 病房监护系统 Ch6 生理参数的远程传输及检测技术 Ch7 医学超声测量及仪器 Ch8 植入式测量及仪器 Ch9 生物医学光子测量技术 Ch10细胞和分子层次的检测技术
课程安排
• 生物医学工程概述 • 生物医学材料 • 生物力学 • 人工器官 • 生物医学仪器 • 生物医学图象
技术发展事例(1/6)
1903年荷兰生理学家艾萨文
(William Einthoven)研制成功了第
一台采用弦线式电流计记录的心 电图仪,创立的肢体标准导联的
概念,沿用至今,艾萨文开创性 的贡献使他获得了1924年医学诺 贝尔奖
Ch7 医学超声测量及仪器
• 医学超声的分类、特点及应用 • 医学超声诊断的声学基础 • A型和M型超声波 • B型超声测量仪器 • 彩色超声血流成像
Ch8 植入式测量及仪器
• 植入式电子系统概述 • 吞服式无线电遥测胶囊 • 植入式无线电遥测系统 • 植入式超声波遥测系统 • 植入式光遥测系统 • 植入式闭环测控系统
整车控制策略

XXX项目VCU控制策略江苏新能源有限公司编制:____________审核:____________批准:____________Document NameVCU系统目录目录 2版本历史 (5)修订历史 (5)第1版 (5)文档简介 (6)文档目的 (6)使用对象 (6)文档构成 (6)信息获得 (6)需求文档 (6)术语 (8)定义 8VCU 整车控制器总成 (8)缩略语 (8)产品原理 (9)VCU系统原理图 (9)整车高压系统框图 (9)整车网络拓扑 (10)VCU输入输出列表 (10)电源管理 (12)VCU系统功能简介 (13)VCU功能汇总及功能描述 (13)高压上下电功能 (15)功能概述 (15)系统框图 (15)驱动高压上电功能描述 (15)驱动高压上电功能框图 (15)驱动上电功能 (16)驱动下电功能描述 (19)驱动高压下电功能框图 (19)驱动下电功能 (19)碰撞绝缘故障下电 (21)功能框图 (22)功能逻辑 (22)一般故障下电功能 (23)功能框图 (23)功能逻辑 (24)充电上电 (27)功能框图 (27)功能逻辑 (27)充电下电 (30)功能框图 (30)功能逻辑 (30)高压上下电仲裁功能描述 (31)充电工况的优先级高于驱动工况 (31)满足以下两个条件之一,则可以判断处于充电工况 (31)不在充电工况,满足以下任一条件,则处于驱动工况 (31)Document NameVCU系统驱动功能说明 (32)挡位识别 (32)功能框图 (32)功能逻辑 (32)驾驶模式识别 (34)功能框图 (34)功能逻辑 (34)滑行回馈功能 (36)功能框图 (36)功能逻辑 (36)制动工况回馈扭矩响应 (39)功能框图 (39)功能逻辑 (39)驱动扭矩控制 (41)功能框图 (41)功能逻辑 (42)扭矩解析功能流程图 (43)挡位防盗 (45)功能框图 (45)功能逻辑 (45)最高车速限制 (45)功能框图 (45)功能逻辑 (46)蠕行功能 (46)功能框图 (46)功能逻辑 (47)跛行回家 (47)功能框图 (48)功能逻辑 (48)坡起辅助功能 (48)功能框图 (48)功能逻辑 (49)高压互锁防护 (51)功能框图 (51)功能逻辑 (51)VCU控制高压互锁S+发送PWM信号(低有效、频率100Hz、占空比50%)进入条件: (51)VCU控制高压互锁S+发送PWM信号退出条件: (51)高压互锁功能执行动作: (51)碰撞防护 (52)功能框图 (52)功能逻辑 (52)真空泵控制 (53)功能框图 (53)功能逻辑 (53)热管理功能 (54)热管理系统框图 (54)高压散热功能 (54)功能框图 (54)功能逻辑描述 (54)空调加热功能 (55)Document NameVCU系统功能框图 (55)功能逻辑描述 (56)空调制冷功能 (56)功能框图 (56)功能逻辑描述 (56)动力防盗 (58)动力防盗功能 (58)功能框图 (58)功能逻辑描述 (58)附件管理功能 (60)DCDC管理功能描述 (60)DCDC管理功能概述 (60)DCDC管理功能示意图 (60)DCDC管理功能详述 (60)剩余里程显示功能 (62)剩余里程显示功能概述 (62)剩余里程计算功能示意图 (62)剩余里程计算功能详述 (62)剩余里程计算功能进入条件 (62)剩余里程功能计算 (62)剩余里程退出条件 (62)故障处理功能 (63)故障故障处理功能概述 (63)故障显示和处理功能示意图 (63)故障分级 (63)故障处理功能详述 (65)网关功能 (66)功能描述 (66)系统框图 (66)信号及报文路由 (66)通讯接口 (67)接口类型 (67)参数要求 (67)BootLoader功能 (67)产品技术参数 (68)特性参数 (68)信号定义 (69)CAN通信矩阵 (69)CAN网络诊断 (69)下线匹配 (69)Document NameVCU系统版本历史修订版本日期所有者描述修订历史第1版建立XXX项目VCU控制策略.Document NameVCU系统文档简介文档目的本文档描述XXX纯电动车型的VCU的硬件接口及所有逻辑策略。
Ch9(WCDMA)

华南农业大学 胡洁
1
蜂窝移动通信系统的发展 蜂窝移动通信系统的发展
2
蜂窝移动通信系统的发展 蜂窝移动通信系统的发展 第三代数字蜂窝移动通信系统
发展历程: 发展历程: 1985年:出现FPLMTS,1996年命名为IMT-2000. 1992年:WRC92在2GHz频段上分配了230MHz频率给FPLMTS陆地和 卫星业务. 1999年3月:完成IMT-2000关键参数. 1999年11月:完成IMT-2000技术规范. 2000年:完成IMT-2000全部网络规范. 经过十几年的研究,特别是从1997年起, 经过十几年的研究,特别是从1997年起,第三代移动通信的基本框 1997年起 网络技术,主要特征, 架,网络技术,主要特征,业务种类已经基本成形
6
第三代移动通信系统 第三代移动通信系统业务特点
智能化 提供灵活的网络业务, 提供灵活的网络业务,终端的智能化
多媒体化 实现语音,图像,数据等多种媒体信息在无线, 实现语音,图像,数据等多种媒体信息在无线,有线网之间的无缝传输
个性化 用户可以在终端,网络能力的范围内, 用户可以在终端,网络能力的范围内,设计自己的业务
WCDMA空中接口协议结构 WCDMA空中接口协议结构
Network Layer Layer 3
Radio Resource Control
RRC
Data Link Layer Layer 2
Radio Link Control
RLC
Logical Channels
Medium Access Control
上行信道导频
切换
软切换,频间切换,软切换,频间切换, 接力切换,频间切换, 与GSM间的切换 与IS-95B间的切换 与GSM间的切换, 与IS-95间的切换
OE-CAE16HD Analog to IP Encoder Quick Start Guide
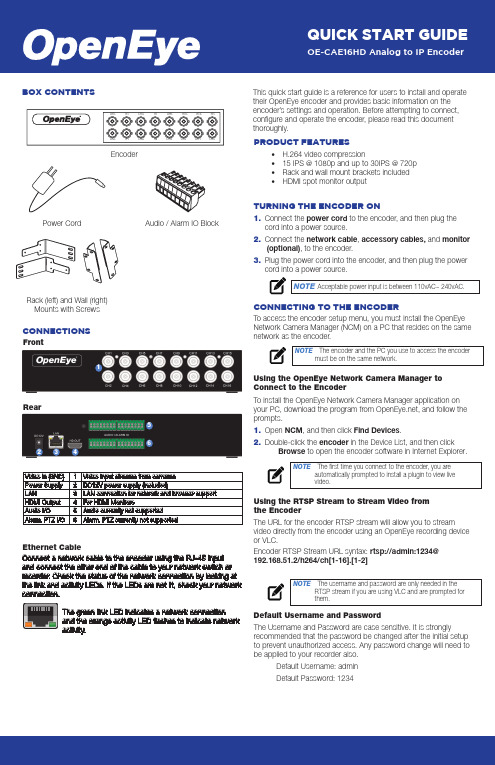
23This quick start guide is a reference for users to install and operate their OpenEye encoder and provides basic information on the encoder’s settings and operation. Before attempting to connect, configure and operate the encoder, please read this document thoroughly.• H.264 video compression• 15 IPS @ 1080p and up to 30IPS @ 720p • Rack and wall mount brackets included •HDMI spot monitor outputCONNECTIONSFrontRearBOX CONTENTSEncoderAudio / Alarm IO BlockPRODUCT FEATURESEthernet CableConnect a network cable to the encoder using the RJ-45 inputand connect the other end of the cable to your network switch or recorder. Check the status of the network connection by looking atconnection.The green link LED indicates a network connection and the orange activity LED flashes to indicate network activity.1TURNING THE ENCODER ON1. Connect the power cord to the encoder, and then plug the cord into a power source.2. Connect the network cable , accessory cables, and monitor (optional), to the encoder.3. Plug the power cord into the encoder, and then plug the power cord into a power source.NOTE Acceptable power input is between 110vAC~ 240vAC.Rack (left) and Wall (right) Mounts with ScrewsCONNECTING TO THE ENCODERTo access the encoder setup menu, you must install the OpenEye Network Camera Manager (NCM) on a PC that resides on the same network as the encoder.Using the OpenEye Network Camera Manager to Connect to the EncoderTo install the OpenEye Network Camera Manager application on your PC, download the program from , and follow the prompts.1. Open NCM , and then click Find Devices .2. Double-click the encoder in the Device List, and then click Browse to open the encoder software in Internet Explorer.NOTE The first time you connect to the encoder, you areautomatically prompted to install a plugin to view livevideo.Default Username and PasswordThe Username and Password are case sensitive. It is stronglyrecommended that the password be changed after the initial setup to prevent unauthorized access. Any password change will need to be applied to your recorder also. Default Username: adminDefault Password: 1234Using the RTSP Stream to Stream Video from the EncoderThe URL for the encoder RTSP stream will allow you to stream video directly from the encoder using an OpenEye recording device or VLC.Encoder RTSP Stream URL syntax: rtsp://admin:1234@ 192.168.51.2/h264/ch[1-16].[1-2]NOTE The username and password are only needed in theRTSP stream if you are using VLC and are prompted for them.NOTE The encoder and the PC you use to access the encodermust be on the same network.6451. To set all channels, select Circular in the channel selection box.- or - Select a single channel from the channel selection box.2. Select the position you desire the channel to appear in thesequence.3. Type the sequence duration time (in seconds) you want eachchannel to display.4. Set sequence activate to ON.5. Click Save.NOTE Sequence Setup is only relevant to spot monitor or localview only.Sequence Setup1. Click Setup, and then click Software.2. Click Upgrade, and then navigate to the desired upgrade file,and then click OK.The encoder firmware will update, and then encoder will rebootupon completion.Firmware Update1. Click Setup, and then click Maintenance.2. Select Reboot or a method of Restore.• Reboot- restart the encoder.• Full Restore - restore the encoder to factory defaultsettings, including network settings.• Partial Restore - restore the encoder to factory defaultsettings, excluding network settings.3. Click Yes (or OK) to accept the Restore or Reboot.Factory Restore and Reboot1. Click Setup, and then click Network Setup.2. To use the encoder default IP address, select Use Fixed IPAddress (recommended).a. Enter the default IP address.b. Verify the subnet mask, default gateway,primaryDN S, and mac address for the encoder.c. Click Save.3. To automatically assign an IP address, select Get IP AddressAutomatically.ENCODER SETUPNetwork SettingsDate / Time Settings1. Click Setup.2. Select the appropriate Time Zone, and then select the desireddate format.3. Select a method of date and time sync.4. Click Save to apply the changes.• Sync with NTP Server - use a specified NTP server andupdate interval for the date and time.• Sync with computer time - use the PC date and time.• Manual - manually enter the date and time.NOTE:S ync with NTP Server is the recommendedDate / Time setting. The NTP server address is.Resolution Sets the resolution of Stream 1 and Stream 2Bit Rate Sets the bit rate of Stream 1 and Stream 2Frame Rate Sets the frame rate of Stream 1 and Stream 2GOP Sets the GOP of Stream 1 and Stream 2Stream SettingsVideo AdjustBrightnessContrastSaturationHueTermination ON or OFFCamera SetupPicture Settings1. Click Encoder Setup.2. In the Monitor Resolution tab, select a resolution.3. Click Yes to accept the resolution change and restart theEncoder.Monitor ResolutionNOTE HDMI spot-out resolution options include 1024 x 768,1280 x 1024, 720p, and 1080p.NOTE The Monitor Resolution section applies to spot-outonly.。
国外毒理学网站

国内外优秀毒理学网站汇总longer整理自bioon毒理学论坛精华Table of Contents1.General Toxicological Sites2.Environmental Toxicology Sites3.Food Toxicology Sites4.Toxicological Plants Sites5.Cancer Sites coming up6.Developmental Toxicology Sites coming up7.Drug Toxicology Sites coming up8.Toxicology Educatation Sites coming up9.Forensic Tox icology Sites coming up10.Genetic & Molecular Toxicology Sites coming up11.Occupational & Environmental Toxicology Sites coming up12.Toxicological Sites in Finland coming up(Note: Be aware of the typos in the http:// addresses listed below!!!)1.General Toxicological SitesBy xmale网友:Society of Toxicology (SOT)/EXtension TOXicology NETwork /info/extoxnet/Canadian Network of Toxicology Centres (CNTC)http://www.uoguelph.ca/cntc/毒物学和生态毒理学新闻(论文覆盖如肾上腺毒理学和钚中毒等主题。
大部分信息免费提供。
).br/te中毒急救(由南非cape town大学提供,有关特殊物质中毒处理的教材。
3GPP 5G基站(BS)R16版本一致性测试英文原版(3GPP TS 38.141-1)

4.2.2
BS type 1-H.................................................................................................................................................. 26
4.3
Base station classes............................................................................................................................................27
1 Scope.......................................................................................................................................................13
All rights reserved. UMTS™ is a Trade Mark of ETSI registered for the benefit of its members 3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational Partners LTE™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM Association
RedHat Linux 9网络配置

RedHat Linux 9网络配置本篇文章来源于黑基网-中国最大的网络安全站点原文链接:/lib/2005-05-27/7461.html计算机需要网络连接才能和其它计算机通讯。
这是通过由操作系统识别接口卡(如:以太网卡、ISDN 调制解调器、权标环),并配置该接口来连接到网络上来实现的。
网络管理工具可以用来配置以下类型的网络接口:以太网ISDN调制解调器xDSL权标环CIPE无线设备要使用网络管理工具,你必须具备根特权。
要启动这个程序,点击面板上的「主菜单」=> 「系统设置」=> 「网络」,或在shell 提示(如XTerm 或GNOME 终端)下键入redhat-config-network 命令。
如果你键入了这个命令,若X 在运行,则图形化版本会被显示,否则,基于文本的版本会被显示。
要强制运行基于文本的版本,使用redhat-config-network-tui 命令。
图12-1. 网络管理工具如果你更喜欢直接修改配置文件,请参阅《Red Hat Linux 参考指南》来获取关于这些配置文件的位置和内容的信息。
窍门:访问Red Hat 硬件兼容性列表(/hcl/ )来判定Red Hat Linux 是否支持你的硬件设备。
12.1. 总览要使用网络管理工具来配置网络连接,执行以下步骤:把物理硬件设备添加到硬件列表中。
添加和该物理硬件设备相关的网络设备。
配置主机名和DNS 设置。
配置你无法通过DNS 查寻的主机。
本章将会针对每类网络连接来讨论以上的每一个步骤。
12.2. 建立以太网连接要建立以太网连接,你需要一张网卡(NIC),一条网络电缆(通常是CAT5 电缆),以及要连接的网络。
不同的网络配置使用不同的速度,请确定你的NIC 与你想连接的网络兼容。
要添加以太网连接,执行以下步骤:点击「设备」标签。
点击工具栏上的「新建」按钮。
从「设备类型」列表中选择「以太网连接」,然后点击「前进」。
ABB工业机器人编程-第四章

X3端子见表4-3
© ABB April 28, 2019
| Slide 9
4.2. ABB标准IO板卡介绍
4.2.1 ABB标准I/O板 DSQC651
X5 端子编号 1 2 3 4 5
表4-4
使用定义 0V BLACK(黑色) CAN信号线low BLUE(蓝色) 屏蔽线 CAN信号线high WHITE(白色) 24V RED(红色) GND 地址选择公共端 模块ID bit 0 (LSB) 模块ID bit 1 (LSB) 模块ID bit 2 (LSB) 模块ID bit 3 (LSB) 模块ID bit 4 (LSB) 模块ID bit 5 (LSB)
© ABB April 28, 2019
| Slide 2
第四章 ABB机器人通讯
4.1.ABB机器人通讯介绍
ABB机器人I/O通讯的种类
ABB机器人提供了丰富I/O通讯接口,如ABB的标准通讯,与PLC的现场总线通
讯,还有与PC机的数据通讯,如图,可以轻松地实现与周边设备的通信
ABB的标准I/O板提供的常用信号处理有数字量输入,数字量输出,组输入,组
工业通讯总线接口(选件), 只支持从站功能如: Devicenet、Profibus、 Profinet、EtherNet IP等
Key:使用 何种现场 总线,要 根据需要 进行选配
© ABB April 28, 2019
| Slide 5
第四章 ABB机器人通讯
4.1.ABB机器人通讯介绍
Key:
表4-8
使用定义 INPUT CH9 INPUT CH10 INPUT CH11 INPUT CH12 INPUT CH13 INPUT CH14 INPUT CH15 INPUT CH16 0V 未使用 地址分配 8 9 10 11 12 13 14 15
工业机器人操作与编程-第十二章输入输出

二 IO板
b.
X5端子见表4-4
模
块
接
口
连
接
说
明
X6端子见表4-5
X5 端子编号 1 2 3 4 5 6 7 8 9 10 11 12
表4-4
使用定义 0V BLACK(黑色) CAN信号线low BLUE(蓝色) 屏蔽线 CAN信号线high WHITE(白色) 24V RED(红色) GND 地址选择公共端 模块ID bit 0 (LSB) 模块ID bit 1 (LSB) 模块ID bit 2 (LSB) 模块ID bit 3 (LSB) 模块ID bit 4 (LSB) 模块ID bit 5 (LSB)
Profibus总线板卡。
Key: 如果使用ABB标准I/O板, 就必须有DeviceNet的总
线
存储插槽及SD 存储卡,标配
2GB.
二 IO板
本节将介绍常用的ABB标准I/O板(具体规格 参数以ABB官方最新公布为准)。
型号 DSQC 651 DSQC 652 DSQC 653 DSQC 355A DSQC 377A
三 IO板配置
定义DSQC651板的总线连接
ABB标准I/O板都是下挂在DeviceNet现场总线下的设备,通过X5端口与DeviceNet现场总线进行通信。
ABB标准I/O板DSQC651是最为常用的模块,下面以创建数字输入信号di、数字输出信号do、组输入 信号gi、组输出信号go和模拟输出信号ao为例做一个详细的讲解。
X6 端子编号
1 2 3 4 5
6
表4-5
使用定义
未使用 未使用 未使用 0V 模拟输出AO1
ADHOC网络学习报告

2.Main research hot points
• Survivability
Network protection mechanism can be divided into link protection and path protection, in addition, there is a segment protection between these two kinds of protection mechanism. According to the arrange of fault influence, there are three types of network fault : OLT class, ONU class and wireless router class.
16
2.Main research hot points
业务t的工作连接 业务t的备用连接
骨干网
业务a的工作连接 业务a的备用连接
ONU-8
ONU-7
ONU-6
ONU-5
…
ONU-4
ONU-1
ONU-3 ONU-2
单位无线链路容量 RCr
{a,t}
业务a 业务t
Fig.10 Path Protection algorithm with Global Connection Availability, PPGCA (Sharing scheme for the allocation of working wireless link capacity in path protection)
1 Introduction 2 Main research hot points 3 Simulation based on OPNET
Philips Dynalite DDRC1220FR-GL 开关机器人控制器说明说明书

• Multiple wiring schemes supported – Controls single phase and neutral or three phase and neutral (star) wiring configurations.
2 x RJ12
DyNet RS485
Ordering Code
Product DDRC1220FR-GL
Philips 12NC 913703243009
© 2023 Signify Holding. All rights reserved. Specifications are subject to change without notice. No representation or warranty as to the accuracy or completeness of the information included herein is given and any liability for any action in reliance thereon is disclaimed. Philips and the Philips Shield Emblem are registered trademarks of Koninklijke Philips N.V. All other trademarks are owned by Signify Holding or their respective owners.
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Chapter7:Network security Foundations:❒what is security?❒cryptography❒authentication❒message integrity❒key distribution and certificationSecurity in practice:❒application layer:secure e-mail❒transport layer:Internet commerce,SSL,SET❒network layer:IP security7:Network Security1Friends and enemies:Alice,Bob,TrudyFigure7.1goes here❒well-known in network security world❒Bob,Alice(lovers!)want to communicate“securely”❒Trudy,the “intruder”may intercept,delete,addmessages7:Network Security2What is network security? Secrecy:only sender,intended receiver should“understand”msg contents❍sender encrypts msg❍receiver decrypts msgAuthentication:sender,receiver want to confirm identity of each otherMessage Integrity:sender,receiver want to ensure message not altered(in transit,or afterwards)without detection7:Network Security37:Network Security 7The language of cryptographysymmetric key crypto:sender,receiver keys identical public-key crypto:encrypt key public ,decrypt keysecret Figure 7.3goes hereplaintext plaintextciphertext K A K BSymmetric key cryptographysubstitution cipher:substituting one thing for another monoalphabetic cipher:substitute one letter for another plaintext:abcdefghijklmnopqrstuvwxyzciphertext:mnbvcxzasdfghjklpoiuytrewqE.g.:Plaintext:bob.i love you.aliceciphertext:nkn.s gktc wky.mgsbc Q:How hard to break this simple cipher?:•brute force(how hard?)•other?7:Network Security8Symmetric key crypto:DESDES:Data Encryption Standard❒US encryption standard[NIST1993]❒56-bit symmetric key,64bit plaintext input ❒How secure is DES?❍DES Challenge:56-bit-key-encrypted phrase(“Strong cryptography makes the world a saferplace”)decrypted(brute force)in4months❍no known“backdoor”decryption approach❒making DES more secure❍use three keys sequentially(3-DES)on each datum ❍use cipher-block chaining7:Network Security97:Network Security10Public Key Cryptographysymmetric key crypto ❒requires sender,receiver know shared secret key ❒Q:how to agree on key in first place (particularly if never“met”)?public key cryptography❒radically different approach[Diffie-Hellman76,RSA78]❒sender,receiver donot share secret key❒encryption key public (known to all)❒decryption keyprivate(known only to receiver)7:Network Security11Public key cryptographyFigure7.7goes here7:Network Security12RSA:Choosing keys1.Choose two large prime numbers p,q.(e.g.,1024bits each)pute n=pq,z=(p-1)(q-1)3.Choose e(with e<n)that has no common factorswith z.(e,z are“relatively prime”).4.Choose d such that ed-1is exactly divisible by z.(in other words:ed mod z=1).5.Public key is(n,e).Private key is(n,d).7:Network Security147:Network Security 16RSA example:Bob chooses p=5,q=7.Then n=35,z=24.e=5(so e,z relatively prime).d=29(so ed-1exactly divisible by z.letter m me c =m mod n e l 12152483217c m =c mod n d 1748196857210675091509141182522307200012c d letterl encrypt:decrypt:7:Network Security 17RSA:Why:m =(m mod n)e mod n d (m mod n)e mod n =m mod nd ed Number theory result:If p,q prime,n =pq,then x mod n =x mod ny y mod (p-1)(q-1)=m mod ned mod (p-1)(q-1)=m mod n1=m(using number theory result above)(since we chose ed to be divisible by (p-1)(q-1)with remainder 1)AuthenticationGoal:Bob wants Alice to“prove”her identityto himProtocol ap1.0:Alice says“I am Alice”Failure scenario??7:Network Security18Authentication:another tryProtocol ap2.0:Alice says“I am Alice”and sends her IPaddress along to“prove”it.Failure scenario??7:Network Security19Authentication:another tryProtocol ap3.0:Alice says“I am Alice”and sends hersecret password to“prove”it.Failure scenario?7:Network Security207:Network Security 21Authentication:yet another tryProtocol ap3.1:Alice says “I am Alice”and sends herencrypted secret password to “prove”it.Failure scenario?I am Alice encrypt(password)7:Network Security22Authentication:yet another tryGoal:avoid playback attackFailures,drawbacks?Figure 7.11goes hereNonce:number (R)used onlyonce in a lifetimeap4.0:to prove Alice “live”,Bob sends Alice nonce ,R.Alicemust return R,encrypted with shared secret key7:Network Security 23Figure 7.12goes hereAuthentication:ap5.0ap4.0requires shared symmetric key❍problem:how do Bob,Alice agree on key❍can we authenticate using public key techniques?ap5.0:use nonce,public key cryptography7:Network Security 24Figure 7.14goes hereap5.0:security holeMan (woman)in the middle attack:Trudy poses as Alice (to Bob)and as Bob (to Alice)Need “certified”public keys (more later …)Digital SignaturesCryptographic technique analogous to hand-written signatures.❒Sender(Bob)digitally signs document,establishing he is document owner/creator.❒Verifiable,nonforgeable: recipient(Alice)can verify that Bob,and no one else, signed document.Simple digital signature for message m:❒Bob encrypts m with his public key d B,creating signed message,d B(m).❒Bob sends m and d B(m)to Alice.7:Network Security25Digital Signatures(more)❒Suppose Alice receives msg m,and digital signature d B(m)❒Alice verifies m signed by Bob by applying Bob’s public key e B tod B(m)then checkse B(d B(m))=m.❒If e B(d B(m))=m, whoever signed m must have used Bob’s private key.Alice thus verifies that:❍Bob signed m.❍No one else signed m.❍Bob signed m and not m’. Non-repudiation:❍Alice can take m,andsignature d B(m)to courtand prove that Bobsigned m.7:Network Security26Message DigestsComputationally expensive to public-key-encrypt long messages Goal:fixed-length,easy to compute digital signature,“fingerprint”❒apply hash function H to m,get fixed size message digest,H(m).Hash function properties:❒Many-to-1❒Produces fixed-size msg digest(fingerprint)❒Given message digest x, computationally infeasibleto find m such that x=H(m)❒computationally infeasibleto find any two messages m and m’such that H(m)=H(m’).7:Network Security27Digital signature=Signed message digestBob sends digitally signed message:Aliceverifies signature and integrity of digitally signed message:7:Network Security28Hash Function Algorithms❒Internet checksum would make a poor message digest.❍Too easy to findtwo messages withsame checksum.❒MD5hash function widely used.❍Computes128-bitmessage digest in4-stepprocess.❍arbitrary128-bit stringx,appears difficult toconstruct msg m whoseMD5hash is equal to x.❒SHA-1is also used.❍US standard❍160-bit message digest7:Network Security29Trusted IntermediariesProblem:❍How do two entitiesestablish sharedsecret key overnetwork? Solution:❍trusted keydistribution center(KDC)acting asintermediarybetween entities Problem:❍When Alice obtainsBob’s public key(from web site,e-mail,diskette),howdoes she know it isBob’s public key,notTrudy’s?Solution:❍trusted certificationauthority(CA)7:Network Security30Key Distribution Center(KDC)❒Alice,Bob need sharedsymmetric key.❒KDC:server sharesdifferent secret keywith each registereduser.❒Alice,Bob know own symmetric keys,K A-KDC K B-KDC,for communicating with KDC.❒Alice communicates with KDC,gets session key R1,and K B-KDC(A,R1)❒Alice sends BobK B-KDC(A,R1),Bob extracts R1❒Alice,Bob now share the symmetric key R1.7:Network Security31Certification Authorities ❒Certification authority(CA)binds public key toparticular entity.❒Entity(person,router,etc.)can register its publickey with CA.❍Entity provides“proofof identity”to CA.❍CA creates certificate binding entity to public key.❍Certificate digitally signed by CA.❒When Alice wants Bob’s public key:❒gets Bob’s certificate(Bob or elsewhere).❒Apply CA’s public key to Bob’scertificate,get Bob’s public key7:Network Security327:Network Security33Secure e-mail•generates random symmetric private key,K S .•encrypts message with K S •also encrypts K S with Bob’s public key.•sends both K S (m)and e B (K S )to Bob.•Alice wants to send secrete-mail message,m,to Bob.7:Network Security34Secure e-mail (continued)•Alice wants to provide sender authenticationmessage integrity.•Alice digitally signs message.•sends bothmessage (in the clear)and digital signature.7:Network Security35Secure e-mail (continued)•Alice wantsto provide secrecy,sender authentication,message integrity.Note:Alice uses both her private key,Bob’s public key.Secure sockets layer(SSL)❒PGP provides security for a specific network app.❒SSL works at transport layer.Provides security to any TCP-based app using SSL services.❒SSL:used between WWW browsers,servers for I-commerce(shttp).❒SSL security services:❍server authentication❍data encryption❍client authentication(optional)❒Server authentication:❍SSL-enabled browserincludes public keys fortrusted CAs.❍Browser requests servercertificate,issued bytrusted CA.❍Browser uses CA’s publickey to extract server’spublic key fromcertificate.❒Visit your browser’s security menu to see its trusted CAs.7:Network Security37SSL(continued)Encrypted SSL session:❒Browser generatessymmetric session key, encrypts it with server’s public key,sends encrypted key to server.❒Using its private key,server decrypts session key.❒Browser,server agree that future msgs will be encrypted.❒All data sent into TCP socket(by client or server) i encrypted with session key.❒SSL:basis of IETF Transport Layer Security (TLS).❒SSL can be used for non-Web applications,e.g., IMAP.❒Client authentication canbe done with client certificates.7:Network Security38Secure electronic transactions(SET)❒designed for payment-card transactions over Internet.❒provides security services among3players:❍customer❍merchant❍merchant’s bankAll must have certificates.❒SET specifies legal meanings of certificates.❍apportionment ofliabilities fortransactions ❒Customer’s card number passed to merchant’s bank without merchant ever seeing number in plain text.❍Prevents merchants fromstealing,leaking paymentcard numbers.❒Three software components:❍Browser wallet❍Merchant server❍Acquirer gateway❒See text for description of SET transaction.7:Network Security39Ipsec:Network Layer Security❒Network-layer secrecy:❍sending host encrypts thedata in IP datagram❍TCP and UDP segments;ICMP and SNMPmessages.❒Network-layer authentication ❍destination host canauthenticate source IPaddress❒Two principle protocols:❍authentication header(AH)protocol❍encapsulation securitypayload(ESP)protocol ❒For both AH and ESP,source, destination handshake:❍create network-layerlogical channel called aservice agreement(SA)❒Each SA unidirectional.❒Uniquely determined by:❍security protocol(AH orESP)❍source IP address❍32-bit connection ID7:Network Security40ESP Protocol❒Provides secrecy,host authentication,data integrity.❒Data,ESP trailer encrypted.❒Next header field is in ESP trailer.❒ESP authentication field is similar to AH authentication field.❒Protocol=50.7:Network Security417:Network Security 42Authentication Header (AH)Protocol ❒Provides source host authentication,data integrity,but not secrecy.❒AH header inserted between IP header and IP data field.❒Protocol field =51.❒Intermediate routers process datagrams as usual.AH header includes :❒connection identifier ❒authentication data:signed message digest,calculated over original IP datagram,providing source authentication,data integrity.❒Next header field:specifiestype of data (TCP,UDP,ICMP,etc.)Network Security(summary) Basic techniques…...❒cryptography(symmetric and public)❒authentication❒message integrity….used in many different security scenarios❒secure email❒secure transport(SSL)❒IP secSee also:firewalls,in network management7:Network Security43。
