毕业设计 英文资料
毕业设计开题报告--英文

Understood on the international present mainstream the technology, the application system as well as our country transform the technological strength and the hardware facility as well as the expenditure which needs.
Construct Enviroment & Equioment
一.The background of research:
Our country heating area are general, the heating time is long, is day by day intense to the energy demand and is urgent, but by the tradition fossil energy primarily our country, the resources dries up day by day, the consumption is big, the pollution serious also cannot regenerate, the energy tense situation aggravating, this requests us to have to improve the heating way unceasingly, the technical method, uses the least energy to produce the greatest quantity of heat in order to.But concentrates heats is not high in our country's popular degree, the centralism heats the production technology is not extremely advanced, this requests us studies the use to this kind of technology and the form, our country's centralism heats only distributes in the city and developed cities, also only is uses the winter various each household bunker coal regarding not the developed area and the general countrysides to warm up, this is to the energy huge waste and the environmental pollution, is the transformation key point.Even if already uses the area which the centralism heated, also was the level is uneven, does things their own way, could not form the unified system, did the heat energy assignment to be uneven, the hot heat, cold cold, affected the efficiency seriously, thus it can be seen, carried on the transformation to the obsolete pipe network, carried on the promotion to the existing equipment, established widespread also the unified big centralism heating pipe network system imperative.
毕业设计外文翻译_英文版

A Design and Implementation of Active NetworkSocket ProgrammingK.L. Eddie Law, Roy LeungThe Edward S. Rogers Sr. Department of Electrical and Computer EngineeringUniversity of TorontoToronto, Canadaeddie@, roy.leung@utoronto.caAbstract—The concept of programmable nodes and active networks introduces programmability into communication networks. Code and data can be sent and modified on their ways to destinations. Recently, various research groups have designed and implemented their own design platforms. Each design has its own benefits and drawbacks. Moreover, there exists an interoperability problem among platforms. As a result, we introduce a concept that is similar to the network socket programming. We intentionally establish a set of simple interfaces for programming active applications. This set of interfaces, known as Active Network Socket Programming (ANSP), will be working on top of all other execution environments in future. Therefore, the ANSP offers a concept that is similar to “write once, run everywhere.” It is an open programming model that active applications can work on all execution environments. It solves the heterogeneity within active networks. This is especially useful when active applications need to access all regions within a heterogeneous network to deploy special service at critical points or to monitor the performance of the entire networks. Instead of introducing a new platform, our approach provides a thin, transparent layer on top of existing environments that can be easily installed for all active applications.Keywords-active networks; application programming interface; active network socket programming;I. I NTRODUCTIONIn 1990, Clark and Tennenhouse [1] proposed a design framework for introducing new network protocols for the Internet. Since the publication of that position paper, active network design framework [2, 3, 10] has slowly taken shape in the late 1990s. The active network paradigm allows program code and data to be delivered simultaneously on the Internet. Moreover, they may get executed and modified on their ways to their destinations. At the moment, there is a global active network backbone, the ABone, for experiments on active networks. Apart from the immaturity of the executing platform, the primary hindrance on the deployment of active networks on the Internet is more on the commercially related issues. For example, a vendor may hesitate to allow network routers to run some unknown programs that may affect their expected routing performance. As a result, alternatives were proposed to allow active network concept to operate on the Internet, such as the application layer active networking (ALAN) project [4] from the European research community. In the ALAN project, there are active server systems located at different places in the networks and active applications are allowed to run in these servers at the application layer. Another potential approach from the network service provider is to offer active network service as the premium service class in the networks. This service class should provide the best Quality of Service (QoS), and allow the access of computing facility in routers. With this approach, the network service providers can create a new source of income.The research in active networks has been progressing steadily. Since active networks introduce programmability on the Internet, appropriate executing platforms for the active applications to execute should be established. These operating platforms are known as execution environments (EEs) and a few of them have been created, e.g., the Active Signaling Protocol (ASP) [12] and the Active Network Transport System (ANTS) [11]. Hence, different active applications can be implemented to test the active networking concept.With these EEs, some experiments have been carried out to examine the active network concept, for example, the mobile networks [5], web proxies [6], and multicast routers [7]. Active networks introduce a lot of program flexibility and extensibility in networks. Several research groups have proposed various designs of execution environments to offer network computation within routers. Their performance and potential benefits to existing infrastructure are being evaluated [8, 9]. Unfortunately, they seldom concern the interoperability problems when the active networks consist of multiple execution environments. For example, there are three EEs in ABone. Active applications written for one particular EE cannot be operated on other platforms. This introduces another problem of resources partitioning for different EEs to operate. Moreover, there are always some critical network applications that need to run under all network routers, such as collecting information and deploying service at critical points to monitor the networks.In this paper, a framework known as Active Network Socket Programming (ANSP) model is proposed to work with all EEs. It offers the following primary objectives.• One single programming interface is introduced for writing active applications.• Since ANSP offers the programming interface, the design of EE can be made independent of the ANSP.This enables a transparency in developing andenhancing future execution environments.• ANSP addresses the interoperability issues among different execution environments.• Through the design of ANSP, the pros and cons of different EEs will be gained. This may help design abetter EE with improved performance in future.The primary objective of the ANSP is to enable all active applications that are written in ANSP can operate in the ABone testbed . While the proposed ANSP framework is essential in unifying the network environments, we believe that the availability of different environments is beneficial in the development of a better execution environment in future. ANSP is not intended to replace all existing environments, but to enable the studies of new network services which are orthogonal to the designs of execution environments. Therefore, ANSP is designed to be a thin and transparent layer on top of all execution environments. Currently, its deployment relies on automatic code loading with the underlying environments. As a result, the deployment of ANSP at a router is optional and does not require any change to the execution environments.II. D ESIGN I SSUES ON ANSPThe ANSP unifies existing programming interfaces among all EEs. Conceptually, the design of ANSP is similar to the middleware design that offers proper translation mechanisms to different EEs. The provisioning of a unified interface is only one part of the whole ANSP platform. There are many other issues that need to be considered. Apart from translating a set of programming interfaces to other executable calls in different EEs, there are other design issues that should be covered, e.g., • a unified thread library handles thread operations regardless of the thread libraries used in the EEs;• a global soft-store allows information sharing among capsules that may execute over different environmentsat a given router;• a unified addressing scheme used across different environments; more importantly, a routing informationexchange mechanism should be designed across EEs toobtain a global view of the unified networks;• a programming model that should be independent to any programming languages in active networks;• and finally, a translation mechanism to hide the heterogeneity of capsule header structures.A. Heterogeneity in programming modelEach execution environment provides various abstractions for its services and resources in the form of program calls. The model consists of a set of well-defined components, each of them has its own programming interfaces. For the abstractions, capsule-based programming model [10] is the most popular design in active networks. It is used in ANTS [11] and ASP [12], and they are being supported in ABone. Although they are developed based on the same capsule model, their respective components and interfaces are different. Therefore, programs written in one EE cannot run in anther EE. The conceptual views of the programming models in ANTS and ASP are shown in Figure 1.There are three distinct components in ANTS: application, capsule, and execution environment. There exist user interfaces for the active applications at only the source and destination routers. Then the users can specify their customized actions to the networks. According to the program function, the applications send one or more capsules to carry out the operations. Both applications and capsules operate on top of an execution environment that exports an interface to its internal programming resources. Capsule executes its program at each router it has visited. When it arrives at its destination, the application at destination may either reply it with another capsule or presents this arrival event to the user. One drawback with ANTS is that it only allows “bootstrap” application.Figure 1. Programming Models in ASP and ANTS.In contrast, ASP does not limit its users to run “bootstrap” applications. Its program interfaces are different from ANTS, but there are also has three components in ASP: application client, environment, and AAContext. The application client can run on active or non-active host. It can start an active application by simply sending a request message to the EE. The client presents information to users and allows its users to trigger actions at a nearby active router. AAContext is the core of the network service and its specification is divided into two parts. One part specifies its actions at its source and destination routers. Its role is similar to that of the application in ANTS, except that it does not provide a direct interface with the user. The other part defines its actions when it runs inside the active networks and it is similar to the functional behaviors of a capsule in ANTS.In order to deal with the heterogeneity of these two models, ANSP needs to introduce a new set of programming interfaces and map its interfaces and execution model to those within the routers’ EEs.B. Unified Thread LibraryEach execution environment must ensure the isolation of instance executions, so they do not affect each other or accessThe authors appreciate the Nortel Institute for Telecommunications (NIT) at the University of Toronto to allow them to access the computing facilitiesothers’ information. There are various ways to enforce the access control. One simple way is to have one virtual machine for one instance of active applications. This relies on the security design in the virtual machines to isolate services. ANTS is one example that is using this method. Nevertheless, the use of multiple virtual machines requires relatively large amount of resources and may be inefficient in some cases. Therefore, certain environments, such as ASP, allow network services to run within a virtual machine but restrict the use of their services to a limited set of libraries in their packages. For instance, ASP provides its thread library to enforce access control. Because of the differences in these types of thread mechanism, ANSP devises a new thread library to allow uniform accesses to different thread mechanisms.C. Soft-StoreSoft-store allows capsule to insert and retrieve information at a router, thus allowing more than one capsules to exchange information within a network. However, problem arises when a network service can execute under different environments within a router. The problem occurs especially when a network service inserts its soft-store information in one environment and retrieves its data at a later time in another environment at the same router. Due to the fact that execution environments are not allowed to exchange information, the network service cannot retrieve its previous data. Therefore, our ANSP framework needs to take into account of this problem and provides soft-store mechanism that allows universal access of its data at each router.D. Global View of a Unified NetworkWhen an active application is written with ANSP, it can execute on different environment seamlessly. The previously smaller and partitioned networks based on different EEs can now be merging into one large active network. It is then necessary to advise the network topology across the networks. However, different execution environments have different addressing schemes and proprietary routing protocols. In order to merge these partitions together, ANSP must provide a new unified addressing scheme. This new scheme should be interpretable by any environments through appropriate translations with the ANSP. Upon defining the new addressing scheme, a new routing protocol should be designed to operate among environments to exchange topology information. This allows each environment in a network to have a complete view of its network topology.E. Language-Independent ModelExecution environment can be programmed in any programming language. One of the most commonly used languages is Java [13] due to its dynamic code loading capability. In fact, both ANTS and ASP are developed in Java. Nevertheless, the active network architecture shown in Figure 2 does not restrict the use of additional environments that are developed in other languages. For instance, the active network daemon, anted, in Abone provides a workspace to execute multiple execution environments within a router. PLAN, for example, is implemented in Ocaml that will be deployable on ABone in future. Although the current active network is designed to deploy multiple environments that can be in any programming languages, there lacks the tool to allow active applications to run seamlessly upon these environments. Hence, one of the issues that ANSP needs to address is to design a programming model that can work with different programming languages. Although our current prototype only considers ANTS and ASP in its design, PLAN will be the next target to address the programming language issue and to improve the design of ANSP.Figure 2. ANSP Framework Model.F. Heterogeneity of Capsule Header StructureThe structures of the capsule headers are different in different EEs. They carries capsule-related information, for example, the capsule types, sources and destinations. This information is important when certain decision needs to be made within its target environment. A unified model should allow its program code to be executed on different environments. However, the capsule header prevents different environments to interpret its information successfully. Therefore, ANSP should carry out appropriate translation to the header information before the target environment receives this capsule.III. ANSP P ROGRAMMING M ODELWe have outlined the design issues encountered with the ANSP. In the following, the design of the programming model in ANSP will be discussed. This proposed framework provides a set of unified programming interfaces that allows active applications to work on all execution environments. The framework is shown in Figure 2. It is composed of two layers integrated within the active network architecture. These two layers can operate independently without the other layer. The upper layer provides a unified programming model to active applications. The lower layer provides appropriate translation procedure to the ANSP applications when it is processed by different environments. This service is necessary because each environment has its own header definition.The ANSP framework provides a set of programming calls which are abstractions of ANSP services and resources. A capsule-based model is used for ANSP, and it is currently extended to map to other capsule-based models used in ANTSand ASP. The mapping possibility to other models remains as our future works. Hence, the mapping technique in ANSP allows any ANSP applications to access the same programming resources in different environments through a single set of interfaces. The mapping has to be done in a consistent and transparent manner. Therefore, the ANSP appears as an execution environment that provides a complete set of functionalities to active applications. While in fact, it is an overlay structure that makes use of the services provided from the underlying environments. In the following, the high-level functional descriptions of the ANSP model are described. Then, the implementations will be discussed. The ANSP programming model is based upon the interactions between four components: application client , application stub , capsule , and active service base.Figure 3. Information Flow with the ANSP.•Application Client : In a typical scenario, an active application requires some means to present information to its users, e.g., the state of the networks. A graphical user interface (GUI) is designed to operate with the application client if the ANSP runs on a non-active host.•Application Stub : When an application starts, it activates the application client to create a new instance of application stub at its near-by active node. There are two responsibilities for the application stub. One of them is to receive users’ instructions from the application client. Another one is to receive incoming capsules from networks and to perform appropriate actions. Typically, there are two types of actions, thatare, to reply or relay in capsules through the networks, or to notify the users regarding the incoming capsule. •Capsule : An active application may contain several capsule types. Each of them carries program code (also referred to as forwarding routine). Since the application defines a protocol to specify the interactions among capsules as well as the application stubs. Every capsule executes its forwarding routine at each router it visits along the path between the source and destination.•Active Service Base : An active service base is designed to export routers’ environments’ services and execute program calls from application stubs and capsules from different EEs. The base is loaded automatically at each router whenever a capsule arrives.The interactions among components within ANSP are shown in Figure 3. The designs of some key components in the ANSP will be discussed in the following subsections. A. Capsule (ANSPCapsule)ANSPXdr decode () ANSPXdr encode () int length ()Boolean execute ()New types of capsule are created by extending the abstract class ANSPCapsule . New extensions are required to define their own forwarding routines as well as their serialization procedures. These methods are indicated below:The execution of a capsule in ANSP is listed below. It is similar to the process in ANTS.1. A capsule is in serial binary representation before it issent to the network. When an active router receives a byte sequence, it invokes decode() to convert the sequence into a capsule. 2. The router invokes the forwarding routine of thecapsule, execute(). 3. When the capsule has finished its job and forwardsitself to its next hop by calling send(), this call implicitly invokes encode() to convert the capsule into a new serial byte representation. length() isused inside the call of encode() to determine the length of the resulting byte sequence. ANSP provides a XDR library called ANSPXdr to ease the jobs of encoding and decoding.B. Active Service Base (ANSPBase)In an active node, the Active Service Base provides a unified interface to export the available resources in EEs for the rest of the ANSP components. The services may include thread management, node query, and soft-store operation, as shown in Table 1.TABLE I. ACTIVE SERVICE BASE FUNCTION CALLSFunction Definition Descriptionboolean send (Capsule, Address) Transmit a capsule towards its destination using the routing table of theunderlying environment.ANSPAddress getLocalHost () Return address of the local host as an ANSPAddress structure. This isuseful when a capsule wants to check its current location.boolean isLocal (ANSPAddress) Return true if its input argument matches the local host’s address andreturn false otherwise.createThread () Create a new thread that is a class ofANSPThreadInterface (discussed later in Section VIA “Unified Thread Abstraction”).putSStore (key, Object) Object getSStore (key) removeSStore (key)The soft-store operations are provided by putSStore(), getSSTore(), and removeSStore(), and they put, retrieve, and remove data respectively. forName (PathName) Supported in ANSP to retrieve a classobject corresponding to the given path name in its argument. This code retrieval may rely on the code loading mechanism in the environment whennecessary.C. Application Client (ANSPClient)boolean start (args[])boolean start (args[],runningEEs) boolean start (args[],startClient)boolean start (args[],startClient, runningEE)Application Client is an interface between users and the nearby active source router. It does the following responsibilities.1. Code registration: It may be necessary to specify thelocation and name of the application code in some execution environments, e.g., ANTS. 2. Application initialization: It includes selecting anexecution environment to execute the application among those are available at the source router. Each active application can create an application client instance by extending the abstract class, ANSPClient . The extension inherits a method, start(), to automatically handle both the registration and initialization processes. All overloaded versions of start() accept a list of arguments, args , that are passed to the application stub during its initialization. An optional argument called runningEEs allows an application client to select a particular set of environment variables, specified by a list of standardized numerical environment ID, the ANEP ID, to perform code registration. If this argument is not specified, the default setting can only include ANTS and ASP. D. Application Stub (ANSPApplication)receive (ANSPCapsule)Application stubs reside at the source and destination routers to initialize the ANSP application after the application clients complete the initialization and registration processes. It is responsible for receiving and serving capsules from the networks as well as actions requested from the clients. A new instance is created by extending the application client abstract class, ANSPApplication . This extension includes the definition of a handling routine called receive(), which is invoked when a stub receives a new capsule.IV. ANSP E XAMPLE : T RACE -R OUTEA testbed has been created to verify the design correctnessof ANSP in heterogeneous environments. There are three types of router setting on this testbed:1. Router that contains ANTS and a ANSP daemonrunning on behalf of ASP; 2. Router that contains ASP and a ANSP daemon thatruns on behalf of ANTS; 3. Router that contains both ASP and ANTS.The prototype is written in Java [11] with a traceroute testing program. The program records the execution environments of all intermediate routers that it has visited between the source and destination. It also measures the RTT between them. Figure 4 shows the GUI from the application client, and it finds three execution environments along the path: ASP, ANTS, and ASP. The execution sequence of the traceroute program is shown in Figure 5.Figure 4. The GUI for the TRACEROUTE Program.The TraceCapsule program code is created byextending the ANSPCapsule abstract class. When execute() starts, it checks the Boolean value of returning to determine if it is returning from the destination. It is set to true if TraceCapsule is traveling back to the source router; otherwise it is false . When traveling towards the destination, TraceCapsule keeps track of the environments and addresses of the routers it has visited in two arrays, path and trace , respectively. When it arrives at a new router, it calls addHop() to append the router address and its environment to these two arrays. When it finally arrives at the destination, it sets returning to false and forwards itself back to the source by calling send().When it returns to source, it invokes deliverToApp() to deliver itself to the application stub that has been running at the source. TraceCapsule carries information in its data field through the networks by executing encode() and decode(), which encapsulates and de-capsulates its data using External Data Representation (XDR) respectively. The syntax of ANSP XDR follows the syntax of XDR library from ANTS. length() in TraceCapsule returns the data length, or it can be calculated by using the primitive types in the XDRlibrary.Figure 5. Flow of the TRACEROUTE Capsules.V. C ONCLUSIONSIn this paper, we present a new unified layered architecture for active networks. The new model is known as Active Network Socket Programming (ANSP). It allows each active application to be written once and run on multiple environments in active networks. Our experiments successfully verify the design of ANSP architecture, and it has been successfully deployed to work harmoniously with ANTS and ASP without making any changes to their architectures. In fact, the unified programming interface layer is light-weighted and can be dynamically deployable upon request.R EFERENCES[1] D.D. Clark, D.L. Tennenhouse, “Architectural Considerations for a NewGeneration of Protocols,” in Proc. ACM Sigcomm’90, pp.200-208, 1990. [2] D. Tennenhouse, J. M. Smith, W. D. Sicoskie, D. J. Wetherall, and G. J.Minden, “A survey of active network research,” IEEE Communications Magazine , pp. 80-86, Jan 1997.[3] D. Wetherall, U. Legedza, and J. Guttag, “Introducing new internetservices: Why and how,” IEEE Network Magazine, July/August 1998. [4] M. Fry, A. Ghosh, “Application Layer Active Networking,” in ComputerNetworks , Vol.31, No.7, pp.655-667, 1999.[5] K. W. Chin, “An Investigation into The Application of Active Networksto Mobile Computing Environments”, Curtin University of Technology, March 2000.[6] S. Bhattacharjee, K. L. Calvert, and E. W. Zegura, “Self OrganizingWide-Area Network Caches”, Proc. IEEE INFOCOM ’98, San Francisco, CA, 29 March-2 April 1998.[7] L. H. Leman, S. J. Garland, and D. L. Tennenhouse, “Active ReliableMulticast”, Proc. IEEE INFOCOM ’98, San Francisco, CA, 29 March-2 April 1998.[8] D. Descasper, G. Parulkar, B. Plattner, “A Scalable, High PerformanceActive Network Node”, In IEEE Network, January/February 1999.[9] E. L. Nygren, S. J. Garland, and M. F. Kaashoek, “PAN: a high-performance active network node supporting multiple mobile code system”, In the Proceedings of the 2nd IEEE Conference on Open Architectures and Network Programming (OpenArch ’99), March 1999. [10] D. L. Tennenhouse, and D. J. Wetherall. “Towards an Active NetworkArchitecture”, In Proceeding of Multimedia Computing and Networking , January 1996.[11] D. J. Wetherall, J. V. Guttag, D. L. Tennenhouse, “ANTS: A toolkit forBuilding and Dynamically Deploying Network Protocols”, Open Architectures and Network Programming, 1998 IEEE , 1998 , Page(s): 117 –129.[12] B. Braden, A. Cerpa, T. Faber, B. Lindell, G. Phillips, and J. Kann.“Introduction to the ASP Execution Environment”: /active-signal/ARP/index.html .[13] “The java language: A white paper,” Tech. Rep., Sun Microsystems,1998.。
毕业设计(论文)外文资料及译文(模板)

大连东软信息学院
毕业设计(论文)外文资料及译文
系所:
专业:
班级:
姓名:
学号:
大连东软信息学院
Dalian Neusoft University of Information
外文资料和译文格式要求
一、装订要求
1、外文资料原文(复印或打印)在前、译文在后、最后为指导教师评定成绩。
2、译文必须采用计算机输入、打印。
3、A4幅面打印,于左侧装订。
二、撰写要求
1、外文文献内容与所选课题相关。
2、本科学生译文汉字字数不少于4000字,高职学生译文汉字字数不少于2000字。
三、格式要求
1、译文字号:中文小四号宋体,英文小四号“Times New Roman”字型,全文统一,首行缩进2个中文字符,1.5倍行距。
2、译文页码:页码用阿拉伯数字连续编页,字体采用“Times New Roman”字体,字号小五,页底居中。
3、译文页眉:眉体使用单线,页眉说明五号宋体,居中“大连东软信息学院本科毕业设计(论文)译文”。
毕业设计英文翻译(英文)
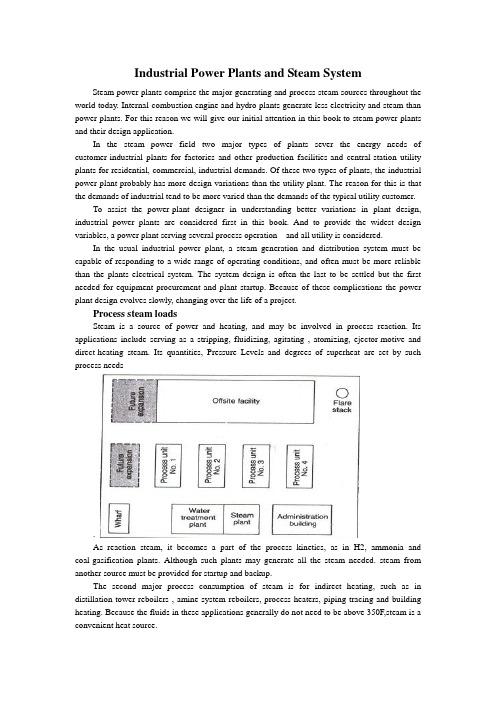
Industrial Power Plants and Steam SystemSteam power plants comprise the major generating and process steam sources throughout the world today. Internal-combustion engine and hydro plants generate less electricity and steam than power plants. For this reason we will give our initial attention in this book to steam power plants and their design application.In the steam power field two major types of plants sever the energy needs of customer-industrial plants for factories and other production facilities-and central-station utility plants for residential, commercial, industrial demands. Of these two types of plants, the industrial power plant probably has more design variations than the utility plant. The reason for this is that the demands of industrial tend to be more varied than the demands of the typical utility customer.To assist the power-plant designer in understanding better variations in plant design, industrial power plants are considered first in this book. And to provide the widest design variables, a power plant serving several process operation and all utility is considered.In the usual industrial power plant, a steam generation and distribution system must be capable of responding to a wide range of operating conditions, and often must be more reliable than the plants electrical system. The system design is often the last to be settled but the first needed for equipment procurement and plant startup. Because of these complications the power plant design evolves slowly, changing over the life of a project.Process steam loadsSteam is a source of power and heating, and may be involved in process reaction. Its applications include serving as a stripping, fluidizing, agitating , atomizing, ejector-motive and direct-heating steam. Its quantities, Pressure Levels and degrees of superheat are set by such process needs.As reaction steam, it becomes a part of the process kinetics, as in H2, ammonia and coal-gasification plants. Although such plants may generate all the steam needed. steam from another source must be provided for startup and backup.The second major process consumption of steam is for indirect heating, such as in distillation-tower reboilers , amine-system reboilers, process heaters, piping tracing and building heating. Because the fluids in these applications generally do not need to be above 350F,steam is a convenient heat source.Again, the quantities of steam required for the services are set by the process design of the facility. There are many options available to the process designer in supplying some of these low-level heat requirements, including heat-exchange system , and circulating heat-transfer-fluid systems, as well as system and electricity. The selection of an option is made early in the design stage and is based predominantly on economic trade-off studies.Generating steam from process heat affords a means of increasing the overall thermal efficiency of a plant. After providing for the recovery of all the heat possible via exchanges, the process designer may be able to reduce cooling requirements by making provisions for the generation of low-pressure(50-150 psig)steam. Although generation at this level may be feasible from a process-design standpoint, the impact of this on the overall steam balance must be considered, because low-pressure steam is excessive in most steam balances, and the generation of additional quantities may worsen the design. Decisions of this type call close coordination between the process and utility engineers.Steam is often generated in the convection section of fired process heaters in order to improve a plant’s thermal efficiency. High-pressure steam can be generated in the furnace convection section of process heater, which have radiant heat duty only.Adding a selective –catalytic-reduction unit for the purpose of lowing NOx emissions may require the generation of waste-heat steam to maintain correct operating temperature to the catalytic-reduction unit.Heat from the incineration of waste gases represents still another source of process steam. Waste-heat flues from the CO boilers of fluid-catalytic crackers and from fluid-coking units, for example, are hot enough to provide the highest pressure level in a steam system.Selecting pressure and temperature levelsThe selecting of pressure and temperature levels for a process steam system is based on:(1)moisture content in condensing-steam turbines,(2)metallurgy of the system,(3)turbine water rates,(4)process requirements ,(5)water treatment costs, and(6)type of distribution system.Moisture content in condensing-steam turbines---The selection of pressure and temperature levels normally starts with the premise that somewhere in the system there will be a condensing turbine. Consequently, the pressure and temperature of the steam must be selected so that its moisture content in the last row of turbine blades will be less than 10-13%. In high speed, a moisture content of 10%or less is desirable. This restriction is imposed in order to minimize erosion of blades by water particles. This, in turn, means that there will be a minimum superheat for a given pressure level, turbine efficiency and condenser pressure for which the system can be designed.System mentallurgy- A second pressure-temperature concern in selecting the appropriate steam levels is the limitation imposed by metallurgy. Carbon steel flanges, for example, are limited to a maximum temperature of 750F because of the threat of graphite (carbides) precipitating at grain boundaries. Hence, at 600 psig and less, carbon-steel piping is acceptable in steam distribution systems. Above 600 psig, alloy piping is required. In a 900- t0 1,500-psig steam system, the piping must be either a r/2 carbon-1/2 molybdenum or a l/2 chromium% molybdenum alloyTurbine water rates - Steam requirements for a turbine are expressed as water rate, i.e., lb of steam/bph, or lb of steam/kWh. Actual water rate is a function of two factors: theoretical water rate and turbine efficiency.The first is directly related to the energy difference between the inlet and outlet of a turbine, based on the isentropic expansion of the steam. It is, therefore, a function of the turbine inlet and outlet pressures and temperatures.The second is a function of size of the turbine and the steam pressure at the inlet, and of turbine operation (i.e., whether the turbine condenses steam, or exhausts some of it to an intermediate pressure level). From an energy stand point, the higher the pressure and temperature, the higher the overall cycle efficiency. _Process requirements - When steam levels are being established, consideration must be given to process requirements other than for turbine drivers. For example, steam for process heating will have to be at a high-enough pressure to prevent process fluids from leaking into the steam. Steam for pipe tracing must be at a certain minimum pressure so that low-pressure condensate can be recovered.Water treatment costs - The higher the steam pressure, the costlier the boiler feedwater treatment. Above 600 psig, the feedwater almost always must be demineralized; below 600 psig, soft,ening may be adequate. It may have to be of high quality if the steam is used in the process, such as in reactions over a catalyst bed (e.g., in hydrogen production).Type of distribution system - There are two types of systems: local, as exemplified by powerhouse distribution; and complex, by wluch steam is distributed to many units in a process plant. For a small local system, it is not impractical from a cost standpoint for steam pressures to be in the 600-1,500-psig range. For a large system, maintaining pressures within the 150-600-psig range is desirable because of the cost of meeting the alloy requirements for higher-pressure steam distribution system.Because of all these foregoing factors, the steam system in a chemical process complex or oil refinery frequently ends up as a three-level arrangement. The highest level, 600 psig, serves primarily as a source of power. The intermediate level, 150 psig, is ideally suitable for small emergency turbines, tracing off the plot, and process heating. The low level, normally 50 psig, can be used for heating services, tracing within the plot, and process requirements. A higher fourth level normally not justified, except in special cases as when alarge amount ofelectric power must be generated.Whether or not an extraction turbine will be included in the process will have a bearing on the intermediate-pressure level selected, because the extraction pressure should be less than 50% of the high-pressure level, to take into account the pressure drop through the throttle valve and the nozzles of the high-pressure section of' the turbine.Drivers for pumps and compressorsThe choice between a steam and an electric driver for a particular pump or compressor depends on a number of things, including the operational philosophy. In the event of a power failure, it must be possible to shut down a plant orderly and safely if normal operation cannot be continued. For an orderly and safe shutdown, certain services must be available during a power failure: (1) instrument air, (2) cooling water, (3) relief and blow down pump out systems, (4) boiler feedwater pumps, (5) boiler fans, (6) emergency power generators, and (7) fire water pumps.These services are normally supplied by steam or diesel drivers because a plant's steam or diesel emergency system is considered more reliable than an electrical tie-line.The procedure for shutting down process units must be analyzed for each type of processplant and specific design. In general, the following represent the minimum services for which spare pumps driven by steam must be provided: column reflux, bottoms and purge-oil circulation, and heater charging. Most important is to maintain cooling; next, to be able to safely pump the plant's inventory into tanks.Driver selection cannot be generalized; a plan and procedure must be developed for each process unit.The control required for a process is at times another consideration in the selection of a driver. For example, a compressor may be controlled via flow or suction pressure. The ability to vary driver speed, easily obtained with a steam turbine, may be basis for selecting a steam driver instead of a constant-speed induction electric motor. This is especially important when the molecular weight of the gas being compressed may vary, as in catalytic-cracking and catalytic-reforming processes.In certain types of plants, gas flow must be maintained to prevent uncontrollable high-temperature excursions during shutdown. For example, hydrocrackers are purged of heavy hydrocarbon with recycle gas to prevent the exothermic reactions from producing high bed temperatures. Steam-driven compressors can do this during a power failure.Each process operation must be analyzed from such a safety viewpoint when selecting drivers for critical equipment. The size of a relief and blowdown system can be reduced by installing steam drivers. In most cases, the size of such a system is based on a total power failure. If heat-removal powered by steam drivers, the relief system can be smaller. For example, a steam driver will maintain flow in the pump-around circuit for removing heat from a column during a power failure, reducing the relief load imposed on the flare system.Equipment support services (such as lubrication and sea-oil systems for compressors) that could be damaged during a loss of power should also be powered by steam drivers.Driver size can also be a factor. An induction electric motor requires large starting currents - typically six times the normal load. The drop in voltage caused by the startup of such a motor imposes a heavy transient demand on the electrical distribution system. For this reason, drivers larger than 10,000 hp are normally steam turbines, although synchronous motors as large as 25,000 hp are used.The reliability of life-support facilities - e.g., building heat, potable water, pipe tracing, emergency lighting-during power failures is of particular concern mates. In such a case, at least one boiler should be equipped with steam-driven auxiliaries to provide these services.Lastly, steam drivers are also selected for the purpose of balancing steam systems and avoiding large amounts of letdown between steam levels. Such decisions regarding drivers are made after the steam balances have been refined and the distribution system has been fully defined. There must be sufficient flexibility to allow balancing the steam system under all operating conditions.Selecting steam driversAfter the number of steam drivers and their services have been established, the utility, or process engineer will estimate the steam consumption for making the steam balance.The standard method of doing this is to use the isentropic expansion of steam correeted for turbine efficiency.Actual steam consumption by a turbine is determined via:SR = (TSR)(bhp)/EHere, SR = actual steam rate, lb/h; TSR = theoretical steam rate, lb/hr/bhp ; bhp = turbine brake horsepower; and E = turbine efficiency.When exhaust steam can be used for process heating, the highest thermodynamic efficiency can be achieved by means of backpressure turbines. Large drivers, which are of high efficiency and require low theoretical steam rates, are normally supplied by the high-pressure header, thus minimizing steam consumption.Small turbines that operate only in emergencies can be allowed to exhaust to atmosphere. Although their water rates are poor, the water lost in short-duration operations may not represent a significant cost. Such turbines obviously play a small role in steam balance planning.Constructing steam balancesAfter the process and steam-turbine demands have been established, the next step is to construct a steam balance for the chemical complex or oil refinery. A sample balance is shown in Fig. 1-4. It shows steam production and consumption, the header systems, letdown stations, and boiler plant. It illustrates a normal (winter) case.It should be emphasized that there is not one balance but a series, representing a variety of operating modes. The object of the balances is to determine the design basis for establishing boiler she, letdown stations and deaerator capacities, boiler feedwater requirements, and steam flows in various parts of the system.The steam balance should cover the following operating modes: normal, all units operating; winter and summer conditions; shutdown of major units; startup of major units; loss of largest condensate source; power failure with flare in service; loss of large process steam generators; and variations in consumption by large steam users.From 50 t0 100 steam balances could be required to adequately cover all the major impacts on the steam system of a large complex.At this point, the general basis of the steam system design should have been developed by the completion of the following work:1. All significant loads have been examined, with particular attention focused on those for which there is relatively little design freedom - i.e., reboilers, sparing steam for process units, large turbines required because of electric power limitation and for shutdown safety.2. Loads have been listed for which the designer has some liberty in selecting drivers. These selections are based on analyses of cost competitiveness.3. Steam pressure and temperature levels have been established.4. The site plan has been reviewed to ascertain where it is not feasible to deliver steam or recover condensate, because piping costs would be excessive.5. Data on the process units are collected according to the pressure level and use of steam - i.e., for the process, condensing drivers and backpressure drivers.6. After Step 5, the system is balanced by trial-and-error calculations or computerized techniques to determine boiler, letdown, deaerator and boiler feedwater requirements.7. Because the possibility of an electric power failure normally imposes one of the major steam requirements, normal operation and the eventuality of such a failure must both be investigated, as a minimum.Checking the design basisAfter the foregoing steps have been completed, the following should be checked:Boiler capacity - Installed boiler capacity would be the maximum calculated (with an allowance of l0-20% for uncertainties in the balance), corrected for the number of boilers operating (and on standby).The balance plays a major role in establishing normal-case boiler specifications, both number and size. Maximum firing typically is based on the emergency case. Normal firing typically establishes the number of boilers required, because each boiler will have to be shut down once a year for the code-required drum inspection. Full-firing levels of the remaining boilers will be set by the normal steam demand. The number of units required (e.g., three 50% units, four 33%units, etc.) in establishing installed boiler capacity is determined from cost studies. It is generally considered double-jeopardy design to assume that a boiler will be out of service during a power failure.Minimum boiler turndown - Most fuel-fired boilers can be operated down to approximately 20% of the maximum continuous rate. The maximum load should not be expected to be below this level.Differences between normal and maximum loads –If the maximum load results from an emergency (such as power failure), consideration should be given to shedding process steam loads under this condition in order to minimize in- stalled boiler capacity. However, the consequences of shedding should be investigated by the process designer and the operating engineers to ensure the safe operation of the entire process.Low-level steam consumption - The key to any steam balance is the disposition of low-level steam. Surplus low-level steam can be reduced only by including more condensing steam turbines in the system, or devising more process applications for it, such as absorption refrigeration for cooling process streams and ranking-cycle systems for generating power. In general, balancing the supply and consumption of low-level steam is a critical factor in the design of the steam system.Quantity of steam at pressure-reducing stations - Because useful work is not recovered from the steam passing through a pressure-reducing station, such flow should be kept at a minimum. In the Fig. 1-5 150/50-psig station, a flow of only 35,000 lb/h was established as normal for this steam balance case (normal, winter). The loss of steam users on the 50-psig systems should be considered, particularly of the large users, because a shutdown of one may demand that the 150/50-psig station close off beyond its controllable limit. If this happened, the 50-psig header would be out of control, and an immediate-pressure buildup in the header wouldbegin, setting off the safety relief valves.The station's full-open capacity should also be checked to ensure that it can make up any 50-psig steam that may be lost through the shutdown of a single large 50-psig source (a turbine sparing a large electric motor, for example}. It would be undesirable for the station to be sized so that it opens more than 80%. In some cases, range ability requirements may dictate two valves (one small and one large).Intermediate pressure level - If large steam users or suppliers may come on stream or go off steam, the normal(day-to-day) operation should be checked. No such change in normal operation should result in a significant upset (e.g.,relief valves set off, or the system pressure control lost).If a large load is lost, the steam supply should be reduced by the letdown-station. If the load suddenly increases, the 600/150-psig station must be able of supplying the additional steam. If steam generated via the process disappears, the station must be capable of making up theload. If150-psig steam is generated unexpectedly, the 600/150-psig station must be able to handle the cutback.The important point here is that where the steam flow could rise t0 700,000 lb/h, this flow should be reduced by a cutback at the 600/150-psig station, not by an increase in the flow to the lower-pressure level, because this steam would have nowhere to go. The normal (600/150-psig) letdown station must be capable of handling some of the negative load swings, even though, overall, this letdown needs to be kept to a minimum.On the other hand, shortages of steam at the 150-psig level can be made up relatively easily via the 600/150-psig station. Such shortages are routinely small in quantity or duration, or both-(startup, purging, electric drive maintenance, process unit shutdown, etc.)High-pressure level - Checking the high-pressure level is generally more straightforward because rate control takes place directly at the boilers. Firing can be increased or lowered to accommodate a shortage or surplus.Typical steam-balance casesThe Fig. 1-4 steam balance represents steady-state condition, winter operation, all process units operating, and no significant unusual demands for steam.An analysis similar to the foregoing might also be required for the normal summertime case, in which a single upset must not jeopardize control but the load may be less (no tank heating, pipe tracing, etc.)The balance representing an emergency (e.g., loss of electric power) is significant. In this case, the pertinent test point is the system's ability to simply weather the upset, not to maintain normal, stable operation. The maximum relief pressure that would develop in any of the headers represents the basis for sizing relief valves. The loss of boiler feed water or condensate return, or both, could result in a major upset, or even a shutdown.Header pressure control during upsetsAt the steady-state conditions associated with the multiplicity of balances, boiler capacity can be adjusted to meet user demands. However, boiler load cannot be changed quickly to accommodate a sharp upset. Response rate is typically limited to 20% of capacity per minute. Therefore, other elements must be relied on to control header pressures during transient conditions.The roles of several such elements in controlling pressures in the three main headers during transient conditions are listed in Table l-3. A control system having these elements will result in a steam system capable of dealing with the transient conditions experienced in moving from one balance point to another.Tracking steam balancesBecause of schedule constraints, steam balances and boiler size are normally established early in the design stage. These determinations are based on assumptions regarding turbine efficiencies, process steam generated in waste-heat furnaces, and other quantities of steam that depend on purchased equipment. Therefore, a sufficient number of steam balances should be tracked through the design period to ensure that the equipment purchased will satisfy the original design concept of the steam system.This tracking represents an excellent application for a utility data-base system and a system linear programming model. During the course of the mechanical design of a large "grass roots" complex, 40 steam balances were continuously updated for changes in steam loads via such an application.Cost tradeoffsTo design an efficient but least-expensive system, the designer ideally develops a total minimum-cost curve – which incorporates all the pertinent costs related to capital expenditures, installation, fuel, utilities, operations and maintenance-and performs a cost study of the final system. However, because the designer is under the constraint of keeping to a project schedule, major, highly expensive equipment must be ordered early in the project, when many key parts of the design puzzle are not available (e.g., a complete load summary, turbine water rates, equipment efficiencies and utility costs).A practical alternative is to rely on comparative-cost estimates, as are conventionally used in assisting with engineering decision points. This approach is particularly useful in making early equipment selections when fine-tuning is not likely to alter decisions, such as regarding the number of boilers required, whether boilers should be shop-fabricated or field-erected, and the practicality of generating steam from waste heat or via cogeneration.The significant elements of a steam-system cost-comparative study are costs for: equipment and installation; ancillaries (i.e., miscellaneous items required to support the equipment,such as additional stacks, upgraded combustion control, more extensive blowdown facilities, etc.); operation(annual); maintenance (annual); and utilities.The first two costs may be obtained from in-house data or from vendors. Operational and maintenance costs can be factored from the capital cost for equipment based on an assessment of the reliability of the purchased equipment.Utility costs are generally the most difficult to establish at an early stage because sources frequently depend on the site of the plant. Some examples of such costs are: purchased fuel gas - $5.35/million Btu, raw water - $0.60/1,000 gal, electricity - $0.07{kWh, and demineralized boiler feedwater -$1.50/1,000 gal. The value of steam at the various pressureLevels can be developed [5J.Let it be further assumed that the emergency balance requires 2,200,000 lb/h of steam (all boilers available). Listed in Table 1 4 are some combinations of boiler installations that meet the design conditions previously stipulated.Table l-4 indicates that any of the several combinations of power-boiler number and size could meet both normal and emergency demand. Therefore, a comparative-cost analysis would be made to assist in making an early decision regarding the number and size of the power boilers.(Table l-4 is based on field-erected, industrial-type boiler Conventional sizing of this type of boiler might range from 100,000 lb/h through 2,000,000 lb/h for each.)An alternative would be the packaged boiler option (although it does not seem practical at this load level. Because it is shop-fabricated, this type of boiler affords a significant saving in terms of field installation cost. Such boilers are available up to a nominal capacity of 100,000 lb/h, with some versions up t0 250,000 lb7h.Selecting turbine water rate i.e., efficiency) represents another major cost concern. Beyond the recognized payout period (e.g., 3 years), the cost of drive steam can be significant in comparison with the equipment capital cost. The typical 30% efficiency ofthe medium-pressure backpressure turbine can be boosted significantly.Driver selections are frequently made with the help of cost-tradeoff studies, unless overriding considerations preclude a drive medium. Electric pump drives are typically recommended on the basis of such studies.Steam tracing has long been the standard way of winterizing piping, not only because of its history of successful performance but also because it is an efficient way to use low-pressure steam.Design consideratonsAs the steam system evolves, the designer identifies steam loads and pressure levels, locates steam loads, checks safety aspects, and prepares cost-tradeoff studies, in order to provide low-cost energy safely, always remaining aware of the physical entity that will arise from the design.How are design concepts translated into a design document? And what basic guidelines will ensure that the physical plant will represent what was intended conceptually?Basic to achieving these ends is the piping and instrument diagram (familiar as the P&ID). Although it is drawn up primarily for the piping designers benefit, it also plays a major role in communicating to the instrumentation designer the process-control strategy, as well as in conveying specialty information to electrical, civil, structural, mechanical and architectural engineers. It is the most important document for representing the specification of the steam。
本科毕业设计的英文资料与中文翻译

英文资料与中文翻译IEEE 802.11 MEDIUM ACCESS CONTROLThe IEEE 802.11 MAC layer covers three functional areas:reliable data delivery, medium access control, and security. This section covers the first two topics.Reliable Data DeliveryAs with any wireless network, a wireless LAN using the IEEE 802.11 physical and MAC layers is subject to considerable unreliability. Noise, interference, and other propagation effects result in the loss of a significant number of frames. Even with error-correction codes, a number of MAC frames may not successfully be received. This situation can be dealt with by reliability mechanisms at a higher layer. such as TCP. However, timers used for retransmission at higher layers are typically on the order of seconds. It is therefore more efficient to deal with errors at the MAC level. For this purpose, IEEE 802.11 includes a frame exchange protocol. When a station receives a data frame from another station. It returns an acknowledgment (ACK) frame to the source station. This exchange is treated as an atomic unit, not to be interrupted by a transmission from any other station. If the source does not receive an ACK within a short period of time, either because its data frame was damaged or because the returning ACK was damaged, the source retransmits the frame.Thus, the basic data transfer mechanism in IEEE802.11 involves an exchange of two frames. To further enhance reliability, a four-frame exchange may be used. In this scheme, a source first issues a request to send (RTS) frame to the destination. The destination then responds with a clear to send (CTS). After receiving the CTS, the source transmits the data frame, and the destination responds with an ACK. The RTS alerts all stations that are within reception range of the source that an exchange is under way; these stations refrain from transmission in order to avoid a collision between two frames transmitted at the same time. Similarly, the CTS alerts all stations that are within reception range of the destination that an exchange is under way. The RTS/CTS portion of the exchange is a required function of the MAC but may be disabled.Medium Access ControlThe 802.11 working group considered two types of proposals for a MAC algorithm: distributed access protocols, which, like Ethernet, distribute the decision to transmit over all the nodes using a carrier-sense mechanism; and centralized access protocols, which involve regulation of transmission by a centralized decision maker. A distributed access protocol makes sense for an ad hoc network of peer workstations (typically an IBSS) and may also be attractive in other wireless LAN configurations that consist primarily of burst traffic. A centralized access protocol is natural for configurations in which a umber of wireless stations are interconnected with each other and some sort of base station that attaches to a backbone wired LAN: it is especially useful if some of the data is time sensitive or high priority.The end result for 802.11 is a MAC algorithm called DFWMAC (distributed foundation wireless MAC) that provides a distributed access control mechanism with an optional centralized control built on top of that. Figure 14.5 illustrates the architecture. The lower sub-layer of the MAC layer is the distributed coordination function (DCF). DCF uses a contention algorithm to provide access to all traffic. Ordinary asynchronous traffic directly uses DCE. The point coordination function (PCF) is a centralized MAC algorithm used to provide contention-free service. PCF is built on top of DCF and exploits features of DCF to assure access for its users. Let us consider these two sub-layers in turn.MAClayerFigure 14.5 IEEE 802.11 Protocol ArchitectureDistributed Coordination FunctionThe DCF sub-layer makes use of a simple CSMA (carrier sense multiple access) algorithm, which functions as follows. If a station has a MAC frame to transmit, it listens to the medium. If the medium is idle, the station may transmit; otherwise the station must wait until the current transmission is complete before transmitting. The DCF does not include a collision detection function (i.e. CSMA/CD) because collision detection is not practical on a wireless network. The dynamic range of the signals on the medium is very large, so that a transmitting station cannot effectively distinguish incoming weak signals from noise and the effects of its own transmission.To ensure the smooth and fair functioning of this algorithm, DCF includes a set of delays that amounts to a priority scheme. Let us start by considering a single delay known as an inter-frame space (IFS). In fact, there are three different IFS values, but the algorithm is best explained by initially ignoring this detail. Using an IFS, the rules for CSMA access are as follows (Figure 14.6):Figure 14.6 IEEE 802.11 Medium Access Control Logic1. A station with a frame to transmit senses the medium. If the medium is idle. It waits to see if the medium remains idle for a time equal to IFS. If so , the station may transmit immediately.2. If the medium is busy (either because the station initially finds the medium busy or because the medium becomes busy during the IFS idle time), the station defers transmission and continues to monitor the medium until the current transmission is over.3. Once the current transmission is over, the station delays another IFS. If the medium remains idle for this period, then the station backs off a random amount of time and again senses the medium. If the medium is still idle, the station may transmit. During the back-off time, if the medium becomes busy, the back-off timer is halted and resumes when the medium becomes idle.4. If the transmission is unsuccessful, which is determined by the absence of an acknowledgement, then it is assumed that a collision has occurred.To ensure that back-off maintains stability, a technique known as binary exponential back-off is used. A station will attempt to transmit repeatedly in the face of repeated collisions, but after each collision, the mean value of the random delay is doubled up to some maximum value. The binary exponential back-off provides a means of handling a heavy load. Repeated failed attempts to transmit result in longer and longer back-off times, which helps to smooth out the load. Without such a back-off, the following situation could occur. Two or more stations attempt to transmit at the same time, causing a collision. These stations then immediately attempt to retransmit, causing a new collision.The preceding scheme is refined for DCF to provide priority-based access by the simple expedient of using three values for IFS:●SIFS (short IFS):The shortest IFS, used for all immediate responseactions,as explained in the following discussion●PIFS (point coordination function IFS):A mid-length IFS, used by thecentralized controller in the PCF scheme when issuing polls●DIFS (distributed coordination function IFS): The longest IFS, used as aminimum delay for asynchronous frames contending for access Figure 14.7a illustrates the use of these time values. Consider first the SIFS.Any station using SIFS to determine transmission opportunity has, in effect, the highest priority, because it will always gain access in preference to a stationwaiting an amount of time equal to PIFS or DIFS. The SIFS is used in the following circumstances:●Acknowledgment (ACK): When a station receives a frame addressed onlyto itself (not multicast or broadcast) it responds with an ACK frame after, waiting on1y for an SIFS gap. This has two desirable effects. First, because collision detection IS not used, the likelihood of collisions is greater than with CSMA/CD, and the MAC-level ACK provides for efficient collision recovery. Second, the SIFS can be used to provide efficient delivery of an LLC protocol data unit (PDU) that requires multiple MAC frames. In this case, the following scenario occurs. A station with a multi-frame LLC PDU to transmit sends out the MAC frames one at a time. Each frame is acknowledged after SIFS by the recipient. When the source receives an ACK, it immediately (after SIFS) sends the next frame in the sequence. The result is that once a station has contended for the channel, it will maintain control of the channel until it has sent all of the fragments of an LLC PDU.●Clear to Send (CTS):A station can ensure that its data frame will getthrough by first issuing a small. Request to Send (RTS) frame. The station to which this frame is addressed should immediately respond with a CTS frame if it is ready to receive. All other stations receive the RTS and defer using the medium.●Poll response: This is explained in the following discussion of PCF.longer than DIFS(a) Basic access methodasynchronous trafficdefers(b) PCF super-frame constructionFigure 14.7 IEEE 802.11 MAC TimingThe next longest IFS interval is the: PIFS. This is used by the centralized controller in issuing polls and takes precedence over normal contention traffic. However, those frames transmitted using SIFS have precedence over a PCF poll.Finally, the DIFS interval is used for all ordinary asynchronous traffic.Point C00rdination Function PCF is an alternative access method implemented on top of the DCE. The operation consists of polling by the centralized polling master (point coordinator). The point coordinator makes use of PIFS when issuing polls. Because PI FS is smaller than DIFS, the point coordinator call seize the medium and lock out all asynchronous traffic while it issues polls and receives responses.As an extreme, consider the following possible scenario. A wireless network is configured so that a number of stations with time, sensitive traffic are controlled by the point coordinator while remaining traffic contends for access using CSMA. The point coordinator could issue polls in a round—robin fashion to all stations configured for polling. When a poll is issued, the polled station may respond using SIFS. If the point coordinator receives a response, it issues another poll using PIFS. If no response is received during the expected turnaround time, the coordinator issues a poll.If the discipline of the preceding paragraph were implemented, the point coordinator would lock out all asynchronous traffic by repeatedly issuing polls. To prevent this, an interval known as the super-frame is defined. During the first part of this interval, the point coordinator issues polls in a round, robin fashion to all stations configured for polling. The point coordinator then idles for the remainder of the super-frame, allowing a contention period for asynchronous access.Figure l4.7 b illustrates the use of the super-frame. At the beginning of a super-frame, the point coordinator may optionally seize control and issues polls for a give period of time. This interval varies because of the variable frame size issued by responding stations. The remainder of the super-frame is available for contention based access. At the end of the super-frame interval, the point coordinator contends for access to the medium using PIFS. If the medium is idle. the point coordinator gains immediate access and a full super-frame period follows. However, the medium may be busy at the end of a super-frame. In this case, the point coordinator must wait until the medium is idle to gain access: this result in a foreshortened super-frame period for the next cycle.OctetsFC=frame control SC=sequence controlD/I=duration/connection ID FCS=frame check sequence(a ) MAC frameBitsDS=distribution systemMD=more data MF=more fragmentsW=wired equivalent privacy RT=retryO=orderPM=power management (b) Frame control filedFigure 14.8 IEEE 802.11 MAC Frame FormatMAC FrameFigure 14.8a shows the 802.11 frame format when no security features are used. This general format is used for all data and control frames, but not all fields are used in all contexts. The fields are as follows:● Frame Control: Indicates the type of frame and provides contr01information, as explained presently.● Duration/Connection ID: If used as a duration field, indicates the time(in-microseconds) the channel will be allocated for successful transmission of a MAC frame. In some control frames, this field contains an association, or connection, identifier.●Addresses: The number and meaning of the 48-bit address fields dependon context. The transmitter address and receiver address are the MAC addresses of stations joined to the BSS that are transmitting and receiving frames over the wireless LAN. The service set ID (SSID) identifies the wireless LAN over which a frame is transmitted. For an IBSS, the SSID isa random number generated at the time the network is formed. For awireless LAN that is part of a larger configuration the SSID identifies the BSS over which the frame is transmitted: specifically, the SSID is the MAC-level address of the AP for this BSS (Figure 14.4). Finally the source address and destination address are the MAC addresses of stations, wireless or otherwise, that are the ultimate source and destination of this frame. The source address may be identical to the transmitter address and the destination address may be identical to the receiver address.●Sequence Control: Contains a 4-bit fragment number subfield used forfragmentation and reassembly, and a l2-bit sequence number used to number frames sent between a given transmitter and receiver.●Frame Body: Contains an MSDU or a fragment of an MSDU. The MSDUis a LLC protocol data unit or MAC control information.●Frame Check Sequence: A 32-bit cyclic redundancy check. The framecontrol filed, shown in Figure 14.8b, consists of the following fields.●Protocol Version: 802.11 version, current version 0.●Type: Identifies the frame as control, management, or data.●Subtype: Further identifies the function of frame. Table 14.4 defines thevalid combinations of type and subtype.●To DS: The MAC coordination sets this bit to 1 in a frame destined to thedistribution system.●From DS: The MAC coordination sets this bit to 1 in a frame leaving thedistribution system.●More Fragments: Set to 1 if more fragments follow this one.●Retry: Set to 1 if this is a retransmission of a previous frame.●Power Management: Set to]if the transmitting station is in a sleep mode.●More Data: Indicates that a station has additional data to send. Each blockof data may be sent as one frame or a group of fragments in multiple frames.●WEP:Set to 1 if the optional wired equivalent protocol is implemented.WEP is used in the exchange of encryption keys for secure data exchange.This bit also is set if the newer WPA security mechanism is employed, as described in Section 14.6.●Order:Set to 1 in any data frame sent using the Strictly Ordered service,which tells the receiving station that frames must be processed in order. We now look at the various MAC frame types.Control Frames Control frames assist in the reliable delivery of data frames. There are six control frame subtypes:●Power Save-Poll (PS-Poll): This frame is sent by any station to the stationthat includes the AP (access point). Its purpose is to request that the AP transmit a frame that has been buffered for this station while the station was in power saving mode.●Request to Send (RTS):This is the first frame in the four-way frameexchange discussed under the subsection on reliable data delivery at the beginning of Section 14.3.The station sending this message is alerting a potential destination, and all other stations within reception range, that it intends to send a data frame to that destination.●Clear to Send (CTS): This is the second frame in the four-way exchange.It is sent by the destination station to the source station to grant permission to send a data frame.●Acknowledgment:Provides an acknowledgment from the destination tothe source that the immediately preceding data, management, or PS-Poll frame was received correctly.●Contention-Free (CF)-End: Announces the end of a contention-freeperiod that is part of the point coordination function.●CF-End+CF-Ack:Acknowledges the CF-End. This frame ends thecontention-free period and releases stations from the restrictions associated with that period.Data Frames There are eight data frame subtypes, organized into two groups. The first four subtypes define frames that carry upper-level data from the source station to the destination station. The four data-carrying frames are as follows: ●Data: This is the simplest data frame. It may be used in both a contentionperiod and a contention-free period.●Data+CF-Ack: May only be sent during a contention-free period. Inaddition to carrying data, this frame acknowledges previously received data.●Data+CF-Poll: Used by a point coordinator to deliver data to a mobilestation and also to request that the mobile station send a data frame that it may have buffered.●Data+CF-Ack+CF-Poll: Combines the functions of the Data+CF-Ack andData+CF-Poll into a single frame.The remaining four subtypes of data frames do not in fact carry any user data. The Null Function data frame carries no data, polls, or acknowledgments. It is used only to carry the power management bit in the frame control field to the AP, to indicate that the station is changing to a low-power operating state. The remaining three frames (CF-Ack, CF-Poll,CF-Ack+CF-Poll) have the same functionality as the corresponding data frame subtypes in the preceding list (Data+CF-Ack, Data+CF-Poll, Data+CF-Ack+CF-Poll) but withotit the data. Management FramesManagement frames are used to manage communications between stations and APs. The following subtypes are included:●Association Request:Sent by a station to an AP to request an association,with this BSS. This frame includes capability information, such as whether encryption is to be used and whether this station is pollable.●Association Response:Returned by the AP to the station to indicatewhether it is accepting this association request.●Reassociation Request: Sent by a station when it moves from one BSS toanother and needs to make an association with tire AP in the new BSS. The station uses reassociation rather than simply association so that the new AP knows to negotiate with the old AP for the forwarding of data frames.●Reassociation Response:Returned by the AP to the station to indicatewhether it is accepting this reassociation request.●Probe Request: Used by a station to obtain information from anotherstation or AP. This frame is used to locate an IEEE 802.11 BSS.●Probe Response: Response to a probe request.●Beacon: Transmitted periodically to allow mobile stations to locate andidentify a BSS.●Announcement Traffic Indication Message: Sent by a mobile station toalert other mobile stations that may have been in low power mode that this station has frames buffered and waiting to be delivered to the station addressed in this frame.●Dissociation: Used by a station to terminate an association.●Authentication:Multiple authentication frames are used in an exchange toauthenticate one station to another.●Deauthentication:Sent by a station to another station or AP to indicatethat it is terminating secure communications.IEEE802.11 媒体接入控制IEEE 802.11 MAC层覆盖了三个功能区:可靠的数据传送、接入控制以及安全。
毕业设计英文作文范文

毕业设计英文作文范文Title: The Importance of the Graduation Project in Academic Development。
The graduation project holds a pivotal role in the academic journey of students. It serves as a culmination of years of learning, a platform to showcase acquired skills, and an opportunity to delve deep into a specific subject matter. In this essay, I will elaborate on the significance of the graduation project and its impact on academic development.Firstly, the graduation project fosters independent learning and critical thinking skills. Unlike regular coursework where the parameters are often well-defined, the graduation project requires students to identify a research question or a problem statement independently. This process necessitates thorough literature review, data collection, and analysis, thereby honing research and analytical abilities. Moreover, formulating hypotheses, designingexperiments, or proposing solutions demand creativethinking and problem-solving skills, which are essentialfor academic and professional success.Secondly, the graduation project encourages interdisciplinary learning and collaboration. Many projects involve aspects from various fields, prompting students to integrate knowledge acquired from different courses. This interdisciplinary approach not only enriches the project but also broadens students' perspectives, enabling them to appreciate the interconnectedness of different subjects. Furthermore, collaboration with peers, mentors, or industry professionals enhances teamwork, communication, and project management skills, which are indispensable in any academic or professional setting.Additionally, the graduation project cultivates resilience and perseverance. Research, by its nature, is fraught with challenges, setbacks, and uncertainties. Students encounter obstacles ranging from experimental failures to data inconsistencies, requiring them to adapt, troubleshoot, and persist in the face of adversity.Overcoming these hurdles instills resilience and fortitude, attributes that are invaluable not only in academia but also in life.Moreover, the graduation project offers a platform for personal and intellectual growth. It provides students with the autonomy to explore topics of their interest, delveinto uncharted territories, and push the boundaries of knowledge. This journey of self-discovery not only enhances academic curiosity but also fosters a sense of ownership and accomplishment. Furthermore, presenting findings, defending arguments, and receiving feedback during project evaluations contribute to the development of presentation, communication, and critical evaluation skills, which are essential for academic and professional success.In conclusion, the graduation project is a cornerstone of academic development, offering students a unique opportunity to apply theoretical knowledge to real-world problems, fostering independent learning, interdisciplinary collaboration, resilience, and personal growth. By engaging in this endeavor, students not only demonstrate theiracademic prowess but also equip themselves with essential skills and attributes for future endeavors. Therefore, the graduation project stands as a testament to the culmination of academic journey and the beginning of a new chapter in students' intellectual and professional pursuits.。
毕业设计电动车电池参考文献英文

IntroductionElectric vehicles (EVs) have gained significant attention in recent years due to their potential to reduce greenhouse gas emissions and dependence on fossil fuels. The battery is a crucial component of an electric vehicle, as it provides the energy required for propulsion. A well-designed and efficient battery system is essential for the success of an EV.This research paper aims to explore the various aspects of electric vehicle batteries for a graduation project on electric vehicle battery design. The paper discusses the different types of batteries used in electric vehicles, their characteristics, advantages, and challenges. Additionally, it touches upon the battery management system, charging infrastructure, and future advancements in electric vehicle batteries.Types of Electric Vehicle Batteries1.Lithium-ion Batteries: Lithium-ion batteries are the mostcommonly used batteries in electric vehicles due to their highenergy density, long cycle life, and lightweight characteristics.They provide a good balance between performance, cost, and safety.A comprehensive investigation of the structure, working principle,and limitations of lithium-ion batteries is essential fordesigning an optimized battery system.2.Nickel-Metal Hydride (Ni-MH) Batteries: Ni-MH batteries werewidely used in electric vehicles before the emergence of lithium-ion batteries. They offer a relatively lower energy density thanlithium-ion batteries but have better thermal stability, whichensures safer operation. A comparative analysis between lithium-ion and Ni-MH batteries can aid in choosing the appropriatebattery for the design project.3.Solid-State Batteries: Solid-state batteries are a promisingalternative to traditional lithium-ion batteries. They utilizesolid electrolytes instead of liquid electrolytes, providinghigher energy density, improved safety, and faster chargingcapabilities. Although still under development, solid-statebatteries hold great potential for the future of electric vehicles.Battery Management System (BMS)The Battery Management System (BMS) is responsible for monitoring and controlling the battery’s performance, safety, and lifespan. A well-designed BMS ensures the optimal operation of the battery system, preventing overcharging, undercharging, and excessive discharge. It provides accurate state-of-charge (SOC) and state-of-health (SOH) estimations, which are crucial for maximizing the battery’s efficiency.The BMS consists of various components, including sensors, control algorithms, and battery balancing circuits. In-depth research on BMS architecture, functionality, and control strategies is necessary to design an effective battery management system for the electric vehicle.Charging InfrastructureThe availability of a robust charging infrastructure is essential for widespread adoption and convenience of electric vehicles. The research project should explore the different types of charging stations, including:1.Level 1 Charging: Level 1 charging refers to standard householdoutlets (120V), which provide a slow charging rate but are widely accessible.2.Level 2 Charging: Level 2 charging utilizes dedicated chargingstations (240V). It offers a faster charging rate compared toLevel 1 and is commonly found in residential areas, workplaces,and public charging stations.3.DC Fast Charging: DC Fast Charging, also known as Level 3charging, provides rapid charging capabilities by directlydelivering DC power to the vehicle’s battery. These chargingstations are typically located along highways and major routes.The paper should discuss the importance of a well-established charging infrastructure and address potential challenges and solutions to the deployment of charging stations.Future AdvancementsThe field of electric vehicle batteries is continuously evolving, with ongoing research and advancements. It is crucial for the researchproject to explore future developments, such as:1.Advanced Lithium-ion Batteries: Researchers are constantlyworking on improving the energy density, charging speed, andsafety of lithium-ion batteries. Advancements in materials,electrode designs, and electrolytes are expected to result in more efficient and long-lasting batteries.2.Solid-State Batteries: As mentioned earlier, solid-statebatteries hold immense potential for the future of electricvehicles. The research should discuss the current challenges faced in commercializing solid-state batteries and potentialbreakthroughs that can lead to their widespread adoption.3.Beyond Lithium-ion: Besides solid-state batteries, alternativebattery chemistries like lithium-sulfur (Li-S) and lithium-air(Li-Air) batteries are being explored for their high energydensities. Understanding these emerging battery technologies canpave the way for future advancements in EV batteries.ConclusionDesigning an efficient and reliable battery system is crucial for the success of an electric vehicle. This research paper provides a comprehensive and detailed analysis of different types of electric vehicle batteries, their characteristics, and the importance of a well-designed battery management system and charging infrastructure. Furthermore, it explores future advancements in electric vehicle battery technologies. By understanding these aspects, the research project can aim to design an optimized electric vehicle battery system that contributes to a sustainable and greener transportation future.Note: The content provided above is a suggested structure for the research paper related to the topic of “Graduation Project - Electric Vehicle Battery”. Please add relevan t and specific details from appropriate academic references to complete the paper.。
毕业设计外文资料

THE SECOND MAINTENANCE AND STRENGTHENING OF YONGHEBRIDGE IN TIANJINHongjiang LI1,Feng Zhang2, Pingxia Niu2, Shoukai Zhang21) Research Institute of Highway, the Ministry of Communications2) Geotechnology and Structure Engineering Research Center, Shandong University Abstract: Tension rocker bearing (TRB) cables installed at auxiliary piers were critical members to sustain the structural system in a prestressed concrete cable-stayed bridge. Once these cables fractured or broken, its structural system would change. Based on defects caused by fracture of TRB cables in Yonghe Bridge, corresponding maintenance or strengthening measures were described in detail. These measures included replacement of TRB cables, strengthening of the closure segment of main girder at each side span, and ad-justment of stay cable forces. Monitoring results showed that, its structural system was finally and completely rehabilitated, and the safety factor of new TRB cables is enough under the most unfavorable load combina-tion. Moreover, the line shape of main girder and the inclined displacement at the top of each pylon were im-proved effectively. Thus, Yonghe Bridge accumulated some valuable experience for maintenance and/or strengthening of existing prestressed concrete cable-stayed bridges, and also made a useful exploration.1. INTRODUCTIONMaintenance or strengthening of existing prest-ressed concrete (PC) cable-stayed bridges has become one of difficult but hot engineering issues in China (Zhang, 2007). In the past 15 years, China has accumulated some valuable ex-periences in this area, such as stay cable replace-ment in Jinan Yellow River Highway Bridge (Wang, 2006), stay cable force adjustment in Guangdong Jiujiang Bridge (Li, 2000), strengthen-ing of main girder in Ningbo Zhaobaoshan Bridge (Lin, 2001) and so on. However, traditional main-tenance concepts and strengthening approaches are being challenged due to complexity, diversity and severity of diseases in existing PC cable-stayed bridges. Based on the second maintenance and strengthening of Yonghe Bridge in Tianjin, some new technologies, including replacement of ten-sion rocker bearing (TRB) cables at its auxiliary piers, strengthening of the closure segment of its main girder at side spans etc., are presented in this paper. These will provide new trials or explora-tions for maintenance or strengthening of existing PC cable-stayed bridges.2. OVERVIEW OF YONGHE BRIDGEYonghe Bridge was the earliest and the most representative precast concrete segmental cable-stayed bridge in China. It had one continuous and floatable main girder with 5 spans, and the length of main span was 260 meters (see Fig.1).Also, it was a suspended structural system with double pylons, which were fixed with the piers, and double cable planes. Its cross section of main girderis typical of P-K form (see Fig.2).Figure 1. Elevation of Yonghe bridge.Figure 2. Typical section of main girderStay cables of whole bridge were fan-type and totalled 44 pairs or 176 bundles. Pot-type rubber compression bearings and TRB cables were at the same time set at its auxiliary piers. Thus, the up-ward reaction force was provided by the compres-sion bearings and the downward one by TRB ca-bles. Each TRB cable was actually a short tension-only cable (see Fig.3), formed by 139 high-strength steel wires of 5 mm in diameter. Its exter-nal protection was a hot extrusion polythene sheath with cement paste grouted inside. Its bottom hinged end was spliced by steel plates, and its top hinged end was fixed on main girder. And the de-signed longitudinal floating distance at its top end was ±0.25m.468469Figure 3. TRB cable at each auxiliary pierYonghe Bridge was completed in December, 1987. Then and there, its girder segments were pre-cast by match casting and erected on scaffoldings at side spans and by cantilever-splicing at middle spans. At both sides of each cable tower, girder segments were symmetrically spliced and then rele-vant cables were suspended. One segment was spliced with another segment by the epoxy resin glue. At the same time, prestressed steel bars (cold drawn steel, Grade Ⅳ) were strained and length-ened. After 7 pairs of cables in each half bridge were finished, the cantilever part of main girder firstly closed with the side span, which erected on scaffoldings. After 11 pairs of cables in each half bridge were finished, the two half cantilever parts were finally closed. All closure segments were cast in-situ. The design length of closure segment at each side span was 1.05m and the one at its main span was 4.3m.In the Year 2006, Yonghe Bridge experienced the first maintenance and strengthening (Li et al., 2009). The main measures included replacement and strengthening of the closure segment at its main span, line shape adjustment of main girder, re-placement of stay cables and force adjustment of new cables. After all these measures were finished, a loading test was conducted. Test results showed that, deflection of main girder and concrete stress of main girder under every loading case were con-formed to corresponding calculated values, and the structural system was consistent to the original de-signed structural mode of 5 continuous spans. TRB cables performed well and were in good condition at that time.3. DESCRIPTION OF STRUCTURAL DISEASESIn the Year 2008, TRB cables at auxiliary piers of Yonghe Bridge fractured due to wire corrosion and long-term overloading (see Fig.4) (Li, 2009a). The disengaging distance between the top of com-pression bearing and the bottom of main girderreached 2.5 cm only under dead load. When sub-jected to vehicle loads, its main girder floated up-ward and downward, and the detected floating amplitude was up to 10 cm (see Fig.5).Figure 4. Fracture of the TRB cableFigure 5. Disengaging between the compressionbearing and main girderAccompanied with fracture of TRB cables, the concrete closure segment of its main girder at the south side span crushed (see Fig.6) whereas the one at its north side span had relatively slight deficien-cies.Figure 6. Crushing of the closure segment of thesouth side spanComparing with the structural state after the first maintenance and strengthening for this bridge, there was a significant deflection at its main span.The deflection of mid-span reached 12.7 cm (see Fig.7). Longitudinal horizontal displacement at the top of each pylon increased towards to river side470evidently. The displacement at the top of south pylon changed 4.7 cm, and the north one changed 4.1 cm.Figure 7. Line shape change of main girder inYonghe bridgeAbove diseases were formed mainly due to structural system transformation after fracture of TRB cables. And then under overloading, concrete stress at the bottom of the closure segment at its south side span increased abruptly and then finally crushed. Subsequently, under alternative and repeated vehicle loads, the rigidity of its main girder lowered and the corresponding plastic deformations accumulated with service time. Finally significant deflection occurred at the its main span, and mean-while, the upward deformations generated at its side spans, which eventually led to the disengaging be-tween the compression bearing and its main girder.4. MAINTENANCE AND STRENGTHEN-ING MEASURES4.1 Replacing TRB Cables and Streng-thening of the Closure Segment at Side SpansThe number of steel wires of each new TRB cable was designed at this time to be the same as that of the original design of Yonghe Bridge, but the ultimate fracture force of steel wires increased by 11%. Water tanks, served as temporary weights, were applied at deck near the closure segment of each side span to eliminate the disengaging distance between the compression bearing and main girder. Besides, new TRB cables were installed and their initial tensioning were controlled to ensure the con-tact between the top of compression bearing and the bottom of main girder to be in compacted state and fasten components of each TRB cable.Different strengthening ways were adopted respectively for the closure segment of its south andnorth side span. For the south one, epoxy concrete or epoxy mortar was used to repair the crushed re-gion, and then reinforced it with externally longitudinally bonded steel plates of 10 mm in thickness at both its bottom slabs and inclined webs (see Fig.8).Figure 8. Externally bonded steel plates at thecrushed closure segmentIn order to compensate itself and its adjacent segments, the Enlarging Cross Section Method was used at vertical webs of the south closure segment and its adjacent segments. Vertical webs were thickened 54 cm with concrete of higher grade. Within the thickened concrete, unbonded external prestressing tendons were arranged and stretched to locally reinforce the main girder (see Fig.9).Figure 9. Strengthening of local girder segments byexternal prestressingFor the closure segment at the north side span, only external bonded steel plates were used at bottom slabs and inclined webs like that of the south one.The whole construction procedure of above measures could be described in sequence as fol-lows:1) Removing all old TRB cables and installing new ones.2) Gradually applying temporary weight (to-taled 300 kN) at deck near the south side span to eliminate the disengaging distance between the top of compression bearing and the bottom of main girder.3) Erecting temporary support at the wind fair-ing near the south closure segment.4) Gradually increasing the temporary weight to 600 kN at deck near the south side span to make the main girder fixed vertically, which was used to balance thermal deformation and create a stable condition for repairing the south closure segment.5) Initially stretching and then anchoring TRB cables at the south auxiliary pier.6) Repairing the south closure segment and re-inforcing it with externally bonded steel plates.7) Gradually applying temporary weight (to-taled 300 kN) at deck near the north side span to eliminate the disengaging distance between the top of compression bearing and the bottom of main girder.8) Initially stretching and then anchoring TRB ca bles at the north auxiliary pier.9) Strengthening the south closure segment with Enlarging Cross Section Method.10) Removing all temporary weight at deck.11) Strengthening the south closure segment by external prestressing and the north one by externally bonded steel plates.4.2 Stay Cable Force Adjustment4.2.1 Adjustment objectivesAccording to construction monitoring results after replacement of TRB cables and strengthening of the closure segment at side spans, differences between the current structural state and the one after the first maintenance and strengthening for Yonghe Bridge were analyzed, and then objectives of stay cable force adjustment are determined as follows:1) Through adjustment, the displacements to-wards river side at the top of pylons should be de-creased. The displacement change towards bank side at both pylons was determined by 4.0 cm at least. In other words, both pylons must keep vertical or inclined slightly to bank side.2) The uplift displacement at mid-span must reach 13.0 cm at least to improve the line shape of main girder.4.2.2 Adjustment principlesTo ensure the safety factor of stay cable itself and consider simultaneously reasonability of other structural indexes, some principles must be fol-lowed for the stay cable force adjustment as below:1) The safety factor of stay cable must meet the requirement of current cable-stayed bridge codes after adjustment.2) The adjustment must regard the line shape of main girder and the displacement at the top of each pylon as the guiding principle.3) The adjustment should consider changes of structural reaction forces, especially should relievethe bearing burden of TRB cables at auxiliary piers.After adjustment, the safety factor of each TRB ca-ble under the most unfavourable load combination must reach 3.0 or above.4) Based on calculation, the adjustment schemeof stay cable force should be optimized moderately.The scheme with smaller adjustment amplitude and fewer adjustment cable numbers should be adopted.4.2.3 Adjustment schemeUsing the theory of Influence Matrix Method (Yang, 2009), the relativity between stay cable forces and structural indexes was studied, and then cable numbers for adjustment were firstly deter-mined. Then trial and iterative calculations were used to determine the adjustment sequence and op-timize relative schemes. The final adjustment scheme was listed in Table 1.Table 1. Stay cable force adjustment scheme. adjustment se-quencestay cable numberstay cable forceincrement*(kN)SC2' +320 Step1SC2' +280 Step2 SC8' +400SC9' +800 Step3NC9' +800SC10' +800 Step4NC10' +800SC11' +800SC11 +560NC11 +560 Step5NC11' +800 * Stay cable force increment means an incremental value based on the current cable force.5. EFFECT ANALYSIS5.1 Tensile Forces of TRB CablesDuring the second maintenance and strengthen-ing of Yonghe Bridge,measured tensile forces ofTRB cables were listed in Table 2. It could be shown that the adjustment of stay cable forces decreased the initial tensions of TRB cables, and sotheir bearing burdens were reduced. It was calcu-lated that the south and north TRB cables’ safety factors under the most unfavorable load combina-tion reached 3.4 and 3.2 respectively, which satis-fied the need of bearing capacity.471Table 2. Measured axial forces of TRB cables.Load cases South* North* after stretching of all TRB cables(kN)1350 1650 after removal of all temporaryweight at deck (kN)1510 1800 after completion of externalprestressing at the south side span(kN)1230 1710 after stay cable adjustment (kN) 1020 1390* each value in this table was the summation of all TRB cables at the same side span.5.2 Line Shape of Main GirderDuring the second maintenance and strengthen-ing of Yonghe Bridge, the measured line shapes of main girder corrected by thermal effect (Li, 2009b) were shown as Fig.10.Figure 10. Measured line shape of main girder in the second maintenance and strengthen-ingFrom Fig.10, it could be shown that, replace-ment of TRB cables and strengthening of the clo-sure segments at side spans not only eliminated up-ward deformation of main girder at side spans (or disengaging distance between the compression bearing and main girder), but also deduced the de-flection at mid-span of the main span, in which up-lift value at mid-span reached 9.3 cm caused by these measures. Thereafter, the displacement at mid-span of the main span kept upward, in which uplift value at mid-span reached 9.0cm caused by the adjustment of stay cable force merely.When all maintenance and strengthening meas-ures were completed, original deflection (see Fig.7) at mid-span was completely eliminated, and further-more a little uplift displacement was reserved. Con-sequently, the line shape of main girder of Yonghe Bridge was significantly improved after the second maintenance and strengthening.5.3 Inclined Displacement at the Top of PylonsMeasured values of the longitudinal horizontal displacements at the top of each pylon corrected by thermal effect (Li, 2009b) were listed in Table 3. It can be shown that inclined displacements of both pylons changed toward bank sides after the second maintenance and strengthening. Therefore, the trend of inclination to river side at both pylons was re-versed. Thus, the structural state of pylons was im-proved obviously.Table 3. Inclined displacements at the top of pylons before and after the Second Maintenanceand strengthening.PylonBefore(Marchٛ16,2009,7:30)After(September 14,2009,5:40)Displace-mentchange* South0.0670 m 0.0172 m -0.0498 m North0.0540 m -0.0043 m -0.0583 m* the displacement is positive when inclined to river side. 5.4 Stay Cable ForceAfter the second maintenance and strengthen-ing, the safety factor of each stay cable of Yonghe Bridge reached 2.4 or above under the most unfa-vourable load combination, and met the requirement of current cable-stayed codes (CPC, 2007).6. CONCLUSIONSDefects of Yonghe Bridge were rather severe, and the conversion of structural system and damage of partial members were involved. Thus its mainte-nance and strengthening difficulty was great. Through the second maintenance and strengthening of Yonghe Bridge, the following conclusions can be obtained:1) TRB cables at auxiliary piers were important members to sustain the structural system for a PC cable-stayed bridge. Once these cables fractured, its structural system would be transferred, which was extremely detrimental to the structural safety. Therefore, the recovery or replacement of TRB ca-bles should be the first maintenance measure to re-habilitate its structural system, and then secondary diseases could be treated to restore the structural rigidity and bearing capacity of whole bridge.2) Under the premise of ensuring the safety fac-tor of each stay cable force itself, adjustment of stay cable force is effective measure to improve the structural state of existing PC cable-stayed bridges.3) There were many construction procedures in the second maintenance and strengthening of Yonghe Bridge, and thus effective monitoring was very important, especially for those temperature-dependent indexes, such as line shape of main472girder, longitudinal horizontal displacements at the top of each pylon, etc. These indexes directly reflect structural state changes, and decide the objective and direction of maintenance or strengthening. Be-sides, measurement of stay cable force is a key for maintenance or strengthening of a PC cable-stayed bridge and it decides the adjustment amplitude and precision of stay cable forces. ACKNOWLEDGEMENTSThis work is sponsored by the Science and Technology Project for Western Transportation Construction in China (200731822340), founded by the Ministry of Communications of China. REFERENCESChina Communications Press (CPC). 2007. Guide-lines for Design of Highway Cable-stayed Bridge, Beijing.Lin G X, Qin S Q, and Zhu H M, et al. 2001. De-sign for the strengthening and rehabilitation ofZhaobaoshan Bridge in Ningbo. Bridge Construction, 31(3):pp.18-21.Li G X, Deng S Y, and Xiao W, et al. 2000. Calcu-lation method for cable force adjustment in Jiu-jiang Bridge. Guangdong Highway Communi-cations, 26(s1):pp.176-178. Li H J, Li W H, and Zhang J Q, et al. 2009. Reha-bilitation and strengthening of Yonghe Bridge inTianjin. World Bridges, 37(1):pp.53-56.Li H J. 2009. Fracture mechanism analysis of ten-sion rocker bearing cables at the subsidiary pier in a PC cable-stayed bridge. The proceed-ings of the 18th national conference on struc-tural engineering, Guangzhou, China: pp.465-470.Li H J. 2009. Temperature effect analysis for struc-tural state estimation of PC cable-stayed bridges. Journal of Civil, Architectural and En-vironmental Engineering, 31(5):pp.81-85. Wang W T. 2006. “Chapter 2: Typical Engineering examples of cable replacement.” Replacementof Stay Cables for Cable-stayed Bridges, ChinaCommunications Press, Beijing: pp.53-68. Yang X, ZhangM, Zhou Sh. 2009. Application of influence matrix method to secondary cable-adjustment of cable-stayed bridges. Journal ofChongqing Jiaotong University (Natural Sci-ence), 28(3):pp.508-511.Zhang J Q, Wang W T. 2007. “Section 3: Strength-ening of steel bridges and cable-supported bridges.” Handbook of inspection and strength-ening for bridges (Volume 2), China Commu-nications Press, Beijing: pp.926-943.473。
毕业设计作品英文

毕业设计作品英文Graduation ProjectThe completion of a graduation project is a significant milestone in the academic journey of a student. It represents the culmination of years of hard work, dedication, and the acquisition of knowledge and skills. The graduation project serves as a platform for students to demonstrate their mastery of a particular subject or field, and to showcase their ability to conduct independent research, analyze data, and present their findings in a coherent and compelling manner.The process of undertaking a graduation project is often a challenging and rewarding experience. It requires students to delve deeply into a topic of their choice, to critically analyze existing research and theories, and to develop their own unique perspectives and solutions. Throughout this process, students are expected to work closely with faculty advisors, who provide guidance, support, and feedback to ensure the success of the project.One of the key aspects of a graduation project is the ability toconduct thorough and rigorous research. This involves reviewing relevant literature, identifying gaps in existing knowledge, and formulating a research question or hypothesis that can be explored through empirical investigation. Students must then design and implement a research methodology that is appropriate for their topic, and collect and analyze data using a variety of qualitative and quantitative techniques.In addition to research skills, the graduation project also requires strong writing and communication abilities. Students must be able to articulate their ideas clearly and concisely, and to present their findings in a well-organized and coherent manner. This often involves the creation of a written thesis or dissertation, as well as the development of visual aids and presentations that can be used to effectively communicate their work to a wider audience.Throughout the graduation project process, students are also expected to demonstrate their ability to think critically and to solve complex problems. This may involve the development of innovative solutions to real-world challenges, or the application of theoretical concepts to practical scenarios. By engaging in this process, students gain valuable experience in problem-solving, decision-making, and critical thinking, all of which are essential skills for success in their future careers.One of the most rewarding aspects of the graduation project is the opportunity for students to make a meaningful contribution to their field of study. Through their research and analysis, students may uncover new insights or develop novel approaches that can be applied to address pressing social, economic, or environmental issues. This sense of making a difference can be a powerful motivator for students, and can inspire them to continue pursuing their passions and interests long after the completion of their graduation project.Despite the challenges and demands of the graduation project, many students find the experience to be deeply fulfilling and transformative. The process of conducting independent research, developing new skills, and presenting their work to a wider audience can be a source of immense pride and accomplishment. Moreover, the skills and knowledge gained through the graduation project can serve as a foundation for future academic and professional pursuits, and can open up a world of new opportunities for students as they embark on the next chapter of their lives.In conclusion, the graduation project is a crucial component of the academic experience, one that challenges students to push the boundaries of their knowledge and capabilities. Through this process, students develop a deeper understanding of their chosen field, hone their critical thinking and problem-solving skills, and make ameaningful contribution to the broader academic and professional community. For those who embrace the challenges and opportunities of the graduation project, the rewards can be truly transformative, shaping their future trajectories and opening up new avenues for personal and professional growth.。
大学本科毕业设计--英文原文+中文翻译

Library of C the CNC industrialdeveloped tens of thousands and educational field, he hasNUMERICAL CONTROLNumerical Control technology as it is known today, emerged in the mid 20th century. It can be traced to the year of 1952, the U.S. Air Force, and the names of John Parsons and the Massachusetts Institute of Technology in Cam-bridge, MA, USA. It was not applied in production manu-facturing until the early 1960's. The real boom came in the form of CNC, around the year of 1972, and a decade later with the introduction of affordable micro computers. The history and development of this fascinating technology has been well documented in many publications.In the manufacturing field, and particularly in the area of metal working, Numerical Control technology has caused something of a revolution. Even in the days before comput-ers became standard fixtures in every company and in many homes, the2machine tools equipped with Numerical Control system found their special place in the machine shops. The recent evolution of micro electronics and the never ceasing computer development, including its impact on Numerical Control, has brought significant changes to the manufacturing sector in general and metalworking in-dustry in particular.DEFINITION OF NUMERICAL CONTROLIn various publications and articles, many descriptions have been used during the years, to define what Numerical Control is. It would be pointless to try to find yet another definition, just for the purpose of this handbook. Many of these definitions share the same idea, same basic concept, just use different wording.The majority of all the known definitions can be summed up into a relatively simple statement:Numerical Control can be defined as an operation of machine tools by the means of specifically coded instructions to the machine control systemThe instructions are combinations of the letters of alpha-bet, digits and selected symbols, for example, a decimal point, the percent sign or the parenthesis symbols. All in-structions are written in a logical order and a predetermined form. The collectionNUMERICAL CONTROLof all instructions necessary to ma-chine a part is called an NC Program, CNC Program, or a Part Program. Such a program can be stored for a future use and used repeatedly to achieve identical machining re-sults at any time.♦ NC and CNC TechnologyIn strict adherence to the terminology, there is a differ-ence in the meaning of the abbreviations NC and CNC. The NC stands for the older and original Numerical Control technology, whereby the abbreviation CNC stands for the newer Computerized Numerical Control technology, a modem spin-off of its older relative. However, in practice, CNC is the preferred abbreviation. To clarify the proper us-age of each term, look at the major differences between the NC and the CNC systems.Both systems perform the same tasks, namely manipula-tion of data for the purpose of machining a part. In both cases, the internal design of the control system contains the logical instructions that process the data. At this point the similarity ends. The NC system (as opposed to the CNC system) uses a fixed logical functions, those that are built-in and perma-nently wired within the control unit. These functions can-not be changed by the programmer or the machine opera-tor. Because of the fixed4wiring of the control logic, the NC control system is synonymous with the term 'hardwired'. The system can interpret a part program, but it does not al-low any changes to the program, using the control features. All required changes must be made away from the control, typically in an office environment. Also, the NC system re-quires the compulsory use of punched tapes for input of the program information.The modem CNC system, but not the old NC system, uses an internal micro processor (i.e., a computer). This computer contains memory registers storing a variety of routines that are capable of manipulating logical functions. That means the part programmer or the machine operator can change the program on the control itself (at the ma-chine), with instantaneous results. This flexibility is the greatest advantage of the CNC systems and probably the key element that contributed to such a wide use of the tech-nology in modern manufacturing. The CNC programs and the logical functions are stored on special computer chips, as software instructions, rather than used by the hardware connections, such as wires, that control the logical func-tions. In contrast to the NC system, the CNC system is syn-onymous with the term 'softwired'.NUMERICAL CONTROLWhen describing a particular subject that relates to the numerical control technology, it is customary to use either the term NC or CNC. Keep in mind that NC can also mean CNC in everyday talk, but CNC can never refer to the older technology, described in this handbook under the abbrevia-tion ofNC. The letter 'C 'stands for Computerized, and it is not applicable to the hardwired system. All control systems manufactured today are of the CNC design. Abbreviations such as C&C or C'n 'C are not correct and reflect poorly on anybody that uses them.CONVENTIONAL AMD CNC MACHININGWhat makes the CNC machining superior to the conven-tional methods? Is it superior at all? Where are the main benefits? If the CNC and the conventional machining pro-cesses are compared, a common general approach to ma-chining a part will emerge: Obtain and study the drawingSelect the most suitable machining methodDecide on the setup method (work holding)Select the cutting toolsEstablish speeds and feedsMachine the part6This basic approach is the same for both types of machin-ing. The major difference is in the way how various data are input. A feedrate of 10 inches per minute (10 in/min) is the same in manual or CNC applications, but the method of applying it is not. The same can be said about a coolant - it can be activated by turning a knob, pushing a switch or programming a special code. All these actions will result in a coolant rushing out of a nozzle. In both kinds of machin-ing, a certain amount of knowledge on the part of the user is required. After all, metal working, particularly metal cut-ting, is mainly a skill, but it is also, to a great degree, an art and a profession of large number of people. So is theappli-cation of Computerized Numerical Control. Like any skill or art or profession, mastering it to the last detail is neces-sary to be successful. It takes more than technical knowl-edge to be a CNC machinist or a CNC programmer. Work experience and intuition, and what is sometimes called a 'gut-feel', is a much needed supplement to any skill.In a conventional machining, the machine operator sets up the machine and moves each cutting tool, using one or both hands, to produce the required part. The design of a manual machine tool offers many features that help the process of machining a part -NUMERICAL CONTROLlevers, handles, gears and di-als, to name just a few. The same body motions are re-peated by the operator for every part in the batch. However, the word 'same 'in this context really means'similar 'rather than 'identical'. Humans are not capable to repeat every process exactly the same at all times - that is the job ofma-chines. People cannot work at the same performance level all the time, without a rest. All of us have some good andsome bad moments. The results of these moments, when*applied to machining a part, are difficult to predict. There will be some differences and inconsistencies within each batch of parts. The parts will not always be exactly the same. Maintaining dimensional tolerances and surface fin-ish quality are the most typical problems in conventional machining. Individual machinists may have their own time 'proven' methods, different from those of their fellow col-leagues. Combination of these and other factors create a great amount of mconsistency.The machining under numerical control does away with the majority of inconsistencies. It does not require the same physical involvement as manual machining. Numerically controlled machining does not need any levers or dials or handles, at least8not in the same sense as conventional ma-chining does. Once the part program has been proven, it can be used any number of times over, always returning consistent results. That does not mean there are no limiting factors. The cutting tools do wear out, the material blank in one batch is not identical to the material blank in another batch, the setups may vary, etc. These factors should be considered and compensated for, whenever necessary.The emergence of the numerical control technology does not mean an instant, or even a long term, demise of all man-ual machines. There are times when a traditional machin-ing method is preferable to a computerized method. For ex-ample, a simple one time job may be done more efficiently on a manual machine than a CNC machine. Certain types of machining jobs will benefit from manual or semiauto-matic machining, rather than numerically controlled ma-chining. The CNC machine tools are not meant to replace every manual machine, only to supplement them.In many instances, the decision whether certain machin-ing will be done on a CNC machine or not is based on the number of required parts and nothing else. Although the volume of partsNUMERICAL CONTROLmachined as a batch is always an important criteria, it should never be the only factor. Consideration should also be given to the part complexity, its tolerances, the required quality of surface finish, etc. Often, a single complex part will benefit from CNC machining, while fifty relatively simple parts will not.Keep in mind that numerical control has never machined a single part by itself. Numerical control is only a process or a method that enables a machine tool to be used in a pro-ductive, accurate and consistent way.NUMERICAL CONTROL ADVANTAGESWhat are the main advantages of numerical control?It is important to know which areas of machining will benefit from it and which are better done the conventional way. It is absurd to think that a two horse power CNC mill will win over jobs that are currently done on a twenty times more powerful manual mill. Equally unreasonable are ex-pectations of great improvements in cutting speeds and feedrates over a conventional machine. If the machining and tooling conditions are the same, the cutting time will be very close in both cases.Some of the major areas where the CNC user can and should expect improvement:10Setup time reductionLead time reductionAccuracy and repeatabilityContouring of complex shapesSimplified tooling and work holdingConsistent cutting timeGeneral productivity increaseEach area offers only a potential improvement. Individ-ual users will experience different levels of actual improve-ment, depending on the product manufactured on-site, the CNC machine used, the setup methods, complexity of fixturing, quality of cutting tools, management philosophy and engineering design, experience level of the workforce, individual attitudes, etc.Setup Time ReductionIn many cases, the setup time for a CNC machine can be reduced, sometimes quite dramatically. It is important to realize that setup is a manual operation, greatly dependent on the performance of CNC operator, the type of fixturing and general practices of the machine shop. Setup time is unproductive, but necessary - it is a part of the overhead costs of doing business. To keep the setupNUMERICAL CONTROLtime to a mini-mum should be one of the primary considerations of any machine shop supervisor, programmer and operator. Because of the design of CNC machines, the setup time should not be a major problem. Modular fixturing, standard tooling, fixed locators, automatic tool changing, pallets and other advanced features, make the setup time more efficient than a comparable setup of a conventional machine. With a good knowledge of modern manufacturing, productivity can be increased significantly.The number of parts machined under one setup is also important, in order to assess the cost of a setup time. If a great number of parts is machined in one setup, the setup cost per part can be very insignificant. A very similar re-duction can be achieved by grouping several different oper-ations into a single setup. Even if the setup time is longer, it may be justified when compared to the time required to setup several conventional machines.Lead Time ReductionOnce a part program is written and proven, it is ready to be Bsed again in the future, even at a short notice. Although the lead time for the first run is usually longer, it is virtually nil for any subsequent run. Even if an engineering change of the part design12requires the program to be modi tied, it can be done usually quickly, reducing the lead time.Long lead time, required to design and manufacture sev-eral special fixtures for conventional machines, can often be reduced by preparing a part program and the use of sim-plified fixturing. Accuracy and RepeatabilityThe high degree of accuracy and repeatability of modern CNC machines has been the single major benefit to many users. Whether the part program is stored on a disk or in the computer memory, or even on a tape (the original method), it always remains the same. Any program can be changed at will, but once proven, no changes are usually required any more. A given program can be reused as many times as needed, without losing a single bit of data it contains. True, program has to allow for such changeable factors as tool wear and operating temperatures, it has to be stored safely, but generally very little interference from the CNC pro-grammer or operator will be required. The high accuracy of CNC machines and their repeatability allows high quality parts to be produced consistently time after time. Contouring of Complex ShapesNUMERICAL CONTROLCNC lathes and machining centers are capable of con-touring a variety of shapes. Many CNC users acquired their machines only to be able to handle complex parts. A good examples are CNC applications in the aircraft and automo-tive industries. The use of some form of computerized pro-gramming is virtually mandatory for any three dimensional tool path generation.Complex shapes, such as molds, can be manufactured without the additional expense of making a model for trac-ing. Mirrored parts can be achieved literally at the switch of a button. Storage of programs is a lot simpler than storage of patterns, templates, wooden models, and other pattern making tools.Simplified Tooling and Work HoldingNonstandard and 'homemade' tooling that clutters the benches and drawers around a conventional machine can be eliminated by using standard tooling, specially designed for numerical control applications. Multi-step tools such as pilot drills, step drills, combination tools, counter borers and others are replaced with several individual standard tools. These tools are often cheaper and easier to replace than special and nonstandard tools.Cost-cutting measures have forced many tool suppliers to keep a low or even a nonexistent inventory, increasing the delivery lime14to the customer. Standard, off-the-shelf tooling can usually beob-tained faster then nonstandard tooling.Fixturing and work holding for CNC machines have only one major purpose - to hold the part rigidly and in the same position for all parts within a batch. Fixtures designed for CNC work do not normally require jigs, pilot holes and other hole locating aids.♦ Cutting Time and Productivity IncreaseThe cutting time on the CNC machine is commonly known as the cycle time - and is always consistent. Unlike a conventional machining, where the operator's skill, experi-ence and personal fatigue are subject to changes, the CNC machining is under the control of a computer. The small amount of manual work is restricted to the setup andload-ing and unloading the part. For large batch runs, the high cost of the unproductive time is spread among many parts, making it less significant. The main benefit of a consistent cutting time is for repetitive jobs, where the production scheduling and work allocation to individual machine tools can be done very accurately.The main reason companies often purchase CNCma-chines is strictly economic - it is a serious investment. Also, having a competitive edge is always on the mind of every plant manager. The numerical control teclmology offers excellent means to achieve a significant improvement in the manufacturing productivity and increasing the overall quality of the manufactured parts. Like any means, it has to be used wisely and knowledgeably. When more and more companies use the CNCtechnology, just having a CNC machine does not offer the extra edge anymore. Thecom-panies that get forward are those who know how to use the technology efficiently and practice it to be competitive in the global economy.To reach the goal of a major increase in productivity, it is essential that users understand the fundamental principles on which CNC technology is based. These principles take many forms, for example, understanding the electronic cir-cuitry, complex ladder diagrams, computer logic, metrol-ogy, machine design, machining principles and practices and many others. Each one has to be studied and mastered by the person in charge. In this handbook, the emphasis is on the topics that relate directly to the CNC programming and understanding the most common CNC machine tools, the Machining Centers and the lathes (sometimes also called the Turning Centers). The part quality consideration should be very important to every programmer and ma-chine tool operator and this goal is also reflected in the handbook approach as well as in the numerous examples.TYPES OF CNC MACHINE TOOLSDifferent kinds of CNCmachines cover an extremelylarge variety. Their numbersare rapidly increasing, as thetechnology developmentadvances. It is impossible toiden-tify all the applications,they would make a long list.Here is a brief list of some ofthe groups CNC machines canbe part of: *Mills and Machining centersLathes and Turning CentersDrilling machines CNC machining centers andlathes dominate the number ofinstallations in industry. Thesetwo groups share the marketjust about equally. Someindustries may have a higherneed for one group ofmachines, depending on their □ Boring mills and Profilers □ EDM machines □ Punch presses and Shears □ Flame cutting machines □ Routers □ Water jet and Laser profilers □ Cylindrical grinders □ Welding machines □ Benders, Winding and Spinning machines, etc.needs. One must remember that there are many different kinds of ladies and equally many different kinds ofma-chining centers. However, the programming process for a vertical machine is similar to the one for a horizontalma-chine or a simple CNC mill. Even between differentma-chine groups, there is a great amount of general applica-tions and the programming process is generally the same. For example, a contour milled with an end mill has a lot in common with a contour cut with a wire.♦ Mills and Machining Centers Standard number of axes on a milling machine is three - the X, Y and Z axes. The part set on a milling system is al-ways stationary, mounted on a moving machine table. The cutting tool rotates, it can move up and down (or in and out), but it does not physically follow the tool path.CNC mills - sometimes called CNC milling machines - are usually small, simple machines, without a tool changer or other automatic features. Their power rating is often quite low. In industry, they are used for toolroom work, maintenance purposes, or small part production. They are usuallydesigned for contouring, unlike CNC drills.CNC machining centers are far more popular and effi-cient than drills and mills, mainly for their flexibility. The main benefit the user gets out of a CNC machining center is the ability to group several diverse operations into a single setup. For example, drilling, boring, counter boring, tap-ping, spot facing and contour milling can be incorporated into a single CNC program. In addition, the flexibility is enhanced by automatic tool changing, using pallets to minimize idle time, indexing to a different side of the part, using a rotary movement of additional axes, and a number of other features. CNC machining centers can be equipped with special software that controls the speeds and feeds, the life of the cutting tool, automatic in-process gauging and offset adjustment and other production enhancing and time saving devices.There are two basic designs of a typical CNC machining center. They are the vertical and the horizontal machining centers. The major difference between the two types is the nature of work that can be done on them efficiently. For a vertical CNC machining center, the most suitable type of work are flat parts, either mounted to the fixture on the ta-ble, or held in a vise or a chuck. The work that requires ma-chining on two or more faces m a single setup is more de-sirable to be done on a CNC horizontal machining center. An good example is a pump housing and other cubic-like shapes. Some multi-face machining of small parts can also be done on a CNC vertical machining center equipped with a rotary table.The programming process is the same for both designs, but an additional axis (usually a B axis) is added to the hori-zontal design. This axis is either a simple positioning axis (indexing axis) for the table, or a fully rotary axis for simul-taneous contouring. This handbook concentrates on the CNC vertical ma-chining centers applications, with a special section dealing with the horizontal setup and machining. The program-ming methods are also applicable to the small CNC mills or drilling and/or tapping machines, but the programmer has to consider their restrictions.♦ Lathes and Turning CentersA CNC lathe is usually a machine tool with two axes, the vertical X axis and the horizontal Z axis. The main feature of a lathe that distinguishes it from a mill is that the part is rotating about the machine center line. In addition, the cut-ting tool is normally stationary, mounted in a sliding turret. The cutting tool follows the contour of the programmed tool path. For the CNC lathes with a milling attachment, so called live tooling, the milling tool has its own motor and rotates while the spindle is stationary.The modem lathe design can be horizontal or vertical. Horizontal type is far more common than the vertical type, but both designs have their purpose in manufacturing. Sev-eral different designs exist for either group. For example, a typical CNC lathe of the horizontal group can be designed with a flat bed or a slant bed, as a bar type, chucker type or a universal type. Added to these combinations are many ac-cessories that make a CNC lathe an extremely flexible ma-chine tool. Typically, accessories such as a tailstock, steady rests or follow-up rests, part catchers,pullout-fingers and even a third axis milling attachment are popular compo-nents of the CNC lathe. ?CNC lathe can be veiy versatile - so versatile in fact, that it is often called a CNC TurningCenter. All text and program examples in this handbook use the more traditional term CNC lathe, yet still recogniz-ing all its modern functions.中文翻译:数控正如我们现在所知,数控技术出现于20世纪中叶。
英文毕业设计教案模板范文

I. IntroductionThe graduation design is an essential part of the undergraduate education process, providing students with an opportunity to apply the knowledge and skills acquired during their studies to real-world problems. This teaching plan outlines the structure, objectives, and methodology for conducting a successful graduation design project.II. Course OverviewCourse Title: Graduation Design (Undergraduate)Course Code: [Insert Course Code]Credit Hours: [Insert Credit Hours]Course Duration: [Insert Duration, e.g., 16 weeks]III. Course ObjectivesUpon completion of this course, students will be able to:1. Identify and define a specific research problem or design challenge.2. Conduct comprehensive literature reviews and analyze existing research or solutions.3. Develop a research plan or design proposal, including methodology, data collection, and analysis techniques.4. Implement the research plan or design project, adhering to ethical guidelines and professional standards.5. Present and defend their research findings or design solutions in a professional manner.6. Reflect on the project experience and articulate the learned lessons and personal growth.IV. Course Content1. Introduction to Graduation Design- Importance of graduation design in undergraduate education- Overview of the graduation design process- Role of the supervisor in the graduation design project2. Problem Identification and Definition- Techniques for identifying and defining research problems- Importance of clear and concise problem statements3. Literature Review- Conducting a comprehensive literature review- Analyzing and synthesizing existing research- Identifying gaps in the current literature4. Research Plan and Design Proposal- Developing a research plan or design proposal- Methodology, including data collection and analysis techniques - Ethical considerations and professional standards5. Implementation of the Project- Time management and project planning- Implementation of research methods or design solutions- Documentation and progress reporting6. Presentation and Defense- Preparing for the final presentation- Guidelines for effective presentations- Preparing for the defense of the project7. Reflection and Conclusion- Reflecting on the project experience- Articulating learned lessons and personal growth- Final project submission and evaluationV. Teaching MethodologyThe course will employ a combination of lectures, seminars, individual work, and group discussions to facilitate learning. The following methods will be used:1. Lectures: To provide an overview of the concepts, methodologies, and ethical considerations involved in graduation design.2. Seminars: To facilitate in-depth discussions on specific topics, allowing students to share their progress and receive feedback frompeers and instructors.3. Individual Work: To enable students to develop their research plansor design proposals independently.4. Group Discussions: To encourage collaborative learning and the exchange of ideas among students.5. Supervision: Regular meetings with the supervisor to provide guidance, feedback, and support throughout the project.VI. AssessmentThe assessment of the graduation design project will be based on the following criteria:1. Problem Identification and Definition (10%): Clarity and relevance of the research problem or design challenge.2. Literature Review (20%): Depth and breadth of the literature review, identification of research gaps.3. Research Plan and Design Proposal (30%): Soundness of the research plan or design proposal, adherence to ethical guidelines.4. Implementation of the Project (20%): Quality of the research or design implementation, adherence to the project plan.5. Presentation and Defense (10%): Clarity, coherence, and persuasiveness of the presentation, defense of the project.VII. ConclusionThis teaching plan aims to provide a comprehensive。
毕业设计英文翻译中英文对照版

Feasibility assessment of a leading-edge-flutter wind power generator前缘颤振风力发电机的可行性评估Luca Caracoglia卢卡卡拉克格里亚Department of Civil and Environmental Engineering, Northeastern University, 400 Snell Engineering Center, 360 Huntington A venue, Boston, MA 02115, USA美国东北大学土木与环境工程斯内尔工程中心400,亨廷顿大道360,波士顿02115This study addresses the preliminary technical feasibility assessment of a mechanical apparatus for conversion of wind energy. 这项研究涉及的是风能转换的机械设备的初步技术可行性评估。
The proposed device, designated as ‘‘leading-edge-fl utter wind power generator’’, employs aeroelastic dynamic instability of a blade airfoil, torsionally rotating about its leading edge. 这种被推荐的定义为“前缘颤振风力发电机”的设备,采用的气动弹性动态不稳定叶片翼型,通过尖端旋转产生扭矩。
Although the exploitation of aeroelastic phenomena has been proposed by the research community for energy harvesting, this apparatus is compact, simple and marginally susceptible to turbulence and wake effects.虽然气动弹性现象的开发已经有研究界提出可以通过能量采集。
毕业设计英文原文

-/L
t
1
Rise time of input signal
Input Response of probe to perfect input Scope probe
~--~-/L v-- t
3
Response of vertical amplifier to perfect input
Vertical amplifier
2Equation 3.1 holds strictly true only when each impulse response in Figure 3.2 is gaussian. For other impulse response shapes Equation 3.1 is very close to true, but not exact. See Appendix B for more information about the exact calculation of rise time in cascaded systems.
T.
10-90 -
_ 0.338
F
[3.2]
3dB
Specifications from instrument manufacturers quoting RMS bandwidth, or equivalent noise bandwidth F RMS ' should be converted according to (see also Equation 1.7)
Figure 3.2
Rise time of oscilloscope components.
When a realistic input feeds the combination of probe and vertical amplifier, as in Figure 3.3, the rise time of the result is equal to the square root of the sum of the squares of the rise times of each component.
(完整版)_毕业设计外文资料翻译_54103673

General programmable manipulator structure designRobot is a type of mechantronics equipment which synthesizes the last research achievement of engine and precisionengine,micro-electronics and computer,automation control and dr ive,sensor and message dispose and artificial intelligence and so on.With thedevelopment of economic and the demand for automation control, robot technology isdeveloped quickly and all types of the robots products are com e into being.The practicalityuse of robot products not only solves the problems which are difficult to operate for humanbeing,but also advances the industrial automation program.Modern industrial robots aretrue marvels of engineering.A robot the size of a person can easily carry a load over one,transformsystem,drive device and control system and guided by the idea of the characteristic andcomplex of mechanical configuration,electronic,software and har dware.In this article,themechanical configuration combines the character of direction coor dinate and the arthrosiscoordinate which can improve the stability and operation flexibility of the system.The mainfunction of the transmission mechanism is to transmit power to implement department andcomplete thenecessary movement.In this transmission structure,the screw tr ansmissionmechanism transmits the rotary motion into linear motion.Worm gear can give varytransmission ratio.Both of the transmission mechanisms have a characteristic of compactstructure.The design of drive system often is limited by the environment condition and thefactor of cost and technical lever.''''The step motor can rec eive digital signal directly and hasthe ability to response outer environment immediately and has n o accumulation error,whichoften is used in driving system.In this driving system,open-loop control system is composedof stepping motor,which can satisfy the demand not only for control precision but also for thetarget of economic and practicality.On this basis the analysis of stepping motor in powercalculating and style selecting is also given.The analysis of kinematics and dynamics forobject holding manipulator is given in completing the design ofmechanical structure and drivesystem.Kinematics analysis is the basis of path programming an d track control.The positiveand reverse analysis of manipulator gives the relationship betwe en manipulator space anddrive space in position and speed.The relationship between man ipulator’s.tip.position.and.arthrosis angles is concluded by coordinate transform method.Th e geometry method is usedin solving inverse kinematics problem and the result will provi de theory evidence for controlsystem.The f0unction of dynamics is to get the relationship b etween the movement and forceand the target is to satisfy the demand of real time control.in this chamfer,Newton-Euripidesmethod is used in analysis dynamic problem ofthe cleaning robot and the arthrosis force andtorque are given which provide the foundation for step motor s electing and structure dynamicoptimal ting.Control system is the key and core part of the object holding manipulator systemdesign which will direct effect the reliability and practicality of the robot system in the divisionof configuration and control function and also will effect or limit the development cost and cycle.With the demand of the PCL-839card,the PC computer which ha s a.tight structure and iseasy to be extended is used as the principal computer cell an d takes the function of systeminitialization,data operation and dispose,step motor drive and error diagnose and so on.A tthe same time,the configuration structure features,task princi ples and the position functionwith high precision of the control card PCL-839are analyzed. Hardware is the matterfoundation of the control.System and the software is the spir it of the control system.Thetarget of the software is to combine all the parts in optimiz ing style and to improve theefficiency and reliability of the control system.The software design of the object holdingmanipulator control system is divided into several blocks such as system initialization block,data process block and error station detect and dispose model and so on.PCL-839card cansolve the communication between the main computer and the contr ol cells and take themeasure of reducing the influence of the outer signal to the control system.The start and stopfrequency of the step motor is far lower than the maximum running frequency.In order toimprove the efficiency of the step motor,the increase and dec rease of the speed is mustconsidered when the step motor running in high speed and start or stop with great acceleration.The increase and decrease of the motor’s.speed can be controlled by the pulse freque ncysent to the step motor drive with a rational method.This can be implemented either bythe dynamic response of acomputer-based manipulator in accordance with some prespecified system performance anddesired goals. In general, the dynamic performance of a manipulator directly depends on theefficiency of the control algorithms and the dynamic model of the manipulator. The controlproblem consists of obtaining dynamic models of the physical robot arm system and thenspecifying corresponding control laws or strategies to achieve the desired system response andperformance.Current industrial approaches to robot arm control treat each joint of the robot arm as asimple joint servomechanism. The servomechanism approach models the varying dynamics of amanipulator inadequately because it neglects the motion and configuration of the whole armmechanism. These changes in the parameters of the controlled system sometimes are significantenough to render conventional feedback control strategies ineffective. The result is reduced servoresponse speed and damping, limiting the precision and speed of the end-effector and making itappropriate only for limited-precision tasks. Manipulators controlled in this manner move at slowspeeds with unnecessary vibrations. Any significant performance gain in this and other areas ofrobot arm control require the consideration of more efficient dynamic models, sophisticatedcontrol approaches, and the use of dedicated computer architectures and parallel processingtechniques.In the industrial production and other fields,people often end angered by such factors as,but also is of great significance for physical security protect ion,improvement of theenvironment for labor,reducing labor intensity,improvement of labor productivity,raw materialconsumption savings and lowering production costs.There are such mechanical components as ball footbridge,slides, an air control mechanical.A programmable controller,a programming device,stepping motors,stepping motors drives,direct current motors,sensor,s witch power supply,anelectromagnetism valve and control desk are used in electrical connection.The programmablecontroller output two lines pulses to stepping motors drives to drive the two stepping motorsdrives on beam and vertical axis;direct current motors drive the rotation of the base and the,up and down,moves location;the mainframe sendsignals to control the opening and closing of the hand to car ry objects.Related parameterscan be changed according to request of the changes of the obj ects and movement flow at anytime change the relevant parameters in the design,so it has great flexibility and operability.。
毕业设计英文版

Graduation ProjectCourse Code: 82157600Couse Title: Graduation ProjectCredits:6 Semester Classes:The 11’s SemesterTeaching People:All undergraduate students of the School of Mathematical and StatisticsPre-Course:Mathematical ModelThe Charger of the Course:Qi Haitao,DoctorCourse Description:《 Graduation Project》 will play a significant role in assisting students to demonstrate their learned knowledge and skills through a 21st Century performance-based process. This process will involve students, schools, parents and communities. It is an opportunity for students to spend extended time delving into a topic for which they have a particular interest and passion, and serves as a summary and reflect ion of the student’s experience. Prior to graduation, students are given the opportunity to present what they have accomplished and learned to their project partners, school family, and members of the community. This culminating demonstration is a personal affirmation of a student’s individual achievement and a memorable experience to mark the conclusion of four years of undergraduate education.Practice Teaching:We will study some applications of Mathematical and Statistics.Course Assesement:The examination results will be decided by the papers that students finished.。
毕业设计外文翻译英文翻译英文原稿

Harmonic source identification and current separationin distribution systemsYong Zhao a,b,Jianhua Li a,Daozhi Xia a,*a Department of Electrical Engineering Xi’an Jiaotong University, 28 West Xianning Road, Xi’an, Shaanxi 710049, Chinab Fujian Electric Power Dispatch and Telecommunication Center, 264 Wusi Road, Fuzhou, Fujian, 350003, China AbstractTo effectively diminish harmonic distortions, the locations of harmonic sources have to be identified and their currents have to be separated from that absorbed by conventional linear loads connected to the same CCP. In this paper, based on the intrinsic difference between linear and nonlinear loads in their V –I characteristics and by utilizing a new simplified harmonic source model, a new principle for harmonic source identification and harmonic current separation is proposed. By using this method, not only the existence of harmonic source can be determined, but also the contributions of the harmonic source and the linear loads to harmonic voltage distortion can be distinguished. The detailed procedure based on least squares approximation is given. The effectiveness of the approach is illustrated by test results on a composite load.2004 Elsevier Ltd. All rights reserved.Keywords: Distribution system; Harmonic source identification; Harmonic current separation; Least squares approximation1. IntroductionHarmonic distortion has experienced a continuous increase in distribution systems owing to the growing use of nonlinear loads. Many studies have shown that harmonics may cause serious effects on power systems, communication systems, and various apparatus [1–3]. Harmonic voltages at each point on a distribution network are not only determined by the harmonic currents produced by harmonic sources (nonlinear loads), but also related to all linear loads (harmonic current sinks) as well as the structure and parameters of the network. To effectively evaluate and diminish the harmonic distortion in power systems, the locations of harmonic sources have to be identified and the responsibility of the distortion caused by related individual customers has to be separated.As to harmonic source identification, most commonly the negative harmonic power is considered as an essential evidence of existing harmonic source [4–7]. Several approaches aiming at evaluating the contribution of an individual customer can also be found in the literatures. Schemes based on power factor measurement to penalize the customer’s harmonic currents are discussed in Ref. [8]. However, it would be unfair to use economical penalization if we could not distinguish whether the measured harmonic current is from nonlinear load or from linear load.In fact, the intrinsic difference between linear and nonlinear loads lies in their V –I characteristics. Harmonic currents of a linear load are i n linear proportion to its supplyharmonic voltages of the same order 次, whereas the harmonic currents of a nonlinear load are complex nonlinear functions of its supply fundamental 基波and harmonic voltage components of all orders. To successfully identify and isolate harmonic source in an individual customer or several customers connected at same point in the network, the V –I characteristics should be involved and measurement of voltages and currents under several different supply conditions should be carried out.As the existing approaches based on measurements of voltage and current spectrum or harmonic power at a certain instant cannot reflect the V –I characteristics, they may not provide reliable information about the existence and contribution of harmonic sources, which has been substantiated by theoretical analysis or experimental researches [9,10].In this paper, to approximate the nonlinear characteristics and to facilitate the work in harmonic source identification and harmonic current separation, a new simplified harmonic source model is proposed. Then based on the difference between linear and nonlinear loads in their V –I characteristics, and by utilizing the harmonic source model, a new principle for harmonic source identification and harmonic current separation is presented. By using the method, not only the existence of harmonic source can be determined, but also the contributions of the harmonic sources and the linear loads can be separated. Detailed procedure of harmonic source identification and harmonic current separation based on least squares approximation is presented. Finally, test results on a composite load containing linear and nonlinear loads are given to illustrate the effectiveness of the approach.2. New principle for harmonic source identification and current separationConsider a composite load to be studied in a distribution system, which may represent an individual consumer or a group of customers supplied by a common feeder 支路in the system. To identify whether it contains any harmonic source and to separate the harmonic currents generated by the harmonic sources from that absorbed by conventional linear loads in the measured total harmonic currents of the composite load, the following assumptions are made.(a) The supply voltage and the load currents are both periodical waveforms withperiod T; so that they can be expressed by Fourier series as1()s i n (2)h h h v t ht T πθ∞==+ (1)1()sin(2)h h h i t ht πφ∞==+The fundamental frequency and harmonic components can further be presented bycorresponding phasorshr hi h h hr hi h hV jV V I jI I θφ+=∠+=∠ , 1,2,3,...,h n = (2)(b) During the period of identification, the composite load is stationary, i.e. both its composition and circuit parameters of all individual loads keep unchanged.Under the above assumptions, the relationship between the total harmonic currents of the harmonic sources(denoted by subscript N) in the composite load and the supply voltage, i.e. the V –I characteristics, can be described by the following nonlinear equation ()()()N i t f v t = (3)and can also be represented in terms of phasors as()()122122,,,...,,,,,,...,,Nhr r i nr ni Nh Nhi r inr ni I V V V V V I I V V V V V ⎡⎤=⎢⎥⎣⎦ 2,3,...,h n = (4)Note that in Eq. (4), the initial time (reference time) of the voltage waveform has been properly selected such that the phase angle u1 becomes 0 and 10i V =, 11r V V =in Eq. (2)for simplicity.The V –I characteristics of the linear part (denote by subscript L) of the composite load can be represented by its equivalent harmonic admittance Lh Lh Lh Y G jB =+, and the total harmonic currents absorbed by the linear part can be described as,Lhr LhLh hr Lh Lhi LhLh hi I G B V I I B G V -⎡⎤⎡⎤⎡⎤==⎢⎥⎢⎥⎢⎥⎣⎦⎣⎦⎣⎦2,3,...,h n = (5)From Eqs. (4) and (5), the whole harmonic currents absorbed by the composite load can be expressed as()()122122,,,...,,,,,,...,,hr Lhr Nhr r i nr ni h hi Lhi Nhi r inr ni I I I V V V V V I I I I V V V V V ⎡⎤⎡⎤⎡⎤==-⎢⎥⎢⎥⎢⎥⎣⎦⎣⎦⎣⎦ 2,3,...,h n = (6)As the V –I characteristics of harmonic source are nonlinear, Eq. (6) can neither be directly used for harmonic source identification nor for harmonic current separation. To facilitate the work in practice, simplified methods should be involved. The common practice in harmonic studies is to represent nonlinear loads by means of current harmonic sources or equivalent Norton models [11,12]. However, these models are not of enough precision and new simplified model is needed.From the engineering point of view, the variations of hr V and hi V ; ordinarily fall into^3% bound of the rated bus voltage, while the change of V1 is usually less than ^5%. Within such a range of supply voltages, the following simplified linear relation is used in this paper to approximate the harmonic source characteristics, Eq. (4)112222112322,ho h h r r h i i hnr nr hni ni Nh ho h h r r h i i hnr nr hni ni a a V a V a V a V a V I b b V b V b V b V b V ++++++⎡⎤=⎢⎥++++++⎣⎦2,3,...,h n = (7)这个地方不知道是不是原文写错?23h r r b V 其他的都是2The precision and superiority of this simplified model will be illustrated in Section 4 by test results on several kinds of typical harmonic sources.The total harmonic current (Eq. (6)) then becomes112222112222,2,3,...,Lh Lh hr ho h h r r h i i hnr nr hni ni h Lh Lh hi ho h h r r h i i hnr nr hni ni G B V a a V a V a V a V a V I B G V b b V b V b V b V b V h n-++++++⎡⎤⎡⎤⎡⎤=-⎢⎥⎢⎥⎢⎥++++++⎣⎦⎣⎦⎣⎦= (8)It can be seen from the above equations that the harmonic currents of the harmonic sources (nonlinear loads) and the linear loads differ from each other intrinsically in their V –I characteristics. The harmonic current component drawn by the linear loads is uniquely determined by the harmonic voltage component with same order in the supply voltage. On the other hand, the harmonic current component of the nonlinear loads contains not only a term caused by the same order harmonic voltage but also a constant term and the terms caused by fundamental and harmonic voltages of all other orders. This property will be used for identifying the existence of harmonic source sin composite load.As the test results shown in Section 4 demonstrate that the summation of the constant term and the component related to fundamental frequency voltage in the harmonic current of nonlinear loads is dominant whereas other components are negligible, further approximation for Eq. (7) can be made as follows.Let112'012()()nh h hkr kr hki ki k k h Nhnh h hkr kr hki kik k h a a V a V a V I b b V b V b V =≠=≠⎡⎤+++⎢⎥⎢⎥=⎢⎥⎢⎥+++⎢⎥⎢⎥⎣⎦∑∑ hhr hhi hr Nhhhr hhi hi a a V I b b V ⎡⎤⎡⎤''=⎢⎥⎢⎥⎣⎦⎣⎦hhrhhihr Lh Lh Nh hhrhhi hi a a V I I I b b V ''⎡⎤⎡⎤'''=-=⎢⎥⎢⎥''⎣⎦⎣⎦,2,3,...,hhr hhiLh Lh hhrhhi hhr hhi Lh Lh hhr hhi a a G B a a h n b b B G b b ''-⎡⎤⎡⎤⎡⎤=-=⎢⎥⎢⎥⎢⎥''⎣⎦⎣⎦⎣⎦The total harmonic current of the composite load becomes112012(),()2,3,...,nh h hkr kr hki ki k k hhhrhhi hr h Lh NhLhNh n hhrhhi hi h h hkr kr hki kik k h a a V a V a V a a V I I I I I b b V b b V b V b V h n=≠=≠⎡⎤+++⎢⎥⎢⎥''⎡⎤⎡⎤''=-=-=-⎢⎥⎢⎥⎢⎥''⎣⎦⎣⎦⎢⎥+++⎢⎥⎢⎥⎣⎦=∑∑ (9)By neglecting ''Nh I in the harmonic current of nonlinear load and adding it to the harmonic current of linear load, 'Nh I can then be deemed as harmonic current of thenonlinear load while ''Lh I can be taken as harmonic current of the linear load. ''Nh I =0 means the composite load contains no harmonic sources, while ''0NhI ≠signify that harmonic sources may exist in this composite load. As the neglected term ''Nh I is not dominant, it is obviousthat this simplification does not make significant error on the total harmonic current of nonlinear load. However, it makes the possibility or the harmonic source identification and current separation.3. Identification procedureIn order to identify the existence of harmonic sources in a composite load, the parameters in Eq. (9) should be determined primarily, i.e.[]0122hr h h h rh i hhr hhihnr hni C a a a a a a a a ''= []0122hi h h h rh i hhrhhihnr hni C b b b b b b b b ''=For this purpose, measurement of different supply voltages and corresponding harmoniccurrents of the composite load should be repeatedly performed several times in some short period while keeping the composite load stationary. The change of supply voltage can for example be obtained by switching in or out some shunt capacitors, disconnecting a parallel transformer or changing the tap position of transformers with OLTC. Then, the least squares approach can be used to estimate the parameters by the measured voltages and currents. The identification procedure will be explained as follows.(1) Perform the test for m (2m n ≥)times to get measured fundamental frequency andharmonic voltage and current phasors ()()k k h h V θ∠,()()k k hh I φ∠,()1,2,,,1,2,,k m h n == .(2) For 1,2,,k n = ,transfer the phasors corresponding to zero fundamental voltage phase angle ()1(0)k θ=and change them into orthogonal components, i.e.()()11kkr V V = ()10ki V =()()()()()()()()()()11cos sin kkkkk kkkhr h h hihhV V h V V h θθθθ=-=-()()()()()()()()()()11cos sin k kkkk kkkhrhhhihhI I h I I h φθφθ=-=-,2,3,...,h n =(3)Let()()()()()()()()1221Tk k k k k k k k r i hr hi nr ni VV V V V V V V ⎡⎤=⎣⎦ ,()1,2,,k m = ()()()12Tm X V V V ⎡⎤=⎣⎦ ()()()12T m hr hr hr hrW I I I ⎡⎤=⎣⎦()()()12Tm hi hi hihi W I I I ⎡⎤=⎣⎦ Minimize ()()()211hr mk hr k I C V=-∑ and ()()()211him k hi k IC V=-∑, and determine the parametershr C and hi C by least squares approach as [13]:()()11T T hr hr T T hi hiC X X X W C X X X W --== (10)(4) By using Eq. (9), calculate I0Lh; I0Nh with the obtained Chr and Chi; then the existence of harmonic source is identified and the harmonic current is separated.It can be seen that in the course of model construction, harmonic source identification and harmonic current separation, m times changing of supply system operating condition and measuring of harmonic voltage and currents are needed. More accurate the model, more manipulations are necessary.To compromise the needed times of the switching operations and the accuracy of the results, the proposed model for the nonlinear load (Eq. (7)) and the composite load (Eq. (9)) can be further simplified by only considering the dominant terms in Eq. (7), i.e.01111,Nhr h h hhr hhi hr Nh Nhi ho h hhrhhi hi I a a V a a V I I b b V b b V +⎡⎤⎡⎤⎡⎤⎡⎤==+⎢⎥⎢⎥⎢⎥⎢⎥+⎣⎦⎣⎦⎣⎦⎣⎦2,3,,h n = (11) 01111h h Nh ho h a a V I b b V +⎡⎤'=⎢⎥+⎣⎦01111,hr hhrhhi hr h h h LhNh hi hhr hhihi ho h I a a V a a V I I I I b b V b b V ''+⎡⎤⎡⎤⎡⎤⎡⎤''==-=-⎢⎥⎢⎥⎢⎥⎢⎥''+⎣⎦⎣⎦⎣⎦⎣⎦2,3,,h n = (12) In this case, part equations in the previous procedure should be changed as follows[]01hr h h hhrhhi C a a a a ''= []01hi h h hhrhhiC b b b b ''= ()()()1Tk k k hr hi V V V ⎡⎤=⎣⎦ Similarly, 'Nh I and 'Lh I can still be taken as the harmonic current caused by thenonlinear load and the linear load, respectively.4. Experimental validation4.1. Model accuracyTo demonstrate the validity of the proposed harmonic source models, simulations are performed on the following three kind of typical nonlinear loads: a three-phase six-pulse rectifier, a single-phase capacitor-filtered rectifier and an acarc furnace under stationary operating condition.Diagrams of the three-phase six-pulse rectifier and the single-phase capacitor-filtered rectifier are shown in Figs. 1 and 2 [14,15], respectively, the V –I characteristic of the arc furnace is simplified as shown in Fig. 3 [16].The harmonic currents used in the simulation test are precisely calculated from their mathematical model. As to the supply voltage, VekT1 is assumed to be uniformly distributed between 0.95 and 1.05, VekThr and VekThi ek 1; 2;…;m T are uniformly distributed between20.03 and 0.03 with base voltage 10 kV and base power 1 MVFig. 1. Diagram of three-phase six-pulse rectifier.Fig. 2. Diagram of single-phase capacitor-filtered rectifierFig. 3. Approximate V –I characteristics of arc furnace.Three different models including the harmonic current source (constant current) model, the Norton model and the proposed simplified model are simulated and estimated by the least squares approach for comparison.For the three-phase six-pulse rectifier with fundamental currentI=1.7621; the1 parameters in the simplified model for fifth and seventh harmonic currents are listed in Table 1.To compare the accuracy of the three different models, the mean and standard deviations of the errors on Ihr; Ihi and Ih between estimated value and the simulated actual value are calculated for each model. The error comparison of the three models on the three-phase six-pulse rectifier is shown in Table 2, where mhr; mhi and mha denote the mean, and shr; shi and sha represent the standard deviations. Note that I1 and _Ih in Table 2are the current values caused by rated pure sinusoidal supply voltage.Error comparisons on the single-phase capacitor-filtered rectifier and the arc furnace load are listed in Table 3 and 4, respectively.It can be seen from the above test results that the accuracy of the proposed model is different for different nonlinear loads, while for a certain load, the accuracy will decrease as the harmonic order increase. However, the proposed model is always more accurate than other two models.It can also be seen from Table 1 that the componenta50 t a51V1 and b50 t b51V1 are around 20:0074 t0:3939 0:3865 and 0:0263 t 0:0623 0:0886 while the componenta55V5r and b55V5i will not exceed 0:2676 £0:03 0:008 and 0:9675 £0:003 0:029; respectively. The result shows that the fifth harmonic current caused by the summation of constant term and the fundamental voltage is about 10 times of that caused by harmonic voltage with same order, so that the formal is dominant in the harmonic current for the three-phase six-pulse rectifier. The same situation exists for other harmonic orders and other nonlinear loads.4.2. Effectiveness of harmonic source identification and current separationTo show the effectiveness of the proposed harmonic source identification method, simulations are performed on a composite load containing linear load (30%) and nonlinear loads with three-phase six-pulse rectifier (30%),single-phase capacitor-filtered rectifier (20%) and ac arc furnace load (20%).For simplicity, only the errors of third order harmonic current of the linear and nonlinear loads are listed in Table 5, where IN3 denotes the third order harmonic current corresponding to rated pure sinusoidal supply voltage; mN3r ;mN3i;mN3a and mL3r ;mL3i;mL3a are error means of IN3r ; IN3i; IN3 and IL3r ; IL3i; IL3 between the simulated actual value and the estimated value;sN3r ;sN3i;sN3a and sL3r ;sL3i;sL3a are standard deviations.Table 2Table 3It can be seen from Table 5 that the current errors of linear load are less than that of nonlinear loads. This is because the errors of nonlinear load currents are due to both the model error and neglecting the components related to harmonic voltages of the same order, whereas only the later components introduce errors to the linear load currents. Moreover, it can be found that more precise the composite load model is, less error is introduced. However, even by using the very simple model (12), the existence of harmonic sources can be correctly identified and the harmonic current of linear and nonlinear loads can be effectively separated. Table 4Error comparison on the arc furnaceTable 55. ConclusionsIn this paper, from an engineering point of view, firstly anew linear model is presented for representing harmonic sources. On the basis of the intrinsic difference between linear and nonlinear loads in their V –I characteristics, and by using the proposed harmonic source model, a new concise principle for identifying harmonic sources and separating harmonic source currents from that of linear loads is proposed. The detailed modeling and identification procedure is also developed based on the least squares approximation approach. Test results on several kinds of typical harmonic sources reveal that the simplified model is of sufficient precision, and is superior to other existing models. The effectiveness of the harmonic source identification approach is illustrated using a composite nonlinear load.AcknowledgementsThe authors wish to acknowledge the financial support by the National Natural Science Foundation of China for this project, under the Research Program Grant No.59737140. References[1] IEEE Working Group on Power System Harmonics, The effects of power system harmonics on power system equipment and loads. IEEE Trans Power Apparatus Syst 1985;9:2555–63.[2] IEEE Working Group on Power System Harmonics, Power line harmonic effects on communication line interference. IEEE Trans Power Apparatus Syst 1985;104(9):2578–87.[3] IEEE Task Force on the Effects of Harmonics, Effects of harmonic on equipment. IEEE Trans Power Deliv 1993;8(2):681–8.[4] Heydt GT. Identification of harmonic sources by a State Estimation Technique. IEEE Trans Power Deliv 1989;4(1):569–75.[5] Ferach JE, Grady WM, Arapostathis A. An optimal procedure for placing sensors and estimating the locations of harmonic sources in power systems. IEEE Trans Power Deliv 1993;8(3):1303–10.[6] Ma H, Girgis AA. Identification and tracking of harmonic sources in a power system using Kalman filter. IEEE Trans Power Deliv 1996;11(3):1659–65.[7] Hong YY, Chen YC. Application of algorithms and artificial intelligence approach for locating multiple harmonics in distribution systems. IEE Proc.—Gener. Transm. Distrib 1999;146(3):325–9.[8] Mceachern A, Grady WM, Moncerief WA, Heydt GT, McgranaghanM. Revenue and harmonics: an evaluation of someproposed rate structures. IEEE Trans Power Deliv 1995;10(1):474–82.[9] Xu W. Power direction method cannot be used for harmonic sourcedetection. Power Engineering Society Summer Meeting, IEEE; 2000.p. 873–6.[10] Sasdelli R, Peretto L. A VI-based measurement system for sharing the customer and supply responsibility for harmonic distortion. IEEETrans Instrum Meas 1998;47(5):1335–40.[11] Arrillaga J, Bradley DA, Bodger PS. Power system harmonics. NewYork: Wiley; 1985.[12] Thunberg E, Soder L. A Norton approach to distribution networkmodeling for harmonic studies. IEEE Trans Power Deliv 1999;14(1):272–7.[13] Giordano AA, Hsu FM. Least squares estimation with applications todigital signal processing. New York: Wiley; 1985.[14] Xia D, Heydt GT. Harmonic power flow studies. Part I. Formulationand solution. IEEE Trans Power Apparatus Syst 1982;101(6):1257–65.[15] Mansoor A, Grady WM, Thallam RS, Doyle MT, Krein SD, SamotyjMJ. Effect of supply voltage harmonics on the input current of single phase diode bridge rectifier loads. IEEE Trans Power Deliv 1995;10(3):1416–22.[16] Varadan S, Makram EB, Girgis AA. A new time domain voltage source model for an arc furnace using EMTP. IEEE Trans Power Deliv 1996;11(3):1416–22.。
本科毕业设计(论文)英文翻译模板
本科毕业设计(论文)英文翻译论文标题(中文)学院******姓名***专业*******班级**********大气探测2班学号*************** 大气探测、信处、两个专业填写电子信息工程。
生物医学工程、电子信息科学与技术、雷电防护科学与技术As its name implies, region growing is a procedure that groups pixels or subregions into larger regions based on predefined criteria. The basic approach is to start with a set of “seed ” points and from these grow regions by appending to each seed those gray level or color).be used to assignpixels to regions during the centroid of these clusters can be used as seeds.… … …左右手共面波导的建模与带通滤波器设计速发展之势,而它的出现却是源于上世纪本研究提出了一种新型混合左右手(CPW )的独特功能。
目前这种有效电长度为0°的新型混合左右手共面波导(CRLH CPW )谐振器正在兴起,这种谐振器工作在5GHz 时的体积比常规结构的谐振器缩减小49.1%。
有关图、表等表格和图片必须有说明,宋体五号公式:公式的编号用括号起写在右边行末,其间不加虚线。
图、表、公式等与正文之间要有6磅的行间距。
文中的图、表、附注、公式一律采用阿拉伯数字分章连续编号。
如:图2-5,表3-2,公式(5-1)等。
若图或表中有附注,采用英文小写字母顺序编号,附注写在图或表的下方。
毕业设计作品集英文

毕业设计作品集英文Here's a sample of an English portfolio for a graduation project, adhering to the given requirements:I started this journey with a blank canvas, eager to explore the possibilities within. My imagination was my guide, leading me through a maze of creativity.The first step was to immerse myself in the subject, to delve deep into the heart of the matter. I researched, experimented, and questioned every detail. It was a quest for knowledge, a pursuit of excellence.Then came the moment of inspiration. It hit me like a bolt of lightning, a flash of brilliance that illuminated my path. The ideas flowed freely, each one more exciting than the last.But the hardest part was bringing these ideas to life.I faced challenges, setbacks, and even moments of doubt.But I persevered, determined to see my vision come to fruition.In the end, it was all worth it. The finished product stands before me, a testament to my hard work and dedication. It's not just a project, it's a piece of me, a reflection of my creativity and passion.Looking back, I realize how much I've grown. This experience has taught me resilience, the importance of perseverance, and the joy of creating something unique.It's a journey I'll never forget.Now, as I share.。
毕业设计手册英语

毕业设计手册英语Graduation Project HandbookIntroductionGraduation projects are an essential part of the academic journey for students pursuing higher education. These projects provide an opportunity for students to apply the knowledge and skills they have acquired throughout their studies to real-world problems. In this handbook, we will explore the various aspects of a graduation project, including its importance, the steps involved in its completion, and tips for success.Importance of a Graduation ProjectA graduation project serves as a culmination of a student's academic journey. It allows students to demonstrate their ability to apply theoretical concepts to practical situations. Moreover, it provides a platform for students to showcase their creativity, critical thinking, and problem-solving skills. The completion of a successful graduation project not only enhances a student's academic profile but also prepares them for future professional endeavors.Choosing a TopicSelecting an appropriate topic for a graduation project is crucial. It should align with the student's field of study and reflect their interests. The topic should also be relevant and address a real-world problem or contribute to existing knowledge. It is advisable to consult with faculty members or advisors to ensure the chosen topic is feasible and aligns with the project's objectives.Planning and ResearchOnce the topic is finalized, it is essential to create a detailed plan outlining the project's objectives, timeline, and required resources. Conducting thorough research is a fundamental step in the process. It involves gathering information from various sources such as books, academic journals, and online databases. The research phase helps students gain a comprehensive understanding of the topic and identify any existing gaps in knowledge.Design and ImplementationAfter completing the research phase, students can proceed with designing their graduation project. This may involve developing a prototype, conducting experiments, or creating a software application, depending on the nature of the project. It is essential to document the design process, including any challenges faced and modifications made along the way.Data Collection and AnalysisIf the project involves collecting data, it is crucial to ensure the data collection process is systematic and accurate. Students should use appropriate methods and tools to gather relevant data. Once the data is collected, it needs to be analyzed using statistical techniques or other appropriate methods. The analysis should be objective and provide meaningful insights that contribute to the project's objectives.Documentation and PresentationProper documentation is vital to ensure the project's findings and methodologyare clearly presented. Students should maintain a record of their work, including research notes, design plans, data collection methods, and analysis techniques. This documentation will serve as a reference for future researchers and can also be included in the final project report.In addition to documentation, students are required to present their graduation projects to a panel of faculty members and peers. The presentation should be well-structured, concise, and engaging. Visual aids such as slides or posters can be used to enhance the presentation. It is essential to practice the presentation beforehand to ensure a confident and professional delivery.ConclusionA graduation project is a significant undertaking that requires careful planning, research, and execution. It provides students with an opportunity to showcase their skills and knowledge while contributing to their field of study. By following the steps outlined in this handbook, students can successfully complete their graduation projects and embark on their professional journey with confidence. Remember, the graduation project is not just a requirement for obtaining a degree; it is a chance to leave a lasting impact in the academic community.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Compensation of Control System1.Multiple Constrains in DesignThe performance of a feedback control system is of primary importance.We have found that a suitable control system should have some of the following properties.1)It should be stable and present acceptable response to inputcommand,i.e,the controlled variable should follow the changes in the input at a suitable speed without unduly large oscillations or overshoots.2)It should operate with as little error as possible.3)It should be able to mitigate the effect of undesirabledisturbances.A feedback control system that provided an optimum perfprmance without any necessary adjustments is rare ually it is necessary to compromise among the many conflicting and demanding specifications and to adjust the system parameters to provide a suitable and acceptable performance when it is not possible to obtain all the desired optimum specifications.The preceding chapters have showen that it is often possible to adjust the system parameters in order to provide the desired system response.When the achievement of a simple performance requirement may be met by selecting a particular value of K, the process is called gain compensation.However,we often find that it is not sufficient to adjust a system parameter and thus obtain the desired performance.Rather we are required to reconsider the structure of the system and redesign the system in order to obtain a suitable one.That is ,we must examine scheme of the system and obtain a new design that results in a suitable system.Thus the design of a control system is concerned with the arrangement of the systemstructure and the selection of suitable components and parameters.When we are not able to relax several perfprmance requirements,we must alter the system in some way.The alteration or adjustment of a control system in oreder to provider a suitable performance is called compensation.In redesigning a control system to alter the system response,an additional component or device is inserted within the structure of the feedback system to compensate for the performance deficiency.The compensating device may be electric,mechanical,hydraulic,pneumatic,or some other type of devices or networks and is often called a monly an electric network serves as a compensator in many control systems.Quite often,in practice,the best and simplest way to improve the performance of a control system is to alter,if possible,the plant itself.That is,if the system designer is able to specify and alter the design of the plant,then the performance of the system may be readily improved.For example,to improve the transient behavior of a servomechanism position controller,we often can choose a better motor for the system.Thus a control system designer should recognize that an alteration of the plant maybe result in an improved system.However,often the plant is unalterable or has been altered as much as possible and still result in unsatisfactory performance.Then the addition of compensator becomes useful for improving the performance of the system.2.Types of CompensationThe compensator is placed in a suitable location within the system,and can be done in several ways .An additional component may be interested in the forward path.This is called the cascade or serial compensation.The transfer function of the compensator is designated as Gc(s),whereas that of the original plant(or process)is denoted by Gp(s).Alternatively,the compensator may be placed in the feedbackpath .This is called the feedback compensation. A combination of these two schemes.The selection of the compensation scheme depends upon a consideration of the specifications, the power levels at various signal nodes in the system,and the compensators available for us.3.Cascade CompensationAlthough many different types of compensators can be used,the simplest among them are cascade phase-lead,phase-lag,and phase-lag-lead networks.Each of these can be realized by using an operational amplifier network.The Bode diagram is used to determine a suitable cascade compensator in preference to other frequence plots.The frequence response of the cascade compensator is added to the frequency response of the uncompensated system.It is assumed, in below discussion, that the compensator Gc(s),is used with an uncompensated system so that the overall open-loop gain can be set to satisfy the steady-state error requirement,then Gc(s) is used to adjust the system dynamics favorably without affecting the steady-stste error.For convenience,the open-loop transfer function of the uncompensated system,Gp(s)H(s),is denoted by Go(s).At first,consider a system described by the open-loop transfer functionGo(s)=k/s(0.2s+1)Suppose we wish the closed-loop system to meet the following performance requirements:a)The steady-state error for a unit ramp is to be no more than 0.00316.b)The phase margin is to be no less than 45.For the first requirement,the static velocity error constant can be cocalculated from equationεss=1/Kv=1/K≦0.00316and thus the required open-loop gain is K=Kv=3.16It may also be seen that the phase margin will be about 45.at w=5 rad/s;therefore,to meet the second requirement,the magnitude must be zero at this frequency.Obviously,it is not possible to satisfy both system performance requirements with a singular value of gain.The system needs to be modified in some way,i.e,the shape of the Bode diagram has to be altered in some way to allow it to achieve both perfprmance requirements. The system perfprmance requirements stated in the example are typical of those found in many design cases;a steady-state error determines one value of gain while a desired transient response determines anthor.Note how each requirement relates to a different region of frequency acxis in the Bode diagram.(1)The steady-state error relates to the slope and magnitude at lowfrequency.(2)The phase margin relates to the gain crossover frequency,which usuallyoccurs at higher frequency.4.Approaches to System DesignThe performance of a control system can be specified by requirement of certain maximum overshoot and setting time for a step input. Furthermore it is usually necessary to specify the maximum allowable steady-state error for several test signal inputs and disturbances .These performance specifications are related to the location of the poles and zeros of the closed-loop transfer function.Thus the location of the closed-loop poles and zeros can be specified.As we found in chapter4,the locus of the roots of the closed-loop system can be readily obtained for the variation of one system parameter.However,when the locus of roots does not result in a suitable root configuration,we must add a compensator to alter the locus of the roots as parameter is varied.Therefore we can use the root locus method and determine a suitsble compensator transfer function so that the resultant root ;ocus yields the desired closed-looproot configuration.Alternatively,the performance of a control system can be specified in terms of the relative resonant peak,resonant frequency,and bandwidth of the closed-loop frequency response,or in terms of the phase margin, gain margin and gain crossover frequency of the open-loop frequency response.We can add a suitable compensator,if necessary,in order to satisfy the system perfprmancr.The design of the compensator is developed in terms of the frequency response as portrayed on the polar plot,the Bode diagram,or the Nichols chart.Because a cascade transfer function is readily accounted for on a Bode diagram by adding the frequency response of the compensator,we usually prefer to approach the frequency response method by utilizing the Bode diagram.5.Phase-Lead Compensation1. Phase-Lead CompensationThe phase-lead compensator is a form of high-pass filter,through which the signals at high frequencies are amplified relatively than that at low frequencies.It introduces a gain at high frequencies,which in general is destabilizing.However,its positive phase angle is stablilzing .Hence,we must carefully choose two break frequencies so that the stabilizing effect of the positive phase angle is dominant.ments on the Applicability and ResultsPhase-lead compensation has some distinct advantages over other forms of compensation,wherease it may also be difficult to use .Some observations from the example just analyzed allow a few generalizations to be made regarding phase lead compensation.1)The phase-lead compensation method provides an additional phaselead to limit the system’s overshoot to a required value.2)The open-loop(and usually the closed-loop)bandwidths isincreased.This is usually beneficial since the inclusion ofhigher frequencies in the response results in a faster response.Itmay cause problem,however,if noise exists at the higherfrequencies.3)Problem may occur when the uncompensated phase plot has a steeoslope in the vicinity of φm.This occurs because,as the new gaincrossover point moves to the right ,larger and larger phase leadis required from the compensator,demanding very large value ofα.This is difficult to achieve when the compensator is realizedwith physical components.For this reason ,value of α>15 shouldbe avoided,and methods to compensate the system using othertechniques,such as phaselag,should be investigated.6.Phase-Lag Compensation1.Phase-Lag Compensation ProcessIn phase-lag compensation,the magnitude part of the uncompensated Bode diagram is attenuated in order to reduce the gain crossover frequency,thereby allowing the uncompensated phase plot to produce the necessary phase margin.The phase-lag compensator is used to provide an attenuation and therefore to lower the crossover frequency of the system.Furthermore,at lower crossover frequency,we usually find that the phase margin of the system is increased,and the specifications can be satisfied.Of cause,the influence of the phase lag caused by the compensator should be taken into ually,the lag phase is about 5~12 if the break frequency corresponding to the zero of the compensator is wz=(0.1~0.2)wc.ments on the Applicability and Results1)The phase-lag method provides the necessary damping ratio in orderto limit the overshoot to the required value.2)The compensation process is somewhat simpler than the phase-leadcompensation in that the selection of the break frequencies is not too critical.3)As can be seen from the compensated system,the phase-lag techniquereduces the open and hence the closed-loop bandwith,which results ina slower response.4)Unlike phase-lead compensation,theoretically,phase lag compensationmay change the phase margin by more than 90.7.Phase Lag-Lead CompensationIn the compensator design it is usual to assume that the two break frequencies of the lag portion are lower than the two break frequencies of the lead portion.Further features of the Bode diagram include the following.1)The magnitude at lower frequencies is 0 db while the magnitude athigher frequencies is 20lg(αβ)ually,the compensator provides attenuation only and no gain.2)The phase angle first lags and then leads ,but the high-andlow-frequency phases are both zeros.3)The maximum phase-lag and the maximum phase-lead occur between theirrespective break frequencies.The phase lag-lead compensator utilizes the best feature of the individual lag and lead portions,usually without their disadvantages.For example,the lag-lead compensation allows the introduction of phase lead to stabilize a system,while providing attenuation at higher frequencies to filter out noise.8.Feedback CompensationIn order to improve the system performances,besides the cascade compensation,the feedback compensation is often used as another scheme.By using local feedback compensation,almost same effect,as that of cascade compensation,can be obtained.Morever ,additional specific functions forimproving system perfprmance are obtained.。
