CISCOASA 5510中文最新配置案例
Asa 5510配置

Asa 5510的配置ciscoasa> en 进入系统Password:(没有密码的话直接回车)ciscoasa# conf t (进入全局)ciscoasa(config)# hostname xinhua (更改设备名称)xinhua(config)# int e0/0 (外网设置端口E0/0)xinhua(config-if)# nameif outside (外网接入名称)INFO: Security level for "outside" set to 0 by default.xinhua(config-if)# security-level 0(安全级别)xinhua(config-if)# ip address x.x.x.x x.x.x.x(ip地址:电信或网通的固定式)xinhua(config-if)# no shutdown(激活端口)xinhua(config-if)# int e0/1 (设置内网端口E0/1)xinhua(config-if)# nameif inside (内网接入名称)INFO: Security level for "inside" set to 100 by default.xinhua(config-if)# security-level 100 (安全级别)xinhua(config-if)# ip address 192.168.0.1 255.255.255.0(局域网ip)xinhua(config-if)# no shutdown(激活端口)xinhua(config-if)# int m0/0 (控制5510端口m0/0)xinhua(config-if)# nameif management (控制名称)INFO: Security level for "management" set to 0 by default.xinhua(config-if)# security-level 100 (安全级别)xinhua(config-if)# ip address 192.168.1.1 255.255.255.0(控制ip地址)xinhua(config-if)# no shutdown(激活端口)xinhua(config-if)# wr(保存设置)xinhua(config-if)# route outside 0.0.0.0 0.0.0.0 x.x.x.x(创建一条外网默认路由,通过网关:x.x.x.x 转发)xinhua(config)# global (outside) 1 interface(网通或电信只提供一个ip 时这么做,所以内网共享一个ip上网)INFO: outside interface address added to PA T poolxinhua(config)# nat (inside) 1 192.168.0.0 255.255.255.0(ip为内网的网段)xinhua(config)# access-list inside_to_outside extended permit icmp any anyxinhua(config)# access-list inside_to_outside extended permit ip any any xinhua(config)# wr配置完毕。
asa5510限速等配置

gametuzi(config)# hostname gametuzi5510 新的名字
gametuzi5510(config)# int e0/0 进入E0/0 接口
gametuzi5510(config-if)# security-level 0 配置安全级别 因为是外部接口,安全级别为最高
拓扑图如下:
限速配置如下:
access-list rate_limit_1 extended permit ip any host 192.168.1.2 //(限制192.168.1.2下载)
access-list rate_limit_1 extended permit ip host 192.168.1.2 any //(限制192.168.1.2上传)
gametuzi5510# conf t
gametuzi5510(config)# global (outside) 1 interface PAT地址转换!
gametuzi5510(config)# end
gametuzi5510# conf t
gametuzi5510(config)# route outside 0.0.0.0 0.0.0.0 192.168.3.254 默认路由 访问所有外部地址从192.168.3.254 流出。
Ciscoasa(config)#access-group 100 in intercae outside per-user-override
访问必须调用ACL
备注如果,只是需要将内网一个服务器映射到公网可以这样做
ciscoasa(config)#static (inside, outside) 219.139.*.* 192.168.16.254
ASA5510配置实例1

配置设备介绍:(只为做实验实际应用请根据自己具体情况更改相关参数即可)核心交换机 4507提供VLAN3 网关地址:192.168.3.254提供 DNS 服务器连接:192.168.0.1接入交换机 2960提供 VLAN3 TURNK 连接,可用IP 地址为192.168.3.0-192.168.3.240掩码:255.255.255.0网关:192.168.3.254DNS: 192.168.0.1内网实验防火墙 CISCO ASA 5510E0/0 IP:192.168.3.234E0/1 IP 10.1.1.1实现配置策略1. 动态内部 PC1 DHCP 自动获得IP 地址,可访问INTERNET,并PING 通外部网关。
PC1 Ethernet adapter 本地连接:Connection-specific DNS Suffix . : gametuziDescription . . . . . . . . . . . : Broadcom 440x rollerPhysical Address. . . . . . . . . : 00-13-77-04-9Dhcp Enabled. . . . . . . . . . . : YesAutoconfiguration Enabled . . . . : YesIP Address. . . . . . . . . . . . : 10.1.1.20Subnet Mask . . . . . . . . . . . : 255.255.0.0Default Gateway . . . . . . . . . : 10.1.1.1DHCP Server . . . . . . . . . . . : 10.1.1.1DNS Servers . . . . . . . . . . . : 192.168.0.12. 静态内部 PC2 手动分配地址,可访问 INTERNET ,并PING 通外部网关。
ASA5510防火墙VPN配置

ASA5510防火墙remote ipsec vpn配置1、IPSEC VPN 基本配置access-list no-nat extended permit ip//定义VPN数据流nat (inside) 0 access-list no-nat//设置IPSEC VPN数据不作nat翻译1ip local pool vpn-pool mask//划分地址池,用于VPN用户拨入之后分配的地址。
crypto ipsec transform-set vpnset esp-des esp-md5-hmac//定义一个变换集myset,用esp-md5加密的。
(网上一般都是用esp-3des esp-sha-hmac 或esp-des esp-sha-hmac,而我使用的防火墙没开启3des,所以只能使用esp-des;至于esp-sha-hmac ,不知为什么,使用它隧道组始终无法连接上,所以改用esp-md5-hmac。
具体原因不清楚。
)(补充:后来利用ASA5520防火墙做了关于esp-3des esp-sha-hmac 加密的测试,成功!)crypto dynamic-map dymap 10 set transform-set vpnset//把vpnset添加到动态加密策略dynmapcrypto dynamic-map dymap 10 set reverse-routecrypto map vpnmap 10 ipsec-isakmp dynamic dymap//把动态加密策略绑定到vpnmap动态加密图上crypto map vpnmap interface outside//把动态加密图vpnmap绑定到outside口2crypto isakmp identity addresscrypto isakmp enable outside// outside接口启用isakmpcrypto isakmp policy 10//进入isakmp的策略定义模式authentication pre-share//使用pre-shared key进行认证encryption des//定义协商用DES加密算法(与前面对应,这里使用des,而不是3des)hash md5//定义协商用md5加密算法(和前面一样,网上使用的是sha,我这里为了配合前面的esp-md5-hmac,而使用md5) group 2//定义协商组为2,标准有1、2、3、5等多组,主要用于块的大小和生命时间等3lifetime 86400//定义生命时间group-policy whjt internal//定义策略组(用于想进入的)想要运用策略组就必须用默认的策略组名,否则无法激活该组。
Cisco_A5510(HA)配置

Failover LAN Interface: failover Ethernet0/3 (up)
Unit Poll frequency 1 seconds, holdtime 15 seconds
Interface Poll frequency 5 seconds, holdtime 25 seconds
hostname(config)# interface Ethernet0/3
hostname(config-if)# no shutdown
hostname(config)# failover
hostname(config)# copy running-config startup-config
hostname(config-if)# failover lan unit secondary
hostname(config)# failover
hostname(config)# copy running-config startup-config
! 在配置完成后,主机自动将当前配置同步到备机上,此时在两台主机上show run看到的配置已经一致了。
注意:在配置完网络接口以后,运行no shutdown 启用接口。
A5510 -1 (Secondary Host):
hostname(config)# interface Ethernet0/3 description LAN Failover Interface
hostname(config)# failover lan interface failover Ethernet0/3
Cisco ASA5510 双出口策略路由配置

Asa/PIX的Static Route Tracking命令可以有效解决双ISP出口的问题存在问题:静态路由没有固定的机制来决定是否可用,即使下一跳不可达,静态路由还是会存在路由表里,是有当ASA自己的和这条路由相关接口down了,才会从路由表里删除解决办法:Static Route Tracking这个feature提供一种方法来追踪静态路由,当主路由失效时可以安装备份路由进路由表,例如:2条缺省指向不同ISP,当主的ISP 断了,可以立即启用备用ISP 链路,它是使用ICMP来进行追踪的,如果在一定holdtime没有收到reply的话就认为这条链路down了,就会立即删除该静态路由,预先设置的备份路由就会进入路由表。
注意:配置时要在outside口上放开icmp reply(如果打开了icmp限制)pixFirewall(config)#sla monitor sla_id #指定检测的slaIDPixfirewall(config-sla-monitor)# type echo protocol ipIcmpEcho target_ip interfaceif_name #指定检测的协议类型为ICMP协议,并指定检测目的地址和接口这个必须是个可以ping通的地址,当这个地址不可用时,track跟踪的路由就会被删除,备份路由进路由表pixFirewall(config)#sla monitor schedule sla_id [life {forever | seconds}][start-time {hh:mm [:ss][month day | day month]| pending | now | after hh:mm:ss}][ageout seconds][recurring]#指定一个Schedule,一般会是start now必须要写时间表,不然track的路由进不了路由表pixFirewall(config)# track track_id rtr sla_id reachability #指定一个TrackID,并要求追踪SlaID 的可达性pixFirewall(config)# route if_name dest_ip mask gateway_ip [admin_distance]track track_i #设定默认路由,并绑定一个TrackID配置实例:sla monitor 1type echo protocol ipIcmpEcho 202.1.1.2 interface dxsla monitor schedule 1 start-time now(必须配置,不然track的路由进不了路由表)track 2 rtr 1 reachabilityroute dx 0.0.0.0 0.0.0.0 202.1.1.2 1 track 2 (电信默认网关,会追踪地址的可达性)route wt 0.0.0.0 0.0.0.0 101.1.1.2 2 (网通默认网关)当配置的202.1.1.2 ping不通(ICMP协议不能Reachability)的时候,route dx 0.0.0.0 0.0.0.0 202.1.1.2 1就会在路由表里删除,并由第二条默认路由即route wt 0.0.0.0 0.0.0.0 101.1.1.2 2取代,当202.1.1.2恢复后,又会重新变为dx 0.0.0.0 0.0.0.0 202.1.1.2 1这个feature我想大家在很多项目里都会遇到,ASA可以有效解决!这与我们用路由器实现双出口备份是一样的,通过配置SAA,检查其连通性。
cisco ASA5510配置实例
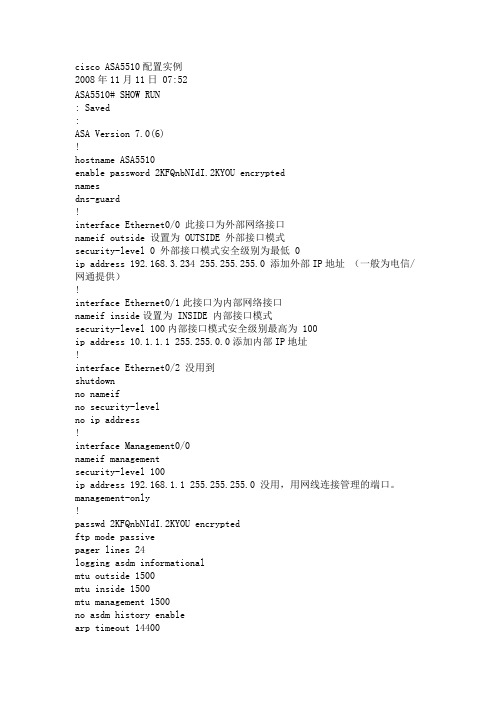
cisco ASA5510配置实例2008年11月11日 07:52ASA5510# SHOW RUN: Saved:ASA Version 7.0(6)!hostname ASA5510enable password 2KFQnbNIdI.2KYOU encryptednamesdns-guard!interface Ethernet0/0 此接口为外部网络接口nameif outside 设置为 OUTSIDE 外部接口模式security-level 0 外部接口模式安全级别为最低 0ip address 192.168.3.234 255.255.255.0 添加外部IP地址(一般为电信/网通提供)!interface Ethernet0/1此接口为内部网络接口nameif inside设置为 INSIDE 内部接口模式security-level 100内部接口模式安全级别最高为 100ip address 10.1.1.1 255.255.0.0添加内部IP地址!interface Ethernet0/2 没用到shutdownno nameifno security-levelno ip address!interface Management0/0nameif managementsecurity-level 100ip address 192.168.1.1 255.255.255.0 没用,用网线连接管理的端口。
management-only!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passivepager lines 24logging asdm informationalmtu outside 1500mtu inside 1500mtu management 1500no asdm history enablearp timeout 14400global (outside) 1 interface 一定要打表示 PAT端口扩展:“1”为其NAT ID nat (inside) 1 10.1.0.0 255.255.0.0 转换所有10.1.0.0 的内部地址route outside 0.0.0.0 0.0.0.0 192.168.3.254 1 缺省路由timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00timeout mgcp-pat 0:05:00 sip 0:30:00 sip_media 0:02:00timeout uauth 0:05:00 absolutehttp server enable 打开http serverhttp 192.168.1.0 255.255.255.0 management 限定能通过http方式访问防火墙的机器no snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstart telnet timeout 5ssh timeout 5console timeout 0dhcpd address 10.1.1.30-10.1.1.200 inside DHCP 自动提供分配范围为10.1.1.30-200dhcpd address 192.168.1.2-192.168.1.254 managementdhcpd dns 192.168.0.1 DNS 添加:可以是电信网通提供直接添加,或者自己的DNS服务器地址。
思科ASA 5510防火墙实战配置中文手册

思科A S A5510防火墙实战配置中文手册配置设备介绍:(只为做实验实际应用请根据自己具体情况更改相关参数即可)核心交换机 4507提供VLAN3 网关地址:192.168.3.254提供 DNS 服务器连接:192.168.0.1接入交换机 2960提供 VLAN3 TURNK 连接,可用IP 地址为192.168.3.0-192.168.3.240掩码:255.255.255.0网关:192.168.3.254DNS: 192.168.0.1内网实验防火墙 CISCO ASA 5510E0/0 IP:192.168.3.234E0/1 IP 10.1.1.1实现配置策略1. 动态内部 PC1 DHCP 自动获得IP 地址,可访问INTERNET,并PING 通外部网关。
PC1 Ethernet adapter 本地连接:Connection-specific DNS Suffix . : gametuziDescription . . . . . . . . . . . : Broadcom 440x rollerPhysical Address. . . . . . . . . : 00-13-77-04-9Dhcp Enabled. . . . . . . . . . . : YesAutoconfiguration Enabled . . . . : YesIP Address. . . . . . . . . . . . : 10.1.1.20Subnet Mask . . . . . . . . . . . : 255.255.0.0Default Gateway . . . . . . . . . : 10.1.1.1DHCP Server . . . . . . . . . . . : 10.1.1.1DNS Servers . . . . . . . . . . . : 192.168.0.12. 静态内部 PC2 手动分配地址,可访问 INTERNET ,并PING 通外部网关。
Cisco ASA 5510 (8.2) 配置过程

Cisco ASA 5510 (8.2)配置过程1.为了配置简单,准备安装ASDM(6.5)图形管理界面,经过查看手册和网上收集资料,我具体安装方法如下:1)从随机光盘里安装Java,然后安装ASDM,安装比较简单,也不需要做什么配置;刚开始是win7 64位操作系统,然后直接安装ASDM,提示需要安装Java,直接从Oracle 网上下载最新版本安装,再安装ASDM还是提示需要安装Java,怀疑环境变量的问题,进行设置,还是没有弄好。
系统本来有点慢,格了安装XP,直接从光盘安装Java(1.6),再安装ASDM,什么也不用设置,一切正常。
2)用串口线连接进5510,需要进行简单设置才能使用ASDM正常登录。
串口下输入以下命令:ciscoasa>ciscoasa> enPassword:ciscoasa# conf t 进入全局模式ciscoasa(config)# web*** 进入WEB***模式(经过测试不进这个模式,直接设置用户名和密码也可以)ciscoasa(config-web***)# username cisco password cisco 新建一个用户和密码ciscoasa(config)# int m 0/0 进入管理口ciscoasa(config-if)# ip address 172.16.0.1 255.255.255.0 添加IP地址(新设备默认就有管理IP:192.168.1.1)ciscoasa(config-if)# nameif guanli 给管理口设个名字ciscoasa(config-if)# no shutdown 激活接口ciscoasa(config)#q 退出管理接口ciscoasa(config)# http server enable 开启HTTP服务ciscoasa(config)# http 172.16.0.0 255.255.255.0 guanli 在管理口设置可管理的IP地址ciscoasa(config)# show run 查看一下配置ciscoasa(config)# wr m 保存经过以上配置就可以用ASDM配置防火墙了。
ASA 5510中文最新配置案例

GAMETUZI 企业应用 07-8-20 设备CISCO ASA5510 购买时间07年8月20日案例一ASA5510# SHOW RUN: Saved:ASA Version 7.0(6)!hostname ASA5510enable password 2KFQnbNIdI.2KYOU encryptednamesdns-guard!interface Ethernet0/0 此接口为外部网络接口nameif outside 设置为 OUTSIDE 外部接口模式security-level 0 外部接口模式安全级别为最高 0ip address 192.168.3.234 255.255.255.0 添加外部IP地址(一般为电信÷网通提供)!interface Ethernet0/1此接口为内部网络接口nameif inside设置为 INSIDE 内部接口模式security-level 100内部接口模式安全级别为 100ip address 10.1.1.1 255.255.0.0添加内部IP地址(一般为公司自行分配)!interface Ethernet0/2没用到 SHUTDOWN 关闭shutdownno nameifno security-levelno ip address!interface Management0/0没用到 SHUTDOWN 关闭nameif managementsecurity-level 100ip address 192.168.1.1 255.255.255.0 没用,用网线连接管理的端口。
management-only!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passivepager lines 24logging asdm informationalmtu outside 1500mtu inside 1500mtu management 1500no asdm history enablearp timeout 14400global (outside) 1 interface 一定要打表示 PAT端口扩展:“1”为其NAT IDnat (inside) 1 10.1.0.0 255.255.0.0 转换所有10.1.0.0 的内部地址route outside 0.0.0.0 0.0.0.0 192.168.3.254 1 内部所有地址访问外部地址出口为电信-网通提供的网关地址timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00timeout mgcp-pat 0:05:00 sip 0:30:00 sip_media 0:02:00timeout uauth 0:05:00 absolutehttp server enablehttp 192.168.1.0 255.255.255.0 managementno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstarttelnet timeout 5ssh timeout 5console timeout 0dhcpd address 10.1.1.30-10.1.1.200 inside DHCP 自动提供分配范围为10.1.1.30-200 dhcpd address 192.168.1.2-192.168.1.254 management 无效dhcpd dns 192.168.0.1 DNS 添加:可以是电信网通提供直接添加,或者自己的DNS服务器地址。
ASA 5510 配置案例(解决端口映射问题)

ASA 5510 配置案例(解决端口映射问题).txt老公如果你只能在活一天,我愿用我的生命来延续你的生命,你要快乐的生活在提出分手的时候请不要说还爱我。
Cisco ASA 5505防火墙端口映射问题解决基本情况:WAN: 221.221.147.195 Gateway: 221.221.147.200 LAN: 192.168.0.1内网中有一台服务器,地址: 192.168.0.10 端口: 8089故障描述: 内网可正常连接至服务器,外网无法连接. 端口映射出现问题.解决方法: 命令行错误, 已更正并解决.问题重点: 采用 "static (inside,outside) 221.221.147.195 192.168.0.10 tcp 8089" 映射.目前配置如下:ASA Version 7.2(2)!hostname ciscoasaenable password 8Ry2YjIyt7RRXU24 encryptednames!interface Vlan1nameif insidesecurity-level 100ip address 192.168.0.1 255.255.255.0!interface Vlan2nameif outsidesecurity-level 0ip address 221.221.147.195 255.255.255.252!interface Ethernet0/0switchport access vlan 2!interface Ethernet0/1!interface Ethernet0/2!!interface Ethernet0/4!interface Ethernet0/5!interface Ethernet0/6!interface Ethernet0/7!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passiveaccess-list 101 extended permit tcp any host 221.221.147.195 eq 8089access-list 101 extended permit icmp any anyaccess-list 101 extended permit tcp any anyaccess-list 101 extended permit udp any anypager lines 24logging asdm informationalmtu inside 1500mtu outside 1500icmp unreachable rate-limit 1 burst-size 1no asdm history enablearp timeout 14400global (outside) 1 interfacestatic (inside,outside) 221.221.147.195 192.168.0.10 netmask 255.255.255.255 tcp 8089 0access-group 101 in interface outsideroute outside 0.0.0.0 0.0.0.0 221.221.147.200 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout uauth 0:05:00 absolutehttp server enableno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstarttelnet timeout 5ssh timeout 5console timeout 0dhcpd auto_config outside!!class-map inspection_defaultmatch default-inspection-traffic!policy-map type inspect dns preset_dns_mapparametersmessage-length maximum 512policy-map global_policyclass inspection_defaultinspect dns preset_dns_mapinspect ftpinspect h323 h225inspect h323 rasinspect rshinspect rtspinspect esmtpinspect sqlnetinspect skinnyinspect sunrpcinspect xdmcpinspect sipinspect netbiosinspect tftp!service-policy global_policy globalprompt hostname contextCryptochecksum:30e219cbc04a4c919e7411de55e14a64: endciscoasa(config)#------------------------------------------------------------在找寻解决方案过程中,有朋友做了重要提示, 采用: static (inside,outside) int 192.168.0.10 tcp 8089 做映射,但出现警告提示:WARNING: static redireting all traffics at outside interface;WARNING: all services terminating at outside interface are disabled.后来将命令改成: static (inside,outside) 221.221.147.195 192.168.0.10 tcp 8089 问题解决.这几天又配置一个asa5505的防火墙采用static (inside,outside) 221.221.147.195 192.168.0.10 tcp 8089 不通。
CISCOASA5510配置手册

CISCOASA5510 // OKciscoasa#showverCiscoAdaptiveSecurityApplianceSoftwareVersion7.2(4) DeviceManagerVersion5.2(4)CompiledonSun06-Apr-0813:39bybuildersSystemimagefileis"disk0:/asa724-k8.bin" Configfileatbootwas"startup-config"ciscoasaup3mins5secsHardware:ASA5520,512MBRAM,CPUPentium4Celeron2000MHz InternalATACompactFlash,256MBBIOSFlashFirmwareHub@0xffe00000,1024KBEncryptionhardwaredevice:CiscoASA-55x0on-boardaccelerator(revision0x0) Bootmicrocode:CNlite-MC-Boot-Cisco-1.2SSL/IKEmicrocode:CNlite-MC-IPSEC-Admin-3.03IPSecmicrocode:CNlite-MC-IPSECm-MAIN-2.050:Ext:GigabitEthernet0/0:addressisc47d.4f85.1708,irq91:Ext:GigabitEthernet0/1:addressisc47d.4f85.1709,irq92:Ext:GigabitEthernet0/2:addressisc47d.4f85.170a,irq93:Ext:GigabitEthernet0/3:addressisc47d.4f85.170b,irq94:Ext:Management0/0:addressisc47d.4f85.1707,irq115:Int:Notused:irq116:Int:Notused:irq5MaximumVLANs:150InsideHosts:UnlimitedFailover:Active/ActiveVPN-DES:EnabledVPN-3DES-AES:DisabledSecurityContexts:2GTP/GPRS:DisabledVPNPeers:750WebVPNPeers:2ThisplatformhasanASA5520VPNPluslicense.SerialNumber:JMX1406L0Y6RunningActivationKey:0x6a2659550xf07c223d0x2cf345f40xb34478840xc128879b Configurationregisteris0x1Configurationlastmodifiedbyenable_15at12:23:52.072UTCMonSep62010 ciscoasa#showrun:Saved:ASAVersion7.2(4)!hostnameciscoasadomain-namedefault.domain.invalidenablepasswordgfFm2E3sthJOc7bqencryptedpasswd2KFQnbNIdI.2KYOUencryptednames!interfaceGigabitEthernet0/0nameifuntrust!interfaceGigabitEthernet0/1 nameifdmzsecurity-level50ipaddress172.18.19.254255.255.255.0!interfaceGigabitEthernet0/2 nameiftrustsecurity-level100ipaddress172.18.1.1255.255.255.0!interfaceGigabitEthernet0/3nonameifnosecurity-levelnoipaddress!interfaceManagement0/0 nameifmanagementsecurity-level100ipaddress192.168.1.1255.255.255.0 management-only!ftpmodepassivednsserver-groupDefaultDNSdomain-namedefault.domain.invalid access-list102extendedpermiticmpanyany access-list102extendedpermitipanyany pagerlines24loggingenablemtudmz1500mtutrust1500mtumanagement1500nofailovericmpunreachablerate-limit1burst-size1asdmimagedisk0:/ASDM-524.BINnoasdmhistoryenablearptimeout14400global(untrust)1interfacenat(trust)10.0.0.00.0.0.0static(trust,untrust)tcp113.105.88.5786172.18.11.886netmask255.255.255.255static(trust,untrust)tcp113.105.88.575000172.18.11.85000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.586800172.18.11.1306800netmask255.255.255.255 static(trust,untrust)tcp113.105.88.584800172.18.11.1304800netmask255.255.255.255 static(trust,untrust)tcp113.105.88.583306172.18.11.1303306netmask255.255.255.255 static(trust,untrust)udp113.105.88.586800172.18.11.1306800netmask255.255.255.255 static(trust,untrust)udp113.105.88.584800172.18.11.1304800netmask255.255.255.255 static(trust,untrust)udp113.105.88.583306172.18.11.1303306netmask255.255.255.255 static(trust,untrust)tcp113.105.88.5881172.18.11.13081netmask255.255.255.255 static(trust,untrust)udp113.105.88.5881172.18.11.13081netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601011172.18.11.91011netmask255.255.255.255 static(trust,untrust)udp113.105.88.601011172.18.11.91011netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601018172.18.11.91018netmask255.255.255.255 static(trust,untrust)udp113.105.88.601018172.18.11.91018netmask255.255.255.255 static(trust,untrust)tcp113.105.88.5981172.18.15.99wwwnetmask255.255.255.255 static(trust,untrust)tcp113.105.88.592000172.18.15.992000netmask255.255.255.255 static(trust,untrust)udp113.105.88.592000172.18.15.992000netmask255.255.255.255 static(trust,untrust)udp113.105.88.59www172.18.15.99wwwnetmask255.255.255.255 static(trust,untrust)tcp113.105.88.598080172.18.15.998080netmask255.255.255.255static(trust,untrust)tcp113.105.88.59ftp-data172.18.11.123ftp-datanetmask255.255.255.255 static(trust,untrust)tcp113.105.88.59ftp172.18.11.123ftpnetmask255.255.255.255static(trust,untrust)tcp113.105.88.59telnet172.18.11.123telnetnetmask255.255.255.255 static(trust,untrust)tcp113.105.88.591010172.18.11.1231000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598003172.18.11.1238003netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598010172.18.11.1238010netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598012172.18.11.1238012netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598880172.18.11.1238880netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601012172.18.11.91012netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601013172.18.11.91013netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601014172.18.11.91014netmask255.255.255.255 static(trust,untrust)udp113.105.88.601012172.18.11.91012netmask255.255.255.255 static(trust,untrust)udp113.105.88.601013172.18.11.91013netmask255.255.255.255 static(trust,untrust)udp113.105.88.601014172.18.11.91014netmask255.255.255.255 static(trust,untrust)tcp113.105.88.595000172.18.15.995000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.594000172.18.15.994000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602000172.18.11.92000netmask255.255.255.255 static(trust,untrust)udp113.105.88.602000172.18.11.92000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.592009172.18.15.992009netmask255.255.255.255 static(trust,untrust)udp113.105.88.592009172.18.15.992009netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598081172.18.15.998081netmask255.255.255.255 static(trust,untrust)udp113.105.88.598081172.18.15.998081netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602001172.18.11.92001netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602002172.18.11.92002netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602003172.18.11.92003netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602004172.18.11.92004netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602005172.18.11.92005netmask255.255.255.255static(trust,untrust)tcp113.105.88.602010172.18.11.92010netmask255.255.255.255 static(trust,untrust)udp113.105.88.602001172.18.11.92001netmask255.255.255.255 static(trust,untrust)udp113.105.88.602002172.18.11.92002netmask255.255.255.255 static(trust,untrust)udp113.105.88.602003172.18.11.92003netmask255.255.255.255 static(trust,untrust)udp113.105.88.602004172.18.11.92004netmask255.255.255.255 static(trust,untrust)udp113.105.88.602005172.18.11.92005netmask255.255.255.255 static(trust,untrust)udp113.105.88.602006172.18.11.92006netmask255.255.255.255 static(trust,untrust)udp113.105.88.602007172.18.11.92007netmask255.255.255.255 static(trust,untrust)udp113.105.88.602008172.18.11.92008netmask255.255.255.255 static(trust,untrust)udp113.105.88.602009172.18.11.92009netmask255.255.255.255 static(trust,untrust)udp113.105.88.602010172.18.11.92010netmask255.255.255.255 static(trust,untrust)113.105.88.61172.18.11.10netmask255.255.255.255access-group102ininterfaceuntrustrouteuntrust0.0.0.00.0.0.010.92.8.91routetrust172.18.11.0255.255.255.0172.18.1.21routetrust172.18.12.0255.255.255.0172.18.1.21routetrust172.18.13.0255.255.255.0172.18.1.21routetrust172.18.14.0255.255.255.0172.18.1.21routetrust172.18.15.0255.255.255.0172.18.1.21routetrust172.18.16.0255.255.255.0172.18.1.21routetrust172.18.17.0255.255.255.0172.18.1.21routetrust172.18.18.0255.255.255.0172.18.1.21timeoutxlate3:00:00timeoutconn1:00:00half-closed0:10:00udp0:02:00icmp0:00:02timeoutsunrpc0:10:00h3230:05:00h2251:00:00mgcp0:05:00mgcp-pat0:05:00 timeoutsip0:30:00sip_media0:02:00sip-invite0:03:00sip-disconnect0:02:00 timeoutsip-provisional-media0:02:00uauth0:05:00absolutenosnmp-serverlocationnosnmp-servercontactsnmp-serverenabletrapssnmpauthenticationlinkuplinkdowncoldstart telnet0.0.0.00.0.0.0trusttelnettimeout5ssh0.0.0.00.0.0.0untrustsshtimeout30consoletimeout0usernameadminpasswordf3UhLvUj1QsXsuK7encrypted!!prompthostnamecontextCryptochecksum:634aa0023e75546939c8b013c69a61b7:endciscoasa#showstartciscoasa#showstartup-config:Saved:Writtenbyenable_15at12:24:22.081UTCMonSep62010!ASAVersion7.2(4)!hostnameciscoasadomain-namedefault.domain.invalidenablepasswordgfFm2E3sthJOc7bqencryptedpasswd2KFQnbNIdI.2KYOUencryptednames!interfaceGigabitEthernet0/0nameifuntrust!interfaceGigabitEthernet0/1 nameifdmzsecurity-level50ipaddress172.18.19.254255.255.255.0!interfaceGigabitEthernet0/2 nameiftrustsecurity-level100ipaddress172.18.1.1255.255.255.0!interfaceGigabitEthernet0/3nonameifnosecurity-levelnoipaddress!interfaceManagement0/0 nameifmanagementsecurity-level100ipaddress192.168.1.1255.255.255.0 management-only!ftpmodepassivednsserver-groupDefaultDNSdomain-namedefault.domain.invalid access-list102extendedpermiticmpanyany access-list102extendedpermitipanyany pagerlines24loggingenablemtudmz1500mtutrust1500mtumanagement1500nofailovericmpunreachablerate-limit1burst-size1asdmimagedisk0:/ASDM-524.BINnoasdmhistoryenablearptimeout14400global(untrust)1interfacenat(trust)10.0.0.00.0.0.0static(trust,untrust)tcp113.105.88.5786172.18.11.886netmask255.255.255.255static(trust,untrust)tcp113.105.88.575000172.18.11.85000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.586800172.18.11.1306800netmask255.255.255.255 static(trust,untrust)tcp113.105.88.584800172.18.11.1304800netmask255.255.255.255 static(trust,untrust)tcp113.105.88.583306172.18.11.1303306netmask255.255.255.255 static(trust,untrust)udp113.105.88.586800172.18.11.1306800netmask255.255.255.255 static(trust,untrust)udp113.105.88.584800172.18.11.1304800netmask255.255.255.255 static(trust,untrust)udp113.105.88.583306172.18.11.1303306netmask255.255.255.255 static(trust,untrust)tcp113.105.88.5881172.18.11.13081netmask255.255.255.255 static(trust,untrust)udp113.105.88.5881172.18.11.13081netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601011172.18.11.91011netmask255.255.255.255 static(trust,untrust)udp113.105.88.601011172.18.11.91011netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601018172.18.11.91018netmask255.255.255.255 static(trust,untrust)udp113.105.88.601018172.18.11.91018netmask255.255.255.255 static(trust,untrust)tcp113.105.88.5981172.18.15.99wwwnetmask255.255.255.255 static(trust,untrust)tcp113.105.88.592000172.18.15.992000netmask255.255.255.255 static(trust,untrust)udp113.105.88.592000172.18.15.992000netmask255.255.255.255 static(trust,untrust)udp113.105.88.59www172.18.15.99wwwnetmask255.255.255.255 static(trust,untrust)tcp113.105.88.598080172.18.15.998080netmask255.255.255.255static(trust,untrust)udp113.105.88.598000172.18.11.1238000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.596999172.18.11.1236999netmask255.255.255.255 static(trust,untrust)tcp113.105.88.59ftp-data172.18.11.123ftp-datanetmask255.255.255.255 static(trust,untrust)tcp113.105.88.59ftp172.18.11.123ftpnetmask255.255.255.255static(trust,untrust)tcp113.105.88.59telnet172.18.11.123telnetnetmask255.255.255.255 static(trust,untrust)tcp113.105.88.591010172.18.11.1231000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598003172.18.11.1238003netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598010172.18.11.1238010netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598012172.18.11.1238012netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598880172.18.11.1238880netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601012172.18.11.91012netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601013172.18.11.91013netmask255.255.255.255 static(trust,untrust)tcp113.105.88.601014172.18.11.91014netmask255.255.255.255 static(trust,untrust)udp113.105.88.601012172.18.11.91012netmask255.255.255.255 static(trust,untrust)udp113.105.88.601013172.18.11.91013netmask255.255.255.255 static(trust,untrust)udp113.105.88.601014172.18.11.91014netmask255.255.255.255 static(trust,untrust)tcp113.105.88.595000172.18.15.995000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.594000172.18.15.994000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602000172.18.11.92000netmask255.255.255.255 static(trust,untrust)udp113.105.88.602000172.18.11.92000netmask255.255.255.255 static(trust,untrust)tcp113.105.88.592009172.18.15.992009netmask255.255.255.255 static(trust,untrust)udp113.105.88.592009172.18.15.992009netmask255.255.255.255 static(trust,untrust)tcp113.105.88.598081172.18.15.998081netmask255.255.255.255 static(trust,untrust)udp113.105.88.598081172.18.15.998081netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602001172.18.11.92001netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602002172.18.11.92002netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602003172.18.11.92003netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602004172.18.11.92004netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602005172.18.11.92005netmask255.255.255.255static(trust,untrust)tcp113.105.88.602008172.18.11.92008netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602009172.18.11.92009netmask255.255.255.255 static(trust,untrust)tcp113.105.88.602010172.18.11.92010netmask255.255.255.255 static(trust,untrust)udp113.105.88.602001172.18.11.92001netmask255.255.255.255 static(trust,untrust)udp113.105.88.602002172.18.11.92002netmask255.255.255.255 static(trust,untrust)udp113.105.88.602003172.18.11.92003netmask255.255.255.255 static(trust,untrust)udp113.105.88.602004172.18.11.92004netmask255.255.255.255 static(trust,untrust)udp113.105.88.602005172.18.11.92005netmask255.255.255.255 static(trust,untrust)udp113.105.88.602006172.18.11.92006netmask255.255.255.255 static(trust,untrust)udp113.105.88.602007172.18.11.92007netmask255.255.255.255 static(trust,untrust)udp113.105.88.602008172.18.11.92008netmask255.255.255.255 static(trust,untrust)udp113.105.88.602009172.18.11.92009netmask255.255.255.255 static(trust,untrust)udp113.105.88.602010172.18.11.92010netmask255.255.255.255 static(trust,untrust)113.105.88.61172.18.11.10netmask255.255.255.255access-group102ininterfaceuntrustrouteuntrust0.0.0.00.0.0.010.92.8.91routetrust172.18.11.0255.255.255.0172.18.1.21routetrust172.18.12.0255.255.255.0172.18.1.21routetrust172.18.13.0255.255.255.0172.18.1.21routetrust172.18.14.0255.255.255.0172.18.1.21routetrust172.18.15.0255.255.255.0172.18.1.21routetrust172.18.16.0255.255.255.0172.18.1.21routetrust172.18.17.0255.255.255.0172.18.1.21routetrust172.18.18.0255.255.255.0172.18.1.21timeoutxlate3:00:00timeoutconn1:00:00half-closed0:10:00udp0:02:00icmp0:00:02timeoutsunrpc0:10:00h3230:05:00h2251:00:00mgcp0:05:00mgcp-pat0:05:00 timeoutsip0:30:00sip_media0:02:00sip-invite0:03:00sip-disconnect0:02:00 timeoutsip-provisional-media0:02:00uauth0:05:00absolutehttpserverenablehttp0.0.0.00.0.0.0trustnosnmp-serverlocationnosnmp-servercontactsnmp-serverenabletrapssnmpauthenticationlinkuplinkdowncoldstart telnet0.0.0.00.0.0.0trusttelnettimeout5ssh0.0.0.00.0.0.0untrustsshtimeout30consoletimeout0usernameadminpasswordf3UhLvUj1QsXsuK7encrypted!!prompthostnamecontextCryptochecksum:634aa0023e75546939c8b013c69a61b7 ciscoasa#。
ASA5510 配置手册

ASA5510配置手册首先通过超级终端用串口线连接到ASA5510 console口上,设置如图:1.设置主机名:<config>#hostname szhndasa2.设置时区:szhndasa<config>#clock timezone EST 73.设置时钟:Szhndasa#clock set 15:45:30 28 FEB 20084.配置内接口IPSzhndasa<config>#int Ethernet 0/0Szhndasa<config-if>#nameif insideSzhndasa<config-if>#security-level 100Szhndasa<config-if>#ip address 192.168.55.254 255.255.255.05配置外部接口IPSzhndasa<config>#int Ethernet 0/1Szhndasa<config-if>#nameif outsideSzhndasa<config-if>#security-level 0Szhndasa<config-if>#ip address 210.X.X.X 255.255.255.2486.配置用户名和密码Szhndasa<config>#username admin password ********* encrypted privilege 15 注:15表示有最高权限7.配置HTTP和TELNETSzhndasa<config>#aaa authentication telnet console LOCALSzhndasa<config>#http server enableSzhndasa<config>#http 192.168.55.0 255.255.255.0 insideSzhndasa<config>#telnet 192.168.55.0 255.255.255.0 inside8.配置site to site vpncrypto map outside_map 20 match address outside_cryptomap_20_1 crypto map outside_map 20 set pfscrypto map outside_map 20 set peer 210.75.1.Xcrypto map outside_map 20 set transform-set ESP-3DES-SHAcrypto map outside_map 20 set nat-t-disablecrypto map outside_map interface outside注:还可通过http方式用ASDM管理软件图形化配置ASA。
使用中控WebSight发布的防火墙ASA5510配置说明

使⽤中控WebSight发布的防⽕墙ASA5510配置说明使⽤WebSight发布的防⽕墙配置说明⼀、综述在某项⽬中⽤户要求利⽤DCS数据服务站将⼯艺装置的数据通过WEB发布,在⼚长办公室的办公电脑上可以实时查看控制装置的信息,同时为了防⽌⼯⼚管理⽹的病毒等侵⼊控制⽹,在两者之间设置了⼀个防⽕墙。
⼆、硬件配置2.1 DCS控制室1)历史数据服务器电脑⼀台。
配置4块⽹卡,其中3块连接DCS内部的控制⽹和操作⽹;第四块⽹卡作为web发布端⼝。
操作系统WINDOWS XP。
2)思科防⽕墙ASA5510⼀台。
3)⽹络双绞线若⼲。
2.2 ⼚长办公室1)办公电脑⼀台。
此电脑有⼀块单独⽤于和DCS通讯的⽹卡接⼝。
操作系统WINDOWS XP,安装了IE浏览器。
2)若有⼚长办公室内有多台电脑需要连接查看控制装置信息需要配置交换机。
2.3连接附件1)根据CCR中央控制室和⼚长办公室距离的不同,需要配置相应的光纤,光纤尾纤,光纤跳线和光纤接续盒等。
三、软件配置2.1 DCS控制室1)WINDOWS XP,并安装IIS(Internet 信息服务)组件。
2)AdvanTrol Pro2.5 SP06。
3)PIMS WebSight 发布软件2.2⼚长办公室1)WINDOWS XP,并安装了IE6.0以上的版本。
四、参考⽂件1)《中控WebSight监控软件Web发布软件使⽤⼿册》及《Internet 信息服务组件IIS安装规范》2)《ASA5510 User Manual》五、⽹络拓扑图整个⽹络拓扑结构如下图所⽰:第 2 页共10 页六、连接步骤6.1 在历史数据服务器HS140上安装IIS服务组件,websight发布软件。
设置第四块⽹卡的IP地址为:172.30.1.140,⼦⽹掩码为:255.255.255.0,默认⽹关为:172.30.1.1。
注意默认⽹关不能忘记设置。
如下图所⽰做好组态,点击web发布命令,启动监控软件,为DCS数据web发布做好准备。
asa5510新增vpn用户

确定一至,单击 SAVE -保存。 第三步:单击-Connect
第四步:输入分配的用户名和密码
电脑屏幕右下脚出现:
,VPN 已经拨通。
客户端配置 VPN
1、客户端的配置 我使用的客户端是 cisco VPN Client 5.0,配置如下图,
第一:单击 Biblioteka EWConnection Entry: CBTnews Host:114.113.222.98 name:vpnclint password:cisco confirm password: cisco
添加vpn用户1telnet你的防火墙101112输入防火墙密码cisco3在尖括号模式下输入en4输入密码进入模式5输入confitt6输入username你的用户名password你的密码完成回车7输入exit进入模式8输入wr保存9代码如下
添加 VPN 用户
1 telnet 你的防火墙 10.1.1.1 2 输入防火墙密码 cisco 3 在尖括号模式下 输入 en 4 输入密码 进入#模式 5 输入 confit t 6 输 入 username 你 的 用 户 名 password 你 的 密 码 完 成 回 车 7 输入 exit 进入#模式 8 输入 wr 保存 9 代码如下: 10
ASA 5510限制客户端并发连接数和流量

近期公司网站遭到大量攻击,内网ping网站ip 丢包很严重。
查看asa 状态如图:01.asdm 上面看到的攻击状态:02. 连接状态如下:03. 在服务器上看到的出现大量time waite 状态的连接(全是无效连接),导致web服务器很卡,严重丢包,cpu和内存正常。
04. 处理办法:a.检测是不是web服务器有没有大量的对外的连接(非80端口)是不是中毒之类的。
b.在asa防火墙上限制客户端的并发连接数和流量:第一种:hostname(config)# access-list allip permit ip any any 设置需限制的访问列表hostname(config)# class-map c_all_ip 设置类别图hostname(config-cmap)# match access-list allip 匹配访问列表alliphostname(config)# policy-map p_all_ip 设置策略图p_all_iphostname(config-pmap)# class c_all_ip 使用类别c_all_iphostname(config-pmap-c)# set connection per-client-max 50 (限制每客户端连接数最大50)hostname(config-pmap-c)# police output 250000 限制此类别速率bit/shostname(config)# service-policy p_all_ip interface outside(将策略应用到接口,每个接口只能用一个策略图policy-map)注:在policy-map里面使用命令set connection conn-max 10 现实最大连接数10个set connection embryonic-conn-max 5 限制最大的半打开连接时5个set connection per-client-max 10 限制每用户最大连接数10个set connection per-client-embryonic-max 5 限制每用户最大半打开连接数5个police output 10000 20000 conform-action drop 出口速率10000B,允许爆发到20000,违反规则丢弃数据包例子:access-list 101 extended permit tcp any host 192.168.0.115 eq wwwclass-map c_all_ipmatch access-list 101policy-map p_call_ipclass c_all_ipset connection embryonic-conn-max 60 per-client-max 60service-policy p_call_ip interface outside超过60个连接,在asa日志上可以看到以下内容:说明已经生效了。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
GAMETUZI 企业应用 07-8-20 设备CISCO ASA5510 购买时间07年8月20日案例一
ASA5510# SHOW RUN
: Saved
:
ASA Version 7.0(6)
!
hostname ASA5510
enable password 2KFQnbNIdI.2KYOU encrypted
names
dns-guard
!
interface Ethernet0/0 此接口为外部网络接口
nameif outside 设置为 OUTSIDE 外部接口模式
security-level 0 外部接口模式安全级别为最高 0
ip address 192.168.3.234 255.255.255.0 添加外部IP地址(一般为电信÷网通提供)!
interface Ethernet0/1此接口为内部网络接口
nameif inside设置为 INSIDE 内部接口模式
security-level 100内部接口模式安全级别为 100
ip address 10.1.1.1 255.255.0.0添加内部IP地址(一般为公司自行分配)
!
interface Ethernet0/2没用到 SHUTDOWN 关闭
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0没用到 SHUTDOWN 关闭
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0 没用,用网线连接管理的端口。
management-only
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
pager lines 24
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu management 1500
no asdm history enable
arp timeout 14400
global (outside) 1 interface 一定要打表示 PAT端口扩展:“1”为其NAT ID
nat (inside) 1 10.1.0.0 255.255.0.0 转换所有10.1.0.0 的内部地址
route outside 0.0.0.0 0.0.0.0 192.168.3.254 1 内部所有地址访问外部地址出口为电信-网通提供的网关地址
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00
timeout mgcp-pat 0:05:00 sip 0:30:00 sip_media 0:02:00
timeout uauth 0:05:00 absolute
http server enable
http 192.168.1.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
telnet timeout 5
ssh timeout 5
console timeout 0
dhcpd address 10.1.1.30-10.1.1.200 inside DHCP 自动提供分配范围为10.1.1.30-200 dhcpd address 192.168.1.2-192.168.1.254 management 无效
dhcpd dns 192.168.0.1 DNS 添加:可以是电信网通提供直接添加,或者自己的DNS服务器地址。
dhcpd lease 3600
dhcpd ping_timeout 50
dhcpd domain suzhou.jy 域名
dhcpd enable inside 打开内部网段自动分配
dhcpd enable management 无效
Cryptochecksum:6148633dac00f8f7a3418833f98d5ad4
: end
MSN AIPAOTUZI@以上很多命令都和PIX 不太相同,有不明白 MSN联系。
