Kernel whitening for one-class classification David M.J. Tax 1
oneclasssvm原理

oneclasssvm原理
One-Class SVM(支持向量机)是一种用于异常检测的机器学习算法。
它的原理基于支持向量机的思想,旨在通过构建一个边界来区分正常样本和异常样本。
One-Class SVM的原理可以分为以下几个步骤:
1. 数据预处理:首先,将训练数据集中的正常样本作为训练样本,不包含异常样本。
这些正常样本被假设为来自同一分布。
2. 特征转换:接下来,对训练样本进行特征转换,将其映射到高维空间中。
这可以通过使用核函数(如线性核、多项式核或高斯核)来实现。
3. 构建边界:在高维空间中,One-Class SVM试图找到一个超平面,使得正常样本位于超平面的一侧,而异常样本位于另一侧。
这个超平面被称为决策边界。
4. 寻找支持向量:One-Class SVM选择离决策边界最近的一些正常样本作为支持向量。
这些支持向量将决定决策边界的位置。
5. 异常检测:对于新的未知样本,通过计算其在高维空间中与决策边界的距离来进行异常检测。
如果距离超过某个阈值,那么该样本被判定为异常。
One-Class SVM的原理基于正常样本的分布特点,通过构建一个边界来区分正常样本和异常样本。
它在异常检测领域有着广泛的应用,例如网络入侵检测、欺诈检测等场景。
内核正常显示后安卓中出现白条
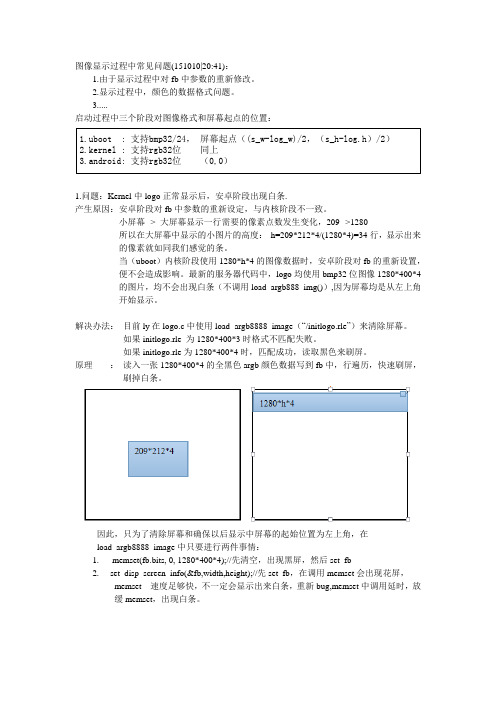
图像显示过程中常见问题(151010|20:41):1.由于显示过程中对fb中参数的重新修改。
2.显示过程中,颜色的数据格式问题。
3.....启动过程中三个阶段对图像格式和屏幕起点的位置:1.uboot : 支持bmp32/24,屏幕起点((s_w-log_w)/2,(s_h-log.h)/2)2.kernel : 支持rgb32位同上3.android: 支持rgb32位(0,0)1.问题:Kernel中logo正常显示后,安卓阶段出现白条.产生原因:安卓阶段对fb中参数的重新设定,与内核阶段不一致。
小屏幕--> 大屏幕显示一行需要的像素点数发生变化,209-->1280所以在大屏幕中显示的小图片的高度:h=209*212*4/(1280*4)=34行,显示出来的像素就如同我们感觉的条。
当(uboot)内核阶段使用1280*h*4的图像数据时,安卓阶段对fb的重新设置,便不会造成影响。
最新的服务器代码中,logo均使用bmp32位图像1280*400*4的图片,均不会出现白条(不调用load_argb888_img()),因为屏幕均是从左上角开始显示。
解决办法:目前ly在logo.c中使用load_argb8888_image(“/initlogo.rle”)来清除屏幕。
如果initlogo.rle 为1280*400*3时格式不匹配失败。
如果initlogo.rle为1280*400*4时,匹配成功,读取黑色来刷屏。
原理:读入一张1280*400*4的全黑色argb颜色数据写到fb中,行遍历,快速刷屏,刷掉白条。
因此,只为了清除屏幕和确保以后显示中屏幕的起始位置为左上角,在load_argb8888_image中只要进行两件事情:1. memset(fb.bits, 0, 1280*400*4);//先清空,出现黑屏,然后set_fb2.set_disp_screen_info(&fb,width,height);//先set_fb,在调用memset会出现花屏,memset 速度足够快,不一定会显示出来白条,重新bug,memset中调用延时,放缓memset,出现白条。
oneclasssvm参数

`OneClassSVM` 是一个无监督学习模型,它通常用于异常检测。
它不需要标签信息,并且假设数据点都是正常的,只有一小部分数据点是异常的。
在 `scikit-learn` 中,`OneClassSVM` 的参数包括:1. **kernel**:核函数。
可以是'linear', 'poly', 'rbf', 'sigmoid' 中的一个。
默认是 'rbf'。
2. **degree**:多项式核函数的度。
只在多项式核中有效。
3. **gamma**:核函数的系数。
如果 kernel 是 'linear',gamma 必须为 1。
如果 kernel 是 'poly','rbf' 或 'sigmoid',gamma 默认值为 1/(n_features * (n_features - 1) / 2)。
4. **coef0**:核函数的常数项。
只在 'poly' 和 'sigmoid' 中有效。
5. **nu**:nu-SVM 的参数。
它是一个介于 0 和 1 之间的值,控制错误分类的比例。
更大的 nu 更保守,将更多的点视为异常。
6. **kernel_params**:其他核函数参数。
例如,对于 'rbf' 核,您可以使用关键字参数 gamma, coef0, 或者 degree。
7. **eps**:决定异常的上界和下界之间的间隔的参数。
异常点在上下边界之外。
8. **metric**:距离度量方法,用于计算输入样本之间的距离。
可以是'euclidean', 'manhattan', 'chebyshev', 'hamming','jaccard' 或 'precomputed' 中的一个。
《Kernel Sparse Representation》中文翻译

Kernel Sparse Representation-BasedClassifier一、问题:1、针对不同类别的样本相互融合的分布情况,或者不能用线性的方法将它们有效分开的一般分类问题,SRC 失去了分类能力,如何选择一个有效的方法实现有效分类;2、KSR 虽然是SRC 的非线性扩展,但是它不能使用用于稀疏信号重构的方法,并且在实验中,测试时间较长,如何缩短测试时间;3、在KSRC 中,我们需要选择一个参数内核,例如一个RBF 内核,则必须选择有效的方法来确定相应的参数,使得效果优于SRC 的分类效果。
二、解决方法:为了解决以上的问题,在SRC 的基础上,文章引入了核函数。
核函数定义为: 1212(,)()()T k x x x x φφ=。
最常用的核函数分别有:高斯核径向基函数212122(,)()k x x exp x x γ=--,其中0γ>,还有线性核函数:1212(,)T k x x x x =等。
文章定义一个训练数据集:()(){}{},|,1,2,...,,1,2,...,m i i i i x y x X R y c i n ∈⊆∈=,其中,c 是类别的数目,m 是数据输入空间X 的维数,i y 是和i x 相对应的类标。
给定一个测试数据集x X ∈,我们的目标是从给定的c 类训练样本中预测出它的实际类标y 。
现在定义第j 类训练样本作为矩阵,1,[,...,],1,...,j j m n j j j n X x x R j c ⨯=∈=的各个列,其中,,j i x 被定义为第j 类样本,j n 是第j 类训练样本的数目。
下面定义新的训练样本矩阵来表示所有的样本数据:12c [,,...,]m n X X X X R ⨯=∈其中,1c j j n n ==∑.根据映射,将输入空间X (低维空间)的数据映射到核特征空间F (高维空间)中,有:12:()[(),(),...,()]T D x X x x x x F φφφφφ∈→=∈,其中,D m 是核特征空间F 的维度。
3GPP TS 36.331 V13.2.0 (2016-06)

3GPP TS 36.331 V13.2.0 (2016-06)Technical Specification3rd Generation Partnership Project;Technical Specification Group Radio Access Network;Evolved Universal Terrestrial Radio Access (E-UTRA);Radio Resource Control (RRC);Protocol specification(Release 13)The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented.This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organizational Partners' Publications Offices.KeywordsUMTS, radio3GPPPostal address3GPP support office address650 Route des Lucioles - Sophia AntipolisValbonne - FRANCETel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16InternetCopyright NotificationNo part may be reproduced except as authorized by written permission.The copyright and the foregoing restriction extend to reproduction in all media.© 2016, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC).All rights reserved.UMTS™ is a Trade Mark of ETSI registered for the benefit of its members3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational PartnersLTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM AssociationBluetooth® is a Trade Mark of the Bluetooth SIG registered for the benefit of its membersContentsForeword (18)1Scope (19)2References (19)3Definitions, symbols and abbreviations (22)3.1Definitions (22)3.2Abbreviations (24)4General (27)4.1Introduction (27)4.2Architecture (28)4.2.1UE states and state transitions including inter RAT (28)4.2.2Signalling radio bearers (29)4.3Services (30)4.3.1Services provided to upper layers (30)4.3.2Services expected from lower layers (30)4.4Functions (30)5Procedures (32)5.1General (32)5.1.1Introduction (32)5.1.2General requirements (32)5.2System information (33)5.2.1Introduction (33)5.2.1.1General (33)5.2.1.2Scheduling (34)5.2.1.2a Scheduling for NB-IoT (34)5.2.1.3System information validity and notification of changes (35)5.2.1.4Indication of ETWS notification (36)5.2.1.5Indication of CMAS notification (37)5.2.1.6Notification of EAB parameters change (37)5.2.1.7Access Barring parameters change in NB-IoT (37)5.2.2System information acquisition (38)5.2.2.1General (38)5.2.2.2Initiation (38)5.2.2.3System information required by the UE (38)5.2.2.4System information acquisition by the UE (39)5.2.2.5Essential system information missing (42)5.2.2.6Actions upon reception of the MasterInformationBlock message (42)5.2.2.7Actions upon reception of the SystemInformationBlockType1 message (42)5.2.2.8Actions upon reception of SystemInformation messages (44)5.2.2.9Actions upon reception of SystemInformationBlockType2 (44)5.2.2.10Actions upon reception of SystemInformationBlockType3 (45)5.2.2.11Actions upon reception of SystemInformationBlockType4 (45)5.2.2.12Actions upon reception of SystemInformationBlockType5 (45)5.2.2.13Actions upon reception of SystemInformationBlockType6 (45)5.2.2.14Actions upon reception of SystemInformationBlockType7 (45)5.2.2.15Actions upon reception of SystemInformationBlockType8 (45)5.2.2.16Actions upon reception of SystemInformationBlockType9 (46)5.2.2.17Actions upon reception of SystemInformationBlockType10 (46)5.2.2.18Actions upon reception of SystemInformationBlockType11 (46)5.2.2.19Actions upon reception of SystemInformationBlockType12 (47)5.2.2.20Actions upon reception of SystemInformationBlockType13 (48)5.2.2.21Actions upon reception of SystemInformationBlockType14 (48)5.2.2.22Actions upon reception of SystemInformationBlockType15 (48)5.2.2.23Actions upon reception of SystemInformationBlockType16 (48)5.2.2.24Actions upon reception of SystemInformationBlockType17 (48)5.2.2.25Actions upon reception of SystemInformationBlockType18 (48)5.2.2.26Actions upon reception of SystemInformationBlockType19 (49)5.2.3Acquisition of an SI message (49)5.2.3a Acquisition of an SI message by BL UE or UE in CE or a NB-IoT UE (50)5.3Connection control (50)5.3.1Introduction (50)5.3.1.1RRC connection control (50)5.3.1.2Security (52)5.3.1.2a RN security (53)5.3.1.3Connected mode mobility (53)5.3.1.4Connection control in NB-IoT (54)5.3.2Paging (55)5.3.2.1General (55)5.3.2.2Initiation (55)5.3.2.3Reception of the Paging message by the UE (55)5.3.3RRC connection establishment (56)5.3.3.1General (56)5.3.3.1a Conditions for establishing RRC Connection for sidelink communication/ discovery (58)5.3.3.2Initiation (59)5.3.3.3Actions related to transmission of RRCConnectionRequest message (63)5.3.3.3a Actions related to transmission of RRCConnectionResumeRequest message (64)5.3.3.4Reception of the RRCConnectionSetup by the UE (64)5.3.3.4a Reception of the RRCConnectionResume by the UE (66)5.3.3.5Cell re-selection while T300, T302, T303, T305, T306, or T308 is running (68)5.3.3.6T300 expiry (68)5.3.3.7T302, T303, T305, T306, or T308 expiry or stop (69)5.3.3.8Reception of the RRCConnectionReject by the UE (70)5.3.3.9Abortion of RRC connection establishment (71)5.3.3.10Handling of SSAC related parameters (71)5.3.3.11Access barring check (72)5.3.3.12EAB check (73)5.3.3.13Access barring check for ACDC (73)5.3.3.14Access Barring check for NB-IoT (74)5.3.4Initial security activation (75)5.3.4.1General (75)5.3.4.2Initiation (76)5.3.4.3Reception of the SecurityModeCommand by the UE (76)5.3.5RRC connection reconfiguration (77)5.3.5.1General (77)5.3.5.2Initiation (77)5.3.5.3Reception of an RRCConnectionReconfiguration not including the mobilityControlInfo by theUE (77)5.3.5.4Reception of an RRCConnectionReconfiguration including the mobilityControlInfo by the UE(handover) (79)5.3.5.5Reconfiguration failure (83)5.3.5.6T304 expiry (handover failure) (83)5.3.5.7Void (84)5.3.5.7a T307 expiry (SCG change failure) (84)5.3.5.8Radio Configuration involving full configuration option (84)5.3.6Counter check (86)5.3.6.1General (86)5.3.6.2Initiation (86)5.3.6.3Reception of the CounterCheck message by the UE (86)5.3.7RRC connection re-establishment (87)5.3.7.1General (87)5.3.7.2Initiation (87)5.3.7.3Actions following cell selection while T311 is running (88)5.3.7.4Actions related to transmission of RRCConnectionReestablishmentRequest message (89)5.3.7.5Reception of the RRCConnectionReestablishment by the UE (89)5.3.7.6T311 expiry (91)5.3.7.7T301 expiry or selected cell no longer suitable (91)5.3.7.8Reception of RRCConnectionReestablishmentReject by the UE (91)5.3.8RRC connection release (92)5.3.8.1General (92)5.3.8.2Initiation (92)5.3.8.3Reception of the RRCConnectionRelease by the UE (92)5.3.8.4T320 expiry (93)5.3.9RRC connection release requested by upper layers (93)5.3.9.1General (93)5.3.9.2Initiation (93)5.3.10Radio resource configuration (93)5.3.10.0General (93)5.3.10.1SRB addition/ modification (94)5.3.10.2DRB release (95)5.3.10.3DRB addition/ modification (95)5.3.10.3a1DC specific DRB addition or reconfiguration (96)5.3.10.3a2LWA specific DRB addition or reconfiguration (98)5.3.10.3a3LWIP specific DRB addition or reconfiguration (98)5.3.10.3a SCell release (99)5.3.10.3b SCell addition/ modification (99)5.3.10.3c PSCell addition or modification (99)5.3.10.4MAC main reconfiguration (99)5.3.10.5Semi-persistent scheduling reconfiguration (100)5.3.10.6Physical channel reconfiguration (100)5.3.10.7Radio Link Failure Timers and Constants reconfiguration (101)5.3.10.8Time domain measurement resource restriction for serving cell (101)5.3.10.9Other configuration (102)5.3.10.10SCG reconfiguration (103)5.3.10.11SCG dedicated resource configuration (104)5.3.10.12Reconfiguration SCG or split DRB by drb-ToAddModList (105)5.3.10.13Neighbour cell information reconfiguration (105)5.3.10.14Void (105)5.3.10.15Sidelink dedicated configuration (105)5.3.10.16T370 expiry (106)5.3.11Radio link failure related actions (107)5.3.11.1Detection of physical layer problems in RRC_CONNECTED (107)5.3.11.2Recovery of physical layer problems (107)5.3.11.3Detection of radio link failure (107)5.3.12UE actions upon leaving RRC_CONNECTED (109)5.3.13UE actions upon PUCCH/ SRS release request (110)5.3.14Proximity indication (110)5.3.14.1General (110)5.3.14.2Initiation (111)5.3.14.3Actions related to transmission of ProximityIndication message (111)5.3.15Void (111)5.4Inter-RAT mobility (111)5.4.1Introduction (111)5.4.2Handover to E-UTRA (112)5.4.2.1General (112)5.4.2.2Initiation (112)5.4.2.3Reception of the RRCConnectionReconfiguration by the UE (112)5.4.2.4Reconfiguration failure (114)5.4.2.5T304 expiry (handover to E-UTRA failure) (114)5.4.3Mobility from E-UTRA (114)5.4.3.1General (114)5.4.3.2Initiation (115)5.4.3.3Reception of the MobilityFromEUTRACommand by the UE (115)5.4.3.4Successful completion of the mobility from E-UTRA (116)5.4.3.5Mobility from E-UTRA failure (117)5.4.4Handover from E-UTRA preparation request (CDMA2000) (117)5.4.4.1General (117)5.4.4.2Initiation (118)5.4.4.3Reception of the HandoverFromEUTRAPreparationRequest by the UE (118)5.4.5UL handover preparation transfer (CDMA2000) (118)5.4.5.1General (118)5.4.5.2Initiation (118)5.4.5.3Actions related to transmission of the ULHandoverPreparationTransfer message (119)5.4.5.4Failure to deliver the ULHandoverPreparationTransfer message (119)5.4.6Inter-RAT cell change order to E-UTRAN (119)5.4.6.1General (119)5.4.6.2Initiation (119)5.4.6.3UE fails to complete an inter-RAT cell change order (119)5.5Measurements (120)5.5.1Introduction (120)5.5.2Measurement configuration (121)5.5.2.1General (121)5.5.2.2Measurement identity removal (122)5.5.2.2a Measurement identity autonomous removal (122)5.5.2.3Measurement identity addition/ modification (123)5.5.2.4Measurement object removal (124)5.5.2.5Measurement object addition/ modification (124)5.5.2.6Reporting configuration removal (126)5.5.2.7Reporting configuration addition/ modification (127)5.5.2.8Quantity configuration (127)5.5.2.9Measurement gap configuration (127)5.5.2.10Discovery signals measurement timing configuration (128)5.5.2.11RSSI measurement timing configuration (128)5.5.3Performing measurements (128)5.5.3.1General (128)5.5.3.2Layer 3 filtering (131)5.5.4Measurement report triggering (131)5.5.4.1General (131)5.5.4.2Event A1 (Serving becomes better than threshold) (135)5.5.4.3Event A2 (Serving becomes worse than threshold) (136)5.5.4.4Event A3 (Neighbour becomes offset better than PCell/ PSCell) (136)5.5.4.5Event A4 (Neighbour becomes better than threshold) (137)5.5.4.6Event A5 (PCell/ PSCell becomes worse than threshold1 and neighbour becomes better thanthreshold2) (138)5.5.4.6a Event A6 (Neighbour becomes offset better than SCell) (139)5.5.4.7Event B1 (Inter RAT neighbour becomes better than threshold) (139)5.5.4.8Event B2 (PCell becomes worse than threshold1 and inter RAT neighbour becomes better thanthreshold2) (140)5.5.4.9Event C1 (CSI-RS resource becomes better than threshold) (141)5.5.4.10Event C2 (CSI-RS resource becomes offset better than reference CSI-RS resource) (141)5.5.4.11Event W1 (WLAN becomes better than a threshold) (142)5.5.4.12Event W2 (All WLAN inside WLAN mobility set becomes worse than threshold1 and a WLANoutside WLAN mobility set becomes better than threshold2) (142)5.5.4.13Event W3 (All WLAN inside WLAN mobility set becomes worse than a threshold) (143)5.5.5Measurement reporting (144)5.5.6Measurement related actions (148)5.5.6.1Actions upon handover and re-establishment (148)5.5.6.2Speed dependant scaling of measurement related parameters (149)5.5.7Inter-frequency RSTD measurement indication (149)5.5.7.1General (149)5.5.7.2Initiation (150)5.5.7.3Actions related to transmission of InterFreqRSTDMeasurementIndication message (150)5.6Other (150)5.6.0General (150)5.6.1DL information transfer (151)5.6.1.1General (151)5.6.1.2Initiation (151)5.6.1.3Reception of the DLInformationTransfer by the UE (151)5.6.2UL information transfer (151)5.6.2.1General (151)5.6.2.2Initiation (151)5.6.2.3Actions related to transmission of ULInformationTransfer message (152)5.6.2.4Failure to deliver ULInformationTransfer message (152)5.6.3UE capability transfer (152)5.6.3.1General (152)5.6.3.2Initiation (153)5.6.3.3Reception of the UECapabilityEnquiry by the UE (153)5.6.4CSFB to 1x Parameter transfer (157)5.6.4.1General (157)5.6.4.2Initiation (157)5.6.4.3Actions related to transmission of CSFBParametersRequestCDMA2000 message (157)5.6.4.4Reception of the CSFBParametersResponseCDMA2000 message (157)5.6.5UE Information (158)5.6.5.1General (158)5.6.5.2Initiation (158)5.6.5.3Reception of the UEInformationRequest message (158)5.6.6 Logged Measurement Configuration (159)5.6.6.1General (159)5.6.6.2Initiation (160)5.6.6.3Reception of the LoggedMeasurementConfiguration by the UE (160)5.6.6.4T330 expiry (160)5.6.7 Release of Logged Measurement Configuration (160)5.6.7.1General (160)5.6.7.2Initiation (160)5.6.8 Measurements logging (161)5.6.8.1General (161)5.6.8.2Initiation (161)5.6.9In-device coexistence indication (163)5.6.9.1General (163)5.6.9.2Initiation (164)5.6.9.3Actions related to transmission of InDeviceCoexIndication message (164)5.6.10UE Assistance Information (165)5.6.10.1General (165)5.6.10.2Initiation (166)5.6.10.3Actions related to transmission of UEAssistanceInformation message (166)5.6.11 Mobility history information (166)5.6.11.1General (166)5.6.11.2Initiation (166)5.6.12RAN-assisted WLAN interworking (167)5.6.12.1General (167)5.6.12.2Dedicated WLAN offload configuration (167)5.6.12.3WLAN offload RAN evaluation (167)5.6.12.4T350 expiry or stop (167)5.6.12.5Cell selection/ re-selection while T350 is running (168)5.6.13SCG failure information (168)5.6.13.1General (168)5.6.13.2Initiation (168)5.6.13.3Actions related to transmission of SCGFailureInformation message (168)5.6.14LTE-WLAN Aggregation (169)5.6.14.1Introduction (169)5.6.14.2Reception of LWA configuration (169)5.6.14.3Release of LWA configuration (170)5.6.15WLAN connection management (170)5.6.15.1Introduction (170)5.6.15.2WLAN connection status reporting (170)5.6.15.2.1General (170)5.6.15.2.2Initiation (171)5.6.15.2.3Actions related to transmission of WLANConnectionStatusReport message (171)5.6.15.3T351 Expiry (WLAN connection attempt timeout) (171)5.6.15.4WLAN status monitoring (171)5.6.16RAN controlled LTE-WLAN interworking (172)5.6.16.1General (172)5.6.16.2WLAN traffic steering command (172)5.6.17LTE-WLAN aggregation with IPsec tunnel (173)5.6.17.1General (173)5.7Generic error handling (174)5.7.1General (174)5.7.2ASN.1 violation or encoding error (174)5.7.3Field set to a not comprehended value (174)5.7.4Mandatory field missing (174)5.7.5Not comprehended field (176)5.8MBMS (176)5.8.1Introduction (176)5.8.1.1General (176)5.8.1.2Scheduling (176)5.8.1.3MCCH information validity and notification of changes (176)5.8.2MCCH information acquisition (178)5.8.2.1General (178)5.8.2.2Initiation (178)5.8.2.3MCCH information acquisition by the UE (178)5.8.2.4Actions upon reception of the MBSFNAreaConfiguration message (178)5.8.2.5Actions upon reception of the MBMSCountingRequest message (179)5.8.3MBMS PTM radio bearer configuration (179)5.8.3.1General (179)5.8.3.2Initiation (179)5.8.3.3MRB establishment (179)5.8.3.4MRB release (179)5.8.4MBMS Counting Procedure (179)5.8.4.1General (179)5.8.4.2Initiation (180)5.8.4.3Reception of the MBMSCountingRequest message by the UE (180)5.8.5MBMS interest indication (181)5.8.5.1General (181)5.8.5.2Initiation (181)5.8.5.3Determine MBMS frequencies of interest (182)5.8.5.4Actions related to transmission of MBMSInterestIndication message (183)5.8a SC-PTM (183)5.8a.1Introduction (183)5.8a.1.1General (183)5.8a.1.2SC-MCCH scheduling (183)5.8a.1.3SC-MCCH information validity and notification of changes (183)5.8a.1.4Procedures (184)5.8a.2SC-MCCH information acquisition (184)5.8a.2.1General (184)5.8a.2.2Initiation (184)5.8a.2.3SC-MCCH information acquisition by the UE (184)5.8a.2.4Actions upon reception of the SCPTMConfiguration message (185)5.8a.3SC-PTM radio bearer configuration (185)5.8a.3.1General (185)5.8a.3.2Initiation (185)5.8a.3.3SC-MRB establishment (185)5.8a.3.4SC-MRB release (185)5.9RN procedures (186)5.9.1RN reconfiguration (186)5.9.1.1General (186)5.9.1.2Initiation (186)5.9.1.3Reception of the RNReconfiguration by the RN (186)5.10Sidelink (186)5.10.1Introduction (186)5.10.1a Conditions for sidelink communication operation (187)5.10.2Sidelink UE information (188)5.10.2.1General (188)5.10.2.2Initiation (189)5.10.2.3Actions related to transmission of SidelinkUEInformation message (193)5.10.3Sidelink communication monitoring (195)5.10.6Sidelink discovery announcement (198)5.10.6a Sidelink discovery announcement pool selection (201)5.10.6b Sidelink discovery announcement reference carrier selection (201)5.10.7Sidelink synchronisation information transmission (202)5.10.7.1General (202)5.10.7.2Initiation (203)5.10.7.3Transmission of SLSS (204)5.10.7.4Transmission of MasterInformationBlock-SL message (205)5.10.7.5Void (206)5.10.8Sidelink synchronisation reference (206)5.10.8.1General (206)5.10.8.2Selection and reselection of synchronisation reference UE (SyncRef UE) (206)5.10.9Sidelink common control information (207)5.10.9.1General (207)5.10.9.2Actions related to reception of MasterInformationBlock-SL message (207)5.10.10Sidelink relay UE operation (207)5.10.10.1General (207)5.10.10.2AS-conditions for relay related sidelink communication transmission by sidelink relay UE (207)5.10.10.3AS-conditions for relay PS related sidelink discovery transmission by sidelink relay UE (208)5.10.10.4Sidelink relay UE threshold conditions (208)5.10.11Sidelink remote UE operation (208)5.10.11.1General (208)5.10.11.2AS-conditions for relay related sidelink communication transmission by sidelink remote UE (208)5.10.11.3AS-conditions for relay PS related sidelink discovery transmission by sidelink remote UE (209)5.10.11.4Selection and reselection of sidelink relay UE (209)5.10.11.5Sidelink remote UE threshold conditions (210)6Protocol data units, formats and parameters (tabular & ASN.1) (210)6.1General (210)6.2RRC messages (212)6.2.1General message structure (212)–EUTRA-RRC-Definitions (212)–BCCH-BCH-Message (212)–BCCH-DL-SCH-Message (212)–BCCH-DL-SCH-Message-BR (213)–MCCH-Message (213)–PCCH-Message (213)–DL-CCCH-Message (214)–DL-DCCH-Message (214)–UL-CCCH-Message (214)–UL-DCCH-Message (215)–SC-MCCH-Message (215)6.2.2Message definitions (216)–CounterCheck (216)–CounterCheckResponse (217)–CSFBParametersRequestCDMA2000 (217)–CSFBParametersResponseCDMA2000 (218)–DLInformationTransfer (218)–HandoverFromEUTRAPreparationRequest (CDMA2000) (219)–InDeviceCoexIndication (220)–InterFreqRSTDMeasurementIndication (222)–LoggedMeasurementConfiguration (223)–MasterInformationBlock (225)–MBMSCountingRequest (226)–MBMSCountingResponse (226)–MBMSInterestIndication (227)–MBSFNAreaConfiguration (228)–MeasurementReport (228)–MobilityFromEUTRACommand (229)–Paging (232)–ProximityIndication (233)–RNReconfiguration (234)–RNReconfigurationComplete (234)–RRCConnectionReconfiguration (235)–RRCConnectionReconfigurationComplete (240)–RRCConnectionReestablishment (241)–RRCConnectionReestablishmentComplete (241)–RRCConnectionReestablishmentReject (242)–RRCConnectionReestablishmentRequest (243)–RRCConnectionReject (243)–RRCConnectionRelease (244)–RRCConnectionResume (248)–RRCConnectionResumeComplete (249)–RRCConnectionResumeRequest (250)–RRCConnectionRequest (250)–RRCConnectionSetup (251)–RRCConnectionSetupComplete (252)–SCGFailureInformation (253)–SCPTMConfiguration (254)–SecurityModeCommand (255)–SecurityModeComplete (255)–SecurityModeFailure (256)–SidelinkUEInformation (256)–SystemInformation (258)–SystemInformationBlockType1 (259)–UEAssistanceInformation (264)–UECapabilityEnquiry (265)–UECapabilityInformation (266)–UEInformationRequest (267)–UEInformationResponse (267)–ULHandoverPreparationTransfer (CDMA2000) (273)–ULInformationTransfer (274)–WLANConnectionStatusReport (274)6.3RRC information elements (275)6.3.1System information blocks (275)–SystemInformationBlockType2 (275)–SystemInformationBlockType3 (279)–SystemInformationBlockType4 (282)–SystemInformationBlockType5 (283)–SystemInformationBlockType6 (287)–SystemInformationBlockType7 (289)–SystemInformationBlockType8 (290)–SystemInformationBlockType9 (295)–SystemInformationBlockType10 (295)–SystemInformationBlockType11 (296)–SystemInformationBlockType12 (297)–SystemInformationBlockType13 (297)–SystemInformationBlockType14 (298)–SystemInformationBlockType15 (298)–SystemInformationBlockType16 (299)–SystemInformationBlockType17 (300)–SystemInformationBlockType18 (301)–SystemInformationBlockType19 (301)–SystemInformationBlockType20 (304)6.3.2Radio resource control information elements (304)–AntennaInfo (304)–AntennaInfoUL (306)–CQI-ReportConfig (307)–CQI-ReportPeriodicProcExtId (314)–CrossCarrierSchedulingConfig (314)–CSI-IM-Config (315)–CSI-IM-ConfigId (315)–CSI-RS-Config (317)–CSI-RS-ConfigEMIMO (318)–CSI-RS-ConfigNZP (319)–CSI-RS-ConfigNZPId (320)–CSI-RS-ConfigZP (321)–CSI-RS-ConfigZPId (321)–DMRS-Config (321)–DRB-Identity (322)–EPDCCH-Config (322)–EIMTA-MainConfig (324)–LogicalChannelConfig (325)–LWA-Configuration (326)–LWIP-Configuration (326)–RCLWI-Configuration (327)–MAC-MainConfig (327)–P-C-AndCBSR (332)–PDCCH-ConfigSCell (333)–PDCP-Config (334)–PDSCH-Config (337)–PDSCH-RE-MappingQCL-ConfigId (339)–PHICH-Config (339)–PhysicalConfigDedicated (339)–P-Max (344)–PRACH-Config (344)–PresenceAntennaPort1 (346)–PUCCH-Config (347)–PUSCH-Config (351)–RACH-ConfigCommon (355)–RACH-ConfigDedicated (357)–RadioResourceConfigCommon (358)–RadioResourceConfigDedicated (362)–RLC-Config (367)–RLF-TimersAndConstants (369)–RN-SubframeConfig (370)–SchedulingRequestConfig (371)–SoundingRS-UL-Config (372)–SPS-Config (375)–TDD-Config (376)–TimeAlignmentTimer (377)–TPC-PDCCH-Config (377)–TunnelConfigLWIP (378)–UplinkPowerControl (379)–WLAN-Id-List (382)–WLAN-MobilityConfig (382)6.3.3Security control information elements (382)–NextHopChainingCount (382)–SecurityAlgorithmConfig (383)–ShortMAC-I (383)6.3.4Mobility control information elements (383)–AdditionalSpectrumEmission (383)–ARFCN-ValueCDMA2000 (383)–ARFCN-ValueEUTRA (384)–ARFCN-ValueGERAN (384)–ARFCN-ValueUTRA (384)–BandclassCDMA2000 (384)–BandIndicatorGERAN (385)–CarrierFreqCDMA2000 (385)–CarrierFreqGERAN (385)–CellIndexList (387)–CellReselectionPriority (387)–CellSelectionInfoCE (387)–CellReselectionSubPriority (388)–CSFB-RegistrationParam1XRTT (388)–CellGlobalIdEUTRA (389)–CellGlobalIdUTRA (389)–CellGlobalIdGERAN (390)–CellGlobalIdCDMA2000 (390)–CellSelectionInfoNFreq (391)–CSG-Identity (391)–FreqBandIndicator (391)–MobilityControlInfo (391)–MobilityParametersCDMA2000 (1xRTT) (393)–MobilityStateParameters (394)–MultiBandInfoList (394)–NS-PmaxList (394)–PhysCellId (395)–PhysCellIdRange (395)–PhysCellIdRangeUTRA-FDDList (395)–PhysCellIdCDMA2000 (396)–PhysCellIdGERAN (396)–PhysCellIdUTRA-FDD (396)–PhysCellIdUTRA-TDD (396)–PLMN-Identity (397)–PLMN-IdentityList3 (397)–PreRegistrationInfoHRPD (397)–Q-QualMin (398)–Q-RxLevMin (398)–Q-OffsetRange (398)–Q-OffsetRangeInterRAT (399)–ReselectionThreshold (399)–ReselectionThresholdQ (399)–SCellIndex (399)–ServCellIndex (400)–SpeedStateScaleFactors (400)–SystemInfoListGERAN (400)–SystemTimeInfoCDMA2000 (401)–TrackingAreaCode (401)–T-Reselection (402)–T-ReselectionEUTRA-CE (402)6.3.5Measurement information elements (402)–AllowedMeasBandwidth (402)–CSI-RSRP-Range (402)–Hysteresis (402)–LocationInfo (403)–MBSFN-RSRQ-Range (403)–MeasConfig (404)–MeasDS-Config (405)–MeasGapConfig (406)–MeasId (407)–MeasIdToAddModList (407)–MeasObjectCDMA2000 (408)–MeasObjectEUTRA (408)–MeasObjectGERAN (412)–MeasObjectId (412)–MeasObjectToAddModList (412)–MeasObjectUTRA (413)–ReportConfigEUTRA (422)–ReportConfigId (425)–ReportConfigInterRAT (425)–ReportConfigToAddModList (428)–ReportInterval (429)–RSRP-Range (429)–RSRQ-Range (430)–RSRQ-Type (430)–RS-SINR-Range (430)–RSSI-Range-r13 (431)–TimeToTrigger (431)–UL-DelayConfig (431)–WLAN-CarrierInfo (431)–WLAN-RSSI-Range (432)–WLAN-Status (432)6.3.6Other information elements (433)–AbsoluteTimeInfo (433)–AreaConfiguration (433)–C-RNTI (433)–DedicatedInfoCDMA2000 (434)–DedicatedInfoNAS (434)–FilterCoefficient (434)–LoggingDuration (434)–LoggingInterval (435)–MeasSubframePattern (435)–MMEC (435)–NeighCellConfig (435)–OtherConfig (436)–RAND-CDMA2000 (1xRTT) (437)–RAT-Type (437)–ResumeIdentity (437)–RRC-TransactionIdentifier (438)–S-TMSI (438)–TraceReference (438)–UE-CapabilityRAT-ContainerList (438)–UE-EUTRA-Capability (439)–UE-RadioPagingInfo (469)–UE-TimersAndConstants (469)–VisitedCellInfoList (470)–WLAN-OffloadConfig (470)6.3.7MBMS information elements (472)–MBMS-NotificationConfig (472)–MBMS-ServiceList (473)–MBSFN-AreaId (473)–MBSFN-AreaInfoList (473)–MBSFN-SubframeConfig (474)–PMCH-InfoList (475)6.3.7a SC-PTM information elements (476)–SC-MTCH-InfoList (476)–SCPTM-NeighbourCellList (478)6.3.8Sidelink information elements (478)–SL-CommConfig (478)–SL-CommResourcePool (479)–SL-CP-Len (480)–SL-DiscConfig (481)–SL-DiscResourcePool (483)–SL-DiscTxPowerInfo (485)–SL-GapConfig (485)。
深度学习试题500问

深度学习试题500问1.1标量、向量、张量之间的联系 1 [填空题]_________________________________1.2张量与矩阵的区别? 1 [填空题]_________________________________1.3矩阵和向量相乘结果 1 [填空题]_________________________________1.4向量和矩阵的范数归纳 1 [填空题]_________________________________1.5如何判断一个矩阵为正定? 2 [填空题]_________________________________1.6导数偏导计算 3 [填空题]_________________________________1.7导数和偏导数有什么区别? 3 [填空题]_________________________________1.8特征值分解与特征向量 3 [填空题]_________________________________1.9奇异值与特征值有什么关系? 4 [填空题]_________________________________1.10机器学习为什么要使用概率? 4 [填空题]_________________________________1.11变量与随机变量有什么区别? 4 [填空题]_________________________________1.12常见概率分布? 5 [填空题]_________________________________1.13举例理解条件概率 9 [填空题]_________________________________1.14联合概率与边缘概率联系区别? 10 [填空题]_________________________________1.15条件概率的链式法则 10 [填空题]_________________________________1.16独立性和条件独立性 11 [填空题]_________________________________1.17期望、方差、协方差、相关系数总结 11 [填空题] *_________________________________2.1 各种常见算法图示 14 [填空题]_________________________________2.2监督学习、非监督学习、半监督学习、弱监督学习? 15 [填空题] _________________________________2.3 监督学习有哪些步骤 16 [填空题]_________________________________2.4 多实例学习? 17 [填空题]_________________________________2.5 分类网络和回归的区别? 17 [填空题]_________________________________2.6 什么是神经网络? 17 [填空题]_________________________________2.7 常用分类算法的优缺点? 18 [填空题]_________________________________2.8 正确率能很好的评估分类算法吗? 20 [填空题]_________________________________2.9 分类算法的评估方法? 20 [填空题]_________________________________2.10 什么样的分类器是最好的? 22 [填空题]_________________________________2.11大数据与深度学习的关系 22 [填空题]_________________________________2.12 理解局部最优与全局最优 23 [填空题]_________________________________2.13 理解逻辑回归 24 [填空题]_________________________________2.14 逻辑回归与朴素贝叶斯有什么区别? 24 [填空题] _________________________________2.15 为什么需要代价函数? 25 [填空题]_________________________________2.16 代价函数作用原理 25 [填空题]_________________________________2.17 为什么代价函数要非负? 26 [填空题]_________________________________2.18 常见代价函数? 26 [填空题]_________________________________2.19为什么用交叉熵代替二次代价函数 28 [填空题]_________________________________2.20 什么是损失函数? 28 [填空题]_________________________________2.21 常见的损失函数 28 [填空题]_________________________________2.22 逻辑回归为什么使用对数损失函数? 30 [填空题] _________________________________0.00 对数损失函数是如何度量损失的? 31 [填空题] _________________________________2.23 机器学习中为什么需要梯度下降? 32 [填空题] _________________________________2.24 梯度下降法缺点? 32 [填空题]_________________________________2.25 梯度下降法直观理解? 32 [填空题]_________________________________2.23 梯度下降法算法描述? 33 [填空题]_________________________________2.24 如何对梯度下降法进行调优? 35 [填空题]_________________________________2.25 随机梯度和批量梯度区别? 35 [填空题]_________________________________2.26 各种梯度下降法性能比较 37 [填空题]_________________________________2.27计算图的导数计算图解? 37 [填空题]_________________________________2.28 线性判别分析(LDA)思想总结 39 [填空题] _________________________________2.29 图解LDA核心思想 39 [填空题]_________________________________2.30 二类LDA算法原理? 40 [填空题]_________________________________2.30 LDA算法流程总结? 41 [填空题]_________________________________2.31 LDA和PCA区别? 41 [填空题]_________________________________2.32 LDA优缺点? 41 [填空题]_________________________________2.33 主成分分析(PCA)思想总结 42 [填空题] _________________________________2.34 图解PCA核心思想 42 [填空题]_________________________________2.35 PCA算法推理 43 [填空题]_________________________________2.36 PCA算法流程总结 44 [填空题]_________________________________2.37 PCA算法主要优缺点 45 [填空题]_________________________________2.38 降维的必要性及目的 45 [填空题]_________________________________2.39 KPCA与PCA的区别? 46 [填空题]_________________________________2.40模型评估 47 [填空题]_________________________________2.40.1模型评估常用方法? 47 [填空题]_________________________________2.40.2 经验误差与泛化误差 47 [填空题]_________________________________2.40.3 图解欠拟合、过拟合 48 [填空题]_________________________________2.40.4 如何解决过拟合与欠拟合? 49 [填空题] _________________________________2.40.5 交叉验证的主要作用? 50 [填空题]_________________________________2.40.6 k折交叉验证? 50 [填空题]_________________________________2.40.7 混淆矩阵 50 [填空题]_________________________________2.40.8 错误率及精度 51 [填空题]_________________________________2.40.9 查准率与查全率 51 [填空题]_________________________________2.40.10 ROC与AUC 52 [填空题]_________________________________2.40.11如何画ROC曲线? 53 [填空题]_________________________________2.40.12如何计算TPR,FPR? 54 [填空题]_________________________________2.40.13如何计算Auc? 56 [填空题]_________________________________2.40.14为什么使用Roc和Auc评价分类器? 56 [填空题]_________________________________2.40.15 直观理解AUC 56 [填空题]_________________________________2.40.16 代价敏感错误率与代价曲线 57 [填空题]_________________________________2.40.17 模型有哪些比较检验方法 59 [填空题]_________________________________2.40.18 偏差与方差 59 [填空题]_________________________________2.40.19为什么使用标准差? 60 [填空题]_________________________________2.40.20 点估计思想 61 [填空题]_________________________________2.40.21 点估计优良性原则? 61 [填空题]_________________________________2.40.22点估计、区间估计、中心极限定理之间的联系? 62 [填空题] _________________________________2.40.23 类别不平衡产生原因? 62 [填空题]_________________________________2.40.24 常见的类别不平衡问题解决方法 62 [填空题] _________________________________2.41 决策树 64 [填空题]_________________________________2.41.1 决策树的基本原理 64 [填空题]_________________________________2.41.2 决策树的三要素? 64 [填空题]_________________________________2.41.3 决策树学习基本算法 65 [填空题]_________________________________2.41.4 决策树算法优缺点 65 [填空题]_________________________________2.40.5熵的概念以及理解 66 [填空题]_________________________________2.40.6 信息增益的理解 66 [填空题]_________________________________2.40.7 剪枝处理的作用及策略? 67 [填空题]_________________________________2.41 支持向量机 67 [填空题]_________________________________2.41.1 什么是支持向量机 67 [填空题]_________________________________2.25.2 支持向量机解决的问题? 68 [填空题]_________________________________2.25.2 核函数作用? 69 [填空题]_________________________________2.25.3 对偶问题 69 [填空题]_________________________________2.25.4 理解支持向量回归 69 [填空题]_________________________________2.25.5 理解SVM(核函数) 69 [填空题]_________________________________2.25.6 常见的核函数有哪些? 69 [填空题]_________________________________2.25.6 软间隔与正则化 73 [填空题]_________________________________2.25.7 SVM主要特点及缺点? 73 [填空题]_________________________________2.26 贝叶斯 74 [填空题]_________________________________2.26.1 图解极大似然估计 74 [填空题]_________________________________2.26.2 朴素贝叶斯分类器和一般的贝叶斯分类器有什么区别? 76 [填空题] _________________________________2.26.4 朴素与半朴素贝叶斯分类器 76 [填空题]_________________________________2.26.5 贝叶斯网三种典型结构 76 [填空题]_________________________________2.26.6 什么是贝叶斯错误率 76 [填空题]_________________________________2.26.7 什么是贝叶斯最优错误率 76 [填空题]_________________________________2.27 EM算法解决问题及实现流程 76 [填空题] _________________________________2.28 为什么会产生维数灾难? 78 [填空题]_________________________________2.29怎样避免维数灾难 82 [填空题]_________________________________2.30聚类和降维有什么区别与联系? 82 [填空题] _________________________________2.31 GBDT和随机森林的区别 83 [填空题]_________________________________2.32 四种聚类方法之比较 84 [填空题] *_________________________________3.1基本概念 88 [填空题]_________________________________3.1.1神经网络组成? 88 [填空题]_________________________________3.1.2神经网络有哪些常用模型结构? 90 [填空题] _________________________________3.1.3如何选择深度学习开发平台? 92 [填空题] _________________________________3.1.4为什么使用深层表示 92 [填空题]_________________________________3.1.5为什么深层神经网络难以训练? 93 [填空题]_________________________________3.1.6深度学习和机器学习有什么不同 94 [填空题]_________________________________3.2 网络操作与计算 95 [填空题]_________________________________3.2.1前向传播与反向传播? 95 [填空题]_________________________________3.2.2如何计算神经网络的输出? 97 [填空题]_________________________________3.2.3如何计算卷积神经网络输出值? 98 [填空题]_________________________________3.2.4如何计算Pooling层输出值输出值? 101 [填空题] _________________________________3.2.5实例理解反向传播 102 [填空题]_________________________________3.3超参数 105 [填空题]_________________________________3.3.1什么是超参数? 105 [填空题]_________________________________3.3.2如何寻找超参数的最优值? 105 [填空题]_________________________________3.3.3超参数搜索一般过程? 106 [填空题]_________________________________3.4激活函数 106 [填空题]_________________________________3.4.1为什么需要非线性激活函数? 106 [填空题]_________________________________3.4.2常见的激活函数及图像 107 [填空题]_________________________________3.4.3 常见激活函数的导数计算? 109 [填空题]_________________________________3.4.4激活函数有哪些性质? 110 [填空题]_________________________________3.4.5 如何选择激活函数? 110 [填空题]_________________________________3.4.6使用ReLu激活函数的优点? 111 [填空题]_________________________________3.4.7什么时候可以用线性激活函数? 111 [填空题]_________________________________3.4.8怎样理解Relu(<0时)是非线性激活函数? 111 [填空题] _________________________________3.4.9 Softmax函数如何应用于多分类? 112 [填空题]_________________________________3.5 Batch_Size 113 [填空题]_________________________________3.5.1为什么需要Batch_Size? 113 [填空题]_________________________________3.5.2 Batch_Size值的选择 114 [填空题]_________________________________3.5.3在合理范围内,增大 Batch_Size 有何好处? 114 [填空题] _________________________________3.5.4盲目增大 Batch_Size 有何坏处? 114 [填空题]_________________________________3.5.5调节 Batch_Size 对训练效果影响到底如何? 114 [填空题] _________________________________3.6 归一化 115 [填空题]_________________________________3.6.1归一化含义? 115 [填空题]_________________________________3.6.2为什么要归一化 115 [填空题]_________________________________3.6.3为什么归一化能提高求解最优解速度? 115 [填空题]_________________________________3.6.4 3D图解未归一化 116 [填空题]_________________________________3.6.5归一化有哪些类型? 117 [填空题]_________________________________3.6.6局部响应归一化作用 117 [填空题]_________________________________3.6.7理解局部响应归一化公式 117 [填空题]_________________________________3.6.8什么是批归一化(Batch Normalization) 118 [填空题] _________________________________3.6.9批归一化(BN)算法的优点 119 [填空题]_________________________________3.6.10批归一化(BN)算法流程 119 [填空题]_________________________________3.6.11批归一化和群组归一化 120 [填空题]_________________________________3.6.12 Weight Normalization和Batch Normalization 120 [填空题] _________________________________3.7 预训练与微调(fine tuning) 121 [填空题]_________________________________3.7.1为什么无监督预训练可以帮助深度学习? 121 [填空题]_________________________________3.7.2什么是模型微调fine tuning 121 [填空题]_________________________________3.7.3微调时候网络参数是否更新? 122 [填空题]_________________________________3.7.4 fine-tuning模型的三种状态 122 [填空题]_________________________________3.8权重偏差初始化 122 [填空题]_________________________________3.8.1 全都初始化为0 122 [填空题]_________________________________3.8.2 全都初始化为同样的值 123 [填空题]_________________________________3.8.3 初始化为小的随机数 124 [填空题]_________________________________3.8.4用1/sqrt(n)校准方差 125 [填空题]_________________________________3.8.5稀疏初始化(Sparse Initialazation) 125 [填空题]_________________________________3.8.6初始化偏差 125 [填空题]_________________________________3.9 Softmax 126 [填空题]_________________________________3.9.1 Softmax定义及作用 126 [填空题]_________________________________3.9.2 Softmax推导 126 [填空题]_________________________________3.10 理解One Hot Encodeing原理及作用? 126 [填空题] _________________________________3.11 常用的优化器有哪些 127 [填空题]_________________________________3.12 Dropout 系列问题 128 [填空题]_________________________________3.12.1 dropout率的选择 128 [填空题]_________________________________3.27 Padding 系列问题 128 [填空题] *_________________________________4.1LetNet5 129 [填空题]_________________________________ 4.1.1模型结构 129 [填空题]_________________________________ 4.1.2模型结构 129 [填空题]_________________________________ 4.1.3 模型特性 131 [填空题]_________________________________ 4.2 AlexNet 131 [填空题]_________________________________ 4.2.1 模型结构 131 [填空题]_________________________________ 4.2.2模型解读 131 [填空题]_________________________________ 4.2.3模型特性 135 [填空题]_________________________________ 4.3 可视化ZFNet-解卷积 135 [填空题] _________________________________ 4.3.1 基本的思想及其过程 135 [填空题] _________________________________ 4.3.2 卷积与解卷积 136 [填空题]_________________________________ 4.3.3卷积可视化 137 [填空题]_________________________________ 4.3.4 ZFNe和AlexNet比较 139 [填空题] _________________________________4.4 VGG 140 [填空题]_________________________________ 4.1.1 模型结构 140 [填空题]_________________________________ 4.1.2 模型特点 140 [填空题]_________________________________ 4.5 Network in Network 141 [填空题] _________________________________ 4.5.1 模型结构 141 [填空题]_________________________________ 4.5.2 模型创新点 141 [填空题]_________________________________ 4.6 GoogleNet 143 [填空题]_________________________________ 4.6.1 模型结构 143 [填空题]_________________________________ 4.6.2 Inception 结构 145 [填空题]_________________________________ 4.6.3 模型层次关系 146 [填空题]_________________________________ 4.7 Inception 系列 148 [填空题]_________________________________ 4.7.1 Inception v1 148 [填空题]_________________________________4.7.2 Inception v2 150 [填空题]_________________________________4.7.3 Inception v3 153 [填空题]_________________________________4.7.4 Inception V4 155 [填空题]_________________________________4.7.5 Inception-ResNet-v2 157 [填空题]_________________________________4.8 ResNet及其变体 158 [填空题]_________________________________4.8.1重新审视ResNet 159 [填空题]_________________________________4.8.2残差块 160 [填空题]_________________________________4.8.3 ResNet架构 162 [填空题]_________________________________4.8.4残差块的变体 162 [填空题]_________________________________4.8.5 ResNeXt 162 [填空题]_________________________________4.8.6 Densely Connected CNN 164 [填空题]_________________________________4.8.7 ResNet作为小型网络的组合 165 [填空题] _________________________________4.8.8 ResNet中路径的特点 166 [填空题]4.9为什么现在的CNN模型都是在GoogleNet、VGGNet或者AlexNet上调整的? 167 [填空题] *_________________________________5.1 卷积神经网络的组成层 170 [填空题]_________________________________5.2 卷积如何检测边缘信息? 171 [填空题]_________________________________5.2 卷积的几个基本定义? 174 [填空题]_________________________________5.2.1卷积核大小 174 [填空题]_________________________________5.2.2卷积核的步长 174 [填空题]_________________________________5.2.3边缘填充 174 [填空题]_________________________________5.2.4输入和输出通道 174 [填空题]_________________________________5.3 卷积网络类型分类? 174 [填空题]_________________________________5.3.1普通卷积 174 [填空题]_________________________________5.3.2扩张卷积 175 [填空题]_________________________________5.3.3转置卷积 176 [填空题]5.3.4可分离卷积 177 [填空题]_________________________________5.3 图解12种不同类型的2D卷积? 178 [填空题]_________________________________5.4 2D卷积与3D卷积有什么区别? 181 [填空题]_________________________________5.4.1 2D 卷积 181 [填空题]_________________________________5.4.2 3D卷积 182 [填空题]_________________________________5.5 有哪些池化方法? 183 [填空题]_________________________________5.5.1一般池化(General Pooling) 183 [填空题]_________________________________5.5.2重叠池化(OverlappingPooling) 184 [填空题]_________________________________5.5.3空金字塔池化(Spatial Pyramid Pooling) 184 [填空题] _________________________________5.6 1x1卷积作用? 186 [填空题]_________________________________5.7卷积层和池化层有什么区别? 187 [填空题]_________________________________5.8卷积核一定越大越好? 189 [填空题]_________________________________5.9每层卷积只能用一种尺寸的卷积核? 189 [填空题]_________________________________5.10怎样才能减少卷积层参数量? 190 [填空题]_________________________________5.11卷积操作时必须同时考虑通道和区域吗? 191 [填空题]_________________________________5.12采用宽卷积的好处有什么? 192 [填空题]_________________________________5.12.1窄卷积和宽卷积 192 [填空题]_________________________________5.12.2 为什么采用宽卷积? 192 [填空题]_________________________________5.13卷积层输出的深度与哪个部件的个数相同? 192 [填空题]_________________________________5.14 如何得到卷积层输出的深度? 193 [填空题]_________________________________5.15激活函数通常放在卷积神经网络的那个操作之后? 194 [填空题] _________________________________5.16 如何理解最大池化层有几分缩小? 194 [填空题]_________________________________5.17理解图像卷积与反卷积 194 [填空题]_________________________________5.17.1图像卷积 194 [填空题]_________________________________5.17.2图像反卷积 196 [填空题]_________________________________5.18不同卷积后图像大小计算? 198 [填空题]_________________________________5.18.1 类型划分 198 [填空题]_________________________________5.18.2 计算公式 199 [填空题]_________________________________5.19 步长、填充大小与输入输出关系总结? 199 [填空题] _________________________________5.19.1没有0填充,单位步长 200 [填空题]_________________________________5.19.2零填充,单位步长 200 [填空题]_________________________________5.19.3不填充,非单位步长 202 [填空题]_________________________________5.19.4零填充,非单位步长 202 [填空题]_________________________________5.20 理解反卷积和棋盘效应 204 [填空题]_________________________________5.20.1为什么出现棋盘现象? 204 [填空题]_________________________________5.20.2 有哪些方法可以避免棋盘效应? 205 [填空题]_________________________________5.21 CNN主要的计算瓶颈? 207 [填空题]_________________________________5.22 CNN的参数经验设置 207 [填空题]_________________________________5.23 提高泛化能力的方法总结 208 [填空题]_________________________________5.23.1 主要方法 208 [填空题]_________________________________5.23.2 实验证明 208 [填空题]_________________________________5.24 CNN在CV与NLP领域运用的联系与区别? 213 [填空题] _________________________________5.24.1联系 213 [填空题]_________________________________5.24.2区别 213 [填空题]_________________________________5.25 CNN凸显共性的手段? 213 [填空题]_________________________________5.25.1 局部连接 213 [填空题]_________________________________5.25.2 权值共享 214 [填空题]_________________________________5.25.3 池化操作 215 [填空题]_________________________________5.26 全卷积与Local-Conv的异同点 215 [填空题]_________________________________5.27 举例理解Local-Conv的作用 215 [填空题]_________________________________5.28 简述卷积神经网络进化史 216 [填空题] *_________________________________6.1 RNNs和FNNs有什么区别? 218 [填空题]_________________________________6.2 RNNs典型特点? 218 [填空题]_________________________________6.3 RNNs能干什么? 219 [填空题]_________________________________6.4 RNNs在NLP中典型应用? 220 [填空题]_________________________________6.5 RNNs训练和传统ANN训练异同点? 220 [填空题] _________________________________6.6常见的RNNs扩展和改进模型 221 [填空题]_________________________________6.6.1 Simple RNNs(SRNs) 221 [填空题]_________________________________6.6.2 Bidirectional RNNs 221 [填空题]_________________________________6.6.3 Deep(Bidirectional) RNNs 222 [填空题]_________________________________6.6.4 Echo State Networks(ESNs) 222 [填空题]_________________________________6.6.5 Gated Recurrent Unit Recurrent Neural Networks 224 [填空题] _________________________________6.6.6 LSTM Netwoorks 224 [填空题]_________________________________6.6.7 Clockwork RNNs(CW-RNNs) 225 [填空题] *_________________________________7.1基于候选区域的目标检测器 228 [填空题]_________________________________7.1.1滑动窗口检测器 228 [填空题]_________________________________7.1.2选择性搜索 229 [填空题]_________________________________7.1.3 R-CNN 230 [填空题]_________________________________7.1.4边界框回归器 230 [填空题]_________________________________7.1.5 Fast R-CNN 231 [填空题]_________________________________7.1.6 ROI 池化 233 [填空题]_________________________________7.1.7 Faster R-CNN 233 [填空题]_________________________________7.1.8候选区域网络 234 [填空题]_________________________________7.1.9 R-CNN 方法的性能 236 [填空题]_________________________________7.2 基于区域的全卷积神经网络(R-FCN) 237 [填空题] _________________________________7.3 单次目标检测器 240 [填空题]_________________________________7.3.1单次检测器 241 [填空题]_________________________________7.3.2滑动窗口进行预测 241 [填空题]_________________________________7.3.3 SSD 243 [填空题]_________________________________7.4 YOLO系列 244 [填空题]_________________________________7.4.1 YOLOv1介绍 244 [填空题]_________________________________7.4.2 YOLOv1模型优缺点? 252 [填空题]_________________________________7.4.3 YOLOv2 253 [填空题]_________________________________7.4.4 YOLOv2改进策略 254 [填空题]_________________________________7.4.5 YOLOv2的训练 261 [填空题]_________________________________7.4.6 YOLO9000 261 [填空题]_________________________________7.4.7 YOLOv3 263 [填空题]_________________________________8.1 传统的基于CNN的分割方法缺点? 269 [填空题]_________________________________8.1 FCN 269 [填空题]_________________________________8.1.1 FCN改变了什么? 269 [填空题]_________________________________8.1.2 FCN网络结构? 270 [填空题]_________________________________8.1.3全卷积网络举例? 271 [填空题]_________________________________8.1.4为什么CNN对像素级别的分类很难? 271 [填空题]_________________________________8.1.5全连接层和卷积层如何相互转化? 272 [填空题]_________________________________8.1.6 FCN的输入图片为什么可以是任意大小? 272 [填空题]_________________________________8.1.7把全连接层的权重W重塑成卷积层的滤波器有什么好处? 273 [填空题] _________________________________8.1.8反卷积层理解 275 [填空题]_________________________________8.1.9跳级(skip)结构 276 [填空题]_________________________________8.1.10模型训练 277 [填空题]_________________________________8.1.11 FCN缺点 280 [填空题]_________________________________8.2 U-Net 280 [填空题]_________________________________8.3 SegNet 282 [填空题]_________________________________8.4空洞卷积(Dilated Convolutions) 283 [填空题] _________________________________8.4 RefineNet 285 [填空题]_________________________________8.5 PSPNet 286 [填空题]_________________________________8.6 DeepLab系列 288 [填空题]_________________________________8.6.1 DeepLabv1 288 [填空题]_________________________________8.6.2 DeepLabv2 289 [填空题]_________________________________8.6.3 DeepLabv3 289 [填空题]_________________________________8.6.4 DeepLabv3+ 290 [填空题]_________________________________8.7 Mask-R-CNN 293 [填空题]_________________________________8.7.1 Mask-RCNN 的网络结构示意图 293 [填空题]_________________________________8.7.2 RCNN行人检测框架 293 [填空题]_________________________________8.7.3 Mask-RCNN 技术要点 294 [填空题]_________________________________8.8 CNN在基于弱监督学习的图像分割中的应用 295 [填空题] _________________________________8.8.1 Scribble标记 295 [填空题]_________________________________8.8.2 图像级别标记 297 [填空题]_________________________________8.8.3 DeepLab+bounding box+image-level labels 298 [填空题]_________________________________8.8.4统一的框架 299 [填空题] *_________________________________9.1强化学习的主要特点? 301 [填空题]_________________________________9.2强化学习应用实例 302 [填空题]_________________________________9.3强化学习和监督式学习、非监督式学习的区别 303 [填空题] _________________________________9.4 强化学习主要有哪些算法? 305 [填空题]_________________________________9.5深度迁移强化学习算法 305 [填空题]_________________________________9.6分层深度强化学习算法 306 [填空题]_________________________________9.7深度记忆强化学习算法 306 [填空题]_________________________________9.8 多智能体深度强化学习算法 307 [填空题]_________________________________9.9深度强化学习算法小结 307 [填空题] *_________________________________10.1 什么是迁移学习? 309 [填空题]_________________________________10.2 什么是多任务学习? 309 [填空题]_________________________________10.3 多任务学习有什么意义? 309 [填空题]_________________________________10.4 什么是端到端的深度学习? 311 [填空题]_________________________________10.5 端到端的深度学习举例? 311 [填空题]_________________________________10.6 端到端的深度学习有什么挑战? 311 [填空题] _________________________________10.7 端到端的深度学习优缺点? 312 [填空题] *_________________________________13.1 CPU和GPU 的区别? 314 [填空题]_________________________________13.2如何解决训练样本少的问题 315 [填空题]_________________________________13.3 什么样的样本集不适合用深度学习? 315 [填空题]_________________________________13.4 有没有可能找到比已知算法更好的算法? 316 [填空题]_________________________________13.5 何为共线性, 跟过拟合有啥关联? 316 [填空题]_________________________________13.6 广义线性模型是怎被应用在深度学习中? 316 [填空题]_________________________________13.7 造成梯度消失的原因? 317 [填空题]_________________________________13.8 权值初始化方法有哪些 317 [填空题]_________________________________13.9 启发式优化算法中,如何避免陷入局部最优解? 318 [填空题]_________________________________13.10 凸优化中如何改进GD方法以防止陷入局部最优解 319 [填空题] _________________________________13.11 常见的损失函数? 319 [填空题]_________________________________13.14 如何进行特征选择(feature selection)? 321 [填空题]_________________________________13.14.1 如何考虑特征选择 321 [填空题]_________________________________13.14.2 特征选择方法分类 321 [填空题]_________________________________13.14.3 特征选择目的 322 [填空题]_________________________________13.15 梯度消失/梯度爆炸原因,以及解决方法 322 [填空题]_________________________________13.15.1 为什么要使用梯度更新规则? 322 [填空题]_________________________________13.15.2 梯度消失、爆炸原因? 323 [填空题]_________________________________13.15.3 梯度消失、爆炸的解决方案 324 [填空题]_________________________________13.16 深度学习为什么不用二阶优化 325 [填空题]_________________________________13.17 怎样优化你的深度学习系统? 326 [填空题]_________________________________13.18为什么要设置单一数字评估指标? 326 [填空题]_________________________________13.19满足和优化指标(Satisficing and optimizing metrics) 327 [填空题] _________________________________13.20 怎样划分训练/开发/测试集 328 [填空题]_________________________________13.21如何划分开发/测试集大小 329 [填空题]_________________________________13.22什么时候该改变开发/测试集和指标? 329 [填空题]_________________________________13.23 设置评估指标的意义? 330 [填空题]_________________________________13.24 什么是可避免偏差? 331 [填空题]_________________________________13.25 什么是TOP5错误率? 331 [填空题]_________________________________13.26 什么是人类水平错误率? 332 [填空题]_________________________________13.27 可避免偏差、几大错误率之间的关系? 332 [填空题] _________________________________13.28 怎样选取可避免偏差及贝叶斯错误率? 332 [填空题] _________________________________13.29 怎样减少方差? 333 [填空题]_________________________________13.30贝叶斯错误率的最佳估计 333 [填空题]_________________________________13.31举机器学习超过单个人类表现几个例子? 334 [填空题] _________________________________13.32如何改善你的模型? 334 [填空题]_________________________________13.33 理解误差分析 335 [填空题]_________________________________13.34 为什么值得花时间查看错误标记数据? 336 [填空题] _________________________________13.35 快速搭建初始系统的意义? 336 [填空题]_________________________________13.36 为什么要在不同的划分上训练及测试? 337 [填空题] _________________________________13.37 如何解决数据不匹配问题? 338 [填空题]_________________________________13.38 梯度检验注意事项? 340 [填空题]_________________________________13.39什么是随机梯度下降? 341 [填空题]_________________________________13.40什么是批量梯度下降? 341 [填空题]_________________________________13.41什么是小批量梯度下降? 341 [填空题]_________________________________13.42怎么配置mini-batch梯度下降 342 [填空题]_________________________________13.43 局部最优的问题 343 [填空题]_________________________________13.44提升算法性能思路 346 [填空题] *_________________________________14.1 调试处理 358 [填空题]_________________________________14.2 有哪些超参数 359 [填空题]_________________________________14.3 如何选择调试值? 359 [填空题]_________________________________14.4 为超参数选择合适的范围 359 [填空题]_________________________________14.5 如何搜索超参数? 359 [填空题] *_________________________________15.1 什么是正则化? 361 [填空题]_________________________________15.2 正则化原理? 361 [填空题]_________________________________15.3 为什么要正则化? 361 [填空题]_________________________________15.4 为什么正则化有利于预防过拟合? 361 [填空题] _________________________________15.5 为什么正则化可以减少方差? 362 [填空题]_________________________________15.6 L2正则化的理解? 362 [填空题]_________________________________15.7 理解dropout 正则化 362 [填空题]_________________________________15.8 有哪些dropout 正则化方法? 362 [填空题]_________________________________15.8 如何实施dropout 正则化 363 [填空题]_________________________________。
SignalWhiteningPreprocessingfor:信号白化预处理

Signal Whitening Preprocessing for Improved Classification Accuracies in Myoelectric Control Lukai Liu1, Pu Liu1, Edward A. Clancy1, Erik Scheme2 and Kevin B. Englehart21Worcester Polytechnic Institute, 100 Institute Road, Worcester, MA 01609 U.S.A.2Institute of Biomedical Engineering, University of New Brunswick, Fredericton, NB E3B 5A3, Canada.Abstract— The surface electromyogram (EMG) signal collected from multiple channels has frequently been investigated for use in controlling upper-limb prostheses. One common control method is EMG-based motion classification. Time and frequency features derived from the EMG have been investigated. We propose the use of EMG signal whitening as a preprocessing step in EMG-based motion classification. Whitening decorrelates the EMG signal, and has been shown to be advantageous in other EMG applications. In a ten-subject study of up to 11 motion classes and ten electrode channels, we found that whitening improved classification accuracy by approximately 5% when small window length durations (<100ms) were considered.I.I NTRODUCTIONThe surface EMG has often been used in prosthesis control, ergonomics analysis and clinical biomechanics. Whitening has been used as a preprocessor to decorrelate the EMG signal. In the context of EMG-based motion selection for prosthetic control, we hypothesized that whitening would provide a decrease in the in-class variation of features leading to improved classification accuracy. The present study examined the influence of whitening on classification using time and frequency features of the EMG, in particular at shorter time durations. Three time domain features: mean absolute value (MAV), signal waveform length and zero-crossing rate; and 7th order autoregressive (AR) coefficients as frequency features, were used in our study. We observed an accuracy improvement of about 5% at smaller window lengths (less than 100 ms) with diminishing returns at longer window durations.II.M ETHODSA.Experimental Data and MethodsData from a prior study [1] were reanalyzed. The WPI IRB approved and supervised this reanalysis. Briefly, ten electrodes were applied transversely about the entire circumference of the proximal forearm. A custom electrode amplifier system provided a frequency response spanning approximately 30–450 Hz. Ten subjects with intact upper limbs began and ended each trial at "rest" with their elbow supported on an armrest. Each trial consisted of two repetitions of 11 sequential motion classes: 1, 2) wrist pronation/supination; 3, 4) wrist flexion/extension; 5) hand open; 6) key grip; 7) chuck grip; 8) power grip; 9) fine pinch grip; 10) tool grip; and 11) no motion. Each motion within a trial was maintained for 4 s, after which the subject returned to no motion for a specified inter-motion delay period. Trials 1–4 used an inter-motion delay of 3, 2, 1 and 0 s, respectively, and trials 5–8 used an inter-motion delay of 2 s. A minimum 2-min rest was given between trials. EMG data were sampled at 1000 Hz with a 16-bit ADC. Notch filters were used to attenuate power-line interference at the fundamental frequency and its harmonics.B.Methods of AnalysisThe inter-trial delay segments were removed from the data recordings, resulting in 22, four-second epochs per electrode, per trial (two repetitions of 11 motion classes). For all features, 0.5 seconds of data were truncated from the beginning and end of each epoch. Contiguous, non-overlapping windows were formed from the remaining 3-second epoch segments.Feature sets were computed for each window within an epoch. A time-domain feature set consisting of three features per window—MAV, signal length and zero-crossing [2] rate—was evaluated. A frequency domain feature set consisted of seven features per window, comprised of the coefficients of a seventh order autoregressive (AR) power spectral density estimate [3]. A third feature set concatenating the seven frequency domain features and the MAV was also evaluated.Trials 1–4 were used to train the coefficients of the classifier, and trials 5–8 were used to test classifier performance. Initially, all channels and all motions were included in the classifier. The models were trained and tested for each individual subject. Only the test results are reported. Ten window durations were used: 25, 50, 75, 100, 150, 200, 250, 300, 400 and 500 ms. The analysis was then repeated after the data had been whitened. When doing so, each epoch was high-pass filtered at 15Hz, then adaptively whitened using an algorithm that is tuned to the power spectrum of each EMG channel [4]. Two global variants were also considered. First, the entire analysis was repeated using only nine pre-selected motion classes (the classes denoted above as numbers 1–8 and 11), and again using only seven pre-selected motion classes (1–5, 8 and 11). Second, the entire analysis was repeated using a preselected set of six of the electrode channels. A linear discriminant classifier was used for the recognition task.Window length/ms Window length/ms A c c u r a c y (%)Fig. 1. Classification accuracies for intact subjects with (triangle)/without (circle) whitening used for pre-processing. The frequency feature set (Freq) iscomprised of the seven AR coefficients. The time domain feature set (TD) is comprised of three features, and the concatenated feature set (MAR) uses the AR coefficients and MAV. Window durations up to 300 ms are shown. Note the different y-axis scale for each plot.III. R ESULTS Fig. 1 shows the averaged test accuracies for the motion–channel combinations with lowest (left) and highest (right) overall performance. Classifying with more channels andfewer motion types (right) produced better overall performance. The concatenated (AR-MAV) feature set gave the highest overall classification accuracy, and the frequency domain feature set the lowest. A consistent 4–5% classification performance increase can be seen at shorterwindow durations for all three feature sets due to whitening, although the improvement decreases with longer windowduration. Paired t-tests (p <0.05) at all window lengths suggestthat use of whitening as a preprocessing stage provides a statistically significant performance improvement.IV. D ISCUSSIONWe have shown that the use of signal whitening prior toclassification analysis of the EMG system consistently improves the recognition accuracy, especially at shorter time durations. This improvement is modest (~5% for windowdurations less than 100 ms), but may help improve the accuracy of EMG-based artificial limb controllers. The factthat the most substantial improvement is seen with smallwindow lengths is important, as it may allow a control system to use less data, and therefore improve response time.Further work may apply to other EMG processing techniques, such as universal principal components analysis [1] and more sophisticated classifiers to further improve classification performance. R EFERENCES [1] L. J. Hargrove, G. Li, K. B. Englehart, B. S. Hudgins, “PrincipalComponents Analysis for Improved Classification Accuracies inPattern-Recognition-Based Myoelectric Control,” IEEE Trans. Biomed. Eng., Vol 56, pp. 1407–1414, 2009. [2] B. Hudgins, P. Parker, R. N. Scott, “A New Strategy for MultifunctionMyoelectric Control,” IEEE Trans. Biomed. Eng., Vol 40, pp 82–94,1993. [3] A. Neumaier, T. Schneider, “Estimation of Parameters and Eigenmodes of Multivariate Autoregressive Models,” ACM Trans. Math. Software , vol. 27, pp. 27–57, 2001.[4] E. A. Clancy, K. A. Farry, “Adaptive whitening of the electromyogramto improve amplitude estimation,” IEEE Trans. Biomed. Eng., vol. 47, pp. 709–719, 2000.。
mlpclassifier默认参数

MLPClassifier默认参数简介在机器学习中,M LPC l as si fi er是一种常用的多层感知器(M ul ti la ye rP er ce p tr on)分类器模型。
多层感知器是一种前馈神经网络,通过学习输入特征来预测输出类别。
本文将介绍ML PC la s si fi er 模型的默认参数及其含义,并探讨如何根据实际问题进行参数调整。
默认参数概述M L PC la ss if ie r模型具有多个参数,其中一些参数在实际使用中可能需要进行调整,以获得更好的性能。
以下是M LP Cl as si fi er的默认参数及其含义:-`hi dd en_l ay er_si z es`:默认为(100,),表示隐藏层的数量和每个隐藏层的神经元数量。
例如,(100,)表示一个具有100个神经元的单隐藏层。
-`ac ti va ti on`:默认为're lu',表示激活函数的类型。
常见的激活函数包括'r el u'、'l o gi st ic'和't an h'。
-`so lv er`:默认为'a da m',表示优化器的类型。
可选的优化器有'l bf gs'、's gd'和'a da m'。
-`al ph a`:默认为0.0001,表示L2正则化项的参数。
较大的a lp ha 值可以减小过拟合风险。
-`ba tc h_si ze`:默认为'au to',表示优化算法的小批量样本大小。
'a ut o'根据输入数据的大小自动设置。
-`le ar ni ng_r at e`:默认为'c on st an t',表示学习率的调整策略。
可选的策略有'c on st a nt'、'i nv sc al in g'和'a da pt iv e'。
DS2208数字扫描器产品参考指南说明书

-05 Rev. A
6/2018
Rev. B Software Updates Added: - New Feedback email address. - Grid Matrix parameters - Febraban parameter - USB HID POS (formerly known as Microsoft UWP USB) - Product ID (PID) Type - Product ID (PID) Value - ECLevel
-06 Rev. A
10/2018 - Added Grid Matrix sample bar code. - Moved 123Scan chapter.
-07 Rev. A
11/2019
Added: - SITA and ARINC parameters. - IBM-485 Specification Version.
No part of this publication may be reproduced or used in any form, or by any electrical or mechanical means, without permission in writing from Zebra. This includes electronic or mechanical means, such as photocopying, recording, or information storage and retrieval systems. The material in this manual is subject to change without notice.
人工智能训练师(3级)理论知识复习题
输入层
输出层
激活函数
22
在知识图谱中,用于表示实体间关系的边通常具有什么类型?
有向边
无向边
加权边
线性边
23
类脑计算的主要目标是:
模拟人类的大脑功能 b) 创建一个全新的智能
创建一个全新的智能生物
提高计算机的运算速度
优化网络安全性
24
在模式识别中,特征选择的目标是:
降低维度
增加噪声
增强数据
数据预处理
任务目标
项目预算
数据来源
项目截止时间
11
在评估人工智能系统时,下列哪个因素是最重要的评估指标?
a) 系统的准确性
系统的准确性
系统的响应速度
系统的外观设计
系统的品牌知名度
12
评估人工智能系统时,下列哪个因素可以衡量系统的可靠性和鲁棒性?
系统的安全性
系统的用户友好性
系统的社会影响
系统的数据处理能力
13
当模型在验证集上不能达到理想的评估指标时,( )。
加强与行业人员的联系
提高技术实施效率
提升数据分析准确性
减少团队协作难度
4
人工智能是通过什么来呈现人类智能的技术?
计算机程序
机械装置
化学合成物
电子设备
5
人工智能的研究内容主要包括什么?
计算机实现智能的原理
网络安全技术
建筑设计原理
动物行为研究方法
6
人工智能科学是一门研究、开发和应用智能体的( )。
跨学科领域
57
VMAF是用于评估视频质量的指标,它基于以下哪个原理进行评估?
人眼感知模型
编码效率
数据压缩算法
kernel_initializer方法

kernel_initializer方法kernel_initializer是神经网络中的初始化方法,用于初始化神经网络的权重和偏置项。
在神经网络中,权重和偏置项的初始化是非常重要的,良好的初始化方法可以帮助神经网络更好地学习和适应输入数据。
kernel_initializer就是一种用于初始化权重的方法。
在深度学习中,通常使用的初始化方法有随机初始化、零初始化、Xavier初始化和He初始化等。
而kernel_initializer就是其中的一种。
在深度学习中,权值初始化是非常重要的一步,合适的初始化可以避免神经网络中的梯度消失或梯度爆炸问题,有助于神经网络更好地收敛和学习。
kernel_initializer方法的作用是初始化神经网络中的权重矩阵,也就是卷积核。
它是在卷积神经网络(Convolutional Neural Network)中使用的。
初始化卷积核的方式是随机初始化,即在训练开始时,将权重矩阵的值设定为一个接近于零的随机值。
这样做的目的是为了打破对称性,使得每个卷积核可以学习到不同的特征,提高网络的表达能力。
常用的随机初始化方法有截断正态分布初始化和均匀分布初始化。
截断正态分布初始化是指通过使用正态分布来初始化权重,但是对超过两个标准差的随机值进行截断。
这样可以保证随机初始化的权重值不会过大或过小,防止网络中的梯度爆炸或梯度消失问题。
常见的截断正态分布初始化方法是使用均值为0,标准差为0.1或0.01的正态分布来初始化卷积核。
另一种常用的初始化方法是均匀分布初始化,它将权重均匀分布在一个特定的区间内。
这种初始化方法可以通过设置均匀分布的上下界来控制初始化的范围。
一般来说,权重的范围可以在训练开始时设定为一个较小的值,以保持随机初始化的权重接近于零。
常用的均匀分布初始化方法是将权重初始化在[-0.05, 0.05]范围内。
除了随机初始化的方法外,还有一些其他的初始化方法可以用来初始化卷积神经网络中的卷积核权重。
linux 内核编译各个选项的含义

Code maturity level options代码成熟度选项Prompt for development and/or incomplete code/drivers显示尚在开发中或尚未完成的代码与驱动.除非你是测试人员或者开发者,否则请勿选择General setup常规设置Local version - append to kernel release在内核版本后面加上自定义的版本字符串(小于64字符),可以用"uname -a"命令看到Automatically append version information to the version string 自动在版本字符串后面添加版本信息,编译时需要有perl以及git仓库支持Support for paging of anonymous memory (swap)使用交换分区或者交换文件来做为虚拟内存System V IPCSystem V进程间通信(IPC)支持,许多程序需要这个功能.必选,除非你知道自己在做什么IPC NamespacesIPC命名空间支持,不确定可以不选POSIX Message QueuesPOSIX消息队列,这是POSIX IPC中的一部分BSD Process Accounting将进程的统计信息写入文件的用户级系统调用,主要包括进程的创建时间/创建者/内存占用等信息BSD Process Accounting version 3 file format使用新的第三版文件格式,可以包含每个进程的PID和其父进程的PID,但是不兼容老版本的文件格式Export task/process statistics through netlink通过netlink接口向用户空间导出任务/进程的统计信息,与BSD Process Accounting的不同之处在于这些统计信息在整个任务/进程生存期都是可用的Enable per-task delay accounting在统计信息中包含进程等候系统资源(cpu,IO同步,内存交换等)所花费的时间UTS NamespacesUTS名字空间支持,不确定可以不选Auditing support审计支持,某些内核模块(例如SELinux)需要它,只有同时选择其子项才能对系统调用进行审计Enable system-call auditing support支持对系统调用的审计Kernel .config support把内核的配置信息编译进内核中,以后可以通过scripts/extract-ikconfig脚本来提取这些信息Enable access to .config through /proc/config.gz允许通过/proc/config.gz访问内核的配置信息Cpuset support只有含有大量CPU(大于16个)的SMP系统或NUMA(非一致内存访问)系统才需要它Kernel->user space relay support (formerly relayfs)在某些文件系统上(比如debugfs)提供从内核空间向用户空间传递大量数据的接口Initramfs source file(s)initrd已经被initramfs取代,如果你不明白这是什么意思,请保持空白Optimize for size (Look out for broken compilers!)编译时优化内核尺寸(使用"-Os"而不是"-O2"参数编译),有时会产生错误的二进制代码Enable extended accounting over taskstats收集额外的进程统计信息并通过taskstats接口发送到用户空间Configure standard kernel features (for small systems)配置标准的内核特性(为小型系统)Enable 16-bit UID system calls允许对UID系统调用进行过时的16-bit包装Sysctl syscall support不需要重启就能修改内核的某些参数和变量,如果你也选择了支持/proc,将能从/proc/sys存取可以影响内核行为的参数或变量Load all symbols for debugging/kksymoops装载所有的调试符号表信息,仅供调试时选择Include all symbols in kallsyms在kallsyms中包含内核知道的所有符号,内核将会增大300KDo an extra kallsyms pass除非你在kallsyms中发现了bug并需要报告这个bug才打开该选项Support for hot-pluggable devices支持热插拔设备,如usb与pc卡等,Udev也需要它Enable support for printk允许内核向终端打印字符信息,在需要诊断内核为什么不能运行时选择BUG() support显示故障和失败条件(BUG和WARN),禁用它将可能导致隐含的错误被忽略Enable ELF core dumps内存转储支持,可以帮助调试ELF格式的程序Enable full-sized data structures for core在内核中使用全尺寸的数据结构.禁用它将使得某些内核的数据结构减小以节约内存,但是将会降低性能Enable futex support快速用户空间互斥体可以使线程串行化以避免竞态条件,也提高了响应速度.禁用它将导致内核不能正确的运行基于glibc的程序Enable eventpoll support支持事件轮循的系统调用Use full shmem filesystem完全使用shmem来代替ramfs.shmem是基于共享内存的文件系统(可能用到swap),在启用TMPFS后可以挂载为tmpfs供用户空间使用,它比简单的ramfs先进许多Use full SLAB allocator使用SLAB完全取代SLOB进行内存分配,SLAB是一种优秀的内存分配管理器,推荐使用Enable VM event counters for /proc/vmstat允许在/proc/vmstat中包含虚拟内存事件记数器Loadable module support可加载模块支持Enable loadable module support打开可加载模块支持,如果打开它则必须通过"make modules_install"把内核模块安装在/lib/modules/中Module unloading允许卸载已经加载的模块Forced module unloading允许强制卸载正在使用中的模块(比较危险)Module versioning support允许使用其他内核版本的模块(可能会出问题)Source checksum for all modules为所有的模块校验源码,如果你不是自己编写内核模块就不需要它Automatic kernel module loading让内核通过运行modprobe来自动加载所需要的模块,比如可以自动解决模块的依赖关系Block layer块设备层Enable the block layer块设备支持,使用硬盘/USB/SCSI设备者必选Support for Large Block Devices仅在使用大于2TB的块设备时需要Support for tracing block io actions块队列IO跟踪支持,它允许用户查看在一个块设备队列上发生的所有事件,可以通过blktrace程序获得磁盘当前的详细统计数据Support for Large Single Files仅在可能使用大于2TB的文件时需要IO SchedulersIO调度器Anticipatory I/O scheduler假设一个块设备只有一个物理查找磁头(例如一个单独的SATA硬盘),将多个随机的小写入流合并成一个大写入流,用写入延时换取最大的写入吞吐量.适用于大多数环境,特别是写入较多的环境(比如文件服务器) Deadline I/O scheduler使用轮询的调度器,简洁小巧,提供了最小的读取延迟和尚佳的吞吐量,特别适合于读取较多的环境(比如数据库)CFQ I/O scheduler使用QoS策略为所有任务分配等量的带宽,避免进程被饿死并实现了较低的延迟,可以认为是上述两种调度器的折中.适用于有大量进程的多用户系统Default I/O scheduler默认IO调度器Processor type and features中央处理器(CPU)类型及特性Symmetric multi-processing support对称多处理器支持,如果你有多个CPU或者使用的是多核CPU就选上.此时"Enhanced Real Time Clock Support"选项必须开启,"Advanced Power Management"选项必须关闭Subarchitecture Type处理器的子架构,大多数人都应当选择"PC-compatible"Processor family处理器系列,请按照你实际使用的CPU选择Generic x86 support通用x86支持,如果你的CPU能够在上述"Processor family"中找到就别选HPET Timer SupportHPET是替代8254芯片的新一代定时器,i686及以上级别的主板都支持,可以安全的选上Maximum number of CPUs支持的最大CPU数,每增加一个内核将增加8K体积SMT (Hyperthreading) scheduler support支持Intel的超线程(HT)技术Multi-core scheduler support针对多核CPU进行调度策略优化Preemption Model内核抢占模式No Forced Preemption (Server)适合服务器环境的禁止内核抢占Voluntary Kernel Preemption (Desktop)适合普通桌面环境的自愿内核抢占Preemptible Kernel (Low-Latency Desktop)适合运行实时程序的主动内核抢占Preempt The Big Kernel Lock可以抢占大内核锁,应用于实时要求高的场合,不适合服务器环境Machine Check Exception让CPU检测到系统故障时通知内核,以便内核采取相应的措施(如过热关机等)Check for non-fatal errors on AMD Athlon/Duron / Intel Pentium 4 每5秒检测一次这些cpu的非致命错误并纠正它们,同时记入日志check for P4 thermal throttling interrupt当P4的cpu过热时显示一条警告消息Enable VM86 support虚拟X86支持,在DOSEMU下运行16-bit程序或XFree86通过BIOS初始化某些显卡的时候才需要Toshiba Laptop supportToshiba笔记本模块支持Dell laptop supportDell笔记本模块支持Enable X86 board specific fixups for reboot修正某些旧x86主板的重起bug,这种主板基本绝种了/dev/cpu/microcode - Intel IA32 CPU microcode support使用不随Linux内核发行的IA32微代码,你必需有IA32微代码二进制文件,仅对Intel的CPU有效/dev/cpu/*/msr - Model-specific register support在多cpu系统中让特权CPU访问x86的MSR寄存器/dev/cpu/*/cpuid - CPU information support能从/dev/cpu/x/cpuid获得CPU的唯一标识符(CPUID)Firmware Drivers固件驱动程序BIOS Enhanced Disk Drive calls determine boot disk有些BIOS支持从某块特定的硬盘启动(如果BIOS不支持则可能无法启动),目前大多数BIOS还不支持BIOS update support for DELL systems via sysfs仅适用于DELL机器Dell Systems Management Base Driver仅适用于DELL机器High Memory Support最高内存支持,总内存小于等于1G的选"off",大于4G的选"64G" Memory split如果你不是绝对清楚自己在做什么,不要改动这个选项Memory model一般选"Flat Memory",其他选项涉及内存热插拔64 bit Memory and IO resources使用64位的内存和IO资源Allocate 3rd-level pagetables from highmem在内存很多(大于4G)的机器上将用户空间的页表放到高位内存区,以节约宝贵的低端内存Math emulation数学协处理器仿真,486DX以上的cpu就不要选它了MTRR (Memory Type Range Register) support打开它可以提升PCI/AGP总线上的显卡2倍以上的速度,并且可以修正某些BIOS错误Boot from EFI supportEFI是一种可代替传统BIOS的技术(目前的Grub/LILO尚不能识别它),但是现在远未普及Enable kernel irq balancing让内核将irq中断平均分配给多个CPU以进行负载均衡,但是要配合irqbanlance守护进程才行Use register arguments使用"-mregparm=3"参数编译内核,将前3个参数以寄存器方式进行参数调用,可以生成更紧凑和高效的代码Enable seccomp to safely compute untrusted bytecode只有嵌入式系统可以不选Timer frequency内核时钟频率,桌面推荐"1000 HZ",服务器推荐"100 HZ"或"250 HZ" kexec system call提供kexec系统调用,可以不必重启而切换到另一个内核kernel crash dumps被kexec启动后产生内核崩溃转储Physical address where the kernel is loaded内核加载的物理地址,除非你知道自己在做什么,否则不要修改.在提供kexec系统调用的情况下可能要修改它Support for hot-pluggable CPUs对热插拔CPU提供支持Compat VDSO support如果Glibc版本大于等于2.3.3就不选,否则就选上Power management options电源管理选项Power Management support电源管理有APM和ACPI两种标准且不能同时使用.即使关闭该选项,X86上运行的Linux也会在空闲时发出HLT指令将CPU进入睡眠状态Legacy Power Management API传统的电源管理API,比如软关机和系统休眠等接口Power Management Debug Support仅供调试使用Driver model /sys/devices/.../power/state files内核帮助文档反对使用该选项,即将被废除ACPI (Advanced Configuration and Power Interface) Support 必须运行acpid守护程序ACPI才能起作用.ACPI是为了取代APM而设计的,因此应该尽量使用ACPI而不是APMAC Adapter如果你的系统可以在AC和电池之间转换就可以选Battery通过/proc/acpi/battery向用户提供电池状态信息,用电池的笔记本可以选Button守护程序捕获Power,Sleep,Lid按钮事件,并根据/proc/acpi/event做相应的动作,软件控制的poweroff需要它Video仅对集成在主板上的显卡提供ACPI2.0支持,且不是所有集成显卡都支持Generic Hotkey统一的热键驱动,建议不选Fan允许通过用户层的程序来对系统风扇进行控制(开,关,查询状态),支持它的硬件并不多Dock支持由ACPI控制的集线器(docking stations)Processor让ACPI处理空闲状态,并使用ACPI C2和C3处理器状态在空闲时节省电能,同时它还被cpufreq的"Performance-state drivers"选项所依赖Thermal Zone系统温度过高时可以利用ACPI thermal zone及时调整工作状态以避免你的CPU被烧毁ASUS/Medion Laptop ExtrasASUS笔记本专用,以提供额外按钮的支持,用户可以通过/proc/acpi/asus来打开或者关闭LCD的背光/调整亮度/定制LED的闪烁指示等功能IBM ThinkPad Laptop ExtrasIBM ThinkPad专用Toshiba Laptop ExtrasToshiba笔记本专用Disable ACPI for systems before Jan 1st this year输入四位数的年份,在该年的1月1日前不使用ACPI的功能("0"表示一直使用)Debug Statements详细的ACPI调试信息,不搞开发就别选Power Management Timer Support这个Timer在所有ACPI兼容的平台上都可用,且不会受PM功能的影响,建议总是启用它.如果你在kernel log中看到了'many lost ticks'那就必须启用它ACPI0004,PNP0A05 and PNP0A06 Container Driver支持内存和CPU的热插拔Smart Battery System支持依赖于I2C的"智能电池".这种电池非常老旧且罕见,还与当前的ACPI标准兼容性差APM (Advanced Power Management) BIOS SupportAPM在SMP机器上必须关闭,一般来说当前的笔记本都支持ACPI,所以应尽量关闭该该选项Ignore USER SUSPEND只有NEC Versa M系列的笔记本才需要选择这一项Enable PM at boot time系统启动时即启用APM,选上这个选项能让系统自动的进行电源管理,但常常导致启动时死机Make CPU Idle calls when idle系统空闲时调用空闲指令(halt),只有老式的CPU才需要选它,且对于SMP 系统必须关闭Enable console blanking using APM在屏幕空白时关闭LCD背光,事实上对所有的笔记本都无效RTC stores time in GMT将硬件时钟应该设为格林威治时间,否则视为本地时间.建议你使用GMT,这样你无须为时区的改变而担心Allow interrupts during APM BIOS calls允许APM的BIOS调用时中断,IBM Thinkpad的一些新机器需要这项.如果休眠时挂机(包括睡下去就醒不来),可以试试它Use real mode APM BIOS call to power off此驱动为某些有Bug的BIOS准备,如果你的系统不能正常关机或关机时崩溃,可以试试它CPU Frequency scaling允许动态改变CPU主频,达到省电和降温的目的,必须同时启用下面的一种governor才行Enable CPUfreq debugging允许对CPUfreq进行调试CPU frequency translation statistics通过sysfs文件系统输出CPU频率变换的统计信息CPU frequency translation statistics details输出详细的CPU频率变换统计信息Default CPUFreq governor默认的CPU频率调节器'performance' governor'性能'优先,静态的将频率设置为cpu支持的最高频率'powersave' governor'节能'优先,静态的将频率设置为cpu支持的最低频率'userspace' governor for userspace frequency scaling既允许手动调整cpu频率,也允许用户空间的程序动态的调整cpu频率(需要额外的调频软件,比如cpufreqd)'ondemand' cpufreq policy governor'立即响应',周期性的考察CPU负载并自动的动态调整cpu频率(不需要额外的调频软件),适合台式机'conservative' cpufreq governor'保守',和'ondemand'相似,但是频率的升降是渐变式的(幅度不会很大),更适合用于笔记本/PDA/AMD64环境ACPI Processor P-States driver将ACPI2.0的处理器性能状态报告给CPUFreq processor drivers以决定如何调整频率,该选项依赖于ACPI->Processor{省略的部分请按照自己实际使用的CPU选择}/proc/acpi/processor/../performance interface内核帮助文档反对使用该选项,即将被废除Relaxed speedstep capability checks放松对系统的speedstep兼容性检查,仅在某些老旧的Intel系统上需要打开Bus options (PCI, PCMCIA, EISA, MCA, ISA)总线选项PCI supportPCI支持,如果使用了PCI或PCI Express设备就必选PCI access modePCI访问模式,强列建议选"Any"(系统将优先使用"MMConfig",然后使用"BIOS",最后使用"Direct"检测PCI设备)PCI Express supportPCI Express支持(目前主要用于显卡和千兆网卡)PCI Express Hotplug driver如果你的主板和设备都支持PCI Express热插拔就可以选上Use polling mechanism for hot-plug events对热插拔事件采用轮询机制,仅用于测试目的Root Port Advanced Error Reporting support由PCI Express AER驱动程序处理发送到Root Port的错误信息Message Signaled Interrupts (MSI and MSI-X)PCI Express支持两类中断:INTx使用传统的IRQ中断,可以与现行的PCI 总线的驱动程序和操作系统兼容;MSI则是通过inbound Memory Write触发和发送中断,更适合多CPU系统.可以使用"pci=nomsi"内核引导参数关闭MSIPCI Debugging将PCI调试信息输出到系统日志里Interrupts on hypertransport devices允许本地的hypertransport设备使用中断ISA support现在基本上没有ISA的设备了,如果你有就选吧MCA support微通道总线,老旧的IBM的台式机和笔记本上可能会有这种总线NatSemi SCx200 support在使用AMD Geode处理器的机器上才可能有PCCARD (PCMCIA/CardBus) supportPCMCIA卡(主要用于笔记本)支持Enable PCCARD debugging仅供调试16-bit PCMCIA support一些老的PCMCIA卡使用16位的CardBus32-bit CardBus support当前的PCMCIA卡基本上都是32位的CardBusCardBus yenta-compatible bridge support使用PCMCIA卡的基本上都需要选择这一项,子项请按照自己实际使用的PCMCIA卡选择{省略的部分请按照自己实际使用的PCMCIA卡选择}PCI Hotplug SupportPCI热插拔支持,如果你有这样的设备就到子项中去选吧Executable file formats可执行文件格式Kernel support for ELF binariesELF是开放平台下最常用的二进制文件格式,支持动态连接,支持不同的硬件平台.除非你知道自己在做什么,否则必选Kernel support for a.out and ECOFF binaries早期UNIX系统的可执行文件格式,目前已经被ELF格式取代Kernel support for MISC binaries允许插入二进制的封装层到内核中,使用Java,.NET,Python,Lisp等语言编写的程序时需要它Networking网络Networking options网络选项Network packet debugging在调试不合格的包时加上额外的附加信息,但在遇到Dos攻击时你可能会被日志淹没Packet socket这种Socket可以让应用程序(比如tcpdump,iptables)直接与网络设备通讯,而不通过内核中的其它中介协议Packet socket: mmapped IO让Packet socket驱动程序使用IO映射机制以使连接速度更快Unix domain sockets一种仅运行于本机上的效率高于TCP/IP的Socket,简称Unix socket.许多程序都使用它在操作系统内部进行进程间通信(IPC),比如X Window和syslogTransformation user configuration interface为IPsec(可在ip层加密)之类的工具提供XFRM用户配置接口支持Transformation sub policy supportXFRM子策略支持,仅供开发者使用PF_KEY sockets用于可信任的密钥管理程序和操作系统内核内部的密钥管理进行通信,IPsec依赖于它TCP/IP networkingTCP/IP协议当然要选IP: multicasting群组广播,似乎与网格计算有关,仅在使用MBONE的时候才需要IP: advanced router高级路由,如果想做一个路由器就选吧IP: policy routing策略路由IP: equal cost multipath用于路由的基于目的地址的负载均衡IP: verbose route monitoring显示冗余的路由监控信息IP: kernel level autoconfiguration在内核启动时自动配置ip地址/路由表等,需要从网络启动的无盘工作站才需要这个东西IP: tunnelingIP隧道,将一个IP报文封装在另一个IP报文内的技术IP: GRE tunnels over IP基于IP的GRE(通用路由封装)隧道IP: multicast routing多重传播路由IP: ARP daemon support这东西尚处于试验阶段就已经被废弃了IP: TCP syncookie support抵抗SYN flood攻击的好东西,要启用它必须同时启用/proc文件系统和"Sysctl support",然后在系统启动并挂载了/proc之后执行"echo1 >/proc/sys/net/ipv4/tcp_syncookies"命令IP: AH transformationIPsec验证头(AH)实现了数据发送方的验证处理,可确保数据既对于未经验证的站点不可用也不能在路由过程中更改IP: ESP transformationIPsec封闭安全负载(ESP)实现了发送方的验证处理和数据加密处理,用以确保数据不会被拦截/查看或复制IP: IPComp transformationIPComp(IP静荷载压缩协议),用于支持IPsecIP: IPsec transport modeIPsec传输模式,常用于对等通信,用以提供内网安全.数据包经过了加密但IP头没有加密,因此任何标准设备或软件都可查看和使用IP头IP: IPsec tunnel modeIPsec隧道模式,用于提供外网安全(包括虚拟专用网络).整个数据包(数据头和负载)都已经过加密处理且分配有新的ESP头/IP头和验证尾,从而能够隐藏受保护站点的拓扑结构IP: IPsec BEET modeIPsec BEET模式INET: socket monitoring interfacesocket监视接口,一些Linux本地工具(如:包含ss的iproute2)需要使用它TCP: advanced congestion control高级拥塞控制,如果没有特殊需求(比如无线网络)就别选了,内核会自动将默认的拥塞控制设为"Cubic"并将"Reno"作为候补IP: Virtual Server ConfigurationIP虚拟服务器允许你基于多台物理机器构建一台高性能的虚拟服务器,不玩集群就别选了The IPv6 protocol你要是需要IPv6就选吧NetLabel subsystem supportNetLabel子系统为诸如CIPSO与RIPSO之类能够在分组信息上添加标签的协议提供支持,如果你看不懂就别选了Security Marking对网络包进行安全标记,类似于nfmark,但主要是为安全目的而设计,如果你不明白的话就别选Network packet filtering (replaces ipchains)Netfilter可以对数据包进行过滤和修改,可以作为防火墙("packet filter"或"proxy-based")或网关(NAT)或代理(proxy)或网桥使用.选中此选项后必须将"Fast switching"关闭,否则将前功尽弃Network packet filtering debugging仅供开发者调试Netfilter使用Bridged IP/ARP packets filtering如果你希望使用一个针对桥接的防火墙就打开它Core Netfilter Configuration核心Netfilter配置(当包流过Chain时如果match某个规则那么将由该规则的target来处理,否则将由同一个Chain中的下一个规则进行匹配,若不match所有规则那么最终将由该Chain的policy进行处理) Netfilter netlink interface允许Netfilter在与用户空间通信时使用新的netlink接口.netlink Socket是Linux用户态与内核态交流的主要方法之一,且越来越被重视.Netfilter NFQUEUE over NFNETLINK interface通过NFNETLINK接口对包进行排队Netfilter LOG over NFNETLINK interface通过NFNETLINK接口对包记录.该选项废弃了ipt_ULOG和ebg_ulog机制,并打算在将来废弃基于syslog的ipt_LOG和ip6t_LOG模块Layer 3 Independent Connection tracking独立于第三层的链接跟踪,通过广义化的ip_conntrack支持其它非IP协议的第三层协议Netfilter Xtables support如果你打算使用ip_tables,ip6_tables,arp_tables之一就必须选上"CLASSIFY" target support允许为包设置优先级,一些排队规则(atm,cbq,dsmark,pfifo_fast,htb,prio)需要使用它"CONNMARK" target support类似于"MARK",但影响的是连接标记的值"DSCP" target support允许对ip包头部的DSCP(Differentiated Services Codepoint)字段进行修改,该字段常用于Qos"MARK" target support允许对包进行标记(通常配合ip命令使用),这样就可以改变路由策略或者被其它子系统用来改变其行为"NFQUEUE" target Support用于替代老旧的QUEUE(iptables内建的target之一),因为NFQUEUE能支持最多65535个队列,而QUEUE只能支持一个"NOTRACK" target support允许规则指定哪些包不进入链接跟踪/NAT子系统"SECMARK" target support允许对包进行安全标记,用于安全子系统"CONNSECMARK" target support针对链接进行安全标记,同时还会将连接上的标记还原到包上(如果链接中的包尚未进行安全标记),通常与SECMARK target联合使用"comment" match support允许你在iptables规则集中加入注释"connbytes" per-connection counter match support允许针对单个连接内部每个方向(进/出)匹配已经传送的字节数/包数"connmark" connection mark match support允许针对每个会话匹配先前由"CONNMARK"设置的标记值"conntrack" connection tracking match support连接跟踪匹配,是"state"的超集,它允许额外的链接跟踪信息,在需要设置一些复杂的规则(比如网关)时很有用"DCCP" protocol match supportDCCP是打算取代UDP的新传输协议,它在UDP的基础上增加了流控和拥塞控制机制,面向实时业务"DSCP" match support允许对IP包头的DSCP字段进行匹配"ESP" match support允许对IPSec包中的ESP头进行匹配,使用IPsec的话就选上吧"helper" match support加载特定协议的连接跟踪辅助模块,由该模块过滤所跟踪的连接类型的包,比如ip_conntrack_ftp模块"length" match support允许对包的长度进行匹配"limit" match support允许根据包的进出速率进行规则匹配,常和"LOG target"配合使用以抵抗某些Dos攻击"mac" address match support允许根据以太网的MAC进行匹配,常用于无线网络环境"mark" match support允许对先前由"MARK"标记的特定标记值进行匹配IPsec "policy" match support使用IPsec就选上吧Multiple port match support允许对TCP或UDP包同时匹配多个端口(通常情况下只能匹配一个端口) "physdev" match support允许对到达的或将要离开的物理桥端口进行匹配"pkttype" packet type match support允许对封包目的地址类别(广播/群播/直播)进行匹配"quota" match support允许对总字节数的限额值进行匹配"realm" match support允许对iptables中的路由子系统中的realm值进行匹配"sctp" protocol match support流控制传输协议(SCTP),十年以后也许能够普及的东西"state" match support这是对包进行分类的有力工具,它允许利用连接跟踪信息对连接中处于特定状态的包进行匹配"statistic" match support允许根据一个给定的百分率对包进行周期性的或随机性的匹配"string" match support允许根据包所承载的数据中包含的特定字符串进行匹配"tcpmss" match support允许根据TCP SYN包头中的MSS(最大分段长度)选项的值进行匹配IP: Netfilter Configuration针对IPv4的Netfilter配置Connection tracking (required for masq/NAT)链接跟踪.可用于报文伪装或地址转换,也可用于增强包过滤能力Connection tracking flow accounting允许针对每个连接记录已经传送的字节/包数,常用于connbytes match Connection mark tracking support允许对连接进行标记,与针对单独的包进行标记的不同之处在于它是针对连接流的.CONNMARK target和connmark match需要它的支持Connection tracking security mark support允许对连接进行安全标记,通常这些标记包(SECMARK)复制到其所属连接(CONNSECMARK),再从连接复制到其关联的包(SECMARK)Connection tracking events连接跟踪事件支持.如果启用这个选项,连接跟踪代码将提供一个notifier链,它可以被其它内核代码用来获知连接跟踪状态的改变Connection tracking netlink interface支持基于netlink的用户空间接口SCTP protocol connection tracking supportSCTP是IP网面向多媒体通信的新一代的流控制传输协议FTP protocol supportFTP协议IRC protocol supportIRC协议是一种用来实时聊天协议,用过mIRC的人应当不陌生NetBIOS name service protocol supportNetBIOS名字服务协议TFTP protocol supportTFTP是基于UDP的比FTP简单的文件传输协议Amanda backup protocol supportAmanda备份协议PPTP protocol support点对点隧道协议(PPTP)是一种支持多协议虚拟专用网络的网络技术,ADSL 用户对它应该很熟悉H.323 protocol supportITU-T提出的用于IP电话的协议SIP protocol supportIETE提出的用于IP电话的协议IP Userspace queueing via NETLINK已废弃IP tables support (required for filtering/masq/NAT)要用iptables就肯定要选上IP range match support允许对ip地址的范围进行匹配TOS match support允许对ip包头的TOS(Type Of Service)字段进行匹配recent match support可以创建一个或多个刚刚使用过的ip地址列表,然后根据这些列表进行匹配ECN match support允许对TCP/IP包头的ECN(Explicit Congestion Notification)字段进行匹配.ECN是一种显式拥塞通知技术,它不但要求路由器支持而且要求端到端主机的支持,其基本思想是当路由器发生早期拥塞时不是丢弃包而是尽量对包进行标记,接收方接到带有ECN提示的包时,通知发送方网络即将发生拥塞,也就是它通过对包的标记提示TCP源即将发生拥塞,从而引发拥塞避免算法AH match support允许对IPSec包头的AH字段进行匹配TTL match support允许对ip包头的TTL(生存期)字段进行匹配Owner match support允许对本地生成的包按照其宿主(user,group,process,session)进行匹配address type match support允许对地址类型(单播,本地,广播)进行匹配。
linux 内核编译各个选项的含义

Code maturity level options代码成熟度选项Prompt for development and/or incomplete code/drivers显示尚在开发中或尚未完成的代码与驱动.除非你是测试人员或者开发者,否则请勿选择General setup常规设置Local version - append to kernel release在内核版本后面加上自定义的版本字符串(小于64字符),可以用"uname -a"命令看到Automatically append version information to the version string 自动在版本字符串后面添加版本信息,编译时需要有perl以及git仓库支持Support for paging of anonymous memory (swap)使用交换分区或者交换文件来做为虚拟内存System V IPCSystem V进程间通信(IPC)支持,许多程序需要这个功能.必选,除非你知道自己在做什么IPC NamespacesIPC命名空间支持,不确定可以不选POSIX Message QueuesPOSIX消息队列,这是POSIX IPC中的一部分BSD Process Accounting将进程的统计信息写入文件的用户级系统调用,主要包括进程的创建时间/创建者/内存占用等信息BSD Process Accounting version 3 file format使用新的第三版文件格式,可以包含每个进程的PID和其父进程的PID,但是不兼容老版本的文件格式Export task/process statistics through netlink通过netlink接口向用户空间导出任务/进程的统计信息,与BSD Process Accounting的不同之处在于这些统计信息在整个任务/进程生存期都是可用的Enable per-task delay accounting在统计信息中包含进程等候系统资源(cpu,IO同步,内存交换等)所花费的时间UTS NamespacesUTS名字空间支持,不确定可以不选Auditing support审计支持,某些内核模块(例如SELinux)需要它,只有同时选择其子项才能对系统调用进行审计Enable system-call auditing support支持对系统调用的审计Kernel .config support把内核的配置信息编译进内核中,以后可以通过scripts/extract-ikconfig脚本来提取这些信息Enable access to .config through /proc/config.gz允许通过/proc/config.gz访问内核的配置信息Cpuset support只有含有大量CPU(大于16个)的SMP系统或NUMA(非一致内存访问)系统才需要它Kernel->user space relay support (formerly relayfs)在某些文件系统上(比如debugfs)提供从内核空间向用户空间传递大量数据的接口Initramfs source file(s)initrd已经被initramfs取代,如果你不明白这是什么意思,请保持空白Optimize for size (Look out for broken compilers!)编译时优化内核尺寸(使用"-Os"而不是"-O2"参数编译),有时会产生错误的二进制代码Enable extended accounting over taskstats收集额外的进程统计信息并通过taskstats接口发送到用户空间Configure standard kernel features (for small systems)配置标准的内核特性(为小型系统)Enable 16-bit UID system calls允许对UID系统调用进行过时的16-bit包装Sysctl syscall support不需要重启就能修改内核的某些参数和变量,如果你也选择了支持/proc,将能从/proc/sys存取可以影响内核行为的参数或变量Load all symbols for debugging/kksymoops装载所有的调试符号表信息,仅供调试时选择Include all symbols in kallsyms在kallsyms中包含内核知道的所有符号,内核将会增大300KDo an extra kallsyms pass除非你在kallsyms中发现了bug并需要报告这个bug才打开该选项Support for hot-pluggable devices支持热插拔设备,如usb与pc卡等,Udev也需要它Enable support for printk允许内核向终端打印字符信息,在需要诊断内核为什么不能运行时选择BUG() support显示故障和失败条件(BUG和WARN),禁用它将可能导致隐含的错误被忽略Enable ELF core dumps内存转储支持,可以帮助调试ELF格式的程序Enable full-sized data structures for core在内核中使用全尺寸的数据结构.禁用它将使得某些内核的数据结构减小以节约内存,但是将会降低性能Enable futex support快速用户空间互斥体可以使线程串行化以避免竞态条件,也提高了响应速度.禁用它将导致内核不能正确的运行基于glibc的程序Enable eventpoll support支持事件轮循的系统调用Use full shmem filesystem完全使用shmem来代替ramfs.shmem是基于共享内存的文件系统(可能用到swap),在启用TMPFS后可以挂载为tmpfs供用户空间使用,它比简单的ramfs先进许多Use full SLAB allocator使用SLAB完全取代SLOB进行内存分配,SLAB是一种优秀的内存分配管理器,推荐使用Enable VM event counters for /proc/vmstat允许在/proc/vmstat中包含虚拟内存事件记数器Loadable module support可加载模块支持Enable loadable module support打开可加载模块支持,如果打开它则必须通过"make modules_install"把内核模块安装在/lib/modules/中Module unloading允许卸载已经加载的模块Forced module unloading允许强制卸载正在使用中的模块(比较危险)Module versioning support允许使用其他内核版本的模块(可能会出问题)Source checksum for all modules为所有的模块校验源码,如果你不是自己编写内核模块就不需要它Automatic kernel module loading让内核通过运行modprobe来自动加载所需要的模块,比如可以自动解决模块的依赖关系Block layer块设备层Enable the block layer块设备支持,使用硬盘/USB/SCSI设备者必选Support for Large Block Devices仅在使用大于2TB的块设备时需要Support for tracing block io actions块队列IO跟踪支持,它允许用户查看在一个块设备队列上发生的所有事件,可以通过blktrace程序获得磁盘当前的详细统计数据Support for Large Single Files仅在可能使用大于2TB的文件时需要IO SchedulersIO调度器Anticipatory I/O scheduler假设一个块设备只有一个物理查找磁头(例如一个单独的SATA硬盘),将多个随机的小写入流合并成一个大写入流,用写入延时换取最大的写入吞吐量.适用于大多数环境,特别是写入较多的环境(比如文件服务器) Deadline I/O scheduler使用轮询的调度器,简洁小巧,提供了最小的读取延迟和尚佳的吞吐量,特别适合于读取较多的环境(比如数据库)CFQ I/O scheduler使用QoS策略为所有任务分配等量的带宽,避免进程被饿死并实现了较低的延迟,可以认为是上述两种调度器的折中.适用于有大量进程的多用户系统Default I/O scheduler默认IO调度器Processor type and features中央处理器(CPU)类型及特性Symmetric multi-processing support对称多处理器支持,如果你有多个CPU或者使用的是多核CPU就选上.此时"Enhanced Real Time Clock Support"选项必须开启,"Advanced Power Management"选项必须关闭Subarchitecture Type处理器的子架构,大多数人都应当选择"PC-compatible"Processor family处理器系列,请按照你实际使用的CPU选择Generic x86 support通用x86支持,如果你的CPU能够在上述"Processor family"中找到就别选HPET Timer SupportHPET是替代8254芯片的新一代定时器,i686及以上级别的主板都支持,可以安全的选上Maximum number of CPUs支持的最大CPU数,每增加一个内核将增加8K体积SMT (Hyperthreading) scheduler support支持Intel的超线程(HT)技术Multi-core scheduler support针对多核CPU进行调度策略优化Preemption Model内核抢占模式No Forced Preemption (Server)适合服务器环境的禁止内核抢占Voluntary Kernel Preemption (Desktop)适合普通桌面环境的自愿内核抢占Preemptible Kernel (Low-Latency Desktop)适合运行实时程序的主动内核抢占Preempt The Big Kernel Lock可以抢占大内核锁,应用于实时要求高的场合,不适合服务器环境Machine Check Exception让CPU检测到系统故障时通知内核,以便内核采取相应的措施(如过热关机等)Check for non-fatal errors on AMD Athlon/Duron / Intel Pentium 4 每5秒检测一次这些cpu的非致命错误并纠正它们,同时记入日志check for P4 thermal throttling interrupt当P4的cpu过热时显示一条警告消息Enable VM86 support虚拟X86支持,在DOSEMU下运行16-bit程序或XFree86通过BIOS初始化某些显卡的时候才需要Toshiba Laptop supportToshiba笔记本模块支持Dell laptop supportDell笔记本模块支持Enable X86 board specific fixups for reboot修正某些旧x86主板的重起bug,这种主板基本绝种了/dev/cpu/microcode - Intel IA32 CPU microcode support使用不随Linux内核发行的IA32微代码,你必需有IA32微代码二进制文件,仅对Intel的CPU有效/dev/cpu/*/msr - Model-specific register support在多cpu系统中让特权CPU访问x86的MSR寄存器/dev/cpu/*/cpuid - CPU information support能从/dev/cpu/x/cpuid获得CPU的唯一标识符(CPUID)Firmware Drivers固件驱动程序BIOS Enhanced Disk Drive calls determine boot disk有些BIOS支持从某块特定的硬盘启动(如果BIOS不支持则可能无法启动),目前大多数BIOS还不支持BIOS update support for DELL systems via sysfs仅适用于DELL机器Dell Systems Management Base Driver仅适用于DELL机器High Memory Support最高内存支持,总内存小于等于1G的选"off",大于4G的选"64G" Memory split如果你不是绝对清楚自己在做什么,不要改动这个选项Memory model一般选"Flat Memory",其他选项涉及内存热插拔64 bit Memory and IO resources使用64位的内存和IO资源Allocate 3rd-level pagetables from highmem在内存很多(大于4G)的机器上将用户空间的页表放到高位内存区,以节约宝贵的低端内存Math emulation数学协处理器仿真,486DX以上的cpu就不要选它了MTRR (Memory Type Range Register) support打开它可以提升PCI/AGP总线上的显卡2倍以上的速度,并且可以修正某些BIOS错误Boot from EFI supportEFI是一种可代替传统BIOS的技术(目前的Grub/LILO尚不能识别它),但是现在远未普及Enable kernel irq balancing让内核将irq中断平均分配给多个CPU以进行负载均衡,但是要配合irqbanlance守护进程才行Use register arguments使用"-mregparm=3"参数编译内核,将前3个参数以寄存器方式进行参数调用,可以生成更紧凑和高效的代码Enable seccomp to safely compute untrusted bytecode只有嵌入式系统可以不选Timer frequency内核时钟频率,桌面推荐"1000 HZ",服务器推荐"100 HZ"或"250 HZ" kexec system call提供kexec系统调用,可以不必重启而切换到另一个内核kernel crash dumps被kexec启动后产生内核崩溃转储Physical address where the kernel is loaded内核加载的物理地址,除非你知道自己在做什么,否则不要修改.在提供kexec系统调用的情况下可能要修改它Support for hot-pluggable CPUs对热插拔CPU提供支持Compat VDSO support如果Glibc版本大于等于2.3.3就不选,否则就选上Power management options电源管理选项Power Management support电源管理有APM和ACPI两种标准且不能同时使用.即使关闭该选项,X86上运行的Linux也会在空闲时发出HLT指令将CPU进入睡眠状态Legacy Power Management API传统的电源管理API,比如软关机和系统休眠等接口Power Management Debug Support仅供调试使用Driver model /sys/devices/.../power/state files内核帮助文档反对使用该选项,即将被废除ACPI (Advanced Configuration and Power Interface) Support 必须运行acpid守护程序ACPI才能起作用.ACPI是为了取代APM而设计的,因此应该尽量使用ACPI而不是APMAC Adapter如果你的系统可以在AC和电池之间转换就可以选Battery通过/proc/acpi/battery向用户提供电池状态信息,用电池的笔记本可以选Button守护程序捕获Power,Sleep,Lid按钮事件,并根据/proc/acpi/event做相应的动作,软件控制的poweroff需要它Video仅对集成在主板上的显卡提供ACPI2.0支持,且不是所有集成显卡都支持Generic Hotkey统一的热键驱动,建议不选Fan允许通过用户层的程序来对系统风扇进行控制(开,关,查询状态),支持它的硬件并不多Dock支持由ACPI控制的集线器(docking stations)Processor让ACPI处理空闲状态,并使用ACPI C2和C3处理器状态在空闲时节省电能,同时它还被cpufreq的"Performance-state drivers"选项所依赖Thermal Zone系统温度过高时可以利用ACPI thermal zone及时调整工作状态以避免你的CPU被烧毁ASUS/Medion Laptop ExtrasASUS笔记本专用,以提供额外按钮的支持,用户可以通过/proc/acpi/asus来打开或者关闭LCD的背光/调整亮度/定制LED的闪烁指示等功能IBM ThinkPad Laptop ExtrasIBM ThinkPad专用Toshiba Laptop ExtrasToshiba笔记本专用Disable ACPI for systems before Jan 1st this year输入四位数的年份,在该年的1月1日前不使用ACPI的功能("0"表示一直使用)Debug Statements详细的ACPI调试信息,不搞开发就别选Power Management Timer Support这个Timer在所有ACPI兼容的平台上都可用,且不会受PM功能的影响,建议总是启用它.如果你在kernel log中看到了'many lost ticks'那就必须启用它ACPI0004,PNP0A05 and PNP0A06 Container Driver支持内存和CPU的热插拔Smart Battery System支持依赖于I2C的"智能电池".这种电池非常老旧且罕见,还与当前的ACPI标准兼容性差APM (Advanced Power Management) BIOS SupportAPM在SMP机器上必须关闭,一般来说当前的笔记本都支持ACPI,所以应尽量关闭该该选项Ignore USER SUSPEND只有NEC Versa M系列的笔记本才需要选择这一项Enable PM at boot time系统启动时即启用APM,选上这个选项能让系统自动的进行电源管理,但常常导致启动时死机Make CPU Idle calls when idle系统空闲时调用空闲指令(halt),只有老式的CPU才需要选它,且对于SMP 系统必须关闭Enable console blanking using APM在屏幕空白时关闭LCD背光,事实上对所有的笔记本都无效RTC stores time in GMT将硬件时钟应该设为格林威治时间,否则视为本地时间.建议你使用GMT,这样你无须为时区的改变而担心Allow interrupts during APM BIOS calls允许APM的BIOS调用时中断,IBM Thinkpad的一些新机器需要这项.如果休眠时挂机(包括睡下去就醒不来),可以试试它Use real mode APM BIOS call to power off此驱动为某些有Bug的BIOS准备,如果你的系统不能正常关机或关机时崩溃,可以试试它CPU Frequency scaling允许动态改变CPU主频,达到省电和降温的目的,必须同时启用下面的一种governor才行Enable CPUfreq debugging允许对CPUfreq进行调试CPU frequency translation statistics通过sysfs文件系统输出CPU频率变换的统计信息CPU frequency translation statistics details输出详细的CPU频率变换统计信息Default CPUFreq governor默认的CPU频率调节器'performance' governor'性能'优先,静态的将频率设置为cpu支持的最高频率'powersave' governor'节能'优先,静态的将频率设置为cpu支持的最低频率'userspace' governor for userspace frequency scaling既允许手动调整cpu频率,也允许用户空间的程序动态的调整cpu频率(需要额外的调频软件,比如cpufreqd)'ondemand' cpufreq policy governor'立即响应',周期性的考察CPU负载并自动的动态调整cpu频率(不需要额外的调频软件),适合台式机'conservative' cpufreq governor'保守',和'ondemand'相似,但是频率的升降是渐变式的(幅度不会很大),更适合用于笔记本/PDA/AMD64环境ACPI Processor P-States driver将ACPI2.0的处理器性能状态报告给CPUFreq processor drivers以决定如何调整频率,该选项依赖于ACPI->Processor{省略的部分请按照自己实际使用的CPU选择}/proc/acpi/processor/../performance interface内核帮助文档反对使用该选项,即将被废除Relaxed speedstep capability checks放松对系统的speedstep兼容性检查,仅在某些老旧的Intel系统上需要打开Bus options (PCI, PCMCIA, EISA, MCA, ISA)总线选项PCI supportPCI支持,如果使用了PCI或PCI Express设备就必选PCI access modePCI访问模式,强列建议选"Any"(系统将优先使用"MMConfig",然后使用"BIOS",最后使用"Direct"检测PCI设备)PCI Express supportPCI Express支持(目前主要用于显卡和千兆网卡)PCI Express Hotplug driver如果你的主板和设备都支持PCI Express热插拔就可以选上Use polling mechanism for hot-plug events对热插拔事件采用轮询机制,仅用于测试目的Root Port Advanced Error Reporting support由PCI Express AER驱动程序处理发送到Root Port的错误信息Message Signaled Interrupts (MSI and MSI-X)PCI Express支持两类中断:INTx使用传统的IRQ中断,可以与现行的PCI 总线的驱动程序和操作系统兼容;MSI则是通过inbound Memory Write触发和发送中断,更适合多CPU系统.可以使用"pci=nomsi"内核引导参数关闭MSIPCI Debugging将PCI调试信息输出到系统日志里Interrupts on hypertransport devices允许本地的hypertransport设备使用中断ISA support现在基本上没有ISA的设备了,如果你有就选吧MCA support微通道总线,老旧的IBM的台式机和笔记本上可能会有这种总线NatSemi SCx200 support在使用AMD Geode处理器的机器上才可能有PCCARD (PCMCIA/CardBus) supportPCMCIA卡(主要用于笔记本)支持Enable PCCARD debugging仅供调试16-bit PCMCIA support一些老的PCMCIA卡使用16位的CardBus32-bit CardBus support当前的PCMCIA卡基本上都是32位的CardBusCardBus yenta-compatible bridge support使用PCMCIA卡的基本上都需要选择这一项,子项请按照自己实际使用的PCMCIA卡选择{省略的部分请按照自己实际使用的PCMCIA卡选择}PCI Hotplug SupportPCI热插拔支持,如果你有这样的设备就到子项中去选吧Executable file formats可执行文件格式Kernel support for ELF binariesELF是开放平台下最常用的二进制文件格式,支持动态连接,支持不同的硬件平台.除非你知道自己在做什么,否则必选Kernel support for a.out and ECOFF binaries早期UNIX系统的可执行文件格式,目前已经被ELF格式取代Kernel support for MISC binaries允许插入二进制的封装层到内核中,使用Java,.NET,Python,Lisp等语言编写的程序时需要它Networking网络Networking options网络选项Network packet debugging在调试不合格的包时加上额外的附加信息,但在遇到Dos攻击时你可能会被日志淹没Packet socket这种Socket可以让应用程序(比如tcpdump,iptables)直接与网络设备通讯,而不通过内核中的其它中介协议Packet socket: mmapped IO让Packet socket驱动程序使用IO映射机制以使连接速度更快Unix domain sockets一种仅运行于本机上的效率高于TCP/IP的Socket,简称Unix socket.许多程序都使用它在操作系统内部进行进程间通信(IPC),比如X Window和syslogTransformation user configuration interface为IPsec(可在ip层加密)之类的工具提供XFRM用户配置接口支持Transformation sub policy supportXFRM子策略支持,仅供开发者使用PF_KEY sockets用于可信任的密钥管理程序和操作系统内核内部的密钥管理进行通信,IPsec依赖于它TCP/IP networkingTCP/IP协议当然要选IP: multicasting群组广播,似乎与网格计算有关,仅在使用MBONE的时候才需要IP: advanced router高级路由,如果想做一个路由器就选吧IP: policy routing策略路由IP: equal cost multipath用于路由的基于目的地址的负载均衡IP: verbose route monitoring显示冗余的路由监控信息IP: kernel level autoconfiguration在内核启动时自动配置ip地址/路由表等,需要从网络启动的无盘工作站才需要这个东西IP: tunnelingIP隧道,将一个IP报文封装在另一个IP报文内的技术IP: GRE tunnels over IP基于IP的GRE(通用路由封装)隧道IP: multicast routing多重传播路由IP: ARP daemon support这东西尚处于试验阶段就已经被废弃了IP: TCP syncookie support抵抗SYN flood攻击的好东西,要启用它必须同时启用/proc文件系统和"Sysctl support",然后在系统启动并挂载了/proc之后执行"echo1 >/proc/sys/net/ipv4/tcp_syncookies"命令IP: AH transformationIPsec验证头(AH)实现了数据发送方的验证处理,可确保数据既对于未经验证的站点不可用也不能在路由过程中更改IP: ESP transformationIPsec封闭安全负载(ESP)实现了发送方的验证处理和数据加密处理,用以确保数据不会被拦截/查看或复制IP: IPComp transformationIPComp(IP静荷载压缩协议),用于支持IPsecIP: IPsec transport modeIPsec传输模式,常用于对等通信,用以提供内网安全.数据包经过了加密但IP头没有加密,因此任何标准设备或软件都可查看和使用IP头IP: IPsec tunnel modeIPsec隧道模式,用于提供外网安全(包括虚拟专用网络).整个数据包(数据头和负载)都已经过加密处理且分配有新的ESP头/IP头和验证尾,从而能够隐藏受保护站点的拓扑结构IP: IPsec BEET modeIPsec BEET模式INET: socket monitoring interfacesocket监视接口,一些Linux本地工具(如:包含ss的iproute2)需要使用它TCP: advanced congestion control高级拥塞控制,如果没有特殊需求(比如无线网络)就别选了,内核会自动将默认的拥塞控制设为"Cubic"并将"Reno"作为候补IP: Virtual Server ConfigurationIP虚拟服务器允许你基于多台物理机器构建一台高性能的虚拟服务器,不玩集群就别选了The IPv6 protocol你要是需要IPv6就选吧NetLabel subsystem supportNetLabel子系统为诸如CIPSO与RIPSO之类能够在分组信息上添加标签的协议提供支持,如果你看不懂就别选了Security Marking对网络包进行安全标记,类似于nfmark,但主要是为安全目的而设计,如果你不明白的话就别选Network packet filtering (replaces ipchains)Netfilter可以对数据包进行过滤和修改,可以作为防火墙("packet filter"或"proxy-based")或网关(NAT)或代理(proxy)或网桥使用.选中此选项后必须将"Fast switching"关闭,否则将前功尽弃Network packet filtering debugging仅供开发者调试Netfilter使用Bridged IP/ARP packets filtering如果你希望使用一个针对桥接的防火墙就打开它Core Netfilter Configuration核心Netfilter配置(当包流过Chain时如果match某个规则那么将由该规则的target来处理,否则将由同一个Chain中的下一个规则进行匹配,若不match所有规则那么最终将由该Chain的policy进行处理) Netfilter netlink interface允许Netfilter在与用户空间通信时使用新的netlink接口.netlink Socket是Linux用户态与内核态交流的主要方法之一,且越来越被重视.Netfilter NFQUEUE over NFNETLINK interface通过NFNETLINK接口对包进行排队Netfilter LOG over NFNETLINK interface通过NFNETLINK接口对包记录.该选项废弃了ipt_ULOG和ebg_ulog机制,并打算在将来废弃基于syslog的ipt_LOG和ip6t_LOG模块Layer 3 Independent Connection tracking独立于第三层的链接跟踪,通过广义化的ip_conntrack支持其它非IP协议的第三层协议Netfilter Xtables support如果你打算使用ip_tables,ip6_tables,arp_tables之一就必须选上"CLASSIFY" target support允许为包设置优先级,一些排队规则(atm,cbq,dsmark,pfifo_fast,htb,prio)需要使用它"CONNMARK" target support类似于"MARK",但影响的是连接标记的值"DSCP" target support允许对ip包头部的DSCP(Differentiated Services Codepoint)字段进行修改,该字段常用于Qos"MARK" target support允许对包进行标记(通常配合ip命令使用),这样就可以改变路由策略或者被其它子系统用来改变其行为"NFQUEUE" target Support用于替代老旧的QUEUE(iptables内建的target之一),因为NFQUEUE能支持最多65535个队列,而QUEUE只能支持一个"NOTRACK" target support允许规则指定哪些包不进入链接跟踪/NAT子系统"SECMARK" target support允许对包进行安全标记,用于安全子系统"CONNSECMARK" target support针对链接进行安全标记,同时还会将连接上的标记还原到包上(如果链接中的包尚未进行安全标记),通常与SECMARK target联合使用"comment" match support允许你在iptables规则集中加入注释"connbytes" per-connection counter match support允许针对单个连接内部每个方向(进/出)匹配已经传送的字节数/包数"connmark" connection mark match support允许针对每个会话匹配先前由"CONNMARK"设置的标记值"conntrack" connection tracking match support连接跟踪匹配,是"state"的超集,它允许额外的链接跟踪信息,在需要设置一些复杂的规则(比如网关)时很有用"DCCP" protocol match supportDCCP是打算取代UDP的新传输协议,它在UDP的基础上增加了流控和拥塞控制机制,面向实时业务"DSCP" match support允许对IP包头的DSCP字段进行匹配"ESP" match support允许对IPSec包中的ESP头进行匹配,使用IPsec的话就选上吧"helper" match support加载特定协议的连接跟踪辅助模块,由该模块过滤所跟踪的连接类型的包,比如ip_conntrack_ftp模块"length" match support允许对包的长度进行匹配"limit" match support允许根据包的进出速率进行规则匹配,常和"LOG target"配合使用以抵抗某些Dos攻击"mac" address match support允许根据以太网的MAC进行匹配,常用于无线网络环境"mark" match support允许对先前由"MARK"标记的特定标记值进行匹配IPsec "policy" match support使用IPsec就选上吧Multiple port match support允许对TCP或UDP包同时匹配多个端口(通常情况下只能匹配一个端口) "physdev" match support允许对到达的或将要离开的物理桥端口进行匹配"pkttype" packet type match support允许对封包目的地址类别(广播/群播/直播)进行匹配"quota" match support允许对总字节数的限额值进行匹配"realm" match support允许对iptables中的路由子系统中的realm值进行匹配"sctp" protocol match support流控制传输协议(SCTP),十年以后也许能够普及的东西"state" match support这是对包进行分类的有力工具,它允许利用连接跟踪信息对连接中处于特定状态的包进行匹配"statistic" match support允许根据一个给定的百分率对包进行周期性的或随机性的匹配"string" match support允许根据包所承载的数据中包含的特定字符串进行匹配"tcpmss" match support允许根据TCP SYN包头中的MSS(最大分段长度)选项的值进行匹配IP: Netfilter Configuration针对IPv4的Netfilter配置Connection tracking (required for masq/NAT)链接跟踪.可用于报文伪装或地址转换,也可用于增强包过滤能力Connection tracking flow accounting允许针对每个连接记录已经传送的字节/包数,常用于connbytes match Connection mark tracking support允许对连接进行标记,与针对单独的包进行标记的不同之处在于它是针对连接流的.CONNMARK target和connmark match需要它的支持Connection tracking security mark support允许对连接进行安全标记,通常这些标记包(SECMARK)复制到其所属连接(CONNSECMARK),再从连接复制到其关联的包(SECMARK)Connection tracking events连接跟踪事件支持.如果启用这个选项,连接跟踪代码将提供一个notifier链,它可以被其它内核代码用来获知连接跟踪状态的改变Connection tracking netlink interface支持基于netlink的用户空间接口SCTP protocol connection tracking supportSCTP是IP网面向多媒体通信的新一代的流控制传输协议FTP protocol supportFTP协议IRC protocol supportIRC协议是一种用来实时聊天协议,用过mIRC的人应当不陌生NetBIOS name service protocol supportNetBIOS名字服务协议TFTP protocol supportTFTP是基于UDP的比FTP简单的文件传输协议Amanda backup protocol supportAmanda备份协议PPTP protocol support点对点隧道协议(PPTP)是一种支持多协议虚拟专用网络的网络技术,ADSL 用户对它应该很熟悉H.323 protocol supportITU-T提出的用于IP电话的协议SIP protocol supportIETE提出的用于IP电话的协议IP Userspace queueing via NETLINK已废弃IP tables support (required for filtering/masq/NAT)要用iptables就肯定要选上IP range match support允许对ip地址的范围进行匹配TOS match support允许对ip包头的TOS(Type Of Service)字段进行匹配recent match support可以创建一个或多个刚刚使用过的ip地址列表,然后根据这些列表进行匹配ECN match support允许对TCP/IP包头的ECN(Explicit Congestion Notification)字段进行匹配.ECN是一种显式拥塞通知技术,它不但要求路由器支持而且要求端到端主机的支持,其基本思想是当路由器发生早期拥塞时不是丢弃包而是尽量对包进行标记,接收方接到带有ECN提示的包时,通知发送方网络即将发生拥塞,也就是它通过对包的标记提示TCP源即将发生拥塞,从而引发拥塞避免算法AH match support允许对IPSec包头的AH字段进行匹配TTL match support允许对ip包头的TTL(生存期)字段进行匹配Owner match support允许对本地生成的包按照其宿主(user,group,process,session)进行匹配address type match support允许对地址类型(单播,本地,广播)进行匹配。
人工智能(专升本)单选习题库

人工智能单选习题库一、单选题(共100题,每题1分,共100分)1、rcnn网络用()结构生成候选框?A、SelectiveSearchB、RCNNC、NMSD、RPN正确答案:A2、下列不属于人工智能学派的是A、机会主义B、连接主义C、行为主义D、符号主义正确答案:A3、决策树中不包含一下哪种结点()。
A、内部结点B、外部结点C、叶结点D、根结点正确答案:B4、传统的IT产品的开发遵循的原则是()。
A、三分技术、五分管理、十一分数据B、三分数据、五分管理、十一分体验C、三分技术、七分管理、十二分数据D、三分数据、七分智慧、十二分体验正确答案:C5、Python使用()符号标示注释。
A、#B、&C、//D、*正确答案:A6、()是一个具有大量的专门知识与经验的程序系统,它应用人工智能技术和计算机技术,根据某领域一个或多个专家提供的知识和经验,进行推理和判断,模拟人类专家的决策过程,以便解决那些需要人类专家处理的复杂问题。
A、智能芯片B、机器系统C、人机交互D、专家系统正确答案:D7、数据在完成特征工程的操作后,在构建模型的过程中,以下哪个选项不属于决策树构建过程当中的步骤?A、决策树生成B、特征选取C、剪枝D、数据清理正确答案:D8、一般来讲,下列语言属于人工智能语言的是()。
A、FoxproB、C#C、VJD、LISP正确答案:D9、下面哪个/些超参数的增加可能会造成随机森林数据过拟合()A、学习速率B、树的数量C、树的深度正确答案:C10、下列朴素贝叶斯估计描述错误的是(___)A、为了避免条件概率是所以属性上的联合概率;B、假设属性之间相互独立;C、假设属性之间是相关的;D、采用属性条件独立性假设;正确答案:C11、numpy中向量转成矩阵使用A、reshapeB、arangeC、randomD、reval正确答案:A12、云计算提供的支撑技术,有效解决虚拟化技术、()、海量存储和海量管理等问题A、实际操作B、并行计算C、数据研发D、数据分析正确答案:B13、从产品形态看,以下()属于数据产品中的知识类产品。
典型的白化权函数的定义

典型的白化权函数的定义
典型的白化权函数是指在数据处理中用于消除不相关信息或噪声的一种数学函数。
白化是一种数据预处理方法,其目的是使数据具有相同的方差和零均值。
一个典型的白化权函数通常采用矩阵变换的方式,将数据进行转换,使得数据的协方差矩阵变成单位矩阵,从而消除噪声和不相关信息的影响,提高数据处理的精度和可靠性。
常见的白化权函数包括PCA、ZCA和ICA等,它们都具有不同的特点和适用范围。
在实际应用中,选择合适的白化权函数可以有效地提高数据处理的效率和准确性。
- 1 -。
yolo 颜色归一化参数

yolo 颜色归一化参数【原创实用版】目录1.YOLO 颜色归一化参数的概念2.YOLO 颜色归一化参数的作用3.YOLO 颜色归一化参数的计算方法4.YOLO 颜色归一化参数的实际应用正文1.YOLO 颜色归一化参数的概念YOLO(You Only Look Once)是一种实时目标检测算法,其颜色归一化参数是用于改善算法中颜色空间处理的参数。
在计算机视觉领域,颜色空间处理对于提高识别准确率至关重要,因为不同的颜色空间可能导致相同的颜色在不同的图像中具有不同的表示。
为了解决这个问题,YOLO 采用了颜色归一化参数来统一处理颜色空间。
2.YOLO 颜色归一化参数的作用YOLO 颜色归一化参数的主要作用是统一不同颜色空间的图像处理,使得算法在不同的图像中具有更好的鲁棒性和准确性。
通过使用统一的颜色归一化参数,可以有效地提高算法的识别速度和识别准确率。
3.YOLO 颜色归一化参数的计算方法YOLO 颜色归一化参数的计算方法通常基于一种称为“归一化”的数学操作。
归一化是将一个图像的颜色值映射到另一个颜色值范围的过程,以实现不同颜色空间之间的统一。
常用的归一化方法有最小 - 最大归一化、线性归一化等。
YOLO 颜色归一化参数的具体计算方法取决于所采用的归一化方法。
4.YOLO 颜色归一化参数的实际应用在实际应用中,YOLO 颜色归一化参数通常用于处理来自不同设备、不同摄像头或者不同图像格式的图像。
通过使用合适的颜色归一化参数,可以有效地提高算法在不同场景下的识别准确率和速度。
同时,颜色归一化参数也可以根据实际需求进行调整,以满足不同应用场景的需求。
综上所述,YOLO 颜色归一化参数是一种在计算机视觉领域中具有重要作用的参数,它可以有效地提高算法的识别速度和准确率。
class-f-1原理 -回复

class-f-1原理-回复什么是[classf1原理][classf1原理]是一种用于机器学习和数据分析的算法原理。
它是一种监督学习算法,广泛应用于分类问题,尤其在文本分类和图像识别任务中表现出色。
简单来说,[classf1原理]通过计算分类器的准确率和召回率之间的调和平均值来评估分类器的性能。
[classf1原理]取名自调和平均值的其中一个分数,即F1分数。
F1分数是分类器性能指标的重要衡量标准之一,尤其适用于处理不平衡数据集的场景。
不平衡数据集是指在分类任务中,不同类别的样本数量差距很大。
在这种情况下,仅仅使用准确率来评估分类器的性能可能是不够的,因为分类器可以通过预测多数类别来达到很高的准确率,但却无法很好地识别少数类别。
F1分数通过综合考虑准确率和召回率,能更全面地评价分类器的性能。
F1分数的计算公式为:F1 = 2 * (precision * recall) / (precision + recall)其中,准确率(precision)指的是分类器正确预测为正例的样本数除以分类器预测为正例的总样本数。
召回率(recall)指的是分类器正确预测为正例的样本数除以真实为正例的总样本数。
通过调和平均的方式综合了准确率和召回率,F1分数在不同情况下能够更全面地反映分类器的性能。
[classf1原理]的目标是寻找最佳的分类器,即在给定数据集上能够取得最高F1分数的分类器。
为了达到这个目标,[classf1原理]通常通过交叉验证和参数调优来进行模型选择和优化。
交叉验证是一种将数据集划分为训练集和验证集的技术,用于评估模型的性能和选择最佳参数。
参数调优是通过调整分类器的超参数(例如正则化参数、学习率等)来优化模型的表现。
[classf1原理]的实现可以使用各种机器学习算法,例如逻辑回归、支持向量机(SVM)、决策树和随机森林等。
这些算法在实现[classf1原理]时,通常会使用一些优化技巧,例如特征选择和特征工程,以提高分类器的性能。
bbknn原理

bbknn原理
BBKNN是一种基于KNN的图神经网络模型,它通过将KNN图嵌入
到神经网络中,实现了对图数据的高效处理和学习。
BBKNN的核心思想是将KNN图嵌入到神经网络中,使得神经网络能够利用KNN图中的局部结构信息,从而更好地学习图数据的特征。
BBKNN的实现过程可以分为两个步骤。
首先,需要构建KNN图。
KNN图是一种基于K近邻算法的图结构,它将每个节点与其K个最近邻节点相连。
构建KNN图的过程可以使用传统的K近邻算法,也可
以使用基于局部敏感哈希(LSH)的K近邻算法,以提高构建效率。
其次,需要将KNN图嵌入到神经网络中。
BBKNN使用了一种特殊的嵌入方式,即将KNN图中的每个节点表示为一个向量,并将这些向量作为神经网络的输入。
在神经网络中,每个节点的向量会被传递到相
邻节点,并通过神经网络的层次结构进行处理和学习。
最终,神经网
络会输出每个节点的特征向量,这些特征向量可以用于图数据的分类、聚类和可视化等任务。
BBKNN的优点在于它能够高效地处理大规模的图数据,并且能够利用KNN图中的局部结构信息进行学习。
此外,BBKNN还具有较好的可
扩展性和泛化能力,可以应用于各种类型的图数据。
总之,BBKNN是一种基于KNN的图神经网络模型,它通过将KNN 图嵌入到神经网络中,实现了对图数据的高效处理和学习。
BBKNN具有高效、可扩展和泛化能力强等优点,可以应用于各种类型的图数据处理任务。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Kernel whitening for one-class classificationDavid M.J.Tax1and Piotr Juszczak21Fraunhofer Institute FIRST.IDA,Kekul´e str.7,D-12489Berlin,Germanydavidt@first.fraunhofer.de2Pattern Recognition GroupFaculty of Applied Science,Delft University of TechnologyLorentzweg1,2628CJ Delft,The Netherlandspiotr@ph.tn.tudelft.nlAbstract.In one-class classification one tries to describe a class of tar-get data and to distinguish it from all other possible outlier objects.Obvious applications are areas where outliers are very diverse or verydifficult or expensive to measure,such as in machine diagnostics or inmedical applications.In order to have a good distinction between the tar-get objects and the outliers,good representation of the data is essential.The performance of many one-class classifiers critically depends on thescaling of the data and is often harmed by data distributions in(non-linear)subspaces.This paper presents a simple preprocessing methodwhich actively tries to map the data to a spherical symmetric clusterand is almost insensitive to data distributed in subspaces.It uses tech-niques from Kernel PCA to rescale the data in a kernel feature space tounit variance.This transformed data can now be described very well bythe Support Vector Data Description,which basicallyfits a hyperspherearound the data.The paper presents the methods and some preliminaryexperimental results.1IntroductionIn almost all machine learning and pattern recognition research,it is assumed that a(training)dataset is available which reflects well what can be expected in practice.On this data a classifier or regressor should befitted such that good generalization over future instances will be achieved[1].Unfortunately,it is very hard to guarantee that the training data is a truly identically distributed sample from the real application.In the data gathering process certain events can easily be missed,because of their low probability of occurance,their measuring costs or because of changing environments.In order to detect these’unexpected’or’ill represented’objects in new,in-coming data,a classifier should befitted,which detects the objects that do not resemble the bulk of the training data in some sense.This is the goal of one-class classification[2,3],novelty detection[4],outlier detection[5]or concept learning [6].Here,one class of objects,the target class,has to be distinguished from all other possible objects,the outlier objects.2A common solution for outlier or novelty detection is tofit a probability density on the target data[7,5,8],and classify an object as outlier when the object falls into a region with density lower than some threshold value.This works well in the cases where the target data is sampled well.That means, the sample size is sufficient and the distribution is representative.But density estimation requires large sample sizes.When the boundary of the target class with limited sample size is to be estimated,it might be better to directlyfit the boundary instead of estimating the complete target density.This is Vapnik’s principle to avoid solving a more general problem than what is actually needed to solve[9].Using this principle,the problem is changed from density estimation to domain description.The support vector data description(SVDD,[2])is a method which tries to fit directly a boundary with minimal volume around the target data without performing density estimation.It is inspired by the(two-class)support vector classifier[9].All objects inside the hypersphere will be’accepted’and classified as target objects.All other objects are labeled outliers.By minimizing the volume of the hypersphere,it is hoped that the chance of accepting outliers is minimized. In[10]a linear one-class classifier is presented,based on the idea to separate the data with maximal margin from the origin.In[11]again a linear classifier was used,but here the problem was posed as a linear programming problem,instead of a quadratic progamming problem.In general,the hypersphere model is notflexible enough to give a tight description of the target class and analogous to the Support Vector Classifier (SVC),the SVDD is made moreflexible by transforming the objects from the input space representation to a representation in kernel space.It appears that not all kernels that were proposed for the SVC can be used by the SVDD.In most cases the data classes are elongated,which is useful for discrimination be-tween two classes,but is harmful for one-class classification.An exception is the Gaussian kernel,where good performances can be obtained.Unfortunately,even using the Gaussian kernel still an homogeneous input feature space is assumed,which means that distances in all directions in the space should be comparable.In practice,data is often distributed in subspaces, resulting in very small typical distances between objects in directions perpen-dicular to the subspace.Moving inside the subspace will change the objects just slightly,but moving out of the subspace will result in an illegal object,or an outlier.Although comparable distances are traveled,the class memberships of the objects differ drastically.This homogeneity of the distances does not just harm the SVDD,but in principle all one-class methods which rely on distances or similarities between the objects.In this paper we propose a rescaling of the data in the kernel feature space, which is robust against large scale differences in scaling of the input data.It rescales the data in a kernel space such that the variances of the data are equal in all directions.We will use the techniques of Kernel-PCA[12].In section2we will present the SVDD,followed by an example where it fails.In section3the rescaling of the data is presented,followed by some experiments and conclusions.3 2SVDDTo describe the domain of a dataset,we enclose the data by a hypersphere with minimum volume(minimizing the chance of accepting outlier objects).Assume we have a d-dimensional data set containing n data objects,X tr:{x i,i=1,..,n} and the hypersphere is described by center a and radius R.We will assume throughout the paper that a sum i will sum over all training objects,which means n i=1.To allow the possibility of outliers in the training set,the distance from x i to the center a need not be strictly smaller than R2,but larger distances should be penalized.An extra parameterνis introduced for the trade-offbetween the volume of the hypersphere and the errors.Thus,an error function L,containing the volume of the hypersphere and the distances,is minimized.The solution is constrained with the requirement that(almost)all data is within the hyper-sphere.The constraints can be incorporated in the error function by applying Lagrange multipliers[1].This yields the following function to maximize with respect toα(for details[2]):L= iαi(x i·x i)− i,jαiαj(x i·x j)with0≤αi≤14mapped to a new feature space.Ideally,this mapping would map the data into a spherical constrained domain,such that the assumptions for the SVDD are fulfilled.Several kernels have been proposed[9],mainly in the application of Support Vector Classifiers.A popular choice is the polynomial kernel(x·y)→K(x,y)= (x y+1)p,which maps the data to a feature space spanned by all monomial fea-tures up to p.For one-class classification this kernel works poorly,because it tends to transform the data into elongated,flat structures instead of spherical clusters.Especially for larger degrees p,taking the power will stress the differ-ences in the variances in different feature directions.For large p the direction with largest variance in input space will overwhelm all smaller variances in kernel space.For another popular kernel,the Gaussian kernel,this is not the case:(x·y)→K(x,y)=exp(− x−y 2/σ2).(4) The width parameterσin the kernel(from definition(4))determines the scale or resolution at which the data is considered in input space.Although here the data is implicitly mapped to an infinitely dimensional space F[13],the inner products(or the kernel outputs)are between0and1.Furthermore,K(x,x)=1 indicating that all objects have length1,placing the objects effectively on a hypersphere with radius1.For good performance of the SVDD with the Gaussian kernel,still properly scaled distances are required.The new inner product(4)now depends on distance x−y 2.Very inhomogeneous distances will still result in elongated clusters and large empty areas around the target class in input feature space that are still accepted.Fig.1.Decision boundary of an SVDD trained on an artificial2D dataset.Infigure1a scatterplot of an artificial2-dimensional dataset is show.The SVDD is trained tofit a boundary around it such that about25%of the target data is on the boundary.Although the SVDD follows the curve in the data,it does notfit tightly the subspace structure in the data.A large strip inside the5 curve is classified as target object,but does not contain target training objects. This is caused by the large scale difference of the data parallel and perpendicular to the subspace.In the approach of[10]a linear hyperplane instead of an hyperspherically shaped boundary is used.This plane should separate the target data with max-imal margin from the origin of the feature space.Although in input space this is incomparable with the hypersphere approach,the method can be’kernalized”and using the Gaussian kernel this method appears to be identical to the SVDD [2].3Kernel whiteningInstead of directlyfitting a hypersphere in the kernel space,we propose to rescale the data to have equal variance.Fitting a hypersphere in the rescaled space F will be identical tofitting an ellipsoid in the original kernel space.The rescaling is easily done,using the derivation of the Kernel PCA[12].The data is basically mapped onto the principal components(or the largest eigenvalues)of the data covariance matrix and then rescaled by the corresponding eigenvalues.Therefore the eigenvectors and eigenvalues of the covariance matrix in the kernel space have to be estimated.The eigenvectors with eigenvalues close or equal to zero will be disregarded.Assume the data X tr is mapped to the kernel space F by some(possibly non-linear)mappingΦ:R d→F.When we also assume that the data is centered in this space,i.e. iΦ(x i)=0,the covariance matrix C of the mapped dataset can be estimated by:1C=n j(Φ(x j)·v)Φ(x j)=λv.(6)Equation(6)shows that the eigenvectors with non-zero eigenvalue must be in the span of the mapped data{Φ(x i)},which means that v can be expanded as:v= iαiΦ(x i).(7) Multiplying Equation(6)from the left withΦ(x k)and using(7)gives:16When again the kernel matrix K ij=Φ(x i)·Φ(x j)is introduced,it appears that the coefficientsαfrom Equation(7)can directly be obtained by solving the eigenvalue problem:λα=Kα.(9) For normal kernel-PCA the eigenvectors should be normalized to unit length, and this means that for each eigenvector v k theαk are rescaled to:λk αk·αk =1.(10) We assumed that the data is centered in F.This can be done by transforming the original kernel matrix.Assume K is the n×n kernel matrix of the training data and K tst the m×n matrix of some new data(or possibly the same training data).The centered kernel matrix is computed by:˜K=K tst−1∗nK−K tst1n+1∗n K1n(11)where1n is an n×n matrix and1∗n is an m×n matrix both with all entries 1/n[12].We will assume that we always have centered the kernel matrices using (11).When the coefficientsαare obtained,a new object z can be mapped onto eigenvector v k in F by:(ˆz)k=(v k·Φ(z))= iαk i(Φ(x i)·Φ(z))= iαk i K(x i,x)(12)where(ˆz)k means the k-th component of vectorˆz.To transform the data into a representation with equal variance in each fea-ture direction(for directions withλk>0)the normalization from Equation(10) has to be slightly adapted.The variance of the mapped data along component v k is:var(X tr)=1n jiαk i k(x i,x j) 2=1and large amounts of data should be available to follow both the large sinusoidal structure and be tight around the subspace.The SVDD are optimized to have about30%error on the target set.The decision boundary are given by the white line.It is clear that it does not model the subspace structure in the data.4Characteristics whiteningHow efficient the mapping of the data to the new representation with unit vari-ance is,depends on the choice of the kernel and parameters.When this feature extraction captures the data structure,it is easy to train a one-class classifier on this data and obtain good classification performance.In table1decision bound-aries for the artificial data for different choices of the kernels are shown.The left column shows the results for the polynomial kernel of degree d=1,d=2to d=3(from top to bottom).The left column shows the results for the Gaussian kernel,forσ=5,15and50.Results show large dependence on the choice of the free parameter.The rescaling tend to overfit for high values of the degree d and low values ofσ.Visually it can be judged that for the polynomial kernel d=3is reasonable,for the Gaussian kernel aσbetween15and50can be used. Applying an ill-fitting kernel results in spurious areas in the input space.Many one-class classifiers rely on the distances between the objects in the input space.When the data is whitened in the kernel space,and all significant eigenvectors are taken into account,the influence of rescaling(one of the)features is eliminated.In table2the results of rescaling one of the features is shown.In the middle row a scatterplot of the original data is shown.On this dataset an SVDD,an SVDD on the whitened data with all non-zero principal components, and an SVDD using just thefirst5principal components are trained.It appears that for this data there are just8non-zero principal components.In the upper row of the table,the horizontal feature was rescaled to10%of the original size,while on the lower row the data the feature was10times enlarged. The SVDD on the(kernel-)whitened data not only gives a tight description,8d=5d=15d=50Table1.The influence of the choice of the kernel.The left column shows the results using the polynomial kernel with varying degrees,the right column the Gaussian kernel with varyingσ.but is also robust against rescaling the single feature.The SVDD in input space heavily suffers from rescaling the ing just a few principal components from the mapped data also results in poorer results and in spurious areas.The fact that the data is unit variance with uncorrelated features makes the normal distribution a good choice for describing the dataset in the kernel space. Infigure3again the sinusoidal data set is shown,now with one prominent outlier present.Furthermore,typical decision boundaries of thefitted normal distribu-tion(left)and the support vector data description(right)are shown.In most cases the difference in decision boundary between the SVDD and the Gaussian model are minor.In case the training data contains some significant outliers, The SVDD tends to be obtain tighter descriptions,because it can effectively ignore prominent outliers in the data.The normal distribution is still influenced by it,and starts to accept superfluous areas in feature space.This is also visible infigure3.In both cases the decision boundary was optimized such that10%of the training data is rejected.90.11×10Table2.Influence of the scaling of the features.The left column shows the decision boundary of the SVDD,the middle column the results of the data description using the whitening with all non-zero variance directions and the right column shows the output using thefive principal components.The middle row shows the original data.In the upper row the horizontal feature is10times shrinked,the lower the horizontal feature is 10times enhanced.For display purposes the data is scaled to show comparable scales.5ExperimentsTo show the results on real world datasets,we use the standard Concordia dataset[14],in which the digits are stored in32×32black-and-white images.Each of the digit classes can be designated to be the target class.Then all other digits are considered outliers.For training400objects per class,and for testing 200objects per class are available.Infigure4typical images of rejected objects are shown.The one-class clas-sifier was trained on class’2’and’3’respectively.The32×32images arefirst preprocessed to retain80%of the variance,to remove all pixels with(almost) zero variance over the whole dataset.Then the data was(kernel-)whitened using10Fig.3.Typical decision boundaries of the normal distribution(left)and the support vector data description(right),trained on the normalized data in F.The SVDD tends to be tighter,especially when some outliers are present in the training data.Fig.4.Examples of rejected handwritten digits from the Concordia dataset.An SVDD trained on class2and3,kernel whitened using a polynomial kernel with d=2.a polynomial kernel,degree2.Thefirst20principal components were chosen, the eigenvalues of the other principal components always were a factor10−6 or more smaller than the largest eigenvalue.On this data a normal SVDD was fitted,such that about5%of the target data is rejected.The results show that rejected objects are often skewed or are written very fatly,or contain big curls.Infigure5the results are shown to compare the outliers obtained by using normal PCA and the kernel whitening,using the polynomial kernel with degree 3.In the normal PCA12objects are rejected.Some of them look reasonable by human interpretation.In the kernel whitening processing,10objects are rejected. Some of the objects are rejected in both methods,for instance the upper left object in PCA and the second object in the kernel whitening.Other objects are specifically rejected because the do notfit the particular model,for instance the lower right object in both the PCA and kernel whitening.Infigure6results on all Concordia digit classes are shown.On each of the digit classes one-class classifiers are trained and the ROC curve is computed.11 Fig.5.An SVDD trained on digit class’4’.On the left the data was preprocessed using normal PCA,on the right kernel whitening with polynomial d=3is used.Fig.6.AUC errors on the10classes of the Concordia handwritten digits.Left shows the AUC error on all10classes for a simple Gaussian density,a Mixture of Gaussians (k=5),SVDD,whitening with polynomial degree1,2and3.The ROC gives the error on the outlier data given varying values for the error on the target class[15].From the ROC curves a error is derived,called the Area Under the ROC curve(AUC).Low values of the AUC indicates a good separation between the target and outlier data.On each of the classes6one-class classifiers have been trained.Thefirst two methods are density models:the Normal Density and the Mixture of Gaussians (with5clusters).The third is the basic SVDD directly trained in the input space,optimized such that about10%of the target class is rejected.In the last three classifiers the data is mapped using the kernel whitening(polynomial kernel,d=1,2and3).Again thefirst20principal components were considered, retaining about75%of the variance.In the left subplot,the data is not preprocessed.The density methods are not capable in estimating the density and give the highest AUC error of0.5.In most12cases the best performances is obtained by applying the whitening procedure with d=2.The SVDD can perform poorly,due to the relative low sample size and the complexity of following the boundary in the high dimensional feature space.Whitening with higher polynomial degrees also suffers from low sample size effects.In the right subplot,the data is preprocessed by basic to retain again80%of the variance.By the reduction of the dimensionality,in some cases some overlap between the classes is introduced and the performance of the best whitening procedures deteriorate.The density methods now work well and often outper-form the poorer whitening versions.The actual performance increase or decrease is mainly determined by how well the modelfits the data.That means for the whitening procedure that good performance is obtained when the data is dis-tributed in some(nonlinear)subspace.6ConclusionsThis paper presents a simple whitening preprocessing for one-class classification problems.It uses the idea of Kernel PCA to extract the non-linear principal fea-tures of the dataset.After mapping the data to this new feature space(implicitly defined by the kernel function),feature directions with(almost)zero variance are removed and the other features are rescaled to unit variance.By the Kernel PCA and rescaling,the resulting data is zero mean with an identity covariance matrix.Finally,this data can now in principle be described by any one-class classifier.By this preprocessing step one-class classifiers can be trained which contain large differences in scale in the input space.In particular,data in(non-linear) subspaces can be described well.For most one-class classifiers data distributed in subspaces are problematic,because the data contains large differences in typical scale within the subspace and perpendicular to the subspace.By using a suitable kernel in the kernel PCA,these scale differences in the data are recognized and modeled in the mapping.The transformed data now has equal variance in each feature direction.This subspace modeling comes at a price though.The mapping requires a rea-sonable sample size,in order to extract the more complex non-linear subspaces. Using too complex mappings and too many principal components in combina-tion with small sample sizes will result in overfitting on the data and in poor results on independent test data.A drawback of this rescaling on the Kernel PCA basis is that the expansion in(13)is in general not sparse.This means that for each projection of a test point onto a principal direction,all training objects have to be taken into account.For large training sets this can become very expensive.Fortunately,approximations can be made,which reduce the number of objects in the expansion(7)drastically [10].Finally,the problem how to choose the kernel function and values for the hyperparameters is still open.When test data is available,both from the target13as the outlier class,this can be used for evaluation of the model(which then includes both the whitening and the classifier in the kernel space).In the general case of one-class classification,we have just a very poorly represented outlier class,and estimating the performance on this dataset will give a bad indication of the expected performance.In these cases we have to rely on,for instance, artificially generated outlier data.7AcknowledgementsThis research was supported through a European Community Marie Curie Fel-lowship.The author is solely responsible for information communicated and the European Commission is not responsible for any views or results expressed. References1.Bishop,C.:Neural Networks for Pattern Recognition.Oxford University Press,Walton Street,Oxford OX26DP(1995)2.Tax,D.:One-class classification.PhD thesis,Delft University of Technology,http://www.ph.tn.tudelft.nl/˜davidt/thesis.pdf(2001)3.Moya,M.,Hush,D.:Network contraints and multi-objective optimization for one-class classification.Neural Networks9(1996)463–4744.Ritter,G.,Gallegos,M.:Outliers in statistical pattern recognition and an appli-cation to automatic chromosome classification.Pattern Recognition Letters18 (1997)525–5395.Bishop,C.:Novelty detection and neural network validation.IEE Proceedingson Vision,Image and Signal Processing.Special Issue on Applications of Neural Networks141(1994)217–2226.Japkowicz,N.,Myers,C.,Gluck,M.:A novelty detection approach to classifica-tion.In:Proceedings of the Fourteenth International Joint Conference on Artificial Intelligence.(1995)518–5237.Tarassenko,L.,Hayton,P.,Brady,M.:Novelty detection for the identification ofmasses in mammograms.In:Proc.of the Fourth International IEE Conference on Artificial Neural Networks.Volume409.(1995)442–4478.Surace,C.,Worden,K.,Tomlinson,G.:A novelty detection approach to diagnosedamage in a cracked beam.In:Proceedings of SPIE.(1997)947–9439.Vapnik,V.:Statistical Learning Theory.Wiley(1998)10.Sch¨o lkopf,B.,Williamson,R.,Smola,A.,Shawe-Taylor,J.:SV estimation of adistribution’s support.In:Advances in Neural Information Processing Systems.(1999)11.Campbell,C.,Bennett,K.P.:A linear programming approach to novelty detection.In:NIPS.(2000)395–40112.Scholkopf,B.,Smola,A.J.,M¨u ller,K.R.:Nonlinear component analysis as a kerneleigenvalue problem.Neural Computation10(1998)1299–131913.Smola,A.:Learning with kernels.PhD thesis,Technischen University Berlin(1998)14.Cho,S.B.:Recognition of unconstrained handwritten numerals by doubly self-organizing neural network.In:International Cconference on Pattern Recognition.(1996)15.Metz,C.:Basic principles of ROC analysis.Seminars in Nuclear Medicine VIII(1978)。
