CCIEASA实验手册
CCNA实验手册

如图 2 所示为 10Base-T 网 RJ-45 端口,而图 3 所示的为 10/100Base-TX 网 RJ-45 端口。其实 这两种 RJ-45 端口仅就端口本身而言是完全一样的,但端口中对应的网络电路结构是不同的, 所以也不能随便接。
(3)SC 端口 SC 端口也就是我们常说的光纤端口,它是用于与光纤的连接。光纤端口通常是不直接用
(2)AUX 端口 AUX 端口为异步端口,主要用于远程配置,也可用于拔号连接,还可通过收发器 与
(3)高速同步串口 在路由器的广域网连接中,应用最多的端口还要算“高速同步串口”(SERIAL)了,如图 7
所示。
这种端口主要是用于连接目前应用非常广泛的 DDN、帧中继(Frame Relay)、X.25、PSTN(模 拟电话线路)等网络连接模式。在企业网之间有时也通过 DDN 或 X.25 等广域网连接技术进 行专线连接。这种同步端口一般要求速率非常高,因为一般来说通过这种端口所连接的网络 的两端都要求实时同步。 (4)异步串口
第 3 页 共 70 页 鸿鹄论坛:/
(5)ISDN BRI 端口 因 ISDN 这种互联网接入方式连接速度上有它独特的一面还得到了充分的应用。ISDN BRI 端口用于 ISDN 线路通过路由器实现 与 Internet 或其他远程网络的连接,可实现 128Kbps 的通信速率。ISDN 有两种速率连接端口, 一种是 ISDN BRI(基本速率接口);另一种是 ISDN PRI(基群速率接口)。ISDN BRI 端口是 采用 RJ-45 标准,与 ISDN NT1 的连接使用 RJ-45-to-RJ-45 直通线。如图 9 所示的 BRI 为 ISDN BRI 端口。
Cisco CCIE ASA实验手册

思科asa系列常规操作cli配置指南-软件版本9.4说明书

思科系统公司思科在全球设有 200 多个办事处。
有关地址、电话号码和传真号码信息, 可查阅思科网站:/go/offices 。
思科 ASA 系列常规操作 CLI 配置指南软件版本 9.4适用于 ASA 5506-X 、ASA 5506H-X 、ASA 5506W-X 、ASA 5508-X 、ASA 5512-X 、ASA 5515-X 、ASA 5516-X 、ASA 5525-X 、ASA 5545-X 、ASA 5555-X 、ASA 5585-X 、ASA 服务模块和自适应安全虚拟设备首次发行日期:2015 年 3 月 23 日最后更新日期:2015 年 4 月 7 日文本部件号: 不适用,仅在线提供本手册中有关产品的规格和信息如有更改,恕不另行通知。
本手册中的所有声明、信息和建议均准确可靠,但我们不为其提供任何明示或暗示的担保。
用户必须承担使用产品的全部责任。
随附产品的软件许可和有限担保在随产品一起提供的信息包中提供,且构成本文的一部分。
如果您无法找到软件许可或有限担保,请与思科代表联系以获取副本。
思科所采用的 TCP 信压缩是加州大学伯克莱分校 (UCB) 开发的一个程序的改版,是 UCB 的 UNIX 操作系统公共域版本的一部分。
保留所有权利。
版权所有 © 1981,加州大学董事会。
无论在该手册中是否作出了其他担保,来自这些供应商的所有文档文件和软件都按“原样”提供且仍有可能存在缺陷。
思科和上述供应商不承诺所有明示或暗示的担保,包括(但不限于)对特定用途的适销性、适用性、非侵权性以及因交易、使用或商业惯例所衍生的担保。
在任何情况下,对于任何间接、特殊、连带发生或偶发的损坏,包括(但不限于)因使用或无法使用本手册而导致的任何利润损失或数据损失或损坏,思科及其供应商概不负责,即使思科及其供应商已获知此类损坏的可能性也不例外。
思科和思科徽标是思科和/或其附属公司在美国和其他国家/地区的商标或注册商标。
ASA Lab Guide

思科Adaptive Security Appliance 产品动手培训实验指南思科系统(中国)网络技术有限公司2007年第一部分: 防火墙配置实验 (3)Exercise 1: Getting Start with Network Access (3)Lab environment (3)1.1 PC1, PC2 DNS Configuration .............................................................. 错误!未定义书签。
1.2 Reset ASA configuration to default (5)1.3 Enter Minimum Configuration to start ASDM (5)1.4 Enable ASDM Logging (9)1.5 Exploring ASDM (10)1.6 ASA对外的基本访问配置 (11)1.7 Review (13)Exercise 2 –配置安全控制策略 (14)2.1. ASA安全策略的基本配置 (14)2.2. 允许Ping数据包通过ASA (15)2.3. 配置企业私有DNS服务器工作环境 (15)2.4. 确认Yahoo messenger的状态 ........................................................... 错误!未定义书签。
2.5. 检查邮件系统工作状态 (16)2.6. 开放DMZ区域的WWW服务器对外进行服务 (17)2.7 Save the configuration (18)Exercise 3: 配置针对各类应用的检查功能 (Application Inspections) (19)Overview (19)3.1. 屏蔽Instant Messengers (19)3.2 Time Based Policy (22)3.3 : Rate Limiting (23)3.4 FTP Application Control (25)第二部分: ASA Security Service Module (IPS) (26)Overview (26)Exercise 4 : Getting Start with IPS SSM (26)4.1 Restore IPS configuration to default (27)4.2 Explore SSM-IPS CLI (30)4.3 CONFIGURE IPS (31)Exercise 5 : Stop RFC1918 Spoofing attack (33)Exercise 6 : Stop Attack with Meta Event Creation (36)Exercise 7: Basic IPS Tuning (39)7.1 Risk Rating (39)7.2 Event Filter (41)第三部分: WEB VPN的配置实验 (42)Exercise 8: Configuring the ASA for WebVPN (42)8.1 : Enabling WebVPN on the ASA Outside Interface (42)Exercise 9: Creating WebVPN Group Policy (45)Exercise 10: Creating WebVPN Users (49)Exercise 11: Configuring Web Access Function (52)11.1: Preparing the Web Server for WebVPN Access Function (52)11.2: Configuring the ASA for WebVPN Web Access (53)11.3: Preparing the Client PC for WebVPN Web Access (56)11.4: Testing the WebVPN Web Access Function (58)Exercise 14: Configuring Port Forwarding Function ...................................... 错误!未定义书签。
ASA基本配置与实验环境搭建

扩展ACL:asa802(config)#access-list acl-name extended {permit | deny} protocol src-ip-add src-mask dst-ip-add dst-mask [operator port]
NETSCREEN防火墙:通过对外网端口MIP和访问策略(set policy)来实现外网对内网及DMZ专项服务的访问限制。
ASA防火墙: 通过静态映射(static
(inside,outside))和策略(access-list)来实现外网对内网及DMZ专项服务的访问限制。
3、
内网地址转换
Telnet或SSH密码:
asa802(config)#passwd cisco
ASA接口名字和安全级别
asa802(config-if)#nameif inside(不起名,ping不通)
asa802(config-if)#security-level 100(取值0—100 ,值越大,安全级越高)
5、
路由的实现
PIX防火墙:通过route outside 、route inside来实现内外网的访问路由。
NETSCREEN防火墙:通过set route来实现内外网的访问路由。
ASA防火墙:通过route outside 、route inside来实现内外网的访问路由。
6、
管理地址的定义
定义一个全局地址池:
asa802(config)#global (outside) 1 200.1.1.100-200.0.0.110
ASA实验一
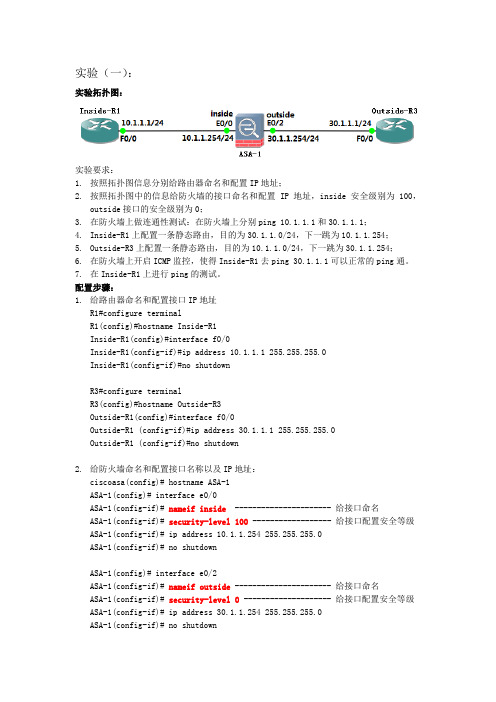
实验(一):实验拓扑图:实验要求:1.按照拓扑图信息分别给路由器命名和配置IP地址;2.按照拓扑图中的信息给防火墙的接口命名和配置IP地址,inside安全级别为100,outside接口的安全级别为0;3.在防火墙上做连通性测试:在防火墙上分别ping 10.1.1.1和30.1.1.1;4.Inside-R1上配置一条静态路由,目的为30.1.1.0/24,下一跳为10.1.1.254;5.Outside-R3上配置一条静态路由,目的为10.1.1.0/24,下一跳为30.1.1.254;6.在防火墙上开启ICMP监控,使得Inside-R1去ping 30.1.1.1可以正常的ping通。
7.在Inside-R1上进行ping的测试。
配置步骤:1.给路由器命名和配置接口IP地址R1#configure terminalR1(config)#hostname Inside-R1Inside-R1(config)#interface f0/0Inside-R1(config-if)#ip address 10.1.1.1 255.255.255.0Inside-R1(config-if)#no shutdownR3#configure terminalR3(config)#hostname Outside-R3Outside-R1(config)#interface f0/0Outside-R1 (config-if)#ip address 30.1.1.1 255.255.255.0Outside-R1 (config-if)#no shutdown2.给防火墙命名和配置接口名称以及IP地址:ciscoasa(config)# hostname ASA-1ASA-1(config)# interface e0/0ASA-1(config-if)# nameif inside ---------------------- 给接口命名ASA-1(config-if)# security-level 100 ------------------ 给接口配置安全等级ASA-1(config-if)# ip address 10.1.1.254 255.255.255.0ASA-1(config-if)# no shutdownASA-1(config)# interface e0/2ASA-1(config-if)# nameif outside ---------------------- 给接口命名ASA-1(config-if)# security-level 0 -------------------- 给接口配置安全等级ASA-1(config-if)# ip address 30.1.1.254 255.255.255.0ASA-1(config-if)# no shutdown3.在ASA-1上做连通性测试:ASA-1# ping 10.1.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 10.1.1.1, timeout is 2 seconds: !!!!!Success rate is 100 percent (5/5)ASA-1# ping 30.1.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 30.1.1.1, timeout is 2 seconds: !!!!!Success rate is 100 percent (5/5)4.在Inside-R1上配置去往30.1.1.0/24网段的静态路由:Inside-R1(config)#ip route 30.1.1.0 255.255.255.0 10.1.1.2545.在Outside-R3上配置去往10.1.1.0/24网段的静态路由:Outside-R3(config)#ip route 10.1.1.0 255.255.255.0 30.1.1.2546.在防火墙的全局策略里面添加ICMP的监控策略:ASA-1(config)# policy-map global_policyASA-1(config-pmap)# class inspection_defaultASA-1(config-pmap-c)# inspect icmp7.在Inside-R1上进行测试:Inside-R1#ping 30.1.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 30.1.1.1, timeout is 2 seconds: !!!!!Success rate is 100 percent (5/5)。
实验10-思科ASA防火墙的NAT配置

实验10 思科ASA防火墙的NAT配置一、实验目标1、掌握思科ASA防火墙的NAT规则的基本原理;2、掌握常见的思科ASA防火墙的NAT规则的配置方法。
二、实验拓扑根据下图搭建拓扑通过配置ASA防火墙上的NAT规则,使得inside区能单向访问DMZ区和outside区,DMZ区和outside区能够互访。
三、实验配置1、路由器基本网络配置,配置IP地址和默认网关R1#conf tR1(config)#int f0/0R1(config-if)#ip address 192.168.2.1 255.255.255.0R1(config-if)#no shutdownR1(config-if)#exitR1(config)#ip default-gateway 192.168.2.254 //配置默认网关R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.2.254 //添加默认路由R1(config)#exitR1#writeR2#conf tR2(config)#int f0/0R2(config-if)#ip address 202.1.1.1 255.255.255.0R2(config-if)#no shutdownR2(config-if)#exitR2(config)#ip default-gateway 202.1.1.254R2(config)#exitR2#writeServer#conf tServer(config)#no ip routing //用路由器模拟服务器,关闭路由功能Server(config)#int f0/0Server(config-if)#ip address 192.168.1.1 255.255.255.0Server(config-if)#no shutdownServer(config-if)#exitServer(config)#ip default-gateway 192.168.1.254Server(config)#exitServer#write*说明:实际配置中最好在三台路由器上都添加一条通往防火墙的默认路由,但在本实验中Server和R2不配置不影响实验效果。
实验2ASA防火墙配置.

国家高等职业教育网络技术专业教学资源库PIX防火墙PIX防火墙安全典型案例实验二ASA防火墙配置实验二ASA防火墙配置一、实验目的通过该实验了解ASA防火墙的软硬件组成结构,掌握ASA防火墙的工作模式,熟悉ASA 防火墙的基本指令,掌握ASA防火墙的动态、静态地址映射技术,掌握ASA防火墙的访问控制列表配置,熟悉ASA防火墙在小型局域网中的应用。
二、实验任务●观察ASA防火墙的硬件结构,掌握硬件连线方法●查看ASA防火墙的软件信息,掌握软件的配置模式●了解ASA防火墙的基本指令,实现内网主机访问外网主机,外网访问DMZ区三、实验设备ASA5505防火墙一台,CISCO 2950交换机两台,控制线一根,网络连接线若干,PC机若干四、实验拓扑图及内容详细配置:内网R6:R1>enR1#R1#conf tEnter configuration commands, one per line. End with CNTL/Z.R1(config)#int f0/0R1(config-if)#ip add 10.1.1.2 255.255.255.0R1(config-if)#no shutR1(config-if)#*Mar 1 00:01:32.115: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up *Mar 1 00:01:33.115: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to upR1(config-if)#exitR1(config)#ip route 0.0.0.0 0.0.0.0 10.1.1.3R1(config)#exitR1#DMZ区R3:R2>enR2#conf tEnter configuration commands, one per line. End with CNTL/Z.R2(config)#int f0/0R2(config-if)#ip add 20.1.1.2 255.255.255.0R2(config-if)#no shutR2(config-if)#*Mar 1 00:01:28.895: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up *Mar 1 00:01:29.895: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to upR2(config-if)#exitR2(config)#ip route 0.0.0.0 0.0.0.0 20.1.1.3R2(config)#exitR2#*Mar 1 00:03:11.227: %SYS-5-CONFIG_I: Configured from console by consoleR2#外网R4:R4#conf tEnter configuration commands, one per line. End with CNTL/Z.R4(config)#int f0/0R4(config-if)#ip add 192.168.1.2 255.255.255.0R4(config-if)#no shutR4(config-if)#*Mar 1 00:00:45.559: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up *Mar 1 00:00:46.559: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to upR4(config-if)#exitR4(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.3R4(config)#exitR4#PIX防火墙上的配置:pixfirewall# conf tpixfirewall(config)# hostname pixpix(config)# int e0pix(config-if)# ip add 10.1.1.3 255.255.255.0pix(config-if)# nameif insideINFO: Security level for "inside" set to 100 by default.pix(config-if)# no shutpix(config-if)# int e1pix(config-if)# nameif outsideINFO: Security level for "outside" set to 0 by default.pix(config-if)# ip add 192.168.1.3 255.255.255.0pix(config-if)# no shutpix(config-if)# int e2pix(config-if)# nameif dmzINFO: Security level for "dmz" set to 0 by default.pix(config-if)# secpix(config-if)# security-level 50pix(config-if)# ip add 20.1.1.3 255.255.255.0pix(config-if)# no shutpix(config-if)# nat (inside) 11 10.1.1.0 255.255.255.0pix(config)# nat (inside) 11 10.1.1.0 255.255.255.0Duplicate NAT entrypix(config)# global (outside) 11 20.1.1.74 netmask 255.255.255.255INFO: Global 20.1.1.74 will be Port Address Translatedpix(config)# access-list 100 permit icmp any anypix(config)# access-grpix(config)# access-group 100 in interface outsidepix(config)# static (dmz,outside) 192.168.1.5 20.1.1.5 netmask 255.255.255.255 pix(config)# access-group 100 in interface dmzpix(config)#五、实验结果内网PING外网:外网PING DMZ:外网PING内网:总结:比起上次试验,这次是多添加了一个DMZ区,在DMZ和outside之间配置static命令。
ccna实验手册

东莞斯瑞教育中心CCNA实验手册V5.0CCNA实验手册实验一基础实验一、拓扑图如下:二、实验目的1、掌握CISCO设备的基础配置。
2、2台设备能够ping 通。
3、熟练使用各种show命令查看设备状态。
三、实验要求:假设公司架设了一条东莞到香港的专线,作为网络管理员的你需要完成设备的基本配置,两台设备要PING通。
四、实验步骤:1、按照拓扑图所示,搭建实验平台2、完成CISCO设备的基础配置➢基本配置包括。
➢设置主机名称和设备标识。
➢关闭设备的DNS查询功能。
➢开启光标跟随功能。
➢设置超时时间,要求HongKong超时时间是10分30秒,DongGuan永远不超时。
➢配置控制台密码,配置VTY密码,配置特权密码,启用密码加密服务。
➢完成基本和辅助配置之后,按照拓扑图配置好设备的IP地址,测试相邻设备之间能否ping通。
➢使用CDP协议查看邻居设备信息,可以对设备进行远程telnet。
➢保存配置文件后,备份IOS软件和配置文件。
3、配置如下:设备命名:Router(config)#hostname dongguanDongguan(config)#关闭DNS查询:Router(config)#no ip domain-lookup注释:IOS软件会把未知的命令当做网络上设备的主机名称,通过广播去查找这台设备,这个过程需要比较久的时间,用这个命令可以避免DNS查询过程,节省时间。
启用光标跟随:Router(config)#line console 0Router(config-line)#logging synchronous注释:IOS软件会对系统状态变化自动的跳出提示信息,这会打乱我们的命令输入会影响我们命令的输入,启动光标跟随可以解决这个问题。
设置超时时间Router(config)#line console 0Router(config-line)#exec-timeout 0(分) 0 (秒)『永不超时』注释:当我们一段时间没有对设备进行操作后,会自动跳出登录,好比windows系统在多长时间没有活动后自动锁定,需要我们重新登录。
实验一 ASA的基本设置

实验1:ASA的基本设置
1.实验目的:
1. 掌握手工对ASA防火墙进行初始配置的步骤和方法
2.实验要点:
1. 通过运行vmware中,利用超级终端软件对ASA防火墙进行手工初始配置。
3.实验设备:
1. vmware工具
2. 虚拟ASA防火墙一台
4.实验环境
5.实验步骤:
1启动vmware中的ASA1.4。
2启动piped。
3启动putty。
连接成功后显示如下界面
在这里面输入yes后然后回车。
接下来要配置日期时间,IP地址,子网掩码。
Host name处填写你自己的学号,比如你的学号为123456789001,就填写123456789001。
Domain name处随意填写即可
注意最下面的要输入yes后,单击回车键
当前进入的是用户模式
进入特权模式
进入全局配置模式
命令输入
练习35页2.3.1 命令输入的内容
最后修改防火墙的名称,命令为:
Ciscoasa(config)#hostname 123456789001(此处填写你自己的学号,比如你的学号为123456789001,就填写123456789001。
)如下图
将这个界面截图填入到实验报告中。
CCNA 实验室操作指南

CCNA实验室操作指南Version交大绍天CCIE实验室2004.10心得:1.实验手册有两个作用:一是认识和了解实验设备,二是熟悉配置和排错过程;所以实验手册重点要在介绍实验设备和实验配置和排错方面;第一章 认识CISCO 路由器本章主题z 路由器z 内存体系z 启动路由器1.1 认识CISCO 路由器路由器是一种连接多个网络或网段的网络设备,它能将不同网络或网段之间的数据信息进行“翻译”,以使它们能够相互“读”懂对方的数据,从而构成一个更大的网络。
路由器有两大典型功能,即数据通道功能和控制功能。
数据通道功能包括转发决定、背板转发以及输出链路调度等,一般由特定的硬件来完成;控制功能一般用软件来实现,包括与相邻路由器之间的信息交换、系统配置、系统管理等。
现在CISCO 的路由器分为三个等级,十多个系列:1)低端接入路由器,包括CISCO2600,3600,3700系列;2)终端模块化访问路由器,包括CISCO7200,7600系列;3)高端电信级核心路由器,包括CISCO10000,12000GSR 系列;CISCO 最近发布了下一代IP 路由器,包括低端的CISCO2800,3800系列,高端的ISR 系列。
1.2 2600系列路由器的界面1.2 内存体系z ROM 相当于PC 机的BIOSz FLASH 相当于PC 机硬盘,包含IOSz DRAM 动态内存z NVRAM 配置文件1.3 启动路由器(初始配置)打开路由器电源时,它首先需要测试它的硬件,包括内存和接口。
下一步就是查找和Console 口电源接口Ethernet0模块槽加载I O S映像,即路由器操作系统。
最后,在路由器可以在网络中正常工作之前,它需要找到它的配置信息,并使用它。
如果在打开电源的时候位于路由器控制台,则可以看见类似下面的信息:此时,路由器已经从R O M中加载了引导程序。
下一步,它将从闪存中加载它的I O S 映像。
CCIE实验手册

CCIE R&S v4.0 实验当前位置: 首页→CCIE资料库→CCIE R&S v4.0 实验→CCIE LAB K1CCIE LAB K1目录K1 拓朴VTPVLAN2层接口Frame relayStorm contrlTrunkOSPFEIGRPRIP V2IPv6BGPMulticastSecure HTTPPPP CHAP 认证Class-Base FRTSAuto QOSGLBPNTPDHCPNetflowEEMTFTPK1 拓朴实验拓朴图:设备串口连接拓朴图:注:★本文档所有配置基于2号机架,所以Y取值为2。
★所有设备loopback0 地址为 Y.Y.X.X/32,分别为:R1:2.2.1.1/32R2:2.2.2.2/32R3:2.2.3.3/32R4:2.2.4.4/32R5:2.2.5.5/32SW1:2.2.7.7/32SW2:2.2.8.8/32SW3:2.2.9.9/32SW4:2.2.10.10/32★BackBone地址分别为:BB1:150.1.2.254/24BB2:150.2.2.254/24BB3:150.3.2.254/24★其中,G与F相等,0/0与0/0/0相等。
返回目录VTP4台交换机上全部配置VTP域名为:CCIERoutingandSwitching,密码为:cisco,模式为透明模式。
配置:说明:此题配置共分为1步。
1.在4台交换机上配置VTP:说明:共分1小步。
(1)在4台交换机上同时做如下配置:vtp domain CCIERoutingandSwitchingvtp password ciscovtp mode transparen返回目录VLAN交换机上的VLAN信息如下:配置:说明:此题配置共分为1步。
1.在4台交换机上配置VLAN:说明:共分1小步。
(1)在4台交换机上同时做如下配置:VLAN 15name VLAN_BB1 exitVLAN 2name VLAN_BB2 exitVLAN 3name VLAN_BB3 exitVLAN 11name VLAN_A exitVLAN 13name VLAN_B exitVLAN 22name VLAN_C exitVLAN 24name VLAN_H exitVLAN 44name VLAN_FexitVLAN 45name VLAN_Gexit返回目录2层接口原题:Implement the access-switch ports of switched networkConfigure all of the appropriate nontrunking access switch ports onsw1,sw2,sw3,according to the following requirements:Configure the VLANS for the access switch ports show as the vlan tables,include the ports to BB1,BB2 and BB3.Configure trunk between SW2 F0/2 and R2 G0/1.Make sure that the spanning tree enters the forwarding state immediately.Only for these access switch ports,bypassing the listening and learning states.Avoid transmitting bridge protocol date units(BPDUS)on these access switch ports.If a BPDU is received on any of these ports,the ports should transition back to the listening,learning and forward states.Add any special layer 2 commands that are required on the routers including trunk configuration.中文注释:1.在SW1,SW2,SW3上将所有相关的access接口全部划入图表中相应的VLAN,其中包括连接BB1,BB2和BB3的接口。
Cisco ASA硬件防火墙

Cisco ASA硬件防火墙实验【实验目的】ASA防火墙的基本配置和高级的URL过滤等【实验拓扑】【实验步骤】一、Cisco ASA防火墙的基本配置:1、配置主机名、域名、密码EnableConf tHostname ASA5520 配置主机名为ASA5520Domaln-name 配置域名为Enable password ASA5520 配置特权密码Password cisco 配置远程登录密码2、配置接口Conf tInterface e0/0Nameif inside 配置接口的名字为insideSecurity-level 100 配置接口的安全级别为100Ip address 192.168.0.1 255.255.255.0 配置接口IP地址No shutdown 开启端口ExitInterface e0/1Nameif outside 配置接口的名字为outsideSecurity-level 0 配置接口的安全级别为0Ip address 202.140.11.2 255.255.255.0 配置接口IP地址No shutdown 开启端口ExitInterface e0/0Nameif DMZ 配置接口的名字为DMZSecurity-level 50 配置接口的安全级别为50Ip address 192.168.1.1 255.255.255.0 配置接口IP地址No shutdown 开启端口Exit3、配置路由Conf tRoute outside 0.0.0.0 0.0.0.0 202.140.11.1 配置缺省路由是任意到达出口的地址的下一条是202.140.11.1(因为防火墙有可能不是直接W AN所以要设置默认路由)4、配置远程管理接入配置telnet接入Conf ttelnet 192.168.0.0 255.255.255.0 inside 配置telnet管理接入地址为inside的192.168.0.0/24这个网段的地址telnet 192.168.0.3 255.255.255.255 inside 也可以配置只允许一台主机的接入telnet timeout 30 配置telnet超时为30分钟配置ssh接入Conf tCrypto key generate rsa modulus 1024 生成RSA密钥对Ssh 192.168.0.0 255.255.255.0 inside 配置ssh接入地址为inside的192.168.0.0/24这个网段的地址Ssh 0 0 outside 配置ssh接入地址为outside的任意网段的地址Ssh timeout 30 配置超时为30分钟Ssh version 2 配置版本号为2配置ASDM(自适应安全设备管理器)接入Conf tHttp server enable 65123 打开防火墙HTTPS服务功能http 0 0 outside 配置防火墙允许HTTPS接入的地址为任意asdm image disk0:/asdmfile 指定ASDM映像位置username zhangsan password zhangsan privilege 15 配置客户端登录使用的用户名和密码为zhangsan特权为最高的15级5、为出站流量配置网络地址转换Conf tNat control 启用NAT功能Nat (inside) 1 0 0 指定需要被转换的地址为全内网Global (outside) 1 interface 定义一个全局地址池Global (dmz) 1 192.168.1.100-192.168.1.110 定义一个到达dmz的地址池6、配置ACLConf tAccess-list test1 standard permit 192.168.0.0 255.255.255.0 配置允许192.168.0.0/24这个网段的地址Access-list test2 extended permit tcp any any eq www 配置允许任意的地址访问任意网站Access-group test1 in interface dmz 把test1应用到接口上7、过滤URL配置例子:IP地址范围在192.168.0.2-192.168.0.15中的主机只能访问,不能访问其它任何网站。
ASA安全实验2
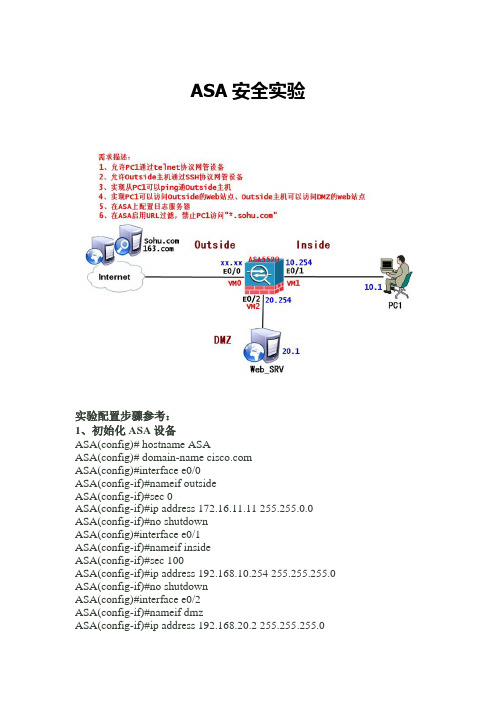
ASA安全实验实验配置步骤参考:1、初始化ASA设备ASA(config)# hostname ASAASA(config)# domain-name ASA(config)#interface e0/0ASA(config-if)#nameif outsideASA(config-if)#sec 0ASA(config-if)#ip address 172.16.11.11 255.255.0.0 ASA(config-if)#no shutdownASA(config)#interface e0/1ASA(config-if)#nameif insideASA(config-if)#sec 100ASA(config-if)#ip address 192.168.10.254 255.255.255.0 ASA(config-if)#no shutdownASA(config)#interface e0/2ASA(config-if)#nameif dmzASA(config-if)#ip address 192.168.20.2 255.255.255.0ASA(config-if)#sec 50ASA(config-if)#no shutdown2、配置ASA静态路由ASA(config)#route outside 0.0.0.0 0.0.0.0 172.16.1.13、配置ASA的telnet、SSH远程管理接入ASA(config)#telnet 192.168.10.0 255.255.255.0 insideASA(config)#crypto key generate rsa modulus 1024ASA(config)#ssh 0 0 outside4、配置PAT与Static NATASA(config)#nat (inside) 1 192.168.10.0 255.255.255.0ASA(config)#global (outside) 1 interfaceASA(config)#static (dmz,outside) tcp interface www 192.168.20.1 www 5、通过配置ACL放行WWW、ICMP流量ASA(config)#access-list OUT extended permit icmp any anyASA(config)#access-list OUT extended permit tcp any interface outside eq www6、配置日志服务器(192.168.10.1)ASA(config)# logging enableASA(config)# logging trap informationalASA(config)# logging host inside 192.168.10.17、ASA启用URL过滤ASA(config)# regex url1 "\.sohu\.com"---""----------------------------------------------------------------------------------ASA(config)# access-list tcp_filter permit tcp 192.168.10.0 255.255.255.0 any eq wwwASA(config)# class-map tcp_filter_classASA(config-cmap)# match access-list tcp_filter-------------------------------------------------------------------------ASA(config)# class-map type inspect http http_class--------把字符串划分类ASA(config-cmap)# match request header host regex url1-------------------------------------------------------------------------ASA(config)# policy-map type inspect http http_url_policy-----带http检测类型的策略映射ASA(config-pmap)# class http_classASA(config-pmap-c)# drop-connection log---------------------------------------------------------------------------- ASAconfig)# policy-map inside_http_url_policy ---标准的策略映射ASA(config-pmap)# class tcp_filter_classASA(config-pmap-c)# inspect http http_url_policyASA(config)# service-policy inside_http_url_policy interface inside8、测试从pc1访问测试从pc1telnet防火墙。
CCIE实验室ASA实验手册

二、防火墙对流量的控制........................................................................................................................- 3 -三、Basic Initialization............................................................................................................................- 4 -3.1 防火墙功能和许可证.......................................................................................................................- 4 -3.2 初始设置(Initial Setup)...............................................................................................................- 5 -3.3 配置接口参数..................................................................................................................................- 6 -3.4 实验练习:.....................................................................................................................................- 9 -四、IP Routing.......................................................................................................................................- 11 -4.1 静态和缺省路由.............................................................................................................................- 11 -4.2 路由图——route-map....................................................................................................................- 11 -4.3 动态路由协议——RIP和OSPF......................................................................................................- 11 -4.4 实验练习.......................................................................................................................................- 12 -五、 ACL..............................................................................................................................................- 15 -5.1配置ACL.....................................................................................................................................- 15 -5.2 Object Group................................................................................................................................- 16 -5.2 实验练习.......................................................................................................................................- 17 -六、NAT................................................................................................................................................- 18 -6.1 OVERVIEW..................................................................................................................................- 18 -6.2 NAT Bypass..................................................................................................................................- 19 -6.3 策略NAT.......................................................................................................................................- 20 -6.4 DNS和NAT...................................................................................................................................- 22 -6.5 动态NAT和PAT.............................................................................................................................- 23 -6.6 实验练习.......................................................................................................................................- 26 -七、AAA...............................................................................................................................................- 28 -7.1 AAA OVERVIEW..........................................................................................................................- 28 -7.2 RADIUS........................................................................................................................................- 28 -7.3 TACACS+.....................................................................................................................................- 29 -7.4 ASA上AAA的实现........................................................................................................................- 30 -7.5 配置AAA.......................................................................................................................................- 30 -7.6 配置可下载ACL............................................................................................................................- 34 -7.7 使用MAC地址免除流量的认证和授权...........................................................................................- 37 -7.8 实验练习.......................................................................................................................................- 38 -八、Filtering Services...........................................................................................................................- 39 -8.1 过滤ActiveX和Java.......................................................................................................................- 39 -8.2 URL Flitering................................................................................................................................- 40 -8.3 实验练习.......................................................................................................................................- 41 -九、防火墙模式.....................................................................................................................................- 41 -9.1 路由模式(Route Mode Overview)............................................................................................- 41 -9.2 透明模式(Transparent Mode)..................................................................................................- 42 -9.3 配置透明模式防火墙.....................................................................................................................- 42 -9.4 配置ARP审查...............................................................................................................................- 43 -9.5 定制MAC表..................................................................................................................................- 43 -9.6 实验练习.......................................................................................................................................- 44 -十、多虚拟防火墙(Multiple Context Mode)......................................................................................- 45 -10.2 流量分类.....................................................................................................................................- 45 -10.3 配置多虚拟防火墙......................................................................................................................- 47 -10.4 实验练习.....................................................................................................................................- 48 -十一、Failover......................................................................................................................................- 49 -11.1 Failover Overview.......................................................................................................................- 49 -11.2 Active/Standby Failover..............................................................................................................- 51 -11.3 Active/Active Failover.................................................................................................................- 51 -11.4 Failover Health Monitoring..........................................................................................................- 52 -11.5 实验练习.....................................................................................................................................- 53 -一、Firewall Overview防火墙技术分为三种:包过滤防火墙、代理服务器和状态包过滤;包过滤防火墙,使用ACL控制进入或离开网络的流量,ACL可以根据匹配包的类型或其他参数(如:源IP 地址、目的IP地址、端口号等)来制定;该类防火墙有以下不足,ACL制定的维护比较困难;可以使用IP欺骗很容易的绕过ACL;代理防火墙,也叫做代理服务器。
Cisco ASA 配置文件+IOS 备份与恢复实验手册---董荣才

Cisco ASA 配置文件+IOS 备份与恢复Cisco 路由器+ASA亲测,交换机理论上可以,期待测试...前言以下所有配置过程以ASA为例,路由器与其区别不大......Cisco ASA防火墙自带TFTP 导入导出配置命令(ASA 5505 ASDM界面访问ASA也有体现)......从一开始接触ASA到现在为止,已经有约半年时间,这么长时间的努力,多数时间浪费在了该死的英文界面以及网上区区的极少文章。
我们长时间的奋斗是否该助新入手的朋友一臂之力?ubuntu(linux 系统的一种)主张的一句话叫做:”我的存在,是因为大家的存在!“我决定要这么做!鄙视微软和cisco代码等技术不透明....吼吼.....奋斗了2天的成果,分享一下!目的:为了防御不测,网络受到黑客恶性攻击等因素,熟练掌握备份与还原配置文件以及IOS文件。
流程:1. 在客户端搭建TFTP服务器,并保持TFTP服务在自动启动状态.2.备份还原ASA配置文件3.备份还原IOS配置文件一准备工作:(在此特意说明一下,我是用笔记本server 2003系统通过telnet登录ASA 命令行)在2003系统中安装TFTP服务,使2003系统成为TFTP服务器。
在此强烈推荐solarwinds—TFTP-server ,下载地址:/soft/480772/,默认安装完成后,启用solarwinds-tftp服务!二备份还原ASA配置文件cisco 只能通过TFTP的方法来备份和恢复数据....(1)备份第一步:登录ASA防火墙命令行界面(如图)第二步:执行 copy running-config tftp命令(如图)Source filename[running-config] 意思是确认备份默认文件running-config吗?按照默认,按回车下一步即可!第三步:指定TFTP服务器IP地址address or name of remote host [192.168.1.13]? 意思是需要将TFTP服务器IP设置为默认192.168.1.13吗?在此我不需要,手动输入正确的TFTP服务器IP即可。
Cisco-ASA-5500防火墙个人基本配置手册-去水印
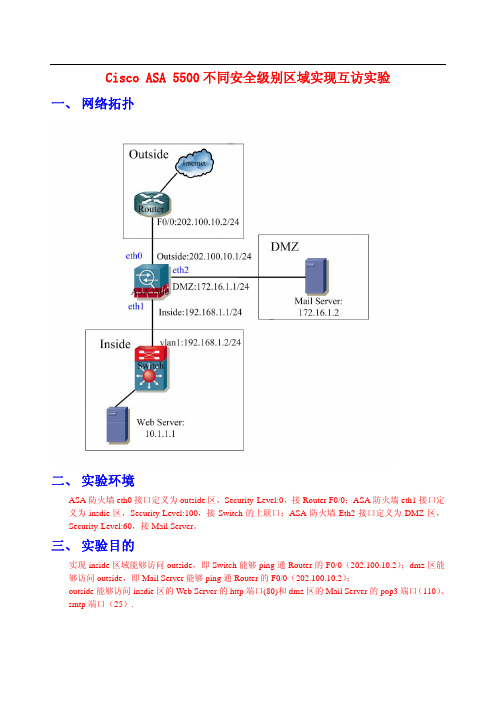
Cisco ASA 5500不同安全级别区域实现互访实验一、 网络拓扑二、 实验环境ASA防火墙eth0接口定义为outside区,Security-Level:0,接Router F0/0;ASA防火墙eth1接口定义为insdie区,Security-Level:100,接Switch的上联口;ASA防火墙Eth2接口定义为DMZ区,Security-Level:60,接Mail Server。
三、 实验目的实现inside区域能够访问outside,即Switch能够ping通Router的F0/0(202.100.10.2);dmz区能够访问outside,即Mail Server能够ping通Router的F0/0(202.100.10.2);outside能够访问insdie区的Web Server的http端口(80)和dmz区的Mail Server的pop3端口(110)、smtp端口(25).四、 详细配置步骤1、端口配置CiscoASA(config)# interface ethernet 0CiscoASA(config)#nameif ousideCiscoASA(config-if)# security-level 0CiscoASA(config-if)# ip address 202.100.10.1 255.255.255.0CiscoASA(config-if)# no shutCiscoASA(config)# interface ethernet 1CiscoASA(config)#nameif insideCiscoASA(config-if)# security-level 100CiscoASA(config-if)# ip address 192.168.1.1 255.255.255.0CiscoASA(config-if)# no shutCiscoASA(config)# interface ethernet 2CiscoASA(config)#nameif dmzCiscoASA(config-if)# security-level 50CiscoASA(config-if)# ip address 172.16.1.1 255.255.255.0CiscoASA(config-if)# no shut2、路由配置CiscoASA(config)# route outside 0.0.0.0 0.0.0.0 202.100.10.2 1 #默认路由CiscoASA(config)# route inside 10.0.0.0 255.0.0.0 192.168.1.2 1 #外网访问内网服务器的路由3、定义高安全接口区域需要进行地址转换的IP范围CiscoASA(config)# nat (inside) 1 0 0CiscoASA(config)# nat (dmz) 1 0 04、定义低安全接口区域用于高安全接口区域进行IP转换的地址范围CiscoASA(config)# global (outside) 1 interfaceCiscoASA(config)# global (dmz) 1 interface5、定义静态IP映射(也称一对一映射)CiscoASA(config)# static (inside,outside) tcp 202.100.10.1 www 10.1.1.1 www netmask 255.255.255.255#实现从outside区访问inside区10.1.1.1的80端口时,就直接访问10.1.1.1:80 对outside区的映射202.100.10.1:80CiscoASA(config)# static (dmz,outside) tcp 202.100.10.1 pop3 172.16.1.2 pop3 netmask 255.255.255.255#实现从outside区访问dmz区172.16.1.2的110时,就直接访问172.16.1.2:110 对outside区的映射202.100.10.1:110CiscoASA(config)# static (dmz,outside) tcp 202.100.10.1 smtp 172.16.1.2 smtp netmask 255.255.255.255#实现从outside区访问dmz区172.16.1.2的25时,就直接访问172.16.1.2:25 对outside区的映射202.100.10.1:256、定义access-listCiscoASA(config)# access-list 101 extended permit ip any anyCiscoASA(config)# access-list 101 extended permit icmp any anyCiscoASA(config)# access-list 102 extended permit tcp any host 10.1.1.1 eq wwwCiscoASA(config)# access-list 102 extended permit icmp any anyCiscoASA(config)# access-list 103 extended permit tcp any host 172.16.1.2 eq pop3CiscoASA(config)# access-list 103 extended permit tcp any host 172.16.1.2 eq smtp7、在接口上应用access-listCiscoASA(config)# access-group 101 in interface outsideCiscoASA(config)#access-group 102 in interface insideCiscoASA(config)#access-group 103 in interface dmz五、 实验总结1、当流量从高权限区域流向低权限区域时1、只要路由配通了,无须配置nat/global,也无须配置access-list,就可以直接telnet低权限区域主机;2、只要路由配通了,同时配置了access-list,无须配置nat/global,就可以直接ping通低权限区域主机;3、只要路由配通了,同时配置了nat/global/access-list,此时telnet/ping均会执行地址转换2、当流量从低权限区域流向高权限区域时1、即使路由已经配通了,也不能成功访问;2、路由已经配通了,同时必须正确配置了static IP地址映射及access-list,才能成功访问;3、调通路由是基础,同时只跟static/access-list有关,而跟nat/global毫无关系。
cisco ASA防火墙产品动手培训教材之二

如果满足条件客户端可以正常访问,在此我们不做演示如果客户端没有安全诺顿,或为启动扫描进程访问将是失败:四AIP-SSM 模块测试1准备HTTPS的登陆__________________________________________________________________________________________________________________________________________________________ASA AIP模块密码恢复:在AIP OS 6.0 之前大家都使用下面的命令实现密码恢复,比较烦琐,_____________________________________________________________________________而且时间过长,恢复后Signature 需要重新灌入,进一步加大了维护的时间和成本,在ASA 8.0+AIP 6.0中新加入了一个新的命令实现了密码的一键恢复,具体过程如下:AIP OS 5.X 版本密码恢复过程:首先在ASA上执行如下命令。
这个命令的作用是为软件的重灌设置TFTP参数,IP地址可以随便设,保证同一网段即可。
Port IP Address 指的是AIP-SSM模块管理端口的IP地址,这个地址将在模块重启以后生效。
CISCOASA# hw-module module 1 recover conifgImage URL [tftp://0.0.0.0/]:tftp://192.168.1.2/IPS-SSM-K9-sys-1.1-a-6.0-2-E1.imgPort IP Address [0.0.0.0]: 192.168.1.1VLAN ID [0]:Gateway IP Address [0.0.0.0]:参数设置好了,现在我们来重启AIP-SSM模块。
这个命令执行以后,AIP-SSM模块会进行重启,并按照之前设置的TFTP服务器去自动加载新的6.0软件,所以记得在执行命令前打开TFTP软件。
Cisco ASA with FirePOWER Services数据手册说明书

Data SheetCisco ASA with FirePOWER ServicesMeet the industry’s first adaptive, threat-focused next-generation firewall (NGFW) designed for a new era of threat and advanced malware protection. Cisco® ASA with FirePOWER Services delivers integrated threat defense for the entire attack continuum - before, during, and after an attack. How? By combining the proven security capabilities of the Cisco ASA firewall with the industry-leading Sourcefire®threat and Advanced Malware Protection (AMP) features together in a single device. The solution uniquely extends the capabilities of the Cisco ASA 5500-X Series Next-Generation Firewalls beyond what today’s NGFW solutions are capable of. Whether you need protection for a small or midsized business, a distributed enterprise, or a single data center, Cisco ASA with FirePOWER Services provides the needed scale and context in a NGFW solution.Superior Multilayered ProtectionCisco ASA with FirePOWER Services brings distinctive threat-focused next-generation security services to the Cisco ASA 5500-X Series Next-Generation Firewalls. It provides comprehensive protection from known and advanced threats, including protection against targeted and persistent malware attacks (Figure 1). Cisco ASA is the world’s most widely deployed, enterpr ise-class stateful firewall. Cisco ASA with FirePOWER Services features these comprehensive capabilities:●Site-to-site and remote access VPN and advanced clustering provide highly secure, high-performanceaccess and high availability to help ensure business continuity.●Granular Application Visibility and Control (AVC) supports more than 4,000 application-layer and risk-basedcontrols that can launch tailored intrusion prevention system (IPS) threat detection policies to optimizesecurity effectiveness.●The industry-leading Cisco ASA with FirePOWER next-generation IPS (NGIPS) provides highly effectivethreat prevention and full contextual awareness of users, infrastructure, applications, and content to detect multivector threats and automate defense response.●Reputation- and category-based URL filtering offer comprehensive alerting and control over suspicious webtraffic and enforce policies on hundreds of millions of URLs in more than 80 categories.●AMP provides industry-leading breach detection effectiveness, sandboxing, a low total cost of ownership,and superior protection value that helps you discover, understand, and stop malware and emerging threats missed by other security layers.Figure 1. Cisco ASA with FirePOWER Services: Key Security FeaturesUnprecedented Network VisibilityCisco ASA with FirePOWER Services is centrally managed by the Cisco Firepower Management Center (formerly known as Cisco FireSIGHT Management Center), which provides security teams with comprehensive visibility into and control over activity within the network. Such visibility includes users, devices, communication between virtual machines, vulnerabilities, threats, client-side applications, files, and web sites. Holistic, actionable indications of compromise (IoCs) correlate detailed network and endpoint event information and provide further visibility into malware infections. Cisco’s enterprise-class management tools help administrators reduce complexity with unmatched visibility and control across NGFW deployments. Cisco Firepower Management Center also provides content awareness with malware file trajectory that aids infection scoping and root cause determination to speed time to remediation.Cisco Security Manager provides scalable and centralized network operations workflow management. It integrates a powerful suite of capabilities; including policy and object management, event management, reporting, and troubleshooting for Cisco ASA firewall functions when utilizing Cisco Firepower Management Center.For local, on-device management including deployments for small and midsized businesses, Cisco Adaptive Security Device Manager (ASDM) 7.3.x provides, access control and advanced threat defense management. ASDM V 7.3.x provides an enhanced user interface that provides quick views on trends and the ability to drill down for further analysis.Figure 2. Cisco Firepower Management Center: Intuitive High-Level and Detailed Drill-Down DashboardsReduced Costs and ComplexityCisco ASA with FirePOWER Services incorporates an integrated approach to threat defense, reducing capital and operating costs and administrative complexity. It smoothly integrates with the existing IT environment, work stream, and network fabric. The appliance family is highly scalable, performs at up to multigigabit speeds, and provides consistent and robust security across branch, Internet edge, and data centers in both physical and virtual environments.With Cisco Firepower Management Center, administrators can streamline operations to correlate threats, assess their impact, automatically tune security policy, and easily attribute user identities to security events. Cisco Firepower Management Center continually monitors how the network is changing over time. New threats are automatically assessed to determine which ones can affect your business. Responses are then focused on remediation and network defenses are adapted to changing threat conditions. Critical security activities such as policy tuning are automated, saving time and effort, while protections and countermeasures are maintained in an optimal state.Cisco Firepower Management Center integrates easily with third-party security solutions through the eStreamer API to streamline operation workflows and fit existing network fabrics.Table 1 highlights the best-in-class features and benefits of Cisco ASA with FirePOWER Services. Table 1. Features and Benefits of Cisco ASA with FirePOWER ServicesProduct Performance and SpecificationsTable 2 details the NGFW capabilities and capacities of the Cisco ASA with FirePOWER Services for Cisco ASA 5500-X Series.Table 2. Cisco ASA 5500-X with FirePOWER Services Capabilities and CapacitiesThroughput: Application Control (AVC) 250 Mbps 250 Mbps 250 Mbps 450 Mbps 850 Mbps 300 Mbps 500Mbps1,100 Mbps 1,500Mbps1,750MbpsThroughput: Application Control (AVC) and IPS 125 Mbps 125 Mbps 125 Mbps 250 Mbps 450 Mbps 150 Mbps 250Mbps650 Mbps 1,000Mbps1,250MbpsMaximum concurrent sessions 20,000;50000120,000;50000150000 100,000 250,000 100,000 250,000 500,000 750,000 1,000,00Maximum NewConnectionsper second5,000 5,000 5,000 10,000 20,000 10,000 15,000 20,000 30,000 50,000SupportedapplicationsMore than 3,000URL categories 80+Number ofURLscategorizedMore than 280 millionCentralizedconfiguration,logging,monitoring,and reportingMulti-device Cisco Security Manager (CSM) and Cisco Firepower Management CenterOn-DeviceManagementASDM (version 7.3 or higher required) ASDM1 Higher specifications are associated with the Security Plus license.Table 3 compares the features and capacities of the different ASA 5500-X Series Next-Generation Firewalls for small offices, branch locations, and Internet edge deployments.Table 3. Cisco ASA 5500-X Series Next-Generation FirewallsStatefulinspectionthroughput(maximum1)750 Mbps 750 Mbps 750 Mbps 1 Gbps 1.8 Gbps 1 Gbps 1.2 Gbps 2 Gbps 3 Gbps 4 GbpsStatefulinspectionthroughput(multiprotocol2)300 Mbps 300 Mbps 300 Mbps 500 Mbps 900 Mbps 500 Mbps 600 Mbps 1 Gbps 1.5 Gbps 2 GbpsTriple DataEncryptionStandard/AdvancedEncryptionStandard(3DES/AES)VPNthroughput3100 Mbps 100 Mbps 100 Mbps 175 Mbps 250 Mbps 200 Mbps 250 Mbps 300 Mbps 400 Mbps 700 MbpsUsers/nodes Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited IPsec site-to-site VPNpeers10; 50410; 50450 100 300 250 250 750 2500 5000Cisco CloudWeb SecurityusersFor detailed sizing guidance see the CWS Connector Sizing for ASA 5500 and ASA 5500-XCiscoAnyConnectPlus/ApexVPNmaximumsimultaneousconnections5505505505100530052505250575052500550005Virtualinterfaces(VLANs)5; 3045; 30430 50 100 50; 100 100 200 300 500Securitycontexts5(included;maximum)N/A N/A N/A 2; 5 2; 5 0,0; 2,5 2;5 2; 20 2; 50 2; 100High availability4RequiresSecurityPlusLicense;Active/StandbyRequiresSecurity PlusLicense;Active/StandbyActive/StandbyActive/Active andActive/StandbyActive/Active andActive/StandbyRequiresSecurityPlusLicense;Active/Active andActive/StandbyActive/Active andActive/StandbyActive/Active andActive/StandbyActive/Active andActive/StandbyActive/Active andActive/StandbyIntegrated Wireless Access Point (See Cisco AP 702 datasheet for WiFi technical details) N/A WirelessBandsa/b/g/n; Maxn wifithroughput54 Mbps;internalantenna only;localmanagementor centralizedvia CiscoWLCN/A N/A N/A N/A N/A N/A N/A N/AExpansion slot N/A N/A N/A N/A N/A 1 interfacecard1 interfacecard1 interfacecard1 interfacecard1 interfacecardUser-accessibleFlash slotNo No No No No No No 0 - 0USB 2.0 ports USB porttype ‘A’,HighSpeed 2.0 USB porttype ‘A’, HighSpeed 2.0USB porttype ‘A’,HighSpeed 2.0USB porttype ‘A’,HighSpeed 2.0USB porttype ‘A’,HighSpeed 2.02 2 2 2 2Integrated I/O 8 x 1GigabitEthernet(GE) 8 x 1GE 4 x 1GE 8 x 1GE 8 x 1GE 6 GEcopper6 GEcopper8 GEcopper8 GEcopper8 GEcopperExpansion I/O N/A N/A N/A N/A N/A 6 GEcopper or 6 GEcopper or6 GEcopper or6 GEcopper or6 GEcopper or6 GESmallForm-FactorPluggable(SFP)6 GE SFP 6 GE SFP 6 GE SFP 6 GE SFPDedicated management port Yes (Tobe sharedwithFirePOWERServices),10/100/1000Yes (To beshared withFirePOWERServices),10/100/1000Yes (Tobe sharedwithFirePOWERServices),10/100/1000Yes (Tobe sharedwithFirePOWERServices),10/100/1000Yes (Tobe sharedwithFirePOWERServices),10/100/1000Yes (1GE)Yes (1GE)Yes (1GE)Yes (1GE)Yes (1GE)Serial ports 1 RJ-45and MiniUSBconsole 1 RJ-45 andMini USBconsole1 RJ-45and MiniUSBconsole1 RJ-45and MiniUSBconsole1 RJ-45and MiniUSBconsole1 RJ-45console1 RJ-45console1 RJ-45console1 RJ-45console1 RJ-45consoleSolid-state drive 50 GBmSata650 GBmSata650 GBmSatatested forheat80 GBmSata6100 GBmSata61 slot, 120GBmultilineconfigurator self-encryptingdrive(MLCSED)1 slot, 120GB MLCSED1 slot,2 slots,RAID 12 slots,RAID 1120 GBMLC SED120 GBMLC SED120 GBMLC SEDMemory 4 GB 4 GB 4 GB 8 GB 8 GB 4 GB 8 GB 8 GB 12 GB 16 GB System flash 8 GB 8 GB 8 GB 8 GB 8 GB 4 GB 8 GB 8 GB 8 GB 8 GBSystem bus Multibusarchitecture MultibusarchitectureMultibusarchitectureMultibusarchitectureMultibusarchitectureMultibusarchitectureMultibusarchitectureMultibusarchitectureMultibusarchitectureMultibusarchitectureOperating ParametersTemperature 32 to104°F (0to 40 °C) 32 to 104°F(0 to 40 °C)-4 to140°F (-20to 60 °C)32 to104°F (0to 40 °C)32 to104°F (0to 40 °C)23 to104°F (-5to 40°C)23 to104°F (-5to 40°C)23 to104°F (-5to 40°C)23 to104°F (-5to 40°C)23 to104°F (-5to 40°C)Relative humidity 90 percentnoncondensing90 percentnoncondensing95 percentnoncondensing10 to 90percentnoncondensing10 to 90percentnoncondensing10 to 90percentnoncondensing10 to 90percentnoncondensing90 percent 90 percent 90 percentAltitude Designedand testedfor 0 to10,000 ft(3048 m) Designed andtested for 0 to10,000 ft(3048 m)Designedand testedfor 0 to10,000 ft(3050 m)Designedand testedfor 0 to10,000 ft(3048 m)Designedand testedfor 0 to10,000 ft(3048 m)Designedand testedfor 0 to15,000 ft(4572 m)Designedand testedfor 0 to15,000 ft(4572 m)Designedand testedfor 0 to10,000 ft(3050 m)Designedand testedfor 0 to10,000 ft(3050 m)Designedand testedfor 0 to10,000 ft(3050 m)1 Maximum throughput measured with UDP traffic under ideal conditions.2 Multiprotocol = Traffic profile consisting primarily of TCP-based protocols/applications like HTTP, SMTP, FTP, IMAPv4, BitTorrent, and DNS.3 VPN throughput and sessions count depend on the ASA device configuration and VPN traffic patterns. These elements should be taken into consideration as part of your capacity planning.4 Higher specifications are associated with the Security Plus license.5 Separately licensed feature. For AnyConnect, licenses are purchased based on feature tier (Plus/Apex), term and authorized user license. See ordering guide below for detailed ordering instructions.6 Usable space dependent upon system software.7 Derate the maximum operating temperature 1.5°C per 1000 ft above sea level.Hardware Product ComplianceCurrent information on ASA with FirePOWER product compliance information can be found on the Cisco Product Approval Status (PAS) link:/cse/prdapp.If you are not registered with , please refer to the registration link locatedat: /RPF/register/register.do.To access information please follow the below steps:1. Select the Product Certifications by Country radio button select GO2. Under option 2 enter product ID or part of it in the product name box (one at a time only) for example FPR-C93003. Under additional filter select or highlight your country of interest or keep all countries selected for full results4. Select submit5. Your results will be displayed. Under status select the hyperlink Details6. Find your corresponding documentsHardware Product Performance and SpecificationsPlatform Support/CompatibilityCisco ASA with FirePOWER Services include Cisco ASA firewalling, AVC, URL filtering, NGIPS, and AMP. This unique set of capabilities is available on the Cisco ASA 5500-X Series NGFW platforms: Cisco ASA 5506-X, 5506W-X, 5506H-X, 5508-X, 5516-X, 5512-X, 5515-X, 5525-X, 5545-X, 5555-X.Cisco ASA with FirePOWER Services software is supported on the Cisco ASA 5500-X Series of next-generation midrange security appliances running Cisco ASA Software Release 9.2.2 and later. Cisco Firepower Management Center and Cisco Security Manager are required to manage Cisco ASA with FirePOWER Services ASA 5512-X, 5515-X, 5525-X, 5545-X, 5555-X. ASDM V 7.3.x is available on-device to manage single instance deployments of Cisco ASA 5506-X, 5506W-X, 5506H-X, 5508-X, and 5516-X with FirePOWER Services.Cisco ASA 5500-X Series 6-Port GE Interface CardsCisco ASA 5500-X Series 6-port Gigabit Ethernet Interface Cards extend the I/O profile of the Cisco ASA 5500-X Series appliances* by providing additional GE ports. The cards provide the following benefits:●Better segmentation of network traffic into separate security zones●Fiber-optic cable connectivity for long-distance communication●Load sharing of traffic as well as protection against link failure through the use of EtherChannel●Support for jumbo Ethernet frames of up to 9000 bytes●Protection against cable failure for the most demanding active/active failover and full-mesh firewalldeploymentsNote: *Not available on ASA 5508-X or ASA 5516-XTable 4 lists the characteristics of the Cisco ASA 5500-X Series 6-port GE interface cards.Table 4. Characteristics of Cisco ASA 5500-X Series 6-Port GE Interface CardsSix 10/100/1000BASE-T Six GE optical SFP 1000BASE-SX, 1000BASE-LX, or1000BASE-LH transceiver supportedOrdering InformationTo place an order, visit the Cisco ordering homepage. Table 5 provides ordering information for Cisco ASA with FirePOWER Services.Table 5. Cisco ASA with Fire POWER Services Ordering InformationThe following table includes Cisco ASA FirePOWER Services bundle SKUs (including hardware and subscription) that offer a convenient mechanism for ordering both the appliances and software subscriptions in a single SKU configuration. It is the recommended mode of configuration for ordering. Standalone AMP license and subscriptions are also available to upgrade an existing TA or TAC subscription license. Please see the ASA with FirePOWER Services Ordering Guide for details.To Download the SoftwareVisit the Cisco Software Center to download Cisco ASA with FirePOWER Services Software.Cisco CapitalFinancing Helps You Achieve Your ObjectivesCisco Capital® financing can help you acquire the technology you need to achieve your objectives and stay competitive. We can help you reduce capital expenditures (CapEx), accelerate your growth, and optimize your investment dollars and ROI. Cisco Capital financing gives you flexibility in acquiring hardware, software, services, and complementary third-par ty equipment. And there’s just one predictable payment. Cisco Capital financing is available in more than 100 countries. Learn more.For More InformationFor more information, please visit the following links:●Cisco ASA 5500-X Series Next-Generation Firewalls:/go/asa.●Cisco Security Manager:/c/en/us/products/security/security-manager/index.html.●Cisco Adaptive Security Device Manager:/c/en/us/products/security/adaptive-security-device-manager/index.html.●Cisco Security Services: /en/US/products/svcs/ps2961/ps2952/serv_group_home.html.●Cisco AnyConnect Secure Mobility Client/go/anyconnect.●Cisco AnyConnect Ordering Guide/c/dam/en/us/products/security/anyconnect-og.pdf.Printed in USA C78-733916-14 02/18。
思科ASA 5510防火墙实战配置中文手册

配置设备介绍:(只为做实验实际应用请根据自己具体情况更改相关参数即可)核心交换机4507提供VLAN3 网关地址:192.168。
3。
254提供DNS 服务器连接:192。
168.0。
1接入交换机2960提供VLAN3 TURNK 连接,可用IP 地址为192。
168。
3。
0-192.168。
3.240掩码:255.255。
255.0网关:192.168.3.254DNS:192.168。
0.1内网实验防火墙CISCO ASA 5510E0/0 IP:192.168。
3。
234E0/1 IP 10。
1。
1。
1实现配置策略1. 动态内部PC1 DHCP 自动获得IP 地址,可访问INTERNET,并PING 通外部网关。
PC1 Ethernet adapter 本地连接:Connection—specific DNS Suffix 。
: gametuziDescription . 。
. . . . 。
:Broadcom 440x rollerPhysical Address。
. . 。
. . 。
: 00-13-77-04—9Dhcp Enabled。
. 。
. 。
. 。
:YesAutoconfiguration Enabled 。
. . :YesIP Address. 。
. 。
. . . 。
. :10.1.1。
20Subnet Mask . . . . 。
. 。
. 。
: 255.255。
0.0Default Gateway . . 。
. 。
: 10.1。
1.1DHCP Server . 。
. 。
. 。
. : 10。
1。
1。
1DNS Servers . . . . . 。
. . 。
: 192.168.0。
12. 静态内部PC2 手动分配地址,可访问INTERNET ,并PING 通外部网关. PC1 Ethernet adapter 本地连接:Connection—specific DNS Suffix 。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
二、防火墙对流量的控制........................................................................................................................- 3 - 三、Basic Initialization............................................................................................................................- 4 - 3.1 防火墙功能和许可证.......................................................................................................................- 4 - 3.2 初始设置(Initial Setup )...............................................................................................................- 5 - 3.3 配置接口参数..................................................................................................................................- 6 - 3.4 实验练习:.....................................................................................................................................- 9 - 四、IP Routing.......................................................................................................................................- 11 - 4.1 静态和缺省路由.............................................................................................................................- 11 - 4.2 路由图——route-map....................................................................................................................- 11 - 4.3 动态路由协议——RIP 和OSPF......................................................................................................- 11 - 4.4 实验练习.......................................................................................................................................- 12 - 五、 ACL..............................................................................................................................................- 15 - 5.1 配置ACL.....................................................................................................................................- 15 - 5.2 Object Group................................................................................................................................- 16 - 5.2 实验练习.......................................................................................................................................- 17 - 六、NAT................................................................................................................................................- 18 - 6.1 OVERVIEW..................................................................................................................................- 18 - 6.2 NAT Bypass..................................................................................................................................- 19 - 6.3 策略NAT.......................................................................................................................................- 20 - 6.4 DNS 和NAT...................................................................................................................................- 22 - 6.5 动态NAT 和PAT.............................................................................................................................- 23 - 6.6 实验练习.......................................................................................................................................- 26 - 七、AAA ...............................................................................................................................................- 28 - 7.1 AAA OVERVIEW..........................................................................................................................- 28 - 7.2 RADIUS........................................................................................................................................- 28 - 7.3 TACACS+.....................................................................................................................................- 29 - 7.4 ASA 上AAA 的实现........................................................................................................................- 30 - 7.5 配置AAA.......................................................................................................................................- 30 - 7.6 配置可下载ACL............................................................................................................................- 34 - 7.7 使用MAC 地址免除流量的认证和授权...........................................................................................- 37 - 7.8 实验练习.......................................................................................................................................- 38 - 八、Filtering Services...........................................................................................................................- 39 - 8.1 过滤ActiveX 和Java.......................................................................................................................- 39 - 8.2 URL Flitering................................................................................................................................- 40 - 8.3 实验练习.......................................................................................................................................- 41 - 九、防火墙模式.....................................................................................................................................- 41 - 9.1 路由模式(Route Mode Overview )............................................................................................- 41 - 9.2 透明模式(Transparent Mode )..................................................................................................- 42 - 9.3 配置透明模式防火墙.....................................................................................................................- 42 - 9.4 配置ARP 审查...............................................................................................................................- 43 - 9.5 定制MAC 表..................................................................................................................................- 43 - 9.6 实验练习.......................................................................................................................................- 44 - 十、多虚拟防火墙(Multiple Context Mode )......................................................................................- 45 -www.n e t 527.c n小牛10.2 流量分类.....................................................................................................................................- 45 - 10.3 配置多虚拟防火墙......................................................................................................................- 47 - 10.4 实验练习.....................................................................................................................................- 48 - 十一、Failover......................................................................................................................................- 49 - 11.1 Failover Overview.......................................................................................................................- 49 - 11.2 Active/Standby Failover..............................................................................................................- 51 - 11.3 Active/Active Failover.................................................................................................................- 51 - 11.4 Failover Health Monitoring..........................................................................................................- 52 - 11.5 实验练习.....................................................................................................................................- 53 -www.n e t 527.c n小牛一、Firewall Overview防火墙技术分为三种:包过滤防火墙、代理服务器和状态包过滤;包过滤防火墙,使用ACL控制进入或离开网络的流量,ACL可以根据匹配包的类型或其他参数(如:源IP 地址、目的IP地址、端口号等)来制定;该类防火墙有以下不足,ACL制定的维护比较困难;可以使用IP欺骗很容易的绕过ACL;代理防火墙,也叫做代理服务器。
