dberr
BDE错误代码

附录B BDE错误代码使用BDE(Borland Database Engine)时,有时候屏幕上会显示一个错误信息框,这表明数据库存引擎出现错误。
很多情况下,这是因为用户在安装软件时配置不当。
一般情况下,上述错误信息框显示的是一个十六进制的错误代码。
问题是,这些数字到底代表什么含义呢?为了更好地帮助你,我们制作了表B -1。
表B -1列出了所有可能的B D E错误代码以及对每个错误的简短解释。
表B-1 BDE错误代码错误代码简短描述十进制十六进制00 000成功3 30 021系统错误3 40 022感兴趣的对象未找到3 50 023物理数据损坏3 60 024I /O相关错误3 70 025资源或限定错误3 80 026数据完整性违例3 90 027非法的请求4 00 028锁定违例4 10 029访问/安全违例4 20 02A非法的环境4 30 02B操作系统错误4 40 02C网络错误4 50 02D可选的参数4 60 02E查询处理器4 70 02F版本不匹配4 80 030不支持的能力4 90 031系统本配置错误5 00 032警告5 10 033杂项5 20034 兼容性错误6 20 03E驱动程序规范错误6 30 03F内部符号2 560 100违反主键2 570 101问题2 580 102已改变5 120 200产品索引文件丢失、损坏或无法识别5 130 201以只读打开5 140 202以只读模式打开一个表5 150 203打开并分离5 160 204打开一个表并分离出产品索引文件5 170 205打开失败5 180 206不要打开表(续)错误代码简短描述十进制十六进制5 190 207转换非d B A S E索引5 200 208把产品索引转换为d B A S E格式5 210 209 B L O B文件未找到5 220 20A打开但不包含B L O B文件5 230 20B打开表但不包含B L O B文件5 240 20C清空所有B L O B字段5 250 20D重新初始化B L O B文件5 260 20E打开失败5 270 20F不要打开这个表5 280 210导入非dBASE BLOB文件5 290 211以d B A S E格式导入B L O B文件5 300 212打开非d B A S E表5 310 213打开表和B L O B文件5 320 214产品索引语言驱动程序不匹配5 330 215产品索引已坏5 340 216重建产品索引5 350 217重建所有的产品索引1 0240 400L o o k u p表未找到或已破坏1 0250 401 B L O B文件未找到或已破坏1 0260 402以只读打开1 0270 403以只读模式打开一个表1 0280 404打开失败1 0290 405不要打开表1 0300 406删除查找1 0310 407删除与l o o k u p表的链接1 2800 500字典对象已存在1 2810 501跳过这个对象1 2820 502跳过这个对象及其相关的关系1 2830 503使用现有的对象1 2840 504使用现有的字典对象1 2850 505放弃1 2860 506放弃这个操作1 2870 507导入字典对象失败4 608 1 200未知的S Q L命令4 609 1 201准备执行S Q L命令4 610 1 202执行S Q L命令4 611 1 203S Q L错误4 612 1 204S Q L语句4 613 1 205S Q L连接4 614 1 206S Q L事务4 615 1 207SQL BLOB IO4 616 1 208S Q L杂项4 617 1 209S Q L供应者4 618 1 20A O R A C L E-o r l o n(续)错误代码简短描述十进制十六进制4 619 1 20B O R A C L E-o l o n4 620 1 20C O R A C L E-o l o g o f4 621 1 20D O R A C L E-o c o n4 622 1 20E O R A C L E-o c o f4 623 1 20F O R A C L E-o o p e n4 624 1 210O R A C L E-o s q134 625 1 211O R A C L E-o d s c4 626 1 212O R A C L E-o d e f i n4 627 1 213O R A C L E-o b n d r v4 628 1 214O R A C L E-o b n d r v n4 629 1 215O R A C L E-o e x e c4 630 1 216O R A C L E-o f e t c h4 631 1 217O R A C L E-o f e n4 632 1 218O R A C L E-o c a n4 633 1 219O R A C L E-o c l o s e4 634 1 21A O R A C L E-o e r h m s4 635 1 21B O R A C L E-o p a r s e4 636 1 21C O R A C L E-o f l n g4 637 1 21D O R A C L E-o d e s s p4 638 1 21E O R A C L E-o d e s c r4 639 1 21F O R A C L E-o e x n4 648 1 228I N T R B A S E-i s c_a t t a c h_d a t a b a s e4 649 1 229I N T R B A S E-i s c_b l o b_d e f a u l t_d e s c4 650 1 22A I N T R B A S E-i s c_b l o b_g e n_b p b4 651 1 22B I N T R B A S E-i s c_b l o b_i n f o4 652 1 22C I N T R B A S E-i s c_b l o b_l o o k u p_d e s c4 653 1 22D I N T R B A S E-i s c_c l o s e_b l o b4 654 1 22E I N T R B A S E-i s c_c o m m i t_r e t a i n i n g4 655 1 22F I N T R B A S E-i s c_c o m m i t_t r a n s a c t i o n4 656 1 230I N T R B A S E-i s c_c r e a t e_b l o b4 657 1 231I N T R B A S E-i s c_c r e a t e_b l o b24 658 1 232I N T R B A S E-i s c_d e c o d e_d a t e4 659 1 233I N T R B A S E-i s c_d e t a c h_d a t a b a s e4 660 1 234I N T R B A S E-i s c_d s q l_a l l o c a t e_s t a t e m e n t4 661 1 235I N T R B A S E-i s c_d s q l_e x e c u t e4 662 1 236I N T R B A S E-i s c_d s q l_e x e c u t e24 663 1 237I N T R B A S E-i s c_d s q l_f e t c h4 664 1 238I N T R B A S E-i s c_d s q l_f r e e_s t a t e m e n t4 665 1 239I N T R B A S E-i s c_d s q l_p r e p a r e4 666 1 23A I N T R B A S E-i s c_d s q l_s e t_c u r s o r_n a m e4 667 1 23B I N T R B A S E-i s c_d s q l_s q l_i n f o4 668 1 23C I N T R B A S E-i s c_e n c o d e_d a t e4 669 1 23D I N T R B A S E-i s c_g e t_s e g m e n t4 670 1 23E I N T R B A S E-i s c_i n t e r p r e t e(续)错误代码简短描述十进制十六进制4 671 1 23F I N T R B A S E-i s c_o p e n_b l o b4 672 1 240I N T R B A S E-i s c_o p e n_b l o b24 673 1 241I N T R B A S E-i s c_p u t_s e g m e n t4 674 1 242I N T R B A S E-i s c_r o l l b a c k_t r a n s a c t i o n4 675 1 243I N T R B A S E-i s c_s q l c o d e4 676 1 244I N T R B A S E-i s c_s t a r t_t r a n s a c t i o n4 677 1 245I N T R B A S E-i s c_v a x_i n t e g e r4 688 1 250M S S Q L-d b b i n d4 689 1 251M S S Q L-d b c m d4 690 1 252M S S Q L-d b c a n c e l4 691 1 253M S S Q L-d b c l o s e4 692 1 254M S S Q L-d b c o l l e n4 693 1 255M S S Q L-d b c o l n a m e4 694 1 256M S S Q L-d b c o l t y p e4 695 1 257M S S Q L-d b c o n v e r t4 696 1 258M S S Q L-d b d a t a r e a d y4 697 1 259M S S Q L-d b d a t l e n4 698 1 25A M S S Q L-d b e r r h a n d l e4 699 1 25B M S S Q L-d b f r e e b u f4 700 1 25C M S S Q L-d b f r e e l o g i n4 701 1 25D M S S Q L-d b h a s r e t s t a t4 702 1 25E M S S Q L-d b i n i t4 703 1 25F M S S Q L-d b l o g i n4 704 1 260M S S Q L-d b m o r e t e x t4 705 1 261M S S Q L-d b m s g h a n d l e4 706 1 262M S S Q L-d b n e x t r o w4 707 1 263M S S Q L-d b n u m c o l s4 708 1 264M S S Q L-d b n u m r e t s4 709 1 265M S S Q L-d b o p e n4 710 1 266M S S Q L-d b r e s u l t s4 711 1 267M S S Q L-d b r e t d a t a4 712 1 268M S S Q L-d b r e t l e n4 713 1 269M S S Q L-d b r e t s t a t u s4 714 1 26A M S S Q L-d b r p c i n i t4 715 1 26B M S S Q L-d b r p c p a r a m4 716 1 26C M S S Q L-d b r p c s e n d4 717 1 26D M S S Q L-d b s e t l o g i n t i m e4 718 1 26E M S S Q L-d b s e t m a x p r o c s4 719 1 26F M S S Q L-d b s e t o p t4 720 1 270M S S Q L-d b s e t t i m e4 721 1 271M S S Q L-d b s q l e x e c4 722 1 272M S S Q L-d b s q l o k4 723 1 273M S S Q L-d b s q l s e n d4 724 1 274M S S Q L-d b t x p t r(续)错误代码简短描述十进制十六进制4 725 1 275M S S Q L-d b t x t i m e s t a m p4 726 1 276M S S Q L-d b t x t s n e w v a l4 727 1 277M S S Q L-d b u s e4 728 1 278M S S Q L-d b w i n e x i t4 729 1 279M S S Q L-d b w r i t e t e x t4 738 1 282O D B C-S Q L A l l o c C o n n e c t4 739 1 283O D B C-S Q L A l l o c E n v4 740 1 284O D B C-S Q L A l l o c S t m t4 741 1 285O D B C-S Q L B i n d C o l4 742 1 286O D B C-S Q L B i n d P a r a m e t e r4 743 1 287O D B C-S Q L C a n c e l4 744 1 288O D B C-S Q L C o l u m n s4 745 1 289O D B C-S Q L C o n n e c t4 746 1 28A O D B C-S Q L D a t a S o u r c e s4 747 1 28B O D B C-S Q L D e s c r i b e C o l4 748 1 28C O D B C-S Q L D i s c o n n e c t4 750 1 28E O D B C-S Q L E r r o r4 751 1 28F O D B C-S Q L E x e c D i r e c t4 752 1 290O D B C-S Q L E x e t e n d e d F e t c h4 753 1 291O D B C-S Q L F e t c h4 754 1 292O D B C-S Q L F r e e C o n n e c t4 755 1 293O D B C-S Q L F r e e E n v4 756 1 294O D B C-S Q L F r e e S t m t4 757 1 295O D B C-S Q L G e t C o n n e c t O p t i o n4 758 1 296O D B C-S Q L G e t C u r s o r N a m e4 760 1 298O D B C-S Q L G e t F u n c t i o n s4 761 1 299O D B C-S Q L G e t I n f o4 762 1 29A O D B C-S Q L G e t T y p e I n f o4 763 1 29B O D B C-S Q L N u m R e s u l t C o l s4 764 1 29C O D B C-S Q L P r o c e d u r e s4 765 1 29D O D B C-S Q L P r o c e d u r e C o l u m n s4 766 1 29E O D B C-S Q L R o w C o u n t4 767 1 29F O D B C-S Q L S e t C o n n e c t O p t i o n4 768 1 2A0O D B C-S Q L S e t C u r s o r N a m e4 769 1 2A1O D B C-S Q L S e t P a r a m4 770 1 2A2O D B C-S Q L S e t S t m t O p t i o n4 771 1 2A3O D B C-S Q L S t a t i s t i c s4 772 1 2A4O D B C-S Q L Ta b l e s4 773 1 2A5O D B C-S Q L Tr a n s a c t4 788 1 2B4S Y B A S E-d b b i n d4 789 1 2B5S Y B A S E-d b c m d4 790 1 2B6S Y B A S E-d b c a n c e l4 791 1 2B7S Y B A S E-d b c l o s e4 792 1 2B8S Y B A S E-d b c o l l e n(续)错误代码简短描述十进制十六进制4 793 1 2B9S Y B A S E-d b c o l n a m e4 794 1 2B A S Y B A S E-d b c o l t y p e4 795 1 2B B S Y B A S E-d b c o n v e r t4 796 1 2B C S Y B A S E-d b p o l l4 797 1 2B D S Y B A S E-d b d a t l e n4 798 1 2B E S Y B A S E-d b e r r h a n d l e4 799 1 2B F S Y B A S E-d b f r e e b u f4 800 1 2C0S Y B A S E-d b l o g i n f r e e4 801 1 2C1S Y B A S E-d b h a s r e t s t a t4 802 1 2C2S Y B A S E-d b i n i t4 803 1 2C3S Y B A S E-d b l o g i n4 804 1 2C4S Y B A S E-d b m o r e t e x t4 805 1 2C5S Y B A S E-d b m s g h a n d l e4 806 1 2C6S Y B A S E-d b n e x t r o w4 807 1 2C7S Y B A S E-d b n u m c o l s4 808 1 2C8S Y B A S E-d b n u m r e t s4 809 1 2C9S Y B A S E-d b o p e n4 810 1 2C A S Y B A S E-d b r e s u l t s4 811 1 2C B S Y B A S E-d b r e t d a t a4 812 1 2C C S Y B A S E-d b r e t l e n4 813 1 2C D S Y B A S E-d b r e t s t a t u s4 814 1 2C E S Y B A S E-d b r p c i n i t4 815 1 2C F S Y B A S E-d b r p c p a r a m4 816 1 2D0S Y B A S E-d b r p c s e n d4 817 1 2D1S Y B A S E-d b s e t l o g i n t i m e4 818 1 2D2S Y B A S E-d b s e t m a x p r o c s4 819 1 2D3S Y B A S E-d b s e t o p t4 820 1 2D4S Y B A S E-d b s e t t i m e4 821 1 2D5S Y B A S E-d b s q l e x e c4 822 1 2D6S Y B A S E-d b s q l o k4 823 1 2D7S Y B A S E-d b s q l s e n d4 824 1 2D8S Y B A S E-d b t x p t r4 825 1 2D9S Y B A S E-d b t x t i m e s t a m p4 826 1 2D A S Y B A S E-d b t x t s n e w v a l4 827 1 2D B S Y B A S E-d b u s e4 828 1 2D C S Y B A S E-d b w i n e x i t4 829 1 2D D S Y B A S E-d b w r i t e t e x t4 830 1 2D E S Y B A S E-d b c o u n t4 831 1 2D F S Y B A S E-d b d e a d4 942 1 34E未映射的S Q L错误代码8 449 2 101无法打开一个系统文件8 450 2 102一个系统文件出现I /O错误8 451 2 103数据结构破坏8 452 2 104无法找到B D E配置文件(续)错误代码简短描述十进制十六进制8 453 2 105无法写B D E配置文件8 454 2 106无法用不同的配置文件初始化8 455 2 107系统被非法进入8 456 2 108无法定位I D A P I32.D L L8 457 2 109无法装载I D A P I32.D L L8 458 2 10A无法装载一个I D A P I服务库8 459 2 10B无法创建或打开临时文件8 705 2 201在表的开头8 706 2 202在表的末尾8 707 2 203由于键值已变,记录被移走8 708 2 204记录/主键被删除8 709 2 205没有当前记录8 710 2 206无法找到记录8 711 2 207 B L O B的末尾8 712 2 208无法找到对象8 713 2 209无法找到家族成员8 714 2 20A B L O B文件丢失8 715 2 20B无法找到语言驱动程序8 961 2 301表/索引头坏8 962 2 302文件坏8 963 2 303M e m o/B L O B文件坏8 965 2 305索引坏8 966 2 306锁定文件坏8 967 2 307家族文件坏8 968 2 308.VA L文件坏或丢失8 969 2 309外来的索引文件格式9 217 2 401读失败9 218 2 402写失败9 219 2 403无法访问目录9 220 2 404文件删除操作失败9 221 2 405无法访问文件9 222 2 406由于错误无法访问表9 473 2 501内存不够9 474 2 502文件句柄不够9 475 2 503磁盘空间不够9 476 2 504临时表太多了9 477 2 505记录的长度太大了9 478 2 506打开了太多的游标9 479 2 507表已满9 480 2 508这个工作站打开了太多的会话9 481 2 509序号限制( P a r a d o x)9 482 2 50A某些内部限制9 483 2 50B打开了太多的表9 484 2 50C每个表打开了太多的游标(续)错误代码简短描述十进制十六进制9 485 2 50D锁定了太多的记录9 486 2 50E太多的客户9 487 2 50F太多的索引9 488 2 510太多的会话9 489 2 511打开了太多的数据库9 490 2 512太多的口令9 491 2 513太多的活动驱动程序9 492 2 514太多的字段9 493 2 515锁定了太多的表9 494 2 516打开了太多的B L O B9 495 2 517锁定文件太大9 496 2 518打开了太多的查询9 498 2 51A太多的B L O B9 499 2 51B对Paradox 5.0来说,文件名太长9 500 2 51C太多的行9 501 2 51D不允许长文件名9 729 2 601违反主键9 730 2 602最小值校验失败9 731 2 603最大值校验失败9 732 2 604字段需要有值9 733 2 605主记录丢失9 734 2 606由于有明细记录,无法删除或修改主记录9 735 2 607主表不正确9 736 2 608字段值超出了L o o k u p表范围9 737 2 609L o o k u p表打开失败9 738 2 60A明细表打开失败9 739 2 60B主表打开失败9 740 2 60C字段是空的9 741 2 60D与主表的链接已建立9 742 2 60E主表已打开9 743 2 60F明细表已存在9 744 2 610主记录有明细记录,无法清空9 745 2 611自引用完整性必须在表中没有其他改变时引入9 746 2 612明细表已打开9 747 2 613这个主表不能成为另一个表的明细表,如果它的明细表不为空的话9 748 2 614引用完整性字段必须被列入索引9 749 2 615这个表需要口令才能打开9 750 2 616字段不能同时链接几个主表9 985 2 701数字超出范围9 986 2 702非法的参数9 987 2 703非法的文件名9 988 2 704文件不存在9 989 2 705非法的选项9 990 2 706非法的函数(续)错误代码简短描述十进制十六进制9 991 2 707未知的表类型9 992 2 708无法打开文件9 993 2 709无法重新定义主键9 994 2 70A无法修改9 995 2 70B外来的键值与主键不匹配9 996 2 70C非法的修改9 997 2 70D索引不存在9 998 2 70E非法的偏移量9 999 2 70F非法的描述编号1 00002 710非法的字段类型1 00012 711非法的字段描述符1 0002 2 712非法的字段转换1 00032 713非法的记录结构1 00042 714非法的描述符1 00052 715非法的数组1 00062 716非法的数组校验1 00072 717非法的数组引用1 00082 718非法的表顺序1 00092 719名称不是唯一的1 00102 71A需要给出索引名称1 00112 71B非法的会话句柄1 0012 2 71C非法的重构操作1 00132 71D未知的驱动程序1 00142 71E未知的数据库1 00152 71F非法的口令1 00162 720没有回调函数1 00172 721非法的回调缓冲区长度1 00182 722非法的目录1 00192 723转换错误:值超出边界1 00202 724无法把一个表的游标设给另一个表1 00212 725书签与表不匹配1 0022 2 726非法的索引/标记名称1 00232 727非法的索引描述符1 00242 728表不存在1 00252 729表的用户太多1 00262 72A无法计算键值或者没有传递过滤条件1 00272 72B索引已存在1 00282 72C索引已打开1 00292 72D非法的B L O B长度1 00302 72E记录缓冲区中的B L O B句柄是非法的1 00312 72F表已打开1 0032 2 730表需要重构1 00332 731非法的模式1 00342 732无法关闭的索引(续)错误代码简短描述十进制十六进制1 00352 733索引正在用于排序1 00362 734未知的用户名或口令1 00372 735不支持多重层叠1 00382 736非法的字段名1 00392 737非法的表名1 00402 738非法的链接游标表达式1 00412 739名称是保留的1 0042 2 73A非法的文件扩展名1 00432 73B非法的语言驱动程序1 00442 73C别名目前没有打开1 00452 73D不兼容的记录结构1 00462 73E名称是D O S中保留的1 00472 73F目标必须已建立索引1 00482 740非法的索引类型1 00492 741表的语言驱动程序与索引不匹配1 00502 742过滤器句柄是非法的1 00512 743非法的过滤器1 0052 2 744创建表的请求是非法的1 00532 745删除表的请求是非法的1 00542 746创建索引的请求是非法的1 00552 747删除索引的请求是非法的1 00562 748非法的表1 00582 74A非法的时间1 00592 74B非法的日期1 00602 74C非法的日期时间1 00612 74D位于不同目录中的表1 0062 2 74E参数的个数不匹配1 00632 74F服务库中没有找到这个函数1 00642 750必须使用基序1 00652 751非法的过程名1 00662 752字段映射是非法的1 02412 801记录被另一个用户锁定1 0242 2 802解锁失败1 02432 803表正忙1 02442 804目录正忙1 02452 805文件被锁定1 02462 806目录被锁定1 02472 807记录已经被这个会话期锁定1 02482 808对象未锁定1 02492 809锁定超时1 02502 80A主键被锁定1 02512 80B表的锁定丢失1 0252 2 80C独占访问丢失1 02532 80D表不能独占错误代码简短描述十进制十六进制1 02542 80E记录的锁定冲突1 02552 80F检测到有死锁1 02562 810一个事务正在处理当中1 02572 811当前没有处理事务1 02582 812记录锁定失败1 02592 813无法编辑,因为另一个用户已经修改了记录1 02602 814无法编辑,因为另一个用户已经删除或移走了记录1 0497 2 901这个操作需要字段权限1 04982 902这个操作需要口令1 04992 903这个操作需要家族权限1 05002 904这个目录是只读的1 05012 905数据库是只读的1 0502 2 906试图修改只读的字段1 05032 907不支持加密的d B A S E表1 05042 908这个操作需要S Q L权限1 07532 A01这个字段不是B L O B1 07542 A02 B L O B已打开1 07552 A03 B L O B没有打开1 07562 A04操作不适用1 07572 A05表没有建立索引1 07582 A06引擎未初始化1 07592 A07试图重新初始化引擎1 07602 A08试图混淆不同会话期的对象1 07612 A09P a r a d o x驱动程序未激活1 0762 2 A0A驱动程序未调入1 07632 A0B表是只读的1 07642 A0C没有索引1 07652 A0D表未打开,无法进入这个操作1 07662 A0E表不支持这个操作1 07672 A0F索引是只读的1 07682 A10表不支持这个操作,因为它没有建立索引1 07692 A11只能针对当前会话期进行这个操作1 07702 A12关键字使用不当1 07712 A13另一个语句正在使用连接1 0772 2 A14直通S Q L连接必须被共享11 009 2 B01非法的函数编号11 010 2 B02文件或目录不存在11 011 2 B03路径未找到11 012 2 B04打开了太多的文件。
PV Link
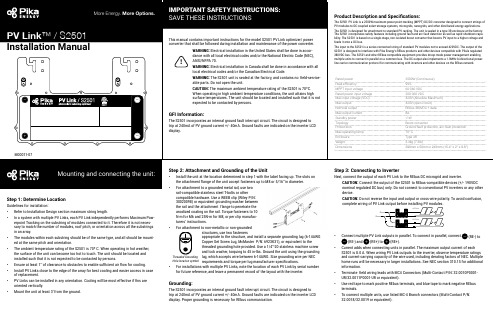
Step 1: Determine LocationGuidelines for installation:• Refer to Installation Design section maximum string length.• In a system with multiple PV Links, each PV Link independently performs Maximum Pow-erpoint Tracking on the substring of modules connected to it. Therefore it is not neces-sary to match the number of modules, roof pitch, or orientation across all the substrings in an array.• The modules within each substring should be of the same type, and all should be mount-ed at the same pitch and orientation.• The ambient temperature rating of the S2501 is 70º C. When operating in hot weather,the surface of the unit can become too hot to touch. The unit should be located and installed such that it is not expected to be contacted by persons.• Ensure at least 1” of clearance to obstacles to enable sufficient air flow for cooling.• Install PV Links close to the edge of the array for best cooling and easier access in caseof replacement.• PV Links can be installed in any orientation. Cooling will be most effective if fins areoriented vertically.• Mount the unit at least 3’ from the ground.rail-compatible stainless steel T-bolts or other compatible hardware. Use a WEEB clip (Wiley P/N: 30020098) or equivalent grounding washer between the rail and the attachment flange to penetrate the anodized coating on the rail. Torque fasteners to 10 N-m for M6 and 25N-m for M8, or per clip manufac-turers’ instructions.• For attachment to non-metallic or non-groundedstructures, use two fastenersappropriate to the structure, and install a separate grounding lug (6-14AWG Copper Set Screw Lug, McMaster P/N: 6923K31), or equivalent to the threaded grounding hole provided. Use a 1/4”-20 stainless machine screw and lock washer, torquing to 45 in-lbs. Ground the unit using the groundinglug, which accepts wire between 6-14AWG. Size grounding wire per NEC requirements and torque per lug manufacturer specifications.• For installations with multiple PV Links, note the location of each PV Link by serial numberfor future reference, and leave a permanent record of the layout with the inverter.Grounding:The S2501 incorporates an internal ground fault interrupt circuit. The circuit is designed to trip at 240mA of PV ground current +/- 40mA. Ground faults are indicated on the inverter LCD display. Proper grounding is necessary for REbus communication.device.CAUTION: Do not reverse the input and output or cross-wire polarity. To avoid confusion, complete wiring of PV Link output before installing PV modules.• Connect multiple PV Link outputs in parallel. To connect in parallel, connect (RE-) to (RE-) and (RE+) to (RE+).•Current adds when connecting units in parallel. The maximum output current of each S2501 is 8.0 A. When wiring PV Link outputs to the inverter, observe temperature ratings and current-carrying capacity of the wire used, including derating factors of NEC. Multiple home runs will be necessary in larger installations. See NEC section 310.15 for additional information.• Terminate field wiring leads with MC4 Connectors (Multi-Contact P/N: 32.0010P0001-UR/32.0011P0001-UR or equivalent).• Use red tape to mark positive REbus terminals, and blue tape to mark negative REbus terminals.•To connect multiple units, use listed MC-4 Branch connectors (Multi-Contact P/N:32.0018/32.0019 or equivalent).Threaded Grounding Hole location symbol REbus380VDC OUTPUTPVSUBSTRIN INPUTWARNING: ELECTRIC SHOCK HAZARD - THE DC CONDUCTORS OF THISPHOTOVOL TAIC SYSTEM ARE UNGROUNDED AND MAY BE ENERGIZED. ELECTRIC SHOCKHAZARD - DC OUTPUT CONDUCTORS MAY BE ENERGIZED REGARDLESS OF SUN EXPOSURE.CAUTION: RISK OF ELECTRIC SHOCK - WHEN THE PHOTOVOL TAIC ARRAY ISEXPOSED TO LIGHT, IT SUPPLIES A DC VOL TAGE TO EQUIPMENT. COVER PV MODULE INOPAQUE MATERIAL BEFORE CONNECTING OR DISCONNECTING THIS OPTIMIZER. DURING FAUL T, ZERO CURRENT IS SOURCED INTO DC ARRAY BY THIS CONVERTER. INSTALL IN。
教你如何使用淘宝助理,新手必看!
教你如何使用淘宝助理,新手必看!《一》如何下载淘宝助理?首先,在浏览器的地址栏内输入/tbassistant/点击“下载淘宝助理”按钮,点击保存,将执行文件下载到本地机器上。
然后双击安装文件,并点击运行(这里需要提醒一下的是,淘宝助理请尽量从淘宝网上下载,因为在其他网站下载,不排除带有病毒或者木马的风险):开始进入安装向导,点击“下一步”:点击“我接受”许可协议:接下来选择安装目录,您可以点击“浏览”修改安装目录。
默认的路径是:C:\Program Files\淘宝网\淘宝助理\ ,点击“安装”:开始进入程序安装过程,请耐心等待几秒钟:程序安装完毕,点击“完成”,整个安装过程结束。
最后会在您的桌面上生成这样的图标,是不是很像一顶神奇的魔法帽:想知道如何使用它吗?别着急,让我们接下来看看它的神奇之处。
《二》使用淘宝助理上传宝贝时出现错误,如何处理如您在更新淘宝助理或上传宝贝时出错,请先判断是否是以下错误提示:1、错误号: ERR_WEBSERVICE_ERROR错误描述: Web service hresult error!, hr = 0x80004005.附加描述: 未指定的错误文件名: \WebKiss.cpp如是上述错误提示,您可以通过以下方法解决:下载安装最新的淘宝助理客户端,淘宝助理的地址:/help/wangwang/wangwang_0628_05.ph p,打开此页面后选择“下载淘宝助理”。
2、错误号: INETERR_SEND_REQUESTEX错误描述: Sending extended request failed. system errcode: 12019. 附加描述: 要求操作句柄的状态错误文件名: .\InternetProtocols.cpp行号: 809或者:error code:ineterr send requestexerror desc:sending extended request failed system errode:12029 extra edsc:无法与服务器建立连接filename:internet protocol.cppline number:809如是上述错误提示,您可以通过以下方法解决:1、打开淘宝助理安装目录下的configure目录,打开文件名为network.ini的文件,把ServerUrl=https:///member/login.jhtml改为ServerUrl=/member/login.jhtml2、如您按照上述方式操作无效,请您查看您所使用的防火墙是否限制了淘宝助理的相关操作。
dberr

CatalogDB: 16:14:43 2016/2/2: catdbsvc.cpp at line #3001 encountered error 0x00000570
Catalogt line #3001 encountered error 0x00000570
CatalogDB: 16:14:40 2016/2/2: catdbcli.cpp at line #606 encountered error 0x00000570
CatalogDB: 16:14:40 2016/2/2: catdbsvc.cpp at line #7326 encountered error 0x00000570
CatalogDB: 16:14:40 2016/2/2: catdbsvc.cpp at line #3761 encountered error 0x00000570
CatalogDB: 16:14:42 2016/2/2: catdbsvc.cpp at line #2029 encountered error 0x00000570
CatalogDB: 16:14:42 2016/2/2: catdbsvc.cpp at line #2146 encountered error 0x00000570
CatalogDB: 16:14:40 2016/2/2: catadnew.cpp at line #1942 encountered error 0x00000570
CatalogDB: 16:14:40 2016/2/2: catadnew.cpp at line #951 encountered error 0x00000570
电脑系统盘windowsSystem32 下文件夹详解

电脑系统盘windows/System32 下文件夹详解system32 文件夹中包含了大量的用于 Windows 的文件. 这里主要用于存储DLL 文件, 控制面板小程序(.CPL), 设备驱动 (.drv), 帮助文件 (.hlp和 .cnt), MS-DOS 工具 (.com), 语言支持文件 (.nls), 屏幕保护 (.scr),安装信息文件 (.inf), 以及其它用于支持, 配置, 或操作的文件.-------------------------------------------------------C:\WINDOWS\system32com_dmi我把这个文件夹删掉了.C:\WINDOWS\system3225, 1028, 1031, 1033, 1037, 1041, 1053, 2052 ,3076 我把其中的空文件夹都删掉了. 1033 (英语). 2052 (简体中文).这些以数字命名的文件夹中包含了本地化语言文件. 其中大多数文件夹都可能是空的.据 Microsoft 说: 用于指定语言的本地化 (语言) 文件, 按照数字指派到对应的文件夹中. 除非 Windows 被本地化为特定的语言, 否则其它不对应的文件夹就是空的.-------------------------------------------------------C:\WINDOWS\system32\CatRoot和C:\WINDOWS\system32\CatRoot2CatRoot文件夹中包含了安全编录文件.CatRoot2 文件夹中包含了编录数据库文件.你也许能够删除这两个文件夹以及其中的内容. 这个就取决于你的系统了.当你安装某些第三方程序时, 可能会需要某些特定的 .CAT 文件存在. 这些 .CAT 存在于以下文件夹中:C:\WINDOWS\system32\CatRoot\有些人可以将其删除而不出现任何问题. 而其它人就不行.在我的系统上, 我发现, 使用 Acronis True Image 的浏览磁盘镜像的功能时, 需要某些 .CAT 文件. 如果不存在, 那么就会弹出一个Windows 硬件安装窗口, 它会告诉你 "你为以下硬件所安装的软件: 通用卷没有通过Windows 标识测试,(用来验证它与 Windows 的兼容性)...等等."如果我选择继续, 那么就会弹出对话框, 说 "无法为分区指派盘符."简而言之, Acronis True Image 的浏览磁盘镜像功能离不开特定的 .CAT 文件. 你所安装的某些第三方程序可能会依赖于某些特定的 .CAT文件.我还发现在我的系统上需要以下两个 .CAT 文件存在:"oemO.CAT" 和 "1.CAT".当 oemO.CAT 和 1.CAT 不存在时, "dberr.txt" 中就会出现错误记录, 其存在于 C:\WINDOWS\system32\CatRoot2 中.我注意到, 当我打开设备管理器中的设备属性时就会出现这些错误, 并且当我使用 Acronis True Image 的浏览镜像功能时也会出现这些错误.我偶尔也会在 dberr.txt 中看到其它的 .CAT 错误: FP4.CAT, IMS.CAT,MSMSGS.CAT, msn7.cat, msn9.cat, MSTSWEB.CAT, NTPRINT.CAT, SP2.CAT, startoc.cat 和 wmerrenu.cat.在我的系统中有这么多的 .CAT 文件, 很难确定哪些 .CAT 文件可被删除.我只是把所有的 Hotfix .CAT 文件 (KB*.* files) 删掉了. 你可以通过Hotfix 号码将其识别出来.以下是一些你可以做的东西, 只要你愿意...把所有的 .CAT 文件放置到一个别的文件夹中. 周期性地检查C:\WINDOWS\system32\CatRoot2 中的 "dberr.txt". 查看是否有缺失 .cat 文件的错误信息. 然后把有提示的 .CAT 文件放回到C:\WINDOWS\system32\CatRoot\ 文件夹中当你把所有所需的 .CAT 文件放回原位之后, "dberr.txt" 就会停止显示错误了.dberr.txt..........关于编录文件注册情况的日志文件. 包含了未注册编录文件的相关信息, 并且只有当识别出未注册的编录时才会存在.缺失编录文件时也会产生 dberr.txt.关于 CatRoot2 文件夹, 我一般都是用文件清理工具删除其中的某些垃圾文件, 而不是删除整个文件夹. CatRoot2 文件夹中产生的文件都是临时文件. 其扩展名为 *.chk, *. emb, *log, 以及 *.txt.-------------------------------------------------------C:\WINDOWS\system32\Com组件对象模型 (COM) 组件.我把这个文件夹以及其中的内容都删掉了.然后打开“控制面板” -> “管理工具”, 把其中的“组件服务” 快捷方式删.顺便, 我还会把用不到的 "数据源 (ODBC)" 快捷方式删掉.C:\WINDOWS\system32\config包含了用于引导的注册表储备, 还有可通过事件查看器查看的系统, 安全以及应用程序日志文件.我把所有能删的文件都删掉了. 有些文件, Windows 是不会让你删的. 它们是你的注册表实体.其它的文件都可以删掉, 且不会引起任何问题.以下是 13 个重要的文件:AppEvent.Evtdefaultdefault.LOGSAMSAM.LOGSecEvent.EvtSECURITYSECURITY.LOGsoftwaresoftware.LOGSysEvent.Evtsystemsystem.LOGC:\WINDOWS\system32\config\systemprofile我把这个文件夹以及其中的内容都删掉了.这个文件夹中包含了一个用于本地系统的标准配置文件.我发现, 要在安全模式下才能彻底地删掉这个文件夹.systemprofile 文件夹本身, 以及其中的一些空文件夹, 有可能会自动重新出现.这是那些古怪的文件夹中的一个. 有些时候将其删除之后, 就不会重新出现了. 而有时重装系统之后, 将其删除, 它又可能会莫名其妙地重新出现. (真是受打击...)==(C:\WINDOWS\system32\dhcp我把这个文件夹删掉了.这个文件夹一般是空的, 如果你想让主机作为一台 DHCP 服务器, 那么这个文件夹就会用于保存动态主机配置协议 (DHCP) 数据库文件.)==此段话不正确.因为==(路由器给你提供网络通道。
B、dB、dBm、dBi、dBd、dBc的含义与区别

在谈到天线增益的时候,会有方向性增益和功率增益的区分,它们是通过辐射效率相互联系 的,方向性增益总是大于功率增益的,并与天线波束宽度有密切关系。
天线方向图可以看出在空间不同方向有大小不同的增益,我们常说的“天线增益”通常是指产 生最大增益方向上的增益,单位为dBi或者dBd。这二个单位的参考基准不同,前者是以各 向同性天线(isotropic antenna)为基准,后者是以偶极子天线(dipole antenna)为基准。偶极 子天线的增益:
PingWest品玩 · 今天 07:23
2
日媒:华为有望赶超苹果跃居第二大手机供货商
环球网 · 今天 14:31
1
又一批假蜂蜜被查封,赴深山调查,终于揭开蜂蜜惊天骗局,引发国人震怒!
广告 · 今天 16:14
铅笔道pencilnews · 今天 12:26
163
美女总裁的窝囊废未婚夫,竟是雇佣兵中的顶尖高手
广告 · 今天 16:14
英伟达股价持续下跌,“人工智能第一股”仍待反弹
时代财经 · 今天 07:37
4
LG 加入苹果英特尔阵营,支持韩国对高通的反垄断罚款
站长之家 · 今天 08:49
36
特斯拉再推车主引荐计划 未试驾下单可获3月免费充电
1W=1000mW=30dBm=0dBW 更一般的对数关系
在雷达通信电子战领域,你会经常看到或听到这些词,例如天线增益、放大器增益、线缆衰 减、传播损耗等等,那么它们有啥联系与区别呢? 增益与衰减(dB) 先看大器增益或线缆衰减,这是大家一看就知道其所表示的是一个功率比,用输出的功率比 输入的功率,如果大于1就是正的dB值,也就是放大了;如果小于1就是负的dB值,也就是 说衰减了或者说是损耗了,很好理解。 天线增益(dB)与dBi/dBd/dBc 通常所说的天线发射或接收信号的能力是用参照全向天线的分贝数(dBi)来表示的。比如说 天线增益有10dBi不是说这副天线能把信号的功率放大10倍,而是意味着通过控制信号发射 的角度,将功率集中到一定的方向上。 在输入功率相等的情况下,天线增益是指实际天线和全向天线在空间同一点处的功率密度之 比,描述的是天线将功率集中辐射的程度,因此与天线方向图密切相关。一般来说,天线方 向图主瓣越窄、副瓣越小,则增益越高。
dberr

CatalogDB: 8:17:09 2013/1/9: DONE Adding Catalog File: Package_for_KB2778930_SP1~31bf3856ad364e35~x86~~6.1.1.0.cat
CatalogDB: 11:41:01 2013/1/9: Adding Catalog File: Package_for_KB2736422~31bf3856ad364e35~x86~~6.1.1.0.cat
CatalogDB: 11:41:01 2013/1/9: DONE Adding Catalog File: Package_for_KB2736422~31bf3856ad364e35~x86~~6.1.1.0.cat
CatalogDB: 8:17:31 2013/1/9: Adding Catalog File: Package_for_KB2785220_SP1~31bf3856ad364e35~x86~~6.1.1.0.cat
CatalogDB: 8:17:32 2013/1/9: DONE Adding Catalog File: Package_for_KB2785220_SP1~31bf3856ad364e35~x86~~6.1.1.0.cat
CatalogDB: 13:43:29 2012/12/15: catadnew.cpp at line #1197 encountered error 0x00000057
flexible working arrangement

In current high speed developing society, flexibility in work has become a significant concern for managers due to the feasibility and practicability of it (Houseman, 2001:151). Flexible working ar-rangements (FWAs) include, such as ‘flexitime, term time working, part-time or reduced hours, job sharing, career breaks, family-related and other leaves, compressed workweeks and teleworking’(Lewis, 2003:2). This definition showed that FWAs are modern working styles that diverge from traditional working hours and spaces(work 8 hours a day, 40 hours a week in office). Given the practical nature of FWAs, new world organisations considered that it might be a practicality strate-gy to reform the formalist working style (DBERR, 2007:3). On the other hand, for those employees who work at irregular time or without supervisor and colleagues, the significant drawbacks might be the uncertainty of task quality and lack of team spirit (Maitlan and Thomson, 2011:94). There-fore, this essay will explore both positive and negative aspects of flexible working arrangements. It will consider two patterns of FWAs, flexitime and various working places, so as to critically ex-plore the mutual advantages of FWAs for both employers and employees.Given the urgent need for talent and skills, many organisations are worried about the challenge they face in keeping employees motivated and committed due to the less productivity may result from these. (Lewis, 2003:2). A feasible free-time working schedule is, to a certain extent, a practical strategy to solve this problem. To give an example, the majority employees (71%) in Microsoft in the US said they were more productive when they controlled over starting and finishing working times (Maitland and Thomson, 2011:155). In addition, according to Lewis (2001:15), when people are trusted in their time controlling, they will feel more stimulated in their works and suffer fewer distractions from the monotonous office time so as to achieve the productivity rising goal. Further-more, as Kelliher and Anderson (2009:85) mention, a simple method for organisations to inspire the workers is arranging a staff-schedule which depends on individual aspirations. This means that they can follow a timetable which is more suitable for their habits or life styles (Allen, 2001:417). For example, some administrative staff work part of the time and do shifts so they come in and leave the office at different times. To be detailed, three admin assistants in an accounting office do a rotating schedule according to their own conditions, each working a compressed week(four 10-hour days) every third week, while the other two do normal eight-hour days (Mailtand and Thomas, 2011:62). This flexible working pattern not only benefited them but also provided extended cover for the partners. In this case, due to the working time used efficiently, regular employees can be less stressed from work and attain better performance in their job (Houseman, 2001: 151). As a result, not only for inspiring the worker to do better, this will also improve the production and benefit their company because of staff’s promoted productivity. This means that flexitime in work will help em-ployees to reach a higher level of work achievement and in return of higher profit for the company as well. In other words, simply having greater autonomy over one’s working time can boost effi-ciency for both staffs and companies.Traditional working time is form 9am to 5pm, Monday to Friday, whereas, flexitime employees work are under unstable working schedule. Therefore, this topic has been debated for decades due to the uncertainty working time which may lead to an undermined attitudes to employees’ job and unfair work loads to different timetable owners (Lewis, 2003: 3). For instance, in traditional general service posts, such as clerical and related workers, instead of inspired, they may tend to disobedi-ence working guideline of institutions, such as tardiness, due to no limitation in working time (Ressler and Thompson, 2011:24). Moreover, a disagreement between the staff and the managers will occur when loads of tasks are hit in a day, and there are a few workers scheduled while the rest of the team may have their leisure time at that time (Semler, 2003: 56). Since the urgent conditions for special firms, such as law firms and translation companies, may difficult to predict, introducing a results measurement system into a conventional management culture is unlikely to have much im-pact (Allen, 2001:425).It is true that the unlimited deadline may lead to a lower concentration on working, and the variety employee timetables may result in a complexity of management. Nevertheless, a two-year study of formal and informal flexibility in seven large UK-based companies found that a pure results-only system relies on a relationship of trust between a manager and employee (Dex and Scheibl, 2001:422). It is based on the belief that when people are given a clear goal to achieve in a support-ive environment, they will be motivated to do so without having to be monitored, supervised or forced (ibid:425). It assumes that most people will make better use of the freedom to manage their own work, and they will prefer to achieve the best results (Maitland and Thomson, 2011:42). When it comes to centre staff, they have no choice over the location of their work, but they have a degree of flexibility over timing: they work in shifts that are self-rostered, with management guidance when needed (Fagan, 2011:256).From a strategic perspective, organisations have redesigned their organisational structures to the emergent demand of work-life balancing and increase the interests of the company in recent de-cades. They put another type of FWAs, flexible working place, into effect, which can provide a wide range of benefits for business and people, including cost savings, increased speed to market, productivity gains and improved employee morale (Houseman, 2001; Gibson, 2003; Maitland and Thomson, 2011; Kelliher and Anderson, 2009). For example, an US national accounting firm givesits employees a freedom to work at where they prefer to, then moved its New York office from a famous avenue to a smaller work pace. It was able to cut the space per person by 20 percent and achieve projected cost savings of $1.5m to $2m a year by encouraging teleworking (Maitland and Thomas, 2011:62). The CEO of this organisation has said that instead of demanding for his working and travelling time, he has enhanced his ability to work at home and also enjoying a rewarding per-sonal life with his wife and family (ibid, 2011:62). Furthermore, flexible working location can ben-efit the employees to enhance their relationship with children and parents, especially for middle-aged adults. Hayward and Fong (2007:5) have conducted a study in 2007 to present the work-life balance and it was found that almost all (99 per cent) staff in British workplace in favour of the working arrangement with regular office off for looking after their children or parents; 85 per cent would like to handle with their ordinary emergency. If parents’ special requirements can be fulfilled by unlimited working space arrangement, they will able to suffer fewer distractions from office in-terruptions or the stresses of commuting, and this will improve their life satisfaction rating as well (Dex and Scheibl, 2001: 420). Consequently, them are able to achieve the companies’ productivity rising goals.Nonetheless, a common concern about new work styles is the suffering of team spirit which will be a stumbling block to the development of a company. In a conventional workplace, people sit to-gether and exchange ideas. By virtue of sitting together, a team spirit is born, in the new world of work, however, this team building is at risk (Miller, 2014:161). According to Gibson (2003: 14), managers discover that there is hardly ever a time when all their people are together, whether virtu-ally or in a physical office. For people who see their colleagues once a week instead of every work-ing day, there is an increasing chance that remote working, and virtual teamwork across space zones mean that some people rarely see the rest of the team. Apart from the former issue, informal com-munications between team members can be a crucial topic for managers to recognise. This is be-cause that the group cohesiveness decreasing will result in a decline in cohesion and unity into the company which will damage the core competition of the company (Lewis, 2003:13).In fact, the modern working markets has their new rules to help workers to get rid of the traditional working style and ensure them to adopt the new ones. The arrangement of team meetings, monthly and weekly even daily, can provide a communication of the latest business information and gather people to discuss their ideas (Semler, 2003:156). While another strategy, face-to-face meetings, are used for individuals and teams who spend most of their time working remotely (Maitland and Thompson, 2011:153). More formal team building exercises have their place and can gain real re-wards in terms of improved collaboration, especially if people are dispersed across different coun-tries and only meet rarely (Bruyne and Beijier, 2015:126). Moreover, there are a great deal of tech-nologies available to achieve the desired results without taking up people’s place and energy to at-tend a meeting room, from simple text solutions such as Instant Messaging to sophisticated Virtual Presence conferencing systems (Miller, 2014:164). The instant contact between dispersive employ-ees can consequent on a cohesive and connected bond in company which can achieve a stronger market competition in the future (Lewis, 2003:16).Above all, in spite of the limitations which may restrict the implement of FWAs, such as managers’fears about productivity may threatening employment, the pros outweigh its cons. The flexitime can motivate employees to achieve a higher efficiency which can ensure the success of the company; the unlimited work place can provide employees a positive work environment which can balance the relationship between job and family, and also can reach the goals of less expense and higher ambitious for the companies. Under a flexible working system, employees will have a more con-venient lift style because they are not subject to time and space limits, and the employer is not obliged to remunerate overtime and office rental fee. In short, the positive factors in terms of effi-ciency and convenient life style for employees, the more profit and increasing computation for companies will be meet by the use of FWAs. It can be summarised that although this new working style may have some possible risks, the FWAs has be regarded as an appropriate solution to benefit both employees and employers.word count: 1766ReferenceAllen, T. D. (2001). Family-supportive Work Environments: The Role of Organisational Percep-tions. Journal of Vocational Behaviour, 58 (1), 414-435.Bruyne, E. D. and Beijier, M. (2015). Calculating NWoW office space with the PACT model. Jour-nal of Corporate Real Estate, 17 (2), 122-133.Department for Business Enterprise & Regulatory Reform. (2007) The Third Work-Life Balance Employer Survey: Main Findings.Dex, S. and Scheibl, F. (2001). Flexible and Family-Friendly Working Arrangements in UK-Based SMEs: Business Cases. British Journal of Industrial Relations, 39 (3), 411-431.Fagan, C. (2001). Time, Money and the Gender Order: Work Orientations and Working-Time Pref-erences in Britain. Gender, Work & Organisations, 8 (3), 239-266.Gibson, V. (2003). Flexible working needs flexible space?: Towards an alternative workplace strat-egy. J ournal of Property Investment & Finance, 21 (1), 12-22.Houseman, S. N. (2001). Why Employers Use Flexible Staffing Arrangements: Evidence from an Establishment Survey. Industrial and Labor Relations Review, 55 (1), 149-170.Kelliher, C. and Anderson, D. (2009). Doing more with less? Flexible working practices and the intensification of work. Human Relations, 63 (1), 83-106.Lewis, S. (2003). Flexible Working Arrangements: Implementation, Outcomes, and Management. In Cooper, C. L. and Robertson, I. T. (Eds.), International Review of Industrial and Organisational Psychology (1-23).Maitland, A. and Thomson, P. (2011). Future Work: How Businesses Can Adapt and Thrive in the New World of Work. Badingstoke: Palgrave Macmillan.Miller, N. G. (2014). Workplace Trends in Office Space: implications for future office demand. Journal of Corporate Real Estate, 16 (3), 159-181.Ressler, C. and Thompson, J. (2011). Why Works Sucks and How to fix it:The Results-Only Revolu-tion. New York: Penguin Group.Semler, R. (2003). The Seven-Day Weekend: A Better Way to Work in the 21st Century. Lon-don:Century.。
ICD模型内部对应关系

1ICDൟݙᾬᇍᑨ݇ி1 ЎՓICDˈ៥S1ǃಯICDˈϬTXTǃҹ2 DŽ3 ICD˖LN<>LN0<> LNodeType<>DO<>DADŽ4 <SCL >5 <Substation name="newSubstation">6 </Substation>7 <Communication>8 <SubNetwork name="SubNectWork">9 <ConnectedAP iedName="PSL_XXX" apName="S1"> 10 <Address> 11 <P type="OSI-AP-Title">1 3 9999 23</P> 12 <P type="OSI-AE-Qualifier">23</P> 13 <P type="OSI-PSEL">00 00 00 01</P> 14 <P type="OSI-SSEL">00 01</P> 15 <P type="OSI-TSEL">00 01</P> 16 <P type="IP">127.0.0.1</P> 17 </Address> 18 </ConnectedAP> 19 </SubNetwork> 20 </Communication>21222 23 24 25 26 <GetDataSetValue/> 27 <DataSetDirectory/> 28 <ConfDataSet max="16" maxAttributes="128"/> 29 <ReadWrite/> 30 <ConfReportControl max="16"/> 31 <GetCBValues/> 32 <FileHandling/> 33 <ConfLogControl max="1"/> 34 <ReportSettings bufTime="Dyn" cbName="Conf" datSet="Conf" intgPd="Dyn" optFields="Dyn" rptID="Dyn"/> 35 36 37 38 <Server> 39 <Authentication/> 40 41 42 43 44 45 46 473</DataSet> 4849rptID="brcbCommStateA"> 50 51 52 seqNum="true" timeStamp="true"/> 53 <Rptnabled max="8"/> 54 </ReportControl> 55 56 57 58 59 60 61 62 63 64 <V al>false</Val> 65 </DAI> 66 </DOI> 67 <DOI name="P_01T_B" desc="#1B "> 68 <DAI name="stVal"> 69 <V al>false</Val> 70 </DAI> 71 </DOI> 72 <DOI name="P_02T_B" desc="#2B ">734<DAI name="stVal"> 74 <V al>false</Val> 75 </DAI> 76 </DOI> 77 </LN> 78 </LDevice> 79 </Server> 8081 82 83 84 85 <DO name="Beh" type="CN_Beh_EFIS"/> 86 <DO name="Health" type="CN_Health_EFIS"/> 87 88 89 90 91 92 93 94 95 96 97 </LNodeType>98 <LNodeType id="CN_GGIO_Dev" lnClass="GGIO">995<DO name="Mod" type="CN_Mod_EFIS"/> 100 <DO name="Beh" type="CN_Beh_EFIS"/>101 <DO name="Health" type="CN_Health_EFIS"/> 102 <DO name="NamPlt" type="CN_NamPlt_EFIS"/> 103 <DO desc="GPS " name="GPSErr" type="CN_SPS_EFIS"/> 104 <DO desc="" name="StroageErr" type="CN_SPS_EFIS"/> 105 <DO desc="CPU " name="CPULoadErr" type="CN_SPS_EFIS"/> 106 <DO desc="" name="NICErr" type="CN_SPS_EFIS"/> 107 <DO desc="" name="DBErr" type="CN_SPS_EFIS"/> 108 <DO name="RcdMade" type="CN_SPS_EFIS"/> 109 <DO name="FltNum" type="CN_INS"/> 110111 112 113 114 115 116 117 118 119 120 121 122 123 124 1256<DO name="NamPlt" type="CN_NamPlt_EFIS"/>126 <DO desc="" name="Alm_PT5001A_A" type="CN_SPS_EFIS"/> 127 <DO desc="" name="Alm_PT5001B_A" type="CN_SPS_EFIS"/> 128 <DO desc="" name="Alm_PT5004A_A" type="CN_SPS_EFIS"/> 129 <DO desc="" name="Alm_PT5004B_A" type="CN_SPS_EFIS"/> 130131 132 133 134 135 136 137 138 139 140 141 142 143 <DA name="stVal" fc="ST" bType="Enum" dchg="true" type="Beh"/> 144 <DA name="q" fc="ST" bType="Quality" qchg="true"/> 145 <DA name="t" fc="ST" bType="Timestamp"/> 146 </DOType>147 <DOType id="CN_Health_EFIS" cdc="INS">148 <DA name="stVal" fc="ST" bType="Enum" type="Health"/> 149 <DA name="q" fc="ST" bType="Quality" qchg="true"/> 150 <DA name="t" fc="ST" bType="Timestamp"/>1517</DOType>152 <DOType id="CN_NamPlt_EFIS" cdc="LPL">153 <DA name="vendor" fc="DC" bType="VisString255"/> 154 <DA name="swRev" fc="DC" bType="VisString255"/> 155 <DA name="d" fc="DC" bType="VisString255"/> 156 <DA name="ldNs" fc="EX" bType="VisString255"/> 157 </DOType> 158 <DOType id="EFIS_DPL_EFIS" cdc="DPL"> 159 <DA name="vendor" fc="DC" bType="VisString255"/> 160 <DA name="hwRev" fc="DC" bType="VisString255"/> 161 <DA name="swRef" fc="DC" bType="VisString255"/> 162 <DA bType="VisString255" fc="DC" name="serNum"/> 163 <DA bType="VisString255" fc="DC" name="model"/> 164 <DA bType="VisString255" fc="DC" name="location"/> 165 </DOType> 166 <DOType cdc="STG" id="CN_STG_SG"> 167 <DA bType="Unicode255" fc="SP" name="setV al"/> 168 <DA bType="Unicode255" fc="DC" name="dU"/> 169 <DA bType="VisString255" fc="EX" name="cdcNs"> 170 <Val>ZPEPC MODEL:2008</V al> 171 </DA> 172 <DA bType="VisString255" fc="EX" name="cdcName"> 173 <Val>ZPEPC MODEL:2008</V al> 174 </DA> 175 <DA bType="VisString255" fc="EX" name="dataNs"> 176 <Val>ZPEPC MODEL:2008</V al>1778</DA> 178 <DA bType="Unicode255" fc="SE" name="setVal"/> 179 </DOType> 180 <DOType id="CN_INS" cdc="INS"> 181 <DA name="stVal" bType="INT32" dchg="true" fc="ST"/> 182 <DA name="q" bType="Quality" qchg="true" fc="ST"/> 183 <DA name="t" bType="Timestamp" fc="ST"/> 184 <DA name="subEna" bType="BOOLEAN" fc="SV"/> 185 <DA name="subV al" bType="INT32" fc="SV"/> 186 <DA name="subQ" bType="Quality" fc="SV"/> 187 <DA name="subID" bType="VisString64" fc="SV"/> 188 <DA name="dU" bType="Unicode255" fc="DC"/> 189 </DOType>190 <EnumType id="Beh">191 <EnumV al ord="1">on</EnumV al>192 <EnumV al ord="2">blocked</EnumV al> 193 <EnumV al ord="3">test</EnumVal>194 <EnumV al ord="4">test/blocked</EnumVal> 195 <EnumV al ord="5">off</EnumVal> 196 </EnumType>197 <EnumType id="Health">198 <EnumV al ord="1">Ok</EnumVal>199 <EnumV al ord="2">Warning</EnumV al> 200 <EnumV al ord="3">Alarm</EnumVal> 201 </EnumType>202 <EnumType id="ctlModel">2039<EnumV al ord="0">status-only</EnumVal>204 <EnumV al ord="1">direct-with-normal-security</EnumVal> 205 <EnumV al ord="2">sbo-with-normal-security</EnumV al> 206 <EnumV al ord="3">direct-with-enhanced-security</EnumV al> 207 <EnumV al ord="4">sbo-with-enhanced-security</EnumVal> 208 </EnumType> 209 </DataTypeTemplates> 210 </SCL>211 ᮹⏤ˈএǃˊICD/SCDDŽԚ212 ˈc ICD/SCD61850DŽҹDŽ213 214 ˖߬ 215 2013ᑈ4᳜8᮹216217218。
PB 郭宝利老师视频笔记-4

第二十七讲dw_1.ModifiedCount()作用:判断数据窗口中有多少行数据被改动过。
返回值:long类型,修改过的行数dw_1.DeletedCount()作用:判断有多少行数据被删除返回值:删除的行数,long类型。
w_dw窗口的closequery()事件if dw_1.ModifiedCount() + dw_1.DeletedCount() > 0 thenif MessageBox(‘提示’,’数据已修改,是否确定要关闭?’,Question!,YesNo!,2) =1 thenreturn 0end ifelsereturn 0end if //以上为特例,返回0,允许关闭return 1//应该和上面具有相同的效果,书上164页integer li_numif dw_1.ModifiedCount() + dw_1.DeleteCount() > 0 thenli_num = MessageBox(‘提示’,’数据已修改,需要保存么?’,Question!,YesNo!)choose case li_numcase 1dw_1.update()return 0case 2return 0case 3return 1end chooseend ifreturn 0w_dw窗口的cb_exit按钮的clicked事件close(parent)上机:数据处理程序的编程框架,目的是:对数据窗口的功能有一个大致的了解了解数据窗口控件的常用函数了解数据窗口的常用编程复习窗口的CloseQuery事件数据窗口控件--------------常用事件1在做数据操作的时候,在每个单元格(横向和纵向交叉的位置)里改动数据的时候,并不是直接对数据窗口里面的数据进行操作,而是对一个假想的编辑控件进行操作,这个控件是你走到哪就跟到哪,我们输入的内容都是在编辑控件里面输入的,这个控件,只有当焦点切换的时候,数据窗口才会把数据从假想的编辑控件里面取出来,放在刚才所在的单元里面。
DieHarder随机数生成器测试套件 R 接口说明书

RDieHarder:An R interface to the Die Harder suite of RandomNumber Generator TestsDirk EddelbuettelDebian**************Robert G.Brown Physics,Duke University ************.eduInitial Version as of May2007Rebuilt on January12,2023using RDieHarder0.2.51IntroductionRandom number generators are critically important for computational statistics.Simulation methods are becoming ever more common for estimation;Monte Carlo Markov Chain is but one approach.Also,simu-lation methods such as the Bootstrap have long been used in inference and are becoming a standard part of a rigorous analysis.As random number generators are at the heart of the simulation-based methods used throughout statistical computing,`good'random numbers are therefore a crucial aspect of a statistical,or quantitative,computing environment.However,there are very few tools that allow us to separate`good' from`bad'random number generators.Based on work that started with the random package(Eddelbuettel,2007)(which provides functions that access a non-deterministic random number generator(NDRNG)based on a physical source of randomness), we wanted to compare the particular NDRNG to the RNGs implemented in GNU R(R Development Core Team,2007)itself,as well as to several RNGs from the GNU GSL(Galassi et al.,2007),a general-purpose scienti c computing library.Such a comparison is possible with the Die Harder test suite by Brown(2007) which extends the DieHard test suite by Marsaglia.From this work,we became interested in making Die Harder directly accessible from GNU R.The RDieHarder package presented here allows such access.This paper is organized as follows.Section2describes the history and design of the Die Harder suite. Section3describes the RDieHarder package facilities,and section4shows some examples.Section5discusses current limitations and possible extensions before section6concludes.2Die HarderDie Harder is described at length in Brown(2006).Due to space limitations,this section cannot provide as much detail and will cover only a few key aspects of the DieHarder suite.2.1DieHardDie Harder reimplements and extends George Marsaglia's Diehard Battery of Tests of Randomness(Marsaglia, 1996).Due to both its robust performance over a wide variety of RNGs,as well as an ability to discern numerous RNGs as weak,DieHard has become something close to a`gold standard'for assessing RNGs.However,there are a number of drawbacks with the existing DieHard test battery code and implementa-tion.First,Marsaglia undertook a large amount of the original work a number of years ago when computing resources were,compared to today's standards,moderately limited.Second,neither the Fortran nor the (translated)C sources are particularly well documented,or commented.Third,the library design is not1modular in a way that encourages good software engineering.Fourth,and last but not least,no licensing statement is provided with the sources or on the support website.This led one of the authors of this paper (rgb)to a multi-year e ort of rewriting the existing tests from DieHard in a)standard C in a modular and extensible format,along with extensive comments,and to b)relicense it under the common and understood GNU GPL license (that is also used for GSL,R,the Linux kernel,and numerous other projects)allowing for wider use.Moreover,new tests from NIST were added (see next subsection)and some genuinely new tests were developed (see below).2.2STSThe National Institute of Standards and Technology (NIST)has developed its own test suite,the 'Statistical Test Suite'(STS).These tests are focussed on bit-level tests of randomness and bit sequences.Currently,three tests based on the STS suite are provided by Die Harder :STS Monobit ,STS Runs and STS Block .2.3RGB extensionsThree new tests have been developed by rgb.A fourth 'test'is a timing function:for many contexts,not only do the mathematical properties of a generator matter,but so does computational cost measured in computing time that is required for a number of draws.2.4Basic methodologyLet us suppose a random number generator can provides a sequence of N uniform draws from the range [0,1).As the number of draws increases,the mean of the sum of all these values should,under the null hypothesis of a proper generator,converge closer and closer to µ=N/2.Each of these N draws forms one experiment.If N is su ciently large,then the means of all experiments should be normally distributed with a standard deviation of σ= N/12.1Given this asymptotic result,we can,for any given experiment i ∈1,...,M transform the given sum x i of N draws into a probability value p i using the inverse normal distribution.2The key insight is that,under the null hypothesis of a perfect generator,these p i values should be uni-formly ing our set of M probability values,we can compute one 'meta-test'of whether we can reject the null of a perfect generator by rejecting that our M probability values are not uniformly distributed.One suitable test is for example the non-parametric Kolmogorov-Smirnov (KS)3statistic.Die Harder uses the Kuiper 4variant of the KS test which uses the combination D ++D −of the maximum and minimum distance to the alternative distribution,instead of using just one of these as in the case of the KS test.This renders the test more sensitive across the entire test region.2.5GSL frameworkDie Harder is primarily focussed on tests for RNGs.Re-implementing RNGs in order to supply input to the tests is therefore not an objective of the library.The GNU Scienti c Library (GSL),on the other hand,provides over 1000mathematical functions,including a large number of random number ing the GSL 1.9.0release,the following generators are de ned 5:1Thisis known as the Irwin-Hall distribution,see /wiki/Irwin-Hall_distribution .2Running print(quantile(pnorm(replicate(M,(sum(runif(N))-N/2)/sqrt(N/12))),seq(0,1,by=0.1))*100,digits=2)performs a Monte Carlo simulation of M experiments using N uniform deviates to illustrate this.Suitable values are e.g.N <-1000;M <-500.3C.f.the Wikipedia entry /wiki/Kolmogorov-Smirnov_test .4C.f.the Wikipedia entry /wiki/Kuiper%27s_test .5This is based on the trailing term in each identi er de ned in /usr/include/gsl/gsl_rng.h .2borosh13coveyou cmrg fishman18fishman20fishman2x gfsr4knuthran knuthran2knuthran2002lecuyer21minstd mrg mt19937mt19937_1999mt19937_1998r250ran0ran1ran2ran3rand rand48random128_bsd random128_glibc2random128_libc5random256_bsd random256_glibc2random256_libc5random32_bsd random32_glibc2random32_libc5random64_bsd random64_glibc2random64_libc5random8_bsd random8_glibc2random8_libc5random_bsd random_glibc2random_libc5randu ranf ranlux ranlux389 ranlxd1ranlxd2ranlxs0ranlxs1ranlxs2ranmar slatec taus taus2taus113transputer tt800uni uni32vax waterman14zufThe GNU GSL,a well-known and readily available library of high quality,therefore provides a natural tfor Die Harder.All of these generators are available in Die Harder via a standardized interface in which a generator is selected,parameterized as needed and the called via the external GSL library against which Die Harder is linked.Beyond these GSL generators,Die Harder also provides two generators based on the`devices'/dev/random and/dev/urandom that are commonly available on Unix.They provide non-deterministic random-numbers based on entropy generated by the operating system.Die Harder also o ers a text and a raw le input stly,a new algorithmic generator named'ca'that is based on cellular automata has recently been added as well.2.6R random number generatorsTo assess the quality of the non-deterministic RNG provided in the GNU R add-on package random,bench-mark comparisons with the generators provided by the R language and environment have been a natural choice.To this end,one of the authors(edd)ported the R generator code(taken from R2.4.0)to the GNU GSL random number generator framework used by Die Harder.This allows a direct comparison of the random generator with those it complements in R.It then follows somewhat naturally that the other generators available in Die Harder,as well as the Die Harder tests,should also be available in R.This provided the motivation for the R package presented here.2.7Source code and building Die HarderRecent versions of Die Harder use the GNU autotools.On Unix system,the steps required to build and install Die Harder should only be the familiar steps configure;make;sudo make install.For Debian,initial packages have been provided and are currently available at http://dirk.eddelbuettel. com/code/tmp.Within due course,these packages should be uploaded to Debian,and thus become part ofthe next Debian(and Ubuntu)releases.Die Harder is also expected to be part of future Fedora Core(and other RPM-based distribution)releases.On Windows computers and other systems,manual builds should also be possible given that the source code is written in standard C.3RDieHarderThe RDieHarder package provides one key function:dieharder.It can be called with several arguments. The rst one is the name of the random number generator,and the second one is the name of the test to be applied.For both options,the textual arguments are matched against internal vectors to obtain a numeric argument index;alternatively the index could be supplied directly.The remaining arguments(currently) permit to set the number of samples(i.e.the number of experiments run,and thus the sample size for thenal Kolmogorov-Smirnov test),the random number generator seed and whether or not verbose operationis desired.The returned object is of class dieharder,inheriting from the standard class htest common for all hypothesis tests.The standard print method for htest is used;however not all possible slots are being lled (as there is for example no choice of alternative hypothesis).3A custom summary method is provided that also computes the Kolmogorov-Smirnov and Wilcoxon tests in R and displays a simple stem-and-leaf stly,a custom plot method shows both a histogram and kernel density estimate,as well as the empirical cumulative distribution function.4ExamplesThe possibly simplest usage of RDieHarder is provided in the examples section of the help page.The code dh <-dieharder;summary(dh);plot(dh)simply calls the dieharder function using the default arguments,invokes a summary and then calls plot on the object.6A more interesting example follows below.We select the 2dsphere test for the generators ran0and mt19937with a given seed.The results based on both the Kuiper KS test and the KS test suggest that we would reject ran0but not mt19937,which is in accordance with common knowledge about the latter (the Mersenne Twister)being a decent RNG.It is worth nothing that the Wilcoxon test centered on µ=0.5would not reject the null at conventional levels for ran0.Histogram and Density estimated e n s i t y0.00.20.40.60.81.00.01.02.0.00.20.40.60.8 1.00.00.40.8ECDFDiehard Minimum Distance (2d Circle) TestCreated by RNG ‘ran0' with seed=2, sample of size 100T est p−values: 0.0099 (Kuiper−K−S), 0.0056 (K−S), 0.3506 (Wilcoxon)Histogram and Density estimated e n s i t y0.00.20.40.60.81.00.00.51.01.50.00.20.40.60.8 1.00.00.40.8ECDFDiehard Minimum Distance (2d Circle) TestCreated by RNG ‘mt19937' with seed=2, sample of size 100T est p−values: 0.2449 (Kuiper−K−S), 0.199 (K−S), 0.1696 (Wilcoxon)Figure 1:Comparison of ran0and mt19937under test 2dsphereA programmatic example follows.We de ne a short character vector containing the names of the six R RNGs,apply the Die Harder function to each of these,and then visualize the resulting p -values in simple qqplot.All six generators provide p -value plots that are close to the ideal theoretical outcome (shown in gray).Unsurprisingly,p -values for the Kuiper KS test also show no support for rejecting these generators.5Current Limitations and Future ResearchThe implementation of RDieHarder presented here leaves a number of avenues for future improvement and research.Some of these pertain to Die Harder itself adding new,more sophisticated,more systematic tests including those from the STS suite and tests that probe bitlevel randomness in unique new ways.Others pertain more to the integration of Die Harder with R,which is the topic of this work.6Weomit the output here due to space constraints.4>rngs <-c("R_wichmann_hill","R_marsaglia_multic",+"R_super_duper","R_mersenne_twister",+"R_knuth_taocp","R_knuth_taocp2")>if (!exists("rl"))rl <-lapply(rngs,function(rng)dieharder(rng,"diehard_runs",seed=12345))>oldpar <-par(mfrow=c(2,3),mar=c(2,3,3,1))>invisible(lapply(rl,function(res){+qqplot(res$data,seq(0,1,length.out=length(res$data)),+main=paste(res$generator,":",round(res$p.value,digits=3)),+ylab="",type="S")+abline(0,1,col='gray ')+}))>par(oldpar)#reset graph defaults>0.00.20.40.60.8 1.00.00.20.40.60.81.0R_wichmann_hill : 0.1420.00.20.40.60.81.00.00.20.40.60.81.0R_marsaglia_multic. : 0.8460.00.20.40.60.8 1.00.00.20.40.60.81.0R_super_duper : 0.8680.00.20.40.60.8 1.00.00.20.40.60.81.0R_mersenne_twister : 0.8690.00.20.40.60.81.00.00.20.40.60.81.0R_knuth_taocp : 0.7150.00.20.40.60.8 1.00.00.20.40.60.81.0R_knuth_taocp2 : 0.715Figure 2:Comparing six GNU R generators under the runs test5Not all of Die Harder's features are yet supported in this initial port.In the near future we expect to add code to deal with tests that support extra parameters,or that return more than one p-value per instance of a test.Ultimately,RDieHarder should support the full set of options of the the command-line version of Die Harder.There is no direct interface from the R generators to the RDieHarder module for evaluation;rather, the'ported'R generators are called from the libdieharder library.This could introduce coding/porting errors,and also prevents the direct use of user-added generators that R supports.It would be worthwhile to overcome this by directly letting RDieHarder call back into R to generate draws.On the other hand,the current setup corresponds more closely to the command-line version of Die Harder.Next,the R generators in Die Harder may need to be updated to the2.5.0code.The GSL RNGs provided by libdieharder may as well be exported to R via RDieHarder given that the GSL library is already linked in.Indeed,it would be worthwhile to integrate the two projects and both avoid needless code duplication and ensure even more eyes checking both the quality and accuracy of the code in both.It could be useful to also build RDieHarder with an`embedded'libdieharder rather than relying on an externally installed libdieharder.This may make it easier to build RDieHarder for systems without libdieharder(and on Windows).Likewise,it is possible to reorganize the Die Harder front-end code into a common library to avoid duplication of code with RDieHarder.Lastly,on the statistical side,an empirical analysis of size/power between KS,Wilcoxon and other alternatives for generating a nal p-value from the vector of p-values returned from Die Harder tests suggests itself.Similarly,empirical comparisons between the resolving power of the various tests(some of which may not actually be terribly useful in the sense that they yield new information about the failure modes of any given RNG)could be stly,there is always room for new generators,new tests,and new visualizations.One thing that one should remember while experimenting with Die Harder is that there really is no such thing as a random number generator.It is therefore likely that all RNGs will fail any given(valid)test if one cranks up the resolution up high enough by accumulating enough samples per p-value,enough p-values per run.It is also true that a number of Marsaglia's tests have target distributions that were computed empirically by simulation(with the best RNGs and computers available at the time).Here one has to similarly remember that one can do in a few hours of work what it would have taken him months if not years of simulation to equal back when the target statistics were evaluated.It is by no means unlikely that a problem that Die Harder eventually resolves is not not the quality of the RNG but rather the accuracy of the target statistics.These are some of the things that are a matter for future research to decide.A major motivation for writing Die Harder and making it open source,and integrating it with R,is to facilitate precisely this sort of research in an easy to use,consistent testing framework.We welcome the critical eyes and constructive suggestions of the statstical community and invite their participation in examining the code and algorithms used in Die Harder.6ConclusionThe RDieHarder package presented here introduces several new features.First,it makes the Die Harder suite (Brown,2007)available for interactive use from the GNU R environment.Second,it also exports Die Harder results directly to R for further analysis and visualization.Third,it adds adds additional RNGs from GNU R to those from GNU GSL that were already testable in Die Harder.Fourth,it provides a re-distribution of the Die Harder`test engine'via GNU R.ReferencesRobert G.Brown.Die Harder:A Gnu public licensed random number tester.Draft paper included as le manual/dieharder.tex in the dieharder st version dated20Feb2006.,2006.6Robert G.Brown.dieharder:A Random Number Test Suite,2007.URL / ~rgb/General/dieharder.php.C program archive dieharder,version2.24.3.Dirk Eddelbuettel.random:True random numbers using ,2007.URL http://cran.r-project. org/src/contrib/Descriptions/random.html.R package random,current version0.1.2.Mark Galassi,Brian Gough,Gerald Jungman,James Theiler,Jim Davies,Michael Booth,and Fabrice Rossi. The GNU Scienti c Library Reference Manual,2007.URL /software/gsl.ISBN 0954161734;C program archive gsl,current version1.9.0.George Marsaglia.The Marsaglia random number CDROM including the diehard battery of tests of ran-domness.Also at /pub/diehard.,1996.R Development Core Team.R:A Language and Environment for Statistical Computing.R Foundation for Statistical Computing,Vienna,Austria,2007.URL .ISBN3-900051-07-0.7。
Windows system32文件夹说明

WINDOWS C :/system32 文件夹详解在C:\WINDOWS\system32 文件夹中包含了大量的用于Windows 的文件,此主要是用于存储DLL 文件、控制面板小程序(.CPL)、设备驱动(.drv)、帮助文件(.hlp 和.cnt)、MS-DOS 工具(.com)、语言支持文件(.nls)、屏幕保护(.scr)、安装信息文件(.inf),以及其它用于支持、配置、或操作的文件。
*3com_dmi:一般为空,可以删除。
1025、1028、1031、1033、1037、1041、1053、2052、3076:用于指定语言的本地化(语言)文件,其中1033是英语,2052是简体中文,其他的空文件夹可以删除。
*BITS :(后台智能传送服务) ,它可以在前台或后台异步传输文件,为保证其他网络应用程序获得响应而调整传输速度,并在重新启动计算机或重新建立网络连接之后自动恢复文件传输.*CatRoot、CatRoot2:CatRoot 文件夹中包含了安全编录文件,CatRoot2 文件夹中包含了编录数据库文件。
某些第三方程序可能会需要CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}文件夹中某些特定的.CAT 文件。
此外CatRoot2 中的oemO.CAT 和1.CAT 比较重要,不建议删除。
也可以把所有的.CAT 文件放置到一个别的文件夹中,周期性地检查CatRoot2\dberr.txt 中是否有缺失.cat 文件的错误信息,然后把有提示的.CAT 文件放回到CatRoot\{F750E6C3-38EE-11D1-85E5-00C04FC295EE} 文件夹中,直到dberr.txt 停止显示错误。
CatRoot2 文件夹中产生的文件一般都是*.chk、*.emb、*.log、*.txt 的临时文件。
]*Com:组件对象模型(COM)组件,控制面板-->管理工具-->组建服务的快捷方式源自这里,不建议删除。
胶体金标记技术

胶体金标记技术胶体金标记技术是以胶体金作为示踪标志物或显色剂,应用于抗原抗体反应的一种新型免疫标记技术。
由于它不存在内源酶干扰及放射性同位素污染等问题,且利用不同颗粒大小的胶体金还可以作双重甚至多重标记,使定位更加精确。
因此已成为继荧光素、酶、同位素及乳胶标记技术之后的一种新型标记技术。
现已广泛应用于电镜、流式细胞仪、免疫印迹、蛋白染色、体外诊断试剂的制造等领域。
用胶体金作为特殊标记物的研究始于60年代初,1962年Feldberr等报道了用胶体金标记细胞进行电子显微镜的研究。
1971年,Taylor又将胶体金引入电镜免疫标记技术中。
近年来的研究表明,胶体金也可作为体外免疫加层试验的指示物。
由于胶体金作为标记物具有很多优点,因此自其问世以来,在国内外的许多研究领域中得到了迅速的发展。
近年来,它更多的被应用于免疫学和细胞学相关分子水平的检测中。
尤其随着人们物质生活的改善,有关人类健康的问题在现实生活中已显得非常突出。
从90年代至今的多篇报道都是关于动物体或人体相关抗体和病原体检测的。
制备方法在溶液中金颗粒呈圆形,边缘平整,界线十分清楚。
金颗粒表面带有大量负电荷,由于静电的排斥力,使其在水中保持稳定状态,形成稳定的胶体,所以称其为胶体金。
胶体金的制作方法有白磷还原法,抗坏血酸还原法,柠檬酸三钠还原法和鞣酸—柠檬酸三钠还原法。
通过改变反应体系中氯金酸与还原剂的比例(即增加或减少还原剂的量)可得到所需不同直径的金颗粒。
但前两种方法制备得到的金颗粒直径大小不均一,所以目前常用后两种方法,以柠檬酸三钠还原法为例,有两种方法。
1.Frens标准方法:1)取0.01%HAuCl4溶液50mL,加热煮沸,随即快速加入1%柠檬酸三钠溶液0.5mL。
2)约过25s沸腾的溶液变为淡蓝色,大约再过70s,蓝色突然转变为亮红色,3)继续煮沸约5分钟后结束反应。
4)冷却后用0.1M K2CO3溶液调至所需PH值。
5)此后再延长反应时间或另加入额外的柠檬酸三钠都不影响实验结果。
golang错误码配置

golang错误码配置//配置⽂件package modelsconst (RECODE_OK = "0"RECODE_DBERR = "4001"RECODE_NODATA = "4002"RECODE_DATAEXIST = "4003"RECODE_DATAERR = "4004"RECODE_SESSIONERR = "4101"RECODE_LOGINERR = "4102"RECODE_PARAMERR = "4103"RECODE_USERERR = "4104"RECODE_ROLEERR = "4105"RECODE_PWDERR = "4106"RECODE_REQERR = "4201"RECODE_IPERR = "4202"RECODE_THIRDERR = "4301"RECODE_IOERR = "4302"RECODE_SERVERERR = "4500"RECODE_UNKNOWERR = "4501")var recodeText = map[string]string{RECODE_OK: "成功",RECODE_DBERR: "数据库查询错误",RECODE_NODATA: "⽆数据",RECODE_DATAEXIST: "数据已存在",RECODE_DATAERR: "数据错误",RECODE_SESSIONERR: "⽤户未登录",RECODE_LOGINERR: "⽤户登录失败",RECODE_PARAMERR: "参数错误",RECODE_USERERR: "⽤户不存在或未激活",RECODE_ROLEERR: "⽤户⾝份错误",RECODE_PWDERR: "密码错误",RECODE_REQERR: "⾮法请求或请求次数受限",RECODE_IPERR: "IP受限",RECODE_THIRDERR: "第三⽅系统错误",RECODE_IOERR: "⽂件读写错误",RECODE_SERVERERR: "内部错误",RECODE_UNKNOWERR: "未知错误",}func RecodeText(code string) string {str, ok := recodeText[code]if ok {return str}return recodeText[RECODE_UNKNOWERR]}//使⽤⽅式func (this*TestController) Test(){resp := make(map[string]interface{})resp["errno"] =models.RECODE_DATAERRresp["errmsg"] = models.RecodeText(models.RECODE_DATAERR)this.RetData(resp)}。
【IT专家】MBR和DBR详细分析

MBR和DBR详细分析系统2KPROSP4,C盘采用NTFS,用WinHex提取MBR和DBR,拿IDA分析的.关键在DBR几处不明白. 1.一点预备知识: 主引导扇区代码(MBR);======================================================= =============================;;MBR(MasterBootRecord)主引导记录包含两部分的内容,前446字节为启动代码及数据,而;从446(0x1BE)开始则是分区表,分区表由四个分区项组成,每个分区项数据为16字节,记录了;启动时需要的分区参数。
;在CPU上电之后,若由硬盘启动,则BIOS将硬盘的主引导记录(位于0柱面、0磁道、1扇区)读;入7C00处,然后将控制权交给主引导代码。
主引导代码的任务包括:;(1)扫描分区表,找到一个激活(可引导)分区;;(2)找到激活分区的起始扇区;;(3)将激活分区的引导扇区装载到内存7C00处;;(4)将控制权交给引导扇区代码;;;如果主引导代码无法完成上述任务,它将显示以下错误信息之一:;Noactivepartition.;Invalidpartitiontable.;Errorloadingoperatingsystem.;Missingoperat ingsystem.;======================================================== ============================;FAT16分区尺寸与LBA;============================================================ ========================;LBAHeadsPerCylinderSectorsPerTrackMaximumSizefo rBootPartition;Disabled64321GB;Enabled255634GB;为了适应超过8G的硬盘,Windows2000忽略了StartCHS和EndCHS,而使用StartLBA和TotalSector;来确定分区在整个磁盘中的位置和大小。
U盘MBR、DBR的基本知识

U盘MBR、DBR的基本知识点击: 次时间:2011-11-23 08:30一、几个基本概念BIOS(Basic Input/Output System)基本输入输出系统,全称是ROM-BIOS,是只读存储器基本输入/输出系统的简写,它实际是一组被固化到电脑中,为电脑提供最低级最直接的硬件控制的程序。
CMOS(Complementary Metal Oxide Semiconductor)大白菜官网本意是指互补金属氧化物半导体,一种大规模应用于集成电路芯片制造的原料,在计算机领域,CMOS 常指保存计算机基本启动信息(如日期、时间、启动设置等)的芯片。
CMOS 的功耗很低,计算机主板上一个纽扣电池就可以给它长时间地提供电力,即使系统掉电,信息也不会丢失。
而当主板电池供电不足时CMOS的信息会丢失,此时启动机器会有一些特殊的现象,如启动时提示CMOS 参数丢失需重新设置,甚至机器黑屏,不能启动,更换主板上的纽扣电池即恢复正常。
有时人们会把CMOS和BIOS混称,其实CMOS是主板上的一块可读写的RAM芯片,是用来保存BIOS的硬件配置和用户对某些参数的设定。
而对CMOS中各项参数的设定要通过专门的程序,现在多数厂家将CMOS设置程序做到了BIOS芯片中,在开机时通过按下某个特定键就可进入CMOS设置程序而非常方便地对系统进行设置,因此这种CMOS设置又通常被叫做BIOS设置。
ESCD(Extended System Configuration Data)扩展系统配置数据,ESCD是系统BIOS用来与操作系统交换硬件配置信息的一种手段,这些数据被存放在CMOS(一小块特殊的RAM,由主板上的电池来供电)之中,通常ESCD数据只在系统硬件配置发生改变后才会更新。
扇区(Sector)硬盘划分的最小单位,一个扇区固定为512 个字节(Byte)。
MBR(master boot record)即主引导记录,有时也称主引导扇区。
Informix监控和管理命令 电脑资料

Informix监控和管理命令电脑资料监控ONLINE系统后动情况的工具主要有以下三类:系统监控接口( I)、tbstat和tbcheck,不能对 I中的表加锁或使用隔离级别。
不允许使用insert,delete,update等语句(只读)不能使用dbsche ,dbexport等命令使用select rowid语句将会产生不可预料的结果主要的 I表有:sysdatabases:online中的数据库信息systabnames:某数据库中所有表的信息syslogs:逻辑日志信息sysdbspaces:数据库信息syschunks,syslocks等例1:显示处于脱机(offline)状态的chunk的序号和所在数据库空间Select chknum,dbsnum from syschunks where isoffline=1 or misline=!例二:显示满chunk的信息Select chknum,dbsnum from syschunks where nfree=0 二、TBSTAT ? 列出当前时刻的信息(实际也是读取 I表)不需要磁盘I/O不需要锁等系统资源,因此不会影响系统性能用法:tbstat [-abcdklmpstuzBDFPRX] [-r seconds] [-o file] [infile] -a print all info (options: bcdklmpstu)-b print buffers(缓冲区)-c print configuration file(配置文件)-d print dbspaces and chunks(dbspace和chunk)-k print locks(锁)-l print logging(日志)-m print message log(日志)-p print profile(profile文件)-s print latches(门闸)-t print tblspaces(表空间)-u print users(用户)-z zero profile counts-B print all buffers-D print dbspaces and detailed chunk stats-F print page flushers(页刷新进程)-P print profile, including BIGreads-R print LRU queues(LRU队列)-X print entire list of sharers and waiters for buffers-r repeat options every n seconds (default: 5)-o put shared memory into specified file (default: tbstat.out) infile use infile to obtain shared memory infor tion三、几个常用的tbstat选项 tbstat -m :显示消息日志的最后20行. 消息日志的内容包括:1)、检查点信息2)、读写错误信息3)、ONLINE模式转换信息4)、长事务5)、日志文件满(LOG FILE FULL )假设想显示完整信息,可直接编译消息日志文件.Tbstat -d:磁盘空间的使用情况,包括DBSPACE和CHUNK的信息例:RSAM Version 5.03.UC1 -- On-Line -- Up 09:45:41 -- 816 Kbytes Dbspaces address number flagsfchunk nchunksflags ownername 8040a244 1111 N informix rootdbs 1 active, 8 total Chunks address chk/dbs offset size free bpages flags pathname 80409d84 1 1 0 300000 231871PO-/dev/rdata 1 active, 8 total其中的FREE项,显示了该CHUNK的空闲空间大小(Kbytes).Tbstat -l :日志文件情况Physical Logging Buffer bufused bufsize numpages numwrits pages/io P-2 016 000.00 phybegin physize phypos phyused %used 101782 15000960 00.00 Logical Logging Buffer bufused bufsize numrecs numpages numwrits recs/pages pages/io L-2 016 1111.01.0 address number flagsuniqid beginsize used%used 8042de94 1U---C-L 110521a 7500 630 8.408042deb0 2F------ 0106f66 75000 0.00 8042de 3F------0108cb2 75000 0.00 8042dee8 4F------ 010a9fe 75000 0.00 8042df04 5F------ 010c74a 75000 0.00 8042df20 6F------010e496 75000 0.00其中:%USED:使用百分比FLAGS字段的含义:F: 空闲B:已备份C: 正在接收事物记录U: 正在使用A: 新增日志L: 包含最后一个检查点Tbstat - u:ONLINE的用户情况Users address flags pid user tty waittout locks nreads nwrites 804019f4 ------D 329 root console 0 00 179 2 80401a64 ------D 0 root console 0 00 00 80401ad4 ------F 330 root 0 00 00 3 active, 20 total Transactions address flags user locks log begin isolation retrys coordinator 804022b4 A---- 804019f4 0 0 NOTRANS 0 804028d8 A----80401a64 0 0 NOTRANS 0 2 active, 20 total其中:flages字段的含义:第一列:(S:等待mutex;Y:等待条件;L:等待锁;B:等待缓冲区;C:等待检查点;X:长事务清理;G:等待长缓冲写;T:等待事务)第二列:(*:事务执行时,发生I/O错误)第三列:(A:正在备份;B:操作已被记录在日志中;P:分布处理已准备好;C:正在提交;R:正在回滚)第四列:(P:会话的主线索)第五列:(R:在read rsam 调用中;X:进程在关键分区)第七列:(M:特殊监控;D:特殊线索;C:清理线索;F:特殊清页进程;B:特殊B+树清页线索) Tbstat -k :用户持有锁的情况锁按照粒度分为6种: 库锁、表锁、页锁、行锁、字节锁、键锁字节锁:更新包含有VARCHAR类型的行时,加在该行上的锁,键锁:用于索引树上的锁。
dbl类型 r语言 -回复

dbl类型r语言-回复什么是dbl类型?在R语言中,dbl类型是一种数据类型,表示双精度浮点数(double precision float)。
双精度浮点数是一种用于存储和计算非整数数字的数据类型,它提供了更高的精度和范围,相比于单精度浮点数。
双精度浮点数的数据范围远比整型数字和单精度浮点数更大,可以存储非常小或非常大的数字,以及具有小数点的数字。
双精度浮点数通常由两部分组成:一个浮点数的数值部分和一个基于2的指数部分。
浮点数的数值部分决定了数值的大小和精度,而指数部分表示浮点数的指数。
为了更好地理解dbl类型的用法,让我们看一些具体的示例和操作。
首先,我们可以使用函数typeof()来检查一个变量或数值的类型。
例如,我们可以创建一个双精度浮点数变量x并检查其类型:rx <- 3.14159typeof(x)输出将是"double",表示x是一个dbl类型的变量。
双精度浮点数可以进行各种数学运算,例如加法、减法、乘法和除法。
我们可以使用运算符+、-、*和/进行这些操作。
下面是一些示例:ra <- 2.5b <- 1.75# 加法c <- a + bprint(c) # 输出为4.25# 减法d <- a - bprint(d) # 输出为0.75# 乘法e <- a * bprint(e) # 输出为4.375# 除法f <- a / bprint(f) # 输出为1.428571双精度浮点数还支持其他一些常用的数学函数,例如平方根、幂运算和取整操作。
下面是一些示例:r# 平方根g <- sqrt(a)print(g) # 输出为1.581139# 幂运算h <- a^2print(h) # 输出为6.25# 取整操作i <- floor(a)print(i) # 输出为2在R语言中,双精度浮点数还可以用于表示缺失值或非数值的情况。
iFIX域参数索引

域参数索引自动/手动状态 (_AUTO)显示块的自动/手动状态。
此状态确定块如何取值。
如果状态为:则数值取自:自动 I/O设备。
手动操作员输入或来自另一块,CDA或处方的数值。
如果块连接为手动状态,按切换为自动状态。
如果块连接为自动状态,按切换为手动状态。
注: 也可以用只读的浮点格式(F_AUTO)显示此域格式。
当块为自动方式时此域参数显示1,当为手动方式时显示0。
如果想要基于块的特殊条件动态改变画面中对象的颜色,可以应用此工具。
扩展趋势块域参数下列特殊块域参数应用于扩展趋势块。
那些可以用浮点格式的域用红色标识。
域参数显示... 有效输入A_BC 输入于清除缓冲区域的清除缓冲区标志状态。
显示是或否。
是,否A_GET1 其值被级联的趋势块。
点名输入于输入域。
输入以下格式的点名: [ETR block].F_INP 扩展趋势块点名A_INP 通过输入于输入域的扩展趋势块传送给块的输入值。
数字值A_TIME 输入于平均/Com 压力域的数字。
数字值G_DATA 图形连接中用于显示趋势信息的数据。
只显示I/O地址域参数 (_IOAD)I/O工程变换域参数 (_IOSC)I/O驱动器名称域参数 (_IODV)I/O硬件类型域参数 (_IOHT)On-Off控制块域参数下列特殊块域参数应用于On-Off控制块。
那些可以用浮点格式的域用红色标识。
域参数显示... 有效输入A_C1ENA 联系1 是否被允许的状态。
状态输入于激活域。
显示是或否。
是,否A_C2ENA 联系2 是否被允许的状态。
状态输入于激活域。
显示是或否。
是,否A_HI1 联系1的高限。
值输入于 C1-OFF 域。
数字值A_HI2 联系2的高限。
值输入于 C2-OFF 域。
数字值A_IOAD1 输入于低联系数据组框 I/O 地址域的 I/O 地址。
参见I/O 驱动器手册查看有效输入A_IOAD2 输入于高联系数据组框 I/O 地址域的 I/O 地址。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
CatalogDB: 8:03:29 2015/10/2: DONE Adding Catalog File (16ms): Package_686_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:30 2015/10/2: DONE Adding Catalog File (16ms): Package_699_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (15ms): Package_700_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:30 2015/10/2: DONE Adding Catalog File (109ms): Package_695_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:30 2015/10/2: DONE Adding Catalog File (0ms): Package_696_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:30 2015/10/2: DONE Adding Catalog File (0ms): Package_697_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:30 2015/10/2: DONE Adding Catalog File (16ms): Package_698_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:29 2015/10/2: DONE Adding Catalog File (47ms): Package_692_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:30 2015/10/2: DONE Adding Catalog File (32ms): Package_694_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 20 (15ms): Package_702_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (16ms): Package_704_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:28 2015/10/2: DONE Adding Catalog File (0ms): Package_679_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:28 2015/10/2: DONE Adding Catalog File (16ms): Package_680_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (15ms): Package_722_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (15ms): Package_723_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:29 2015/10/2: DONE Adding Catalog File (0ms): Package_681_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:29 2015/10/2: DONE Adding Catalog File (31ms): Package_682_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (32ms): Package_709_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (0ms): Package_710_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (16ms): Package_724_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (0ms): Package_725_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:28 2015/10/2: DONE Adding Catalog File (0ms): Package_668_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:28 2015/10/2: DONE Adding Catalog File (0ms): Package_669_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (0ms): Package_707_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (0ms): Package_708_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:29 2015/10/2: DONE Adding Catalog File (62ms): Package_683_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:29 2015/10/2: DONE Adding Catalog File (0ms): Package_684_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:28 2015/10/2: DONE Adding Catalog File (16ms): Package_670_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:28 2015/10/2: DONE Adding Catalog File (16ms): Package_671_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (0ms): Package_713_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:31 2015/10/2: DONE Adding Catalog File (0ms): Package_714_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:28 2015/10/2: DONE Adding Catalog File (78ms): Package_672_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
CatalogDB: 8:03:28 2015/10/2: DONE Adding Catalog File (16ms): Package_678_for_KB3093266~31bf3856ad364e35~amd64~~10.0.1.4.cat
