毕设外文翻译
毕业设计外文翻译原文.

Optimum blank design of an automobile sub-frameJong-Yop Kim a ,Naksoo Kim a,*,Man-Sung Huh baDepartment of Mechanical Engineering,Sogang University,Shinsu-dong 1,Mapo-ku,Seoul 121-742,South KoreabHwa-shin Corporation,Young-chun,Kyung-buk,770-140,South KoreaReceived 17July 1998AbstractA roll-back method is proposed to predict the optimum initial blank shape in the sheet metal forming process.The method takes the difference between the ®nal deformed shape and the target contour shape into account.Based on the method,a computer program composed of a blank design module,an FE-analysis program and a mesh generation module is developed.The roll-back method is applied to the drawing of a square cup with the ¯ange of uniform size around its periphery,to con®rm its validity.Good agreement is recognized between the numerical results and the published results for initial blank shape and thickness strain distribution.The optimum blank shapes for two parts of an automobile sub-frame are designed.Both the thickness distribution and the level of punch load are improved with the designed blank.Also,the method is applied to design the weld line in a tailor-welded blank.It is concluded that the roll-back method is an effective and convenient method for an optimum blank shape design.#2000Elsevier Science S.A.All rights reserved.Keywords:Blank design;Sheet metal forming;Finite element method;Roll-back method1.IntroductionIt is important to determine the optimum blank shape of a sheet metalpart.However,because its deformation during the forming process is very complicated,it is not easy to design the optimum blank shape even by the skilled labor based on the experience of many years.Recently,computa-tional analysis for a complex automobile part has been able to be carried out easily due to improved computer perfor-mance and the numerical analysis technique.In the analysis process,all kinds of variables that affect the deformation should be considered.The optimum blank shape leads to the prevention of tearing,uniform thickness distribution and to the reduction of the press load during drawing.If the blank shape is designed optimally,the formability will be increased and the ®nal product will require the least amount of trimming at the end of theprocess.Therefore,it is desirable to design the blank shape with a uniform ¯ange of its periphery after deep drawing.Several numerical solutions for the deep drawing process of non-circular components have been reported.Hasek and Lange [1]gave an analytical solution to this problem usingthe slip-line ®eld-method with the assumption of plane-strain ¯ange deformation.Also,Jimma [2]and Karima [3]used the same method.V ogel and Lee [4]and Chen and Sowerby [5]developed ideal blank shapes by the method of plane-stress characteristics.Sowerby et al.[6]developed a geometric mapping method providing a trans-formation between a ¯at sheet and the ®nal surface.Majlessi and Lee [7,8]developed a multi-stage sheet metal forming analysis method.Chung and Richmond [9±12]determined ideal con®gurations for both the initial and the intermediate stages that are required to form a speci®ed ®nal shape using the ideal forming theory.Lee and Huh [13]introduced a three-dimensional multi-step inverse method for the optimum design of blank shapes.Toh and Kobayashi [14]developed arigid±plastic ®nite-element method for the drawing of general shapes based on membrane theory and ®nite-strain formulations.Zhaotao [15]used the boundary element method for a 2D potential problem to design optimum blank shapes.This paper presents an optimum design method of blank shapes for the square cup drawing process considering process variables.An optimum blank shape of square cup drawing was obtained using the proposed method.Also,it was applied to the deep drawing of an automobile sub-frame,and an optimum blank shape with a uniform ¯ange at its periphery weredetermined.Journal of Materials Processing Technology 101(200031±43*Corresponding author.Tel.: 82-2-705-8635;fax: 82-2-712-0799.E-mailaddress :nskim@ccs.sogang.ac.kr (Naksoo Kim0924-0136/00/$±see front matter #2000Elsevier Science S.A.All rights reserved.PII:S 0924-0136(9900436-72.Design of optimum blank shapeThe de®nition of the optimum blank shape is the mini-mization of the difference between the outer contour of the deformed blank and the target contour that indicates the residual ¯ange of uniform size around the periphery of the product.The target contour is generated from the outer contour of the product and determines an optimum blank shape using the results of ®nite-element simulation with the roll-back method.In the process of blank design the simula-tion is performed using an explicit ®nite-element software PAM-STAMP and the interface program is developed for con-necting the blank design module,the remeshing module,the post-processor module and the FE-analysis package.2.1.Roll-back method`The roll-back method starts by de®ning the target con-tour.After determining the length of the ¯ange that remains around the periphery of the product,the pro®le of the target contour is created by offsetting an equal distance from the outer contour of the product and its mesh system is gener-ated by beam elements.The process of blank design is illustrated in Fig.1.The mesh system of the prepared square blank for initial analysis is shown in Fig.1(a.After an analysis,the mesh system of the deformed blank and the target contour are shown in Fig.1(b.At the ¯ange of the deformed blank,a distinction is made between the interior ¯ange within the target contour and the exterior ¯ange out ofthe target contour.The ¯ange out of the target contour is the part that will be trimmed and the ¯ange within the target contour is the part which does not keep shape is due to the incompletion of the blank shape.Thus the modi®ed blank shape should be designed to take the shape of the outer contour of the product completely.The contour of themodi®ed blank shape using the roll-back method and the initial blank shape is shown in Fig.1(c.The mesh system of the modi®ed blank shape for FE-analysis is shown in Fig.1(d.The blank design method will be introduced in detail.The quarter of the deformed blank and the target contour are shown in Fig.2(a.According to the previous explanation,the remained ¯ange can be divided into the interior and the exterior ¯ange.The design process of region A is shown in Fig.2(b.In the mesh of the deformed blank a square grid IJKL on the target contour will be considered,and then the internal dividing point Q in will be calculated at the ratio of m tonFig.1.Illustrating the process of ®nding the optimum blank:(ainitial blankshape;(bdeformed blank and target contour;(croll-back blank and contour;(dmodi®ed blankshape.Fig.2.The roll-back process of a mesh located on the surface of the ¯ange:(aa mesh located on the surface of the ¯ange;(bregion A:residual drawing part out of target contour;(cregion B:residual drawing part inside the target contour.32J.-Y.Kim et al./Journal of Materials Processing Technology 101(200031±43between the node J and K.This point is mapped back into the mesh system of the initial blank.The internal dividing point Q H in is calculated at the ratio of m to n between the same node J H and K H.The following process is performed on the element of the deformed blank on the target contour.The describing point of the outer contour of themodi®ed blank shape can be calculated.If the coordinates of the nodes J and K areJ(x1,y1,K(x2,y2and the coordinates of the nodes J H and K H are J H x H1Y y H1 Y K H x H2Y y H2 ,the ratio of m to n ism X n JQJKX QKJK(1The coordinate of the internal dividing point Q H in can be expressed asQ H inmx H2 nx H1m nYmy H2 ny H1m n(2The design process of region B is shown in Fig.2(c.In the mesh of the deformed blank a square grid MNOP of which the outward edge crosses the target contour should be considered,and then the external dividing point Q out can be calculated at the ratio of m to n between nodes O and P.This point is mapped back into the mesh system of the initial blank.The external dividing point Q H out can be calculated at the ratio of m to nbetween the same nodes Q H and P H.If the coordinates of the nodes O and P areO(x1,y1,P(x2,y2and the coordinates of the O H and P H are O H x H1Y y H1 Y P H xH2Y y H2 ,the ratio of m to n ism X n OQOPX QPOP(3The coordinate of the external dividing point Q H out can be expressed asQ H outmx H2Ànx H1Ymy H2Àny H1(4The following process is performed on all the element of the deformed blank related on the target contour.The points describing the outer contour of modi®ed blank shape can be calculated.When all points of two cases are connected by the spline,the outer contour of modi®ed blank can be described.This process is shown in Fig.3.2.2.The development of the optimum blank design programTo optimize the initial blank shape,a design program was developed following the prescribing method and procedures. This program consists of the blank shaper designmodule, the mesh generation module and the post-processor module. The whole procedure is illustrated in Fig.4.To perform the design process of a blank shape,an interface module is needed.This module is developed to read the output®le of ®nite-element analysis and design the optimum blank shape and generate theinput®le.3.Designs of blank shape and application3.1.Blank design of a square cupTo verify the validity of the roll-back method,it is applied to the process of square cup deep drawing.Several numerical solutions of the deep drawing process for non-circular components have been reported recently.The pub-lished blank shapes by Lee and coworkers[16±18]are compared with the resultusing the roll-back method.The Fig.3.Flowchart of the blank design module.Fig.4.Flow chart of the main program.J.-Y.Kim et al./Journal of Materials Processing Technology101(200031±4333dimensions of the die and punch set for an analysis are shown in Fig.5.The material of the sheet metal is cold-rolled steel for an automobile part.The following are the material propertiesand process variables.Stress±strain relation:"s58X 78Â 0X 00003 "e0X 274 kgf a mm 2 ;Lankford value:"R 1X 679;initial blank size:160mm Â160mm square blank;initial thickness:t 0.69mm;friction coef®cient:m 0.123;and blank-holding force:4000kgf (1kgf 9.81N.The deformed shapes of the square cup obtained from the initial blank and the optimum blank are shown in Fig.6.Inthe present work the optimum blank shape for a square cup that is of 40mm height and 5mm width of ¯ange will be determined.Each modi®ed blank shape after the application of the roll-back method is illustrated in Fig.7.When an 160mm Â160mm square blank is used for an initial blank the outer contour of deformed blank is shown in Fig.7(a.A ®rst modi®ed blank shape can be calculated with the result of the initial square blank.An analysis result is shown inFig.7(b.The difference between the deformed shape and the target contour issigni®cant.If the blank design process is repeated several times the difference decreases and con-verges to zero.Hence a square cup with a uniform ¯ange at its periphery can be made.The comparison between the ®nal result and a published result is shown in Fig.8.In the transverse direction the optimum blank shape using the roll-back method is larger than the published result.The load±displacement curves in square cup drawing process with various initial blank shapes are shown in Fig.9.As the modi®cation is repeated,the gap of the load±displacement curves before and after iteration decreases.Thus after the third modi®cation the maximum value of the load becomes the mean value between that of the ®rst and second modi®cation.After three modi®cations the optimum blank shape is determined,then the result with the optimum blank shape is compared with results in the literature.The thickness strain distribution in the diagonal direction is shown in Fig.10(a,whilst the thickness strain distribution in the transverse direction is shown in Fig.10(b.In the thickness strain distribution the result using the roll-back method is slightly different from the published result,but the overall strain distributions are quite similar.It is thus veri®ed that the roll-back method is a useful approach in the design of optimum blank shapes.3.2.Blank design of the left member of a front sub-frameAn analysis for members of a box-type front sub-frame is performed.The left member is selected as one of the subjects for analysis because its shape is shallow but complex.Fig.11shows the manufacturing set-up as modeled for the numer-ical simulation.The left member requires a uniform ¯ange for the spot welding between the upper and the lower parts besides the improvement of formability.It is recommended that the length of uniform ¯ange is 30mm.The target contour is de®ned at the position which is 30mm from the outer contour of product and is shown in Fig.12.Its mesh system is generated by beam elements.The material of the sheet metal is SAPH38P,a hot-rolled steel for automobile parts.The following are the material properties and process variables.Stress±strain relationship:"s 629Â"e 0X 274(MPa;Lankford value:"R1X 030;initial thickness:t 2.3mm;friction coef®cient:m 0.1;blank holding pressure:1MPa.Fig.5.Geometrical description of the tooling for the deep drawing of a square cup (dimensions:mm.Fig.6.The deformed shape of square cups with FE-mesh geometry where the cup height is 40mm:(adeformed shape of the square cup obtained from the initialblank;(bdeformed shape of the square cup obtained from the optimum blank.34J.-Y.Kim et al./Journal of Materials Processing Technology 101(200031±43A hexagonal blank is used as the initial blank.After three modi®cations the optimum blank shape is determined.For this case,the load±displacement curves with various blank shapes are shown in Fig.13.The comparison of the initial ¯ange and the deformed ¯ange with various blank shapes is shown in Fig.14.As the modi®cation is repeated,the maximum punch load is reduced and the outer contour may be drawn to the target contour at the same time.The thickness distribution is improved step by step;the thickness distribution with various blank shapes being shown in Fig.15.The comparison between the optimum blank shape designed by the roll-back method and the blank shape for mass production is illustrated in Fig.16.The optimum blank shape shows curvature because the outer contour of the product and the ¯ow rate of the sheet metal are considered.However,the blank shape for mass production is simple and straight because the convenience of cutting is considered.To verify the result an initial blank cut by a laser-cutting machine was prepared.The ®nal shape drawn with the initial blank in the press shop isshownparison of the initial ¯ange shapes and the deformed ¯angeshapes:(ainitial square blank;(b®rst modi®ed blank;(csecond modi®ed blank;(dthird modi®edblank.parison of the initial blank contour between the roll-back method and Huh's method.J.-Y.Kim et al./Journal of Materials Processing Technology 101(200031±4335in Fig.17.It had a ¯ange of uniform size around its periphery.The thickness distribution at the position of four sections in the longitudinal direction of the left member was mea-sured.Fig.18shows a comparison of thickness between the computed results and the experimental results in each sec-tion.In section A,the thickness distribution has some error at the end of the ¯ange,whilst in sections B and C,the computed results are compatible with the experimental results.In section D,the computed results predicted that a split might happen,but the experimental cup did notsplit.Fig.9.Load±displacement curves in the square cup drawing process with various initial blankshapes.Fig.10.Thickness strain distribution in a square cup:(adiagonal direction;(btransversedirection.Fig.11.FE-model for a sub-frame left member.If the initial blank shape,the ®nal shape and thickness distribution are considered,the results predicted by the roll-back method has a good agreement with the experimental values.Therefore,as well as the roll-back method being applicable to a simple shape,it can be applied to a complex and large shape.3.3.Blank design of No.2member of front sub-frameAn analysis of No.2member is performed,with its deep and complex shape.Its optimum blank shape is designed using the roll-back method.Fig.19shows the manufacturing set-up as modeled for the numerical simulation.Because its drawing depth is very deep,eccentricity may occur due to the blank initial position or shape.Thus the target contour is de®ned at the position that is 40mm from the outer contour of product and it is shown in Fig.20.A square blank is used as the initial blank.After threemodi®cations the optimum blank shape isdetermined.Fig.12.Target contour for the leftmember.Fig.13.Load±displacement curves in the left member drawing process with various blankparison of the initial ¯ange shapes and the deformed ¯ange shapes:(ainitial blank;(b®rst modi®ed blank;(csecond modi®ed blank;(dthird modi®ed blank.Fig.15.Thickness distribution with various blank shapes(unit:mm:(ainitial blank;(b®rst modi®ed blank;(csecond modi®ed blank;(dthird modi®ed blank.parison of the initial blank shapes predicted by the roll-back method and those designed by skilled labor.For this case,load±displacement curves for various blank shapes are shown in Fig.21,whilst a comparison of the initial ¯ange and the deformed ¯ange with various blank shapes in shown in Fig.22.The thickness distribution with the initial shape is shown in Fig.23,whilst the thickness distribution with the optimum blank shape is shown in Fig.24.The thickness distribution of the side-wall and of the ®llet connecting the side-wall to the top isimproved.Fig.17.Left member drawn in the press shop with the initial blank predicted by the roll-backmethod.Fig.18.(aSections for measuring the thickness distribution.(b±eThickness distributions at sections A±D,respectively.3.4.Design of the welding line with TWB analysis of No.2memberAfter designing the optimum blank shape of No.2member,a tailor-welded blank is applied to this member.To reduce the weight of the sub-frame,structural analysis is performed.On the area where the stress intensity level is low,it is proposed to reduce the thickness locally.Therefore,it is required to design a tailor-welded blank that makes a speci®ed shape after deformation.When two sheet metals of different thickness are welded together,their metal ¯ow is different from that of sheet metal of the same thickness.Thus it is dif®cult to design the location of the weld line.In this simulation the weld line is designed by the use of the roll-back method and the welding line should be located at the speci®ed position after deformation:the speci®ed position is 120mm on both sides of the centerline.Thus the target line is de®ned and meshed by beam elements.The outer contour of TWB and the welding line are shown in Fig.25,and the results are shown in Figs.26and 27.The welding lines can be reached to the target line but,on the top of the blank that has the lower thickness,fracture may occur.This is the same as the result that in the deep drawing of a tailor-welded blank with different thickness,failure occurred at the ¯at bottom of the punch parallel to the weld line.This is due to the deformation not beingdis-Fig.19.FE-model for the sub-frame leftmember.Fig.20.Target contour for the No.2member.Fig.21.Load±displacement curves in the No.2member drawing process with various blank shapes.J.-Y. Kim et al. / Journal of Materials Processing Technology 101 (2000 31±43 41 Fig. 23. Thickness distribution with the initial blank shape (unit: mm: (a front view; (b rear view. Fig. 24. Thickness distribution with the optimum blank shape (unit: mm: (a front view; (b rear view. Fig. 22. Comparison of the initial ¯ange shapes and the deformed ¯ange shapes: (a initial blank; (b ®rst modi®ed blank; (c second modi®ed blank; (d third modi®ed blank. Fig. 25. Comparison of the weld line between the initial blank shape and the deformed blank shape.42 J.-Y. Kim et al. / Journal of Materials Processing Technology 101 (2000 31±43 4. Conclusions In this paper the roll-back method that designs an optimum blank shape is proposed. Based on the method, a computer program composed of a blank design module,an FE-analysis program and a mesh generation module is developed and it is applied to the deep drawing of a front sub-frame. The results of the present paper are summarized as follows: 1. To verify the validity of the proposed method it is applied to the deep drawing of a square cup. The outer contour may be drawn to the target contour. 2. The roll-back method is applied to the optimum blank design of a left member of an automobile sub-frame. The thickness distribution and the load level are improved. When the initial blank shape, the ®nal shape and thickness distribution are compared, the results predicted by the roll-back method have a good agreement with the experimental results. It is concluded that this method can be applied to the deep drawing of the complex automobile parts. 3. The analysis of No. 2 member with a tailor-welded blank is performed. The position of welding lines on the initial blank is designed. The roll-back method can be applied to the design of the welding line position. 4. In most cases, the edge of blank takes the shape of the target contour within a few iterations, which shows that the roll-back method is an effective and convenient method for an optimum blank shape design. Fig. 26. Deformed shape of No. 2 member with the tailor-welded blank. Fig. 27. Deformed shape of No. 2 member with the tailor-welded blank: (a front view; (b rear view. tributed uniformly, most of the stretching being concentrated on the side of the blank with lower strength. The process condition without fracture should be determined for the combination of the drawing depth and the two different thickness as shown in Fig.28. References [1] V.V. Hasek, K. Lange, Use of slip line ®eld method in deep drawing of large irregular shaped components, Proceedings of the Seventh NAMRC, Ann Arbor, MI, 1979, pp. 65±71. [2] T. Jimma, Deep drawing convex polygon shell researches on the deep drawing of sheet metal by the slip line theory. First report, Jpn. Soc. Tech. Plasticity 11 (116 (1970 653±670. [3] M. Karima, Blank development and tooling design for drawn parts using a modi®ed slip line ®eld based approach, ASME Trans. 11 (1989 345±350. [4] J.H. Vogel, D. Lee, An analysis method for deep drawing process design, Int. J. Mech. Sci. 32 (1990 891. [5] X. Chen, R. Sowerby, The development of ideas blank shapes by the method of plane stress characteristics, Int. J. Mech. Sci. 34 (2 (1992159±166. [6] R. Sowerby, J.L. Duncan, E. Chu, The modelling of sheet metal stamping, Int. J. Mech. Sci. 28 (7 (1986 415±430. [7] S.A. Majlessi, D. Lee, Further development of sheet metal forming analysis method, ASME Trans. 109 (1987 330±337. [8] S.A. Majlessi, D. Lee, Development of multistage sheet metal forming analysis method, J. Mater. Shap. Technol. 6 (1 (1988 41± 54. [9] K. Chung, O. Richmond, Ideal forming-I. Homogeneous deformation with minimum plastic work, Int. J. Mech. Sci. 34 (7 (1992 575±591. [10] K. Chung, O. Richmond, Ideal forming-II. Sheet forming with optimum deformation, Int. J. Mech. Sci. 34 (8 (1992 617±633. Fig. 28. Thickness distribution with the tailor-welded blank (unit: mm: (a front view; (b rear view.J.-Y. Kim et al. / Journal of Materials Processing Technology 101 (2000 31±43 [11] K. Chung, O. Richmond, Sheet forming process design based on ideal forming theory, Proceedings of the Fourth International Conference on NUMIFORM, 1992, pp. 455±460.[12] K. Chung, O. Richmond, The mechanics of ideal forming, ASME Trans. 61 (1994 176±181. [13] C.H. Lee, H. Huh, Blank design and strain prediction of automobile stamping parts by and inverse ®nite element approach, J. Mater. Process. Technol. 63 (1997 645±650. [14] C.H. Toh, S. Kobayashi, Deformation analysis and blank design in square cup drawing, Int. J. Mech. Tool Des. Res. 25 (1 (1985 15± 32. 43 [15] Z. Zhatao, L. Bingwen, Determination of blank shapes for drawing irregular cups using and electrical analogue methods, Int. J. Mech. Sci. 28 (8 (1986 499±503. [16] H. Huh, S.S. Han, Analysis of square cup deep drawing from two types of blanks with a modi®ed membrane ®nite element method, Trans. KSME 18 (10 (1994 2653±2663. [17] C.H. Lee, H. Huh, Blank design and strain prediction in sheet metal forming process, Trans. KSME A 20 (6 (1996 1810±1818. [18] C.H. Lee, H. Huh, Three-dimensional multi-step inverse analysis for optimum design of initial blank in sheet metal forming, Trans. KSME A 21 (12 (1997 2055±2067.。
毕业设计外文翻译_英文版

A Design and Implementation of Active NetworkSocket ProgrammingK.L. Eddie Law, Roy LeungThe Edward S. Rogers Sr. Department of Electrical and Computer EngineeringUniversity of TorontoToronto, Canadaeddie@, roy.leung@utoronto.caAbstract—The concept of programmable nodes and active networks introduces programmability into communication networks. Code and data can be sent and modified on their ways to destinations. Recently, various research groups have designed and implemented their own design platforms. Each design has its own benefits and drawbacks. Moreover, there exists an interoperability problem among platforms. As a result, we introduce a concept that is similar to the network socket programming. We intentionally establish a set of simple interfaces for programming active applications. This set of interfaces, known as Active Network Socket Programming (ANSP), will be working on top of all other execution environments in future. Therefore, the ANSP offers a concept that is similar to “write once, run everywhere.” It is an open programming model that active applications can work on all execution environments. It solves the heterogeneity within active networks. This is especially useful when active applications need to access all regions within a heterogeneous network to deploy special service at critical points or to monitor the performance of the entire networks. Instead of introducing a new platform, our approach provides a thin, transparent layer on top of existing environments that can be easily installed for all active applications.Keywords-active networks; application programming interface; active network socket programming;I. I NTRODUCTIONIn 1990, Clark and Tennenhouse [1] proposed a design framework for introducing new network protocols for the Internet. Since the publication of that position paper, active network design framework [2, 3, 10] has slowly taken shape in the late 1990s. The active network paradigm allows program code and data to be delivered simultaneously on the Internet. Moreover, they may get executed and modified on their ways to their destinations. At the moment, there is a global active network backbone, the ABone, for experiments on active networks. Apart from the immaturity of the executing platform, the primary hindrance on the deployment of active networks on the Internet is more on the commercially related issues. For example, a vendor may hesitate to allow network routers to run some unknown programs that may affect their expected routing performance. As a result, alternatives were proposed to allow active network concept to operate on the Internet, such as the application layer active networking (ALAN) project [4] from the European research community. In the ALAN project, there are active server systems located at different places in the networks and active applications are allowed to run in these servers at the application layer. Another potential approach from the network service provider is to offer active network service as the premium service class in the networks. This service class should provide the best Quality of Service (QoS), and allow the access of computing facility in routers. With this approach, the network service providers can create a new source of income.The research in active networks has been progressing steadily. Since active networks introduce programmability on the Internet, appropriate executing platforms for the active applications to execute should be established. These operating platforms are known as execution environments (EEs) and a few of them have been created, e.g., the Active Signaling Protocol (ASP) [12] and the Active Network Transport System (ANTS) [11]. Hence, different active applications can be implemented to test the active networking concept.With these EEs, some experiments have been carried out to examine the active network concept, for example, the mobile networks [5], web proxies [6], and multicast routers [7]. Active networks introduce a lot of program flexibility and extensibility in networks. Several research groups have proposed various designs of execution environments to offer network computation within routers. Their performance and potential benefits to existing infrastructure are being evaluated [8, 9]. Unfortunately, they seldom concern the interoperability problems when the active networks consist of multiple execution environments. For example, there are three EEs in ABone. Active applications written for one particular EE cannot be operated on other platforms. This introduces another problem of resources partitioning for different EEs to operate. Moreover, there are always some critical network applications that need to run under all network routers, such as collecting information and deploying service at critical points to monitor the networks.In this paper, a framework known as Active Network Socket Programming (ANSP) model is proposed to work with all EEs. It offers the following primary objectives.• One single programming interface is introduced for writing active applications.• Since ANSP offers the programming interface, the design of EE can be made independent of the ANSP.This enables a transparency in developing andenhancing future execution environments.• ANSP addresses the interoperability issues among different execution environments.• Through the design of ANSP, the pros and cons of different EEs will be gained. This may help design abetter EE with improved performance in future.The primary objective of the ANSP is to enable all active applications that are written in ANSP can operate in the ABone testbed . While the proposed ANSP framework is essential in unifying the network environments, we believe that the availability of different environments is beneficial in the development of a better execution environment in future. ANSP is not intended to replace all existing environments, but to enable the studies of new network services which are orthogonal to the designs of execution environments. Therefore, ANSP is designed to be a thin and transparent layer on top of all execution environments. Currently, its deployment relies on automatic code loading with the underlying environments. As a result, the deployment of ANSP at a router is optional and does not require any change to the execution environments.II. D ESIGN I SSUES ON ANSPThe ANSP unifies existing programming interfaces among all EEs. Conceptually, the design of ANSP is similar to the middleware design that offers proper translation mechanisms to different EEs. The provisioning of a unified interface is only one part of the whole ANSP platform. There are many other issues that need to be considered. Apart from translating a set of programming interfaces to other executable calls in different EEs, there are other design issues that should be covered, e.g., • a unified thread library handles thread operations regardless of the thread libraries used in the EEs;• a global soft-store allows information sharing among capsules that may execute over different environmentsat a given router;• a unified addressing scheme used across different environments; more importantly, a routing informationexchange mechanism should be designed across EEs toobtain a global view of the unified networks;• a programming model that should be independent to any programming languages in active networks;• and finally, a translation mechanism to hide the heterogeneity of capsule header structures.A. Heterogeneity in programming modelEach execution environment provides various abstractions for its services and resources in the form of program calls. The model consists of a set of well-defined components, each of them has its own programming interfaces. For the abstractions, capsule-based programming model [10] is the most popular design in active networks. It is used in ANTS [11] and ASP [12], and they are being supported in ABone. Although they are developed based on the same capsule model, their respective components and interfaces are different. Therefore, programs written in one EE cannot run in anther EE. The conceptual views of the programming models in ANTS and ASP are shown in Figure 1.There are three distinct components in ANTS: application, capsule, and execution environment. There exist user interfaces for the active applications at only the source and destination routers. Then the users can specify their customized actions to the networks. According to the program function, the applications send one or more capsules to carry out the operations. Both applications and capsules operate on top of an execution environment that exports an interface to its internal programming resources. Capsule executes its program at each router it has visited. When it arrives at its destination, the application at destination may either reply it with another capsule or presents this arrival event to the user. One drawback with ANTS is that it only allows “bootstrap” application.Figure 1. Programming Models in ASP and ANTS.In contrast, ASP does not limit its users to run “bootstrap” applications. Its program interfaces are different from ANTS, but there are also has three components in ASP: application client, environment, and AAContext. The application client can run on active or non-active host. It can start an active application by simply sending a request message to the EE. The client presents information to users and allows its users to trigger actions at a nearby active router. AAContext is the core of the network service and its specification is divided into two parts. One part specifies its actions at its source and destination routers. Its role is similar to that of the application in ANTS, except that it does not provide a direct interface with the user. The other part defines its actions when it runs inside the active networks and it is similar to the functional behaviors of a capsule in ANTS.In order to deal with the heterogeneity of these two models, ANSP needs to introduce a new set of programming interfaces and map its interfaces and execution model to those within the routers’ EEs.B. Unified Thread LibraryEach execution environment must ensure the isolation of instance executions, so they do not affect each other or accessThe authors appreciate the Nortel Institute for Telecommunications (NIT) at the University of Toronto to allow them to access the computing facilitiesothers’ information. There are various ways to enforce the access control. One simple way is to have one virtual machine for one instance of active applications. This relies on the security design in the virtual machines to isolate services. ANTS is one example that is using this method. Nevertheless, the use of multiple virtual machines requires relatively large amount of resources and may be inefficient in some cases. Therefore, certain environments, such as ASP, allow network services to run within a virtual machine but restrict the use of their services to a limited set of libraries in their packages. For instance, ASP provides its thread library to enforce access control. Because of the differences in these types of thread mechanism, ANSP devises a new thread library to allow uniform accesses to different thread mechanisms.C. Soft-StoreSoft-store allows capsule to insert and retrieve information at a router, thus allowing more than one capsules to exchange information within a network. However, problem arises when a network service can execute under different environments within a router. The problem occurs especially when a network service inserts its soft-store information in one environment and retrieves its data at a later time in another environment at the same router. Due to the fact that execution environments are not allowed to exchange information, the network service cannot retrieve its previous data. Therefore, our ANSP framework needs to take into account of this problem and provides soft-store mechanism that allows universal access of its data at each router.D. Global View of a Unified NetworkWhen an active application is written with ANSP, it can execute on different environment seamlessly. The previously smaller and partitioned networks based on different EEs can now be merging into one large active network. It is then necessary to advise the network topology across the networks. However, different execution environments have different addressing schemes and proprietary routing protocols. In order to merge these partitions together, ANSP must provide a new unified addressing scheme. This new scheme should be interpretable by any environments through appropriate translations with the ANSP. Upon defining the new addressing scheme, a new routing protocol should be designed to operate among environments to exchange topology information. This allows each environment in a network to have a complete view of its network topology.E. Language-Independent ModelExecution environment can be programmed in any programming language. One of the most commonly used languages is Java [13] due to its dynamic code loading capability. In fact, both ANTS and ASP are developed in Java. Nevertheless, the active network architecture shown in Figure 2 does not restrict the use of additional environments that are developed in other languages. For instance, the active network daemon, anted, in Abone provides a workspace to execute multiple execution environments within a router. PLAN, for example, is implemented in Ocaml that will be deployable on ABone in future. Although the current active network is designed to deploy multiple environments that can be in any programming languages, there lacks the tool to allow active applications to run seamlessly upon these environments. Hence, one of the issues that ANSP needs to address is to design a programming model that can work with different programming languages. Although our current prototype only considers ANTS and ASP in its design, PLAN will be the next target to address the programming language issue and to improve the design of ANSP.Figure 2. ANSP Framework Model.F. Heterogeneity of Capsule Header StructureThe structures of the capsule headers are different in different EEs. They carries capsule-related information, for example, the capsule types, sources and destinations. This information is important when certain decision needs to be made within its target environment. A unified model should allow its program code to be executed on different environments. However, the capsule header prevents different environments to interpret its information successfully. Therefore, ANSP should carry out appropriate translation to the header information before the target environment receives this capsule.III. ANSP P ROGRAMMING M ODELWe have outlined the design issues encountered with the ANSP. In the following, the design of the programming model in ANSP will be discussed. This proposed framework provides a set of unified programming interfaces that allows active applications to work on all execution environments. The framework is shown in Figure 2. It is composed of two layers integrated within the active network architecture. These two layers can operate independently without the other layer. The upper layer provides a unified programming model to active applications. The lower layer provides appropriate translation procedure to the ANSP applications when it is processed by different environments. This service is necessary because each environment has its own header definition.The ANSP framework provides a set of programming calls which are abstractions of ANSP services and resources. A capsule-based model is used for ANSP, and it is currently extended to map to other capsule-based models used in ANTSand ASP. The mapping possibility to other models remains as our future works. Hence, the mapping technique in ANSP allows any ANSP applications to access the same programming resources in different environments through a single set of interfaces. The mapping has to be done in a consistent and transparent manner. Therefore, the ANSP appears as an execution environment that provides a complete set of functionalities to active applications. While in fact, it is an overlay structure that makes use of the services provided from the underlying environments. In the following, the high-level functional descriptions of the ANSP model are described. Then, the implementations will be discussed. The ANSP programming model is based upon the interactions between four components: application client , application stub , capsule , and active service base.Figure 3. Information Flow with the ANSP.•Application Client : In a typical scenario, an active application requires some means to present information to its users, e.g., the state of the networks. A graphical user interface (GUI) is designed to operate with the application client if the ANSP runs on a non-active host.•Application Stub : When an application starts, it activates the application client to create a new instance of application stub at its near-by active node. There are two responsibilities for the application stub. One of them is to receive users’ instructions from the application client. Another one is to receive incoming capsules from networks and to perform appropriate actions. Typically, there are two types of actions, thatare, to reply or relay in capsules through the networks, or to notify the users regarding the incoming capsule. •Capsule : An active application may contain several capsule types. Each of them carries program code (also referred to as forwarding routine). Since the application defines a protocol to specify the interactions among capsules as well as the application stubs. Every capsule executes its forwarding routine at each router it visits along the path between the source and destination.•Active Service Base : An active service base is designed to export routers’ environments’ services and execute program calls from application stubs and capsules from different EEs. The base is loaded automatically at each router whenever a capsule arrives.The interactions among components within ANSP are shown in Figure 3. The designs of some key components in the ANSP will be discussed in the following subsections. A. Capsule (ANSPCapsule)ANSPXdr decode () ANSPXdr encode () int length ()Boolean execute ()New types of capsule are created by extending the abstract class ANSPCapsule . New extensions are required to define their own forwarding routines as well as their serialization procedures. These methods are indicated below:The execution of a capsule in ANSP is listed below. It is similar to the process in ANTS.1. A capsule is in serial binary representation before it issent to the network. When an active router receives a byte sequence, it invokes decode() to convert the sequence into a capsule. 2. The router invokes the forwarding routine of thecapsule, execute(). 3. When the capsule has finished its job and forwardsitself to its next hop by calling send(), this call implicitly invokes encode() to convert the capsule into a new serial byte representation. length() isused inside the call of encode() to determine the length of the resulting byte sequence. ANSP provides a XDR library called ANSPXdr to ease the jobs of encoding and decoding.B. Active Service Base (ANSPBase)In an active node, the Active Service Base provides a unified interface to export the available resources in EEs for the rest of the ANSP components. The services may include thread management, node query, and soft-store operation, as shown in Table 1.TABLE I. ACTIVE SERVICE BASE FUNCTION CALLSFunction Definition Descriptionboolean send (Capsule, Address) Transmit a capsule towards its destination using the routing table of theunderlying environment.ANSPAddress getLocalHost () Return address of the local host as an ANSPAddress structure. This isuseful when a capsule wants to check its current location.boolean isLocal (ANSPAddress) Return true if its input argument matches the local host’s address andreturn false otherwise.createThread () Create a new thread that is a class ofANSPThreadInterface (discussed later in Section VIA “Unified Thread Abstraction”).putSStore (key, Object) Object getSStore (key) removeSStore (key)The soft-store operations are provided by putSStore(), getSSTore(), and removeSStore(), and they put, retrieve, and remove data respectively. forName (PathName) Supported in ANSP to retrieve a classobject corresponding to the given path name in its argument. This code retrieval may rely on the code loading mechanism in the environment whennecessary.C. Application Client (ANSPClient)boolean start (args[])boolean start (args[],runningEEs) boolean start (args[],startClient)boolean start (args[],startClient, runningEE)Application Client is an interface between users and the nearby active source router. It does the following responsibilities.1. Code registration: It may be necessary to specify thelocation and name of the application code in some execution environments, e.g., ANTS. 2. Application initialization: It includes selecting anexecution environment to execute the application among those are available at the source router. Each active application can create an application client instance by extending the abstract class, ANSPClient . The extension inherits a method, start(), to automatically handle both the registration and initialization processes. All overloaded versions of start() accept a list of arguments, args , that are passed to the application stub during its initialization. An optional argument called runningEEs allows an application client to select a particular set of environment variables, specified by a list of standardized numerical environment ID, the ANEP ID, to perform code registration. If this argument is not specified, the default setting can only include ANTS and ASP. D. Application Stub (ANSPApplication)receive (ANSPCapsule)Application stubs reside at the source and destination routers to initialize the ANSP application after the application clients complete the initialization and registration processes. It is responsible for receiving and serving capsules from the networks as well as actions requested from the clients. A new instance is created by extending the application client abstract class, ANSPApplication . This extension includes the definition of a handling routine called receive(), which is invoked when a stub receives a new capsule.IV. ANSP E XAMPLE : T RACE -R OUTEA testbed has been created to verify the design correctnessof ANSP in heterogeneous environments. There are three types of router setting on this testbed:1. Router that contains ANTS and a ANSP daemonrunning on behalf of ASP; 2. Router that contains ASP and a ANSP daemon thatruns on behalf of ANTS; 3. Router that contains both ASP and ANTS.The prototype is written in Java [11] with a traceroute testing program. The program records the execution environments of all intermediate routers that it has visited between the source and destination. It also measures the RTT between them. Figure 4 shows the GUI from the application client, and it finds three execution environments along the path: ASP, ANTS, and ASP. The execution sequence of the traceroute program is shown in Figure 5.Figure 4. The GUI for the TRACEROUTE Program.The TraceCapsule program code is created byextending the ANSPCapsule abstract class. When execute() starts, it checks the Boolean value of returning to determine if it is returning from the destination. It is set to true if TraceCapsule is traveling back to the source router; otherwise it is false . When traveling towards the destination, TraceCapsule keeps track of the environments and addresses of the routers it has visited in two arrays, path and trace , respectively. When it arrives at a new router, it calls addHop() to append the router address and its environment to these two arrays. When it finally arrives at the destination, it sets returning to false and forwards itself back to the source by calling send().When it returns to source, it invokes deliverToApp() to deliver itself to the application stub that has been running at the source. TraceCapsule carries information in its data field through the networks by executing encode() and decode(), which encapsulates and de-capsulates its data using External Data Representation (XDR) respectively. The syntax of ANSP XDR follows the syntax of XDR library from ANTS. length() in TraceCapsule returns the data length, or it can be calculated by using the primitive types in the XDRlibrary.Figure 5. Flow of the TRACEROUTE Capsules.V. C ONCLUSIONSIn this paper, we present a new unified layered architecture for active networks. The new model is known as Active Network Socket Programming (ANSP). It allows each active application to be written once and run on multiple environments in active networks. Our experiments successfully verify the design of ANSP architecture, and it has been successfully deployed to work harmoniously with ANTS and ASP without making any changes to their architectures. In fact, the unified programming interface layer is light-weighted and can be dynamically deployable upon request.R EFERENCES[1] D.D. Clark, D.L. Tennenhouse, “Architectural Considerations for a NewGeneration of Protocols,” in Proc. ACM Sigcomm’90, pp.200-208, 1990. [2] D. Tennenhouse, J. M. Smith, W. D. Sicoskie, D. J. Wetherall, and G. J.Minden, “A survey of active network research,” IEEE Communications Magazine , pp. 80-86, Jan 1997.[3] D. Wetherall, U. Legedza, and J. Guttag, “Introducing new internetservices: Why and how,” IEEE Network Magazine, July/August 1998. [4] M. Fry, A. Ghosh, “Application Layer Active Networking,” in ComputerNetworks , Vol.31, No.7, pp.655-667, 1999.[5] K. W. Chin, “An Investigation into The Application of Active Networksto Mobile Computing Environments”, Curtin University of Technology, March 2000.[6] S. Bhattacharjee, K. L. Calvert, and E. W. Zegura, “Self OrganizingWide-Area Network Caches”, Proc. IEEE INFOCOM ’98, San Francisco, CA, 29 March-2 April 1998.[7] L. H. Leman, S. J. Garland, and D. L. Tennenhouse, “Active ReliableMulticast”, Proc. IEEE INFOCOM ’98, San Francisco, CA, 29 March-2 April 1998.[8] D. Descasper, G. Parulkar, B. Plattner, “A Scalable, High PerformanceActive Network Node”, In IEEE Network, January/February 1999.[9] E. L. Nygren, S. J. Garland, and M. F. Kaashoek, “PAN: a high-performance active network node supporting multiple mobile code system”, In the Proceedings of the 2nd IEEE Conference on Open Architectures and Network Programming (OpenArch ’99), March 1999. [10] D. L. Tennenhouse, and D. J. Wetherall. “Towards an Active NetworkArchitecture”, In Proceeding of Multimedia Computing and Networking , January 1996.[11] D. J. Wetherall, J. V. Guttag, D. L. Tennenhouse, “ANTS: A toolkit forBuilding and Dynamically Deploying Network Protocols”, Open Architectures and Network Programming, 1998 IEEE , 1998 , Page(s): 117 –129.[12] B. Braden, A. Cerpa, T. Faber, B. Lindell, G. Phillips, and J. Kann.“Introduction to the ASP Execution Environment”: /active-signal/ARP/index.html .[13] “The java language: A white paper,” Tech. Rep., Sun Microsystems,1998.。
毕业设计外文翻译

外文文献原稿和译文原稿IntroductionIn the modern industrial control field,along with the rapid developmentof computer technology,the emergence of a new trend o fintelligent control, namely to machinesimulationhuman thinkingmode, using reasoning, deduce and induction,so the means, the production control, thisisartificialintelligence.One expertsystem,fuzzy logicand neuralnetwork is the artificial intelligence of several keyresearch hot spot. Relativeto the expert system,the fuzzy logicbelongs to the category of c omputational mathematicsandcontainthe genetic algorithm,the chaos theoryandlinear theoryetc,it comprehensive of operators practice experience,has thedesign issimple andeasy to use, strong anti-interference abilityand reaction speed,ea sy tocontrol and adaptiveability, etc. In recent years, ina process control,built to touch, estimation, identify,diagnosis, the stockmarket forecast,agriculturalproductionandmilitary sciences toawiderange ofapplications.To carry o ut in-depthresearch and application offuzzy control technology, the paperintroduces thebasic theory offuzzycontrol technology and development,andto some in the application ofthepower electronics areintroduced.Fuzzy Logic andFuzzyControl1,fuzzy logic and fuzzy controlconceptIn1965,the university of California, Berkeley, computer expertsLoftyZadeh put forward"fuzzylogic" concept,the root lies inthearea'slogic orclear logic distribution, usedto define theconfused,unable to quantify orthe problem ofp recision,for ˙ in a man'svonbased on"true-false" reasoningmechanism, and thus createa electronic circuit and integrated circuit of theBoolean algorithm, fuzzy logic to fill thegapsin specialthings insampling and analysis ofblank.On the basisof fuzzy logic fuzzy set theory, aparticular things as the set of features membership, he can be in"is" and"no" within the scop eofthe takebetween any value. And fuzzy logicis reasonablequantitativemathematicaltheory,the mathematical basis forfundamental for isto deal with thesethe statistical uncertai nimprecise information.Fuzzy control based onfuzzylogic isa processo fdescription of the control algorithm.For parameters preciselyknownmathematical model, wecan use Berd grap hor chart toanalyststhe Nyquist process to obtain th eaccuratedesign parameters.Andfor some complex system, such as particle reaction, meteorological forecast equipment, establishing a reasonable and accurate mathematicalmodel is very difficult,and for power transmissionspeedof vectorcontrol problems,although it can be measured byt he modelthat,butfor many variables andnonlinearvariation, the accuratecontrol is very difficult. And fuzzy control technology only on the basis ofthepractical experience and the operator andintuitive inference,also relies ondesign personnel an dresearch and developmentpersonnel of experience and knowledge accumulation,itdoes not needto establish equipment model,so basically is adaptive,and havestrong robustnes s.After manyyears development, therehave been manysuccessful application ofthefuzzy control theory of the case, s uch asRutherford, Carter and Ostergaardwere applied and metallurgical furnaceand heat exchangerscontroldevic e.2,the analysis method is discussedIndustrial control stabilityof the systemisdiscussedthe premise of the problem, because of the nonlinear and not to the unity of the description,make a judgment,sothefuzzy co ntrolsystem analysis method ofstability analysis has beena hot spot,comprehensive in recentyears youof scholars paper published thesystem stability analysis has these several circumstances :1), LiPuYa panov method: direct method based on the discrete t ime (D-T)and continuous time fuzzy control stabilityanalysis and designmethod, the stability condition of the relative comparis onconservative.2), sliding variablestructuresystem analysis method3),round stability criterionmethods: use sector bounded nonlinearconcept, according to the stability criterion, led to the stability of thefuzzycontrol.4),POPOVcriterion5), othermethodssuch asrelationship matrix analys is, exceed stable theory, phase-plane, matrix inequality or conve xoptimization method,fuzzyhole-hole mapping etc, detailed information and relevantliterature many, in this one no longer etc.Set Design ofFuzzy ControlThe design of the fuzzy control is a very complicated process,in general, take thedesign steps and tools is more normative.Thefuzzycontroller generaluse of the special software andhardwa re,universalhardwarechip in on the marketat present ismore, includingmain products are shownbelow. And special IC has developedveryfast,itspecial IC and softwarecont roller integratesin together.In the processof design,thedesignof thegeneral to take stepsfor:1,consideringwhether the subject by fuzzycontrol system.That is considered the routine controlmode ofmay.2, from equipment operation personnel place togetas much information.3 and selecting the mathematical model could, if use the conventionalmethod design,estimate the equipment performance characteristics.4, determinethe fuzzy logiccontrolobject.5, determine the inputand output variables.6,determine thevariables asdetermined the belonging of the range.7, confirmthe variables of the corresponding rules.8, determinethe scale coefficients.9,ifhaveaready-made, mathematical model of fuzzycontroller with already certainof system simulation, observation equipment performance,and constantly adjustrules and scale coefficientsuntilreachingsatisfaction performance. Or to design fuzzy controller.10,real-timeoperation controller, constantly adjust to the best performance.FuzzyControlApplication and ProspectAs artificial intelligence of anewresearch field, thefuzzycontrol absorb lessons from the traditional design method and other newtechnology's essence,in manyfields has madeconsiderableprogress. In the new typeof powerelectronic andautomatic controlsystem,some expertsin the linearadding theconditions ofthe poweramplifier, the application of thefuzzy control based on the servo motor control,in the fuzzycontrol syst em withthe PIDand model referenceadaptive control(MRAC)comparison proved the advantages of the method of fuzzycontrol. Fuzzy turn sentgain tuned controller viewsofthe induction motor drive system vector controlFuzzycontrol as a is the development of new technology, now inmost experts also to focus onapplicationsystemresearch, and make considerable achievement, butin the theory resea rch and system analysisor relative backward, somuch so that some scholars have questionedits theoretical basis andeffective. In view ofthiscanbe clear that the fuzzy control thecombinationof theory and practice isstillneedstobe further explored. Thedevelopment prospects are veryattractive, andin recent years,its theoreticalstudy also madesignificant progress.In thepast forty years of thedevelopment process, the f uzzycontrol alsohas somelimitations: 1) control precisionlo w,performance is not high,stability is poorer;2)theory system is not complete. 3) theadaptive ability low.Fortheseweaknesses,the fuzzy control and someothernew technology, suchas neuralnetwork(NN), genetic algorithm,and t he combination of to a higherlevel ofapplicationdevelopmentexpand the huge space.SummaryFuzzy control as a comprehensiveapplication example, in the globalinformationthe push ofwave, in the nextfewd ecades, to the rapiddevelopment of economy will injectne wvitality,the expert thinks,thenext generation ofindust rial control isthe basis of fuzzy control and neural network, and chaos theory as the pillar oftheartificial intelligence.Wi ththe fuzzycontroltheory research and further more perfect of, the scope ofapplicationofthe growingand supportingthe development and manufactureofIC,thefuzzycontrolwill be open tothe field of industrial automation development oflightapplicationprospect, but also tothevarious areas of the researchers suggestmore important task.译文引言在现代工业控制领域,伴随着计算机技术的突飞猛进,出现了智能控制的新趋势,即以机器模拟人类思维模式,采用推理、演绎和归纳等手段,进行生产控制,这就是人工智能。
毕业设计外文文献翻译

Encoding the Java Virtual Machine’s Instruction Set1 IntroductionThe development of programs that parse and analyze Java Bytecode [9] has a long history and new programs are still developed [2,3,4,7,13]. When developing such tools, however, a lot of effort is spent to develop a parser for the bytecode and for (re-) developing standard control- and data-flow analyses which calculate, e.g., the control-flow graph or the data-dependency graph.To reduce these efforts, we have developed a specification language (OPAL SPL) for encoding the instructions of stack-based intermediate languages. The idea is that—once the instruction set is completely specified using OPAL SPL—generating both bytecode parsers and standard analyses is much easier than their manual development. To support this goal, OPAL SPL supports the specification of both the format of bytecode instructions and the effect on the stack and registers these instructions have when executed. An alternative use of an OPAL SPL specification is as input to a generic parser or to generic analyses as illustrated by Fig. 1Though the language was designed with Java Bytecode specifically in mind and is used to encode the complete instruction set of the Java Virtual Machine (JVM) , we have striven for a Java-independent specification language. In particular, OPAL SPL focuses on specifying the instruction set rather than the complete class file format, not only because the former’s structure is much more regular than the latter’s,but also because a specifi cation of the instruction set promises to be most beneficial. Given the primary focus of OPAL SPL—generating parsers and facilitating basic analyses—we explicitly designed the language such that it is possible to group related instructions. This makes specifications more concise and allows analyses to treat similar instructions in nearly the same way. For example, the JVM’s iload 5 instruction, which loads the integer value stored in register #5, is a special case of the generic iload instruction where the instruction’s operand is 5. We also designed OPAL SPL in such a way that specifications do not prescribe how a framework represents or processes information; i.e., OPAL SPL is representation agnostic.The next section describes the specification langua ge. In Section3we reason about the language’s design by discussing the specification of selected JVM instructions. In Section4the validation of specifications is discussed. The evaluation of the approach is presented in Section5. The paper ends with a discussion of related work and a conclusion.2 Specifying Bytecode InstructionsThe language for specifying bytecode instructions (OPAL SPL) was primarily designed to enable aconcise specification of the JVM’s instruction set. OPAL SPL supports the sp ecification of both an instruction’s format and its effect on the stack and local variables (registers)when the instruction is executed. It is thus possible to specify which kind of values are popped from and pushed onto the stack as well as which local variables are read or written. Given a specification of the complete instruction set the information required by standard control- and data-flow analyses is then available.However, OPAL SPL is not particularly tied to Java as it abstracts from the particularities of the JVM Specification. For example, the JVM’s type system is part of an OPAL SPL specification rather than an integral part of the OPAL SPL language itself.Next, we first give an overview of the language before we discuss its semantics.2.1 SyntaxThe OPAL Specification Language (OPAL SPL) is an XML-based language. Its grammar is depicted in Fig.2using an EBNF-like format. Non-terminals are written in capital letters (INSTRUCTIONS, TYPES, etc.), the names of XML-elements are written in small letters (types, stack, etc.) and the names of XML-attributes start with ―@‖ (@type, @var, etc.). We refer to the content of an XML-element using symbols that start with―/‖ (/V ALUEEXPRESSION, /EXPECTEDV ALUE, etc.). ―<>‖ is used to specify nesting of elements. ―( ),?,+,*,{},|‖ have the usual semantics. For example,exceptions<(exception @type)+>specifies that the XML-elementexceptionshas one or moreexceptionchild elements that always have the attributetype.2.2 SemanticsFormat SpecificationEach specification written in OPAL SPL consists of four major parts (line 1 in Fig.2). The first part(types, lines 2–3) specifies the type system that is used by the underlying virtual machine. The second part (exceptions, line 4) declares the exceptions that may be thrown when instructions are executed. The third part (functions, line 5) declares the functions that are used in instruction specifications. The fourth part is the specification of the instructions themselves (lines 6–12), each of which may resort to the declared functions to access information not simply stored along with the instruction. For example,invoke instructions do not store the signature and declaring class of the called methods. Instead, a reference to an entry in the so-called constant pool is stored. Only this constant pool entry has all information about the method. To obtain, e.g., the return type of the called method, an abstract function TYPE method refreturn type(method ref) is declared that takes a reference to the entry as i nput and returns the method’s return type. Using abstract function declarations, we abstract—in the specification of the instructions—from the concrete representation of such information by the enclosing by tecode toolkit.The specification of an instruction consists of up to four parts:the instruction’s format (lines 7–8), a description of the effect the instruction has on the stack when executed (lines 9–10), a descriptions of theregisters it affects upon execution (lines 11–12), and information about the exceptions that may be thrown during execution (end of line 6). An instruction’s format is specified by sequences which describe how an instruction is stored. Theu1, u2andu4elements (line 8) of each format sequence specify that the current value is an unsigned integer value with 1, 2 and 4 bytes, respectively. Similarly, thei1, i2 andi4 elements (line 8) are used to specify that the current value is a (1, 2 or 4 byte) signed integer value. The values can be bound to variables using thevarat tribute and can be given a second semantics using thetype attribute. For example,<i2 type=‖short‖ var=‖value‖/>is a twobyte signed integer value that is bound to the variable value and has type short with respect to the instruction set’s type system. Additionally, it is possible to specify expected values (line 8). This enables the selection of the format sequence to be used for reading in the instruction. E.g., <sequence><u1 var=‖opcode‖>171</u1>... specifies that this sequence matches if the value of the first byt e is 171. A sequence’s list element is used to specify that a variable number of values need to be read. The concrete number of elements is determined by the count attribute. The attribute’s value is an expression that can use values that were previously assigned to a variable. The sequence elements implicit and implicit type are used to bind implicit value and type information to variables that can later on be used in type or value expressions(line 7, 10 and 11). To make it possible to aggregate related bytecode instructions to one logical instruction, several format sequences can be defined. The effect on the stack is determined by the number and type of stack operands that are popped (line 9) and pushed (line 10). If multiple stack layouts are specified, the effect on the stack is determined by the firstbefore-executionstack layout that matches; i.e., to determine the effect on the stack a data-flow analysis is necessary.Unique Prefix RuleOne constraint placed upon specifications written in OPAL SPL is that a format sequence can be identified unambiguously by only parsing a prefix of the instruction; no lookahead is necessary. In other words, if each format sequence is considered a production and eachu1, u2, etc. is considered a terminal, then OPAL SPL requires the format sequences to constitute an LR(0) grammar This unique prefix rule is checked automatically (cf. Sec.4); furthermore, this rule facilitates generating fast parsers from the specification, e.g., using nestedswitchstatements.Type SystemOPAL SPL does not have a hard-coded type hierarchy. Instead, each specification written in SPL contains a description of the type system used by the bytecode language being described. The only restriction is that all types have to be arranged in a single, strict hierarchy.The Java Virtual Machine Specification [9]’s type hierarchy is shown in Fig.3(1). It captures all runtime types known to the Java virtual machine, as well as those types that are used only at link- or compile-time, e.g., branchoffset, fieldref and methodref. The hierarchy is a result of the peculiarities of theJVM’s instruction set. The byteorbooleantype, e.g., is required to model the baloadandbastore instructions, which operate on arrays of byteorbooleanalike.OPAL SPL’s type system implicitly defines a second type hierarchy ((2) in Fig. 3). The declared hierarchy of types (1) is mirrored by a hierarchy of kinds (2); for every (lower-case) type there automatically exists an (upper-case) kind. This convention ensures their consistency and keeps the specification itself brief. The values of kindINT LIKEareint, short, etc., just as the values of type int like are 1, 2, etc. Kinds enable parameterizing logical instructions likeareturnwith types,thus making a concise specification of related instructions (e.g., freturn, ireturn, andareturn) possible (cf. Sec.3.12).Information FlowIn OPAL SPL, the flow of information (values, types, register IDs) is modeled by means of named variables and expressions using the variables. In general, the flow of information is subject to the constraints illustrated by Fig.4. For example, variables defined within a specific format sequence can only be referred to by later elements within the same format sequence; a variable cannot be referred to across format sequences. If the same variable is bound by all format sequences, i.e., it is common to all format sequences, then the variable can be used to identify register IDs, the values pushed onto the stack, etc. Similarly, if an instruction defines multiple stack layouts, then a value can only flow from the i-th stack layout before execution to the i-th stack layout after execution and only information that is common to all stack layouts before execution may be stored in a register.3 Design DiscussionThe design of the OPAL specification language (OPAL SPL) is influenced by the peculiarities of the JVM’s instruction set [9, Chapter 6]. In the following, we discuss those instructions that had a major influence on the design.3.1 Modeling the Stack Bottom(athrow)All JVM instructions—with the exception ofathrow—specify only the number and types of operands popped from and pushed onto the stack; they do not determine the layout of the complete stack. In case of the athrowinstruction, however, the stack layout after its execution is completely determined (Fig.5, line 6); the single element on the stack is the thrown exception. This necessitates explicit modeling of the stack’s contents beyond the operands that are pushed and popped by a particular instruction. The explicit modeling of the rest of the stack (line5) here by allows for the (implicit) modeling of stacks of a fixed size (line6).3.2 Pure Register Instructions(iinc)The flow of information for instructions that do not affect the stack—e.g., the JVM’siinc instruction—is depicted in Fig. 7and adheres to the general scheme of information flow (cf. Fig. 4). After parsing the instruction according to the format sequence(Fig. 6, lines3–5), the two variables lvIndex an dincrement are initialized.3.3 Interpretation of Arithmetic Instructions (iinc, add, sub,etc.)The specification ofiinc (Fig. 6) also illustrates OPAL SPL’s ability to model computed values, e.g., add(value, increment). This information can subsequently be used, e.g., by static analyses to determine data dependencies or to perform abstract interpretations.3.4 Constant Pool Handling (ldc)The Java class file format achieves its compactness in part through the use of a constant pool. Hereby, immediate operands of an instruction are replaced by an index into the (global) pool. For example, in case of the load constant intructionldc, the operand needs to be programmatically retrieved from the constant pool (Fig.8, line 5). To obtain the value’s type, one uses the reflective type offunction that the enclosing toolkitx has to provide (line14).3.5 Multiple Format Sequences, Single Logical InstructionAn instruction such asldc, which may refer to an integer value in the constant pool, is conceptually similar to instructions such asiconst 0orsipush;allofthem push a constant value onto the operand stack. The primary difference between the format sequences of ldc(Fig. 8, lines 3–5)andiconst 0(lines 6–7)isthat the former’s operand resides in th e constant pool. In contrast, sipushencodes its operand explicitly in the bytecode stream as an immediate value (line9).To facilitate standard control- and data-flow analyses, OPAL SPL abstracts away from such details, so that similar instructions can be subsumed by more generic instructions using explicit or implicit type and value bindings. A generic push instruction (Fig. 8), e.g., subsumes all JVM instructions that just push a constant value onto the stack. In this case the pushed value is either a computed value (line5), an implicit value (line7), or an immediate operand (line9).3.6 Variable Operand Counts (invokevirtual, invokespecial,etc.)Some instructions pop a variable number of operands, e.g., the four invoke instructions invokevirtual, invokespecial, invokeinterface,andinvokestatic. In their case the number of popped operands directly depends on the number of arguments of the method. To support instructions that pop a variable number of operands, OPAL SPL provides the list element (Fig.9, line 8). Using the list element’scountattribute, it is possible to specify a function that determines the number of operands actually popped from the stack. It is furthermore possible, by using theloop varattribute, to specify a variable iterating over these operands. The loop variable (i) can then be used inside the list element to specify the expected operands (line10). This enables specification of both the expected number and type of operands, i.e., of the method arguments (lines8–10).Using functions (methodrefargcount, methodrefargtype, ...) offloads the intricate handling of the constant pool to externally supplied code (cf. Sec.3.4)—the enclosing toolkit; the OPAL specification language itself remains independent of how the framework or toolkit under development stores suchinformation.3.7 ExceptionsThe specification of invokevirtual (Fig. 9) also makes explicit which exceptions the instruction may throw (line 16). This information is required by control-flow analyses and thus needs to be present in specifications. To identify the instructions which may handle the exception the function (caughtby)needs to be defined by the toolkit. This functions computes, given both the instruction’s address and the type of the exception, the addresses of all instructions in the same method that handle the exception. Similar to the handling of the constant pool, OPAL SPL thus offloads the handling of the exceptions attribute.3.8 Variable-length Instructions (tableswitch, lookupswitch)The support for variable-length instructions (tableswitch, lookupswitch) is similar to the support for instructions with a variable stack size (cf. Sec. 3.6). In this case, anelementselement can be used to specify how many times (Fig.10, line 7) which kind of values (lines8–9) need to be read. Hereby, the elementsconstruct can accommodate multiple sequence elements (lines7–10).The variable number of cases is, however, just one reason why table switch and lookupswitch are classified as variable-length instructions; the JVM Specification mandates that up to three padding bytes are inserted, to align the following format elements on a four-byte boundary (line4).3.9 Single Instruction, Multiple Operand Stacks (dup2)The JVM specification defines several instructions that operate on the stack independent of their operands’ types or—if we change the perspective—that behave differently depending on the type of the operands present on the stack prior to their execution. For example, thedup2instruction (Fig. 11) duplicates the contents of two one-word stack slots.Instructions such asdup2anddup2x1distinguish their operands by their computational type (category 1 or 2) rather than by their actual type (int, reference,etc.). This makes it possible to compactly encode instructions such asdup2and motivates the corresponding level in the type hierarchy (cf. Sec.2.2). Additionally, this requires that OPAL SPL supports multiple stack layouts.In OPAL SPL, the stack is modeled as a list of operands, not as a list of slots as discussed in the JVM specification. While the effect of an instruction such asdup2 is more easily expressed in terms of stack slots, the vast majority of instructions naturally refers to operands. In particular, the decision to base the stack model on operands rather than slots avoids explicit modeling of the higher and lower halves of category-2-values, e.g., the high and low word of a 64 bitlong operand.3.10 (Conditional) Control Transfer Instructions (if, goto, jsr, ret)To perform control-flow analyses it is necessary to identify those instructions that may transfer control, either by directly manipulating the program counter or terminating the current method. This information is specified using theinstruction element’s optional transferscontrol attribute (Fig.12, line 1). Itspecifies if control is transfered conditionally or always. The target instruction to which control is transferredisidentifiedbythevaluesoftype branchoffset orabsoluteaddress.For these two types the type system contains the meta-information (cf. Fig.3)thatthe values have to be interpreted either as relative or absolute program counters.3.11 Multibyte Opcodes and Modifiers (wideinstructions, newarray)The JVM instruction set consists mostly of instructions whose opcode is a single byte, although a few instructions have longer opcode sequences. In most cases this is due to the widemodifier, a single byte prefix to the instruction. In case of the newarray instruction, however, a suffix is used to determine its precise effect. As can be seen in Fig.13, the parser needs to examine two bytes to determine the correct format sequence.3.12 Implicit Types and Type ConstructorsThe specification ofnewarray(Fig.13) also illustrates the specification of implied types and type constructors. As the JVM instruction set is a typed assembly language, many instructions exist in a variety of formats, e.g., asiadd, ladd, fadd, anddadd.Theimplicit type construct is designed to eliminate this kind of redundancy in the specification, resulting in a single, logical instruction:add. Similarily, newarraymakes use of type bindings (lines5, 8).But, to precisely model the effect ofnewarrayon the operand stack, an additional function that constructs a type is needed. Given a type and an integer, the function arrayconstructs a new type; here, a one-dimensional array of the base type (line14).3.13 Extension MechanismOPAL SPL has been designed with extensibility in mind. The extension point for additional information is the instruction element’sappinfochild, whose content can consist of arbitrary elements with a namespace other than OPAL SPL’s own.To illustrate the mechanism, suppose that we want to create a Prolog representation for Java Bytecode, in which information about operators is explicit, i.e., in which theifgt instruction is an if instruction which compares two values using the greater than operator, as illustrated by Fig.14.4 V alidating SpecificationsTo validate an OPAL SPL specification, we have defined an XML Schema which ensures syntactic correctness of the specification and performs basic identity checking. It checks, for example, that each declared type and each instruction’s mnemonic is unique. Additionally, we have developed a program which analyzes a specification and detects the following errors: (a) a format sequence does not have a unique prefix path, (b) multiple format sequences of a single instruction do not agree in the variables bound by them, (c) the number or type of function’s a rguments is wrong or its result is of the wrong type.5 EvaluationWe have used the specification of the JVM’s instruction set [9] for the implementation of a highly flexible bytecode toolkit. The toolkit supports four representations of Java bytecode: a native representation, which is a one-to-one representation of the Java Bytecode; a higher-level representation, which abstracts away some details of Java bytecode—in particular from the constant pool; an XML representation which uses the higher-level representation; a Prolog-based representation of Java Bytecode, which is also based on the higher-level representation.6 Related WorkApplying XML technologies to Java bytecode is not a new idea [5]. The XML serialization of class files, e.g., allows for their declarative transformation using XSLT. The XMLVM [11] project aims to support not only the JVM instruction set [9], but also the CLR instruction set [8]. This requires that at least the CLR’s operand stack is transformed [12], as the JVM r equires. The description of the effect that individual CLR instructions have on the operand stack is, however, not specified in an easily accessible format like OPAL SPL, but rather embedded within the XSL transformations.7 Conclusion and Future WorkIn future work, we will investigate the use of OPAL SPL for the encoding of other bytecode languages, such as the Common Intermediate Language. This would make it possible to develop (control- and dataflow-) analyses with respect to the OPAL SPL and to use the same analysis to analyze bytecode of different languages.From:Encoding the Java Virtual Machine’s Instruction SetJava虚拟机指令系统的编码1引言解释和分析Java字节码程序的发展有已经长的历史了,新的方案仍在研究。
毕设三项文档之-外文翻译

本科生毕业设计 (论文)
外文翻译
原文标题
Worlds Collide:
Exploring the Use of Social Media Technologies for
Online Learning
译文标题
世界的碰撞:
探索社交媒体技术在在线学习的应用
作者所在系别计算机科学与工程系作者所在专业计算机科学与技术作者所在班级
作者姓名
作者学号
指导教师姓名
指导教师职称讲师
完成时间2013年2月
北华航天工业学院教务处制
注:1. 指导教师对译文进行评阅时应注意以下几个方面:①翻译的外文文献与毕业设计(论文)的主题是否高度相关,并作为外文参考文献列入毕业设计(论文)的参考文献;②翻译的外文文献字数是否达到规定数量(3 000字以上);③译文语言是否准确、通顺、具有参考价值。
2. 外文原文应以附件的方式置于译文之后。
毕业设计论文外文文献翻译

毕业设计(论文)外文文献翻译院系:财务与会计学院年级专业:201*级财务管理姓名:学号:132148***附件: 财务风险管理【Abstract】Although financial risk has increased significantly in recent years risk and risk management are not contemporary issues。
The result of increasingly global markets is that risk may originate with events thousands of miles away that have nothing to do with the domestic market。
Information is available instantaneously which means that change and subsequent market reactions occur very quickly。
The economic climate and markets can be affected very quickly by changes in exchange rates interest rates and commodity prices。
Counterparties can rapidly become problematic。
As a result it is important to ensure financial risks are identified and managed appropriately. Preparation is a key component of risk management。
【Key Words】Financial risk,Risk management,YieldsI. Financial risks arising1.1What Is Risk1.1.1The concept of riskRisk provides the basis for opportunity. The terms risk and exposure have subtle differences in their meaning. Risk refers to the probability of loss while exposure is the possibility of loss although they are often used interchangeably。
毕设外文文献+翻译1

毕设外文文献+翻译1外文翻译外文原文CHANGING ROLES OF THE CLIENTS、ARCHITECTSAND CONTRACTORS THROUGH BIMAbstract:Purpose –This paper aims to present a general review of the practical implications of building information modelling (BIM) based on literature and case studies. It seeks to address the necessity for applying BIM and re-organising the processes and roles in hospital building projects. This type of project is complex due to complicated functional and technical requirements, decision making involving a large number of stakeholders, and long-term development processes.Design/methodology/approach–Through desk research and referring to the ongoing European research project InPro, the framework for integrated collaboration and the use of BIM are analysed.Findings –One of the main findings is the identification of the main factors for a successful collaboration using BIM, which can be recognised as “POWER”: product information sharing (P),organisational roles synergy (O), work processes coordination (W), environment for teamwork (E), and reference data consolidation (R).Originality/value –This paper contributes to the actual discussion in science and practice on the changing roles and processes that are required to develop and operate sustainable buildings with the support of integrated ICT frameworks and tools. It presents the state-of-the-art of European research projects and some of the first real cases of BIM application inhospital building projects.Keywords:Europe, Hospitals, The Netherlands, Construction works, Response flexibility, Project planningPaper type :General review1. IntroductionHospital building projects, are of key importance, and involve significant investment, and usually take a long-term development period. Hospital building projects are also very complex due to the complicated requirements regarding hygiene, safety, special equipments, and handling of a large amount of data. The building process is very dynamic and comprises iterative phases and intermediate changes. Many actors with shifting agendas, roles and responsibilities are actively involved, such as: the healthcare institutions, national and local governments, project developers, financial institutions, architects, contractors, advisors, facility managers, and equipment manufacturers and suppliers. Such building projects are very much influenced, by the healthcare policy, which changes rapidly in response to the medical, societal and technological developments, and varies greatly between countries (World Health Organization, 2000). In The Netherlands, for example, the way a building project in the healthcare sector is organised is undergoing a major reform due to a fundamental change in the Dutch health policy that was introduced in 2008.The rapidly changing context posts a need for a building with flexibility over its lifecycle. In order to incorporate life-cycle considerations in the building design, construction technique, and facility management strategy, a multidisciplinary collaboration is required. Despite the attempt for establishing integrated collaboration, healthcare building projects still facesserious problems in practice, such as: budget overrun, delay, and sub-optimal quality in terms of flexibility, end-user?s dissatisfaction, and energy inefficiency. It is evident that the lack of communication and coordination between the actors involved in the different phases of a building project is among the most important reasons behind these problems. The communication between different stakeholders becomes critical, as each stakeholder possesses different setof skills. As a result, the processes for extraction, interpretation, and communication of complex design information from drawings and documents are often time-consuming and difficult. Advanced visualisation technologies, like 4D planning have tremendous potential to increase the communication efficiency and interpretation ability of the project team members. However, their use as an effective communication tool is still limited and not fully explored. There are also other barriers in the information transfer and integration, for instance: many existing ICT systems do not support the openness of the data and structure that is prerequisite for an effective collaboration between different building actors or disciplines.Building information modelling (BIM) offers an integrated solution to the previously mentioned problems. Therefore, BIM is increasingly used as an ICT support in complex building projects. An effective multidisciplinary collaboration supported by an optimal use of BIM require changing roles of the clients, architects, and contractors; new contractual relationships; and re-organised collaborative processes. Unfortunately, there are still gaps in the practical knowledge on how to manage the building actors to collaborate effectively in their changing roles, and todevelop and utilise BIM as an optimal ICT support of the collaboration.This paper presents a general review of the practical implications of building information modelling (BIM) based on literature review and case studies. In the next sections, based on literature and recent findings from European research project InPro, the framework for integrated collaboration and the use of BIM are analysed. Subsequently, through the observation of two ongoing pilot projects in The Netherlands, the changing roles of clients, architects, and contractors through BIM application are investigated. In conclusion, the critical success factors as well as the main barriers of a successful integrated collaboration using BIM are identified.2. Changing roles through integrated collaboration and life-cycle design approachesA hospital building project involves various actors, roles, and knowledge domains. In The Netherlands, the changing roles of clients, architects, and contractors in hospital building projects are inevitable due the new healthcare policy. Previously under the Healthcare Institutions Act (WTZi), healthcare institutions were required to obtain both a license and a building permit for new construction projects and major renovations. The permit was issued by the Dutch Ministry of Health. The healthcare institutions were then eligible to receive financial support from the government. Since 2008, new legislation on the management of hospital building projects and real estate has come into force. In this new legislation, a permit for hospital building project under the WTZi is no longer obligatory, nor obtainable (Dutch Ministry of Health, Welfare and Sport, 2008). This change allows more freedom from the state-directed policy, and respectively,allocates more responsibilities to the healthcare organisations to deal with the financing and management of their real estate. The new policy implies that the healthcare institutions are fully responsible to man age and finance their building projects and real estate. The government?s support for the costs of healthcare facilities will no longer be given separately, but will be included in the fee for healthcare services. This means that healthcare institutions must earn back their investment on real estate through their services. This new policy intends to stimulate sustainable innovations in the design, procurement and management of healthcare buildings, which will contribute to effective and efficient primary healthcare services.The new strategy for building projects and real estate management endorses an integrated collaboration approach. In order to assure the sustainability during construction, use, and maintenance, the end-users, facility managers, contractors and specialist contractors need to be involved in the planning and design processes. The implications of the new strategy are reflected in the changing roles of the building actors and in the new procurement method.In the traditional procurement method, the design, and its details, are developed by the architect, and design engineers. Then, the client (the healthcare institution) sends an application to the Ministry of Healthto obtain an approval on the building permit and the financial support from the government. Following this, a contractor is selected through a tender process that emphasises the search for the lowest-price bidder. During the construction period, changes often take place due to constructability problems of the design and new requirements from the client.Because of the high level of technical complexity, and moreover, decision-making complexities, the whole process from initiation until delivery of a hospital building project can take up to ten years time. After the delivery, the healthcare institution is fully in charge of the operation of the facilities. Redesigns and changes also take place in the use phase to cope with new functions and developments in the medical world.The integrated procurement pictures a new contractual relationship between the parties involved in a building project. Instead of a relationship between the client and architect for design, and the client and contractor for construction, in an integrated procurement the client only holds a contractual relationship with the main party that is responsible for both design and construction. The traditional borders between tasks and occupational groups become blurred since architects, consulting firms, contractors, subcontractors, and suppliers all stand on the supply side in the building process while the client on the demand side. Such configuration puts the architect, engineer and contractor in a very different position that influences not only their roles, but also their responsibilities, tasks and communication with the client, the users, the team and other stakeholders.The transition from traditional to integrated procurement method requires a shift of mindset of the parties on both the demand and supply sides. It is essential for the client and contractor to have a fair and open collaboration in which both can optimally use their competencies. The effectiveness of integrated collaboration is also determined by the client?s capacity and strategy to organize innovative tendering procedures.A new challenge emerges in case of positioning an architect in a partnership with the contractor instead of with the client. In case of the architect enters a partnership with the contractor, an important issues is how to ensure the realisation of the architectural values as well as innovative engineering through an efficient construction process. In another case, the architect can stand at the client?s side in a strategic advisory role instead of being the designer. In this case, the architect?s responsibility is translating client?s requirements and wishes into the architectural values to be included in the design specification, and evaluating the contractor?s proposal against this. In any of this new role, the architect holds the responsibilities as stakeholder interest facilitator, custodian of customer value and custodian of design models.The transition from traditional to integrated procurement method also brings consequences in the payment schemes. In the traditional building process, the honorarium for the architect is usually based on a percentage of the project costs; this may simply mean that the more expensive the building is, the higher the honorarium will be. The engineer receives the honorarium based on the complexity of the design and the intensity of the assignment. A highly complex building, which takes a number of redesigns, is usually favourable for the engineers in terms of honorarium. A traditional contractor usually receives the commission based on the tender to construct the building at the lowest price by meeting the minimum specifications given by the client. Extra work due to modifications is charged separately to the client. After the delivery, the contractor is no longer responsible for the long-term use of the building. In the traditional procurement method, all risks are placed with theclient.In integrated procurement method, the payment is based on the achieved building performance; thus, the payment is non-adversarial. Since the architect, engineer and contractor have a wider responsibility on the quality of the design and the building, the payment is linked to a measurement system of the functional and technical performance of the building over a certain period of time. The honorarium becomes an incentive to achieve the optimal quality. If the building actors succeed to deliver a higher added-value thatexceed the minimum client?s requirements, they will receive a bonus in accordance to the client?s extra gain. The level of transparency is also improved. Open book accounting is an excellent instrument provided that the stakeholders agree on the information to be shared and to its level of detail (InPro, 2009).Next to the adoption of integrated procurement method, the new real estate strategy for hospital building projects addresses an innovative product development and life-cycle design approaches. A sustainable business case for the investment and exploitation of hospital buildings relies on dynamic life-cycle management that includes considerations and analysis of the market development over time next to the building life-cycle costs (investment/initial cost, operational cost, and logistic cost). Compared to the conventional life-cycle costing method, the dynamic life-cycle management encompasses a shift from focusing only on minimizing the costs to focusing on maximizing the total benefit that can be gained. One of the determining factors for a successful implementation of dynamic life-cycle management is the sustainable design of the building and building components, which means that the design carriessufficient flexibility to accommodate possible changes in the long term (Prins, 1992).Designing based on the principles of life-cycle management affects the role of the architect, as he needs to be well informed about the usage scenarios and related financial arrangements, the changing social and physical environments, and new technologies. Design needs to integrate people activities and business strategies over time. In this context, the architect is required to align the design strategies with the organisational, local and global policies on finance, business operations, health and safety, environment, etc.The combination of process and product innovation, and the changing roles of the building actors can be accommodated by integrated project delivery or IPD (AIA California Council, 2007). IPD is an approach that integrates people, systems, business structures and practices into a process that collaboratively harnesses the talents and insights of all participants to reduce waste and optimize efficiency through all phases of design, fabrication and construction. IPD principles can be applied to a variety of contractual arrangements. IPD teams will usually include members well beyond the basic triad of client, architect, and contractor. At a minimum, though, an Integrated Project should include a tight collaboration between the client, the architect, and the main contractor ultimately responsible for construction of the project, from the early design until the project handover. The key to a successful IPD is assembling a team that is committed to collaborative processes and is capable of working together effectively. IPD is built on collaboration. As a result, it can only be successful if the participants share and apply common values and goals.3. Changing roles through BIM applicationBuilding information model (BIM) comprises ICT frameworks and tools that can support the integrated collaboration based on life-cycle design approach. BIM is a digital representation of physical and functional characteristics of a facility. As such it serves as a shared knowledge resource for information about a facility forming a reliable basis for decisions during its lifecycle from inception onward (National Institute of Building Sciences NIBS, 2007). BIM facilitates time and place independent collaborative working. A basic premise of BIM is collaboration by different stakeholders at different phases of the life cycle of a facility to insert, extract, update or modify information in the BIM to support and reflect the roles of that stakeholder. BIM in its ultimate form, as a shared digital representation founded on open standards for interoperability, can become a virtual information model to be handed from the design team to the contractor and subcontractors and then to the client.BIM is not the same as the earlier known computer aided design (CAD). BIM goes further than an application to generate digital (2D or 3D) drawings. BIM is an integrated model in which all process and product information is combined, stored, elaborated, and interactively distributed to all relevant building actors. As a central model for all involved actors throughout the project lifecycle, BIM develops andevolves as the project progresses. Using BIM, the proposed design and engineering solutions can be measured against the client?s requirements and expected building performance. The functionalities of BIM to support the design process extend to multidimensional (nD), including: three-dimensional visualisation and detailing, clash detection, material schedule, planning, costestimate, production and logistic information, and as-built documents. During the construction process, BIM can support the communication between the building site, the factory and the design office– which is crucial for an effective and efficient prefabrication and assembly processes as well as to prevent or solve problems related to unforeseen errors or modifications. When the building is in use, BIM can be used in combination with the intelligent building systems to provide and maintain up-to-date information of the building performance, including the life-cycle cost.To unleash the full potential of more efficient information exchange in the AEC/FM industry in collaborative working using BIM, both high quality open international standards and high quality implementations of these standards must be in place. The IFC open standard is generally agreed to be of high quality and is widely implemented in software. Unfortunately, the certification process allows poor quality implementations to be certified and essentially renders the certified software useless for any practical usage with IFC. IFC compliant BIM is actually used less than manual drafting for architects and contractors, and show about the same usage for engineers. A recent survey shows that CAD (as a closed-system) is still the major form of technique used in design work (over 60 per cent) while BIM is used in around 20 percent of projects for architects and in around 10 per cent of projects for engineers and contractors.The application of BIM to support an optimal cross-disciplinary and cross-phase collaboration opens a new dimension in the roles and relationships between the building actors. Several most relevant issues are: the new role of a model manager; the agreement on the access right and IntellectualProperty Right (IPR); the liability and payment arrangement according to the type of contract and in relation to the integrated procurement; and the use of open international standards.Collaborative working using BIM demands a new expert role of a model manager who possesses ICT as well as construction process know-how (InPro, 2009). The model manager deals with the system as well as with the actors. He provides and maintains technological solutions required for BIM functionalities, manages the information flow, and improves the ICT skills of the stakeholders. The model manager does not take decisions on design and engineering solutions, nor the organisational processes, but his roles in the chain of decision making are focused on:the development of BIM, the definition of the structure and detail level of the model, and the deployment of relevant BIM tools, such as for models checking, merging, and clash detections;the contribution to collaboration methods, especially decision making and communication protocols, task planning, and risk management;and the management of information, in terms of data flow and storage, identification of communication errors, and decision or process (re-)tracking.Regarding the legal and organisational issues, one of the actual questions is: “In what way does the intellectual property right (IPR) in collaborative working using BIM differ from the IPR in a traditional teamwork?”. In terms of combine d work, the IPR of each element is at tached to its creator. Although it seems to be a fully integrated design, BIM actually resulted from a combination of works/elements; for instance: the outline of the building design, is created by the architect, the design for theelectrical system, is created by the electrical contractor, etc. Thus, in case of BIM as a combined work, the IPR is similar to traditional teamwork. Working with BIM with authorship registration functionalities may actually make it easier to keep track of the IPR.How does collaborative working, using BIM, effect the contractual relationship? On the one hand,collaborative working using BIM does not necessarily change the liability position in the contract nor does it obligate an alliance contract. The General Principles of BIM A ddendum confirms: …This does not effectuate or require a restructuring of contractual relationships or shifting of risks between or among the Project Participants other than as specifically required per the Protocol Addendum and its Attachments? (ConsensusDOCS, 2008). On the other hand, changes in terms of payment schemes can be anticipated. Collaborative processes using BIM will lead to the shifting of activities from to the early design phase. Much, if not all, activities in the detailed engineering and specification phase will be done in the earlier phases. It means that significant payment for the engineering phase, which may count up to 40 per cent of the design cost, can no longer be expected. As engineering work is done concurrently with the design, a new proportion of the payment in the early design phase is necessary.4. Review of ongoing hospital building projects using BIMIn The Netherlands, the changing roles in hospital building projects are part of the strategy, which aims at achieving a sustainable real estate in response to the changing healthcare policy. Referring to literature and previous research, the main factors that influence the success of the changing roles can be concluded as: the implementation of an integrated procurementmethod and a life-cycle design approach for a sustainable collaborative process; the agreement on the BIM structure and the intellectual rights; and the integration of the role of a model manager. The preceding sections have discussed the conceptual thinking on how to deal with these factors effectively. This current section observes two actual projects and compares the actual practice with the conceptual view respectively.The main issues, which are observed in the case studies, are: the selected procurement method and the roles of the involved parties within this method;the implementation of the life-cycle design approach;the type, structure, and functionalities of BIM used in the project;the openness in data sharing and transfer of the model, and the intended use of BIM in the future; and the roles and tasks of the model manager.The pilot experience of hospital building projects using BIM in the Netherlands can be observed at University Medical Centre St Radboud (further referred as UMC) and Maxima Medical Centre (further referred as MMC). At UMC, the new building project for the Faculty of Dentistry in the city of Nijmegen has been dedicated as a BIM pilot project. At MMC, BIM is used in designing new buildings for Medical Simulation and Mother-and-Child Centre in the city of Veldhoven.The first case is a project at the University Medical Centre (UMC) St Radboud. UMC is more than just a hospital. UMC combines medical services, education and research. More than 8500 staff and 3000 students work at UMC. As a part of the innovative real estate strategy, UMC has considered to use BIM for its building projects. The new development of the Faculty ofDentistry and the surrounding buildings on the Kapittelweg in Nijmegen has been chosen as a pilot project to gather practical knowledge and experience on collaborative processes with BIM support.The main ambition to be achieved through the use of BIM in the building projects at UMC can be summarised as follows: using 3D visualisation to enhance the coordination and communication among the building actors, and the user participation in design;integrating the architectural design with structural analysis, energy analysis, cost estimation, and planning;interactively evaluating the design solutions against the programme of requirements and specifications;reducing redesign/remake costs through clash detection during the design process; andoptimising the management of the facility through the registration of medical installations andequipments, fixed and flexible furniture, product and output specifications, and operational data.The second case is a project at the Maxima Medical Centre (MMC). MMC is a large hospital resulted from a merger between the Diaconessenhuis in Eindhoven and St Joseph Hospital in Veldhoven. Annually the 3,400 staff of MMC provides medical services to more than 450,000 visitors and patients. A large-scaled extension project of the hospital in Veldhoven is a part of its real estate strategy. A medical simulation centre and a women-and-children medical centre are among the most important new facilities within this extension project. The design has been developed using 3D modelling with several functionalities of BIM.The findings from both cases and the analysis are as follows.Both UMC and MMC opted for a traditional procurement method in which the client directly contracted an architect, a structural engineer, and a mechanical, electrical and plumbing (MEP) consultant in the design team. Once the design and detailed specifications are finished, a tender procedure will follow to select a contractor. Despite the choice for this traditional method, many attempts have been made for a closer and more effective multidisciplinary collaboration. UMC dedicated a relatively long preparation phase with the architect, structural engineer and MEP consultant before the design commenced. This preparation phase was aimed at creating a common vision on the optimal way for collaboration using BIM as an ICT support. Some results of this preparation phase are: a document that defines the common ambition for the project and the collaborative working process and a semi-formal agreement that states the commitment of the building actors for collaboration. Other than UMC, MMC selected an architecture firm with an in-house engineering department. Thus, the collaboration between the architect and structural engineer can take place within the same firm using the same software application.Regarding the life-cycle design approach, the main attention is given on life-cycle costs, maintenance needs, and facility management. Using BIM, both hospitals intend to get a much better insight in these aspects over the life-cycle period. The life-cycle sustainability criteria are included in the assignments for the design teams. Multidisciplinary designers and engineers are asked to collaborate more closely and to interact with the end-users to address life-cycle requirements. However, ensuring the building actors to engage in an integrated collaboration to generate sustainable design solutions that meet the life-cycle。
毕业设计外文文献翻译(原文+译文)

Environmental problems caused by Istanbul subway excavation and suggestionsfor remediation伊斯坦布尔地铁开挖引起的环境问题及补救建议Ibrahim Ocak Abstract:Many environmental problems caused by subway excavations have inevitably become an important point in city life. These problems can be categorized as transporting and stocking of excavated material, traffic jams, noise, vibrations, piles of dust mud and lack of supplies. Although these problems cause many difficulties,the most pressing for a big city like Istanbul is excava tion,since other listed difficulties result from it. Moreover, these problems are environmentally and regionally restricted to the period over which construction projects are underway and disappear when construction is finished. Currently, in Istanbul, there are nine subway construction projects in operation, covering approximately 73 km in length; over 200 km to be constructed in the near future. The amount of material excavated from ongoing construction projects covers approximately 12 million m3. In this study, problems—primarily, the problem with excavation waste(EW)—caused by subway excavation are analyzed and suggestions for remediation are offered.摘要:许多地铁开挖引起的环境问题不可避免地成为城市生活的重要部分。
毕业设计外文及翻译4

What is circulating fluidized bed boiler?∙Fluidized Bed Reactors : High temperature systems for labs: Excellent mass and heat transfer∙Fluidized Bed Dryer for porboiled, paddy,corn,coffee,beans,jusmin etc.∙Fluid Bed Processor: Powder Coater Granulator Drying/Granulating/Coating Answer:CIRCULATING FLUIDIZED BED (CFB) BOILERTECHNOLOGY...a unique type of technology that converts various sources of fuel into energyDuring normal operation CFB technology does not utilize higher temperature gas, coal or oil burners in its furnace; instead it utilizes fluidization technology to circulate the fuel source as they burn in a low-temperature combustion process. The low burningtemperature minimizes the formation of nitrogen. The fuel is recycled over and over which results in high efficiency for fuel burning, capturing certain gaseous emissions, andtransferring the fuel's heat energy into high-quality steam used to produce power. The vigorous mixing, long burning time, and low-temperature combustion process allow CFBs to cleanly burn virtually any combustible material. CFBs capture and control gaseous emissions as required by the EPA during the conversion process generally eliminating the need to add additional emission control equipment.CFB technology has proven to be very capable of converting fuels with substantially lower BTU (British Thermal Unit) heating values such as waste coal.Simply put, by suspending (circulating) low quality fuel in air, it could be ignited and swirl inside the boiler like a fluid --- hence the "fluidized bed" part of the name. By circulating the burning fuel in a tall boiler-furnace until all of the available carbon is converted to energy, even a low BTU source such as coal refuse can be effectively and efficiently utilized.Accordingly even coal refuse that had been randomly discarded and unused for decades could now be used and converted into viable alternative energy....coal that had never been considered as "useful fuel" prior to the development of CFB Technology.CFB units are inherently designed and have proven over time to cleanly convert low BTU fuels into viable alternative energy.。
毕业设计(论文)外文翻译【范本模板】

华南理工大学广州学院本科生毕业设计(论文)翻译英文原文名Review of Vibration Analysis Methods for Gearbox Diagnostics and Prognostics中文译名对变速箱振动分析的诊断和预测方法综述学院汽车工程学院专业班级车辆工程七班学生姓名刘嘉先学生学号201130085184指导教师李利平填写日期2015年3月15日英文原文版出处:Proceedings of the 54th Meeting of the Society for Machinery Failure Prevention Technology, Virginia Beach,V A, May 1-4,2000,p. 623-634译文成绩:指导教师(导师组长)签名:译文:简介特征提取技术在文献中有描述;然而,大多数人似乎掩盖所需的特定的预处理功能。
一些文件没有提供足够的细节重现他们的结果,并没有一个全面的比较传统的功能过渡齿轮箱数据。
常用术语,如“残差信号”,是指在不同的文件不同的技术.试图定义了状态维修社区中的常用术语和建立所需的特定的预处理加工特性。
本文的重点是对所使用的齿轮故障检测功能。
功能分为五个不同的组基于预处理的需要。
论文的第一部分将提供预处理流程的概述和其中每个特性计算的处理方案。
在下一节中,为特征提取技术描述,将更详细地讨论每一个功能。
最后一节将简要概述的宾夕法尼亚州立大学陆军研究实验室的CBM工具箱用于齿轮故障诊断。
特征提取概述许多类型的缺陷或损伤会增加机械振动水平。
这些振动水平,然后由加速度转换为电信号进行数据测量。
原则上,关于受监视的计算机的健康的信息被包含在这个振动签名。
因此,新的或当前振动签名可以与以前的签名进行比较,以确定该元件是否正常行为或显示故障的迹象。
在实践中,这种比较是不能奏效的。
由于大的变型中,签名的直接比较是困难的。
相反,一个涉及从所述振动署名数据特征提取更多有用的技术也可以使用。
毕业设计外文翻译原文

CLUTCHThe engine produces the power to drive the vehicle. The drive line or drive train transfers the power of the engine to the wheels. The drive train consists of the parts from the back of the flywh eel to the wheels. These parts include the clutch, th e transmission, the drive shaft, and the final drive assembly (Figure 8-1).The clutch which includes the flywheel, clutch disc, pressure plate, springs, pressure plate cover and the linkage necessary to operate the clutch is a rotating mechanism between t he engine and the transmission (Figure 8-2). It operates through friction which comes from contact between the parts. That is the reason why the clutch is called a friction mechanism. After engagement, the clutch must continue to transmit all the engine torque to the transmission depending on the friction without slippage. The clutch is also used to disengage the engine from the drive train whenever the gears in the transmission are being shifted from one gear ratio to another.To start the engine or shift the gears, the driver has to depress the clutch pedal with the purpose of disengagement the transmission from the engine. At that time, the driven members connected to the transmission input shaft are either stationary or rotating at a speed that is slower or faster than the driving members connected to the engine crankshaft. There is no spring pressure on the clutch assembly parts. So there is no friction between the driving members and driven members. As the driver lets loose the clutch pedal, spring pre ssure increases on the clutch parts. Friction between the parts also increases. The pressure exerted by the springs on the driven members is controlled by the driver through the clutch pedal and linkage. The positive engagement of the driving and driven members is made possible by the friction between the surfaces of the members. When full spring pressure is applied, the speed of the driving and driven members should be the same. At themoment, the clutch must act as a solid coupling device and transmit al l engine power to the transmission, without slipping.However, the transmission should be engaged to the engine gradually in order to operate the car smoothly and minimize torsional shock on the drive train because an engine at idle just develops little power. Otherwise, the driving members are connected with the driven members too quickly and the engine would be stalled.The flywheel is a major part of the clutch. The flywheel mounts to the engine’s crankshaft and transmits engine torque to the clutch assembly. The flywheel, when coupled with the clutch disc and pressure plate makes and breaks the flow of power from the engine to the transmission.The flywheel provides a mounting location for the clutch assembly as well. When the clutch is applied, the flyw heel transfers engine torque to the clutch disc. Because of its weight, the flywheel helps to smooth engine operation. The flywheel also has a large ring gear at its outer edge, which engages with a pinion gear on the starter motor during engine cranking.The clutch disc fits between the flywheel and the pressure plate. The clutch disc has a splined hub that fits over splines on the transmission input shaft. A splined hub has grooves that match splines on the shaft. These splines fit in the grooves. Thus, t he two parts are held together. However, back-and-forth movement of the disc on the shaft is possible. Attached to the input shaft, At disc turns at the speed of the shaft.The clutch pressure plate is generally made of cast iron. It is round and about the same diameter as the clutch disc. One side of the pressure plate is machined smooth. This side will press the clutch disc facing are against the flywheel. The outer side has various shapes to facilitate attachment of spring and release mechanisms. The two primary types of pressure plate assemblies are coil spri ng assembly and diaphragmspring (Figure 8-3).In a coil spring clutch the pressure plate is backed by a number of coil springs and housed with them in a pressed-steel cover bolted to the flywheel. The springs push against the cover. Neither the driven plate nor the pressure plate is connected rigidly to the flywh eel and both can move either towards it or away. When the clutch pedal is depressed a thrust pad riding on a carbon or ball thrust bearing i s forced towards the flywheel. Levers pivoted so that they engage with the thrust pad at one end and the pressure plate at the other end pull the pressure plate ba ck against its springs. This releases pressure on the driven plate disconnecting the gearbox from the engine (Figure 8-4).Diaphragm spring pressure plate assemblies are widely used in most modern cars. The diaphragm spring is a single thin sheet of metal which yields when pressure is applied to it. When pressure is removed the metal springs back to its original shape. The centre portion of the diaphragm spring is slit into numerous fingers that act as release levers. When the clutch assembly rotates with the engine these weights are flung outwards by centrifugal forces and cause the levers to pre ss against the pressure plate. During disengagement of the clutch the fingers are moved forward by the release bearing. The spring pivots over the fulcrum ring and its outer rim moves away from the flywheel. The retracting spring pulls the pressure plate a way from the clutch plate thus disengaging the clutch (Figure 8-5).When engaged the release bearing and the fingers of the diaphragm spring move towards the transmission. As the diaphragm pivots over the pivot ring its outer rim forces the pressure plate against the clutch disc so that the clutch plate is engaged to the flywheel.The advantages of a diaphragm type pres sure plate assembly are its compactness, lower weight, fewer moving parts, less effort to engage, reduces rotational imbalance by providin g a balanced force around the pressure plate and less chances of clutch slippage.The clutch pedal is connected to the disengagement mechanism either by a cable or, more com monly, by a hydraulic system. Either way, pushing the pedal down operates the dise ngagement mechanism which puts pressure on the fingers of the clutch diaphragm via a release bearing and causes the diaphragm to release the clutch plate. With a hydraulic mechanism, the clutch pedal arm operates a piston in the clutch master cylinder. Thi s forces hydraulic fluid through a pipe to the clutch release cylinder where another piston operates the clutch disengagement mechanism. The alternative is to link the clutch pedal to the disengagement mechanism by a cable.The other parts including the cl utch fork, release bearing, bell-housing, bell housing cover, and pilot bushing are needed to couple and uncouple the transmission. The clutch fork, which connects to the linkage, actually operates the clutch. The release bearing fits between the clutch fork and the pressure plate assembly. The bell housing covers the clutch assembly. The bell housing c over fastens to the bottom of the bell housing. This removable cover allows a mechanic to inspect the clutch without removing the transmission and bell housing. A pilot bushing fits into the back of th e crankshaft and holds the transmission input shaft.A Torque ConverterThere are four components inside the very strong housing of the torque converter:1. Pump;2. Turbine;3. Stator;4. Transmission fluid.The housing of the torque converter is bolted to the flywheel of the engine, so it turns at what ever speed the engine is running at. The fins that make up the pump of the torque converter are at tached to the housing, so they also turn at the same speed a s the engine. The cutaway below shows how everything is connected inside the torque converter (Figure 8-6).The pump inside a torque converter is a type of centrifugal pump. As it spins, fluid is flung to the outside, much as the spin cycle of a washing machine flings water and clothes to the outside of the wash tub. As fluid is flung to the outside, a vacuum is created that draws more fluid in at the center.The fluid then enters the blades of the turbine, which is connected to the transmission. The turbin e causes the transmission to spin, which basically moves the car. The blades of the turbine are curved. This means that the fluid, which enters the turbine from the outside, has to change direction before it exits the center of the turbine. It is this directional change that causes the turbine to spin.The fluid exits the turbine at the center, moving in a different direction than when it entered. The fluid exits the turbine moving opposite the direction that the pump (and engine) is turning. If the fluid were allowed to hit the pump, it would slow the engine down, wasting power. This is why a torque converter has a stator.The stator resides in the very center of the torque converter. Its job is to redirect the fluid returning from the turbine before it hits the pump again. This dramatically increases the efficiency of the torque converter.The stator has a very aggressive blade design that almost completely reverses the direction of the fluid. A one-way clutch (inside the stator) connects the stator to a fixed shaft in the transmission. Because of this arrangement, the stator cannot spin with the fluid - i tc a n s p i n o n l y i n t h e o p p o s i t ed i re c t i o n,f o r c i ng th e f l ui d t oc h a n g ed i re c t i o n a s i t h i t s t h e s t a t o r b l a d e s.Something a little bit tricky happens when the car gets moving. There is a point, around 40 mph (64 kph), at which both the pump and the turbine are spinning at almost the same speed (the pump alwaysspins slightly faster). At this point, the fluid returns from the turbine, entering the pump already moving in the same direction as the pump, so the stator is not needed.Even though the turbine changes the direction of the fluid and flings it out the back, the fluid still ends up moving in the direction that the turbine is spinning because the turbin e is spinning faster in one direction than the fluid is being pumped in the other direction. If you were standing in the back of a pickup moving at 60 mph, and you threw a ball out the back of that pickup at 40 mph, the ball would still be going forward at 20 mph. This is similar to what happens in the tur bine: The fluid is being flung out the back in one direction, but not as fast as it was going to start with in the other direction.At these speeds, the fluid actually strikes the back sides of the stator blades, causing the stator to freewheel on its one-way clutch so it doesn’t hinder the fluid moving through it.Benefits and Weak PointsIn addition to the very important job of allowing a car come to a complete stop without stalling the engine; the torqu e converter actually gives the car more torque when you accelerate out of a Stop. Modern torque converters can multiply the torque of the engine by two to three times. This effect only happens when the engine is turning much faster than the transmission.At higher speeds, the transmission catches up to the engine, eventually moving at almost the same speed. Ideally, though, the transmission would move at exactly the same speed as the engine, because this difference in speed wastes power. This is part of th e reason why cars with automatic transmissions get worse gas mileage than cars with manual transmissions.To counter this effect, some cars have a torque converter with alockup clutch. When the two halves of the torque converter get up to speed, this clutch locks them together, eliminating the slip page and improving efficiency.。
毕业设计(论文)外文资料翻译(学生用)

毕业设计外文资料翻译学院:信息科学与工程学院专业:软件工程姓名: XXXXX学号: XXXXXXXXX外文出处: Think In Java (用外文写)附件: 1.外文资料翻译译文;2.外文原文。
附件1:外文资料翻译译文网络编程历史上的网络编程都倾向于困难、复杂,而且极易出错。
程序员必须掌握与网络有关的大量细节,有时甚至要对硬件有深刻的认识。
一般地,我们需要理解连网协议中不同的“层”(Layer)。
而且对于每个连网库,一般都包含了数量众多的函数,分别涉及信息块的连接、打包和拆包;这些块的来回运输;以及握手等等。
这是一项令人痛苦的工作。
但是,连网本身的概念并不是很难。
我们想获得位于其他地方某台机器上的信息,并把它们移到这儿;或者相反。
这与读写文件非常相似,只是文件存在于远程机器上,而且远程机器有权决定如何处理我们请求或者发送的数据。
Java最出色的一个地方就是它的“无痛苦连网”概念。
有关连网的基层细节已被尽可能地提取出去,并隐藏在JVM以及Java的本机安装系统里进行控制。
我们使用的编程模型是一个文件的模型;事实上,网络连接(一个“套接字”)已被封装到系统对象里,所以可象对其他数据流那样采用同样的方法调用。
除此以外,在我们处理另一个连网问题——同时控制多个网络连接——的时候,Java内建的多线程机制也是十分方便的。
本章将用一系列易懂的例子解释Java的连网支持。
15.1 机器的标识当然,为了分辨来自别处的一台机器,以及为了保证自己连接的是希望的那台机器,必须有一种机制能独一无二地标识出网络内的每台机器。
早期网络只解决了如何在本地网络环境中为机器提供唯一的名字。
但Java面向的是整个因特网,这要求用一种机制对来自世界各地的机器进行标识。
为达到这个目的,我们采用了IP(互联网地址)的概念。
IP以两种形式存在着:(1) 大家最熟悉的DNS(域名服务)形式。
我自己的域名是。
所以假定我在自己的域内有一台名为Opus的计算机,它的域名就可以是。
毕设外文翻译 (英文原文+翻译)

英文翻译:PARTⅠ各种光纤接入技术Optical Fiber Technology With Various Access1 光网络主流1.1 光纤技术光纤生产技术已经成熟,现在大批量生产,广泛应用于今天的零色散波长λ0=1.3μm的单模光纤,而零色散波长λ0=1.55μm的单模光纤已开发并已进入实用阶段,这是非常小的1.55μm的波长衰减,约0.22dB/km,它更适合长距离大容量传输,是首选的长途骨干传输介质。
目前,为了适应不同的线路和局域网的发展要求,已经制定了一个非分散纤维,低色散斜率光纤,大有效面积光纤,水峰光纤等新型光纤。
长波光学研究人员研究认为,传输距离可以达到数千公里的理论,可以实现无中继传输距离,但它仍然是阶段理论。
1.2 光纤放大器1550nm波长掺铒(ER)的光纤放大器(EDFA),掺铒数字,模拟和相干光通信中继器可以以不同的速率传输光纤放大器,也可以发送特定波长的光信号。
在从模拟信号转换成数字信号、从低到高比特率比特率的光纤网络升级中,系统采用光复用技术的扩大,他们都不必改变掺铒放大器电路和设备。
掺铒放大器可作为光接收机前置放大器,后置放大器的光发射机和放大器的补偿光源装置。
1.3 宽带接入不同的环境中企业和住宅客户提供了多种宽带接入解决方案。
接入系统主要完成三大功能:高速传输,复用/路由,网络的扩展。
目前,接入系统的主流技术,ADSL 技术可以双绞铜线传输经济每秒几兆比特的信息,即支持传统的语音服务,而且还支持面向数据的因特网接入位,理事会结束的ADSL多路复用访问的数据流量,路由的分组网络,语音流量将传送到PSTN,ISDN或其它分组网络。
电缆调制解调器在HFC网络提供高速数据通信,将带宽分为上行和下行信道同轴电缆渠道,它可以提供挥发性有机化合物的在线娱乐,互联网接入等服务,同时还提供PSTN业务。
固定无线接入系统如智能天线和接收机的无线接入系统使用了许多高新技术,是一个以创新的方式接入的技术,作为目前仍滞留在今后进一步探索实践的方式最不确定的接入技术。
毕业设计外文资料翻译——翻译译文

毕业设计外文资料翻译(二)外文出处:Jules Houde 《Sustainable development slowed down by bad construction practices and natural and technological disasters》2、外文资料翻译译文混凝土结构的耐久性即使是工程师认为的最耐久和最合理的混凝土材料,在一定的条件下,混凝土也会由于开裂、钢筋锈蚀、化学侵蚀等一系列不利因素的影响而易受伤害。
近年来报道了各种关于混凝土结构耐久性不合格的例子。
尤其令人震惊的是混凝土的结构过早恶化的迹象越来越多。
每年为了维护混凝土的耐久性,其成本不断增加。
根据最近在国内和国际中的调查揭示,这些成本在八十年代间翻了一番,并将会在九十年代变成三倍。
越来越多的混凝土结构耐久性不合格的案例使从事混凝土行业的商家措手不及。
混凝土结构不仅代表了社会的巨大投资,也代表了如果耐久性问题不及时解决可能遇到的成本,更代表着,混凝土作为主要建筑材料,其耐久性问题可能导致的全球不公平竞争以及行业信誉等等问题。
因此,国际混凝土行业受到了强烈要求制定和实施合理的措施以解决当前耐久性问题的双重的挑战,即:找到有效措施来解决现有结构剩余寿命过早恶化的威胁。
纳入新的结构知识、经验和新的研究结果,以便监测结构耐久性,从而确保未来混凝土结构所需的服务性能。
所有参与规划、设计和施工过程的人,应该具有获得对可能恶化的过程和决定性影响参数的最低理解的可能性。
这种基本知识能力是要在正确的时间做出正确的决定,以确保混凝土结构耐久性要求的前提。
加固保护混凝土中的钢筋受到碱性的钝化层(pH值大于12.5)保护而阻止了锈蚀。
这种钝化层阻碍钢溶解。
因此,即使所有其它条件都满足(主要是氧气和水分),钢筋受到锈蚀也都是不可能的。
混凝土的碳化作用或是氯离子的活动可以降低局部面积或更大面积的pH值。
当加固层的pH值低于9或是氯化物含量超过一个临界值时,钝化层和防腐保护层就会失效,钢筋受腐蚀是可能的。
毕业设计外文文献翻译【范本模板】

毕业设计(论文)外文资料翻译系别:专业:班级:姓名:学号:外文出处:附件: 1. 原文; 2。
译文2013年03月附件一:A Rapidly Deployable Manipulator SystemChristiaan J。
J。
Paredis, H. Benjamin Brown,Pradeep K. KhoslaAbstract:A rapidly deployable manipulator system combines the flexibility of reconfigurable modular hardware with modular programming tools,allowing the user to rapidly create a manipulator which is custom-tailored for a given task. This article describes two main aspects of such a system,namely,the Reconfigurable Modular Manipulator System (RMMS)hardware and the corresponding control software。
1 IntroductionRobot manipulators can be easily reprogrammed to perform different tasks, yet the range of tasks that can be performed by a manipulator is limited by mechanicalstructure。
Forexample,a manipulator well-suited for precise movement across the top of a table would probably no be capable of lifting heavy objects in the vertical direction. Therefore,to perform a given task,one needs to choose a manipulator with an appropriate mechanical structure.We propose the concept of a rapidly deployable manipulator system to address the above mentioned shortcomings of fixed configuration manipulators。
毕业设计外文翻译例文

大连科技学院毕业设计(论文)外文翻译学生姓名专业班级指导教师职称所在单位教研室主任完成日期 2016年4月15日Translation EquivalenceDespite the fact that the world is becoming a global village, translation remains a major way for languages and cultures to interact and influence each other. And name translation, especially government name translation, occupies a quite significant place in international exchange.Translation is the communication of the meaning of a source-language text by means of an equivalent target-language text. While interpreting—the facilitating of oral or sign-language communication between users of different languages—antedates writing, translation began only after the appearance of written literature. There exist partial translations of the Sumerian Epic of Gilgamesh (ca. 2000 BCE) into Southwest Asian languages of the second millennium BCE. Translators always risk inappropriate spill-over of source-language idiom and usage into the target-language translation. On the other hand, spill-overs have imported useful source-language calques and loanwords that have enriched the target languages. Indeed, translators have helped substantially to shape the languages into which they have translated. Due to the demands of business documentation consequent to the Industrial Revolution that began in the mid-18th century, some translation specialties have become formalized, with dedicated schools and professional associations. Because of the laboriousness of translation, since the 1940s engineers have sought to automate translation (machine translation) or to mechanically aid the human translator (computer-assisted translation). The rise of the Internet has fostered a world-wide market for translation services and has facilitated language localizationIt is generally accepted that translation, not as a separate entity, blooms into flower under such circumstances like culture, societal functions, politics and power relations. Nowadays, the field of translation studies is immersed with abundantly diversified translation standards, with no exception that some of them are presented by renowned figures and are rather authoritative. In the translation practice, however, how should we select the so-called translation standards to serve as our guidelines in the translation process and how should we adopt the translation standards to evaluate a translation product?In the macro - context of flourish of linguistic theories, theorists in the translation circle, keep to the golden law of the principle of equivalence. The theory of Translation Equivalence is the central issue in western translation theories. And the presentation of this theory gives great impetus to the development and improvement of translation theory. It‟s not diffi cult for us to discover that it is the theory of Translation Equivalence that serves as guidelines in government name translation in China. Name translation, as defined, is the replacement of thename in the source language by an equivalent name or other words in the target language. Translating Chinese government names into English, similarly, is replacing the Chinese government name with an equivalent in English.Metaphorically speaking, translation is often described as a moving trajectory going from A to B along a path or a container to carry something across from A to B. This view is commonly held by both translation practitioners and theorists in the West. In this view, they do not expect that this trajectory or something will change its identity as it moves or as it is carried. In China, to translate is also understood by many people normally as “to translate the whole text sentence by sentence and paragraph by paragraph, without any omission, addition, or other changes. In both views, the source text and the target text must be “the same”. This helps explain the etymological source for the term “translation equivalence”. It is in essence a word which describes the relationship between the ST and the TT.Equivalence means the state or fact or property of being equivalent. It is widely used in several scientific fields such as chemistry and mathematics. Therefore, it comes to have a strong scientific meaning that is rather absolute and concise. Influenced by this, translation equivalence also comes to have an absolute denotation though it was first applied in translation study as a general word. From a linguistic point of view, it can be divided into three sub-types, i.e., formal equivalence, semantic equivalence, and pragmatic equivalence. In actual translation, it frequently happens that they cannot be obtained at the same time, thus forming a kind of relative translation equivalence in terms of quality. In terms of quantity, sometimes the ST and TT are not equivalent too. Absolute translation equivalence both in quality and quantity, even though obtainable, is limited to a few cases.The following is a brief discussion of translation equivalence study conducted by three influential western scholars, Eugene Nida, Andrew Chesterman and Peter Newmark. It‟s expected that their studies can instruct GNT study in China and provide translators with insightful methods.Nida‟s definition of translation is: “Translation consists in reproducing in the receptor language the closest natural equivalent of the source language message, first in terms of meaning and secondly in terms of style.” It i s a replacement of textual material in one language〔SL〕by equivalent textual material in another language(TL). The translator must strive for equivalence rather than identity. In a sense, this is just another way of emphasizing the reproducing of the message rather than the conservation of the form of the utterance. The message in the receptor language should match as closely as possible the different elements in the source language to reproduce as literally and meaningfully as possible the form and content of the original. Translation equivalence is an empirical phenomenon discovered bycomparing SL and TL texts and it‟s a useful operational concept like the term “unit of translati on”.Nida argues that there are two different types of equivalence, namely formal equivalence and dynamic equivalence. Formal correspondence focuses attention on the message itself, in both form and content, whereas dynamic equivalence is based upon “the principle of equivalent effect”.Formal correspondence consists of a TL item which represents the closest equivalent of a ST word or phrase. Nida and Taber make it clear that there are not always formal equivalents between language pairs. Therefore, formal equivalents should be used wherever possible if the translation aims at achieving formal rather than dynamic equivalence. The use of formal equivalents might at times have serious implications in the TT since the translation will not be easily understood by the target readership. According to Nida and Taber, formal correspondence distorts the grammatical and stylistic patterns of the receptor language, and hence distorts the message, so as to cause the receptor to misunderstand or to labor unduly hard.Dyn amic equivalence is based on what Nida calls “the principle of equivalent effect” where the relationship between receptor and message should be substantially the same as that which existed between the original receptors and the message. The message has to be modified to the receptor‟s linguistic needs and cultural expectation and aims at complete naturalness of expression. Naturalness is a key requirement for Nida. He defines the goal of dynamic equivalence as seeking the closest natural equivalent to the SL message. This receptor-oriented approach considers adaptations of grammar, of lexicon and of cultural references to be essential in order to achieve naturalness; the TL should not show interference from the SL, and the …foreignness …of the ST setting is minimized.Nida is in favor of the application of dynamic equivalence, as a more effective translation procedure. Thus, the product of the translation process, that is the text in the TL, must have the same impact on the different readers it was addressing. Only in Nida and Taber's edition is it clearly stated that dynamic equivalence in translation is far more than mere correct communication of information.As Andrew Chesterman points out in his recent book Memes of Translation, equivalence is one of the five element of translation theory, standing shoulder to shoulder with source-target, untranslatability, free-vs-literal, All-writing-is-translating in importance. Pragmatically speaking, observed Chesterman, “the only true examples of equivalence (i.e., absolute equivalence) are those in which an ST item X is invariably translated into a given TL as Y, and vice versa. Typical examples would be words denoting numbers (with the exceptionof contexts in which they have culture-bound connotations, such as “magic” or “unlucky”), certain technical terms (oxygen, molecule) and the like. From this point of view, the only true test of equivalence would be invariable back-translation. This, of course, is unlikely to occur except in the case of a small set of lexical items, or perhaps simple isolated syntactic structure”.Peter Newmark. Departing from Nida‟s receptor-oriented line, Newmark argues that the success of equivalent effect is “illusory “and that the conflict of loyalties and the gap between emphasis on source and target language will always remain as the overriding problem in translation theory and practice. He suggests narrowing the gap by replacing the old terms with those of semantic and communicative translation. The former attempts to render, as closely as the semantic and syntactic structures of the second language allow, the exact contextual meaning of the original, while the latter “attempts to produce on its readers an effect as close as possible to that obtained on the readers of the original.” Newmark‟s description of communicative translation resembles Nida‟s dynamic equivalence in the effect it is trying to create on the TT reader, while semantic translation has similarities to Nida‟s formal equivalence.Meanwhile, Newmark points out that only by combining both semantic and communicative translation can we achieve the goal of keeping the …spirit‟ of the original. Semantic translation requires the translator retain the aesthetic value of the original, trying his best to keep the linguistic feature and characteristic style of the author. According to semantic translation, the translator should always retain the semantic and syntactic structures of the original. Deletion and abridgement lead to distortion of the author‟s intention and his writing style.翻译对等尽管全世界正在渐渐成为一个地球村,但翻译仍然是语言和和文化之间的交流互动和相互影响的主要方式之一。
毕业设计外文翻译英文

Bid Compensation Decision Model for Projectswith Costly Bid PreparationS.Ping Ho,A.M.ASCE 1Abstract:For projects with high bid preparation cost,it is often suggested that the owner should consider paying bid compensation to the most highly ranked unsuccessful bidders to stimulate extra effort or inputs in bid preparation.Whereas the underlying idea of using bid compensation is intuitively sound,there is no theoretical basis or empirical evidence for such suggestion.Because costly bid preparation often implies a larger project scale,the issue of bid compensation strategy is important to practitioners and an interest of study.This paper aims to study the impacts of bid compensation and to develop appropriate bid compensation strategies.Game theory is applied to analyze the behavioral dynamics between competing bidders and project owners.A bid compensation model based on game theoretic analysis is developed in this study.The model provides equilibrium solutions under bid compensation,quantitative formula,and quali-tative implications for the formation of bid compensation strategies.DOI:10.1061/(ASCE )0733-9364(2005)131:2(151)CE Database subject headings:Bids;Project management;Contracts;Decision making;Design/build;Build/Operate/Transfer;Construction industry .IntroductionAn often seen suggestion in practice for projects with high bid preparation cost is that the owner should consider paying bid compensation,also called a stipend or honorarium,to the unsuc-cessful bidders.For example,according to the Design–build Manual of Practice Document Number 201by Design–Build In-stitute of America (DBIA )(1996a ),it is suggested that that “the owner should consider paying a stipend or honorarium to the unsuccessful proposers”because “excessive submittal require-ments without some compensation is abusive to the design–build industry and discourages quality teams from participating.”In another publication by DBIA (1995),it is also stated that “it is strongly recommended that honorariums be offered to the unsuc-cessful proposers”and that “the provision of reasonable compen-sation will encourage the more sought-after design–build teams to apply and,if short listed,to make an extra effort in the prepara-tion of their proposal.”Whereas bid preparation costs depend on project scale,delivery method,and other factors,the cost of pre-paring a proposal is often relatively high in some particular project delivery schemes,such as design–build or build–operate–transfer (BOT )contracting.Plus,costly bid preparation often im-plying a large project scale,the issue of bid compensation strat-egy should be important to practitioners and of great interest of study.Existing research on the procurement process in constructionhas addressed the selection of projects that are appropriate for certain project delivery methods (Molenaar and Songer 1998;Molenaar and Gransberg 2001),the design–build project procure-ment processes (Songer et al.1994;Gransberg and Senadheera 1999;Palaneeswaran and Kumaraswamy 2000),and the BOT project procurement process (United Nations Industrial Develop-ment Organization 1996).However,the bid compensation strat-egy for projects with a relatively high bid preparation cost has not been studied.Among the issues over the bidder’s response to the owner’s procurement or bid compensation strategy,it is in own-er’s interest to understand how the owner can stimulate high-quality inputs or extra effort from the bidder during bid prepara-tion.Whereas the argument for using bid compensation is intuitively sound,there is no theoretical basis or empirical evi-dence for such an argument.Therefore,it is crucial to study under what conditions the bid compensation is effective,and how much compensation is adequate with respect to different bidding situa-tions.This paper focuses on theoretically studying the impacts of bid compensation and tries to develop appropriate compensation strategies for projects with a costly bid preparation.Game theory will be applied to analyze the behavioral dynamics between com-peting bidders.Based on the game theoretic analysis and numeric trials,a bid compensation model is developed.The model pro-vides a quantitative framework,as well as qualitative implica-tions,on bid compensation strategies.Research Methodology:Game TheoryGame theory can be defined as “the study of mathematical models of conflict and cooperation between intelligent rational decision-makers”(Myerson 1991).Among economic theories,game theory has been successfully applied to many important issues such as negotiations,finance,and imperfect markets.Game theory has also been applied to construction management in two areas.Ho (2001)applied game theory to analyze the information asymme-try problem during the procurement of a BOT project and its1Assistant Professor,Dept.of Civil Engineering,National Taiwan Univ.,Taipei 10617,Taiwan.E-mail:spingho@.twNote.Discussion open until July 1,2005.Separate discussions must be submitted for individual papers.To extend the closing date by one month,a written request must be filed with the ASCE Managing Editor.The manuscript for this paper was submitted for review and possible publication on March 5,2003;approved on March 1,2004.This paper is part of the Journal of Construction Engineering and Management ,V ol.131,No.2,February 1,2005.©ASCE,ISSN 0733-9364/2005/2-151–159/$25.00.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .implication in project financing and government policy.Ho and Liu (2004)develop a game theoretic model for analyzing the behavioral dynamics of builders and owners in construction claims.In competitive bidding,the strategic interactions among competing bidders and that between bidders and owners are com-mon,and thus game theory is a natural tool to analyze the prob-lem of concern.A well-known example of a game is the “prisoner’s dilemma”shown in Fig.1.Two suspects are arrested and held in separate cells.If both of them confess,then they will be sentenced to jail for 6years.If neither confesses,each will be sentenced for only 1year.However,if one of them confesses and the other does not,then the honest one will be rewarded by being released (in jail for 0year )and the other will be punished for 9years in jail.Note that in each cell,the first number represents player No.1’s payoff and the second one represents player No.2’s.The prisoner’s dilemma is called a “static game,”in which they act simultaneously;i.e.,each player does not know the other player’s decision before the player makes the decision.If the payoff matrix shown in Fig.1is known to all players,then the payoff matrix is a “common knowledge”to all players and this game is called a game of “complete information.”Note that the players of a game are assumed to be rational;i.e.,to maximize their payoffs.To answer what each prisoner will play/behave in this game,we will introduce the concept of “Nash equilibrium ,”one of the most important concepts in game theory.Nash equilibrium is a set of actions that will be chosen by each player.In a Nash equilib-rium,each player’s strategy should be the best response to the other player’s strategy,and no player wants to deviate from the equilibrium solution.Thus,the equilibrium or solution is “strate-gically stable”or “self-enforcing”(Gibbons 1992).Conversely,a nonequilibrium solution is not stable since at least one of the players can be better off by deviating from the nonequilibrium solution.In the prisoner’s dilemma,only the (confess,confess )solution where both players choose to confess,satisfies the stabil-ity test or requirement of Nash equilibrium.Note that although the (not confess,not confess )solution seems better off for both players compared to Nash equilibrium;however,this solution is unstable since either player can obtain extra benefit by deviating from this solution.Interested readers can refer to Gibbons (1992),Fudenberg and Tirole (1992),and Myerson (1991).Bid Compensation ModelIn this section,the bid compensation model is developed on the basis of game theoretic analysis.The model could help the ownerform bid compensation strategies under various competition situ-ations and project characteristics.Illustrative examples with nu-merical results are given when necessary to show how the model can be used in various scenarios.Assumptions and Model SetupTo perform a game theoretic study,it is critical to make necessary simplifications so that one can focus on the issues of concern and obtain insightful results.Then,the setup of a model will follow.The assumptions made in this model are summarized as follows.Note that these assumptions can be relaxed in future studies for more general purposes.1.Average bidders:The bidders are equally good,in terms oftheir technical and managerial capabilities.Since the design–build and BOT focus on quality issues,the prequalification process imposed during procurement reduces the variation of the quality of bidders.As a result,it is not unreasonable to make the “average bidders”assumption.plete information:If all players consider each other tobe an average bidder as suggested in the first assumption,it is natural to assume that the payoffs of each player in each potential solution are known to all players.3.Bid compensation for the second best bidder:Since DBIA’s(1996b )manual,document number 103,suggests that “the stipend is paid only to the most highly ranked unsuccessful offerors to prevent proposals being submitted simply to ob-tain a stipend,”we shall assume that the bid compensation will be offered to the second best bidder.4.Two levels of efforts:It is assumed that there are two levelsof efforts in preparing a proposal,high and average,denoted by H and A ,respectively.The effort A is defined as the level of effort that does not incur extra cost to improve quality.Contrarily,the effort H is defined as the level of effort that will incur extra cost,denoted as E ,to improve the quality of a proposal,where the improvement is detectable by an effec-tive proposal evaluation system.Typically,the standard of quality would be transformed to the evaluation criteria and their respective weights specified in the Request for Pro-posal.5.Fixed amount of bid compensation,S :The fixed amount canbe expressed by a certain percentage of the average profit,denoted as P ,assumed during the procurement by an average bidder.6.Absorption of extra cost,E :For convenience,it is assumedthat E will not be included in the bid price so that the high effort bidder will win the contract under the price–quality competition,such as best-value approach.This assumption simplifies the tradeoff between quality improvement and bid price increase.Two-Bidder GameIn this game,there are only two qualified bidders.The possible payoffs for each bidder in the game are shown in a normal form in Fig.2.If both bidders choose “H ,”denoted by ͑H ,H ͒,both bidders will have a 50%probability of wining the contract,and at the same time,have another 50%probability of losing the con-tract but being rewarded with the bid compensation,S .As a re-sult,the expected payoffs for the bidders in ͑H ,H ͒solution are ͑S /2+P /2−E ,S /2+P /2−E ͒.Note that the computation of the expected payoff is based on the assumption of the average bidder.Similarly,if the bidders choose ͑A ,A ͒,the expected payoffswillFig.1.Prisoner’s dilemmaD o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .be ͑S /2+P /2,S /2+P /2͒.If the bidders choose ͑H ,A ͒,bidder No.1will have a 100%probability of winning the contract,and thus the expected payoffs are ͑P −E ,S ͒.Similarly,if the bidders choose ͑A ,H ͒,the expected payoffs will be ͑S ,P −E ͒.Payoffs of an n -bidder game can be obtained by the same reasoning.Nash EquilibriumSince the payoffs in each equilibrium are expressed as functions of S ,P ,and E ,instead of a particular number,the model will focus on the conditions for each possible Nash equilibrium of the game.Here,the approach to solving for Nash equilibrium is to find conditions that ensure the stability or self-enforcing require-ment of Nash equilibrium.This technique will be applied throughout this paper.First,check the payoffs of ͑H ,H ͒solution.For bidder No.1or 2not to deviate from this solution,we must haveS /2+P /2−E ϾS →S ϽP −2E͑1͒Therefore,condition (1)guarantees ͑H ,H ͒to be a Nash equilib-rium.Second,check the payoffs of ͑A ,A ͒solution.For bidder No.1or 2not to deviate from ͑A ,A ͒,condition (2)must be satisfiedS /2+P /2ϾP −E →S ϾP −2E͑2͒Thus,condition (2)guarantees ͑A ,A ͒to be a Nash equilibrium.Note that the condition “S =P −2E ”will be ignored since the con-dition can become (1)or (2)by adding or subtracting an infinitely small positive number.Thus,since S must satisfy either condition (1)or condition (2),either ͑H ,H ͒or ͑A ,A ͒must be a unique Nash equilibrium.Third,check the payoffs of ͑H ,A ͒solution.For bid-der No.1not to deviate from H to A ,we must have P −E ϾS /2+P /2;i.e.,S ϽP −2E .For bidder No.2not to deviate from A to H ,we must have S ϾS /2+P /2−E ;i.e.,S ϾP −2E .Since S cannot be greater than and less than P −2E at the same time,͑H ,A ͒solution cannot exist.Similarly,͑A ,H ͒solution cannot exist either.This also confirms the previous conclusion that either ͑H ,H ͒or ͑A ,A ͒must be a unique Nash equilibrium.Impacts of Bid CompensationBid compensation is designed to serve as an incentive to induce bidders to make high effort.Therefore,the concerns of bid com-pensation strategy should focus on whether S can induce high effort and how effective it is.According to the equilibrium solu-tions,the bid compensation decision should depend on the mag-nitude of P −2E or the relative magnitude of E compared to P .If E is relatively small such that P Ͼ2E ,then P −2E will be positive and condition (1)will be satisfied even when S =0.This means that bid compensation is not an incentive for high effort when the extra cost of high effort is relatively low.Moreover,surprisingly,S can be damaging when S is high enough such that S ϾP −2E .On the other hand,if E is relatively large so that P −2E is negative,then condition (2)will always be satisfied since S can-not be negative.In this case,͑A ,A ͒will be a unique Nash equi-librium.In other words,when E is relatively large,it is not in the bidder’s interest to incur extra cost for improving the quality of proposal,and therefore,S cannot provide any incentives for high effort.To summarize,when E is relatively low,it is in the bidder’s interest to make high effort even if there is no bid compensation.When E is relatively high,the bidder will be better off by making average effort.In other words,bid compensation cannot promote extra effort in a two-bidder game,and ironically,bid compensa-tion may discourage high effort if the compensation is too much.Thus,in the two-bidder procurement,the owner should not use bid compensation as an incentive to induce high effort.Three-Bidder GameNash EquilibriumFig.3shows all the combinations of actions and their respective payoffs in a three-bidder game.Similar to the two-bidder game,here the Nash equilibrium can be solved by ensuring the stability of the solution.For equilibrium ͑H ,H ,H ͒,condition (3)must be satisfied for stability requirementS /3+P /3−E Ͼ0→S Ͼ3E −P͑3͒For equilibrium ͑A ,A ,A ͒,condition (4)must be satisfied so that no one has any incentives to choose HS /3+P /3ϾP −E →S Ͼ2P −3E͑4͒In a three-bidder game,it is possible that S will satisfy conditions (3)and (4)at the same time.This is different from the two-bidder game,where S can only satisfy either condition (1)or (2).Thus,there will be two pure strategy Nash equilibria when S satisfies conditions (3)and (4).However,since the payoff of ͑A ,A ,A ͒,S /3+P /3,is greater than the payoff of ͑H ,H ,H ͒,S /3+P /3−E ,for all bidders,the bidder will choose ͑A ,A ,A ͒eventually,pro-vided that a consensus between bidders of making effort A can be reached.The process of reaching such consensus is called “cheap talk,”where the agreement is beneficial to all players,and no player will want to deviate from such an agreement.In the design–build or BOT procurement,it is reasonable to believe that cheap talk can occur.Therefore,as long as condition (4)is satis-fied,͑A ,A ,A ͒will be a unique Nash equilibrium.An important implication is that the cheap talk condition must not be satisfied for any equilibrium solution other than ͑A ,A ,A ͒.In other words,condition (5)must be satisfied for all equilibrium solution except ͑A ,A ,A͒Fig.2.Two-biddergameFig.3.Three-bidder gameD o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .S Ͻ2P −3E ͑5͒Following this result,for ͑H ,H ,H ͒to be unique,conditions (3)and (5)must be satisfied;i.e.,we must have3E −P ϽS Ͻ2P −3E͑6͒Note that by definition S is a non-negative number;thus,if one cannot find a non-negative number to satisfy the equilibrium con-dition,then the respective equilibrium does not exist and the equi-librium condition will be marked as “N/A”in the illustrative fig-ures and tables.Next,check the solution where two bidders make high efforts and one bidder makes average effort,e.g.,͑H ,H ,A ͒.The ex-pected payoffs for ͑H ,H ,A ͒are ͑S /2+P /2−E ,S /2+P /2−E ,0͒.For ͑H ,H ,A ͒to be a Nash equilibrium,S /3+P /3−E Ͻ0must be satisfied so that the bidder with average effort will not deviate from A to H ,S /2+P /2−E ϾS /2must be satisfied so that the bidder with high effort will not deviate from H to A ,and condi-tion (5)must be satisfied as argued previously.The three condi-tions can be rewritten asS Ͻmin ͓3E −P ,2P −3E ͔andP −2E Ͼ0͑7͒Note that because of the average bidder assumption,if ͑H ,H ,A ͒is a Nash equilibrium,then ͑H ,A ,H ͒and ͑A ,H ,H ͒will also be the Nash equilibria.The three Nash equilibria will constitute a so-called mixed strategy Nash equilibrium,denoted by 2H +1A ,where each bidder randomizes actions between H and A with certain probabilities.The concept of mixed strategy Nash equilib-rium shall be explained in more detail in next section.Similarly,we can obtain the requirements for solution 1H +2A ,condition (5)and S /2+P /2−E ϽS /2must be satisfied.The requirements can be reorganized asS Ͻ2P −3EandP −2E Ͻ0͑8͒Note that the conflicting relationship between “P −2E Ͼ0”in condition (7)and “P −2E Ͻ0”in condition (8)seems to show that the two types of Nash equilibria are exclusive.Nevertheless,the only difference between 2H +1A and 1H +2A is that the bidder in 2H +1A equilibrium has a higher probability of playing H ,whereas the bidder in 1H +2A also mixes actions H and A but with lower probability of playing H .From this perspective,the difference between 2H +1A and 1H +2A is not very distinctive.In other words,one should not consider,for example,2H +1A ,to be two bidders playing H and one bidder playing A ;instead,one should consider each bidder to be playing H with higher probabil-ity.Similarly,1H +2A means that the bidder has a lower probabil-ity of playing H ,compared to 2H +1A .Illustrative Example:Effectiveness of Bid Compensation The equilibrium conditions for a three-bidder game is numerically illustrated and shown in Table 1,where P is arbitrarily assumed as 10%for numerical computation purposes and E varies to rep-resent different costs for higher efforts.The “*”in Table 1indi-cates that the zero compensation is the best strategy;i.e.,bid compensation is ineffective in terms of stimulating extra effort.According to the numerical results,Table 1shows that bid com-pensation can promote higher effort only when E is within the range of P /3ϽE ϽP /2,where zero compensation is not neces-sarily the best strategy.The question is that whether it is benefi-cial to the owner by incurring the cost of bid compensation when P /3ϽE ϽP /2.The answer to this question lies in the concept and definition of the mix strategy Nash equilibrium,2H +1A ,as explained previously.Since 2H +1A indicates that each bidderwill play H with significantly higher probability,2H +1A may already be good enough,knowing that we only need one bidder out of three to actually play H .We shall elaborate on this concept later in a more general setting.As a result,if the 2H +1A equilib-rium is good enough,the use of bid compensation in a three-bidder game will not be recommended.Four-Bidder Game and n-Bidder GameNash Equilibrium of Four-Bidder GameThe equilibrium of the four-bidder procurement can also be ob-tained.As the number of bidders increases,the number of poten-tial equilibria increases as well.Due to the length limitation,we shall only show the major equilibria and their conditions,which are derived following the same technique applied previously.The condition for pure strategy equilibrium 4H ,is4E −P ϽS Ͻ3P −4E͑9͒The condition for another pure strategy equilibrium,4A ,isS Ͼ3P −4E͑10͒Other potential equilibria are mainly mixed strategies,such as 3H +1A ,2H +2A ,and 1H +3A ,where the numeric number asso-ciated with H or A represents the number of bidders with effort H or A in a equilibrium.The condition for the 3H +1A equilibrium is3E −P ϽS Ͻmin ͓4E −P ,3P −4E ͔͑11͒For the 2H +2A equilibrium the condition is6E −3P ϽS Ͻmin ͓3E −P ,3P −4E ͔͑12͒The condition for the 1H +3A equilibrium isS Ͻmin ͓6E −3P ,3P −4E ͔͑13͒Illustrative Example of Four-Bidder GameTable 2numerically illustrates the impacts of bid compensation on the four-bidder procurement under different relative magni-tudes of E .When E is very small,bid compensation is not needed for promoting effort H .However,when E grows gradually,bid compensation becomes more effective.As E grows to a larger magnitude,greater than P /2,the 4H equilibrium would become impossible,no matter how large S is.In fact,if S is too large,bidders will be encouraged to take effort A .When E is extremely large,e.g.,E Ͼ0.6P ,the best strategy is to set S =0.The “*”in Table 2also indicates the cases that bid compensation is ineffec-Table pensation Impacts on a Three-Bidder GameEquilibriumE ;P =10%3H 2H +1A 1H +2A 3A E ϽP /3e.g.,E =2%S Ͻ14%*N/A N/N 14%ϽS P /3ϽE ϽP /2e.g.,E =4%2%ϽS Ͻ8%S Ͻ2%N/A 8%ϽS P /2ϽE Ͻ͑2/3͒P e.g.,E =5.5%N/AN/AS Ͻ3.5%*3.5%ϽS͑2/3͒P ϽEe.g.,E =7%N/A N/A N/A Always*Note:*denotes that zero compensation is the best strategy;and N/A =the respective equilibrium does not exist.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .tive.To conclude,in a four-bidder procurement,bid compensation is not effective when E is relatively small or large.Again,similar to the three-bidder game,when bid compensation becomes more effective,it does not mean that offering bid compensation is the best strategy,since more variables need to be considered.Further analysis shall be performed later.Nash Equilibrium of n -Bidder GameIt is desirable to generalize our model to the n -bidder game,al-though only very limited qualified bidders will be involved in most design–build or BOT procurements,since for other project delivery methods it is possible to have many bidders.Interested readers can follow the numerical illustrations for three-and four-bidder games to obtain the numerical solutions of n -bidder game.Here,only analytical equilibrium solutions will be solved.For “nA ”to be the Nash equilibrium,we must have P −E ϽS /n +P /n for bidder A not to deviate.In other words,condition (14)must be satisfiedS Ͼ͑n −1͒P −nE͑14͒Note that condition (14)can be rewritten as S Ͼn ͑P −E ͒−P ,which implies that it is not likely for nA to be the Nash equilib-rium when there are many bidders,unless E is very close to or larger than P .Similar to previous analysis,for “nH ”to be the equilibrium,we must have S /n +P /n −E Ͼ0for stability requirement,and condition (15)for excluding the possibility of cheap talk or nA equilibrium.The condition for the nH equilibrium can be reorga-nized as condition (16).S Ͻ͑n −1͒P −nE ͑15͒nE −P ϽS Ͻ͑n −1͒P −nE͑16͒Note that if E ϽP /n ,condition (16)will always be satisfied and nH will be a unique equilibrium even when S =0.In other words,nH will not be the Nash equilibrium when there are many bidders,unless E is extremely small,i.e.,E ϽP /n .For “aH +͑n −a ͒A ,where 2Ͻa Ͻn ”to be the equilibrium so-lution,we must have S /a +P /a −E Ͼ0for bidder H not to devi-ate,S /͑a +1͒+P /͑a +1͒−E Ͻ0for bidder A not to deviate,and condition (15).These requirements can be rewritten asaE −P ϽS Ͻmin ͓͑a +1͒E −P ,͑n −1͒P −nE ͔͑17͒Similarly,for “2H +͑n −2͒A ,”the stability requirements for bidder H and A are S /͑n −1͒ϽS /2+P /2−E and S /3+P /3−E Ͻ0,re-spectively,and thus the equilibrium condition can be written as ͓͑n −1͒/͑n −3͔͒͑2E −P ͒ϽS Ͻmin ͓3E −P ,͑n −1͒P −nE ͔͑18͒For the “1H +͑n −1͒A ”equilibrium,we must haveS Ͻmin ͕͓͑n −1͒/͑n −3͔͒͑2E −P ͒,͑n −1͒P −nE ͖͑19͒An interesting question is:“What conditions would warrant that the only possible equilibrium of the game is either “1H +͑n −1͒A ”or nA ,no matter how large S is?”A logical response to the question is:when equilibria “aH +͑n −a ͒A ,where a Ͼ2”and equilibrium 2H +͑n −2͒A are not possible solutions.Thus,a suf-ficient condition here is that for any S Ͼ͓͑n −1͒/͑n −3͔͒͑2E −P ͒,the “S Ͻ͑n −1͒P −nE ”is not satisfied.This can be guaranteed if we have͑n −1͒P −nE Ͻ͓͑n −1͒/͑n −3͔͒͑2E −P ͒→E Ͼ͓͑n −1͒/͑n +1͔͒P͑20͒Conditions (19)and (20)show that when E is greater than ͓͑n −1͒/͑n +1͔͒P ,the only possible equilibrium of the game is either 1H +͑n −1͒A or nA ,no matter how large S is.Two important practical implications can be drawn from this finding.First,when n is small in a design–build contract,it is not unusual that E will be greater than ͓͑n −1͒/͑n +1͔͒P ,and in that case,bid compensa-tion cannot help to promote higher effort.For example,for a three-bidder procurement,bid compensation will not be effective when E is greater than ͑2/4͒P .Second,when the number of bidders increases,bid compensation will become more effective since it will be more unlikely that E is greater than ͓͑n −1͒/͑n +1͔͒P .The two implications confirm the previous analyses of two-,three-,and four-bidder game.After the game equilibria and the effective range of bid compensation have been solved,the next important task is to develop the bid compensation strategy with respect to various procurement situations.Table pensation Impacts on a Four-Bidder GameEquilibriumE ;P =10%4H 3H +1A 2H +2A 1H +3A 4A E ϽP /4e.g.,E =2%S Ͻ22%*N/A N/A N/A S Ͼ22%P /4ϽE ϽP /3e.g.,E =3%2%ϽS Ͻ18%S Ͻ2%N/A N/A S Ͼ18%P /3ϽE ϽP /2e.g.,E =4%6%ϽS Ͻ14%2%ϽS Ͻ6%S Ͻ2%N/A S Ͼ14%P /2ϽE Ͻ͑3/5͒P e.g.,E =5.5%N/A 6.5%ϽS Ͻ8%3%ϽS Ͻ6.5%S Ͻ3%S Ͼ8%͑3/5͒P ϽE Ͻ͑3/4͒P e.g.,E =6.5%N/AN/AN/AS Ͻ4%*S Ͼ4%͑3/4͒P ϽEe.g.,E =8%N/A N/A N/A N/AAlways*Note:*denotes that zero compensation is the best strategy;and N/A=respective equilibrium does not exist.D o w n l o a d e d f r o m a s c e l i b r a r y .o r g b y N A N J I N G U N I VE R S I T Y OF o n 01/06/14. C o p y r i g h t A S C E . F o r p e r s o n a l u s e o n l y ; a l l r i g h t s r e s e r v e d .。
毕设外文翻译电子版
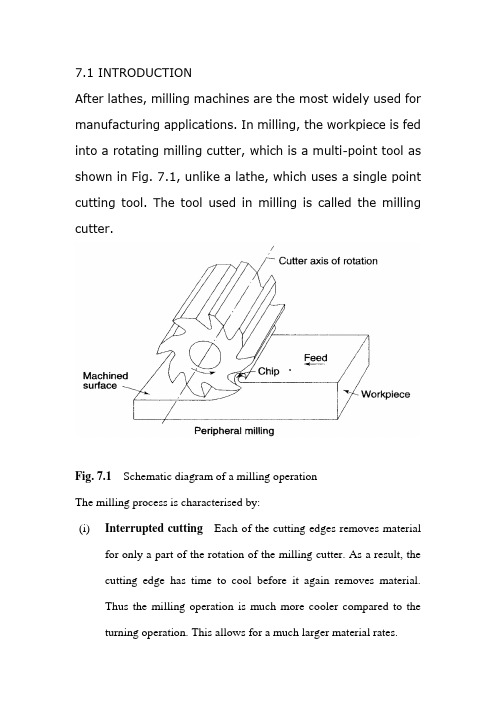
7.1 INTRODUCTIONAfter lathes, milling machines are the most widely used for manufacturing applications. In milling, the workpiece is fed into a rotating milling cutter, which is a multi-point tool as shown in Fig. 7.1, unlike a lathe, which uses a single point cutting tool. The tool used in milling is called the milling cutter.Fig. 7.1Schematic diagram of a milling operationThe milling process is characterised by:(i)Interrupted cutting Each of the cutting edges removes materialfor only a part of the rotation of the milling cutter. As a result, the cutting edge has time to cool before it again removes material.Thus the milling operation is much more cooler compared to the turning operation. This allows for a much larger material rates.(ii)Small size of chips Though the size of the chips is small, in view of the multiple cutting edges in contact a large amount of material is removed and as a result the component is generally completed ina single pass unlike the turning process which requires a largenumber of cuts for finishing.(iii)Variation in chip thickness This contributes to the non-steady state cyclic conditions of varying cutting forces during the contact of the cutting edge with the chip thickness varying from zero to maximum size or vice versa. This cyclic variation of the force can excite any of the natural frequencies of the machine tool system and is harmful to the tool life and surface finish generatedA milling machine is one of the most versatile machine tools. It is adaptable for quantity production as well as in job shops and tool rooms. The versatility of milling is because of the large variety of accessories and tools available with milling machines. The typical tolerance expected from the process is about ±0.050 mm.7.2 TYPES OF MILLING MACHINESTo satisfy various requirements milling machines come in a number of sizes and varieties. In view of the large material removal ratesmilling machines come with a very rigid spindle and large power. The varieties of milling machines available are:(i) Knee and Column type(a) horizontal(b) vertical(c) universal(d) turret typeThese are the general purpose milling machines, which have a high degree of flexibility and are employed for all types of works including batch manufacturing. A large variety of attachments to improve the flexibility are available for this class of milling machines.(ii) Production (Bed) type(a) simplex(b) duplex(c) triplexThese machines are generally meant for regular production involving large batch sizes. The flexibility is relatively less in these machines which is suitable for productivity enhancement.(iii) Plano millersThese machines are used only for very large workpieces involving table travels in meters.(iv) Special type(a) Rotary table(b) Drum type(c) Copy milling (Die sinking machines)(d) Key way milling machines(e) Spline shaft milling machinesThese machines provide special facilities to suit specific applications that are not catered to by the other classes of milling machines.7.2.1 Knee and Column Milling MachinesThe knee(升降台) and column type is the most commonly used machine in view of its flexibility and easier setup. A typical machine construction is shown in Fig. 7.2 for the horizontal axis. The knee houses the feed mechanism and mounts the saddle and table. The table basically has the T-slots running along the X-axis for the purpose of work holding. The table moves along the X-axis on the saddle while the saddle moves along the Y-axis on the guide ways provided on the knee.The feed is provided either manually with a hand wheel or connected for automatic by the lead screw, which in turn is coupled to the main spindle drive. The knee can move up and down (Z-axis) on a dovetail provided on the column.Fig. 7.2 Horizontal knee and column type milling machineThe massive column at the back of the machine houses all the power train including the motor and the spindle gearbox. The power for feeding the table lead screw is taken from the main motor through a separate feed gearbox. Sometimes a separate feed motor is provided for the feed gearbox as well.While the longitudinal and traverse motions are provided with automatic motion, the raising of the knee is generally made manually.The spindle is located at the top end of the column. The arbour used to mount the milling cutters is mounted in the spindle and is provided with a support on the other end to take care of the heavy cutting forces by means of an overarm with bearing. As shown in Fig.7.2 the overarm extends from the column with a rigid design. The spindle nose has the standard Morse taper of the suitable sizedepending upon the machine size.The milling cutters are mounted on the arbour at any desired position, the rest of the length being filled by standard hardened collars of varying widths to fix the position of the cutter. The arbour is clamped in the spindle with the help of a draw bar and then fixed with nuts.Milling machines are generally specified on the following basis:(i) Size of the table, which specifies the actual working area on the table and relates to the maximum size of the workpiece that can be accommodated.(ii) Amount of table travel, which gives the maximum axis movement that is possible.(iii) Horse power of the spindle, which actually specifies the power of the spindle motor used. Smaller machines may come with 1 to 3 hp while the production machines may go from 10 to 50 hp.Another type of knee and column milling machine is the vertical axis type. Its construction is very similar to the horizontal axis type, except for the spindle type and location.The vertical axis milling machine is relatively more flexible (Fig. 7.4) and suitable for machining complex cavities such as die cavities in tool rooms. The vertical head is provided with a swiveling facility in horizontal direction whereby the cutter axis can be swivelled. This isuseful for tool rooms where more complex milling operations are carried out.The spindle is located in the vertical direction and is suitable for using the shank mounted milling cutters such as end mills, In view of the location of the tool, the setting up of the workpiece and observing the machining operation is more convenient.Fig, 7.3 Vertical knee and column type milling machineFig.7.4 Some of the milling operations normally carried out on vertical axis machinesThe universal machine has the table which can be swivelled in a horizontal plane at about 45o to either the left or right. This makes the universal machine suitable for milling spur and helical gears as well as worm gears and cams.7.2.2 Bed Type Milling MachineIn production milling machines it is desirable to increase the metal removal rates. If it is done on conventional machines by increasingthe depth of cut, there is possibility of chatter. Hence another varietyof milling machines named as bed type machines are used which are made more rugged and are capable of removing more material. The ruggedness is obtained as a consequence of the reduction in versatility.The table in the case of bed type machines is directly mounted on the bed and is provided with only longitudinal motion.The spindle moves along with the column to provide the cutting action. Simplex machines (Fig. 7.5) are the ones with only one spindle head while duplex machines have two spindles (Fig. 7.6). The two spindles are located on either side of a heavy workpiece and remove material from both sides simultaneously.Fig. 7.5 Simplex bed type milling machineFig. 7.6 Duplex bed type milling machine7.3 MILLING CUTTERSThere are a large variety of milling cutters available to suit specific requirements. The versatility of the milling machine is contributed toa great extent by the variety of milling cutters that are available.7.3.1 Types of Milling CuttersMilling cutters are classified into various types based on a variety of methods.(i) Based on construction:(a) Solid(b) Inserted tooth typeBased on mounting:(a) Arbor mounted(b) Shank mounted(c) Nose mountedBase on rotation:(a) Right hand rotation (counter clockwise)(b) Left hand rotation (clockwise)Based on helix:(a) Right hand helix(b) Left hand helixMilling cutters are generally made of high speed steel or cemented carbides. The cemented carbide cutters can be of a brazed tip variety or with indexable tips. The indexable variety is more common since it is normally less expensive to replace the worn out cutting edges than to regrind them.Plain milling cutters These are also called slab milling cutters and are basically cylindrical with the cutting teeth on the periphery as shown in Fig. 7.7. These are generally used for machining flat surfaces.Fig. 7.7 Arbor mounted milling cutters for general purposeLight duty slab milling cutters generally have a face width, which is small of the order of 25 mm. They generally have straight teeth and large number of teeth.Heavy duty slab milling cutters come with a smaller number of teeth to allow for more chip space. This allows taking deeper cuts and consequently high material removal rates.Helical milling cutters have a very small number of teeth but a large helix angle. This type of cutter cuts with a shearing action, which can produce a very fine finish. The large helix angle allows the cutter to absorb most of the end load and therefore the cutter enters and leaves the workpiece very smoothly.Side and face milling cutters These have the cutting edges not only onthe face like the slab milling cutters, but also on both the sides. As aresult, these cutters become more versatile since they can be used for side milling as well as for slot milling.Staggered tooth side milling cutters are a variation where the teeth are arranged in an alternate helix pattern. This type is generally used for milling deep slots, since the staggering of teeth provides for greater chip space.Another variation of the side and face cutter is the half side milling cutter, which has cutting edges only on one side. This arrangement provides a positive rake angle and is useful for machining on only one side. These have a much smoother cutting action and a long tool life. The power consumed is also less for these cutters.Fig. 7.8Special forms of arbor mounted milling cuttersSlitting saws The other common form of milling cutters in the arbor mounted category is the slitting saw. This is very similar to a saw blade inappearance as well as function. Most of these have teeth around the circumference while some have side teeth as well. The thickness of these cutters is generally very small and is used for cutting off operations or for deep slots.Special form cutters In addition to the general type of milling cutters described above, there are a large number of special form milling cutters available which are used for machining specific profiles.Angular milling cutters are made in single or double angle cutters for milling any angle such as 30, 45 or 60o Form relieved cutters are made of various shapes such as circular, corner rounding, convex or concave shapes.T-slot milling cutters are used for milling T-slots such as those in the milling machine table. The central slot is to be milled first using an end mill before using the T-slot milling cutter. Woodruff key seat milling cutters are used for milling as the name suggests, woodruff key seats Some other special form cutters are dovetail milling cutters and gear milling cutters.End mills These are shank mounted as shown in Fig. 7.9 and are generally used in vertical axis milling machines. They are used for milling slots, key ways and pockets where other type of milling cutters cannot be used. A depth of cut of almost half the diameter can be taken with the end mills.The end mills have the cutting edge running through the length of the cutting portion as well as on the face radially up to a certain length. The helix angle of the cutting edge promotes smooth and efficient cutting even at high cutting speeds and feed rates. High cutting speeds(转速?) are generally recommended for this type of milling cutters.Fig. 7.9 Shank mounted milling cutters and various types of end mills There are a large variety of end mills. One of the distinctions is based on the method of holding, i.e., the end mill shank can be straight or tapered. The straight shank is used on end mills of small size and held in the milling machine spindle with the help of a suitable collet. The tapered shank can be directly mounted in the spindle with the help of the selfholding taper. If the taper is small compared to the spindle taper, then an adopter accommodating both the tapers is used.The end teeth of the end mills may be terminated at a distance from the cutter center or may proceed till the center (Fig. 7.9 f). Those with the cutting edge up to the center are called slot drills or end cutting end mills since they have the ability to cut into the solid material (Fig. 7.9 g). The other type of end mills which have a larger number of teeth cannot cut into solid material and hence require a pilot hole drilled before a pocket is machined.The cutting edge along the side of an end mill is generally straight and sometimes can be tapered by grinding on a tool and cutter grinder such that the draft required for mould and die cavities can be automatically generated.。
(完整版)_毕业设计(论文)外文翻译_(原文)

毕业设计(论文)——外文翻译(原文)NEW APPLICATION OF DATABASERelational databases in use for over two decades. A large portion of the applications of relational databases in the commercial world, supporting such tasks as transaction processing for banks and stock exchanges, sales and reservations for a variety of businesses, and inventory and payroll for almost of all companies. We study several new applications, which recent years.First. Decision-support systemAs the online availability of data , businesses to exploit the available data to make better decisions about increase sales. We can extract much information for decision support by using simple SQL queries. Recently support based on data analysis and data mining, or knowledge discovery, using data from a variety of sources.Database applications can be broadly classified into transaction processing and decision support. Transaction-processing systems are widely used today, and companies generated by these systems.The term data mining refers loosely to finding relevant information, or “discovering knowledge,” from a large volume of data. Like knowledge discovery in artificial intelligence, data mining attempts to discover statistical rules and patterns automatically from data. However, data mining differs from machine learning in that it deals with large volumes of data, stored primarily on disk.Knowledge discovered from a database can be represented by a set of rules. We can discover rules from database using one of two models:In the first model, the user is involved directly in the process of knowledge discovery.In the second model, the system is responsible for automatically discovering knowledgefrom the database, by detecting patterns and correlations in the data.Work on automatic discovery of rules influenced strongly by work in the artificial-intelligence community on machine learning. The main differences lie in the volume of data databases, and in the need to access disk. Specialized data-mining algorithms developed to which rules are discovered depends on the class of data-mining application. We illustrate rule discovery using two application classes: classification and associations.Second. Spatial and Geographic DatabasesSpatial databases store information related to spatial locations, and provide support for efficient querying and indexing based on spatial locations. Two types of spatial databases are particularly important:Design databases, or computer-aided-design (CAD) databases, are spatial databases used to store design information about databases are integrated-circuit and electronic-device layouts.Geographic databases are spatial databases used to store geographic information, such as maps. Geographic databases are often called geographic information systems.Geographic data are spatial in nature, but differ from design data in certain ways. Maps and satellite images are typical examples of geographic data. Maps may provide not only location information -such as boundaries, rivers and roads---but also much more detailed information associated with locations, such as elevation, soil type, land usage, and annual rainfall.Geographic data can be categorized into two types: raster data (such data consist a bit maps or pixel maps, in two or more dimensions.), vector data (vector data are constructed from basic geographic objects). Map data are often represented in vector format.Third. Multimedia DatabasesRecently, there much interest in databases that store multimedia data, such as images, audio, and video. Today multimedia data typically are stored outside the database, in files systems. When the number of multimedia objects is relatively small, features provided by databases are usually not important. Database functionality becomes important when the number of multimedia objects stored is large. Issues such as transactional updates, querying facilities, and indexing then become important. Multimedia objects often they were created, who created them, and to what category they belong. One approach to building a database for such multimedia objects is to use database for storing the descriptive attributes, and for keeping track of the files in which the multimedia objects are stored.However, storing multimedia outside the database makes it the basis of actual multimedia data content. It can also lead to inconsistencies, such a file that is noted in the database, but whose contents are missing, or vice versa. It is therefore desirable to store the data themselves in the database.Forth. Mobility and Personal DatabasesLarge-scale commercial databases stored in central computing facilities. In the case of distributed database applications, there strong central database and network administration. Two technology trends which this assumption of central control and administration is not entirely correct:1.The increasingly widespread use of personal computers, and, more important, of laptop or “notebook” computers.2.The development of a relatively low-cost wireless digital communication infrastructure, base on wireless local-area networks, cellular digital packet networks, and other technologies.Wireless computing creates a situation where machines no longer at which to materialize the result of a query. In some cases, the location of the user is a parameter of the query. A example is a traveler’s information system that provides data on the current route must be processed based on knowledge of the user’s location, direction of motion, and speed.Energy (battery power) is a scarce resource for mobile computers. This limitation influences many aspects of system design. Among the more interesting consequences of the need for energy efficiency is the use of scheduled data broadcasts to reduce the need for mobile system to transmit queries. Increasingly amounts of data may reside on machines administered by users, rather than by database administrators. Furthermore, these machines may, at times, be disconnected from the network.SummaryDecision-support systems are gaining importance, as companies realize the value of the on-line data collected by their on-line transaction-processing systems. Proposed extensions to SQL, such as the cube operation, of summary data. Data mining seeks to discover knowledge automatically, in the form of statistical rules and patterns from large databases. Data visualization systems data as well as geographic data. Design data are stored primarily as vector data; geographic data consist of a combination of vector and raster data.Multimedia databases are growing in importance. Issues such as similarity-based retrieval and delivery of data at guaranteed rates are topics of current research.Mobile computing systems , leading to interest in database systems that can run on such systems. Query processing in such systems may involve lookups on server database.毕业设计(论文)——外文翻译(译文)数据库的新应用我们使用关系数据库已经有20多年了,关系数据库应用中有很大一部分都用于商业领域支持诸如银行和证券交易所的事务处理、各种业务的销售和预约,以及几乎所有公司都需要的财产目录和工资单管理。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
英文翻译题目:通过分析变压器中溶解气体而进行故障诊断的专家系统姓名: 宋日成学院: 工学院专业: 自动化班级: 自动化112 班学号: 32211218指导教师: 陆静职称: 讲师2015年3月14日南京农业大学教务处制An Expert System for Transformer Fault Diagnosis UsingDissolved Gas AnalysisW. S. Chan ·Y. L. Xu ·X. L. Ding ·W. J. DaiReceived: 9 November 2005 / Accepted: 11 August 2006 / Published online: 7 September 2006© Springer-Verlag 2006Abstract In order to automate the transformer fault diagnosis, improve the accuracy of judgment, the introduction of artificial intelligence expert system fault diagnosis. The system is based on fuzzy reasoning confidence by observing the information, the use of knowledge to reach a conclusion. Test proved this method reduces the randomness of judgment, improved diagnosis.Keywords:Expert System Transformer Troubleshooting1 IntroductionThe power transformer is a major apparatus in a power system, and its correct functioning is vital to system operations. In order to minimize system outages,many devices have evolved to monitor the serviceability of power transformers. These devices, such as, Buchholz relays or differential relays, respond only to a severe power failure requiring immediate removal of the transformer from service, in which case, outages are inevitable. Thus, preventive techniques for early detection faults to avoid outages would be valuable. In this way, analysis of the mixture of the faulty gases dissolved in insulation oil of power transformer has received worldwide recognition as an effective method for the detection of incipient faults. Many researchers and electrical utilities have reported on their experience and developed interpretative criteria on the basis of DGA. However, criteria tend to vary from utility to utility. Each approach has limitations and none of them has a firm mathematical description. Therefore, transformer diagnosis is still in the heuristic stage. For this reason, knowledge-based programming is a suitable approach to implement in such a diagnostic problem. Based on the interpretation of DGA, a prototype of an expert system for diagnosis of suspected transformer faults and their maintenance procedures is proposed. The significant source in this knowledge base is the gas ratio method. Some limitations of this approach are overcome by incorporating the diagnostic procedure and the synthetic expertise method. Furthermore, data bases adopted from TPCS gas records of transformers are incorporated into the expert system to increase the practical performance. Uncertainty of diagnosis is managed by using fuzzy set concepts. This expert system is constructed with rule based knowledge representation, since it can be expressed by experts. The expert system building tool, Knowledge Engineering System (KES), is used in the development of the knowledge systembecause, it has excellent man-machine interface that provides suggestions. Moreover, its inference strategy is similar to the MYCIN. A famous rule-based expert system used for medical diagnosis. The uncertainty of human qualitative diagnostic expertise, e.g., key gas analysis, and another quantitative imprecision, such as, norms threshold and gas ratio boundaries etc., are smoothed by appropriate fuzzy models. With the results of such implementation, different certainty factors will be assigned to the corresponding expertise variables. Both event-driven (forward chaining) andgoal-driven (backward chaining) inferences are used in the inference engine to improve the inference efficiency. To demonstrate the feasibility of the proposed expert system, around hundreds of TPC historical gas records have been tested. It is found that more appropriate faulty types and maintenance suggestions can support the maintenance personals to increase the performance of transformer diagnosis.2.DEVELOPMENT OF DIAGNOSIS AND INTERPRETATIONLike many diagnostic problems, diagnosis of an oil-immersed power transformer is a skilled task. A transformer may function well externally with monitors, while some incipient deterioration may occur internally to cause a fatal problem in the latter development. According to a Japanese experience, nearly 80% of all faults result from incipient deteriorations. Therefore, faults should be identified and avoided at the earliest possible stage by some predictive maintenance technique. DGA is one of the most popular techniques for this problem. Fault gases in transformers are generally produced by oil degradation and other insulating materials, e.g., cellulose and paper. Theoretically, if an incipient oractive fault is present, the individual dissolved gas concentration, gassing rate, total combustible gas (TCG) and cellulose degradation are all significantly increased. By using gas chromatography to analyze the gas dissolved in a transformer's insulating oil, it becomes feasible to judge the incipient fault types. This study is concerned with the following representative combustible gases; hydrogen(H2), methane(C2H 2), ethane(C2H6), ethylene(C2H4), acetylene(C2H2) and carbon monoxide(C0). Many interpretative methods based on DGA to diagnose the nature of incipient deterioration have been reported. Even under normal transformer operational conditions, some of these gases may be formed inside. Thus, it is necessary to build concentration norms from a sufficiently large sampling to assess the statistics. TPC investigated gas data from power transformers to construct its criteria. The developed knowledge base in this paper is partially based on these data. On the other hand, Dornerburg developed a method to judge different faults by rating pairs of concentrations of gases, e.g., CH /H , C H /C2H4, with approximately equal solubility and fusion coefficients. Rogers established mare comprehensive ratio codes to interpret the thermal fault types with theoretical thermodynamic assessments. This gas ratio method was promising because it eliminated the effect of oil volume and simplified the choice of units. Moreover, it systematically classified the diagnosis expertise in a table form. Table 1 displays the ratio method as proposed by Rogers . The dissolved gas may vary with the nature and severity of different faults. By analyzing the energy density of faults, it's possible to distinguish three basic fault processes: overheating(pyrolysis),corona (partial discharge) and arcing discharge.Corona and arcing arise from electrical faults, while overheating is a thermal fault. Both types of faults m y lead to deterioration, while damage from overheating is typically less than that from electrical stress. Infect, different gas trends lead to different faulty types, the key gas method is identified.' For example large amounts of C H and H are produced with minor arcing fault 4. quantities of CH 2aid C2H4 2 may be a symptom of an arcing fault.3.THE PROPOSED DIAGNOSTIC EXPERT SYSTEMThis study is aimed at developing a rule-based expert system to perform transformer diagnosis similar to a human expert. The details of system processing are described below.3.1 The Proposed Diagnostic MethodDiagnosis is a task that requires experience. It is unwise to determine an approach from only a few investigations. Therefore, this study uses the synthetic expertise method with the experienced procedure to assist the popular gas ratio method and complete practical performance.3.1.1 Experienced Diagnostic ProcedureThe overall procedure of routine maintenance for transformers is listed. The core of this procedure is based on the implementation of the DGA technique. The gas ratio method is the significant knowledge source. Some operational limitations of the gas ratio method exist. The ratio table is unable to cover all possible cases. Minimum levels of gases must be present. The solid insulation involving CO and CO are handled separately and the gas ratio codes have been developed mainlyfrom afree-breathing transformer. Other diagnostic expertise should be used to assist this method. Norms, synthetic expertise method and data base records have been incorporated to complete these limitations. The first step of this diagnostic procedure begins by asking DGA for an oil sample to be tested. More important relevant information about the transformer's condition, such as the voltage level, the preservative type, the on-line-tap-changer (OLTC) state, the operating period and degassed time must be known for further inference. Noms (criteria) Set up by TPC power transformers' gas characteristic data are then used to judge the transformers' cactive fault is present, the individual dissolved gas concentration, gassing rate, total combustible gas (TCG) and cellulose degradation are all significantly increased. By using gas chromatography to analyze the gas dissolved in a transformer's insulating oil, it becomes feasible to judge the incipient fault types. This study is concerned with the following representative combustible gases; hydrogen(H2), methane(C2H 2), ethane(C2H6), ethylene(C2H4), acetylene(C2H2) and carbon monoxide(C0). Many interpretative methods based on DGA to diagnose the nature of incipient deterioration have been reported. Even under normal transformer operational conditions, some of these gases may be formed inside. Thus, it is necessary to build concentration normsfrom a sufficiently large sampling to assess the statistics. TPC investigated gas data from power transformers to construct its criteria. The developed knowledge base in this paper is partially based on these data. On the other hanondition. For the abnormal cases, the gas ratio method is used to diagnose transformer fault type. If different or unknown diagnosis results are found from these ratio methods, a further synthetic expertise method is adopted. After these procedures, different severity degrees are assigned to allow appropriate corresponding maintenance suggestions.3.1.2 Synthetic Expertise MethodThe ratio trend, norms threshold, key gas analysis and some expertise are considered as different evidences to confirm some special fault types. In other words, more significant evidences have been collected for some special fault type, better assessment of the transformer status is obtained. The ratio trend can be seen as a modification of the conventional gas ratio and key gas method. Obviously, the above gas trends should be incorporated with other evidences under the experienced procedure for practical use. Noms threshold, the gassing rate, the quantity of total combustible gas (TCG), the TPC maintenance expertise and the fuzzy set assignment are all important evidences considered in the synthetic diagnosis. Other expertise based on a transformer historical data base is also used to analyze the characteristicsof a case transformer. Section 3 . 4 gives some details of these rules. 3.2 Expert System Structure The proposed diagnostic expert system is composed of four components, working memory, a knowledge base, an inference engine and aman-machine interface. Working memory (global data base) contains the current data relevant to solve the present problem. In this study, most of the diagnostic variables stored in the data base are current gas concentration, some are from the user, others are retrieved from the transformer's historical data base. Note that the fuzzy set concept 1s incorporated to create fuzzy variables on the request of system reasoning.A knowledge base is the collection of domain expertise. It contains facts and knowledge relationship, which uses these facts, as the basis for decision making. The production rule used in this system is expressed in IF-THEN forms. A successful expert system depends on a high quality knowledge base. For this transformer diagnostic system, the knowledge base incorporates some popular interpretative methods of DGA, synthetic expertise method and heuristic maintenance rules. Section 3.4 will describe this knowledge base. Another special consideration in the expert system is its inference engine. The inference engine controls the strategies of reasoning and searching for appropriate knowledge. The reasoning strategy employs both forward chaining (data-driven) and backward chaining (goal-driven). Fuzzy rules, norms rules, gas ratio rules, synthetic expertise rules and some of the maintenance rules are implemented by backward chaining. Other rules, such as, procedure rules and some maintenance rules, use forward chaining. As for the searching strategy in KES, the depth first searching and short-circuit evaluation are adopted. The former can improve the search efficiency by properly arranging the location of significant rules in the inference procedures. The latter strategy only searches the key conditional statements in the antecedent that are responsible for establishing whether the entirerule is true or false. Taking the advantages of these two approaches in the building and structuring of a knowledge base improves inference efficiency significantly. As for man-machine interface. KES has an effective interface which is better than typical knowledge programming languages, such as, PROLOG or LISP. With the help of this interface, the capability of tracing, explaining and training in an expert system is greatly simplified.4. IMPLEMENTATION OF THE PROPOSED EXPERT SYSTEMAn expert system is developed based on the proposed interpretative rules and diagnostic procedures of the overall system. To demonstrate the feasibility of this expert system in diagnosis, the gas data supported by MTL of TPC have been tested. In Taiwan, the MTL of TPC performs the DGA and sends the results to all acting divisions relating to power transformers. In return, these acting divisions are requested to collect and supply their transformer oil samples periodically. After analyzing oil samples, more than ten years' worthy gas records are collected and classified into three voltage levels, 69KV,161KV and 345KV. Thus, gas records for one transformer are composed of several groups of data. In the process of DGA interpretation, all of these data may be considered, but only the recent data which have significant effects on diagnosis are listed in the later demonstration. In MTL, all gas concentrations are expressed by ppm in volume concentration. 100 ppm is equal to 0.01 ml (gas)/100 ml (oil). From the expertise of diagnosis, the normal state can be confirmed only by inspection of the transformers' norms level. In practice, most of the transformer oil samples are normal, and this can be inferred successfully on the early execution of this expert system. However, the Success of an expert system is mainly dependent on the capability of diagnosis for the transformers in question. In the implementation, many gas records which are in abnormal condition are chosen to test the Justification of this diagnostic system. A total of 101 transformer records have been executed and the results are summarized in Table 5. Among those implemented, three are listed and demonstrated. Shown in Table 5 are the test results of 101 units of transformers in three types of remedy: normal, thermal fault and arc fault. After comparing them with the actual state and expert judgment, a summary of results was obtained. As previously stated, one unit of transformer may include many groups of gas data. In evaluation, we depicted some key groups in one unit to justify because some transformers may have different incipient faults during different operational stages. Some mistakes implemented from testing are caused by the remaining oil in the oil sampling container, unstable gas characteristics of the new degassing sample and some obscure gas types. If more information or new techniques support other uncertain membership functions, they can be added into the knowledge bas to enlarge the performance of this prototype expert system. Furthermore, the parameters described in Table 2, 3 and 4 are suitable for TPC power transformer. Different regions may be modified if the maintenance personnel find more suitable system parameters.5.CONCLUSIONSA prototype expert system is developed on a personal computer using KES. It can diagnose the incipient faults of the suspected transformers and suggest proper maintenance actions. Fuzzy set concept is used to handle uncertain norms thresholds, gas ratio boundaries and key gas analysis. The synthetic method and diagnostic procedure are proposed to assist the situation which can not be handled properly by the gas ratio methods. Results from the implementation of the expert system shows that the expert system is a useful tool to assist human experts and maintenance engineers. The knowledge base of this expert system is incorporated within the popular interpretative method of DGA, synthetic expertise and heuristic maintenance rules. The data base supported by TPC MTL for about 10 year collection of transformer inspection data is also used to improve the interpretation of diagnosis. Through the development of the proposed expert system, the expertise of TPC MTL can be reserved. In addition, this work can be continued to expand the knowledge base by adding any new experience, measurement and analysis techniques.通过分析变压器中溶解气体而进行故障诊断的专家系统W. S. Chan ·Y. L. Xu ·X. L. Ding ·W. J. DaiReceived: 9 November 2005 / Accepted: 11 August 2006 / Published online: 7September 2006© Springer-Verlag 2006摘要:为了实现变压器故障诊断的自动化,提高判断的准确性,把人工智能专家系统引入到故障诊断中。
