计算机英语 选择题
计算机英语考试题目及答案

计算机英语考试题目及答案一、选择题1. What does HTML stand for?a) Hyper Text Markup Languageb) High Technology Multimedia Languagec) Home Tool Management Languaged) Human Token Marker Language答案:a) Hyper Text Markup Language2. Which of the following is not a programming language?a) Javab) Pythonc) HTMLd) C++答案:c) HTML3. What is the purpose of CSS?a) To add interactivity to web pagesb) To structure the content of web pagesc) To define the layout and style of web pagesd) To create dynamic web pages答案:c) To define the layout and style of web pages4. What is the function of a router in a computer network?a) To connect computers to the internetb) To store and manage data on a networkc) To protect the network from security threatsd) To direct network traffic between devices答案:d) To direct network traffic between devices5. Which of the following is a commonly used database management system?a) Microsoft Wordb) Adobe Photoshopc) MySQLd) Windows Media Player答案:c) MySQL二、填空题1. The process of converting source code into machine code is called ________.答案:compilation2. The most widely used programming language for web development is ________.答案:JavaScript3. TCP/IP stands for ________.答案:Transmission Control Protocol/Internet Protocol4. The physical components of a computer are referred to as ________.答案:hardware5. SQL stands for ________.答案:Structured Query Language三、简答题1. What are the advantages of using cloud computing?答案:Cloud computing offers several advantages, including:- Cost savings: Companies can reduce their infrastructure costs by using cloud services instead of maintaining their own hardware.- Scalability: Cloud services can easily scale up or down based on demand, allowing businesses to only pay for what they need.- Flexibility: Users can access cloud services from anywhere with an internet connection, enabling remote work and collaboration.- Disaster recovery: Cloud providers often have backup systems in place, ensuring data can be recovered in case of a disaster.- Automatic updates: Cloud services are typically updated regularly by the provider, ensuring users have access to the latest features and security patches.2. Explain the difference between HTTP and HTTPS.答案:HTTP (Hypertext Transfer Protocol) is a protocol used for transmitting data over the internet. It is not secure, meaning that the data being transmitted can be intercepted and read by anyone. HTTPS (Hypertext Transfer Protocol Secure), on the other hand, is a secure version of HTTP. It uses encryption to ensure that data is encrypted before transmission, making it much more difficult for hackers to intercept and read. HTTPS is commonly used for secure online transactions, such as submitting credit card information or personal details.四、编程题请编写一个Python程序,实现计算圆的面积和周长的功能。
计算机英语试题3及答案

计算机英语试题3及答案一、选择题(每题2分,共20分)1. Which of the following is not a type of computer virus?A. TrojanB. WormC. Antivirus softwareD. Virus2. What does the acronym "CPU" stand for?A. Central Processing UnitB. Central Processing UnitC. Central Processing UnitD. Central Processing Unit3. In computer terminology, what does "RAM" refer to?A. Random Access MemoryB. Random Access MemoryC. Random Access MemoryD. Random Access Memory4. What is the primary function of a router?A. To store dataB. To transmit dataC. To receive dataD. To process data5. What is the term used to describe the process of converting data into a format that can be transmitted over anetwork?A. EncryptionB. CompressionC. DecompressionD. Encoding6. Which of the following is not a type of software?A. Operating systemB. Application softwareC. Utility softwareD. Hardware7. What does the acronym "GUI" stand for in the context of computer interfaces?A. Graphical User InterfaceB. Graphical User InterfaceC. Graphical User InterfaceD. Graphical User Interface8. What is the term for a computer program that is designed to perform a specific task?A. ApplicationB. ApplicationC. ApplicationD. Application9. What is the term used to describe a computer network that spans a relatively small area?A. LANB. LANC. LAND. LAN10. What does the acronym "USB" stand for?A. Universal Serial BusB. Universal Serial BusC. Universal Serial BusD. Universal Serial Bus二、填空题(每题2分,共20分)1. A computer virus is a type of malicious software that can replicate itself and spread to other computers without the user's permission.2. The central processing unit (CPU) is the primary component of a computer that performs most of the processing inside the computer.3. Random Access Memory (RAM) is a type of computer memory that can be read and changed freely and quickly.4. A router is a networking device that forwards data packets between computer networks.5. Encoding is the process of converting data into a format that can be transmitted over a network.6. Software is a collection of data or computer instructions that tell the hardware what to do and how to do it.7. A Graphical User Interface (GUI) is a type of interface that allows users to interact with electronic devices through graphical icons and visual indicators.8. An application is a computer program designed to help the user to perform specific tasks, such as word processing or web browsing.9. A Local Area Network (LAN) is a computer network that interconnects computers in a localized area.10. Universal Serial Bus (USB) is an industry standard developed in the 1990s that defines the cables, connectors and communications protocols used in a bus for connection, communication, and power supply between computers and electronic devices.三、简答题(每题10分,共40分)1. Explain the difference between a computer virus and a computer worm.A computer virus requires a host program to replicate itself, whereas a computer worm can replicate and spread independently without needing a host program.2. Describe the role of a firewall in computer security.A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks, such as the Internet.3. What are the benefits of using a cloud-based service? Cloud-based services offer benefits such as scalability, accessibility, cost-effectiveness, and the ability to store and process large amounts of data in a remote location.4. Discuss the importance of data backup and recovery in a computer system.Data backup and recovery are crucial for protecting against data loss due to hardware failure, software bugs, data corruption, or cyber-attacks. Regular backups ensure that data can be restored in the event of a system failure,minimizing downtime and potential financial loss.四、论述题(20分)Discuss the impact of the Internet of Things (IoT) on society and the economy.The Internet of Things (IoT) has had a profound impact on society and the economy by enabling the interconnection of everyday objects, allowing them to send and receive data. This has led to increased efficiency in various industries, improved quality of life through smart home technologies, and the creation of new business models and markets. However, it also raises concerns about data privacy and security, as well as the potential for increased surveillance and control.。
计算机英语考试题库

计算机英语考试题库1. 选择题(1) Which of the following is NOT an example of a programming language?a) Pythonb) Javac) HTMLd) CSS(2) What does CPU stand for?a) Central Processing Unitb) Control Processing Unitc) Computer Programming Unitd) Central Programming Unit(3) Which of the following is NOT a type of malware?a) Virusb) Trojanc) Routerd) Worm(4) What does HTML stand for?a) Hyperlink Text Markup Languageb) Hyper Text Markup Languagec) High Text Markup Languaged) Hyperlink Text Manipulation Language(5) What is the purpose of a firewall?a) To block access to websitesb) To protect against malware attacksc) To increase internet speedd) To encrypt confidential data2. 填空题(1) The process of converting source code into machine code is called ___________.(2) TCP stands for ___________.(3) ___________ is a programming language commonly used for web development.(4) RAM stands for ___________.(5) A ___________ is a unique identifier for a network adapter.3. 简答题(1) What is the difference between hardware and software in a computer system?Hardware refers to the physical components of a computer system, such as the monitor, keyboard, and motherboard. Software, on the other hand, refers to the programs and data that are stored on the computer and control its operations. Hardware is tangible and can be seen and touched, while software is intangible and cannot be physically interacted with.(2) What is the purpose of an operating system?An operating system (OS) is a software that manages computer hardware and software resources and provides common services for computer programs. Its purpose is to facilitate the execution of user programs and make it easier for users to interact with the computer. The OS handles tasks such as process management, memory management, file management, and device management.(3) Explain the concept of object-oriented programming.Object-oriented programming (OOP) is a programming paradigm that organizes data and behaviors into objects, which are instances of classes. A class defines the structure and behavior of objects, and objects can interact with each other through methods and attributes. OOP promotes modular and reusable code, as well as encapsulation and abstraction of data. This approach allows for more efficient and easier development, maintenance, and modification of software systems.4. 问答题(1) What are the main programming paradigms?The main programming paradigms include:- Procedural programming: Focuses on procedures or routines that manipulate data.- Object-oriented programming: Focuses on organizing data and behaviors into objects.- Functional programming: Focuses on using mathematical functions and avoids changing state and mutable data.- Logical programming: Focuses on using logical rules and constraints to solve problems.- Imperative programming: Focuses on expressing computation steps explicitly and changing program state.- Event-driven programming: Focuses on handling events and responding to user actions or system events.- Parallel programming: Focuses on executing tasks concurrently to improve performance.(2) What are the differences between HTTP and HTTPS?HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertext Transfer Protocol Secure) are both protocols used for communication over the internet. The main differences are:- Security: HTTP is not secure and data is transmitted as plain text, making it vulnerable to interception and manipulation. HTTPS encrypts data using SSL/TLS protocols, providing confidentiality and integrity.- Port: HTTP uses port 80 by default, while HTTPS uses port 443.- Certificate: HTTPS requires a digital certificate from a trusted Certificate Authority (CA) to establish a secure connection. HTTP does not require a certificate.- Speed: HTTPS may be slightly slower than HTTP due to the encryption and decryption processes.5. 名词解释(1) Firewall: A firewall is a network security device that monitors and filters incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and an untrusted external network, preventing unauthorized access and protecting against malware and other cyber threats.(2) Cache: In computing, a cache is a high-speed data storage layer that stores frequently accessed or recently used data. It serves as a temporary storage to improve data retrieval speed and reduce latency. Caches can be found at different levels in a computer system, such as CPU cache, web browser cache, and DNS cache.(3) Algorithm: An algorithm is a set of step-by-step instructions or rules used to solve a problem or perform a task. It provides a clear and unambiguous method for solving a problem, and it is an essential concept in computer science and programming. Algorithms can be represented using pseudocode, flowcharts, or programming languages.(4) Encryption: Encryption is the process of converting plain text or data into a coded form, known as ciphertext, using an encryption algorithm and a secret key. It ensures the confidentiality and integrity of data by making itunreadable to unauthorized users. Encryption is widely used in data transmission, online banking, and secure communication.(5) Database: A database is an organized collection of structured data stored and accessed electronically. It is designed to efficiently store, retrieve, and manage large volumes of data. Databases are used in various applications, such as e-commerce, customer relationship management (CRM), inventory management, and more.。
计算机专业英语多选题

1.A user interface we said here is __ABC________A.a text-based user interface or GUIB.an interface between a computer and its peripheral deviceC.an interaction between an operating system and a userD.an interaction between an application program and a user2.___A___provides transparent transfer of data between end users, providing reliable data transfer services to the upper layers.A.The Transport LayerB. Session LayerC. Network LayerE.Application Layer E. Presentation Layer3.Many viruses do harmful things such as (ABCD ).A.deleting filesB. slowing your PC downB.simulating typos D. changing random data on your disk4.We can classify programming languages under two types:(AB ) languages and ( )languages.A.high-levelB. low-levelC. advanced-levelD. basic-level5.With an Internet connection you can get some of the basic services available are:___ABCD_______A.E-mailB. TelnetC. FTPD. Usenet news6. A general purpose computer has four main sections: ( ABCE).A.the control unitB. the memoryC. the input and output devicesD. the cpuE. the arithmetic and logic unit (ALU),7.Windows 2000 has the key technologies, they are (ABCD ).A.securityB. active directoryC. flat directoryD. enterprise management8.The register file is___ACD_______A.addressed by much shorter addressesB. physically largeC.physically smallD. one the same chip as the CPU9. A stack protocol can be used for (A ).A.removing the latest element ins( )ertedB. removing the earliest element ins( )ertedC. subroutine callsD. operation of arithmetic expressions10.The end equipment in a communication system includes (ABCD ).A.printersB. computersC. CRTsD. keyboards11.Microsoft Office Professional 2000 include____ABCD______.A.Excel 2000B. PowerPoint 2000C. Word 2000D. Outlook 200012. A general purpose computer has four main sections: ______ABCE______A.the input and output devicesB. the memoryC. the arithmetic and logic unit (ALU),D. the cpuE. the control unit13.The two most common types of scanners are (BC ) and ( )A. hand-held scannersB. flatbed scannersC. auto scannersD. handler scanners14.Some viruses use (CD ) and ( ) techniques to hide their existence.A.quickly spreadB. replace a part of system softwareC. stealthD. polymorphic15.The Windows 2000 product line includes____ABCD______.A.Windows 2000 Datacenter ServerB. Windows 2000 ProfessionalC. Windows 2000 ServerD. Windows 2000 Advanced Server16.Similar to viruses, you can also find malicious code in (ABC ).A.Trojan HorsesB. logic bombsC. wormsD. Microsoft Word Documents17.Viruses all have two phases to their execution, the ( ) and the ( BD).A.create phaseB. attack phaseC. del( )ete phaseD. infection phase18.Active Directory can help you (ACD ).A.get off the limits of down level networksB. deliver complete enterprise security by itselfC. build a complex international networkD. manage every resource with a single logon19.High-level languages are commonly classified as (ACDE ).A.object-orientedB. automaticC. functionalD. logic languagesE. procedure-oriented20.(CD )is a type of executable file .A.TXT fileB. JPG fileC. EXE fileD. COM file21.( ABCD) maybe a certain cause that some viruses infect upon.A.an external event on your PCB. a dayC. a counter within the virusD. a time22.(BC )is a type of executable file .A.TXT fileB. EXE fileC. COM fileD. JPG file23.The web browsers which is normal used, such as(ABCE ).A.FirefoxB. Internet ExplorerC. OpraD. ICQE. Apple Safari24.Newer ideas in computing such as(ABDE ) have radically altered the traditional concepts that once determined program form and functionA.artificial intelligenceB. distributed computingC. software engineeringD. parallel computingE. data mining25.Microsoft Windows currently supports __AC___and _____file systemsA.NTFSB. OCFSC. FATD. ext2E. NILFS26.Modem is ____ACD______.A.a modulator/demodulatorB. a data setC. a demodulatorD. a modulator27.The equipment _AB_____.A.transfers the number of bits in serial formB.manipulates digital information internally in word unitsC.transfers the number of bits in parallelD. manipulates digital information internally in serial form28.Electronic commerce that is conducted between businesses is referred to as business-to-business or DA. C2CB. C2BC. e-commerceD. B2B29.The World Wide Web also subsumes previous Internet information systems such as (AC ).A.GopherB. FtpC. FTPD. Telnet relies on the services of .NET data providers.There are ABCDA.ConnectionB. Data AdapterC. DataReaderD. Command31.The development process in the software life cycle involves four phases: analysis, design, implementation, and ___ACDE_____.A.analysisB. auditC. implementationD. designE. testing32.The end equipment in a communication system includes __ABCD____.A.printersB. CRTsC. computersD. keyboards33.In electronic commerce ,information search and discovery services include (ABCDE ).A.search enginesB. information filtersC. software agentsD. directoriesE. electronic catalogs34.GIS work with two fundamentally different types of geographic models.They are the (BD ).A.geography modelB. vector modelC. mathematic modelD. raster modelE. data model35.The two most common types of scanners are ____AC___and _____A.flatbed scannersB. hand-held scannersC. auto scannersD. handler scanners36.Windows 2000 has the key technologies, they are ( ABCD).A.active directoryB. flat directoryC. enterprise managementD. securityputer software, or just software is a general term used to describe a collection of computer programs, procedures and documentation that perform some tasks on a computer system.The term includes: ABCA.Firmware which is software programmed resident to electrically programmable memorydevices on board mainboards or other types of integrated hardware carriers.B.Application software such as word processors which perform productive tasks for users.C.Middleware which controls and co-ordinates distributed systems.38.Software engineering is related to the disciplines of ___ADE_____A.project managementB. natural languageC. netural networkD. systems engineeringE. computer science39.What make it is difficult to agree on how to count viruses? ABCDA.some viruses can create different versions when they infect other programsB.just a trivial change may create a new virusC.some viruses can use polymorphic techniqueD.new virus arise from an existing virus40. A virus is a program that reproduces its own code by (ABC ).A.ins_erting into the middle of a fileB. simply placing a pointerC. adding to the end of a fileD. replacing another program41.Input devices include: ____ABCD______.A.the keyboardB. microphoneC. touch screenD. the mouse42.Viruses all have two phases to their execution, the ( ) and the ( AD).A.attack phaseB. create phaseC. del_ete phaseD. infection phase43.The equipment (BC ).A.manipulates digital information internally in serial formB.manipulates digital information internally in word unitsC.transfers the number of bits in serial formD.transfers the number of bits in parallel44.Office automation is___CD_______.A.. the computerB. communications technologyC. the application of computerD. used to improve the productivity of people45.The types (classes, structs, enums, and so on) associated with each .NET data provider are located in their own namespaces are: ABCDEA.System.Data.SqlClient. Contains the SQL Server .NET Data Provider types.B.System.Data.Odbc. Contains the ODBC .NET Data Provider types.C.System.Data. Contains provider-independent types such as the DataSet and DataTable.D.System.Data.OracleClient. Contains the Oracle .NET Data ProviderE.System.Data.OleDb. Contains the OLE DB .NET Data Provider types.46.C++ is __ACD________.A.extended from CB. a superset of CC. object-orientedD. procedure-oriented47.Some viruses, with no attack phase, often damage the programs or disks they infect because they (AD ).A.have bugs in themB. show messages on your screenC. steal storageD. contain poor quality code48.Windows 2000 is ( A).A.an inventive technologyB. used for building a scalable networkB.the same as Windows NT D. new lease of Windows49.Some common applications related to electronic commerce are the following:A.TeleconferencingB. Online bankingC. EmailD. Instant messagingE. Enterprise content managementF. NewsgroupsG. Shopping cart software50. A program is a sequence of ( ) that can be executed by a computer.It can either be built into the hardware or exist independently in the form of (BC ).A.hardwareB. softwareC. instructionsD. data51.Electronic payments include ___ABCD______.A.credit card paymentsB. electronic checksC. digital currenciesD. cash payment52.The web browsers which is normal used, such as____ABCD_____.A.OpraB. Internet ExplorerC. FirefoxD. Apple SafariE. ICQputer programs fall into two major classes: __AC____and ____.A.application programsB. application suiteC. operating systemsD. database application54.Database connection ( B) allows an application to reuse an existing connection from a pool instead of repeatedly establishing a new connection with the database.A.pondB. poolingC. linkD. connection55.The development process in the software life cycle involves four phases: analysis, design, implementation, and (ABCE ).A.implementationB. designC. analysisD. auditE. testing56.Hypermedia include ( ABCDEF)A.video clipsB. imagesC. textD. flashE. vidoeF. sounds57.An asleep state is_____ABD_____ed to lessen wear-and tear on the computerB. used for saving energyC. indicated by the indicator light putting outD. a low power standby mode58.Electronic payments include (ABCD ).A.digital currenciesB. electronic checksC. credit card paymentsD. cash payment59.You want to (BCD ) maybe wake up a virus that has residented in memory.A.del( )ete a fileB. access a disketteC. execute a programD. copy a file60.Before you turn the power on with a new computer, you should make sure_____ABCD_____A.the computer system has been set upB. the computer is already out of the boxB.appropriate software have been installed D. appropriate cables are correctly connected61.Security is usually enforced through ___ABE________.A.access controlB. encryptionC. data retrievingD. data storingE. auditingputer programming is the process of ABCD__the source code of computer programs.A. testingB. maintainingC. debuggingD. writing63.Queues that occur everyday life can be seen ( ABCD).A.as automobiles waiting for a traffic lightB. as people waiting for service at a bankC. in certain societies lacking equalityD. in an emergency room of a hospital64.Static graphics include____AB______.A.animatorsB. photographsC. moviesD. pictures66.which is the threat to computer security in the following choices ? ABCDA. Computer CriminalsB. Human ErrorsC. Computer CrimeD. earthquake65.The attributes of the stack are______A____.A.queueB. FIFOC. built into their circuitryD. LIFO66.If a virus simply reproduce and have no cause for an attack phase, but it will still ( ) without your permission. BDA.play musicB. stealing storageC. del( )ete filesD. pilfer CPU cycles67.According to the text,modern digital computers can be divided into four major categories on the basis of cost and performance.They are _______ABDE___________. A.minicomputers B. mainframes C. note book D. workstation E. microcomputers F. lenovo68.The Application layer in TCP/IP Model is correspond to (ABD ) in OSI ModelA.Presentation LayerB. Session LayerC. Transport LayerD. Application LayerE. Network Layer69. A computer system user generally more cares for___ABD_______A.speed of computationB. storage sizeC. physical size of the computerD. efficiency of the computer71.Cache is____ABC______A. slowB. high costC. fastD. relatively small72.We can say a bus is simply_____ABC_____ .A. a wireB. a 16-bit busC. a group of wiresD. a 8-bit bus73.Viruses can delay their attack for (ABCD ).A.yearsB. monthsC. weeksD. days74.In order to increase our computer’s performance we need to____BCD______A.buy a L1 cacheB. have a much larger main memoryC. have a L2 cacheD. buy a L2 cache75.The software that controls the interaction between the input and output hardware is called BIOS,which stands of __A________A.Basic Input Output SystemB. Classic Input Output SystemB.Advanced Input Output System D. Junior Input Output System76.To enhance performance of a computer system we should____ACD______A.improve the pattern of referencing operandB. optimize the simple movement of dataC. optimize the basic sequence control mechanismD. use IF and LOOP instructions as many as possible77.Their company used international lawyers to prosecute a crime ring involving software ____A____in Thailand.A.piracyB. copyingC. duplicationD. cloning78.The software that controls the interaction between the input and output hardware is called BIOS,which stands of (B)A.Advanced Input Output SystemB. Basic Input Output SystemC. Classic Input Output SystemD. Junior Input Output System79.Some viruses use ( AC) and ( ) techniques to hide their existence.A.stealthB. quickly spreadC. polymorphicD. replace a part of system software80.Middleware lies in______ACD____A.the middle of interactions between different application programsB.the top of the layering vertical stackC.the top of an operating systemD.the middle of the layering vertical stack81.Software includes ( ACDE) etcA.video gamesB. all kinds of filesC. programsD. websitesE. mobile application82.The major functional components of an office automation system include: ___ABCD__A.electronic mailB. personal assistance featuresC. information storage and retrievalD. text processing83.The Internet carries various information resources and services, such as (ACDEF ) and the inter-linked hypertext documentsA.online chatB. talkingC. electronic mailD. file transferE. online gamingF. file sharing84. A processor is composed of:____ABCD______.A.an arithmeticB. a control unitC. RegistersD. logic unit85.Functions of the compiler used in RISC are ___ABC_______A.to optimize register usageB.to maximize register usageC.to allocate registers to those variables that will be used the most in a given time periodD.to compile a high level language program86. A digital computer is generally made up of five dstinct elements: a central processing unit,(ABCD).A.a busB. input devicesC. memeory storage devicesD. output devicesE. crt screen87.There are AB (CD)_between the DTEs.A.digital-to-analog converterB. the modemC. communications equipmentD. will be replaced by an upd_ated standard88.What make it is difficult to agree on how to count viruses? ABCDA.just a trivial change may create a new virusB.some viruses can use polymorphic techniqueC.some viruses can create different versions when they infect other programsD.new virus arise from an existing virus89.which aspect have to be considered in the design of a piece of software. ABCDEFGA.Fault-toleranceB. ExtensibilityC. ModularityD. CompatibilityE.MarketabilityF. PackagingG. Maintainability90.Active Directory can help you (ACD ).A.build a complex international networkB. deliver complete enterprise security by itselfC.manage every resource with a single logonD. get off the limits of down level networks91.Early computer solved_____CD_____ problems.A.controlB. engineeringC. mathematicalD. business applications92.The tools which Programming software usually provides include: ABCDEA.debuggersB. text editorsC. linkersD. compilersE. interpreters93.DTE is ( AB).A.data terminal equipmentB.the last piece of equipment that belonged to the subscriber in a data link systemC.satelliteD. Digital T-carrier94.According to the text,modern digital computers can be divided into four major categories on the basis of cost and performance.They are ( BDEF).A.note bookB. microcomputersC. lenovoD. minicomputersE. workstationF. mainframes95.which is the type of electronic commerce in the following choice ACA.B2BB. C2CC. B2C96.The operations of a structured data type might act on (ABCD ).A.a stackB. the values of the data typeC. component elements of the data structureD. a queue97.Types of media include__ACD________.A.textB. animationC. audioD. full-motion video98. A virus is a program that reproduces its own code by (ABC ).A.simply placing a pointerB. adding to the end of a fileC. ins( )erting into the middle of a fileD. replacing another program99.According to the text,the author mentions three of the most commonly used types of printer.They are (BDE ).A.belt printerB. dot-matrix printers;C. array printerD. laser printerE. inkjet printers100.The end equipment in a communication system includes ___ABD_______A.keyboardsB. DCEC. CRTsD. computers101.Software includes _____ACDE________etcA.programsB. all kinds of filesC. video gamesD. websitesE. mobile application102.With .NET, Microsoft is opening up a channel both to ( ) in other programming languages and to ( BC). (developers; components)A.coderB. developersC. componentsD. architecturemon contemporary operating systems include (ABCD ).A.LinuxB. Microsoft WindowsC. SolarisD. Mac OS104.A mechanism for translating Internet hostnames into IP addresses is___BCD_______A.equipped into the general-purpose operating systemB.typically inside of operating system kernelC.as a middleware by author’s definitionD.typically outside of operating system kernel105.RISC is____ABC______ed for many computer manufacturers nowadaysB.guided to be built from studying the execution behavior of high-level language programsC.abbreviation of reduced instruction set computerD.abbreviation of complex instruction set computer106.With .NET, Microsoft is opening up a channel both to _BC_______in other programming languages and to ________. (developers; components)A.coderB. componentsC. developersD. architecture107.The tools which Programming software usually provides include: ABCDEpilersB. interpretersC. text editorsD. linkersE. debuggers108.The following products of software are belong to middleware____BCD______A.OracleB. IBM’s Web Sphere MQC. Java 2 PlatformD. J2EE109.The system manager used by a fast processor can____BCD______A.connect a networkB. monitor processor’s core temperatureC. monitor processor’s supply voltagesD. reset a system110.Queues that occur everyday life can be seen (ABCD ).A.as automobiles waiting for a traffic lightB. as people waiting for service at a bankC. in an emergency room of a hospitalD. in certain societies lacking equality111.C++ include the following pillars: ____ABCD______.A.data hidingB. polymorphismC. encapsulationD. inheritance112.Windows 2000 is____ACD______A.new lease of WindowsB. an inventive technologyC. the same as Windows NTD. used for building a scalable network113.We use paged virtual memory to___ABCD_______A.extend the size of memoryB. reduce latency of the diskC. store large program and data setD. increase bandwidth of the disk114.According to the physical size of computers we can classify the __ABCD____ computers into A. supercomputer B. minicomputer C. microcomputer D. mainframe115.Some common applications related to electronic commerce are the following: ABCDEFGA.EmailB. TeleconferencingC. Instant messagingD. Shopping cart softwareE.NewsgroupsF. Enterprise content managementG. Online banking116.One machine cycle in RISC has _B_________A.two machine instructionsB. one machine instructionC. four machine instructionsD. three machine instructions117.The function of computer hardware is typically divided into three main categories.They are____ADE_____.A.inputB. motherboardC. cpuD. storageE. output118.Active Directory supports ( ABCD).A.granular access controlB. inheritanceC. encapsulationD. delegation of administrative task119.The core of SQL is formed by a command language that allows the (ACDE ) and performing management and administrative functions.A.deletion of dataB. process of dataC. updating of dataD. retrieval of dataE. ins( )ertion of data120.Some commentators say the outcome of the information revolution is likely to be as profound as the shift in (ABCD )A.industrialB. agriculturalC. Service IndustryD. handicraft industry。
计算机英语期末考试试题及答案

计算机英语期末考试试题及答案一、选择题1. 在计算机网络中,IP地址用于标识网络上的的哪个设备?A. 路由器B. 交换机C. 服务器D. 主机答案:D2. 在计算机安全中,以下哪项属于恶意软件?A. 防火墙B. 杀毒软件C. 木马病毒D. 数据备份答案:C3. 在计算机术语中,RAM代表什么?A. 随机读取存储器B. 只读存储器C. 可擦除可编程读取存储器D. 磁盘存储器答案:A4. 在计算机网络中,HTTP协议是用于实现什么功能的?A. 网络连接B. 文件传输C. 数据加密D. 网络浏览答案:D5. 下列哪个不属于常见的文件压缩格式?A. .zipB. .rarC. .isoD. .txt答案:D二、填空题1. 在计算机程序中,循环结构可以用来多次执行特定的代码段,常见的循环结构包括_______和_______。
答案:for、while2. 在计算机图像处理中,________是指将一幅图像分割成若干个连续的小区域,并对每个小区域进行处理。
答案:图像分割三、判断题1. 计算机网络是指将多台计算机通过通信设备连接起来,实现信息共享和资源共享。
答案:正确2. 在计算机程序中,注释是用来向其他程序员解释代码功能的。
答案:正确四、简答题请简述计算机网络的优点和缺点。
优点:1. 资源共享:计算机网络可以实现多台计算机之间的文件共享、打印共享等,提高资源利用率;2. 信息交流:计算机网络可以快速传输信息,实现实时通信,方便人们之间的交流;3. 远程访问:计算机网络可以远程访问其他计算机,方便远程办公和学习。
缺点:1. 安全性问题:计算机网络容易受到黑客攻击和恶意软件感染,存在一定的安全隐患;2. 依赖性:对于依赖网络的应用和服务而言,一旦网络故障,将会导致服务中断,影响工作和生活;3. 隐私问题:在计算机网络中,个人信息和隐私面临泄露的风险,需要加强数据保护和隐私保护措施。
答案仅供参考,具体答案可能根据题目要求有所变化。
高三英语计算机语言单选题40题(含答案)

高三英语计算机语言单选题40题(含答案)1.The computer's CPU is like the ______ of a car.A.engineB.wheelC.seatD.window答案:A。
CPU(中央处理器)就像汽车的发动机一样,是计算机的核心部件。
选项B“wheel”是轮子;选项C“seat”是座位;选项D“window”是窗户,都与CPU 的功能和作用不相符。
2.The monitor is often called the ______ of a computer.A.heartB.eyeC.handD.foot答案:B。
显示器通常被称为计算机的眼睛,因为它像眼睛一样展示信息。
选项A“heart”是心脏;选项C“hand”是手;选项D“foot”是脚,都不符合显示器的特点。
3.The hard drive is like a computer's ______.A.memory bankB.speakerC.keyboardD.mouse答案:A。
硬盘就像计算机的存储库,用于存储数据。
选项B“speaker”是扬声器;选项C“keyboard”是键盘;选项D“mouse”是鼠标,都与存储功能无关。
4.The RAM of a computer is similar to the ______ of a building.A.foundationB.roofC.wallD.door答案:A。
计算机的随机存取存储器((RAM)类似于建筑物的基础,为计算机的运行提供临时的存储空间。
选项B“roof”是屋顶;选项C“wall”是墙;选项D“door”是门,都与RAM 的作用不相符。
5.The graphics card is mainly responsible for ______.A.processing dataB.displaying imagesC.storing filesD.typing words答案:B。
计算机英语试题及答案

计算机英语试题及答案一、选择题(每题2分,共20分)1. What does the term "CPU" stand for?A. Central Processing UnitB. Central Power UnitC. Customer Personal UnitD. Control Power Unit答案:A2. The term "RAM" refers to:A. Random Access MethodB. Random Access MemoryC. Remote Access ModuleD. Real-time Application Module答案:B3. Which of the following is a type of computer virus?A. TrojanB. TractorC. TrackerD. Tracker答案:A4. The acronym "GUI" stands for:A. Graphical User InterfaceB. General User InterfaceC. Graphical Unified InterfaceD. Global User Interface答案:A5. What is the purpose of an "API" in computer programming?A. Application Programming InterfaceB. Advanced Programming InterfaceC. Automated Programming InterfaceD. Advanced Programming Indicator答案:A6. The term "LAN" is short for:A. Local Area NetworkB. Long Area NetworkC. Limited Area NetworkD. Large Area Network答案:A7. Which of the following is a common file extension for a text document?A. .txtB. .jpgC. .exeD. .mp3答案:A8. The process of finding and removing errors in a computer program is called:A. DebuggingB. BuggingC. LoggingD. Tagging答案:A9. What does "FTP" stand for?A. File Transfer ProtocolB. Fast Transfer ProtocolC. Full-Time ProtocolD. Future Technology Protocol答案:A10. The term "URL" stands for:A. Uniform Resource LocatorB. Unique Resource LocatorC. Universal Resource LocatorD. User Resource Locator答案:A二、填空题(每空1分,共10分)11. The basic unit of data in a computer is the _______.答案:bit12. A computer's _______ is the primary component that controls and processes data.答案:CPU13. The _______ is a type of software that protects a computer from malicious software.答案:antivirus14. A _______ is a location on a network where files can be stored and accessed.答案:server15. The process of converting data into a code to protect its confidentiality is known as _______.答案:encryption16. A _______ is a set of data that describes the characteristics of a file or set of files.答案:metadata17. The _______ is the process of recovering data after a system failure.答案:backup18. The term _______ refers to the use of a computer to create visual content, such as images and videos.答案:graphics19. A _______ is a program that controls the way a computer system operates.答案:operating system20. The _______ is the process of connecting two or morenetworks to enable communication between them.答案:networking三、简答题(每题5分,共20分)21. Explain the difference between a "bit" and a "byte".答案:A bit is the smallest unit of data in computing, representing a single binary digit (0 or 1). A byte is a group of eight bits, which is used to represent a character or a string of data.22. What is the role of a "firewall" in a computer system?答案:A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks, such as the Internet.23. Describe the purpose of a "router" in a computer network.答案:A router is a networking device that forwards data packets between computer networks. It uses routing tables to determine the best path for data to travel, allowing multiple devices to communicate with each other across different networks.24. What is "cloud computing" and how does it benefit users?答案:Cloud computing is the delivery of computing services, including storage, processing power, and software, over the internet. It benefits users by providing scalable resources, reducing the need for on-premises infrastructure, and allowing for remote access to applications and data.四、翻译题(每题5分,共20分)25. Translate the following sentence into English: "操作系统是管理计算机硬件和软件资源的程序。
计算机专业英语考试试题及答案

计算机专业英语考试试题及答案一、选择题1. Which of the following is NOT a programming language?A. JavaB. PythonC. HTMLD. CSS2. What does the acronym "SQL" stand for?A. Structured Query LanguageB. Simple Query LanguageC. Script Query LanguageD. Secure Query Language3. Which protocol is commonly used for sending and receiving emails?A. FTPB. HTTPC. SMTPD. TCP4. What does the term "CPU" refer to?A. Central Processing UnitB. Computer Processing UnitC. Central Program UnitD. Computer Program Unit5. Which of the following is NOT a type of network topology?A. StarB. RingC. MeshD. Scroll二、填空题1. HTML stands for Hypertext Markup Language, which is used for ____________.2. The process of converting source code into machine code is called ____________.3. IP address stands for ____________.4. The act of copying files from a remote server to a local computer is known as ____________.5. The programming language developed by Apple Inc. for iOS and macOS is ____________.三、简答题1. What is the difference between a compiler and an interpreter? Provide examples of programming languages that use each of these methods.2. Explain the concept of object-oriented programming (OOP) and provide an example of a programming language that utilizes this paradigm.3. Describe the client-server model and provide an example of a commonly used protocol within this model.四、论述题Discuss the impact of artificial intelligence (AI) on various industries. Provide examples of how AI is being used in fields such as healthcare, finance, and transportation. Analyze the potential benefits and challenges of implementing AI in these industries.答案:一、选择题1. C. HTML2. A. Structured Query Language3. C. SMTP4. A. Central Processing Unit5. D. Scroll二、填空题1. creating and structuring the content of a webpage2. compilation3. Internet Protocol4. downloading5. Swift三、简答题1. A compiler translates the entire source code into machine code before the program is executed. Examples of languages that use compilers are C, C++, and Java. On the other hand, an interpreter translates and executes the source code line by line. Python and Ruby are examples of languages that use interpreters.2. Object-oriented programming (OOP) is a programming paradigm that organizes data and functions into reusable objects. It focuses on the concept of classes and objects, allowing for code reuse and encapsulation. An example of a programming language that uses OOP is Java, where objects are instances of classes and can interact with each other through methods and attributes.3. The client-server model is a distributed computing architecture wherea server provides services or resources to multiple clients. The clients request and receive these resources through the network. An example of a commonly used protocol within this model is the Hypertext Transfer Protocol (HTTP), which is used for communication between web browsers (clients) and web servers.四、论述题Artificial intelligence (AI) has had a significant impact on various industries. In healthcare, AI is being used for diagnoses and treatments, analyzing medical images, and personalized medicine. For example, AI-powered algorithms can help detect diseases like cancer at an early stage, leading to better treatment outcomes. In finance, AI is utilized for fraud detection, algorithmic trading, and customer service. AI algorithms can analyze large amounts of financial data to identify patterns and make accurate predictions. In transportation, AI is being employed for autonomous vehicles, traffic management, and logistics optimization. Self-driving cars, for instance, use AI algorithms to navigate and make decisions on the road.The implementation of AI in these industries brings about many benefits, such as increased efficiency, improved accuracy, and cost savings. AI systems can process and analyze vast amounts of data much faster than humans, leading to faster and more accurate results. However, there are also challenges to consider. Privacy and security concerns arise as AI systems handle sensitive information. There is also the worry of job displacement, as AI automation may replace certain human tasks. Additionally, ethical considerations need to be addressed, such as bias in algorithms and the potential for AI to be used for malicious purposes.Overall, the impact of AI on various industries is undeniable. It has the potential to revolutionize healthcare, finance, transportation, and many other sectors. However, careful implementation and regulation are necessary to ensure its responsible and beneficial use.。
计算机英语考试试题

计算机英语考试试题一、单选题1. What does CPU stand for?A. Central Personal UnitB. Central Processing UnitC. Computer Personal UnitD. Computer Processing Unit2. Which of the following is NOT a type of computer memory?A. RAMB. ROMC. CPUD. Cache3. What is the primary function of an operating system?A. Run applicationsB. Manage computer hardwareC. Connect to the internetD. Play games4. Which programming language is often used for web development?A. JavaB. PythonC. HTMLD. C++5. What does HTML stand for?A. Hyper Text Markup LanguageB. High Tech Modern LanguageC. How To Make LasagnaD. Happy Turtles Move Slowly二、填空题6. The process of finding and correcting errors in a computer program is called ___________.7. A software program that spreads from one computer to another is called a computer ___________.8. A ___________ is a group of interconnected computers that share resources.9. A ___________ is a set of instructions that tells a computer how to perform specific tasks.10. The abbreviation URL stands for ___________.三、简答题11. Explain the difference between hardware and software.12. What is the purpose of an internet browser?13. Describe the role of a firewall in computer security.14. What is cloud computing and how does it work?15. How does a computer virus infect a computer system?四、编程题16. Write a short Python program that takes a user's name as input and prints out a personalized greeting.17. Create an HTML webpage that displays your favorite quote and includes an image.18. Write a C++ program that calculates the area of a circle when the user inputs the radius.五、综合题19. Explain the differences between a desktop computer, laptop, and tablet in terms of size, portability, and functionality.20. Discuss the impact of artificial intelligence on society and the role it plays in various industries.以上为计算机英语考试试题,希望您能认真作答。
计算机英语考试题及答案

计算机英语考试题及答案一、选择题(每题2分,共20分)1. Which of the following is not a type of computer hardware?A. CPUB. RAMC. SoftwareD. Hard Disk答案:C2. What does the acronym "USB" stand for?A. Universal Serial BusB. User System BusC. User Storage BusD. Universal Storage Bus答案:A3. What is the primary function of a router in a computer network?A. To store dataB. To process dataC. To connect multiple devicesD. To print documents答案:C4. Which of the following is a programming language?A. HTMLB. CSSC. JavaScriptD. All of the above答案:D5. What does "RAM" stand for in computer terminology?A. Random Access MethodB. Random Access MemoryC. Remote Access MemoryD. Rapid Access Memory答案:B6. What is the term for a collection of data stored on a computer?A. FileB. FolderC. DatabaseD. Memory答案:A7. Which of the following is a type of computer virus?A. WormB. TrojanC. Both A and BD. None of the above答案:C8. What is the purpose of a firewall in a computer system?A. To prevent unauthorized accessB. To speed up internet connectionsC. To store dataD. To print documents答案:A9. What does "GUI" stand for in the context of computer systems?A. Graphical User InterfaceB. General User InterfaceC. Global User InterfaceD. Graphical Universal Interface答案:A10. What is the term for a small computer program that performs a specific task?A. ApplicationB. SoftwareC. UtilityD. Script答案:D二、填空题(每题2分,共20分)1. The basic unit of data in a computer is called a____________.答案:bit2. A computer's operating system is an example of______________.答案:system software3. The process of converting data into a form that can be understood by a computer is called ______________.答案:encoding4. The term used to describe the speed of a computer's processor is ______________.答案:clock speed5. A computer network that spans a large geographical area is known as a ______________.答案:WAN (Wide Area Network)6. The process of recovering lost data is called______________.答案:data recovery7. A computer program that is designed to disrupt or damage a computer system is known as a ______________.答案:malware8. The primary storage medium for a computer's operating system and most frequently used programs is the______________.答案:hard drive9. The term used to describe the process of transferring data from one computer to another is ______________.答案:data transfer10. A computer that is part of a network and shares its resources with other computers is called a ______________.答案:server三、简答题(每题10分,共40分)1. What are the main components of a computer system?答案:The main components of a computer system include the central processing unit (CPU), memory (RAM), storage devices (hard disk, solid-state drive, etc.), input devices (keyboard, mouse, etc.), output devices (monitor, printer, etc.), andthe operating system.2. Explain the difference between hardware and software in a computer system.答案:Hardware refers to the physical components of a computer, such as the CPU, memory, and storage devices. Software, on the other hand, comprises the programs and instructions that run on the hardware, including theoperating system, applications, and utilities.3. What is the role of a firewall in a computer network?答案:A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks,such as the Internet, to prevent unauthorized access and protect the internal network from potential threats.4. Describe the process of data encryption and its importance in computer security.答案:Data encryption is the process of converting readable data into an unreadable format, called ciphertext, using an algorithm and a key. This process ensures that only authorized parties with the correct key can access and decrypt the data. Encryption is crucial for protecting sensitive information from unauthorized access, ensuring data privacy and security in computer systems and networks.。
计算机专业英语试题

计算机专业英语试题一、选择题(20分,每题2分)1. There are two main sections found in the CPU of a typical personal computer system: the arithmetic-logic section and ( ).A. the control sectionB. the registersC. the data processing sectionD. the bus section2. ( ) is the functional unit that provides the computer with logical and computational capabilities.A. The control unitB. MemoryC. The Arithmetic/Logical UnitD. Register3. One megabyte equals approximately ( ).A. 1000000 bytesB. 1024 bytesC. 65535 bytesD. 10000 bytes.4. When power is removed, information in the semiconductor memory is ( ).A. reliableB. lostC. manipulatedD. remain5. The ( ) are usually located at the top of the keyboard and they are used to give the computer commands.A. function keysB. arrow keysC. numeric keysD. special-purpose keys6. In Excel, formulas and functions can be used to perform statistics or computations of data in ( ).A. electronic spreadsheetsB. sheetsC. filesD. documents7. To facilitate execution of I/O operations, most ( ) have a standard set of control instructions to handle the processing of all input and output instructions.A. operating systemsB. softwareC. system dataD. I/O system8. ( ) may near to relation to any given computer but does assume that a computer is going to be used.A. A high-level programming languageB. Machine languageC. A low-level programming languageD. Assembly language9. The ( ) must retrieve each of the required physical records and construct the logical view of the data requested by the user.A. data processorB. databaseC. DBMSD. MIS10. Computers that are part of a ( ) can share data, messages, graphics, printers, fax machines, modems, CD-ROMs, hard disks, and other data storage equipment.A. systemB. unitC. structureD. network二、词汇题(15分,每个1分)(一)写出下列缩略词的全称DBMS()RAM ()LAN()TCP/IP ( ) SQL ( )(二)将下列短语翻译成英语中央处理器()多道程序设计()缓冲技术()办公自动化()汇编语言()(三)将下列英文短语翻译成汉语Machine Language ()Object-Oriented Language ( ) bus topology ( ) The data link layer ( ) Entity-relationship (ER) modeling ( )三、翻译题(35分,句子每题5分,段落每题10分)1. In a big mainframe computer the processor is called a Central Processing Unit, or CPU, while ina microcomputer, it is usually known as a microprocessor.2. The program, which tells the computers what to do and the data, which provide the information needed to solve the problem, are kept inside the computer in a place called memory.3. A modem is a device that converts data from digital computer signals to analog signals that can be sent over a phone line.4. Microsoft Excel is a spreadsheet program that allows you to organize data, complete calculations, make decisions, graph data, develop professional looking reports, publish organized data on the Web, and access real-time data from Web sites.5. Operating systems can use virtual memory to run processes that require more main memory than is actually available.6. An operating system is a program, which acts as an interface between a user of a computer and the computer hardware. The purpose of an operating system is to provide an environment in which a user may execute programs. The primary goal of an operating system is thus to make the computer system convenient to use. A secondary goal is to use the computer hardware in an efficient manner. An operating system is similar to a government. Its hardware, software, and data provide the basic resource of a computer system. The operating system provides the means for the proper use of these resources in the operation of the computer system. Like government, the operating system performs no useful function by itself. It simply provides an environment within which other programs can do useful work.四、问答题(30分,每题10分)1.What is a Processor? Describe components of the Processor.2. Describe the basic application software: Microsoft Office automation (Word, Excel, PPT).3. Describe the seven layers of the OSI reference model.。
计算机英语试题及答案

计算机英语试题及答案一、选择题(每题2分,共20分)1. Which of the following is not a programming language?A. JavaB. C++C. PythonD. Photoshop2. What does CPU stand for?A. Central Processing UnitB. Central Power UnitC. Central Printing UnitD. Central Programming Unit3. What is the full form of HTML?A. Hyper Text Markup LanguageB. Hyper Text Markup LanguageC. Hyper Text Markup LanguageD. Hyper Text Markup Language4. In computer networking, what does IP stand for?A. Internet ProtocolB. Internet ProgrammingC. Internet ProviderD. Internet Processor5. What is the primary function of a router?A. To print documentsB. To store dataC. To connect multiple networksD. To provide internet access6. Which of the following is a type of database management system?A. MS WordB. MS ExcelC. MS AccessD. MS PowerPoint7. What does the acronym RAM stand for?A. Random Access MemoryB. Rapid Access MemoryC. Remote Access MemoryD. Real Access Memory8. What is the term for a collection of data stored in a computer in a structured format?A. FileB. DocumentC. DatabaseD. Folder9. Which of the following is not a type of computer virus?A. TrojanB. WormC. AntivirusD. Ransomware10. What does the term "bandwidth" refer to in the context ofinternet usage?A. The width of the cableB. The speed of data transferC. The number of usersD. The quality of the connection二、填空题(每题2分,共20分)1. The basic unit of data in computing is called a ________.2. A ________ is a type of software that is designed to prevent, detect, and remove malware.3. The process of converting data into a form that can be easily transmitted or stored is known as ________.4. A ________ is a hardware device that allows a computer to connect to a network.5. The term "cybersecurity" refers to the practice of protecting systems, networks, and programs from ________ and other types of cyber attacks.6. A ________ is a collection of related data and the way it is organized.7. The ________ is a type of computer memory that retains data even when the power is off.8. The process of finding and fixing errors in a program is known as ________.9. A ________ is a type of software that allows users to create and edit documents.10. The ________ is a set of rules that define how data is formatted, transmitted, and received.三、简答题(每题10分,共30分)1. Explain the difference between a server and a client in a network.2. Describe the role of an operating system in a computer system.3. What are the key components of a computer system?四、论述题(每题30分,共30分)1. Discuss the importance of data backup and recovery in a computer system.答案:一、选择题1. D2. A3. A4. A5. C6. C7. A8. C9. C10. B二、填空题1. bit2. Antivirus3. Encoding4. Network Interface Card (NIC)5. unauthorized access6. Database7. Hard disk8. Debugging9. Word processor10. Protocol三、简答题1. In a network, a server is a computer system or device that provides resources or services to other computers, known as clients. The server manages network traffic, centralizes data storage, and provides access to shared resources, while the client is a computer that requests and uses these resourcesor services.2. An operating system is the software that manages computer hardware, software resources, and provides services for computer programs. It acts as an intermediary between theuser and the computer hardware, allowing users to interactwith the computer without needing detailed knowledge of the hardware.3. The key components of a computer system include thecentral processing unit (CPU), memory (RAM), storage devices (hard disk, SSD), input devices (keyboard, mouse), output devices (monitor, printer), and peripheral devices (scanner, webcam).四、论述题1. Data backup and recovery are critical in a computer system because they ensure that data is preserved in case ofhardware failure, data loss, or cyber attacks. Regularbackups allow for the restoration of data to a previous state, minimizing downtime and potential loss of information. This process is essential for maintaining business continuity and protecting against data loss.。
计算机笔试英语试题及答案

计算机笔试英语试题及答案一、选择题1. I usually take a _______ to work, but today I decided to walk.A. busB. carC. taxiD. bike答案: D2. It is important to _______ regular backups of your files to prevent data loss.A. takeB. makeC. doD. perform答案: B3. The new software update _______ several bug fixes and performance improvements.A. containsB. includesC. comprisesD. consists答案: A4. Could you please _______ the volume on the television? It's too loud.A. turn upB. turn downC. turn onD. turn off答案: B5. The mouse and the keyboard are both _______ input devices.A. primaryB. secondaryC. externalD. internal答案: A二、填空题1. The acronym "HTML" stands for HyperText Markup _______.答案: Language2. JavaScript is a widely-used _______-side scripting language.答案: client3. The most commonly used programming language for developing Android apps is _______.答案: Java4. The process of converting source code into machine code is called_______.答案: compilation5. The _______ command in Unix-like operating systems is used to display the contents of a file.答案: cat三、简答题1. What is the purpose of an operating system?答案: The purpose of an operating system is to manage the hardware and software resources of a computer system. It provides a platform for other software applications to run on, handles input and output, manages memory, and performs various system tasks.2. What is the difference between HTTP and HTTPS?答案: The main difference between HTTP and HTTPS is that HTTPS encrypts the data transmitted between a web server and a web browser, while HTTP does not. This encryption ensures that the data cannot be intercepted or tampered with by unauthorized individuals. HTTPS iscommonly used for secure transactions, such as online banking and e-commerce websites.3. What is a database and how is it used in computer programming?答案: A database is a structured collection of data that is organized and stored in a computer system. It allows for efficient data storage, retrieval,and manipulation. In computer programming, databases are commonly usedto store and manage large amounts of structured data. They provide mechanisms for querying the data, updating it, and ensuring data integrity. Popular database management systems include MySQL, Oracle, and Microsoft SQL Server.四、编程题请编写一个简单的Python程序,实现以下功能:用户输入一个整数,程序输出该整数的平方值。
计算机专业英语试题及答案

计算机专业英语试题及答案1. 选择题1. Which of the following is not a programming language?a) Javab) HTMLc) Pythond) CSS答案: b) HTML2. Which protocol is used for sending and receiving email?a) HTTPSb) FTPc) SMTPd) DNS答案: c) SMTP3. What does the acronym CPU stand for?a) Central Processing Unitb) Computer Processing Unitc) Control Processing Unitd) Central Power Unit答案: a) Central Processing Unit4. Which programming language is commonly used for web development?a) C++b) Javac) JavaScriptd) Swift答案: c) JavaScript5. What does HTML stand for?a) Hyperlinks and Text Markup Languageb) Hyper Text Markup Languagec) Home Tool Markup Languaged) Hyper Text Modeling Language答案: b) Hyper Text Markup Language2. 填空题1. The process of converting high-level programming code into machine code is called ___________.答案: compilation2. HTTP stands for ___________ Transfer Protocol.答案: Hyper Text3. The process of testing software by executing it is called ___________.答案: debugging4. Java is an object-_____________ programming language.答案: oriented5. DNS stands for Domain Name ___________.答案: System3. 简答题1. What is the difference between TCP and UDP?答案: TCP (Transmission Control Protocol) is a connection-oriented protocol, which means it establishes a connection between the sender and receiver before transferring data. It ensures that all packets are received in the correct order and provides error checking. UDP (User Datagram Protocol), on the other hand, is a connectionless protocol that does not establish a direct connection before transmitting data. It does not guarantee packet delivery or order but is faster and more efficient for time-sensitive applications.2. What is the purpose of an operating system?答案: An operating system (OS) is a software that manages computer hardware and software resources and provides common services forcomputer programs. Its primary purpose is to enable the user to interact with the computer and provide a platform for running applications. It manages memory, file systems, input/output devices, and multitasking. The OS also handles system security and resource allocation to ensure optimal performance.4. 解答题请参考下文并给出自己的解答。
大学生《计算机专业英语》考试题目

《计算机专业英语》一、Choice (选择)(15 题,每题1 分,共15 分)Choose the best answer for each blank.(从每题四个选项中,选出最合适的一项)1) As an operating system repeatedly allocates and frees storage space, many physically separated unused areas appear. This phenomenon is called ______.A. fragmentationB. compactionC. swappingD. paging2) We can use the word processor to _________ your documents.A. editB. computeC. translateD. unload3) _____________ infected computer may lose its data.A. FileB. Data baseC. VirusD. Program4) One use of networks is to let several computers share ____ such as file system, printers, and tape drives.A. CPUB. memoryC. resourcesD. data5) A firewall is a ____ system designed to ___ an organization’s network against threats.A. operating, preventB. programming, developC. security, protectD. service, exploit6) The ____ has several major components, including the system kernel, a memory management system, the file system manager, device drivers, and the system libraries.A. applicationB. information systemC. networkD. operating system7) ____ is the address of a variable or a variable in which the address of anothervariable is stored.A. DirectorB. PointerC. ArrayD. Record8) C++ is used with proper ____ design techniques.A. object-orientedB. object-basedC. face to objectD. face to target9) A data ( ) is a file that contains metadata-that is, data about data.A. structureB. tableC. baseD. dictionary10) A network software consists of ( ), or rules by which processes can communicate.A. protocolsB. programsC. devicesD. computers11) The firewall device is a ( ) system for connecting a computer network toother computer network.A. hardwareB. softwareC. securityD. I/O12) We can use the word processor to _________ your documents.A. editB. computeC. translateD. unload13) _________ processing offers many ways to edit text and establish document formats. You can easily insert, delete, change, move and copy words or blocks of text.A. DataB. DatabaseC. WordD. File14) A ________ copies a photograph, drawing or page of text into the computer. A.scanner B.printer C.display D.Keyboard15) _________ is the sending and receiving of the message by computer. It is a fast, low-cost way of communicating worldwide.A.LAN B.Post office C.E-Mail D.Interface二、Cloze (完形填空)(4 篇篇20 题,每题1.5 分,共30 分)Choose the best answer for each blank.(从每题选项中,选出最合适的一项)Passage 1Have you ever wondered how information processed by the system unit is1) into a form that you can use? That is the role of output devices. While inputdevices convert what we understand into what the system unit can process, output devicesconvert what the system unit has processed into a form that we can understand. Output devices 2) machine language into letters, numbers, sounds, and images that peoplecan understand.Competent end users need to know about the most commonly used input devices, including keyboards, mice, 3) , digital cameras, digitizing tablets, voice recognition,and MIDI devices. Additionally, they need to know about the most commonly used output devices. And end users need to be aware of 4) input and output devices such as fax machines, multifunctional devices, 5) telephones, and terminals.1) A. converted B. convinced2) A. transact B. translate3) A. scanners B. scan4) A. combination B. communication5) A. Intranet B. InternetPassage 2ABC is an interactive programming language and environment for personal computing, originally 6) ____ as a good replacement for BASIC. It was designed by 7)____ a task analysis of the programming task.ABC is easy to learn (an hour or so for someone who has already programmed), and yet easy to use. Originally intended as a language for 8) ______, it has evolved into a powerful tool for beginners and experts alike.Some features of the language:op-down programmingSome features of the environment:logging outediting, or entering input to a program6) A. intending B. intended7) A. first does B. first doing8) A. beginners B. beginning9) A. easily be combined B. easy be combined10) A. is shown to B. is showing toPassage 3Bulletin Board Systems (BBS)Bulletin Board Systems are a 11)______ telecommunications services provided bythe internet, public information services, and 12)_______ of business firms, organization, and end user groups. An electronic bulletin board system allows you to post public or private messages that other end 13)______ can read by accessing the BBS with their computers. Establishing a small BBS for a business is not that difficult. Minimum requirements are a microcomputer with a hard disk drive, custom or packaged BBS 14)_______, modem and a telephone line. Bulletin Board System serves as a central location to post and pick up messages or upload and download data files or programs 24 hours a day. A BBS helps end users ask questions, get advice, locate and share information, and get 15)_______ touch with other end users.11) A. popular B. unpopular12) A. thousand B. thousands13) A. use B. users14) A. software B. hardware15) A. on B. inPassage 4A: displaying B: messages C: received D: network E: usersElectronic MailMillions of end 16)________ now depend on electronic mail (e-mail) to send andreceive electronic 17)________. You can send e-mail to anyone on your 18)________ for storage in his/her electronic mail boxes or magnetic disk drives. Whenever they are ready, they can read their electronic mail by 19)________ it on the video screens at their workstations. So, with only a few minutes of effort (and a microseconds of transmission),a message to one or many individuals can be composed, sent, and 20)_______.三、Term Translation (术语翻译)(10 题,每题1.5 分,共15 分)Write out their English abbreviations of the following terms and then translate them into Chinese.(写出下列专业术语的英文简称,并将其翻译成汉语)1) Personal Digital Assistant2) Wireless-Fidelity3)Digital Video Disc4)Joint Photographic Experts Group5)Graphical User Interface6)Professional Hypertext Preprocessor7)Simulation Language8)Object-oriented Programming9)Uninterruptable Power Supply10)Universal Serial Bus四、Short Answer (简答)(2 题,每题4 分,共8 分)Answer the following questions in English.(用英文回答下列问题)1)Please write down the components of hardware.2) Please write down the classification(分类)of operating system according to the application area(应用领域).五、Sentence Translation (句子翻译)(8 题,每题4 分,共32 分)Translate the following English sentences into Chinese.(将下列英文句子翻译成汉语)1) This input is digitized and converted to standard text that can be further processed by programs such as a word processor.2)The most common input devices are the keyboard and the mouse.3) The network operating system is designed to control the computers that are linked together via a network.4) The BIOS (Basic Input Output System)is responsible for waking up the computer when you turn it off.5)A primary purpose of programming languages is to enable programmers to express their intent for a computation more easily than they could with a lower-level language or machine code.6)During the last few decades, a large number of computer languages have been introduced.7) The entire office automation system comprises five sub-systems.8) Image Processing System allows end users to electronically capture, store, process, and retrieve images of documents.。
英文版计算机试题及答案

英文版计算机试题及答案一、选择题(每题2分,共20分)1. Which of the following is not a function of an operating system?A. Process managementB. Memory managementC. Data storageD. File management2. In a computer network, what does the term "bandwidth" refer to?A. The width of the network cableB. The maximum rate of data transferC. The number of users connectedD. The speed of the network processor3. What is the primary purpose of a firewall?A. To prevent unauthorized access to a networkB. To encrypt dataC. To manage network trafficD. To store user passwords4. Which of the following is a type of software used for creating and editing documents?A. Spreadsheet softwareB. Database softwareC. Word processing softwareD. Graphics software5. What is the term used to describe the process of converting data from one format to another?A. Data migrationB. Data transformationC. Data conversionD. Data translation6. What does the acronym "CPU" stand for in computing?A. Central Processing UnitB. Central Processing UnitC. Computer Processing UnitD. Computing Processing Unit7. What is the function of a router in a network?A. To connect multiple networksB. To store dataC. To provide power to devicesD. To print documents8. What is the process of finding and fixing errors in software called?A. DebuggingB. PatchingC. UpdatingD. Patching9. Which of the following is a type of computer virus that replicates itself by attaching to other programs?A. TrojanB. WormC. RansomwareD. Spyware10. What is the term for the graphical representation of data on a computer screen?A. Data visualizationB. Data representationC. Data graphingD. Data mapping二、填空题(每题2分,共20分)1. The _________ is the primary memory used by a computer to store data and instructions that are currently being processed.2. A _________ is a type of software that allows users to create and edit images.3. The process of converting analog signals to digital signals is known as _________.4. A _________ is a collection of data stored in a structured format.5. The _________ is a hardware component that connects a computer to a network.6. In computer programming, a _________ is a sequence of statements that perform a specific task.7. The _________ is a type of malware that hides its presence and waits for a trigger to activate.8. A _________ is a type of software that is designed to protect a computer from unauthorized access.9. The _________ is the process of organizing and managing data in a database.10. A _________ is a type of software that allows users tocreate and edit spreadsheets.三、简答题(每题10分,共30分)1. Describe the role of a server in a computer network.2. Explain the difference between a compiler and an interpreter in programming.3. Discuss the importance of data backup and recovery in a computing environment.四、编程题(每题15分,共30分)1. Write a simple program in Python that calculates the factorial of a given number.2. Create a function in Java that takes an array of integers and returns the largest number in the array.答案:一、选择题1. C2. B3. A4. C5. C6. A7. A8. A9. B10. A二、填空题1. RAM (Random Access Memory)2. Graphics software3. Analog-to-digital conversion4. Database5. Network interface card (NIC)6. Function or procedure7. Trojan8. Antivirus software9. Database management10. Spreadsheet software三、简答题1. A server in a computer network is a powerful computer or system that manages network resources, including hardware and software, and provides services to other computers on the network, such as file storage, web hosting, and print services.2. A compiler is a program that translates source codewritten in a programming language into machine code that a computer can execute. An interpreter, on the other hand, reads and executes the source code line by line without the need for a separate compilation step.3. Data backup and recovery are crucial in a computing environment to prevent data loss due to hardware failure, software bugs, or malicious attacks. Regular backups ensure that data can be restored to a previous state in case of corruption or deletion.四、编程题1. Python Program for Factorial Calculation:```pythondef factorial(n):if n == 0:return 1 else:。
大一计算机英语试题及答案

大一计算机英语试题及答案一、单选题1. What does RAM stand for?A. Random Access MemoryB. Read-only MemoryC. Central Processing UnitD. Graphics Processing Unit正确答案:A2. Which of the following is NOT an operating system?A. WindowsB. LinuxC. macOSD. Microsoft Office正确答案:D3. What is the primary purpose of a compiler?A. To execute program instructionsB. To translate source code into machine codeC. To store large amounts of dataD. To control input and output devices正确答案:B4. What is the function of a firewall?A. To protect against hardware failureB. To block unauthorized access to a networkC. To enhance the performance of a computerD. To connect multiple devices together正确答案:B5. Which programming language is used for web development?A. JavaB. PythonC. HTMLD. C++正确答案:C二、填空题1. HTML stands for "Hypertext Markup Language".2. The binary number system consists of only two digits, 0 and 1.3. TCP/IP stands for "Transmission Control Protocol/Internet Protocol".4. The main function of an operating system is to manage computer hardware and software resources.5. SQL stands for "Structured Query Language".三、简答题1. What is the difference between software and hardware?答:Software refers to the programs, applications, and data that are stored on a computer, while hardware refers to the physical components of a computer system, such as the processor, memory, and storage devices. Software is intangible and can be easily modified or updated, whereas hardware is tangible and cannot be easily changed.2. What is the purpose of an operating system?答:The purpose of an operating system is to manage computer hardware and software resources, provide a user interface for interaction with the computer, and coordinate the execution of programs. It handles tasks such as memory management, process management, file system management, and device management.3. What is the difference between a compiler and an interpreter?答:A compiler translates the entire program into machine code before execution, generating an executable file. An interpreter, on the other hand, translates and executes the program line-by-line, without generating an executable file. Interpreted languages are typically slower than compiled languages, but allow for easier debugging and modification of code.四、阅读理解Read the following passage and answer the questions below.Computer viruses are malicious software programs that can replicate themselves and infect a computer system. They are often spread through email attachments, downloads from untrusted sources, or infected USB drives. Once inside a system, viruses can cause a range of harmful effects, from disrupting normal system operations to stealing personal information.1. How are computer viruses typically spread?答:Computer viruses are typically spread through email attachments, downloads from untrusted sources, or infected USB drives.2. What can viruses do once they infect a computer?答:Viruses can cause a range of harmful effects, including disrupting normal system operations and stealing personal information.五、写作题Write a short paragraph (approximately 150 words) about the importance of cybersecurity.In today's digital age, cybersecurity plays a crucial role in protecting our sensitive information and ensuring the smooth operation of computer systems. With the increasing reliance on technology for various aspects of our daily lives, including communication, banking, and healthcare, the risk of cyber threats has never been greater. Cyberattacks can result in financial loss, identity theft, and even the compromise of national security. Therefore,it is essential for individuals, organizations, and governments to prioritize cybersecurity measures. This includes implementing strong passwords, regularly updating software, and educating users about potential threats. Additionally, cybersecurity professionals play a vital role in detecting and preventing cyberattacks, as well as responding to incidents effectively. By ensuring the confidentiality, integrity, and availability of information, cybersecurity helps maintain trust in our digital world.。
计算机专业英语
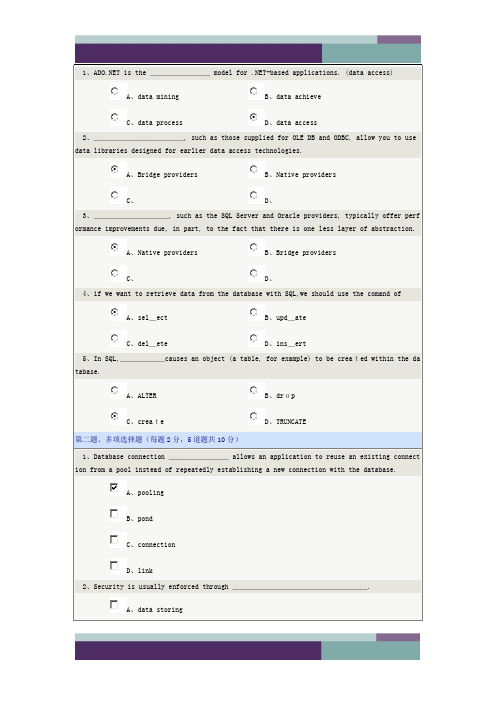
1、 is the ________ model for .NET-based applications. (data access)A、data miningB、data achieveC、data processD、data access2、____________, such as those supplied for OLE DB and ODBC, allow you to use data libraries designed for earlier data access technologies.A、Bridge providersB、Native providersC、D、3、__________, such as the SQL Server and Oracle providers, typically offer perf ormance improvements due, in part, to the fact that there is one less layer of abstraction.A、Native providersB、Bridge providersC、D、4、if we want to retrieve data from the database with SQL,we should use the comand ofA、sel_ectB、upd_ateC、del_eteD、ins_ert5、In SQL,______causes an object (a table, for example) to be created within the da tabase.A、ALTERB、dropC、createD、TRUNCATE第二题、多项选择题(每题2分,5道题共10分)1、Database connection ________ allows an application to reuse an existing connect ion from a pool instead of repeatedly establishing a new connection with the database.A、poolingB、pondC、connectionD、link2、Security is usually enforced through __________________.A、data storingB、auditingC、encryptionD、access controlE、data retrieving3、 relies on the services of .NET data providers.There areA、ConnectionB、CommandC、DataReaderD、Data Adapter4、The core of SQL is formed by a command language that allows the ________ and pe rforming management and administrative functions.A、retrieval of dataB、ins_ertion of dataC、updating of dataD、deletion of dataE、process of data5、The types (classes, structs, enums, and so on) associated with each .NET data provider are located in their own namespaces are:A、System.Data.SqlClient. Contains the SQL Server .NET Data Providertypes.B、System.Data.OracleClient. Contains the Oracle .NET Data ProviderC、System.Data.OleDb. Contains the OLE DB .NET Data Provider types.D、System.Data.Odbc. Contains the ODBC .NET Data Provider types.E、System.Data. Contains provider-independent types such as the DataSet and DataTable.正确错误A computer database relies upon DBMS to organize the storage of data.正确错误All of these databases can not take advantage of indexing to increase their speed.正确错误Database security denotes the system, processes, and procedures that protect a database正确错误Enforcing security is one of the major tasks of the DBA.正确A BC DA(n) ________ is a connecting device that only regenerates the signal.A BC DWhereas a repeater operates only in the physical layer of the OSI model, a bridge operaA BC DA(n) ________ is usually a computer installed with the necessary software and aA BC DThe distinction between the two terms gateway andy are now used interchangeably.A、hubB、routerC、swtichD、gateway第二题、多项选择题(每题2分,5道题共10分)1、The equipment ______.A、manipulates digital information internally in serial formB、manipulates digital information internally in word unitsC、transfers the number of bits in parallelD、transfers the number of bits in serial form2、DTE is ______.A、Digital T-carrierB、data terminal equipmentC、satelliteD、the last piece of equipment that belonged to the subscriber in a data link system3、There are AB_ between the DTEs.A、the modemB、communications equipmentC、digital-to-analog converterD、will be replaced by an upd_ated standard4、__________ provides transparent transfer of data between end users, providing reliable data transfer services to the upper layers.A、The Transport LayerB、Session LayerC、Presentation Layer正确错误TCP means it is on the network layer and IP means it is on the transport layer separate正确错误The four topologies in common use are star, router, ring and hub.正确错误Three techniques have been adopted for use of the medium access control in the LANs.正确错误Control token is the only way of controlling access to a shared transmission medium.正确错误A BC DTo access a page on the WWW, one needs a ________A、routerB、codeC、passwordD、browser3、_____ is an architectural framework.A、httpB、wwwC、ftpD、dns4、_____ is built around hypertext and hypermedia.A、DNSB、HTTPC、The WebD、FTP5、__________is a network protocol used to transfer data from one computer to an other through a network such as the Internet.A、SMTPB、HttpC、DNSD、FTP第二题、多项选择题(每题2分,5道题共10分)1、Hypermedia include ( )A、soundsB、video clipsC、textD、flashE、vidoeF、images2、The World Wide Web also subsumes previous Internet information systems such as ( ).A、GopherB、TelnetC、FTPD、Ftp3、The Internet carries various information resources and services, such as ______________________________ and the inter-linked hypertext documentsA、electronic mailB、online chatC、file transferD、file sharingE、online gamingF、talking4、The World Wide Web is a huge set of ________, linked by hyperlinks and URLs.A、interlinked documentsB、imagesC、flashD、all kinds of dataE、pages5、The web browsers which is normal used, such as________________.A、Internet ExplorerB、FirefoxC、Apple SafariD、OpraE、ICQ第三题、判断题(每题1分,5道题共5分)1、Because the Internet is made up of many diverse computers, so together they work like o ne world-wide computer system.正确错误The World Wide Web ties the information together into a big collection of interactive m正确错误The surfing is you can sel ect paths to browse online resource.正确错误If a person read a hypermedia document about mobile phones, then he might sel正确错误Previously the Web provides a wealth of additional capabilities.正确错误A BC D According to Intel,there are _____________A、OneB、TwoC、ThreeD、Four3、A companyˊs ability to deploy and support customer-oriented ___________ sys tems will be of vital importance to its prosperity.A、e-LearningB、e-BankingC、e-BusinessD、e-Shopping4、When most people think of opening a Web business,the first thing that springs to mind i s selling products or ____________online.A、qualityB、servicesC、consciousnessD、5、A Web site is often more effective as a(n) _______ tool than a selling tool.A、PoliticB、TechnicalC、MarketingD、Electronical第二题、多项选择题(每题2分,5道题共10分)1、which is the type of electronic commerce in the following choiceA、B2BB、B2CC、C2C2、Electronic commerce that is conducted between businesses is referred to as business-to-business orA、C2CB、C2BC、B2BD、e-commerce3、Electronic commerce that is conducted between businesses and consumers, on the other ha nd, is referred to asA、B2CB、C2CC、B2BD、e-commerce4、Electronic commerce may be defined as the entire set of processes that suport _____________activities on a(n) ________ and involve information analysis.A、commercial,networkB、society,humanC、personal,society5、Electronic payments include ___________________.A、digital currenciesB、credit card paymentsC、electronic checksD、cash payment第三题、判断题(每题1分,5道题共5分)1、Online shopping is the process consumers go through to purchase products or services ov er the Internet.正确错误2、In general, shopping has always catered to middle class and upper class women.正确错误3、Electronic money is also called digital cash or electronic token正确错误4、Online content providers make money in two ways:advertisements and selling.正确错误5、Designers of online shops should consider the effects of information load.正确错误A BC DAnti-Virus protects your computer from viruses byA BC DA virus is aA BC DIn 2000, the number of viruses topped ( ).A BC DThe Whale will crea e ( ) different versions of itself when it infects files.A BC DC、logic bombsD、Microsoft Word Documents3、( ) maybe a certain cause that some viruses infect upon.A、a dayB、a timeC、an external event on your PCD、a counter within the virus4、If a virus simply reproduce and have no cause for an attack phase, but it will still ( ) without your permission.A、stealing storageB、pilfer CPU cyclesC、del_ete filesD、play music5、which is the threat to computer security in the following choices ?A、Computer CriminalsB、Computer CrimeC、earthquakeD、Human Errors第三题、判断题(每题1分,5道题共5分)1、Computer security is a branch of technology known as information security as applied to computers.正确错误2、Michelangelo is a file sector.正确错误3、Computer virus is remote from us.正确错误Computer virus may affect the your phisical health .正确错误The author thinks that understanding how an attacker approaches your computer system ca 正确错误When you are old and grey and full of sleep,And nodding by the fire, take down this book,And slowly read, and dream of the soft lookYour eyes had once, and of their shadows deep;How many loved your moments of glad grace,And loved your beauty with love false or true,But one man loved the pilgrim soul in you,And loved the sorrows of your changing face;And bending down beside the glowing bars,Murmur, a little sadly, how love fledAnd paced upon the mountains overheadAnd hid his face amid a crowd of stars.The furthest distance in the worldIs not between life and deathBut when I stand in front of youYet you don't know thatI love you.The furthest distance in the worldIs not when I stand in front of youYet you can't see my loveBut when undoubtedly knowing the love from both Yet cannot be together.The furthest distance in the worldIs not being apart while being in loveBut when I plainly cannot resist the yearningYet pretending you have never been in my heart. The furthest distance in the worldIs not struggling against the tidesBut using one's indifferent heartTo dig an uncrossable riverFor the one who loves you.倚窗远眺,目光目光尽处必有一座山,那影影绰绰的黛绿色的影,是春天的颜色。
计算机英语选择题

计算机英语选择题(1) A large main memory can be used forstoring a,b,c .a. datab. operating systemc. applicationsd. interface(2) Early computer solved c,d problems.a. controlb. business applicationsc. engineeringd. mathematical(3) The system manager used by a fast processor cana,b,c .a. reset a systemb. monitor processor’s core temperaturec. monito r processor’s supply voltagesd. connect a network(4) We can say a bus is simply a,c,d .a. a group of wiresb. a wirec. a 8-bit busd. a 16-bit bus(5) A computer system user generally more cares for b,c,d .a. physical size of the computerb. storage sizec. speed of computationd. efficiency of the computer(6) According to the physical size of computers we canclassify thecomputers into a,b,c,d .a. microcomputerb. minicomputerc. mainframed. supercomputer(7) The basic hardware components of any computerinclude a,b,c,d .a. CPUb. main memoryc. input devicesd. output devices(8) The following devices are belong to the mass storages a,b,d .a. DVDb. CD-ROMc. moused. disk(1) Cache is a,c,d .a. fastb. slowc. relatively smalld. high cost(2) Information stored in semiconductor RAMis b,c .a. permanentb. nonpermanentc. volatiled. non volatile(3) We use paged virtual memory to a,b,c,d.a. extend the size of memoryb. increase bandwidth of the diskc. reduce latency of the diskd. store large program and data set(4)We read data on the disk by a,d .(5) The three desiderata of memory system are b,c .a.independentb. exclusivec.closely approximated todayd. Less approximated tomorrow(6) The processor performance would be high as we reference instructions and data from b,d.a. hard diskb. cachec. floppy diskd. memory(7) Page frame is used in a .a. real memoryb. virtual memoryc. diskd. cache(8) In order to increase our computer’s performance we need to a,b,c ,a. have a L2 cacheb. buy a L2 cachec. have a much larger main memoryd. buy a L1 cache(1) RISC is b,c,d .a. abbreviation of complex instruction set computerb. abbreviation of reduced instruction set computerc. guided to be built from studying the execution behavior of high-level language programsd. used for many computer manufacturers nowadays(2) To enhance performance of a computer system we should a,b,d .a. improve the pattern of referencing operandb. optimize the simple movement of datac. use IF and LOOP instructions as many as possibled. optimize the basic sequence control mechanism(5) Register storage has b,d .a. a large capacityb. a small capacityc. the slower speedd. the faster speed(6) Instruction format in RISC has a,c,d .a. one kindb. many kindsc. a few kindsd. one or a few kinds(7) CISC machine instructions compared with RISC machine are a,d .a. more complicatedb. more simplec. more faster to be executedd. more slower to be executed(8) Functions of the compiler used in RISCare b,c,d .a. to compile a high level language programb. to optimize register usagec. to maximize register usaged. to allocate registers to those variables that will beused the most in a given time period(9) One machine cycle in RISC has c .a. two machine instructionsb. three machineinstructionsc. one machine instructiond. four machineinstructions(10) The register file is a,c,d .a. physically smallb. physically largec. one the same chip as the CPUd. addressed by much shorter addresses Operating systems and middleware b,c,da. have less in commonb. both can support other softwarec. have much in commond. both can support application programs2. An operating system provides the services in its API by a,c,da. using the features of the hardwareb. offering database accessibilityc. using disk drive’s abilityd. offering fixed-length blocks of data4. Middleware lies in b,c,da. the top of the layering vertical stackb. the middle of the layering vertical stackc. the top of an operating systemd. the middle of interactions between different application programs5. The following products of software are belong to middleware a,b,ca. IBM’s Web Sphere MQb. Java 2 Platformc. J2EEd. Oracle6. A mechanism for translating Internet hostnames into IP addresses is a,c,da. typically outside of operating system kernelb. typically inside of operating system kernelc. equipped into the general-purpose operating systemd. as a middleware by author’s definition7. With middleware we can b,c,da. run programs on a centralized computer system onlyb. keep computations largely isolated from undesirable interactionsc. run programs on different computer systemd. allow computations to communicate with one another8. Middleware has mechanisms to support controlled interaction through a,b,c,da. communicationb. namingc. persistent storaged. coordination1. Before you turn the power on with a new computer, you should make sure a,b,c,d.a. the computer is already out of the boxb. appropriate cables are correctly connectedc. the computer system has been set upd. appropriate software have been installed2. An asleep state is a,c,d .a. a low power standby modeb. indicated by the indicator light putting outc. used for saving energyd. used to lessen wear-and tear on the computer4. During the boot procedure we can see a,b,conthe screen.a. amount of memoryb. the number of attached devicesc. the operating system being usedd. beeps and whirling noises5. A user interface we said here is a,b,d .a. an interaction between an operating system anda userb. an interaction between an application program and a userc. an interface between a computer and its peripheral deviced. a text-based user interface or GUI6. Today Microsoft’s ope rating system Windows hasa variety of versions, they are a,b,c,d.a. Windows 2007b. Windows 2003c. Windows XPd. Windows vista7. The Windows desktop contains common elements, such as .a. desktop iconsb. taskbarc. Start buttond. task button9. With the window of the GUI we can use.a. menusb. dialog boxesc. iconsd. documents10. Main menu category in some Microsoft programs .a. is a menu bar at the top of many windowsb. can display a pull-down menusc. can’t display a drop-down menusd. can display personalized menus1. Upgrading a computer system means .a. buying new hardwareb. buying new softwarec. extending the life of your current systemd. keeping your computer in present situation2. To formulate an upgrade strategy, you should consider .a. the PC adheres to a well-supported standardb. you anticipate all your future needsc. there is room for additional expansion cardsd. there is room for memory3. Some common hardware upgrades nclude.a. adding more RAMb. installingADSLc. adding an image scannerd. installing a color printer4. The ways to seriously upgrade an Intel 80486- based PC include .a. installing the most modern softwareb. replacing the motherboardc. replacing other items inside the system unitd. just purchasing a new PC5. Relationship between version and release in a software is .a. version has major numberb. release has minor numberc. version typically increase its number in increments of 1d. release typically increase its number in increments of 0.1 or 0.016. Compatible mode of the software products can be categorized into .a. upwardb. downwardc. crossd. aboveall1. A Wide Area Network can..a. cover a wide geographical areab. link two or more LANsc. link two LANs onlyd. be created by individual users2. According to the flow of information on a transmission facility we can categorize WANinto network.a. circuit switchedb. packet switchedc. local aread. Lease d. line3. In packet switched networks data send in..a. byteb. piecesc. framed. packet4. The most important items contained in a packet should be.a. data to be transmittedb. header of the packetc. tail of the packetd. date5. The popular approaches we used in the packet switched network are .a. circuit switchingb. datagramc. virtual circuitd. real circuit6. In the datagram mode when datagrams arrive at their destination, the datagrams .a. may be out of orderb. must be in orderc. should be reorderedd. may lose7. In the virtual circuit mode all packets sent by a user at a time belong to .a. a messageb. a sessionc. different messagesd. different sessions8. Main characteristics of the leased line networks are .a. the line is private for the userb. the user has himself inter-exchangec. very short response timed. the user computer is always physically connected to the line8. Main characteristics of the leased line networks are .a. the line is private for the userb. the user has himself inter-exchangec. very short response timed. the user computer is always physically connected to the line9. A typical frame relay network has .a. seven componentsb. five componentsc. six componentsd. five major physical components and one "virtual" components10. Router has the following name .a. ARPANETb. IMP (Interface Message Processor)c. gatewayd. IS (Intermediate System)11. In Fig.4-6 a router creates a logical path between networks, these networksinclude .a. FDDIb. Token Busc. Token Ringd. Ethernet12. Encapsulation is used here for data delivering on .a. the circuit switchingb. the physical pathc. the analog circuitd. the logical path1. Connecting to the Internet usually includes the following decisions type of .a. deviceb. connectionc. userd. Internet serviceprovider2. Which device can be used to access the Internet ? .a. PCb.DVDc. notebook computerd. Internetappliance3. Following device belongs to the one of dial-up connection .a.HFCb. modemc. dedicate line devicedd. ADSL4. Using a PC we can retrieve much contents from the Web, they are .a. Web pagesb. multimedia contentsc. video clipsd. music files5. Mobile Web is used for usually.a. notebook computersb. mobile phonesc. handheld computersd. pagers6. When we use a dial-up connection to access the Internet, we need .a. a TV cableb. a regulartelephone linec. a modemd. a temporary IPaddress7. ADSL works at a rate of .a. asymmetric transmissionb. symmetric transmissionc. asymmetric transmission with 9Mb/s downstreamd. asymmetric transmission with 16K-64Kb/s upstream8. We can find the following facilities in an HFC system .a. optical fiberb. coaxial cablec. cable modemd. head end9. With the dedicated connection to connect the Internet we should .a. use dial-up connectionb. keep a continual connectionc. use a static IP addressd. keep a temporary connection10. If some one wants to use mobile wireless connection, he or her should have.a. mobile deviceb. a fixed radioconnectionc. Web-enable cell phoned. a mobile transceiver(1) The true goal of ERP is .a. to integrate all departmentsb. to integrate all functionsc. to work across a companyd.d.to work on a single computer system(2) To do ERP right the ways should change.a. people do their jobsb. you do business with ERPc. you do business without ERPd. people do their jobs with ERP(3) ERP can serve the needs of people in.a. financeb. human resourcesc. warehoused. all above(4) Real transformational ERP efforts usually run .a. five yearsb. three yearsc. two yearsd. one year(5) A business process should include .a. order fulfillmentb. shipping goodsc. billing for the orderd. understanding the customer’s cre dit rating(6) Companies that measure their products by flow rather than individual units arecompanies.a. utilityb. oilc. chemicald. mechanicalparts(7) With ERP, the customer service representatives .a. are just typistsb. are no longer just typistsc. should be business peopled. should not be business people(8) With the manufacturing companiescansave time, increase productivity and reduce headcount.a. standardizing manufacturing processesb. using a single, integrated computer systemc. using ERPd. in-basket mode1. Internet telephony system aresystems.a. synchronous distributedb. asynchronous distributedc. so called as IP telephonyd. synchronous centralized2. The operating platforms that are currently supported by the various Internet telephonysystem include .a. QoSb. UNIXc. Windowsd. Mac3. With an Internet telephone system developed by using Java applet users should .a. have a standard web browser with Java supportb. install the telephony system every time they want to talkc. worry about the underlying workings of a telephony systemd. have a network connection4. The following components are the basic ones of an Internet telephony system .a. host computerb. modemc. local area networkd. router5. The communication p rocess that the caller’s telephony system handled includes .a. acquiring the real-time voice datab. digitizing the analogue signalsc. compressing the digitized datad. decrypting the digitized data6. The communication process that the recipient’s telephony system handled includes .a. encrypting the digitized datab. receiving incoming datac. decompressing incoming datad. playing back on the audio output device7. The major problems encountered in the current Internet telephone are .a. the working model of the best-effort Internetb. transmitting delayc. transmitting delay jittersd. packet loss8. We can find the following voice recovery methods .a. silence substitutionb. waveform substitutionc. sample interpolationd. embedded speech coding9. When we make a distance telephony call such as from Beijing to Guangzhou with Internet telephony system, we should pay communication fees that include .a. transcontinental telephone callsb. local telephone callsc. ISP’s feesd. nominal standard Internet connectivity charges10. The current Internet telephony systems .a. are launched as stand-alone applicationsb. must be downloaded prior to operationc. must purchase a new version of thesoftware of the system for upgradingd. must be installed prior to operation1. The Web took a bold step forward, it .a. was spurred by little-known technologiesb. was spurred by well-known technologiesc. shattered the traditional usage model of the Webd. kept the traditional usage model of the Web2. In order to develop a new web application model we should use some technologies, such as .a. traditional web browsersb. JavaScript remotingc. web remote procedure callsd. dynamic updating3. Using Ajax we can .a. perform the web interactionb. transmit only a small amount of information to and from the serverc. give the user the most responsive experience possibled. substitute the traditional web application model4. In the traditional web application model the browser .a. has an Ajax engineb. is responsible for initiating requests to the Web serverc. is responsible for processing requests from the Web serverd. sends a HTML request to the Web server5. Ajax engine is .a. a JavaScript objectb. a JavaScript functionc. responsible for linking to another resourced. responsible for executing the request from the Web server6. The traditional Web server would serveup .a. JavaScriptb. CSSc. HTMLd. images7. After receiving a server response the Ajax engine .a. goes into actionb. provides a link to another Web pagec. often parses the datad. makes several changes to the user interface8. To make an Ajax solution we must use the following technologies: .a.CSSb. HTML/XHTMLc. DOMd. JavaScript9. With Ajax engine we can .a. transfer less information than the traditional Web application modelb. update user interface more fasterc. work more quicklyd. transfer more information than the traditional web application model10. The data that the Ajax engine can useshould be .a. plain textb. understood by the Ajax enginec. XMLd. any other data format。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
(1) A large main memory can be used forstoring a,b,c .a. datab. operating systemc. applicationsd. interface(2) Early computer solved c,d problems.a. controlb. business applicationsc. engineeringd. mathematical(3) The system manager used by a fast processor cana,b,c .a. reset a systemb. monitor processor’s core temperaturec. monito r processor’s supply voltagesd. connect a network(4) We can say a bus is simply a,c,d .a. a group of wiresb. a wirec. a 8-bit busd. a 16-bit bus(5) A computer system user generally more cares for b,c,d .a. physical size of the computerb. storage sizec. speed of computationd. efficiency of the computer(6) According to the physical size of computers we can classify thecomputers into a,b,c,d .a. microcomputerb. minicomputerc. mainframed. supercomputer(7) The basic hardware components of any computerinclude a,b,c,d .a. CPUb. main memoryc. input devicesd. output devices(8) The following devices are belong to the mass storages a,b,d .a. DVDb. CD-ROMc. moused. disk(1) Cache is a,c,d .a. fastb. slowc. relatively smalld. high cost(2) Information stored in semiconductor RAMis b,c .a. permanentb. nonpermanentc. volatiled. non volatile(3) We use paged virtual memory to a,b,c,d.a. extend the size of memoryb. increase bandwidth of the diskc. reduce latency of the diskd. store large program and data set(4)We read data on the disk by a,d .(5) The three desiderata of memory system are b,c .a.independentb. exclusivec.closely approximated todayd. Less approximated tomorrow(6) The processor performance would be high as wereference instructions and data from b,d.a. hard diskb. cachec. floppy diskd. memory(7) Page frame is used in a .a. real memoryb. virtual memoryc. diskd. cache(8) In order to increase our computer’s performancewe need to a,b,c ,a. have a L2 cacheb. buy a L2 cachec. have a much larger main memoryd. buy a L1 cache(1) RISC is b,c,d .a. abbreviation of complex instruction set computerb. abbreviation of reduced instruction set computerc. guided to be built from studying the executionbehavior of high-level language programsd. used for many computer manufacturersnowadays(2) To enhance performance of a computer system weshould a,b,d .a. improve the pattern of referencing operandb. optimize the simple movement of datac. use IF and LOOP instructions as many aspossibled. optimize the basic sequence control mechanism(5) Register storage has b,d .a. a large capacityb. a small capacityc. the slower speedd. the faster speed(6) Instruction format in RISC has a,c,d .a. one kindb. many kindsc. a few kindsd. one or a few kinds(7) CISC machine instructions compared with RISCmachine are a,d .a. more complicatedb. more simplec. more faster to be executedd. more slower to be executed(8) Functions of the compiler used in RISCare b,c,d .a. to compile a high level language programb. to optimize register usagec. to maximize register usaged. to allocate registers to those variables that willbeused the most in a given time period(9) One machine cycle in RISC has c .a. two machine instructionsb. three machineinstructionsc. one machine instructiond. four machineinstructions(10) The register file is a,c,d .a. physically smallb. physically largec. one the same chip as the CPUd. addressed by much shorter addressesOperating systems and middleware b,c,da. have less in commonb. both can support other softwarec. have much in commond. both can support application programs2. An operating system provides the services in itsAPI by a,c,da. using the features of the hardwareb. offering database accessibilityc. using disk drive’s abilityd. offering fixed-length blocks of data4. Middleware lies in b,c,da. the top of the layering vertical stackb. the middle of the layering vertical stackc. the top of an operating systemd. the middle of interactions between differentapplication programs5. The following products of software are belong tomiddleware a,b,ca. IBM’s Web Sphere MQb. Java 2 Platformc. J2EEd. Oracle6. A mechanism for translating Internet hostnamesinto IP addresses is a,c,da. typically outside of operating system kernelb. typically inside of operating system kernelc. equipped into the general-purpose operatingsystemd. as a middleware by author’s definition7. With middleware we can b,c,da. run programs on a centralized computersystem onlyb. keep computations largely isolated fromundesirable interactionsc. run programs on different computer systemd. allow computations to communicate with oneanother8. Middleware has mechanisms to supportcontrolled interaction through a,b,c,da. communicationb. namingc. persistent storaged. coordination1. Before you turn the power on with a newcomputer, you should make sure a,b,c,d.a. the computer is already out of the boxb. appropriate cables are correctly connectedc. the computer system has been set upd. appropriate software have been installed2. An asleep state is a,c,d .a. a low power standby modeb. indicated by the indicator light putting outc. used for saving energyd. used to lessen wear-and tear on the computer4. During the boot procedure we can see a,b,conthe screen.a. amount of memoryb. the number of attached devicesc. the operating system being usedd. beeps and whirling noises5. A user interface we said here is a,b,d .a. an interaction between an operating system anda userb. an interaction between an applicationprogram and a userc. an interface between a computer and itsperipheral deviced. a text-based user interface or GUI6. Today Microsoft’s ope rating system Windows hasa variety of versions, they are a,b,c,d.a. Windows 2007b. Windows 2003c. Windows XPd. Windows vista7. The Windows desktop contains common elements,such as .a. desktop iconsb. taskbarc. Start buttond. task button9. With the window of the GUI we can use.a. menusb. dialog boxesc. iconsd. documents10. Main menu category in some Microsoftprograms .a. is a menu bar at the top of many windowsb. can display a pull-down menusc. can’t display a drop-down menusd. can display personalized menus1. Upgrading a computer system means .a. buying new hardwareb. buying new softwarec. extending the life of your current systemd. keeping your computer in present situation2. To formulate an upgrade strategy, you shouldconsider .a. the PC adheres to a well-supported standardb. you anticipate all your future needsc. there is room for additional expansion cardsd. there is room for memory3. Some common hardware upgrades nclude.a. adding more RAMb. installingADSLc. adding an image scannerd. installing a color printer4. The ways to seriously upgrade an Intel 80486-based PC include .a. installing the most modern softwareb. replacing the motherboardc. replacing other items inside the system unitd. just purchasing a new PC5. Relationship between version and release in asoftware is .a. version has major numberb. release has minor numberc. version typically increase its number inincrements of 1d. release typically increase its number inincrements of 0.1 or 0.016. Compatible mode of the software products canbe categorized into .a. upwardb. downwardc. crossd. aboveall1. A Wide Area Network can..a. cover a wide geographical areab. link two or more LANsc. link two LANs onlyd. be created by individual users2. According to the flow of information on atransmission facility we can categorize WANinto network.a. circuit switchedb. packet switchedc. local aread. Lease d. line3. In packet switched networks data send in..a. byteb. piecesc. framed. packet4. The most important items contained in a packetshould be.a. data to be transmittedb. header of the packetc. tail of the packetd. date5. The popular approaches we used in the packetswitched network are .a. circuit switchingb. datagramc. virtual circuitd. real circuit6. In the datagram mode when datagrams arrive attheir destination, the datagrams .a. may be out of orderb. must be in orderc. should be reorderedd. may lose7. In the virtual circuit mode all packets sent by auser at a time belong to .a. a messageb. a sessionc. different messagesd. different sessions8. Main characteristics of the leased line networksare .a. the line is private for the userb. the user has himself inter-exchangec. very short response timed. the user computer is always physicallyconnected to the line8. Main characteristics of the leased line networksare .a. the line is private for the userb. the user has himself inter-exchangec. very short response timed. the user computer is always physicallyconnected to the line9. A typical frame relay network has .a. seven componentsb. five componentsc. six componentsd. five major physical components and one"virtual" components10. Router has the following name .a. ARPANETb. IMP (Interface Message Processor)c. gatewayd. IS (Intermediate System)11. In Fig.4-6 a router creates a logical pathbetween networks, these networksinclude .a. FDDIb. Token Busc. Token Ringd. Ethernet12. Encapsulation is used here for data deliveringon .a. the circuit switchingb. the physical pathc. the analog circuitd. the logical path1. Connecting to the Internet usually includes thefollowing decisions type of .a. deviceb. connectionc. userd. Internet serviceprovider2. Which device can be used to access theInternet ? .a. PCb.DVDc. notebook computerd. Internetappliance3. Following device belongs to the one of dial-upconnection .a.HFCb. modemc. dedicate line devicedd. ADSL4. Using a PC we can retrieve much contents fromthe Web, they are .a. Web pagesb. multimedia contentsc. video clipsd. music files5. Mobile Web is used for usually.a. notebook computersb. mobile phonesc. handheld computersd. pagers6. When we use a dial-up connection to access theInternet, we need .a. a TV cableb. a regulartelephone linec. a modemd. a temporary IPaddress7. ADSL works at a rate of .a. asymmetric transmissionb. symmetric transmissionc. asymmetric transmission with 9Mb/sdownstreamd. asymmetric transmission with 16K-64Kb/supstream8. We can find the following facilities in an HFCsystem .a. optical fiberb. coaxial cablec. cable modemd. head end9. With the dedicated connection to connect theInternet we should .a. use dial-up connectionb. keep a continual connectionc. use a static IP addressd. keep a temporary connection10. If some one wants to use mobile wirelessconnection, he or her should have.a. mobile deviceb. a fixed radioconnectionc. Web-enable cell phoned. a mobile transceiver(1) The true goal of ERP is .a. to integrate all departmentsb. to integrate all functionsc. to work across a companyd.d.to work on a single computer system(2) To do ERP right the ways shouldchange.a. people do their jobsb. you do business with ERPc. you do business without ERPd. people do their jobs with ERP(3) ERP can serve the needs of people in.a. financeb. human resourcesc. warehoused. all above(4) Real transformational ERP efforts usuallyrun .a. five yearsb. three yearsc. two yearsd. one year(5) A business process should include .a. order fulfillmentb. shipping goodsc. billing for the orderd. understanding the customer’s credit rating(6) Companies that measure their products by flowrather than individual units arecompanies.a. utilityb. oilc. chemicald. mechanicalparts(7) With ERP, the customer servicerepresentatives .a. are just typistsb. are no longer just typistsc. should be business peopled. should not be business people(8) With the manufacturing companiescansave time, increase productivity and reduceheadcount.a. standardizing manufacturing processesb. using a single, integrated computer systemc. using ERPd. in-basket mode1. Internet telephony system aresystems.a. synchronous distributedb. asynchronous distributedc. so called as IP telephonyd. synchronous centralized2. The operating platforms that are currentlysupported by the various Internet telephonysystem include .a. QoSb. UNIXc. Windowsd. Mac3. With an Internet telephone system developed byusing Java applet users should .a. have a standard web browser with Java supportb. install the telephony system every time theywant to talkc. worry about the underlying workings of atelephony systemd. have a network connection4. The following components are the basic ones ofan Internet telephony system .a. host computerb. modemc. local area networkd. router5. The communication process that the caller’stelephony system handled includes .a. acquiring the real-time voice datab. digitizing the analogue signalsc. compressing the digitized datad. decrypting the digitized data6. The communication process that the recipient’stelephony system handled includes .a. encrypting the digitized datab. receiving incoming datac. decompressing incoming datad. playing back on the audio output device7. The major problems encountered in the currentInternet telephone are .a. the working model of the best-effort Internetb. transmitting delayc. transmitting delay jittersd. packet loss8. We can find the following voice recoverymethods .a. silence substitutionb. waveform substitutionc. sample interpolationd. embedded speech coding9. When we make a distance telephony call suchas from Beijing to Guangzhou with Internettelephony system, we should paycommunication fees that include .a. transcontinental telephone callsb. local telephone callsc. ISP’s feesd. nominal standard Internet connectivitycharges10. The current Internet telephony systems .a. are launched as stand-alone applicationsb. must be downloaded prior to operationc. must purchase a new version of thesoftware of the system for upgradingd. must be installed prior to operation1. The Web took a bold step forward, it .a. was spurred by little-known technologiesb. was spurred by well-known technologiesc. shattered the traditional usage model ofthe Webd. kept the traditional usage model of theWeb2. In order to develop a new web applicationmodel we should use some technologies,such as .a. traditional web browsersb. JavaScript remotingc. web remote procedure callsd. dynamic updating3. Using Ajax we can .a. perform the web interactionb. transmit only a small amount of informationto and from the serverc. give the user the most responsiveexperience possibled. substitute the traditional web applicationmodel4. In the traditional web application model thebrowser .a. has an Ajax engineb. is responsible for initiating requests to theWeb serverc. is responsible for processing requests fromthe Web serverd. sends a HTML request to the Web server5. Ajax engine is .a. a JavaScript objectb. a JavaScript functionc. responsible for linking to another resourced. responsible for executing the request fromthe Web server6. The traditional Web server would serveup .a. JavaScriptb. CSSc. HTMLd. images7. After receiving a server response the Ajaxengine .a. goes into actionb. provides a link to another Web pagec. often parses the datad. makes several changes to the user interface8. To make an Ajax solution we must use thefollowing technologies: .a.CSSb. HTML/XHTMLc. DOMd. JavaScript9. With Ajax engine we can .a. transfer less information than thetraditional Web application modelb. update user interface more fasterc. work more quicklyd. transfer more information than thetraditional web application model10. The data that the Ajax engine can useshould be .a. plain textb. understood by the Ajax enginec. XMLd. any other data format。
