抓tag报文设置
Ethereal -抓包、报文分析工具
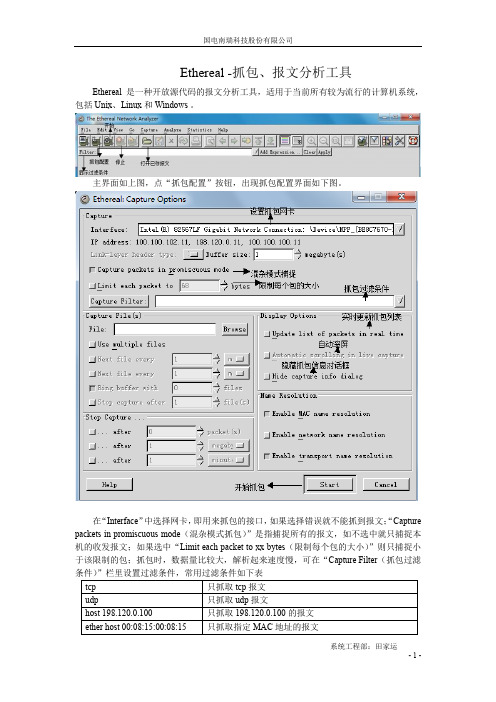
Ethereal -抓包、报文分析工具Ethereal 是一种开放源代码的报文分析工具,适用于当前所有较为流行的计算机系统,包括 Unix、Linux 和 Windows 。
主界面如上图,点“抓包配置”按钮,出现抓包配置界面如下图。
在“Interface”中选择网卡,即用来抓包的接口,如果选择错误就不能抓到报文;“Capture packets in promiscuous mode(混杂模式抓包)”是指捕捉所有的报文,如不选中就只捕捉本机的收发报文;如果选中“Limit each packet to xx bytes(限制每个包的大小)”则只捕捉小于该限制的包;抓包时,数据量比较大,解析起来速度慢,可在“Capture Filter(抓包过滤设置“Display Options(显示设置)”中建议选中“Update list of packets in realtime(实时更新抓包列表)”、“Automatic scrolling in live capture(自动滚屏)”和“Hide capture info dialog(隐藏抓包信息对话框)”三项。
抓包配置好就可以点击“Start”开始抓包了。
抓包结束,按“停止”按钮即可停止。
为了快速查看需要的报文,在“Filter”栏中输入过滤条件后按回车键即可对抓到的包进行过滤。
注意“Filter”栏中输入的过滤条件正确则其底色为绿色,错误则其底色为红色。
常用有些报文还可以判断网络的状况,例如输入显示过滤条件tcp.analysis.flags,可以显示丢失、重发等异常情况相关的TCP报文,此类报文的出现频率可以作为评估网络状况的一个标尺。
偶尔出现属于正常现象,完全不出现说明网络状态上佳。
tcp.flags.reset==1。
SYN是TCP建立的第一步,FIN是TCP连接正常关断的标志,RST是TCP连接强制关断的标志。
统计心跳报文有无丢失。
在statistics->conversations里选择UDP,可以看到所有装置的UDP报文统计。
如何设置抓带VLAN的包

vlan tag 设置.txtVLAN tag 是在802.1Q 中定义的标签,带VLAN tag 的报文头格式如下:01 0c cd 01 00 01 00 01 7a 01 00 52 81 00 00 0081 00为TPID ,即表明此数据包为带802.1Q/802.1P 标签的数据包;接下去的00 00为TCI (标签控制信息字段),表示为二进制共有16位,其中前3位为优先级,第4位为CFI ,通常为0,第5-16位为VLAN ID ,VLAN ID 为0用于识别帧优先级。
某一些网卡驱动默认会在接收数据包的时候过滤vlan tag ,使得用wireshark 抓到的数据包中不含vlan tag ,此时需要通过修改注册表让驱动保留vlan tag 。
对于Intel PRO/1000或PRO/100网卡,需要将注册表HKEYLOCALMACHINE\SYSTEM\ControlSet001\Control\Class{4D36E972-E325-11CE-BFC1-08002BE10318}\00xx 下的MonitorModeEnabled 改为1,如果不存在则新建这么一个dword 键。
对于Broadcom 千兆网卡,需要在注册表里增加一项PreserveVlanInfoInRxPacket=1,类型为string 。
位置与TxCoalescingTicks 相同,后者可以在HKEYLOCALMACHINE\SYSTEM\CurrentControlSet 下搜索到。
修改后需要重启机器让它生效。
这个修改办法是在UniCA User Manual 中看到的,较新的网卡驱动里都支持这个设置,原文如下:Intel PRO/1000 or PRO/100 Ethernet controller which are used in e.g. IBM Notebooks (T40 series and others) do not forward VLAN tags to the upper layers; By default, Intel adapters strip the VLAN tag before passing it up the stack. If you need to see the tag you need to use these driver versions: PRO/1006.x or 7.x or later base driver, PRO/1000 7.2.17.803 (plain 7.2.17 does not have this feature). Toenable, you must go into the registry and either add a registry dword and value (for e100) or change the value of the registry key (for e1000). The registry dword is MonitorModeEnabled (for both). It should be placed at HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class{4D36E972-E325-11CE-BFC1-08002BE10318}\00xx where xx is the instance of the network adapter that you need to see tags on. (Check by opening and viewing the name of the adapter). It should be set to read: MonitorModeEnabled= 1. Note: ControlSet001 may need to be CurrentControlSet or another 00x numberFor Broadcom 570x Gigabit adapters (for example in Dell systems); Add a registry key underHKEYLOCALMACHINE\SYSTEM\CurrentControlSet to cause the driver not to strip the 802.1Q VLAN header. In order to set that key, you need to find the right instance of the driver in Registry Editor and set that key for it.* Run the Registry Editor (regedt32).* Search for “TxCoalescingTicks ” under “HKEYLOCALMACHINE\SYSTEM\CurrentControlSet ” and ensure this is the only instance that you have.* Right-click on the instance number (eg. 0008) and add a new string value.* Enter “PreserveVlanInfoInRxPacket ” and give it the value “1″.* Save and Reboot* You may need to install a recent driver (version 8.27) to make this setting effective第 1 页Edited by Foxit Reader Copyright(C) by Foxit Software Company,2005-2007For Evaluation Only.。
思科设备开通MPLS VPN后无法访问网页故障分析

网络拓扑1.1.2 问题描述:安徽政法网主干思科设备开通MPLS VPN后,用户反映位于市政法委的PC无法打开省政法委的WEB服务器的网页,但是能够Ping通,FTP和网络共享都通。
主干思科设备为PE,我们的路由器为CE。
C7206和C7513之间通过2*2M采用MP方式互连。
1.1.3 问题分析根据故障现象,排除网络连通性问题。
经过现场观察,在省厅本地能够正常访问服务器网页,排除服务器IIS设置问题,在市局采用同一台机器访问其他站点正常,排除其IE浏览器设置问题。
在省厅和市局对服务器和PC流量分别进行抓包,如下图,发现服务器收到了对端发起的TCP连接请求,正常建立连接,并且已经把HTTP数据包发送出去,但是对端PC 只是抓到TCP握手的报文始终没有抓到服务器返回的HTTP报文,说明报文在传输过程中被丢弃。
根据初步掌握的现象和借鉴类似案例的经验,初步判断是转发路径上的设备MTU设置有问题。
顺序检查转发路径上设备的配置,发现两端CE设备没有设置任何ACL规则,广域网接口MTU为1500,且不可更改,不会造成问题;检查思科设备与我们设备的互连接口,也是缺省1500。
检查发现思科C7513和C7206的互连接口Int multilink 1的MTU为1500,由于此两个互连接口开启MPLS VPN,所以其接口的MTU应该比正常的MTU1500多8个字节(增加MPLS和VPN两层标签)。
而没有开启MPLS 的接口的MTU都是1500字节,所以开启MPLS接口的MTU应该大于等于1508,而抓到的服务器报文的帧长度为1514=1500(ip包长度)+14(帧头),这个报文到达主干后变成1508字节,由此判断思科设备MPLS接口的MTU缺省值设置太小造成1508字节的HTTP报文被丢弃。
在PC机上面采用如下命令Ping省厅WEB服务器: ping –f –l 1472 172.18.17.4 无法PING通,-f为不分片,1472为数据长度,加上20字节IP头和8个字节ICMP头正好为1500字节。
H3C交换机三种端口模式

Hybrid端口和Trunk端口在接收数据时,处理方法是一样的,唯一不同之处在于发送数据时:Hybrid端口可以允许多个VLAN的报文发送时不打标签,而Trunk端口只允许缺省VLAN的报文发送时不打标签。
[Switch-Ethernet0/1]port hybrid vlan 10 20 untagged
[Switch-Ethernet0/1] int e0/2
[Switch-Ethernet0/2]port link-type hybrid
[Switch-Ethernet0/2]port hybrid pvid vlan 20
untag就是普通的ethernet报文,普通PC机的网卡是可以识别这样的报文进行通讯;
tag报文结构的变化是在源mac地址和目的mac地址之后,加上了4bytes的vlan信息,也就是vlan tag头;一般来说这样的报文普通PC机的网卡是不能识别的
带802.1Q的帧是在标准以太网帧上插入了4个字节的标识。其中包含:
H3C交换机以太网端口类型:Access、Hybrid和Trunk三种模式的理解
2010-11-04 14:30
预备知识:
Tag,untag以及交换机的各种端口模式是网络工程技术人员调试交换机时接触最多的概念了,然而笔者发现在实际工作中技术人员往往对这些概念似懂非懂,笔者根据自己的理解再结合一个案例,试图向大家阐明这些概念
注:对于华为交换机缺省VLAN被称为“Pvid Vlan”, 对于思科交换机缺省VLAN被称为“Native Vlan”
PVID的作用及和VID的区别

PVID和VID彻底研究(上)——PVID的作用及和VID的区别Pvid和Vid经常出现于二、三层交换机里,由于PVID和VID的设置不合理,造成VLAN划分变得混乱。
本文就对PVID和VID进行了彻底研究。
pvid是交换机上的概念,说的是进入该端口的报文如果没有打vlan id就按pvid 的值打上,vid是报文上的vlan tag的意思.不是同个概念哦.首先解释一下什么是PVID,PVID英文解释为Port-base VLAN ID,是基于端口的VLAN ID,一个端口可以属于多个vlan,但是只能有一个PVID,收到一个不带tag头的数据包时,会打上PVID所表示的vlan号,视同该vlan的数据包处理,所以也有人说PVID就是某个端口默认的vlan ID号。
默认情况下,简单的理解为:ACCESS端口接PC,VID=PVIDTRUNK端口级联,VID=全部,PVID=1简单的说,VID(VLAN ID)是VLAN的标识,定义其中的端口可以接收发自这个VLAN的包;而PVID(Port VLAN ID)定义这个untag端口可以转发哪个VLAN的包。
比如,当端口1同时属于VLAN1、VLAN2和VLAN3时,而它的PVID为1,那么端口1可以接收到VLAN1,2,3的数据,但发出的包只能发到VLAN1中在网上发现一个比较好的解释是:PVID并不是加在帧头的标记,而是端口的属性,用来标识端口接收到的未标记的帧。
也就是说,当端口收到一个未标记的帧时,则把该帧转发到VID和本端口PVID相等的VLAN中去。
为了验证这一说法,在S3026上做了以下实验:在S3026上选两个端口,连接两台主机A、B,按照下表给端口设置不同的PVID 和VID,用A ping B,并在B上抓包,记录实验结果。
注:结果中“有”表示抓包有ICMP的包(但ping不同),“无”表示没有,“通”表示可以ping通。
VID为“无”表示该端口没有加到任何VLAN里。
如何设置Windows以抓取报文的vlan tag

?: HKEYLOCALMACHINE\SYSTEM\CurrentControlSet\Control\Class{4D36E972-E325-11CE-BFC1-08002BE10318}\00xx
/thread-19235-1-1.html
如何设置windows以抓取报文的vlan tag(针对Broadcom57xx网卡
Q:
在定位问题时,经常需要抓包,有时需要抓取带有报文里的tag,但通常情况下,windows会自动将收到的带有vlan tag的报文的tag去掉,那么如何设置才能抓取到报文的vlan tag呢?
A:
针对Broadcom 57xx系列网卡,可以通过修改注册表表项来实现该功能:
1、在注册表HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet中搜索 TxCoalescingTicks 。
2、在TxCoalescingTicks同一个位置,新建一字符串值 PreserveVlanInfoInRxPacket 。
3、将新建的PreserveVlanInfoInRxPacket的值设置为1。
4、重启电脑。
CLASS的值是确定的。00xx通过wireshark查看网卡detail的NPF索引对比确定
?: HKEYLOCALMACHINE\SYSTEM\ControlSet001\Control\Class{4D36E972-E325-11CE-BFC1-08002BE10318}\00xx
常见报文
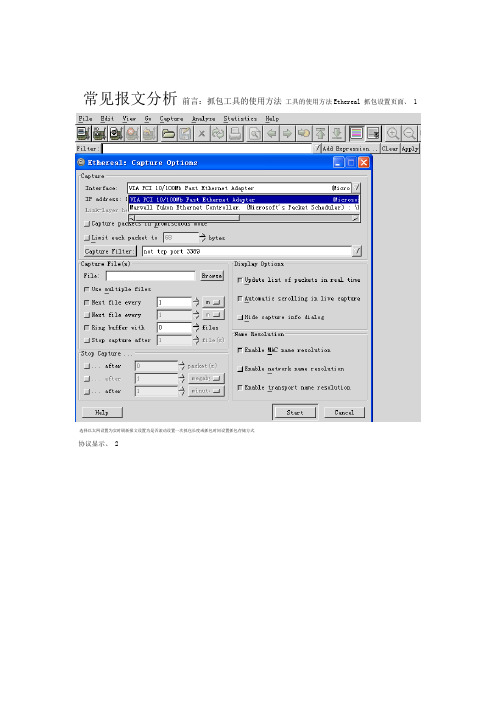
常见报文分析前言:抓包工具的使用方法工具的使用方法Ethereal 抓包设置页面、1选择以太网设置为实时刷新报文设置为是否滚动设置一次抓包长度或抓包时间设置抓包存储方式协议显示、2GOOSESV、ping报文抓包时间报文建立以太网通讯时会发ARPSNTP报文MMS 显示信息3、报文序号时间抓取该帧报文时刻,PC该帧报文是谁发出的该帧报文是发给谁的以太网类型码--协议类型报文长度4、过滤机制 4.1 关键字段过滤地址过滤MAC1)按目的2)按源MAC地址过滤)按优先级过滤3.4)按VLAN过滤语法vlan.id == 210 5)按以太网类型码过滤vlan.etype == 0x88b8 6)按APPID过滤7)按GOOSE控制块过滤个字节9个字节读取30从该帧报文的第frame[30:9] == 80:07:67:6f:63:62:52:65:66 语法:8)其他字段的过滤类似不在一一举例 4.1 组合过滤)找到特征报文的起始点1找到自己关注GOOSE的APPID 根据GOOSE变位时sequencenumber会变0的特性找到第一帧变位GOOSE)标注起始报文2.36、注意报文编号:28)去掉过滤条件,在所有的原始报文中显示标注报文,能找到事件之间的时间关系3、,在“Apply28去掉过滤条件并”附近发生的事情一目了然36)进一步优化时间显示4显示绝对时不含年、月、日绝对时间以第一帧报文为计时起点相对时间以上一帧报文为计时起点查看相邻两帧报文的间隔设置特征报文为计时参考点过滤结果“28”以后的报文均以其为计时起点1、MMS报文MMS(GBT 16720.2-2005 )是一种实时通信机制。
1.对象建模:对一个实际设备进行抽象,利用面向对象思想理解设备的逻辑构成。
参考7-2中进行抽象建模,提炼出设备所含有的逻辑节点,每个逻辑节点所含的参数、属性,找出逻辑节点之间数据流向。
整个过程需要对设备有大概的了解,知道设备可以被抽象为哪几个逻辑节点组成,特别是数据流向问题,还有该设备可能和哪些其他设备发生数据关系。
三层交换机08-添加或修改报文的VLAN Tag典型配置举例

H3C S5130-EI 添加或修改报文的VLAN Tag 配置举例目录1 简介···························································································································· 1-12 配置前提······················································································································ 2-23 QinQ配置举例··············································································································· 3-23.1 组网需求···················································································································3-23.2 配置思路···················································································································3-33.3 使用版本···················································································································3-33.4 配置注意事项·············································································································3-33.5 配置步骤···················································································································3-33.5.1 PE A的配置 ······································································································3-33.5.2 PE B的配置 ······································································································3-43.5.3 运营商网络设备的配置························································································3-43.6 验证配置···················································································································3-53.7 配置文件···················································································································3-54 1:2 VLAN映射配置举例··································································································· 4-64.1 组网需求···················································································································4-64.2 配置思路···················································································································4-74.3 使用版本···················································································································4-84.4 配置注意事项·············································································································4-84.5 配置步骤···················································································································4-84.5.1 PE A的配置 ······································································································4-84.5.2 PE B的配置 ······································································································4-94.5.3 公共网络设备的配置························································································· 4-114.6 验证配置················································································································· 4-114.7 配置文件················································································································· 4-115 使用QoS策略添加外层VLAN Tag并修改外层VLAN Tag的802.1p优先级配置举例······················5-135.1 组网需求················································································································· 5-135.2 配置思路················································································································· 5-155.3 使用版本················································································································· 5-155.4 配置注意事项··········································································································· 5-165.5 配置步骤················································································································· 5-165.5.1 Provider A的配置····························································································· 5-165.5.2 Provider B的配置····························································································· 5-195.5.3 运营商网络设备的配置······················································································ 5-215.6 验证配置················································································································· 5-215.7 配置文件················································································································· 5-226 1:1 和N:1 VLAN映射配置举例 ·························································································6-266.1 组网需求················································································································· 6-266.2 使用版本················································································································· 6-276.3 配置步骤················································································································· 6-276.3.1 Switch A的配置 ······························································································· 6-276.3.2 Switch B的配置 ······························································································· 6-286.3.3 Switch C的配置 ······························································································· 6-286.3.4 Switch D的配置 ······························································································· 6-306.4 验证配置················································································································· 6-306.5 配置文件················································································································· 6-317 2:2 VLAN映射配置举例··································································································7-347.1 组网需求················································································································· 7-347.2 使用版本················································································································· 7-357.3 配置注意事项··········································································································· 7-357.4 配置步骤················································································································· 7-357.4.1 Switch A的配置 ······························································································· 7-357.4.2 Switch B的配置 ······························································································· 7-367.4.3 Switch C的配置 ······························································································· 7-367.4.4 Switch D的配置 ······························································································· 7-377.5 验证配置················································································································· 7-377.6 配置文件················································································································· 7-378 使用QoS重标记功能修改报文内层VLAN Tag配置举例 ·························································8-398.1 组网需求················································································································· 8-398.2 配置思路················································································································· 8-398.3 使用版本················································································································· 8-408.4 配置步骤················································································································· 8-408.4.1 PE A的配置 ···································································································· 8-408.4.2 PE B的配置 ···································································································· 8-428.4.3 运营商网络设备的配置······················································································ 8-448.5 验证配置················································································································· 8-448.6 配置文件················································································································· 8-459 相关资料·····················································································································9-48。
Tag 和 untag

T ag 和untaguntag 就是普通的Ethernet 报文,普通PC 机的网卡是可以识别这样的报文进行通讯;tag 报文结构的变化是在源mac 地址和目的mac 地址之后,加上了4bytes 的vlan 信息,也就是vlan tag 头;一般来说这样的报文普通PC 机的网卡是不能识别的。
带802.1Q 的帧是在标准以太网帧上插入了 4 个字节的标识。
其中包含:2 个字节的协议标识符(TPID) ,当前置0x8100 的固定值,表明该帧带有802.1Q 的标记信息。
2 个字节的标记控制信息(TCI ),包含了三个域。
Priority 域,占3bits ,表示报文的优先级,取值0 到7 ,7 为最高优先级,0 为最低优先级。
该域被802.1p 采用。
规范格式指示符(CFI) 域,占1bit ,0 表示规范格式,应用于以太网;1 表示非规范格式,应用于T oken Ring 。
VLAN ID 域,占12bit ,用于标示VLAN 的归属。
以太网端口有三种链路类型:Access 、Hybrid 和T runk 。
Access 类型的端口只能属于 1 个VLAN ,一般用于连接计算机的端口;Trunk 类型的端口可以允许多个VLAN 通过,可以接收和发送多个VLAN 的报文,一般用于交换机之间连接的端口;Hybrid 类型的端口可以允许多个VLAN 通过,可以接收和发送多个VLAN 的报文,可以用于交换机之间连接,也可以用于连接用户的计算机。
Hybrid 端口和T runk 端口在接收数据时,处理方法是一样的,唯一不同之处在于发送数据时:Hybrid 端口可以允许多个VLAN 的报文发送时不打标签,而T runk 端口只允许缺省VLAN 的报文发送时不打标签。
在这里先要向大家阐明端口的缺省VLAN 这个概念Access 端口只属于 1 个VLAN ,所以它的缺省VLAN 就是它所在的VLAN ,不用设置;Hybrid 端口和T runk 端口属于多个VLAN ,所以需要设置缺省VLAN ID 。
中国电信定制网关2-1VLAN命令手册
Vlan命令手册目录1 简介 (3)1.1 概述 (3)1.2 Vlan接口简述 (3)2 配置VLAN (4)3 典型组网 (6)1简介1.1概述以太网是一种基于CSMA/CD (Carrier Sense Multiple Access/Collision Detect,载波侦听多路访问/冲突检测)的共享通讯介质的数据网络通讯技术,当主机数目较多时会导致冲突严重、广播泛滥、性能显著下降甚至使网络不可用等问题。
通过交换机实现LAN互联虽然可以解决冲突(Collision)严重的问题,但仍然不能隔离广播报文。
在这种情况下出现了VLAN (Virtual Local Area Network )技术,这种技术可以把一个LAN划分成多个逻辑的LAN——VLAN,每个VLAN是一个广播域,VLAN内的主机间通信就和在一个LAN内一样,而VLAN间则不能直接互通,这样,广播报文被限制在一个VLAN 内,如图1-1所示。
1.2Vlan接口简述根据端口转发报文时对不同tag标签的处理方式,两种端口链路类型:Access类型:一个端口只属于一个VLAN,一般用于连接用户设备。
不可设置缺省VLAN。
Trunk类型:一个端口可以允许多个VLAN通过,可以接受和发送多个VLAN的报文,一般用于网络设备之间的连接。
可设置缺省VLAN。
两种类型接口报文接收处理:Access端口:当接收报文不带tag时,压入缺省VLAN的tag;当接收报文带tag 时,如果VLAN ID与缺省VLAN的ID相同,则接受,否则丢弃。
Trunk端口:当接收报文不带tag时,压入缺省VLAN的tag;当接收报文带tag时,如果VLAN ID是该端口允许通过的VLAN ID,则接受,否则丢弃。
两种类型接口报文发送处理:Access端口:由于VLAN ID就是缺省VLAN ID,所以去掉该tag发送报文;Trunk端口:当VLAN ID等于缺省VLAN ID时,去掉tag,发送报文;当VLAN ID 不等于缺省VLAN ID,且VLAN ID属于该Trunk口允许通过的VLAN时,保留tag,发送报文。
Wireshark录取自定义报文的方法

Wireshark录取自定义报文的方法Wireshark是一款开源的网络协议分析工具,它可以捕获和分析网络流量。
Wireshark支持多种协议,并且允许用户录取自定义的报文进行进一步分析。
下面将介绍一种使用Wireshark录取自定义报文的方法。
首先,我们需要准备一个自定义的报文。
一个典型的报文由报文头和报文体组成。
报文头通常包括各种字段,例如源IP地址、目标IP地址、协议类型等信息。
报文体通常包含报文的具体内容,可以是文本数据、二进制数据或其他类型的数据。
接下来,打开Wireshark并选择一个适当的接口进行网络抓包。
Wireshark支持多种接口,可以是以太网、无线网络或其他类型的接口。
在Wireshark的主界面中,会显示一个实时的网络流量列表。
这个列表显示了从所选接口捕获的所有网络流量。
要录取自定义报文,需要设置过滤器来仅显示希望捕获的报文。
在Wireshark的过滤栏处,可以输入一个过滤表达式。
过滤表达式可以用于选择特定类型的报文。
例如,可以使用IP过滤表达式来仅显示与IP协议相关的报文:ip。
还可以使用端口过滤表达式来仅显示特定端口号的报文:tcp.port == 80。
当我们输入适当的过滤表达式后,Wireshark会自动应用过滤器,并只显示符合条件的报文。
接下来,我们需要发送自定义报文。
我们可以使用一个网络工具,例如cURL或Telnet,来发送自定义报文。
这些工具使我们能够以各种方式与服务器进行交互。
使用cURL发送自定义报文时,可以使用以下命令格式:```curl -X [请求方法] -H "Content-Type: [内容类型]" -d '[报文内容]' [目标URL]```其中,[请求方法]是报文的请求方法,例如GET、POST等。
[内容类型]是报文的内容类型,例如application/json。
[报文内容]是报文的具体内容,例如JSON格式的文本数据。
vlan中pvid和vid的区别

通过分析,得出S3026转发机制大致如下:
1、由主机B发出的包到接口2(由于此时B不知道A的MAC地址,会发出arp广播包)
2、根据接口2的PVID的值(PVID=2),发往VID=2的VLAN中的所有接口
3、接口1属于VLAN 2,所以接口1能收到此包
4、此时如果VLAN 2中接口1是tag端口,则将接口1的PVID值和VID进行比较:
默认情况下,简单的理解为:
ACCESS端口接PC,VID=PVID
TRUNK端口级联,VID=全部,PVID=1
简单的说,VID(VLAN ID)是VLAN的标识,定义其中的端口可以接收发自这个VLAN的包;而PVID(Port VLAN ID)定义这个untag端口可以转发哪个VLAN的包。比如,当端口1同时属于VLAN1、VLAN2和VLAN3时,而它的PVID为1,那么端口1可以接收到VLAN1,2,3的数据,但发出的包只能发到VLAN1中
vid是报文上的vlan tag的意思.不是同个概念哦.
首先解释一下什么是PVID,PVID英文解释为Port-base VLAN ID,是基于端口的VLAN ID,一个端口可以属于多个vlan,但是只能有一个PVID,收到一个不带tag头的数据包时,会打上PVID所表示的vlan号,视同该vlan的数据包处理,所以也有人说PVID就是某个端口默认的vlan ID号。
到此我和大家一样有个疑问,一个VLAN干吗要设置PVID和VID两种标识呀?方正只有当PVID=VID时才能互通,只有一个不就够了吗?请往下看。
当所有VLAN都在一个交换机里时,确实只需要一个标识就够了,但跨设备的VLAN就需要另一种标识,这就是802.1Q的VLAN ID,即VID。
DELL笔记本网卡抓VLAN标签设置
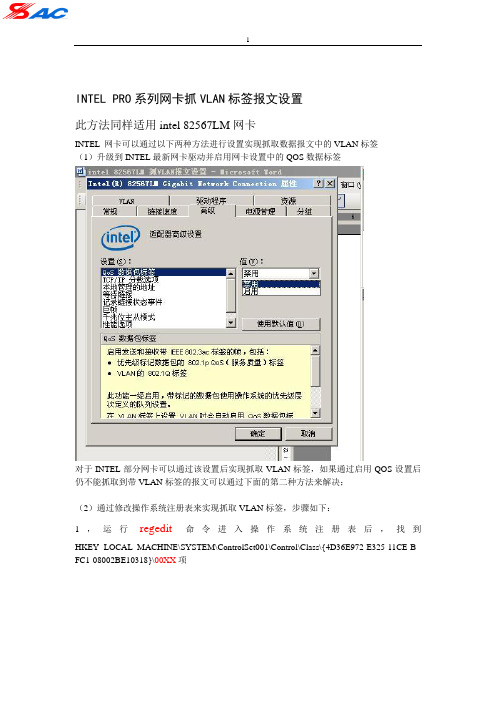
INTEL PRO系列网卡抓VLAN标签报文设置
此方法同样适用intel 82567LM网卡
INTEL 网卡可以通过以下两种方法进行设置实现抓取数据报文中的VLAN标签
(1)升级到INTEL最新网卡驱动并启用网卡设置中的QOS数据标签
对于INTEL部分网卡可以通过该设置后实现抓取VLAN标签,如果通过启用QOS设置后仍不能抓取到带VLAN标签的报文可以通过下面的第二种方法来解决;
(2)通过修改操作系统注册表来实现抓取VLAN标签,步骤如下:
1,运行regedit命令进入操作系统注册表后,找到HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E972-E325-11CE-B FC1-08002BE10318}\00XX项
有时候不一定是在009上,比如我的笔记本就是007
注:
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E972-E325-11CE-B FC1-08002BE10318}下有多项,分别代表系统各个网络接口,依我的系统为例,0009项是我的intel 82567LM网卡项,,除了需要修改ControlSet001下的选项外,还需要修改
ControlSet002下的。
2在右边框中查找是否有MonitorModeEnabled和MonitorMode键如果没有可以通过新建两个DWORD值来添加,32位还是64位可看自己的PC属性,取名为MonitorModeEnabled和MonitorMode并修改值为
16进制1。
通过以上设置重启电脑后就可以抓取到带VLAN标签的报文了。
PC通过流镜像抓包获取VLAN标签报文

一.配置电脑网卡并修改注册表
步骤2:选择Advanced中的优先级和vlan。选择已启用。(如 果没有此选项,请升级你的网卡驱动到高版本)
HUAWEI TECHNOLOGIES CO., LTD.
华为保密信息,未经授权禁止扩散
Page 3
一.配置电脑网卡并修改注册表
步骤3:针对Intel 82577lm/82579lm型号网卡,请到Intel官网
Page 6
HUAWEI TECHNOLOGIES CO., LTD.
华为保密信息,未经授权禁止扩散
Page 7
一.配置电脑网卡并修改注册表
步骤5:
在此目录下,建立两个属性是REG_DWORD的文件,文件名称 分别为MonitorMode和MonitorModeEnabled,参数值分别
填1,类型为DWORD(32)值。如下图所示。
华为保密信息,未经授权禁止扩散
Page 4
HUAWEI TECHNOLOGIES CO., LTD.
华为保密信息,未经授权禁止扩散
Page 5
一.配置电脑网卡并修改注册表
步骤4:进入regedit,选择
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\ Class\{4D36E972-E325-11CE-BFC1-08002bE10318}。在这个
Security Level:
PC抓取VLAN标签报文
HUAWEI TECHNOLOGIES CO., LTD.
一.配置电脑网卡并修改注册表
步骤1:
选择网卡,右键属性
HUAWEI TECHNOLOGIES CO., LTD.
61850典型报文解析说明

61850典型报文解析说明编写:欧灶军1 平台现利用ethereal报文抓捕工具抓取部分典型报文解析说明。
1.1报告类 COS61850报告服务,是一项非常重要的ACSI服务,它通过SCSM映射为MMS协议中的InformationReport服务,我们在调试过程中通过捕包工具得到的61850报告报文,都是经过编码后的InformationReport数据。
建好数据库,连接好装置后,启动SCADA服务器,并用ethereal抓报文,根据报告格式进行解析。
例如抓到的SOE报告ID号为BR03_brcbSOE01,其中03与模板中定义的各种报告类型有关,例如在我使用的装置模板中这么定义的:brcbREC、brcbCHK、brcbSOE分别为BR01、BR02、BR03,01表示该报告已经实例化。
由于InformationReport各成员的数据类型是确定的,根据编码规则,各数据编码后的数据也是确定的:RptID编码后数据为:8a XX XX … XX;OptFlds编码后数据为:84 03 07 XX X0;SqNum编码后数据为:86 XX XX … XX;TimeOfEntry编码后数据为:8C 06 XX XX XX XX XX XX;DataSet编码后数据为:8a XX XX … XX;BufOvfl编码后数据为:83 01 XX;EntryID编码后数据为:89 XX XX … XX;ConfRev编码后数据为:86 XX XX … XX;SubSeqNum编码后数据为:86 XX XX … XX;MoreSegmentFollow编码后数据为:83 01 XX;Inclusion-bitstring编码后数据为:84 XX … XX;Data-Reference编码后数据为:8a XX … XX;Value取决于具体数据类型;ReasonCode编码后数据为:84 XX … XX;下面以SOE报文为例,说明整个报告的含义,报文如下:8a 0e 42 52 30 33 5f 62 72 63 62 53 4f 45 30 31 (RptID)84 03 07 11 80(OptFlds)89 08 00 00 00 00 00 00 00 20 (EntryID)86 01 01 (ConfRev)84 06 05 80 00 00 10 00 (Inclusion-bitstring)a2 12 83 01 01 84 03 03 00 00 91 08 49 f9 70 02 02 d0 e5 8a a213 84 02 06 40 84 03 03 00 00 91 08 49 f9 70 02 05 1e b8 8a (Values,共2个)84 02 02 40 84 02 02 40 (ReasonCode,共2个)报告解析如下:RptID(BR03_brcbSOE01):8a 0e 42 52 30 33 5f 62 72 63 62 53 4f 45 30 31,其中8a为tag,长度为0e,后面的为ID编码。
wireshark抓vlan tag方法

wireshark抓vlan tag方法### Wireshark抓取VLAN Tag的方法VLAN(Virtual Local Area Network)是一种在网络中创建逻辑上的分割的技术,能够提高网络的性能和安全性。
Wireshark是一个流行的网络协议分析工具,可以用于捕获和分析网络数据包,包括带有VLAN Tag的数据包。
以下是如何使用Wireshark抓取带有VLAN Tag的数据包的方法。
#### 前提条件- 确保您的网络接口支持捕捉VLAN Tagged帧。
- 您需要具备管理员权限来捕获数据包。
#### 操作步骤1.**安装Wireshark**:- 从官方网站下载并安装Wireshark。
- 确保选择正确的安装选项,以包括捕获VLAN Tag所需的组件。
2.**启动Wireshark**:- 打开Wireshark应用程序。
- 在主界面上,您将看到所有可用的网络接口列表。
3.**选择正确的网络接口**:- 选择您想要捕获VLAN Tagged帧的网络接口。
- 如果不确定,可以查看接口的描述或连接类型,通常VLAN Tagged 帧会通过交换机端口捕获。
4.**设置捕获过滤器**:- 在开始捕获前,设置一个捕获过滤器可以帮助过滤掉非VLAN Tagged帧。
- 在捕获过滤器栏中输入`vlan` 或者更具体的过滤条件如`vlan && ethertype == 0x0800`(仅捕获带有VLAN Tag的IP帧)。
5.**开始捕获数据包**:- 点击工具栏上的“开始捕获”按钮。
- 执行一些会产生网络流量的操作,例如浏览网页或者ping命令。
6.**分析捕获的数据包**:- 停止捕获后,您将看到捕获到的数据包列表。
- 双击一个数据包,在底部的数据包详情窗格中检查“Ethernet II”层。
- 如果数据包带有VLAN Tag,您将看到“VLAN”标签,其中包括VLAN ID和优先级等信息。
电脑网卡设置抓tag报文方法

电脑网卡设置抓tag 报文方法
VLAN tag 是在802.1Q 中定义的标签,带VLAN tag 的报文头格式如下: 01 0c cd 01 00 01 00 01 7a 01 00 52 81 00 00 00 81 00 为TPID,即表明此数据包为带802.1Q/802.1P 标签的数据包;接下去的00 00 为TCI(标签控制信息字段),表示为二进制共有16 位,其中前3 位为优先级,第4 位为CFI,通常为0,第5-16 位为VLAN ID,VLAN ID 为0 用于识别帧优先级。
某一些网卡驱动默认会在接收数据包的时候过滤vlan tag,使得用wireshark 抓到的数据包中不含vlan tag,此时需要通过修改注册表让驱动保留vlan tag。
对于 Intel PRO/1000 或 PRO/100 网卡,需要将注册表HKEYLOCALMACHINE\SYSTEM\ControlSet001\Control\Class{4D36E972-E325-
11CE-BFC1-0800 2BE10318}\00xx 下的MonitorModeEnabled 改为1,如果不存在则新建这么一个dword 键。
对于 Broadcom 千兆网卡,需要在注册表里增加一项 PreserveVlanInfoInRxPacket=1,类型为 string 。
位置与TxCoalescingTicks 相同,后者可以在
HKEYLOCALMACHINE\SYSTEM\CurrentControlSet 下搜索到。
修改后需要重启机器让它生效。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
网卡设置不剥离VLAN的方法
产品名称:基础类
相关版本:所有版本
关键字:网卡、vlan
在平时的数据抓包时,有时需要抓不剥离VLAN带TAG标签的数据包,但是大部分的网卡在抓包时就剥离掉了VLAN,从而丢掉了一些有用的数据信息。
通过修改注册表可以使网卡抓包时不剥离VLAN,抓到带TAG标签的数据包,设置方法如下:
1、对于Intel PRO/1000或PRO/100网卡
需要将注册表
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E972-E325-11CE-BFC1-08002BE 10318}\00xx下的MonitorModeEnabled改为1,如果不存在则新建这么一个dword键。
2、对于Broadcom千兆网卡
需要在注册表里增加一项PreserveVlanInfoInRxPacket=1,类型为string(字符串)。
位置与TxCoalescingTicks相同,后者可以在HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet下搜索到。
修改后需要重启机器让它生效即可抓到带TAG标签的数据包。
注:对于上述1和2的两种网卡类型可以在“我的电脑”-“设备管理器”里面查询的到。
对于Intel PRO/1000或PRO/100网卡,需要将注册表
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class\{4D36E972-E325-11CE-BFC1-08002BE 10318}\00xx下的MonitorModeEnabled改为1,如果不存在则新建这么一个dword键。
对于Broadcom千兆网卡,需要在注册表里增加一项PreserveVlanInfoInRxPacket=1,类型为string。
位置与TxCoalescingTicks相同,后者可以在HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet下搜索到。
修改后需要重启机器让它生效。
这个修改办法是在UniCA User Manual中看到的,较新的网卡驱动里都支持这个设置,原文如下:
Intel PRO/1000 or PRO/100 Ethernet controller which are used in e.g. IBM Notebooks (T40 series and others) do not forward VLAN tags to the upper layers; By default, Intel adapters strip the VLAN tag before passing it up the stack. If you need to see the tag you need to use these driver versions: PRO/100 6.x or 7.x or later base driver, PRO/1000 7.2.17.803 (plain 7.2.17 does not have this feature). To enable, you must go into the registry and either add a registry dword and value (for e100) or change the value of the registry key (for e1000). The registry dword is MonitorModeEnabled (for both). It should be placed at HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Class{4D36E972-E325-11CE-BFC1-08002BE1 0318}\00xx where xx is the instance of the network adapter that you need to see tags on. (Check by opening and viewing the name of the adapter). It should be set to read:
MonitorModeEnabled= 1. Note: ControlSet001 may need to be CurrentControlSet or another 00x number
For Broadcom 570x Gigabit adapters (for example in Dell systems); Add a registry key under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet to cause the driver not to strip the 802.1Q VLAN header. In order to set that key, you need to find the right instance of the driver in Registry Editor and set that key for it.
Run the Registry Editor (regedt32).
Search for “TxCoalescingTicks” under "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet" and ensure this is the only instance that you have.
Right-click on the instance number (eg. 0008) and add a new string value.
Enter “PreserveVlanInfoInRxPacket” and give it the value “1″.
Save and Reboot
You may need to install a recent driver (version 8.27) to make this setting effective。
