Network Management Chapter 3
Chapter_3

Copyright © 2010. Mobile Communication & Network System. All Rights Reserved.
8
Transmission Line Theory
Characteristic Impedance ( 特性阻抗 )
所以: 所以:传输线上某一点的阻抗为 即:当l->∞时,从输入端出进去的输入阻抗=特性阻抗,因此, 时 从输入端出进去的输入阻抗=特性阻抗,因此, 有限长传输线终接Z 后相当于一无限长情景,即线上无反射波, 有限长传输线终接Zc后相当于一无限长情景,即线上无反射波, 所以Z 是最希望到达的。 所以Zc是最希望到达的。 对无损耗线的理想情况, R=G=0, 对无损耗线的理想情况,即R=G=0,则: 对宽带信号(脉冲中含丰富的谐波,可认为是宽带信号) 对宽带信号(脉冲中含丰富的谐波,可认为是宽带信号)的传 只有当Z 与频率无关时,才可保证波形不失真。 输,只有当Zc与频率无关时,才可保证波形不失真。但实际 上达不到。因为不同谐波,频率不同, 上达不到。因为不同谐波,频率不同,就往往使有些谐波产 生反射,出现失真。措施是尽量满足R/G=G/C R/G=G/C, 生反射,出现失真。措施是尽量满足R/G=G/C,(因由此可导 一般G很小,故应加大L 出 ),一般G很小,故应加大L。
数据通信
Data Communication
刘衍珩
移动通信与网络系统
Mobile Communication & Network System /mcns
Transmission Mediums
Transmission Line Theory Some Problems of Transmission Lines Practical Transmission Lines Other Transmission Media
计算机网络 Chapter_3_V6.0

3.6 principles of congestion control 3.7 TCP congestion control
Transport Layer 3-7
DatagramSocket mySocket2 = new DatagramSocket (9157);
application
DatagramSocket serverSocket = new DatagramSocket (6428);
Chapter 3 Transport Layer
A note on the use of these ppt slides:
We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) that you mention their source (after all, we’d like people to use our book!) If you post any slides on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Thanks and enjoy! JFK/KWR All material copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights Reserved Transport Layer 3-1
CCNA_ERouting_Chapter_3
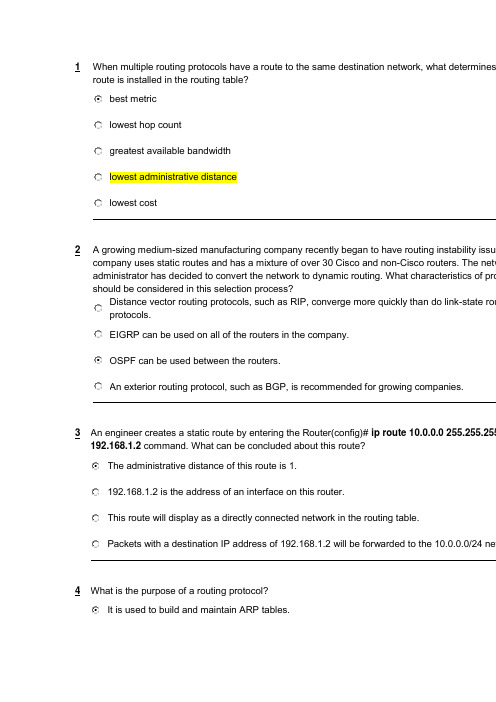
1When multiple routing protocols have a route to the same destination network, what determines route is installed in the routing table?best metriclowest hop countgreatest available bandwidthlowest administrative distancelowest cost2A growing medium-sized manufacturing company recently began to have routing instability issue company uses static routes and has a mixture of over 30 Cisco and non-Cisco routers. The netw administrator has decided to convert the network to dynamic routing. What characteristics of pro should be considered in this selection process?Distance vector routing protocols, such as RIP, converge more quickly than do link-state rou protocols.EIGRP can be used on all of the routers in the company.OSPF can be used between the routers.An exterior routing protocol, such as BGP, is recommended for growing companies.3An engineer creates a static route by entering the Router(config)# ip route 10.0.0.0 255.255.25 192.168.1.2 command. What can be concluded about this route?The administrative distance of this route is 1.192.168.1.2 is the address of an interface on this router.This route will display as a directly connected network in the routing table.Packets with a destination IP address of 192.168.1.2 will be forwarded to the 10.0.0.0/24 ne 4W hat is the purpose of a routing protocol?It is used to build and maintain ARP tables.It provides a method for segmenting and reassembling data packets.It allows an administrator to devise an addressing scheme for the network.It allows a router to share information about known networks with other routers.It provides a procedure for encoding and decoding data into bits for packet forwarding.5Which two conditions would create a setting where the use of a distance-vector routing protocol efficient? (Choose two.)the network requires a special hierarchical designfast convergence of the network is crucialthe network is using a hub and spoke topologythe network is using a flat designthere are more than 15 hops between the most distant routers6Which command would the network administrator issue to determine if load balancing is in effect on a router?show ip protocolsshow ip routeshow ip interface briefshow ip interface7W hich of the following best describes the operation of distance vector routing protocols?They use hop count as their only metric.They only send out updates when a new network is added.They send their routing tables to directly connected neighbors.They flood the entire network with routing updates.8Which two statements correctly describe the concepts of administrative distance and metric? (Choose two.)Administrative distance refers to the trustworthiness of a particular route.A router first installs routes with higher administrative distances.The value of the administrative distance can not be altered by the network administrator.Routes with the smallest metric to a destination indicate the best path.The metric is always determined based on hop count.The metric varies depending which Layer 3 protocol is being routed, such as IP or IPX.9T he following line of code is present in the routing table:O 10.16.1.0/27 [110/129] via 192.168.1.5, 00:00:05, Serial0/0/1What does the number 129 indicate in this output?The cost for this link has a value of 129.The clock rate on this serial interface is set to 129,000.The next-hop router is 129 hops away from this router.This route has been updated 129 times in this routing table.10Which of the following conditions must be met in order for a network to have converged?The routers in the network are operating with dynamic routing protocols.The routers in the network are operating with compatible versions of IOS.The routers in the network are operating with the same routing tables.The routers in the network are operating with consistent routing knowledge.11Refer to the exhibit. Router1 and Router2 are running EIGRP. All interfaces are operational and packets can be forwarde networks. What information will be found in the routing table for Router1?Router1 will have 6 directly connected networks.The administrative distance of the route to network 172.16.0.0 will be 90.The metric for routes to 172.16.0.0 will be 1.The interface that is used to forward packets to 172.16.0.0 will always be the S0/1 interface.12W hich two statements are true regarding the advantages of the use of static routes? (Choose two).increased securityreduced effort in configuring routesthe administrator maintains control over routingeasier to implement in a growing networkreduces the chance of routing errorsincreased router resource usage13The following line of code is displayed in a routing table:R 209.165.201.0/24 [120/2] via 192.168.252.2, 00:00:16, S0/0/0What can be concluded from this output?A packet destined for host 192.168.252.2 will be forwarded out the interface connected to network 209.165.201.0/24The value, 120, is used to determine the best path when a router has more than one routing protocol configured for t destination network.This route was manually configured using the ip route command.192.168.252.2 is an interface on the router that produced this output.14W hat will be the result of the following commands?ORL(config)# interface fastethernet 0/0ORL(config-if)# ip address 172.16.3.1 255.255.255.0ORL(config-if)# no shutdownThe 172.16.3.0 network will be routed by any dynamic routing protocol automatically.A routing table entry is made to the 172.16.3.0 network with a code of "C".A static route is required to route traffic to the 172.16.3.0 network.The commands will be saved to the startup-configuration automatically.15Which two statements are true regarding classless routing protocols? (Choose two.)sends subnet mask information in routing updatessends complete routing table update to all neighborsis supported by RIP version 1allows for use of both 192.168.1.0/30 and 192.168.1.16/28 subnets in the same topologyreduces the amount of address space available in an organization16Which two statements are true regarding metrics? (Choose two.)RIP uses bandwidth as a metric.OSPF uses delay as a metric.EIGRP uses bandwidth as a metric.OSPF uses cost based on bandwidth as a metric.RIP uses delay as a metric.EIGRP uses hop count only as a metric.17W hy is fast convergence desirable in networks that use dynamic routing protocols?Routers will not allow packets to be forwarded until the network has converged.Hosts are unable to access their gateway until the network has converged.Routers may make incorrect forwarding decisions until the network has converged.Routers will not allow configuration changes to be made until the network has converged.18Refer to the exhibit. Which statement correctly describes how R1 will determine the best path to R2?R1 will install a RIP route using network A in its routing table because the administrative distance of RIP is higher thaR1 will install a RIP route using network A in its routing table because the path cost from RIP is lower than EIGRP.R1 will install an EIGRP route using network B in its routing table because the administrative distance of EIGRP is loR1 will install an EIGRP route using network B in its routing table because the path cost from EIGRP is lower than RR1 will install an EIGRP route and a RIP route in its routing table and load balance between them.19Refer to the exhibit. If RIP is the routing protocol, what is the value of the metric from router A to network 192.168.5.0/24?345662472420 A router learns two paths with equal metrics to a destination network via the RIP routing protocol. How will the router handlthe destination network?The router will install the first route it learned into the routing table.The router will install both routes in the routing table and load balance between the two.The router will put the first route in the routing table, and denote the second route as a backup route.The router will pick the path with the higher bandwidth and will place it in the routing table.。
Gigabyte Management Console User's Guide

Gigabyte Management ConsoleUser’s Guide(For ASPEED AST 1250 Chipset)Version: 1.0Table of ContentsUsing Your Gigabyte Management Console (2)Gigabyte Management Console Key Features and Functions (3)Initial Setup (4)Configuring the Management Network (4)Software Install (5)Prerequisites on remote management PC (5)Install Java Tool (5)Gigabyte Management Console Network Configuration (6)Using the Web UI (8)Gigabyte Management Console Overview (9)Enter Gigabyte Management Console (10)Properties (10)Configuration (11)Network (11)Network Security (12)Security (13)Users (14)Services (15)Time Setting (16)Language (17)Sessions (18)LDAP (19)Firmware Updates (20)Utilities (21)FAN Profiles (22)Server Information (23)Sensor Monitor (23)Power Control (24)Power Consumption (25)System Event Log (26)Event Management (27)Platform Event (27)Trap Settings (28)Email Settings (29)Node Information (30)Node Status (30)Node MAC Address (31)Using Your Gigabyte Management ConsoleThe Gigabyte Management Console has a user-friendly Graphics User Interface (GUI) called the Gigabyte Management Console GUI. It is designed to be easy to use. It has a low learning curve because it uses a standard Internet browser. You can expect to be up and running in less than five minutes. This chapter allows you to become familiar with the Gigabyte Management Console GUI’s various functions. Each function is described in detail.Gigabyte Management Console Key Features and Functions ∙Support IPMI v2.0∙Out-of-band monitoring and control for sever management over LAN.∙FRU information report includes main board part number, product name, and manufacturer, etc.) ∙Health status/Hardware monitoring report.∙Events log, view, and clear.∙Event notification via PET (Platform Event Trap).∙Platform Event Filtering (PEF) to take selected action for selected events.∙Chassis management includes power control and status report, front panel buttons and LEDs control.∙Support multi-session user, and alert destination for LAN channel.Initial SetupConfiguring the Management NetworkSelect whether you want to use your CMC’s Ethernet port for stacking (daisy-chained) or use the two CMC Ethernet ports in a redundant manner (ringed).Stacking is best for customers who would like to take advantage of the cable consolidation feature of Multiple-Nodes. It is easy to use an in-band agent like Gigabyte Management Console in the rare case of a CMC port failure.Select the redundant network connection method for a more reliable connection to the management network. This type of network connection changes the default CMC setting before connecting to the network switch.To use this configuration, make sure your top LAN switch supports spanning tree protocol.Standard Shipping Configuration: with one hub and one CMC LAN port.Optional Configuration (Sold Separately): Add an additional hub for stacking or redundant configuration.Stacking Configuration Redundant ConfigurationSoftware InstallPrerequisites on remote management PCBefore installing Java tool, please check your system for the following required configuration requirements:●Supported Browsers:⏹Internet Explorer 8 - 11⏹Google chrome Version 29.0.1547.66m⏹Firefox 2.0●JA V A Recommended Version 8 Update 25 or later version (file size: ~ 623KB)Install Java ToolPlease follow the instruction to install Java in Windows operating system.1.Go to 2.Click Download on the middle of the home page.3.Click on Agree and Start Free Download4.Click see all Java downloads5.Select the operating system you are using.6.Choose the folder location. (Save the file to a known location on your computer)7.Click Save.8.Click Yes to replace.9.Verify that the●Name of the file is JavaSetup8u25.exe●Size is approximately 623KB.10.Close all applications including the browser.11.Double-click on the saved file icon to start the installation process.Gigabyte Management Console Network ConfigurationPlease follow the instruction to enable the console redirection function.1.Plug the VGA port to one of the node system.2.Boot up your node system.3.You can gather the BMC IP address on the POST screen.4.Or, Go to BIOS setup menu.5.Select Server Management.6.Select BMC network Configuration7.Define Configuration Address source to DynamicbmcDhcp or Static.8.Save and Exit.9.The BMC IP Address will appear on the IPv4 Address parameter.10.Save the configuration and exit BIOS setup menu.11.Open a web browser and type in your identified IP.12.Enter the following values:Username: adminPassword: password13.Go to the Properties page.14.Gathering the CMC identified IP address.Using the CMC Web UIThe CMC firmware features an embedded web server, enabling users to connect to the CMC using an Internet browser (Microsoft® Internet Explorer™).The web server shall support 4 concurrent connectionsWeb-based GUI is supported on the following browsers:Microsoft Windows:• Internet Explorer 8 ~ 12• Mozilla® Firefox® 2.0 or laterLinux:Mozilla Firefox 2.0 or laterGigabyte Management Console Overview1.Open a web browser and type in your identified IP. The IP address can be found using yourDHCP server.2. A dialog box prompts you to enter Username and Password.3.Enter the following values:Username: adminPassword: passwordWhen you log in using the root user name and password, you have full administrative powers. It is advised that once you log in, you change the root password.Enter Gigabyte Management ConsoleAfter you successfully log into your Gigabyte Management Console, the Remote Management Console GUI appears.PropertiesProperties displays the firmware version of current remote client system.ConfigurationNetworkYou can view and modify the network settings on this screen. Select the Network Mode from the drop-down list.1.Dedicate ModeWhen set to Dedicate Mode, you can configure the CMC related settings through the CMC port. Click Apply Change to save the settings.Network SecurityYou can configure the network security settings on this screen. Check the IP Blocking Enabled box and input the desire value of IP Blocking Fail Count, IP Blocking Fail Window, and IP Blocking Penalty Time. After you finish the configuration, click Apply Change to save the settings.SecurityThe Security page shows the current certificate status.To generate a new certificate, click Generate Certificate. To upload a certificate, click Upload Certificate.UsersTo configure a specific user, click the Users ID. To display new user information, click Refresh. NOTE: CMC convention for enabling an ‘anonymous’ login is to configure the entry for User ID 1 with a null username (all zero’s) and a null password (all zero’s). Applications may then present this to the user as an anonymous login.ServicesYou can configure the web server parameters (such as, HTTP Port Number, HTTPS Port Number, and Timeout) on a remote computer. By default, the timeout is 1800 seconds.When you finish the configuration, click Apply Changes.Time SettingThis page provides the mechanism to configure the Network Time acquisition method. With Administrator or Operator privilege level, you can modify configuration settings and click the Apply Changes button to execute the settings, as well as click the Sync Time Now button (when in Requested Mode) to request an immediate clock set.Network Time ProtocolOperation ModeConfigures the Operation Mode. You can Disable NTP, set Requested Mode, or Daemon Mode in this parameter.In Requested Mode, you can request an immediate clock synchronization with the NTP server; request will be sent when click the Sync Time Now button.The Daemon Mode runs NTP daemon which sends a NTP request at approximately 5 minute intervals. Multiple NTP servers may be specified to provide redundancy.Time Synchronization MethodSpecifies the synchronization method for Requested Mode. Select Slew mode when you want to adjust the time smoothly over time if there are time sensitive applications in place. Select Step mode to aggressively change the time using settimeofday() system call.Time Zone SettingConfigure the client time zone in this parameter.When you finish the configuration, click Apply Changes.LanguageThis page allow users to choose preferred language when using the WebUI. When you finish the configuration, click Apply Change.SessionsThis screen displays information on Active Sessions. Additionally, the trash can icon provides the delete function for privileged users. Click Session log to view the session log. Click Refresh to refresh the Sessions status.LDAPLDAP screen allows download user list of LDAP server then create Gigabyte Management Console user account from this list directly.Check the box below to enable LDAP authentication and enter the required information to access the LDAP server. Click Apply Changes to save your changes.Firmware UpdatesThe firmware can be updated remotely.To update firmware, follow the instruction below:1.Select Update Type.2.Select the file on your local system by using Browse. Click Upload to update to the new version of firmware.UtilitiesUtilities provides CMC reboot and Factory default restore functions.1.To reboot system, click Reboot.2.To restore factory default, click Factory Default.3.To Adjust the PWM offset for the system fans, enter offset values and click Submit.4.To update Logo, select the file on your local system using Browse and click Update.Fan ProfilesFan Profiles provides user to configure the system fan control policy.Server InformationSensor MonitorThe Sensor monitor provides general configuration for related system hardware monitoring. To view the Probe list, click Show Graph. And click Refresh to update current probe list.Power ControlThe Power Control allows you to power on/off/cycle the remote host system. Additionally you can see the remote power status.To perform the power control operation, select the operation and click Apply Changes.Power ConsumptionThis section allows user to configure the power policies for the system.System Event LogIt records the event when sensor has an abnormal state. When the log matches the pre-defined alert, the system sends out the notification automatically, if it is pre-configured.Event ManagementPlatform EventA platform event filter (PEF) can trigger an action and generate an alert when a critical hardware-related event occurs. For each PEF, you can choose the action to be taken when a platform event occurs.You can also choose to generate and send an alert when a platform event occurs. In the Platform Events screen, you can enable the generation of platform event alerts globally by clicking Global Alerting Enable.When you finish the configuration, click Apply Changes.In the Trap Settings, user can set the IPv4 and Ipv6 Destination List.IPv6 and IPv4 are two completely separate protocols. IPv6 is not backwards compatible with IPv4, and IPv4 hosts and routers will not be able to deal directly with IPv6 traffic.IPv6 has a significantly larger address space than IPv4. This results from the use of a 128-bit address, whereas IPv4 uses only 32 bits.When you finish the configuration, click Apply Changes.If you want the alert to be sent by email, you can configure to specify the e-mail address, subject and message in the Email Settings. After you finish the configuration, click Apply Change to save the settings.SMTPSet E-mail (SMTP) server IP address for sending alert notification to user.Check the SMTP Authentication Enabled box and enter the SMTP IP address, User Name, Password; select the STARTTLS Mode and SASL Mode from the drop-down list.When you finish the configuration, click “Apply Changes”.Node InformationNode StatusThis page displays the technical specifications of the connected node. Click Refresh to refresh current connected node information.Node MAC AddressThis page displays the connected node MAC address information.Click Refresh to refresh current connected node MAC address information.。
Chap3-Vlans

10-Jul-13
S Ward Abingdon and Witney College
17
Static VLAN
The normal type. Port configured to be on a VLAN. Connected device is on this VLAN. VLAN can be created using CLI command, given number and name. VLAN can be learned from another switch. If a port is put on a VLAN and the VLAN does not exist, then the VLAN is created.
5
Solution using routers
BUT Routers are expensive Routers are slower than switches Subnets are restricted to limited physical areas Subnets are inflexible
10-Jul-13
S Ward Abingdon and Witney College
23
Trunking
14
Management VLAN
Has the switch IP address. Used for telnet/SSH or web access for management purposes. Better not to use VLAN 1 for security reasons.
10-Jul-13 S Ward Abingdon and Witney College 8
NAD-chapter3
哈工大计算机学院 李全龙
Network Application Development
Client Software Design
12
Port numbers and network byte order
2
Learning algorithm instead of details
An application that uses TCP/IP must specify many details about the desired communication. Knowing the low-level details of all possible socket functions and their exact parameters does not provide programmers with an understanding of how to build well-designed, distributed program. General understanding of the functions used for network communication is important. If the programmer knows what the program should do, finding out how to do it is straightforward. Although programmers need to understand the conceptual capabilities of the protocol interface, they should concentrate on learning about ways to structure communicating programs instead of memorizing the details of a particular interface.
网络安全 论文题目

网络安全论文题目《网络安全威胁与防护策略研究》摘要:随着网络技术的发展,网络安全问题日益突出。
企业、政府机构和个人面临着日益复杂多样的网络安全威胁。
本论文通过对网络安全威胁的分析,探讨了网络安全威胁对企业和个人的危害,提出了相应的防护策略,并探讨了网络安全管理的重要性和挑战。
第一章:引言1.1 研究背景1.2 研究目的与意义1.3 研究内容与方法第二章:网络安全威胁分析2.1 病毒与恶意软件2.2 黑客攻击2.3 信息泄露与数据丢失2.4 拒绝服务攻击2.5 社会工程与钓鱼攻击第三章:网络安全威胁对企业的危害3.1 网络安全威胁对企业的经济损失3.2 网络安全威胁对企业的声誉影响3.3 网络安全威胁对企业的业务持续性影响第四章:网络安全威胁对个人的危害4.1 网络安全威胁对个人隐私的侵犯4.2 网络安全威胁对个人财产的损失4.3 网络安全威胁对个人信用信息的风险第五章:网络安全的防护策略5.1 安全意识和教育培训5.2 网络安全技术防护5.3 网络安全政策与法规建设5.4 安全管理与应急响应机制第六章:网络安全管理的重要性与挑战6.1 网络安全管理的重要性6.2 网络安全管理的挑战与困境第七章:结论与展望7.1 结论7.2 研究展望关键词:网络安全、网络安全威胁、防护策略、企业危害、个人危害、网络安全管理Abstract: With the development of network technology, network security issues have become increasingly prominent. Enterprises, government agencies, and individuals face increasingly complex and diverse network security threats. This paper analyzes network security threats, explores the harm of network security threats to enterprises and individuals, proposes corresponding protection strategies, and discusses the importance and challenges of networksecurity management.Chapter 1: Introduction1.1 Research Background1.2 Research Objectives and Significance1.3 Research Content and MethodsChapter 2: Analysis of Network Security Threats2.1 Viruses and Malware2.2 Hacker Attacks2.3 Information Leakage and Data Loss2.4 Denial of Service Attacks2.5 Social Engineering and Phishing AttacksChapter 3: Harm of Network Security Threats to Enterprises3.1 Economic Losses of Network Security Threats to Enterprises 3.2 Reputational Impact of Network Security Threats to Enterprises3.3 Impact on Business Continuity of Network Security Threats to EnterprisesChapter 4: Harm of Network Security Threats to Individuals4.1 Invasion of Personal Privacy by Network Security Threats 4.2 Losses of Personal Property due to Network Security Threats 4.3 Risks to Personal Credit Information due to Network Security ThreatsChapter 5: Protection Strategies for Network Security5.1 Security Awareness and Education Training5.2 Network Security Technology Protection5.3 Construction of Network Security Policies and Regulations 5.4 Security Management and Emergency Response Mechanism Chapter 6: Importance and Challenges of Network Security Management6.1 Importance of Network Security Management6.2 Challenges and Dilemmas of Network Security Management Chapter 7: Conclusion and Outlook7.1 Conclusion7.2 Research OutlookKeywords: Network Security, Network Security Threats, Protection Strategies, Enterprise Harm, Individual Harm, Network Security Management。
Chapter 3 Foundation of Computer Network(计算机网络基础)

Key words: networking(网络技术),spreadsheet(电子 表格),share(共享),network(网络),message(信息), graphics(图形),fax machine(传真机),modem(调制解调 器),CD-ROM(只读光盘),data storage equipment(数据存储 设备),Wide Area Network(广域网),Local Area Network (局域网),Metropolitan Area Network(城域网)
教学内容:
计算机网络英语;各相关硬件设备品牌、主要生 产厂商;常用的专业术语。
教学提示:
到学校机房或有关网络公司参观,感受本章内容, 以学到更多的专业知识和词汇。
3.1
Network Concepts(网络基础)
计算机网络的建立是为了满足人们 以即时方式共享数据的需求。个人计 算机在处理数据、电子表格、图形以 及其他类型的信息方面是理想的办公 设备,但却不支持快速(用户输出的) 数据共享。 如果用户能把他的计算机与其他 计算机联系在一起的话,他就可以共 享其他计算机上的数据,包括高性能 的打印机。一组计算机和其他的设备 连接在一起构成的系统叫作网络,互 连的计算机共享资源的技术(概念) 叫作网络技术。 联网的计算机可以共享数据、消息、 图形、打印机、传真机、调制解调器、 只读光盘、硬盘以及其他数据存储设 备。 按照网络作用的范围与计算机相互 连接的距离分,有广域网、局域网和 城域网3种类型的网络。
A computer network is a communication system connecting some computers that work together to exchange and share resources. Generally it is made up of two parts: network operation system (NOS) and hardware or nodes, referring to any devices that are connected to a network. Take LAN for example, the hardware system includes a microcomputer, which is used as file server and workstation, net interface card, Tshape juncture, BNC joint, terminator, and cables etc. File Server is the soul of a whole network, so it must be the best. All the input and output of data are under control of the File Server on the network. A network must have a computer as the network File Server, and it provides the workstation its data on the hard disk. Workstation actually is a set of PC. When it has been connected with File Server and been logged on, it can access data from the File Server, and operates on the workstation with the documents needed. Net card (network interface card: NIC) is the interface between File Server and Workstation.
Network MIB Agent Network Management

The Ohio State University
Raj Jain 30-6
Global Naming Hierarchy
ccitt(0) standard (0) iso9314 (9314) fddiMIB (1) directory (1) iso (1) joint-iso-ccitt (2) org (3) dod (6) internet (1) mgmt(2) mib (1) system (1) interfaces (2)
The Ohio State University
Raj Jain 30-13
OSI Network Management Standards
q q q q q
Common Management Information Protocol (CMIP) Common Management Information Service (CMIS) CMIP is the management (application layer) protocol CMIS is the service interface to CMIP M-GET (read attribute), M-SET (write attribute), MEVENT-REPORT (report an event), M-ACTION (perform an action), M-CREATE (create an instance), M-DELETE (delete an instance)
The Ohio State University
Raj Jain 30-14
Summary
q q q q
Management = Initialization, Monitoring, and Control SNMP = Only 5 commands Standard MIBs defined for each object Uses ASN.1 encoding
计算机专业英语-计算机网络基础-Chapter 3 Foundation of Computer Network(计算机网络基础)

on, it can access data from the File Server, and 需文件后就可以在工作站上运行。
operates on the workstation with the documents 网卡(network interface card: NIC)
needed.
是服务器与工作站之间的接口。
BNC joint, terminator, and cables etc.
服务器( file server )是整个网络的
File Server is the soul of a whole network, so it 灵魂,所以它必须是最好的。网络上所
must be the best. All the input and output of data 有数据的进出都须通过服务器来控制。
configurations or Network are star, bus, ring, 星形、总线形、环形和树形。
and tree.
星形网络
Star Network
星形网络由一台中央处理器、
A star network contains a central unit, a 多台个人计算机、终端或外围设
wonderful business tools for producing data, 算机在处理数据、电子表格、图形以
spreadsheets, graphics, and other types of 及其他类型的信息方面是理想的办公
information, but do not allow you to quickly 设备,但却不支持快速(用户输出的)
Ø 教学提示:
到学校机房或有关网络公司参观,感受本章内容, 以学到更多的专业知识和词汇。
TCP&IPSuite

Chapter 1 Introduction1. In the original ARPANET, _______ were directly connected together.(A) IMPs (B) host computers (C) networks (D) routers2. _______ was formed to connect universities with no defense ties.(A) ARPANET (B) CSNET (C) NSFNET (D) ANSNET3. was the first network.(A) CSNET (B) NSFNET (C) ANSNET (D) ARPANET4. Which organization has authority over interstate and international commerce in the communications field?(A) ITU-T (B) IEEE (C) FCC (D) ISOC5. _______ are special-interest groups that quickly test, evaluate, and standardize new technologies.(A) Forums (B) Regulatory agencies(C) Standards organizations (D) All of the above6. Which agency developed standards for physical connection interfaces and electronic signaling specifications?(A) EIA (B) ITU-T (C) ANSI (D) ISO7. _______ is the protocol suite for the current Internet.(A) TCP/IP (B) NCP (C) UNIX (D) ACM8. A version of the _______ operating system included TCP/IP.(A) DARPA (B) NCP (C)UNIX (D) ACM9. The _______ oversees the IETF and the IRTF.(A)ISOC (B) IAB (C) IANA (D) NIC10. The _______ maintains and supports IAB.(A) ISOC (B) IETF (C) IANA (D) ICANN11. _______ is the precursor to ICANN.(A) ISOC (B) IETF (C)IANA (D) NIC12. _____ refers to the structure or format of the data, meaning the order in which they are presented.(A) Semantics (B) Syntax (C) Timing (D) all of the above13. _____ defines how a particular pattern to be interpreted, and what action is to be taken based on that interpretation.(A) Semantics (B) Syntax (C) Timing (D) none of the above14. _______ refers to two characteristics: when data should be sent and how fast it can be sent.(A) Semantics (B) Syntax (C) Timing (D) none of the above15. An RFC, during its lifetime, falls into one of _______ maturity levels.(A) 5 (B) 2 (C) 6 (D) none of the above16. A proposed standard is elevated to _____ standard status after at least two successful tries.(A) informational (B) historic (C) draft (D) none of the above17. An RFC is labeled ______ if it must be implemented by all Internet systems.(A) required (B) elective (C) recommended (D) none of the aboveChapter 2 The OSI Model and the TCPIP Protocol Suite1. Why was the OSI model developed?(A) manufacturers disliked the TCP/IP protocol suite(B) the rate of data transfer was increasing exponentially(C) standards were needed to allow any two systems to communicate(D) none of the above2. The _______ model shows how the network functions of a computer ought to be organized.(A) CCITT (B) OSI (C) ISO (D) ANSI3. The physical layer is concerned with the movement of _______ over the physical medium.(A) programs (B) dialogs (C) protocols (D) bits4. The OSI model consists of _______ layers.(A) three (B) five (C)seven (D) eight5. In the OSI model, as a data packet moves from the lower to the upper layers, headers are _______.(A) added (B)removed (C) rearranged (D) modified6. In the OSI model, when data is transmitted from device A to device B, the header from A’s layer 5 is read by B’s _______ layer.(A) physical (B) transport (C) session (D) presentation7. In the OSI model, which layer functions as a liaison between user support layers and network support layers?(A) network layer (B) physical layer (C) transport layer (D) session layer8. In the OSI model, what is the main function of the transport layer?(A) node-to-node delivery (B) process-to-process message delivery(C) synchronization (D) updating and maintenance of routing tables9. In the OSI model, encryption and decryption are functions of the ________ layer.(A) transport (B) session (C)presentation (D) application10. In the OSI model, which of the following is an application layer service?(A) network virtual terminal (B) file transfer, access, and management(C) mail service (D) all of the above11. When a host on network A sends a message to a host on network B, which address does the router look at?(A) port (B)logical (C) physical (D) none of the above12. To deliver a message to the correct application program running on a host, the _______ address must be consulted.(A) port (B) IP (C) physical (D) none of the above13. IPv6 has _______ -bit addresses.(A) 32 (B) 64 (C)128 (D) variable14. ICMPv6 includes _______.(A) IGMP (B) ARP (C) RARP (D) a and b15. The ______ layer is responsible for moving frames from one hop (node) to the next.(A) physical (B) data link (C) transport (D) none of the above16. The ______ layer adds a header to the packet coming from the upper layer that includes the logical addresses of the sender and receiver.(A) physical (B) data link (C) network (D) none of the above17. The_____ layer is responsible for the delivery of a message from one process to another.(A) physical (B)transport (C) network (D) none of the above18. The Internetworking Protocol (IP) is a ________ protocol.(A) reliable (B) connection-oriented (C) both a and b (D) none of the above19. ______ is a process-to-process protocol that adds only port addresses, checksum error control, and length information to the data from the upper layer.(A) TCP (B) UDP (C) IP (D) none of the above20. _______ provides full transport layer services to applications.(A)TCP (B) UDP (C) ARP (D) none of the above21. The ________ address, also known as the link address, is the address of a node as defined by its LAN or WAN.(A) port (B)physical (C) logical (D) none of the above22. Ethernet uses a ______ physical address that is imprinted on the network interface card (NIC).(A) 32-bit (B) 64-bit (C) 6-byte (D) none of the above23. Which of the following can be an Ethernet physical address?(A) 01:02:01:2C:4B (B) 07:01:02:01:2C:4B:2C(C) 07:01:02:01:2C:4B (D) none of the above24. A port address in TCP/IP is ______ bits long.(A) 32 (B) 48 (C) 16 (D) none of the above25. IP Version 5 was a proposal based on the ______ model. This version never went beyond the proposal stage due to extensive layer changes and the projected expense.(A) TCP (B)OSI (C) IEEE (D) none of the aboveChapter 3 Underlying Technologies1. 10BASE2 uses _____ cable while 10BASE5 uses _______.(A) thick coaxial, thin coaxial (B) twisted-pair, thick coaxial(C) thin coaxial, thick coaxial (D) none of the above2. ____ specifies a physical star topology featuring a central hub andtwisted-pair cable as the medium.(A) 10BASE5 (B) 10BASE2 (C) 10BASE-T (D) none of the above3. Frame Relay operates in the _______.(A) physical layer (B) data link layer(C) physical and data link layers (D) none of the above4. Which ATM layer has a 53-byte cell as an end product?(A) physical (B)ATM (C) application adaptation (D) none of the above5. The IP protocol uses the _______ sublayer.(A) AAL1 (B) AAL2 (C)AAL5 (D) none of the above6. Repeaters function in the _______ layer.(A) physical (B) data link (C) network (D) none of the above7. Bridges function in the _______ layers.(A) physical and data link (B) data link and network(C) network and transport (D) none of the above8. A bridge has access to the _____ address of a station on the same network.(A) logical (B) physical (C) port (D) none of the above9. Routers function in the _______ layers.(A) physical and data link (B) physical, data link, and network(C) data link and network (D) none of the above10. _____ has a higher transmission rate in the downstream direction than in the upstream direction.(A) VDSL (B) ADSL (C) SDSL (D) none of the above11. _____ is suitable for businesses that require comparable upstream and downstream data rates.(A) VDSL (B) ADSL (C)SDSL (D) none of the above12. _____ was designed as an alternative to the T-1 line.(A) VDSL (B) ADSL (C)HDSL (D) none of the above13. A traditional TV network transmits signals _______.(A) upstream (B) downstream(C) upstream and downstream (D) none of the above14. The second generation of cable networks is called a(n) _______ network.(A)HFC (B) GHC (C) FHC (D) none of the above15. An HFC network uses _______ as the medium from the cable TV office to the fiber node.(A)optical fiber (B) coaxial cable (C) UTP (D) none of the above16. In an ESS the _______ station is mobile.(A) AP (B) server (C) BSS (D) none of the above17. In an ESS the _______ stations are part of a wired LAN.(A) AP (B) server (C) BSS (D) none of the above18. SONET is a standard for _______ networks.(A) twisted-pair cable (B) coaxial cable(C)fiber-optic cable (D) none of the above19. SONET is an acronym for _______ Network.(A)Synchronous Optical (B) Standard Optical(C) Symmetrical Open (D) none of the above20. PPP is a _______ layer protocol.(A) physical (B) data link(C) physical and data link (D) none of the aboveChapter 4 IP Addresses: Classful Addressing1. Identify the class of the following IP address: 4.5.6.7(A)class A (B) class B (C) class C (D) none of the above2. Identify the class of the following IP address: 229.1.2.3(A) class A (B) class B (C) class D (D) none of the above3. Identify the class of the following IP address: 191.1.2.3(A) class A (B) class B (C) class C (D) none of the above4. Which of the following is true of the IP address 231.1.23?(A) The netid is 231. (B) The class is D.(C) The hostid is 1.2.3. (D) none of the above5. Which of the following is true of the IP address 192.0.0.10?(A) The netid is 192. (B) The hostid is 0.10.(C) The network address is 192.0.0.0. (D) none of the above6. Using the direct broadcast address, a ____ sends a packet to _____ on the network.(A) host; all other hosts (B) router; all other hosts(C) host; a specific host (D) none of the above7. Using the limited broadcast address, a ____ sends a packet to _____ on the network.(A) host; all other hosts (B) router; all other hosts(C) host; a specific host (D) none of the above8. The loopback address is used to send a packet from the ___ to ___.(A) host; all other hosts (B) router; all other hosts(C) host; a specific host (D) none of the above9. A host can get its IP address from its server by using _____ as the source address and ____ as the destination address.(A) 255.255.255.255; 0.0.0.0 (B) 127.0.0.0; 255.255.255.255(C)0.0.0.0; 255.255.255.255 (D) none of the above10. A host with an IP address of 142.5.0.1 needs to test internal software. What is the destination address in the packet?(A) 131.0.0.0 (B)127.1.1.1 (C) 129.1.127.127 (D) none of the above11. What is the result of ANDing 255 and 15?(A) 255 (B) 15 (C) 0 (D) none of the above12. What is the result of ANDing 0 and 15?(A) 255 (B) 15 (C)0 (D) none of the above13. What is the result of ANDing 254 and 15?(A) 254 (B) 14 (C) 0 (D) none of the above14. What is the result of ANDing 192 and 65?(A) 192 (B) 65 (C) 64 (D) none of the above15. A subnet mask in class A has 14 1s. How many subnets does it define?(A) 32 (B) 8 (C) 64 (D) none of the above16. A subnet mask in class B has 19 1s. How many subnets does it define?(A) 8 (B) 32 (C) 64 (D) none of the above17. A subnet mask in class C has 25 1s. How many subnets does it define?(A)2 (B) 8 (C) 16 (D) none of the above18. Which one is not a contiguous mask?(A) 255.255.255.254 (B) 255.255.224.0 (C)255.148.0.0 (D) all are19. Given the IP address 201.14.78.65 and the subnet mask 255.255.255.224, what is the subnet address?(A) 201.14.78.32 (B) 201.14.78.65 (C) 201.14.78.64 (D) none of the above20. Given the IP address 180.25.21.172 and the subnet mask 255.255.192.0, what is the subnet address?(A) 180.25.21.0 (B)180.25.0.0 (C) 180.25.8.0 (D) none of the above21. Given the IP address 18.250.31.14 and the subnet mask 255.240.0.0, what is the subnet address?(A) 18.0.0.14 (B) 18.31.0.14 (C)18.240.0.0 (D) none of the above22. The subnet mask for a class C network is 255.255.255.192. How many subnetworks are available?(A) 2 (B)4 (C) 8 (D) none of the above23. The subnet mask for a class B network is 255.255.224.0. How many subnetworks are available?(A) 2 (B) 4 (C) 8 (D) none of the above24. The subnet mask for a class C network is 255.255.255.248. How many subnetworks are available?(A) 4 (B) 8 (C) 16 (D) none of the above25. The number of addresses in a class C block is _______.(A) 65,534 (B) 16,777,216 (C) 256 (D) none of the above26. The number of addresses in a class B block is _______.(A) 65,534 (B) 16,777,216 (C) 256 (D) none of the above27. The number of addresses in a class A block is _______.(A) 65,534 (B) 16,777,216 (C) 256 (D) none of the above28. An organization has been granted a class A address. If the organization has 256 subnets, how many addresses are available in each subnet (including special addresses)?(A) 65,534 (B) 16,777,216 (C) 256 (D) none of the above29. An organization has been granted a class B address. If the organization has 64 subnets, how many addresses are available in each subnet (including special addresses)?(A) 65,534 (B)1024 (C) 256 (D) none of the above30. An organization has been granted a class C address. If the organization has 4 subnets, how many addresses are available in each subnet (including special addresses)?(A) 4 (B) 1024 (C) 256 (D) none of the aboveChapter 5 IP Addresses: Classless Addressing1. In classless addressing, _____ is assigned to a organization.(A)a variable-length block (B) a fixed-length(C) a fixed number of blocks (D) none of the above2. The number of addresses assigned to an organization in classless addressing _____.(A) can be any number (B) must be a multiple of 256(C) must be a power of 2 (D) none of the above3. The first address assigned to an organization in classless addressing _______.(A) must be a power of 4(B) must be evenly divisible by the number of addresses(C) must belong to one of the A, B, or C classes(D) none of the above4. Which address could be the beginning address of a block of 32 classless addresses?(A) 2.4.6.5 (B) 2.4.6.16 (C)2.4.6.64 (D) none of the above5. Which address could be the beginning address of a block of 16 classless addresses?(A) 2.4.6.5 (B) 2.4.6.15 (C) 2.4.6.62 (D) none of the above6. Which address could be the beginning address of a block of 256 classless addresses?(A) 2.4.6.5 (B) 2.4.6.15 (C)2.4.6.0 (D) none of the above7. What is the first address of a block of classless addresses if one of the addresses is 12.2.2.76/27?(A) 12.2.2.0 (B) 12.2.2.32 (C) 12.2.2.64 (D) none of the above8. What is the first address of a block of classless addresses if one of the addresses is 12.2.2.76/10?(A)12.0.0.0 (B) 12.2.0.0 (C) 12.2.2.2 (D) none of the above9. What is the first address of a block of classless addresses if one of the addresses is 12.2.2.127/28?(A) 12.2.2.0 (B) 12.2.2.96 (C) 12.2.2.112 (D) none of the above10. Find the number of addresses in a block of classless addresses if one of the addresses is 12.2.2.7/24.(A) 32. (B) 64 (C)256 (D) none of the above11. Find the number of addresses in a block of classless addresses if one of the addresses is 12.2.2.7/30.(A) 2 (B)4 (C) 8 (D) none of the above12. What is the last address of a block of classless addresses if one of the addresses is 12.2.2.127/28?(A) 12.2.2.16 (B) 12.2.2.112 (C) 12.2.2.127 (D) none of the above13. What is the last address of a block of classless addresses if one of the addresses is 12.2.2.6/30?(A) 12.2.2.2 (B) 12.2.2.6 (C)12.2.2.7 (D) none of the above14. In fixed-length subnetting, the number of subnets must _______.(A)be a power of 2 (B) be a multiple of 128(C) be divisible by 128 (D) none of the above15. An organization is granted a block; one address is 2.2.2.64/20. The organization needs 10 subnets. What is the subnet prefix length?(A) /20 (B) /24 (C) /25 (D) none of the above16. An organization is granted a block; one address is 2.2.2.64/25. If the subnet prefix length is /28, what is the maximum number of subnets?(A) 2 (B) 4 (C)8 (D) none of the above17. An organization is granted a block of classless addresses with the starting address 199.34.76.64/28. How many addresses are granted?(A) 8 (B)16 (C) 32 (D) none of the above18. An organization is granted a block of classless addresses with the starting address 199.34.76.128/29. How many addresses are granted?(A) 8 (B) 16 (C) 32 (D) none of the above19. An organization is granted a block of classless addresses with the starting address 19.9.34.32.0/27. How many addresses are granted?(A) 8 (B) 16 (C) 32 (D) none of the above20. What is the default mask for class A in CIDR notation?(A) /9 (B)/8 (C) /16 (D) none of the above21. What is the default mask for class B in CIDR notation?(A) /9 (B) /8 (C)/16 (D) none of the above22. What is the default mask for class C in CIDR notation?(A) /24 (B) /8 (C)/16 (D) none of the above23. In ______ addressing, when an address is given, we can find the beginning address and the range of addresses.(A)classless (B) classful (C) both a and b (D) none of the above24. In classless addressing, the ____ is another name for the common part of the address range.(A) suffix (B)prefix (C) netid (D) none of the above25. In classless addressing, the _____ is the varying part (similar to the hostid).(A) suffix (B) prefix (C) hostid (D) none of the above26. In classless addressing, the prefix length defines the _____________.(A) netid (B) hostid (C) mask (D) none of the above27. In a block, the prefix length is /22; what is the mask?(A) 255.255.255.0 (B) 255.255.252.0(C) 255.255.0.0 (D) none of the above28. In a block, the prefix length is /15; what is the mask?(A)255.254.0.0 (B) 255.255.255.0(C) 255.255.255.12.8 (D) none of the above29. In a block, the mask is 255.255.192.0; what is the prefix length?(A) /20 (B) /28 (C) /18 (D) none of the above30. In a block, the mask is 255.255.255.224; what is the prefix length?(A) /20 (B) /19 (C) /20 (D) none of the aboveChapter 6 Delivery, Forwarding, and Routing of IP Packets1. In _____ delivery, both the deliverer of the IP packet and the destination are on the same network.(A) a connectionless (B) a direct (C) an indirect (D) none of the above2. In _____ delivery, the deliverer of the IP packet and the destination are on different networks.(A) a connection-oriented (B) a direct (C) an indirect (D) none of the above3. In ____ delivery, packets of a message are logically connected to one another.(A) a connectionless (B) a connection-oriented(C) a direct (D) none of the above4. In _____ delivery, a packet is not connected to any other packet.(A) a connectionless (B) a connection-oriented(C) a direct (D) none of the above5. In classful addressing, when a direct delivery is made, both the deliverer and receiver have the same _______.(A) IP address (B) hostid (C) netid (D) none of the above6. In classful addressing, when an indirect delivery is made, the deliverer and receiver have _______.(A) the same IP address (B)different netids(C) the same netid (D) none of the above7. In _____ forwarding, the full IP address of a destination is given in the routing table.(A) next-hop (B) network-specific (C)host-specific (D) default8. In _____ forwarding, the mask and destination addresses are both 0.0.0.0 in the routing table.(A) next-hop (B) network-specific (C) host-specific (D) default9. In _____ forwarding, the destination address is a network address in the routing table.(A) next-hop (B) network-specific (C) host-specific (D) default10. In _____ forwarding, the routing table holds the address of just the next hop instead of complete route information.(A) next-hop (B) network-specific (C) host-specific (D) default11. In _____ addressing, a typical forwarding module can be designed using three tables, one for each unicast class (A, B, C).(A) classful (B) classless (C) both a and b (D) none of the above12. In classful addressing, the class of the address can be found by shifting the copy of the address ____ bits to the right.(A) 32 (B) 16 (C)28 (D) none of the above13. In classful addressing we need a routing table with at least ___ columns.(A) 4 (B) 3 (C) 8 (D) none of the above14. In classless addressing, we need a routing table with at least _______ columns.(A)4 (B) 3 (C) 8 (D) none of the above15. The idea of address aggregation was designed to alleviate the increase in routing table entries when using ________.(A) classful addressing (B) classless addressing(C) both a and b (D) none of the above16. The principle of ____ states that the routing table is sorted from the longest mask to the shortest mask.(A) first mask matching (B) shortest mask matching(C) longest mask matching (D) none of the above17. The use of hierarchy in routing tables can _____ the size of the routing tables.(A)reduce (B) increase (C) both a and b (D) none of the above18. _____ deals with the issues of creating and maintaining routing tables.(A) Forwarding (B) Routing (C) Directing (D) none of the above19. A _____ routing table contains information entered manually.(A) static (B) dynamic (C) hierarchical (D) none of the above20. A ____ routing table is updated periodically using one of the dynamic routing protocols.(A) static (B)dynamic (C) hierarchical (D) none of the above21. The input and output ports of a router perform the _____ layer functions of the router.(A) physical and data link (B) network (C) transport (D) none of the above22. The routing processor of a router performs the _____ layer functions of the router.(A) physical and data link (B) network (C) transport (D) none of the above23. The task of moving the packet from the input queue to the output queue in a router is done by _________.(A) input and output ports (B) routing processor(C)switching fabrics (D) none of the aboveChapter 7 ARP and RARP1. A _____ address is an internetwork address with universal jurisdiction.(A) physical (B) logical (C) a and b (D) none of the above2. The logical addresses in the TCP/IP protocol suite are called ____ addresses.(A) port (B) IP (C) Email (D) none of the above3. A ______ is a local address. Its jurisdiction is over a local network.(A)physical (B) logical (C) a and b (D) none of the above4. If the sender is a host and wants to send a packet to another host on the same network, the logical address that must be mapped to a physical address is ______.(A) the destination IP address in the datagram header(B) the IP address of the router found in the routing table(C) either a or b(D) none of the above5. If the sender is a host and wants to send a packet to another host on another network, the logical address that must be mapped to a physical address is __.(A) the destination IP address in the datagram header(B) the IP address of the router found in the routing table(C) either a or b(D) none of the above6. The sender is a router that has received a datagram destined for a host on another network. The logical address that must be mapped to a physical address is ______.(A) the destination IP address in the datagram header(B) the IP address of the router found in the routing table(C) either a or b(D) none of the above7. The sender is a router that has received a datagram destined for a host in thesame network. The logical address that must be mapped to a physical address is ______.(A) the destination IP address in the datagram header(B) the IP address of the router found in the routing table(C) either a or b(D) none of the above8. In _____, a table associating a logical address with a physical address is updated manually.(A) static mapping (B) dynamic mapping(C) physical mapping (D) none of the above9. _____ is a dynamic mapping protocol in which a logical address is found fora given physical address.(A) ARP (B) RARP (C) both a and b (D) none of the above10. _____ is a dynamic mapping protocol in which a physical address is found fora given logical address.(A) ARP (B) RARP (C) both a and b (D) none of the above11. The target hardware address on an Ethernet is _______ in an ARP request.(A)0x000000000000 (B) 0.0.0.0 (C) variable (D) class dependent12. An ARP reply is normally _______.(A) broadcast (B) multicast (C)unicast (D) none of the above13. An ARP request is normally _______.(A)broadcast (B) multicast (C) unicast (D) none of the above14. A technique called ______ is used to create a subnetting effect.(A) ARP (B) RARP (C) proxy ARP (D) none of the above15. A ___ is an ARP that acts on behalf of a set of hosts.(A) ARP (B) RARP (C)proxy ARP (D) none of the above16. A sender usually has more than one IP datagram to send to the same destination. It is inefficient to use the ARP protocol for each datagram destined for the same host or router. The solution is the _________.(A) routing table (B)cache table (C) ARP table (D) none of the above17. The RARP request packets are normally _________.(A)broadcast (B) unicast (C) multicast (D) none of the above18. The RARP reply packets are normally_________ .(A) broadcast (B)unicast (C) multicast (D) none of the above19. The ARP component that sends an ARP reply to the data link layer is the _____.(A) cache controller (B) input module(C) output module (D) none of the above20. The ARP component that sends an IP packet to a queue is the _______.(A) cache controller (B) input module(C) output module (D) none of the aboveChapter 8 Internet Protocol (IP)1. The ___ protocol is the transmission mechanism used by the TCP/IP suite.(A) ARP (B) IP (C) RARP (D) none of the above2. IP is _____ datagram protocol.(A) unreliable (B) connectionless (C) both a and b (D) none of the above3. The term ___ means that IP provides no error checking or tracking. IP assumes the unreliability of the underlying layers and does its best to get a transmission through to its destination, but with no guarantees.(A) reliable delivery (B) connection-oriented delivery(C) best-effort delivery (D) none of the above4. A best-effort delivery service such as IP includes _______.(A) error checking (B) error correction(C) datagram acknowledgment (D) none of the above5. An HLEN value of decimal 10 means _______.(A) there are 10 bytes of options (B) there are 40 bytes of options(C) there are 40 bytes in the header (D) none of the above6. A datagram is fragmented into three smaller datagrams. Which of the following is true?(A) The do not fragment bit is set to 1 for all three datagrams.(B) The more fragment bit is set to 0 for all three datagrams.(C) The identification field is the same for all three datagrams.(D) none of the above7. Which field or bit value unambiguously identifies the datagram as a fragment?(A) Do not fragment bit = 0 (B) More Fragment bit = 0(C) Fragment offset = 1000 (D) none of the above8. If the fragment offset has a value of 100, it means that _______.(A) the datagram has not been fragmented(B) the datagram is 100 bytes in size(C) the first byte of the datagram is byte 800(D) none of the above9. What is needed to determine the number of the last byte of a fragment?(A) offset number (B) total length (C) a and b (D) none of the above10. The IP header size _______.(A) is 20 to 60 bytes long (B) is 20 bytes long(C) is 60 bytes long (D) none of the above11. Packets in the IP layer are called _________ .(A) segments (B)datagrams (C) frames (D) none of the above12. The total length field defines the total length of the datagram _________.(A) including the header (B) excluding the header(C) header and option length (D) none of the above13. When a datagram is encapsulated in a frame, the total size of the datagram must be less than the _______.(A) MUT (B) MAT (C) MTU (D) none of the above14. Which IP option is used if exactly four specific routers are to be visited by the datagram?(A) record route (B) strict source route(C) loose source route (D) none of the above。
(完整版)计算机网络英文题库(附答案)chapter3

Chapter 3 Transport Layer1. A transport-layer protocol provides for logical communication between ____.A Application processesB HostsC RoutersD End systems2. Transport-layer protocols run in ____.A ServersB ClientsC RoutersD End systems3. In transport layer, the send side breaks application messages into ____, passes to network layer.A FramesB SegmentsC Data-gramsD bit streams4. Services provided by transport layer include ____.A HTTP and FTPB TCP and IPC TCP and UDPD SMTP5. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers6. These two minimal transport-layer services----____ and ____----are the only two services that UDP provides!A process-to-process data delivery, error checkingB congestion control, reliable data transferC flow control, congestion controlD In-order data transfer, error checking7. Port number’s scop e is ____ to ____.A 0, 1023B 0, 65535C 0, 127D 0,2558. The port numbers ranging from ____to ____ are called well-known port number and are restricted.A 0, 1023B 0, 65535C 0, 127D 0,2559. UDP socket identified by two components, they are ____.A source IP addresses and source port numbersB source IP addresses and destination IP addressesC destination IP address and destination port numbersD destination port numbers and source port numbers10. TCP socket identified by a (an) ____.A 1-tupleB 2-tupleC 3-tupleD 4-tuple11. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP12. Reliable data transfer protocol over a perfectly reliable channel is____.A rdt1.0B rdt2.0C rdt3.0D rdt2.113. Reliable data transfer protocol over a channel with bit errors and packet losses is _ ___.A rdt1.0B rdt2.0C rdt3.0D rdt2.114. Which of the following about reliable data transfer over a channel with bit errors i s not correct?A RDT2.0: assuming ACK and NAK will not be corruptedB RDT2.1: assuming ACK and NAK can be corruptedC RDT2.2: only use ACK-sD RDT2.2: use both ACK-s and NAK-s15. Which of the following protocols is not pipelining protocols?A TCPB rdt3.0C GO-BACK-ND selective repeat16. Which of the following is not correct about GBN protocol?A Only using ACK-sB Using cumulative ACK-sC Receiver discards all out-of-order packetsD It is not pipelined protocol17. Which of the following is not correct about SR protocol?A receiver individually acknowledges all correctly received packetsB sender only resends packets for which ACK not receivedC It limits sequence number of sent but un-ACK-ed packetsD It is not a pipelined protocol18. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection19. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection20. The FIN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection21.How does TCP sender perceive congestion?A Through a timeout eventB Through a receiving duplicate ACK-s eventC Both A and BD Either A or B22. Extending host-to-host delivery to process-to-process delivery is called transport-layer ____ and .A multiplexing and de-multiplexingB storing and forwardingC forwarding and filteringD switching and routing23. UDP is a ____ service while TCP is a connection-oriented service.A ConnectionlessB ReliableC Connection-orientedD In-order24. The UDP header has only four fields, they are____.A Source port number, destination port number, length and checksumB Source port number, destination port number, source IP and destination IPC source IP, destination IP, source MAC address and destination MAC addressD source IP, destination IP, sequence number and ACK sequence number25. There are two 16-bit integers: 1110 0110 0110 0110, 1101 0101 0101 0101. Their checksum is____.A 0100010001000011B 1011101110111100C 1111111111111111D 100000000000000026.The maximum amount of data that can be grabbed and placed in a segment is limited by the____.A Maximum segment size (MSS)B MTUC ChecksumD Sequence number27.The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host----the so-called____.A Maximum transmission unit (MTU)B MSSC ChecksumD Sequence number28. A File size of 500,000bytes, MSS equals 1000bytes. When we want to transmit this file with TCP, the sequence number of the first segment is 0, and the sequence number of the second segment is ____.A 1000B 999C 1001D 50000029.Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide____.A Cumulative acknowledgementsB Selective acknowledgementsC 3 duplicate ACKsD positive ACKs30. Provided α=0.125, current value of Estimated-RTT is 0.4s, Sample-RTT is 0.8s, then the new value of Estimated-RTT is ____s.A 0.45B 0.6C 0.7D 0.831.Provided RcvBuffer=20,LastByteRcvd=20,LastByteRead=15, thenRcvWindow=____.A 14B 15C 16D 1032. TCP service does not provide____.A Reliable data transferB Flow controlC Delay guaranteeD Congestion control33. There are two states in TCP congestion control, which are ____.A slow start and congestion avoidanceB safe start and congestion avoidanceC slow start and congestion abandonD safe start and congestion abandon34. The transport-layer protocol provides logical communication between ____, and the network-layer protocol provides logical communication ____.A hosts, processesB processes, hostsC threads, processesD processes, threads35. To implement the multicast services the Internet employs the ____ protocol.A FTPB TCPC IGMPD UDP36. If an application developer chooses ____ protocol, then the application process is almost directly talking with IP.A HTTPB RIPC CSMA/CDD UDP37. ____ maintains connection-state in the end systems. This connection state includes receive and send buffers, congestion-control parameters, and sequence and acknowledgment number parameters.A UDPB TCPC DNSD HTTP38. The host that initiates the session in the Internet is labeled as ____.A serverB user agentC clientD router39. With TCP there is no _____ between sending and receiving transport-layer entities.A flow controlB handshakingC. congestion control D VC setup40. The Internet’s ____service helps prevent the Internet from entering a state of gridlock.A datagramB congestion controlC sliding windowD timeout event41. Connection setup at the transport layer involves ____.A serverB only the two end systemsC clientD router42. A ____layer protocol provides for logical communication between applications.A transportB applicationC networkingD MAC43. In static congestion window, if it satisfies W*S/R > RTT + S/R, the Latency is ____.A W*S/R – ( RTT+ S/R)B 2RTT + O/RC 2RTT + O/R + (k-1)[W* S/R- (RTT + S/R)]D 2RTT + S/R44. The receive side of transport layer reassembles segments into messages, passes to ____layer.A ApplicationB NetworkingC PhysicalD MAC45. In the following four options, which one is correct?A The variations in the SampleRTT are smoothed out in the computation of the EstimatedRTTB The timeout should be less than the connection’s RTTC Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≥1 secD Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≤1 sec46. The port number used by HTTP is ____.A 80B 25C 110D 5347. The port number used by SMTP is ____.A 80B 25C 110D 5348. The port number used by pop3 is ____.A 80B 25C 110D 5349. The port number used by DNS is ____.A 80B 25C 110D 5350. The port number used by FTP is ____.A 20 and 21B 20C 21D 5351. A UDP socket identified by a ____ tuple(s).A 2B 4C 1D 352. A TCP socket identified by a ____ tuple(s).A 2B 4C 1D 353. A TCP socket does not include____.A Source MAC addressB Source port numberC Destination IP addressD Destination port number54. Which of following about UDP is not correct.A It is a reliable data transfer protocolB It is connectionlessC no handshaking between UDP sender, receiverD it is a best effort service protocol55. DNS uses ____ service.A TCPB UDPC Both TCP and UDPD None of above56. Which of following about UDP is correct?A Finer application-level control over what data is sent, and whenB No connection establishment (which can add delay), so no delay for establish a connectionC No connection state (so, UDP can typically support many active clients)D Large packet header overhead (16-B)57. Streaming media uses a ____ service normally.A TCPB UDPC Both TCP and UDPD None of above58. The UDP header has only ____ fields.A 2B 4C 1D 359. Which of the following does not included in UDP header.A Source port numberB Destination port numberC ChecksumD Sequence number60. Which of the following is not a pipelining protocol.A Rdt1.0B Go-Back-NC Selective repeatD TCP61. In the following four descriptions about MSS and MTU, which one is not correct?A The MSS is the maximum amount of application-layer data in the segmentB The MSS is the maximum size of the TCP segment including headersC The MSS is typically set by MTUD The MTU means the largest link-layer frame62. The job of gathering data chunks, encapsulating each data chunk with header information to create segments and passing the segments to the network is called ____.A multiplexingB de-multiplexingC forwardingD routing63. In the following four descriptions about the relationship between the transport layer and the network layer, which one is not correct?A The transport-layer protocol provides logical communication between hostsB The transport-layer protocol provides logical communication between processesC The services that a transport-layer protocol can provide are often constrained by the service model of the network-layer protocolD A computer network may make available multiple transport protocols64. Suppose the following three 8-bit bytes: 01010101, 01110000, 01001100. What’s the 1s complement of the sum of these 8-bit bytes?A 00010001B 11101101C 00010010D 1000100065. The following four descriptions about multiplexing and de-multiplexing, which one is correct?A A UDP socket is identified by a two-tuples consisting of a source port number and a destination port number.B If two UDP segment have different source port number, they may be directed to the same destination process.C If two TCP segments with different source port number, they may be directed to the same destination process.D If two TCP segments with same destination IP address and destination port number, they must be the same TCP connection.66. UDP and TCP both have the fields except ____.A source port numberB destination port numberC checksumD receive window67. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [nextseqnum,base+N-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged68. Which of the following about TCP is not correct?A It is a connectionless protocolB Point-to-point protocolC Reliable, in-order byte steam protocolD Pipelined protocol69. Which of the following about TCP is not correct?A It is a connectionless protocolB full duplex data transfer protocolC connection-oriented protocolD flow controlled protocol70. The maximum amount of data that can be grabbed and placed in a segment is limited by the ____.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum71. The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host (the so-called____), and then will fit into a single link-layer frame.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum72. The MSS is the maximum amount of ____layer data in the segment, not the maximum size of the TCP segment including headers.A ApplicationB TransportC NetworkingD Link73. Which of the following field is not used for connection setup and teardown?A Sequence numberB TSTC SYND FIN74. ____ is the byte stream number of first byte in the segment.A Sequence numberB ACK numberC ChecksumD port number75. ____ is the byte sequence numbers of next byte expected from other side.A Sequence numberB ACK numberC ChecksumD port number76. Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide ____ acknowledgements.A CumulativeB SelectiveC SingleD Negative77. Fast retransmit means in the case that ____ duplicate ACK-s are received, the TCP sender resend segment before timer expires.A 3B 4C 5D 678. TCP____ means sender won’t overflow receiver’s buffer by tran smitting too much, too fast.A Flow controlB Congestion controlC Reliable data transferD Connection-oriented service79. TCP provides flow control by having the sender maintain a variable called the ____.A Receive windowB Congestion windowC Sliding windowD buffer80. How does TCP sender perceive congestion?A TimeoutB 3 duplicate ACK-sC Both A and BD None of above81. Transport protocols run in ____.A ServersB ClientsC RoutersD End systems82. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers83. Which service does UDP not provide?A multiplexingB de-multiplexingC error-detectionD error-correction84. There are three major events related to data transmission and retransmission in the TCP sender, which one is not in it?A data received from application aboveB de-multiplexing segmentC timer timeoutD ACK receipt85. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP86. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection87. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection88. Which service helps prevent the internet from entering a state of gridlock?A reliable data transferB flow controlC congestion controlD handshaking procedure89. The Internet’s _____is responsible for moving packets from one host to another.A application layerB transport layerC network layerD link layer90.In the following applications, which one is a bandwidth-sensitive application?A E-mailB web applicationC real-time audioD file transfer91. In the following applications, which one uses UDP?A E-mailB web applicationC file transferD DNS92. In the following four descriptions, which one is correct?A If one host’s transport layer uses TCP, then its network layer must use virtual-circuit network.B Datagram network provides connection serviceC The transport-layer connection service is implemented in the routerD The network-layer connection service is implemented in the router as well as in the end system.93.____ is a speeding-matching service---matching the rate which the sender is sending against the rate at which the receiving application is reading.A congestion controlB flow controlC sliding-window controlD variable control94. In the following four descriptions about Rcv-Window, which one is correct?A The size of the TCP RcvWindow never changes throughout the duration of the connectionB The size of the TCP RcvWindow will change with the size of the TCP RcvBufferC The size of the TCP RcvWindow must be less than or equal to the size of the TCP RcvBufferD Suppose host A sends a file to host B over a TCP connection, the number of unacknowledged bytes that A sends cannot exceed the size of the size of the RcvWindow.95. There are 6 flag fields. Which one is to indicate that the receiver should pass the data to the upper layer immediately?A PSHB URGC ACKD RST96. Suppose the TCP receiver receives the segment that partially or completely fills in gap in received data, it will ____.A immediately send ACKB immediately send duplicate ACKC wait some time for arrival of another in-order segmentD send single cumulative97. _____ imposes constrain on the rate at which a TCP sender can send traffic into the network.A sliding windowB congestion windowC receive windowD variable window98. Flow control and congestion control are same at that they all limit the rate of the sender, but differ in that ____.A flow control limits its rate by the size of RcvWindow, but congestion control by the traffic on the linkB congestion control limits its rate by the size of RcvWindow, but flow control by the traffic on the linkC flow control mainly is accomplished by the sender, but congestion control by the receiver.D flow control mainly is accomplished by the receiver, but congestion control bythe link.99. This job of delivering the data in a transport-layer segment to the correct socket is called ____.A multiplexingB de-multiplexingC forwardingD routing100. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [base, nextseqnum-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged101. ____ are the two types of transport services that the Internet provides to the applications.A TCP and UDPB connection-oriented and connectionless serviceC TCP and IPD reliable data transfer and flow control102. In the following descriptions about persistent connection, which one is not correct?A The server leaves the TCP connection open after sending a responseB Each TCP connection is closed after the server sending one objectC There are two versions of persistent connection: without pipelining and with pipeliningD The default mode of HTTP uses persistent connection with pipelining103. The field of Length in UDP segment specifies the length of ____.A the UDP segment, not including the headerB the UDP segment, including the headerC the UDP segment’s headerD the Length field104. In TCP segment header, which field can implement the reliable data transfer?A source port number and destination port numberB sequence number and ACK numberC urgent data pointerD Receive window105. In the following four descriptions about TCP connection management, which one is not correct?A Either of the two processes participating in a TCP connection can end the connectionB If the FIN bit is set to 1, it means that it wants to close the connectionC In the first two step of the three-way handshake, the client and server randomly choose an initial sequence numberD In the three segments of the three-way handshake, the SYN bit must be set to 1 106. Suppose host A sends two TCP segments back to back to host B over a TCP connection. The first segment has sequence number 42, and the second has sequence number 110. If the 1st is lost and 2nd arrives at host B. What will be the acknowledgment number?A 43B ACK42C 109D ACK1101.Consider sending an object of size O=500,000bytes from server to client. LetS=500 bytes and RTT=0.2s. Suppose the transport protocol uses static windows with window size 5. For a transmission rate of 100Kbps, determine the latency for sending the whole object. Recall the number of windows K=O/ WS), and there is K-1 stalled state (that is idle time gaps).2.Consider the following plot of TCP congestion window size as a function of time.Fill in the blanks as follow:a) The initial value of Threshold at the first transmission round is ____. b) The value of Threshold at the 11st transmission round is ____. c) The value of Threshold at the 21st transmission round is ____. d) After the 9th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKe) After the 19th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKf) During ____ transmission round, the 18th segment is sent.3.Consider the TCP reliable data transfer in the given graph. If in Segment 1’s Sequence number =10,data=“AC”, please fill in the following blanks. a) In Segment 2, ACK number=____;b) In Segment 3, Sequence number =____; data=“0123456789”c) If there are some bits corrupted in segment 3 when it arrives Host B, then the ACK number in Segment 5 is ____; and the ACK number in Segment 6 is ____.14 180 26 3000 2 6 4 8 10 12 16 20 22 240 28 32Congestion window sizeTransmission round48121612345674. The client A wants to request a Web page from Server B. Suppose the URL of the page is 172.16.0.200/experiment, and also it wants to receive French version of object. The time-sequence diagram is shown below, please fill in the blanks.12345Packet① to Packet③are TCP connection’s segment, then:Packet ①: SYN flag bit= aACK flag bit= bSequence number= 92Packet ②: SYN flag bit=1ACK flag bit= c Sequence number=100 Packet ③: SYN flag bit= d ACK flag bit=1Sequence number= e5. Consider sending an object of size O=100 Kbytes from server to client. Let S=536 bytes and RTT=100msec. Suppose the transport protocol uses static windows with window size W.(1) For a transmission rate of 25 kbps, determine the minimum possible latency. Determine the minimum window size that achieves this latency. (2) Repeat (1) for 100 kbps.6. Consider the following plot of TCP congestion window size as a function of time. Please fill in the blanks as below.a) The initial value of Threshold at the first transmission round is____. b) The value of Threshold at the 11th transmission round is_____. c) The value of Threshold at the 21st transmission round is_____.14 18 26 30 0 2 6 4 8 10 12 16 20 22 24 28 32 Congestion window sizeTransmission round481216d) After the 9th transmission round, _____ occurs.e) After the 19th transmission round, ____ are detected.。
Chapter3章课件

Transparent bridges(透明网桥)
In 1987, ISO approved it as an international standard. IEEE subdivided the data link layer into two sublayers:
LLC (Logical Link Control) MAC (Media Access Control)
Forwarding Learning(static forwarding tables, dynamic forwarding tables) :
How to build the dynamic forwarding tables? flooding、adding entries
Router (路由器)
Chapter 3 Underlying Technologies
— Network Protocol Analysis
School of Computer and Communication Engineering
Objectives
To discuss the need and use of connecting devices such as repeaters (hubs), bridges (two-layer switches), and routers (threelayer switches).
运筹学(英文版)

运筹学B(双语)复习纲要I 概念汇总1)运筹学模型的三要素2)LP标准形式3)(非)基变量(入基变量、出基变量)4)基解、基可行解、解基逆矩阵5)退化6)人工变量法、两阶段法7)LP解的四种情况8)LP对偶问题的形式及最优解9)LP对偶问题的经济解释10)运输表格及表上作业法((非)基变量、入基变量、出基变量)11)网络的基本概念(点、边、权、有向边、链、道路、圈、回路、树、生成树、最小生成树、连通图、割)12)目标规划的含义(模型、偏差变量)13)整数规划模型(分支定界法、割平面法的思路)II 方法汇总1)LP问题图上求解法2)单纯形法3)对偶单纯形法4)运输问题表上作业法(三大步骤)5)求最小生成树6)求最短路问题7)求最大流问题8)目标规划的图解法9)中国邮路问题III题型1)多选题:20分左右2)判断题:10分左右3)简答题:30分左右4)计算题:50分左右《运筹学B》双语课程词汇表Chapter 1 What is Operations Research?Operations Research 运筹学Mathematic model 数学模型decision alternative 决策选择decision variable 决策变量restriction,constraint 约束条件objective criterion 目标准则objective function 目标函数linear programming 线性规划integer programming 整数规划dynamic programming 动态规划network programming 网络规划nonlinear programming 非线性规划algorithm 算法iteration 迭代Chapter 2 Introduction to Linear Programming Graphical solution 图解法Graphical sensitivity analysis 图上灵敏度分析nonnegativity restrictions 非负约束条件feasible solution 可行解optimal feasible solution 最优可行解coefficient 系数denominator 分母infeasible 不可行unit worth 单位价值Chapter 3 The Simplex Methodsolution space 解空间algebraic solution 代数解graphical solution 几何解optimal solution 最优解equation 方程corner point 顶点basic variable 基变量nonbasic variable 非基变量basic solution 基解The Simplex Method 单纯形法iterative 迭代的origin 原点leaving variable 出基变量entering variable 入基变量ratio 比率Gauss-Jordan row operation 高斯-约当行变换pivot column 主列pivot row 主行pivot element 主元素artificial variable 人工变量M-Method 大M方法Two-Phase Method 两阶段方法penalty 罚数degeneracy 退化degenerate 退化的alternative optima 多重最优解infinity 无穷unbounded 无界的pseudo-optimal solution 伪解Chapter 4 Duality and Sensitivity Analysis dual problem 对偶问题primal problem 原问题matrix 矩阵vector 向量identity matrix 单位矩阵verify 证明dual simplex method 对偶单纯形法generalized simplex method 广义单纯形法Chapter 5 Transportation Model and Its Variants Transportation Model 运输模型nontraditional Transportation Model 非典型运输模型The Transportation Algorithm 运输算法source 出发地destination 目的地node 节点arc 边,弧transportation tableau 运输表格balanced 平衡的Northwest-Corner Method 西北角法Least-Cost Method 最小费用法V ogel Approximation Method 沃格尔法The Assignment Model 指派模型Hungarian Method 匈牙利方法Chapter 6 Network Modelsnetwork 网络Minimal Spanning Algorithm 最小生成树算法Shortest-Route Algorithm 最短路算法path 链connected network 连通网络cycle 回路spanning tree 生成树maximal flow 最大流residue network 剩余网络breakthrough path 关键路线Chapter 8 Goal Programminggoal programming 目标规划deviational variable 偏差变量Chapter 9 Integer Linear ProgrammingInteger Linear Programming 整数线性规划integer variables 整数变量Cutting-Plane Algorithm 割平面法B&B Algorithm 分支定界法。
TRANSLITE GLOBAL LLC TL-9228S多通道编码器用户手册说明书

DISCLAIMERNo part of this document may be reproduced in any form without the written permission of the copyright owner.The contents of this document are subject to revision without notice due to continued progress in methodology, design and manufacturing. TRANSLITE GLOBAL LLC shall have no liability for any error or damage of any kind resulting from the use of this document.COPY WARNINGThis document includes some confidential information. Its usage is limited to the owners of the product that it is relevant to. It cannot be copied, modified, or translated in another language without prior written authorization from TRANSLITE GLOBAL LLCPRODUCT MODEL NUMBER: TL-9228S MULTI-CHANNEL ENCODERABOUT THIS MANUALINDEXTABLE OF CONTENTSCHAPTER 1 INTRODUCTION (3)1.1PRODUCT OVERVIEW (3)1.2KEY FEATURES (3)1.3SPECIFICATIONS (4)1.4PRINCIPLE CHART (5)1.5APPEARANCE AND DESCRIPTION (6)CHAPTER 2 INSTALLATION GUIDE (7)2.1ACQUISITION CHECK (7)2.2INSTALLATION PREPARATION (8)2.3DEVICE’S INSTALLATION FLOW CHART ILLUSTRATED AS FOLLOWING (8)2.4ENVIRONMENT REQUIREMENT (9)2.5GROUNDING REQUIREMENT (9)2.5.1FRAME GROUNDING (10)2.5.2DEVICE GROUNDING (10)2.6WIRE’S CONNECTION (10)2.7SIGNAL CABLE CONNECTION (11)2.7.1HDMI INPUT CABLE ILLUSTRATION (11)2.7.2NETWORK CABLE ILLUSTRATION(CAT5) (12)CHAPTER 3 WEB NMS OPERATION (12)3.1LOGIN (12)3.2OPERATION (13)CHAPTER 4 TROUBLESHOOTING (20)CHAPTER 5 PACKING LIST (21)CHAPTER 1INTRODUCTION1.1 PRODUCT OVERVIEWTL-9228S multi-channel encoder is a professional HD/SD audio & video encoding device. It has 8/16/24 HDMI inputs for option. Every 8 HDMI ports share one encoder module with each module supporting 1MPTS and 8SPTS output. Its high integration and cost-effective design make the device widely used in varieties of digital distribution systems such as cable TV digital head-end, digital TV broadcasting etc.1.2 KEY FEATURES➢8 HDMI inputs with 8 SPTS and 1 MPTS output (each encoder module), max 24 HDMI inputs➢MPEG4 AVC/H.264 video encoding format➢MPEG1 Layer II, LC-AAC,HE-AAC audio encoding format and AC3 Pass Through, and audio gain adjustment➢IP output over UDP and RTP/RTSP protocol; 1 ASI out as mirror of MPTS (Optional)➢Support QR code, LOGO, caption insertion➢Support “Null PKT Filter” function➢Control via web management, and easy updates via web1.3 SPECIFICATIONS1.4 PRINCIPLE CHART1.5 APPEARANCE AND DESCRIPTION Front Panel Illustration1 2 3Rear Panel Illustration1 2CHAPTER 2INSTALLATION GUIDEThis section is to explain the cautions the users must know in some case that possibly injure may bring to users when it’s used or installed. For this reason, please read all details here and make in mind before installing or using the product.2.1 ACQUISITION CHECKWhen users open the package of the device, it is necessary to check items according to packing list. Normally it should include the following items:➢TL-9228S Multi-Channel Encoder➢User’s Manual➢Power Cord➢HDMI cablesIf any item is missing or mismatching with the list above, please contact local dealer.2.2 INSTALLATION PREPARATIONWhen users install device, please follow the below steps. The details of installation will be described at the rest part of this chapter. Users can also refer rear panel chart during the installation.The main content of this chapter including:➢Checking the possible device missing or damage during the transportation ➢Preparing relevant environment for installation➢Installing Encoder➢Connecting signal cables➢Connecting communication port (if it is necessary)2.3 DEVICE’S INSTALLATION FLOW CHARTILLUSTRATED AS FOLLOWING2.4 ENVIRONMENT REQUIREMENT2.5 GROUNDING REQUIREMENT➢All function modules’ good grounding is the basis of reliability and stability of devices. Also, they are the most important guarantee of lightning arresting and interference rejection.Therefore, the system must follow this rule.➢Coaxial cable’s outer conductor and isolation layer should keep proper electric conducting with the metal housing of device.➢Grounding conductor must adopt copper conductor in order to reduce high frequency impedance, and the grounding wire must be as thick and short as possible.➢Users should make sure the 2 ends of grounding wire well electric conducted and be antirust.➢It is prohibited to use any other device as part of grounding electric circuit➢The area of the conduction between grounding wire and device’s frame should be no less than 25mm2.2.5.1 FRAME GROUNDINGAll the machine frames should be connected with protective copper strip. Thegrounding wire should be as short as possible and avoid circling. The area ofthe conduction between grounding wire and grounding strip should be no lessthan 25mm2.2.5.2 DEVICE GROUNDINGConnecting the device’s grounding rod to frame’s grounding pole with copperwire.2.6 WIRE’S CONNECTIONThe grounding wire conductive screw is located at the right end of rear panel, and the power switch, fuse, power supply socket is just besides, whose order goes like this, power switch is on the left, power supply socket is on the right and the fuse is just between them.➢Connecting Power Cord➢User can insert one end into power supply socket, while insert the other end to AC power.➢Connecting Grounding Wire➢When the device solely connects to protective ground, it should adopt independent way, say, share the same ground with other devices. When thedevice adopts united way, the g rounding resistance should be smaller than 1Ω.☞Caution:Before connecting power cord to TL-9228S Multi-Channel Encoder, user should set the power switch to “OFF”.2.7 SIGNAL CABLE CONNECTIONThe signal connections include the connection of input signal cable and the connection of output signal cable. The details are as follows:2.7.1 HDMI INPUT CABLE ILLUSTRATION2.7.2 NETWORK CABLE ILLUSTRATION(CAT5)CHAPTER 3WEB NMS OPERATION3.1 LOGINThe default IP address of this device is 192.168.0.136.Connect the PC (Personal Computer) and the device with net cable and use ping command to confirm they are on the same network segment.I.G. the PC IP address is 192.168.99.252, we then change the device IP to 192.168.99.xxx (xxx can be 0 to 255 except 252 to avoid IP conflict).Use web browser to connect the device with PC by inputting the Encoder’s IP address in the browser’s address bar and press Enter.It will display the Login interface as Figure-1. Input the Username and Password (Both the default Username and Password are “admin”.) and then click “LOGIN” to start the device setting.3.2 OPERATIONWelcomeWhen we confirm the login, it displays the WELCOME interface as Figure-2.System informationUser can click any itemhere to enter thecorresponding interfaceto check information orset the parameters.Figure-2Parameters →EncoderEncode Channel 1-8:From the menu on upper side of the web page, clicking “Enc CH 1-8”, it will display the each encode channel information of the program from the HDMI input port as Figure-3.Figure-3Click this button to apply the modified parameters.Parameters →IP StreamTL-9228S supports TS to output in IP (1MPTS and 8 SPTS) format through the DATA port. When users click “IP Stream”, it will display the interface as Figure-4 where to set IP out parameters. (For Data 1000M GE port)Figure-4Parameters →OSDClicking “OSD ”, it will display the interface where to configuration the OSD parameters as Figure-5/6/7.Figure-5Figure-6Figure-7System→ Network:Clicking “Network”, it will display the interface as Figure-8 where to set NMS and DATAparameters.Figure-8System → Account:C licking “Account”, it will display the screen as Figure-9 where to set the login account andpassword for the web NMS. Both the current username and password are “admin”.Figure-9System → Configuration:Clicking “Configuration”, it will display the screen as Figure-10 where to save/ restore/factoryset/ backup/ load your configurations.Figure-10System → Firmware:Clicking “Firmware”, it will display the screen as Figure-11 where to update firmware for theencoder.Figure-11System → Date/Time:Clicking “Date/Time”, it will display the screen as Figure-12 where to set date and time for thedevice.Figure-12System → Log:Clicking “Log”, it will display the log interface as Figure-13 where to check or export theKernel/System log.Figure-13CHAPTER 4TROUBLESHOOTINGAll Translite Global products have been passed the testing and inspection before shipping out from factory. The testing and inspection scheme already covers all the Optical, Electronic and Mechanical criteria which have been published by Translite Global. To prevent potential hazard, please strictly follow the operation conditions.Prevention Measure➢Installing the device at the place in which environment temperature between 0 to 45 °C ➢Making sure good ventilation for the heat-sink on the rear panel and other heat-sink bores if necessary➢Checking the input AC within the power supply working range and the connection iscorrect before switching on device➢Checking the RF output level varies within tolerant range if it is necessary➢Checking all signal cables have been properly connected➢Frequently switching on/off device is prohibited; the interval between every switching on/off must greater than 10 seconds.Conditions need to unplug power cord➢Power cord or socket damaged.➢Any liquid flowed into device.➢Any stuff causes circuit short➢Device in damp environment➢Device was suffered from physical damage➢Longtime idle.➢After switching on and restoring to factory setting, device still cannot work properly.➢Maintenance neededCHAPTER 5PACKING LIST。
Samstock V48用户手册说明书

U sers ManualPC Software Samstock V48 user ManualC ontentsC hapter 1 – WelcomeC HECK ON WHAT YOU NEED____________________________________________________12 C hapter 2 – InstallingI NSTALLING_______________________________________________________________14 I NSTALLATION O PTIONS______________________________________________________19 F IRST T IME L OAD___________________________________________________________20 L OADING_________________________________________________________________21 L ICENSING________________________________________________________________22 M ODULE L ICENSING_________________________________________________________22 N AVIGATION_______________________________________________________________24 C hapter 3 – Register Configuration SettingsI NITIAL C OMPANY D ETAILS____________________________________________________25 C ASH R EGISTER D ETAILS_____________________________________________________26 M ODEM D ETAILS____________________________________________________________27 E ASY 2T OUCH COMMUNICATIONS_______________________________________________28 S ENTINEL N ETWORK S ET-UP –XP P RO___________________________________________30 S ENTINEL N ETWORK F ILE S HARING______________________________________________31 O N ALL TERMINALS (S HARING H ARD D RIVE)______________________________________31 O N ALL T ERMINALS (M APPING THE D RIVE)_______________________________________31 N ETWORK F ILE S HARING –S ENTINEL____________________________________________32 S ETTING THE D ATA L OCATIONS (EXCEPT T ERMINAL 1)______________________________32 S ETTING T ERMINALS FOR CONSOLIDATION_______________________________________32 S ENTINEL PC C ONNECTION S ETUP______________________________________________33 S ETTING UP C ONNECTION T O S AMSTOCK._______________________________________33 L OADING THE S ENTINEL PC C OMMUNICATIONS P ROGRAM___________________________33 S ENTINEL E THERNET S ETUP___________________________________________________34 A UTO L OAD THE E THERNET S AMSTOCK FTP_____________________________________34 C ONFIGURING E THERNET FTP S ERVER T ERMINAL 01_______________________________34S AMSTOCK E THERNET S ETUP__________________________________________________35 S ETTING THE FTP S ERVER FOR E THERNET______________________________________35 S ENTINEL AND ICR T OUCH M ODEM S ETUP________________________________________36 I NSTALLING THE M ODEM____________________________________________________36 S ENTINEL AND ICR T OUCH M ODEM S ETUP________________________________________37 C ONFIGURING T ERMINAL01 FOR INCOMING CALLS__________________________________37 S AMSTOCK M ODEM S ETUP____________________________________________________38 I NSTALLING THE M ODEM____________________________________________________38 S AMSTOCK SPS2000E THERNET C ONNECTION_____________________________________39 S AMSTOCK RAS C ONNECTION S ETUP____________________________________________41 C ONFIGURING THE RAS CONNECTION FOR SPS2000_______________________________41 C ONFIGURING THE RAS CONNECTION FOR S ENTINEL_______________________________48 S AMSTOCK TO S ENTINEL M ODEM S ETUP__________________________________________49 S ETTING THE FTP S ERVER FOR M ODEM C ONNECTION.______________________________49 S AMSTOCK TO ICR T OUCH S ETUP______________________________________________50 S ETTING THE IP ADDRESS.___________________________________________________50 C OLLECTING PRE-PROGRAMMED ECR D ATA_____________________________________51 S AM E VENT________________________________________________________________52C hapter 4 – Customising SettingsC USTOMISING S ECURITY L EVELS_______________________________________________53 S AMSTOCK O PTIONS_______________________________________________________55 P RODUCT F ILE O PTIONS____________________________________________________56 P RODUCT F ILE O PTIONS____________________________________________________57 L OCATION O PTIONS________________________________________________________58 S HELF E DGE L ABEL O PTIONS________________________________________________59 O RDER /T RANSFER O PTIONS________________________________________________60 R EPORT O PTIONS_________________________________________________________61 C USTOMISING F INANCIALD ATA_________________________________________________62 C USTOMISING S TAFF S ALES D ATA______________________________________________65C USTOMISING S TAFF S ALESD ATA______________________________________________66 C USTOMISING H OURLY S ALES D ATA_____________________________________________68 C USTOMISING V AT R ATES_____________________________________________________69C hapter 5 – Product CreationS UPPLIERS________________________________________________________________71 C LASSIFICATION GROUPS_____________________________________________________73 P RODUCT G ROUPS__________________________________________________________74 S TOCK U NITS______________________________________________________________75 S ALES UNITS______________________________________________________________76 P RODUCTS________________________________________________________________77 P RODUCT D ETAILS________________________________________________________78 P RODUCT P RICING________________________________________________________79 P RODUCT S TOCK_________________________________________________________80 P RODUCT O PTIONS________________________________________________________81 P RODUCT M ONITOR L INES___________________________________________________83 P RODUCT P ICTURE________________________________________________________84 P RODUCT R ECIPES__________________________________________________________85 S ALEABLE ITEM R ECIPES____________________________________________________86 S TOCK R ECIPES__________________________________________________________86 M IX &M ATCH______________________________________________________________89 M IX &M ATCH –S ENTINEL V ERSION 8____________________________________________90 M IX &M ATCH -ICR_________________________________________________________91 M ONITOR L INES____________________________________________________________92C hapter 6 – ECR Product ManagementE ASY 2T OUCH S CREEN M ANAGEMENT___________________________________________93A DDING A N EWB UTTON_____________________________________________________94B UTTON R E-S IZING________________________________________________________94 B UTTON M OVEMENT_______________________________________________________94 B UTTONC OPY___________________________________________________________94 E ASY 2T OUCH C ATEGORIES___________________________________________________95SPS1000/SER-7000–WLU’S_______________________________________________96 SPS1000/SER-7000–S TATUS G ROUPS________________________________________97 SPS1000/SER-7000-K EYBOARD_____________________________________________98 S ENTINEL –S CREEN M ANAGEMENT_____________________________________________99 SPS2000S CREEN D ESIGNER_________________________________________________101 ICR T OUCH –ECR P ROGRAMMING_____________________________________________102C hapter 7 – Email and SMS NotificationsE MAIL A CCOUNT S ETUP_____________________________________________________112 SMS A CCOUNT S ETUP______________________________________________________106 U SER DETAILS____________________________________________________________107 U SER N OTIFICATION G ROUPS_________________________________________________107 SMSF INANCIAL S ETUP_____________________________________________________108 S AM E VENT E MAIL AND SMS S ETUP____________________________________________118C hapter 8 – SameventS AM E VENT -E XECUTE______________________________________________________112 S AM E VENT E XECUTE AN IMMEDIATE TASK________________________________________114 S AM E VENT C REATING A TIMETABLE EVENT_______________________________________115 S AM E VENT E VENTS L ISTING__________________________________________________116 S AM E VENT -L OG__________________________________________________________117 S ALES D ATA R E-FILE______________________________________________________117 S AM E VENT_______________________________________________________________118C hapter 9 – Reporting InformationR EPORTING N AVIGATION_____________________________________________________119 R EPORTING N AVIGATION_____________________________________________________120 R EPORT F ORMAT________________________________________________________121 R EPORT O PTIONS__________________________________________________________122 D ATE R ANGE___________________________________________________________124 L OCATIONS_____________________________________________________________124 R EPORT C RITERIA_________________________________________________________125 P RODUCT G ROUP________________________________________________________125 R EPORT M ENU B AR_______________________________________________________125 R EPORT P RINTING________________________________________________________126 A UTO E XCEL O UTPUT_____________________________________________________126 R EPORT P RINTING O PTIONS__________________________________________________127 C HART D ISPLAY_________________________________________________________127 X R EPORTS_____________________________________________________________128C hapter 10 – Register Sales Journal ReportingE ASY 2T OUCH AND S ENTINEL J OURNAL_________________________________________129V IEW_________________________________________________________________130 S ORTING THE I NFORMATION_________________________________________________131 F ILTERING THE INFORMATION________________________________________________132SPS-1000/2000/7000J OURNAL______________________________________________132 ICR T OUCH J OURNAL_______________________________________________________134 C hapter 11 – Stock PurchasingS TOCK M ANAGEMENT_______________________________________________________135O RDERS_______________________________________________________________136 D ELIVERIES_____________________________________________________________136 P URCHASES____________________________________________________________136 T RANSFERS FROM ONE LOCATION TO ANOTHER__________________________________136 W RITE-OFFS____________________________________________________________136 R EVIEWING I NVOICES_____________________________________________________136 S TOCK M ANAGEMENT_______________________________________________________137 M ETHOD 1-U SING S UGGESTED RE-ORDER LEVELS_____________________________137 O RDER________________________________________________________________137 D ELIVERY______________________________________________________________137 P URCHASE_____________________________________________________________137 M ETHOD 2-M ANUALLY E NTERED RE-ORDER LEVELS___________________________138 O RDER________________________________________________________________138 D ELIVERY______________________________________________________________138 P URCHASE_____________________________________________________________138 M ETHOD 3-N O ORDERS BUT DELIVERY & PURCHASE ENTRY______________________138 D ELIVERY______________________________________________________________138 P URCHASE_____________________________________________________________138M ETHOD 4-P URCHASE ENTRY ONLY._______________________________________138 P URCHASE_____________________________________________________________138 S TOCK M ANAGEMENT_______________________________________________________139 S TOCK M ANAGEMENT N AVIGATION___________________________________________139 M AIN I CONS____________________________________________________________139 O RDERS/D ELIVERY/P URCHASE________________________________________________140 M AIN S CREEN___________________________________________________________140 S UPPLIER D ETAILS_______________________________________________________140 P RODUCT D ETAILS_______________________________________________________141 R EVIEW INVOICES__________________________________________________________142 W RITE OFF STOCK________________________________________________________143 T RANSFERRING S TOCK______________________________________________________144C hapter 12 – Stock TakingS TOCK T AKING PROCEDURE__________________________________________________145 U PDATE CURRENT STOCK MOVEMENTS_________________________________________146 T AKE S TOCK S NAPSHOT___________________________________________________146 P HYSICALLY COUNT STOCK ITEMS____________________________________________146 E NTER S TOCK T AKE______________________________________________________146 A NALYSE RESULTS OF STOCK COUNT__________________________________________146 O PTIONALLY S ET O PENING S TOCK____________________________________________146 M ONTHLY S TOCK T AKING P ROCEDURE________________________________________147 S TOCK T AKING S NAPSHOT__________________________________________________148 E NTERING S TOCK T AKE____________________________________________________149 R EPORTING STOCK T AKE RESULTS____________________________________________150 U PDATE C URRENT STOCK__________________________________________________151 C hapter 13 – Management System SettingsG LOBAL P RICE C HANGE_____________________________________________________153 S YSTEM T ASKS___________________________________________________________156C hapter 14 – Data BackupB ACKING U P DATA_________________________________________________________157C hapter 15 – Import / ExportI MPORT M ODULE___________________________________________________________164 G ROUP C LASSIFICATION___________________________________________________165 P RODUCT G ROUP________________________________________________________165 F ULL P RODUCT D ETAILS___________________________________________________166 P RODUCT S TOCK________________________________________________________167 P RODUCT P RICE_________________________________________________________167 P RODUCT P OINTS (SPS-1000/SER-7000)_____________________________________167 S UPPLIER D ETAILS_______________________________________________________168 P RODUCT S TOCK R EFERENCE_______________________________________________168 S TAFF D ETAILS__________________________________________________________168E XPORT M ODULE__________________________________________________________169F ILENAME:C LASS.SES____________________________________________________170 F ILENAME:P RODUCT D AY.SES______________________________________________170 F ILENAME:P RODUCT F ULL.SES______________________________________________171 F ILENAME:P RODUCT S TOCK.SES____________________________________________171 F ILENAME:P RODUCT P RICE.SES_____________________________________________172 F ILENAME:S TAFF.SES____________________________________________________172 F ILENAME:S UPPLIER.SES__________________________________________________172C hapter 16 – ModulesS AGE L INE 50A CCOUNTING MODULE___________________________________________173C USTOMISING THE S AGE I MPORT_____________________________________________174 G ENERATING T HE S AGE I MPORT F ILE__________________________________________175 V IEWING T HE S AGE I MPORT F ILE_____________________________________________175S AGE L INE 50A CCOUNTING MODULE___________________________________________176I MPORTING THE F ILE I NTO S AGE_____________________________________________176 S UCCESSFUL IMPORT SCREEN_______________________________________________176 D ELETING T HE I MPORTED F ILE_______________________________________________177 S PEDI O RDERING M ODULE___________________________________________________178S ETTING U P THE N ISA L INK_________________________________________________178S PEDI O RDERING M ODULE___________________________________________________179 S ETTING U P THE N ISA S CHEMES_______________________________________________179 S ENDING AN O RDER______________________________________________________181 C OLLECTING P RODUCTS___________________________________________________181 S PEDI O RDERING M ODULE___________________________________________________182 CJ L ANG W HOLESALE E LECTRONIC T RANSFER____________________________________183 C ONSOLIDATING S TOCK_____________________________________________________185 H AND H ELD T ERMINAL MODULE_______________________________________________186 S ENDING F ILES__________________________________________________________187 R ESET HHT____________________________________________________________187 S END P RODUCTS________________________________________________________187 H EAD O FFICE T O B RANCH F ILE T RANSFER_______________________________________188 S ALES F ORMAT__________________________________________________________190 P RODUCT M AINTENANCE F ORMAT____________________________________________191This is a “Table of Contents preview” for quality assuranceThe full manual can be found at /estore/catalog/ We also offer free downloads, a free keyboard layout designer, cable diagrams, free help andsupport. : the biggest supplier of cash register and scale manuals on the net。
计算机网络英文题库(附答案)chapter3解析

计算机⽹络英⽂题库(附答案)chapter3解析Chapter 3 Transport Layer1. A transport-layer protocol provides for logical communication between ____.A Application processesB HostsC RoutersD End systems2. Transport-layer protocols run in ____.A ServersB ClientsC RoutersD End systems3. In transport layer, the send side breaks application messages into ____, passes to network layer.A FramesB SegmentsC Data-gramsD bit streams4. Services provided by transport layer include ____.A HTTP and FTPB TCP and IPC TCP and UDPD SMTP5. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers6. These two minimal transport-layer services----____ and ____----are the only two services that UDP provides!A process-to-process data delivery, error checkingB congestion control, reliable data transferC flow control, congestion controlD In-order data transfer, error checking7. Port number’s scop e is ____ to ____.A 0, 1023B 0, 65535C 0, 127D 0,2558. The port numbers ranging from ____to ____ are called well-known port number and are restricted.A 0, 1023B 0, 65535C 0, 127D 0,2559. UDP socket identified by two components, they are ____.A source IP addresses and source port numbersB source IP addresses and destination IP addressesC destination IP address and destination port numbersD destination port numbers and source port numbers10. TCP socket identified by a (an) ____.A 1-tupleB 2-tupleC 3-tupleD 4-tuple11. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP12. Reliable data transfer protocol over a perfectly reliable channel is____.A rdt1.0B rdt2.0C rdt3.0D rdt2.113. Reliable data transfer protocol over a channel with bit errors and packet losses is _ ___.A rdt1.0B rdt2.0C rdt3.0D rdt2.114. Which of the following about reliable data transfer over a channel with bit errors i s not correct?A RDT2.0: assuming ACK and NAK will not be corruptedB RDT2.1: assuming ACK and NAK can be corruptedC RDT2.2: only use ACK-sD RDT2.2: use both ACK-s and NAK-s15. Which of the following protocols is not pipelining protocols?A TCPB rdt3.0C GO-BACK-ND selective repeat16. Which of the following is not correct about GBN protocol?A Only using ACK-sB Using cumulative ACK-sC Receiver discards all out-of-order packetsD It is not pipelined protocol17. Which of the following is not correct about SR protocol?A receiver individually acknowledges all correctly received packetsB sender only resends packets for which ACK not receivedC It limits sequence number of sent but un-ACK-ed packetsD It is not a pipelined protocol18. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection19. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection20. The FIN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection21.How does TCP sender perceive congestion?A Through a timeout eventB Through a receiving duplicate ACK-s eventC Both A and BD Either A or B22. Extending host-to-host delivery to process-to-process delivery is called transport-layer ____ and .A multiplexing and de-multiplexingB storing and forwardingC forwarding and filteringD switching and routing23. UDP is a ____ service while TCP is a connection-oriented service.A ConnectionlessB ReliableC Connection-orientedD In-order24. The UDP header has only four fields, they are____.A Source port number, destination port number, length and checksumB Source port number, destination port number, source IP and destination IPC source IP, destination IP, source MAC address and destination MAC addressD source IP, destination IP, sequence number and ACK sequence number25. There are two 16-bit integers: 1110 0110 0110 0110, 1101 0101 0101 0101. Their checksum is____.A 0100010001000011B 1011101110111100C 1111111111111111D 100000000000000026.The maximum amount of data that can be grabbed and placed in a segment is limited by the____.A Maximum segment size (MSS)B MTUC ChecksumD Sequence number27.The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host----the so-called____.A Maximum transmission unit (MTU)B MSSC ChecksumD Sequence number28. A File size of 500,000bytes, MSS equals 1000bytes. When we want to transmit this file with TCP, the sequence number of the first segment is 0, and the sequence number of the second segment is ____.A 1000B 999C 1001D 50000029.Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide____.A Cumulative acknowledgementsB Selective acknowledgementsC 3 duplicate ACKsD positive ACKs30. Provided α=0.125, current value of Estimated-RTT is 0.4s, Sample-RTT is 0.8s, then the new value of Estimated-RTT is ____s.A 0.45B 0.6C 0.7D 0.831.Provided RcvBuffer=20,LastByteRcvd=20,LastByteRead=15, thenRcvWindow=____.A 14B 15C 16D 1032. TCP service does not provide____.A Reliable data transferB Flow controlC Delay guaranteeD Congestion control33. There are two states in TCP congestion control, which are ____.A slow start and congestion avoidanceB safe start and congestion avoidanceC slow start and congestion abandonD safe start and congestion abandon34. The transport-layer protocol provides logical communication between ____, and the network-layer protocol provides logical communication ____.A hosts, processesB processes, hostsC threads, processesD processes, threads35. To implement the multicast services the Internet employs the ____ protocol.A FTPB TCPC IGMPD UDP36. If an application developer chooses ____ protocol, then the application process is almost directly talking with IP.A HTTPB RIPC CSMA/CDD UDP37. ____ maintains connection-state in the end systems. This connection state includes receive and send buffers, congestion-control parameters, and sequence and acknowledgment number parameters.A UDPB TCPC DNSD HTTP38. The host that initiates the session in the Internet is labeled as ____.A serverB user agentC clientD router39. With TCP there is no _____ between sending and receiving transport-layer entities.A flow controlB handshakingC. congestion control D VC setup40. The Internet’s ____service helps prevent the Internet from entering a state of gridlock.A datagramB congestion controlC sliding windowD timeout event41. Connection setup at the transport layer involves ____.A serverB only the two end systemsC clientD router42. A ____layer protocol provides for logical communication between applications.A transportB applicationC networkingD MAC43. In static congestion window, if it satisfies W*S/R > RTT + S/R, the Latency is ____.A W*S/R – ( RTT+ S/R)B 2RTT + O/RC 2RTT + O/R + (k-1)[W* S/R- (RTT + S/R)]D 2RTT + S/R44. The receive side of transport layer reassembles segments into messages, passes to ____layer.A ApplicationB NetworkingC PhysicalD MAC45. In the following four options, which one is correct?A The variations in the SampleRTT are smoothed out in the computation of the EstimatedRTTB The timeout should be less than the connection’s RTTC Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≥1 secD Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≤1 sec46. The port number used by HTTP is ____.A 80B 25C 110D 5347. The port number used by SMTP is ____.A 80B 25C 110D 5348. The port number used by pop3 is ____.A 80B 25C 110D 5349. The port number used by DNS is ____.A 80B 25C 110D 5350. The port number used by FTP is ____.A 20 and 21B 20C 21D 5351. A UDP socket identified by a ____ tuple(s).A 2B 4C 1D 352. A TCP socket identified by a ____ tuple(s).A 2B 4C 1D 353. A TCP socket does not include____.A Source MAC addressB Source port numberC Destination IP addressD Destination port number54. Which of following about UDP is not correct.A It is a reliable data transfer protocolB It is connectionlessC no handshaking between UDP sender, receiverD it is a best effort service protocol55. DNS uses ____ service.A TCPB UDPC Both TCP and UDPD None of above56. Which of following about UDP is correct?A Finer application-level control over what data is sent, and whenB No connection establishment (which can add delay), so no delay for establish a connectionC No connection state (so, UDP can typically support many active clients)D Large packet header overhead (16-B)57. Streaming media uses a ____ service normally.A TCPB UDPC Both TCP and UDPD None of above58. The UDP header has only ____ fields.A 2B 4C 1D 359. Which of the following does not included in UDP header.A Source port numberB Destination port numberC ChecksumD Sequence number60. Which of the following is not a pipelining protocol.A Rdt1.0B Go-Back-NC Selective repeatD TCP61. In the following four descriptions about MSS and MTU, which one is not correct?A The MSS is the maximum amount of application-layer data in the segmentB The MSS is the maximum size of the TCP segment including headersC The MSS is typically set by MTUD The MTU means the largest link-layer frame62. The job of gathering data chunks, encapsulating each data chunk with header information to create segments and passing the segments to the network is called ____.A multiplexingB de-multiplexingC forwardingD routing63. In the following four descriptions about the relationship between the transport layer and the network layer, which one is not correct?A The transport-layer protocol provides logical communication between hostsB The transport-layer protocol provides logical communication between processesC The services that a transport-layer protocol can provide are often constrained by the service model of the network-layer protocolD A computer network may make available multiple transport protocols64. Suppose the following three 8-bit bytes: 01010101, 01110000, 01001100. What’s the 1s complement of the sum of these 8-bit bytes?A 00010001B 11101101C 00010010D 1000100065. The following four descriptions about multiplexing and de-multiplexing, which one is correct?A A UDP socket is identified by a two-tuples consisting of a source port number and a destination port number.B If two UDP segment have different source port number, they may be directed to the same destination process.C If two TCP segments with different source port number, they may be directed to the same destination process.D If two TCP segments with same destination IP address and destination port number, they must be the same TCP connection.66. UDP and TCP both have the fields except ____.A source port numberB destination port numberC checksumD receive window67. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [nextseqnum,base+N-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged68. Which of the following about TCP is not correct?A It is a connectionless protocolB Point-to-point protocolC Reliable, in-order byte steam protocolD Pipelined protocol69. Which of the following about TCP is not correct?A It is a connectionless protocolB full duplex data transfer protocolC connection-oriented protocolD flow controlled protocol70. The maximum amount of data that can be grabbed and placed in a segment is limited by the ____.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum71. The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host (the so-called____), and then will fit into a single link-layer frame.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum72. The MSS is the maximum amount of ____layer data in the segment, not the maximum size of the TCP segment including headers.A ApplicationB TransportC NetworkingD Link73. Which of the following field is not used for connection setup and teardown?A Sequence numberB TSTC SYND FIN74. ____ is the byte stream number of first byte in the segment.A Sequence numberB ACK numberC ChecksumD port number75. ____ is the byte sequence numbers of next byte expected from other side.A Sequence numberB ACK numberC ChecksumD port number76. Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide ____ acknowledgements.B SelectiveC SingleD Negative77. Fast retransmit means in the case that ____ duplicate ACK-s are received, the TCP sender resend segment before timer expires.A 3B 4C 5D 678. TCP____ means sender won’t overflow receiver’s buffer by tran smitting too much, too fast.A Flow controlB Congestion controlC Reliable data transferD Connection-oriented service79. TCP provides flow control by having the sender maintain a variable called the ____.A Receive windowB Congestion windowC Sliding windowD buffer80. How does TCP sender perceive congestion?A TimeoutB 3 duplicate ACK-sC Both A and BD None of above81. Transport protocols run in ____.A ServersB ClientsC RoutersD End systems82. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers83. Which service does UDP not provide?B de-multiplexingC error-detectionD error-correction84. There are three major events related to data transmission and retransmission in the TCP sender, which one is not in it?A data received from application aboveB de-multiplexing segmentC timer timeoutD ACK receipt85. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP86. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection87. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection88. Which service helps prevent the internet from entering a state of gridlock?A reliable data transferB flow controlC congestion controlD handshaking procedure89. The Internet’s _____is responsible for moving packets from one host to another.A application layerB transport layerC network layerD link layer90.In the following applications, which one is a bandwidth-sensitive application?A E-mailB web applicationC real-time audioD file transfer91. In the following applications, which one uses UDP?A E-mailB web applicationC file transferD DNS92. In the following four descriptions, which one is correct?A If one host’s transport layer uses TCP, then its network layer must use virtual-circuit network.B Datagram network provides connection serviceC The transport-layer connection service is implemented in the routerD The network-layer connection service is implemented in the router as well as in the end system.93.____ is a speeding-matching service---matching the rate which the sender is sending against the rate at which the receiving application is reading.A congestion controlB flow controlC sliding-window controlD variable control94. In the following four descriptions about Rcv-Window, which one is correct?A The size of the TCP RcvWindow never changes throughout the duration of the connectionB The size of the TCP RcvWindow will change with the size of the TCP RcvBufferC The size of the TCP RcvWindow must be less than or equal to the size of the TCP RcvBufferD Suppose host A sends a file to host B over a TCP connection, the number of unacknowledged bytes that A sends cannot exceed the size of the size of the RcvWindow.95. There are 6 flag fields. Which one is to indicate that the receiver should pass the data to the upper layer immediately?A PSHB URGC ACKD RST96. Suppose the TCP receiver receives the segment that partially or completely fills in gap in received data, it will ____.A immediately send ACKB immediately send duplicate ACKC wait some time for arrival of another in-order segmentD send single cumulative97. _____ imposes constrain on the rate at which a TCP sender can send traffic into the network.A sliding windowB congestion windowC receive windowD variable window98. Flow control and congestion control are same at that they all limit the rate of the sender, but differ in that ____.A flow control limits its rate by the size of RcvWindow, but congestion control by the traffic on the linkB congestion control limits its rate by the size of RcvWindow, but flow control by the traffic on the linkC flow control mainly is accomplished by the sender, but congestion control by the receiver.D flow control mainly is accomplished by the receiver, but congestion control bythe link.99. This job of delivering the data in a transport-layer segment to the correct socket is called ____.A multiplexingB de-multiplexingC forwardingD routing100. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [base, nextseqnum-1] corresponds to packet that____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged101. ____ are the two types of transport services that the Internet provides to the applications.A TCP and UDPB connection-oriented and connectionless serviceC TCP and IPD reliable data transfer and flow control102. In the following descriptions about persistent connection, which one is not correct?A The server leaves the TCP connection open after sending a responseB Each TCP connection is closed after the server sending one objectC There are two versions of persistent connection: without pipelining and with pipeliningD The default mode of HTTP uses persistent connection with pipelining103. The field of Length in UDP segment specifies the length of ____.A the UDP segment, not including the headerB the UDP segment, including the headerC the UDP segment’s headerD the Length field104. In TCP segment header, which field can implement the reliable data transfer?A source port number and destination port numberB sequence number and ACK numberC urgent data pointerD Receive window105. In the following four descriptions about TCP connection management, which one is not correct?A Either of the two processes participating in a TCP connection can end the connectionB If the FIN bit is set to 1, it means that it wants to close the connectionC In the first two step of the three-way handshake, the client and server randomly choose an initial sequence numberD In the three segments of the three-way handshake, the SYN bit must be set to 1 106. Suppose host A sends two TCP segments back to back to host B over a TCP connection. The first segment has sequence number 42, and the second has sequence number 110. If the 1st is lost and 2nd arrives at host B. What will be the acknowledgment number?A 43B ACK42C 109D ACK1101.Consider sending an object of size O=500,000bytes from server to client. LetS=500 bytes and RTT=0.2s. Suppose the transport protocol uses static windows with window size 5. For a transmission rate of 100Kbps, determine the latency for sending the whole object. Recall the number of windows K=O/ WS), and there is K-1 stalled state (that is idle time gaps).2.Consider the following plot of TCP congestion window size as a function of time.Fill in the blanks as follow:a) The initial value of Threshold at the first transmission round is ____. b) The value of Threshold at the 11st transmission round is ____. c) The value of Threshold at the 21st transmission round is ____. d) After the 9th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKe) After the 19th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKf) During ____ transmission round, the 18th segment is sent.3.Consider the TCP reliable data transfer in the given graph. If in Segment 1’s Sequence number =10,data=“AC”, please fill in the following blanks. a) In Segment 2, ACK number=____;b) In Segment 3, Sequence number =____; data=“0123456789”c) If there are some bits corrupted in segment 3 when it arrives Host B, then the ACK number in Segment 5 is ____; and the ACK number in Segment 6 is ____.0 00 Congestion window sizeTransmission round4. The client A wants to request a Web page from Server B. Suppose the URL of the page is 172.16.0.200/experiment, and also it wants to receive French version of object. The time-sequence diagram is shown below, please fill in the blanks.Packet① to Packet③are TCP connection’s segment, then:Packet ①: SYN flag bit= aACK flag bit= bSequence number= 92Packet ②: SYN flag bit=1ACK flag bit= c Sequence number=100 Packet ③: SYN flag bit= d ACK flag bit=1Sequence number= e5. Consider sending an object of size O=100 Kbytes from server to client. Let S=536 bytes and RTT=100msec. Suppose the transport protocol uses static windows with window size W.(1) For a transmission rate of 25 kbps, determine the minimum possible latency. Determine the minimum window size that achieves this latency.(2) Repeat (1) for 100 kbps.6. Consider the following plot of TCP congestion window size as a function of time. Please fill in the blanks as below.a) The initial value of Threshold at the first transmission round is____. b) The value of Threshold at the 11th transmission round is_____. c) The value of Threshold at the 21st transmission round is_____.Congestion window sizeTransmission roundd) After the 9th transmission round, _____ occurs.e) After the 19th transmission round, ____ are detected.。
现代电信交换3.ppt

3.1 Point-to-Point Circuit Switching
3.2 Cost Criteria for Switching
3.3 Multi-Stage Switching Network
In practice, we may tolerate a small probability of blocking.
In return, we reduce the crosspoint complexity and control complexity.
In between these 2 classes of nonblocking networks, there are networks called wide sense nonblocking networks for which new connections can be add without disturbing existing connections, provided we follow some rules for choosing a path for the new connection.
Rearranging paths for connected pairs involved extra control complexity, and may cause disruption of a connection.
A non-blocking network is termed strict-sense nonblocking if a path can be set up between an idle transmitter and an idle receiver (can be more than one receiver for the case of multi-casting) without disturbing the paths already setup.
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
A management network is the network that allows managers and agents to communicate with each other A production network is the network that carries client traffic These two networks can be separate, or they can share the same physical network
Management
Systems provide tools to manage the network such as
• monitoring applications • service provisioning systems • craft terminals
Management systems are applications that interact with the network They are not part of a network Production networks will function normally even if the management system fails
Network elements can be connected to a management system via management ports Routers, for example can be connected to a computer terminal via a serial interface Technicians enter commands to configure and troubleshoot the network device
Management communications may use a dedicated network that is physically separate from the production network Traffic can also be carried on the production network The management network may be overlaid on top of the production network
Management communication is inherently asymmetrical Network elements play the role of ―agents‖ that support a managing application (―manager‖) by responding to manager requests and notifying it of unexpected events
a view of a devices manageable features data in the database constitutes management information The MIB resides on the agent, but a cached version may be stored on a manager
A second way to manage a network element is through its Ethernet port
◦ This allows the network element to be identified by its IP address ◦ This configuration can be managed by SNMP ◦ This is the preferred way of managing a network
◦ Management traffic carried over the production network competes with other networking traffic ◦ Although low in volume, management traffic can be bursty and of non-negligible volume ◦ The amount of management traffic can be sufficient to interfere with other applications
This minimizes network traffic caused by repeated requests for the same information
translates requests from the management interface into operations that retrieve information from a MIB The agent logic maps the names of different MIB counters to the actual registers where the information is stored agent logic can include ―embedded management intelligence‖ that can perform pre or post processing of requests
SNMP agents use UDP and port 161 for management requests Packets specifically addressed to a network element are inspected by the element The NE then passes the packet to its SNMP agent process
This relationship is a client/server relationship with one or a few clients and many servers
software that provides functionality for an agent a network element can actually contain several management agents, each with its own management interface that supports different purposes (reporting, configuring, etc)
The Basic Ingredients ofBiblioteka Network Management
After you have read this chapter, you should be able to Explain the terms manager and agent Describe Management Information Bases (MIBs) Explain how management agents, managed devices, and MIBs relate to each other Explain the difference between in-band and outof-band management communications State the pros and cons of dedicated management networks Describe the role of Network Operations Centers (NOCs)
Reliability
Avoiding Interference
◦ management traffic is separated from traffic on the production network ◦ If a segment on the production network fails, management traffic on a dedicated network can reach the problem area
◦ a dedicated management network is a separate network ◦ This comes with a huge price tag that results in significant additional cost
The three main parts of a Management Agent are a management interface a Management Information Base the core agent logic
handles management communications supports a management protocol allows managing applications to make requests to network elements and receive responses allows agents to send unsolicited messages to alert the manager of events that occur on network elements
Managed devices are called network elements
(NEs)
A management interface that can send requests to the device is a pre-requisite For example, a request for data regarding utilization of a port can be made if the port has management capabilities Network elements can also send responses to the managing system Responses can be solicited or unsolicited, such as when an unexpected event occurs
