APS 审核复习 computer network
电子信息工程APS审核资料 (1)

数组这些按序排列的同类数据元素的集合称为数组。
栈是只能在某一端插入和删除的特殊线性表。
它按照先进后出的原则存储数据,先进入的数据被压入栈底,最后的数据在栈顶,需要读数据的时候从栈顶开始弹出数据(最后一个数据被第一个读出来)。
队列它只允许在表的前端(front)进行删除操作,而在表的后端(rear)进行插入操作。
进行插入操作的端称为队尾,进行删除操作的端称为队头。
队列是按照“先进先出”或“后进后出”的原则组织数据的。
链表链表由一系列结点(链表中每一个元素称为结点)组成,结点可以在运行时动态生成。
每个结点包括两个部分:一个是存储数据元素的数据域,另一个是存储下一个结点地址的指针域。
树二叉排序树或者是一棵空树,或者是具有下列性质的二叉树:(1)若左子树不空,则左子树上所有结点的值均小于它的根结点的值;(2)若右子树不空,则右子树上所有结点的值均大于或等于它的根结点的值;(3)左、右子树也分别为二叉排序树;堆每个结点都有一个值。
通常我们所说的堆的数据结构,是指二叉堆。
堆的特点是根结点的值最小(或最大),且根结点的两个子树也是一个堆。
二叉排序树或者是一棵空树,或者是具有下列性质的二叉树:(1)若左子树不空,则左子树上所有结点的值均小于它的根结点的值;(2)若右子树不空,则右子树上所有结点的值均大于或等于它的根结点的值;(3)左、右子树也分别为二叉排序树;Data structure is the way of computer storage and organization data. Data structure can bring a higher running or storage efficiencyarrayThese sets of similar data elements arranged in order are called arrays.StackIs a special linear list that can only be inserted and deleted at one end. It stores data in accordance with the principle of advanced after the first enter the data is pushed intothe stack, the final data in the stack, need to read data when the data are beginning to pop up from the top of the stack (the last data is read out first).queueIt only allows the front end of the table (front) to delete the operation, and in the back end of the table (rear) to insert the operation. The end of the insertion operation called the end of the team, the end of the delete operation called the head of the team. The queue is organized in accordance with the principle of "advanced first out" or "backward".linked listThe linked list is composed of a series of nodes (called nodes in the list), which can be dynamically generated at runtime. Each node consists of two parts: one is the data field that stores the data elements, and the other is a pointer field that stores the next node address.treeTwo fork sort tree or an empty tree, or has the following nature of the two fork tree:(1) if the left sub tree is not empty, the value of all the nodes in the left tree is smaller than the value of its root node;(2) if the right subtree is not empty, then the right subtree on all nodes of the value is greater than or equal to the value of its root node;(3) the left and right subtree are respectively two binary sort tree;heapEach node has a value. Usually we say the pile of data structure, refers to the two fork heap. The heap is characteristic of the root node of the minimum value (or maximum), and the two is the root node of the subtree of a heap.Two fork sort tree or an empty tree, or has the following nature of the two fork tree:(1) if the left sub tree is not empty, the value of all the nodes in the left tree is smaller than the value of its root node;(2) if the right subtree is not empty, then the right subtree on all nodes of the value is greater than or equal to the value of its root node;(3) the left and right subtree are respectively two binary sort tree;面向对象对象指的是类的实例。
审协笔试
Overfitting过度拟合
(2)图形图像处理
Pixel像素
CAD计算机辅助设计
VRML虚拟现实建模语言
(4)触摸屏
Zoom缩放
Restrictive电阻式
Voltage电压
Surface acoustic wave表面声波
Ultrasonic超声波
Capacitive电容式
Insulator绝缘体
indium tin oxide铟锡氧化物
electrostaticfield静电场
Responsive敏感的
Optical光学的
Project投射
(6)其它技术类词汇
Search搜索
Cost成本,代价
measure度量
discrete离散的
proposition命题
Pseudo code伪代码
Neural networks神经网络
ServiceBroker服务中介器
Consultation查询
Sift through data筛查数据
Raw data原始数据
Inference consideration推理考量
Interestingness metrics兴趣权值(考量)
Spatial indice空间索引
Concise简明的
Deviation偏差,误差
Investigation调查,研究
Applicable适用的
Compact紧凑的,简洁的
Stuff填充,材料
Maintain保持,维护
Remarkable卓越的,非凡的
Popularity普及
Contaminant污染物
APS-computer network-2
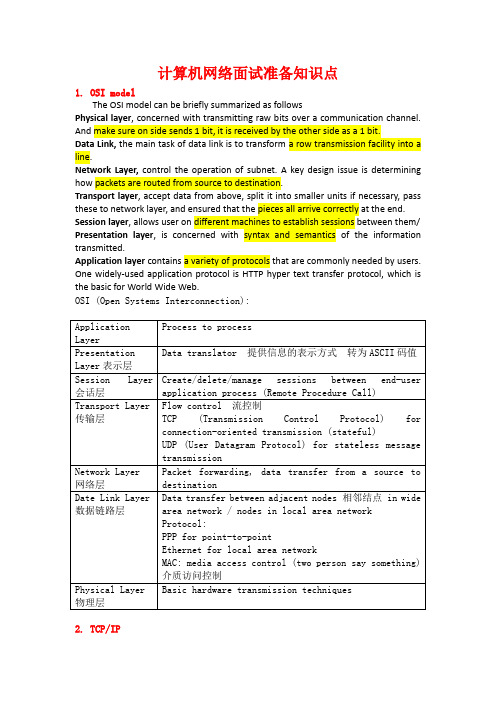
计算机网络面试准备知识点1. OSI modelThe OSI model can be briefly summarized as followsPhysical layer, concerned with transmitting raw bits over a communication channel. And make sure on side sends 1 bit, it is received by the other side as a 1 bit.Data Link, the main task of data link is to transform a row transmission facility into a line.Network Layer,control the operation of subnet. A key design issue is determining how packets are routed from source to destination.Transport layer, accept data from above, split it into smaller units if necessary, pass these to network layer, and ensured that the pieces all arrive correctly at the end. Session layer, allows user on different machines to establish sessions between them/ Presentation layer, is concerned with syntax and semantics of the information transmitted.Application layer contains a variety of protocols that are commonly needed by users. One widely-used application protocol is HTTP hyper text transfer protocol, which is the basic for World Wide Web.OSI (Open Systems Interconnection):2. TCP/IPTCP/IP:The Internet Protocol Suite (commonly TCP/IP) is the set of communications protocols used for the Internet and other similar networksTCP Protocol: Transmission Control Protocol (TCP)UDP Protocol: User Datagram ProtocolDifference:TCP ("Transmission Control Protocol") is a connection-oriented protocol, which means that upon communication it requires handshaking to set up end-to-end connection. A connection can be made from client to server, and from then on any data can be sent along that connection.∙Reliable - TCP manages message acknowledgment, retransmission and timeout. Many attempts to reliably deliver the message are made. If it getslost along the way, the server will re-request the lost part. In TCP, there'seither no missing data, or, in case of multiple timeouts, the connection isdropped.∙Ordered - if two messages are sent along a connection, one after the other, the first message will reach the receiving application first. When data packetsarrive in the wrong order, the TCP layer holds the later data until the earlierdata can be rearranged and delivered to the application.∙Heavyweight - TCP requires three packets just to set up a socket, before any actual data can be sent. It handles connections, reliability and congestioncontrol. It is a large transport protocol designed on top of IP.∙Streaming - Data is read as a "stream," with nothing distinguishing where one packet ends and another begins. Packets may be split or merged into biggeror smaller data streams arbitrarily.Three-way handshake:To establish a connection, TCP uses a three-way handshake. Before a client attempts to connect with a server, the server must first bind to a port to open it up for connections: this is called a passive open. Once the passive open is established, a client may initiate an active open. To establish a connection, the three-way (or 3-step) handshake occurs:1.The active open is performed by the client sending a SYN to the server.2.In response, the server replies with a SYN-ACK.3.Finally the client sends an ACK back to the server4.TCP/IP4.子网的划分Explain why and how to subnet掩码用来确认大网里面有多少个子网,从而确认IP地址所在的网络号默认掩码意味着没有将x类大网划分成小网5.Switching and routingHub, Switch, Router的区别:网桥bridge:数据链路层互联的设备。
2020年同等学力申硕《计算机科学与技术学科综合水平考试》考点手册(计算机网络)

第3章计算机网络【考点1】计算机网络的基本概念1.计算机网络发展过程从面向终端分布的计算机系统到Internet。
因特网发展的三个阶段:(1)从单个网络ARPANET向互联网发展;(2)建成三级结构(主干网、地区网、校园或企业网)的互联网;(3)逐渐形成多层次ISP(互联网服务提供商)结构的互联网。
2.计算机网络定义、功能和组成计算机网络定义、功能和组成如表3-1所示。
表3-1 计算机网络定义、功能和组成3.计算机网络结构(1)实体、协议、服务、服务访问点①实体:任何可以发送或接收信息的硬件或软件进程;②网络协议(简称协议):协议是控制两个对等实体进行通信的规则的集合,其三个要素为语法、语义、同步;③服务:在协议的控制下,两个对等实体间的通信使得本层能够向上一层提供服务,本层协议的实现需要下一层提供的服务;④服务访问点:同一系统中相邻两层的实体进行交互的地方即服务访问点SAP。
(2)ISO/OSI参考模型和TCP/IP参考模型计算机网络的各层及其协议的集合称为网络的体系结构,常见模型包括:①ISO提出的开放系统互联参考模型OSI/RM(简称OSI参考模型);②TCP/IP参考模型。
(3)具有五层协议的体系结构具有五层协议的体系结构如表3-2所示。
表3-2 具有五层协议的体系结构(4)TCP/IP的体系结构事实上,TCP/IP的层次结构已经成为应用广泛的国际标准,它分为应用层、运输层、网际层和网络接口层。
4.计算机网络类型计算机网络类型如下。
5.计算机网络的性能指标计算机网络的性能指标如表3-3所示。
表3-3 计算机网络的性能指标6.网络标准化组织在国际上,有众多的标准化组织负责制定、实施相关网络标准,主要的网络标准化组织和贡献如表3-4所示。
表3-4 主要的网络标准化组织和贡献【考点2】计算机网络体系结构1.计算机网络体系结构的概念计算机网络体系结构是计算机网络的各层及其协议的集合。
2.典型参考模型:ISO/OSI参考模型和TCP/IP参考模型ISO/OSI参考模型和TCP/IP参考模型的体系结构如图3-1所示。
根据同等学力申硕国考计算机科学综测考点整理

根据同等学力申硕国考计算机科学综测考
点整理
为了帮助考生高效备考同等学力申硕国考计算机科学综测,本文整理了相关考点和重点内容。
1. 计算机组成原理
- 计算机的基本组成及功能
- 冯·诺依曼结构
- 存储器的层次结构
- 处理器的组成与功能
2. 数据结构与算法
- 线性表、树、图等基本数据结构的定义和特点
- 基本算法的概念和分类
- 排序算法的原理和实现
- 查找算法的原理和实现
3. 操作系统
- 操作系统的基本概念与功能
- 进程管理
- 存储管理
- 文件管理
- 设备管理
4. 网络技术
- 计算机网络的基本概念与组成
- TCP/IP协议族
- LAN、WAN、Internet的特点与区别- 网络安全与防护技术
5. 数据库技术
- 数据库基本概念与模型
- 关系数据库的设计与实现
- SQL语言的基本操作与高级应用
- 数据库事务管理与并发控制
6. 编程语言与软件工程
- 常见编程语言的基本语法与特点
- 面向对象程序设计基本概念
- 软件开发过程与模型
- 软件需求分析与设计方法
7. 系统分析与设计
- 系统开发的基本概念与阶段
- 需求分析与建模技术
- 系统设计原理与方法
- 系统测试与维护
本文提供了同等学力申硕国考计算机科学综测的考点整理,希
望能够为考生提供有效的备考指导,祝愿考生能够取得优异的成绩。
APS审核--车辆工程专业
Automobile structure
------Fahrzeugaufbau
This course introduces the typical structure of ICE vehicle (internal combustion engine vehicle),including engine, drive line, steering system, braking system and so on.
It lasted about 3 weeks. At the end of the practice, we had a test. I remember my teacher asked me to explain the four strokes of the engine, and the effection of compression ratio. ������↑--- p. T ↑(after compression stroke)---v ↑ (speed of compression)--the output power of engine ↑---economy performance ↑
C drive axle Final drive---change the rotating direction of torque, increase the input torque and reduce rotating speed. Differential---make the right and left wheel rotate in different rotating speeds. --Guarantee pure rolling between two driving wheels and the ground while turning. Half axle Driving axle housing
计算机网络技术复习提纲

计算机网络技术复习提纲一、计算机网络的基本概念1、计算机网络的基本概念及发展a.计算机网络的定义和分类b.计算机网络的发展历程和趋势2、计算机网络体系结构a. OSI参考模型b. TCP/IP模型c.应用层协议二、局域网技术1、局域网的基本概念和特点2、以太网(Ethernet)a.以太网的标准和类型b.以太网的物理层和数据链路层c.以太网的帧格式和传输机制3、令牌环网(Token Ring)a.令牌环网的原理和特点b.令牌环网的物理层和数据链路层c.令牌环网的帧格式和传输机制4、无线局域网(WLAN)a. WLAN的原理和标准b. WLAN的拓扑结构和传输机制c. WLAN的安全性和隐私保护三、网络互联技术1、网络互联的基本概念和协议2、IP和子网掩码a. IP的分类和格式b.子网掩码的作用和应用c.私有IP和动态IP3、路由器和路由协议a.路由器的功能和工作原理b.路由协议的种类和特点c. RIP、OSPF和BGP等常用路由协议的应用和配置4、交换机和交换技术a.交换机的功能和工作原理b.交换技术的种类和应用场景c. VLAN、Trunking和Spanning Tree等技术的应用和配置四、 Internet技术及应用1、Internet的基本概念和发展历程2、WWW服务与HTTP协议3、DNS服务与域名解析4、FTP服务与文件传输5、E-mail服务与邮件传输6、Telnet服务与远程登录计算机操作系统复习提纲一、引言计算机操作系统是计算机系统中的核心组成部分,负责管理和协调计算机硬件和软件资源的运行。
它扮演着“桥梁”的角色,沟通了硬件和应用程序之间的,为用户提供了便利的接口。
操作系统的重要性不容忽视,它是理解计算机体系结构、管理资源、实现系统安全和高效运行的关键。
二、操作系统的基本概念和功能1、基本概念:包括进程、线程、资源、系统调用等。
2、功能:操作系统的主要功能包括处理机管理、内存管理、文件管理、设备管理和用户接口管理等。
examcoo 第4章 计算机网络辅助背诵要点

《计算机网络》辅助背诵复习要点一、通信技术部分1、现代通信:使用电波或光波传递信息的技术。
2、通信的三要素:信源-→信道-→信宿如:有线电话通信:发话人及其话机---信源。
受话人及其话机—信宿。
电话线及中继器—信道。
通信终端:信源中的发信设备或信宿中的收信设备。
如:电话机。
3、现代通信系统中,被传输的信息必须转换成某种电信号(或光信号) 才能进行传输。
4、模拟信号:连续变化的物理量。
数字信号:离散。
有限个状态(一般是2个状态)通信网络分:模拟通信网、数字通信网、混合网。
5、载波:高频振荡的正弦波信号。
特性:比其他信号能传送得更远。
6、MODEM:调制解调器。
目的:使用MODEM是为了远距离传输信号。
发送方:调制。
接收方:解调。
调制方式:调幅、高频、调相。
7、数字信号如何传输?基带传输:不加处理直接传输数字信号(如:USB)。
适用场合:近距离传输。
频带传输:通过载波来传输数字信号。
适用场合:远距离传输8、计算机接MODEM上网:计算机数字信号,经MODEM的调制,调制成模拟的语音信号,在电话线上传输。
接收方经MODEM的解调,将模拟信号还原成数字信号。
因此:计算机通过MODEM方式经过电话线上网,1)要付电话费2)上网与打电话不能同时进行。
9、为什么要使用多路复用技术?提高线路利用率,降低传输成本。
方法:使用同一条传输线,同时传输多路信号10、有几种多路复用方式?1)频分多路复用(FDM)--广播、电视使用。
特点:同一个时刻,有多路信号。
每一路信号,使用一部分带宽。
2)时分多路复用(TDM)--数字通信领域使用。
如计算机网络、GSM手机。
特点:同一个时刻,只有一路信号。
每一路信号之间分时传输。
在一个时间段内,所有信号在传输。
每一路信号,使用全部带宽。
3)波分多路复用(WDM)--光纤通信使用。
特点:同一个时刻,有多路不同波长的光信号传输。
注:Cable Modem(有线电视MODEM,用于有线电视上网):频分多路复用 + 时分多路复用.其中:频分多路复用用于:将上网信号与有线电视信号同时传输(即:上网与看电视两不误)。
APS审核金融学复习资料

In this course, I learned basic financial concepts, such as money, credit and interest rates, financial institutions, financial instruments and financial markets.Basic concepts of finance1.MoneyA commodity that is legally established as an exchangeable equivalent of all other commodities.Money as a medium of exchange. The purchasing and selling are done through the money. Money as a unit of account. It helps to measure the value of goods and services.Money as a store of value. Money held’s in the form of cash is considered highly liquid assets. Money as a standard of deferred payments. In today economy buying and selling of goods are made on the basis of credit.2.CreditThe behavior that they loan you money to use which you must in turn pay back including interest. Credit tools: cheque, commercial bills, commercial paper, bond, stock.3.Interest(Simple interest) Interest paid only on the original principal, not on the interest accrued. Interest = principal x rate x n(期限) 利息=本金x利率x n (期限)。
APS三次面试记录

第一次面试记录,2018.02.08面试官,红色短头发阿姨笔试题:计算机网络五层结构功能,并列举每一层的协议及其功能面试过程:先自我介绍,刚说完名字被打断了然后问我在上大几,我说大四,问我有没有毕设的题目,我说有,然后让我介绍一下毕设,然后我说我毕设名字是,基于衰减因子的论文影响力分析,然后问我是基于哪些论文的研究,我说这个研究不是基于某几篇论文,是针对很多论文研究的论文影响力,她没听懂,然后我就又换了一种方式解释,她还是没听懂,然后就开始问其他的了然后问了我一个实验课,网络综合试验,让我举三个实验出来,我说我只记得两个了,然后她说这才过去了一年半,我不应该忘了,然后让我说,我就说了第一个实验,然后被打断,问了几个问题我记不太清楚了,然后她说这个太简单了就是一个登陆的过程,然后让我说第二个,里面有一个协议,RIP协议,他问我这个协议是什么,这个我没复习,因为实验的时候就是输了一个代码,我说我不记得了,然后她就很生气,说我应该记得这个协议,然后又怼了我几句就开始问其他的了接着她指着我成绩单上的一门课,叫网络协议栈,她问我什么是协议栈,我说我们没学这个,我们学的是。
没说完被打断了,她说可是课程名字里面有协议栈,我应该知道,然后问我这个课学了什么,我说这个课我们提交了一个报告,报告里分析了AODV协议,然后让我讲这个协议,我说了然后她没听懂,然后问我这是哪个层的协议,我说了然后她说不对,应该不是这一层的然后问我最喜欢的是哪一门课,我说是高级c语言编程,然后就让我讲编程部分的内容,我说这门课的重点不是编程,我们学的是。
打断我说可是我们这门课名字里面有编程两个字重点应该是编程,然后我就解释编程的那一部门,我说编程的部分很少,然后就说我考了90分不应该只学了这些编程的内容,然后问了我那一部分程序,我讲了她没听懂,我拿计算机网络的五层协议给解释了还是不懂,然后就结束了然后面试的时候还总是说让我回答她的问题什么的,具体的记不清楚了笔试题:什么是AD hoc问了毕设,解释了一下题目还有题目里的名词无线传感网,根据笔试题提问,听不懂在问什么,中间画了一些图密码理论,解释了RSA问我怎么选择大素数,这里可能我没听懂什么意思,最后我说了65533,他们都笑了,就结束了过程沟通有问题,互相听不懂,最后送我出去的时候说你真的应该好好练习英语具体的想不起来了一个很和蔼的老爷爷,副审是一个很高很帅的小哥哥,红灭坐在进门的椅子上,我也不知道为什么会有三个人,也不知道红灭坐在那里干嘛了,我就看到她拿了一张纸好像要记录,然后时间到了之后提醒了一下,全程没有提问,我审核过程中也没有看过她,因为不想看到她那张脸笔试:密码理论的内容,问对称密码学和非对称密码学的区别我写了区别,还各自举了一个例子面试过程:老爷爷:首先自我介绍他和副审,然后让我说一下我前两次面试没有通过的原因我:第一次是因为没有准备很充分,并且特别紧张,所以很多东西都没有说出来,第二次是因为我很久没有说英语了,所以面试的过程中和审核官沟通有一些问题,但是我会好好准备我的语言的老爷爷(听到我说沟通有问题就笑了):然后请介绍一下自己以及自己的学习计划我:我今天很紧张,但是我正在努力冷静下来,你可以叫我xx,我毕业于xx学校,专业是xx,我想去德国的柏林工业大学,因为我知道他们有一个课题叫做数据分析与云,这和我的毕业设计是相关的,并且我对数据处理这个很感兴趣,我希望可以学习这方面的内容老爷爷:你说一下数字信号处理这门课学了什么我(这门课我根本没有准备,我就用信号与系统的知识回答的):我们学了一些基本概念,还学习了如何通过信号系统建立数学模型,然后解决不等式(被打断)老爷爷:什么样的数学模型我:我拿笔想把数学模型那个公式写出来,然后没写完被打断(公式背得不是很熟)老爷爷:你们有没有学A和B之间通信得过程我:我们这门课里没有学,但是我们在另外一门课里学了老爷爷:哪门课?我:通信原理,然后我在成绩单上给他标注了一下老爷爷:这门课你们学了什么?我:我们学了一些基本概念和两个通信模型,模拟通信模型和数字通信模型老爷爷:什么是模拟通信模型我:我画了一个图,标注专业名词的时候忘记调制器那个单词怎么拼写了,然后老爷爷帮我拼出来了老爷爷:调制器是做什么的我:把模拟信号转换为可以在信道中传输的信号老爷爷:怎么转换我:我们学了AM(这里又忘记了AM是哪两个单词的缩写,老爷爷又帮我拼出来了,我顺口说了问一句真的太感谢你了,然后老爷爷又小了说没关系),我简单的画了一个示意图,解释说调制信号的振幅是根据信源信号的振幅变化而变化的(后来那个单词我又忘了一次,我还问他你能不能再说一下那个词,然后老爷爷说why,应该是在和我开玩笑,然后我说好吧,我就自己继续说了)老爷爷:那频率调制呢我:这个是FM,又画了一张图,说这种方式中调制信号的频率是根据信源信号的频率变化而变化的老爷爷:你说一下微型计算机这门课我(这门课完全没有复习):这门课我们学了一些基本概念,然后学习了移动设备如手机中,传感器节点与设备之间的接口,感觉他并听不懂,我就举例子说手机屏幕在阳光好的时候会变亮,阳光不好的时候会变暗,这是因为手机设备里有一个光传感器老爷爷(他还是没有听懂):你们学了手机上的接口我:对,我们学习了传感器节点在手机设备中的接口,(感觉他不太相信,所以我就开始找借口)因为我们是网络工程的,所以硬件的东西学的不是很多老爷爷:ok,网络工程,那你说一下网络工程里tcp/ip协议,以及计算机网络的四层结构我:画了一张图,我说计算机应该有5层,但是我们只学了前四层,关于物理层的部分我们没有学(老爷爷点头感觉很满意),然后我把tcp,udp,ip协议都大概标注了一下老爷爷:那应用层有什么协议呢(我一开始没有标注应用层的协议)我:有HTTP协议,DNS协议老爷爷:HTTP协议是什么我:这里我本来想解释一下是哪几个词的缩写,结果忘了,又是老爷爷帮我拼出来的,然后我结合DNS协议举了一个例子,比如A想访问一个网址时,HTTP和DNS协议的具体过程,马上要说三次握手的时候,没有解释完就被打断了老爷爷:感觉你没有在回答我的问题,你知道FTP协议吗我:知道,这是文件传输协议老爷爷:你说一下这个协议我:我说服务器存储很多文件,客户端想访问某个文件的话需要和服务器建立连接,有两个连接,一个是控制连接,一个是数据连接,控制连接端口,数据连接端口(被打断,这里应该是觉得我是学过的,就没有再听下去)老爷爷:你说一下密码学的应用(大四一门选修课,也是成绩单上最后一门课,叫密码学理论与应用,他指着课程名字里的应用问我)我:这门课讲了对称与非对称的区别,应用讲了RSA在数字签名里的应用,因为我笔试内容里写了RSA的算法,所以我指了一下我的笔试那张纸老爷爷:对,这个课和笔试内容相关,然后看了一下笔试题,你说一下非对称密码学是什么我(非对称密码学的单词我又忘记了):非对称密码学中公钥和私钥是不一样的,比如说RSA 就是这样的,我们讲了RSA的应用,就是数字签名(我看他有点疑惑然后我就解释了一下什么是数字签名)老爷爷:那什么是对称密码学我:公钥和私钥是一样的,比如AES,DES,但是因为他们的算法太难了我们就没学(老爷爷笑着重复了一下太难了,说好吧)老爷爷:你说一下你的毕设这个时候红灭提醒20分钟到了我:我的毕设是基于衰减因子的论文影响力分析,通过对数据集的分析(被打断)老爷爷:什么是衰减因子我:一个影响因素,比如论文的被引用次数随着时间发展会变化,那么时间就是论文被引用次数的一个衰减因子老爷爷:你的论文多少页我:这里我听错了,我说我数据集有五百万篇论文,他说我问的是你的论文多少页,我说不好意思啊听错了,我的论文40页左右,数据集是五百万论文左右老爷爷:好了时间到了,然后把我送出去了,我怕他觉得我语言不好,我一直解释说我会好好练习语言的,然后他说了啥我没听清,反正最后就是没关系啊,你过两天就可以在网上查结果了过程中我好多次英文单词忘记拼写了,有的是因为紧张,有的是确实不熟悉,有这种情况的话尽量用其他单词代替,毕竟不是每个人都像老爷爷这样好说话,还会提醒,然后就是过程中尽量有礼貌,忘记的地方说抱歉,审核官如果有提醒的话说谢谢,我面试过程说了好多次,因为这个老爷爷提醒了我好多次,面试过程不要太着急,听清楚了再回答,要说得清楚一点复习建议:因为我是三审,前两次因为要工作,又没有提前复习,准备时间就那两个星期,还要上班,所以复习的很浅,每门课都只知道一点点,所以被问住也很正常第三次我找了中介,提前复习了一点,而且这段时间没有工作,就专心复习,就把所有的课都整理了一下然后让中介老师帮我看哪里有问题,总结就是复习要有条理性,可以借助脑图,然后就是这门课大家都会学的一定要准备,比如计算机网络五层结构,还有就是要真的懂,比如说这门课我们学了A,B,C,那这A,B,C最好是大家都需要会的东西,而且这几个知识点要真的弄懂,因为你说你学了A,他可能就会抓着A继续问,如果像我之前什么都只复习皮毛,肯定是不行的还有要提前背英语部分,很多专业名词最后一起背太难了,很容易忘记,要多练习不要紧张,也不要害怕,好好复习都会过得祝大家最后都能顺利通过APS。
计算机网络ComputeNetwork--aps审核

Computer networkThis course introduced some basic knowledge of computer network, such as classification, hardware c omponents and connection method.Classification:1. Local Area Network (LAN), this is a network covering a small geographic area, like a home, office, or building. Current LANs are most likely to be based on Ethernet technology.2. Wide Area Network (WAN), this is a data communications network that covers a relatively broad geographic area and that often uses transmission facilities provided by common carriers, such as telephone companies. WAN technologies generally function at the lower three layers of the OSI reference model: the physical layer, the data link layer, and the network layer.(i.e. one city to another and one country to another country)3. Campus Area Network(CAN), this is a network that connects two or more LANs but that is limited to a specific and contiguous geographical area such as a college campus, industrial complex, office building, or a military base. A CAN may be considered a type of MAN (metropolitan area network), but is generally limited to a smaller area than a typical MAN.4. Metropolitan Area Network(MAN), this is a network that connects two or more Local Area Networks or Campus Area Networks together but does not extend beyond the boundaries of the immediate town/city. Routers, switches and hubs are connected to create a Metropolitan Area Network.5. Personal Area Network(PAN), this is a computer network used for communication among computer devices close to one person. Some examples of devices that are used in a PAN are printers, fax machines, telephones, PDAs and scanners.Connection methodComputer networks can be interconnected the with optical fiber, Ethernet, Wireless LAN and so on.Ethernet uses physical wiring to connect devices. Frequently deployed devices include hubs, switches, bridges and/or routers. Wireless LAN technology is designed to connect devices without wiring. These devices use radio waves or infrared signals as a transmission medium.Introduction to Computer NetworksA network is a collection of computers connected to each other. The network allows computers to communicate with each other and share resources and information.Network ClassificationThe following list presents categories used for classifying networks. Based on their scale, networks can be classified as Local Area Network (LAN), Wide Area Network (WAN), Metropolitan Area Network (MAN), Personal Area Network (PAN),Virtual Private Network (VPN) etc.A personal area network (PAN) is a computer network used for communication among computer devices close to one person. Some examples of devices that are used in a PAN are printers, fax machines, telephones, PDAs and scanners.Local Area Network (LAN)This is a network covering a small geographic area, like a home, office, or building. Current LANs are most likely to be based on Ethernet technology.Campus Area Network (CAN)This is a network that connects two or more LANs but that is limited to a specific and contiguous geographical area such as a college campus, industrial complex, office building, or a military base. A CAN may be considered a type of MAN (metropolitan area network), but is generally limited to a smaller area than a typical MAN. Metropolitan Area Network (MAN) A Metropolitan Area Network is a network that connects two or more Local Area Networks or Campus Area Networks together but does not extend beyond the boundaries of the immediate town/city. Routers, switches and hubs are connected to create a Metropolitan Area Network.Wide Area Network (WAN) A WAN is a data communications network that covers a relatively broad geographic area (i.e. one city to another and one country to another country) and that often uses transmission facilities provided by common carriers, such as telephone companies. WAN technologies generally function at the lower three layers of the OSI reference model: the physical layer, the data link layer, and the network layer.Global Area Network (GAN) specifications are in development by several groups, and there is no common definition. In general, however, a GAN is a model for supporting mobile communications across an arbitrary number of wireless LANs, satellite coverage areas, etc. The key challenge in mobile communications is "handing off" the user communications from one local coverage area to the next. In IEEE Project 802, this involves a succession of terrestrial Wireless local area networks (WLAN).[1]Internetwork. In modern practice, the interconnected networks use the Internet Protocol. There are at least three variants of internetwork, depending on who administers and who participates in them:Intranet, Extranet and Internet.Intranets and extranets may or may not have connections to the Internet. If connected to the Internet, the intranet or extranet is normally protected from being accessed from the Internet without proper authorization. The Internet is not considered to be a part of the intranet or extranet, although it may serve as a portal for access to portions of an extranet. The Internet is a specific internetwork. It consists of a worldwide interconnection of governmental, academic, public, and private networks based upon the networking technologies of the Internet Protocol Suite.Connection methodComputer networks can also be classified according to the hardware and software technology that is used to interconnect the individual devices in the network, such as Optical fiber, Ethernet, Wireless LAN, HomePNA, or Power line communication. Ethernet uses physical wiring to connect devices. Frequently deployed devices include hubs, switches, bridges and/or routers. Wireless LAN technology is designed to connect devices without wiring. These devices use radio waves or infrared signals as a transmission medium.Network topologyComputer networks may be classified according to the network topology upon which the network is based, such as Bus network, Star network, Ring network, Mesh network, Star-bus network, Tree or Hierarchical topology network,Network Topology signifies the way in which devices in the network see their logical relations to one another. The use of the term "logical" here is significant. That is, network topology is independent of the "physical" layout of the network. Even if networked computers are physically placed in a linear arrangement, if they are connected via a hub, the network has a Star topology, rather than a Bus Topology. In this regard the visual and operational characteristics of a network are distinct; the logical network topology is not necessarily the same as the physical layout.Basic Hardware ComponentsAll networks are made up of basic hardware building blocks to interconnect network nodes, such as Network Interface Cards (NICs), Bridges, Hubs, Switches, and Routers.A network card, network adapter or NIC (network interface card) is a piece of computer hardware designed to allow computers to communicate over a computer network. It provides physical access to a networking medium and often provides a low-level addressing system through the use of MAC addresses. It allows users to connect to each other either by using cables or wirelessly.The NIC provides the transfer of data in megabytes.A repeater is an electronic device that receives a signal and retransmits it at a higher power level, or to the other side of an obstruction, so that the signal can cover longer distances without degradation. In most twisted pair ethernet configurations, repeaters are required for cable runs longer than 100 meters away from the computer.A hub contains multiple ports. When a packet arrives at one port, it is copied to all the ports of the hub for transmission. When the packets are copied, the destination address in the frame does not change to a broadcast address. It does this in a rudimentary way: It simply copies the data to all of the Nodes connected to the hub.[2]A network bridge connects multiple network segments at the data link layer (layer 2) of the OSI model. Bridges do not promiscuously copy traffic to all ports, as hubs do, but learn which MAC addresses are reachable through specific ports. Once the bridge associates a port and an address, it will send traffic for that address only to that port. Bridges do send broadcasts to all ports except the one on which the broadcast was received.Bridges learn the association of ports and addresses by examining the source address of frames that it sees on various ports. Once a frame arrives through a port, its source address is stored and the bridge assumes that MAC address is associated with that port. The first time that a previously unknown destination address is seen, the bridge will forward the frame to all por ts other than the one on which the frame arrived.Bridges come in three basic types:1.Local bridges: Directly connect local area networks (LANs)2.Remote bridges: Can be used to create a wide area network (WAN) link between LANs. Remote bridges,where the connecting link is slower than the end networks, largely have been replaced by routers.3.Wireless bridges: Can be used to join LANs or connect remote stations to LANs.A switch is a device that performs switching. Specifically, it forwards and filters OSI layer 2datagrams (chunk of data communication) between ports (connected cables) based on the MAC addresses in the pac kets.[3] This is distinct from a hub in that it only forwards the datagrams to the ports involved in the communications rather than all ports connected. Strictly speaking, a switch is not capable of routing traffic based on IP address (layer 3) which is necessary for communicating between network segments or within a large or complex LAN. Some switches are capable of routing based on IP addresses but are still called switches as a marketing term. A switch normally has numerous ports, with the intention being that most or all of the network is connected directly to the switch, or another switch that is in turn connected to a switch.[4]Switch is a marketing term that encompasses routers and bridges, as well as devices that may distribute traffic on load or by application content (e.g., a Web URL identifier). Switches may operate at one or more OSI model layers, including physical, data link, network, or transport (i.e., end-to-end). A device that operates simultaneously at more than one of these layers is called a multilayer switch.Overemphasizing the ill-defined term "switch" often leads to confusion when first trying to understand networking. Many experienced network designers and operators recommend starting with the logic of devices dealing with only one protocol level, not all of which are covered by OSI. Multilayer device selection is an advanced topic that may lead to selecting particular implementations, but multilayer switching is simply not a real-world design concept.Routers are networking devices that forward data packets between networks using headers and forwarding tables to determine the best path to forward the packets. Routers work at the network layer of the TCP/IP model or layer 3 of the OSI model. Routers also provide interconnectivity between like and unlike media (RFC 1812). This is accomplished by examining the Header of a data packet, and making a decision on the next hop to which it should be sent (RFC 1812) They use preconfigured static routes, status of their hardware interfaces, and routing protocols to select the best route between any two subnets. A router is connected to at least two networks, commonly two LANs or WANs or a LAN and its ISP's network. Some DSL and cable modems, for home (and even office) use, have been integrated with routers to allow multiplehome/office computers to access the Internet through the same connection. Many of these new devices also consist of wireless access points (waps) or wireless routers to allow for IEEE 802.11g/b wireless enabled devices to connect to the network without the need for cabled connections.。
APS审核—计算机英语审核复习-自我介绍

APS审核—计算机英语审核复习-自我介绍计算机英语审核复习:一.自我介绍(简略写了下,问候语可长可短,自己适当添加,但不宜过长)Good morning, nice to meet you here。
My name is XXX。
I’m a senior student in XXX University。
My major is Computer Science & Technology.My objective is to obtain a Master degree of Science with an emphasis on computer software or hardware design and development。
前面寒暄中基本会问到的问题,只要不回答的太出格应该没有题.1.针对考官问你申请了那些学校那些项目的问题Now I'm applying for the universities such as Technical University of Munich, which has a good academic reputation and excellent professors。
Also universities of University of Stuttgart RWTH Aachen University are included. They are all very good universities.2.为什么选择到德国留学German universities have advanced equipments and rigorous study environment, which helps us learn more efficiently as well as improves our self—control spirit. At the same time, I wanna experience international cross-culture opportunity。
计算机网络复习

第十讲 网络安全
• 常用加密算法(公开密钥算法、秘密密 钥算法)
• 防火墙(包过滤、电路层网关、应用层 代理)
计算机网络 Computer N机网络发展经历了三个时代:
– 以单计算机为中心的联机系统 – 计算机—计算机网络 – 网络体系结构的标准化
• 计算机网络的功能 • 计算机网络的组成 • 计算机网络的分类
第二讲 数据通信基础
• 基本概念
• 信道。信道容量-两个公式
FSK、相移键控PSK • PCM编码:采样、量化、编码
第三讲 数据链路
• 流量控制:停-等协议、滑动窗口协议 • 差错控制:奇偶校验、海明码、循环冗
余码CRC • HDLC:面向比特的数据链路控制协议 • 位同步、帧同步
第四讲 广域网
• 电路交换 • 报文分组交换(数据报、虚电路)
第五讲 局域网
• 高速局域网:交换式以太网、快速以太网、千兆以太 网
第六讲 网络设备工作原理
• 网卡的配置参数 • 集线器的类型 • 集线器和中继器的功能 • 交换机、网桥(透明网桥的工作原理,
如何生成地址-端口表) • 路由器(子网的划分、如何生成路由表) • 调制解调器的功能
第七讲 网络体系结构与
TCP/IP
• 传输损耗:衰减、延迟变形、噪声 • 奈奎斯特(Nyquist)公式(无噪声信道) • 香农(Shannon)公式 (有噪声信道) • 传输介质:同轴电缆(基带、宽带)、双绞线
(屏蔽、非屏蔽)、光纤(单模、多模) • 数字信号编码:不归零制NRZ(又分正逻辑和
负逻辑两种)、曼彻斯特码、差分曼彻斯特码 • 数字数据的调制:幅移键控ASK、频移键控
• 传播时延、往返时延、MTU • IEEE802参考模型:物理层、介质访问控制
同等学力申硕-计算机综合网络知识点梳理【值得收藏】

同等学力申硕-计算机综合网络知识点梳理【值得收藏】在当前的信息时代,计算机技术得到了广泛的应用和发展,计算机专业的硕士学位也成为许多人追逐的目标。
然而,对于没有计算机本科背景的同等学力考生来说,申请计算机硕士可能会面临一定的困难。
为了能够更好地应对同等学力考试的计算机综合网络知识,下面将对相关知识点进行梳理,以帮助同等学力考生更好地准备申请计算机硕士。
一、计算机网络基础知识1. OSI参考模型OSI参考模型是计算机网络中最重要的概念之一,它将计算机网络的通信过程分为七个层次,分别是物理层、数据链路层、网络层、传输层、会话层、表示层和应用层。
同等学力考生需要了解每个层次的功能和相互之间的关系,以及在通信过程中所使用的协议和设备。
2. TCP/IP协议TCP/IP协议是当前互联网中最常用的协议,它是计算机网络通信的核心协议。
同等学力考生需要了解TCP/IP协议的基本原理、常用的协议和应用,以及常见的网络故障处理方法。
3. 网络拓扑在计算机网络中,网络拓扑是指计算机和网络设备之间的物理或逻辑连接方式。
同等学力考生需要了解常见的网络拓扑结构,包括总线型、星型、环形、树型和网状等,以及它们的特点和应用场景。
4. IP地址和子网划分IP地址是计算机在网络中的唯一标识,同等学力考生需要了解IP 地址的分类和格式,以及子网划分的方法和原理。
二、网络安全与管理1. 防火墙技术防火墙是计算机网络中常用的安全设备,它可以保护内部网络免受来自外部的攻击。
同等学力考生需要了解防火墙的工作原理、分类和配置方法,以及常见的防火墙策略和规则。
2. 信息安全在信息时代,信息安全成为了社会的重要问题。
同等学力考生需要了解信息安全的基本知识,包括安全机制、加密算法和常见的安全攻击与防范方法。
3. 网络管理网络管理是保证网络正常运行和安全的重要环节。
同等学力考生需要了解网络管理的基本概念、管理模型和常见的网络管理工具,以及网络性能监测和故障处理的方法。
《计算机等级网络技术》第二章网络辅导

本章复习时应以计算机络的层次化结构的概念为线索,结合TCP/IP体系结构, 掌握各个层次的有关概念及其功能,以及层与层之间的关系。
构造出计算机络的整体架构来。
⼀、掌握数字信道中速率的概念速率(⽐特率):每秒可以传输的⽐特数就是信道传输的速率。
单位:bps⼆、掌握络协议的概念让通信硬件按照所规定的控制规则去运⾏,这些规则我们就称之为协议(Protocol)。
计算机络的运⾏是多个协议相互配合作⽤的综合结果,⼀套完整的计算机协议合在⼀起被叫做"协议栈"(Protocol Stack,⼜称Protocol Suits)。
三、了解同等层协议只有在同等层次上的协议实体之间才可以互相联络,这就是同等层协议的概念。
四、掌握主/从的概念在络上的计算机,凡是可以主动发出通信请求的⼀⽅,就称之为主机;⽽在通信过程中从来就不能主动发出请求信息,只能被动地"聆听"并执⾏主机发来的指令的计算机就称之为从机。
五、掌握服务的概念服务是指在络的低层模块向⾼层提供功能性的⽀持,⾼层利⽤底层的"服务"来开展⼯作。
六、单⼯通信和双⼯通信的概念1.单⼯通信2.双⼯通信3.半双⼯通信七、计算机络的模型1.结合上图,掌握横向规程控制信息流和纵向数据流的概念。
2. TCP/IP络模型的概念,每层的名称、每层传输的信息格式(⽐特流、帧、包(报⽂分组)、报⽂)。
3.层间服务的模型,主要了解的概念:络的每个层次都要运⾏与该层次功能相适应的软件或硬件,这个硬件或者软件的运⾏活动称之为该层次的"实体"。
每⼀个实体都要向它的上⼀层提供⽀撑功能,提供⽀撑服务的⽅式是通过⼀个称为"服务访问点"(Service Access Point/简称SAP)的接⼝来提供的。
SAP实际上是⼀个确定的数据结构,它定义了两个功能层次之间的交互所需要的所有内容,两个相邻层之间的⼀切与"服务控制"相关的参数都通过这个地⽅来交换。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
A computer network, also called as a network, is a collection of computers interconnected by communication channels that allow sharing of resources and information.The rules and data formats数据格式for exchanging information in a computer network are defined by communications protocols协议. Well-known communications protocols are Ethernet, a hardware and Link Layer standard in local area networks, and the Internet Protocol Suite, which defines a set of protocols for internetworking, i.e. for data communication between multiple networks, as well as host-to-host data transfer, and application-specific data transmission formats.PropertiesFacilitate communicationsUsing a network, people can communicate efficiently and easily via email, instant messaging, chat rooms, telephone, video telephone calls, and video conferencing. Permit sharing of files, data, and other types of informationIn a network environment, authorized users may access data and information stored on other computers on the network. The capability of providing access to data and information on shared storage devices is an important feature of many networks. Share network and computing resourcesIn a networked environment, each computer on a network may access and use resources provided by devices on the network, such as printing a document on a shared network printer. Distributed computing uses computing resources across a network to accomplish tasks.May be insecureA computer network may be used by computer hackers to deploy computer viruses or computer worms on devices connected to the network, or to prevent these devices from normally accessing the network (denial of service).May interfere冲突with other technologiesPower line communication strongly disturbs certain forms of radio communication, e.g., amateur radio.[5] It may also interfere with last mile access technologies such as ADSL and VDSL.May be difficult to set upA complex computer network may be difficult to set up. It may also be very costly to set up an effective computer network in a large organization or company.OSI ModelData unit Layer FunctionHost layers Data7.ApplicationNetwork process to application6.PresentationData representation, encryption anddecryption, convert machine dependent datato machine independent data5. SessionInterhost communication, managing sessionsbetween applicationsSegments段 4. TransportEnd-to-end connections, reliability and flowcontrolMedia layers Packet/Datagram 3. Network Path determination and logical addressing Frame 2. Data link Physical addressingBit 1. Physical Media, signal and binary transmissionA wide area network (WAN) is a telecommunication network that covers a broad area (links across national boundaries). People utilize WANs to transfer data from various geographical locations. In essence this mode of telecommunication allows a business to effectively carry out its daily function regardless of location.This is in contrast with personal area networks (PANs), local area networks (LANs), campus area networks (CANs), or metropolitan area networks (MANs) which are usually limited to a room, building, campus or specific metropolitan area (e.g., a city) respectively.TCP/IPThe TCP/IP model (Transmission Control Protocol/Internet Protocol) is a descriptive framework描述的框架of computer network protocols. And Transmission Control Protocol/Internet Protocol is the most important protocols of the Internet Protocol Suite网络协议簇The TCP/IP model describes a set of guidelines and performances of specific networking protocols to enable computers to communicate over a network. TCP/IP specifies how data should be formatted格式化, addressed, transmitted, routed and received at the destination. There are a variety of different types of protocols for communication services between computers.The link layer makes the host connected directly by hardware components部分. The internet layer facilitates促进the interconnection of local networks. Host-to-host communication tasks are handled in the transport layer, transmit data between hosts using protocols like the Transmission Control Protocol and the User Datagram Protocol (UDP). Finally, the highest-level application layer contains allprotocols that are defined each specifically for the functioning运行of data communications services.pppIn networking, the Point-to-Point Protocol (PPP) is a data link protocol commonly used in establishing a direct connection between two networking nodes. It can provide connection authentication, transmission encryption, and compression. PPP is commonly used as a data link layer protocol for connection over synchronous and asynchronous circuits.PPP is used over many types of physical networks including serial cable, phone line, trunk line, cellular移动telephone, specialized radio links, and fiber optic光纤links such as SONET. PPP is also used over Internet access connections (now marketed as "broadband"). Internet service providers (ISPs) have used PPP for customer dial-up access to the Internet, since IP packets cannot be transmitted over a modem line on their own, without some data link protocol.FSC Frame Check SequenceCRC Cyclic redundancy checkIPThe Internet Protocol (IP) is the principal communications protocol used for relaying 广播datagrams (packets) across an internetwork using the Internet Protocol Suite. Responsible for routing packets across network boundaries, it is the primary protocol that establishes the Internet.IP is the primary protocol in the Internet Layer of the Internet Protocol Suite and has the task of delivering datagrams from the source host to the destination host solely based on their addresses. For this purpose, IP defines addressing methods and structures for datagram encapsulation.The first major version of IP, now referred to as Internet Protocol Version 4 (IPv4) is the dominant protocol of the Internet, although the successor, Internet Protocol Version 6 (IPv6) is in active, growing deployment worldwide.。
