Mobile agents based routing protocol for mobile ad hoc networks
Routing Protocol

7.2 路由协议路由协议是路由器软件中的重要组成部分。
路由器为互联的网络之间选择最佳的通信路都是通过这些路由协议来完成的。
路由协议的作用还在于建立以及维护路由表。
路由表用于为每个IP包选择输出端口或下一跳地址。
开放的路由协议主要包含RIP、OSPF、IS-IS以及Cisco公司私有的IGRP。
RIP是距离向量路由协议,一般用于企业内部小规模网络。
OSPF 和IS-IS协议的原理和实现都类似,是链路状态协议,一般用于大规模企业网或运营商网络。
7.2.1 静态路由与默认路由静态路由是在路由器中设置固定的路由表,即指定固定的传输路径,除非网络管理干预,否则将不会自动更改。
所以当网络的拓扑结构或链路的状态发生变化时,需要手动去修改路由表中相关的静态路由信息。
静态路由信息在默认情况下是私有的,不会传递给其他的路由器。
当然,网管员也可以通过对路由器进行设置使之成为共享的。
1.静态路由静态路由是一种特殊的路由,它由管理员手工配置而成。
通过静态路由的配置可建立一个互通的网络,但这种配置问题在于:当一个网络故障发生后,静态路由不会自动发生改变,必须有管理员的介入。
在组网结构比较简单的网络中,只需配置静态路由就可以使路由器正常工作,仔细设置和使用静态路由可以改进网络的性能,并可为重要的应用保证带宽。
静态路由还有如下的属性:可达路由。
正常的路由都属于这种情况,即IP 报文按照目的地标示的路由被送往下一跳,这是静态路由的一般用法。
目的地不可达的路由。
当到某一目的地的静态路由具有“丢弃”属性时,任何去往该目的地的IP报文都将被丢弃,并且通知源主机目的地不可达。
目的地为黑洞的路由。
当到某一目的地的静态路由具有“黑洞”属性时,任何去往该目的地的IP报文都将被丢弃,并且不通知源主机。
其中“丢弃”和“黑洞”属性一般用来控制本路由器可达目的地的范围,辅助网络故障的诊断。
通过配置静态路由,可以人为地指定对某一网络访问时所要经过的路径。
移动通信常用词汇中英文对照表
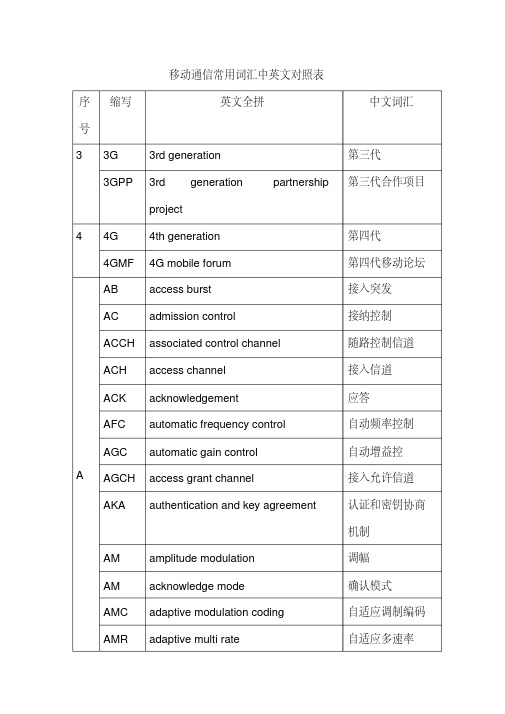
移动通信常用词汇中英文对照表序号缩写英文全拼中文词汇33G3rd generation第三代3GPP3rd generation partnershipproject第三代合作项目44G4th generation第四代4GMF4G mobile forum第四代移动论坛A AB access burst接入突发AC admission control接纳控制ACCH associated control channel随路控制信道ACH access channel接入信道ACK acknowledgement应答AFC automatic frequency control自动频率控制AGC automatic gain control自动增益控AGCH access grant channel接入允许信道AKA authentication and key agreement认证和密钥协商机制AM amplitude modulation调幅AM acknowledge mode确认模式AMC adaptive modulation coding自适应调制编码AMR adaptive multi rate自适应多速率ANM answer message应答消息ARQ automatic repeat request自动重发请求AS access slot接入时隙ASK amplitude shift keying振幅键控ATM asynchronous transfer mode异步转移模式AUC authentication centre鉴权(认证)中心B B3G beyond 3G超(后)3GBB Base band基带信号BCCH broadcast control channel广播控制信道BCH broadcast channel广播信道BPSK binary phase shift keying二进制相移键控BS base station基站BSC base station controller基站控制器BSC binary symmetric channel二进制对称信道BSS base station system基站系统BTS base transceiver station基站收发信机续附录A序号缩写英文全拼中文词汇C CAI common air interface公共空中接口CATT China academy oftelecommunication technology中国电信技术研究院CB cell broadcast小区广播CBC cell broadcast centre小区广播中心CBS cell broadcast service小区广播业务CCH control channel控制信道CCIR consultative committee oninternational radio国际无线电咨询委员会CCITT international consultativecommittee ontelegraphy and telephone国际电报电话咨询委员会CDMA code division multiple access码分多址CEPT conference Europe of post andtelecommunications欧洲邮电行政大会CG counting gateway计费网关CM connection management连接管理CN core network核心网CPCCH common power control channel公共功率控制信道CS circuit switch电路交换CT- 2cordless telephone secondgeneration第二代无绳电话CTCH common traffic channel公共业务信道CWTS China wireless telecommunication standard group 中国无线通信标准组D DCA Dynamic channel allocation动态信道分配DCCH dedicated control channel专用控制信道DCFE dedicated control function entity专用控制功能实体DCH dedicated channel专用信道DCN digital communication network数字通信网络DCS-1800'digital communication system at1800MHz1800MHz数字通信系统DECT digital European cordlesstelephone欧洲数字无蝇电话DFE decision feedback equalizer判决反馈均衡器DHO diversity handover分集切换DL downlink下行链路DLC digital link control数字链路控制DM disconnect mode非连接模式DOA direction of arrival到达方向DPDCH dedicated physical data channel专用物理数据信道DS direct spreading直接扩频DSS1digital subscriber signaling No.11号数字用户信令系统DSSS direct sequence spread spectrum直接序列扩频DTCH dedicated traffic channel专用业务信道DTMF dual tone multiple frequency双音多频续附录A序号缩写英文全拼中文词汇E EFR enhanced full rate增强型全速率EGPRS enhanced GPRS增强型GPRS EIA electronic industry association美国电子工业协会EIR equipment identity register设备标识寄存器ESA European space agency欧洲空间局ESN electronic serial number电子序列号码ETSI European telecommunication 欧洲电信标准standard institute协会F FACH forward access channel前向接入信道FB feedback反馈FBD feedback diversity反馈式发射分集FBF feedback filter反馈滤波器FBI feedback information反馈信息FCC federal communication commission美国联邦通信委员会FCCH frequency correction channel频率校正信道FCH fundamental channel基本信道FDD frequency division duplex频分双工FDMA frequency division multipleaccess频分多址FEC forward error correction前向纠错FER frame error rate误帧率FFPC fast forward power control快速前向功率控制FH frequency hopping跳频FM frequency modulation调频FPLMTS future public land mobiletelecommunication system未来公用陆地移动通信系统FSK frequency shift keying频移键控FT frame type帧类型GGC general control通用控制GI guard interval保护间隔GMM GPRS mobility management通用分组无线业务移动性管理GP guard period保护周期GPRS general packet radio service通用分组无线业务GPS global positioning system全球定位系统GSM global system for mobilecommunication(group specialmobile)全球移动通信系统续附录A序号缩写英文全拼中文词汇HC handover control切换控制HCS hierarchical cell structure混合小区结构H HCS header check sequence报头检验序列HHO hard band over硬切换HLR home location register归属位置寄存器HO handover切换HS high speed高速HSS home subscriber server归属用户服务器HT hill terrain典型山区I IAM initial address message初始地址消息ICC international conference oncommunications国际通信会议ICO intermediate circular orbit中轨道IEEE the institute of electrical andelectronics engineers电器和电子工程师协会IMARSAT International maritimetelecommunicationsatelliteorganization国际海事通信卫星组织IMEI international mobile equipmentidentity国际移动设备码IMSI international mobile subscriber 国际移动用户identity标识码IMT- 2000international mobile telecommunications 2000国际移动通信2000IMTS improved mobile telephone service 改进的移动电话服务IN intelligent network智能网IP internet protocol因特网协议IPv4IP version 4IP第四版本IPv6IP version 6IP第六版本IS- 95interim standard No. 95美国CDMA蜂窝系统标准ISDN integrated service digitalnetwork 综合业务数字网ISO international standard organization 国际标准化组织ITU internationaltelecommunication union国际电信联盟IWF inter working function互通功能J JD joint detection联合检测LA location area位置区LAN local area network局城同LC load control负荷控制L LCU logical control unit逻辑控制单元LLC logical link control逻辑链路控制LQC link quality control链路质量控制LR location registration位置登记续附录A序号缩写英文全拼中文词汇M MA multiple access多址接入MAI multiple accessinterference多址干扰MCC mobile user country code移动用户所属国家代码MC -CDMA multiple carrier CDMA多载波码分多址MCS modulation and code scheme调制和编码方案ME mobile equipment移动设备MFD maximum free distance最大自由距离MGCF media gateway controlfunction媒体网关控制功能MGW media gateway媒体网关MHS message handle system消息处理系统MIMO multiple input and multipleoutput多输入多输出MM mobility management移动管理MRF media resource function媒体资源功能MRFC media resource functioncontroller 媒体资源功能控制器MS mobile station移动台MSC mobile switching center移动业务交换中心MSIN mobile subscriber identity移动用户识别号MSISDNN mobile subscriber ISDNnumber 移动用户国际ISDN号码MSRN mobile subscribe roamingnumber移动用户漫游号MT mobile terminal移动终端MTSO mobile telephone switchoffice移动电话交换局MUI mobile user identifier移动用户标识符MUX multiplex复接N NAS non access stratum非接入层NB normal burst常规突发HDC national district code国内地区码NID network identity网络标志NMS network management system网络管理系统NMSI national mobile subscriberidentity 国内移动用户识别码NMT Nordic mobile telephone北欧移动电话NNI network node interface网络节点接口NSS network subsystem网络子系统O O&M operations and maintenance操作维护OMAP operations, maintenance andadministration part操作维护和管理部分OMC operations and maintenancecenter操作维护中心OSI open system interconnection开发系统互连OTD orthogonal transmitdiversity正交发射分集续附录A序号缩写英文全拼中文词汇PA paging area寻呼区PABX private automatic branchexchange专用自动交换机P PACCH packet associated channel分组辅助控制信道PACS personal accesscommunication services个人接入通信业务PAR peak-to-average ratio峰值平均功率比PC power control功率控制PCG power control group功率控制组PCH paging channel寻呼信道PCM pulse code modulation脉冲编码调制PCN personal communicationnetwork个人通信网PCS personal communicationsystem个人通信系统PDC personal digital cellular个人数字蜂窝系统PDCH packet dedicated controlchannels分组专用控制信道PDN public data network公用数据网PDTCH packet data trafficchannel分组数据业务信道PDU protocol data unit协议数据单元PG processing gain处理增益PHY physical layer物理层PI paging indicator寻呼指示器PICH paging indicator channel寻呼指示信道PLMN public land mobile network公共陆地移动网PN pseudo noise伪随机噪声PNCH packet notificationchannel分组通知信道PPP point-to-point protocol点对点协议PRACH physical random accesschannel物理随机接入信道PS packet switch分组交换PSK phase shift keying相移键控PSTN public switched telephonenetwork公共电话交换网络PU payload unit有效载荷单元QPCH quick paging channel快速寻呼信道R RA rural area乡村地区RA registration area登记区RACH random access channel随机接入信道RAN radio access network无线接入网RBP radio burst protocol无线突发协议REJ reject拒绝REL release释放RF radio frequency射频RFE routing function entity路由功能实体续附录A序号缩写英文全拼中文词汇R RL radio link无线链路RLC radio link control无线链路控制RLCP radio link controlprotocol无线链路控制协议RLP radio link protocol无线链路协议RNC radio network controller无线网络控制器RNT radio network terminal无线网络终端RR radio resources无线资源RRM radio resource management无线资源管理RTT radio transmissiontechnology无线传输技术RU receive unit接收单元Rx receiver接收机SA service area服务区城SA smart antenna智能天线SAP service access point服务接入点SAT supervisory audio tone检测音S SB synchronization bit同步比特SCC system control center系统控制中心SCCH synchronization controlchannel同步控制信道SCH synchronization channel同步信道SCP service control point业务控制点SCTP stream controltransmission protocol流控制传输协议SDH synchronization digitalhierarchy同步数字序列SDMA space division multipleaccess空分多址SDU service data unit业务数据单元SGW signaling gateway信令网关SIB system information block系统信息块SID system identity系统标志SIM subscriber identitymodule用户识别模块SIR signal interference ratio信噪比SLF subscription locationfunction签约位置功能SMS short message service短消息业务SN subscriber number移动用户号码SOM start of message信息启动比特SP switching point切换点信令无线突发协议SRBP signaling radio burstprotocolSRLP signaling radio link信令无线链路协议protocolSS spread spectrum扩展频谱特定业务协调功能SSCF service specificcoordination functionSYNC synchronization同步续附录A缩写英文全拼中文词汇序号全接入通信系统TACS total access communicationsystemTCH traffic channel业务信道TCP transfer control protocol传输控制协议TDD time division duplex时分双工TE terminal equipment终端设备T TF transport format传输格式TFS transport format set传输格式集TH time hopping疏时TLDN temporary local directorynumber临时本地号码TMSI temporary mobilesubscriber identity临时移动用户识别TPC transmit power control发射功率控制TS time slot时隙TSN transmission sequencenumber传输序列号TTI transmission time interval传输时间间隔TU typical urban典型市区U UDP User datagram protocol用户数据报协议UE user equipment用户设备UHF ultra high frequency甚高频UL uplink上行链路UMTS Universal mobiletelecommunication system通用移动通信系统UPT universal personaltelecommunication通用个人通信UTRA UMTS terrestrial radio UMTS陆地无线接入accessUTRAN UMTS terrestrial radioaccess network UMTS陆地无线接入网V VBR variable bit rate可变比特速率VC virtual circuit虚电路VCC virtual circuit connection虚电路连接VHF very high frequency超高频VLR visit location register访问位置寄存器VMSC visited MSC被访MSCVR-QAM variable rate QAM变速率QAMW WARC world administrative radioconference世界无线电管理会议WCDMA wideband code divisionmultiple access宽带码分多址WLAN wireless local areanetwork无线局城网WWRF wireless world researchforum世纪无线研究论坛。
Gossip-based ad hoc routing

a r X i v :c s .N I /0209011 v 1 5 S e p 2002G ossip-Based Ad Hoc RoutingZygmunt J.Haas Joseph Y .Halpern Li LiSchool of Electrical and Computer Engineering/Department of Computer ScienceCornell Universityhaas@ {halpern,lili }@Abstract —Many ad hoc routing protocols are based on some variant of flooding.Despite various optimizations,many routing messa ges are prop-agated unnecessarily.We propose a gossiping-based approa ch,where each node forwards a message with some probability,to reduce the ov erhead of the routing protocols.Gossiping exhibits bimodal behavio r in sufficiently large networks:in some executions,the gossip dies out quic kly and hardly any node gets the message;in the remaining executions,a sub stantial frac-tion of the nodes gets the message.The fraction of execution s in which most nodes get the message depends on the gossiping probability a nd the topol-ogy of the network.In the networks we have considered,using g ossiping probability between 0.6and 0.8suffices to ensure that almost every node gets the message in almost every execution.For large networ ks,this sim-ple gossiping protocol uses up to 35%fewer messages than flood ing,with improved performance.Gossiping can also be combined with va rious opti-mizations of flooding to yield further benefits.Simulations show that adding gossiping to AODV results in significant performance improv ement,even in networks as small as 150nodes.We expect that the improvemen t should be even more significant in larger networks.I.I NTRODUCTIONAn ad hoc network is a multi-hop wireless network with no fixed infrastructure.Rooftop networks and sensor networks are two existing types of networks that might be implemented using the ad hoc networking technology.Ad hoc networks can be use-fully deployed in applications such as disaster relief,tetherless classrooms,and battlefield situations.In ad hoc networks,the power supply of individual nodes is limited,wireless bandwidth is limited,and the channel condition can vary greatly.Moreover,since nodes can be mobile,routes may constantly change.Thus,to enable efficient communica-tion,robust routing protocols must be developed.Many ad hoc routing protocols have been proposed.Some,such as LAR [13],GPSR [12],and DREAM [1]assume that nodes are equipped with GPS hardware and thus know their lo-cations;others,such as DSR [11],AODV [18],ZRP [9],and TORA [17],do not make this assumption.Essentially all proto-cols that do not use GPS (and some that do,such as LAR and DREAM)make use of flooding,usually with some optimiza-tions.Despite the optimizations,in routing protocols that use flood-ing,many routing messages are propagated unnecessarily.In this paper,we show that gossiping —essentially,tossing a coin to decide whether or not to forward a message—can be used to significantly reduce the number of routing messages sent.It follows from results in percolation theory [7],[15]that gos-siping exhibits a certain type of bimodal behavior.Let the gossip probability be p .Then,in sufficiently large “nice”graphs,there are fractions θS (p )and θR (p )such that the gossip quickly diesThe work of Z.Haas was supported in part by NSF under grant number ANI-9980521and ONR under contract number N00014-00-1-0564.The work of J.Halpern and L.Li was supported in part by NSF under grants grants IRI-96-25901,IIS-0090145,and NCR97-25251,and ONR under grants N00014-00-1-03-41,N00014-01-10-511,and N00014-01-1-0795.out in 1−θS (p )of the executions and,in almost all of the frac-tion θS (p )of the executions where the gossip does not die out,a fraction θR (p )of the nodes get the message.Moreover,in many cases of interest,θR (p )is close to 1.Thus,in almost all execu-tions of the algorithm,either hardly any nodes receive the mes-sage,or most of them do.Ideally,we could make the fraction of executions where the gossip dies out relatively low while also keeping the gossip probability low,to reduce the message over-head.The goal of this paper is to investigate the extent to which this can be done.Our results show that,by using appropriate heuristics,we can save up to 35%message overhead compared to flooding.Furthermore,adding gossiping to a protocol such as AODV not only gives improvements in the number of messages sent,but also results in improved network performance in terms of end-to-end latency and throughput.(For readers unfamiliar with AODV ,a brief overview is given in SectionV-A.)We ex-pect that the various optimizations applied to flooding by other protocols (for example,the cluster-based scheme of [16])can also be usefully combined with gossiping to get further perfor-mance improvements.We are certainly not the first to use gossiping in networking applications.For example,it has been applied in networked databases to spread updates among nodes [6]and to multicast-ing [2].However,in almost all of the earlier work on gossiping,it is assumed that any node in the network can send a message to any other node,either because there is a direct link to that node or a route to that node is known.Gossiping proceeds by choosing some set of nodes at random to which to gossip.We do not have the luxury of being able to make such an assumption in the context of ad hoc networks.Our problem is to find routes to different nodes.In an ad hoc network,if a message is transmitted by a node,due to the broadcasting nature of radio communications,the message is usually received by all the nodes one hop away from the sender.Because of the fact that wireless resources are ex-pensive,it makes sense to take advantage of this physical-layer broadcasting feature of the radio transmission.In our gossiping protocol,we control the probability with which this physical-layer broadcast is sent.There has been some recent work on applying gossiping in ad hoc networks,but the focus and thus the techniques used have been very different from our work.Vahdat and Becker [22]apply gossiping to ad hoc unicast routing.However,their usage of gossiping is very different from ours.In their work,they try to ensure that messages are eventually delivered even if there is no connected path between the source and the destina-tion at any given point in time.As long as there exists a path using communication links at some point in time,messages can be delivered through a random pair-wise exchanges among mo-bile hosts.Their techniques are not intended for(and would not perform well in)our setting,where we are trying tofind routes that we assume exist(because network partition is a rare event).Chandra et al.[4]use a gossiping mechanism to improve multicast reliability in ad hoc networks;they do not use gossip-ing to reduce the number of messages sent.Indeed,they start with an arbitrary,possibly unreliable,multicast protocol to mul-ticast a message.They then use gossiping(under the assumption that routes are known)to randomly exchange messages between nodes in order to recover lost messages.Heinzelman et al.[10] have applied gossiping in data dissemination in wireless sen-sor networks,using techniques similar in spirit to those of[22]. Again,the setting and results are quite different from ours.Ni et al.[16]proposefive different approaches to reduce broadcast redundancy.One of them(briefly mentioned in a few sentences) is gossiping.However,they do not study the properties of gos-siping nor do they consider heuristics for dealing with problems introduced by gossiping in realistic ad hoc network topologies. Their experiments do show,however,that,in a100-node net-work,using gossiping can save messages.The rest of this paper is organized as follows:Section II dis-cusses the basic bimodal effect in more detail.Section III pro-vides experimental evidence of the bimodal effect in networks of reasonable size,and also gives a sense of how the probability varies with the average degree of the network and initial con-ditions.Section IV presents a number of heuristics that should improve the performance of gossiping in networks of interests, and investigates the extent to which they do so experimentally. Section V shows that gossiping can help in practical settings,by considering the effect of adding gossiping to AODV.We show by simulation that even in networks with150nodes only,adding gossiping to AODV can result in significant performance im-provements on all standard metrics.We expect that this im-provement will be even more significant in larger networks.Sec-tion VI concludes our paper.II.T HE BIMODAL BEHAVIOR OF GOSSIPINGSinceflooding is a basic element in many of the ad hoc rout-ing protocols,as mentioned in Section I,we start by comparing gossiping toflooding.Our basic gossiping protocol is simple.A source sends the route request with probability1.When a nodefirst receives a route request,with probability p it broadcasts the request to its neighbors and with probability1−p it discards the request;if the node receives the same route request again,it is discarded. Thus,a node broadcasts a given route request at most once.This simple protocol is called GOSSIP1(p).GOSSIP1has a slight problem with initial conditions.If the source has relatively few neighbors,there is a chance that none of them will gossip,and the gossip will die.To make sure this does not happen,we gossip with probability1for thefirst k hops before continuing to gossip with probability p.We call this modified protocol GOSSIP1(p,k).1The performance of GOSSIP1(p,k)clearly depends on the choice of p and k.Clearly,GOSSIP1(1,1)is equivalent toflood-1Of course,the fact that gossiping has difficulties if a node has relatively few neighbors is true not just initially.We return to this point in the next section when we discuss optimizations.ing.What happens in general?That depends in part on the topology of the network(particularly the average degree of the network nodes),the gossip probability p,and the initial condi-tions(as determined by k).If we think of gossiping as spread-ing a disease in an epidemic,this simply says that the likelihood of an epidemic spreading depends in part on how many people each person can infect(the degree),the likelihood of the infec-tion spreading(the gossip probability),and how many people are initially infected.As we said in the introduction,gossiping and,in particular, the performance of GOSSIP1(p,0)(that is,the scenario where even the source gossips with probability p)has been well stud-ied in the work on percolation theory[7],[15].Quite a few types of networks have been studied in the literature.In this section,we focus on two of them.Wefirst study regular net-works,since they allow us to easily analyze how GOSSIP1be-haves with respect to different parameters,such as the gossip probability,network size,and node degree,without other com-plicating factors.We then study random networks constructed as follows.Nodes are placed at random on a two-dimensional area;an edge is placed between any pair of nodes less than a fixed distance d apart.This type of random graph seems appro-priate for modeling a number of applications involving ad hoc networks.Nodes have a limited amount of transmission power, and so can communicate only with reasonably close nodes.The random placement can be viewed as modeling features such as the random mobility of nodes and the random placement of sen-sors in a large region.The following theorem gives a sense of the type of results that have been proved.Theorem II.1:For all p≥0,for all infinite regular graphs G,and for almost all(i.e.,a measure1subset)of the infinite random graphs G constructed as above,if GOSSIP1(p,0)is used by every node to spread a message,then there is a well-defined probabilityθS0(p)<1that the message reaches infinitely many nodes.Moreover,the probabilityθF0(p)that a node receives the message and forwards it in an execution where the message reaches infinitely many nodes is equal toθS0(p).2Note that the probability of a message dying out(i.e.,not spreading to infinitely many nodes)is averaged over the exe-cutions of the algorithm.That is,the theorem says that if we execute the algorithm repeatedly,the probability that a message does not die out in any given execution isθS0(p).On the other hand,θF0(p)talks about the probability that a node receives and forwards the message in a given execution of the algorithm.The intuition behind the equality ofθS0(p)andθF0(p)is easy to ex-plain.A gossip initiated by a source n0dies out if there is a set of nodes N that disconnects n0from the rest of the graph; that is,every infinite path starting at n0must go through a node in N.Thus,θS0(p)is the probability that there is no discon-necting set N such that none of the nodes in N forward the message.(Note that N could consist of the singleton node n0 itself.)Similarly,the probabilityθF0(p)that a random node n receives and forwards the message is precisely the probabil-ity that there is no set N such that N disconnects n from n0 and none of the nodes in N forwards the message.Therefore, 2Note that our bimodal effect is different from[2].They describe a bimodal behavior where either all or no process receives the multicast message.3θS0(p)=θF0(p)=defθ0(p).It follows from these results that,in an execution where the message does not die out,the probability that a random node receives the message isθ0(p)/p,since receiving the message is independent of forwarding it.Thus,in terms of the notation used in the introduction,θS(p)=θ0(p)andθR(p)=θ0(p)/p.LetθS k(p)be the probability that a message reaches infinitely many nodes if GOSSIP1(p,k)is used.It is easy to see that θS1(p)=θ0(p)/p,since the probability that the message reaches infinitely many nodes using GOSSIP1(p,1)is precisely the probability that a message reaches infinitely many nodes using GOSSIP1(p,0)given that the source actually gossips.However, note that the probability that a node receives and forwards a mes-sage if GOSSIP1(p,k)is used,given that the message does not die out,is stillθ0(p).That is,the probability that a node receives the message is independent of the choice of k.On the other hand,it is not hard to see that if each node learns the network topology in a zone of radius k(so that it can route a message directly to any node in its zone),then the probability that a node receives and forwards a message given that the message does not die out isθk(p).All these results are for infinite graphs.It is not hard to show that essentially the same results hold forfinite graphs,except possibly near the boundary.In sufficiently largefinite graphs, there will be two types of executions:those where hardly any node gets the message,and those where the message makes it all the way to the boundary.It follows easily from the Central Limit Theorem that,in sufficiently large graphs,in almost all executions where the gossip does not die out,a fractionθ0(p)/p nodes will get the message.That is,we expect the bimodal be-havior:either hardly any nodes get the message,or a fraction θ0(p)/p receive the message.As we shall see,in cases of in-terest,θ0(p)is quite close to p.Thus,in almost all executions of the algorithm in sufficiently large graphs,either hardly any nodes receive the message,or most do.This leads to a number of obvious questions:•How large is“sufficiently large”?•What is the behavior ofθk(p)for different graphs of interest?•What can be done to improve the performance of gossiping in realistic settings?We investigate these questions in the next two sections.III.G OSSIPING IN FINITE NETWORKSWe did a number of experiments to investigate the behavior of gossiping.We summarize some of the more interesting results here.We assumed an ideal MAC layer for these experiments be-cause we wanted to decouple the effect of the MAC layer from the effect of gossiping.An ideal MAC layer is one that is not subject to packet loss.When we consider more realistic sce-narios in Section V,we use the IEEE802.11MAC layer.In this section,we focus on regular graphs and the random graphs discussed in the previous section.Ourfirst set of experiments involves“medium-sized”net-works,with1000nodes.We start by considering a20-row by 50-column grid(i.e.,a regular graph of degree4).We focus on GOSSIP1(p,4),since taking k=4produces a reasonable tradeoff.(We report the effect of varying k towards the end of this section.)The results depend in part on where we place the route request source.As we would expect from the theoretical arguments,the location of the source node does not affect the fraction of nodes receiving the message.However,it does af-fect the number of executions in which the gossip dies out.The number of executions in which the gossip does not die out is higher for a more central node,and lower for a corner node.We report results here for the case where the route request source is at the left boundary of row10.Our experiments show that,on average,the performance for other locations of the route request source is somewhat better than the results reported here.The results are illustrated in Figure1.Notice that GOSSIP1(.72,4) on the grid ensures that almost all nodes get the message,except for a slight dropoff at distance greater than50.This dropoff is a boundary effect,which we discuss in more detail below.Note that the graph in Figure1(a)represents an average of120exe-cutions of the protocol.With gossip probability.72for this grid size,in almost all the executions of the algorithm,almost all nodes get the message.0.10.20.30.40.50.60.70.80.91102030405060FractionofnodesHop distance to sourceGOSSIP1(0.72,4)0.10.20.30.40.50.60.70.80.9100.10.20.30.40.50.60.70.80.91FractionofexecutionsFraction of nodes receiving the messageGOSSIP1(0.72,4)(a)(b)0.10.20.30.40.50.60.70.80.91102030405060FractionofnodesHop distance to sourceGOSSIP1(0.65,4)0.10.20.30.40.50.60.70.80.9100.10.20.30.40.50.60.70.80.91FractionofexecutionsFraction of nodes receiving the messageGOSSIP1(0.65,4)(c)(d)0.10.20.30.40.50.60.70.80.91102030405060FractionofnodesHop distance to sourceGOSSIP1(0.60,4)0.10.20.30.40.50.60.70.80.9100.10.20.30.40.50.60.70.80.91FractionofexecutionsFraction of nodes receiving the messageGOSSIP1(0.60,4)(e)(f)Fig.1T HE BEHAVIOR OF GOSSIPING ON A20×50GRID.The situation changes significantly if the gossip probability is even a little less than.7.For example,the average perfor-4 mance of GOSSIP1(.65,4)is shown in Figure1(c).As the graphshows,at distance40,on average58%of the nodes got the mes-sage.However,in this case,the graph is somewhat misleading.The averaging is hiding the true behavior.As we would expectfrom Theorem II.1,there is bimodal behavior.This is illustratedin Figure1(d).If we consider nodes at distance15–45(so as toignore initial effects and boundary effects),in14%of the exe-cutions,fewer than10%of the nodes get the message;in19%of the executions,fewer than20%of the nodes get the message; in59%of the executions,more than80%of the nodes get the message;and in41%of the executions,more than90%of the nodes get the message.If we lower the gossip probability further,we get the same bimodal behavior;all that changes is the fraction of executions in which all nodes and no nodes get the message.The dropoff is fairly rapid.For example,Figure1(e)and(f)describe the situation for GOSSIP1(.60,4).By the time we get to probability .6on the grid,in only4%executions of the algorithm is it the case that more than90%of the nodes get the message;in only 11%of the executions do more than80%of the nodes get the message;and in over50%of the executions,fewer than20%of the nodes get the messages.We also investigated the effect of the degree of the network on gossiping.Not surprisingly,increasing the degree makes it better and decreasing it makes it worse.In a20×50regular network of degree6,it suffices to gossip with probability.65to ensure that almost all nodes get the message in almost all exe-cutions;with gossip probability.6,we start to see some dropoff. (Again,the numbers given in the graph are actually the result of averaging over a number of executions of the algorithm,and mask the bimodal behavior observed in the executions.)On the other hand,for a20×50regular network of degree3,we need to gossip with probability.86to ensure that almost all nodes get the message in all executions.While easy to study,regular graphs are not typical of the topology we expect in practical ad hoc networks.Random graphs are a somewhat better model.We considered two fam-ilies of random graphs.In thefirst,we randomly placed1000 nodes in a7500m×3000m rectangular region,where a node can communicate with another node if it is no more than250 meters away.This results in a network with average degree8. Since real networks have boundaries,we did not experiment on wrap-around meshes.As we shall see,dealing with nodes near the boundary raises some interesting issues.The results of our experiments are illustrated in Figure2.The results are qual-itatively similar to those on the grid,as we would expect.In-deed,the bimodal effect is particularly pronounced with GOS-SIP1(.65,4),as shown in Figure2(d).If we consider nodes at distance15–35,Figure2(d)shows,in20%of the executions, fewer than10%of the nodes get the message;in70%of the ex-ecutions,over90%of the nodes get the message,and in75%of the executions,over80%of the nodes get the message.To consider what happens with a higher-degree network,we also placed1200nodes at random in the same rectangular re-gion;this results in a network with average degree10.In this network,it suffices to gossip with probability.65to ensure that almost all nodes get the message in almost all executions.All the graphs above show a marked dropoff in probability for0.10.20.30.40.50.60.70.80.9151015202530354045FractionofnodesHop distance to sourceGOSSIP1(0.75,4)0.10.20.30.40.50.60.70.80.9100.10.20.30.40.50.60.70.80.91FractionofexecutionsFraction of nodes receiving the messageGOSSIP1(0.75,4)(a)(b)0.10.20.30.40.50.60.70.80.9151015202530354045FractionofnodesHop distance to sourceGOSSIP1(0.65,4)0.10.20.30.40.50.60.70.80.9100.10.20.30.40.50.60.70.80.91FractionofexecutionsFraction of nodes receiving the messageGOSSIP1(0.65,4)(c)(d)Fig.2G OSSIPING ON A RANDOM NETWORK OF AVERAGE DEGREE8.nodes that are close to the boundary.This is not just an effect of averaging;this dropoff occurs in almost all executions of the algorithm.The dropoff is due to two related boundary effects.1.Distant nodes have fewer neighbors,since they are close to the boundary.2.Nodes at distance d from the source may well receive mes-sage due to“back-propagation”from nodes at distance d >d that get the message.Such back-propagation is not possible for boundary nodes.We discuss some techniques to deal with this dropoff in Sec-tion IV-D.We did one last set of experiments to better evaluateθk(p).In these experiments,we used1,000,000nodes on a1000×1000 grid,and placed the source at the center of row10.This is far enough away from the boundary to avoid significant boundary effects.3The results of using GOSSIP1(p,k)for particular val-ues of p are illustrated in Figure3.As these results show,the bimodal effect is very marked by the time we get to such a large network,and begins to closely approximate the results expected from the theorem.Figure4shows howθS4(p)varies with p.As we can see,if p is below.59,then the gossip dies out in almost all executions.θS4(p)then increases very rapidly,going from0 at.59to almost1at.65.(The rapid increase in the case of in-finite graphs follows from a deeper mathematical analysis,and has been discussed in the percolation theory literature[7],[15].)3Experimental results show that there are nontrivial boundary effects for val-ues of p very close to.59no matter where we place the source.Intuitively,this is because for p very close to,but above.59,the probability of having a large disconnecting set of nodes is nontrivial,and the boundary can help in forming such sets.50.10.20.30.40.50.60.70.80.91030060090012001500F r a c t i o n o f n o d e sHop distance to sourceGOSSIP1(0.65,4)0.10.20.30.40.50.60.70.80.9100.10.20.30.40.50.60.70.80.91F r a c t i o n o f e x e c u t i o n sFraction of nodes receiving the messageGOSSIP1(0.65,4)(a)(b)0.10.20.30.40.50.60.70.80.91030060090012001500F r a c t i o n o f n o d e sHop distance to sourceGOSSIP1(0.60,4)0.10.20.30.40.50.60.70.80.9100.10.20.30.40.50.60.70.80.91F r a c t i o n o f e x e c u t i o n sFraction of nodes receiving the messageGOSSIP1(0.60,4)(c)(d)Fig.3T HE BEHAVIOR OF GOSSIPING ONA1000X 1000GRID .0.10.20.30.40.50.60.70.80.9100.10.20.30.40.50.60.70.80.91θS 4(p )gossip probability pGOSSIP1(p,4)Fig.4θS 4(p )AS A FUNCTION OF THE GOSSIP PROBABILITY p ON A 1000X 1000GRID .Finally,we considered how θS k (p )and θRk (p )varied with kfor a fixed value of p .As theory predicts,θRk (p )does not changeat all with p .There is some effect on θSk (p ).Of course,since θS 1(p )=θS0(p )/p ,there is a significant jump as k goes from 0to1.As k increases beyond 1,there is an increase in θSk (p ),but it isnot so significant.For example,θS 1(.65)=.95,θS2(.65)=.98,and θS 5(.65)=1;similarly,θS 1(.6)=.53,θS4(.5)=.67,and θS 10=.73.IV.H EURISTICSTO I MPROVE THE P ERFORMANCE OFG OSSIPINGThe results of the previous section suggest an obvious way that gossiping can be applied in ad hoc routing.Rather than flooding,we use GOSSIP1(p ,k )with p sufficiently high to guar-antee that almost all nodes will receive the message in almostall executions.We can practically guarantee that the destina-tion node receives the message,while saving a fraction 1−p of messages.In cases of interest,where the threshold proba-bility seems to be about .65–.75,this means we can ensure that all nodes get the message using 25–35%fewer messages than flooding.Notice that,if the network is congested and every node has a congestion dropping probability f ,then to obtain the same results,the broadcast probability needs to be min(p/(1−f ),1).If congestion is very localized,then we can simply use p be-cause it is not likely to change the outcome of a given run of gossiping.However,the general interaction between gossiping and congestion is a topic that deserves further study.The basic gossiping scheme can be optimized in a number of ways,using ideas that have been applied to flooding and ideas specific to gossiping.We discuss some optimizations in the re-mainder of this section.This section is intended as a proof of concept showing that gossiping is a worthwhile approach to ex-plore.We do not attempt to do an exhaustive analysis to find the optimal parameters.A.A two-threshold schemeIn many cases of interest,a gossip protocol is run in conjunc-tion with other protocols.If the other protocols maintain fairly accurate information regarding a node’s neighbors,we can make use of this information to improve the performance of GOSSIP1further by a simple optimization.In a random network,unlike the grid,a node may have very few neighbors.In this case,the probability that none of the node’s neighbors will propagate the gossip is high.In general,we may want the gossip probability at a node to be a func-tion of its degree,where nodes with lower degree gossip with higher probability.To show the effect of this,we consider a special case here:a protocol with four parameters,p 1,k ,p 2,and n .As in GOSSIP1,p 1is the typical gossip probability and k is the number of hops with which we start gossiping with probability 1.The new features are p 2and n ;the idea is that the neighbors of a node with fewer than n neighbors gossip with probability p 2>p 1.That is,if a node has fewer than n neighbors,it instructs its immediate neighbors to broadcast with probability p 2rather than p 1.Call this modified protocol GOSSIP2(p 1,k,p 2,n ).To understand why the neighbors’gos-sip probability is increased if there are few neighbors,consider the initiator of the gossip.Clearly,if none of its neighbors gos-sip,then the gossip will die.If the initiator has many neighbors,even if each gossips with relatively low probability,the proba-bility that at least one of them will gossip is high.This is not the case if it has few neighbors.GOSSIP2is not of interest in regular networks.However,in random networks which typically have some sparse regions,it can have a significant impact.For example,for the random net-work with average degree 8first considered in Figure 2,GOS-SIP2(0.6,4,1,6)has better performance than GOSSIP1(0.75,4),as shown in Figure 5,while using 4%less messages than GOS-SIP1(0.75,4).Only when p ≥0.8does GOSSIP1(p,4)begin to have the same performance as GOSSIP2(0.6,4,1,6);how-ever,GOSSIP1(0.8,4)uses 13%more messages than GOS-SIP2(0.6,4,1,6).There may be other combinations of parameters for GOSSIP2。
Routing Protocol

RIPRIP 路由协议是目前在使用的路由协议中最简单的一种,RIP是为TCP/IP环境中开发的第一个路由协议标准,距离矢量协议,使用UDP520端口来操作1. 它每30秒发送一次广播更新,正因为它是使用了广播进行发送的更新,所以在大型网络中,如果路由条目多,所有主机都会监听接受路由更新,因此这样的路由协议是非常消耗带宽的。
2. 不适用触发更新。
触发更新就是一旦拓扑有所变化触发就会发送更新包。
加上它是每30秒钟发送一次,所以它的拓扑收敛速度非常的慢,在当今现在目前使用的网络中是不能接受的。
3.有类路由,也就是它不能发送子网掩码,这种也是在大型网络所不能接受的。
也正因为它是有类路由,所以它广播的路由可以没有掩码,这也就意味着能够在整个网络中进行发送。
默认为ver1RIP v2普遍应用于无类域间路由CIDR和可变长子网掩码VLSM支持无类路由和通过网络中子网掩码的发送,支持触发更新RIPv2的更新包使用广播地址224.0.0.9进行广播能够配置邻居包,配置了邻居后,能够使用单播进行发送,这样就减少了网络带宽流量支持在路由器之间支持Authentication无类路由协议在发送子网的时候会自动汇总,也就是意味着我一段10.10.10.0/24的网络将会被他使用10.0.0.0/8的这个大网络进行汇总过去。
一般在设备上默认都是汇总的。
所以我们在配置的路由协议的时候不要忘记配置no auto-summaryEIGRP它全称是增强型内部网关路由协议,属于无类路由协议它是一个非常流行的路由协议,(当然这是对cisco的设备来讲的。
别的设备不支持。
因为这是Cisco的私有路由协议)它是一个非常好的路由协议,当一个网络中规划好IP addr,它将会表现的更加出众特别是在大型网络中。
它是一种距离矢量协议,但它的特性看起来特别像是链路状态协议。
1.使用触发更新,只在拓扑有变更的时候才会有更新。
2.收敛速度非常快,特别是在大型网络中,一个网络中使用RIP 要数分钟的收敛,但通过EIGRP只需要几秒。
网络安全配置命令英语简称

网络安全配置命令英语简称1. ACL (Access Control List) - 访问控制列表2. ARP (Address Resolution Protocol) - 地址解析协议3. BGP (Border Gateway Protocol) - 边界网关协议4. DHCP (Dynamic Host Configuration Protocol) - 动态主机配置协议5. DNS (Domain Name System) - 域名系统6. FTP (File Transfer Protocol) - 文件传输协议7. HTTP (Hypertext Transfer Protocol) - 超文本传输协议8. HTTPS (Hypertext Transfer Protocol Secure) - 安全超文本传输协议9. ICMP (Internet Control Message Protocol) - 互联网控制消息协议10. IP (Internet Protocol) - 网际协议11. IPSec (Internet Protocol Security) - 网际协议安全性12. NAT (Network Address Translation) - 网络地址转换13. NTP (Network Time Protocol) - 网络时间协议14. OSPF (Open Shortest Path First) - 开放最短路径优先路由协议15. PPP (Point-to-Point Protocol) - 点对点协议16. RARP (Reverse Address Resolution Protocol) - 反向地址解析协议17. SMTP (Simple Mail Transfer Protocol) - 简单邮件传输协议18. SNMP (Simple Network Management Protocol) - 简单网络管理协议19. SSH (Secure Shell) - 安全外壳协议20. SSL (Secure Sockets Layer) - 安全套接层21. TCP (Transmission Control Protocol) - 传输控制协议22. Telnet (Telecommunication Network) - 远程登录服务23. TFTP (Trivial File Transfer Protocol) - 简单文件传输协议24. UDP (User Datagram Protocol) - 用户数据报协议25. VLAN (Virtual Local Area Network) - 虚拟局域网26. VPN (Virtual Private Network) - 虚拟私人网络27. VRRP (Virtual Router Redundancy Protocol) - 虚拟路由器冗余协议28. WEP (Wired Equivalent Privacy) - 有线等效保密29. WPA (Wi-Fi Protected Access) - Wi-Fi保护接入30. WPA2 (Wi-Fi Protected Access II) - Wi-Fi保护接入II。
一种支持高速移动自组织网络的路由协议

Co m u iat nd m nc i a Ne wor on t k
一
种支持高速移动 自组织 网络 的路 由协议 木
杨 共 燕 ,邝 育 军 ,隆 克 平
( 子 科 技 大 学 光 互 联 网 与 移 动 信 息 网 络 研 究 中 心 ,四 川 成 都 6 3 ) 电 17 1 1
和 鲁 棒 性 。 仿 真 结 果 表 明 ,MAO V 协 议 能 够 较 好 地 适 应 高速 移 动 的 网 络 环 境 , 在 一 定 程 度 上 降 低 I D 并
网 络 时 延 和 增 加 网络 吞 吐 量 。
关 键 词 :移 动 自组 网 ;A D O V;组 合 度 量 ;I MAO V D
K y WO d e r s:mo i A C n t o k ;A0D b l d HO ew r s e V:c mb n d o ie mer ;I t c MA0D i V
移 动 自组 网 ( NE 是 由 一 系 列 移 动 终 端 组 成 的 MA T) 无 固 定 基 础 设 施 的 多 跳 自组 织 网 络 系 统 …, 拓 扑 结 构 其
A DV路 由协 议 , I O O 即 MA DV(mpo e D 路 由协 议 。该 协 议 主 要 从 路 由 度 量 值 、 L O 消 息 的 发 I rv d AO V) HE L
移动代理服务器 Mobile Agent Server

移动代理服务器Mobile Agent Server一、是Mobile Agent Server的简称,是协助企业原有业务系统实现无线应用的接入工具,实现MAS接入后企业原有的业务系统可以方便的实现无线应用,如:OA 系统可以实现手机办公、邮件通知、手机审批等。
1、MAS系统组成和功能:MAS系统包括MAS终端、MAS服务器和MAS管理平台,中国移动通过在集团客户(主要为拥有完备企业信息系统的政府行业用户和企业)内部部署移动代理服务器,为集团客户提供的基于移动终端(包括短信、彩信、GPRS 、WAP、手机客户端等)的信息化应用服务。
通过移动代理服务器将不同的行业用户应用和业务延伸到移动终端。
1.1 MAS服务器组成和功能:MAS服务器的组成:MAS服务器由应用接入适配插件模块、业务调度模块、移动安全接入模块及管理模块组成。
各组成完成的功能:应用接入适配插件模块实现移动应用业务的移动应用接口,通过多种移动通讯方式完成移动办公、移动Email、数据的现场查询、采集、录入、WAP应用等移动应用业务。
业务处理模块对从应用系统接收到的数据信息进行处理,主要功能包括信息处理及路由、用户认证、业务调度、日志处理和QoS控制等。
移动安全接入模块一方面通过移动行业网关提供的接口协议,实现MAS服务器与行业网关的数据通信。
另一方面采用安全加密技术提供短信安全接入、彩信安全接入、GPRS安全接入、WAP安全接入、USSD安全接入、智能终端安全接入功能,通过这种方式实现信息的空中加密传输,为MAS终端提供安全服务。
管理模块完成MAS服务器的自管理和服务,可提供网络管理、认证鉴权在内的接口子模块。
可选用业务导航、路由管理、业务管理、数据管理、应用发布、统计分析、地址本管理、系统配置管理等功能模块。
1.2、MAS管理平台:MAS管理平台运行于移动公司,通过加密IP通道与MAS服务器进行通讯,完成对MAS服务器的管理和控制,具体的管理的内容有配置管理、认证管理、监控管理、故障管理、安全管理、升级维护管理。
IP组播地址

IP组播地址组播协议的地址在IP协议中属于D类地址。
D类地址是从224.0.0.0到239.255.255.255之间的IP地址其中224.0.0.0到224.0.0.255是被保留的地址。
组播协议的地址范围类似于一般的单播地址,被划分为两个大的地址范围,239.0.0.0—239.255.255.255是私有地址,供各个内部网在内部使用,这个地址的组播不能上公网,类似于单播协议使用的192.168.X.X和10.X.X.X。
224.0.1.0—238.255.255.255是公用的组播地址,可以用于Internet上。
下面是一些常见的有特殊用途的IP组播地址224.0.0.0 - Base address224.0.0.1 -网段中所有支持多播的主机224.0.0.2 -网段中所有支持多播的路由器224.0.0.4 -网段中所有的DVMRP路由器224.0.0.5 -所有的OSPF路由器224.0.0.6 -所有的OSPF指派路由器224.0.0.7 -所有的ST路由器224.0.0.8 -所有的ST主机224.0.0.9 -所有RIPv2路由器224.0.0.10 -网段中所有支的路由器224.0.0.11 - Mobile-Agents224.0.0.12 - DHCP server / relay agent服务专用地址224.0.0.13 -所有的PIM路由器224.0.0.22 -所有的IGMP路由器224.0.0.251 -所有的支持组播的DNS服务器224.0.0.9 RIPv2支持组播更新。
224.0.0.22 IGMPv2使用此地址,这个协议的本意是减少广播,让组员以组播形式通信。
224.0.0.5 224.0.0.6这两个是ospf协议使用的组播地址。
在broadcast network不论是DR,BDR,DRother,大家发送hello packet的时候目标地址都是AllSPFRouter(224.0.0.5);DRother向DR,BDR发送DD,LSA request或者LSA UPdate时目标地址是AllDRouter(224.0.0.6);DR,BDR向DRother发送DD,LSA Request或者LSA Update 时目标地址是AllSPFRouter(224.0.0.5);retransmit的LSA都是unicast,LSA ACK要看是explicit ack(unicast)还是implicit ack(multicast 224.0.0.6);组播IP地址与以太网二层MAC地址的映射:IP组播地址用于标识一个IP组播组。
olt设备与bras之间的通讯协议

olt设备与bras之间的通讯协议OLT设备与BRAS之间的通信协议一、引言OLT(Optical Line Terminal)设备和BRAS(Broadband Remote Access Server)是宽带接入网络中的重要组成部分,它们通过通信协议实现数据的传输和交换。
本文将介绍OLT设备与BRAS之间常用的通信协议,并探讨其工作原理和特点。
二、PPP协议PPP(Point-to-Point Protocol)是OLT设备与BRAS之间常用的通信协议之一。
它是一种在数据链路层进行点对点通信的协议,支持多种物理介质和网络层协议。
在OLT设备与BRAS之间建立连接时,PPP协议负责进行身份验证、链路建立和维护等工作。
通过PPP协议,OLT设备可以将用户的数据封装为PPP帧,并通过物理连接传输给BRAS。
三、L2TP协议L2TP(Layer 2 Tunneling Protocol)是OLT设备与BRAS之间另一种常用的通信协议。
它是一种在网络层进行隧道传输的协议,通常与PPP协议结合使用。
在OLT设备与BRAS之间建立连接时,L2TP 协议负责封装PPP帧,并将其通过IP网络传输。
L2TP协议提供了身份验证、数据加密等功能,保证了数据的安全性和可靠性。
四、BGP协议BGP(Border Gateway Protocol)是OLT设备与BRAS之间用于路由信息交换的协议。
在宽带接入网络中,BRAS负责管理用户的路由信息,而OLT设备则需要将用户的数据转发到正确的目的地。
通过BGP协议,OLT设备可以向BRAS学习到路由信息,并根据路由表进行数据的转发。
BGP协议具有高度的灵活性和可扩展性,适用于大规模网络环境。
五、RADIUS协议RADIUS(Remote Authentication Dial-In User Service)是OLT 设备与BRAS之间进行用户身份验证和账号管理的协议。
在用户接入宽带网络时,OLT设备会向BRAS发送用户的认证请求,并通过RADIUS协议将用户的身份信息传递给BRAS进行验证。
完整LTE缩略语
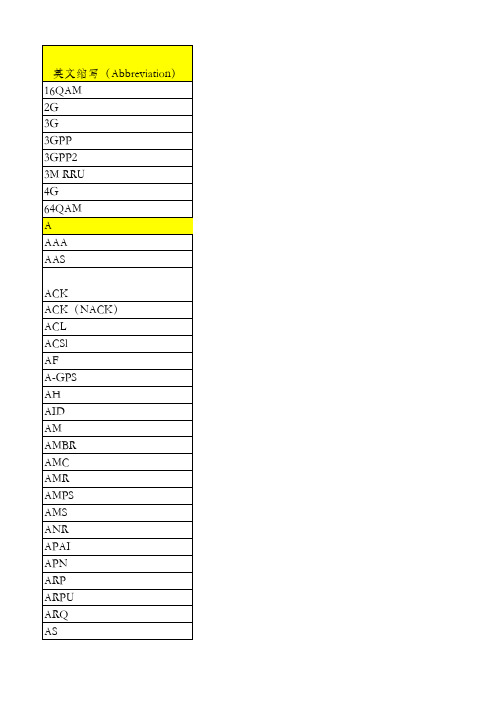
TPC TPMI TSTD TTI TX U UCI UDP UDPAP UE UL UL-SCH UM UMB UMTS UpPTS URL USIM USSD UTC UTRA UTRAN V VLAN VMIMO VoIP VP VRB VSWR W WAP WAP GW WCDMA WiMAX WLAN WRR
COD CP CPC CPE CPRI CQI CRC C-RNTI CS CS CSFB CSG D DAI D-AMPS DBCH D-BCH DC DCCH DC-HSDPA DCI DCS DFT DHCP DiffServ DL DL-SCH DM DM RS DMRS DOA DOS DRB DRS DRX DSCP
X X2 ZC
英文全称(English) 16 Quadrature Amplitude Modulation The Second generation The Third generation 3rd Generation Partnership Project 3rd Generation Partnership Project 2 Multi-band,MIMO,Multi-Standard_Radio Remote RadioUnit The Fourth Generation 64 Quadrature Amplitude Modulation Authentication Authorzation and Accounting Adaptive Antenna System Acknowledgement Acknowledgement/Negative-Acknowledgement Access Control List Average Cell Stay Interval Application Header Assisted-GPS Authentication Header Access Description Data Acknowledged Mode Aggregate Maximum Bit Rate Adaptive Modulation and coding AMR Adaptive MultiRate Advanced Mobile Telephone System Adaptive MIMO switching Automatic Neighbour Relation average packet arrival interval access point name Allocation and retention priority Averrage revenue per user (Automatic Repeat Request) access stratum Advanced Wireless Services
routing guide的用法

routing guide的用法Routing Guide的用法在路由器设置中,Routing Guide(路由指南)是一项重要的功能,用于指定数据包在网络中的传递路径。
以下是Routing Guide的一些常见用法,以及详细的解释:1. 静态路由(Static Routing)•静态路由是一种手动配置的路由方式,管理员需要手动输入目标网络和下一跳地址。
•静态路由适用于小型网络,在网络拓扑稳定且变动不频繁的情况下效果显著。
•静态路由配置简单,但随着网络规模增大,管理和配置静态路由会变得困难和繁琐。
2. 动态路由(Dynamic Routing)•动态路由是一种通过协议自动学习和更新路由表的路由方式。
•常见的动态路由协议有OSPF、RIP和EIGRP等。
•动态路由适用于大型网络或网络拓扑变化频繁的情况下,可以自动适应网络变化,并提供更好的路径选择和故障恢复能力。
3. 路由汇总(Route Summarization)•路由汇总是在路由表中对一组网络地址进行聚合,以降低路由表的大小。
•路由汇总可以减少路由器内存消耗、提高路由转发速度,并降低网络中的路由更新开销。
•路由汇总需要根据网络拓扑和路由协议的要求进行配置,以保证路由信息的准确性和可靠性。
4. 默认路由(Default Route)•默认路由是一种特殊的路由配置,用于指示当路由表中找不到匹配网络时,数据包应该转发到的下一跳地址。
•默认路由常用于连接到Internet的边缘路由器,将未知目标网络的数据包发送到ISP提供的出口网关。
•默认路由的配置可减少路由表的大小,并简化路由器配置。
5. 策略路由(Policy-Based Routing)•策略路由是一种基于某些特定策略或条件来选择路径的路由方式。
•策略路由可以根据源地址、目标地址、应用类型等条件来选择特定的路径。
•策略路由可以灵活地根据需求来控制流量走向,实现灵活的网络管理和负载均衡。
以上是一些常见的Routing Guide的用法及其详细解释。
3GPP 5G基站(BS)R16版本一致性测试英文原版(3GPP TS 38.141-1)

4.2.2
BS type 1-H.................................................................................................................................................. 26
4.3
Base station classes............................................................................................................................................27
1 Scope.......................................................................................................................................................13
All rights reserved. UMTS™ is a Trade Mark of ETSI registered for the benefit of its members 3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational Partners LTE™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM Association
移动通信术语中英文对照

移动通信术语中英文对照移动通信术语中英文对照一、通信网络1、移动通信网络(Mobile communication network)- 移动方式网络(Mobile telephone network)- 蜂窝网络(Cellular network)2、无线局域网(Wireless LAN)- Wi-Fi3、无线电接入网络(Wireless access network)- 码分多址接入(Code Division Multiple Access,CDMA) - 资源分配接入(Time Division Multiple Access,TDMA) - 正交分频多址接入(Orthogonal Frequency Division Multiple Access,OFDMA)4、固定通信网络(Fixed communication network)- PSTN(Public Switched Telephone Network)二、通信设备1、移动方式(Mobile phone)- 智能方式(Smartphone)- 方式卡(SIM Card)- 按键方式(Feature phone)- 通信基带芯片(Baseband chipset)2、无线路由器(Wireless router)3、通信基站(Base station)- 室内基站(Indoor base station)- 室外基站(Outdoor base station)- 微基站(Micro base station)- 宏基站(Macro base station)三、通信协议及技术1、移动通信协议(Mobile communication protocol)- GSM(Global System for Mobile Communications) - WCDMA(Wideband Code Division Multiple Access) - CDMA2000- LTE(Long-Term Evolution)- 5G2、数据通信标准(Data communication standard)- GPRS(General Packet Radio Service)- EDGE(Enhanced Data Rates for GSM Evolution) - HSPA(High-Speed Packet Access)- HSDPA(High-Speed Downlink Packet Access)- HSUPA(High-Speed Uplink Packet Access)3、无线通信技术(Wireless communication technology) - 蓝牙(Bluetooth)- NFC(Near Field Communication)- IR(Infrared)- GPS(Global Positioning System)四、通信服务与功能1、方式(Telephone)- 打方式(Make a call)- 接方式(Receive a call)2、短信(Short Message Service,SMS)- 发送短信(Send a message)- 收到短信(Receive a message)3、彩信(Multimedia Message Service,MMS) - 发送彩信(Send a MMS)- 收到彩信(Receive a MMS)4、上网(Mobile Internet)- 浏览网页(Browse the web)- 文件(Download files)- 视频通话(Video call)5、社交媒体(Social media)- 微博(Microblogging)- (WeChat)-6、移动支付(Mobile payment)- (Alipay)- 支付(WeChat Pay)7、应用软件(Mobile applications)- 游戏(Games)- 音乐(Music)- 视频(Videos)附件:无法律名词及注释:1、通信网络:指移动通信所依托的网络基础设施,用来实现移动方式通信、上网等功能。
The 18th Annual IEEE International Symposium on Personal, Indoor and Mobile Radio Communica

Efficient searching for resources and services is an important issue in various networks. There are two common methods employed for searching - flooding and random walks (RW). In wireless ad-hoc networks, reactive protocols such as AODV and DSR use flooding to locate the destination [16]. In webgraphs, search engines use breadth first search to perform a complete search of the web. However, to reduce the overhead of searching, agents or spiders based on RW, where the next hop is chosen uniformly among the neighbors of the node, or variations of the RW such as the RW strategy where the next hop is chosen as the node with maximum degree are widely used [14]. In peer-to-peer networks, both flooding and RW have been employed to locate services and resources [3, 4, 10]. RWs have been shown to induce lower overhead than constrained flooding for searching in peer-to-peer networks [4, 10]. Multiple RWs have been proposed for searching on unstructured peer-to-peer networks by Lv et al. [4]. However, the optimization of multiple RWs was not analyzed. Adaptive techniques based on RWs have been proposed for searching by Bisnik and Abhouzeid [15]. In the searching technique proposed in [15], the number of RW queries used for searching are varied depending on the previous performance of searching. Our work differs from previous approaches since we study the optimization between the number of queries and the time-to-live (W W O) of queries for different graph topologies. We study the performance of different search strategies based on RWs on ER random graphs and power law graphs generated using preferential attachment. Both these graph topologies are important since ad-hoc wireless networks can be modeled as ER random graphs [11] while the web graphs and peer-to-peer networks can be modeled as power law random graphs [10]. We study both a single query and multiple queries to search for the destination. We do not consider dynamic topologies in this paper. In case of multiple RW queries,
policy-based-route
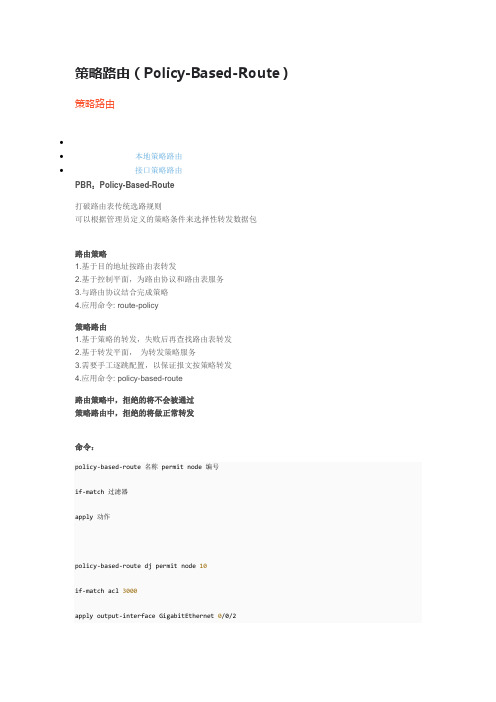
策略路由(Policy-Based-Route)策略路由••本地策略路由•接口策略路由PBR:Policy-Based-Route打破路由表传统选路规则可以根据管理员定义的策略条件来选择性转发数据包路由策略1.基于目的地址按路由表转发2.基于控制平面,为路由协议和路由表服务3.与路由协议结合完成策略4.应用命令: route-policy策略路由1.基于策略的转发,失败后再查找路由表转发2.基于转发平面,为转发策略服务3.需要手工逐跳配置,以保证报文按策略转发4.应用命令: policy-based-route路由策略中,拒绝的将不会被通过策略路由中,拒绝的将做正常转发命令:policy-based-route 名称 permit node 编号if-match 过滤器apply 动作policy-based-route dj permit node 10if-match acl 3000apply output-interface GigabitEthernet 0/0/2node之间是“或”的关系if-match之间是“与”的关系如果未匹配按普通路由转发本地策略路由仅对本机下发的报文进行处理,对转发报文不起作用相关命令policy-based-route dj permit node 10创建PBRif-match acl 2000配置IP地址匹配条件if-match packet-length 641000配置IP报文长度匹配条件apply output-interface g0/0/1 配置出站接口apply ip-address next-hop 12.0.0.2 配置下一-跳ip local policy-based-route djp 调用PBR接口策略路由仅对转发的报文进行处理,对本地下发报文不起作用通过流策略技术实现流策略:将流分类和流行为关联,形成模块化配置方式优点:节省配置,支持批量修改技术:Traffic Classifier:用if-match语句设定流分类的匹配规则TrafficBehavior:执行动作,例如重标记、重定向、负载分担、报文分片、流量限速、流量统计等等Traffic Policy:将流分类和流行为关联,应用到流量的入接口命令创建流分类traffic classifier 名称if-match创建流行为traffic behavior 名称创建流策略traffic policy 名称调用流策略traffic-policy 名称例:策略路由常采用Traffic-Policy工具实现首先使用ACL匹配目标流量然后对目标流量定义行为acl 3000rule permit ip source10.1.1.0 0.0.0.255 destnation 10.1.3.0 0.0.0.255 traffic classifier djp1if-match acl 3000traffic behavior djp2redirect ip-nexthop 12.1.1.2 重定向下一跳traffic policy djpclassifier djp1 behavior djp2 关联流策略int g0/0/2traffic-policy djp inbound验证流策略应用display traffic-policy applied-record。
5g ssb hdl 代码 -回复

5g ssb hdl 代码-回复如何编写5G Standalone Subcarrier Spacing Hopping Dynamic Link (5G SSB HDL) 代码第一步:了解5G SSB HDL的概念和作用5G SSB HDL是5G独立子载波间隔跳跃动态链接(5G SSB HDL)的缩写。
在5G通信中,SSB(Synchronization Signal Block)是用于初始同步和小区检测的重要信号块。
Hopping Dynamic Link是指SSB在频域上的跳频连接,可以增强系统的可靠性和适应性。
第二步:准备环境和工具为了编写5G SSB HDL代码,我们需要准备以下环境和工具:1. 电脑:可以是Windows、Mac或Linux系统2. 集成开发环境(IDE):如Matlab、Python等3. 5G NR软件开发包(SDK):可从5G设备厂商或开源社区获取第三步:创建SSB HDL代码文件在IDE中创建一个新的代码文件,并命名为"5g_ssb_hdl.m"(Matlab)或"5g_ssb_hdl.py"(Python)。
第四步:导入必要的库和模块在代码文件的开头导入所需的库和模块。
例如,在Matlab中,可以导入与5G NR相关的库,如5G Toolbox。
在Python中,可以导入numpy、scipy和pytthon库等。
第五步:定义参数和变量定义5G SSB HDL所需的参数和变量,包括子载波间隔、频率带宽、子载波数量等。
这些参数和变量将用于生成SSB HDL模式和配置资源。
第六步:生成频域资源根据所定义的参数和变量生成频域资源。
可以使用5G NR SDK中的函数或算法来生成SSB HDL模式和配置资源。
第七步:配置SSB HDL信号根据频域资源,配置SSB HDL信号的相关参数,如同步信号类型、子载波映射、参考信号位置等。
三星Rugby II手机说明书

Tough stuff.Samsung Rugby® IIInstant, clear connectionsin a seriously tough package.The Samsung Rugby II is a 3G (7.2 Mbps) rugged flip phone with on-the-job features like Push to Talk (PTT), aGPS and Video Share Calling. Plus, innovations like dual external speakers and Audience® dynamic noise suppression technology will get you through your day loud and clear.Built to last.The Rugby II is certified to Military Standard 810G compliance for shock, vibration, rain and temperature extremes. So you know it can handle everything from the job site to the rugged outdoors.Push to Talk instantly.Two-way-radio-style communication is only one button away. With a single push, you can dispatch job orders, get up-to-the-minute status on critical projects and more. PTT features include:• Unlimited Push to Talk Calls• Unlimited Group Calling• Call Me Alerts: Send Call Me texts to PTT contacts• Call Waiting: Accept voice calls and other PTT calls when you’re ready• Change to Voice Call: Just press a button to convert from a PTT call to a voice call• Contact Alerts: Know when one of your contacts becomes available for a PTT call • Online Administration: Web-based PTT contact administration option available • Presence Notification: See which of your contacts are available for a PTT callSamsung Rugby IIThis rugged phone is built fortough jobs and allows you tobe virtually on site from almostanywhere with instant, one-button Push to Talk and VideoShare Calling.• Quick Groups: Select contacts for agroup call without having to set upgroups ahead of time• Voice Messaging: Send voicemailinstantly to one or more peopleNavigate your work day.The Rugby II has aGPS, giving you anavigation device wherever you are. Plus,you can track your mobile workforce.• AT&T Navigator gets the most out ofaGPS to help you on the job• Enjoy turn-by-turn voice and on-screendirections, plus automatic re-routing ifyou miss a turn or hit congestion• Easily find the closest ATMs, restaurants,gas stations, Wi-Fi hotspots and more• Use TeleNav® Track and Xora to seeyour workers, vehicles and equipmentin the fieldShare what you see.The Rugby II features Video Share Callingwith true “see what I see” streaming.• Share on-site conditions with office oroff-site personnel for trouble shooting,remote issue assessment and more• Combine Video Share and PTT to be“on site” almost anywhere, saving timeand moneyA clear conversation.The Audience Voice Processor deliversthe most powerful and robust noisesuppression technology available today.It can dramatically reduce or eliminateunwanted noise from both yourenvironment and that on the other end.Includes:• Samsung Rugby II• Battery• Charger • USB Cable • CD• Quick Start GuideSamsung Rugby® II SpecificationsPhone Features:• Rugged construction, certified to Military Standard MIL-STD-810G• Quad-Band EDGE (850/900/1800/1900 MHz) worldphone • H SDPA 7.2 (UMTS) Tri-Band 850/1900/2100 MHz • B luetooth® v2.0• B right color display Advanced Features:• Push to Talk• One-touch GPS navigation • 2.0 MP CMOS camera • Video Share Calling • microSD™ card slot • Call List control• Audience® Voice ProcessorEmail and Internet Features:• Email client supporting: Yahoo! Mail, AOL Mail, Hotmail , AT&T Mail, Gmail • Mobile Web browsing• DataConnect tethering (use as a wireless PC modem, requires DataConnect plan)Device Specifications:• Internal Display: 2.2" 240 x 320 pixel 262K TFT • External Display: 1.3" 128 x 128 pixel CSTN • Dimensions: 4.01" H x 2.05" W x 0.86" D • Weight: 3.52 ounces• microSD expandable memory: up to 16 GB • TTY compatible • HAC compliant • Battery: 1300 mAh • Java MIDP 2.0• USB 2.0IMPORTANT INFORMATION: Limited time offer. Coverage not available in all areas. Device subject to availability. This device is sold for use on AT&T’s wireless systems. It may not be compatible with other wireless systems. Network speed is no indication of the speed at which your device sends or receives data. Actual speeds depend on distance from cell site, network availability and traffic, device, applications, tasks, file size and other factors. AT&T BroadbandConnect download speeds only available in AT&T BroadbandConnect markets. Specifications subject to change. Up to $36 activation fee applies. Certain benefits and service features may require you to purchase additional hardware and/or software, obtain a network connection and/or pay monthly access and/or per use charges. Subscriber must live and have a mailing address within AT&T’s wireless owned network coverage area. Availability, speed of delivery and timeliness of information is not guaranteed. Terms of service will vary based on selected service plans. Special credit and tenure restrictions and additional charges may apply to international roaming. Availability, quality of coverage and services while roaming are not guaranteed. Other conditions and restrictions apply. See business/service agreement, rate plan brochure(s) and coverage map(s) for details. Price and availability may vary by market and may not be available from independent retailers. Qualifying data plan required. Early Termination Fee: None if cancelled in the first 30 days, but up to $35 restocking fee may apply to equipment returns; thereafter up to $175. Some agents impose additional fees. Video Share not available in all areas. Video Share requires the sender and receiver to have compatible feature and be in a 3G coverage area to share video. Both sender and receiver will be charged for any call minutes. Only the sender will incur Video Share usage charges. AT&T is not responsible for the content of any video. Unlimited voice services: Unlimited voice services are provided primarily for live dialog between two individuals. No additional discounts are available with unlimited plan. Offnet Usage: If your minutes of use (including unlimited services) on other carrier’s networks (“offnet usage”) during any two consecutive months or your data use during any month exceeds your offnet usage allowance, AT&T may at its option terminate your service, deny your continued use of other carriers’ coverage, or change your plan to one imposing usage charges for offnet usage. Your offnet usage allowance is equal to the lesser of 750 minutes or 40% of the Anytime minutes included with your plan (data offnet usage allowance is the lesser of 24 MB or 20% of the MBs included with your plan). TeleNav and TeleNav Track are trademarks of TeleNav, Inc. Samsung and Rugby are both trademarks of Samsung Electronics America, Inc. and its related entities. The Bluetooth trademarks are owned by their proprietor. All other trademark and product or service names are the property of their respective owners. © 2010 AT&T Intellectual Property. All rights reserved. AT&T and the AT&T logo are trademarks of AT&T Intellectual Property.BUS OB T 0510 3078 EFor more information, please contact an AT&T sales representative,visit /samsungrugbyII or call 866-9ATT-B2B (866-928-8222).。
VIAVI NITRO Mobile 产品简介说明书

5,T0r6o*7u,b'8l7e9s*h6:o9o*/t)i'#n,g49
;'#0/<=2,4>//9*)?
Assurance and Optimization
Application Aware HetNet/C-RAN/vRAN
IoT Device, Location, UP/CP Analytics Real Time, Low Latency Services
Site Planning Small Cells Optimization
Performance Security CEM
VIP Assurance
Location Insights
Handsets
Monetization
Events
Smart Cities
HetNets IoT
Video
3rd Party Applications
Assurance & Optimization
VIAVI Integrated Data Feeds
Real-time Correlation & Mediation Layer
RAN Data Collection
Core Data Collection
All subscribers, all sessions / events, 24 x 7
By increasing the automation of context-driven workflows, NITRO Mobile helps you manage your mobile network with less manual intervention. Through feeding real-time data from instruments and software virtual agents into a single presentation layer, NITRO Mobile, together with the scalability of the virtualized platform, helps reduce complexity and increase the automation necessary to confidently manage the evolution to 5G.
baseband unit的通信协议和监控方式

baseband unit的通信协议和监控方式
BBU(Baseband Unit)是一种室内基带处理单元,主要用于处理和分解信号,如压缩、编码等等。
它有自己的操作系统,可以管控和其相连的RRU(Remote Radio Unit),主要做为核心网络和RRU 或其他通信节点之间的沟通桥梁。
BBU与RRU之间采用光纤传输,RRU再通过同轴电缆及功分器(耦合器)等连接至天线,即主干采用光纤,支路采用同轴电缆。
对于上行方向:用户手机信号被距离最近的通道收到,然后从这个通道经过光纤传到基站,这样也可以大大降低不同通道上用户之间的干扰。
对于通信协议,BBU主要与RRU进行通信,两者之间有专门的通信协议以实现信息的交互和协同工作。
具体协议可能因设备供应商和网络架构的不同而有所差异,一般由设备供应商提供相关协议文档和技术支持。
对于监控方式,BBU可以通过自身的操作系统和网络管理系统进行监控和管理。
通过监控系统的实时数据采集和分析,可以监测BBU的工作状态、性能指标、故障情况等,以便及时发现和解决问题。
同时,监控系统还可以对BBU进行远程控制和管理,实现自动化运维和智能管理。
总的来说,BBU的通信协议和监控方式都是为了保证其正常工作并提高网络性能和稳定性。
具体的通信协议和监控方式需要根据实际应用场景和设备配置来确定。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Mobile Agents based Routing Protocol for Mobile Ad Hoc NetworksS HIVANAJAY M ARWAHA C HEN K HONG T HAM D IPTI S RINIVASAN(engp1609, eletck, elesd) @.sgDepartment of Electrical and Computer Engineering, National University of Singapore10, Kent Ridge Crescent, Singapore 119260Abstract -- A novel routing scheme for mobile ad hoc networks (MANETs), which combines the on-demand routing capability of Ad Hoc On-Demand Distance Vector (AODV) routing protocol with a distributed topology discovery mechanism using ant-like mobile agents is proposed in thispaper. The proposed hybrid protocol reduces route discoverylatency and the end-to-end delay by providing high connectivity without requiring much of the scarce network capacity. On the one side the proactive routing protocols in MANETs like Destination Sequenced Distance Vector (DSDV) require to know, the topology of the entire network. Hence they are not suitable for highly dynamic networks such as MANETs, since thetopology update information needs to be propagated frequentlythroughout the network. These frequent broadcasts limit the available network capacity for actual data communication. On the other hand, on-demand, reactive routing schemes like AODV and Dynamic Source Routing (DSR), require the actual transmission of the data to be delayed until the route isdiscovered. Due to this long delay a pure reactive routing protocol may not be applicable for real-time data and multimedia communication. Through extensive simulations inthis paper it is proved that the proposed Ant-AODV hybrid routing technique, is able to achieve reduced end-to-end delaycompared to conventional ant-based and AODV routingprotocols.I. I NTRODUCTIONCurrent routing protocols for mobile ad hoc networks (MANETs) suffer from certain inherent shortcomings. On the one side the proactive routing schemes like Destination Sequenced Distance Vector (DSDV) [1] continuously update the routing tables of mobile nodes consuming large portion of the scarce network capacity for exchanging huge chunks of routing table data. This reduces the available capacity of the network for actual data communication. The on-demand routing protocols like Ad Hoc On-Demand Distance Vector and Dynamic Source routing [2,3] on the other hand launch route discovery, and require the actual communication to be delayed until the route is determined. This may not be suitable for real-time data and multimedia communication applications. Mobile agents similar to ants [4,5,6,7] can be used for efficient routing in a network and discover the topology, to provide high connectivity at the nodes. However the ant-based algorithms in wireless ad hoc networks havecertain drawbacks. In that the nodes depend solely on the antagents to provide them routes to various destinations in thenetwork. This may not perform well when the networktopology is very dynamic and the route lifetime is small. Inpure ant-based routing, mobile nodes have to wait to start acommunication, till the ants provide them with routes. Insome situations it may also happen that the nodes carrying ants suddenly get disconnected with the rest of the network. This may be due to their movement away from all other nodes in the network or they might go into sleep mode or simply turned off. In such situations the amount of ants left for routing are reduced in the network, which leads to ineffective routing.The current paper tries to overcome these shortcomings of ant-based routing and AODV by combining them to develop a hybrid routing scheme. The Ant-AODV hybrid routing protocol is able to reduce the end-to-end delay and route discovery latency by providing high connectivity as compared to AODV and ant-based routing schemes. The hybrid scheme also does not overload the available network capacity with control messages like the proactive protocols. II. B ACKGROUND D ESCRIPTION O F AODV AND A NT -B ASED R OUTING P ROTOCOLS A. AODV Routing Protocol If a node using AODV [2] desires to send a message to adestination node for which it does not have a valid route to, it initiates a route discovery to locate the destination node. The source node broadcasts a route request (RREQ) packet to all its neighbors, which then forward the request to theirneighbors and so on until either the destination or an intermediate node with a “fresh enough” route to the destination listed in the RREQ is located. AODV makes use of sequence numbers to ensure that the routes are loop free. Each node maintains its own sequence number, and a broadcast ID. The sequence number is incremented whenever there is a change in the neighborhood of a node and the broadcast ID is incremented for every route discovery the node initiates. Along with its own sequence number and the broadcast ID, the source node also includes the most recent sequence number it has for the destination node. Intermediate nodes may reply to the RREQ if they have a route to the destination with a destination sequence number equal to or more than the one listed in the RREQ. If additional copies of the same RREQ are later received, these packets are simply discarded.When the RREQ reaches the destination or anintermediate node (having fresh enough route to thedestination), it responds by sending a route reply (RREP)packet to the source. Periodic HELLO broadcasts are used inAODV by the nodes in the network to inform each mobilenode of other nodes in its neighborhood. These broadcasts areused to maintain local connectivity. If a node along the routemoves, its upstream neighbor notices the move and propagates a link failure notification/route error message (RERR) to each of its active upstream neighbors to inform of the removal of that part of the route.B. Ant-based routingRouting algorithms for MANET which employ ants have been previously explored by [4,5,6]. Ants in network routing applications are simple agents embodying intelligence and moving around in the network from one node to the other and updating the routing tables of the nodes they visit with what they have learned in their traversal so far [4,5,6,]. Routing ants keep a history of the nodes previously visited by them.When an ant arrives at a node it uses the information in its history for updating the routing table at that node with thebest routes it has for the other nodes in the network. The higher the history size the larger the overhead, hence a careful decision on the history size of the ants has to be made. All thenodes in the network rely on the ants for providing them therouting information, as they themselves do not run anyprogram for finding routes. The ant-based routing algorithmimplemented in this paper does not consider anycommunication among the ants. Each ant worksindependently. The population size of the ants is anotherimportant parameter, which affects the routing overhead.Ants that take the “no return rule” [4] while selecting the next hop at a node have been implemented in this paper. In the conventional ant algorithms the next hop is selected randomly. If the next hop selected is the same as the previous node (from where the ant came to the current node) then this route would not be optimal. Data packets sent on such routes would just be visiting a node and going back to the previous node in order to reach the destination. Every node frequently broadcasts HELLO messages to its neighbors so that every node can maintain a neighbor list, which is used for selecting the next hop by the ants. III. ANT-AODV H YBRID R OUTING P ROTOCOL Ant-AODV technique, forms a hybrid of both ant-based routing and AODV routing protocols to overcome some of their inherent drawbacks. The hybrid technique enhances the node connectivity and decreases the end-to-end delay androute discovery latency. Route establishment in conventionalant-based routing techniques is dependant on the ants visiting the node and providing it with routes. If a node wishes to send data packets to a destination for which it does not have a fresh enough route, it will have to keep the data packets in its send buffer till an ant arrives and provides it with a route to that destination. Also, in ant routing algorithms implemented so far there is no local connectivity maintenance as in AODV. Hence when a route breaks the source still keeps on sending data packets unaware of the link breakage. This leads to a large number of data packets being dropped. AODV on the other hand takes too much time for connection establishment due to the delay in the route discovery process whereas in ant-based routing if a node has a route to a destination it just starts sending the data packets without any delay. This long delay in AODV before the actual connection is established may not beapplicable in real-time communication applications. Fig. 1. Propagation of route reply and traversal of ant packet in Ant-AODVrouting protocol.In Ant-AODV ant agents work independently andprovide routes to the nodes as shown in fig. 1. The nodes alsohave capability of launching on-demand route discovery (fig.1) to find routes to destinations for which they do not have afresh enough route entry. The use of ants with AODVincreases the node connectivity (the number of destinationsfor which a node has un-expired routes), which in turnreduces the amount of route discoveries. Even if a nodelaunches a RREQ (for a destination it does not have a fresh enough route), the probability of its receiving replies quickly (as compared to AODV) from nearby nodes is high due to the increased connectivity of all the nodes resulting in reduced route discovery latency. Lastly, as ant agents update the routes continuously, a source node can switch from a longer (and stale) route to a newer and shorter route provided by the ants. This leads to a considerable decrease in the average end-to-end delay as compared to both AODV and ant-based routing. Ant-AODV uses route error messages (RERR) to inform upstream nodes of a local link failure similar to AODV.Routing table in Ant-AODV is common to both ants andAODV. Frequent HELLO broadcasts are used to maintain a neighbor table. This table is used to select a randomly chosen next hop (avoiding the previously visited node) from the list of neighbors by the ant agents. IV. S IMULATION M ODEL Extensive simulations were carried out to compare the Ant-AODV hybrid routing protocol proposed in this paper with the conventional ant-based and AODV routing protocols. Network Simulator (NS-2) [7] is used to simulate these protocols. NS-2 is a discrete event simulator. The latest version of NS-2 (ns-2.1b8a) which can model and simulate a multi-hop wireless ad hoc network was used for the simulations. The physical layer for the simulation uses two-ray ground reflection as the radio propagation model. The link layer is implemented using IEEE 802.11 Distributed Coordination Function (DCF), Media Access Control Protocol (MAC). It uses “RTS/CTS/Data/ACK” pattern for unicastpackets and “data” for broadcast packets. Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) is used to transmit these packets. All protocols simulated maintain a send buffer of 64 data packets, containing the data packets waiting for a route. Packets sent by routing layer are queued at the interface queue till MAC layer can transmit them, which has a maximum size of 50 data packets. The interface queue gives priority to routing packets in being served. The transmission range for each of the mobile nodes is set to 250m and the channel capacity is 2Mbps. Simulations were run for 600 simulated seconds. The routing table used for all the three protocols are similar. Every route entry in the routing table has a destination node address, number of hops to reach that destination, the next hop to route the packets, the sequence number of the destination and the time to live for that route.A. Ant history size and ant populationSeveral combinations of ant population and history sizes were used in the simulations to arrive at the values that gave the best performance. These values of ant population and history size were then chosen so as to keep a balance between control overhead and efficient routing. For simulating ant-based routing protocol the number of ants was kept equal to the number of nodes (which was 50) with a history size of 15. For Ant-AODV, 10 ants with a history size of 12 were used. B. MobilityA network of 50 mobile nodes migrating within an area of 1500m X 300m with a speed of 0 - 10m/s was simulated.A rectangular space was chosen in order to force the use of longer routes between nodes than would be there in a square space with the same amount of nodes [8]. The mobility model uses the random waypoint model in the rectangular field. The simulations were run multiple times for 6 different pause times: 0, 30, 60, 120, 300 and 600 seconds. After pausing for pause time seconds the mobile node again selects a new destination and proceeds at a speed distributed uniformly between 0 and a maximum speed.C. TrafficThe simulations carried out consisted of 20 Continuous Bit Rate (CBR) sources. CBR traffic sources were chosen, as the aim was to test the routing protocols. Source nodes and destination nodes were chosen at random with uniform probabilities. The sending rate used was 4 packets per second with a packet size of 64 bytes. Each data point in the comparison results represents an average of multiple runs with identical traffic models but with different movement scenarios. Same movement and traffic scenarios were used for all the three protocols simulated.V.S IMULATION R ESULTSA. Average end-to-end delayThe average end-to-end delay includes buffering delay during route discovery, queuing delay at interface queue, retransmission delays and propagation and transfer times. The average end-to-end delay for AODV and Ant-AODV hybrid protocol (fig. 2) is very less. But in case of Ant routing technique (fig. 3) the average end-to-end delay is high. The high end-to-end delay in ant-based routing is attributed to the lack of on-demand route discovery capability of the nodes in ant routing. Due to this the packets to be sent by a node keep waiting in the send buffer till the ants visit that node and provide it with routes.Fig. 2. Average end-to-end delay provided by AODV and Ant-AODV routingprotocols.Fig. 3. Average end-to-end delay provided by Ant-based and Ant-AODVrouting protocols.Comparing Ant-AODV and AODV it can be observed that the end-to-end delay (fig. 2) is considerably reduced in Ant-AODV as compared to AODV. Ants help in maintaining high connectivity in Ant-AODV, hence the packets need not wait in the send buffer till the routes are discovered. Even if the source node does not have a ready route to the destination, due to the increased connectivity at all the nodes theprobability of its receiving replies quickly from nearby nodes is high resulting in reduced route discovery latency. Lastly, the dynamic nature in which routes are kept updated by the ants leads to the source node switching from a longer (and stale) route to newer and shorter ones hence reducing end-to-end delay for active routes.B. Goodput and Packet delivery fractionGoodput is the total number of useful packets received at all the destination nodes and packet delivery fraction is the ratio of number of data packets sent to the number of data packets received. Packet delivery fraction is very high for AODV and Ant-AODV (fig. 4) as compared to ant-based routing. Goodput is also higher for Ant-AODV and AODV as compared to ant-based routing (fig. 5).Fig. 4. Packet delivery fraction provided by Ant-based, AODV and Ant-AODV hybrid routing protocols.Fig. 5. Goodput of Ant-based, AODV and Ant-AODV routing protocols.High packet delivery fraction and goodput in Ant-AODV and AODV is because they make use of link failure detection and route error messages. Whereas in case of ant-based routing there is no such feature and so the source nodes keep on sending packets unaware of the link failures. This leads to a large amount of data packets being dropped which reduces the packet delivery fraction and the goodput. Also seen in the graphs for packet delivery fraction (fig. 4) and goodput (fig.5) is that as the pause time increases the goodput and packet delivery ratio increase due to less link failures at low mobility rates (high pause time).C. Normalized Routing overheadNormalized routing overhead is the number of routing packets transmitted per data packet received at the destination. The routing overhead in case of ant-based routing is independent of the traffic. Even if there is no communication the ants would still be traversing the network and update the routing tables. However in case of AODV, the overhead is dependent on the traffic and if there is no communication then there will be no control messages generated in the network. In Ant-AODV the overhead has two components. It has the ants traversing in the network, and the route discovery and route reply messages being generated in case the nodes do not have routes provided to them by the ants for some destinations. From the comparison results (fig. 6) it is seen that the normalized overhead is too high in case of ant-based routing scheme. The reason for this is that the actual data packets delivered are too less and hence the ratio of control overhead to data packets delivered becomes too high. In case of AODV (fig. 6) the normalized overhead is the least. The normalized overhead (fig. 6), is slightly greater in Ant-AODV as compared to AODV because of the continuous movement of ants in the network. The continuous gradual drop in normalized routing overhead (fig. 6) for all the three protocols is attributed to the increased packet delivery fraction and goodput at higher pause times (normalized load is the ratio of total control packets generated to actual data packetsreceived).Fig. 6. Normalized routing overhead of Ant-based, AODV and Ant-AODVrouting protocols.D. Connectivity B. Performance of Ant-AODVIt is evident from the simulation results that by combining ant-like mobile agents with the on-demand route discovery mechanism of AODV, the Ant-AODV hybrid routing protocol would give reduced end-to-end delay and route discovery latency with high connectivity. Such low end-to-end delay cannot be achieved from either of the two base protocols (ant-based and AODV) because of their inherent shortcomings. Connectivity is the average number of nodes in thenetwork for which a node has un-expired routes. In case of Ant-AODV and ant-based routing protocols (fig. 7), ant agents continuously traverse the network and update the routing table entries. Due to this, a node has fresh enough (or un-expired) routes to a large number of nodes in the network at any given point of time. Connectivity in Ant-AODV and ant-based routing schemes is more than double theconnectivity in AODV (fig. 7). Higher connectivity leads tolesser route discoveries and reduced end-to-end delay. VII. C ONCLUSION The shortcomings of on-demand routing protocols likeAODV and ant-based routing have been tried to overcome in this paper by combining both of them to enhance their capabilities and alleviate their weaknesses. Ant-AODV hybrid protocol is able to provide reduced end-to-end delay and high connectivity as compared to AODV. As a result of increased connectivity the number of route discoveries is reduced and also the route discovery latency. This makes Ant-AODV hybrid routing protocol suitable for real-time data and multimedia communication. As a direct result of providing topology information to the nodes (using ants), the foundations for designing a distributed network control and management get automatically laid. Higher connectivity and reduced end-to-end delay are achieved at the cost of extra processing of the ant messages and the slightly higher overhead occupying some network capacity. However this does not adversely affect the packet delivery fraction or the goodput. The future work would be to explore the use of back up or multiple routes provided to the nodes by ants in their frequent and continuous visits to the node.Fig. 7. Average connectivity provided by Ant-based, AODV and Ant-AODVrouting protocols.R EFERENCESVI. D ISCUSSION[1] C. E. Perkins and P. Bhagwat, “Highly dynamic Destination SequencedDistance-Vector routing (DSDV) for mobile computers,” in Proc. of the SIGCOMM ’94 Conf. on Communications Architecture, Protocols and Applications , pp. 234-244, Aug. 1994.A. Ant Visit PeriodDuring the simulations an important characteristic of ant agents for routing in MANETs was observed. After a certain period (nearly 100 simulation seconds), the ant activity (ant hopping from one node to the other and updating routes) would almost subside. This could be due to various reasons such as (i) the ant packets could be lost in wireless transmission, (ii) the next node which was to receive the ant packet moves out of the wireless range of the sending node, or (iii) the ant bearing node goes out of wireless range of every node in the network and there is no next hop node available for the ant. In such situations the number of ants actually available for routing purpose decreases. To overcome this decrease in number of ants available for routing, a “minimum ant visit period” was set. If no ant visited a node within this period the node would generate a new ant and transmit it to one of its neighbors selected randomly. This way the ant activity would never subside and the network would not become devoid of ants. The simulations carried out used a minimum ant visit period of 5 seconds.[2] C. E. Perkins, E. M. Royer and S. R. Das, “Ad Hoc On-DemandDistance Vector (AODV) Routing,” in Proc. IEEE Workshop on Mobile Computing Systems and Applications , pp. 90-100, Feb. 1999.[3] D. B. Johnson and D. A. Maltz, “Dynamic Source Routing in ad hocwireless networks,” Mobile Computing , edited by Tomasz Imielinski and Hank Korth, chapter 5, pp. 153-181. Kluwer Academic Publishers, 1996.[4] N. Minar, K. H. Kramer and P. Maes, “Cooperating Mobile Agents forDynamic Network Routing ,” Software Agents for Future Communications Systems, chapter 12, Springer Verlag, 1999.[5] H. Matsuo and K. Mori, “Accelerated Ants Routing in DynamicNetworks,” in Proc. Intl. Conf. On Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, pp.333-339, Aug. 2001.[6] R. R. Choudhary, S. Bhandhopadhyay and K. Paul, “A DistributedMechanism for topology discovery in Ad Hoc Wireless Networks Using Mobile Agents,” in Proc. of Mobicom , pp. 145-146, Aug. 2000.[7] K. Fall and K. Varadhan, editors. The ns manual. The VINT Project,UC Berkeley, LBL, USC/ISI and XEROX PARC, 2001. /nsnam/ns/ns-documentation.html[8] J. Broch, D. Maltz, D. Johnson, Y.-C. Hu and J. Jetcheva, “APerformance Comparison of Multi-Hop Wireless Ad Hoc Network Routing Protocols,” in Proc. of the Fourth Annual ACM/IEEE International Conference on Mobile Computing and Networking , pp. 85-97, Oct. 1998.。
