1-introduction
TOPIC_1_-_INTRODUCTION_TO_OPERATIONS_AND_SERVICES

Outputs
Operational Strategies:
Employee Performance – six sigma, quality circle, etc Productivity improvement strategies Production system: MRPII, WCM, JIT, six sigma, etc Quality – ISO, TQM
• Hot yet quality food • Satisfied customers resulting in profits Challenge: Finding the most suitable system of food preparation to meet the objectives as stated above. Dissatisfaction could be due to poor quality, e.g., too spicy, too cold, etc
13
Joseph M. Juran Armand V. Feigenbaum Philip B. Crosby Kaoru Ishikawa Genichi Taguchi
Old vs. New Concepts of Quality
Time Early 1900s 1940s 1960s 1980s and beyond
3
System Approach as an Open System:
External Forces: PESTDC
INPUT
TRANSFORMATION PROCESS
OUTPUT
FEEDBACK LOOP
4
Transformation Process:
[英语学习]unit-1-Introduction
![[英语学习]unit-1-Introduction](https://img.taocdn.com/s3/m/c54459bff7ec4afe05a1df71.png)
展。
• a Panorama of Publishing 出版业概况 • book industry 图书出版业 • book community 书业团体
Questions on part 1
• 1 [+ obj] : to prepare and produce (a book, magazine, etc.) for sale ▪ It's a small company that only publishes about four books a year. ▪ The university press publishes academic titles. ▪ The newspaper is published daily. 2 : to have something you wrote included in a book, magazine, newspaper, etc. [no obj] ▪ There is a lot of pressure for professors to publish regularly. [+ obj] ▪ He has not published anything for a long time. 3 [+ obj] : to include (an article, letter, photograph, etc.) in a magazine or newspaper ▪ The magazine published two of my stories.
3. intriguing
1.Introduction

特殊光学显微镜技术
暗视野显微镜 偏光显微镜 倒置显微镜 相位差显微镜 荧光显微镜 激光共聚焦显微镜
荧光显微镜
激光扫描共聚焦显微镜
laser scanning confocal microscope, LSCMope, EM)技术 )
苏木精( 苏木精(Hematoxylin)+ 伊红(Eosin)染色 ) 伊红( ) 碱性染料 将嗜碱性物质( 将嗜碱性物质(本身 酸性) 酸性)染成紫蓝色 细胞核中的DNA、RNA 、 细胞核中的 细胞质中的 细胞质中的RNA 酸性染料 将嗜酸性物质( 将嗜酸性物质(本身 碱性) 碱性)染成粉红色 细胞质、膜性结构 细胞质、 线粒体、溶酶体、 (线粒体、溶酶体、 滑面内质网) 滑面内质网)
细胞化学和组织化学
如: 检测多糖:过碘酸雪夫反应 检测多糖:过碘酸雪夫反应(periodic acid Schiff reaction):简称 PAS反应。 反应。 : 反应 检测脂类 :苏丹III染色法 苏丹III染色法 III
反应) 过碘酸雪夫反应 (PAS反应 反应
脂类组织化学染色(苏丹 染色) 苏丹III染色
一般光学显微镜技术(light microscope, LM) )
石蜡切片、冷冻切片、涂片、舖片、磨片
一般光学显微镜技术
最常用的是石蜡切片,HE染色 切片的制作步骤: 固定(fixation) 包埋 (embedding) 切片 (section) 染色(staining)
HE染色: 染色: 染色
核酸分子原位杂交术
是利用标记的特 异性DNA、RNA或 寡核苷酸探针检 测细胞内某种基 因片断的方法
组织学实验技术的作用
组织学实验技术是现代生物医学领域 诸多基础及前沿学科学习和研究的重 要技术支持。
Lecture 1-Introduction

Imaging in the Visible and Infrared Bands
Sources of Images
Imaging in the Visible and Infrared Bands
Sources of Images
Imaging in the Visible and Infrared Bands
• •
Human Vision System Mathematicians
•
Prior Knowledge Image models Transformations Methodologies
Impacts?
• • •
Categorization – My Viewpoint
•
Image Processing Methodologies
About This Course
Resources?
Scoring policy
Presence – 15% Final exam – 85%
Course Outline
32 hours = 3×10 lectures + 2 for course review Lecture 1 – Introduction Lecture 2 – Digital Image Fundamentals Lecture 3 – Image Transformations Lecture 4 – Image Enhancement Lecture 5 – Image Restorations Lecture 6 – Color Image Processing Lecture 7 – Image Compression Morphological Image Processing Lecture 8 – Image Segmentation Lecture 9 – Representation and Description Lecture 10 – Image Recognition
unit_1_introduction[1]
![unit_1_introduction[1]](https://img.taocdn.com/s3/m/5a44843a10661ed9ad51f372.png)
1.1 Text(2)
• According to the information direction transmitted in channel, modern communication systems can be divided into the simplex communication systems, half-duplex communication systems, and full-duplex communication systems; • According to the number of information communicating approaches, modern communication systems can be divided into the serial communication systems and the parallel communication systems; • According to the control methods of information transmitted in channels, modern communication systems can be divided into the synchronous communication systems and the asynchronous communication systems; • According to the line connecting modes and signal interacting ways between signal source and destination, modern systems can be divided into point-to-point communication systems, one-to-multi-points communication systems and multi-to-multi-points communication systems.
Chapter1-Introduction

共56页
9
信息和知识隐藏在数据中
商务智能要求有一个坚固、可靠的大型数据库作后盾,建立这样一个数据库的任 务是极其艰巨的。数据的质量问题也是令人头疼而又不可以掉以轻心的。 虽然数据是宝贵的财富,然而许多公司并不能充分利用这种财富,因为信息隐藏 在数据中,并不易识别。 为了在竞争中占得优势地位,必须识别和应用隐藏在所收集的数据中的信息。
共56页
15
信息流畅通了还需要?
商务智能BI(business intelligence)
SCM
供应链 管理
ERP
企业资源规划系统
B2B、B2C
CRM
数据
Internet等基础设施
共56页
16
新一代决策支持系统
交易处 理系统 DSS 资料库 外部资料
DSS软件系统模式 OLAP工具 资料挖掘工具 使用者界面
目标市场 资金分配 贸易选择 在哪儿做广告 销售的地理位置
数据爆炸,知识贫乏
共56页 14
Do You Trust Your Information?
Up to 75% have made business decisions that later turned out to be wrong due to flawed data
2
概念解析
何谓智能?企业有智能吗? 智能的表现
信息共享和企业信息集成 知识挖掘与管理
1Introduction
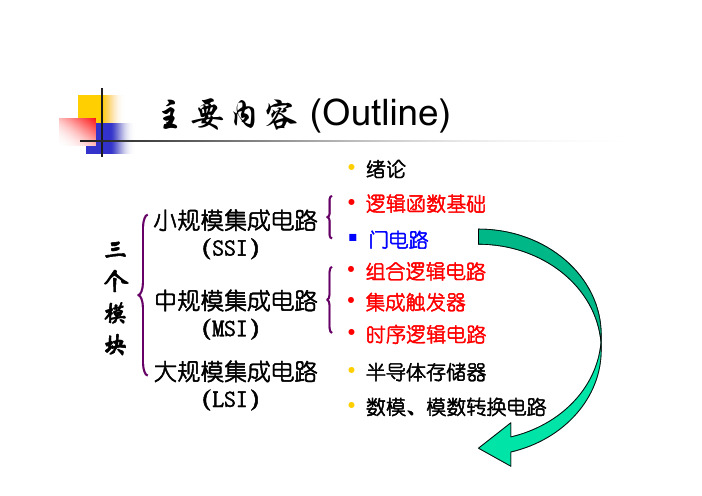
主要内容 (Outline)• 绪论小规模集成电路三(SSI)• 逻辑函数基础 门电路个• 组合逻辑电路模 块中规模集成电路 (MSI)• 集成触发器 • 时序逻辑电路大规模集成电路 • 半导体存储器(LSI)• 数模、模数转换电路绪论 (Introduction)一、数字(digital)信号和模拟(analog)信号 数字量和模拟量 数字电路和模拟电路二、数字信号相关概念 二进制数 Binary Digits 数字信号的逻辑电平 Logic Levels 数字信号波形 Digital Waveforms一、Digital Signal and Analog Signal Digital and Analog Quantities电子 电路 中的 信号模拟信号: 连续analogue signal value数字信号: 离散digital signal valuetime time模拟信号T( C) 30采样信号T( C)sampled3025离散化 2520202 4 6 8 10 12 2 4 6 8 10 12 t (h)A.M.P.M.2 4 6 8 10 12 2 4 6 8 10 12 t (h)A.M.P.M.数字化-表示 为由0、1组成 的二进制码Analog Electronic SystemDigital and Analog Electronic System★ 工作在模拟信号下的电子电路是模拟电路。
研究模拟电路时,注重电路输入、输出信号 间的大小、相位关系。
包括交直流放大器、 滤波器、信号发生器等。
★ 模拟电路中,晶体管一般工作在放大状态。
★ 工作在数字信号下的电子电路是数字电路。
研究数字电路时,注重电路输出、输入间的逻 辑关系。
主要的分析工具是逻辑代数,电路的 功能用真值表、逻辑表达式或波形图表示。
★ 在数字电路中,三极管工作在开关状态, 即工作在饱和状态或截止状态。
#slang 1 - introduction

Idiomsidiom (noun) — a group of words established by usage ashaving a meaning not deducible from those of the individualwords (e.g. “on pins and needles”, meaning to be worriedabout something).(traditional language)Slang (the topic of the final exam)slang (noun) — A kind of language occurring chiefly incasual and playful speech, made up typically of short-livedcoinages and figures of speech that are deliberately used inplace of standard terms for added raciness, humor,irreverence, or other effect.Jargonjargon (noun) — specialized technical terminologycharacteristic of a particular subject; a characteristiclanguage of a particular group.Using the following list of slang words produce a conversational dialogue between students who have just been dismissed from school and are talking about their plans for the weekend (3 nights and 2 days!). The task is to use much slang as possible and in the correct native style. Each member of your group should have 60 seconds of dialogue and grading will be 50% group based and 50% individual based performance. I may also ask students to respond to questions using slang, should I deem it necessary. Grading will be based on accuracy, coherence, fluency, understanding, body language, enthusiasm, intonation, speed, volume and general presentation.。
1.introduction 简介
Introduction
1、生物化学的概念 2、生物化学的发展简史
3、生物化学的主要研究内容 4、生物化学与其它学科的关系
生物化学的概念
生物化学是研究生命 化学的学科,它在分子水 平上探讨生命的本质,即 研究生物体的分子结构与 功能,物质代谢与调节, 及其在生命活动中的作用。
①吴宪
在血液化学分析方面创 立了血滤液的制备和血糖测定法; ②蛋白质方面,提出了蛋白质变 性学说; ③免疫学方面,研究抗原抗体的 反应机制;
④1965年,首先人工合成具
有生物活性的胰岛素; ⑤1981年,成功合成酵母丙 氨酰tRNA; ⑥完成人类基因组计划工作 的1%。
生物化学的研究内容
静态生物化学 动态生物化学 1、 功能生物化学 分子生物学 2、生物化学的研究采用化 学的原理和方法; 3、生物化学与细胞学、遗传学、 生理学关系密切;
生物化学的发展简史
1、初级阶段
2、发展阶段 3、分子生物学阶段
4、现状
初级阶段
1、对糖类、脂类、氨基酸作
了比较系统的研究; 2、发现了核酸; 3、化学合成了简单多肽; 4、酵母发酵过程中可溶性催 化剂的发现奠定了酶学的基础。
1、生物大分子的结构与功能; 2、物质代谢及其调节; 3、基因信息的传递及其调控。
生物大分子:由某些 基本结构单位按照一定的 顺序和方式连接所形成的 多聚体。 分子量一般在104以上
生物化学与其他学科的关系
1、与农业的关系 2、与工业的关系 3、与药学的关系 4、与医学的关系
与农业的关系
人类基因组计划
科学研究证明,人类的生老病死
都与基因有关,如果能够破译人 类基因的序列和功能,就有可能 真正有效地预防、诊断和治疗各 种疾病。因此,1990年正式启动 的人类基因组计划一开始就引起 了全世界的广泛关注。
Lecture1-Introduction

2
Risk Management
• Risk can be defined as the variability or volatility of unexpected outcomes. • Risk management is the process by which various risk exposures are identified, measured and controlled
Note: OTC in 2015 $553 trillion
9
Derivatives in China
• • • • • Dalian Commodity Exchange (DCE) Shanghai Futures Exchange (SHFE) Zhengzhou Commodity Exchange (ZCE) China Financial Futures Exchange (CFFEX) Shanghai Stock Exchange
6
Risk Management with Derivatives
• Hedging
Strategy used to offset some of the risk associated with a given market commitment. A perfect hedge eliminates the possibility of future gain or loss. Example: A firm that wants to be assured the price they will receive (or pay) for a commodity
• Over-the-counter (OTC)
Lecture 1--Introduction

激辐射理论,为激光的出现奠定了理论的基础;
1928年,Landenburg证实了受激辐射和“负吸收”的
存在;
17
Light: Laser 激光的发展史
1947年,Lamb和Reherford在氢原子光谱中发现了明显的受
激辐射,这是受激辐射第一次被实验验证。Lamb由于在氢原 子光谱研究方面的成绩获得1955年诺贝尔物理学奖;
E4 E3 激发态 E2
A 21 自 发 辐 射 系
数,单个原子在单 位时间内发生自发 辐射过程的概率。
h
基态 E1
26
自发辐射过程产生的光子是不相干的 Photons from spontaneous emission are not coherent 处在高能级 E2 上的粒子,各自独立地、随机 地分别跃迁到低能级 E1 上,发射出光子,这 些光子的能量虽然相同,但彼此具有不同的 相位及偏振方向,因此自发辐射发出的光是 非相干光(non-coherent light) 处于高能级 E2 的原子还可以通过放热、碰撞 等方式将能量传给其它粒子或器壁而跃迁到 低 能 级 上 , 即 无 辐 射 跃 迁 (non-radiative decay)。
15
Light: Laser 激光的发展史
黎明前的黑暗
1900年,普朗克提出了能量量子化概念,并因此
获得1918年诺贝尔物理学奖; "in recognition of the services he rendered to the advancement of Physics by his discovery of energy quanta"
unit1_introduction

The aim/ purpose of this report is to… This present report sets out to… My purpose in writing/ My purpose of writing this report is to… In writing this report, I aim to… It has been found out that… The findings show that… I found out that…
an insurance policy covering loss of movable property (e.g. jewelry) regardless of its location
Floating policy is of great importance for export trade; it is, in fact, a convenient method of insuring goods where a number of similar export transactions are intended, e.g. where the insured has to supply an oversea importer under an exclusive sales agreement or maintains sales representatives or subsidiary companies abroad. 统保单对出口贸易至关重要。它实际上是货物保险中 的一种便利的办法, 特别适用于分不同的时间出口的 一批类似的货物,如, 被保险方根据独家代理协议书 向国外的进口方供货,或在国外委任了销售代表设立 分支机构时使用。
Chapter 1 - Introduction

Chapter 1 - I ntroductionEcho sounding is a technique for measuring water depths by transmitting acoustic pulses from the ocean surface and listening for their reflection (or echo) from the sea floor. This technique has been used since the early twentieth century to provide the vital depth input to charts that now map most of the world’s water-covered areas. These charts have permitted ships to navigate safely through the world’s oceans. In addition, information derived from echo sounding has aided in laying trans-oceanic telephone cables, exploring and drilling for off-shore oil, locating important underwater mineral deposits, and improving our understanding of the Earth’s geological processes. Until the early 1960s most depth sounding used single-beam echo sounders. These devices make a single depth measurement with each acoustic pulse (or ping) and include both wide and narrow beam systems. Relatively inexpensive wide-beam “unstabilized” sounders detect echoes within a large solid angle under a vessel and are useful for finding potential hazards to safe navigation. However, these devices are unable to provide much detailed information about the sea bottom. On the other hand, more expensive narrow-beam “stabilized” sounders are capable of providing high spatial resolution with the small solid angle encompassed by their beam, but can cover only a limited survey area with each ping. Neither system provides a method for creating detailed maps of the sea floor that minimizes ship time and is thus cost-effective. The unstabilized systems lack the necessary spatial resolution, while the stabilized systems map too little area with each ping.In 1964, SeaBeam Instruments—at the time the Harris Anti-Submarine Warfare Division of General Instrument Corporation—patented a technique for multiple narrow-beam depth sounding. The first such systems to use this technique were built by SeaBeam for the US Navy and were known as Sonar Array Sounding Systems (SASS). SASS employed two separate sonar arrays oriented orthogonal to one another—one for transmitting and one for receiving—an arrangement called a Mills Cross Array. The arrays and the associated analog electronics provided 90 1°-wide unstabilized beams. Roll and pitch compensation produced 60 1°-wide stabilized beams, which permitted mapping a 60° “fan” of the sea floor with each ping. This system allowed survey vessels to produce high-resolution coverage of wide swaths of the ocean bottom in far less ship time than would have been required for a single-beam echo sounder, greatly reducing the costs of such mapping endeavors.Figure Chapter 1 - -1: Contour Map of Perth CanyonMost multibeam bathymetry systems still use the Mills Cross technique for beam forming. However, as faster computers and Large Scale Integrated (LSI) digital chips have become available, most of the signal processing, including beam forming, moved from analog signal processing into the digital (discrete) signal processing (DSP) domain using digital signal microprocessor (DSPµP) chips. The availability of fast DSPµPs has also permitted the implementation of sophisticated detection algorithms. As a result, survey vessels today can do on-board real-time multibeam processing and display of bathymetry data in a manner impossible only a few years ago. Figure Chapter 1 - -1 shows a sample of a high-quality ocean floor map produced by a SEA BEAM 2100 Multibeam Survey System, the latest generation of multibeam sonar from SeaBeam Instruments.The SEA BEAM 2100 system represents the culmination of over a third of a century of design, development, and production experience by SeaBeam Instruments in the area of multibeam bathymetric systems. With added sophistication, this latest generation multibeam sonar system has added capabilities and complexity. It is necessary to have a basic theoretical understanding of the way multibeam bathymetry systems in general, and the SEA BEAM 2100 in particular, work in order to both:•Operate the system in a manner that maximizes coverage and data quality•Evaluate the system performance for signs of system degradationOrganization of this DocumentThis manual provides a general explanation of the way a multibeam sonar system works and describes in detail the implementation of multibeam technology represented by the SEA BEAM 2100 system.Chapter 2, “Sonar Concepts,” introduces the concepts and definitions involved in echo sounding, using a description of a simple single-beam echo sounder as an example. Characteristics of the creation and transmission of acoustic pulses in water and their echoes off the ocean bottom are discussed. This chapter also explains some of the limitations of a single-beam sonar.Chapter 3, “Introduction to Multibeam Sonar: Projector and Hydrophone Systems,” describes the Mills Cross technique, including the processes of beam forming and beam steering and how it is applied to sonar and to the SEA BEAM 2100 in particular. The chapter discusses how systems that employ the Mills Cross technique can make up for many of the short-comings of single-beam echo sounders.Chapter 4, “Detection Processing and Range Calculation,” describes how the SEA BEAM 2100 extracts signals and determines the location of the sea floor from multibeam echoes. The processes used for ship motion compensation and the formation of stable beams and the implementation of sound velocity profiles are discussed.Chapter 5, “Sidescan Sonar,” discusses sea floor imaging using sidescan sonars and how the SEA BEAM 2100 can be used simultaneously as a depth-finding and sidescan sonar.A glossary of the terminology of multibeam sonar technology is included as an appendix. Scope of this DocumentMultibeam technology involves a number of disciplines including underwater acoustics, digital signal processing, and detection theory statistics. Many excellent texts are available that provide in-depth mathematical treatment of each of these fields. The purpose of this document is not to cover all related topics in rigorous mathematical detail, but instead to present you with a simple, clear understanding of the fundamental concepts required to develop the full potential of a multibeam sonar system. Ideas are presented in a graphical and descriptive way, with minimal use of complex mathematics. Where appropriate, references to texts are provided so you can pursue topics in greater detail. While directed at users of the SEA BEAM 2100 system in particular, most of the concepts explained in this document are common to all multibeam sonars, so much of this information can be applied to any commercially available multibeam system.。
1 Introduction

HLP ImplementationVersion0.1International Computer Science Institute1IntroductionHybrid Link-State Path-Vector Protocol,or HLP,is an inter-domain routing protocol designed as a replacement for the current Border Gateway Protocol(BGP).Using a combination of link-state and path vector routing,it provides greater scalability,better fault isolation and better convergence.The core of HLP is the inclusion of the economic and political structure of the Internet into inter-domain routing.That is,BGP currently considers each AS as a node in a general graph without any specific structure(using explicit policies to constrain routing),whereas HLP assumes that the Internet structure is basically hierarchical with the provider autonomous systems(ASs)being the roots of customer ASs.HLP explicitly includes the relationship between2neighboring ASs in its protocol.This will reduce misconfigurations which should hopefully reduce the occurrence of routing abnormalities.However,the tradeoff is some amount of inflexi-bility in the routing algorithm.This is resolved using exceptions that are expected to be rare and therefore acceptable. This report summarizes implementation of HLP on the XORP[1]software router.The implementation reuses much of the code in XORP’s BGP module.2DefinitionsWe say that two ASs are in the same hierarchy if there exists a directed path between them such that the path consists of any number of provider links followed by any number of customer links.This definition of hierarchy implies that there exists at least one route between two ASs in a hierarchy that does not include(provider)(customer)(provider)links. Two ASs are neighbors if there exists a link between them.The relationship between neighboring ASs(peer,customer, or provider)determine the overall structure of the network,which can be as simple as shown in Figure1a,or consist of overlapping hierarchies as shown in Figure1b.In thefigure,each node represents an AS;the neighboring AS at a higher tier is the provider,similarly an AS at a lower tier is the customer.Thus,AS A is the provider of AS B,which in turn is A’s customer.Neighboring ASs at the same tier are also called peering ASs.Note that the use of tiers in Figure1and inprotocol.subsequentfigures only allows for graphical representation of relationships,it is not present in the actual HLPHLP divides the network into hierarchies consisting of providers and their customer ASs,and peering ASs in different hierarchies allow routing between hierarchies.As will be explained in the next section,this division of the network intoseparate components increases scalability,as well as reduces the convergence time for route updates.3Routing Information DisseminationTwo types of routing packets are used to disseminate routing information:link-state advertisements(LSAs)and fragmented path-vector(FPV)1.As is the case in OSPF,LSAs areflooded throughout a hierarchy,and allow construction of the entire hierarchy topology.FPVs are used to route between ASs;they contain the numbers of peering ASs between hierarchies. LSAs that have not previously been received are forwarded in the following manner:1.if they are from customers,we forward to all neighbors,except the customers from which they arrive.2.if they are from providers,we forward only to neighboring customers,not providers.The objective of the above rules is to restrict LSAs to the hierarchies from which they originate.Failure to do so will imply that multi-homing ASs belonging to different hierarchies can cause LSAs to be disseminated throughout the entire Internet. The rules above implements this restriction,illustrated in Figure2.By definition,AS C belongs to both hierarchies1and 2,and rule1allows LSAs from AS B to be forwarded to C.At C,rule2prevents LSAs from A from being forwarded to AS D.On the other hand,LSAs involving C will be disseminated in both hierarchies,which is correct since C is a member both.ofFPVs are used to forward routes from one hierarchy to another.They are similar to path-vector packets used in BGP,except that they do not include the AS path within hierarchies.Rules that govern forwarding of FPVs are given as follows:1.FPVs from providers are disseminated only to customers,not to peers or other providers.2.FPVs from peers are forwarded to neighboring peers and customers,but not providers.4Routing AlgorithmThe mechanism to choose a route to a particular destination AS is similar to that currently used in BGP.This eases the implementation of exceptions which will be covered in the next section,as well as the creation of FPVs for routes to customers within the hierarchy Basically,we store routes for destination ASs reachable from each neighboring AS,then decide the winning route for a particular destination.The handling of routes contained within FPVs is straightforward and similar to that of BGP,but routing information gained from LSAs needs to be converted to the same form as that in FPVs. The conversion is elaborated on in the next section.4.1From LSAs to RoutesWe denote the least cost of reaching AS A from B by cost(B,A),a route from A to B with cost C by route[(A,B),C], and we perform the conversion in the following manner,assuming that the operations are taking place in AS X:1.for each neighbor N2.if neighbor is a customer3.for each downstream customer AS Apute cost(N,A)5.create AS path[X,A]with cost C=[cost(N,A)+cost(X,N)]6.associate route[(X,A),C]with N7.else if neighbor is a provider8.for each of the non-customer ASs in the hierarchypute cost(N,A)10.create AS path[X,A]with cost C=[cost(N,A)+cost(X,N)]11.associate route[(X,A),C]with NThe computation is broken into two parts,steps2to5,and6to9of the algorithm above.This is required because forwarding of routes from a provider to a peer should take place only if the destination AS is a customer2.To distinguish between the origin of the routes,we tag them with the following:PROVIDERLSA:Route for non-customer destination AS within the same hierarchy,determined using link-state information.PEERLSA:Route for customer destination AS obtained using link-state information.An example is given in Figure3,where we focus on AS C.Table1shows the routes,costs and tags associated with each neighbor.Neighbor Cost(C,A)PROVIDERA3LSA(C,E)PROVIDERA15LSA(C,D)PROVIDERD26LSA(C,A)PROVIDERF5LSATable1:Table containing routes,costs and tags for example converting LSAs to routes4.2From FPV to RoutesCreation of routes from FPVs are much simpler,and is similar to that in BGP:1.if FPV is from a provider P2.extract route and metric,tag with PROVIDER_FPV,and associate them with P3.if FPV is from a peer Q4.extract route(prepending this AS’number)and metric,tag with PEER_FPV,and associate with Q5.if FPV is from customer,treat FPV as coming from peer,extract route(prepending this AS’number)and metric,tag with PEER_FPV,and associate with QNote that step5only occurs due to an exception in the customer AS.Figure3:Example illustrating LSA to route conversion4.3Route SelectionThe winning route to a particular destination is selected according to the following order of preferences:1.customer route(ie.tagged with CUSTOMERNeighbor TypePROVIDER CustomerFPVCUSTOMER PeerTable2:Route types that can be forwarded to corresponding neighboring AS types5ExceptionsHLP supports three different types of exceptions.The primary use of exceptions is to support operations that are currently used in BGP but not covered by the default HLP rules.The format in which exceptions are specified and stored is given by wherefromlink specifies the neighboring link to which winning routes will be propagated,andAS number refers to the destination AS that this particular exception is for.In HLP,a from link is given by the tuple:5.1Exception1Figure4:(a)Example illustrating effect of exception1on rest of hierarchy.D announces that it does not have a customer route to C.B uses graph in(b)to compute shortest paths to all ASs in the same hierarchy except C(i.e.A,D and F).B uses the graph in(c)to compute the shortest path to C.Thefirst exception,illustrated in Figure4,allows an AS(say D)to choose an alternate route to a customer(C)via a peer (E).The route choose is dependent on the customer AS,and should not affect routes to other ASs.D indicates its intention via LSAs to other ASs in the same hierarchy that it is not choosing customer routes to C.D also informs E that it no longer has a customer route to C.If,ignoring customer routes,the winning route is from E,then D forwards that FPV to its peers and customers.However,if the winning route is from another peer not specified in the exception,then the corresponding FPV will not be forwarded.Using the same example,exception1is specified bywhere is specified using the tuple5.2Exception2This exception specifies that winning routes from the stated provider is to be forwarded to a particular peer,which is typically not done.In Figure5,the exceptionallows winning routes to AS Z from provider A to be forwarded to D.5.3Exception3The last exception supported is similar to exception2.Here,routes are forwarded from a peer to a provider.Currently, the provider simply accepts incoming FPVs from customers,treating them as though they are from peers.If,for security reasons,providers should reject FPVs from customers,then additional configuration will be required in the provider.Figure5:Simple network illustrating route forwarding from provider to peer5.4Exception Format and MatchingThe type of exception does not explicitly need to be specified.Instead,the neighbor relationship associated with the links given in each exception rule can be used to determine this.The format is thus simplified,and should hopefully reduce the occurrence of misconfigurations.Table3gives the combination of links that indicate the kind of exception specified.From To Exception TypeNULL1PeerPeer3Table3:Combination of link types associated with each exception type6Data StructuresIn this section we describe the data structures used to maintain state in a HLP router.Figure6shows theflow of routing information through the system,as well as the major components of the system.Figure6:Flow of routing information through systemWe describe each component below:Peer:A peer contains the necessary objects needed for receiving and sending routing information from and to neighboring routers.Each peer maintains the state machine for the connection associated with the corresponding neighbor,as well as the various timers needed during connection establishment and for keepalive messages.RibIpcHandler:Handles insertion of prefixes owned by this AS.Routing Information Base Input Table(RibInTable):Stores routes associated with corresponding neighboring router.Routes may be obtained via FPVs sent from neighbor,or from computation of shortest paths using link-state infor-mation.The type of tag assigned to a route is explained in Section4.1.PeerHandler:Handles reception and transmission of FPVs and LSAs.After a packet has been received,it is broken up into individual components(for instance,link changes,route withdrawals,route announcements,etc.)before being passed to HLPCore for processing.Updates passed from the DecisionTable are aggregated as much as possible within a packet(FPV or LSA)before being transmitted.Routing Information Base Output Table(RibOutTable):Stores the outgoing routes sent via FPVs.The contents of this table is a subset of the corresponding RibInTable of the neighboring router.PeerData:Contains information related to the peering link:–neighbor’s AS number and identification number(ID),–IP tuple of the connection,–neighbor’s peer type(customer,provider or peer),–metric,or cost of the link–various timeout values(hold,retry,keepalive)HLPCore:The HLPCore contains the Lib,DecisionTable,ExceptionTable,and the AS-Prefix Map.It maintains the periodic update timer3,and interfaces between the user and the system.The core also connects Peers with the Lib and DecisionTable,so that incoming routing information can be processed and then pushed out of the system if necessary.Link-State Information Base(LIB):The Lib stores link-state information gathered from LSAs received.The network topology constructed is then used to determine the shortest path to each destination AS from every neighbor.DecisionTable:The DecisionTable chooses the winning route amongst the routes stored in the RibInTables for a particular destination prefix.The selection is based on the order of preferences given in Section4.3.Winning routes are stored in a trie,after which they are pushed to the neighboring routers based on the route type as specified in Section4.4.In general the DecisionTable deals with FPVs,whilst the Lib deals with LSAs.ExceptionTable:The ExceptionTable stores the exceptions raised locally,as well as those raised by other ASs within the same hierarchy(exceptions raised are not explicitly propagated to other hierarchies).Currently,only information with regards to exception1are disseminated via LSAs.The ExceptionTable is used when the DecisionTable is determining whether a particular winning route should be sent to a neighbor,and when the Lib is computing the shortest path to destination ASs taking into account exception1s raised.AS-Prefix Map:This object stores the mapping of ASs to the corresponding advertised prefixes.Since the core of HLP manages routes at the prefix level4,and route changes are disseminated at the AS level,the AS-Prefix Map is required to translate between the two.Thus,for instance,incoming route changes(which will not include the prefixes involved,but just the AS path)will be processed in the HLPCore at the prefix level,and merged again just before the updates are pushed out.7Finite State MachineThefinite state machine for each peering connection is the same as that specified in[2].8Protocol FormatThe message header format as specified in [2]remains unchanged,as is the format of the Keepalive packet.In this section we describe the changes to the Open and Update (renamed Fragmented Path-Vector)packets,as well as introduce the LSA packet.8.1Open PacketVersionMy AS numberHold timeHLP identifierPeer type12241Figure 7:Format of Open packet,numbers denote lengths of corresponding fields in octetsSince a HLP network is dependent on the relationship between neighboring ASs,it is important that they agree on that.We thus include an additional field in the Open packet,the peer type field.The relationship type inserted in the field is with respect to the neighbor.For instance,if AS A is a customer of B,it will insert type corresponding to customer in the field of the Open packet it sends to B.Inconsistencies will result in the connection failing.8.2Fragmented Path Vector PacketThe format of the FPV ,shown in Figure 8,is similar to BGP’s Update packet,but with an additional AS Down field.When an AS becomes unreachable for any reason,rather than withdrawing every route to that AS,we propagate just the AS number in this field.Unfeasible routes lengthWithdrawn routesAS down lengthASnumbersTotal path attribute lengthPath attributesNetwork layerreachability informationX X2X 2X 2Figure 8:Format of FPV packet,the numbers denote lengths of corresponding fields in octets.An X means that the field length is variable.The format in which a network prefix is represented is shown in Figure 9.This representation is used for the network layer reachability information (NLRI)and withdrawn routes in Figures 8and 10.Length1PrefixX Figure 9:Representation of a prefix:the Length field uses 1octet,and the size of the Prefix field is variable.8.3Link State Advertisement PacketThe LSA packet is a new packet type,and the fields are shown in Figure 10.We describe the four main fields and their corresponding subfields as follows:1.link changes :This major field contains information regarding links grouped together according to an endpoint AS’number.For instance,all links stated in “link information (1)”have an end AS with number “AS (1)number”.Thus,multiple link changes can be aggregated and transmitted within the same packet.The format in which information for each link is transmitted is shown in Figure 11.2.unreachable ASs :These fields provide the list of ASs (“Unreachable ASs”)that are declared unreachable from an AS (“AS unreachable from”).This field is used to disseminate an AS’setting of exception 1.lengthLink changesAS unreachable from (1)UnreachableAS length (1)UnreachableASs (1)Unreachable AS lengthReachable AS length AS reachablefrom (1)ReachableAS length (1)ReachableASs (1)AS reachablefrom (n)ReachableAS length (n)ReachableASs (n)Unfeasible routes length Withdrawn routesNLRI total length AS announcingNLRI (1)NLRIlength (1)AS (1)numberLink changeslength (1)Linkinformation (1)NLRI (1)AS announcingNLRI (n)NLRIlength (n)AS unreachablefrom (n)UnreachableAS length (n)UnreachableASs (n)AS (n)numberLink changeslength (n)Linkinformation (n)222 222X2222NLRI (n)2222X2X22X22XXX X22XFigure10:Format of LSA packet.The numbers representfield size in octets,X means thefield size is variable.Neighbor AS number NeighborrelationOperation Reserved Metric1622432Figure11:Link information representation format.The numbers representfield size in bits.3.reachable ASs:Thesefields provide the list of ASs(“Reachable ASs”)that are declared reachable from an AS(“ASreachable from”).Note that the list of ASs must have previously been declared unreachable.Thisfield is used when deleting exception1.4.unfeasible routes:Similar to Update packets,thisfield holds the routes that have been withdrawn by ASs in the samehierarchy.5.NLRI announcements:Thefinalfield gives the prefixes that each AS is announcing.9Boot Up ProcedureThe HLP protocol does not require knowledge of the tier level an AS is at.When connection to a new neighbor is established,the following steps are taken:if neighbor is a peersend all routes tagged with PEER_FPV and CUSTOMER_LSAif neighbor is a customersend all routes tagged with PEER_FPV and CUSTOMER_LSAsend all link-state informationsend all exception informationif neighbor is a providersend all link-state information for customer ASssend all exception informationAdditional routes that match exceptions,if any,are also sent.10Exception Setting and RemovalHLP allows dynamic setting and deletion of exceptions.Setting of exceptions should cause the network state to become the same as if the exceptions were present on bootup.Similarly,deletion of exceptions should cause the state to be the same as if the exceptions were never present.The following steps are taken when the corresponding exceptions are raised or removed:Exception1:Upon setting of exception1,the AS broadcasts an LSA packet in its hierarchy indicating the lack ofa customer route to the destination AS.It removes route(s)to the destination AS(tagged with CUSTOMERLSA and PROVIDER。
【精选】跨文化交际word版(1)

Unit 1 introduction一.文化文化是冻结了的人际交流,而交流是流动着的文化----W.B. Pearce, 1994.背景:长期以来,文化被认为是无处不在,无所不包的人类知识和行为的总体。
被笼统地当作“生活方式”,社会生活的一切方面,积淀物,价值观念体系,众多规范,乃至艺术,政治,经济,教育,修养,文学,语言,思维的总和。
概括地讲,文化即是人们所思,所言,所为,所觉的总和。
在不同的生态或自然环境下,不同的民族创造了自己特有的文化,也被自己的文化所塑造。
It is said that there are at least 150 definitions about culture.“Culture may be defined as what a society does and thinks”(Sapir, 1921) “Culture is man’s medium, there is not one aspect of human life that isnot touched and altered by culture. This means personality, how people expressthemselves, including shows of emotion, the way they think, how they move, howproblems are solved, how their cities are planned and laid out, how transportation systems function and are organized, as well as how economic and government systems are put together and fuction.” (E.T. Hall,1959)“A culture is a collection of beliefs, habits, living patterns, andbehaviors which are held more or less in common by people who occupy particular geographic areas” (D.Brown, 1978)文化的特性:1). 文化是由人们的内隐和外显行为组成的。
英语论文分析学习-第1节-introduction

Contents of an introduction
Q2: which sentence states the importance of the research?
Look at the following examples and find the key words.
E.g1:
The design of reliable hinges is essential for the development of deployable structures in space applications.
The design of reliable hinges is essential for the development of deployable structures in space applications.
E.g2.:
3D-TV has recently received much attention from both academia and industry.
solved explains why the research is being done
(rationale,基本原理)
Contents of an introduction
Practice: fast-read sample 1 and decide how many
parts does the content consist of? And mark the key words if you can which help you to organize the structure.
1.introduction

Introduction to Immunology
Liu chun 2016 – 03 – 01
1
一、发展史:
古老: 16世纪 人痘预防天花
① 接触法 ② 痘浆法 ③ 旱苗法 ④ 水苗法
18世纪 牛痘预防天花 ( Jenner )
Edward Jenner discovered that cowpox vaccination protected against smallpox in 1796. Officially smallpox eradicated in 1979.
中 枢
2、未成熟 LC克隆遇Ag 刺激后发生克隆清除; 成 熟 LC克隆遇Ag刺激后则 活化增殖分化,并清除Ag; 3、由于未成熟 LC克隆 在胸腺、骨髓中与自身Ag 相遇而致自身反应性LC克 隆清除;所以成熟LC克隆 主要针对外来Ag。因而免
疫系统能区别自己与非己。
外 周
7
克隆选择学说 ( Burnet )
44
20世纪获得诺贝尔医学生理学奖的免疫学家
年代 1901 1905 1908 1912 1913 1919 1930 1951 1957 1960 1972 1977 1980 学者姓名 Behring Koch Ehrlich Metchnikoff Carrel Richet Bordet Landsteiner Theler Bovet Burnet Medawar Edelman Porter Yalow Dausset Snell Benacerraf Jerne Kohler Milstein Tonegawa Murray Thomas Doherty Zinkernagel 国家 德国 德国 德国 俄国 法国 法国 比利时 奥地利 南非 意大利 澳大利亚 英国 美国 英国 美国 法国 美国 美国 丹麦 德国 阿根廷 日本 美国 美国 澳大利亚 瑞士 获奖成就 发现抗毒素,开创免疫血清疗法 发现结核杆菌,发明诊断结核病的结核菌素 提出抗体生成侧链学说和体液免疫学说 发现细胞吞噬作用,提出细胞免疫学说 器官移植 发现过敏现象 发现补体, 建立补体结合试验 发现人红细胞血型 发明黄热病疫苗 抗组胺药治疗超敏反应 提出抗体生成的克隆选择学说 发现获得性移植免疫耐受性 阐明抗体的化学结构 阐明抗体的化学结构 创立放射免疫测定法 发现人白细胞抗原 发现小鼠H-2系统 发现免疫应答的遗传控制 提出天然抗体选择学说和免疫网络学说 杂交瘤技术制备单克隆抗体 单克隆抗体技术及Ig基因表达的遗传控制 抗体多样性的遗传基础 第一例肾移植成功 第一例骨髓移植成功 提出MHC限制性,即T细胞的双识别模式 提出MHC限制性,即T细胞的双识别模式
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1Introduction1.1Motivation and Structure of the BookA variety of on-going research is focused on the development and analysis of methods to decrease the time required to progress from the computer modeling of the design surface to the machining while maintaining or improving the quality of the surface.One of the most important areas is tool path planning for numerical control(NC)machining.The main goal is obtaining the cutter location and orientation data that allow for an efficient surface milling within an allowed machining error.Five-axis NC machines are becoming increasingly popular due to their ability to handle geometrically complex workpieces composed of raw material such as wood,wax,rubber,metal,stone,plastic,etc.Moreover,up-to-date five-axis NC machines are characterized by a high material removal rate and an efficient surfacefinish up.Typically,manufacturing of the design surface by an NC machine com-prises two stages,a rough cutting and afinish machining.During the rough cutting,the raw material is removed as fast as possible while ensuring no ex-cessive cutting or gouging.During thefinish machining,the tool is placed at the maximum contact with the surface to remove the remaining excess and create a well-finished and accurate surface.Afterfinishing,the remaining scal-lops which are inevitably generated on the machined surface must be removed by manual surface grinding and polishing.Thefinish machining and manual polishing stages require as much as75%of the total machining time.Besides, manual polishing is prone to error and undesirable irregularities.Five-axis machining offers an improvement in efficiency of both the rough andfinish machining stages over the three-axis counterpart.Infive-axis ma-chining,the tool orientation relative to the workpiece can be controlled by two additional degrees of freedom so as to achieve higher machining efficiency. With these advantages,a large number of tool path planning methods for five-axis machining has been developed and presented in the literature.21IntroductionIn chapter1we present the most popular CAD/CAM data formats and give a short literature survey on mathematical methods for optimization of five-axis machining.The survey has been focused on tool path interpolators, adaptable geometric patterns and methods for tool posture and gouging avoid-ance.Chapter2exposes the readers to basic knowledge required to perform five-axis cutting.The G-code programming,examples offive-axis machining of simple shapes and verification of the cut using solid modeling software is presented and discussed.The chapter can be used as a short introduction into five-axis machining in the framework of an undergraduate course in Computer Aided Design(CAD)and Computer Aided Manufacturing(CAM).Chapter3introduces theories required to embrace the concepts of the tool path optimization forfive-axis machining.The chapter presents such funda-mental issues as kinematics of thefive-axis machines,part surface represen-tation,machining strip,tool orientation and gouging avoidance as well as the forward step error.A variety of configurations of thefive-axis machines is also discussed and analyzed.This chapter can also be used at an undergraduate or a postgraduate level for CAD/CAM related studies.Chapters4and5present advanced optimization schemes based on the adaptable geometric patterns,namely,the space-filling curves(SFC)and adaptive curvilinear grids.The SFC tool path has a number of attractive features such as the possibility to locally adapt the curve in such a way that the cutting device travels along the optimal direction.In addition,the entire surface is cut in one path eliminating the need of tool retractions.The use of the concept of curvilinear grids allows to simultaneously adapt the points on the tool paths to create more efficient zigzag,spiral or even SFC structures. The combination of the SFC and grid generation allows for tool paths on surfaces with complex irregular boundaries,cuts off,pockets,islands,etc.Three-axis machines are often thought of as three dimensional plotters. However thefive-axis machine is more like a big bore machine.That is why changing from three-axis tofive-axis programming is not an easy task.In particular,the idea of optimizing rotations may seem totally foreign from the viewpoint of the three-axis machining.Therefore,chapter6presents the the-ory and practice of optimization of rotations forfive-axis machining.Several optimization algorithms based on the shortest path techniques are presented and discussed.Chapter7presents a theoretical background developed to construct nu-merical algorithms to minimize kinematics error introduced by the initial setup offive-axis milling machines.The initial setup consists of the posi-tion and orientation of the workpiece with respect to the mounting table and, optionally,the machine’s initial configuration.Given a set of cutter contact points and tool orientations,a least-squares optimization procedurefinds the optimal setup parameters.1.2CAD/CAM Formats3 1.2CAD/CAM FormatsSculptured or free-form surfaces are widely used in today’s manufacturing industries for a variety of applications such as the production of dies,molds, aerospace and automotive parts,etc.The surfaces are usually characterized by complex geometries and variable curvatures.A single surface is usually composed of patches represented mathematically by parametric forms such as the Bezier surfaces,B-splines and NURBS.A design and manufacture of the sculptured surface parts is an expensive and time-consuming process.First,a design surface is transformed into a computer model(possibly with the help of CAD programs).The computer model is then used by the CAM programs to generate commands to move the cutting tool of the machine.The resulting set of tool positions and orientations constitutes a tool path to machine the desired surface.Every CAD or CAD/CAM software uses an internal format to represent and control the required part.When the geometrical data is transferred from a CAD system to a CAD or CAM system,a neutral format for the data transfer is used.One of the most popular is the IGES(Initial Graphics Exchange Specification)format(see the history of the IGES format in[40]).The IGES format supports the use of surfaces defined by NURBS(Non Uniform Rational B-Splines)or derivatives of these representation.A good book for a beginner in NURBS is[31].An advanced reader could use[98]and[24].There are also several free libraries designed to control and manipulate the NURBS, such as NURBS++package[1]and NURBS Toolbox[2].Some free IGES-file processing tools are collected at the NIST/IGES web page[3].The STLfiles,originally employed by the so-called layered manufacturing technologies such as the rapid prototyping,are now becoming more and more popular due to the simplicity of describing the part surfaces.As opposed to the complex description of surfaces employed by the IGES format,the STL format defines the surface as a collection of triangles each described by the coordinates of its three corners and a normal-vector.This technology provides an important platform for CAD/CAM applications due to the existence of many robust triangulation algorithms.Besides,the surface models are often composed of many patches.Therefore,by tessellating the patches and creating groups of triangles one can use many well established methods for treating intersections,trimming,shading,hidden surface removal and gouge protection [36].The machining is usually performed by creating contours obtained by slicing the STL-surface[85,115].Of course,slicing of the NURBS surfaces is also possible,but it requires much more sophisticated techniques such as[81]. The contours are then saved using the SLC format(see[4]for instance).Other popular CAD/CAM formats include STEP(Standard for the Ex-change of Product Data),DXF(The Drawing Exchange Format from Au-toDesk)and many others.As a matter of fact,the difference in data formats has created a large software industry specializing in transferring,adapting and41Introductionprocessing the CAD/CAMfiles.A table of compatibility of the CAD/CAM formats can be found,for instance,at[5]or[6].1.3Short Literature SurveyOptimization of tool paths forfive-axis machining may include many features and multiple criteria such as the accuracy,the length of the tool path,the machining time,the size of the remaining scallops,etc.It may also include gouging avoidance,satisfying the machine axis limits,maximizing the volume of the removed material,reducing the tool wear.The optimization may also take into account the thermal characteristics of the cutting process,the tool bending,the vibrations and jacks,the workpiece positioning and many other parameters.The criteria could also include the configuration of the machine or specific parts of the machine as well as the design of the clamping device. Readers interested in citations before1997could use a fairly comprehensive survey by Dragomatz and Mann[25].The survey presents a classification of research papers on three-axis andfive-axis machining related to geometries of the tool paths and tool positioning.These categories include:1)systems,2) isoparametric paths,3)non-isoparametric paths,4)planar pocketing paths, 5)sculptured surface pocketing paths,6)roughing paths,7)tool position-ing,8)offset surface methods,9)five-axis machining,10)mesh models,11) pixel and point models,12)simulation and verification.Of course,the above groups overlap.Techniques involved in one group could be also involved in another group.For example,systems for tool path generation may include all of the above mentioned techniques.Roughing paths may be generated by the isoparametric or non-isoparametric schemes and so on.Our survey is focused onfive-axis machining.It also includes the three-axis methods but as long as they can be extended to thefive-axis case.Besides, we confine ourselves by techniques designed for cutting the part surface by bottom-edge of the tool,e.g.,flat-end milling andfillet milling.Many interest-ing methods designed forfive-axis grinding(flank milling)and plunge milling have not been included.The survey has been focused on the following categories:1)tool path in-terpolators,2)adaptable geometric patterns and3)methods for tool posture and gouging avoidance.We believe that the above procedures are the most important part for efficient design of the numerical methods forfive-axis ma-chining.Tool path interpolatorsIn the CNC machines,the tool motion is controlled by a sequence of reference points that are fed to the servo control system.The NC controllers employ linear interpolation techniques[66]or a circular interpolation which may result in discontinuities of the velocity at the junctions of the segments.They may1.3Short Literature Survey5 also result in high accelerations,subsequent surface inaccuracies and long machining time required to eliminate them.Furthermore,the modern high speed machining requires feedrates up to40m/min with accelerations up to 2g.At such high speeds,small discontinuities in the reference tool path can result in undesirable high frequency harmonics in the reference trajectory, which may end up exciting the natural modes of the mechanical structure and the servo control system.Although the NC program cannot change the way the controller moves the machine parts,the cutter location points and the rotation angles required to cut the prescribed curve can be changed in such a way that these errors are minimized or at least decreased.The task of generating such a sequence of points is called interpolation.Early interpolation schemes solved the problem of discontinuities by smoothing the tool path at the corners[17]and using low passfilters[126].However,the problem is due to the difference between the chord and the arc lengths.That is why,generating the tool positions by incrementing the chord length leads to the feedrate instabilities.Therefore, if thefit curve is parameterized with respect to the arc length,these type of the inaccuracies will be eliminated.Therefore,many modern interpolation schemes are focused onfinding a suitable polynomial interpolation(such as the B-splines)parameterized by means of the arc length.Unfortunately,such parameterization is not analytically possible for gen-eral spline curves.Therefore,a number of approximate solutions were pro-posed.For instance,Wang and Yang[122]generate the trajectory by means of cubic and quintic splines using the chord length and a nearly arc length parameterization,Zhang and Greenway[133]implemented a similar B-spline based interpolation.Coordinate transformations between the workpiece and machine coordinate systems forfive-axis milling were incorporated in the inter-polator by Lo[77,79]and Bohez et al.[14].An extra jerk continuity condition has been included into the solution in[121].Furthermore,the limitations of the machine tool drivers may cause fail-ure in maintaining the commanded feedrate which in turn may lead to the tool chatter or breakage.Therefore,Weck et al.[125]have implemented cubic spline interpolation where adaptation of the feedrate was based on the physical limitations of the drives.The smooth transitions were obtained using fourth order acceleration profiles.Erkorkmaz and Altintas[30]presented a quintic spline trajectory generation algorithm that produced continuous position,ve-locity,and acceleration profiles.Smooth accelerations and decelerations were provided by imposing constrains on thefirst and second time derivatives of the feedrate.In1994,Farouki and Sakkalis[33]introduced the Pythagorean-Hodograph (PH)curves to solve the problem of feedrate control for three-axis machines. The curves provide a mathematically elegant solution to the above mentioned problems occurring in NC machining.In particular,the arc length was repre-sented by a polynomial function of the curve parameter.In[32],a2D Hermite interpolation combined with the PH was proposed and analyzed.The ideas61Introductionwere further developed in[34,35].It was shown that since the arc length of the PH curves can be represented by a polynomial function of the curve parameter,they can be successfully used for the interpolation.Consequently, a variety of planar PH curves matching given Hermite type boundary data were developed(see,for instance,[61,88,119]).M¨u ller et al.[90]presented an algorithm for simultaneousfive-axis spline interpolation which merges the PH interpolation and the analytic solution of the inverse kinematics problem using the template equation method.The result is a time-dependent spline which represents the given tool path with a high ngeron et al.[69]suggested a polynomial B-spline interpo-lation which took into account the kinematics of thefive-axis machine.The B-spline interpolation of the tool path in the part coordinate system includes the accuracy requirements and describes afive-axis tool path in a format adapted to the communication between the CAM software and the NC unit. The CAM output is directly expressed through the B-spline curves.Lo[80] introduced spline interpolators for isoparametric,iso-scallop and iso-planar machining methods(see the forthcoming section).ˇS´ır et al.[118]presented biarc interpolation techniques based on spline curves composed of circular arcs and compared them with the PH curves.Finally,a number of papers introduce interpolators designed for high speed milling.During the high speed machining the actual average feedrate could be significantly lower than the programmed feedrate due to the physical restric-tions of the machine tool and the block processing time of the CNC controller. In many cases the machine tool hardly reaches the maximum feedrates offered by the manufacturer.This happens when the block processing time is longer than the block execution time and the machine reaches the end point of the segment before information required for the next movement is available.In this case modern CNCs automatically reduce the programmed feedrate which results in a lower real feedrate and,consequently,a longer machining time. This relatively new issue has been discussed in[55,64,87,109].Adaptable geometric patternsThis section surveys research aimed to construct geometric patterns adaptable to a criteria which represents a certain estimate of the quality of the tool path such as the kinematics error,scallop heights,undercuts,overcuts,etc.It also includes methods for complex pocket milling since they often require special geometric patterns.Finally,the construction of the geometric patterns might or might not take into account the actual machine kinematics.In many cases, patterns employed for three-axis machining are also applicable,with certain modifications,to thefive-axis machining.The simplest tool path planning algorithms employ structured zigzag or spiral patterns due to their simplicity and the ease of computation(see [25,108]).The zigzag and spiral motions employ uniform steps along a coor-dinate which parametrizes the desired curve extracted from the part surface.1.3Short Literature Survey7 The early adaptable methods replace the uniform spacing in favor of distrib-uting the cutter location points by analogy with interpolation characterized by a variable step.First,the trajectories were assumed to be linear.Next,the desired curve was approximated using a certain technique,for example,em-ploying arcs.Next,the forward step was selected by considering the deviation between the approximation and the straight line(see,for instance,[73]).The choice of the forward step can be performed by bisection or another inexpen-sive method.Some of the recent developments of these ideas are presented in [22,73].As mentioned before the most popular geometric solutions are the zigzag and the spiral isoparametric patterns constructed for single-patch or multi-patch parametric surfaces S(u,v).In this context,the term isoparametric means that the zigzag tool path is generated in the parametric space u−v along one of the coordinates,say,u.The v coordinate is then used to generate the forward steps.Another approach is the contour based or iso-planar machining.In this case the cutter path follows intersection curves of the parametric surface anda series of vertical planes.One of thefirst papers reporting such techniques is[19],see also[104].The both methods calculate the maximum allowable distance between the consecutive tracks using a scallop height limitation.However,if the maximum allowable distance is calculated globally,that is,the minimal allowable dis-tance is taken from all the maximum allowable(pointwise)distances,then the method does not produce a constant scallop height.As the result,the ma-chining efficiency is limited.Methods to maintain the constant scallop height called the iso-scallop machining methods werefirst proposed in[76,112].Lo[78]developed these approach and adapted it tofive-axis machining. His algorithm starts with an initial curve in the parametric domain and calcu-lates offset curves so that the scallop height remains approximately constant. The algorithm is designed forflat-end cuter and includes adaptive inclina-tion which maximizes the machining strip.The algorithm also includes a local gouging avoidance.The local gouging refers to the removal of an excess mater-ial in the vicinity of the cutter contact point(CC point)due to the mismatch in curvatures between the tool as it is carried along the tool path and the desired surface(see the forthcoming section for details).Rao and Sarma[103] introduced similar local gouging avoidance algorithms applicable to surfaces characterized by low curvature and cut by theflat-end cutter.Finally,Lo[80] presents an iso-scallop tool path for ball nose cutters.Evaluation of the machining strip versus the inclination and the direction could lead to complicated tool path topologies.For each tool position on the surface there exists at least one direction which maximizes the machining strip. The corresponding set of vectors mapped onto the parametric space(u,v) constitutes a2D vectorfield which could be further analyzed.A continuous tool path which visits every point and follows the optimal direction at every point constitutes the optimal tool path which will maximize the machining81Introductionstrip globally.However,such a path can rarely be found in practice due to the complexity of the resulting vectorfield.An algorithm tofind a suboptimal solution of this problem is presented in[20].The authors introduce an“initial”tool path which has the largest average machining strip.Next,the entire tool path is constructed by propagating the initial path inside the region until it substantially deviates from the streamlines.A few papers explore other“iso”methods such as the iso-distance and the iso-curvature methods(see,for instance,[47]).In[63]an additional tool path segments are appended to the basic tool path in order to achieve constant cutting forces and to avoid chatter vibrations in the entire machining area. Furthermore,the necessity to create geometric patterns suitable for the so-called pocket milling leaded to a series of methods designed for parts with one or more complex shaped“islands”inside.The methods are also needed to machined the so-called trimmed surfaces when the boundaries of the surface are defined by intersections with other surfaces.In1998,Choi and Jerard[21]introduced a term regional milling referring to situations when the machining operation,occurs in a region specified by boundary curves.According to[96]the regional milling can be performed using the same types of tool path topologies,namely,the contour-based offset type and the direction-parallel type.The direction-parallel type has been analyzed in[45,46,49],whereas the direction-parallel type in[21,48,51,94].One of the most important problems in the contour-based machining is linking the contours in such a way that the number of tool retractions is minimized.Held et al.[51]presents an algorithm designed for this type of machining based on the proximity maps and the Voronoi diagrams.The au-thor suggests a linking procedure requiring a spanning tree of the planar graph of the monotonic pouches.Park and Chung[95]propose a contour linking al-gorithm accommodating minimization of slotting,tool-retractions and drilling holes.Park et al.[96]presented a tool path linking algorithm,which guaran-tees a“zero”number of tool-retractions.The algorithm employs the concept of tool path element net providing information on the parent/child relation-ships.Jeong and Kim[57]present an algorithm designed to offset the bound-ary curves in the complex shaped region using the Voronoi diagram.Each curve segment is offset within the corresponding Voronoi polygon to avoid the degeneracy problem.Jeong and Kim[58]introduce a distance map algorithm which effectivelyfinds the characteristic points and self intersection points of the offset curve segments and as the result eliminates such topological prob-lems as loops,ridges and cusps.A forward locus tracing method is introduced in[68].The algorithm searches for all intervals split by intersections of the planar curves and maps the2D transversal intersections onto a1D interval.Suppose that the part is partitioned into a grid of cells each of them being a curvilinear triangle or a curvilinear rectangle.The optimization can then be considered as constructing a path which visits each cell,does not have intersections,requires minimal number of tool retractions and satisfies1.3Short Literature Survey9 some error related criteria.Pocket machining using staircase or window frame patterns were proposed in[97].Hansen and Arbab[46]developed a scan line algorithm for generating NC tool paths for arbitrarily shapedflat bottom pockets with islands.Flat pocket machining based on grids was suggested by Bao and Yim[11].Treating the tool path generation as a navigation problem on grids leaded to approaches exploiting the shortest path optimization and related tech-niques.Suh and Shin[110]developed a neural network model to obtain the tool path in rough pocket machining as a solution to the traveling salesman problem.A good mathematical analysis of such strategies is given in[9].The problem is formulated as follows:given a region in the parametric plane and the shape of a cutterfind a shortest tour/path for the cutter such that every point within the region is covered by the cutter at some position along the tour(tool path).Additionally the cutter could be constrained to stay within a certain region.Narayanaswami and Choi[91]present a grid-based3D naviga-tion approach for generating NC tool path data for both linear interpolation and a combination of linear and circular interpolation for three-axis milling. The approach can be extended to thefive-axis case.The space-filling curves(SFC),having been applied in computer graphics, image processing,information systems,can be also seen as a suitable naviga-tion pattern for generation offive-axis paths.Thefirst application of the SFC to NC tool path generation was reported in[23,44].Griffiths[44]proposed the use of the Hilbert’s curve as a tool path,while Cox et al.[23]used various forms of space-filling curves such as Moore’s curve.Fractal based techniques were suggested by Chen et al.[18].However,neither SFCs nor fractals have never been very popular in the five-axis machining community due to a large number of sharp turns produced by the conventional SFCs.A concept of an adaptive space-filling curve for tool path planning forfive-axis NC machining was proposed in[8].The space-filling curves,adapted to the local optimal cutting direction,produce shorter tool paths.Besides,the tool path correction stage suggested in[8]makes it possible to eliminate the effect of sharp angular turns which characterize the standard SFC patterns.These techniques will be presented in Chap.4of this book.Finally,the entire tool path can be considered in the framework of the grid generation technologies.The concept wasfirst introduced by Makhanov [82]and developed in[15,83].The grid generation techniques are surprisingly well-adapted to tool path optimizations.As a matter of fact,the concept of a grid refinement contains almost all the main ingredients for tool path plan-ning,such as grid adaptation to the regions of large milling errors,possibility to easily construct curvilinear versions of the conventional zigzag and spiral patterns and adaptation to constraints related to the tool diameter and the scallop height.Moreover,in contrast to the standard techniques characterized by a local error estimate,grid generation deals with a global spatial error and consequently adapts all the CL points simultaneously.These ideas were de-veloped further in[84],specifically forfive-axis machining whereas Bieterman101Introductionand Sandstrom[12]suggested a similar approach,independently.Finally,Sun et al.[111]presented a spiral version of the grid generation algorithm applied to tool path generation.The advanced grid generation techniques forfive-axis machining will be considered in Chap.5of this book.Tool posture and gouging avoidanceThis section deals with techniques providing an optimal position and orien-tation of the tool in a particular neighborhood of the machined surface.The emphasis is on the orientations prescribed independently with regard to a certain criteria such as the local gouging avoidance,machining strip,scallop height,avoiding global gouging constraints,etc.The most important appli-cation of these techniques is cutting the part surface by theflat-end orfillet mill.In1987,Marciniak[86]showed that infive-axis machining the maximum width of machined strip on the surface could be obtained if the tool moved on the surface approximately along the minimum curvature line.The maximum width of the strip depends on the difference of the surface main curvatures at the contact point.Some of the early research papers exploiting this idea are[37,67,74].Furthermore,Kruth and Klewais[67]introduced an optimal milling direction parallel to the principal direction of the surface with the minimum curvature.Gani et al.[37]notice that“One of the critical problems infive-axis milling is the positioning of the cutter in relation to the surfaces in order to machine without having overcut(gouging)or undercut.Because of this problem,ball-end cutters are preferred.Undercutting does not cause a big problem when using ball-end cutters.The calculation of the NC tool path for ball-end cutters is mainly a problem of surface offset.An important drawback of ball-end cutters is the varying cutting speed along the tool radius.The maximal cutting speed is reached on the tool diameter,and at the tool tip it is zero.This leads to cutting edge chipping as well as poor surface roughness”.Recall that as long as thefive-axis machines are considered,the tool has five degrees of freedom relative to the surface.The three spatial degrees are used to locate the tool at the cutter location points point.The extra two ro-tational degrees are used to establish the orientation of the tool represented by the inclination angle and the tilt angle(see,for instance,[103])or the tilt angle and the yaw angle[60].The angles are evaluated in a local coordinate system usually defined by the feed direction,the surface normal and the cor-responding cross product vector.In the case of theflat-end mill the boundary of the base of the tool,which is the part of the tool cylinder is called the cutting circle of the tool.The effective cutting shape(also referred to as the tool swept section)is defined as a projection of the base of the tool onto the plane normal to the feed direction.Actually,in the case offlat-end mill the projected bottom edge becomes an ellipse called the effective cutting ellipse.。
