Replicated Web Objects Design and Implementation
Synopsys OptoDesigner 2020.09安装指南说明书

3. Troubleshooting scanning issues........................................................25
Accidental full scan proliferation by folder paths which include build or commit ID............................ 25 Solution......................................................................................................................................25
Contents
Contents
Preface....................................................................................................5
1. Scanning best practices......................................................................... 8
PDMS英语词汇

PDMS关键字翻译1、主要模块(Module)ADMINISTRATION 项目管理PARAGON 元件库、等级库维护DESIGN 三维设计、多专业集成DRAFT 平竖面图生成ISODRAFT 轴测图生成1.1、Design模块菜单Design三维模型设计、模块切换Display 显示Edit 编辑View 视图Selection 选择Query 查询Settings 设置Utilities 工具Create 生成Modify 修改Delete 删除Window 窗口1.1.1、Design 子菜单Save work 保存任务Get work 获取任务、最新设计Extract ControlSession Comment ———————————————General 总体Equipment 设备Pipework 管道Cable Trays电缆槽盒HVAC Designer暖通Structures 钢结构Beams & Columns 管廊Panels & Plates平台板Walls & Floors墙地面ASL Modeller 平台Hangers & Supports 支吊架Design Templates ———————————————Modules 模块(其他模块)MonitorSpoolerDraft 平竖面图生成Isodraft 轴测图生成Paragon 构造元件库SpeconPropconLexiconAdmin 项目用户管理———————————————Exit 退出1.1.2、Create 子菜单Copy 复制Offset 偏移Rotate 旋转Mirror镜像Site 单元Zone 域Group群组————————————————Equipment 定义设备名称和定位点Sub-EquipmentPrimitive 生成设备管嘴和基本体Standard 标准设备的设计模板---------------------------------------Pipe 生成管道Branch 生成管道分支Component 生成在线管件1.1.3、管道设计模块菜单1.2、基本体(Primitive)基本体分为正实体(Solid)和负实体(Negative),负实体用以在正实体上切削。
三维设计英语试题及答案

三维设计英语试题及答案一、选择题(每题2分,共20分)1. Which of the following is NOT a common 3D modeling software?A. AutoCADB. SketchUpC. PhotoshopD. Blender2. The process of creating a 3D model is known as:A. RenderingB. ModelingC. TexturingD. Lighting3. What does UV mapping refer to in 3D design?A. The process of applying colors to a 3D modelB. The process of mapping a 2D image onto a 3D modelC. The process of creating a wireframeD. The process of adding details to a 3D model4. Which of the following is NOT a type of 3D printing material?A. PLAB. ABSC. InkD. Resin5. In 3D animation, what does 'keyframe' mean?A. The starting point of an animationB. A point in time where an object's position is setC. The end point of an animationD. The speed at which an object moves6. What is the term for the process of making a 3D model appear more realistic by adding surface details?A. SmoothingB. SubdivisionC. DisplacementD. Extrusion7. Which of the following is a unit of measurement used in 3D design?A. PixelB. MeterC. KilogramD. Bit8. What does LOD stand for in 3D modeling?A. Level of DetailB. Line of DefenseC. Light of DayD. Long Overdue9. In 3D design, what is the purpose of a 'rig'?A. To create a skeleton for a characterB. To set the lighting of a sceneC. To define the camera's viewD. To apply textures to a model10. What is the term used to describe the process of converting a 3D model into a 2D image?A. ProjectionB. ExtrusionC. TexturingD. Rendering二、填空题(每空2分,共20分)11. The ________ is a tool in 3D modeling software that allows you to move objects around in the workspace.(答案: Move Tool)12. When creating a 3D model, the first step is usually to create a basic shape known as a ________.(答案: Primitive)13. The process of adding color and texture to a 3D model is called ________.(答案: Texturing)14. In animation, the ________ is the main character or object that the story revolves around.(答案: Protagonist)15. The ________ is the process of adjusting the camera angle and position to frame a scene.(答案: Camera Setup)16. To create a 3D model of a complex object, you may need to use a technique called ________.(答案: Boolean Operations)17. The ________ is the process of adding motion to a 3D model.(答案: Animation)18. In 3D printing, the ________ is the layer-by-layer process of building an object.(答案: Additive Manufacturing)19. The ________ is a tool in 3D modeling software that allows you to modify the shape of a model by dragging points. (答案: Sculpt Tool)20. When a 3D model is complete, it is often saved in a file format that ends with the extension ________.(答案: .obj)三、简答题(每题10分,共20分)21. Explain the difference between a 'polygon mesh' and a'NURBS' in 3D modeling.(答案: A polygon mesh is a collection of vertices, edges, and faces that form a 3D shape. It is commonly used in video games and animation. NURBS, on the other hand, stands for Non-Uniform Rational B-Splines and is a mathematical model used to create smooth, curved surfaces. It is often used in industrial design and automotive applications.)22. What are the advantages and disadvantages of using a'real-time rendering' engine in 3D animation?(答案: Advantages of real-time rendering include theability to see the final product as you work, which can save time and provide immediate feedback. It is also computationally less intensive than pre-rendering. Disadvantages include potential limitations in visual quality compared to pre-rendered scenes, and the fact that it may。
JMGPM 25 M9BW 30 通用接线器型号说明文档说明书

JMGPM 25M9BW30Port thread typeNil M thread ø12 to ø32Rc ø40 to ø100TN NPT TFGTypeSpecial functionElectrical entryI n d i c a t o r l i g h tWiring (Output)Load voltage Auto switch model Lead wire length [m]Pre-wiredconnector Applicable load DCACPerpendicularIn-line0.5(Nil)1(M)3(L)5(Z)S o l i d s t a t e a u t o s w i t c h———Grommet Yes 3-wire (NPN)24 V5 V, 12 V —M9NV M9N V V V v v IC circuit Relay, PLC3-wire (PNP)M9PV M9P V V V v v 2-wire12 V M9BV M9B V V V v v —Diagnostic indication (2-color indicator)3-wire (NPN)5 V, 12 V M9NWV M9NW V V V v v IC circuit 3-wire (PNP)M9PWV M9PW V V V v v 2-wire 12 V M9BWV M9BW V V V v v —Water resistant (2-color indicator)3-wire (NPN) 5 V, 12 V M9NAV ∗∗M9NA ∗∗v v V v v IC circuit 3-wire (PNP)M9PAV ∗∗M9PA ∗∗v v V v v 2-wire12 VM9BAV ∗∗M9BA ∗∗vvVvv—Applicable Auto Switches /Refer to the WEB catalog or Best Pneumatics for further information on auto switches.∗ Lead wire length symbols: 0.5 m………… N il (Example) M9NW 1 m………… M (Example) M9NWM 3 m………… L (Example) M9NWL 5 m………… Z (Example) M9NWZ∗ For details about auto switches with pre-wired connector, refer to the WEB catalog or Best Pneumatics.∗ Auto switches are shipped together, (but not assembled).∗ Solid state auto switches marked with “v ” are produced upon receipt of order.∗∗ Water resistant type auto switches can be mounted on the above models, but in such case SMC cannot guarantee water resistance.Please contact SMC regarding water resistant types with the above model numbers.How to OrderCylinder stroke [mm]Refer to “Standard Strokes” on page 4.Bearing type MSlide bearingBore size1210 mm x 21612 mm x 22016 mm x 22520 mm x 23225 mm x 24032 mm x 25040 mm x 26345 mm x 28056 mm x 210071 mm x 2Auto switchNilWithout auto switch (Built-in magnet)∗ For applicable auto switches, refer to the table below.Number of auto switchesNil 2S 1nnCompactGuide CylinderJMGP Seriesø12, ø16, ø20, ø25, ø32, ø40, ø50, ø63, ø80, ø1003Standard StrokesOUTIN[N]Bore size [mm]Rod size [mm]Operating directionPiston area[mm 2]Operating pressure [MPa]0.20.30.40.50.60.7ø12(ø10 x 2)6OUT 1573147637994110IN 101203040506070ø16(ø12 x 2)6OUT 226456890113136158IN 17034516885102119ø20(ø16 x 2)8OUT 40280121161201241281IN 3026090121151181211ø25(ø20 x 2)10OUT 628126188251314377440IN 47194141188236283330ø32(ø25 x 2)12OUT 982196295393491589687IN 756151227302378453529ø40(ø32 x 2)16OUT 16083224836438049651126IN 1206241362483603724844ø50(ø40 x 2)18OUT 25135037541005125715081759IN 2004401601802100212031403ø63(ø45 x 2)20OUT 31816369541272159019092227IN 25535117661021127615321787ø80(ø56 x 2)25OUT 492698514781970246329563448IN 394478911831578197223672761ø100(ø71 x 2)30OUT 7918158423763167395947515543IN 6505130119512602325239034553Note) Theoretical output [N] = Pressure [MPa] x Piston area [mm 2]Theoretical OutputSpecificationsBore size [mm]Standard stroke [mm]ø12 (ø10 x 2)ø16 (ø12 x 2)10, 20, 30, 50, 100ø20 (ø16 x 2)ø25 (ø20 x 2)20, 30, 50, 100, 150ø32 (ø25 x 2)ø40 (ø32 x 2)ø50 (ø40 x 2)ø63 (ø45 x 2)ø80 (ø56 x 2)ø100 (ø71 x 2)25, 50, 100, 150, 200∗ Intermediate strokes are available as a special order.Bore size [mm]ø12(ø10 x 2)ø16(ø12 x 2)ø20(ø16 x 2)ø25(ø20 x 2)ø32(ø25 x 2)ø40(ø32 x 2)ø50(ø40 x 2)ø63(ø45 x 2)ø80(ø56 x 2)ø100(ø71 x 2)Action Double actingFluidAir Proof pressure1.05 MPa Maximum operating pressure 0.7 MPa ∗1Minimum operating pressure 0.15 MPa Ambient and fluid temperature 5 to 60°CPiston speed Note)∗50 to 300 mm/s ∗150 to 250 mm/s ∗1Cushion Rubber bumper on both ends LubricationNot required (Non-lube)Stroke length tolerance+1.50mmNote) Maximum speed with no load∗ Depending on the system configuration selected, the specified speed may not be satisfied.∗1 Maximum operating pressure and piston speed are different from the current product (MGP series).[kg]Bore size [mm]Stroke [mm]1020253050100150200ø12 (ø10 x 2)0.090.12—0.140.190.30——ø16 (ø12 x 2)0.100.13—0.150.200.32——ø20 (ø16 x 2)—0.21—0.250.330.530.72—ø25 (ø20 x 2)—0.28—0.330.430.680.92—ø32 (ø25 x 2)——0.60—0.77 1.11 1.44 1.78ø40 (ø32 x 2)——0.80— 1.07 1.62 2.16 2.70ø50 (ø40 x 2)—— 1.27— 1.63 2.36 3.09 3.82ø63 (ø45 x 2)—— 1.60— 2.03 2.89 3.74 4.60ø80 (ø56 x 2)—— 2.81— 3.47 4.79 6.127.44ø100 (ø71 x 2)——4.48— 5.407.229.0510.87WeightSymbolRubber bumperRefer to pages 10 and 11 for cylinders with auto switches.·Auto switch proper mounting position (detection at stroke end) and mounting height·Minimum stroke for auto switch mounting ·Operating range·Auto switch mounting4Compact Guide CylinderJMGP Series。
基于拾取算法的产品交互式Web3D模拟的研究与实现

,
为实现对部件的精准获取和控制 , 引擎需要实 现拾 取功 能 .
21 图形在 屏 幕上 的 三维显 示 和拾 取 的基本 原 理 .
要将现实世界的物体 以立体 的视 觉效果在屏 幕上显示 , 需要进行渲染管线 的处理 . 所谓渲染管 线 , 指 图形三 维 显示 时 , 常需 要先 建 立 3 是 通 D场景
收稿 日期 :0 11—1 2 1-01. 基金项 目: 国家自然科学基金资助项 目(0 7 1 o. 6 64 0 ) 作者简介 : 陈煜(9 4 , , 17 ÷ 女 博士研究生 , 讲师 , 主要研究方 向: 计算机 图形学 、 数字图像处理 , ma :hn2 i. uc . E- i c ey @nie .n l td
2 三维 图形 用 三 角形 网格 描述 [ 为 了解 决 过 ) 7 1 , 间的原点到 为视 图空 间下的射线. 3 将步骤 2 中的射线变换到世界空间中, ) ) 则射 度拾取 的问题 , 在包 围盒的范围 内, 线遍 历三角 射 线 可表 示 为 P t= ot, 变 换 由视 图变 换 的逆 运 形求交 , ()P+P. 该 以此来精确拾取图形. 拾 取 可 分 为 3个 步 骤 进 行 :)获 得 射 线 的矢 1 算 来 完成 .
1 )屏 幕 上 被点 击 的二维 坐 标 先 转化 为 投 影 空 间 内的三 维坐标 . 2 再 转换 至视 图空 间下 . 点 为 P, 视 图空 ) 设该 l 从
即通过射线与包 围盒求交 , 以快速确定拾取范围. 由
于各 三 维 图形 的形 状 往往 并 不 规则 , 在包 围盒 的 范 围 内 , 些 点并 不 属 于 图形 对 象 , 这 种 现 象 为 过 有 称 度 拾取 .
中考科技创新教育英语阅读理解25题

中考科技创新教育英语阅读理解25题1<背景文章>Artificial intelligence (AI) is playing an increasingly important role in the field of education. One of the most significant applications is intelligent tutoring systems. These systems can provide personalized learning experiences for students, adapting to their individual needs and learning styles.For example, an intelligent tutoring system can analyze a student's performance on quizzes and assignments and then provide targeted feedback and additional practice materials. It can also adapt the difficulty level of the content to ensure that the student is challenged but not overwhelmed.Another application of AI in education is personalized learning. By analyzing a student's learning history and preferences, AI can recommend learning resources and activities that are tailored to their interests and abilities. This can help students stay engaged and motivated in their learning.In addition, AI-powered chatbots can answer students' questions and provide support outside of class hours. This can be especially helpful for students who may be shy or hesitant to ask questions in class.Overall, AI has the potential to revolutionize education by providing more personalized and effective learning experiences for students.1. What is one of the significant applications of AI in education?A. Online courses.B. Intelligent tutoring systems.C. Traditional textbooks.D. Group study.答案:B。
Net Customisation User Guide

.NET Customization User GuideAVEVA Solutions LtdDisclaimerInformation of a technical nature, and particulars of the product and its use, is given by AVEVA Solutions Ltd and its subsidiaries without warranty. AVEVA Solutions Ltd and its subsidiaries disclaim any and all warranties and conditions, expressed or implied, to the fullest extent permitted by law. Neither the author nor AVEVA Solutions Ltd, or any of its subsidiaries, shall be liable to any person or entity for any actions, claims, loss or damage arising from the use or possession of any information, particulars, or errors in this publication, or any incorrect use of the product, whatsoever.CopyrightCopyright and all other intellectual property rights in this manual and the associated software, and every part of it (including source code, object code, any data contained in it, the manual and any other documentation supplied with it) belongs to AVEVA Solutions Ltd or its subsidiaries.All other rights are reserved to AVEVA Solutions Ltd and its subsidiaries. The information contained in this document is commercially sensitive, and shall not be copied, reproduced, stored in a retrieval system, or transmitted without the prior written permission of AVEVA Solutions Ltd Where such permission is granted, it expressly requires that this Disclaimer and Copyright notice is prominently displayed at the beginning of every copy that is made.The manual and associated documentation may not be adapted, reproduced, or copied, in any material or electronic form, without the prior written permission of AVEVA Solutions Ltd. The user may also not reverse engineer, decompile, copy, or adapt the associated software. Neither the whole, nor part of the product described in this publication may be incorporated into any third-party software, product, machine, or system without the prior written permission of AVEVA Solutions Ltd, save as permitted by law. Any such unauthorised action is strictly prohibited, and may give rise to civil liabilities and criminal prosecution.The AVEVA products described in this guide are to be installed and operated strictly in accordance with the terms and conditions of the respective licence agreements, and in accordance with the relevant User Documentation. Unauthorised or unlicensed use of the product is strictly prohibited.First published September 2007© AVEVA Solutions Ltd, and its subsidiaries 2007AVEVA Solutions Ltd, High Cross, Madingley Road, Cambridge, CB3 0HB, United KingdomTrademarksAVEVA and Tribon are registered trademarks of AVEVA Solutions Ltd or its subsidiaries. Unauthorised use of the AVEVA or Tribon trademarks is strictly forbidden.AVEVA product names are trademarks or registered trademarks of AVEVA Solutions Ltd or its subsidiaries, registered in the UK, Europe and other countries (worldwide).The copyright, trade mark rights, or other intellectual property rights in any other product, its name or logo belongs to its respective owner.AVEVA .NET CustomizationContents Page.NET Customization User GuideIntroduction. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1:1 About this Guide . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:1 .NET Customization Architecture. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:1 Common Application Framework Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:2 Database Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:2 Geometry Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:3 Shared Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:3 Utilities Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:4 Graphics Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:4 Sample Code . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:4 AttributeBrowserAddin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:4 ExamplesAddin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:4 NetGridExample. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:4 PMLNetExample . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:4 PMLGridExample. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:5 Reference Documentation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:5 Compatibility with future versions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1:5How to Write an Addin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2:1 The IAddin Interface. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:1 The WindowManager. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:3 Window Creation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:3IWindow Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:4 Window Events . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:4WindowManager Events. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:5 The StatusBar. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:5Addin Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:6 Writing a Command Class . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:6 Command Events. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:9 Resource Manager. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:9 Configuring a Module to Load an Addin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2:9 Menu and Command Bar Customization . . . . . . . . . . . . . . . . . . . . .3:1 Configuring a Module to Load a UIC File. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:1 Editing the UIC File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:2 Selection of Active Customization File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:3 The Tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:4Selecting a Node in the Tree. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:5 Drag & Drop within the Tree . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:5 Node Context Menus. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:5 List of Command Tools . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:6 Selecting a Node in the List. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:6 Drag & Drop from the List to the Tree. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:6 List Context Menu. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:7 Tool Types. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:8 Sorting List via Heading . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:10 Property Grid . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:10 Action Buttons . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:12 Resource Editor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:13 Resource Editor Command Bar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:14 Using Resources for Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:16 Standalone Resource Editor. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3:16Database Interface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4:1 Data Model Definition Classes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:1 DbElementType . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:1Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:1 Constructors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:1 Methods. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:2 Related ENUMS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:2 Related Pseudo Attributes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:2 DbAttribute. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:3 Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:3 Constructors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:3 Methods. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:3 Related ENUMS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:4 DbElementTypeInstance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:4 DbAttributeInstance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:4Element access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:5 DbElement Basics. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:5 Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:5 Constructors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:5 Identity. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:5 Element Validity. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:6 Error Handling. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:6 Basic Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:6 Navigation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:7 Basic Navigation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:7 Pseudo Attributes Relating to Element Navigation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:8 Secondary Hierarchies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:8 Getting Attribute Values. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:9 Basic Mechanism . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:9 List of Valid Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:10 Qualifier. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:11 Getting an Attribute as a Formatted String . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:11 Database Modifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:11 Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:11 The Modification Pipeline . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:12 Claiming Elements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:13 Pseudo Attributes Relating to Claims . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:13 Set Attribute. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:14 Creating Element. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:14 Moving Element. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:15 Changing Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:15 Pseudo Attributes Relating to Modifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:15 Storage of Rules and Expressions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:16 Database Expressions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:16 Rules. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:17 Pseudo Attributes Relating to Rules and Expressions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:17 Comparison of Data with Earlier Sessions. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:17Filters/Iterators. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:19 Iterators. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:19 Filters. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:19Dabacon Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:19 Overview of Dabacon Tables. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:19 Table Classes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:20 DBs, MDBs and Projects. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:21 MDB Functionality . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:21 DB Functionality. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:22 Events . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:23 Overview of Events . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:23 Overview of C# Mechanism. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:23 General Capture of DB Changes. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:24Adding Pseudo Attribute Code. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:24 DB/MDB Related Events . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4:26PMLNet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5:1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:1 Design Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:1 Using PMLNet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:1Limitations. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:2 Object Names . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:3 Query Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:3 Global Method. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:4 Method Arguments . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:4 Method Overloading . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:5 Custom Attributes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:5 Private Data and Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:6 Scope. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:6 Instantiation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:7 ToString() Method. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:7 Method Names . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:7 Double Precision. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:7 Events. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:7 Error Handling. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:8 Rules for Calling .NET. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:8 Tracing. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:9 .NET Controls. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:9 Creating a Container. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:9 Hosting .NET Control . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:10 Events. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:10 Examples. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:10 PMLGridExample . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:10 PMLNetExample. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5:10The AVEVA C# Grid Control. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6:1Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6:1 Creating a C# Addin which Contains an AVEVA Grid Control. . . . . . . . . . . . . . 6:1 Providing Access to the Addin in PDMS Design or Outfitting Design . . . . . . . 6:3 Using the AVEVA Grid Control with Different Data Sources: . . . . . . . . . . . . . . 6:4 Adding an XML Menu to the Form . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6:5 Adding an Event to the Addin. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6:6 Other Functionality Available within the PDMS Environment. . . . . . . . . . . . . . 6:7 Use of the C# Grid Control with PML. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6:7 AVEVA Grid Control API . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6:7 Input Mask Characters. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6:121Introduction1.1About this GuideThis manual is designed to give a software engineer with experience of softwaredevelopment in C# using Visual Studio guidance on the development of .NET customizationfor the AVEVA PDMS and AVEVA Marine products. Customization ArchitectureThe introduction of a customization capability using Microsoft .NET technology has openedup a whole new world of customization and is particularly relevant for the integration ofAVEVA products with other customer systems. .NET API's provided access to variousaspects of the product including Graphical User Interface, Database and Geometry.As part of AVEVA's strategy of 'continual progression' the .NET customization capability hasbeen introduced in such a way that it can be used alongside the existing PML basedcustomization. Through the use of , an enhancement to PML which allows thePML programmer to call .NET code, customization which utilizes the strengths of .NETcompiled code and PML can be achieved.Figure 1: customization ArchitectureThe above diagram illustrates the two new methods of customization using .NETtechnology. The first is via the concept of a .NET Addin and the second using .Both methods provide a mechanism whereby a .NET assembly (dll) can be dynamicallyloaded into a module at runtime.1.2.1Common Application Framework InterfacesThe Common Application Framework (CAF) is an extensible framework which provides the.NET programmer with access to various services which support both applicationdevelopment and customization. The foundations of the CAF are provided by the twointerface assemblies:•Aveva.ApplicationFramework.dll•Aveva.ApplicationFramework.Presentation.dllThese interfaces provide the following major services:Namespace: Aveva.ApplicationFramework•AddinManager: This class provides properties and methods for the management of ApplicationFramework Addins.•ServiceManager: This class defines an interface which provides a means by which the various components of the ApplicationFramework can publish their services. TheServiceManager also acts as a service provider responding to requests for services. Itcan also be used by applications and application addins to publish additional services.•SettingsManager: This class provides properties and methods for the management of application settings which are stored in settings groups which are persisted betweensessions.Namespace: Aveva.ApplicationFramework.Presentation•CommandBarManager: This provides access to the menus and commandbars of a CAF based application. It also has methods to load the definition of menus andcommandbars from User Interface customization (UIC) files.•CommandManager: This class defines an interface to provide the presentation framework client with a mechanism for the management of command objects whichcan be associated with Tools or other User interface objects. The action of invoking atool (e.g clicking a ButtonTool) will cause the execution of the associated commandobject. It is possible to associated the same command object with a number of differentuser interface objects (e.g. ButtonTool on a Menu and a LinkLabel) thereby allowing forthe centralisation of these user interface objects action within a command. Variousstate-like properties of a command (e.g. enabled/checked) would also be reflected in alluser interface objects associated with a command. For example, disabling a commandwould cause all associated user interface objects to be disabled. User interface objectsare associated with a command via a CommandExecutor derived class.•ResourceManager: This class defines an interface to provide Addins with a simplified mechanism to access localizable resources.The ResourceManager provides a numberof methods which allows an addin to then access the various types of resources (string,image, cursor, icon etc.) which resource files may contain.•WindowManager: This provides access to the main application window, the StatusBar and a collection of MDI and docked windows. It also provides the addin writer withmethods to create MDI and docked windows to host user controls.1.2.2Database InterfacesThe database related interfaces are provided by the interface assemblies:•Aveva.Pdms.Database.dll & PDMSFilters.dllThis interface has the following main classes:Namespace: Aveva.Pdms.Database•DatabaseService: The sole purpose of this class is to open a project.。
精选新版2020年安全专业考试复习题库588题(含答案)

2020年安全专业考试复习题库588题【含答案】一、选择题1.3、下面对于WindowsDNS日志功能的说法,其中错误的是:A、对于DNS服务启动、停止的事件,将记录在windowseventlog日志中B、通过日志功能可以记录的事件包括:区域更新、查询、动态更新等C、通过设定自动定期删除,可以防止日志文件过大D、日志文件缺省存放在系统盘上,应将日志文件存放到非系统盘,以防止将系统盘占满参考答案:C2.16.在安装IIS时就应充分考虑安全性,以下哪些措施能在安装过程中加强IIS安全性:()a)不要将IIS安装在系统分区上b)修改IIS的安装默认路径c)安装windows的最新补丁d)安装IIS的最新补丁参考答案:abcd3.18职责分离的主要目的是?A.不允许任何一个人可以从头到尾整个控制某一交易或者活动;B.不同部门的雇员不可以在一起工作;C.对于所有的资源都必须有保护措施;D.对于所有的设备都必须有操作控制措施。
参考答案:A4.15.SQLSERVER的默认DBA账号是什么?A、administratorB、saC、rootD、SYSTEM参考答案:B5.12.FINGER服务使用哪个TCP端口?A.69B.119C.79D.70参考答案:C6.11.LINUX中,什么命令可以控制口令的存活时间?A.chageB.passwdC.chmodD.umask参考答案:A7.10.UNIX中,可以使用下面哪一个代替Telnet,因为它能完成同样的事情并且更安全?A.S-TELNETB.SSHC.FTPD.RLOGON参考答案:B8.6.Kerberos提供的最重要的安全服务是?A.鉴别B.机密性C.完整性D.可用性参考答案:A9.3.某种防火墙的缺点是没有办法从非常细微之处来分析数据包,但它的优点是非常快,这种防火墙是以下的哪一种?A.电路级网关B.应用级网关C.会话层防火墙D.包过滤防火墙参考答案:D10.2.一般的防火墙不能实现以下哪项功能?A.隔离公司网络和不可信的网络B.防止病毒和特络依木马程序C.隔离内网D.访问控制参考答案:B11.21.windowsterminalserver使用的端口是:A.1433B.5800C.5900D.3389参考答案:D12.6、相对于BIND,WindowsDNS存在很多的不足,处在一个被取代的趋势,下面说法正确的是:A、在认证、加密、访问控制上存在缺陷B、windows代码不公开,不像BIND经过严格测试评估C、在软件开发上,BIND投入很大,对DNS这个领域的发展有很大的影响D、BIND有很高的使用率参考答案:ABCD13.27.僵尸网络有哪些组成A、僵尸程序B、僵尸计算机C、命令控制中心D、ISP参考答案:ABC14.2、在对WindowsDNS访问控制时,可以采用的安全措施是:A、限定允许区域复制的服务器IP,防止区域信息被获取B、配置允许递归查询的IP地址列表C、如果DNS服务器有多个IP时,DNS服务只绑定在某个本地IP地址上D、以上都不正确参考答案:AC15.7、下面对于IIS的wwwroot目录的权限配置,说法正确的是:A、一个目录在操作系统上被分配的权限与在IIS中的被分配的权限无关B、如果wwwroot目录下存在脚本,则必须打开脚本资源访问权限C、如果打开了目录浏览权限,如果缺省网页不存在(index.html)时,客户端就可以直接浏览到wwwroot目录的目录结构D、此目录必须具备读取权限,否则通过ie就不能访问到此站点参考答案:CD16.5、对于IIS的安全,下面说法正确的是:A、asp等cgi脚本会带来很多安全隐患,在有些情况下,用静态网页可以很好的保证web 的安全性B、如果web程序没有对输入进行严格限制,将可能会给web安全造成很大威胁C、SQL注入攻击,与IIS没有关系,是利用SQL的安全漏洞D、通过对连接数目、连接超时的配置,可以减弱synflood、cc等对网站DoS攻击的影响参考答案:ABD17.2、对于缺省安装的IIS,有些文件和目录的存在可能会引入安全隐患,所以在安全配置时,应将它们清除。
DC常用命令及脚本

利用DC进行综合设计(2012-03-25 17:45:10)转载▼标签:dc综合杂谈DC的综合术语用于设计的ASIC的EDA工具往往是一套很复杂的软件,包括大量的工具和文档。
同时,每个公司都有自己的一套术...一、预备知识1.1、DC的综合术语用于设计的ASIC的EDA工具往往是一套很复杂的软件,包括大量的工具和文档。
同时,每个公司都有自己的一套术语。
只有理解了这些术语的含义才能很好的掌握这些工艺。
1 设计和设计对象设计是实现一定逻辑功能的电路的描述。
设计对象就是在设计中被DC命令、属性和约束操作或控制的对象。
常用的设计中包括元件、网络、端口、引脚和时钟。
另外,一个设计可能包括某个相同子设计或库元件的多个例化。
这时候被例化的设计或库元件称作参考。
在一个设计中查找某个对象的命令:find,这是在DC命令中很常用的命令。
如:列出当前设计的所有端口(ports):Dc_shell>findport OR find(port,”*”)列出所有包含”DW”字母的元件:dc_shell>find (cell,”*DW*”)列出cba_core库中的AN2门的所有接脚:dc_shell>find(pin,cba_core/AN2Read –format vhdl ./src/rtl/timer_tugw.vhdRead –format vhdl ./src/rtl/test_top.vhdCheck_error –vIf(dc_shell_status= =1){exit 1}Current_design test_topLinkCheck_error –vIf(dc_shell_status= =1){exit 1}Include pass0/constraint/test_top.conCheck_error –vIf(dc_shell_status= =1){exit 1}Set_max_area 0.0000Set_flatten falseEcho”***doing full compile for the partition ‘test_top’***”Sh date;Compile –map_effort mediumCheck_error –vIf(dc_shell_status= =1){exit 1}Sh date;Check_designCompile_top_acs_partion=tureCompile_top_all_paths=trueEcho”***doing boundary compile for the partition ‘test_top’***”Sh date;Compile –topUniquifyCheck_error –vIf(dc_shell_status= =1){exit 1}Sh date;Current_design test_topWrite –format db –hierarchy –output pass0/db/test_top.dbWrite –format verilog –hierarchy –output pass0/db/test_top.vWrite –format vhdl –hierarchy –output pass0/db/test_top.vhdReport_timing> pass0/report/test_top.timReport_area> pass0/report/test_top.areaReport_constraints> pass0/report/test_top.cstrReport_qor> pass0/report/test_top.qorReport_constraints–all_violators–verbose>pass0/report/test_top.vioquit脚本文件可以使用任何一个文本编辑工具产生或修改,也可以在dc_shell中执行write_scirpt 命令产生。
Adobe Acrobat SDK 开发者指南说明书

This guide is governed by the Adobe Acrobat SDK License Agreement and may be used or copied only in accordance with the terms of this agreement. Except as permitted by any such agreement, no part of this guide may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of Adobe. Please note that the content in this guide is protected under copyright law.
地下水模拟软件GMS中文使用手册

2.1.1 纲要....................................................................................................................................... 17
2.2 开始.............................................................................................................................................. 18 2.3 属性对象...................................................................................................................................... 18
1.12.1 创建概念模型..................................................................................................................... 13 1.12.2 根据 GIS 数据作图............................................................................................................. 13
2.4 结论.............................................................................................................................................. 24 25 3 MODFLOW—概念模型法................................................................................................................ ................................................................................................................25 3.1 简介.............................................................................................................................................. 26
Schurter PG05连接器与IEC家用插座C14或C18说明书
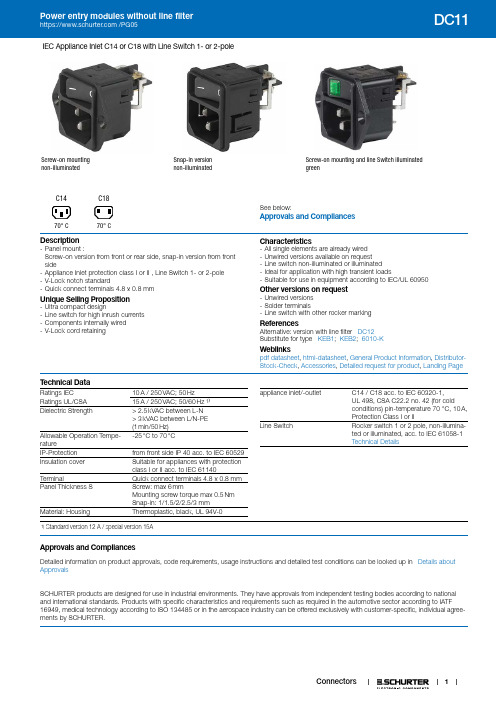
1IEC Appliance Inlet C14 or C18 with Line Switch 1- or 2-poleScrew-on mountingnon-illuminated Snap-in versionnon-illuminated Screw-on mounting and line Switch illuminated greenSee below:Approvals and CompliancesC14 70° CC1870° CDescription- Panel mount :Screw-on version from front or rear side, snap-in version from front side- Appliance Inlet protection class I or II , Line Switch 1- or 2-pole - V-Lock notch standard- Quick connect terminals 4.8 x 0.8 mmUnique Selling Proposition- Ultra compact design- Line switch for high inrush currents - Components internally wired - V-Lock cord retainingCharacteristics- All single elements are already wired - Unwired versions available on request - Line switch non-illuminated or illuminated - Ideal for application with high transient loads- Suitable for use in equipment according to IEC/UL 60950Other versions on request- Unwired versions - Solder terminals- Line switch with other rocker markingReferences Alternative: version with line filter DC12 Substitute for type KEB1; KEB2; 6010-KWeblinkspdf datasheet , html-datasheet , General Product Information , Distributor-Stock-Check , Accessories , Detailed request for product , Landing PageT echnical DataRatings IEC10 A / 250 VAC; 50 HzRatings UL/CSA 15 A / 250 VAC; 50/60 Hz ¹⁾Dielectric Strength> 2.5 kVAC between L-N > 3 kVAC between L/N-PE (1 min/50 Hz)Allowable Operation Tempe-rature-25 °C to 70 °CIP-Protection from front side IP 40 acc. to IEC 60529Insulation cover Suitable for appliances with protection class I or II acc. to IEC 61140TerminalQuick connect terminals 4.8 x 0.8 mm Panel Thickness SScrew: max 6 mmMounting screw torque max 0.5 Nm Snap-in: 1/1.5/2/2.5/3 mm Material: HousingThermoplastic, black, UL 94V-0appliance inlet/-outletC14 / C18 acc. to IEC 60320-1, UL 498, CSA C22.2 no. 42 (for cold conditions) pin-temperature 70 °C, 10 A, Protection Class I or IILine SwitchRocker switch 1 or 2 pole, non-illumina-ted or illuminated, acc. to IEC 61058-1 Technical Details1) Standard version 12 A / special version 15AApprovals and CompliancesDetailed information on product approvals, code requirements, usage instructions and detailed test conditions can be looked up in Details about ApprovalsSCHURTER products are designed for use in industrial environments. They have approvals from independent testing bodies according to national and international standards. Products with specific characteristics and requirements such as required in the automotive sector according to IATF 16949, medical technology according to ISO 134485 or in the aerospace industry can be offered exclusively with customer-specific, individual agree-ments by SCHURTER.ApprovalsThe approval mark is used by the testing authorities to certify compliance with the safety requirements placed on electronic products. Approval Reference T ype: DC11Approval Logo Certificates Certification Body DescriptionVDE Approvals VDE Certificate Number: 40007009UL Approvals ULUL File Number: E96454CQC Approvals CQC CCC Certificate Number: 2013010204594013 Product standardsProduct standards that are referencedOrganization Design StandardDescriptionDesigned according to IEC 60320-1Appliance couplers for household and similar general purposesDesigned according to IEC 61058-1Switches for appliances. Part 1. General requirementsDesigned according to UL 498Standard for Attachment Plugs and ReceptaclesDesigned according to CSA C22.2 no. 42General Use Receptacles, Attachment Plugs, and Similar Wiring Devices Application standardsApplication standards where the product can be usedOrganization Design StandardDescriptionDesigned for applications acc.IEC/UL 60950IEC 60950-1 includes the basic requirements for the safety of informationtechnology equipment.Designed for applications acc.IEC 60335-1Safety of electrical appliances for household and similar purposes. Meetsthe requirements for appliances in unattended use. This includes the en-hanced requirements of glow wire tests acc. to IEC 60695-2-12 and -13. CompliancesThe product complies with following Guide LinesIdentification Details Initiator DescriptionCE declaration of conformity SCHURTER AG The CE marking declares that the product complies with the applicablerequirements laid down in the harmonisation of Community legislation onits affixing in accordance with EU Regulation 765/2008.RoHS SCHURTER AG EU Directive RoHS 2011/65/EUChina RoHS SCHURTER AG The law SJ / T 11363-2006 (China RoHS) has been in force since 1 March2007. It is similar to the EU directive RoHS.REACH SCHURTER AG On 1 June 2007, Regulation (EC) No 1907/2006 on the Registration,Evaluation, Authorization and Restriction of Chemicals 1 (abbreviated as"REACH") entered into force.SCHURTER AG V-Lock system are based on a matching plug-dose combination. Theconnector is equipped with a notch intended for use with the latchingcordset. The cord latching system prevents against accidental removal ofthe cordset.White paper Glow wire test SCHURTER AG Meets the requirements of IEC 60335-1 for appliances in unattended use.This includes the enhanced requirements of glow wire tests acc. to IEC60695-2-12 and -13.23Dimensions [mm]Screw-on mounting1)2)1) 1-pol non-illuminated2) 2-pol illuminated, 2-pol non-illuminatedSnap-in mounting1)2)1) 1-pol non-illuminated2) 2-pol illuminated, 2-pol non-illuminated4DiagramsLine switch non-illuminated 2-poleL PE 1)21PE'2)1) Line 2) Load Line switch illuminated 2-pole21L PE 2)1)1) Line 2) LoadLine switch non-illuminated 1-pole1)21PE'2)1) Line 2) LoadAll VariantsPackaging unit 50 PcsAccessoriesDescriptionWire HarnessWire harness for SCHURTER productsAssorted CoversRear Cover0859.00474311.9403Cord retaining kitsCord retaining strain reliefFlat head, A4700.0001Countersunk, B4700.0002Mating Outlets/ConnectorsCategory / DescriptionAppliance Outlet Overview completeIEC Appliance Outlet F, Screw-on Mounting, Front Side, Solder Terminal4787IEC Appliance Outlet F, Snap-in Mounting, Front Side, Solder or Quick-connect Terminal4788IEC Appliance Outlet F or H, Screw-on Mounting, Front Side, Solder, PCB or Quick-connect Terminal5091Appliance Outlet further types to DC11Connector Overview complete4782 Mounting: Power Cord, 3 x 1 mm² / 3 x 18 AWG, Cable, Connector: IEC C1347824785 Mounting: Power Cord, 3 x 1 mm² / 3 x 18 AWG, Cable, Connector: IEC C1347854300-06 Mounting: Power Cord, 3 x 1 mm² / 3 x 18 AWG, Cable, Connector: IEC C134300-06IEC Connector C15 for hot conditions 120°C, Rewireable, Straight4781IEC Connector C15 for hot conditions 120°C, Rewireable, Angled4784Connector further types to DC11...Power Supply Cord Overview completeCord Sets 10 A, Europlug, 2.5 m, Connector IEC C13, H05VV-F3G1.0, black6004.0215Cord Sets 10 A, Europlug, 2.5 m, Connector IEC C13, H05VV-F3G1.0, black6003.0215Power Supply Cord further types to DC1156Mating Outlets/Connectors shutteredPower Cord Overview completeVAC13KS, Overview, V-Lock cord retaining, diverse Connector IEC C13, diverse, black VAC13KS Power cord with IEC connector C17, V-Lock, straight VAC17KSPower Cord further types to DC11The specifications, descriptions and illustrations indicated in this document are based on currentinformation. All content is subject to modifications and amendments. Information furnished is believed 18.12.2018。
(Linyuan)Link prediction in complex networks-A survey

Author's personal copy
Physica A 390 (2011) 1150–1170
Contents lists available at ScienceDirect
Physica A
journal homepage: /locate/physa
Article history: Received 5 October 2010 Received in revised form 10 November 2010 Available online 2 December 2010 Keywords: Link prediction Complex networks Node similarity Maximum likelihood methods Probabilistic models
article
info
abstract
Link prediction in complex networks has attracted increasing attention from both physical and computer science communities. The algorithms can be used to extract missing information, identify spurious interactions, evaluate network evolving mechanisms, and so on. This article summaries recent progress about link prediction algorithms, emphasizing on the contributions from physical perspectives and approaches, such as the random-walkbased methods and the maximum likelihood methods. We also introduce three typical applications: reconstruction of networks, evaluation of network evolving mechanism and classification of partially labeled networks. Finally, we introduce some applications and outline future challenges of link prediction algorithms. © 2010 Elsevier B.V. All rights reserved.
Design Guides for Plastics

Special features
Assembly
Special techniques
Extrusion ............................................................................................. Blow moulding....................................................................................
22. 23. Design for extrusion blow moulding ...........................................Planned Design for thermoforming ...........................................................Planned
Typeset by Tangram Technology Ltd.
Contents
Preface............................................................................................... 1 Introduction ...................................................................................... 2 Injection moulding ........................................................................... 4
聚合物水泥基防水装饰一体化涂料

目次1 总则 (1)2 术语 (2)3 材料要求 (3)4 设计 (4)4.1 一般规定 (4)4.2 基本构造 (4)4.3 节点构造 (5)5 施工 (8)5.1 一般规定 (8)5.2 施工准备 (8)5.3 施工工艺 (9)5.4 成品保护 (11)6 验收 (12)本规程用词说明 (14)引用标准名录.................................. 错误!未定义书签。
条文说明.. (15)Contents1 General provisions (1)2 Terms (2)3 Materials requirements (3)4 Design (5)4.1 General requirements (5)4.2 Material selection design (6)4.3 Structural design (7)5 Construction (8)5.1 General requirements (8)5.2 Base Preparations (9)5.3 Construction technology (9)5.4 Product Protection (9)6 Acceptance (14)Explanation of wording in this specification (23)List of quoted standards (24)Addition: Explanation of provisions1总则1.0.1为推广聚合物水泥防水装饰涂料的工程应用,做到技术先进、安全适用、经济合理、提高工程质量,制定本规程。
1.0.2本规程适用于聚合物水泥防水装饰涂料工程应用的材料选用、设计、施工及验收。
1.0.3聚合物水泥防水装饰涂料的工程应用除应执行本规程外,尚应符合国家现行有关标准的规定。
2术语2.0.1聚合物水泥防水装饰涂料polymer-modified cementitious coating for waterproofing and decoration以聚合物、水泥、细骨料为主要组份,掺入颜料和添加剂,按适当配比混合制成,具有防水和装饰功能的涂料。
baymax patch tools 原理 -回复

baymax patch tools 原理-回复Baymax Patch Tools(Baymax补丁工具)是一种用于修复计算机中软件和操作系统的漏洞的工具。
它采用图形用户界面(GUI)和命令行接口(CLI)的形式供用户使用。
Baymax Patch Tools主要由以下几个部分组成:扫描模块、修复模块、更新模块和日志模块。
在本文中,我们将一步一步地回答关于Baymax Patch Tools原理的问题。
1. Baymax Patch Tools是如何扫描漏洞的?Baymax Patch Tools通过读取操作系统和软件的配置文件以及相关的数据库进行扫描。
用户可以在GUI或CLI中选择需要扫描的范围,如整个操作系统或特定的软件。
扫描模块通过比对所读取的信息与已知的漏洞数据库中的记录,来确定计算机中存在的漏洞。
2. Baymax Patch Tools是如何修复漏洞的?修复模块是Baymax Patch Tools中的核心组件,它会根据扫描模块的结果,提供相应的修复措施。
这些修复措施可能包括安装补丁程序、更新软件版本、关闭不必要的服务或修改配置文件。
Baymax Patch Tools可以自动执行修复操作,也可以提供手动修复的指南。
3. Baymax Patch Tools是如何更新漏洞数据库的?为了保持与最新漏洞信息的同步,Baymax Patch Tools具有更新模块。
该模块定期连接到漏洞数据库服务器,下载最新的漏洞信息。
漏洞数据库可以由Baymax Patch Tools开发者维护,也可以从其他可靠的来源获取,以确保准确性和及时性。
4. Baymax Patch Tools如何记录修复的过程和结果?Baymax Patch Tools使用日志模块来记录扫描和修复的过程、结果和相关信息。
用户可以查看日志文件获取详细的操作记录,以便跟踪修复的结果和发现潜在问题。
日志文件通常保存在计算机的特定目录中,用户可以随时访问。
highlight_entities的使用方法

highlight_entities的使用方法全文共四篇示例,供读者参考第一篇示例:highlight_entities是一种在自然语言处理中常用的技术,用于识别和突出显示文本中的实体,例如人物、地点、组织等。
在信息抽取、语义分析和搜索引擎等应用中,highlight_entities可以帮助用户快速识别关键信息和重要实体,提高信息检索和浏览的效率。
本文将介绍highlight_entities的使用方法,并结合实际案例,详细说明该技术的原理和实现步骤。
1. 数据准备:首先需要准备待处理的文本数据,可以是一篇文章、一段对话或一个网页内容。
数据的质量和完整性对highlight_entities 的效果和准确性有重要影响,因此在数据准备阶段需尽量保证文本的完整性和准确性。
2. 实体标注:根据文本处理的需求和实际情况,定义需要标注和识别的实体类型,如人名、地名、机构名等。
可以利用已有的实体标注工具或通过自定义标注规则,对文本中的关键词和短语进行标注,并映射到对应的实体类型。
3. highlight_entities处理:利用highlight_entities工具或库对标注好的文本进行实体突出显示处理。
根据实体类型和标注信息,对文本中的关键词进行高亮显示或下划线标记,突出显示实体的位置和重要性。
可以根据需求定制不同的显示效果和样式,提高用户体验和可读性。
4. 实体关联:在highlight_entities处理的过程中,可以进一步分析实体之间的关联性和语义关系,对实体进行归类和聚类。
通过识别实体之间的关系,可以更深入地挖掘文本的含义和价值,为后续的信息抽取和语义分析提供参考和支持。
5. 结果展示:最后将处理好的文本结果展示给用户或应用程序。
用户可以根据实体标注和高亮显示的信息,快速了解文本内容和重点信息;应用程序可以根据实体识别和关联分析的结果,进一步处理和挖掘文本的语义信息,实现智能化的信息抽取和搜索功能。
Java学习之分词工具之HanLP介绍

Java学习之分词⼯具之HanLP介绍HanLP 是由⼀系列模型和算法组成的Java⼯具包。
⽬标是普及⾃然语⾔处理在⽣产环境中的应⽤。
它不仅是分词,还提供了词法分析、句法分析、语义理解等完整的功能。
HanLP 具有功能齐全、性能⾼效、结构清晰、语料最新、功能可定制等特点。
HanLP 是完全开源的,包括字典。
不依赖其他jar,底层使⽤了⼀系列⾼速数据结构,如双数组Trie树、DAWG、AhoCorasickDoubleArrayTrie等,这些基础组件都是开源的。
通过⼯具类HanLP,可以⼀句话调⽤所有函数,⽂档详细,开箱即⽤。
底层算法经过精⼼优化,极速分词模式下每秒可达2000万字,内存仅需要120MB。
IO⽅⾯,字典加载速度极快,快速启动仅需500msPOM⽂件<project xmlns="/POM/4.0.0" xmlns:xsi="/2001/XMLSchema-instance"xsi:schemaLocation="/POM/4.0.0 /xsd/maven-4.0.0.xsd"><modelVersion>4.0.0</modelVersion><groupId>com.iqilu</groupId><artifactId>Segment</artifactId><version>1.0-SNAPSHOT</version><packaging>jar</packaging><name>Hello</name><url></url><properties><project.build.sourceEncoding>UTF-8</project.build.sourceEncoding></properties><dependencies><dependency><groupId>junit</groupId><artifactId>junit</artifactId><version>3.8.1</version><scope>test</scope></dependency><dependency><groupId>com.hankcs</groupId><artifactId>hanlp</artifactId><version>portable-1.3.2</version></dependency></dependencies></project>DemoSegment.javapackage com.iqilu;import com.hankcs.hanlp.HanLP;import mon.Term;import java.util.List;public class DemoSegment {public static void main(String[] args) {String[] testCase = new String[]{"Goods and services","Married and unmarried are indeed interfering with participles","Buy fruits and then come to the Expo and die at the Expo","China's capital is Beijing","Welcome the new teacher to come to dinner","The virgin officer of the industry and information technology must personally explain the installation of technical devices such as 24 switches through the subordinate departments every month", "With the rise of web games, the current web games are prosperous and rely on archives. The design for logical judgment is reduced, but this one cannot be completely ignored.",};for (String sentence : testCase){List<Term> termList = HanLP.segment(sentence);System.out.println(termList);}}}结果[Products/n, and/c, services/vn][Married/v, of/uj, and/c, not yet/d, married/v, of/uj, indeed/ad, at/p, interference/v, participle/n, ah/y][Buy/v, fruit/n, then/c, come/v, Expo/j, finally/f, go/v, Expo/j][China/ns, of/uj, capital/n, yes/v, Beijing/ns][Welcome/v, new/a, teacher/n, before death/t, come/v, dinner/v][Industry and Information Office/n, female/b, secretary/n, monthly/r, passing/p, subordinate/v, department/n, all/nr, personally/d,Explain/v, 24/m, port/q, switch/n, etc/u, technical/n, device/n, of/uj, installation/v, work/vn][With/p, page/q, youxing/n, from/v, to/v, now/t, of/uj, page tour/nz, flourishing/an,,/w,Depend on/v, archive/vn, proceed/v, logic/n, judge/v, of/uj, design/vn, reduce/v, up/ul,,/w,But/c, this piece of/r, also/d, cannot/v, completely/ad, ignore/v, drop/v,./w]Java分词⼯具只是众多的Java开发⼯具之⼀,以后⼤家还会接触到更多相关知识。
additional analysis properties -回复

additional analysis properties -回复additional analysis properties是指额外的分析属性或特性,用于进一步深入分析问题或数据。
在数据分析领域,这些属性可以帮助我们更好地了解数据、发现潜在的关联性,并作出优化决策。
本文将一步一步回答与additional analysis properties相关的问题,并对其重要性和应用进行探讨。
一、什么是additional analysis properties?additional analysis properties是指在进行数据分析时使用的额外属性或特性。
这些属性可以是数据的维度、度量或标签,用于进一步探索数据的内部结构和关系。
通过使用additional analysis properties,我们可以更加全面和准确地理解数据,并从中发现更多隐藏的信息和模式。
例如,在销售数据分析中,我们可以使用additional analysis properties来描述产品的特性(如颜色、尺寸、品牌等),以及顾客的属性(如性别、年龄、地区等)。
通过将这些属性纳入数据分析中,我们可以更好地了解产品的销售趋势、顾客的购买偏好,并作出更有针对性的市场策略。
二、additional analysis properties的重要性是什么?1. 帮助我们理解数据的层次结构:通过使用additional analysis properties,我们可以将数据划分为不同的层次或维度,并更好地理解数据之间的关系。
这有助于我们发现数据中的层级关系,而不仅仅停留在整体上的统计数据。
2. 暴露数据中的规律和模式:通过对additional analysis properties的分析,我们可以更好地发现数据中的规律和模式。
例如,在销售数据中,将产品的特性作为additional analysis properties,我们可以发现某些特定类型的产品在某个季节或地区有更高的销售量。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Replicated Web Objects:Design and ImplementationIhor Kuz,Anne-Marie Kermarrec,Maarten van Steen,Henk J.SipsDelft University of Technology,Delft,the NetherlandsIRISA,Rennes Cedex,FranceVrije Universiteit,Amsterdam,the Netherlandsi.kuz@cs.tudelft.nl,Anne-Marie.Kermarrec@irisa.fr,steen@cs.vu.nl,h.j.sips@cs.tudelft.nlKeywords:distributed systems,object replication,object coherence,World-Wide Web,worldwide scalable sys-temsAbstractThe Web currently suffers from a number of scala-bility problems.While general caching techniques can be used to help some,the vast number of differ-ent resources now available requires an alternative ap-proach.In particular,we need to develop resource-specific strategies.Such an approach is not supported in the current Web infrastructure.Also,the current Web is limited inflexibility with regards to integration of new resources and services.This is partly caused by the rigid nature of the HTTP protocol.We introduce Web objects as a way to address these problems.Web objects are worldwide scalable dis-tributed shared objects that represent Web resources. Each such object provides at least a common interface and encapsulates and implements its own distribution policy.In this paper we concentrate on the design of these Web objects as well as their implementation in Java.1IntroductionAs the Web gains popularity,scalability problems are becoming more and more apparent,the largest of these being the problem of performance.Web servers are often unreachable due to an overload of requests for pages.Likewise,we are faced with long downloading times caused by bandwidth limitations and unreliable links combined with a growing number of users and steadily increasing size of resources such as images, audio,and video.Traditional scaling techniques,such as caching and replication[13],have been applied as solutions to these problems.Unfortunately,inherent to these tech-niques are consistency problems;modifications to one copy of a cached or replicated Web page makes that copy different from all the others.Currently,a sim-ple consistency protocol is used for caches and there is no standardized protocol for replicas.Neither of these are optimal situations so new schemes are being de-veloped and researched.The drawback to most proposed solutions is that they generally assume that a single consistency model is required and that this model is appropriate for all re-sources.With the large variety of Web pages already existing,and the increasing alternative applications of Web technology,it is clear that such a one-size-fits-all approach will eventually fail.Instead,different poli-cies that take Web usage into account will need to co-exist in order for caching and replication to be effec-tive.As an example,caching or replicating a seldom-accessed home page will hardly be effective,whereas for a popular page it might be.As far as different consistency models are concerned,consider a popular Web page that is maintained concurrently by several people at different sites.Such a page would best be physically distr ibuted across those sites.At the same time,its readers may want updates to be immediately pushed to their respective local copies.As a last ex-ample,an online magazine,would most likely benefit from a master/slave strategy by which a master copy is pushed to mirror sites,but where clients pull in copies from those mirrors on demand.Another problem faced by the Web is its limited flexibility with regards to the introduction of new re-sources and services.Although nonstandard resources have been integrated into the Web,the means by which this is done usually requires a unique solution for each new type of resource.Creating such solutions is not always an easy task,and it is rarely elegant.In order to address these problems we introduce Web objects:an object-based infrastructure for the Web.Web objects are distributed objects that repre-sent Web resources.A Web object encapsulates not only the functionality of the Web resource but also the implementations of policies for replicating and dis-tributing the resource.By encapsulating all Web re-sources in Web objects we can provide a standard interface to these resources,allowing new resources to easily be integrated into the Web.Because each Web object implements its own distribution policy, the caching and replication policies can be devised on a per-object basis.This approach opens the way to-wards worldwide scalability as we can now take dis-tribution requirements and possibilities of individual resources into account.In this paper we concentrate on the design of Web objects,as well as its prototype implementation in Java.Our main contribution is that we show how ex-isting Web technology can be deployed to construct better solutions to scalability problems.In addition, we introduce a novel distributed-object model that can be applied to more than just the World-Wide Web.The paper is organized as follows.In Section2 we present our notion of Web objects,concentrating on functional issues rather than distribution aspects. The latter are discussed in Section3.In Section4we present a Java implementation of Web objects and its interface to existing Web browsers.Related work is discussed in Section5.2Web ObjectsAs mentioned above,scalability of the World-Wide Web can be solved only by taking the distribution re-quirements of individual pages into account.Instead of considering only Web pages,our starting point is formed by what we call Web objects.In our model, a Web object represents any kind of resource that can be accessed through the World-Wide Web.Examples of such resources include HTMLfiles,files containing images,CGI scripts,applets,etc.At present,these re-sources can usually be natively handled by browsers and servers.However,we expect new resources to evolve as well.For example,applications are emerg-ing that allow users to make reservations for theaters, hotels,etc.Also,collaborative applications such as shared whiteboards are becoming increasingly avail-able through the Web.Most browsers and servers do not have the capabilities to directly deal with these new resources.Web objects can encapsulate any kind of resource. However,it is necessary that applications can access every kind of Web object in a standard way.The ap-proach we follow is to define interfaces for Web ob-jects.An interface consists of a set of methods offered by a Web object.In this section,we concentrate on what interfaces Web objects offer to their clients,ig-noring distribution aspects and concentrating only on functionality.2.1Common Web Object Interface The success of the Web is partly due to the fact that many different kinds of resources can be transferred and presented to clients in a uniform way.Web objects are no different in this respect.In particular,there is a common(Web object)interface that is offered by each Web object,as shown in Figure1.Method MeaningPut Change the content of the Web objectby writing data in the Web object’s na-tive format to itGet Get the content of the Web object in itsnative formatSize Return the size(in number of bytes)ofthe Web object’s contentGet HTML Get the content of the Web object inHTML format that can be interpreted bya browserHTML Size Return the size(in number of bytes)of the Web object’s content when it isviewed as an HTMLfileClear Clear the content of the Web object Figure1:The common interface that is implemented by each Web object.The common Web object interface includes meth-ods for reading,writing,and clearing the content of the Web object.Each type of Web resource has a spe-cific format for representing its content.For exam-ple,an image will usually be represented as binary data(a pixmap,GIFfile,etc.),whereas a textfile or a Postscriptfile will be represented as plain ASCII text. We call this format a resource’s native format.The Get and Put methods allow a Web object’s content to be retrieved or set in this format.We also offer a method (Get HTML)to acquire an HTML representation of the Web object.For an image or Postscript Web object this might be a simple description of the actual con-tents,whereas for plain text this might be the text en-hanced with some HTML tags.The Web object itself is ultimately responsible for deciding how to represent its content in HTML.2.2Common Management Interface Each Web object has at least three attributes associated with it:one that tells when the Web object’s state was last modified,a resource type,and a name.The com-mon(Web object)management interface,shown in Figure2,contains the methods that are used to read and write these attributes.The management interface can be extended for dif-ferent classes of Web objects.For example,Web ob-jects providing persistent state offer additional meth-ods for storing and retrieving state.Method MeaningLastMod Returns the time the Web object waslast modifiedSetType Sets the type of resource this Web ob-ject representsGetType Returns the type of resource the Webobject representsSetName Associates a name(string)with the WebobjectGetName Returns the Web object’s associatednameFigure2:Methods in the common management interface of each Web object.2.3Object-specific InterfacesBesides the common interfaces,Web objects can have one or more specific interfaces depending on the type of resource they represent.To give an impression of what an object-specific interface would look like,con-sider a Web object representing a general Web page. Such a Web page object includes the HTML code, any inline images,sounds,films,applets,etc.When using a Web page object a client may want to access the Web page object’s entire state(i.e.,all the resources contained in it),or it might want to ac-cess only certain parts of it.For example,a Web browser needs to access each of the resources individ-ually,whereas a client copying the Web page object to another location would prefer to access the whole state at once.As such,the interface provided by a Web page ob-ject has methods which allow each of the resources to be accessed separately.There are,for example,meth-ods which allow clients to access the HTML text of the page,to add images,to get a list of all images,etc. Reading or modifying the entire state of the Web page object can be done through its common Web object in-terface,which we showed in Figure1A Web page object provides persistent state,lead-ing to an extension of the management interface with a Store and ReadFrom method.In our prototype im-plementation,the entire state of a Web page object is stored in an archivefile local to the client.3Web Objects and Distribu-tionSo far,we have concentrated only on the functionality of Web objects and have ignored distribution issues. Ideally,a client is not aware of the distributed nature of a Web object.For example,it should be transparent where the Web object resides,whether it is replicated, or that it can migrate between locations.3.1Remote Method InvocationAn approach currently followed by most object-based distributed systems is to allow clients transparent ac-cess to an object through remote method invocations. In such cases,a proxy is installed at the client that of-fers the same interface as the actual object.When a client invokes a method,the proxy sends a message to the object’s current location containing the iden-tification of the method and its marshalled parame-ters.A server process is responsible for unpacking the message,invoking the method,and sending a reply message containing the method’s return values back to the proxy.The proxy subsequently unpacks the reply message and passes the results of the method invoca-tion to the client.Remote method invocation basically deploys the same technique as RPCs[2],and has recently been in-troduced in Java[20].Combined with object serializa-tion,it forms a powerful technique for transparently invoking remote objects,even in the face of object mi-gration and persistence,as demonstrated by the V oy-ager toolkit[14].However,remote method invocations alone are not enough to handle complex distribution issues such as caching and replication.Moreover,the requirements for distribution are highly dependent on the nature of the object as we discussed in the introduction.In other words,distribution policies for Web objects are ob-ject specific.However,we should take care not to mix the implementation of the functionality of a Web ob-ject,with the implementation of its distribution policy. In particular,it should be possible to change a Web object’s distribution policy without affecting what the Web object does.3.2Separating ConcernsWe adopt an approach by which a Web object is parti-tioned into several subobjects,as shown in Figure3.In this approach,the semantics of the Web object is represented by a semantics object.A semantics ob-ject is a user-defined object that contains an implemen-tation of the functionality of the Web object.In prac-tice,the semantics object is constructed from primi-tive objects and facilities offered by a programming language such as Java or C++.For example,the se-mantics object of a Web page object may consist of several Java objects,each one implementing part of the actual Web page.As such,we could have a Java object encapsulating the page’s text body as HTML code,another Java object implementing an applet,and yet another one offering facilities for displaying an im-age.The important issue is that the semantics object is constructed without considering distribution aspects. The latter are handled by the replication and commu-nication object.Figure3:The organization of a(local)Web object.The function of the replication object is to handle replication and caching of the state of the Web object, as represented by the semantics object.In our model, the semantics object may be copied to multiple ma-chines.It is the responsibility of the replication object to keep these copies consistent.Exactly which con-sistency protocol is used depends on the Web object. We do not enforce a general distribution policy for all Web objects.Although distribution policies may dif-fer between Web objects,replication objects all have the same interface,which is shown in Figure4.Method MeaningStart Called to start an invocation on the se-mantics objectSend Send marshalled parameters to the otherreplicasFinish Called when the invocation hasfinished Figure4:The basic methods provided by the replication ob-ject to support active replication.Basically,each replication object need merely pro-vide three methods.When a client wants to invoke a method at the semantics object,itfirst requires permis-sion from the replication object.The Start method is used for this purpose.Invocation of Start allows the replication object to globally order the invocation re-quest,and if necessary,acquire locks and such.After Start has returned,the client is,in principle,allowed to do the local invocation at the semantics object.The invocation requested by the client is forwarded to the other replicas by invoking Send.The parameters of the semantics object’s method are marshalled,and to-gether with an identifier of that method are passed to Send.This is similar to dynamic invocation mech-anisms as supported by,for example,CORBA[15]. Once all is done,the caller invokes Finish allowing the replication object to synchronize the replicas,and pos-sibly releasing locks as well.Further details can be found in[9]This approach strongly resembles meta-level pro-tocols as used in reflective object-oriented program-ming[11].The replication object provides a standard interface to handle active replication,but policy de-tails are entirely hidden behind that interface.The communication object is used by the replica-tion object for all network communication needs.It offers a standard interface and implements point-to-point as well as group communication.The control object manages invocations,calling the semantic and replication objects at the right times. This control object isolates the semantics object from the replication object.It is responsible for marshalling and unmarshalling invocation requests,and invoking methods at the semantics object when instructed to do so by the replication object.3.3Towards Truly Distributed WebObjectsHaving just split a Web object into separate subob-jects,it is important that clients still view this col-lection of subobjects as one single entity.This is achieved by ensuring that clients can access a Web object only through its control object.In this way clients have only one access point to the Web object and therefore see it as a single object.This approach is sufficient for nondistributed ob-jects.However,we also want this single-object view to persist even when parts of the Web object are repli-cated or distributed.For example,the fact that the state of the Web object is replicated by having copies of the semantics object reside at multiple locations, should be hidden from clients.How those copies are kept consistent,for example when an invocation re-quest is actually executed,should also be hidden.In other words,the Web object must offer the client dis-tribution transparency.Achieving such transparency is relatively simple: the Web object is no longer considered to consist of only the local copy at a specific client,but is taken to be the collection of all those local copies.In other words,the complete management of replicas is now also part of a Web object.When a client binds to a Web object,the Web object can decide to install a replica of the semantics object at the client.Alternatively,the client may get only a proxy implementation of the Web object’s interfaces.Such differences are hidden from the client:they are part of the overall implementation of the Web object.This approach is,in fact,the one adopted in the Globe architecture[8,18].Central to Globe are dis-tributed shared objects which fully encapsulate their own distribution policy,and which can be physically distributed across multiple machines.Web objects as we have described here,are a special instance of Globe’s distributed shared objects.4Implementing Web Objects This section presents the Java1.1implementation of Web objects as described in the previous sections. The reason for choosing Java as the programming lan-guage was the possibility of integrating Web objects with current Web browsers that offer Java support. Another reason was the portability of the resulting bi-naries,which will allow us to experiment with dynam-ically loading Web objects and subobjects.Web objects are based on the Globe architecture, thus their implementation relies heavily on that of Globe.For this reason,wefirst describe the Globe Java run-time and development environment before paying specific attention to the implementation of Web objects.4.1Basic Globe Implementation Globe,like CORBA and many other distributed object architectures,is based on the use of interfaces.One of its main development components is an Interface Def-inition Language(IDL).The Globe IDL is used by de-velopers to define the interfaces that will be exported and used by Globe objects.We have defined a map-ping from the Globe IDL to Java.1A developer starts with defining,in Globe’s IDL, the interfaces for a class of Globe’s distributed shared objects.After that,an Object Definition Language (ODL)is used to describe how a Globe distributed shared object will actually implement and export its interfaces.This may be done in a general program-ming language such as Java,or a special-purpose ODL.Since we have not yet developed such an ODL, Globe distributed shared objects are currently defined directly in Java.The run-time environment itself needs basic ser-vices such as memory management,thread manage-ment,I/O,persistence,etc.In Globe,these are to be implemented as library services or basic objects(e.g. stream objects for I/O or thread objects).For our Java implementation,we have used native Java objects and services whenever possible.Finally,to implement Web objects,the Globe en-vironment must provide implementations of the repli-cation,communication and control subobjects.These are currently available in the form of simple Java ob-jects contained in libraries.1The Globe IDL is different enough from other IDLs to warrant a different mapping than that used by existing systems.Because the interaction of Globe distributed shared objects is based on interfaces,the use and mapping of these interfaces is important.In Globe,interfaces are represented by actual structures that clients can store or pass around(as parameters or return values).These representations of interfaces(which we will refer to as Globe interfaces)are used to perform the actual invocation of methods.A Globe interface provides clients with access to(part of)the methods exported by a Globe distributed shared object.Each Globe in-terface is mapped to a Java class representing that in-terface.In other words,we use a separate Java class for each Globe interface.Such a Java class contains the methods belonging to the Globe interface,and im-plements them by forwarding method invocations to Globe objects containing the actual implementations. Clients can thus invoke a Globe distributed shared ob-ject directly through a Java object.Figure5shows a situation where a Java client has received a Globe interface for a Web object and calls a method from this interface.The Java object represent-ing the Globe interface calls the same method on the control object(also a Java object)of the local imple-mentation of the Web object.The control object then calls methods on the replication and semantics objects (which are also Java objects)as necessary.Figure5:A Java client accessing a Web object through an interface object4.2Web ObjectsThe main activity in creating a Web object is imple-menting a semantics object.Once the semantics ob-ject has been written,a control object is generated from the description of the semantics object.This con-trol object accepts all the method calls from the client and uses the replication object’s knowledge of the dis-tribution policy to decide whether to call the semantics object directly,or to marshal parameters and to let the replication object take care of the call.The replication object uses the communication ob-ject to send and receive messages.The communica-tion object implements point-to-point communication using TCP/IP from Java’s networking API.It can alsodo blocking sends,or nonblocking sends and explicit receives.The replication object uses the control ob-ject to call methods of the semantics object.The repli-cation object need not know which method is to be called,it just passes information on to the control ob-ject.The control object uses Java’s reflection API[16] to unmarshal any parameters and to subsequently call the appropriate method of the semantics object.We have implemented several replication objects, based on different replication coherence requirements of Web objects.Details on the algorithms and policies are described in[10].It is important that Web objects are integrated into the current Web infrastructure in such a way that they can be accessed using currently available Web tools such as Web browsers,spiders,etc.There are three approaches to integrating Web objects into the cur-rent Web.Thefirst approach involves a gateway,the goal of which is to allow standard Web clients(e.g., browsers)to access Web objects.The gateway is a process that runs on a server machine and accepts reg-ular HTTP requests for a Web object.When a re-quest comes in,the gateway locates the desired object, binds to it(i.e.,acquires a Globe interface for it),and retrieves data from it.If necessary,this data is con-verted into an appropriate format(e.g.to HTML)and an HTTP reply containing the data is sent back to the client.With this approach,clients are completely un-aware of the actual implementation of Web objects.The second approach involves a custom extensible browser that is aware of Web objects and knows how tofind and communicate with them.The browser is directly responsible for locating the appropriate Web object,binding to it,and receiving data from it.The browser will also have to be able to deal with the Web object’s data,possibly using plug-in extensions when necessary.The third approach is a hybrid one that combines elements from the previous two approaches using the Java support present in most major Web browsers.As in thefirst approach,a gateway is used to access Web objects.However,instead of returning the data di-rectly to the browser,the gateway returns a custom Java applet.This applet will contact and bind to the Web object via the gateway,and represent the Web object in the client’s browser.Such an applet can be omitted in certain cases,such as for HTML Web ob-jects.This is the approach we have chosen for our pro-totype implementation.5Related WorkWe have presented Web objects as a solution to the Web’s scalability problems.Web objects are however not the only solution devised to solve this problem. Currently a number of replication and caching tech-niques are in standard use in the Web.Popular Web sites(or parts thereof)are often replicated by creating mirror sites.Consistency is usually achieved through manually updating the mirror sites based on changes to the master site.Sometimes these changes are auto-mated by the Web site maintainers.However,the tech-niques used are ad-hoc and have not been standard-ized.Three forms of caching are currently in use.Client caching is done by browsers with a separate local cache for each user.The use af a separate cache for each user results in inefficient use of cache space as there are often many redundant entries among the users.Caching proxies[12]offer a solution to this by keeping site-wide caches.For large sites(compa-nies,universities,etc.)only single copies of resources need to be cached allowing more efficient use of cache space.This solution still suffers from the fact that ev-ery accessed document is added to the cache,and that coherence is not tuned to individual documents.Fi-nally,server caches are pr ovided as a solution to the problem of degrading server performance.By caching recently accessed pages in main memory,servers can speed up access to popular resources,thus increasing their performance.However,at very popular sites the problem of server performance is often coupled with that of bandwidth,so this offers only a partial solution.A number of Web problems are partially addressed in the new HTTP version(1.1)[6].It contains im-proved use of network resources and a large and ex-tendible set of parameters to facilitate the sending of caching information between client and server.This allows current caching techniques to make wiser de-cisions,but the basic drawbacks remain.Due to the limitations of the current caching and replication approaches much work has been done to change current Web caching.Wessels[19]proposes to allow servers to grant or deny a client permis-sion to cache a resource.Push-caching[7]allows popular resources to be optimally distributed to other servers based on knowledge of the resource’s access patterns.Harvest caches[4],which provide a hierar-chical cache,are currently gaining popularity in the Web.The Bayou[17]project,though not directly re-lated to the Web,has looked at the problem of replica and cache coherence,and we have based a number of our coherence models on some of their work[10]. Caching goes Replication[1]looks at caching as repli-cation where updates are pushed to the client rather than the current situation where the client decides when to update the cache.Due to the limited and noninteractive nature of HTTP,much attention has been focused on the com-bination of object technology and the Web.Currently much work is being done in integrating CORBA[15] and similar distributed object technologies and the Web.Especially the combination of Java and CORBA is receiving much attention[5].These approaches do。
