2008影印版)KEY+TERMS
2008年国际商务单证专业考试(缮制与操作)答案1

一、根据下述合同内容审核信用证,并指出不符之处。
(36分)1、受益人名称与合同卖方不符(合同是SHANGHAI SHENG DA CO.,LTD.,信用证SHANGHAI DA SENG CO.,LTD.)2、开证申请人的地址不符(合同是28, IMAMGONJ,信用证是26,IMAMGONJ)3、商品名称不符(合同是STEEL TAPE RULES,信用证是TAPE RULES)4、商品规格不符(合同是JH-392W和JH-380W,信用证是JH-395W和JH-386W)5、单价不符(合同是USD3.60/DOZ PAIR CFR CHITTAGONG和USD4.20/DOZ PAIRCFRCHITTAGON,信用证是HKD3.60 PER DOZEN CIF CHITTAGONG和HKD4.20 PER DOZEN CIF CHITTAGONG)6、总金额不符(合同是USD9,300.00,信用证是CURRENCY HKD AMOUNT 9800.00)7、包装不符(合同是In Cartons,信用证是PACKING: EXPORT STANDARDSEAWORTHY PACKING)8、装运期不符(合同是During May, 2008,信用证是LATEST DATE OF SHIPMET : MAY2, 2008)9、装运港不符(合同是Shanghai,信用证是ANY CHINESE PORTS)10、分批和转运要求不符(合同是Partial Shipment and Transshipment are allowed.,信用证是PARTIAL SHIPMENT: NOT ALLOWED和TRANSSHIPMENT: NOT ALLOWED)11、合同用的是CFR术语,信用证要求受益人提交保险单不符12、CFR术语,提单上要求注明“FREIGHT COLLECT”不符13、付款期限不符(合同是Sight Letter of Credit,信用证DRAFTS AT 60 DAYS SIGHT)二、根据买方订单及相关资料缮制形式发票(24分)(12) DETAILS OF OUR BANK:BANK OF CHINA, SHANGHAI BRANCH,NO.4 Zhongshan road, Shanghai ,P.R.CHINASWIFT CODE: BKCHCNBJ530BENEFICIARY: SHANGHAI LUCKY SAFETY SCREENS CO., LTDACCOUNT NO: 1281 2242012 7091 015ADDRESS: UNIT C 2/F JINGMAO TOWER SHANGHAI ,CHINASHANGHAI LUCKY SAFETY SCREENS CO., LTD三、根据合同、信用证及补充资料缮制商业发票、海运提单、汇票及普惠制产地证FORM A(共40分)凭信用证号Drawn under industrial bank of Japan,ltd.,head office L/C NO.LC196107800日期按…. .息…. 付款Dated Oct.15,2007 Payable with interest @… .. % per annum 号码汇票金额上海NO.YL71001Exchange for USD12630.00 Shanghai …DEC.05,2007……………见票…………………日后(本汇票之正本未付)付交At *** sight of this FIRST of Exchange (Second of Exchange being unpaid) Pay to the order of BANK OF CHINA,SHANGHAI BRANCH金额the sum of SAY US DOLLARS TWELVE THOUSAND SIX HUNDRED AND THIRTY ONLY此致To: INDUSTRIAL BANK OF JAPAN,HEAD OFFICESHANGHAI YILONG CO.,LTD.XXXSHANGHAI YILONG CO.,LTD.X X X.Shipper Insert Name, Address and PhoneSHANGHAI YILONG CO.,LTD.NO.91 NANING ROAD SHANGHAI ,CHINA.B/L No. TH14HK07596.Consignee Insert Name, Address and PhoneTO ORDER中远集装箱运输有限公司COSCO CONTAINERLINESNotify Party Insert Name, Address and Phone(It is agreed that no responsibility shall attach to the Carrier or his agents for failure to notify)ABC COMPANY1-3 MACHI KU STREET OSAKA ,JAPANPort-to-Port or Combined TransportBILL OF LADINGwise noted. The total number of packages or units stuffed in the container, the description of the goods and the weights shown in this Bill of Loading are furnished by the Merchants, and which the carrier has no reasonable means of checking and is not a part of this Bill of Loading contract. The carrier has issued the number of Bills of Lading stated below, all of this tenor and date, one of the original Bills of Lading must be surrendered and endorsed or sig- ned against the delivery of the shipment and whereupon any other original Bills of Lading shall be void. The Merchants agree to be bound by the terms And conditions of this Bill of Lading as if each had personally signed this Bill of Lading.SEE clause 4 on the back of this Bill of Lading (Terms continued on the back hereof, please read carefully)*Applicable Only When Document Used as a Combined Transport Bill of Lading.Combined Transport * Pre-carriage byCombined Transport * Place of ReceiptOcean Vessel Voy. No. KAOHSIUNG V.0707S .Port of Loading SHANGHAI PORT.Port of Discharge OSAKACombined Transport * Place of DeliveryMarks & Nos. Container / Seal No.ABC OSAKANOS.1-60C/N:SNBU7121820No. of Containers or Packages60 CARTONS Description of Goods (If Dangerous Goods, See Clause 20)CARDBOARD BOXCFS-CFSGross Weight Kgs2160.00KGSMeasurement33.000CBMP a r t i c u l a r s F u r n i s h e d b y M e r c h a n t sDescription of Contents for Shipper’s Use Only (Not Part of This B/L Contract).Total Number Of Containers and/or Packages (In Words) SAY SIXTY CARTONS ONLYFreight & Charges FREIGHT PREPAIDRevenue Tons RatePerPrepaidCollectLADEN ON BOARD THE VESSEL DATE:NOV29,2007BY KAOHSIUNG V.0707SCOSCO CONTAINER LINESCNS01 0108895。
考研英语(2008)--考研英语阅读32分高分经典强化---印建坤课程电子版教材

考研英语(2008)--考研英语阅读32分高分经典强化---印建坤课程电子版教材一.阅读技巧篇大家得清楚,学习英语和英语的复习备考不完全是一回事。
学习一门语言讲究的是循序渐进、厚积博发,而对于像考研英语、四六级这种限定性的考试来说,它的命题都是有规律可循的。
只要掌握了这些规律,它的复习备考其实很简单。
本书主要和同学们讲一下,阅读理解的命题规律解题技巧以及对大小作文命题规律的分析。
经常有同学说,石春真、吴祖霖、岳华亭的几百篇都做了好几遍了,星火的词典也背烂了,新概念新视野新东方的教材也读了,怎么还是一看文章就晕,一看题目就蒙,一错就是两位数呢,到底是为什么呢?其实一个主要的问题还是同学们缺少对命题规律和选项特征的了解。
四个选项中,相对于错误选项,正确选项一般都有什么特征?命题者到底是按照什么来命制选项的?经过多年的研究,我们现在可以肯定的说:命题者在命题时遵循了两条基本规律、五个区分方法。
把握住这两条规律、五个方法,阅读理解可以轻易排除干扰项、分析出答案来。
而从测试学的角度来说,阅读理解试题无非就是考察我们的阅读理解能力,而阅读理解能力就是提取有效信息的能力。
所以阅读理解题目的设计无论怎么千变万化,最根本的目的就是在考察我们能否把文章的有效信息找出来。
而我们知道,有效信息就是文中表达的观点、论点、主论点、分论点以及作者的感情倾向和态度,这些就是命题的出题点所在。
大多数的阅读试题中,正确的选项其实就是文章中观点、论点、主论点、分论点和态度等有效信息的直接表达或者变形表达。
而这类观点性有效信息的表达,有两个重要特征:一.表述上必须具有相对的抽象性、概括性、宏观性;二.表述上不能太绝对要留有余地四平八稳,不能带有过于强烈的感情色彩和倾向。
一个表述上极端的论点是站不住脚的,很容易受到攻击。
所以从这儿可以推知:阅读题目的正确选项与非正确选项相比,应该符合上述两个特征。
到底是不是这样呢?我们用真题来验证一下。
Hewlett-Packard Development Company, L.P. 2008年版Po

Pointing Devices and Keyboard User Guide© Copyright 2008 Hewlett-Packard Development Company, L.P.Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation.The information contained herein is subject to change without notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.First Edition: August 2008Document Part Number: 485059-001Product noticeThis user guide describes features that are common to most models. Some features may not be available on your computer.Table of contents1 Using pointing devicesSetting pointing device preferences (2)Using the TouchPad (2)Using the pointing stick (2)Connecting an external mouse (2)2 Using the keyboardUsing hotkeys (3)Displaying system information (fn+esc) (4)Initiating Sleep (fn+f3) (4)Switching the screen image (fn+f4) (5)Viewing battery charge information (fn+f8) (5)Decreasing screen brightness (fn+f9) (5)Increasing screen brightness (fn+f10) (5)Activating the ambient light sensor (fn+f11) (5)3 Using HP Quick Launch ButtonsAccessing the Quick Launch Buttons control panel (8)Displaying the Q Menu (9)4 Using HP QuickLook 2Configuring QuickLook 2 (11)Using manual information collection (11)Using QuickLook 2 (12)For more information (12)5 Using keypadsUsing an optional external numeric keypad (14)6 Cleaning the TouchPad and keyboardIndex (16)iiiiv1Using pointing devicesComponent Description(1)Pointing stick*Moves the pointer and selects or activates items on the screen.(2)Left pointing stick button*Functions like the left button on an external mouse.(3)TouchPad*Moves the pointer and selects or activates items on the screen.(4)Left TouchPad button*Functions like the left button on an external mouse.(5)Center TouchPad button*Functions like the center button on an external mouse.(6)Right TouchPad button*Functions like the right button on an external mouse.(7)TouchPad scroll zone Scrolls up or down.(8)Right pointing stick button*Functions like the right button on an external mouse.(9)Center pointing stick button*Functions like the center button on an external mouse.*This table describes factory settings. To view or change pointing device preferences, select Start>Control Panel>Hardwareand Sound>Mouse.1Setting pointing device preferencesUse Mouse Properties in Windows® to customize settings for pointing devices, such as buttonconfiguration, click speed, and pointer options.To access Mouse Properties, select Start>Control Panel>Hardware and Sound>Mouse.Using the TouchPadTo move the pointer, slide your finger across the TouchPad surface in the direction you want the pointer to go. Use the TouchPad buttons like the corresponding buttons on an external mouse. To scroll up and down using the TouchPad vertical scroll zone, slide your finger up or down over the lines.NOTE:If you are using the TouchPad to move the pointer, you must lift your finger off the TouchPadbefore moving it to the scroll zone. Simply sliding your finger from the TouchPad to the scroll zone will not activate the scrolling function.Using the pointing stickPress the pointing stick in the direction you want to move the pointer on the screen. Use the left andright pointing stick buttons as you would the left and right buttons on an external mouse.Connecting an external mouseYou can connect an external USB mouse to the computer using one of the USB ports on the computer.A USB mouse can also be connected to the system using the ports on an optional docking device.2Chapter 1 Using pointing devices2Using the keyboardUsing hotkeysHotkeys are combinations of the fn key (1) and either the esc key (2) or one of the function keys (3).The icons on the f3, f4, and f8 through f11 keys represent the hotkey functions. Hotkey functions andprocedures are discussed in the following sections.Function HotkeyDisplay system information.fn+escInitiate Sleep.fn+f3Switch the screen image.fn+f4Display battery information.fn+f8Decrease screen brightness.fn+f9Increase screen brightness.fn+f10Activate the ambient light sensor.fn+f11Using hotkeys3To use a hotkey command on the computer keyboard, follow either of these steps:●Briefly press the fn key, and then briefly press the second key of the hotkey command.– or –●Press and hold down the fn key, briefly press the second key of the hotkey command, and thenrelease both keys at the same time.Displaying system information (fn+esc)Press fn+esc to display information about system hardware components and the system BIOS version number.In the Windows fn+esc display, the version of the system BIOS (basic input-output system) is displayed as the BIOS date. On some computer models, the BIOS date is displayed in decimal format. The BIOS date is sometimes called the system ROM version number.Initiating Sleep (fn+f3)CAUTION:To reduce the risk of information loss, save your work before initiating Sleep.Press fn+f3 to initiate Sleep.When Sleep is initiated, your information is stored in system memory, the screen is cleared, and power is conserved. While the computer is in the Sleep state, the power lights blink.The computer must be on before you can initiate Sleep.NOTE:If a critical battery level occurs while the computer is in the Sleep state, the computer initiates Hibernation and the information stored in memory is saved to the hard drive. The factory setting forcritical battery action is Hibernate, but this setting can be changed using Power Options in WindowsControl Panel.To exit Sleep, briefly press the power button.The function of the fn+f3 hotkey can be changed. For example, you can set the fn+f3 hotkey to initiate Hibernation instead of Sleep.NOTE:In all Windows operating system windows, references to the sleep button apply to the fn+f3hotkey.4Chapter 2 Using the keyboardSwitching the screen image (fn+f4)Press fn+f4 to switch the screen image among display devices connected to the system. For example, if a monitor is connected to the computer, pressing fn+f4 alternates the screen image from the computer display to the monitor display to a simultaneous display on both the computer and the monitor.Most external monitors receive video information from the computer using the external VGA videostandard. The fn+f4 hotkey can also alternate images among other devices receiving video information from the computer.The following video transmission types, with examples of devices that use them, are supported by the fn+f4 hotkey:●LCD (computer display)●External VGA (most external monitors)●S-Video (televisions, camcorders, DVD players, VCRs, and video capture cards with S-Video-injacks)●HDMI (televisions, camcorders, DVD players, VCRs, and video capture cards with HDMI ports)●Composite video (televisions, camcorders, DVD players, VCRs, and video capture cards withcomposite-video-in jacks)NOTE:Composite devices and S-Video devices can be connected to the system only by usingan optional docking device.Viewing battery charge information (fn+f8)Press fn+f8 to display charge information for all installed batteries. The display indicates which batteries are charging and reports the amount of charge remaining in each battery.Decreasing screen brightness (fn+f9)Press fn+f9 to decrease screen brightness. Hold down the hotkey to decrease the brightness levelincrementally.Increasing screen brightness (fn+f10)Press fn+f10 to increase screen brightness. Hold down the hotkey to increase the brightness levelincrementally.Activating the ambient light sensor (fn+f11)Press fn+f11 to activate and deactivate the ambient light sensor.Using hotkeys53Using HP Quick Launch Buttons The HP Quick Launch Buttons enable you to quickly open programs, files, or Web sites you usefrequently. You can use the factory settings, which are described in the following table. Or you canreprogram the buttons by opening the Q Menu in the Quick Launch Buttons control panel.The Quick Launch Buttons include the info button (1), the presentation button (2), and the calculatorbutton (3).The following table describes the factory settings for the Quick Launch Buttons.NOTE:Button functions vary, depending on the software installed on your computer.Component Description(1)Info button Launches Info Center, which provides shortcuts to features, suchas the following:NOTE:Some of the features listed may not be included with yourcomputer model.●HP Wireless Assistant●HP ProtectTools Suite6Chapter 3 Using HP Quick Launch ButtonsComponent Description●HP 3D DriveGuard●HP Help and Support●HP Notebook Accessories Product Tour●HP Product User Guides●HP Connection Manager●HP Software Setup●Presto! BizCard 5(2)Presentation button Opens the Presentation Options window, which enables you tostart a frequently used presentation, file, program, or Web site. Youcan also adjust the display settings for optimum viewing.(3)Calculator button Launches the Windows calculator.7Accessing the Quick Launch Buttons control panel The Q Menu in the Quick Launch Buttons control panel enables you to set your own preferences for the info button and the presentation button. Both buttons can be used to launch frequently used programs.You can open the Quick Launch Buttons control panel in any of the following ways:●Select Start>Control Panel>Hardware and Sound>Quick Launch Buttons.– or –Right-click the HP Quick Launch Buttons icon in the notification area, and then select one of thefollowing tasks:◦Adjust HP Quick Launch Buttons Properties◦Launch Q Menu◦Turn Presentation On◦Turn Ambient Light Sensor Off8Chapter 3 Using HP Quick Launch ButtonsDisplaying the Q MenuThe Q Menu provides quick access to the Quick Launch Button settings.To display the Q Menu on the desktop:▲Right-click the HP Quick Launch Buttons icon in the notification area, at the far right of the taskbar, and then select Launch Q Menu.NOTE:For more information about the Q Menu, refer to the software Help.Displaying the Q Menu94Using HP QuickLook 2HP QuickLook 2 enables you to see your Microsoft® Outlook e-mail, calendar, contact, and taskinformation without starting the operating system. After QuickLook 2 has been configured, you canquickly access your important information when the computer is off or in Hibernation by pressing the info button.10Chapter 4 Using HP QuickLook 2Configuring QuickLook 2To configure QuickLook 2, follow these steps:1.Open Microsoft® Outlook.QuickLook 2 displays 2 icons on the Outlook toolbar:The QuickLook 2 Preferences icon enables you to set automatic data collection preferences.The QuickLook Capture icon enables you to manually initiate QuickLook 2 information capture in addition to automatic retrieval.NOTE:For most tasks, you will use the QuickLook 2 Preferences icon.2.Click the QuickLook 2 Preferences icon on the Outlook toolbar.The QuickLook 2 Preferences dialog box opens.3.Set the following preferences:●When you want QuickLook 2 to capture information from Outlook and save it on your harddrive●What types of data you want to be displayed for your calendar, contacts, e-mail, and tasks4.Select security, if needed, and set a personal identification number (PIN).Using manual information collectionEven if you have configured QuickLook 2 to collect information at preset intervals, you can also manually collect and save Outlook information any time you are logged on to your Outlook account.Configuring QuickLook 211Using QuickLook 2The info button behavior depends on the power state of the computer, as shown in the following table.Power state Info button behaviorOff Opens QuickLook.Hibernation Opens QuickLook.On Opens Info Center.Sleep Returns the computer to its previous state.NOTE:QuickLook 2 is enabled at the factory. If you disable QuickLook 2 in the system BIOS, pressing the info button opens Info Center when the computer is on. Pressing the info button when the computer is off, in Hibernation, or in the Sleep state has no effect.For more informationFor more details about setting up and using QuickLook 2, refer to the QuickLook 2 software Help.12Chapter 4 Using HP QuickLook 25Using keypadsThe computer has an integrated numeric keypad and also supports an optional numeric keypad or an optional external keyboard that includes a numeric keypad.Component Description(1)Num lock light On: Num lock is on.(2)num lk key Alternates between the navigation and numeric functions on theintegrated numeric keypad.NOTE:The keypad function that is active when the computer isturned off will be reinstated when the computer is turned back on.(3)Integrated numeric keypad Can be used like the keys on an external numeric keypad.13Using an optional external numeric keypadKeys on most external numeric keypads function differently according to whether num lock is on or off.(Num lock is turned off at the factory.) For example:●When num lock is on, most keypad keys type numbers.●When num lock is off, most keypad keys function like the arrow, page up, or page down keys.When num lock on an external keypad is turned on, the num lock light on the computer is turned on.When num lock on an external keypad is turned off, the num lock light on the computer is turned off.To turn num lock on or off on an external keypad as you work:▲Press the num lk key on the external keypad, not on the computer.14Chapter 5 Using keypads6Cleaning the TouchPad and keyboard Dirt and grease on the TouchPad can cause the pointer to jump around on the screen. To avoid this,clean the TouchPad with a damp cloth, and wash your hands frequently when using the computer.WARNING!To reduce the risk of electric shock or damage to internal components, do not use avacuum cleaner attachment to clean the keyboard. A vacuum cleaner can deposit household debris on the keyboard surface.Clean the keyboard regularly to prevent keys from sticking and to remove dust, lint, and particles thatcan become trapped beneath the keys. A can of compressed air with a straw extension can be used to blow air around and under the keys to loosen and remove debris.15IndexAambient light sensorhotkey5Bbattery charge information5 buttonsinfo6pointing stick1presentation7Quick Launch6TouchPad1Ccomposite video5Ddisplayimage, switching5screen brightness hotkeys5 Ffn key3function keys3HHDMI5hotkeysambient light sensor5battery charge information5 decreasing screenbrightness5description3displaying systeminformation4increasing screenbrightness5initiating Sleep4switching screen image5using4HP QuickLook 210Iinfo button6integrated numeric keypad,identifying13Kkeyboard hotkeys, identifying3keypad, externalnum lock14using14keypad, integratedidentifying13Llight, num lock13Mmouse, externalconnecting2setting preferences2Nnum lk key, identifying13num lock light, identifying13num lock, external keypad14Ppointing devicesidentifying1setting preferences2using2pointing stickidentifying1using2pointing stick buttons,identifying1presentation button7QQuick Launch Buttons6Quick Launch Buttons controlpanel6SS-Video5screen brightness hotkeys5screen image, switching5scroll zone, TouchPad1Sleep hotkey4system information hotkey4TTouchPadidentifying1using2TouchPad buttons,identifying1TouchPad scroll zone,identifying1Vvideo transmission types516Index。
2008年职称英语综合类教材新增部分内容完整版
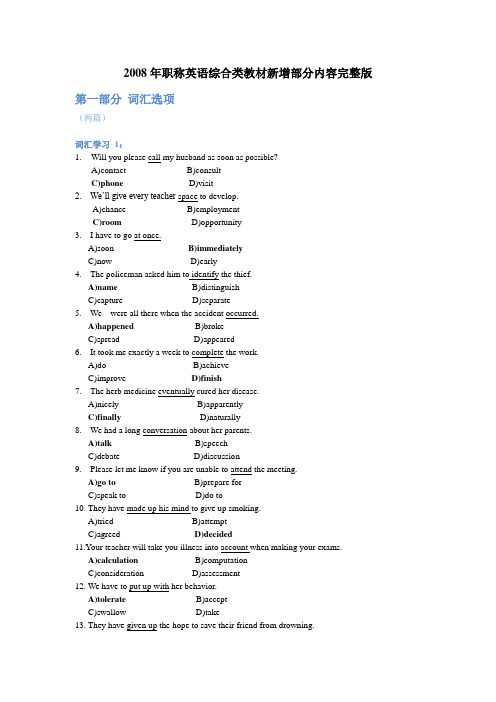
2008年职称英语综合类教材新增部分内容完整版第一部分词汇选项(两篇)词汇学习1:1.Will you please call my husband as soon as possible?A)contact B)consultC)phone D)visit2. We‘ll give every teacher space to develop.A)chance B)employmentC)room D)opportunity3. I have to go at once.A)soon B)immediatelyC)now D)early4. The policeman asked him to identify the thief.A)name B)distinguishC)capture D)separate5. We were all there when the accident occurred.A)happened B)brokeC)spread D)appeared6. It took me exactly a week to complete the work.A)do B)achieveC)improve D)finish7. The herb medicine eventually cured her disease.A)nicely B)apparentlyC)finally D)naturally8. We had a long conversation about her parents.A)talk B)speechC)debate D)discussion9. Please let me know if you are unable to attend the meeting.A)go to B)prepare forC)speak to D)do to10. They have made up his mind to give up smoking.A)tried B)attemptC)agreed D)decided11.Your teacher will take you illness into account when making your exams.A)calculation B)computationC)consideration D)assessment12. We have to put up with her behavior.A)tolerate B)acceptC)swallow D)take13. They have given up the hope to save their friend from drowning.A) ended B) abandonedC) built D)strengthen14. I seldom watch TV.A) rarely B) frequentlyC) normally D) occasionally15. The dentist has decided to take out the girl's bad tooth.A) dig B) drawC) pull D) extract答案:1. C2. C3. B4. A5. A6. D7. C8. A9. A 10. D11.A 12.A 13.B 14.A 15.D词汇练习6:*1. With immense relief, I stopped running.A) much B) enormousC) little D) extensive*2. The scientists began to accumulate a huge mass of data.A) build up B) put upC) make up D) clear up*3. When Jack eventually overtook the last truck he pulled over to the inside lane.A) skipped B) passedC) reached D) led*4. Because of the popularity of the region, it is advisable to book hotels in advance.A) possible B) profitableC) easy D) wise*5. Data from Voyager II have presented astronomers with a puzzle about why our outermost planet exists.A) problem B) mysteryC) question D) point*6. He rolled up his trouser leg to exhibit his wounded knee.A) spread B) openC) show D) examine*7. Why can't you stop your eternal complaining!A) everlasting B) longC) monotonous D) lengthy*8. This poem depicts the beautiful scenery of a small town in the South.A) describes B) drawsC) writes D) introduces*9. The telephone system is no longer operative.A) running B) movingC) rotating D) working*10. Hundreds of buildings were wrecked by the earthquakeA) shaken B) fallenC) damaged D) trembled*11. The latest car model embodies many new improvements.A) consists of B) includesB) makes up D) marks*12. Thick clouds obscured the stars from view..A) darkened B) heldC) blackened D) prevent*13. The parents have to restrain their daughter from running out into the street.A) disallow B) reduceC) prevent D) confine*14. The discovery was sensational.A) sexy B) surprisingC) exceptional D) exciting*15. After supper we usually take a stroll around the park for about an hour.A) walk B) restC) bath D) breath答案:1. B2. A3. B4. D5. B6. C7. A8. A9. D 10. C11.B 12.D 13.C 14.D 15.A第二部分阅读判断第一篇A New StartAfter Christmas comes the anti-Christmas. If the festive season is all about filing up on the things you like that are bad for you, then the new year is the ‗detox season' - when people across the western world adopt special diets to lose weight and get rid of the vague feeling that they have spent the last few weeks poisoning themselves.But are detox diets really necessary? After all, the body itself gets rid of unwanted substances. That's what the liver and kidney are for."The detox fad - or fads, as there are many methods - is an example of the capacity of people to believe in and pay for magic despite the lack of any sound evidence1," says Martin Wiseman, professor of human nutrition at the University of Southampton in the UK.Most of the pills, juices, teas and oils that are sold for their detoxifying effects on the body have no scientific foundation for their claims, according to the research. People would be better off having a glass of water and going to bed early.Detox diets may be magic rather science, but they are the kind of magic which many people want to perform. That may have something to do with the westen diet in general.Scientists and dieticians argue that the benefits people feel are not due to their body getting rid of excessive toxins but are due to changing from what is likely to have been a 'poor' diet.Having fewer headaches, for example, is probably the result of being fully hydrated due to drinking so much water and better skin may be due to eating more fruit and vegetables.Detox diets may also be dangerous, as they may deprive vulnerable groups –pregnant women, for instance, or growing teenagers - of the kind of nutrients they need.Yet their popularity continues to rise. This may be something to do with the way that food works within many western cultures2. Generally, a country's food develops along with its economy and society. Food becomes part of a person's cultural identity.In some countries, this link has been broken. In the UK, for example, rapid industrialization in the 18th and 19th centuries saw millions of people move from the countryside to the towns interrupting the development of a national cuisine. The United States, a country of immigrants from many different places, has found it hard to develop a national cuisine: In both places, comparatively few people cook for themselves and food supply is .dominated by big processing and agribusiness companies.Detox diets are more popular in these countries than in places like France and Italy, where strong links between food and national culture remain, and where far more people regularly cook for themselves instead of buying processed foods.Perhaps detox diets are successful because many westerners have lost mast in what they eat. On the other hand, they may help re-introduce people to the kind of food that is necessary for a healthy diet. And after learning that, they won't poison themselves in the first place.This would mean radical changes in the way that people eat across the west. And that would be an unwelcome development for the food industry. From the business point of view, it is much better to sell people the problem and then sell them the solution.词汇:Detox v. & n. 解毒、去毒fad n.风尚dietician n.饮食学家hydrate v.水化,使吸水cuisine n. 烹饪术agribusiness n. 农业综合经营注释:1. the capacity of people to believe in and pay for magic despite the lack of any sound evidence人们在缺乏证据的情况下相信魔法,并愿意为之付出代价的习性2. This may be something to do with the way that food works within many western cultures.这可能和食物在许多西方文化中的地位有关。
计算机专业英语课后题答案汇总

课后题答案.doc第六章Dbcbbaacbd jachgidefb7Ababdadcdb iefjabgdch8Aacacacddc gajidbhcfe9Cbadcdbbbd gbaihecjdf第10章Aadbacdcbd ghfabcjdei计算机专业英语+单词+部分习题计算机专业英语(2008影印版)高等教育出版社共10页KEY TERMS第一单元application software应用软件basic application基本应用软件communication device通信设备compact disc (CD)光盘computer competency计算机能力Connectivity连通性Data数据database file数据库文件desktop computer台式计算机device driver磁盘驱动程序digital versatile disc(DVD)数字多用途光盘digital video disc(DVD)数字多用途光盘document file文档文件end user终端用户floppy disk软盘handheld computer手持计算机hard disk硬盘Hardware硬件High definition高清Information信息information system信息系统information technology信息技术input device输入设备Internet因特网Keyboard键盘mainframe computer大型机Memory内存Microcomputer微型机Microprocessor微处理器midrange computer中型机Minicomputer小型计算机Modem调制解调器Monitor监视器Mouse鼠标Network网络notebook computer笔记本电脑operating system操作系统optical disk光盘output device输出设备palm computer掌上电脑Peoplepersonal digital assistant(PDA)个人数字助理presentation file演示文稿primary storage主存Printer打印机Procedure规程Program程序random access memory随机存储器secondary storage device辅存Software软件specialized application专门应用软件Supercomputer巨型机system software系统软件system unit系统单元tablet PC平板电脑Utility实用程序wireless revolution无线革命worksheet file工作表第三单元analytical graph分析图application software应用软件Autocontent Wizard内容提示向导basic applications基础应用软件bulleted list项目符号列表business suite商业套装软件Button按键Cell单元格character effect字效Chart图表Column列Computer trainer计算机培训员Contextual tab上下文标签Database数据库database management system (DBMS)数据库管理系统database manager数据库管理员Design template设计模板dialog box对话框Document文件Editing编辑Field字段find and replace查找和替换Font字体font size字号Form窗体Format格式Formula公式Function函数Galleries图库grammar checker语法检查器graphical user interface (GUI)图形用户界面home software家庭软件home suite家庭套装软件Icons图标integrated package集成组件Label标签master slide母板Menu菜单menu bar菜单栏numbered list编号列表numeric entry数值型输入personal software个人软件personal suite个人套装软件Pointer指针presentation graphic图形演示文稿productivity suite生产力套装软件Query查询Range范围Recalculation重算Record记录relational database关系型数据Report报表Ribbons功能区、格式栏Row行Sheet工作表Slide幻灯片software suite软件套装Sort排序specialized applications专用应用程序specialized suite专用套装软件speech recognition语音识别spelling checker拼写检查器spreadsheet电子表格system software系统软件Table表格text entry文本输入Thesaurus[θis?:r?s]分类词汇集Toolbar工具栏user interface用户界面utility suite实用套装软件what-if analysis变化分析Window窗口word processor文字处理软件word wrap字回行workbook file工作簿Worksheet工作表第四单元Animation动画artificial intelligence (AI)人工智能artificial reality虚拟现实audio editing software音频编辑软件bitmap image位图Blog博客Buttons按键clip art剪辑图Desktop publisher桌面发布desktop publishing program桌面印刷系统软件drawing program绘图程序expert systems专家系统Flash动画fuzzy logic模糊逻辑graphical map框图graphics suite集成图HTML editors HTML编辑器illustration program绘图程序Image editors图像编辑器image gallery图库immersive experience沉浸式体验industrial robots工业机器人Interactivity交互性knowledge bases知识库knowledge-based system知识库系统Link链接mobile robot移动式遥控装置Morphing渐变Multimedia多媒体multimedia authoring programs多媒体编辑程序page layout program页面布局程序perception systems robot感知系统机器人Photo editors图像编辑器Pixel[piks?l]像素raster image光栅图像Robot机器人Robotics机器人学stock photographs照片库story boards故事版Vector[vekt?]矢量vector illustration矢量图vector image矢量图象video editing software视频编辑软件virtual environments虚拟环境virtual reality虚拟现实virtual reality modeling language (VRML)虚拟现实建模语言virtual reality wall虚拟现实墙VR虚拟现实Web authoring网络编程Web authoring program网络编辑程序Web log网络日志Web page editor网页编辑器Add Printer Wizard添加打印机向导Antivirus program反病毒程序Backup备份backup program备份程序Booting启动、引导cold boot冷启动computer support specialist计算机支持专家Dashboard widgets仪表盘Desktop桌面desktop operating system桌面操作系统device driver磁盘驱动程序diagnostic program诊断程序dialog box对话框Disk Cleanup磁盘清理Disk Defragmenter磁盘碎片整理器Driver驱动器embedded operating systems嵌入式操作系统File文件file compression program文件压缩程序Folder文件夹Fragmented碎片化graphical user interface (GUI)图形用户界面Help帮助Icon图标language translator语言编译器leopard[lep?d]雪豹操作系统LinuxMac OS Mac操作系统Mac OS XMenu菜单Multitasking多任务处理network operating systems(NOS)网络操作系统network server网络服务器One Button Checkup一键修复operating system操作系统Platform平台Pointer指针Sectors[sekt?]扇区software environment软件环境Spotlight聚光灯stand-alone operating system独立操作系统system software系统软件Tiger老虎操作系统troubleshooting program故障检修程序Uninstall program卸载程序UNIXuser interface用户界面Utility实用程序utility suite实用套装软件Virus[vai?r?s]病毒warm boot热启动Window视窗Windows视窗操作系统Windows Update Windows更新Windows VistaWindows XP第六单元AC adapter 交流适配器Accelerated graphics port(AGP):图形加速端口Arithmetic-logic unit(ALU):算术逻辑单元Arithmetic operation:算术运算ASCII美国标准信息交换码Binary coding schemes:二进制编码制Bit:位Bus:总线Bus line:总线Byte:字节Cable:电缆Cache memory:高速缓存carrier package 封装物Central processing unit (CPU):中央处理器Chip:芯片Clock speed时钟速度Complementary metal-oxide semiconductor:互补金属氧化物半导体Computer technician计算机工程师Control unit:控制单元Coprocessor协处理器Desktop system unit:桌面系统单元Digital数字的Dual-core chips双核芯片EBCDIC:扩展二进制编码的十进制交换码Expansion bus扩展总线Expansion card扩展卡Expansion slot扩展槽FireWire port:火线接口Flash memory闪存Graphics card图形适配卡Graphics coprocessor图形协处理器Handheld computer system unit 手持计算机系统单元Industry standard architecture(ISA)工业标准结构Infrared Data Association(IrDA)红外线传输模组Integrated circuit:集成电路Laptop computer膝式计算机Logical operation逻辑运算Microprocessor:微处理器Motherboard:主板Musical instrument digital interface(MIDI)乐器数字接口Network adapter card网络适配卡Network interface card(NIC)网络接口卡Notebook system unit:笔记本Parallel ports:并行端口Parallel processing并行处理Pc card: :个人计算机插卡PCI Express(PCIe)Peripheral component interconnect (PCI):外围部件互联Personal digital assistant (PDA) 个人数字助理Plug and play:即插即用Port:端口Power supply unit 供电设备Processor:处理器RAM cache: RAM高速缓存Random-access memory (RAM):随机存储器Read-only memory (ROM):只读存储器RFID tag射频识别标签Semiconductor:半导体serial ATA(SATA)串行A TA接口规范Serial ports:串行端口Silicon chip:硅芯片Slot:插槽Smart card:智能卡sound card声卡System board:系统板System cabinet:主机System clock:系统时钟System unit:系统单元tablet PC平板式电脑tablet PC system unit平板式电脑系统单元TV tuner card:电视调频卡Unicode:统一字符编码标准Universal serial bus (USB):通用串行总线Universal serial bus (USB) port:通用串行总线端口Virtual memory:虚拟存储器Word:字第七单元active-matrix monitor有源矩阵显示器bar code条形码bar code reader条形码阅读器cathode ray tube monitor (CRT)阴极射线管显示器Clarity清晰度combination key组合键cordless mouse无线鼠标data projector数据投影仪digital camera数码照相机Digital media player数字媒体播放器Digital music player数码音乐播放器digital video camera数码影像摄录机dot pitch点距dot-matrix printer针式打印机dots-per-inch (dpi)点每英寸dual-scan monitor双向扫描显示器dumb terminal哑终端e-book电子图书阅读器ergonomic keyboard人体工程学键盘Fax machine传真机flat-panel monitor平面显示器Flatbed scanner平板扫描仪flexible keyboard可变形键盘handwriting recognition software手写识别软件Headphones耳机high-definition television (HDTV)高清电视ink-jet printer喷墨打印机intelligent terminal智能终端Internet telephone网络电话Internet telephony网络电话IP Telephony IP电话Joystick游戏杆Keyboard键盘laser printer激光打印机light pen光笔Liquid crystal display(LCD)液晶显示器Magnetic card reader磁卡阅读器magnetic-ink character recognition (MICR)磁性墨水字符识别mechanical mouse机械鼠标Monitor显示器Mouse鼠标mouse pointer鼠标指针multifunction device (MFD)多功能设备network terminal网络终端numeric keypad数字小键盘optical-character recognition (OCR)光学字符识别optical-mark recognition (OMR)光学标记识别optical mouse光电鼠标Optical scanner光电扫描仪passive-matrix monitor无源矩阵显示器PDA keyboard PDA键盘personal laser printer个人激光打印机photo printer照片打印机picture elements 有效像素Pixel像素Pixel pitch像素间距platform scanner平版式扫描仪Plotter绘图仪pointing stick触控点portable printer便携式打印机portable scanner便携式扫描仪Printer打印机Radio frequency card reader射频卡阅读器Radio frequency identification(RFID)射频识别refresh rate刷新率Resolution分辨率roller ball滚动球shared laser printer共享激光打印机Speakers扬声器Stylus[stail?s]输入笔Technical writer技术文档编写员telephony[tilef?ni]电话Terminal终端thermal printer[θ?:m?l]热敏打印机thin client瘦客户端thin film transistor monitor (TFT)薄膜晶体管显示器toggle key[t?ɡl]切换键touch pad触控板touch screen触摸屏Trackball轨迹球traditional keyboard传统键盘Universal Product Code (UPC)同一产品编码voice-over IP (VoIP)网络电话voice recognition system语音识别系统wand reader棒式阅读器WebCam摄像头wheel button滚动键wireless keyboard无线键盘wireless mouse无线鼠标第八单元access speed存取速度Blu-Ray(BD)蓝光Capacity容量CD (compact disc)光盘CD-R (CD-recordable)可录式CDCD-ROM (compact disc-read only memory)光盘库CD-RW (compact disc rewritable)可重写CDCylinder[silind?]柱面Density密度direct access直接存取disk caching磁盘缓存DVD(digital versatile disc or digital video disc)DVD player DVD播放器DVD- R (DVD recordable)可录式DVDDVD +R (DVD recordable)可录式DVDDVD-RAM(DVD random-access memory)DVD随机存取器DVD-ROM(DVD random-read-only memory)DVD只读存储器DVD-ROM jukeboxDVD-RW (DVD rewritable)可重写DVDEnterprise storage system企业存储系统erasable optical disk可擦光盘file compression文件压缩file decompression文件解压缩File server文件服务器flash memory card闪存卡floppy disk软盘Floppy disk cartridge软盘盒floppy disk drive (FDD)软磁盘驱动器hard disk硬盘hard-disk cartridge硬盘盒hard-disk pack硬盘组HD DVD(high-definition DVD)高清DVDhead crash磁头碰撞Hi def(high definition)高清high capacity disk高容量磁盘internal hard disk内置硬盘Internet hard drive网络硬盘驱动器Label标签Land平地magnetic tape磁带magnetic tape reel磁带盒magnetic tape streamer磁带条Media多媒体optical disk光盘optical disk drive光盘驱动器Organizational Internet storage组织性网络存储PC Card hard disk PC卡硬盘Pit坑primary storage主存RAID system磁碟阵列系统Redundant array of inexpensive disks(RAID)廉价磁盘冗余阵列secondary storage辅存Sector扇区sequential access顺序存取Shutter滑盖Software engineer软件工程师solid-state storage固态存储器storage devices存储装置tape cartridge盒式带Track轨道USB drive USB驱动器write-protection notch写入保护缺口第九单元3G cellular networkanalog signal 模拟信号asymmetric digital subscriber line(ADSL)非对称数字用户线路Backbone中枢Bandwidth带宽base station基址bits per second位/秒Bluetooth 蓝牙Broadband宽带broadcast radio无线广播Bus总线bus network总线网络cable modem电缆调制解调器cellular service无线服务Client 客户client/server network system客户/服务网络系统coaxial cable同轴电缆communication channel 信道communication system 通信系统computer network计算机网络Connectivity连通性Demodulation 解调dial-up service拨号服务digital signal数字信号digital subscriber line (DSL)数字用户线路distributed data processing分布式数据处理系统distributed processing分布处理domain name server (DNS)域名服务Ethernet以太网external modem外置调制解调器Extranet外联网fiber-optic cable 光纤电缆Firewall防火墙global positioning system (GPS)全球卫星定位系统hierarchical network树型网络home network家庭网络host computer主机Hub集线器Infrared红外线internal modem 内置式调制解调器Intranet内联网IP address (Internet Protocol address)IP地址local area network (LAN)局域网low bandwidth低频带宽medium band 中频波段metropolitan area network (MAN) 城域网Microwave微波Modem调制解调器Modulation调制network administrator网络管理员network architecture网络体系结构network gateway 网关network hub 网络集线器network interface card (NIC)网络接口卡network operating system (NOS)网络操作系统Node 节点Packet 数据包PC card modem PC卡调制解调器peer-to-peer network system 对等网络系统Polling 轮流检测Protocol协议proxy server代理服务器ring network环型网络Satellite卫星satellite/air connection service卫星互连服务Server服务器star network 星型网络Strategy策略T1, T2, T3, T4 linestelephone line电话线terminal network 终端网络time-sharing system并发式系统Topology拓扑结构transfer rate传输率TCP/IP (transmission control protocol/Internet protocol)传输控制协议/因特网协议voiceband声音带宽wide area network (W AN)广域网Wi-FI (wireless fidelity)无限保真wireless LAN (WLAN)无线局域网wireless modem无线调制解调器wireless receiver无线接收器课后习题答案:Ch1: Ch6:bbabd,dacdd; eichafgbdj. dbcbb,aacbd; jachgidefb.Ch3: Ch7:dcbdd,abccb; jachbdiegf. Ababd,adcdb; iefjabgdch.Ch4: Ch8:aaaba,bcbab; igdecfhbja. dacac,acddc; gajidbhcfe.Ch5: Ch9:cdcaa,cbbac; gdfbghaeic. abadc,dbbbd; gbaidecjhf.中英文对照的ERP专业词汇介绍:B2C、B2B、ASP、APS、BOM、C/S、CAD、CAM、CPC、EDI、GUI、ISO、MIS、PM、SCM、SQL、TQM、line item、planned capacity、rated capacity、virtual warehouse……1 ABM Activity-based Management 基于作业活动管理2 AO Application Outsourcing 应用程序外包3 APICS American Production and Inventory Control Society,Inc 美国生产与库存管理协会4 APICS Applied Manufacturing Education Series 实用制造管理系列培训教材5 APO Advanced Planning and Optimization 先进计划及优化技术6 APS Advanced Planning and Scheduling 高级计划与排程技术7 ASP Application Service/Software Provider 应用服务/软件供应商8 ATO Assemble To Order 定货组装9 ATP Available To Promise 可供销售量(可签约量)10 B2B Business to Business 企业对企业(电子商务)11 B2C Business to Consumer 企业对消费者(电子商务)12 B2G Business to Government 企业对政府(电子商务)13 B2R Business to Retailer 企业对经销商(电子商务)14 BIS Business Intelligence System 商业智能系统15 BOM Bill Of Materials 物料清单16 BOR Bill Of Resource 资源清单17 BPR Business Process Reengineering 业务/企业流程重组18 BPM Business Process Management 业务/企业流程管理19 BPS Business Process Standard 业务/企业流程标准20 C/S Client/Server(C/S)\Browser/Server(B/S) 客户机/服务器\浏览器/服务器21 CAD Computer-Aided Design 计算机辅助设计22 CAID Computer-Aided Industrial Design 计算机辅助工艺设计23 CAM Computer-Aided Manufacturing 计算机辅助制造24 CAPP Computer-Aided Process Planning 计算机辅助工艺设计25 CASE Computer-Aided Software Engineering 计算机辅助软件工程26 CC Collaborative Commerce 协同商务27 CIMS Computer Integrated Manufacturing System 计算机集成制造系统28 CMM Capability Maturity Model 能力成熟度模型29 COMMS Customer Oriented Manufacturing Management System 面向客户制造管理系统30 CORBA Common Object Request Broker Architecture 通用对象请求代理结构31 CPC Collaborative Product Commerce 协同产品商务32 CPIM Certified Production and Inventory Management 生产与库存管理认证资格33 CPM Critical Path Method 关键线路法34 CRM Customer Relationship Management 客户关系管理35 CRP capacity requirements planning 能力需求计划36 CTI Computer Telephony Integration 电脑电话集成(呼叫中心)37 CTP Capable to Promise 可承诺的能力38 DCOM Distributed Component Object Model 分布式组件对象模型39 DCS Distributed Control System 分布式控制系统40 DMRP Distributed MRP 分布式MRP41 DRP Distribution Resource Planning 分销资源计划42 DSS Decision Support System 决策支持系统43 DTF Demand Time Fence 需求时界44 DTP Delivery to Promise 可承诺的交货时间45 EAI Enterprise Application Integration 企业应用集成46 EAM Enterprise Assets Management 企业资源管理47 ECM Enterprise Commerce Management 企业商务管理48 ECO Engineering Change Order 工程变更订单49 EDI Electronic Data Interchange 电子数据交换50 EDP Electronic Data Processing 电子数据处理51 EEA Extended Enterprise Applications 扩展企业应用系统52 EIP Enterprise Information Portal 企业信息门户53 EIS Executive Information System 高层领导信息系统54 EOI Economic Order Interval 经济定货周期55 EOQ Economic Order Quantity 经济订货批量(经济批量法)56 EPA Enterprise Proficiency Analysis 企业绩效分析57 ERP Enterprise Resource Planning 企业资源计划58 ERM Enterprise Resource Management 企业资源管理59 ETO Engineer To Order 专项设计,按订单设计60 FAS Final Assembly Schedule 最终装配计划61 FCS Finite Capacity Scheduling 有限能力计划62 FMS Flexible Manufacturing System 柔性制造系统63 FOQ Fixed Order Quantity 固定定货批量法64 GL General Ledger 总账65 GUI Graphical User Interface 图形用户界面66 HRM Human Resource Management 人力资源管理67 HRP Human Resource Planning 人力资源计划68 IE Industry Engineering/Internet Exploration 工业工程/浏览器69 ISO International Standard Organization 国际标准化组织70 ISP Internet Service Provider 互联网服务提供商71 ISPE International Society for Productivity Enhancement 国际生产力促进会72 IT/GT Information/Group Technology 信息/成组技术73 JIT Just In Time 准时制造/准时制生产74 KPA Key Process Areas 关键过程域75 KPI Key Performance Indicators 关键业绩指标76 LP Lean Production 精益生产77 MES Manufacturing Executive System 制造执行系统78 MIS Management Information System 管理信息系统79 MPS Master Production Schedule 主生产计划80 MRP Material Requirements Planning 物料需求计划81 MRPII Manufacturing Resource Planning 制造资源计划82 MTO Make To Order 定货(订货)生产83 MTS Make To Stock 现货(备货)生产84 OA Office Automation 办公自动化85 OEM Original Equipment Manufacturing 原始设备制造商86 OPT Optimized Production Technology 最优生产技术87 OPT Optimized Production Timetable 最优生产时刻表88 PADIS Production And Decision Information System 生产和决策管理信息系统89 PDM Product Data Management 产品数据管理90 PERT Program Evaluation Research Technology 计划评审技术91 PLM Production Lifecycle Management 产品生命周期管理92 PM Project Management 项目管理93 POQ Period Order Quantity 周期定量法94 PRM Partner Relationship Management 合作伙伴关系管理95 PTF Planned Time Fence 计划时界96 PTX Private Trade Exchange 自用交易网站97 RCCP Rough-Cut Capacity Planning 粗能力计划98 RDBM Relational Data Base Management 关系数据库管理99 RPM Rapid Prototype Manufacturing 快速原形制造100 RRP Resource Requirements Planning 资源需求计划101 SCM Supply Chain Management 供应链管理102 SCP Supply Chain Partnership 供应链合作伙伴关系103 SFA Sales Force Automation 销售自动化104 SMED Single-Minute Exchange Of Dies 快速换模法105 SOP Sales And Operation Planning 销售与运作规划106 SQL Structure Query Language 结构化查询语言107 TCO Total Cost Ownership 总体运营成本108 TEI Total Enterprise Integration 全面企业集成109 TOC Theory Of Constraints/Constraints managemant 约束理论/约束管理110 TPM Total Productive Maintenance 全员生产力维护111 TQC Total Quality Control 全面质量控制112 TQM Total Quality Management 全面质量管理113 WBS Work Breakdown System 工作分解系统114 XML eXtensible Markup Language 可扩展标记语言115 ABC Classification(Activity Based Classification) ABC分类法116 ABC costing 作业成本法117 ABC inventory control ABC 库存控制118 abnormal demand 反常需求119 acquisition cost ,ordering cost 定货费120 action message 行为/活动(措施)信息121 action report flag 活动报告标志122 activity cost pool 作业成本集123 activity-based costing(ABC) 作业基准成本法/业务成本法124 actual capacity 实际能力125 adjust on hand 调整现有库存量126 advanced manufacturing technology 先进制造技术127 advanced pricing 高级定价系统128 AM Agile Manufacturing 敏捷制造129 alternative routing 替代工序(工艺路线)130 Anticipated Delay Report 拖期预报131 anticipation inventory 预期储备132 apportionment code 分摊码133 assembly parts list 装配零件表134 automated storage/retrieval system 自动仓储/检索系统135 Automatic Rescheduling 计划自动重排136 available inventory 可达到库存137 available material 可用物料138 available stock 达到库存139 available work 可利用工时140 average inventory 平均库存141 back order 欠交(脱期)订单142 back scheduling 倒排(序)计划/倒序排产?143 base currency 本位币144 batch number 批号145 batch process 批流程146 batch production 批量生产147 benchmarking 标杆瞄准(管理)148 bill of labor 工时清单149 bill of lading 提货单150 branch warehouse 分库151 bucketless system 无时段系统152 business framework 业务框架153 business plan 经营规划154 capacity level 能力利用水平155 capacity load 能力负荷156 capacity management 能力管理157 carrying cost 保管费158 carrying cost rate 保管费率159 cellular manufacturing 单元式制造160 change route 修改工序161 change structure 修改产品结构162 check point 检查点163 closed loop MRP 闭环MRP164 Common Route Code(ID) 通用工序标识165 component-based development 组件(构件)开发技术166 concurrent engineering 并行(同步)工程167 conference room pilot 会议室模拟168 configuration code 配置代码169 continuous improvement 进取不懈170 continuous process 连续流程171 cost driver 作业成本发生因素172 cost driver rate 作业成本发生因素单位费用173 cost of stockout 短缺损失174 cost roll-up 成本滚动计算法175 crew size 班组规模176 critical part 急需零件177 critical ratio 紧迫系数178 critical work center 关键工作中心179 CLT Cumulative Lead Time 累计提前期180 current run hour 现有运转工时181 current run quantity 现有运转数量182 customer care 客户关怀183 customer deliver lead time 客户交货提前期184 customer loyalty 客户忠诚度185 customer order number 客户订单号186 customer satisfaction 客户满意度187 customer status 客户状况188 cycle counting 周期盘点189 DM Data Mining 数据挖掘190 Data Warehouse 数据仓库191 days offset 偏置天数192 dead load 空负荷193 demand cycle 需求周期194 demand forecasting 需求预测195 demand management 需求管理196 Deming circle 戴明环197 demonstrated capacity 实际能力198 discrete manufacturing 离散型生产199 dispatch to 调度200 DRP Distribution Requirements Planning 分销需求计划201 drop shipment 直运202 dunning letter 催款信203 ECO workbench ECO工作台204 employee enrolled 在册员工205 employee tax id 员工税号206 end item 最终产品207 engineering change mode flag 工程变更方式标志208 engineering change notice 工程变更通知209 equipment distribution 设备分配210 equipment management 设备管理211 exception control 例外控制212 excess material analysis 呆滞物料分析213 expedite code 急送代码214 external integration 外部集成215 fabrication order 加工订单216 factory order 工厂订单217 fast path method 快速路径法218 fill backorder 补足欠交219 final assembly lead time 总装提前期220 final goods 成品221 finite forward scheduling 有限顺排计划222 finite loading 有限排负荷223 firm planned order 确认的计划订单224 firm planned time fence 确认计划需求时界225 FPR Fixed Period Requirements 定期用量法226 fixed quantity 固定数量法227 fixed time 固定时间法228 floor stock 作业现场库存229 flow shop 流水车间230 focus forecasting 调焦预测231 forward scheduling 顺排计划232 freeze code 冻结码233 freeze space 冷冻区234 frozen order 冻结订单235 gross requirements 毛需求236 hedge inventory 囤积库存237 in process inventory 在制品库存238 in stock 在库239 incrementing 增值240 indirect cost 间接成本241 indirect labor 间接人工242 infinite loading 无限排负荷243 input/output control 投入/产出控制244 inspection ID 检验标识245 integrity 完整性246 inter companies 公司内部间247 interplant demands 厂际需求量248 inventory carry rate 库存周转率249 inventory cycle time 库存周期250 inventory issue 库存发放251 inventory location type 仓库库位类型252 inventory scrap 库存报废量253 inventory transfers 库存转移254 inventory turns/turnover 库存(资金)周转次数255 invoice address 发票地址256 invoice amount gross 发票金额257 invoice schedule 发票清单258 issue cycle 发放周期259 issue order 发送订单260 issue parts 发放零件261 issue policy 发放策略262 item availability 项目可供量263 item description 项目说明264 item number 项目编号265 item record 项目记录266 item remark 项目备注267 item status 项目状态268 job shop 加工车间269 job step 作业步骤270 kit item 配套件项目271 labor hour 人工工时272 late days 延迟天数273 lead time 提前期274 lead time level 提前期水平275 lead time offset days 提前期偏置(补偿)天数276 least slack per operation 最小单个工序平均时差277 line item 单项产品278 live pilot 应用模拟279 load leveling 负荷量280 load report 负荷报告281 location code 仓位代码282 location remarks 仓位备注283 location status 仓位状况284 lot for lot 按需定货(因需定量法/缺补法)285 lot ID 批量标识286 lot number 批量编号287 lot number traceability 批号跟踪288 lot size 批量289 lot size inventory 批量库存290 lot sizing 批量规划291 low level code 低层(位)码292 machine capacity 机器能力293 machine hours 机时294 machine loading 机器加载295 maintenance ,repair,and operating supplies 维护修理操作物料296 make or buy decision 外购或自制决策297 management by exception 例外管理法298 manufacturing cycle time 制造周期时间299 manufacturing lead time 制造提前期300 manufacturing standards 制造标准301 master scheduler 主生产计划员302 material 物料303 material available 物料可用量304 material cost 物料成本305 material issues and receipts 物料发放和接收306 material management 物料管理307 material manager 物料经理308 material master,item master 物料主文件309 material review board 物料核定机构310 measure of velocity 生产速率水平311 memory-based processing speed 基于存储的处理速度312 minimum balance 最小库存余量313 Modern Materials Handling 现代物料搬运314 month to date 月累计315 move time , transit time 传递时间316 MSP book flag MPS登录标志317 multi-currency 多币制318 multi-facility 多场所319 multi-level 多级320 multi-plant management 多工厂管理321 multiple location 多重仓位322 net change 净改变法323 net change MRP 净改变式MRP324 net requirements 净需求325 new location 新仓位326 new parent 新组件327 new warehouse 新仓库328 next code 后续编码329 next number 后续编号330 No action report 不活动报告331 non-nettable 不可动用量332 on demand 急需的333 on-hand balance 现有库存量334 on hold 挂起335 on time 准时336 open amount 未清金额337 open order 未结订单/开放订单338 order activity rules 订单活动规则339 order address 订单地址340 order entry 订单输入341 order point 定货点342 order point system 定货点法343 order policy 定货策略344 order promising 定货承诺345 order remarks 定货备注346 ordered by 定货者347 overflow location 超量库位348 overhead apportionment/allocation 间接费分配349 overhead rate,burden factor,absorption rate 间接费率350 owner's equity 所有者权益351 parent item 母件352 part bills 零件清单353 part lot 零件批次354 part number 零件编号355 people involvement 全员参治356 performance measurement 业绩评价357 physical inventory 实际库存358 picking 领料/提货359 planned capacity 计划能力360 planned order 计划订单361 planned order receipts 计划产出量362 planned order releases 计划投入量363 planning horizon 计划期/计划展望期364 point of use 使用点365 Policy and procedure 工作准则与工作规程366 price adjustments 价格调整367 price invoice 发票价格368 price level 物价水平369 price purchase order 采购订单价格370 priority planning 优先计划371 processing manufacturing 流程制造372 product control 产品控制373 product family 产品系列374 product mix 产品搭配组合375 production activity control 生产作业控制376 production cycle 生产周期377 production line 产品线378 production rate 产品率379 production tree 产品结构树380 PAB Projected Available Balance 预计可用库存(量) 381 purchase order tracking 采购订单跟踪382 quantity allocation 已分配量383 quantity at location 仓位数量384 quantity backorder 欠交数量385 quantity completion 完成数量386 quantity demand 需求量387 quantity gross 毛需求量388 quantity in 进货数量389 quantity on hand 现有数量390 quantity scrapped 废品数量391 quantity shipped 发货数量392 queue time 排队时间393 rated capacity 额定能力394 receipt document 收款单据395 reference number 参考号396 regenerated MRP 重生成式MRP397 released order 下达订单398 reorder point 再订购点399 repetitive manufacturing 重复式生产(制造)400 replacement parts 替换零件401 required capacity 需求能力402 requisition orders 请购单403 rescheduling assumption 重排假设404 resupply order 补库单405 rework bill 返工单406 roll up 上滚407 rough cut resource planning 粗资源计划408 rounding amount 舍入金额409 run time 加工(运行)时间410 safety lead time 安全提前期411 safety stock 安全库存412 safety time 保险期413 sales order 销售订单414 scheduled receipts 计划接收量(预计入库量/预期到货量) 415 seasonal stock 季节储备416 send part 发送零件417 service and support 服务和支持418 service parts 维修件419 set up time 准备时间420 ship address 发运地址421 ship contact 发运单联系人422 ship order 发货单423 shop calendar 工厂日历(车间日历)424 shop floor control 车间作业管理(控制)425 shop order , work order 车间订单426 shrink factor 损耗因子(系数)427 single level where used 单层物料反查表428 standard cost system 标准成本体系429 standard hours 标准工时430 standard product cost 标准产品成本431 standard set up hour 标准机器设置工时432 standard unit run hour 标准单位运转工时433 standard wage rate 标准工资率434 status code 状态代码435 stores control 库存控制436 suggested work order 建议工作单437 supply chain 供应链438 synchronous manufacturing 同步制造/同期生产439 time bucket 时段(时间段)。
英语课文翻译 2008 影印 部分

手持电脑系统单元更小并且设计适合放入一只手内。这些系统包含全部的计算机系统,包括电子部件,可选择的二级存储设备和输入输出设备。个人数字助理是最广泛使用的手持式电脑。
system board 系统板
系统板也被称为母板。系统板是整个计算机系统的通信媒介。每一个系统单元的组成部件连接到系统板上。作为数据通路允许不同的部件访问另一个部件。外设,例如键盘,鼠标和显示器若没有系统板是不能访问系统单元的。
sockets 插孔
插孔为小的专门的电子零件称为芯片提供连接点。芯片由微小的电路板构成蚀刻在像沙的材料的平方上面称为硅。这些电路板可能比手指的指尖还要小。芯片也被称为硅片,半导体,或者集成电路。芯片被控制在封装载体上。这些包无论是直接插入系统板的插座或插入卡内然后插入系统板的插槽上。插座是用来连接系统板,以各种不同类型的芯片,包括微处理器和存储芯片。
mechanical mouse 机械鼠标
机械鼠标一般被认为是传统类并且是当然最广泛使用的。它的底下有一个球和一条电源线连接到系统单元。当你移动它在光滑的表面上,滚球旋转并且控制在屏幕上的指针。
joystick 游戏杆
游戏杆是计算机游戏中最受欢迎的输入设备。你可以通过变换压力,速度和游戏杆的方向来控制游戏的操作。其它的控制,例如按钮和触发器是用于指定命令或者启动特定操作。
search engines 搜索引擎
搜索引擎是一个专业的程序用来帮助你在web和因特网上查询信息。要寻找信息,你可以到搜索服务网站并且使用搜索引擎。例如,Yahoo的搜索引擎。这种搜索引擎,类似于其它的,提供了两不同的搜索检索方式。
Key terms

Key TermsChapter 1General Agreement on Trade in Services服务贸易总协定Domestic regulation国内规制Individual service providers个人服务供应商Non-preferential treatment非特惠待遇MFN 最惠国待遇Public monopolies公共垄断Natural monopoly自然垄断Inadequate information信息不充分Externality 外部性Universal access普遍获得性Regulatory harmonization 监管协调Temporary migration 临时性移民NAFTA北美自由贸易区Chapter 2Business services 商业服务Communication services 通信服务Construction services建筑服务Distribution services 分销服务Educational services教育服务Environmental services 环境服务Financial services金融服务Health-related and social services健康与社会服务Tourism and travel-related services旅游服务Recreational, cultural and sporting services娱乐、文化与体育服务Transport services运输服务Government-mandated regulators 政府委托的监管部门Schedule of commitment承诺表Non-scheduled sectors非承诺部门Market access 市场准入National treatment 国民待遇Quota-type limits 数量限制Joint venture requirements合资企业要求Foreign capital participation外国资本参与Foreign equity ceilings 外国股权限制Foreign land ownership外国土地所有权Discriminatory training requirements歧视性培训要求Regulatory disciplines监管规则Competitive safeguards竞争保护Transparency and institutional obligations透明性和制度性义务Horizontal Commitments水平承诺Sector Commitments部门承诺Discriminatory restrictions 歧视性限制Phase-in Commitments阶段性承诺Modification or Suspension of Commitments承诺的修改与取消Council for Trade in Services 服务贸易委员会Balance-of-payments difficulties国际收支困难Conditional obligations & unconditional obligations 有条件和无条件承诺Objective and transparent criteria客观性与透明性标准Market failure 市场失灵Natural monopolies or oligopolies自然垄断与寡头垄断Asymmetric information信息不对称2Guidelines and Procedures for the Negotiations on Trade in Services国际服务贸易谈判指南与程序Modalities and Procedures模式与程序Chapter 3Discriminatory taxes 歧视性税收Domestic regulations 国内规制Trade barriers贸易壁垒Physical proximity实质靠近comparative advantage比较优势increasing returns to scale规模报酬递增lock-in锁定market-niche effect市场细分效应Agglomeration effect集聚效应A general concentration综合性集聚The specialized concentration专业性集聚Cores and peripheries structure中心外围结构spillover effects溢出效应labor-intensive services劳动密集型服务Modes of Supply as Substitutes供给模式的替代性Modes of Supply as Complements供给模式的互补性Instruments of Protection保护工具NTBs非关税贸易壁垒Government procurement policies政府采购政策lack of transparency of domestic regulations国内监管缺乏透明性Licensing and certification requirements许可和证书要求the firm-specific fixed costs 企业特定固定成本3The plant-level fixed costs工厂固定成本Chapter 4The Manual on Statistics of International Trade in Services国际服务贸易统计手册BOP statistics 国际收支平衡统计EBOPS扩展的国际收支平衡统计IMF Balance of Payments Manual国际货币基金国际收支手册Foreign Affiliates Trade in Services (FATS) statistics外国附属机构服务贸易统计Residents and non-residents Transactions 居民与非居民交易A product-based classification以产品基础分类Geographical allocations of the statistics按地理分类统计Trading partners贸易伙伴Resident affiliates of foreign firms (inward FATS)外国企业的国内附属机构Affiliates abroad of resident firms (outward FATS)本国企业的国外附属机构establishment-level statistics 分支机构层面的统计enterprise-level statistics企业层面的统计Net operating surplus营业盈余净额Gross fixed capital formation固定资本形成总值The geographical breakdown 地理分类The industrial activity breakdown 产业分类Services Product breakdown服务产品分类Temporary nature of the movement of natural persons暂时性人员流动Intra-corporate transferees公司内部转移4Chapter 5Tariff equivalent关税等价Measurements of trade barriers贸易壁垒度量Price and quantity measurements基于价格与数量的衡量方法Ad valorem tax从价税Entry regulations 进入限制Operations regulations经营限制Discriminatory and nondiscriminatory regulations 歧视性与非歧视性规制Regulations of ongoing operations对经营的规制Ownership and control restrictions所有权与控制权限制Chapter 6FTA自贸区Regional trade agreements (RTAs)区域贸易协定Services-trade liberalization服务贸易自由化Economics of regional integration区域一体化的经济学Regulatory cooperation 监管合作Multilateral disciplines on regional agreements 区域协议的多边规则The criteria for regional agreements区域协议的标准Detrimental to non-members对非成员方的损害Preferential agreements优惠协议Preferential treatment优惠待遇Preferential Liberalization of Services Trade服务贸易的特惠制自由化Rules of origin on investment投资来源地规则Location-specific sunk costs区位特定沉淀成本5Infant industry argument幼稚产业论Regulatory convergence or harmonization规则趋同与协调Restriction on services output or on the number of service providers 服务贸易产量与服务者数量限制Allocation of the quota to a preferred source来源于配额分配的优惠Protectionist instrument 保护的工具Welfare-enhancing福利改进Deter new entrants阻止新的进入者The commitment value承诺价值Capital depreciates资本折旧The first-mover advantage 先发优势Inferior supplier劣质供给商The Merge & acquisition(M&Ac)并购Learning by doing干中学A trade-off between scale economies and competition规模经济与竞争的折衷Dynamic economies of scale 动态规模经济Constellation of vested interests利益集团Optimum regulatory areas最优监管区域Adverse effects on non-members and on the multilateral trading system 对非成员和多边贸易体系的负面影响Services trade and investment liberalization服务贸易和投资自由化emergency safeguards紧急保障Establishment right开业权T he positive list or ‘bottom-up’ approach正面列表或自下而上的方法The negative list or top-down approach负面清单或自上而下的方法Non-conforming measures不符点6Domestic policy dialogue国内政策对话Ratchet mechanism棘轮效应Chapter 7Financial services providers (FSPs)金融供给商Financial intermediaries金融中介Brokerages and securities firms经纪商与券商The primary and secondary markets初级与二级市场Deregulation of domestic financial services放松国内金融管制Withdrawal of government intervention取消政府干预Privatizing state-owned banks国有银行私有化Freeing key prices to be market-determined主要价格由市场决定Removal of restrictions on intra-sectoral activities取消混业经营限制Financial services liberalization金融服务自由化Policy coherence政策一致性Trade policy reform贸易政策改革Domestic financial reform国内金融改革Capital account opening资本账户开放Catalysts for Domestic Reform国内改革的催化剂Resilient in the face of shocks面对冲击的弹性Efficiency of credit allocation信贷配给效率The access of low-income savers and borrowers to financial services 低收入借贷者对金融服务的可获得性Permitting foreign entry and full equity participation允许外资进入和全部股权Binding at the status quo绑定现状Grandfathering溯往原则7Chapter 8Credible threat of replacement by a rival被竞争对手替代的可值信性威胁Input to downstream services下游服务的投入Segments of infrastructure industries基础设施的分解Electricity transmission 电力传送Generation and retail distribution电力生产与分销Local loop 当地回路Cellular services移动电话服务Runways and landing rights起飞与着陆权Ground-handling services机场服务Competitive upstream or downstream activities上游或下游竞争的服务Competitive segment is downstream of the bottleneck facility 竞争部分位于瓶颈设施下游Competition is upstream of the bottleneck facility竞争部分位于瓶颈设施上游Access to the monopoly input垄断投入的可获得性Access to a bottleneck facility瓶颈设施的可获得性Pricing the services of a natural monopoly facility自然垄断设施服务定价Two-part pricing两步定价Access to infrastructure基础设施的可获得性Structural separation of the generation and transmission facilities 发电与电力传输的结构性分解Long-term contracts长期合同Problem of lock-in 锁定问题A wholesale pricing pool批发定价池8Chapter 9Local operations当地企业Congestion and environmental problems 拥挤和环境问题Local collection systems 本地收集系统A hub point运输中心Hubs and a series of spokes中心-辐射结构Economies of density密度效应Capacity Building能力建设Chapter 10Basic Telecommunications Agreement (BTA)基础电信协议Wired networks有线网络Economies of scale and scope in networks网络的规模经济和范围经济Private leased circuit私人租赁电路Transmission capacity传输能力network infrastructure 网络基础设施Wireless-mobile systems 无线移动系统Interconnection policy互联政策Interconnection Consensus 互联许可Phasing out the obligation逐渐实现的义务Interconnecting wired and wireless networks互联有线和无线网络Wireless resale operators 无线转售运营商Reference Paper 参考文件Universal service平台服务International Telecommunications Union (ITU)国际电信联盟The transfer price转移价格9Settlement rate结算率Accounting rates分账率End-to- end services终端对终端服务Spectrum Allocation 频谱分配Spectrum licenses频谱许可10。
IBM Impact 2008 展会邀请函说明书

Dear IBM Business Partner,We are pleased to invite you to exhibit at Impact 2008 in Las Vegas, April 6 -11, 2008 at the MGM Grand. More than 6,000 IBM Customers and Business Partners are expected to join us in accelerating the pace for innovation. This annual conference on Service Oriented Architecture (SOA) offers an ideal venue for:• Unparalleled technical education about SOA and IBM thought leadership• Networking with key customers• Developing sales opportunitiesImpact 2008 will put you in touch with the customers and Business Partners you want to reach.The exhibit floor at Impact 2007 in Orlando sold out very quickly and we expect it to do the same for Impact 2008. Do not miss this GREAT opportunity to network, showcase your solutions, meet key customers, spend time with IBM developers, marketing and sales teams, learn a lot, and have some fun in the process!We are delighted to offer these exciting Impact 2008 Sponsorships to help you get the most out of your con-ference experience and get a jumpstart on new 2008 opportunities. We listened to your feedback and made significant changes to the Impact 2008 sponsorships including more exhibit space, enhanced pedestals, im-proved solution center hours, better customer draws to the Solution Center, Exhibitor-Only Passes, and more!Ifyouhaveanyquestions,*******************************************************************.I personally look forward to seeing you at Impact 2008! Don’t miss this signature SOA business event. Spaceis limited so reserve your space in the Solution Center early!Thanks for your continued support. See you in Las Vegas!John B. GordonDirector of Channels MarketingIBM SOA and WebSphere SoftwareThe Advantage of ImpactIf you were among the 500 Business Partners who attended Impact 2007 you know what an exciting event this is. In its first year, the conference drew more than 4,000 attendees and featured more than 500 sessions—both technical education and business leadership tracks. There were over 100 customer and Business Partner speakers, more than 1,000 complimentary certification exams and more than 40 Birds of a Feather sessions. At the hub of the networking activities was our SOLD OUT Solution center, featuring over 40 Business Partner Sponsors and more than 30 IBM demos. With over 200 press articles within 48 hours, 30 Business Partner press releases, including 100 analysts attending the event, this year’s event was a great success! Impact 2008 promises to be even greater with expected attendance to reach 6,000.A Unique Opportunity• Showcase your solutions at the premier event in the industry, with over 6,000 attendees• Take advantage of invaluable networking opportunities with customers, industry experts, peersand IBM executives• Generate revenue by negotiating and closing existing deals—nearly one-third of attendees will beLine of Business and IT decision makers!• Generate leads and increase sales• Gain insight into IBM’s WebSphere and SOA strategy and vision• Differentiate yourself in your markets by learning more about the full breadth of WebSphere andSOA technologiesThe Solution Center• THE place to close business and showcase your solution• Exhibitor hours include dedicated time in the program including two evening receptions• Multiple sponsorship opportunitiesDATES TIMES DETAILS-Business Partner Day – Sunday April 6, 2008• Participate in this special one-day event, just for IBM Business Partners• Learn about unique Business Partner programs and current initiatives• Hear from the IBM Software Group Executive Management Team• Discover how IBM can help you maximize your business resultsFor more informationShould you have any questions about sponsorships, please contact Linda Wolfe at 781-251-7717 or via e-mail *******************************.Ready to purchase your Impact 2008 Sponsorship? Visit the Impact 2008 Web site.Sponsorship and Exhibit OpportunitiesDIAMOND LEVEL• Early Bird Fee$80,000 Prior to January 31, 2008$96,000 January 31, 2008The deadline for applications is February 29, 2008Applications received after this date will be subject to rush charges.PLATINUM LEVEL• Early Bird Fee$70,000 Prior to January 31, 2008$84,000 January 31, 2008The deadline for applications is February 29, 2008Applications received after this date will be subject to rush charges.GOLD LEVEL• Early Bird Fee$50,000 Prior to January 31, 2008$60,000 January 31, 2008The deadline for applications is February 29, 2008Applications received after this date will be subject to rush charges.SILVER LEVEL• Early Bird Fee$20,000 Prior to January 31, 2008$24,000 January 31, 2008The deadline for applications is February 29, 2008Applications received after this date will be subject to rush charges.© Copyright IBM Corporation 2007IBM Corporation1 North Castle DriveArmonk, NY 10504U.S.A.Produced in the United States of America11-07All Rights ReservedIBM, , and the IBM logo are trademarks of International Business Machines Corporation in the United States, other countries or both.Other company, product or service names may be trademarks or service marks of others.。
计算机专业英语影印版(Computing Essentials 2008课后答案大全)第三单元Basic Application Software
Crossword Puzzle Answers:Open Ended Questions:1.Explain the difference between general-purpose and special-purpose applications.General-purpose applications are widely used in nearly every discipline and occupation. They include word processors, spreadsheets, database management systems, and presentation graphics.special-purpose applications are more narrowly focused on specific disciplines and occupations, such as graphics programs, audio and video editors,2.Discuss the common features of most software programs. Describe the new interfaceintroduced with 2007 Microsoft Office.The newest Office version, 2007 Microsoft Office, has a redesigned interface that is intended to make it easier for users to find and use all the features of an application. This new designintroduces ribbons, contextual tabs, galleries, and more.• Ribbons replace menus and toolbars by organizing commonly used commands into a set of tabs.These tabs display command buttons that are the most relevant to the tasks being performed by the user.• Contextual tabs are tabs that appear automatically. These tabs only appear when they are needed and anticipate the next operations to be performed by the user.• Galleries simplify the process of making a selection from a list of alternatives. This isaccomplished by replacing many dialog boxes with visual presentations of potential results.This new interface is the first major change in over a decade.3.What is the difference between a function and a formula? How is a formula related to what-if analysis?A formula is an instruction to calculate or process. Functions are prewritten formulas providedby the spreadsheet program that perform calculations such as adding a series of cells. If a change is made to one or more numbers in a spreadsheet, all related formulas will automaticallyrecalculate and charts will be recreated. Observing these changes is what-if analysis.4.What are presentation graphics programs? How are they used?Presentation graphics are programs that combine a variety of visual objects to create attractive, visually interesting presentations. They are excellent tools to communicate a message and to persuade people.5.What is the difference between an integrated package and a software suite? Whatare the advantages and disadvantages of each?An integrated package is a single program that provides the functionality of a wordprocessor, spreadsheet, database manager, and more. The primary disadvantage of an integrated package is that the capabilities of each function (such as word processing) are not as extensive as in the individual programs (such as Microsoft Word). The primary advantages are cost and simplicity.A software suite is a collection of separate application programs bundled together andsold as a group. While the applications function exactly the same whether purchased in a suite or separately, it is significantly less expensive to buy a suite of applications than to buy each application separately.1. Expanding Your Technology exercise #3 Shareware explores how shareware programswork and what the risks involved in using them are.2.Writing About Technology exercise #1 Acquiring Software asks the student to explorefive ways of acquiring software. And asks if it is wrong to obtain and use unauthorized software.Web Tools1.Applying Technology exercise #3 Corel WordPerfect Office Suite has the studentresearch the suite and compare/contrast it to the Microsoft Office suite. It asks thestudent to do critical thinking and decide which is better for them.2. Expanding Your Technology exercise #2 Sharing Data between Applications has thestudent research object linking and embedding. The student is asked to provide examples and be able to define the difference between linking and embedding.Software Tools1.Applying Technology exercise #1 Speech Recognition explores the technology of speechrecognition software. How it is configured and what are its uses. It asks them to writeabout the advantages and disadvantages of it.2.Applying Technology exercise #2 Presentation Graphics explores the requirements,features, and uses of a presentation graphics application found on the website.3.Applying Technology exercise #3 Corel WordPerfect Office Suite has the studentscompare and contrast the Corel Suite with the Microsoft Suite products, and asks them to choose one.Writing Skills1.Applying Technology exercise #1 Speech Recognition explores the technology of speechrecognition software. How it is configured and what are its uses. It asks them to writeabout the advantages and disadvantages of it.2.Applying Technology exercise #3 Corel WordPerfect Office Suite has the studentscompare and contrast the Corel Suite with the Microsoft Suite products, and asks them to choose one.3.Expanding Your Knowledge exercise #1 How Speech Recognition Works has the studentexplore how speech recognition could enhance applications and to describe a profession that could benefit from it.4.Expanding Your Technology exercise #3 Shareware explores how shareware programswork and what the risks involved in using them are.5.Writing About Technology exercise #1 Acquiring Software asks the student to explorefive ways of acquiring software. And asks if it is wrong to obtain and use unauthorized software.6.Writing About Technology exercise #2 Software Standards has the student explore theissue of standardization of computer software. It asks them to find out about therequirements of certifications and how compliance is handled.。
考研英语阅读翻译-2008Text1

2008 Text 1在现代生活中女性就算是在某些领域可以追赶上男性,但至少在一个方面是领先的,尽管是她们不太想要的。
纽约的退伍军管理医院精神科首席医生Yehuda博士说道,和男性相比,女性面对压力时,更容易受到影响,导致抑郁和紧张。
对于动物和人类的研究都显示出性激素会在某种程度去影响面对压力的反应,导致在同样的条件下,女性产生更多的致病化学物质。
在几项研究中,当受到压力的雌鼠的卵巢(雌性的生殖器官)被拿掉后,它们的化学反应变得和那些雄性的一样了。
对于女性来说,除了产生更多的导致压力的化学物质外,她们产生压力的“机会”也更多。
“并不是女性要处理的事情太少,而是她们有更多的事情要处理。
”Yehuda博士说道。
“她们对于压力的承受能力有时候甚至比男性的还大”,她观察到,“她们只是需要处理的事情太多,看起来会更容易精疲力尽。
”Yehuda博士注意到了另一个男女之间的不同点。
“我认为,女性通常要做的事是慢性的,重复的。
而男人去战场,承受的是格斗的压力。
男性面临的更多的是随意的身体上的暴力。
女性面对的人与人之间的暴力是在家庭环境中的。
不幸的是,她们与父母还有其他的家庭成员之间不是能够一次性解决的问题。
这种长期的关系的磨合是更有破坏性的。
Adeline Alvarez 18岁结婚并生了个儿子,但她决定完成大学学业。
“我尽了很大的努力拿到大学学位,因为我在实际生活中有很多的挫折,而这就是我的逃避,去学校,争取上游,做到更好。
”不久后,她离了婚变成一个单亲母亲。
“除了照顾一个十几岁的孩子,还要工作,付房租,养车,还债是最难的事情了。
我的生活就是不停的支付自己的账单。
”不是每个人经历着和Alvarez describes一样的长期的压力,但是大多数女性都在处理着太多的责任,很少得到喘息,从而感到了压力。
Alvarez的经历证明了当压力威胁你的健康和正常生理功能之前解压是非常重要的。
21.下面的哪一项符合文章的前两段?[A] 妇女在生理上更容易受到压力的影响。
2008影印版考点翻译

CHAPTER 11.SOFTWARE (P7)Software, as we mentioned(提到的), is another name for programs. Programs are the instructions(指令)that tell the computer how to process data into the form you want. In most cases, the words software and programs are interchangeable(可以互换的). There are two major kinds of software: system software and application(应用软件) software. You can think of application software as the kind you use. Think of system software as the kind the computer uses.软件,正如我们所提到的,它的另外一个名字叫程序。
程序是告诉计算机如何按照你的想法处理数据的一系列指令集。
在大多数情况下,软件和程序是可以互换。
主要有两个不同种类的软件:系统软件和应用程序软件。
你可以认为软件是你使用的那类,系统软件就是给电脑使用的那类。
2. (P11)System unit: The system unit is a container(容器) that houses(装载/收藏)most of the electric components(组件)that make up(组成)a computer system. Two important components of the system unit are the microprocessor(微处理器) and memory(内存). The microprocessor controls(控制)and manipulates(处理)data to produce information. Many times the microprocessor is contained(放置)within a protective(受保护的) cartridge(盒子). Memory, also known as primary storage(主存) or random access memory (RAM)(随机存取存储器), holds(保存) data and program instructions(指令) for processing the data. It also holds the processed information before it is output. Memory is sometimes referred to as temporary(暂时的) storage because its contents will typically be lost if the electrical power to the computer is disrupted(消失).系统单元:系统单元是一个装满许多电子组件的容器,构成一个计算机系统。
2008 - Chapter 5

123Chapter 5 Overview•Importance of Information Security Management•Logical Access Exposures and Controls•Network Infrastructure Security•Auditing Information Security Management and Logical Access Issues and Exposures•Auditing Network Infrastructure Security•Environmental Exposures and Controls•Physical Access Exposures and Controls•Personal Computer “LAPTOP”Security (Logical/Physical) Access Issues4Chapter 5 Exam Content Area“Protection of information assets—Provide assurance that the security architecture (policies, standards, procedures andcontrols) ensures the confidentiality, integrity and availabilit y of information assets.”5Chapter 5 Summary6Importance of Information Security Management7Importance of Information Security Management•Security Objectives to Meet Organization’s Business Requirements–Ensure the integrity of the information stored on their computer systems–Preserve the confidentiality of sensitive data–Ensure the continued availability of their information systems–Ensure conformity to applicable laws, regulations and standards8Importance of Information Security Management•Key Elements of Information Security Management–Senior management commitment and support–Policies and procedures–Organization–Security awareness and education–Monitoring and compliance–Incident handling and response9Importance of Information Security Management•Roles and Responsibilities–Executive management–Process owners–Users–Data owners–Security committee–Security specialists/advisors–IT developers–IS auditors–External parties10Importance of Information Security Management•Data Classification Measures–Who has access rights and to what?–Who is responsible for determining the access rights and access levels?–What approvals are needed for access?11Importance of Information Security Management•Data classification operates on•System access•Security awareness and education•Monitoring and compliance•Incident handling and response12Importance of Information Security Management•Privacy issues and information security•The goals of a privacy impact assessment9Identifying the nature of personally identifiable information associated with business processes9Documenting the collection, use, disclosure and destruction of personally identifiable information9Providing management with a tool to make informed policy, operations and system design decisions based on anunderstanding of privacy risk and the options available for mitigating that risk13Importance of Information Security Management•Privacy issues and information security•The goals of a privacy impact assessment include: (cont.)9Creating a consistent format and structured process for analyzing both technical and legal compliance with relevantregulations9Ensuring that accountability for privacy issues is incorporated clearly incorporated into the project9Reducing revisions and retrofitting of the information systems for privacy compliance14Importance of Information Security Management15Importance of Information Security Management–Computer crime issues and exposures•Threats to business include the following:9Financial loss9Legal repercussions9Loss of credibility or competitive edge9Blackmail/industrial espionage9Disclosure of confidential, sensitive or embarrassing information9Sabotage16Importance of Information Security Management–Computer crime issues and exposures•Computer crime vs. computer abuse•“Crime”depending on statistics of the jurisdiction•Civil offense vs. criminal offence•When should a crime be suspected?17Importance of Information Security Management•Possible perpetrators include:•Hackers•Crackers•Employees (authorized or unauthorized)9IS personnel9End users•Former employees•Interested or educated outsiders•Part-time and temporary personnel•Vendors and consultants•Accidental ignorant18Logical Access Exposuresand Controls19Logical Access Exposures and Controls20Logical Access Exposures and Controls•Familiarization with the organization's IT environment–These layers are:9the network9operating system platform9database and application layers21Logical Access Exposures and Controls•Paths of Logical Access–General points of entry9Network connectivity9Remote access9Operator console9Online workstations or terminals22Logical Access Exposures and Controls•Logical Access Control Softwareprevents unauthorized access and modification to an organization’s sensitive data and use of systemcritical functions23Logical Access Exposures and Controls•Logical access control software functionality•General operating systems access control functions include:9User identification and authentication mechanisms9Restricted logon IDs9Rules for access to specific information resources9Create individual accountability and auditability9Create or change user profiles9Log events9Log user activities9Report capabilities24Logical Access Exposures and Controls•Logical Access Control Software•Database and/or application-level access control functions include:9Create or change data files and database profiles9Verify user authorization at the application and transaction levels9Verify user authorization within the application9Verify user authorization at the field level for changes within a database9Verify subsystem authorization for the user at the file level9Log database/data communications access activities for monitoring access violations25Logical Access Exposures and Controls•Identification and Authentication–Logon-ids and passwords9Features of passwords9Password syntax (format) rules–Token devices-one time passwords–Biometric26Logical Access Exposures and Controls•Identification and Authentication–Single sign-on (SSO)SSO is the process for the consolidating all organization platform-based administration, authentication and authorizationfunctions into a single centralized administrative function. A single sign-on product that interfaces with:9client-server and distributed systems9mainframe systems9network security including remote access mechanisms27Logical Access Exposures and Controls•Identification and Authentication–Single sign-on (SSO) advantages9Multiple passwords are no longer required, therefore, whereby a user may be more inclined and motivated to select astronger password9It improves an administrator’s ability to manage users’accounts and authorizations to all associates systems9It reduces administrative overhead in resetting forgotten passwords over multiple platforms and applications9It reduces the time taken by users to log into multiple applications and platforms28Logical Access Exposures and Controls•Identification and Authentication–Single sign-on (SSO) disadvantages include:9Support for all major operating system environments is difficult9The costs associated with SSO development can be significant when considering the nature and extent of interfacedevelopment and maintenance that may be necessary9The centralized nature of SSO presents the possibility of a single point of failure and total compromise of anorganization’s information assets29Logical Access Exposures and Controls•Social EngineeringIs the human side of braking into a corporate network.The best means of defense for social engineering is an ongoing security awareness program,wherein all employees are educated about the dangers social engineering can present.30Logical Access Exposures and Controls•Authorization Issues–Typical access rights include:9Read, inquiry or copy only9Write, create, update or delete only9Execute only9A combination of the above31Logical Access Exposures and Controls•Authorization Issues–Access control lists refer to:9Users (including groups, machines, processes) who have been given permission to use a particular system resource9The types of access permitted32Logical Access Exposures and Controls•Authorization Issues•Logical access security administration9Centralized environment9Decentralized environment33Logical Access Exposures and Controls•Authorization Issues•Advantages of conducting security in a decentralized environment9The security administration is on-site at the distributed location9Security issues are resolved in a more timely manner9Security controls are monitored on a more frequent basis34Logical Access Exposures and Controls•Authorization Issues–Remote access securityToday’s organizations require remote access connectivity to their information resources for different types of users such asemployees, vendors, consultants, business partners and customer representatives. In providing this capability, a variety ofmethods and procedures are available to satisfy an organization’s business need for this level of access.35Logical Access Exposures and Controls•Authorization Issues–Remote access security risks include:9Denial of service9Malicious third parties9Misconfigured communications software9Misconfigured devices on the corporate computing infrastructure9Host systems not secured appropriately9Physical security issues over remote users’computers36Logical Access Exposures and Controls•Authorization Issues–Remote access security controls include:9Policy and standards9Proper authorizations9Identification and authentication mechanisms9Encryption tools and techniques, such as the use of VPN9System and network management37Logical Access Exposures and Controls38Logical Access Exposures and Controls39Logical Access Exposures and Controls40Logical Access Exposures and Controls41Logical Access Exposures and Controls42Logical Access Exposures and Controls43Logical Access Exposures and Controls44Logical Access Exposures and Controls45Network InfrastructureSecurity46•LAN SecurityLocal area networks facilitate the storage and retrieval of programs and data used by a group of people.LAN software and practices also need to provide for the security of these programs and data.–LAN risk and issues–Dial-up access controls47•Client-Server Security–Control techniques in place¾Securing access to data or application¾Use of network monitoring devices¾Data encryption techniques¾Authentication systems¾Use of application level access control programs48•Client/Server Security•Client/server risks and issues¾Access controls may be weak in a client-server environment.¾Change control and change management procedures.¾The loss of network availability may have a serious impact on the business or service.¾Obsolescence of the network components¾The use of modems to connect the network to other networks49•Client/Server Security•Client/server risks and issues¾The connection of the network to public switched telephone networks may be weak¾Changes to systems or data¾Access to confidential data and data modification may be unauthorized¾Application code and data may not be located on a single machine enclosed in a secure computer room, as withmainframe computing50•Internet Threats and Security•Passive attacks¾Network analysis¾Eavesdropping¾Traffic analysis•Active attacks¾Brute-force attack¾Masquerading¾Packet replay¾Message modification¾Unauthorized access through the Internet or web-based services¾Denial of service¾Dial-in penetration attacks¾E-mail bombing and spamming¾E-mail spoofing51•Internet Threats and Security–Threat impact¾Loss of income¾Increased cost of recovery¾Increased cost of retrospectively securing systems¾Loss of information¾Loss of trade secrets¾Damage to reputation¾Legal and regulatory noncompliance¾Failure to meet contractual commitments¾Legal action by customers for loss of confidential data52•Internet Threats and Security–Causal factors for internet attacks9Availability of tools and techniques on the Internet9Lack of security awareness and training9Exploitation of security vulnerabilities9Inadequate security over firewalls–Internet security controls53•Firewall Security Systems–Firewall general features–Firewall types•Router packet filtering•Application firewall systems•Stateful inspection54•Firewall Security Systems–Examples of firewall implementations•Screened-host firewall•Dual-homed firewall•Demilitarized zone (DMZ)55•Firewall Security Systems–Firewall issues9A false sense of security9The circumvention of firewall9Misconfigured firewalls9What constitutes a firewall9Monitoring activities may not occur on a regular basis9Firewall policies56•Intrusion Detection Systems (IDS)An IDS works in conjunction with routers and firewalls by monitoring network usage anomalies.•Network-based IDSs•Host-based IDSs57•Intrusion Detection Systems (IDS)Components:•Sensors that are responsible for collecting data•Analyzers that receive inputo from sensors and determine intrusive activity•An administration console• A user interface58•Intrusion Detection Systems (IDS)Types include:•Signature-based•Statistical-based•Neural networks59•Intrusion Detection Systems (IDS)Features:•Intrusion detection•Gathering evidence on intrusive activity•Automated response•Security monitoring•Interface with system tolls•Security policy management60•Intrusion Detection Systems (IDS)Limitations:•Weaknesses in the policy definition•Application-level vulnerabilities•Backdoors into applications•Weaknesses in identification and authentication schemes61•Encryption–Key elements of encryption systems9Encryption algorithm9Encryption key9Key length–Private key cryptographic systems–Public key cryptographic systems62•Encryption (Continued)–Elliptical curve cryptosystem (ECC)–Quantum cryptography–Digital signatures63•Encryption (Continued)–Digital signatures¾Data integrity¾Authentication¾Nonrepudiation¾Replay protection64•Encryption (Continued)–Public key infrastructure9Digital certificates9Certificate authority (CA)9Registration authority (RA)9Certificate revocation list9Certification practice statement (CPS)65•Encryption (Continued)–Use of encryption in OSI protocols¾Secure sockets layer (SSL)¾Secure Hypertext Transfer Protocol (S/HTTP)¾IP security¾SSH¾Secure multipurpose Internet mail extensions (S/MIME)¾Secure electronic transactions (SET)66Auditing Information Security Management and Logical Access Issues and Exposures676869•Auditing Information Security Management–Review written policies, procedures and standards–Logical access security policies–Formal security awareness and training–Data ownership (data classification scheme)–Data owners70•Auditing Information Security Management (Continued)–Data custodians–Security administrator–Data users–Documented authorizations–Terminated employee access–Access standards71•Auditing Logical Access–Familiarization with the organization's IT environment–Document access paths–Interview systems personnel–Review reports from access control software–Review application systems operations manual72•Test Security–Use of terminal cards and keys–Terminal identification–Logon-ids and passwords–Controls over production resources–Logging and reporting of computer access violations73•Test Security (Continued)–Follow-up access violations–Dial-up access controls–Authorization of network changes–Identification of methods of bypassing security and compensating controls–Review access controls and password administration74Auditing Network InfrastructureSecurity75•Auditing Remote Access–Auditing Internet “Points of Presence”–Network penetration tests–Full network assessment reviews–LAN networks assessments–Development and authorization of network changes–Unauthorized changes76Environmental Exposuresand Controls77•Environmental Issues and ExposuresEnvironmental exposures are due primarily to naturally occurring events, such as lightning storms, earthquakes, volcanic eruptions, hurricanes, tornados and other types of extreme weather conditions.78•Environmental Issues and Exposures–Power failures can be grouped into distinct categories¾Total failure (blackout)¾Severely reduced voltage (brownout)¾Sags, spikes and surges¾Electromagnetic interference (EMI)79•Controls for Environmental Exposures–Alarm control panels–Water detectors–Handheld fire extinguishers–Manual fire alarms–Smoke detectors–Fire suppression systems–Strategically locating the computer room80•Controls for Environmental Exposures (cont.)–Regular inspection by fire department–Fireproof walls, floors and ceilings surrounding the computer room–Electrical surge protectors–Uninterruptible power supply/generator–Emergency power-off switch–Power leads from two substations81•Controls for Environmental Exposures (cont.)–Wiring placed in electrical panels and conduit–Prohibitions against eating, drinking and smoking within the information processing facility–Fire resistant office materials–Documented and tested emergency evacuation plans82•Auditing Environmental Controls–Water and smoke detectors–Handheld fire extinguishers–Fire suppression systems–Regular inspection by fire department–Fireproof walls, floors and ceilings surrounding the computer room–Electrical surge protectors83•Auditing Environmental Controls (cont.)–Power leads from two substations–Fully documented and tested business continuity plan–Wiring placed in electrical panels and conduit–UPS/generator–Documented and tested emergency evacuation plans–Humidity/temperature control84Physical Access Exposuresand Controls85•Physical Access Issues and Exposures–Physical access exposures•Unauthorized entry•Damage, vandalism or theft to equipment or documents•Copying or viewing of sensitive ore copyrighted information•Alteration of sensitive equipment and information•Public disclosure of sensitive information•Abuse of data processing resources•Blackmail•Embezzlement86•Physical Access Issues and Exposures–Possible perpetrators9Disgruntled9On strike9Threatened by disciplinary action or dismissal9Addicted to a substance or gambling9Experiencing financial or emotional problems9Notified of their termination87•Physical Access Controls–Bolting door locks–Combination door locks (cipher locks)–Electronic door locks–Biometric door locks–Manual logging–Electronic logging88•Physical Access Controls (continued)–Identification badges (photo IDs)–Video cameras–Security guards–Controlled visitor access–Bonded personnel–Deadman doors89•Physical Access Controls (continued)–Not advertising the location of sensitive facilities–Computer workstation locks–Controlled single entry point–Alarm system–Secured report/document distribution cart90•Auditing Physical Access–Touring the information processing facility (IPF)–Testing of physical safeguards91Personal Computer (Laptop)Security92•Mobile Computing Controls–Engrave or brand a serial number and company name and logo–Use a cable locking system–Back up business critical or sensitive data–Encrypt data–Allocate passwords to individual files–Establish a theft response team and develop procedures to follow when a laptop is stolen93•Access control table•Asymmetric key (public key)•Authentication•Biometrics•Card Swipes•Challenge/response token•Digital signature•Dry-pipe94•Group Discussion•Questions951.Which of the following BEST provides access control to payroll d ata being processed on a local server?A. Logging of access to personal informationB. Separate password for sensitive transactionsC. Software restricts access rules to authorized staffD. System access restricted to business hours962. Which of the following concerns about the security of an electro nic message would beaddressed by digital signatures?A. Unauthorized readingB. TheftC. Unauthorized copyingD. Alteration973. The MOST effective method for limiting the damage of an attack b y a software virus is:A. software controls.B. policies, standards and procedures.C. logical access controls.D. data communication standards.984. Which of the following BEST determines that complete encryption and authentication protocols exist forprotecting information while transmitted?A. A digital signature with RSA has been implemented.B. Work is being done in tunnel mode with the nested services of AH and ESPC. Digital certificates with RSA are being used.D. Work is being done in transport mode, with the nested servi ces of AH and ESP995. Which of the following would be MOST appropriate to ensure the c onfidentiality oftransactions initiated via the Internet?A. Digital signatureB. Data encryption standard (DES)C. Virtual private network (VPN)D. Public key encryption。
计算机专业英语影印版(Compu...

Key Terms Page 1of 6 Key TermsKey TermDefinition3G cellular network (249) A computer network that allows users to download data from the Internet at 400 to 700 Kbps using cell phone technology. analog signal (247) Continuous electronic waves. asymmetric digital subscriber line (ADSL) (248) The most widely used types of DSL. backbone (258) A common connecting cable on which all communications travel along. (see also bus) bandwidth (249) A measurement of the width or capacity of the communication channel. base station (254) A network’s centrally located receiver that interprets incoming radio frequencies and routes communications to the appropriate devices. (see also wireless receiver) bits per second (bps) (247) How transfer speed is measured Bluetooth (245) A short-range wireless communication standard that uses microwaves to transmit data over short distances broadband (250) The bandwidth used for high-capacity transmissions. broadcast radio (245) Uses radio signals to send and receive signals from wireless devices. bus (258) A common connecting cable on which all communications travel along. (see also backbone) bus network (258) Each device in the network handles its own communications control. cable modem (249) Use existing television cables to provide high-speed connections to the Internet. cellular service (249) Offer an alternative for mobile devices and laptops. client (251) A node that requests and uses resources available from other nodes. client/server network system (260) A computer network where one computer coordinates and supplies services to other nodes on the network. coaxial cable (244) A high-frequency transmission cable with a single solid-copper core. Communication channel (244) The actual connecting or transmission medium that carries the message. Communication system (243) An electronic system that transmit data from one location to another computer network (251) A communication system that connects two or more computers so that they can exchange information and share resources. connectivity (242) Using computer networks to link people and resources. demodulation (247) The process of converting from analog to digital. dial-up service (248) Using standard telephone lines and conventional modems to link to the Internet or other computers digital signal (247) A representation of the presence or absence of an electronic pulse – on/off digital subscriber line (DSL) (248) Uses existing telephone lines to provide high-speed connections distributed data processing system Computers that can perform processing tasks at their own Key Terms Page 2of 6 (258) dispersed locations. distributed processing (251) A system in which computing power is located and shared at different locations. domain name server (DNS) (250) Converts text-based addresses to IP addresses Ethernet (253) The most common way in which nodes can be connected to one another and communications can be controlled. external modem (247) A modem that stands apart from the computer and typically is connected by a cable to the computer’s serial port. extranet (262) A private network that connects more than one organization. fiber-optic cable (244) Transmits data as pulses of light through tiny tubes of glass. firewall (263) A security system designed to protect an organization’s network against external threats. global positioning system (GPS) (245) Global positioning system (GPS) devices use location information sent by satellites to uniquely determine the geographic location of the device. hierarchical network (258) Consists of several computers linked to a central host computer, but also are hosts to other, smaller computers or peripheral devices. home network (254) Local Area Networks used by individuals in their homes and apartments. host computer (251) A large centralized computer, usually a minicomputer or a mainframe. hub (251) The center or central node for other nodes. infrared (245) A type of wireless connection that uses infrared light waves to communicate over short distances. internal modem (248) A modem that consists of a plug-in circuit board inside the system unit. intranet (262) A private network within an organization that resembles the Internet. IP address (Internet Protocol address) (250) A unique numeric address for every computer on a network. local area network (LAN) (253) Networks with nodes that are in close physical proximity low bandwidth (250) Used for standard telephone communication. (see also voiceband) medium band (250) the bandwidth used in special leased lines to connect minicomputers and mainframes metropolitan area network (MAN) (254) A network that span distances up to 100 miles. microwave (245) A type of communication uses high-frequency radio waves. modem (247) Modulator-demodulator, enables digital microcomputers to communicate across analog telephone lines. modulation (247) The process of converting from digital to analog. network administrator (251, 264) A computer specialist responsible for efficient network operations and implementation of new networks. network gateway (253) A device that allows one LAN to be linked to other LANs or to larger networks. network hub (255) A central unit in a network, such as a server. Key Terms Page 3of 6 network interface card (NIC) (251) Expansion cards located within the system unit that connect the computer to a network network operating system (NOS) (251) An operating system that control and coordinate the activities of all computers and other devices on a network. node (251) Any device that is connected to a network. packet (250) Data reformatted or broken down into small parts PC Card modem (248) A modem that is a credit card –size expansion board that is inserted into portable computers peer-to-peer network system (261) A network system where nodes have equal authority and can act as both clients and servers. polling (255) A type of communications where each connecting device is asked whether it has a message to send. protocol (250) Rules for exchanging data between computers proxy server (263) A computer through which all communications between the company’s internal n etworks and the outside world must pass. ring network (258) Each device is connected to two other devices, forming a ring with no central computer satellite (245) A type of communication that uses satellites orbiting about 22,000 miles above the earth as microwave relay stations. satellite/air connection service (249) Use satellites and the air to download or send data to users at a rate seven times faster than dial-up connections. server (251) A node that shares resources with other nodes. star network (255) A number of small computers or peripheral devices are linked to a central unit. strategy (260) A way of coordinating the sharing of information and resources T1, T2, T3, T4 lines (248) Special high-speed lines leased from telephone companies. telephone line (244) A type of cable that uses 2, 4, or 8 pairs of copper wire. terminal network (260) A network system where processing power is centralized in one large computer, usually a mainframe. time-sharing system (258) Several users can share resources (time) on a central computer. topology (255) How a network is arranged or configured transfer rate (247) The speed at which data can be transmitted Transmission Control Protocol/Internet Protocol (TCP/IP) (250) The standard protocol for the Internet voiceband (250) Used for standard telephone communication. (see also low bandwidth) wide area network (WAN) (254) A countrywide or worldwide network that spans distances greater than 100 miles. Wi-FI (wireless fidelity) (245) A wireless standard used to connect computers to each other and to the Internet. wireless LAN (WLAN) (254) Local area network that uses wireless devices to connect nodes together. wireless modem (248) A modem that may be internal, external, or a PC Card sends and receives through the air. wireless receiver (254) A network’s centrally located receiver that interprets incoming radio frequencies and routes communications to the appropriate devices. (see also base station) Crossword Puzzle Answers:AcrossNum. Clue Answer 5 Interprets and routs incoming radio frequencies. Base station7 Continuous electronic waves. Analog9 Configuration of a network. topology10 Network interface card. NIC11 Transfer speed or transfer rate. bps12 Short range wireless communication standard. bluetooth14 Measurement of the width of the communication channel. bandwidth DownNum. Clue Answer 1 Node that requests and uses resources available from other nodes. client 2 Each device in the network handles its own communications. Bus network 3 Device that allows links between LANs. Network gateway 4 Process that converts digital to analog. modulation6 Pieces of a message sent over the Internet. packets8 Global positioning system. GPS13 Any device that is connected to a network. node15 Uses existing telephone lines to provide high-speed connections. DSL 16 Central node for other nodes. hubNum Multiple ChoiceAnswers Matching Answers1 C G 2 B B 3 A A 4 D I 5 C H 6 D E 7 B C 8 B J 9 B D 10 D F Open Ended Questions:to another 2.Identify and describe the various physical and wireless communication channels.PhysicalTelephone lines - consist of twisted-pair cable made up of hundreds of copper wires. Coaxial cable- a high-frequency transmission cable with a single solid-copper core. Fiber-optic cable - transmits data as pulses of light through tiny tubes of glass. WirelessInfrared - uses infrared light waves to communicate over short distances. Broadcast radio sends and receive radio signals through transceivers. Microwave - uses high-frequency radio waves. Satellite - uses satellites orbiting above the earth as microwave relay stations. 3.Identify the standard Internet protocol and discuss its essential features.The standard protocol for the Internet is TCP/IP (transmission control protocol/Internet protocol). Every computer on the Internet has a unique numeric address called an IP address. Information is reformatted or broken down into small parts called packets. 4.Define and discuss the four principal network topologies.S tar network - a number of small computers or peripheral devices are linked to a central unit. Bus network - each device in the network handles its own communications control. Ring network - each device is connected to two other devices, forming a ring. Hierarchical network— consists of several computers linked to a central host computer, and also hosts to other, smaller computers or to peripheral devices. 5.Define and discuss the three most common network strategies.Terminal network system,- processing power is centralized in one large computer, usually a mainframe. - use one computer to coordinate and supply services to other Client/server network systems - use one computer to coordinate and supply services to other nodes on the network. Peer-to-peer network system, nodes have equal authority and can act as both clients and servers. Answers to End of Chapter materials Page 5 of 6 Focus Applying Technology Expanding YourKnowledgeWriting AboutTechnologyEthical Electronic Monitoring Digital Rights Management Web Tools Palm How Napster and Gnutella Work Software Tools Home Networking Distributed Computing How Wireless Home Networks Work Hotspots Writing Skills Ethical focusWriting About Technology exercise #1 Electronic Monitoring explores the FBI Carnivore monitoring system and how it affects personal privacy. Writing About Technology exercise #2 Digital Rights Management explores the issue of sharing copyrighted material over the Internet and how it affects software piracy. Applying Technology exercise #3 Palm explores how Palms work with the Internet and looks at the types of information are available. Expanding Your Knowledge #2 How Napster and Gnutella Work looks at the different types of network architectures employed by each program and their efficiencies. Applying Technology exercise #1 Home Networking works with the Making it Work for you section in exploring the different types of home networking and how to configure Applying Technology exercise #2 Distributed Computing has the students research the concept of distributed computing, how it works, and why it is beneficial. Expanding Your Knowledge exercise #1 How Wireless Home Networks Work has the students discover basic features and functionalities of home networking and how they can Expanding Your Knowledge exercise #3 Hotspots has the student explore the technology of public Internet access and what is necessary to use it. 。
高等教育出版社影印版计算机专业英语习题3ch_5_im

I. Ch 3 System SoftwareLecture OutlineA. Competencies pg 1201. Describe the differences between system software andapplication software2. Discuss the four types of system software3. Discuss the basic functions, features and categoriesof operating systems4. Describe the Windows, Mac OS, UNIX, and Linux(operating systems)5. Describe the purpose of utilities and utility suites6. Identify the five most essential utilities7. Discuss Windows utility programs8. Describe device drivers including printer driversB. Introduction pg 121▪Most people think of software as just applicationssoftware.▪Systems software handles the more mundane computeractivities such as loading and running programs,coordinating networks, organizing files, protecting thecomputer from viruses, etc.▪These activ ities SHOULD be “behind-the-scenes”, but a computer literate user should know about system softwarein case something goes wrong, such as applicationsoftware that won’t run on the current system, a harddisk fails, or the computer is affected by a virus.▪Key Terms: Operating Systems: manage resources, provide a user interface, and run application programs. Utilities:make computing easier by providing tools to correctproblems and to avoid problems.C. System Software pg 122▪System software works with end users, applicationsoftware and computer hardware to handle the majority oftechnical details.▪System software is not a single program. It is acollection or a system of programs.▪System software consists of four types of programs:▪Operating systems: programs that coordinate computer resources, provide a user interface, and run applications,for example the Windows XP operating system.▪Utilities (aka service programs) perform specific tasks related to managing computer resources, for example, afile compression utility like WinZip.▪Device drivers allow input and output devices tocommunicate with the rest of the computer system, forexample, a printer driver.▪Language translators convert programming instructions written by programmers into a language that computersunderstand and process. For example, you may have a C++compiler that translates the C++ source code into anexecutable file the computer can run.D. Operating Systems pg 123▪An operating system is a collection of programs that manage computer resources, provides a user interface, andruns applications.▪Computer Resources include memory, processing, storage, input & output devices. The OS also monitors systemperformance, schedules jobs, and provides some securityfor the computer.▪User Interface: on older systems, a character based interface may have been used, e.g. “Copy A:assign.docC:”. Most operating systems use a Graphical UserInterface (GUI), with icons and windows.▪Applications: are programs such as word processors and spreadsheets. Most operating systems allow“multitasking”, the running of more than oneapplication at a time. The program you are currentlyrunning is in the “foreground”, and those that arerunning, but not currently active are in the “background”.1. Features▪Booting: starting or restarting a computer▪Warm boot: restart without turning off the power▪Cold boot: start after power has been off.▪Desktop: the place to access computer resources –items you’ll typically find on the desktop include:a)Icons:▪graphical representations of a program orfunctionb)Pointer:▪Controlled by the mouse, changes appearancedepending on the current function.c)Windows:▪Rectangular areas for displaying informationand running programs.d)Menus:▪provide a list of options or commandse)Dialog boxes:▪provide info or request input, e.g. File Save dialog boxf)Help:▪Provides online assistance for OS functionsand procedures.▪Files: used to store data and programs▪Folders: related files are stored in folders2. Categories▪There are three basic categories of operating systems:a)Embedded Operating Systems:▪Used for handheld computers and PDAs. EntireOS is stored within the device.▪Examples include Windows CE and Palm OSb)Network Operating Systems (aka NOS):▪Used to control and coordinate computers thatare networked. NOS are typically located onone computer in the network, the NetworkServer.▪Examples include Novell NetWare, Windows NTServer, UNIX, VSE/ESA and z/OS.c)Stand alone OS (aka desktop OS):▪Control a single desktop or notebook computer.If the computer is connected on a network, itmay have a client operating system.▪Examples of stand alone systems includeWindows, Mac OS, and some versions of UNIX.▪The OS is often referred to as the SoftwareEnvironment or Platform.▪Most OS are Proprietary OS: they are owned andlicensed by a corporation.▪Some OS are Non-Proprietary OS: they are not owned by any one corporation. These are also called OpenSource programs. An example is Linux.3. Windows▪Microsoft Windows is by far the most popularmicrocomputer operating system with over 80% of themarket.▪There are a variety of versions of Windows such as Windows NT Workstation, Windows 2000 Professional,Windows ME, etc.4. Mac OS▪Introduced in 1984, it provided one of the first GUIs.▪Has a much smaller market share, but is still popular with professional graphic designers, desktoppublishers, and some home users.▪One of the latest versions is Mac OS X. The desktop features Dock, a tool for visually organizing files.It also has the Sherlock search tool to help locateinformation on the web & system.5. UNIX and Linux▪Unix OS was originally designed to run on networked microcomputers.▪Now, it’s used on servers on the Web.▪Linux is one of the many versions of UNIX.▪Linux is open source, created by Linus Torvalds in 1991.▪Linux is one of the most popular and powerfulalternatives to Windows.E. Utilities pg 128▪Utilities are specialized programs that recognize and correct problems, ideally before they become serious.Some of the most essential utilities include:▪Troubleshooting or diagnostic programs: recognize and correct problems before they become serious▪Antivirus: guard your computer against viruses and other damaging programs that can invade your computer system ▪Uninstall programs: allow you to safely and completely remove un-needed programs and related files from yourhard disk▪Backup programs: make copies of important files in case the original are lost or damaged.▪File compression programs: reduce the size of files so they can be stored and/or sent over a network moreefficiently.▪Many of these utilities are included with modernoperating systems, and some may be purchased from a thirdparty either separately or in utility suites.1. Windows Utilities▪Windows has several utilities that can be accessed from the Systems Tools menu:▪Backup: makes copies of your files onto another storage medium▪Disk Cleanup: removes unnecessary files such as temporary Internet files▪Disk Defragmenter: locates and eliminates unnecessary file fragments and rearranges files and unused diskspace to optimize operations. When files are storedon hard drives, they are physically written ontotracks and sectors. A track is a concentric ring on adisk, a sector is a wedge shaped portion of thesetracks.2. Utility Suites▪Utility suites combine several utility programs into one package.▪An advantage of a Utility Suite is it is cheaper than buying each program separately.▪Examples include eSafe Desktop, McAfee Office, and Norton SystemWorks.▪Norton SystemWorks is one of the most widely used Utility Suites. It includes the following components:▪Norton Antivirus: protects your system from computer viruses▪Norton Cleansweep: removes unneeded programs and files, archives and backs up the hard drive, and protectsexisting files when installing new software.▪Web Cleanup: checks and can eliminate unneeded files that are stored on your hard drive when you surf theInternet▪Connection Keep Alive: prevents dial up Internet connections from “timing out”▪GoBack Personal Edition – restores systemconfigurations, finds lost files, and repairs damagedfiles.▪Norton Utilities: a collection of trouble shooting utilities to improve system performance▪On Button Checkup: integrates several troubleshooting utilities.F. Device Drivers pg 133▪Device Drivers (aka Drivers) work with the operating system to allow communications between the device and therest of the computer system.▪Each time the computer is booted, the OS loads all device drivers into memory.▪If a new device is added, you need to add the device driver to your computer.▪Microsoft Windows has wizards that can help in this process, such as the Windows Add Printer Wizard.▪Windows Update can help you to make sure you have all the latest versions of your device drivers.G. Making IT Work For You – Virus Protection - pg 134▪This section covers how to install an Internet security site from bbb://aaaesafedesktopaaa▪Some of the features that can be loaded include:▪Sandbox: a protective area where suspicious andpotentially dangerous programs can be run▪Personal firewall: monitors all inbound and outbound network traffic to a computer system.▪Anti-virus: controls how frequently the system is checked for computer viruses.▪Check Tim’s toolbox or the CD for updates on this system.▪According to the bbb://aaaesafedesktopaaa website, “Aladdin no longer develops, supports or distributes theeSafe Desktop anti virus product for personal and homeuse. Virus updates for Desktop were terminated on 31-December-2003”.H. A Look to the Future pg 1371. IBM Builds an Aware Supercomputer:▪IBM researchers are working on a plan to develop acomputer that can “fix itself”.▪Using “autonomic computing”, the machine will be able to run with little human intervention.▪Such compu ters would not have “self-awareness”, but would be “self-correcting”. They would sense slowprograms or disk response times, and optimize it toimprove response time.▪Additional material can be found at bbb://www-3.ibmaaa/autonomic/index.shtmlI. Visual Summary at a glance– System Software pg 1381. System Softwarea)Operating Systemsb)Utilities (service programs)c)Device Driversd)Language translators2. Operating Systemsa)Featuresb)Categories(1)Embedded(2)Network(3)Client3. Operating Systemsa)Windowsb)Mac OSc)UNIX and Linux4. Utilitiesa)Windows Utilitiesb)Utility Suites5. Device DriversJ. Key Terms pg 140。
2008考研英语真题与答案

2008年全国硕士研究生考试英语真题及答案Section I Use of EnglishDirections:Read the following text. Choose the best word(s) for each numbered blank and mark A, B, C or D on ANSWER SHEET 1. (10 points)The idea that some groups of people may be more intelligent than others is one of those hypotheses that dare not speak its name. But Gregory Cochran is 1 to say it anyway. He is that 2 bird, a scientist who works independently 3 any institution. He helped popularize the idea that some diseases not 4 thought to have a bacterial cause were actually infections, which aroused much controversy when it was first suggested.5 he, however, might tremble at the6 of what he is about to do. Together with another two scientists, he is publishing a paper which not only7 that one group of humanity is more intelligent than the others, but explains the process that has brought this about. The group in8 are a particular people originated from central Europe. The process is natural selection. This group generally do well in IQ test,9 12-15 points above the 10 value of 100, and have contributed 11 to the intellectual and cultural life of the West, as the 12 of their elites, including several world-renowned scientists,13 hey also suffer more often than most people from a number of nasty genetic diseases, such as breast cancer. These facts, 14 ave previously been thought unrelated. The former has been 15 social effects, such as a strong tradition of 16 ucation. The latter was seen as a (an) 17 genetic isolation. Dr. Cochran suggests that the intelligence and diseases are intimately18 is argument is that the unusual history of these people has 19 em to unique evolutionary pressures that have resulted in this 20 ate of affairs.1. [A] selected [B] prepared [C] obliged [D] pleased2. [A] unique [B] particular [C] special [D] rare3. [A] of [B] with [C] in [D] against4. [A] subsequently [B] presently [C] previously [D] lately5. [A] Only [B] So [C] Even [D] Hence6. [A] thought [B] sight [C] cost [D] risk7. [A] advises [B] suggests [C] protests [D] objects8. [A] progress [B] fact [C] need [D] question9. [A] attaining [B] scoring [C] reaching [D] calculating10. [A] normal [B] common [C] mean [D] total11. [A] unconsciously [B] disproportionately[C] indefinitely [D] unaccountably12. [A] missions [B] fortunes [C] interests [D] careers13. [A] affirm [B] witness [C] observe [D] approve14. [A] moreover [B] therefore [C] however [D] meanwhile15. [A] given up [B] got over [C] carried on [D] got down16. [A] assessing [B] supervising [C] administering [D] valuing17. [A] development [B] origin [C] consequence [D] instrument18. [A] linked [B] integrated [C] woven [D] combined19. [A] limited [B] subjected [C] converted [D] directed20. [A] paradoxical [B] incompatible [C] inevitable [D] continuousSection II Reading ComprehensionPart ADirections:Read the following four texts. Answer the questions below each text by choosing A, B, C or D. Mark your answers on ANSWER SHEET 1. (40 points)Text 1While still catching-up to men in some spheres of modern life, women appear to be way ahead in at least one undesirable category. ―Women are particularly susceptible to developing depression and anxiety disorders in response to stress compared to men,‖ according to Dr. Yehuda, chief psychiatrist at New York’s Veteran’s Administration Hospital.Studies of both animals and humans have shown that sex hormones somehow affect the stress response, causing females under stress to produce more of the trigger chemicals than do males under the same conditions. In several of the studies, when stressed-out female rats had their ovaries (the female reproductive organs) removed, their chemical responses became equal to those of the males.Adding to a woman’s increased dose of stress chemicals, are her increased ―opportunities‖ for stress. ―It’s not necessarily that women don’t cope as well. It’s just that they have so much more to cope with,‖ says Dr. Yehuda. ―Their capacity for tolerating stress may even be greater than men’s,‖ she observes, ―it’s just that they’re deal ing with so many more things that they become worn out from it more visibly and sooner.‖Dr. Yehuda notes another difference between the sexes. ―I think that the kinds of things that women are exposed to tend to be in more of a chronic or repeated nature. Men go to war and are exposed to combat stress. Men are exposed to more acts of random physical violence. The kinds of interpersonal violence that women are exposed to tend to be in domestic situations, by, unfortunately, parents or other family members, and they tend not to be one-shot deals. The wear-and-tear that comes from these longer relationships can be quite devastating.‖Adeline Alvarez married at 18 and gave birth to a son, but was determined to finish college. ―I struggled a lot to get the college degree. I was living in so much frustration that that was my escape, to go to school, and get ahead and do better.‖ Later, her marriage ended and she became a single mother. ―It’s the hardest thing to take care of a teenager, have a job, pay the rent, pa y the car payment, and pay the debt. I lived from paycheck to paycheck.‖Not everyone experiences the kinds of severe chronic stresses Alvarez describes. But most women today are coping with a lot of obligations, with few breaks, and feeling the strain. Al varez’s experience demonstrates the importance of finding ways to diffuse stress before it threatens your health and your ability to function.21. Which of the following is true according to the first two paragraphs?[A] Women are biologically more vulnerable to stress.[B] Women are still suffering much stress caused by men.[C] Women are more experienced than men in coping with stress.[D] Men and women show different inclinations when faced with stress.22. Dr. Yehuda’s research suggests that women[A] need extra doses of chemicals to handle stress.[B] have limited capacity for tolerating stress.[C] are more capable of avoiding stress.[D] are exposed to more stress.23. According to Paragraph 4, the stress women confront tends to be[A] domestic and temporary.[B] irregular and violent.[C] durable and frequent.[D] trivial and random.24. The sentence ―I lived from paycheck to paycheck.‖ (Line 6, Para. 5) shows that[A] Alvarez cared about nothing but making money.[B] Alvarez’s salary barely covered h er household expenses.[C] Alvarez got paychecks from different jobs.[D] Alvarez paid practically everything by check.25. Which of the following would be the best title for the text?[A] Strain of Stress: No Way Out?[B] Responses to Stress: Gender Difference[C] Stress Analysis: What Chemicals Say[D] Gender Inequality: Women Under StressText 2It used to be so straightforward. A team of researchers working together in the laboratory would submit the results of their research to a journal. A journal edi tor would then remove the authors’ names and affiliations from the paper and send it to their peers for review. Depending on the comments received, the editor would accept the paper for publication or decline it. Copyright rested with the journal publisher, and researchers seeking knowledge of the results would have to subscribe to the journal.No longer. The Internet – and pressure from funding agencies, who are questioning why commercial publishers are making money from government-funded research by restricting access to it – is making access to scientific results a reality. The Organization for Economic Co-operation and Development (OECD) has just issued a report describing the far-reaching consequences of this. The report, by John Houghton of Victoria University in Australia and Graham Vickery of the OECD, makes heavy reading for publishers who have, so far, made handsome profits. But it goes further than that. It signals a change in what has, until now, been a key element of scientific endeavor. The value of knowledge and the return on the public investment in research depends, in part, upon wide distribution and ready access. It is big business. In America, the core scientific publishing market is estimated at between $7 billion and $11 billion. The International Association of Scientific, Technical and Medical Publishers says that there are more than 2,000 publishers worldwide specializing in these subjects. They publish more than 1.2 million articles each year in some 16,000 journals.This is now changing. According to the OECD report, some 75% of scholarly journals are now online. Entirely new business models are emerging; three main ones were identified by the report’s authors. There is the so-called big deal, where institutional subscribers pay for access to a collection of online journal titles through site-licensing agreements. There is open-access publishing, typically supported by asking the author (or his employer) to pay for the paper to be published. Finally, there are open-access archives, where organizations such as universities or international laboratories support institutional repositories. Other models exist that are hybrids of these three, such as delayed open-access, where journals allow only subscribers to read a paper for the first six months, before making it freely available to everyone who wishes to see it. All this could change the traditional form of the peer-review process, at least for the publication of papers.26. In the first paragraph, the author discusses[A] the background information of journal editing.[B] the publication routine of laboratory reports.[C] the relations of authors with journal publishers.[D] the traditional process of journal publication.27. Which of the following is true of the OECD report?[A] It criticizes government-funded research.[B] It introduces an effective means of publication.[C] It upsets profit-making journal publishers.[D] It benefits scientific research considerably.28. According to the text, online publication is significant in that[A] it provides an easier access to scientific results.[B] it brings huge profits to scientific researchers.[C] it emphasizes the crucial role of scientific knowledge.[D] it facilitates public investment in scientific research.29. With the open-access publishing model, the author of a paper is required to[A] cover the cost of its publication.[B] subscribe to the journal publishing it.[C] allow other online journals to use it freely.[D] complete the peer-review before submission.30. Which of the following best summarizes the main idea of the text?[A] The Internet is posing a threat to publishers.[B] A new mode of publication is emerging.[C] Authors welcome the new channel for publication.[D] Publication is rendered easier by online service.Text 3In the early 1960s Wilt Chamberlain was one of only three players in the National Basketball Association (NBA) listed at over seven feet. If he had played last season, however, he would have been one of 42. The bodies playing major professional sports have changed dramatically over the years, and managers have been more than willing to adjust team uniforms to fit the growing numbers of bigger, longer frames.The trend in sports, though, may be obscuring an unrecognized reality: Americans have generally stopped growing. Though typically about two inches taller now than 140 years ago, today’s people –especially those born to families who have lived in the U.S. for many generations – apparently reached their limit in the early 1960s. And they aren’t likely to get any taller. ―In the general population today, at this genetic, environmental level, we’ve pretty much gone as far as we can go,‖ says anthropologist William Cameron Chumlea of Wright State University. In the case of NBA players, their increase in height appears to result from the increasingly common practice of recruiting players from all over the world.Growth, which rarely continues beyond the age of 20, demands calories and nutrients – notably, protein – to feed expanding tissues. At the start of the 20th century, under-nutrition and childhood infections got in the way. But as diet and health improved, children and adolescents have, on average, increased in height by about an inch and a half every 20 years, a pattern known as the secular trend in height. Yet according to the Centers for Disease Control and Prevention, average height –5′9″ for men, 5′4″ for women –hasn’t really changed since 1960. Genetically speaking, there are advantages to avoiding substantial height. During childbirth, larger babies have more difficulty passing through the birth canal. Moreover, even though humans have been upright for millions of years, our feet and back continue to struggle with bipedal posture and cannot easily withstand repeated strain imposed by oversize limbs. ―There are some real constraints that are set by the genetic architecture of the individual organism,‖ says anthropologist William Leonard of Northwestern University.Genetic maximums can change, but don’t expect this to happen soon. Claire C. Gordon, sen ior anthropologist at the Army Research Center in Natick, Mass., ensures that 90 percent of the uniforms and workstations fit recruits without alteration. She says that, unlike those for basketball, the length of military uniforms has not changed for some time. And if you need to predict human height in the near future to design a piece of equipment, Gordon says that by and large, ―you could use today’s data and feel fairly confident.‖31. Wilt Chamberlain is cited as an example to[A] illustrate the change of height of NBA players.[B] show the popularity of NBA players in the U.S..[C] compare different generations of NBA players.[D] assess the achievements of famous NBA players.32. Which of the following plays a key role in body growth according to the text?[A] Genetic modification.[B] Natural environment.[C] Living standards.[D] Daily exercise.33. On which of the following statements would the author most probably agree?[A] Non-Americans add to the average height of the nation.[B] Human height is conditioned by the upright posture.[C] Americans are the tallest on average in the world.[D] Larger babies tend to become taller in adulthood.34. We learn from the last paragraph that in the near future[A] the garment industry will reconsider the uniform size.[B] the design of military uniforms will remain unchanged.[C] genetic testing will be employed in selecting sportsmen.[D] the existing data of human height will still be applicable.35. The text intends to tell us that[A] the change of human height follows a cyclic pattern.[B] human height is becoming even more predictable.[C] Americans have reached their genetic growth limit.[D] the genetic pattern of Americans has altered.Text 4In 1784, five years before he became president of the United States, George Washington, 52, was nearly toothless. So he hired a dentist to transplant nine teeth into his jaw – having extracted them from the mouths of his slaves. That’s a far different image from the cherry-tree-chopping George most people remember from their history books. But recently, many historians have begun to focus on the roles slavery played in the lives of the founding generation. They have been spurred in part by DNA evidence made available in 1998, which almost certainly proved Thomas Jefferson had fathered at least one child with his slave Sally Hemings. And only over the past 30 years have scholars examined history from the bottom up. Works of several historians reveal the moral compromises made by the nation’s early leaders and the fragile nature of the country’s infancy. More significantly, they argue that many of the Founding Fathers knew slavery was wrong – and yet most did little to fight it.More than anything, the historians say, the founders were hampered by the culture of their time. While Washington and Jefferson privately expressed distaste for slavery, they also understood that it was part of the political and economic bedrock of the country they helped to create.For one thing, the South could not afford to part with its slave s. Owning slaves was ―like having a large bank account,‖ says Wiencek, author of An Imperfect God: George Washington, His Slaves, and the Creation of America. The southern states would not have signed the Constitution without protections for the ―peculiar institution,‖ including a clause that counted a slave as three fifths of a man for purposes of congressional representation.And the statesmen’s political lives depended on slavery. The three-fifths formula handed Jefferson his narrowvictory in the presidential election of 1800 by inflating the votes of the southern states in the Electoral College. Once in office, Jefferson extended slavery with the Louisiana Purchase in 1803; the new land was carved into 13 states, including three slave states.Still, Jef ferson freed Hemings’s children –though not Hemings herself or his approximately 150 other slaves. Washington, who had begun to believe that all men were created equal after observing the bravery of the black soldiers during the Revolutionary War, overcame the strong opposition of his relatives to grant his slaves their freedom in his will. Only a decade earlier, such an act would have required legislative approval in Virginia.36. George Washington’s dental surgery is mentioned to[A] show the primitive medical practice in the past.[B] demonstrate the cruelty of slavery in his days.[C] stress the role of slaves in the U.S. history.[D] reveal some unknown aspect of his life.37. We may infer from the second paragraph that[A] DNA technology has been widely applied to history research.[B] in its early days the U.S. was confronted with delicate situations.[C] historians deliberately made up some stories of Jefferson’s life.[D] political compromises are easily found throughout the U.S. history.38. What do we learn about Thomas Jefferson?[A] His political view changed his attitude towards slavery.[B] His status as a father made him free the child slaves.[C] His attitude towards slavery was complex.[D] His affair with a slave stained his prestige.39. Which of the following is true according to the text?[A] Some Founding Fathers benefit politically from slavery.[B] Slaves in the old days did not have the right to vote.[C] Slave owners usually had large savings accounts.[D] Slavery was regarded as a peculiar institution.40. Washington’s decision to free slaves originated from his[A] moral considerations.[B] military experience.[C] financial conditions.[D] political stand.Part BDirections:In the following article, some sentences have been removed. For Questions 41—45, choose the most suitable one from the list A-G to fit into each of the numbered blanks. There are two extra choices, which do not fit in any of the blanks. Mark your answers on ANSWER SHEET 1. (10 points)The time for sharpening pencils, arranging your desk, and doing almost anything else instead of writing has ended. The first draft will appear on the page only if you stop avoiding the inevitable and sit, stand up, or lie down to write. (41) -------Be flexible. Your outline should smoothly conduct you from one point to the next, but do not permit it to railroad you. If a relevant and important idea occurs to you now, work it into the draft.(42) ------- Grammar, punctuation, and spelling can wait until you revise. Concentrate on whatyou are saying. Good writing most often occurs when you are in hot pursuit of an idea rather than in a nervous search for errors.(43) ------- Your pages will be easier to keep track of that way, and, if you have to clip a paragraph to place it elsewhere, you will not lose any writing on the other side.If you are working on a word processor, you can take advantage of its capacity to make additions and deletions as well as move entire paragraphs by making just a few simple keyboard commands. Some software programs can also check spelling and certain grammatical elements in your writing.(44) ------- These printouts are also easier to read than the screen when you work on revisions. Once you have a first draft on paper, you can delete material that is unrelated to your thesis and add material necessary to illustrate your points and make your paper convincing. The student who wrote “The A & P as a State of Mind” wisely dropped a paragraph that questioned whether Sammy displays chauvinistic attitudes toward women. (45) -------Remember that your initial draft is only that. You should go through the paper many times – and then again – working to substantiate and clarify your ideas. You may even end up with several entire versions of the paper. Rewrite. The sentences within each paragraph should be related to a single topic. Transitions should connect one paragraph to the next so that there are no abrupt or confusing shifts. Awkward or wordy phrasing or unclear sentences and paragraphs should be mercilessly poked and prodded into shape.[A] To make revising easier, leave wide margins and extra space between lines so that you can easily add words, sentences, and corrections. Write on only one side of the paper.[B] After you have clearly and adequately developed the body of your paper, pay particular attention to the introductory and concluding paragraphs. It’s probably best to write the introduction last, after you know precisely what you are introducing. Concluding paragraphs demand equal attention because they leave the reader with a final impression.[C] It’s worth remembering, however, that though a clean copy fresh off a printer may look terrific, it will read only as well as the thinking and writing that have gone into it. Many writers prudently store their data on disks and print their pages each time they finish a draft to avoid losing any material because of power failures or other problems.[D] It makes no difference how you write, just so you do. Now that you have developed a topic into a tentative thesis, you can assemble your notes and begin to flesh out whatever outline you have made.[E] Although this is an interesting issue, it has nothing to do with the thesis, which explains how the setting influences Sammy’s decision to quit his job. Instead of incl uding that paragraph, she added one that described Lengel’s crabbed response to the girls so that she could lead up to the A & P “policy” he enforces.[F] In the final paragraph about the significance of the setting in “A & P,” the student brings together the reasons Sammy quit his job by referring to his refusal to accept Lengel’s store policies.[G] By using the first draft as a means of thinking about what you want to say, you will very likely discover more than your notes originally suggested. Plenty of good writers don’t use outlines at all but discover ordering principles as they write. Do not attempt to compose a perfectly correct draft the first time around.Part CDirections:Read the following text carefully and then translate the underlined segments into Chinese. Your translation should be written clearly on ANSWER SHEET 2. (10 points)In his autobiography, Darwin himself speaks of his intellectual powers with extraordinary modesty. He points out that he always experienced much difficulty in expressing himself clearly and concisely, but (46) he believes that this very difficulty may have had the compensating advantage of forcing him to think long and intently about every sentence, and thus enabling him to detect errors in reasoning and in his own observations. He disclaimed the possession of any great quickness of apprehension or wit, such as distinguished Huxley. (47) He asserted, also, that his power to follow a long and purely abstract train of thought was very limited, for which reason he felt certain that he never could have succeeded with mathematics. His memory, too, he described as extensive, but hazy. So poor in one sense was it that he never could remember for more than a few days a single date or a line of poetry. (48) On the other hand, he did not accept as well founded the charge made by some of his critics that, while he was a good observer, he had no power of reasoning. This, he thought, could not be true, because the “Origin of Species” is one long argument from the beginning to the end, and has convinced many able men. No one, he submits, could have written it without possessing some power of reasoning. He was willing to assert that “I have a fair share of invention, and of common sense or judgment, such as every fairly successful lawye r or doctor must have, but not, I believe, in any higher degree.” (49) He adds humbly that perhaps he was “superior to the common run of men in noticing things which easily escape attention, and in observing them carefully.”Writing in the last year of his life, he expressed the opinion that in two or three respects his mind had changed during the preceding twenty or thirty years. Up to the age of thirty or beyond it poetry of many kinds gave him great pleasure. Formerly, too, pictures had given him considerable, and music very great, delight. In 1881, however, he said: “Now for many years I cannot endure to read a line of poetry. I have also almost lost my taste for pictures or music.” (50) Darwin was convinced that the loss of these tastes was not only a loss of happiness, but might possibly be injurious to the intellect, and more probably to the moral character.Section III WritingPart A51. Directions:You have just come back from Canada and found a music CD in your luggage that you forgot to return to Bob, your landlord there. Write him a letter to1) make an apology, and2) suggest a solution.You should write about 100 words on ANSWER SHEET 2.Do not sign your own name at the end of the letter. Use “Li Ming” instead.Do not write the address. (10 points)Part B52. Directions:Write an essay of 160-200 words based on the following drawing. In your essay, you should1) describe the drawing briefly,2) explain its intended meaning, and then3) give your comments.You should write neatly on ANSWER SHEET 2. (20 points)2008年硕士研究生考试英语真题详解完型填空1、答案:B解析:本题测试语义逻辑衔接。
UPS Rate Guide 2008说明书

Rate Guide JAMAICAEffective May 5, 2008T A B L E O F C O N T E N T S 1Table of ContentsHow to Process Your ShipmentsSelect the Service Determine the Weight Determine the Zone Determine the Rate Determine the Additional Charges International ServicesExportZone Chart Rate ChartUPS Worldwide Express SM UPS Worldwide Express Saver SM ImportZone Chart Rate ChartUPS Worldwide Express Saver Additional ChargesFuel Surcharge Address Correction Duty and Tax Forwarding Surcharge Extended Areas Shipping Charges Refusal by Consignee Missing or Invalid UPS Account Number Declared Value Proof of Delivery UPS Returns ®Service Over Maximum Limits .........................................2......................................2........................................2........................................2. (2)...............................................3..................................4.............................5...............................................6 (7)............................................8.........................................8..........................8............................................8.......................8.......................8............................................8..........................................8.......................................8.. (8)Contact the UPS Customer Service Center to obtain the most recent information about guarantee details, product limitations (UPS Express Envelope,Documents and Non Documents), service availability and delivery time commitments. You can also obtain this information when you visit us at .H O W T O P R O C E S S Y O U R S H I P M E N T S 2How to Process Your ShipmentsUPS offers a wide variety of door-to-door services with guaranteed delivery time and customs clearance.1. Select the Service UPS Worldwide Express SMUPS Worldwide Express Saver SM1 TO 3 DAYSGuaranteed delivery within one or two business days before 12 p.m. in the United States and Canada, and within two or three business days usually before 12:00 p.m. to main metropolitan areas in Europe, Asia and Latin America. This service is not available for your imports.Guaranteed delivery for export within one or two business days, before the end of day, in the United States and Canada,and before end of the second or third business day to main metropolitan areas in Europe, Asia, Latin America, Africa and other destinations. For your imports, the delivery is guaranteed before end of business day from more than 186 countries and territories worldwide.2. Determine the WeightRates are based on the total actual weight or the total dimensional weight of all packages in a shipment, whichever is greater.Dimensional WeightDimensional Weight is determined by using the International Air Transport Association (IATA) volumetric standard, which is subject to change without prior notice.1st stepCalculate the VolumeMultiply the length by the width by the height (each rounded to the nearest whole centimeters) of each package. For a multiple piece shipment, add the results for all the packages together. The total is the cubic size of the shipment.2nd stepDetermine the Dimensional WeightDivide the cubic size of the shipment by 6,000 to determine the dimensional weight in kilograms. Increase fractions of a weight to the next full kilogram. If the resulting dimensional weight is larger than the actual weight of the shipment, use the dimensional weight to calculate the rate.Shipment PricingShipment Pricing applies when shipping multiple packages to one destination on the same day and the packages are listed on the same UPS Air WayBillor Shipping Label. The sum of the weight of all packages is considered as one shipment.Shipment Pricing does not apply to UPS Express Envelopes, as these cannot be part of a multiple-package shipment. Shipment Pricing applies for all your exports and imports.To determine the applicable zone for the country of destination of your exports for UPS Worldwide Express and UPS Worldwide Express Saver, please refer to the Zone Chart on page 3.To determine the applicable zone for the country of origin of your imports for UPS Worldwide Express Saver, please refer to the Zone Chart on page 6.Note:If a zone number is not indicated in the corresponding column for the service you want to use, then UPS does not offer this service to that origin and/ordestination country.The rate is based on the service, the weight and zone.To determine if your shipment will incur any additional charges based on UPS additional services, please refer to the Additional Charges section on page 8 of this Rate Guide.3. Determine the Zone4. Determine the Rate5. Determine Additional ChargesLWHL x W x H 6,000Dimensional Weight=L =Length in centimeters W =Width in centimeters H =Height in centimetersE X P O R T S E R V I C EZone ChartDetermine the zone number according to destination country and selected service.ZonesDestination Express SaverReunion Islands ∞Romania ∞Russia ∞Rwanda San Marino ∞Saudi Arabia ∞SenegalSerbia & Montenegro ∞Seychelles Sierra Leone Singapore ∞Slovakia ∞Slovenia ∞Solomon Islands South Africa ∞South Korea ∞Spain ∞Sri Lanka ∞St. Kitts & Nevis ∞St. Lucia ∞St. Vincent & the Grenadines ∞Suriname ∞Swaziland Sweden ∞Switzerland ∞Taiwan ∞Tajikistan Tanzania Thailand ∞Togo TongaTrinidad & Tobago ∞Tunisia Turkey ∞Turkmenistan Turks & Caicos ∞Tuvalu Uganda Ukraine ∞United Arab Emirates ∞United Kingdom ∞United States ∞Miami Metro+ New York Metro+ Rest of U.S.A.Uruguay ∞U.S. Virgin Islands ∞Uzbekistan VanuatuVatican City (Italy) ∞Venezuela ∞VietnamWallis & Futuna Western Samoa Zambia ∞Zimbabwe6666466666466664463335644466466366636666412353664566666Express6646644444464123ZonesDestination Express SaverLatvia ∞Lebanon ∞Lesotho Liberia LibyaLiechtenstein ∞Lithuania ∞Luxembourg ∞Macau ∞Macedonia Madagascar ∞Madeira Island ∞Malawi Malaysia ∞Maldives ∞Mali Malta ∞Marshall Islands Martinique ∞Mauritania ∞Mauritius ∞Mayotte Melilla Mexico ∞Micronesia Moldova ∞Monaco ∞Mongolia Montserrat ∞Morocco ∞Mozambique Namibia NepalNetherlands ∞Netherlands Antilles ∞New Caledonia New Zealand ∞Nicaragua ∞Niger Nigeria ∞Norfolk Island ∞Northern Mariana Islands Norway ∞Oman ∞Pakistan Palau Panama ∞Papua New Guinea Paraguay ∞Peru ∞Philippines ∞Poland ∞Portugal ∞Puerto Rico ∞Qatar ∞Republic of Yemen66666464666464666636666566463666643665666646665655464366Express64644544454643ExceptionsAt the time of producing this Rate Guide, these countries were under embargo: Cuba, North Korea, Iran and Sudan.∞In certain countries, UPS offers the option of billing freight charges and/or duties and taxes to the consignee.For more information regarding this option, please contact your local UPS office.+ Please contact your local UPS office for more information about Miami Metro and New York Metro coverage.ZonesDestinationExpress SaverAfghanistan Albania ∞Algeria ∞American Samoa Andorra ∞Angola Anguilla ∞Antigua & Barbuda ∞Argentina ∞Armenia Aruba ∞Australia ∞Austria ∞Azerbaijan Azores Island ∞Bahamas ∞Bahrain ∞Bangladesh Barbados ∞Belarus ∞Belgium ∞Belize Benin Bermuda ∞Bhutan Bolivia ∞Bosnia & Herzegovina ∞Botswana ∞Brazil ∞British Virgin Islands ∞Brunei ∞Bulgaria ∞Burkina Faso Burundi Cambodia Cameroon Canada ∞Canary Islands ∞Cape VerdeCayman Islands ∞Central African Republic Ceuta ChadChannel Islands ∞Chile ∞China ∞Colombia ∞ComorosCongo (Brazaville) Congo Kinshasa (Zaire) Cook Islands Costa Rica ∞Croatia ∞Cyprus ∞Czech Republic ∞Denmark ∞66664633563446436636456365665366666626636664545666656664Express544646562545564ZonesDestination Express SaverDjibouti Dominica ∞Dominican Republic ∞East Timor Ecuador ∞Egypt ∞El Salvador ∞Equatorial Guinea Eritrea Estonia ∞Ethiopia ∞Faroe Islands Fiji Islands Finland ∞France ∞French GuianaFrench Polynesia & Tahiti Gabon Gambia Georgia Germany ∞Ghana Gibraltar ∞Greece ∞Greenland Grenada ∞Guadeloupe ∞Guam ∞Guatemala ∞Guernsey Island (United Kingdom)∞GuineaGuinea-Bissau Guyana ∞Haiti ∞Honduras ∞Hong Kong ∞Hungary ∞Iceland ∞India ∞Indonesia ∞IraqIreland ∞Israel ∞Italy ∞Ivory Coast ∞Japan ∞Jersey Island(United Kingdom)∞Jordan ∞Kazakhstan ∞Kenya ∞Kiribati Kuwait ∞Kyrgyzstan Laos633656566666644566664664633654665354666464646446666666Express644444664444E X P O R T S E R V I C ERATE CHARTUPS Worldwide ExpressSMThese rates are for door-to-door export shipments originating in Jamaica.For shipments over 31.5 Kg.For shipments weighing over 31.5 kilograms, the rate is calculated bymultiplying the total shipment weight (rounding up to the next full kilogram) by the price per kilograms shown at the bottom of the Rate Chart. UPS will bill the result of this calculation or the Minimum Rate that is indicated, whichever is greater.International air shipments may be subject to the Warsaw Convention, including its limitations and responsibilities.Any fraction of a kilogram is rounded up to the next full kilograms.Envelope 0.5 Kg.1.01.52.02.53.03.54.04.55.05.56.06.57.07.58.08.59.09.510.010.511.011.512.012.513.013.514.014.515.015.516.016.517.017.518.018.519.019.520.020.521.021.522.022.523.023.524.024.525.0US$21.80 25.20 27.60 30.00 31.40 32.70 34.30 35.80 37.20 38.60 40.60 41.10 43.00 45.00 46.20 47.50 48.90 50.50 51.80 53.50 54.90 56.50 58.70 61.10 62.40 64.00 65.70 67.20 68.90 70.30 72.10 73.60 74.60 75.60 76.80 77.90 78.80 80.10 81.10 82.10 83.50 85.00 86.90 88.90 90.90 92.90 94.90 96.90 98.90 100.90 102.90US$23.30 26.30 29.00 31.00 32.40 34.30 35.30 36.70 38.30 39.80 41.10 44.80 46.30 47.80 49.50 51.10 52.50 54.20 55.90 57.40 59.00 60.60 62.20 63.80 65.40 67.00 68.50 70.10 71.80 73.30 75.00 76.50 78.10 79.70 81.30 82.30 83.30 84.40 85.40 86.50 87.40 87.50 88.50 90.30 92.20 94.20 96.10 98.10 100.10 102.10 104.10US$27.60 31.60 32.90 35.20 37.40 39.30 41.40 42.80 44.70 47.10 49.10 50.10 52.20 55.20 58.40 61.90 65.90 69.30 71.20 73.50 75.60 77.80 79.90 82.00 84.20 86.30 88.40 90.60 92.70 95.00 96.90 99.10 101.30 103.50 105.70 107.60 108.90 109.80 111.00 112.50 115.30 116.40 119.10 121.80 124.50 127.30 130.10 132.80 135.60 138.30 141.10US$30.60 34.50 37.00 39.20 41.40 43.70 45.90 48.50 50.70 52.90 55.20 56.70 59.10 61.50 63.80 66.10 68.40 70.90 73.20 75.70 78.00 80.30 82.70 85.00 87.40 89.80 92.20 94.60 96.90 99.20 101.70 103.90 106.30 108.70 111.00 113.40 115.80 118.20 120.60 122.80 124.80 127.90 131.00 133.90 136.90 139.80 142.80 145.80 148.80 151.70 154.70US$33.30 37.00 39.20 41.40 43.90 46.50 49.20 51.80 54.30 57.10 59.60 62.20 66.50 69.10 71.60 74.20 76.90 79.50 82.10 84.70 87.40 90.00 93.10 96.40 99.50 102.60 105.70 108.80 112.00 115.20 118.30 121.30 124.40 127.60 130.70 133.80 137.00 140.10 141.50 142.80 145.20 148.50 151.90 155.30 158.80 162.40 166.00 169.50 173.10 176.70 180.2025.526.026.527.027.528.028.529.029.530.030.531.031.5Price per Kg.Minimum RateUS$104.90 106.90 108.90 110.90 112.90 114.90 116.90 118.90 120.90 122.90 124.90 126.90 128.204.05 128.20US$106.10 108.10 110.10 111.90 113.90 115.90 117.90 119.80 121.80 123.80 125.80 127.70 129.704.10 129.70US$143.90 146.70 149.40 152.20 154.90 157.70 160.40 163.20 165.90 168.70 171.40 174.20 176.805.60 176.80US$157.70 160.70 163.70 166.70 169.60 172.60 175.60 178.60 181.60 184.60 187.60 189.80 193.906.10 193.90US$183.80 187.40 190.90 194.50 198.10 201.70 205.20 208.60 212.10 215.60 219.10 222.40 223.007.05 223.00US$39.20 43.00 45.40 47.60 50.50 53.20 56.10 58.80 61.60 64.40 67.20 68.10 70.40 73.00 76.20 80.10 82.40 85.60 88.70 91.90 95.00 98.10 101.20 104.40 107.60 110.70 113.80 116.90 120.10 123.30 126.40 129.50 132.70 135.80 138.90 142.10 145.20 148.40 151.50 154.60 157.70 161.60 165.40 169.30 173.10 177.00 180.80 184.70 188.50 192.40 196.20US$200.00 203.90 207.80 211.70 215.40 219.30 223.20 227.10 230.80 234.70 238.60 242.50 244.507.75 244.50For shipments over 31.5 Kg.Zones 123456Zones 123456E X P O R T S E R V I C ERATE CHARTUPS Worldwide Express SaverSMThese rates are for door-to-door export shipments originating in Jamaica.For shipments over 31.5 Kg.For shipments weighing over 31.5 kilograms, the rate is calculated bymultiplying the total shipment weight (rounding up to the next full kilogram) by the price per kilograms shown at the bottom of the Rate Chart. UPS will bill the result of this calculation or the Minimum Rate that is indicated, whichever is greater.International air shipments may be subject to the Warsaw Convention, including its limitations and responsibilities.Any fraction of a kilogram is rounded up to the next full kilograms.Envelope 0.5 Kg.1.01.52.02.53.03.54.04.55.05.56.06.57.07.58.08.59.09.510.010.511.011.512.012.513.013.514.014.515.015.516.016.517.017.518.018.519.019.520.020.521.021.522.022.523.023.524.024.525.0US$21.4024.7027.1029.4030.8032.1033.6035.1036.5037.8039.8040.3042.2044.1045.3046.6047.9049.3050.5052.2053.6055.1057.3059.6060.9062.4064.1065.6067.2068.6070.3071.8072.8073.8074.9076.0076.9078.1079.1080.1081.1082.7084.7086.7088.6090.6092.6094.6096.6098.50100.50US$22.8025.8028.4030.4031.8033.6034.6036.0037.5039.0040.3043.9045.4046.9048.5050.1051.5053.1054.8056.3057.8059.4061.0062.5064.1065.7067.2068.7070.4071.9073.5075.0076.6078.1079.7080.7081.7082.7083.7084.8085.7085.8085.9087.8089.8091.7093.7095.7097.7099.70101.70US$27.1030.4031.6033.8036.0037.8039.8041.2043.0045.3047.2048.2050.2053.1056.2059.5063.4066.6068.5070.7072.7074.8076.8078.8081.0083.0085.0087.1089.1091.3093.2095.3097.4099.50101.60103.50104.70105.60106.70108.20110.90111.90114.50117.10119.70122.40125.10127.70130.40133.00135.70US$30.0033.8036.3038.4040.6042.8045.0047.5049.7051.9054.1055.6057.9060.3062.5064.8067.1069.5071.8074.2076.5078.7081.1083.3085.7088.0090.4092.7095.0097.3099.70101.90104.20106.60108.80111.20113.50115.90118.20120.40122.40125.40128.40131.30134.20137.10140.00142.90145.90148.70151.70US$32.6036.3038.4040.6043.0045.6048.2050.8053.2056.0058.4061.0065.2067.7070.2072.7075.4077.9080.5083.0085.7088.2091.3094.5097.50100.60103.60106.70109.80112.90116.00118.90122.00125.10128.10131.20134.30137.40138.70140.00142.40145.60148.90152.30155.70159.20162.70166.20169.70173.20176.7025.526.026.527.027.528.028.529.029.530.030.531.031.5Price per Kg.Minimum RateUS$102.40104.30106.30108.30110.20112.20114.20116.20118.10120.10122.10123.90125.203.95125.20US$103.70105.70107.70109.70111.60113.60115.60117.60119.60121.60123.60125.60127.504.00127.50US$138.40141.10143.80146.30148.90151.60154.20156.90159.50162.20164.80167.50170.005.35170.00US$154.50157.50160.30163.30166.30169.20172.10175.00178.00180.80183.80185.90186.405.90186.40US$180.20183.70187.20190.70194.20197.70201.20204.40207.90211.30214.80218.30218.606.90218.60US$38.4042.2044.5046.7049.5052.2055.0057.6060.4063.1065.9066.8069.0071.6074.7078.5080.8083.9087.0090.1093.1096.2099.20102.40105.50108.50111.60114.60117.70120.90123.90127.00130.10133.10136.20139.30142.40145.50148.50151.60154.60158.40162.20166.00169.70173.50177.30181.10184.80188.60192.40US$196.10199.90203.70207.50211.20215.00218.80222.60226.30230.10233.90237.70239.707.60239.70For shipments over 31.5 Kg.Zones 123456Zones 123456I M P O R T S E R V I C EZone ChartDetermine the zone number according to country of origin and selected service.ZonesOriginExpress SaverAlbania AlgeriaAmerican Samoa Angola AnguillaAntigua & Barbuda Argentina Armenia Aruba Australia Austria Azerbaijan Azores Island Bahamas Bahrain Bangladesh Barbados Belarus Belgium Benín Bermuda Bhutan BoliviaBosnia & Herzegovina Botswana BrazilBritish Virgin Islands Brunei Bulgaria Burkina Faso Cambodia Cameroon CanadaCanary Islands Cape Verde Cayman Islands Ceuta ChadChannel Islands Chile China Colombia ComorosCongo (Brazaville) Congo Kinshasa (Zaire) Costa Rica Croatia CyprusCzech Republic Denmark Djibouti DominicaDominican Republic Ecuador EgyptEl Salvador Eritrea Estonia Ethiopía Fiji Islands Finland FranceFrench Polynesia & Tahiti Gabon 6666113615666166166616366316666626616643536663666661136366666666ZonesOrigin Express SaverGambia Georgia Germany Ghana Gibraltar Greece Grenada Guadeloupe Guam GuatemalaGuernsey Island (United Kingdom)GuineaGuinea-Bissau Guyana Haiti Honduras Hong Kong Hungary Iceland India Indonesia Iraq Ireland Israel ItalyIvory Coast JapanJersey Island (United Kingdom)Jordan Kazakhstan Kenya Kuwait Kyrgyzstan Laos Latvia Liberia LibyaLiechtenstein Lithuania Luxembourg Macau Macedonia Madagascar Madeira Island Malawi Malaysia Mali Malta Martinique Mauritania Mauritius Mayotte Melilla Mexico Moldova Monaco Mongolia Montserrat Morocco Namibia NepalNetherlandsNetherlands Antilles New Caledonia 6646641163466313566656466654666666666666666665661666626661666416ZonesOrigin Express SaverNew Zealand Nicaragua Niger NigeriaNorthern Mariana Islands Norway Oman Pakistan Panama Paraguay PeruPhilippines Poland Portugal Puerto Rico QatarRepublic of Yemen Reunion Islands Romania Russia San Marino Saudi Arabia SenegalSerbia & Montenegro Seychelles Sierra Leone Singapore Slovakia Slovenia South Africa South Korea Spain Sri LankaSt. Kitts & Nevis St. LuciaSt. Vincent & the Grenadines Surinam Sweden Switzerland Syria Taiwan Tanzania Thailand TogoTrinidad & Tobago Tunisia Turkey Uganda UkraineUnited Arab Emirates United Kingdom United States UruguayU.S. Virgin Islands UzbekistanVatican City (Italy) Venezuela VietnamWestern Samoa Zambia Zimbabwe6366666633356616666666666656665661113666565616666642316636666I M P O R T S E R V I C ERATE CHARTUPS Worldwide Express SaverSMThese rates are for door-to-door imports to Jamaica with Consignee* payment option.For shipments over 31.5 Kg.For shipments weighing over 31.5 kilograms, the rate is calculated bymultiplying the total shipment weight (rounding up to the next full kilogram) by the price per kilograms shown at the bottom of the Rate Chart. UPS will bill the result of this calculation or the Minimum Rate that is indicated, whichever is greater.International air shipments may be subject to the Warsaw Convention, including its limitations and responsibilities.* All charges will be billed to the consignee.When the payer is located in a third country (not origin country nor destination country), the prepaid rates of the origin country will apply, unless otherwise agreed upon between UPS and the customer.Any fraction of a kilogram is rounded up to the next full kilograms.Envelope 0.5 Kg.1.01.52.02.53.03.54.04.55.05.56.06.57.07.58.08.59.09.510.010.511.011.512.012.513.013.514.014.515.015.516.016.517.017.518.018.519.019.520.020.521.021.522.022.523.023.524.024.525.0US$28.1041.8046.3050.8056.6062.5067.4072.1081.2090.2097.50102.30105.90109.70113.70118.40123.20127.60134.20139.60143.50147.10152.20156.00160.10163.90168.10172.40176.60181.40186.00190.70195.40200.00204.80209.50214.20218.90223.70228.40233.10237.80242.60247.20251.80256.50261.30266.00270.70275.40280.20US$28.4044.0048.5052.9058.8064.7069.6074.2083.3092.4099.70104.40108.10111.70115.90120.60125.30129.70136.30141.70145.70149.30154.40158.00162.30166.00170.30174.60178.70183.40188.20192.90197.60202.30207.10211.80216.40221.10225.70230.50235.20239.90244.60249.40254.10258.80263.50268.30272.90277.50282.20US$35.7049.5053.9058.3064.2070.1075.0079.6088.7097.80105.10109.90113.50117.20121.30126.00130.70135.20141.70147.10151.10154.70159.80163.40167.70171.40175.70180.00184.10188.80193.60198.30203.00207.70212.50217.20221.90226.50231.10235.90240.60245.30250.00254.80259.50264.20268.90273.70278.40282.90287.60US$47.6065.7070.1074.6080.4086.4091.3095.80105.00114.00121.30126.10129.70133.40137.50142.20146.90151.40157.90163.30167.30171.00176.10179.70183.90187.60192.00196.20200.40205.00209.80214.50219.20223.90228.70233.40238.10242.80247.50252.10256.80261.50266.20271.00275.70280.40285.10289.90294.60299.30303.90US$50.9076.5081.0085.4091.3097.20102.10106.70115.80124.80132.10136.90140.60144.20148.40153.00157.70162.20168.70174.10178.10181.80186.90190.50194.70198.40202.80207.10211.20215.90220.60225.30230.00234.70239.50244.20248.90253.60258.30263.10267.60272.30277.00281.80286.50291.20295.90300.70305.40310.10314.8025.526.026.527.027.528.028.529.029.530.030.531.031.5Price per Kg.Minimum RateUS$284.90289.60294.30299.00303.70308.30313.00317.70322.50327.20331.90336.60341.4010.80341.40US$287.00291.70296.40301.10305.90310.60315.30320.00324.70329.40334.10338.70343.4010.90343.40US$292.40297.10301.80306.50311.30316.00320.70325.40330.10334.80339.50344.10348.8011.05348.80US$308.70313.30318.00322.70327.50332.20336.90341.60346.40351.00355.70360.40365.1011.55365.10US$319.50324.20328.80333.50338.30343.00347.70352.40357.20361.90366.50371.20375.9011.90375.90US$67.1092.7097.20101.70107.50113.40118.30122.90132.00141.10148.40153.10156.80160.40164.60169.30173.90178.40185.00190.40194.30198.00203.10206.80211.00214.60219.00223.30227.50232.20236.90241.50246.20250.90255.70260.40265.10269.80274.50279.30284.00288.60293.30298.00302.70307.40312.10316.90321.60326.30331.00US$335.80340.40345.10349.80354.60359.20363.90368.60373.40378.10382.80387.40392.1012.40392.10For shipments over 31.5 Kg.Zones 123456Zones 123456A D D I T I O N A L C H A R G E SA D D I T I O N A L C H A R G E S 8Fuel SurchargeUPS reserves the right to charge a fuel surcharge for all deliveries without prior notification.Address CorrectionA fee of US$8.75 will apply for each package that requires an address correction. The maximum address fee will never exceed US$35.00 per shipment.Duty and Tax Forwarding SurchargeThis charge applies when duties and taxes are charged to the shipper or a third party that is not located in the destination country. This fee covers the cost incurred to bill the duties and taxes outside of the destination country.When you choose this billing option, a fee of US$16.00 will apply per shipment.Extended AreasFor each shipment to an extended area, UPS will charge US$20.00 per shipment or US$0.50 per kilogram, whichever is greater. For moreinformation, refer to the Extended Areas Guide in .Shipping Charges Refusal by Consignee If the consignee refuses to pay the shipping charges, an administrative fee of US$10.75 will be charged per shipment to the shipper, in addition to the return shipping charges and any other fee that is incurred during the return process.Missing or Invalid UPS Account Number A fee of US$6.25 per shipment will be applied for a missing or invalid account number when the account number is missing, the account number is not the correct number for the bill-to party, or if it is the account number for a receiver or third party who fails to pay the shipping charges.Declared ValueA shipment is automatically protected against loss or damage up to US$100.00 per package.For each shipment with a declared value over US$100.00, US$0.40 will be charged for each additional US$100.00 or fraction thereof, with a minimum of US$1.20.Protection against loss or damage excludes or does not provide protection to items that have been incorrectly packed, that have been packed with inadequate materials or with adhesive tape that does not meet the requirements established by UPS. It is the shipper’s responsibility to make sure that the shipping materials used are adequate.The declared value fee can be charged to the shipper, consignee or a third party.The maximum declared value and the maximum legal responsilibity of UPS for international service is US $50,000.00 per shipment.Proof of Delivery Signature RequiredWhen the customer selects this service, the driver will require a signature in order to complete the delivery. A fee of US$2.75 per shipment will apply.Adult Signature RequiredThe driver will require the signature of an adult 18-21 years of age or older at the time ofdelivery. If no adult is available, UPS will make a second or third delivery attempt. Indirect deliveries or "deliver to" notes will not be accepted. A fee of US$3.25 per shipment will apply.An adult signature is required when shipping international special products such as tobacco and/or alcohol.UPS Returns ®ServiceThis service is offered to UPS WorldShip ®version 10.0 users, UPS Internet Shipping or other UPS Online compatible services. UPS Returns service may not be available to or from all countries.An additional fee will apply to the following:• For each UPS Print Return Label requested -US$0.50.• For each Electronic Return Label requested -US$1.00.• For each UPS Print and Mail Return Label requested to be sent by mail - US$2.25.• For each Web Return Label requested online -US$1.50.• For the first pick-up attempt of a package to be returned (One Attempt) - US$4.00.• For each package that cannot be picked up at the first attempt, UPS will attempt to pick up in the next two business days (Three Attempts) -US$6.00.Over Maximum LimitsPackages with an actual weight of more than 70 kilograms, or packages that, when measured to determine the billable weight, exceed 270 centimeters in length, or exceed a total of 330 centimeters in length and girth [(2 x Width) + (2 x Height)] combined.If found in the UPS system beginning July 2008,they will be subject to one or more of the following additional charges:• Over Maximum Weight: US$50.00• Over Maximum Length: US$50.00• Over Maximum Size: US$50.00Additional charges are subject to UPS Terms and Conditions. For more information about the availability of these Additional Charges, please contact your local UPS office.EXPORT AND IMPORTAdditional Charges®018793-JM-E Rev. 5/08© Copyright 2008. United Parcel Service of America, Inc. UPS, the UPS brandmark and the color brown are trademarks of United Parcel Service of America, Inc. All rights reserved.UPS JamaicaKingstonAirpak ExpressAirways International Limited Tinson Pen Aerodrome Marcus Garvey Drive Kingston 11Tel.: 876-923-0371Fax: 876-923-5089Ocho Rios Shop # 57,Ocean Village Shopping Centre Ocho RiosTel.: (876) 974-0910-1Fax: (876) 795-3080Montego BaySangster International Airport Montego Bay, St. James Tel.: 940-0003-4Fax: (876) 940-0005NegrilNegril AerodromeNorman Manley Boulevard NegrilTel.: (876) 957-5051Fax: (876) 95-9967Mandeville Shop # 12E17 Caledonia Road MandevilleTel.:(876) 962-5101-2Fax: (876) 961-5487May Pen B&J Mall44 Main Street May PenTel.: (876) 986-7403Fax: (876) 986-7403Savanna La Mar82 Great George Street Savanna-la-MarTel.: (876) 918-1238Fax (876) 918-1869Half-Way-Tree Shop #8Miel Plaza1 Molynes Road Kingston 10Tel.: (876) 754-5298-9Fax: (876) 754-5300Liguanea Shop #210 Northside Plaza Northside Drive Kingston 6Tel.: (876)927-2408; 927-2488Fax: (876) 970-2659Website: 。
国际贸易key terms的中文解释

Chapter One Barter trade: 易货贸易Credit reference: 资信证明Direct transit trade: 直接过境贸易Economies of scale: 规模经济Commodity inspection: 商检Customs clearance: 清关Documentation: 文件Entrepot trade: 转口贸易Comparative advantage : 比较优势Direct trade: 直接贸易Domestic trade: 国内贸易Export license: 出口许可证Export procedures: 出口手续General trade: 一般贸易Import trade: 进口贸易International trade: 国际贸易Special trade: 特殊贸易Export trade: 出口贸易Import license: 进口许可证Indirect trade: 间接贸易Invisible trade: 无形贸易Transit trade: 过境贸易Free-liquidation trade: 自由结算贸易Import procedures: 进口手续Indirect transit trade: 间接过境贸易Payment: 支付Visible trade: 有形贸易Chapter Two Actual delivery: 实际交货Appropriation: 划拨Arrival contract: 到达合同(或目的地契约)Customary practice: 报关实务Customs clearance: 清关Customs formalities: 报关Delivery: 交货Inspection: 商检Means of transport: 运输工具Mode of transport: 运输方式Obligation: 义务Shipment contract: 转运合同Shipment notice: 转船通知Symbolic delivery:象征性交货Transfer of risk: 风险转移Chapter Three Acceptance: 受盘Commission: 佣金Counter-offer: 还盘Discount:折扣;贴现Enquiry: 询盘Export cost for foreign: exchange: 出口换汇成本Exchange: 汇兑Export profit margin:出口盈亏率Final price: 最终价格Total price: 总价Unfixed price: 非固定价Firm offer: 实盘Initial price: 最初价格Irrevocable offer: 不可撤销发盘Material price index: 原材料价格指数Money of account: 计价货币Money of payment: 支付货币Net price: 净价Non-firm offer: 虚盘Unit price: 单价Validity period: 有效期Offer: 发盘;报盘Offeree: 受盘者Offeror: 发盘者Price adjustment clause: 价格调整条款Price including commission: 含佣价Quotation: 配额Rebate: 回扣Revocation of an offer: 撤销报盘Wage index: 工资指数Withdrawal of an offer: 撤回报盘Chapter Four Bar code: 条形码Conditioned weight: 公量Confirming sample: 确认样Counter sample: 回样/ 对等样Gross for net: 以毛作净Gross weight: 毛重Indicative mark: 指示性标志More or less clause: 溢短装条款Net weight: 净重Quality tolerance: 品质公差Quantity latitude: 数量机动幅度Reference sample: 参考样Regain: 回潮率Sale by actual commodity: 凭实际货物买卖Sale by actual quality: 凭实际品质买卖Sale by description or illustrations: 凭说明书或图样买卖Sale by grade: 凭等级买卖Sale by origin: 凭产地名称买卖Sale by sample: 凭样品买卖Sale by specifications: 凭规格买卖Sale by standard: 凭标准买卖Sale by trade mark or brand name: 凭商标或品牌买卖Shipping mark: 运输标志Shipping package: 运输包装Shipping sample: 装船样Tare: 皮重Neutral packing: 中性包装Chapter FiveSea transportation:海运Air transportation: 空运Rail(way )transportation: 铁路运输Road transportation:陆路运输Measurement ton:尺码吨Freight ton:运费吨Ad valorem: 从价运费Charter(tramp):不定期货船Voyage charter:程租船Time charter:期租船Liner/gross terms:班轮条件Containerization: 集装箱运输Liners transportation: 班轮运输Charter transportation:租船运输Freight rates:运输率Lay day:装卸天数Demurrage: 滞期费Straight B/L: 记名提单Order B/L:指示提单Stale B/L:过期提单Ante-dated B/L:倒签提单Advanced B/L:预签提单Surcharge:附加费Additional:附加费Basic freight:基本运费Weight ton:重量吨Sea waybill: 海运单Air waybill:空运单Partial shipments:分批装运Transshipment: 转船Time of delivery: 交货期Port of shipment: 转运港Port of destination:目的港Optional port: 选择港Chapter Six Actual total loss: 实际全损Fortuitous accidents: 意外事故Insurance coverage: 保险险别Claimant: 索赔人Franchise: 免赔率Insurance policy: 保险单Combined certificate: 联合凭证General average: 共同海损Insurance premium: 保险费Constructive total loss: 推定全损General risks: 一般外来风险Insurance rate: 保险费率Contribution: 分摊Indemnity: 赔偿金Natural calamity: 自然灾害Exclusions: 除外责任Insurable interest: 保险标的物Open policy: 预约保单External risks: 外部风险Insurance certificate: 保险凭证Partial loss: 部分损失Extraneous risks: 外来风险Insurance claim: 保险索赔Particular average: 单独海损Perils of the sea: 海上风险Proximate cause: 近因(原则)Special risks: 特殊外来风险Subject matter: 保险标的Subrogation: 代为求偿权Sum insured: 投保金额The insured/insurant: 被保险人The insurer: 保险人Total loss: 全部损失Underwriter: 承保人Unexpected accidents: 意外事故Utmost good faith: 最大诚信原则Chapter Seven Acceptance: 承兑Anticipatory credit: 预支信用证Back-to-back credit: 背对背信用证Beneficiary: 受益人Bill of exchange: 汇票Check: 支票Clean bill: 光票Clean credit: 光票信用证Confirmed L/C: 保兑信用证Deferred payment: 延期付款Discount: 折扣,贴现Documentary bill:跟单汇票Documentary letter of credit: 跟单信用证Endorsement: 背书Factoring: 保理业务Forfeiting: 包买票据Irrevocable L/C: 不可撤销信用证Paying instrument: 支付工具Payment by installments: 分期付款Payment in advance: 预付Payment term: 支付方式Presentation: 提示Promissory note: 本票Reciprocal credit: 对开信用证Red clause credit: 红条款信用证Remittance: 汇付Revocable L/C: 可撤销信用证Revolving credit: 循环信用证Sight draft: 即期汇票Sight L/C: 即期信用证Standby L/C: 备用信用证Tenor: 汇票期限Time/usance draft: 远期汇票Transferable L/C: 可转让信用证Chapter EightBill of exchange(a draft): 汇票Bill of lading:海运提单Booking note:托运单Certificates of origin:原产地证明书Cleanness: 清洁Commercial invoice: 商业发票Completeness: 完整性Conciseness:简洁性Consular invoices:领事发票Correctness: 准确性Customs declaration:报关Customs invoices: 海关发票Export license: 出口许可证Inspection certificate:检验证书Insurance policy: 保险单Letters of credit: 信用证Packing list: 装箱单Proforma invoices: 形式发票Promptness:敏捷Sales of contract: 销售合同Shipping advice: 装船通知Shipping order:装货单Chapter NineArbitration 仲裁Arbitration agreement: 仲裁协议Arbitration award: 仲裁裁决Arbitration body: 仲裁机构Arbitration tribunal: 仲裁法庭Arbitration hearing: 仲裁审理Arbitrator: 仲裁员Breach of contract: 违约Claim: 索赔Claimant: 索赔人Claimee: 被索赔人Dispute:纠纷Force majeure: 不可抗力Inspection: 检验Inspection certificate:检验证书Inspection body: 检查局Litigation: 诉讼Mediation: 调停Negotiation: 谈判Non-statutory inspection: 非法定检验statutory inspection: 法定检验panel of arbitration: 仲裁小组penalty clause: 罚金条款。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
共10页KEY TERMS第一单元application software应用软件basic application基本应用软件communication device通信设备compact disc (CD)光盘computer competency计算机能力Connectivity连通性Data数据database file数据库文件desktop computer台式计算机device driver磁盘驱动程序digital versatile disc(DVD)数字多用途光盘digital video disc(DVD)数字多用途光盘document file文档文件end user终端用户floppy disk软盘handheld computer手持计算机hard disk硬盘Hardware硬件High definition高清Information信息information system信息系统information technology信息技术input device输入设备Internet因特网Keyboard键盘mainframe computer大型机Memory内存Microcomputer微型机Microprocessor微处理器midrange computer中型机Minicomputer小型计算机Modem调制解调器Monitor监视器Mouse鼠标Network网络notebook computer笔记本电脑operating system操作系统optical disk光盘output device输出设备palm computer掌上电脑Peoplepersonal digital assistant(PDA)个人数字助理presentation file演示文稿primary storage主存Printer打印机Procedure规程Program程序random access memory随机存储器secondary storage device辅存Software软件specialized application专门应用软件Supercomputer巨型机system software系统软件system unit系统单元tablet PC平板电脑Utility实用程序wireless revolution无线革命worksheet file工作表第三单元analytical graph分析图application software应用软件Autocontent Wizard内容提示向导basic applications基础应用软件bulleted list项目符号列表business suite商业套装软件Button按键Cell单元格character effect字效Chart图表Column列Computer trainer计算机培训员Contextual tab上下文标签Database数据库database management system (DBMS)数据库管理系统database manager数据库管理员Design template设计模板dialog box对话框Document文件Editing编辑Field字段find and replace查找和替换Font字体font size字号Form窗体Format格式Formula公式Function函数Galle ries图库grammar checker语法检查器graphical user interface (GUI)图形用户界面home software家庭软件home suite家庭套装软件Icons图标integrated package集成组件Label标签master slide母板Menu菜单menu bar菜单栏numbered list编号列表numeric entry数值型输入personal software个人软件personal suite个人套装软件Pointer指针presentation graphic图形演示文稿productivity suite生产力套装软件Query查询Range范围Recalculation重算Record记录relational database关系型数据Report报表Ribbons功能区、格式栏Row行Sheet工作表Slide幻灯片software suite软件套装Sort排序specialized applications专用应用程序specialized suite专用套装软件speech recognition语音识别spelling checker拼写检查器spreadsheet电子表格system software系统软件Table表格text entry文本输入Thesaurus[θisɔ:rəs]分类词汇集Toolbar工具栏user interface用户界面utility suite实用套装软件what-if analysis变化分析Window窗口word processor文字处理软件word wrap字回行workbook file工作簿W orksheet工作表第四单元Animation动画artificial intelligence (AI)人工智能artificial reality虚拟现实audio editing software音频编辑软件bitmap image位图Blog博客Buttons按键clip art剪辑图Desktop publisher桌面发布desktop publishing program桌面印刷系统软件drawing program绘图程序expert systems专家系统Flash动画fuzzy logic模糊逻辑graphical map框图graphics suite集成图HTML editors HTML编辑器illustration program绘图程序Image editors图像编辑器image gallery图库immersive experience沉浸式体验industrial robots工业机器人Interactivity交互性knowledge bases知识库knowledge-based system知识库系统Link链接mobile robot移动式遥控装置Morphing渐变Multimedia多媒体multimedia authoring programs多媒体编辑程序page layout program页面布局程序perception systems robot感知系统机器人Photo editors图像编辑器Pixel[piksəl]像素raster image光栅图像Robot机器人Robotics机器人学stock photographs照片库story boards故事版Vector[vektə]矢量vector illustration矢量图vector image矢量图象video editing software视频编辑软件virtual environments虚拟环境virtual reality虚拟现实virtual reality modeling language (VRML)虚拟现实建模语言virtual reality wall虚拟现实墙VR虚拟现实W eb authoring网络编程W eb authoring program网络编辑程序W eb log网络日志W eb page editor网页编辑器第五单元Add Printer Wizard添加打印机向导Antivirus program反病毒程序Backup备份backup program备份程序Booting启动、引导cold boot冷启动computer support specialist计算机支持专家Dashboard widgets仪表盘Desktop桌面desktop operating system桌面操作系统device driver磁盘驱动程序diagnostic program诊断程序dialog box对话框Disk Cleanup磁盘清理Disk Defragmenter磁盘碎片整理器Driver驱动器embedded operating systems嵌入式操作系统File文件file compression program文件压缩程序Folder文件夹Fragmented碎片化graphical user interface (GUI)图形用户界面Help帮助Icon图标language translator语言编译器leopard[lepəd]雪豹操作系统LinuxMac OS Mac操作系统Mac OS XMenu菜单Multitasking多任务处理network operating systems(NOS)网络操作系统network server网络服务器One Button Checkup一键修复operating system操作系统Platform平台Pointer指针Sectors[sektə]扇区software environment软件环境Spotlight聚光灯stand-alone operating system独立操作系统system software系统软件Tiger老虎操作系统Tracks磁道troubleshooting program故障检修程序Uninstall program卸载程序UNIXuser interface用户界面Utility实用程序utility suite实用套装软件Virus[vaiərəs]病毒warm boot热启动Window视窗Windows视窗操作系统Windows Update Windows更新Windows VistaWindows XP第六单元AC adapter 交流适配器Accelerated graphics port(AGP):图形加速端口Arithmetic-logic unit(ALU):算术逻辑单元Arithmetic operation:算术运算ASCII美国标准信息交换码Binary coding schemes:二进制编码制Bit:位Bus:总线Bus line:总线Byte:字节Cable:电缆Cache memory:高速缓存carrier package 封装物Central processing unit (CPU):中央处理器Chip:芯片Clock speed时钟速度Complementary metal-oxide semiconductor:互补金属氧化物半导体Computer technician计算机工程师Control unit:控制单元Coprocessor协处理器Desktop system unit:桌面系统单元Digital数字的Dual-core chips双核芯片EBCDIC:扩展二进制编码的十进制交换码Expansion bus扩展总线Expansion card扩展卡Expansion slot扩展槽FireWire port:火线接口Flash memory闪存Graphics card图形适配卡Graphics coprocessor图形协处理器Handheld computer system unit 手持计算机系统单元Industry standard architecture (ISA)工业标准结构Infrared Data Association(IrDA)红外线传输模组Integrated circuit:集成电路Laptop computer膝式计算机Logical operation逻辑运算Microprocessor:微处理器Motherboard:主板Musical instrument digital interface (MIDI)乐器数字接口Network adapter card网络适配卡Network interface card(NIC)网络接口卡Notebook system unit:笔记本Parallel ports:并行端口Parallel processing并行处理Pc card: :个人计算机插卡PCI Express(PCIe)Peripheral component interconnect (PCI):外围部件互联Personal digital assistant (PDA) 个人数字助理Plug and play:即插即用Port:端口Power supply unit 供电设备Processor:处理器RAM cache: RAM高速缓存Random-access memory (RAM):随机存储器Read-only memory (ROM):只读存储器RFID tag射频识别标签Semiconductor:半导体serial ATA(SATA)串行ATA接口规范Serial ports:串行端口Silicon chip:硅芯片Slot:插槽Smart card:智能卡sound card声卡System board:系统板System cabinet:主机System clock:系统时钟System unit:系统单元tablet PC平板式电脑tablet PC system unit平板式电脑系统单元TV tuner card:电视调频卡Unicode:统一字符编码标准Universal serial bus (USB):通用串行总线Universal serial bus (USB) port:通用串行总线端口Virtual memory:虚拟存储器W ord:字第七单元active-matrix monitor有源矩阵显示器bar code条形码bar code reader条形码阅读器cathode ray tube monitor (CRT)阴极射线管显示器Clarity清晰度combination key组合键cordless mouse无线鼠标data projector数据投影仪digital camera数码照相机Digital media player数字媒体播放器Digital music player数码音乐播放器digital video camera数码影像摄录机dot pitch点距dot-matrix printer针式打印机dots-per-inch (dpi)点每英寸dual-scan monitor双向扫描显示器dumb terminal哑终端e-book电子图书阅读器ergonomic keyboard人体工程学键盘Fax machine传真机flat-panel monitor平面显示器Flatbed scanner平板扫描仪flexible keyboard可变形键盘handwriting recognition software手写识别软件Headphones耳机high-definition television (HDTV)高清电视ink-jet printer喷墨打印机intelligent terminal智能终端Internet telephone网络电话Internet telephony网络电话IP Telephony IP电话Joystick游戏杆Keyboard键盘laser printer激光打印机light pen光笔Liquid crystal display(LCD)液晶显示器Magnetic card reader磁卡阅读器magnetic-ink character recognition (MICR)磁性墨水字符识别mechanical mouse机械鼠标Monitor显示器Mouse鼠标mouse pointer鼠标指针multifunction device (MFD)多功能设备network terminal网络终端numeric keypad数字小键盘optical-character recognition (OCR)光学字符识别optical-mark recognition (OMR)光学标记识别optical mouse光电鼠标Optical scanner光电扫描仪passive-matrix monitor无源矩阵显示器PDA keyboard PDA键盘personal laser printer个人激光打印机photo printer照片打印机picture elements 有效像素Pixel像素Pixel pitch像素间距platform scanner平版式扫描仪Plotter绘图仪pointing stick触控点portable printer便携式打印机portable scanner便携式扫描仪Printer打印机Radio frequency card reader射频卡阅读器Radio frequency identification (RFID)射频识别refresh rate刷新率Resolution分辨率roller ball滚动球shared laser printer共享激光打印机Speakers扬声器Stylus[stailəs]输入笔Technical writer技术文档编写员telephony[tilefəni]电话Terminal终端thermal printer[θə:məl]热敏打印机thin client瘦客户端thin film transistor monitor (TFT)薄膜晶体管显示器toggle key[tɔɡl]切换键touch pad触控板touch screen触摸屏Trackball轨迹球traditional keyboard传统键盘Universal Product Code (UPC)同一产品编码voice-over IP (VoIP)网络电话voice recognition system语音识别系统wand reader棒式阅读器W ebCam摄像头wheel button滚动键wireless keyboard无线键盘wireless mouse无线鼠标第八单元access speed存取速度Blu-Ray(BD)蓝光Capacity容量CD (compact disc)光盘CD-R (CD-recordable)可录式CDCD-ROM (compact disc-read only memory)光盘库CD-RW (compact disc rewritable)可重写CDCylinder[silində]柱面Density密度direct access直接存取disk caching磁盘缓存DVD(digital versatile disc or digital video disc)DVD player DVD播放器DVD- R (DVD recordable)可录式DVDDVD +R (DVD recordable)可录式DVDDVD-RAM(DVD random-access memory)DVD随机存取器DVD-ROM(DVD random-read-only memory)DVD只读存储器DVD-ROM jukeboxDVD-RW (DVD rewritable)可重写DVD Enterprise storage system企业存储系统erasable optical disk可擦光盘file compression文件压缩file decompression文件解压缩File server文件服务器flash memory card闪存卡floppy disk软盘Floppy disk cartridge软盘盒floppy disk drive (FDD)软磁盘驱动器hard disk硬盘hard-disk cartridge硬盘盒hard-disk pack硬盘组HD DVD(high-definition DVD)高清DVDhead crash磁头碰撞Hi def(high definition)高清high capacity disk高容量磁盘internal hard disk内置硬盘Internet hard drive网络硬盘驱动器Label标签Land平地magnetic tape磁带magnetic tape reel磁带盒magnetic tape streamer磁带条Media多媒体optical disk光盘optical disk drive光盘驱动器Organizational Internet storage组织性网络存储PC Card hard disk PC卡硬盘Pit坑primary storage主存RAID system磁碟阵列系统Redundant array of inexpensive disks(RAID)廉价磁盘冗余阵列secondary storage辅存Sector扇区sequential access顺序存取Shutter滑盖Software engineer软件工程师solid-state storage固态存储器storage devices存储装置tape cartridge盒式带Track轨道USB drive USB驱动器write-protection notch写入保护缺口第九单元3G cellular networkanalog signal 模拟信号asymmetric digital subscriber(ADSL)非对称数字用户线路Backbone中枢Bandwidth带宽base station基址bits per second位/秒Bluetooth 蓝牙Broadband宽带broadcast radio无线广播Bus总线bus network总线网络cable modem电缆调制解调器cellular service无线服务Client 客户client/server network system客户/服务网络系统coaxial cable同轴电缆communication channel 信道communication system 通信系统computer network计算机网络Connectivity连通性Demodulation 解调dial-up service拨号服务digital signal数字信号digital subscriber line (DSL)数字用户线路distributed data processing分布式数据处理系统distributed processing分布处理domain name server (DNS)域名服务Ethernet以太网external modem外置调制解调器Extranet外联网fiber-optic cable 光纤电缆Firewall防火墙global positioning system (GPS)全球卫星定位系统hierarchical network树型网络home network家庭网络host computer主机Hub集线器Infrared红外线internal modem 内置式调制解调器Intranet内联网IP address (Internet Protocol address)IP地址local area network (LAN)局域网low bandwidth低频带宽medium band 中频波段metropolitan area network (MAN) 城域网Microwave微波Modem调制解调器Modulation调制network administrator网络管理员network architecture网络体系结构network gateway 网关network hub 网络集线器network interface card (NIC)网络接口卡network operating system (NOS)网络操作系统Node 节点Packet 数据包PC card modem PC卡调制解调器peer-to-peer network system 对等网络系统Polling 轮流检测Protocol协议proxy server代理服务器ring network环型网络Satellite卫星satellite/air connection service卫星互连服务Server服务器star network 星型网络Strategy策略T1, T2, T3, T4 linestelephone line电话线terminal network 终端网络time-sharing system并发式系统Topology拓扑结构transfer rate传输率TCP/IP (transmission control protocol/Internet protocol)传输控制协议/因特网协议voiceband声音带宽wide area network (W AN)广域网Wi-FI (wireless fidelity)无限保真wireless LAN (WLAN)无线局域网wireless modem无线调制解调器wireless receiver无线接收器课后习题答案:Ch1: Ch6:bbabd,dacdd; eichafgbdj. dbcbb,aacbd; jachgidefb. Ch3: Ch7:dcbdd,abccb; jachbdiegf. Ababd,adcdb; iefjabgdch. Ch4: Ch8:aaaba,bcbab; igdecfhbja. dacac,acddc; gajidbhcfe. Ch5: Ch9:cdcaa,cbbac; gdfbghaeic. abadc,dbbbd; gbaidecjhf.。
