5000字英文文献翻译
英文文献翻译

外文文献原稿和译文原稿Sodium Polyacrylate:Also known as super-absorbent or “SAP”(super absorbent polymer), Kimberly Clark used to call it SAM (super absorbent material). It is typically used in fine granular form (like table salt). It helps improve capacity for better retention in a disposable diaper, allowing the product to be thinner with improved performance and less usage of pine fluff pulp. The molecular structure of the polyacrylate has sodium carboxylate groups hanging off the main chain. When it comes in contact with water, the sodium detaches itself, leaving only carboxylions. Being negatively charged, these ions repel one another so that the polymer also has cross-links, which effectively leads to a three-dimensional structure. It has hige molecular weight of more than a million; thus, instead of getting dissolved, it solidifies into a gel. The Hydrogen in the water (H-O-H) is trapped by the acrylate due to the atomic bonds associated with the polarity forces between the atoms. Electrolytes in the liquid, such as salt minerals (urine contains 0.9% of minerals), reduce polarity, thereby affecting superabsorbent properties, especially with regard to the superabsorbent capacity for liquid retention. This is the main reason why diapers containing SAP should never be tested with plain water. Linear molecular configurations have less total capacity than non-linear molecules but, on the other hand, retention of liquid in a linear molecule is higher than in a non-linear molecule, due to improved polarity. For a list of SAP suppliers, please use this link: SAP, the superabsorbent can be designed to absorb higher amounts of liquids (with less retention) or very high retentions (but lower capacity). In addition, a surface cross linker can be added to the superabsorbent particle to help it move liquids while it is saturated. This helps avoid formation of "gel blocks", the phenomenon that describes the impossibility of moving liquids once a SAP particle gets saturated.History of Super Absorbent Polymer ChemistryUn til the 1980’s, water absorbing materials were cellulosic or fiber-based products. Choices were tissue paper, cotton, sponge, and fluff pulp. The water retention capacity of these types of materials is only 20 times their weight – at most.In the early 1960s, the United States Department of Agriculture (USDA) was conducting work on materials to improve water conservation in soils. They developed a resin based on the grafting of acrylonitrile polymer onto the backbone of starch molecules (i.e. starch-grafting). The hydrolyzed product of the hydrolysis of this starch-acrylonitrile co-polymer gave water absorption greater than 400 times its weight. Also, the gel did not release liquid water the way that fiber-based absorbents do.The polymer came to be known as “Super Slurper”.The USDA gave the technical know how several USA companies for further development of the basic technology. A wide range of grating combinations were attempted including work with acrylic acid, acrylamide and polyvinyl alcohol (PVA).Since Japanese companies were excluded by the USDA, they started independent research using starch, carboxy methyl cellulose (CMC), acrylic acid, polyvinyl alcohol (PVA) and isobutylene maleic anhydride (IMA).Early global participants in the development of super absorbent chemistry included Dow Chemical, Hercules, General Mills Chemical, DuPont, National Starch & Chemical, Enka (Akzo), Sanyo Chemical, Sumitomo Chemical, Kao, Nihon Starch and Japan Exlan.In the early 1970s, super absorbent polymer was used commercially for the first time –not for soil amendment applications as originally intended –but for disposable hygienic products. The first product markets were feminine sanitary napkins and adult incontinence products.In 1978, Park Davis (d.b.a. Professional Medical Products) used super absorbent polymers in sanitary napkins.Super absorbent polymer was first used in Europe in a baby diaper in 1982 when Schickendanz and Beghin-Say added the material to the absorbent core. Shortly thereafter, UniCharm introduced super absorbent baby diapers in Japan while Proctor & Gamble and Kimberly-Clark in the USA began to use the material.The development of super absorbent technology and performance has been largely led by demands in the disposable hygiene segment. Strides in absorption performance have allowed the development of the ultra-thin baby diaper which uses a fraction of the materials – particularly fluff pulp – which earlier disposable diapers consumed.Over the years, technology has progressed so that there is little if any starch-grafted super absorbent polymer used in disposable hygienic products. These super absorbents typically are cross-linked acrylic homo-polymers (usually Sodium neutralized).Super absorbents used in soil amendments applications tend to be cross-linked acrylic-acrylamide co-polymers (usually Potassium neutralized).Besides granular super absorbent polymers, ARCO Chemical developed a super absorbent fiber technology in the early 1990s. This technology was eventually sold to Camelot Absorbents. There are super absorbent fibers commercially available today. While significantly more expensive than the granular polymers, the super absorbent fibers offer technical advantages in certain niche markets including cable wrap, medical devices and food packaging.Sodium polyacrylate, also known as waterlock, is a polymer with the chemical formula [-CH2-CH(COONa)-]n widely used in consumer products. It has the ability to absorb as much as 200 to 300 times its mass in water. Acrylate polymers generally are considered to possess an anionic charge. While sodium neutralized polyacrylates are the most common form used in industry, there are also other salts available including potassium, lithium and ammonium.ApplicationsAcrylates and acrylic chemistry have a wide variety of industrial uses that include: ∙Sequestering agents in detergents. (By binding hard water elements such as calcium and magnesium, the surfactants in detergents work more efficiently.) ∙Thickening agents∙Coatings∙Fake snowSuper absorbent polymers. These cross-linked acrylic polymers are referred to as "Super Absorbents" and "Water Crystals", and are used in baby diapers. Copolymerversions are used in agriculture and other specialty absorbent applications. The origins of super absorbent polymer chemistry trace back to the early 1960s when the U.S. Department of Agriculture developed the first super absorbent polymer materials. This chemical is featured in the Maximum Absorbency Garment used by NASA.译文聚丙烯酸钠聚丙烯酸钠,又可以称为超级吸收剂或者又叫高吸水性树脂,凯博利克拉克教授曾经称它为SAM即:超级吸收性物质。
英文文献整篇翻译

英文文献整篇翻译Title: The Impact of Climate Change on BiodiversityClimate change is a pressing issue that has significant impacts on biodiversity worldwide. Changes in temperature, precipitation patterns, and extreme weather events are altering ecosystems and threatening the survival of many species. The loss of biodiversity not only affects the natural world but also has implications for human societies.One of the major impacts of climate change onbiodiversity is the shifting of habitats. As temperatures rise, many species are forced to move to higher latitudesor elevations in search of suitable conditions. This can disrupt ecosystems and lead to the decline or extinction of species that are unable to adapt to the new conditions.In addition to habitat loss, climate change is also causing changes in the timing of biological events such as flowering, migration, and reproduction. These changes can disrupt the delicate balance of ecosystems and lead to mismatches between species that depend on each other for survival.Furthermore, climate change is exacerbating otherthreats to biodiversity such as habitat destruction, pollution, and overexploitation. The combination of these factors is putting immense pressure on many species and pushing them closer to extinction.It is essential that we take action to mitigate the impacts of climate change on biodiversity. This includes reducing greenhouse gas emissions, protecting and restoring habitats, and implementing conservation measures to safeguard vulnerable species. By addressing the root causes of climate change and protecting biodiversity, we canensure a sustainable future for both the natural world and human societies.气候变化对生物多样性的影响气候变化是一个紧迫的问题,对全球的生物多样性产生重大影响。
驱动桥5000字外文翻译文献
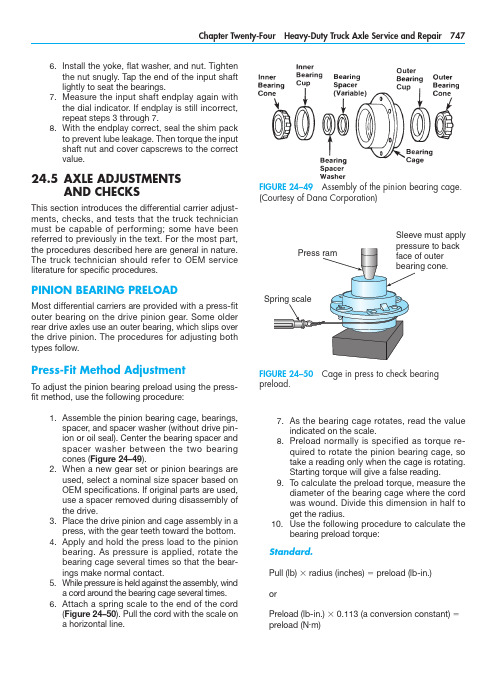
As the bearing cage rotates, read the value7. indicated on the scale.Preload normally is specified as torque re-8. quired to rotate the pinion bearing cage, so take a reading only when the cage is rotating. Starting torque will give a false reading.To calculate the preload torque, measure the 9. diameter of the bearing cage where the cord was wound. Divide this dimension in half to get the radius.10. U se the following procedure to calculate thebearing preload torque:Standard.Pull (lb) 3 radius (inches) 5 preload (lb-in.)orPreload (lb-in.) 3 0.113 (a conversion constant) 5 preload (N .m)Install the yoke, flat washer, and nut. Tighten 6. the nut snugly. Tap the end of the input shaft lightly to seat the bearings.Measure the input shaft endplay again with 7. the dial indicator. If endplay is still incorrect, repeat steps 3 through 7.With the endplay correct, seal the shim pack 8. to prevent lube leakage. Then torque the i nput shaft nut and cover capscrews to the correct value.24.5 A XLE ADJUSTMENTSAND CHECKSThis section introduces the differential carrier adjust-ments, checks, and tests that the truck technician must be capable of performing; some have beenr eferred to previously in the text. For the most part, the procedures described here are general in nature. The truck technician should refer to OEM servicel iterature for specific procedures.PINION BEARING PRELOADMost differential carriers are provided with a press-fit outer bearing on the drive pinion gear. Some older rear drive axles use an outer bearing, which slips over the drive pinion. The procedures for adjusting both types follow.Press-Fit Method AdjustmentTo adjust the pinion bearing preload using the press-fit method, use the following procedure:Assemble the pinion bearing cage, bearings, 1. spacer, and spacer washer (without drive pin-ion or oil seal). Center the bearing spacer and spacer washer between the two bearing cones (Figure 24–49).When a new gear set or pinion bearings are 2. used, select a nominal size spacer based on OEM specifications. If original parts are used, use a spacer removed during disassembly of the drive.Place the drive pinion and cage assembly in a 3. press, with the gear teeth toward the bottom.Apply and hold the press load to the pinion 4. bearing. As pressure is applied, rotate the bearing cage several times so that the bear-ings make normal contact.While pressure is held against the assembly, wind 5. a cord around the bearing cage several times.Attach a spring scale to the end of the cord 6. (Figure 24–50). Pull the cord with the scale ona horizontal line.FIGURE 24–49 Assembly of the pinion bearing cage.(Courtesy of Dana Corporation)FIGURE 24–50 Cage in press to check bearingp reload.Sleeve must applymust be against the outer bearing. If the fit between the yoke or flange splines and drive pinion splines is tight, use a press to install the yoke or flange (Figure 24–51).Temporarily install the drive pinion and cage 4. assembly in the carrier (Figure 24–52). Do not install shims under the bearing cage.Install the bearing cage to the carrier cap-5. screws. Washers are not required at this time. Hand-tighten the capscrews.Fasten a yoke or flange bar to the yoke or 6. flange (Figure 24–53). The bar will hold the drive pinion in position when the nut ist ightened.Metric.Pull (kg) 3 radius (cm) 5 preload (kg-cm) orPreload (kg-cm) 3 0.098 (a conversion constant) 5 preload (N .m)Examples. We can convert the foregoing equa-tions into examples by applying some data to them:Standard7.5 lb 3 3.31 in. 5 24.8 lb-in. (preload) or24.8 lb-in. 3 0.113 5 2.8 N .m (preload)Metric3.4 kg 3 8.4 cm 5 28.6 kg-cm (preload) or28.6 kg-cm 3 0.098 5 2.8 N .m (preload)11. I f necessary, adjust the pinion bearing preloadby changing the pinion bearing spacer. A thicker spacer will decrease preload, whereas a thinner spacer will increase the preload.12. O nce the correct bearing preload has beenestablished, note the spacer size used. Select a spacer 0.001 inch (0.025 mm) larger for use in the final pinion bearing cage assembly pro-cedures. The larger spacer compensates for slight expansion of the bearing, which occurs when pressed on the pinion shank. The trial spacer pack should result in correct pinion bearing preload in three times out of four cases.Y oke Method of AdjustmentTo adjust the pinion bearing preload using the yoke or flange method, proceed as follows:Assemble the complete pinion bearing cage 1. as recommended in the press-fit method.A forward axle pinion is equipped with a heli-2. cal gear. For easier disassembly during bear-ing adjustment procedures, use a dummy yoke (if available) in place of the helical gear.Install the input yoke or flange, nut, and 3.washer on the drive pinion. The yoke or flangeFIGURE 24–51 Using a press to install the yoke orflange to the drive pinion. (Courtesy of Arvin Meritor)FIGURE 24–52 Install the pinion and cage assembly in the carrier housing. (Courtesy of Arvin Meritor)indicated on the torque wrench (see Figure 24–55). Typical value is 50 lb-ft. (68 N .m)m aximum applied to one side gear.If the torque value exceeds the specification, 5. disassemble the differential gears from the case halves.Check the case halves, spider, gears, and 6. thrust washers for the problem that caused the torque value to exceed specifications. Re-pair or replace defective parts as required. Remove any foreign debris.Check/Adjust Pinion Cage Shim PackThis procedure is used to check and adjust the thick-ness of the shim pack used in the pinion bearing cage. Use this procedure if a new drive pinion and crownTighten the nut on the drive pinion to specifi-7. cation, typically 400 to 700 lb-ft. (542 to 950 N .m).Remove the yoke or flange bar.8. Attach a torque wrench to the drive pinion 9. nut. Rotate the drive pinion and read the value indicated on the torque wrench. Preload is correct when the torque required to rotate the pinion bearing cage is from 15 to 35 lb-in. (1.7 to 4.0 N .m).To adjust the pinion bearing preload, disas-10. semble the pinion bearing cage and change the pinion bearing spacer size. A thicker spacer will decrease preload, whereas a thin-ner spacer will increase preload.Differential Rolling ResistanceA check to measure and establish differential rolling resistance follows. To perform this check, a special tool must be made. You can easily make this tool from an old axle shaft that matches the spline size of the differential side gear. Figure 24–54 illustrates the fab-rication specifications for this special tool.To check differential resistance to rotation, use the following procedure:Install soft metal covers over the vise jaws to 1. protect the ring gear (Figure 24–55).Place the differential and crown gear assem-2. bly in the vise.Install the special tool into the differential until 3. the splines of the tool and one side gear are engaged.Attach a torque wrench to the nut of the spe-4. cial tool and rotate the differential gears. As the differential gears rotate, read the valueFIGURE 24–55 Reading the torque value to check the rolling resistance. (Courtesy of Arvin Meritor)FIGURE 24–53 Using a flange bar to hold the drivepinion in position. (Courtesy of Arvin Meritor)FIGURE 24–54 Fabrication details for a tool to checkthe rolling resistance. (Courtesy of Arvin Meritor)If the new pinion cone number is a minus (–), sub-8. tract the number from the standard shim packthickness that was calculated in step 3 or 4.The value calculated in step 7 or 8 is the 9.t hickness of the new shim pack that will bei nstalled. Figure 24–59 illustrates several e xamples of determining shim pack t hickness.Install the drive pinion, bearing cage, and new10. shim pack into the differential carrier.gear set is to be installed, or if the depth of the drive pinion has to be adjusted. You are checking the rolling resistance using a torque wrench.To check/adjust the shim pack thickness (Figure 24–56), do the following:With a micrometer, measure the thickness of 1. the old shim pack removed from under the pinion cage (Figure 24–57). Record the mea-surement for later use.Look at the pinion cone (PC) variation number 2. on the drive pinion being replaced (Figure 24–58). Record this number for later use also.If the old pinion cone number is a plus (+), 3. subtract the number from the old shim pack thickness that was recorded in step 1.If the old pinion cone number is a minus (–), 4. add the number to the old shim thickness that was measured in step 1.The value calculated in step 3 or 4 is the 5.t hickness of the standard shim pack without variation.Look at the PC variation number on the new 6. drive pinion that will be installed. Record the number for later use.If the new pinion cone number is a plus (+), 7. add the number to the standard shim packthickness that was calculated in step 3 or 4.FIGURE 24–56 Drive pinion depth controlled by shimpack thickness. (Courtesy of Arvin Meritor)FIGURE 24–57 Measuring the thickness of the old shim pack. Mike each shim individually then add tocalculate total thickness. (Courtesy of Arvin Meritor)FIGURE 24–58 Location of the pinion cone (PC)v ariation number. (Courtesy of Arvin Meritor)Adjust Differential Bearing PreloadOne of two methods can be used to check and adjust the preload of the differential bearings.Method One.Attach a dial indicator onto the mounting 1. flange of the carrier and adjust the indicator so that the plunger rides on the back surface of the crown ring gear (Figure 24–60).Loosen the bearing adjusting ring that is op-2. posite the ring gear so that a small amount of endplay is indicated on the dial indicator. To turn the adjusting rings, use a T-bar wrench that engages two or more opposite notches in the ring (Figure 24–61).Move the differential and crown gear to the 3. left and right using prybars as you read the dial indicator. Use two prybars that fit be-tween the bearing adjusting rings and the ends of the differential case (Figure 24–62). You also can use two prybars between the differential case or crown gear and the carrier at locations other than those just described. In either case, the prybars must not touch the differential bearings.EXAMPLES:Inchesmm 1.Old Shim Pack Thickness Old PC Number, PC +2Standard Shim Pack Thickness New PC Number, PC +5New Shim Pack Thickness .030.76–.002–.05.028.71+.005+.13.033.842.Old Shim Pack Thickness Old PC Number, PC –2Standard Shim Pack Thickness New PC Number, PC +5New Shim Pack Thickness .030.76+.002+.05.032.81+.005+.13.037.943.Old Shim Pack Thickness Old PC Number, PC +2Standard Shim Pack Thickness New PC Number, PC –5New Shim Pack Thickness .030.76–.002–.05.028.71–.005–.13.023.584.Old Shim Pack Thickness Old PC Number, PC –2Standard Shim Pack Thickness New PC Number, PC –5New Shim Pack Thickness.030.76+.002+.05.032.81–.005–.13.027.68FIGURE 24–59 Determining shim pack thickness.(Courtesy of ArvinMeritor Inc.)FIGURE 24–60 Dial indicator attached to carrier-mounted flange. (Courtesy of Arvin Meritor)FIGURE 24–61 Turning the adjusting ring using aT-bar wrench. (Courtesy of Arvin Meritor)FIGURE 24–62 Using pry bars to adjust play in the crown gear. (Courtesy of Arvin Meritor)Tighten the same bearing adjusting ring4.so that no endplay shows on the diali ndicator.Move the differential and crown gear to the5.left and right as needed. Repeat step 3 untilzero endplay is achieved.Tighten each bearing adjusting ring one6.notch from the zero endplay measured instep 4.Method Two.A second method of checking pre-load is to measure the expansion between the bearing caps after you tighten the adjusting rings. Use the following procedure:Turn both adjusting rings hand tight against1.the differential bearings.Measure the distance X or Y between oppo-2.site surfaces of the bearing caps (Figure24–63A) using a large micrometer of thec orrect size (Figure 24–63B). Make a note ofthe m easurement.Tighten each bearing adjusting ring one3.notch.Measure the distance X or Y again. Compare4.the dimension with the distance X or Y mea-sured in step 2. The difference between thetwo dimensions is the amount that the bear-ing caps have expanded.Example: Measurements of a carrier.Distance X or Y before tightening adjusting rings5 15.315 inches (389.00 mm)Distance X or Y after tightening adjusting rings5 15.324 inches (389.23 mm)15.324 inches minus 15.315 inches5 0.009 inch (0.23 mm) differenceIf the dimension is less than specification, repeat steps 3 and 4 as needed.Crown Gear Runout CheckTo check the runout of the crown/ring gear, do the f ollowing:Attach a dial indicator on the mounting flange1.of the differential carrier (Figure 24–64).Adjust the dial indicator so that the plunger or2.pointer is against the back surface of thecrown gear.FIGURE 24–63 (A) Location of distances measured to check expansion between bearing caps aftert ightening adjusting rings; (B) measuring this distance.(Courtesy of Arvin Meritor)FIGURE 24–64 Checking crown gear runout. (Courtesy of Arvin Meritor)Pinion and Crown Tooth ContactA djustment Correct tooth contact between the pinion and crown gear cannot be overemphasized, because improper tooth contact results in noisy operation and prema-ture failure. The tooth contact pattern consists of the lengthwise bearing (along the tooth of the ring gear) and the profile bearing (up and down the tooth). F igure 24–68 shows crown gear toothn omenclature.Adjust the dial of the indicator to zero.3. Rotate the differential and crown gear when4. reading the dial indicator. The runout of the crown gear must not exceed 0.008 inch (2 mm) (a typical value; refer to the applicable OEM service literature for the specificv alues).If runout of the crown gear exceeds the speci-5. fication, remove the differential and crown gear assembly from the carrier. Check the dif-ferential components, including the carrier, for the problem causing the runout of the gear to exceed specification. Repair or replace defec-tive components.After the components are repaired or re-6. placed, install the differential and crown gear into the carrier.Repeat the preload adjustment of the 7. differential bearings. Then repeat this runout procedure.Check/Adjust Crown Gear BacklashIf the used crown and pinion gear set is installed, ad-just the backlash to the setting that was measured before the carrier was disassembled. If a new gear set is to be installed, adjust backlash to the correct speci-fication for the new gear set.To check and adjust ring gear backlash, do thef ollowing: Attach a dial indicator onto the mounting1. flange of the carrier (see Figure 24–64).Adjust the dial indicator so that the plunger is 2. against the tooth surface at a right angle.Adjust the dial of the indicator to zero, making 3. sure that the plunger is loaded through at least one revolution.Hold the drive pinion in position.4. When reading the dial indicator, rotate the5. crown gear a small amount in both directions against the teeth of the drive pinion (Figure 24–65). If the backlash reading is not within specification (typically ranging from 0.010 to 0.020 inch or 254 to 508 mm), adjust backlash as outlined in steps 6 and 7.Loosen one bearing adjusting ring one notch 6. and then tighten the opposite ring the same amount. Backlash is increased by moving the crown gear away from the drive pinion (Figure 24–66). Backlash is decreased by moving the crown gear toward the drive pin-ion (Figure 24–67).Repeat steps 2 through 5 until the backlash is 7.within specifications.FIGURE 24–65 Check crown gear backlash. ( Courtesy of Arvin Meritor)FIGURE 24–66 Adjustments to increase backlash. (Courtesy of Arvin Meritor)the pattern in an unloaded condition (such as when you are performing this test) will be approximately one-half to two-thirds of the crown gear tooth in most models and ratios.Checking Tooth Contact Pattern on a Used Gear Set. Used gearing will not usually display the square, even contact pattern found in new gear sets. The gear will normally have a pocket at the toe-end of the gear tooth (Figure 24–71) that tails into a contact line along the root of the tooth. The more use a gear has had, the more the line becomes the dominant characteristic of the pattern.Adjusting Tooth Contact Pattern. When dis-assembling, make a drawing of the gear tooth con-tact pattern so that when reassembling it is possible to replicate approximately the same pattern. A cor-rect pattern should be clear of the toe and centers evenly along the face width between the top land and the root. Otherwise, the length and shape of the pattern can be highly variable and are usually con-sidered acceptable—providing the pattern does not run off the tooth at any time. If necessary, adjust the contact pattern by moving the crown gear and drive pinion.Checking Tooth Contact Pattern on a New Gear Set. Paint 12 crown gear teeth with a marking compound (Figure 24–69) and roll the gear to obtain a tooth contact pattern. A correct pattern should be well centered on the crown gear teeth with lengthwise contact clear of the toe (Figure 24–70). The length ofFIGURE 24–67 Adjustments to decrease backlash.(Courtesy of Arvin Meritor)FIGURE 24–68 Crown gear tooth nomenclature.(Courtesy of Dana Corporation)FIGURE 24–69 Application of a marking compoundto check tooth contact. (Courtesy of Dana Corporation)FIGURE 24–70 Correct tooth contact patternfor new gearing. (Courtesy of Dana Corporation)FIGURE 24–71 Correct tooth contact pattern for used gearing. (Courtesy of Dana Corporation)making adjustments, first adjust the pinion and then the backlash. Continue this sequence until the pattern is satisfactory.Thrust Screw AdjustmentFor those differential carriers equipped with a thrust screw, perform the following procedure. (If the carrier assembly does not have a thrust block, proceed to step 4 of this procedure.)Rotate the carrier in the repair stand until the 1. back surface of the crown gear is toward the top.Put the thrust block on the back surface of 2. the ring gear. The thrust block must be in the center between the outer diameter of the gear and the differential case.Rotate the crown gear until the thrust block 3. and hole for the thrust screw, in the carrier, are aligned.Install the jam nut on the thrust screw, one-4. half the distance between both ends (Figure 24–74).Install the thrust screw into the carrier until the 5. screw stops against the crown gear or thrust block.Loosen the thrust screw one-half turn, or 180 6. degrees.Tighten the jam nut to the correct torque value 7. against the carrier (typical values range from 150 to 295 lb-ft. or 200 to 400 N .m) (Figure 24–75).Axle TrackingAxle tracking can be measured using the older tram bar method or electronic alignment equipment. The procedures for setting axle alignment and tracking areexplained in Chapter 25.FIGURE 24–72 Two incorrect patterns when adjusting pinion position. (Courtesy of Dana Corporation)Crown gear position controls the backlash setting. This adjustment also moves the contact pattern along the face width of the gear tooth (Figure 24–72). Pinion position is determined by the size of the pinion bear-ing cage shim pack. It controls contact on the tooth depth of the gear tooth (Figure 24–73).These adjustments are interrelated. As a result, they must be considered together even though thepattern is altered by two distinct operations. WhenFIGURE 24–73 Two incorrect patterns when adjusting backlash. (Courtesy of Dana Corporation)• Most differential carriers are replaced as rebuilt/exchange units, so the role of the technician is, more often than not, to diagnose the problem and then, if necessary, to replace the defective assembly as a unit.• The technician who has disassembled and reas-sembled differential carriers should find trouble-shooting procedures easier to follow.• Follow the OEM procedure when disassem-bling differential carriers. Taking a few mo-ments to measure shim packs and gear tooth contact patterns on disassembly can save considerable time when reassembling thec arrier.• A crown and pinion gear set often can ber eused when rebuilding a differential carrier. Make sure that you inspect it properly ond isassembly.• Crown and pinion gear sets are always replaced as a matched pair during a rebuild.• When setting crown and pinion backlash, it is increased by moving the crown gear away from the drive pinion and decreased by moving the crown gear toward the drive pinion.• Adhering to OEM-recommended lubrication schedules is the key to ensuring the longest service life from both drive and dead axles.• Knowing the correct procedure to check lubricant level is essential. The level is correct when lubri-cant is exactly level with the bottom of the fill hole.• Because most OEMs approve of the use of syn-thetic lubricants in final drive carriers, lubrication drain schedules have been greatly increased in recent years. Drain schedules are determined by the actual lubricant used and the type of appli-cation to which the vehicle is subjected.• Servicing of axles on heavy-duty trucks consists of routine inspection, lubrication, cleaning, and, when required, troubleshooting and component overhaul.• Failure analysis is required to prevent recurrent failures.• Drive axle carrier components usually fail for one of the following reasons: Shock load Fatigue Spinout Lubrication problemsNormal wearFIGURE 24–74 Installing the jam nut on the thrust screw. (Courtesy of Arvin Meritor)FIGURE 24–75 Tighten the jam nut to the correct torque value. (Courtesy of Arvin Meritor)SUMMARY。
5000字外文翻译

附录外文文献原文1。
IntroductionMarketing continues to be a mystery to those who create it and to those who sponsor it. Often,the ad that generates record-breaking volume for a retail store one month is repeated the following month and bombs。
A campaign designed by the best Madison Avenue ad agency may elicit mediocre response. The same item sells like hotcakes after a 30—word classified ad,with abominable grammar, appears on page 35 of an all—advertising shopper tossed on the front stoops of homes during a rainstorm! The mystery eludes solution but demands attention。
The success of an enterprise and development of enterprises depends to a large extent on whether or not they have advanced,meet the needs of the enterprise marketing strategy. For Marketing is the definition, The well-known American scholar Philips marketing of the core marketing concept of the following description :"Marketing is individuals or groups to create,provide and exchange with other valuable products,to satisfy their own needs and desires of a social activities and management process. " In the core concept contains a number of elements: needs,desires and needs; Products or provide; Value and satisfaction;exchange and transactions;and networking; market; Marketing and sales were a series of concept.This article is devoted to the idea that your marketing results can be improved through a better Understanding of your customers。
五千字外文翻译

SCRAPER WINCH MOTORS ON SOUTH AFRICAN GOLD MINES – ANINVESTIGATION INTO THEIR FAILUREJF Pritchard CF LandyDept. of Electrical EngineeringABSTRACTThis paper investigates some of the probable reasons forfailure of squirrel cage induction machnes dnving scraperwinches in South African Gold Mines. The paper shows theresults of load current and voltage unbalance measurements that were recorded on winches in operation. There arefurther measurements showing the presence of time harmonics in the supply to some winches. More importantly,the paper shows the measured torque-speed curve of atypicai scraper winch machine. This curve seems to inhace that there are significant space harmonics present in the air gap of the winches, which may be causing rotor heating and pre-mature bearing failure.INTRODUCTIONIn South African gold mines, a winch known as a “scraper winch” is used to scrape ore-bearing rock from the rock -face after blasting. The winch consists of a mechanical winch powered by a squirrel cage induction motor. The mostcommon rating for the scraper winch motor is 37kW, 525V,5 1A.It is well known in the SA mining industry that these winches do not last for more than about 4 to 6 months in operation underground before they bum out and have to be sent to the surface for re-winding. A number of theories have been advanced by engineers working on the mines as to why these machines fail so often, however, none of these theories have so far been adequately documented or proven.Scraper winches normally operate in the stopes (the sections where mining operations are on-going) and as such, it is difficult to install and remove them easily since the railway lines underground do not extend all the way into the stopes. Once a winch bums out, it may often take up to 2 to 3 full shifts before a new winch can be installed in its place and as a result, a significant amount of production is lost. If one considers that a large gold mine with more than one active shaft, may have up to 1000 scraper winches in operation at any one time (and these winches are being replaced on average, twice a year), and one factors in the cost of rewinds as well as lost production, it becomes evident that scraper winches are costing the gold mining industry a lot of money every year. This paper highlights some research that has been done at the University of the Witwatersrand to investigate the reasons for failure of scraper winch motors in South African gold mines. The paper describes part of the preliminary investigation that involved researchmg literature on squirrel cage induction machine failures as well as the results of visits to machine repair organisations involved with winch motor repairs for the mines. Thereafter, the results of measurements that were taken underground are discussed. Laboratory tests that were camed out on scraper winch motors are also highlighted and the results thereof are discussed.THE PRELIMINARY INVESTIGATIONThe reasons for squirrel cage induction machine failures are quite well documented in the literature [1,2,3,7]. It seems that in meQum voltage, small machmes, the predominant componentthat fails is the stator winding insulation. Stator failures can often be attributed to electrical supply problems such as voltage unbalance, single phasing, time harmonic voltages in the supply, undervoltage, overvoltage and voltage transients. There are also load factors such as mechanical overloading of the machine, and thermal cycling of the insulation that can lead to thermal as well as mechanical ageing of the insulation. Environmental factors111 are also often cited as stresses that act on the stator insulation. In particular, voltage tracking (even in med” voltage motors) across the slot insulation due to moisture and dirt finding their way inside the machne is a common rea son for failures in machines that operate in “dusty”environments. Clogging of the airways, corrosion of the laminations and deterioration of the insulation due to moisture [1,4] are also sometimes quoted as environmental reasons for failure. Mechanical abrasion of the insulation due to foreign particles entering the machine may also lead to machine failure.DriR-uroof machinesDuring the investigation, a number of failed scraper winch motors were observed at two machine repair organizations. Of these, the majority were enclosed in drip-proof enclosures, while some were housed in totally enclosed, fan cooled enclosures (TEFC enclosures). The drip proof machines were found to all have evidence of rust on the stator cores, with small stones and mine sludge being found in the overhangs of the machines. Large amounts of grease and oil were also found inside most machines, which came either from the bearings, or from the gear-box to whch the machines are attached, or both. In one case a stone of 3cm diameter was found in the overhang. One repairer claimed that he sometimes finds it necessary to press the rotor out of the stator using a machine (once the bearings were of€) due to the large number of foreign particles jammed into the air gap. Regarding the drip-proof machines, it became evident hat a major factor leading to failure was abrasion of the stator insulation due to the presence of foreign particles inside the machine.Because of these obvious short-comings associated with drip-proof motors, according to one source in the mining industry, most of the mines nowadays purchase only TEFC machines. For this reason, it was decided to neglect drip proof machines in the investigation and focus solely on TEFC machines.TEFC machinesOf the failed TEFC machines, it seemed that there was also evidence of rust and sometimes grease inside some of the “sealed‟ machines, however, it was of a lesser extent compared to the drip-proof machines. It seems that the grease found in these machines also worked its way into the sealed housing from the bearings and the adjacent gear-box. The appearance of rust in supposedly “sealed machines is also not dflicult to explain if one considers that when a machine is run, the air inside heats up and expands, hence pressure the seals and some of it may find its way out. When the machine is allowed to cool, the air inside contracts and a partial vacuum is established which may allow moisture-laden air to enter the machine, depending on how well it is sealed.Both machne repairers claimed that when machines come in for repair they sometimes findthat an earth fault that…was noticed when the machine came in initially, is alleviated when the machine is opened up and dried out. Also, it seems that the bearings are almost always in need of replacement and the machine repairers replace the bearings every time asa matter of course. Based on this evidence, it seems that bearing failures and voltage traclung due to moisture may at least be one component leading to TEFC scraper winch failures.pH measurements inside failed machinesSome engineers have claimed that scraper winches fail because of non-balanced pH aqueous solutions finding their way onto the stator winding and corroding it. While it is not clear that an acidic or alkali solution does in fact corrode the insulation or the impregnating varnish faster than normal water [4], it was decided to check if this may in fact be one additional factor to consider.A relatively recent paper in a mining journal [5] indicates that fissure water in South African gold mines has a pH value that varies from 2.67 in some areas in the Witwatersrand to 9.77 in the Free State. Furthermore,another paper was found [6] that showed that significant amounts of nitrous fumes are given off during the blasting process whch can combine with water vapour (of which there is an abundance underground) to produce nitrous acid. Since the scraper motors are very near to the blasting area and are always in the presence of water vapour, it seems that dilute acids and alkalis may find their way into scrapermachmes in some mines.As a further test, a sample of 10 failed, drip proof machines (since they are more exposed to the environment than TEFC machines) from 2 mines in the Witwatersrand were opened up and tested for pH content using colour fixed pH indxator sticks (with a pH accuracy of 1). The procedure was to dip the sticks into distilled water and then press them against the inside of the stator bore in 4 different places. Of all the machines that were tested, not one registered a pH content of other than 7 (balanced), indicating that there was no sigruficant acid or alkali concentration inside the machines. Although this was a rather crude experiment on a very small sample of machines, it does seem to indicate that pH content is not a real factor when looking for reasons for failure of scraper winch motors.UNDERGROUND MEASUREMENT RESULTSIn order to assess the quality of the supply to scraper winch motors underground, as well as to assess the loading on the machines, it was decided to log measurements of the three phase line current, voltage and power to a series of machines in operation underground. Coupled with this, it was decided to record spot current waveforms for analysis later.The data was sampled and logged on a portable computer using a 16 bit data acquisition card PAC). The measurement transducers consisted of two wide bandwidth, battery powered current probes and two small voltage transformers. These were connected to a unit housing a high order anti-aliasing filter, which in turn passed the signal to the DAC. The voltage and current on two lines was measured directly using the transducers and the voltage and current on the other 2 phases was inferred using the fact that the voltage and current in a 3 phase, 3 wire system sum to zero. The input power was measured using the standard 2 wattmeter method,using the voltage and current transducers, with the multiplication etc., being done in the software.The software was set up in such a way as to allow the DAC to sample at 15& and acquirebatches of 3000 points. This enabled a true RMS reading of all 3 line voltages and currents to be taken roughly every 314 of a second and recorded. The high loggmg frequency was necessary in order to capture machmes running up, as well as rapid load changes which can happen in less than a second. The current waveforms that were captured were also sampled at 15&, with 60000 points being stored. This was done to give a frequency resolution of 0.25Hi in the frequency domain.Due to the physical constraints involved with measuring underground, it was only possible to log data measured at one machine site for three shifts. Unfortunately, the only suitable site for measurement was in an area of the mine where the machines were not being pushed too hard (according to some miners) because of the relatively short haulage path for the winches (for more discussion of the actors affecting loading on the machine, see [lo]). While the results that were recorded may presumably not be taken to be true of scraper winches in general, they do give what appears to be a good indication of the duty cycle of scraper winches. Figures 1-3 below show the average current (i.e. the sum of all three phases divided by 3) that was recorded over 3 shifts of operation.It is clear from the current plots that the scraper winch being observed has a highly irregular duty cycle. It is also clear from the plots that the amount of loading is very irregular. The large current peaks correspond to starting current peaks. The reason some starting peaks are less than others is to do with the fact that the sample batches were not synchronised with the starting of the machine. Since the machme can run up to speed in almost a second (there is no load during starting), the lower starting peaks correspond to a sample batch that was taken by the time the machine had almost run up to speed.If one analyses the data in the plots carefully, it becomes evident that the worst case duty cycle is 60% of one hour, while the average duty cycle is 50%. Th e average “on time” per start (as calculated over all 3 shifts) is 5 minutes, while the average number of starts per half hour is 3. The maximum number of starts per half hour is 5. The average on time per half hour is 15 minutes.The plots show that apart from starting and one or two short periods of overload, this machine was not heavily loaded over the three nights of observation (the rated current is 51A). In order to definitively state the average load current for a 37kW scraper winch in operation, one would have to take more measurements on a larger variety of machines in operation than these.Regarding voltage unbalance, one may state the % unbalance as follows [7]:%100%⨯-=average averagev v v unbalancewhere V is the RMS line voltage of a particular line. The worst case voltage unbalance over all three shifts is shown for the affected phase in figure 4 below.The figure shows that apart from one short period ofsubstantial voltage unbalance, there was no real voltage unbalance in the supply to the observed machine. Most researchers say that asupply voltage unbalance of up to 3% is acceptable for most induction motors, however in this case, the unbalance is almost always less than 1%.If one plots the average 3 phase line voltage out and averages that over the periods that the machine is on, one finds that at the site in question, the scraper winch was supplied with an average voltage of 500V during its “on” periods. While the rated voltage is 525V, this machine was not affected at all by a corresponding overcurrent as the plots on the previous page show. The time domain current waveform that was captured underground during the machine‟s operation was processed afterwards by performing a fast Fourier transform on it. The FFT was done in Matlab@, with due attention being given to spectral leakage effects. The frequency domam data of relevance is plotted in the figure below. The current amplitudes are normalised to the 50Hz current and are given in decibels (2010glo(actual magnitude)).The plot in figure 5 shows that there are significant third and fifth harmonic currents present in the stator current (magnitudes are 1.6% and 4.4% of the fundamental respectively). These time harmonics, particularly the fifth harmonic (which is negative phase sequence) can cause considerable heating of the rotor circuit (Gomes [9]). The harmonic content and magnitude may vary from region to regon within a mine and even more so from mine to mine, however the harmonic currents shown in this plot (particularly the ffih harmonic) are unacceptably high and will definitely contribute towards shortening the life of themachine.LABORATORY TEST WSULTSFor the laboratory work, 2 scraper winch motors were tested. A TEFC machme which had been in service for some time on a mine and had been re-wound recently was initially tested. It had not been in service since the re-wind. The second machine was new and was supplied by the manufacturer. When the two machines were stripped and compared, it was found that their electrical designs were identical and their mechanical designs were almost identical, with only minor differences in the casing being noticed.It was decided that the amount of loadmg shown in figures (1-3) could not be taken to be a typical load on a scraper winch motor in operation and hence for the laboratory tests, the rated current was used. However, it was decided that the duty cycle information in the plots may be considered typical. Since it was anticipated that the bearings of the machine would be getting too hot, heat sensors (resistive temperature detectors - RTD‟s) were fitted into holes drilled in the end-shields of the machine from the mine (machine 1) and pushed up against the outer race of the bearings. In addition, an RTD was placed on each overhang, as close as possible to the core. These sensors were placed at the top of the overhang on the outside and were held in place by some silicon gel. A number of heat runs were done at rated output power and Werent duty cycles. These results are plotted in the table below.The machine was operated at a voltage of between 490 and 500V and the rated current for this voltage was calculated by working out the losses for the machine at a range of currents and then calculating the output power by subtracting the machine losses from the input power.The table shows that for the cases where the average winding temperature rise was measured (done by measuring the change in the DC stator windmg resistance), the average temperature was higher than the overhang temperatures.This is because the overhang temperature sensors are only able to measure the temperature at a point, whereas the average winding resistance method inherently averages the temperature distribution around the machine inside the conductors themselves.The shaft temperature measurements indicated above were taken using a temperature probe which was positioned as close to the drive end end-shield as possible, immediately after the machine stopped. To a first approximation, the shaft temperature rise was taken to indicate the temperature rise of the inner drive end bearing race.If one considers that the ambient temperature in the vicinity of a scraper winch in operation in a mine may be as high as 35°C typically, the actual temperatures measured would be those in the table plus 35°C. Thls would place the shaft temperature at 112°C for the worst case and 95°C for the best case condition in the table. The diagram below shows the actual assembly of the drive end bearing and shaft for the machine under test.If one considers that the shaft temperature is measured immediately adjacent to the oil seal as shown in the diagram, it is conceivable that the temperature of the bearing seal (on the bearing side closest to the rotor) is because of the space displacement.According to the bearing manufacturers, a sealed bearing may not operate at a temperature of higher than 110°C without the lubricant leaking out. In this case, after about 10 different heat runs were done, all at or below rated current, it was noticed that there was a sigNticant amount of lubricant lying under the machine. When the machine was stripped, it was found that there was a large pool of lubricant inside the bearing housing as well as inside the machine next to the stator overhang. Also, the rotor steel had become extremely dark indicating that the rotor was getting very hot during operation. This evidence was consistent with the observations made at the machine repairers where it was found that there were large quantities of grease lying inside the machine housing.The second machine (the new machine) was subsequently coupled to the load being used (a DC machine) and a continuous heat run was performed on it. The rated current of the machine (as given by the manufacturers) is 51A, but because the machine was being fed by 500V instead of 525V, the heat run was performed at a load current of 54A. In this case, the machme had heat sensitive strips pasted inside; on the shaft, end-rings and the bearing seals facing the rotor. After the machine had run continuously for 4 hours and 40 minutes, the drive end bearing seized completely and the machine stalled. When the machine was opened, all the temperature strips had gone off-scale.The results from these tests showed that although the stator winding wasn‟t getting excessively hot for class F insulation, the rotors were getting extremely hot and damaging the bearings. It was suspected at this stage that the machine rotors were getting hot because of large high frequency currents flowing in the rotor bars due to space harmonic effects in the air-gap of the machine.Landy [9] shows that harmomc currents of significant magnitude flowing in the rotors ofinduction machmes can be picked up by measuring the torque speed curve of the machine under reduced voltage conditions. The harmonic mmfs caused by the stepped nature of the mmf wave in the air gap, produce harmonic currents in the rotor circuit. These harmonic currents in turn produce a “family” of harmonic“ f s of their own which interact with the stator mmf waves to produce either asynchronous or synchronous torques which will be superimposed on the fundamental torque speed envelope. Figure 6 below shows the measured torque speed w e of the new machine (which is the same as that of the older machine) along with the curve that would be expected if there were no space harmonics present in the machine. For convenience, the curve has been normalised with respect to the maximum pull-out torque.It is obvious from figure 7 that there are very significant space harmonic effects in the air-gap of the machmes under test. The machines have relatively deep rectangular bars and if there are large, high frequency rotor harmonic currents (as the torque-speed curve suggests), they will flow close to the top of the bar and cause severe heating of the rotor bars and the rotor as a whole.CONCLUSIONSThis paper has shown that there are a number of factors that may be shortening the life of TEFC scraper winch motors. In particular, it appears that at some machine sites underground, there are time harmonic voltages present in the supply to the machines which can cause unacceptable heating of the machines and hence reduce their life. V oltage unbalance does not appear to be a problem, but there is evidence that there is a lower voltage than 525V at some Sites.Furthermore, as was evidenced by observations of failed machines, there appear to be numerous incidences of moisture getting into the machine windings whilst in operation underground. This can assist voltage tracking across the insulation and cause an earth or phase-phase fault inside the machine. The moisture can also damage the machine bearings and stator laminations with time.Coupled with this evidence, the paper shows strong experimental evidence which suggests that typical 37kW scraper winch motors may be experiencing bearing failures induced byexcessive rotor generated heat. As a feasible explanation for this, a measurement of the steady-state torque speed curve of two 37kW, TEFC scraper winch motors reveals that there appear to be large magnitude, high frequency currents circulating in the rotor bars. Thus, even though the loading experienced by a scraper winch may be lower than the rated current (as was shown for a particular winch underground), that winch may still experience a bearing failure because of the space harmonic rotor heating effects. A further analysis of the space harmonic effects expected in the winch motors in the laboratory is being undertaken at present, with a view to recommendmg design changes to the standard scraper winch motors.ACKNOWLEDGEMENTSThe authors would like to thank AngloVad Minerals and Hartebeestfontein Gold Mine for their financial assistance and for supplying a scraper winch for laboratory work. In addition, the authors would like to acknowledge the assistance of Powermote (PTY) LTD who supplied a scraper winch as well, and gave some details on its design. Finally, thanks must also go to the Eskom TESP program for further financial assistance and to the University of the Witwatersrand who supplied the laboratory facilities for the research.REFERENCES1. Bonnet A.H., Soukop G.C., Cause andAnalysis of Stator and Rotor Failures in Three-phase Squirrel-Cage Induction Motors, IEEE Transactions on Industry Applications, V ol. 28, No.4, JulyIAugust 19922.Bonnet A.H., Soukop G.C, Rotor Failures in Squirrel-Cage Induction Motors, LEEE Transactions on Industry Applications, V ol. IA-22, No. 6, NovemberDecember 2.1986, pp 1165-1 1733. Bonnet A.H., Analysis of Winding Failures in Three-Phase Squirrel Cage Induction Motors, IEEE Transactions on Industry Applications, V ol. IA- 14, No. 3, MayJJune 1978 pp. 223-2264. Campbell F. J., Temperature Dependance of Hydrolysis of Polyimide Wire Insulation, IEEE Transactions on Electrical Insulation V ol. EI-20 No.1, February 1985,5.Pulles W., Water Pollution: ItsManagement and Control in the South African Gold Mining Industry, Journal of the Mine Ventilation Society of South Africa, february 1992, pp 18-36,pp 11 1-1 166. Burton R.C. and Wrigley D.E., Blast Fume Filters in Mines - A Review of the Current State of the Art, Journal of the Mine Ventilation Society of South Africa, October 1991, pp 167-1717.Woll R.F., Effect of Unbalanced V oltage on the Operation of Polyphase Induction Motors, IEEE Transactions on Industry Applications, V ol. IA-11, No.1, January/February 1975, pp 38-428.Gomes A.A.D.F.P, Landy C.F., The Effects of Supply Time Harmonics on the Torque Speed Curves of Squirrel Cage Induction Machines, proc. IEEE Intemational Conference on Electrical Machines-Design and Application, London, July 1982, p104ndy C.F., A Technique For Assessing Space Harmonic Effects in Squirrel Cage Induction Motors, SAJEE Transactions, vol73, part 1, 1982, pp 3-1110. Pritchard J.F., An Investigation into the Reasons for Failure of Scraper Winch Motors on South African GoldMines, M.Sc. (eng.) Thesis, University of the Witwatersrand, 1996 Authorized licensed中文译文南非金矿的刮刀绞盘电机-他们的失败调查摘要本文研究的是在南非金矿使用的刮板绞车采用的鼠龙式异步电机故障的原因。
范文——翻译材料(不少于5000汉字)

山东理工大学英-中文翻译材料英文题目:Brief Introduction中文题目:.NET简介学院:计算机科学与技术专业:软件工程学生姓名:米东文指导教师:刘秋香二O一五年六月Brief Introduction to .NETThe .NET FrameworkThe .NET Framework is a multi-language environment for building, deploying, and running XML Web services and applications. It consists of three main parts:∙Common Language Runtime Despite its name, the runtime actually has a role in both a component's runtime and development time experiences. While the component is running, the runtime is responsible for managing memory allocation, starting up and stopping threads and processes, and enforcing security policy, as well as satisfying any dependencies that the component might have on other components. At development time, the runtime's role changes slightly; because it automates so much (for example, memory management), the runtime makes the developer's experience very simple, especially when compared to COM as it is today. In particular, features such as reflection dramatically reduce the amount of code a developer must write in order to turn business logic into a reusable component.∙Unified programming classes The framework provides developers with a unified, object-oriented, hierarchical, and extensible set of class libraries (APIs). Currently, C++ developers use the Microsoft Foundation Classes and Java developers use the Windows Foundation Classes. The framework unifies these disparate models and gives Visual Basic and JScript programmers’ access to class libraries as well. By creating a common set of APIs across all programming languages, the common language runtime enables cross-language inheritance, error handling, and debugging.All programming languages, from JScript to C++, have similar access to the framework and developers are free to choose the language that they want to use.∙ builds on the programming classes of the .NET Framework, providing a Web application model with a set of controls and infrastructure that make it simple to build ASP Web applications. includes a set of controls that encapsulate common HTML user interface elements, such as text boxes and drop-down menus. These controls run on the Web server, however, and push their user interface as HTML to the browser. On the server, the controls expose an object-oriented programming model that brings the richness of object-oriented programming to the Web developer. also provides infrastructure services, such as session state management and process recycling, which further reduce theamount of code a developer must write and increase application reliability. In addition, uses these same concepts to enable developers to deliver software as a service. Using XML Web services features, developers can write their business logic and use the infrastructure to deliver that service via SOAP.DATA CONNECTIONIntroductionThe top of the stack is the API or object library layer. Applications connect to Microsoft® SQL Server through either API functions or interfaces exposed by an object library. Examples of APIs used to access SQL Server include ODBC and DB-Library. Examples of object libraries used to access SQL Server include OLE DB, ADO, and . Because ADO ultimately uses OLE DB to communicate with the server, there are really just two object libraries commonly used by Windows applications to communicate with SQL Server: OLE DB and . Connecting through ADO or is certainly more common than doing so over ODBC (although SQL Server's Query Analyzer and Enterprise Manager Still connect over ODBC), so I'll discuss the client-side of SQL Server's connection architecture in terms of ADO/OLE DB and . Most apps these days get to SQL Server by way of an object library rather than ODBC or something similar.ADO and OLE DBOLE DB clients (also known as consumers) communicate with servers and other back-ends by means of a client-side provider. This provider is a set of one or more COM components that translate application requests into network interposes communication (IPC) requests. In the case of SQL Server, the OLE DB provider that is most commonly used is SQLOLEDB, the Microsoft-provided OLE DB provider for SQL Server. SQLOLEDB comes with SQL Server and is installed as part of the Microsoft Data Access Components (MDAC) stack.Applications that communicate with SQL Server using ADO do so by first establishing a connection to the server using a Connection object. ADO's Connectionobject accepts a connection string that specifies the OLE DB provider to be used as well as the parameters to pass to it. You'll see "SQLOLEDB" in this string if an app is connecting to SQL Server using the SQLOLEDB provider.It's also possible for an ADO application to connect over ODBC to SQL Server. To do this, the app uses the OLE DB provider for ODBC and specifies an ODBC data source that references the target SQL Server in its connection string. In this scenario, the application communicates with OLE DB, and the OLE DB provider for ODBC makes the appropriate ODBC API calls to talk to SQL Server. applications typically connect to SQL Server using the .NET Framework Data Provider for SQL Server. This native provider allows objects to communicate directly with SQL Server. Typically, an application uses a SqlConnection object to establish a connection, and then uses a SqlCommand object to send commands to the server and receive results back from it. The SqlDataAdapter and SqlDataReader classes are typically used in conjunction with SqlCommand to interact with SQL Server from managed code applications.By making use of the OleDbConnection class, applications can also use the SQLOLEDB OLE DB provider to interact with SQL Server. And they can access SQL Server by way of ODBC through the OdbcConnection class. So, from managed code alone, you have three distinct ways of accessing SQL Server from an application. This is good to know from a troubleshooting standpoint because it can help you isolate connection-related problems you encounter to a particular data access layer or library.Client-Side Net-LibrariesThe next layer down in the stack is the Net-Library. A Net-Library provides the conduit between the API or object library an application uses to communicate with SQL Server and the networking protocols used to exchange data with the network. SQL Server provides Net-Libraries for all major networking protocols. These libraries transparently handle sending requests from the client to the SQL Server and returningthe server's responses to the client. You can configure which Net-Libraries are available on a particular client using SQL Server's Client Network Utility. Supported client-side protocols include TCP/IP, Named Pipes, Multiprotocol (RPC), and a few others.One Net-Library that's worth special mention here is the shared memory Net-Library. As the name suggests, this Net-Library uses Windows' shared memory facility to communicate between a SQL Server client and server. Naturally, this means that the client and server must reside on the same physical machine.Because it is able to bypass the physical network stack, the shared memory Net-Library can be considerably faster than other Net-Libraries. Access to the shared memory region is protected by synchronization objects, so the speed of the communication between the client and server is constrained mainly by Windows' ability to signal and unsigned kernel objects and processes' ability to copy data to and from the shared memory region.You can indicate that the shared memory Net-Library should be used by specifying either a period or (local) as your machine name when connecting. You can also prefix your machine\instance name with loc:when connecting to indicate that you want to use the shared memory Net-Library.Understand that, even when connecting to a SQL Server on the same machine, the shared memory Net-Library is not necessarily your best connection option. The directness of the connection between the client and server can limit its scalability in some situations. As with other elements in an application's overall architecture, you should always thoroughly test a given technology solution before assuming that it scales well or is faster than alternate approaches.ConnectionsWhen a client connects, SQL Server's user mode scheduler (UMS) component assigns it to a particular scheduler. At startup, SQL Server creates a separate UMS scheduler for each CPU on the system. As clients connect to the server, they are assigned to the scheduler with the fewest number of connections. Once connected, aclient never changes schedulers—it will remain on its assigned scheduler until it disconnects.This has important implications for applications that establish multiple connections to the server. If an application is poorly designed or does not evenly distribute work across its connections, it's possible for the app to cause needless contention for CPU resources between some of its connections, while others remain virtually idle.Say, for example, that at application establishes four connections to SQL Server that is running on a machine with two processors and that connections 1 and 3 end up on processor 0, while connections 2 and 4 end up on processor 1. If the lion's share of the app's work is carried out over connections 1 and 3, they will contend for CPU 0 while CPU 1 might remain virtually idle. In this situation, there's nothing the app can do but disconnect/reconnect some of its connections and hope that connections 1 and 3 end up on different CPUs (there's no way to specify processor affinity when connecting) or redistribute its workload across its connections such that they are more balanced. The latter is, of course, far preferable to the former.Connection MemorySQL Server sets aside three packet buffers for every connection made from a client. Each buffer is sized according to the default network packet size specified by the sp_configure stored procedure. If the default network packet size is less than 8KB, the memory for these packets comes from SQL Server's buffer pool. If it's 8KB or larger, the memory is allocated from SQL Server's MemToLeave region.It's worth noting that the default network packet size for the .NET Framework Data Provider for SQL Server is 8KB, so the buffers associated with managed code client connections typically come from SQL Server's MemToLeave region. This contrasts with classic ADO applications, where the default packet size is 4KB, and the buffers are allocated form the SQL Server buffer pool.EventsOnce connected, client requests typically fall into one of two broad categories: language events and remote procedure calls. Although there are certainly others, most requests from a SQL Server client to a server consist of one of these two types. A language event is a batch of T-SQL sent from the client to the server. For example, if you call the Execute method of an ADO Command object whose CommandText property is set to a T-SQL query and whose CommandType property is set to adCmdText, the query is submitted to the server as a language event. Likewise, if you set CommandType to adCmdTable and call the Execute method, ADO will generate an internal query that selects all the columns in the table identified by the CommandText property and submit it to the server as a language event. On the other hand, if you set CommandType to adStoredProc, calling Execute will cause ADO to submit a remote procedure call request to the server to execute the stored procedure listed in the CommandText property.Why do you care about whether you're submitting requests to the server as language events or RPCs? You care because RPCs, generally speaking, perform better, especially when you're repeatedly calling the same query with different filter values. Although SQL Server can auto-parameterize plain language event requests, its ability to do so is pretty limited. It will not attempt to auto-parameterize certain types of queries at all. This can cause different executions of what is essentially the same query to incur the cost of plan compilation on the server simply because they filter on different values. Quite often, this is not what you want—you want to compile a new plan for the first execution of a query, then reuse the plan for subsequent executions that happen to feature different parameters.An RPC, on the other hand, encourages plan reuse by explicitly parameter zing a query rather than relying on the server to do it. A single plan is generated for the first execution of the procedure, and subsequent executions automatically reuse it, even if they supply different values for the parameters. Calling a stored procedure using an RPC versus doing so through a language event not only saves the execution time and CPU resources required for plan compilation, it also makes better use ofSQL Server's memory resources because it avoids wasting memory on redundant execution plans.This is the same reason that sp_executesql is generally preferred to EXEC() when executing dynamic T-SQL. Sp_executesql works by creating a stored procedure using the specified query, then calling it using the supplied parameters. Unlike EXEC(), sp_executesql provides a mechanism that allows you to parameterize dynamic T-SQL and encourage plan reuse. A dynamic query that is executed using sp_executesql has a much better chance of avoiding unnecessary compilation and resource costs than one ran using EXEC().TDSRPCs, language events, and other types of requests sent from a client to SQL Server are formatted into a SQL Server-specific data format known as Tabular Data Stream (TDS). TDS is the "language" spoken between SQL Server clients and servers. Its exact format is no longer documented, but a client must speak TDS if it wishes to communicate with SQL Server.Currently, SQL Server supports three versions of TDS: TDS 8.0 (for SQL 2000 clients), TDS 7.0 (for SQL Server 7.0 clients), and TDS 4.2 (for SQL Server 4.2, 6.0, and 6.5 clients). The only version that completely supports all SQL Server 2000 features is TDS 8.0. The others are maintained for backward compatibility.Server-Side Net-LibrariesOn the server side, client requests are initially received by listeners SQL Server sets up to listen on particular networking protocols. These listeners consist of networking libraries on the server and the server-side Net-Libraries that provide a conduit between them and the server. You can configure the protocols on which the server listens using the Server Network Utility. Except when dealing with clusters, SQL Servers support the same range of networking protocols as is supported by clients. For clustered SQL Servers, only TCP/IP and Named Pipes are available.SQL Server sets up one thread per networking protocol on which it listens for client requests, and uses Windows' I/O completion port mechanism to wait for and process requests efficiently. As TDS packets are received from the network, the Net-Library listener reassembles them into their original client requests and passes them on to SQL Server's command-processing layer, Open Data Services (ODS).Returning Results to the ClientWhen the server is ready to return results for a particular client request, it uses the same network stack over which the request was initially received. It sends results over the server-side Net-Library to the appropriate networking protocol, and these, in turn, are sent back across the network to the client in TDS format.On the client-side, the TDS packets received from the server are reassembled from the IPC layer by the client-side Net-Library, and then forwarded on to the API or object library that initiated the request.Putting It All TogetherDespite all the pieces involved, the roundtrip between a SQL Server client and server can be quite fast—sub-second response time is not unusual at all, especially when working with the shared memory Net-Library. There are several data points here that are worth keeping in mind as you build and tune your own SQL Server client applications:∙If your app runs on the same machine as your SQL Server, consider using the shared memory Net-Library if you aren't already. Shared memory Net-Library-based connections are often considerably faster than other types of connections. Keep in mind what I said earlier, though: always thoroughly test a solution and compare it with viable alternatives before assuming that it is inherently better or faster. The proof is in the pudding.∙Because a client is assigned to a particular UMS scheduler when it first connects and will not leave that scheduler until it disconnects, it's important to ensure that an application's workload is balanced across the connections itestablishes to the server. Unbalanced workloads can cause unnecessary CPU contention and suboptimal resource usage.∙The default network packet size you configure on the server and that clients specify when connecting directly affects how much memory they require on the server and the pool from which it is allocated. Keep this in mind as you configure servers for scalability and speed. Also keep in mind that, by default, apps will have a larger network packet size than ADO apps.∙Generally speaking, you should prefer RPCs to language events when sending requests to the server. Set the appropriate properties in the ADO or objects you're using to facilitate this.∙When executing dynamic T-SQL, use sp_executesql rather than EXEC() when possible. About the only time this isn't possible is when using EXEC()'s ability to concatenate query fragments into dynamic query strings that exceed what can be stored in a single local variable (a rare situation).∙When you run into client-side problems that you suspect may have to do with the object library or API you're using to reach the server, one troubleshooting technique you can use is to change the client-side mechanism you're using so that you can isolate the problem to a particular component. For example, let's say that you upgrade MDAC and begin seeing 17805 errors in your SQL Server error log indicating that malformed TDS packets are arriving from a client-side ADO application. You might try switching the app to use the OLE DB provider for ODBC, if you can do so without much trouble, to see whether the problem is related to the SQLOLEDB provider in some way. Conversely, if your ADO-based app has been connecting over ODBC, you might switch to SQLOLEDB to see if that remedies the problem or at least helps you narrow the scope.∙Along these same lines, it sometimes makes sense to change out the Net-Library you're using when troubleshooting connection-related problems.If you're using TCP/IP, perhaps Named Pipes would be worth trying. For example, if you're running into an issue with your DHCP server and don't havea valid IP address, you won't be able to connect to SQL Server using TCP/IP.By switching to Named Pipes, you can quickly isolate the problem to something specific to TCP/IP. On the other hand, if you switch Net Libraries and still have the same problem, you can probably rule out Net-Library-specific issues. Perhaps the server is down or a piece of the network infrastructure between you and the server is not functioning properly.If nothing else, being able to easily change the Net-Library an app uses without having to change the app itself gives you a tool for helping isolate problems. Even if a particular Net-Library isn't viable for you in the long term, temporarily switching a client to use it can help narrow down where a connection-related issue resides.Introduction to information management system of the hotelPurpose of this project are: universal access to computer technology, the traditional hotel management technology does not suit the needs of the contemporary development of hotel and guesthouse accommodation, hotel management to keep the guests one of the major factors. Hotel business links related to the work of more broad, the hotel is no longer only the traditional accommodation and settlement, but contains a wider range of services. As a service industry, from the guests scheduled to stay at the hotel registration until you check out, if you can provide fast and convenient service to guests, you will give guests a better feeling, so that you can enhance the rate of second glance of the hotel. Hotel information management system is in such demand.This project is mainly to solve daily basic requirements of hotels involved in the management of information, the goal is to make the administrator a convenient, speedy and efficient room on the Web site management, reservations, check out business. This site includes basic information management staff, rooms basic information management, reservation management, room unsubscribe management, sales management, and other important modules..NET简介.NET 框架.NET Framework 是用于生成、部署和运行 XML Web services 和应用程序的多语言环境。
英文文献小短文(原文加汉语翻译)

A fern that hyperaccumulates arsenic(这是题目,百度一下就能找到原文好,原文还有表格,我没有翻译)A hardy, versatile, fast-growing plant helps to remove arsenic from contaminated soilsContamination of soils with arsenic,which is both toxic and carcinogenic, is widespread1. We have discovered that the fern Pteris vittata (brake fern) is extremely efficient in extracting arsenic from soils and translocating it into its above-ground biomass. This plant —which, to our knowledge, is the first known arsenic hyperaccumulator as well as the first fern found to function as a hyperaccumulator— has many attributes that recommend it for use in the remediation of arsenic-contaminated soils.We found brake fern growing on a site in Central Florida contaminated with chromated copper arsenate (Fig. 1a). We analysed the fronds of plants growing at the site for total arsenic by graphite furnace atomic absorption spectroscopy. Of 14 plant species studied, only brake fern contained large amounts of arsenic (As;3,280–4,980 We collected additional samples of the plant and soil from the contaminated site –1,603 As) and from an uncontaminated site –As). Brake fern extracted arsenic efficiently from these soils into its fronds: plantsgrowing in the contaminated site contained 1,442–7,526 Arsenic and those from the uncontaminated site contained –These values are much higher than those typical for plants growing in normal soil, which contain less than of arsenic3.As well as being tolerant of soils containing as much as 1,500 arsenic, brake fern can take up large amounts of arsenic into its fronds in a short time (Table 1). Arsenic concentration in fern fronds growing in soil spiked with 1,500 Arsenic increased from to 15,861 in two weeks. Furthermore, in the same period, ferns growing in soil containing just 6 arsenic accumulated 755 Of arsenic in their fronds, a 126-fold enrichment. Arsenic concentrations in brake fernroots were less than 303 whereas those in the fronds reached 7,234 of 100 Arsenic significantly stimulated fern growth, resulting in a 40% increase in biomass compared with the control (data not shown).After 20 weeks of growth, the plant was extracted using a solution of 1:1 methanol:water to speciate arsenic with high-performance liquid chromatography–inductively coupled plasma mass spectrometry. Almost all arsenic was present as relatively toxic inorganic forms, with little detectable organoarsenic species4. The concentration of As(III) was greater in the fronds (47–80%) than in the roots %), indicating that As(V)was converted to As(III) during translocation from roots to fronds.As well as removing arsenic from soils containing different concentrations of arsenic (Table 1), brake fern also removed arsenic from soils containing different arsenic species (Fig. 1c). Again, up to 93% of the arsenic was concentrated in the fronds. Although both FeAsO4 and AlAsO4 are relatively insoluble in soils1, brake fern hyperaccumulated arsenic derived from these compounds into its fronds (136–315 levels 3–6 times greater than soil arsenic.Brake fern is mesophytic and is widely cultivated and naturalized in many areas with a mild climate. In the United States, it grows in the southeast and in southern California5. The fern is versatile and hardy, and prefers sunny (unusual for a fern) and alkaline environments (where arsenic is more available). It has considerable biomass, and is fast growing, easy to propagate,and perennial.We believe this is the first report of significant arsenic hyperaccumulation by an unmanipulated plant. Brake fern has great potential to remediate arsenic-contaminated soils cheaply and could also aid studies of arsenic uptake, translocation, speciation, distribution anddetoxification in plants.*Soil and Water Science Department, University ofFlorida, Gainesville, Florida 32611-0290, USAe-mail†Cooperative Extension Service, University ofGeorgia, Terrell County, PO Box 271, Dawson,Georgia 31742, USA‡Department of Chemistry & SoutheastEnvironmental Research Center, FloridaInternational University, Miami, Florida 33199,1. Nriagu, J. O. (ed.) Arsenic in the Environment Part 1: Cycling and Characterization (Wiley, New York, 1994).2. Brooks, R. R. (ed.) Plants that Hyperaccumulate Heavy Metals (Cambridge Univ. Press, 1998).3. Kabata-Pendias, A. & Pendias, H. in Trace Elements in Soils and Plants 203–209 (CRC, Boca Raton, 1991).4. Koch, I., Wang, L., Ollson, C. A., Cullen, W. R. & Reimer, K. J. Envir. Sci. Technol. 34, 22–26 (2000).5. Jones, D. L. Encyclopaedia of Ferns (Lothian, Melbourne, 1987).积累砷的蕨类植物耐寒,多功能,生长快速的植物,有助于从污染土壤去除砷有毒和致癌的土壤砷污染是非常广泛的。
英文文献及翻译(计算机专业)

英文文献及翻译(计算机专业)The increasing complexity of design resources in a net-based collaborative XXX common systems。
design resources can be organized in n with design activities。
A task is formed by a set of activities and resources linked by logical ns。
XXX managementof all design resources and activities via a Task Management System (TMS)。
which is designed to break down tasks and assign resources to task nodes。
This XXX。
2 Task Management System (TMS)TMS is a system designed to manage the tasks and resources involved in a design project。
It poses tasks into smaller subtasks。
XXX management of all design resources and activities。
TMS assigns resources to task nodes。
XXX。
3 Collaborative DesignCollaborative design is a process that XXX a common goal。
In a net-based collaborative design environment。
n XXX n for all design resources and activities。
英文文献翻译

Preparation and characterization of Ag-TiO2 hybrid clusters powders[1](Ag-TiO2混合团簇粉末的制备和表征)Abstract:液相电弧放电法被用于制备纳米Ag-TiO2复合超细粉末。
XRD和TEM图表明颗粒呈葫芦状形态,分布狭窄。
我们讨论了实验条件对产品的影响,比较了这种方法制备的粉末和其他γ射线辐照法制备的粉末。
Introduction:材料合成技术,提高了研究特定电子和光学特性的能力。
这也导致了设备和不同效应的快速发展,如集成光学型偏振器[1]和量子霍耳效应。
所需的长度尺度对于这些结构的控制是在纳米级别的[ 2 ]。
科学家面临的一个新的挑战是半导体量子点的生长,它具有新的光学响应,引起了对其基础物理方面和三阶非线性光致发光的应用等的研究兴趣。
这方面的一个例子是Ag-TiO2复合材料通过胶体方法合成[ 3 ]或由γ射线辐照法合成[ 4 ]。
对比其他制备超细金属颗粒的方法,γ射线辐照法能在室温的环境压力下产生粉末。
在这封信中,我们开发了一种新的方法,即液相电弧放电法,用以制备纳米复合材料,当它经水热处理可以得到纳米级别的超细粉。
Preparation and photocatalytic activity of immobilized composite photocatalyst (titania nanoparticle/activated carbon)[2]固定化复合光催化剂(TiO2纳米颗粒/活性炭)的制备和光催化活性研究Abstract:制备了一种固定化复合光催化剂——TiO2纳米颗粒/活性炭(AC),并研究了它在降解纺织染料的光催化活性。
AC通过油菜籽壳制备。
碱性红18(BR18)和碱性红46(BR46)被用来作为模型染料。
并采用了傅里叶变换红外(FTIR),波长色散X射线光谱(WDX),扫描电子显微镜(SEM),紫外可见分光光度法,化学需氧量(COD)和离子色谱(IC)分析。
中英文文献翻译

Database introduction and ACCESS2000The database is the latest technology of data management, and the important branch of computer science. The database , as its name suggests, is the warehouse to preserve the data. The warehouse to store apparatus in computer only, and data to deposit according to sure forms。
The so-called database is refers to the long-term storage the data acquisition which in the computer, organized, may share。
In the database data according to the certain data model organization, the description, and the storage, has a smaller redundance, the higher data independence and the easy extension, and may altogether shine for each kind of user。
The effective management database, frequently has needed some database management systems (DBMS) is the user provides to database operation each kind of order, the tool and the method, including database establishment and recording input, revision, retrieval, demonstration, deletion and statistics。
外文文献翻译原文+译文

外文文献翻译原文Analysis of Con tin uous Prestressed Concrete BeamsChris BurgoyneMarch 26, 20051、IntroductionThis conference is devoted to the development of structural analysis rather than the strength of materials, but the effective use of prestressed concrete relies on an appropriate combination of structural analysis techniques with knowledge of the material behaviour. Design of prestressed concrete structures is usually left to specialists; the unwary will either make mistakes or spend inordinate time trying to extract a solution from the various equations.There are a number of fundamental differences between the behaviour of prestressed concrete and that of other materials. Structures are not unstressed when unloaded; the design space of feasible solutions is totally bounded;in hyperstatic structures, various states of self-stress can be induced by altering the cable profile, and all of these factors get influenced by creep and thermal effects. How were these problems recognised and how have they been tackled?Ever since the development of reinforced concrete by Hennebique at the end of the 19th century (Cusack 1984), it was recognised that steel and concrete could be more effectively combined if the steel was pretensioned, putting the concrete into compression. Cracking could be reduced, if not prevented altogether, which would increase stiffness and improve durability. Early attempts all failed because the initial prestress soon vanished, leaving the structure to be- have as though it was reinforced; good descriptions of these attempts are given by Leonhardt (1964) and Abeles (1964).It was Freyssineti’s observations of the sagging of the shallow arches on three bridges that he had just completed in 1927 over the River Allier near Vichy which led directly to prestressed concrete (Freyssinet 1956). Only the bridge at Boutiron survived WWII (Fig 1). Hitherto, it had been assumed that concrete had a Young’s modulus which remained fixed, but he recognised that the de- ferred strains due to creep explained why the prestress had been lost in the early trials. Freyssinet (Fig. 2) also correctly reasoned that high tensile steel had to be used, so that some prestress would remain after the creep had occurred, and alsothat high quality concrete should be used, since this minimised the total amount of creep. The history of Freyssineti’s early prestressed concrete work is written elsewhereFigure1:Boutiron Bridge,Vic h yFigure 2: Eugen FreyssinetAt about the same time work was underway on creep at the BRE laboratory in England ((Glanville 1930) and (1933)). It is debatable which man should be given credit for the discovery of creep but Freyssinet clearly gets the credit for successfully using the knowledge to prestress concrete.There are still problems associated with understanding how prestressed concrete works, partly because there is more than one way of thinking about it. These different philosophies are to some extent contradictory, and certainly confusing to the young engineer. It is also reflected, to a certain extent, in the various codes of practice.Permissible stress design philosophy sees prestressed concrete as a way of avoiding cracking by eliminating tensile stresses; the objective is for sufficient compression to remain after creep losses. Untensionedreinforcement, which attracts prestress due to creep, is anathema. This philosophy derives directly from Freyssinet’s logic and is primarily a working stress concept.Ultimate strength philosophy sees prestressing as a way of utilising high tensile steel as reinforcement. High strength steels have high elastic strain capacity, which could not be utilised when used as reinforcement; if the steel is pretensioned, much of that strain capacity is taken out before bonding the steel to the concrete. Structures designed this way are normally designed to be in compression everywhere under permanent loads, but allowed to crack under high live load. The idea derives directly from the work of Dischinger (1936) and his work on the bridge at Aue in 1939 (Schonberg and Fichter 1939), as well as that of Finsterwalder (1939). It is primarily an ultimate load concept. The idea of partial prestressing derives from these ideas.The Load-Balancing philosophy, introduced by T.Y. Lin, uses prestressing to counter the effect of the permanent loads (Lin 1963). The sag of the cables causes an upward force on the beam, which counteracts the load on the beam. Clearly, only one load can be balanced, but if this is taken as the total dead weight, then under that load the beam will perceive only the net axial prestress and will have no tendency to creep up or down.These three philosophies all have their champions, and heated debates take place between them as to which is the most fundamental.2、Section designFrom the outset it was recognised that prestressed concrete has to be checked at both the working load and the ultimate load. For steel structures, and those made from reinforced concrete, there is a fairly direct relationship between the load capacity under an allowable stress design, and that at the ultimate load under an ultimate strength design. Older codes were based on permissible stresses at the working load; new codes use moment capacities at the ultimate load. Different load factors are used in the two codes, but a structure which passes one code is likely to be acceptable under the other.For prestressed concrete, those ideas do not hold, since the structure is highly stressed, even when unloaded. A small increase of load can cause some stress limits to be breached, while a large increase in load might be needed to cross other limits. The designer has considerable freedom to vary both the working load and ultimate load capacities independently; both need to be checked.A designer normally has to check the tensile and compressive stresses, in both the top and bottom fibre of the section, for every load case. The critical sections are normally, but not always, the mid-span and the sections over piers but other sections may become critical ,when the cable profile has to be determined.The stresses at any position are made up of three components, one of which normally has a different sign from the other two; consistency of sign convention is essential.If P is the prestressing force and e its eccentricity, A and Z are the area of the cross-section and its elastic section modulus, while M is the applied moment, then where ft and fc are the permissible stresses in tension and compression.c e t f ZM Z P A P f ≤-+≤Thus, for any combination of P and M , the designer already has four in- equalities to deal with.The prestressing force differs over time, due to creep losses, and a designer isusually faced with at least three combinations of prestressing force and moment;• the applied moment at the time the prestress is first applied, before creep losses occur,• the maximum applied moment after creep losses, and• the minimum applied moment after creep losses.Figure 4: Gustave MagnelOther combinations may be needed in more complex cases. There are at least twelve inequalities that have to be satisfied at any cross-section, but since an I-section can be defined by six variables, and two are needed to define the prestress, the problem is over-specified and it is not immediately obvious which conditions are superfluous. In the hands of inexperienced engineers, the design process can be very long-winded. However, it is possible to separate out the design of the cross-section from the design of the prestress. By considering pairs of stress limits on the same fibre, but for different load cases, the effects of the prestress can be eliminated, leaving expressions of the form:rangestress e Perm issibl Range Mom entZ These inequalities, which can be evaluated exhaustively with little difficulty, allow the minimum size of the cross-section to be determined.Once a suitable cross-section has been found, the prestress can be designed using a construction due to Magnel (Fig.4). The stress limits can all be rearranged into the form:()M fZ PA Z e ++-≤1 By plotting these on a diagram of eccentricity versus the reciprocal of the prestressing force, a series of bound lines will be formed. Provided the inequalities (2) are satisfied, these bound lines will always leave a zone showing all feasible combinations of P and e. The most economical design, using the minimum prestress, usually lies on the right hand side of the diagram, where the design is limited by the permissible tensile stresses.Plotting the eccentricity on the vertical axis allows direct comparison with the crosssection, as shown in Fig. 5. Inequalities (3) make no reference to the physical dimensions of the structure, but these practical cover limits can be shown as wellA good designer knows how changes to the design and the loadings alter the Magnel diagram. Changing both the maximum andminimum bending moments, but keeping the range the same, raises and lowers the feasible region. If the moments become more sagging the feasible region gets lower in the beam.In general, as spans increase, the dead load moments increase in proportion to the live load. A stage will be reached where the economic point (A on Fig.5) moves outside the physical limits of the beam; Guyon (1951a) denoted the limiting condition as the critical span. Shorter spans will be governed by tensile stresses in the two extreme fibres, while longer spans will be governed by the limiting eccentricity and tensile stresses in the bottom fibre. However, it does not take a large increase in moment ,at which point compressive stresses will govern in the bottom fibre under maximum moment.Only when much longer spans are required, and the feasible region moves as far down as possible, does the structure become governed by compressive stresses in both fibres.3、Continuous beamsThe design of statically determinate beams is relatively straightforward; the engineer can work on the basis of the design of individual cross-sections, as outlined above. A number of complications arise when the structure is indeterminate which means that the designer has to consider, not only a critical section,but also the behaviour of the beam as a whole. These are due to the interaction of a number of factors, such as Creep, Temperature effects and Construction Sequence effects. It is the development of these ideas whichforms the core of this paper. The problems of continuity were addressed at a conference in London (Andrew and Witt 1951). The basic principles, and nomenclature, were already in use, but to modern eyes concentration on hand analysis techniques was unusual, and one of the principle concerns seems to have been the difficulty of estimating losses of prestressing force.3.1 Secondary MomentsA prestressing cable in a beam causes the structure to deflect. Unlike the statically determinate beam, where this motion is unrestrained, the movement causes a redistribution of the support reactions which in turn induces additional moments. These are often termed Secondary Moments, but they are not always small, or Parasitic Moments, but they are not always bad.Freyssinet’s bridge across the Marne at Luzancy, started in 1941 but not completed until 1946, is often thought of as a simply supported beam, but it was actually built as a two-hinged arch (Harris 1986), with support reactions adjusted by means of flat jacks and wedges which were later grouted-in (Fig.6). The same principles were applied in the later and larger beams built over the same river.Magnel built the first indeterminate beam bridge at Sclayn, in Belgium (Fig.7) in 1946. The cables are virtually straight, but he adjusted the deck profile so that the cables were close to the soffit near mid-span. Even with straight cables the sagging secondary momentsare large; about 50% of the hogging moment at the central support caused by dead and live load.The secondary moments cannot be found until the profile is known but the cablecannot be designed until the secondary moments are known. Guyon (1951b) introduced the concept of the concordant profile, which is a profile that causes no secondary moments; es and ep thus coincide. Any line of thrust is itself a concordant profile.The designer is then faced with a slightly simpler problem; a cable profile has to be chosen which not only satisfies the eccentricity limits (3) but is also concordant. That in itself is not a trivial operation, but is helped by the fact that the bending moment diagram that results from any load applied to a beam will itself be a concordant profile for a cable of constant force. Such loads are termed notional loads to distinguish them from the real loads on the structure. Superposition can be used to progressively build up a set of notional loads whose bending moment diagram gives the desired concordant profile.3.2 Temperature effectsTemperature variations apply to all structures but the effect on prestressed concrete beams can be more pronounced than in other structures. The temperature profile through the depth of a beam (Emerson 1973) can be split into three components for the purposes of calculation (Hambly 1991). The first causes a longitudinal expansion, which is normally released by the articulation of the structure; the second causes curvature which leads to deflection in all beams and reactant moments in continuous beams, while the third causes a set of self-equilibrating set of stresses across the cross-section.The reactant moments can be calculated and allowed-for, but it is the self- equilibrating stresses that cause the main problems for prestressed concrete beams. These beams normally have high thermal mass which means that daily temperature variations do not penetrate to the core of the structure. The result is a very non-uniform temperature distribution across the depth which in turn leads to significant self-equilibrating stresses. If the core of the structure is warm, while the surface is cool, such as at night, then quite large tensile stresses can be developed on the top and bottom surfaces. However, they only penetrate a very short distance into the concrete and the potential crack width is very small. It can be very expensive to overcome the tensile stress by changing the section or the prestress。
英文文献翻译(1)

英文文献翻译二〇一四年月日科技文章摘译Preventing electricity-stolen smart metersWith the development, it has been increasingly used in smart instrumentation equipment, so that the instrument performance have been greatly improved. This article describes the preventing electricity-stolen smart meters is to the ATMEL AT89C51 microcontroller as the core of the design, it achieves 32 power measurement and touring shows, and other functions, but also preventing electricity-stolen, anti-submarine-moving, high-precision, long-life And low power consumption and other characteristics of the new residential areas and is the preferred meter in the urban network reform.Hardware design(l) Signal acquisition and conversion of the electric circuit is more complicated measures, the traditional way is to sample the respective current, voltage, the AID conversion after their multiplication. This approach is not only to analog circuit design of high demand, the software programming requirements are also high, but it is difficult to achieve multiple users on the measure. Therefore, we choose BL0932B as a signal acquisition and conversion circuit core, it is an electronic power meter ASIC. BL0932B design based on the signal acquisition and conversion external circuit board with simple, high precision and stability, and other characteristics, especially for single-phase two-line power users of energy metering.BLO932B within the buffer amplifier, analog multiplier, VIF converters, counting circuit and drive circuit, can accurately measure positive and negative direction of the two active power and computing power in the same direction. The output in two ways: rapid pulse output and slow output for the former computer data processing, the latter used to drive pulse motor work.As the signal acquisition and conversion circuit board as well as the high-voltage 220 v, there Baidoa v order of magnitude of the small-signal, which requires the printed circuit board design and production process to be very scientific and rational. In addition, in order to protect the motherboard, BL0932B rapid pulse of the photoelectric sent to isolation after the SCM.(2) MCU control circuitSCM control circuit, including analog switch arrays, display and keypad circuit, datastorage, serial communications interface and watchdog circuit.l) analog switch array Preventing electricity-stolen smart meters are centralized meter, the MCU to the multi-pulse signals in real-time detection, therefore, it uses an Analog Switches CD405I of four eight-select and a 3 to 8 decoder 74 LS138 common Composed of analog switch arrays,ang it achieve a 32-way pulse of the cycle of detection.2) And show circuit as a key focus on smart meters, need to show the contents of many. Main form of households, electricity, the status of various instructions and error information. To this end, we designed the LED display, from 10 strings and static converters 74 LSl64 drive so you can at least take up the MCU resources. In addition, the signal input terminal also designed the 25 LED indicator, to display the 25 electricity capacity.The meters are "checking" and "cleared" two function keys are directly linked to the P3 in 89 C51 on the mouth. Through a combination of the two keys, can easily achieve the MCU cleared meter, single households cleared, online check, such as locking and unlocking operation.3) Data storage because of the configuration of the table need to record a large number of important data, in order to ensure data security, we designed the two data memory: parallel data memory and serial data memory. Parallel data memory by 6264, it has SK bytes of storage space, to fully meet the requirements of the table. In order to prevent power-down when the data loss, to the 6264 allocation of the 3.6 v backup battery. Backup battery switch and the 6264 election signals the film, by special worship P MAx691 provide monitoring chip. Serial data memory by 24 LC65, it also has a SK bytes of storage space, and through IZC bus connected with the MCU. Although there is no IZC 89C51 microcontroller bus interface, but through software programming, P1 I can simulate the two lines of its timing, completion of the 24 LC65 read and write operations. 24LC65 is a serial EZPROM, without battery backup, data can be safely stored in 200 years.4) Serial communication interface 89 C51 has a full-duplex serial interface, used in this meter for meter reading and communication interface. In order to achieve far more concentrated form clusters copied, in the serial interface on the basis of plus RS485 driver chips 75 LBC184. This can be through various meter RS485 bus and data acquisition system for communication links, and concentrate meter reading, remote meter reading.4) watchdog circuit watchdog circuit used for monitoring chip mix P MAX691, it has a power-on reset, brownout detection, backup battery switch and watchdog timer input output, and other functions. To determine whether the cumulative electricity. This part of the programming is mainly used in order to achieve the operation, with fewer bytes RAMoccupation, the code simple and fast, and other advantages.(3) Data validation and multi-site storage of data directly related to electricity users and property management departments of vital interests, is the most important data, we must ensure that its security is absolutely right and, therefore, in the real data storage, all of the electricity Check to ensure the accuracy of the data. Data in 6264 and 2465 have been taken in the multi-site storage, backup each other to ensure that data foolproof. Practice has proved that these measures, the data will no longer be an error or lost, the effect is very obvious.(4) of electricity and stepping roving show that the normal operation procedure, the pulse measurement, shows that various tour operators, and its power, when the last one shows that the electricity consumption, to calculate the unit's total electricity consumption and display, and then To start from scratch cycle show. In order to facilitate the spot meter reading, specially designed step show: that is, each press a button detection, household electricity consumption, and also shows the integral part.防偷电智能电表随发展,它已被越来越多地用于仪器仪表中构成智能仪器,从而使仪器仪表的性能得到极大改善。
英文文献全文翻译

英文文献全文翻译全文共四篇示例,供读者参考第一篇示例:English literature has a long and rich history, with countless works that have been translated into various languages around the world. From ancient epics like Beowulf and The Odyssey to modern classics like To Kill a Mockingbird and Harry Potter, English literature has captured the hearts and minds of readers for centuries.第二篇示例:The world of academic research is vast and ever-growing, with a wealth of knowledge and information being produced every day. One important aspect of this research is the publication of English-language academic articles. These articles cover a wide range of topics across various fields, from science and technology to social sciences and humanities.第三篇示例:English literature is a treasure trove of human culture and knowledge. The literary works of great writers from around theworld offer insights into the human experience, emotions, and imagination. Through the process of translation, these literary masterpieces are made accessible to a global audience, allowing people from different cultures and backgrounds to connect and appreciate the beauty of language and storytelling.第四篇示例:Abstract:Introduction:English literature holds a prominent position in the field of international academia, with a vast number of research articles, books, and journals being published in English. For researchers and scholars in non-English speaking countries, access to English literature is essential for staying up-to-date with the latest developments in their respective fields. However, understanding and interpreting English texts can present significant challenges due to linguistic, cultural, and contextual differences.Challenges in Translating English Literature:。
5000字英文范文翻译类

In new network on 2 September Xinhua comprehensive report, the situation in Syria is currently in the United States of America in the teeth of the storm, President Obama issued a statement in August 31st, decided to take military action against the Syrian government target, the White House has formally asked Congress to authorize. But in the United States, Obama faces two trials of Congress and the public; in foreign countries, the multinational NATO would not send troops, many countries also oppose the United States plans. Analysis refers to the Syrian military command, Obama was "imminent", but his support for the difficulties, may "itself".The contradiction: the Congress attitude unknown Obama fears "riding a tiger"Local time on August 31st, the United States President Barack Obama issued a statement at the White House, said that "after careful consideration, I have decided that the United States should the regime in Syria to take military action against the target. It will not be indefinite intervention, we will not send ground troops, instead we aim to limit the action time and scale."But Obama said, he also made second decisions, is "to get authorization from Congress to", only the consent of Congress, I ordered the U.S. war on Syria. On the same day, the official White House to Congress a proposal, according to the United States Congress "War Powers Act" and the United Nations Security Council in 2004 passed a resolution, authorized the president to take military action in Syria.In the proposal, Obama asked Congress to use the authorization bill Syria, intended to deter, prevent and reduce blow, Syria continue to use chemical weapons and other weapons of mass destruction in the future. He also said, Syria internal conflict was resolved by political consultation.The analysis thinks, Obama remarks on the question of Syria to slam the brakes, to seek congressional approval for a military attack against Syria, is likely to lead to the United States at least 10 days delay action.However, Obama this "gambling" type decision will make it a tough fight. Obama broke the decades of practice, has announced that it will seek congressional approval Syria suspected use chemical weapons to act. But the United States senators would support Obama, will defeat him swallow bitter is still uncertain.Analysis pointed out that, Obama this bet is risky, he bet he could get Congress agreed to a limited attack Syria, defending against the international ban, the United States national security interests, and to protect Turkey, Jordan, Israel and other allies in the middle east.Obama had previously insisted, he retained ignore Congress decided to attack the right, White House officials said the change would give Obama more time to win internationalsupport. But for Obama, the most difficult and most threatening the authority of the president's war, or between members of Congress of political wrangling, because it cannot determine the Congress will support the attack on Syria.Observers caution, Obama could face the same fate with British Prime Minister Cameron. Cameron for the British Parliament authorized military action, but was rejected.Obama may be full of confidence, that he can win the vote in the Democratic controlled senate. The Senate also has many Republicans to take military action. However, he is in the house of Representatives won the support of the opportunity is not sure. The house has many conservative core people everywhere, to interfere with Obama's plan.In addition, the American people on the government military intervention plan highlights the ambivalence, and the Obama administration, Congress and the U.S. is unease shrouded. The Afghan war and the Iraq war, costly delay for a long time, the American people are unwilling to once again involved in the conflict in the middle east.The United States National Broadcasting Company (NBC) recently in a poll, half of Americans polled for the government of Syria military strikes do not support, only 35% behind Obama in the process encountered a time he was the most difficult questions of the 700 respondents.Only 1/5 of respondents said the military action, which is in the American national interest, and only 27% of the people think that the military can make the situation in Syria.If the United States to take action, 56% of people said that, the aim should be to prevent the use of chemical weapons. Only a small number of people (16% or less), military action to overthrow the Assad regime or stop Syria clashes between government forces and armed opposition.Outside the opposition: 12 NATO countries to the international community to anti war emotionWhen Obama published "on the Syrian military" statement on the same day, the United States anti war organizations held a protest outside the White House, shouting anti war slogans. People playing white banners and placards reading "not yellow, the Syrian war", "the Syrian military built on lies" etc.. The activities of the organization responsible person said, the day before and after the estimated 500 people have been involved in the protests, the organizers also prepared during the three day "Labor Day" long weekend continue to hold protest in front of the White House, where all over the United States would have to Washington to participate in.In August 31st, the British capital London is also the outbreak of large-scaledemonstrations, oppose aggression against Syria. According to the organization of this parade "anti war alliance", a total of 5000 people took part in the parade.The British Parliament in August 29th voted against Prime Minister Cameron to attack Syria's proposal, was named the greatest shame Cameron to be in power for three years "suffer". Although Obama assured Cameron that the relationship between them is still strong, but the British media will Cameron's the signs of failure as the so-called "special relationship" and "doomsday". They worry, support for military action.。
毕业论文5000字英文文献翻译(c++)

英文翻译英语原文:. Introducing ClassesThe only remaining feature we need to understand before solving our bookstore problem is how to write a data structure to represent our transaction data. In C++ we define our own data structure by defining a class. The class mechanism is one of the most important features in C++. In fact, a primary focus of the design of C++ is to make it possible to define class types that behave as naturally as the built-in types themselves. The library types that we've seen already, such as istream and ostream, are all defined as classesthat is,they are not strictly speaking part of the language.Complete understanding of the class mechanism requires mastering a lot of information. Fortunately, it is possible to use a class that someone else has written without knowing how to define a class ourselves. In this section, we'll describe a simple class that we canuse in solving our bookstore problem. We'll implement this class in the subsequent chapters as we learn more about types,expressions, statements, and functionsall of which are used in defining classes.To use a class we need to know three things:What is its name?Where is it defined?What operations does it support?For our bookstore problem, we'll assume that the class is named Sales_item and that it is defined in a header named Sales_item.h.The Sales_item ClassThe purpose of the Sales_item class is to store an ISBN and keep track of the number of copies sold, the revenue, and average sales price for that book. How these data are stored or computed is not our concern. To use a class, we need not know anything about how it is implemented. Instead, what we need to know is what operations the class provides.As we've seen, when we use library facilities such as IO, we must include the associated headers. Similarly, for our own classes, we must make the definitions associated with the class available to the compiler. We do so in much the same way. Typically, we put the class definition into a file. Any program that wants to use our class must include that file.Conventionally, class types are stored in a file with a name that, like the name of a program source file, has two parts: a file name and a file suffix. Usually the file name is the same as the class defined in the header. The suffix usually is .h, but some programmers use .H, .hpp, or .hxx. Compilers usually aren't picky about header file names, but IDEs sometimes are. We'll assume that our class is defined in a file named Sales_item.h.Operations on Sales_item ObjectsEvery class defines a type. The type name is the same as the name of the class. Hence, our Sales_item class defines a type namedSales_item. As with the built-in types, we can define a variable of a class type. When we write "Sales_item item" we are saying that item is an object of type Sales_item. We often contract the phrase "an object of type Sales_item" to"aSales_ item object" or even more simply to "a Sales_item."In addition to being able to define variables of type Sales_item, we can perform the following operations on Sales_item objects:Use the addition operator, +, to add two Sales_items,Use the input operator, << to read a Sales_item object,Use the output operator, >> to write a Sales_item object,Use the assignment operator, =, to assign one Sales_item object to another,Call the same_isbn function to determine if two Sales_items refer to the same book.Classes are central to most C++ programs: Classes let us define our own types that are customizedfor the problems we need to solve, resulting in applications that are easier to write and understand.Well-designed class types can be as easy to use as the built-in types.A class defines data and function members: The data members store the state associated with objectsof the class type, and the functions perform operations that give meaning to the data. Classeslet us separate implementation and interface. The interface specifies the operations that the classsupports. Only the implementor of the class need know or care about the details of the implementation. This separation reduces the bookkeeping aspects that make programming tedious anderror-prone.Class types often are referred to as abstract data types. An abstract data type treats the data<state> and operations on that state as a single unit. We can think abstractly about what the classd oes, rather than always having to be aware of how the class operates. Abstract data types arefundamental to both object-oriented and generic programming.Data abstraction is a programming <and design> technique that relies on the separation of interfaceand implementation. The class designer must worry about how a class is implemented, but programmersthat use the class need not know about these details. Instead, programmers who use a type need to know only the type's interface; they can think abstractly about what the type does rather than concretely about how the type works.Encapsulation is a term that describes the technique of combining lower-level elements to forma new, higher-level entity. A function is one form of encapsulation: The detailed actions performedby the function are encapsulated in the larger entity that is the function itself. Encapsulated elements hide the details of their implementationwe may call a function but have no access to the statements that it executes. In the same way, a class is an encapsulated entity: It represents an aggregation of several members, and most <well-designed> class types hide the members that implement the type.If we think about the library vector type, it is an example of both data abstraction andencapsulation. It is abstract in that to use it, we think about its interfaceabout the operations that it can perform. It is encapsulated because we have no access to the details of how the type is representated nor to any of its implementation artifacts. An array, on the other hand, is similar in concept to a vector but is neither abstract nor encapsulated. We manipulate an array directly by accessing the memory in which the array is stored.Not all types need to be abstract. The library pair class is a good example of a useful, well-designed class that is concrete rather than abstract. A concrete class is a class that exposes, rather than hides, its implementation.Some classes, such as pair, really have no abstract interface. The pair type exists to bundle two data members into a single object. There is no need or advantage to hiding the data members. Hiding the members in a class like pair would only complicate the use of the type.Even so, such types often have member functions. In particular, it is a good idea for any class that has data members of built-in or compound type to define constructor<s> to initialize those members. The user of the class could initialize or assign to the data members but it is less error-prone for the class to do so.Programmers tend to think about the people who will run their applications as "users." Applicationsare designed for and evolve in response to feedback from those who ultimately "use" the applications. Classes are thought of in a similar way: A class designer designs and implements a class for "users" of that class. In this case, the "user" is a programmer, not the ultimate user of the application.Authors of successful applications do a good job of understanding and implementing the needs ofthe application's users. Similarly, well-designed, useful classes are designed with a close attention to the needs of the users of the class.In another way, the division between class designer and class user reflects the division betweenusers of an application and the designers and implementors of the application. Users care only if the application meets their needs in a cost-effective way. Similarly, users of a class care only about its interface. Good class designers define a class interface that is intuitive and easy to use. Users care about the implementation only in so far as the implementation affects their use of the class. If the implementation is too slow or puts burdens on users of the class, then the users must care. In well-designed classes, only the class designer worries about the implementation.In simple applications, the user of a class and the designer of the class might be one and the same person. Even in such cases, it is useful to keep the roles distinct. When designing the interface to a class, the class designer should think about how easy it will be to use the class. When using the class, the designer shouldn't think about how the class works.When referring to a "user," the context makes it clear which kind of user is meant. If we speak of "user code" or the "user" of the Sales_item class, we mean a programmer whois using a class in writing an application. If we speak of the "user" of the bookstore application, we mean the manager of the store who is running the application.Data abstraction and encapsulation provide two important advantages:1.Class internals are protected from inadvertent user-level errors, which might corrupt the state of the object.2.The class implementation may evolve over time in response to changing requirements or bug reports without requiring change in user-level code.By defining data members only in the private section of the class, the class author is free to make changes in the data. If the implementation changes, only the class code needs to be examined to see what affect the change may have. If data are public, then any function that directly accesses the data members of the old representation might be broken. It would be necessary to locate and rewrite all those portions of code that relied on the old pesentation before the program could be used again.Similarly, if the internal state of the class is private, then changes to the member data can happen in only a limited number of places. The data is protected from mistakes that users might introduce. If there is a bug that corrupts the object's state, the places to look for the bug are localized: When data are private, only a member function could be responsible for the error. The search for the mistake is limited, greatly easing the problems of maintenance and program correctness.If the data are private and if the interface to the member functions does not change, then user functions that manipulate class objects require no change.Because changing a class definition in a header file effectively changes the text of every source file that includes that header, code that uses a class must be recompiled when the class changes.Classes are the most fundamental feature in C++. Classes let us define new types that are tailored to our own applications, making our programs shorter and easier to modify.Data abstractionthe ability to define both data and function membersand encapsulationthe ability to protect class members from general accessare fundamental to classes. Member functions define the interface to the class. We encapsulate the class by making the data and functions used by the implementation of a class private.Classes may define constructors, which are special member functions that control how objects of the class are initialized. Constructors may be verloaded. Every constructor should initialize every data member. Constructors should use a constructor initializer list to initialize the data members. Initializer lists are lists of namevalue pairs where the name is a member and the value is an initial value for that member.Classes may grant access to their nonpublic members to other classes or functions. A class grants access by making the class or function a friend.Classes may also define mutable or static members. A mutable member is a data member that is never const; its value may be changed inside a const member function. Astatic member can be either function or data; static members exist independently of the objects of the class type.Copy ControlEach type, whether a built-in or class type, defines the meaning of a <possibly empty> set of operations on objects of that type. We can add two int values, run size on a vector, and so on. These operations define what can be done with objects of the given type.Each type also defines what happens when objects of the type are created. Initialization of objects of class type is defined by constructors. Types also control what happens when objects of the type are copied, assigned, or destroyed. Classes control these actions through special member functions: the copy constructor, the assignment operator, and the destructor. This chapter covers these operations.When we define a new type, we specifyexplicitly or implicitlywhat happens when objects of that type are copied, assigned, and destroyed. We do so by defining special members: the copy constructor, the assignment operator, and the destructor. If we do not explicitly define the copy constructor or the assignment operator, the compiler will <usually> define them for us.The copy constructor is a special constructor that has a single parameter that is a <usually const> reference to the class type. The copy constructor is used explicitly when we define a new object and initialize it from an object of the same type. It is used implicitly when we pass or return objects of that type to or from functions.Collectively, the copy constructor, assignment operator, and destructor are referred to as copy control. The compiler automatically implements these operations, but the class may define its own versions.Copy control is an essential part of defining any C++ class. Programmers new to C++ are often confused by having to define what happens when objects arecopied, assigned, or destroyed. This confusion is compounded because if we do not explicitly define these operations, the compiler defines them for usalthough they might not behave as we intend.Often the compiler-synthesized copy-control functions are finethey do exactly the work that needs to be done. But for some classes, relying on the default definitions leads to disaster. Frequently,the most difficult part of implementing the copy-control operations is recognizing when we need to override the default versions. One especially common case that requires the class to define its own the copy-control members is if the class has a pointer member.The Copy ConstructorThe constructor that takes a single parameter that is a <usually const> reference to an object of the class type itself is called the copy constructor. Like the default constructor, the copy constructor can be implicitly invoked by the compiler. The copy constructor is used to:1.Explicitly or implicitly initialize one object from another of the same type;2.Copy an object to pass it as an argument to a function;3.Copy an object to return it from a function;4.Initialize the elements in a sequential container;5.Initialize elements in an array from a list of element initializers.Forms of Object DefinitionRecall that C++ supports two forms of initialization <Section , p. 48>: direct and copy.Copy-initialization uses the = symbol, and direct-initialization places the initializer in parentheses.The copy and direct forms of initialization, when applied to objects of class type, are subtly different. Direct-initialization directly invokes the constructor matched by the arguments. Copy-initialization always involves the copy constructor. Copy-initialization first uses the indicated constructor to create a temporary object <Section , p. 247>. It then uses the copy constructor to copy that temporary into the one we are creating: string null_book = "9-999-99999-9"; // copy-initializationstring dots<10, '.'>; // direct-initializationstring empty_copy = string<>; // copy-initializationstring empty_direct; // direct-initializationFor objects of class type, copy-initialization can be used only when specifying a single argument or when we explicitly build a temporary object to copy.When dots is created, the string constructor that takes a count and a character is called and directly initializes the members in dots. To create null_book, the compiler first creates a temporary by invoking the string constructor that takes a C-style character string parameter. The compiler then uses the string copy constructor to initialize null_book as a copy of that temporary.The initialization of empty_copy and empty_direct both call the string default constructor. In the first case, the default constructor creates a temporary object, which is then used by the copy constructor to initialize empty_copy. In the second case, the default constructor is run directly on empty_direct.The copy form of initialization is primarily supported for compatibility with C usage. When it can do so, the compiler is permitted <but not obligated> to skip the copy constructor and create the object directly.Usually the difference between direct- or copy-initialization is at most a matter of low-level optimization. However, for types that do not support copying, or when using a constructor that is nonexplicit <Section , p. 462> the distinction can be essential: ifstream file1<"filename">; // ok: direct initializationifstream file2 = "filename"; // error: copy constructor is private// This initialization is okay only if// the Sales_item<const string&> constructor is not explicitSales_item item = string<"9-999-99999-9">;The initialization of file1 is fine. The ifstream class defines a constructor that can be called with a C-style string. That constructor is used to initialize file1.The seemingly equivalent initialization of file2 uses copy-initialization. That definition is not okay. We cannot copy objects of the IO types <Section 8.1, p. 287>, so we cannot use copy-initialization on objects of these types.Whether the initialization of item is okay depends on which version of our Sales_item class we are using. Some versions define the constructor that takes a string as explicit. If the constructor is explicit, then the initialization fails. If the constructor is not explicit, then the initialization is fine.If a class does not define one or more of these operations, the compiler will define them automatically. The synthesized operations perform memberwise initialization, assignment, or destruction: Taking each member in turn, the synthesized operation does whatever is appropriate to the member's type to copy, assign, or destroy that member. If the member is a class type, the synthesized operation calls the corresponding operation for that class <e.g., the copy constructor calls the member's copy constructor, the destructor calls its destructor, etc.>. If the member is a built-in type or a pointer, the member is copied or assigned directly; the destructor does nothing to destroy members of built-in or pointer type. If the member is an array, the elements in the array are copied, assigned, or destroyed in a manner appropriate to the element type.中文译文类的简介解决书店问题之前,还需要弄明白如何编写数据结构来表示交易数据.C++ 中我们通过定义类来定义自己的数据结构.类机制是 C++ 中最重要的特征之一.事实上,C++ 设计的主要焦点就是使所定义的类类型的行为可以像内置类型一样自然.我们前面已看到的像 istream 和 ostream 这样的库类型,都是定义为类的,也就是说,它们严格说来不是语言的一部分.完全理解类机制需要掌握很多内容.所幸我们可以使用他人写的类而无需掌握如何定义自己的类.在这一节,我们将描述一个用于解决书店问题的简单类.当我们学习了更多关于类型、表达式、语句和函数的知识〔所有这些在类定义中都将用到〕后,将会在后面的章节实现这个类.使用类时我们需要回答三个问题:类的名字是什么?它在哪里定义?它支持什么操作?对于书店问题,我们假定类命名为Sales_item 且类定义在命名为Sales_item.h 的头文件中.Sales_item 类Sales_item 类的目的是存储 ISBN 并保存该书的销售册数、销售收入和平均售价.我们不关心如何存储或计算这些数据.使用类时我们不需要知道这个类是怎样实现的,相反,我们需要知道的是该类提供什么操作.正如我们所看到的,使用像 IO 一样的库工具,必须包含相关的头文件.类似地,对于自定义的类,必须使得编译器可以访问和类相关的定义.这几乎可以采用同样的方式.一般来说,我们将类定义放入一个文件中,要使用该类的任何程序都必须包含这个文件.依据惯例,类类型存储在一个文件中,其文件名如同程序的源文件名一样,由文件名和文件后缀两部分组成.通常文件名和定义在头文件中的类名是一样的.通常后缀是 .h,但也有一些程序员用 .H、.hpp 或 .hxx.编译器通常并不挑剔头文件名,但 IDE 有时会.假设我们的类定义在名为 Sale_item.h 的文件中.Sales_item 对象上的操作每个类定义一种类型,类型名与类名相同.因此,我们的 Sales_item 类定义了一种命名为 Sales_item 的类型.像使用内置类型一样,可以定义类类型的变量.当写下" Sales_item item",就表示 item 是类型 Sales_item 的一个对象.通常将"类型 Sales_item 的一个对象〞简称为"一个 Sales_item 对象〞,或者更简单地简称为"一个 Sales_item〞.除了可以定义 Sales_item 类型的变量,我们还可以执行 Sales_item 对象的以下操作:使用加法操作符,+,将两个 Sales_item 相加;使用输入操作符,<<,来读取一个 Sales_item 对象;使用输出操作符,>>,来输出一个 Sales_item 对象;使用赋值操作符,=,将一个 Sales_item 对象赋值给另一个 Sales_item 对象;调用 same_isbn 函数确定两个 Sales_item 是否指同一本书.在大多数 C++ 程序中,类都是至关重要的:我们能够使用类来定义为要解决的问题定制的数据类型,从而得到更加易于编写和理解的应用程序.设计良好的类类型可以像内置类型一样容易使用.类定义了数据成员和函数成员:数据成员用于存储与该类类型的对象相关联的状态,而函数成员则负责执行赋予数据意义的操作.通过类我们能够将实现和接口分离,用接口指定类所支持的操作,而实现的细节只需类的实现者了解或关心.这种分离可以减少使编程冗长乏味和容易出错的那些繁琐工作.类类型常被称为抽象数据类型〔abstract data types〕.抽象数据类型将数据〔即状态〕和作用于状态的操作视为一个单元.我们可以抽象地考虑类该做什么,而无须知道何去完成这些操作.抽象数据类型是面向对象编程和泛型编程的基础.数据抽象是一种依赖于接口和实现分离的编程〔和设计〕技术.类设计者必须关心类是如何实现的,但使用该类的程序员不必了解这些细节.相反,使用一个类型的程序员仅需了解类型的接口,他们可以抽象地考虑该类型做什么,而不必具体地考虑该类型如何工作.封装是一项低层次的元素组合起来的形成新的、高层次实体珠技术.函数是封装的一种形式:函数所执行的细节行为被封装在函数本身这个更大的实体中.被封装的元素隐藏了它们的实现细节——可以调用一个函数但不能访问它所执行的语句.同样地,类也是一个封装的实体:它代表若干成员的聚焦,大多数〔良好设计的〕类类型隐藏了实现该类型的成员.标准库类型 vector 同时具备数据抽象和封装的特性.在使用方面它是抽象的,只需考虑它的接口,即它能执行的操作.它又是封装的,因为我们既无法了解该类型如何表示的细节,也无法访问其任意的实现制品.另一方面,数组在概念上类似于vector,但既不是抽象的,也不是封装的.可以通过访问存放数组的内存来直接操纵数组.并非所有类型都必须是抽象的.标准库中的 pair 类就是一个实用的、设计良好的具体类而不是抽象类.具体类会暴露而非隐藏其实现细节.一些类,例如 pair,确实没有抽象接口.pair 类型只是将两个数据成员捆绑成单个对象.在这种情况下,隐藏数据成员没有必要也没有明显的好处.在像 pair 这样的类中隐藏数据成员只会造成类型使用的复杂化.尽管如此,这样的类型通常还是有成员函数.特别地,如果类具有内置类型或复合类型数据成员,那么定义构造函数来初始化这些成员就是一个好主意.类的使用都也可以初始化或赋值数据成员,但由类来做更不易出错.程序员经常会将运行应用程序的人看作"用户〞.应用程序为最终"使用〞它的用户而设计,并响应用户的反馈而完善.类也类似:类的设计者为类的"用户〞设计并实现类.在这种情况下,"用户〞是程序员,而不是应用程序的最终用户.成功的应用程序的创建者会很好地理解和实现用户的需求.同样地,良好设计的、实用的类,其设计也要贴近类用户的需求.另一方面,类的设计者与实现者之间的区别,也反映了应用程序的用户与设计和实现者之间的区分.用户只关心应用程序能否以合理的费用满足他们的需求.同样地,类的使用者只关心它的接口.好的类设计者会定义直观和易用的类接口,而使用者只关心类中影响他们使用的部分实现.如果类的实现速度太慢或给类的使用者加上负担,则必然引起使用者的关注.在良好设计的类中,只有类的设计者会关心实现.在简单的应用程序中,类的使用者和设计者也许是同一个人.即使在这种情况下,保持角色区分也是有益的.设计类的接口时,设计者应该考虑的是如何方便类的使用;使用类的时候,设计者就不应该考虑类如何工作.提到"用户〞时,应该由上下文清楚地标明所指的是哪类用户.如果提到"用户代码〞或 Sales_item 类的〞用户",指的就是使用类编写应用程序的程序员.如果提到书店应用程序的〞用户",那么指的是运行应用程序的书店管理人员.数据抽象和封装提供了两个重要优点:1.避免类内部出现无意的、可能破坏对象状态的用户级错误.2.随时间推移可以根据需求改变或缺陷〔bug〕报告来完美类实现,而无须改变用户级代码.仅在类的私有部分定义数据成员,类的设计者就可以自由地修改数据.如果实现改变了,那么只需检查类代码来了解此变化可能造成的影响.如果数据为仅有的,则任何直接访问原有数据成员的函数都可能遭到破坏.在程序可重新使用之前,有必要定位和重写依赖原有表示的那部分代码.同样地,如果类的内部状态是私有的,则数据成员的改变只可能在有限的地方发生.避免数据中出现用户可能引入的错误.如果有缺陷会破坏对象的状态,就在局部位置搜寻缺陷:如果数据是私有的,那么只有成员函数可能对该错误负责.对错误的搜寻是有限的,从而大大方便了程序的维护和修正.如果数据是私有的并且没有改变成员函数的接口,则操纵类对象的用户函数无须改变.改变头文件中的类定义可有效地改变包含该头文件的每个源文件的程序文本,所以,当类发生改变时,使用该类的代码必须重新编译.类是 C++ 中最基本的特征,允许定义新的类型以适应应用程序的需要,同时使程序更短且更易于修改.数据抽象是指定义数据和函数成员的能力,而封装是指从常规访问中保护类成员的能力,它们都是类的基础.成员函数定义类的接口.通过将类的实现所用到的数据和函数设置为 private 来封装类.类可以定义构造函数,它们是特殊的成员函数,控制如何初始化类的对象.可以重载构造函数.每个构造函数就初始化每个数据成员.初始化列表包含的是名—值对,其中的名是一个成员,而值则是该成员的初始值.类可以将对其非 public 成员的访问权授予其他类或函数,并通过将其他的类或函数设为友元来授予其访问权.类也可以定义 mutable 或 static 成员.mutable 成员永远都不能为 const;它的值可以在 const 成员函数中修改.static 成员可以是函数或数据,独立于类类型的对象而存在.拷贝控制每种类型,无论是内置类型还是类类型,都对该类型对象的一组〔可能为空的〕操作的含义进行了定义.比如,我们可以将两个 int 值相加,运行 vector 对象的size 操作,等等.这些操作定义了用给定类型的对象可以完成什么任务.每种类型还定义了创建该类型的对象时会发生什么——构造函数定义了该类类型对象的初始化.类型还能控制复制、赋值或撤销该类型的对象时会发生什么——类通过特殊的成员函数:复制构造函数、赋值操作符和析构函数来控制这些行为.本章将介绍这些操作.当定义一个新类型的时候,需要显式或隐式地指定复制、赋值和撤销该类型的对象时会发生什么——这是通过定义特殊成员:复制构造函数、赋值操作符和析构函数来达到的.如果没有显式定义复制构造函数或赋值操作符,编译器〔通常〕会为我们定义.拷贝构造函数是一种特殊构造函数,具有单个形参,该形参〔常用 const 修饰〕是对该类类型的引用.当定义一个新对象并用一个同类型的对象对它进行初始化时,将显式使用复制构造函数.当将该类型的对象传递给函数或函数返回该类型的对象时,将隐式使用复制构造函数.复制构造函数、赋值操作符和析构函数总称为复制控制.编译器自动实现这些操作,但类也可以定义自己的版本.复制控制是定义任意 C++ 类必不可少的部分.初学 C++ 的程序员常对必须定义在复制、赋值或撤销对象时发生什么感到困惑.因为如果我们没有显式定义这些操作,编译器将为我们定义它们〔尽管它们也许不像我们期望的那样工作〕,这往往使初学者更加困惑.通常,编译器合成的复制控制函数是非常精练的——它们只做必需的工作.但对某些类而言,依赖于默认定义会导致灾难.实现复制控制操作最困难的部分,往往在于识别何时需要覆盖默认版本.有一种特别常见的情况需要类定义自己的复制控制成员的:类具有指针成员.拷贝构造函数只有单个形参,而且该形参是对本类类型对象的引用〔常用 const 修饰〕,这样的构造函数称为复制构造函数.与默认构造函数一样,复制构造函数可由编译器隐式调用.复制构造函数可用于:1.根据另一个同类型的对象显式或隐式初始化一个对象.2.复制一个对象,将它作为实参传给一个函数.3.从函数返回时复制一个对象.4.初始化顺序容器中的元素.5.根据元素初始化式列表初始化数组元素.对象的定义形式回忆一下,C++ 支持两种初始化形式〔第节〕:直接初始化和复制初始化.复制初始化使用 = 符号,而直接初始化将初始化式放在圆括号中.当用于类类型对象时,初始化的复制形式和直接形式有所不同:直接初始化直接调用与实参匹配的构造函数,复制初始化总是调用复制构造函数.复制初始化首先使用指定构造函数创建一个临时对象〔第节〕,然后用复制构造函数将那个临时对象复制到正在创建的对象:string null_book = "9-999-99999-9"; // copy-initializationstring dots<10, '.'>; // direct-initialization string empty_copy = string<>; // copy-initializationstring empty_direct; // direct-initialization 对于类类型对象,只有指定单个实参或显式创建一个临时对象用于复制时,才使用复制初始化. 创建 dots 时,调用参数为一个数量和一个字符的 string 构造函数并直接初始化 dots 的成员.创建 null_book 时,编译器首先调用接受一个 C 风格字符串形参的 string 构造函数,创建一个临时对象,然后,编译器使用 string 复制构造函数将 null_book 初始化为那个临时对象的副本.empty_copy 和 empty_direct 的初始化都调用默认构造函数.对前者初始化时,默认构造函数函数创建一个临时对象,然后复制构造函数用该对象初始化empty_copy.对后者初始化时,直接运行 empty_direct 的默认构造函数.。
英文文献翻译成中文

英文文献翻译成中文per a la garantia, plans de beneficis per poder posar empresa de totes les activitats empresarials de producció són orgànics al'organització cap amunt. Quart anual pla integral és el mitjà- i pla de desenvolupament a llarg termini d'encarnació i garantia principal, però també és la base per a la preparació de trimestral i l'objectiu de les decisions de gestió empresarials. Cinquè anual integrat de planificació i implementació per procedir de la realitat, reforçar la recerca ianàlisi exhaustiva, àmpliament mobilitzar les masses, segons l'esperit avançada, positiu, fiable, realista, conservador, adonar-se del potencial de producció existent, producció més productes comercialitzables, assequibles, les necessitats de l'estat i el mercat. Sisena anual pla integral... Vuit, pla de reparació d'equips: inclou dos DPS arribant: elaborat per l'equip és responsable. Nou, un plad'infraestructures: preparat per la construcció és responsable. Deu, laboral, pla de salari: elaborat pel Departament d'educació de les persones. Planificació financera, tercer: elabora el Departament de Finances és responsable. 12, subministrament de materials, pla de consum de eina: elabora el Departament de subministrament, l'eina és responsable. 13, personal, formació, planificaciód'introducció de talent: elaborat pel Departament d'educació de les persones. Vuitè pla els tipus d'indicadors i el Departament: els principals indicadorstècnics i econòmics pel Director a càrrec, sota el Director a càrrec,oficina funcional centralitzat preparació, planificació i programació total consolidat. 1, rendiment producte mitjançant la programació de servei és responsable de la preparació d'un pla. 2, elaborat perl'empresa Màrqueting responsable. 3, qualitat total divisió és responsable de la p reparació. ?, taxa de pas de examen de varietat. B, les parts principals de la taxa de mostreig principal. ?, mecanitzat de ferralla. 4, preparat pel Departament de Finances és responsable del cost. ?, productes comparables Costa declivi. ?, producció cost de les taxes. 5, consumits per l'oferta Departament és responsable de preparar. ? milions de iuans sortida valor i b eficiència, consumenergètic i acer. 6, productivitat que elabori el Departament de seguretat laboral és responsable. 7, el fons preparat pel Departament de Finances és responsable. ?, el nombre de capital fix ocupat. ?, capitals dies hàbils. ?, cent Yuan sortida valor pren cap amunt de liquiditat. 8, elaborat pel Departament de Finances s'encarrega de beneficis. Els beneficis ? es va conver tir en benefici del valor de producció c b d benefici marges tots els marges ?, vendes marge de benefici 9, valor total de la producció industrial del Departament de planificació és responsable de la preparació dels plans novena i objectius del programa: e n primer lloc, la fase de preparació: 1 reunió, Director, preparació de mobilització de disposició plans i objectius per a l'any i va proposarl'elaboració de研究的INTERACT德业? (2007 ) 1:143-154作者10.1007/s12008-007-0016-2模拟的数值控制工具机( NCMT )基于虚拟现实使我们以前的可视化上生产的部分执行不同的进程。
5000字英文论文

5000字英文论文篇一:论文用5000字中英文翻译MCU DescriptionSCM is also known as micro-controller (Microcontroller Unit), commonly used letters of the acronym MCU that it was first used in industrial control. Only a single chip by the CPU chip developed from a dedicated processor. The first design is by a large number of peripherals and CPU on a chip in the computer system, smaller, more easily integrated into a complex and demanding on the volume control device which. INTEL s Z80 is the first designed in accordance with this idea processor, then on the development of microcontroller and dedicated processors have parted ways.Are 8-bit microcontroller early or 4 bits. One of the most successful is the INTEL 8031, for a simple, reliable and good performance was a lot of praise. Then developed in 8031 out of MCS51 MCU Systems. SCM systems based on this system until now are still widely used. With the increased requirements of industrial control field, began a 16-bit microcontroller, because the cost is not satisfactory but have not been very widely used. After 90 years with the great development of consumer electronics, microcontroller technology has been a huge increase. With INTEL i960 series, especially the later series of widely used ARM, 32-bit microcontroller quickly replace high-end 16-bit MCU status and enter the mainstream market. The traditional 8-bit microcontroller performances have been the rapid increase capacity increase compared to 80 the number of times. Currently, high-end 32-bit microcontroller clocked over 300MHz, the performance catching the mid-90 s dedicated processor, while the average model prices fall to one U.S. dollars; the most high-end model only 10 dollars. Modern SCM systems are no longer only in the developmentand use of bare metal environment, a large number of proprietary embedded operating system is widely used in the full range of SCM. The handheld computers and cell phones as the core processing of high-end microcontroller can even use a dedicated Windows and Linux operating systems.SCM is more suitable than the specific processor used in embedded systems, so it was up to the application. In fact the number of SCM is the world s largest computer. Modern human life used in almost every piece of electronic and mechanical products will be integrated single chip. Phone, telephone, calculator, home appliances,electronic toys, handheld computers and computer accessories such as a mouse with a 1-2 in both the Department of SCM. Personal computer will have a large number of SCM in the work. General car with more than 40 SCM, complex industrial control systems may even have hundreds of SCM in the same time work! SCM is not only far exceeds the number of PC and other computing the sum, or even more than the number of human beingsSingle chip, also known as single-chip microcontroller, it is not complete a certain logic chips, but to a computer system integrated into a chip. Equivalent to a micro-computer, and computer than just the lack of a microcontroller I / O devices. General talk: a chip becomes a computer. Its small size, light weight, cheap, for the study, application and development of facilities provided. At the same time, learning to use the MCU is to understand the principle and structure of the computer the best choice. SCM and the computer functions internally with similar modules, such as CPU, memory, parallel bus, the same effect as well, and hard disk memory devices, and different is its performance of these components were relatively weak many of our home computer, but the price is low , usually not more than 10 yuan you can do with it ...... some control for a class is not very complicated electrical work is enough of. We are usingautomatic drum washing machine, smoke hood, VCD and so on appliances which could see its shadow! ...... It is primarily as a control section of the core componentsIt is an online real-time control computer, control-line is that the scene is needed is a stronger anti-jamming ability, low cost, and this is, and off-line computer (such as home PC), the main difference.Single chipMCU is through running, and can be modified. Through different procedures to achieve different functions, in particular special unique features, this is another device much effort needs to be done, some great efforts are very difficult to do. A not very complex functions if the 50 s with the United States developed 74 series, or the 60 s CD4000 series of these pure hardware buttoned, then the circuit must be a large PCB board! But if the United States if the 70 s with a series of successful SCM market, theresult will be a drastic change! Just because you are prepared by microcomputer programs can achieve high intelligence, high efficiency and high reliability!As the microcontroller on the cost-sensitive, so now the dominant software or the lowest level assembly language, which is the lowest level in addition to more than binary machine code language, and as so low why is the use? Many high-level language has reached the level of visual programming Why is not it? The reason is simply that there is no home computer as a single chip CPU, not as hard as a mass storage device. A visualization of small high-level language program which even if only one button, will reach tens of K of size! For the home PC s hard drive in terms of nothing, but in terms of the MCU is not acceptable. SCM in the utilization of hardware resources to be very high for the job so although the original is still in the compilation of a lot of use. The same token,if the giant computer operating system and applications run up to get home PC, home PC, also can not afford to.Can be said that the twentieth century across the three power era, that is, the age of electricity, the electronic age and has entered into the computer age. However, this computer, usually refers to the personal computer, referred to as PC. It consists of the host, keyboard, monitor and other components. Another type of computer, most people do not know how. This computer is to give all kinds of intelligent machines single chip (also known as micro-controller). As the name suggests, this computer system took only a minimal integrated circuit, can be a simple operation and control. Because it is small, usually hidden in the charged mechanical stomach in. It is in the device, like the human brain plays a role, it goes wrong, the whole plant was paralyzed. Now, this microcontroller has a very broad field of use, such as smart meters, real-time industrial control, communications equipment, navigation systems, and household appliances. Once all kinds of products were using SCM, can serve to upgrade the effectiveness of products, often in the product name preceded by the adjective - intelligent, such as intelligent washing machines. Now some technical personnel of factories or other amateur electronics developers to engage in out of certain products, not the circuit is too complicated, that function is too simple and can easily be copied. The reason may be stuck in the product did not use a microcontrolleror other programmable logic device.SCM historySCM was born in the late 20th century, 70, experienced SCM, MCU, SoC three stages.First model1.SCM the single chip microcomputer (Single Chip Microcomputer) stage, mainly seeking the best of the best single form of embedded systemsarchitecture. Innovation model success, laying the SCM and general computer completely different path of development. In the open road of independent development of embedded systems, Intel Corporation contributed.2.MCU the micro-controller (Micro Controller Unit) stage, the main direction of technology development: expanding to meet the embedded applications, the target system requirements for the various peripheral circuits and interface circuits, highlight the object of intelligent control. It involves the areas associated with the object system, therefore, the development of MCU s responsibility inevitably falls on electrical, electronics manufacturers. From this point of view, Intel faded MCU development has its objective factors. In the development of MCU, the most famous manufacturers as the number of Philips Corporation. Philips company in embedded applications, its great advantage, the MCS-51 single-chip micro-computer from the rapid development of the micro-controller. Therefore, when we look back at the path of development of embedded systems, do not forget Intel and Philips in History.Embedded SystemsEmbedded system microcontroller is an independent development path, the MCU important factor in the development stage, is seeking applications to maximize the solution on the chip; Therefore, the development of dedicated single chip SoC trend of the natural form. As the microelectronics, IC design, EDA tools development, application system based on MCU SOC design have greater development. Therefore, the understanding of the microcontroller chip microcomputer can be, extended to the single-chip micro-controller applications.MCU applicationsSCM now permeate all areas of our lives, which is almost difficult to find traces of the field without SCM. Missile navigation equipment,aircraft, all types of instrument control, computer network communications and data transmission, industrial automation, real-time process control and data processing, extensive use of various smart IC card, civilian luxury car security system, video recorder, camera, fully automatic washing machine control, and program-controlled toys, electronic pet, etc., which are inseparable from the microcontroller. Not to mention the area of robot control, intelligent instruments, medical equipment was. Therefore, the MCU learning, development and application of the large number of computer applications and intelligent control of the scientists, engineers.SCM is widely used in instruments and meters, household appliances, medical equipment, aerospace, specialized equipment, intelligent management and process control fields, roughly divided into the following several areas:1. In the application of Intelligent InstrumentsSCM has a small size, low power consumption, controlling function, expansion flexibility, the advantages of miniaturization and ease of use, widely used instrument, combining different types of sensors can be realized Zhuru voltage, power, frequency, humidity, temperature, flow, speed, thickness, angle, length, hardness, elemental, physical pressure measurement. SCM makes use of digital instruments, intelligence, miniaturization, and functionality than electronic or digital circuits more powerful. Such as precision measuring equipment (power meter, oscilloscope, various analytical instrument).2. In the industrial control applicationWith the MCU can constitute a variety of control systems, data acquisition system. Such as factory assembly line of intelligent control 3. In Household AppliancesCan be said that the appliances are basically using SCM, praise from the electric rice, washing machines, refrigerators, air conditioners, color TV, and other audio video equipment, to the electronic weighing equipment, varied, and omnipresent.篇二:毕业论文5000字英文文献翻译(c++)┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书英文翻译英语原文:. Introducing ClassesThe only remaining feature we need to understand before solving our bookstore problem is how to write a data structure to represent our transaction data. In C++ we define our own data structure by defining a class. The class mechanism is one of the most important features in C++. In fact, a primary focus of the design of C++ is to make it possible to define class types that behave as naturally as the built-in types themselves. The library types that we ve seen already, such as istream and ostream, are all defined as classesthat is,they are not strictly speaking part of the language.Complete understanding of the class mechanism requires mastering a lot of information. Fortunately, it is possible to use a class that someone else has written without knowing how to define a class ourselves. In this section, we ll describe a simple class that we canuse in solving our bookstore problem. We ll implement this class in the subsequent chapters as we learn more about types,expressions, statements, and functionsall of which are used in defining classes.To use a class we need to know three things:What is its name? Where is it defined?What operations does it support?For our bookstore problem, we ll assume that the class is named Sales_item and that it is defined in a header named Sales_item.h.The Sales_item ClassThe purpose of the Sales_item class is to store an ISBN and keep track of the number of copies sold, the revenue, and average sales price for that book. How these data are stored or computed is not our concern. To use a class, we need not know anything about how it is implemented. Instead, what we need to know is what operations the class provides.As we ve seen, when we use library facilities such as IO, we must include the associated headers. Similarly, for our own classes, we must make the definitions associated with the class available to the compiler. We do so in much the same way. Typically, we put the class definition into a file. Any program that wants to use our class must include that file. Conventionally, class types are stored in a file with a name that, like the name of a program source file, has two parts: a file name and a file suffix. Usually the file name is the same as the class defined in the header. The suffix usually is .h, but some programmers use .H, .hpp, or .hxx. Compilers usually aren t picky about header file names, but IDEs ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书sometimes are. We ll assume that our class is defined in a file named Sales_item.h.Operations on Sales_item ObjectsEvery class defines a type. The type name is the same as the name of the class. Hence, our Sales_item class defines a type namedSales_item. As with the built-in types, we can define a variable of a class type. When we write Sales_item item we are saying that item is an object of type Sales_item. We often contract the phrase an object of type Sales_item to aSales_ item object or even more simply to a Sales_item. In addition to being able to define variables of type Sales_item, we can perform the following operations on Sales_item objects:Use the addition operator, +, to add two Sales_items,Use the input operator, to read a Sales_item object,Use the output operator, to write a Sales_item object,Use the assignment operator, =, to assign one Sales_item object to another,Call the same_isbn function to determine if two Sales_items refer to the same book.Classes are central to most C++ programs: Classes let us define our own types that are customizedfor the problems we need to solve, resulting in applications that are easier to write andunderstand.Well-designed class types can be as easy to use as the built-in types.A class defines data and function members: The data members store the state associated with objectsof the class type, and the functions perform operations that give meaning to the data. Classeslet us separate implementation and interface. The interface specifies the operations that the classsupports. Only the implementor of the class need know or care about the details of the implementation. This separation reduces the bookkeeping aspects that make programming tedious anderror-prone.Class types often are referred to as abstract data types. An abstract data type treats the data(state) and operations on that state as a single unit. We can think abstractly about what the classd oes, rather than always having to be aware of how the class operates. Abstract data types arefundamental to both object-oriented and generic programming.Data abstraction is a programming (and design) technique that relies on the separation of interfaceand implementation. The class designer must worry about how a class is implemented, but programmersthat use the class need not know about these details. Instead, programmers who use a type need to know only the type s interface; they can think abstractly about what the type does rather than concretely about how the type works. Encapsulation is a term that describes the technique of combining lower-level elements to forma new, higher-level entity. A function is one form of encapsulation: The detailed actions performedby the function are encapsulated in the larger entity that is the function itself. Encapsulated elements hide the details of their implementationwe may call ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书a function but have no access to the statements that it executes. In the same way, a class is an encapsulated entity: It represents an aggregation of several members, and most (well-designed) class types hide the members that implement the type.If we think about the library vector type, it is an example of both data abstraction and encapsulation. It is abstract in that to use it, we think about its interfaceabout the operations that it can perform. It is encapsulated because we have no access to the details of how the type is representated nor to any of its implementation artifacts. An array, on the other hand, is similar in concept to a vector but is neither abstract nor encapsulated. We manipulate an array directly by accessing the memory in which the array is stored.Not all types need to be abstract. The library pair class is a good example of a useful, well-designed class that is concrete rather thanabstract. A concrete class is a class that exposes, rather than hides, its implementation.Some classes, such as pair, really have no abstract interface. The pair type exists to bundle two data members into a single object. There is no need or advantage to hiding the data members. Hiding the members in a class like pair would only complicate the use of the type.Even so, such types often have member functions. In particular, it is a good idea for any class that has data members of built-in or compound type to define constructor(s) to initialize those members. The user of the class could initialize or assign to the data members but it is less error-prone for the class to do so.Programmers tend to think about the people who will run their applications as users. Applicationsare designed for and evolve in response to feedback from those who ultimately use the applications. Classes are thought of in a similar way: A class designer designs and implements a class for users of that class. In this case, the user is a programmer, not the ultimate user of the application.Authors of successful applications do a good job of understanding and implementing the needs ofthe application s users. Similarly,well-designed, useful classes are designed with a close attention to the needs of the users of the class.In another way, the division between class designer and class user reflects the division betweenusers of an application and the designers and implementors of the application. Users care only if the application meets their needs in a cost-effective way. Similarly, users of a class care only about its interface. Good class designers define a class interface that is intuitive and easy to use. Users care about the implementation only in so far as the implementation affects their use of the class. If the implementation is too slow or puts burdens on users ofthe class, then the users must care. In well-designed classes, only the class designer worries about the implementation.In simple applications, the user of a class and the designer of the class might be one┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书and the same person. Even in such cases, it is useful to keep the roles distinct. When designing the interface to a class, the class designer should think about how easy it will be to use the class. When using the class, the designer shouldn t think about how the class works.When referring to a user, the context makes it clear which kind of user is meant. If we speak of user code or the user of the Sales_item class, we mean a programmer who is using a class in writing an application. If we speak of the user of the bookstore application, we mean the manager of the store who is running the application.Data abstraction and encapsulation provide two important advantages: 1.Class internals are protected from inadvertent user-level errors, which might corrupt the state of the object.2.The class implementation may evolve over time in response to changing requirements or bug reports without requiring change inuser-level code.By defining data members only in the private section of the class, the class author is free to make changes in the data. If the implementation changes, only the class code needs to be examined to see what affect the change may have. If data are public, then any function that directly accesses the data members of the old representation might be broken. Itwould be necessary to locate and rewrite all those portions of code that relied on the old pesentation before the program could be used again. Similarly, if the internal state of the class is private, then changes to the member data can happen in only a limited number of places. The data is protected from mistakes that users might introduce. If there is a bug that corrupts the object s state, the places to look for the bug are localized: When data are private, only a member function could be responsible for the error. The search for the mistake is limited, greatly easing the problems of maintenance and program correctness.If the data are private and if the interface to the member functions does not change, then user functions that manipulate class objects require no change.Because changing a class definition in a header file effectively changes the text of every source file that includes that header, code that uses a class must be recompiled when the class changes.Classes are the most fundamental feature in C++. Classes let us define new types that are tailored to our own applications, making our programs shorter and easier to modify.Data abstractionthe ability to define both data and function membersand encapsulationthe ability to protect class members from general accessare fundamental to classes. Member functions define the interface to the class. We encapsulate the class by making the data and functions used by the implementation of a class private.Classes may define constructors, which are special member functions that control how┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ 装┊ ┊ ┊ ┊ ┊ 订┊ ┊ ┊ ┊ ┊ 线┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊ ┊安徽工业大学毕业设计(论文)说明书objects of the class are initialized. Constructors may be verloaded. Every constructor should initialize every data member. Constructors should use a constructor initializer list to initialize the data members. Initializer lists are lists of namevalue pairs where the name is a member and the value is an initial value for that member.Classes may grant access to their nonpublic members to other classes or functions. A class grants access by making the class or function a friend.Classes may also define mutable or static members. A mutable member is a data member that is never const; its value may be changed inside a const member function. A static member can be either function or data; static members exist independently of the objects of the class type. Copy ControlEach type, whether a built-in or class type, defines the meaning of a (possibly empty) set of operations on objects of that type. We can add two int values, run size on a vector, and so on. These operations define what can be done with objects of the given type.Each type also defines what happens when objects of the type are created. Initialization of objects of class type is defined by constructors. Types also control what happens when objects of the type are copied, assigned, or destroyed. Classes control these actions through special member functions: the copy constructor, the assignment operator, and the destructor. This chapter covers these operations.When we define a new type, we specifyexplicitly or implicitlywhat happens when objects of that type are copied, assigned, and destroyed. We do so by defining special members: the copy constructor, the assignment operator, and the destructor. If we do not explicitly define the copy constructor or the assignment operator, the compiler will (usually) define them for us.The copy constructor is a special constructor that has a single parameter that is a (usually const) reference to the class type. The copy constructor is used explicitly when we define a new object and initialize it from an object of the same type. It is used implicitly when we pass or return objects of that type to or from functions.Collectively, the copy constructor, assignment operator, and destructor are referred to as copy control. The compiler automatically implements these operations, but the class may define its own versions. Copy control is an essential part of defining any C++ class. Programmers new to C++ are often confused by having to define what happens when objects arecopied, assigned, or destroyed. This confusion is compounded because if we do not explicitly define these operations, the compiler defines them for usalthough they might not behave as we intend.Often the compiler-synthesized copy-control functions are finethey do exactly the篇三:毕业设计的5000字英文文献翻译外文及翻译英语原文 Android Application FundamentalsAndroid applications are written in the Java programming language. The Android SDK tools compile the code—along with any data and resource files—into an Android package, an archive file with an .apk suffix. All the code in a single .apk file is considered to be one application and is the file that Android-powered devices use to install the application. Once installed on a device, each Android application lives in its own security sandbox: ? The Android operating system is a multi-user Linux system in which eachapplication is a different user.? By default, the system assigns each application a unique Linux user ID (the ID is used only by the system and is unknown to the application). The system setspermissions for all the files in an application so that only the user ID assigned to that application can access them.? Each process has its own virtual machine (VM), so an application s code runs in isolation from other applications.? By default, every application runs in its own Linux process. Android starts the process when any of the application s components need to be executed, then shuts down the process when it s no longer needed or when the system must recovermemory for other applications.In this way, the Android system implements the principle of least privilege. That is, each application, by default, has access only to the components that it requires to do its work and no more. This creates a very secure environment in which an application cannot access parts of the system for which it is not given permission.However, there are ways for an application to share data with other applications and for an application to access system services:? It s possible to arrange for two applications to share the same Linux user ID, in whichcase they are able to access each other s files. To conserve system resources,applications with the same user ID can also arrange to run in the same Linux processand share the same VM (the applications must also be signed with the samecertificate).。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
沈阳建筑大学毕业论文外文及翻译原文题目Android Application Fundamentals 学院专业班级信息与控制工程学院计算机08-1 学生姓名XXX 性别X指导教师XXX 职称XX年月日外文及翻译英语原文Android Application FundamentalsAndroid applications are written in the Java programming language. The Android SDK tools compile the code—along with any data and resource files—into an Android package, an archive file with an .apk suffix. All the code in a single .apk file is considered to be one application and is the file that Android-powered devices use to install the application.Once installed on a device, each Android application lives in its own security sandbox:●The Android operating system is a multi-user Linux system in which each applicationis a different user.●By default, the system assigns each application a unique Linux user ID (the ID isused only by the system and is unknown to the application). The system setspermissions for all the files in an application so that only the user ID assigned to thatapplication can access them.●Each process has its own virtual machine (VM), so an application's code runs inisolation from other applications.●By default, every application runs in its own Linux process. Android starts theprocess when any of the application's components need to be executed, then shutsdown the process when it's no longer needed or when the system must recovermemory for other applications.In this way, the Android system implements the principle of least privilege. That is, each application, by default, has access only to the components that it requires to do its work and no more. This creates a very secure environment in which an application cannot access parts of the system for which it is not given permission.However, there are ways for an application to share data with other applications and for an application to access system services:●It's possible to arrange for two applications to share the same Linux user ID, in whichcase they are able to access each other's files. To conserve system resources,applications with the same user ID can also arrange to run in the same Linux processand share the same VM (the applications must also be signed with the samecertificate).●An application can request permission to access device data such as the user'scontacts, SMS messages, the mountable storage (SD card), camera, Bluetooth, andmore. All application permissions must be granted by the user at install time.That covers the basics regarding how an Android application exists within the system. The rest of this document introduces you to:●The core framework components that define your application.●The manifest file in which you declare components and required device features foryour application.●Resources that are separate from the application code and allow your application togracefully optimize its behavior for a variety of device configurations.Application ComponentsApplication components are the essential building blocks of an Android application. Each component is a different point through which the system can enter your application. Not all components are actual entry points for the user and some depend on each other, but each one exists as its own entity and plays a specific role—each one is a unique building block that helps define your application's overall behavior.There are four different types of application components. Each type serves a distinct purpose and has a distinct lifecycle that defines how the component is created and destroyed.Here are the four types of application components:ActivitiesAn activity represents a single screen with a user interface. For example, an email application might have one activity that shows a list of new emails, another activity tocompose an email, and another activity for reading emails. Although the activities work together to form a cohesive user experience in the email application, each one is independent of the others. As such, a different application can start any one of these activities (if the email application allows it). For example, a camera application can start the activity in the email application that composes new mail, in order for the user to share a picture.An activity is implemented as a subclass of Activity and you can learn more about it in the Activities developer guide.ServicesA service is a component that runs in the background to perform long-runningoperations or to perform work for remote processes. A service does not provide a user interface. For example, a service might play music in the background while the user is in a different application, or it might fetch data over the network without blocking user interaction with an activity. Another component, such as an activity, can start the service and let it run or bind to it in order to interact with it.A service is implemented as a subclass of Service and you can learn more about it inthe Services developer guide.Content providersA content provider manages a shared set of application data. You can store the data inthe file system, an SQLite database, on the web, or any other persistent storage location your application can access. Through the content provider, other applications can query or even modify the data (if the content provider allows it). For example, the Android system provides a content provider that manages the user's contact information. As such, any application with the proper permissions can query part of the content provider (such as ContactsContract.Data) to read and write information abouta particular person.Content providers are also useful for reading and writing data that is private to your application and not shared. For example, the Note Pad sample application uses a content provider to save notes.A content provider is implemented as a subclass of ContentProvider and mustimplement a standard set of APIs that enable other applications to perform transactions.For more information, see the Content Providers developer guide.Broadcast receiversA broadcast receiver is a component that responds to system-wide broadcastannouncements. Many broadcasts originate from the system—for example, a broadcast announcing that the screen has turned off, the battery is low, or a picture was captured.Applications can also initiate broadcasts—for example, to let other applications know that some data has been downloaded to the device and is available for them to use.Although broadcast receivers don't display a user interface, they may create a status bar notification to alert the user when a broadcast event occurs. More commonly, though, a broadcast receiver is just a "gateway" to other components and is intended to do a very minimal amount of work. For instance, it might initiate a service to perform some work based on the event.A broadcast receiver is implemented as a subclass of BroadcastReceiver and eachbroadcast is delivered as an Intent object. For more information, see the BroadcastReceiver class.A unique aspect of the Android system design is that any application can start another application’s component. For example, if you want the user to capture a photo with the device camera, there's probably another application that does that and your application can use it, instead of developing an activity to capture a photo yourself. You don't need to incorporate or even link to the code from the camera application. Instead, you can simply start the activity in the camera application that captures a photo. When complete, the photo is even returned to your application so you can use it. To the user, it seems as if the camera is actually a part of your application.When the system starts a component, it starts the process for that application (if it's not already running) and instantiates the classes needed for the component. For example, if your application starts the activity in the camera application that captures a photo, that activity runs in the process that belongs to the camera application, not in your application's process.Therefore, unlike applications on most other systems, Android applications don't have a single entry point (there's no main()function, for example).Because the system runs each application in a separate process with file permissions that restrict access to other applications, your application cannot directly activate a component from another application. The Android system, however, can. So, to activate a component in another application, you must deliver a message to the system that specifies your intent to start a particular component. The system then activates the component for you.Activating ComponentsThree of the four component types—activities, services, and broadcast receivers—are activated by an asynchronous message called an intent. Intents bind individual components to each other at runtime (you can think of them as the messengers that request an action from other components), whether the component belongs to your application or another.An intent is created with an Intent object, which defines a message to activate either a specific component or a specific type of component—an intent can be either explicit or implicit, respectively.For activities and services, an intent defines the action to perform (for example, to "view" or "send" something) and may specify the URI of the data to act on (among other things that the component being started might need to know). For example, an intent might convey a request for an activity to show an image or to open a web page. In some cases, you can start an activity to receive a result, in which case, the activity also returns the result in an Intent (for example, you can issue an intent to let the user pick a personal contact and have it returned to you—the return intent includes a URI pointing to the chosen contact).For broadcast receivers, the intent simply defines the announcement being broadcast (for example, a broadcast to indicate the device battery is low includes only a known action string that indicates "battery is low").The other component type, content provider, is not activated by intents. Rather, it is activated when targeted by a request from a ContentResolver. T he content resolver handles all direct transactions with the content provider so that the component that's performingtransactions with the provider doesn't need to and instead calls methods onthe ContentResolver object. This leaves a layer of abstraction between the content provider and the component requesting information (for security).There are separate methods for activating each type of component:•You can start an activity (or give it something new to do) by passingan Intent to startActivity() or startActivityForResult() (when you want the activity to return a result).•You can start a service (or give new instructions to an ongoing service) by passing an Intent to startService(). Or you can bind to the service by passingan Intent to bindService().•You can initiate a broadcast by passing an Intent to methodslike sendBroadcast(), sendOrderedBroadcast(), or sendStickyBroadcast().•You can perform a query to a content provider by calling query() ona ContentResolver.For more information about using intents, see the Intents and Intent Filters document. More information about activating specific components is also provided in the following documents: Activities, Services, BroadcastReceiver and Content Providers.Declaring componentsThe primary task of the manifest is to inform the system about the application's components. For example, a manifest file can declare an activity as follows:In the <application> element, the android:icon attribute points to resources for an icon that identifies the application.In the <activity> element, the android:name at tribute specifies the fu lly qualified class name of the Activity subclass and the android:label attributes specifies a string to use as the user-visible label for the activity.You must declare all application components this way:●<activity>elements for activities●<service> elements for services●<receiver>elements for broadcast receivers●<provider>elements for content providersActivities, services, and content providers that you include in your source but do not declare in the manifest are not visible to the system and, consequently, can never run. However, broadcast receivers can be either declared in the manifest or created dynamically in code (as BroadcastReceiver objects) and registered with the system bycalling registerReceiver().Declaring component capabilitiesAs discussed above, in Activating Components, you can use an Intent to start activities, services, and broadcast receivers. You can do so by explicitly naming the target component (using the component class name) in the intent. However, the real power of intents lies in the concept of intent actions. With intent actions, you simply describe the type of action you want to perform (and optionally, the data upon which you’d like to per form the action) and allow the system to find a component on the device that can perform the action and start it. If there are multiple components that can perform the action described by the intent, then the user selects which one to use.The way the system identifies the components that can respond to an intent is by comparing the intent received to the intent filters provided in the manifest file of other applications on the device.When you declare a component in your application's manifest, you can optionally include intent filters that declare the capabilities of the component so it can respond to intents from other applications. You can declare an intent filter for your component by addingan <intent-filter>element as a child of the component's declaration element.For example, an email application with an activity for composing a new email might declare an intent filter in its manifest entry to respond to "send" intents (in order to send email). An activity in your application can then create an intent with the “send” action (ACTION_SEND), which the system m atches to the email application’s “send” activity and launches it when you invoke the intent with startActivity().For more about creating intent filters, see the Intents and Intent Filters document.Declaring application requirementsThere are a variety of devices powered by Android and not all of them provide the same features and capabilities. In order to prevent your application from being installed on devices that lack features needed by your application, it's important that you clearly define a profile for the types of devices your application supports by declaring device and software requirements in your manifest file. Most of these declarations are informational only and the system does not read them, but external services such as Google Play do read them in order to provide filtering for users when they search for applications from their device.For example, if your application requires a camera and uses APIs introduced in Android 2.1 (API Level 7), you should declare these as requirements in your manifest file. That way, devices that do not have a camera and have an Android version lower than 2.1 cannot install your application from Google Play.However, you can also declare that your application uses the camera, but doesnot require it. In that case, your application must perform a check at runtime to determine if the device has a camera and disable any features that use the camera if one is not available.Here are some of the important device characteristics that you should consider as you design and develop your application:Screen size and densityIn order to categorize devices by their screen type, Android defines two characteristics for each device: screen size (the physical dimensions of the screen) and screen density (the physical density of the pixels on the screen, or dpi—dots per inch). To simplify all the different types of screen configurations, the Android system generalizes them into select groups that make them easier to target.The screen sizes are: small, normal, large, and extra large.The screen densities are: low density, medium density, high density, and extra highdensity.By default, your application is compatible with all screen sizes and densities, because the Android system makes the appropriate adjustments to your UI layout and imageresources. However, you should create specialized layouts for certain screen sizes and provide specialized images for certain densities, using alternative layout resources, and by declaring in your manifest exactly which screen sizes your application supportswith the <supports-screens> element.For more information, see the Supporting Multiple Screens document.Input configurationsMany devices provide a different type of user input mechanism, such as a hardware keyboard, a trackball, or a five-way navigation pad. If your application requires a particular kind of input hardware, then you should declare it in your manifest with the <uses-configuration> e lement. However, it is rare that an application should require a certain input configuration.Device featuresThere are many hardware and software features that may or may not exist on a given Android-powered device, such as a camera, a light sensor, bluetooth, a certain version of OpenGL, or the fidelity of the touchscreen. You should never assume that a certain feature is available on all Android-powered devices (other than the availability of the standard Android library), so you should declare any features used by your application with the <uses-feature> element.Platform VersionDifferent Android-powered devices often run different versions of the Android platform, such as Android 1.6 or Android 2.3. Each successive version often includes additional APIs not available in the previous version. In order to indicate which set of APIs are available, each platform version specifies an API Level (for example, Android 1.0 is API Level 1 and Android 2.3 is API Level 9). If you use any APIs that were added to the platform after version 1.0, you should declare the minimum API Level in which those APIs were introduced using the <uses-sdk> element.It's important that you declare all such requirements for your application, because, when you distribute your application on Google Play, the store uses these declarations to filter which applications are available on each device. As such, your application should be available only to devices that meet all your application requirements.For more information about how Google Play filters applications based on these (and other) requirements, see the Filters on Google Play document.Application ResourcesAn Android application is composed of more than just code—it requires resources that are separate from the source code, such as images, audio files, and anything relating to the visual presentation of the application. For example, you should define animations, menus, styles, colors, and the layout of activity user interfaces with XML files. Using application resources makes it easy to update various characteristics of your application without modifying code and—by providing sets of alternative resources—enables you to optimize your application for a variety of device configurations (such as different languages and screen sizes).For every resource that you include in your Android project, the SDK build tools define a unique integer ID, which you can use to reference the resource from your application code or from other resources defined in XML. For example, if your application c ontains an image file named logo.png (saved in the res/drawable/ directory), the SDK tools generate a resource ID named R.drawable.logo, which you can use to reference the image and insert it in your user interface.One of the most important aspects of providing resources separate from your source code is the ability for you to provide alternative resources for different device configurations. For example, by defining UI strings in XML, you can translate the strings into other languages and save those strings in separate files. Then, based on a language qualifier that you append to the resource directory's name (such as res/values-fr/for French string values) and the user's language setting, the Android system applies the appropriate language strings to your UI.Android supports many different qualifiers for your alternative resources. The qualifier is a short string that you include in the name of your resource directories in order to define the device configuration for which those resources should be used. As another example, you should often create different layouts for your activities, depending on the device's screen orientation and size. For example, when the device screen is in portrait orientation (tall), you might want a layout with buttons to be vertical, but when the screen is in landscape orientation (wide), the buttons should be aligned horizontally. To change the layout depending on the orientation, you can define two different layouts and apply the appropriate qualifier to each layout's directory name. Then, the system automatically applies the appropriate layout depending on the current device orientation.For more about the different kinds of resources you can include in your application and how to create alternative resources for various device configurations, see the Application Resources developer guide.中文译文安卓应用基础1.绪论在Java编程语言编写的Android应用程序的Android的SDK工具编译代码以及与任何数据和到一个Android的包,一个归档文件档案资源的.apk后缀,所有的在一个单一的代码.apk文件被认为是一个应用程序,是Android的文件,供电设备来安装应用程序。
