CAtxtAppB
病理生理学一些常见缩写

X——XD/O黄嘌呤脱氢酶/氧化酶
R——RAS/RAA/RAAS-肾素-血管紧张素-醛固酮系统 ROS-活性氧 RTK-受体酪氨酸激酶 RTA-肾小管性酸中毒 RFI-呼吸衰竭指数 R-呼吸商
S——SB-标准碳酸氢盐 SP-调定点/应激蛋白 SIRS-全身炎症反应综合症 SO2-血氧饱和度
T——TRH-促甲状腺激素释放激素 TSH-促甲状腺激素 TNF-肿瘤坏死因子 TF-组织因子 TLR-Toll样受体 TPR-总外周阻力 TH-酪氨酸羟化酶
H——HSP-热休克蛋白 5-HT—5羟色胺HSE/F/R-热休克元件/因子/反应 HE-肝性脑病 HRS-肾病综合征 HA-组胺 HAT-组蛋白乙酰转移酶 HGP-人类基因组计划 HPA-下丘脑-垂体-肾上腺轴
I——IL-1—白细胞介素1 IFN-干扰素 IAPs-凋亡抑制蛋白 IR-胰岛素受体 ICF-细胞内液
A——AngⅡ-血管紧张素Ⅱ AVP-精氨酸加压素 APN-心房钠尿肽 ADH-抗利尿激素 AP-急性期反应蛋白 AB-实际碳酸氢盐 ACTH-促肾上腺皮质激素 APCR-APC抵抗 ALI-急性肺损伤 ARDS-急性呼吸窘迫综合症 ACE(I)-血管紧张素转化酶(抑制剂) AAA-芳香族氨基酸 AG-阴离子间隙 AQP-水通道蛋白 ATN-急性肾小管坏死 APP-急性期蛋白 APR-急性期反应 Ad-肾上腺素 AGE-晚期糖基化终末产物 AD-阿尔茨海默病 AIS-雄激素不敏感综合症 APA/S-抗磷脂抗体/综合症 ARAS-上行网状激动系统
F——FF-肾小球滤过分数 FDP-纤维蛋白原降解产物 FGF-成纤维细胞生长因子 FH-家族性高胆固醇血症
1000个常用意大利语单词

divertire 使得到娱乐 使消遣 使有兴
dividere 分 分开 隔开
dolce 甜的 甜食
dolore 疼痛 悲痛
domanda 问题 申请
domandare 问 询问
domani 明天
bianco 白的 白色的
biondo 金黄色的
bisognare 需要 必须 应该
bisogno 需要 必要
bocca 口腔 嘴
bosco 树木 森林
braccio 手臂 胳膊
bravo 好的 能干的 优良的
breve 1.短期的 短暂的 短促的 2.(罗马教皇的)敕书 (古罗马教皇的)敕书
dimostrare 表现 表明
dinanzi 在前 向前面
dio 上帝
dipendere 依靠的 从属的 从属者
dire 说
diretto 直接
direttore 经理 主任 处长
direzione 向导 领导
dirigere 领导
diritto 直的
discorso 话题 报告
corpo 物体 实体
corrente 流动的 流行的
correre 跑 奔跑
corsa 跑 奔跑
corso 水流 流动
cortile 院子 庭院
cosa 物 事物 东西
coscienza 意识 知觉
costa 在那里 彼处
costituire 设立 成立 建立
costringere 逼迫 迫使 强迫
carattere 字 字体
caratteristico 特有的 独特的
CA证书和TLS介绍

CA证书和TLS介绍数字签名⽤⾃⼰的私钥给数据加密就叫数字签名公钥传输威胁在A和B的通信中,C可以把⾃⼰的公钥发给A,让A把C的公钥当成B的公钥,这样的话.B拿到加密数据反⽽⽆法解密,⽽C却可以解密出数据.从⽽实现C截获AB之间的数据所以在两者的通信中必须要对公钥的来源进⾏确认A和B如果想安全交换公钥,就必须通过CA(证书颁发机构) 证书的通信过程 A和B⾸先都内置了CA的公钥根CA的证书是⾃⼰给⾃⼰签名的(⾃签名)CA和证书PKI: Public Key Infrastructure签证机构:CA(Certificate Authority)注册机构:RA证书吊销列表:CRL证书存取库: X.509:定义了证书的结构以及认证协议标准版本号序列号签名算法颁发者有效期限主体名称主体公钥 CRL分发点扩展信息发⾏者签名SSLSSL(Secure Socket Layer)和TLS(Transport Layer Security )本⾝是⼀个东西实现功能: 机密性认证完整性重放保护(正确同样的数据不能重复发送)两阶段协议,分为握⼿阶段和应⽤阶段握⼿阶段(协商阶段):客户端和服务器端认证对⽅⾝份(依赖于PKI体系,利⽤数字证书进⾏⾝份认证),并协商通信中使⽤的安全参数、密码套件以及主密钥.后续通信使⽤的所有密钥都是通过MasterSecret⽣成。
应⽤阶段:在握⼿阶段完成后进⼊,在应⽤阶段通信双⽅使⽤握⼿阶段协商好的密钥进⾏安全通信taobao 证书 https的通信过程taobao 证书内容包含 SCA(Ptaobao) CA密钥加密签名过的taobao公钥 + CA证书描述+过期时间+证书其它信息 taobao⽹站把证书发给客户端客户端由于信任CA并且拿到了CA的公钥,就可以解密SCA(Ptaobao) 获得taobao的公钥 Ptaobao客户端(浏览器)会在本地⽣成⼀个对称密钥(key)⽤taobao的公钥加密发送给taobao Ptaobao(key) sendto taobaotaobao通过⾃⼰的私钥解密得到客户端发送过来的key Staobao(Ptaobao(key)) = key 这样在客户端和服务端都存在相同的对称密钥key客户端和服务端就可以通过key(data)对⼤量的⽹页数据进⾏对称加密,实现通信双⽅的安全通信OpenSSL 开源实现证书申请和颁发base64编码是6bit编码包含字符a-z,A-Z,/,+ 总共64个符号⽣成私钥openssl genrsa -out /PATH/TO/PRIVATEKEY.FILE NUM_BITS (umask 077; openssl genrsa –out test.key –des 2048) -des表⽰对密钥对称称加密openssl rsa -in test.key –out test2.key 将加密key解密从私钥中提取出公钥openssl rsa -in PRIVATEKEYFILE –pubout –out PUBLICKEYFILE openssl rsa –in test.key –pubout –out test.key.pub实验:向CA申请证书建⽴Root CA1. 创建CA重要的配置⽂件openssl的配置⽂件:/etc/pki/tls/f2. 默认CA的⼯作⽬录在 /etc/pki/CA1 [root@centos7 ~]# cd /etc/pki/CA2 #创建CA服务器的私钥3 [root@centos7 CA]# (umask 077;openssl genrsa -out private/cakey.pem 4096)4 Generating RSA private key, 4096 bit long modulus5 ...................................................++6 ..............................................................................................................................................................................................................................................................................................++7 e is 65537 (0x10001)8 [root@centos7 CA]# ls private9 cakey.pem1011 #根CA给⾃⼰的私钥签名证书12 [root@centos7 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365013 You are about to be asked to enter information that will be incorporated14 into your certificate request.15 What you are about to enter is what is called a Distinguished Name or a DN.16 There are quite a few fields but you can leave some blank17 For some fields there will be a default value,18 If you enter '.', the field will be left blank.19 -----20 Country Name (2 letter code) [XX]:CN21 State or Province Name (full name) []:beijing22 Locality Name (eg, city) [Default City]:beijing23 Organization Name (eg, company) [Default Company Ltd]:mage24 Organizational Unit Name (eg, section) []:M3025 Common Name (eg, your name or your server's hostname) []:26 Email Address []:27 #以可读的⽂本格式显⽰证书内容28 [root@centos7 CA]# openssl x509 -in cacert.pem -noout -text29 Certificate:30 Data:31 Version: 3 (0x2)32 Serial Number:33 f9:72:0f:e1:6c:80:e3:aa34 Signature Algorithm: sha256WithRSAEncryption35 Issuer: C=CN, ST=beijing, L=beijing, O=mage, OU=M30, CN=36 Validity37 Not Before: May 1908:58:142018 GMT38 Not After : May 1608:58:142028 GMT39 Subject: C=CN, ST=beijing, L=beijing, O=mage, OU=M30, CN=40 Subject Public Key Info:41 Public Key Algorithm: rsaEncryption42 Public-Key: (4096 bit)43 Modulus:4400:e4:70:ef:fe:9a:43:87:41:ca:05:3d:a6:98:df:4589:19:64:ac:fb:24:04:42:be:bc:87:7a:e9:b5:be:46 9d:21:40:cf:c7:08:a1:ab:8e:03:92:29:e9:50:ed:47dd:8d:06:3c:5f:fa:23:9f:96:04:76:b9:be:56:43:4858:f8:43:db:24:cf:79:87:be:cc:bd:c0:af:41:04:49 d4:e1:6b:78:fb:b1:74:8e:25:93:22:9e:f1:22:98:5097:7e:dd:dc:af:45:97:93:16:93:8a:89:5c:b0:00:5162:a5:2f:72:ec:54:aa:3a:ec:0b:24:72:34:4a:c0:5270:ab:02:d8:36:53:93:d1:cc:98:43:a9:a8:f2:3b:53 b7:fb:be:44:64:9d:c6:bb:7d:16:b5:39:d1:1f:6d:54 e2:89:c7:9f:b7:e6:10:87:37:01:41:25:af:61:b5:55 7c:93:3c:bd:75:cb:46:ff:0e:e2:58:92:aa:25:2b:5606:b1:25:27:e5:7d:76:02:d8:c5:63:db:d0:e6:ab:57 ef:ce:69:37:7e:eb:b1:f3:59:05:e1:bf:47:b7:d1:58 4c:59:45:c9:d6:f0:35:dd:95:b0:c2:69:5b:7e:83:59 3e:64:8e:66:28:ba:06:f4:99:30:00:4d:76:72:a3:6016:d7:7e:f1:9e:9d:fe:15:88:d0:b8:e4:8f:cd:56:61 c3:89:5c:cf:40:a5:2b:9d:38:56:e2:30:09:85:22:62 b2:f6:58:20:c2:c0:65:b9:0e:61:f0:b3:a2:94:ea:6357:72:77:90:26:7d:90:11:98:18:52:ab:dc:a1:78:6468:0d:f0:d8:6b:01:c5:5d:e5:ca:a5:36:68:81:ba:65 ca:4c:b9:98:fd:f4:54:e3:eb:7f:3d:30:50:34:a6:66 5e:38:1c:82:93:9b:91:76:34:ab:df:e8:95:dd:2e:67 d0:c6:98:c5:77:a6:67:13:aa:96:3f:7c:70:7e:54:6850:77:cc:5c:d0:70:34:93:90:4a:83:25:d8:1e:1d:69 6c:17:3c:84:20:df:ee:78:28:e7:63:7f:d5:44:9c:70 c3:cb:ec:78:a7:2f:05:dc:e7:e9:20:32:34:38:66:71 fc:1f:54:79:64:bc:92:e9:59:c5:bf:35:4c:aa:1f:7293:7a:e7:8c:29:b2:58:03:bf:4f:19:36:da:2f:bd:7300:e0:0e:cd:32:09:0b:c7:1d:6c:12:19:b4:fa:4c:74 a2:b0:24:be:d3:1e:47:55:17:c3:14:ce:cd:af:01:75 ca:d8:48:44:12:40:99:f2:9f:87:1e:ea:2f:cb:0f:76 a7:0d:b7:99:d5:e1:3b:68:50:00:80:6f:59:7c:19:7796:72:51:bb:9d:6b:02:01:c1:7b:88:d9:20:57:64:78 1f:86:9579 Exponent: 65537 (0x10001)80 X509v3 extensions:81 X509v3 Subject Key Identifier:82 C6:80:BB:D0:7D:12:F4:EF:1A:69:CD:92:D3:F7:E1:3D:8A:27:CD:7683 X509v3 Authority Key Identifier:84 keyid:C6:80:BB:D0:7D:12:F4:EF:1A:69:CD:92:D3:F7:E1:3D:8A:27:CD:76 8586 X509v3 Basic Constraints:87 CA:TRUE88 Signature Algorithm: sha256WithRSAEncryption89 a0:df:1a:b4:22:69:a7:8f:92:8b:c0:67:91:66:df:5f:0f:47:90 2d:2e:6a:fd:d7:21:48:29:46:e7:7e:9b:6a:46:32:04:39:c2:91 fb:06:2e:eb:d2:f5:25:16:f7:03:f9:d1:e5:d1:d8:1d:96:8e:9222:fc:37:d7:22:97:36:4c:2c:f2:8f:09:24:5b:61:a2:29:13:9348:21:c9:db:1e:1e:24:18:d0:02:2f:ff:35:fd:21:4c:b6:af:9436:33:8a:d0:2f:22:75:f4:89:8b:99:4f:32:69:55:35:13:35:9500:d4:f3:82:44:5f:25:a8:82:1c:51:01:31:e2:7b:c0:72:0a:96 5d:a8:a8:37:30:a7:64:e5:2b:86:e4:92:57:59:ae:0b:a9:7b:97 fa:be:64:be:7a:d4:f1:6a:1d:9e:07:d4:79:7d:9c:d9:c5:98:98 ec:fc:d0:0d:55:45:41:81:c9:5a:d1:0e:ba:f1:14:c1:43:ea:9926:62:a3:c2:8f:fe:54:fe:03:9d:8c:ca:96:48:66:9f:83:88:100 c3:e7:d8:6b:e9:43:34:3c:77:b6:2f:97:54:65:39:74:09:a5:101 a3:c6:d1:aa:52:7b:d3:91:44:32:ee:1a:45:40:ff:1e:46:b9:10247:06:68:6e:91:a6:88:77:4a:df:07:bd:81:ae:6e:a0:2d:67:10339:15:b6:9b:28:e3:0a:34:bf:0d:f0:01:af:8a:f2:2b:8b:3f:10412:a7:8b:cf:c4:eb:c5:bc:58:58:10:6a:84:85:26:01:39:9a:105 fa:aa:1a:dc:83:46:61:1b:12:90:ad:5a:d7:67:78:68:a9:8c:10672:71:f0:64:b7:bf:08:85:9b:71:4a:3f:00:94:43:a7:73:3b:107 c3:95:da:07:1f:8b:ca:f4:d7:a4:af:34:95:42:a5:e0:46:e8:10818:22:29:c4:b7:b0:a0:9a:7b:e8:e5:b1:11:67:07:f3:7d:bd:109 f7:2f:5f:65:5e:32:5d:0c:65:a1:70:ad:50:6c:02:5c:a5:e6:110 0c:41:c9:26:9d:95:c4:1b:df:26:a2:43:4f:b6:e0:98:6f:ba:111 cb:83:e6:1c:00:ba:d6:48:cc:a4:2e:8d:cc:6c:f4:9d:5a:ee:11262:0e:57:e2:2e:1f:8c:6c:cd:a3:2d:63:4b:0f:6b:11:bd:18:11347:23:0b:b7:7c:fc:d5:45:01:6e:72:a0:7c:43:29:6b:ef:dd:11433:d1:39:2a:14:cd:c3:2e:91:4f:78:3d:e2:08:a5:dd:bd:00:115 aa:18:19:48:03:3a:a1:9d:1c:e7:c3:87:51:a4:42:7a:fd:7f:11690:40:c6:bb:ba:8e:22:be:63:5a:10:bb:a4:fd:ef:21:4f:d1:11784:a9:fb:2e:61:cc:b0:76118119 [root@centos7 CA]# openssl x509 -in cacert.pem -noout -issuer120 issuer= /C=CN/ST=beijing/L=beijing/O=mage/OU=M30/CN=创建CA服务器⽤户或者服务器申请证书1.⽣成私钥⽂件[root@yxh6 data]# (umask 077;openssl genrsa -out app.key 1024)Generating RSA private key, 1024 bit long modulus ..............................++++++.....................++++++e is 65537 (0x10001)[root@yxh6 data]# lsapp.key2.利⽤私钥⽂件⽣成申请⽂件[root@yxh6 data]# openssl req -new -key app.key -out app.csrYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:beijingLocality Name (eg, city) [Default City]:beijingOrganization Name (eg, company) [Default Company Ltd]:mageOrganizational Unit Name (eg, section) []:M30Common Name (eg, your name or your server's hostname) []:Email Address []:Please enter the following 'extra' attributesto be sent with your certificate requestA challenge password []:An optional company name []:[root@yxh6 data]# lsapp.csr app.key3.将申请⽂件发送给CAscp app.csr 192.168.33.130:/etc/pki/CA4.CA颁发证书回到CA服务器执⾏颁发证书touch index.txtecho 0F > serial[root@centos7 CA]# openssl ca -in app.csr -out certs/app.crt -days 100Using configuration from /etc/pki/tls/fCheck that the request matches the signatureSignature okCertificate Details:Serial Number: 15 (0xf)ValidityNot Before: May 1909:35:372018 GMTNot After : Aug 2709:35:372018 GMTSubject:countryName = CNstateOrProvinceName = beijingorganizationName = mageorganizationalUnitName = M30commonName = X509v3 extensions:X509v3 Basic Constraints:CA:FALSENetscape Comment:OpenSSL Generated CertificateX509v3 Subject Key Identifier:71:DC:D4:AE:8A:5A:16:A4:13:62:D7:3A:C9:C7:DD:A7:9C:95:B0:4FX509v3 Authority Key Identifier:keyid:C6:80:BB:D0:7D:12:F4:EF:1A:69:CD:92:D3:F7:E1:3D:8A:27:CD:76Certificate is to be certified until Aug 2709:35:372018 GMT (100 days)Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]yWrite out database with 1 new entriesData Base Updated[root@centos7 certs]# lsapp.crt5.证书发送客户端scp app.csr 192.168.33.129:/data客户端可以拿着这个证书在应⽤程序中使⽤CA签发证书(客户端)windows下查看⽣成的证书信息和安装证书可以把证书cacert.pem下载到windows中进⾏可视化查看证书信息需要.pem(cacert.pem)后缀名改成windows能识别的.cer(cacert.cer)或者.crt 点击安装证书可以把此证书安装到可信任的证书路径中证书管理查看证书中的信息:openssl x509 -in /PATH/FROM/CERT_FILE -noout -text|issuer|subject|serial|datesopenssl ca -status SERIAL 查看指定编号的证书状态吊销证书在客户端获取要吊销的证书的serialopenssl x509 -in /PATH/FROM/CERT_FILE -noout -serial -subject在CA上,根据客户提交的serial与subject信息,对⽐检验是否与index.txt⽂件中的信息⼀致,吊销证书:openssl ca -revoke /etc/pki/CA/newcerts/SERIAL.pem指定第⼀个吊销证书的编号,注意:第⼀次更新证书吊销列表前,才需要执⾏ echo 01 > /etc/pki/CA/crlnumber更新证书吊销列表 openssl ca -gencrl -out /etc/pki/CA/crl.pem查看crl⽂件: openssl crl -in /etc/pki/CA/crl.pem -noout -textSSH安全服务ssh: secure shell, protocol, 22/tcp, 安全的远程登录两种⽅式的⽤户登录认证:1.基于password1.客户端向服务端发送SSH请求2.服务端收到请求,发送公钥给客户端3.客户端输⼊⽤户名和密码通过公钥加密回传给服务端4.服务端通过私钥解密得到⽤户名和密码和本地的⽤户名密码进⾏验证匹配2.基于key1.⾸先在客户端⽣成⼀对密钥对2.客户端将公钥拷贝给服务端并重命名为 authorized_keys3.客户端向服务端发送⼀个连接请求,信息包括ip,⽤户名4.服务端得到客户端消息后,会到authorized_keys查找是否有对应信息并且随机⽣成⼀个字符串5.服务端把随机⽣成的字符串⽤客户端公钥加密发送给客户端6.客户端接收到加密字符串后⽤⾃⼰的私钥对字符串进⾏解密,并且把解密后的字符串发送给服务端7.服务端会把接收到的字符串和原来⾃⼰⽣成的随机字符串进⾏验证匹配ssh客户端:1.客户端配置⽂件 /etc/ssh/ssh_config ssh服务端的配置⽂件 /etc/ssh/sshd_configssh客户端会在第⼀次连接的时候把远程主机的公钥下载到本机,如果需要冒充其它已经连接过的主机,需要把对⽅的私钥拷贝到本地来实现基于ssh key的认证实现指定⽤户⽆密码连接,默认是root⽤户在ssh-copy-id命令中指定特定的⽤户名就会把公钥⽂件拷贝到指定⽤户的家⽬录下ssh-copy-id yxh@192.168.33.1301.在客户端⽣成密钥对[root@yxh6 data]# ssh-keygen -t rsaGenerating public/private rsa key pair.Enter file in which to save the key (/root/.ssh/id_rsa):Enter passphrase (empty for no passphrase):Enter same passphrase again:Your identification has been saved in /root/.ssh/id_rsa.Your public key has been saved in /root/.ssh/id_rsa.pub.The key fingerprint is:84:69:ce:6b:19:1d:09:c4:94:66:06:2e:76:57:8b:0b root@yxh6.localdomainThe key's randomart image is:+--[ RSA 2048]----+| .=+.. || . ** o || o E+* = || . o * + . || = S || + || + || . || |+-----------------+[root@yxh6 data]# cd /root/.ssh[root@yxh6 .ssh]# lsid_rsa id_rsa.pub known_hosts2.把公钥复制到服务端主机[root@yxh6 .ssh]# ssh-copy-id192.168.33.130root@192.168.33.130's password:Now try logging into the machine, with "ssh '192.168.33.130'", and check in:.ssh/authorized_keysto make sure we haven't added extra keys that you weren't expecting.3.直接连接远程主机[root@yxh6 .ssh]# ssh192.168.33.130Last login: Sat May 1917:31:502018 from 192.168.33.1this is etc/motd,welcome....[root@centos7 ~]#View Code多台主机之间实现相互key认证登录1.在⼀台主机A上⽣成⼀对密钥对所有主机使⽤同⼀密钥2.ssh-copy-id A3.scp -rp /root/.ssh B:/root4.scp -rp /root/.ssh C:/rootssh key认证脚本⾃动化expect匹配输出规则:#Are you sure you want to continue connecting (yes/no)? #root@192.168.33.129's password:1⽣成ip列表⽂件2 [root@centos7 .ssh]# cat ip.txt3192.168.33.1294192.168.33.13056 #!/bin/bash7 rpm -q expect &> /dev/null || yum install -y expect8ssh-keygen -P "" -f "/root/.ssh/id_rsa"9 password=root10while read ipaddr;do11echo $ipaddr12 expect <<EOF13 spawn ssh-copy-id $ipaddr14 expect {15"yes/no" { send "yes\n";exp_continue } 16"password:" { send "$password\n" }17 }18 expect eof19 EOF20done < ip.txt2122给脚本⽂件设置执⾏权限23chmod +x ssh_key.sh2425执⾏脚本26 ./ssh_key.shView Code。
阅读新体验—Apabi Reader(方正阿帕比)阅读软件使用说明

阅读新体验—Apabi Reader(方正阿帕比)阅读软件Apabi Reader(方正阿帕比阅读软件)是方正公司推出的一款集RSS阅读与PDF、CEB、PDF、XEB、HTML、TXT、和OEB多种数字化的书籍阅读的软件,不论是休闲性的书籍阅读、机密性的企业内部文件、高附加价值的研究报告、专属性质的报价文件等类数字内容,都可经由本软件满足阅读、说明、收藏及保密的需求;看电子书的同时,还可以直接使用翻译软件、关键词查找,还能很方便地在电子书上加着重、圈注、批注、划线,插入书签;亦具备快速点选网上书店、书架管理及网页浏览等功能。
近日该软件发布了4.0.1版,在原有的基础上增加了一些新功能的同时也修正了一些BUG,所以在整体的运用方面会更加的出色一、Apabi Reader资料下载地址<><><><><><><><><>(华军下载)、(官网下载)二、Apabi Reader更新说明4.0.1版本主要改进:1、提供放映模式。
2、支持Windows 7 的任务栏新特性。
3、支持Windows 7搜索筛选器。
4、支持Windows 7资源管理器的预览窗格和Outlook 2007里展示CEB和CEBX。
6、提高打开CEB和PDF的速度。
7、提高普通模式和读书模式下的翻页速度。
8、改进图书借阅下载。
9、改进安装程序不同版本相互修复、二次打包等功能。
10、改进文档管理器。
11、支持错误报告跟踪机制。
12、支持插件数据的打印。
13、支持CEBX本地安全性。
14、支持CEBX电子表单填写。
15、修正若干Bug。
三、Apabi Reader试用1、安装Apabi Reader的安装过程很正规,并不存在所谓的插件及强制安装类工具等图1、安装主程序图2、设置默认阅读器3、试用安装完毕后,双击桌面图标进入软件的主体部分,和其他的阅读器类似,都是采用1:3分栏的常规模式,上方是菜单栏,左侧为工具提示栏,中部为主体的框架部分图3、软件界面单击左上角的打开按钮,定位到一个软件所支持的格式文件即可立即打开该文件,在4.0.1版本中,CEB以及PDF格式的文件打开速度也得到了一定的提升图4、PDF文档阅读下面笔者就其主要的功能做个简单的介绍,首先来看下该软件的工具栏部分,也就是菜单栏下方的一排按钮部分图5、各种功能按钮1:文件区域,包括打开、保存、打印2:指针操作区,单击手型可移动文件进行查看3:单页显示或者连续页显示选项4:文档查看方式,放大、缩小5:翻页显示及定位页数6:文件内搜索7:阅读模式选择8:文本旋转9:新增的放映模式,有点类似于PowerPoint的幻灯片放映10:注释工具,包括各种直线、矢量图、批注等等11:有声朗读(需要手动下载语音包)图6、放大、缩小按钮图7、阅读模式图8、文档旋转图9、放映模式软件基本上大体按钮都集中在上面的部分,另外一些特殊的功能需要利用菜单栏另外开启,后面笔者会介绍。
IEC 60384-14-1-2016

E l ectroped i a - www. el ectroped i a. org
Th e
wo rl d ' s
l ead i n g
on l i n e
d i cti o n ary
of
el ectro n i c
an d
e l e c tri c al te rm s c o n tai n i n g 2 0 0 0 0 t e rm s an d d efi n i ti o n s i n
A l l ri g h ts re s e rve d . U n l e s s o th e rwi s e s p e c i f i e d , n o p a rt o f t h i s pu b l i c a ti o n m a y be re p ro d u c e d o r u t i l i z e d i n a n y f o rm o r b y a n y m e a n s , e l e c t ro n i c o r m e c h a n i c a l , i n c l u d i n g p h o t o c o p yi n g an d m i c ro fi l m , wi t h o u t p e rm i s s i o n i n wri t i n g f ro m e i t h e r I E C o r I E C ' s m em be r N at i o n a l C o m m i tte e i n t h e co u n t ry o f t h e req u es t e r. I f yo u h ave an y q u e s ti o n s ab o u t I E C c o p yri g h t o r h a ve an e n q u i ry abo u t o b tai n i n g ad d i ti o n al ri g h ts t o t h i s p u bl i c ati o n , pl e as e co n t act th e a d d re s s b e l o w o r yo u r l o c al I E C m em be r N ati o n al C o m m i tt e e fo r fu rth e r i n f o rm at i o n .
ca数字证书下载安装

CA数字证书下载安装1. 什么是CA数字证书?CA(Certificate Authority)数字证书是一种用于验证和加密网络通信的安全协议。
它基于公钥加密技术,能够确保通信的机密性、完整性和身份认证。
CA数字证书是由可信的第三方机构颁发的,用于验证网站、服务器或应用程序的真实性和可信度。
2. 为什么需要CA数字证书?在网络通信过程中,有许多潜在的安全风险,如数据窃取、篡改和伪装等。
为了保护通信的安全性,确保数据的保密性和完整性,使用CA数字证书显得尤为重要。
通过使用CA数字证书,用户可以验证服务器或网站的身份,确保所访问的是合法的服务,并且所有传输的信息都是经过加密的,不易被第三方窃取或篡改。
同时,CA数字证书还可以提供其他安全功能,如数字签名和加密通信。
3. 下载CA数字证书在安装CA数字证书之前,首先需要下载证书文件。
可以通过以下步骤进行下载:1.打开网页浏览器,进入CA数字证书颁发机构(CA)的官方网站;2.寻找并点击「证书下载」或类似的选项;3.根据需要选择所需的证书类型,如SSL证书、代码签名证书等;4.在证书下载页面中,选择相应的操作系统和服务器软件类型;5.点击「下载」按钮或链接,开始下载CA数字证书。
4. 安装CA数字证书安装CA数字证书的具体步骤因操作系统和服务器软件的不同而有所差异。
下面将列举几个常见操作系统和服务器软件的安装方法。
4.1 Windows系统4.1.1 IIS服务器以下是在Windows系统上安装CA数字证书的步骤:1.将下载好的证书文件保存到本地计算机;2.打开IIS管理器,进入服务器的「站点」;3.在右侧的「操作」菜单中,找到「绑定…」选项;4.在「站点绑定」对话框中,选择需要安装证书的网站;5.点击「编辑…」按钮,在SSL证书部分选择「从列表中选择」;6.在弹出的证书选择窗口中,点击「添加…」按钮;7.找到并选择之前下载的证书文件,点击「确定」;8.点击「关闭」按钮,完成证书安装。
同济大学工程数学线性代数第六版答案(全)

第一章行列式1。
利用对角线法则计算下列三阶行列式:(1)381141102---; 解381141102--- =2⨯(-4)⨯3+0⨯( 1)⨯(-1)+1⨯1⨯8-0⨯1⨯3-2⨯(-1)⨯8 1⨯( 4)⨯( 1)=24+8+16 4=-4。
(2)ba c a cbc b a ; 解ba c a cbc b a =acb +bac +cba bbb aaa -ccc=3abc a 3 b 3 c 3。
(3)222111c b a c b a ; 解222111c b a c b a =bc 2+ca 2+ab 2 ac 2 ba 2-cb 2=(a -b )(b c )(c a ).(4)yx y x x y x y y x y x +++. 解 yx y x x y x y y x y x +++ =x (x +y )y +yx (x +y )+(x +y )yx -y 3 (x +y )3 x 3=3xy (x +y )-y 3 3x 2y -x 3 y 3-x 3=2(x 3+y 3).2。
按自然数从小到大为标准次序,求下列各排列的逆序数:(1)1 2 3 4;解逆序数为0(2)4 1 3 2;解 逆序数为4: 41, 43, 42, 32。
(3)3 4 2 1;解 逆序数为5: 3 2, 3 1, 4 2, 4 1, 2 1.(4)2 4 1 3;解 逆序数为3: 2 1, 4 1, 4 3。
(5)1 3 ⋅⋅⋅ (2n -1) 2 4 ⋅⋅⋅ (2n );解 逆序数为2)1(-n n : 3 2 (1个)5 2, 5 4(2个)7 2,7 4,7 6(3个)⋅⋅⋅⋅⋅⋅(2n 1)2,(2n-1)4,(2n 1)6,⋅⋅⋅,(2n-1)(2n 2)(n-1个)(6)1 3 ⋅⋅⋅(2n-1) (2n) (2n 2)⋅⋅⋅ 2。
解逆序数为n(n 1):3 2(1个)5 2,5 4 (2个)⋅⋅⋅⋅⋅⋅(2n-1)2,(2n 1)4,(2n 1)6,⋅⋅⋅,(2n-1)(2n 2)(n 1个)4 2(1个)6 2,6 4(2个)⋅⋅⋅⋅⋅⋅(2n)2,(2n)4,(2n)6,⋅⋅⋅,(2n)(2n 2)(n 1个)3。
ASANTE TECHNOLOGIES, INC. v. PMC-SIERRA, INC.

ASANTE TECHNOLOGIES, INC. v. PMC-SIERRA, INC. No. C 01-20230 JW.164 F.Supp.2d 1142 (2001)ASANTE TECHNOLOGIES, INC., Plaintiff, v. PMC-SIERRA, INC., Defendant.United States District Court, N.D. California, San Jose Division.July 30, 2001.Jeffrey J. Lederman, Gray Cary Ware & Freidenrich, Palo Alto, CA, for plaintiff.Michael A. Jacobs, Morrison & FOerster, San Francisco, CA, for defendant.O R D E R D E N Y I N G M O T I O N T O R E M AN D AN D R E Q U E S T F O R AT T O R N E Y S' F E E S WARE, District Judge.I.I N T R O D U C T I O NThis lawsuit arises out of a dispute involving the sale of electronic components. Plaintiff, Asante Technologies Inc., filed the action in the Superior Court for the State of California, Santa Clara County, on February 13, 2001. Defendant, PMC-Sierra, Inc., removed the action to this Court, asserting federal question jurisdiction pursuant to 28 U.S.C. section 1331. Specifically, Defendant asserts that Plaintiff's claims for breach of contract and breach of express warranty are governed by the United Nations Convention on Contracts for the International Sale of Goods ("CISG"). Plaintiff disputes jurisdiction and filed this Motion To Remand And For Attorneys' Fees. The Court conducted a hearing on June 18, 2001. Based upon the submitted papers and oral arguments of the parties, the Court DENIES the motion to remand and the associated request for attorneys' fees.I I.B A C K G R O U N DThe Complaint in this action alleges claims based in tort and contract. Plaintiff contends that Defendant failed to provide it with electronic components meeting certain designated technical specifications. Defendant timely removed the action to this Court on March 16, 2001.Plaintiff is a Delaware corporation having its primary place of business in Santa Clara County, California. Plaintiff produces network switchers, a type of electronic component used to connect multiple computers to one another and to the Internet. Plaintiff purchasescomponent parts from a number of manufacturers. In particular, Plaintiff purchases application-specific integrated circuits ("ASICs"), which are considered the control center of its network switchers, from Defendant.Defendant is also a Delaware corporation. Defendant asserts that, at all relevant times, its corporate headquarters, inside sales and marketing office, public relations department, principal warehouse, and most design and engineering functions were located in Burnaby, British Columbia, Canada. Defendant also maintains an office in Portland, Oregon, where many of its engineers are based. Defendant's products are sold in California through Unique Technologies, which is an authorized distributor of Defendant's products in North America. It is undisputed that Defendant directed Plaintiff to purchase Defendant's products through Unique, and that Defendant honored purchase orders solicited by Unique. Unique is located in California. Determining Defendant's "place of business" with respect to its contract with Plaintiff is critical to the question of whether the Court has jurisdiction in this case.Plaintiff's Complaint focuses on five purchase orders.1 Four of the five purchase orders were submitted to Defendant through Unique as directed by Defendant. However, Plaintiff does not dispute that one of the purchase orders, dated January 28, 2000, was sent by fax directly to Defendant in British Columbia, and that Defendant processed the order in British Columbia. Defendant shipped all orders to Plaintiff's headquarters in California.2 Upon delivery of the goods, Unique sent invoices to Plaintiff, at which time Plaintiff tendered payment to Unique either in California or in Nevada.The Parties do not identify any single contract embodying the agreement pertaining to the sale. Instead, Plaintiff asserts that acceptance of each of its purchase orders was expressly conditioned upon acceptance by Defendant of Plaintiff's "Terms and Conditions," which were included with each Purchase Order. Paragraph 20 of Plaintiff's Terms and Conditions provides "APPLICABLE LAW. The validity [and] performance of this [purchase] order shall be governed by the laws of the state shown on Buyer's address on this order." (Contos Decl., Exh. H, ¶ 16.) The buyer's address as shown on each of the Purchase Orders is in San Jose, California. Alternatively, Defendant suggests that the terms of shipment are governed by a document entitled "PMC-Sierra TERMS AND CONDITIONS OF SALE." Paragraph 19 of Defendant's Terms and conditions provides "APPLICABLE LAW: The contract between the parties is made, governed by, and shall be construed in accordance with the laws of the Province of British Columbia and the laws of Canada applicable therein, which shall be deemed to be the proper law hereof ...." (Wechsler Decl., Exh. D, ¶ 6.)Plaintiff's Complaint alleges that Defendant promised in writing that the chips would meet certain technical specifications. (Compl. ¶¶ 13, 14, 15, 17, 18, 22, 23, & 25.) Defendant asserts that the following documents upon which Plaintiff relies emanated from Defendant's office in British Columbia: (1) Defendant's August 24, 1998 press release that it would be making chips available for general sampling (Doucette Decl. ¶ 13); (2) Defendant's periodic updates of technical specifications (Doucette Decl., Exh. H); and (3) correspondence from Defendant to Plaintiff, including a letter dated October 25, 1999. It is furthermore undisputed that the Prototype Product Limited Warranty Agreements relating to some or all of Plaintiff's purchases were executed with Defendant's British Columbia facility. (Doucette Decl., Exhs. B & C.)Defendant does not deny that Plaintiff maintained extensive contacts with Defendant's facilities in Portland Oregon during the "development and engineering" of the ASICs. (Amended Supplemental Decl. of Anthony Contos, ¶ 3.) These contacts included daily email and telephone correspondence and frequent in-person collaborations between Plaintiff's engineers and Defendant's engineers inPortland. (Id.) Plaintiff contends that this litigation concerns the inability of Defendant's engineers in Portland to develop an ASIC meeting the agreed-upon specifications. (Id.)Plaintiff now requests this Court to remand this action back to the Superior Court of the County of Santa Clara pursuant to 28 U.S.C. section 1447(c), asserting lack of subject matter jurisdiction. In addition, Plaintiff requests award of attorneys fees and costs for the expense of bringing this motion.I I I.S T A N D A R D SA defendant may remove to federal court any civil action brought in a state court that originally could have been filed in federal court. 28 U.S.C. § 1441(a); Caterpillar, Inc. v. Williams,482 U.S. 386, 107 S.Ct. 2425, 96 L.Ed.2d 318 (1987). When a case originally filed in state court contains separate and independent federal and state law claims, the entire case may be removed to federal court. 28 U.S.C. 1441 (c).The determination of whether an action arises under federal law is guided by the "well-pleaded complaint" rule. Franchise Tax Board v. Construction Laborers Vacation Trust,463 U.S. 1, 10, 103 S.Ct. 2841, 77 L.Ed.2d 420 (1983). The rule provides that removal is proper when a federal question is presented on the face of the Complaint.Id. at 9, 103 S.Ct. 2841. However, in areas where federal law completely preempts state law, even if the claims are purportedly based on state law, the claims are considered to have arisen under federal law. Ramirez v. Fox Television Station, Inc.,998 F.2d 743(9th Cir. 1993). Defendant has the burden of establishing that removal is proper. Gaus v. Miles, Inc.,980 F.2d 564 (9th Cir.1992). If, at any time before judgment, the district court determines that the case was removed from state court improvidently and without jurisdiction, the district court must remand the case. 28 U.S.C. § 1447(c).The Convention on Contracts for the International Sale of Goods ("CISG") is an international treaty which has been signed and ratified by the United States and Canada, among other countries. The CISG was adopted for the purpose of establishing "substantive provisions of law to govern the formation of international sales contracts and the rights and obligations of the buyer and the seller." U.S. Ratification of 1980 United Nations Convention on Contracts for the International Sale of Goods: Official English Text, 15 U.S.C.App. at 52 (1997). The CISG applies "to contracts of sale of goods between parties whose places of business are in different States ... when the States are Contracting States." 15 U.S.C.App., Art.1(1)(a). Article 10 of the CISG provides that "if a party has more than one place of business, the place of business is that which has the closest relationship to the contract and its performance." 15 U.S.C.App. Art. 10.I V.D I S C U S S I O NDefendant asserts that this Court has jurisdiction to hear this case pursuant to 28 U.S.C. section 1331, which dictates that the "district courts shall have original jurisdiction of all civil actions arising under the Constitution, laws, or treaties of the United States." Specifically, Defendant contends that the contract claims at issue necessarily implicate the CISG, because the contract is between parties having their places of business in two nations which have adopted the CISG treaty. The Court concludes that Defendant's place of business for the purposes of the contract at issue and its performance is Burnaby, British Columbia, Canada. Accordingly, the CISG applies. Moreover, the parties did not effectuate an "opt out" of application of the CISG. Finally, because the Court concludes that the CISG preempts state laws that address the formation of a contract of sale and the rights and obligations of the seller and buyer arising from such a contract, the well-pleaded complaint rule does not preclude removal in this case.A.F e d e r a l J u r i s d i c t i o n A t t a c h e s t o C l a i m s G o v e r n e d B y th e C I S GAlthough the general federal question statute, 28 U.S.C. § 1331(a), gives district courts original jurisdiction over every civil action that "arises under the ... treaties of the United States," an individual may only enforce a treaty's provisions when the treaty is self-executing, that is, when it expressly or impliedly creates a private right of action. See Tel-Oren v. Libyan Arab Republic,726 F.2d 774, 808 (D.C.Cir.1984) (Bork, J., concurring); Handel v. Artukovic,601 F.Supp. 1421, 1425 (C.D.Cal.1985). The parties do not dispute that the CISG properly creates a private right of action. See Delchi Carrier v. Rotorex Corp.,71 F.3d 1024, 1027-28 (2d Cir.1995); Filanto, S.p.A. v. Chilewich Int'l Corp.,789 F.Supp. 1229, 1237 (S.D.N.Y.1992); U.S. Ratification of 1980 United Nations Convention on Contracts for the International Sale of Goods: Official English Text, 15 U.S.C.App. at 52 (1997) ("The Convention sets out substantive provisions of law to govern the formation of international sales contracts and the rights and obligations of the buyer and seller. It will apply to sales contracts between parties with their places of business in different countries bound by Convention, provided the parties have left their contracts silent as to applicable law."). Therefore, if the CISG properly applies to this action, federal jurisdiction exists.3B.T h e C o n t r a c t I n Q u e s t i o n I s B e t w e e n P a r ti e s F r o m T w o D i f f e r e n tC o n t r a c t i n g S ta t e sThe CISG only applies when a contract is "between parties whose places of business are in different States."4 15 U.S.C.App., Art. 1(1)(a). If this requirement is not satisfied, Defendant cannot claim jurisdiction under the CISG. It is undisputed that Plaintiff's place of business is Santa Clara County, California, U.S.A. It is further undisputed that during the relevant time period, Defendant's corporate headquarters, inside sales and marketing office, public relations department, principal warehouse, and most of its design and engineering functions were located in Burnaby, British Columbia, Canada. However, Plaintiff contends that, pursuant to Article 10 of the CISG, Defendant's "place of business" having the closest relationship to the contract at issue is the United States.5The Complaint asserts inter alia two claims for breach of contract and a claim for breach of express warranty based on the failure of the delivered ASICS to conform to the agreed upon technical specifications. (Compl. ¶¶ 40-53.) In support of these claims, Plaintiff relies on multiple representations allegedly made by Defendant regarding the technical specifications of the ASICS products at issue. Among the representations are: (1) an August 24, 1998 press release (Id., ¶ 13); (2) "materials" released by Defendant in September, 1998 (Id., ¶ 14);(3) "revised materials" released by Defendant in November 1998 (Id., ¶ 15); (4) "revised materials" released by Defendant in January, 1999 (Id., ¶ 17); (5) "revised materials" released by Defendant in April, 1999 (Id., ¶ 18); (6) a September, 1999 statement by Defendant which included revised specifications indicating that its ASICS would comply with 802.1q VLAN specifications (Id., ¶22); (7) a statement made by Defendant's President and Chief Executive Officer on October 25, 1999 (Id., ¶ 23); (8) a communication of December, 1999 (Id., ¶ 24); and (9) "revised materials" released by Defendant in January, 2000 (Id., ¶ 25). It appears undisputed that each of these alleged representations regarding the technical specifications of the product was issued from Defendant's headquarters in British Columbia, Canada. (See Opposition Brief at 3.)Rather than challenge the Canadian source of these documents, Plaintiff shifts its emphasis to the purchase orders submitted by Plaintiff to Unique Technologies, a nonexclusive distributor of Defendant's products. Plaintiff asserts that Unique acted in the United States as an agent of Defendant, and that Plaintiff's contacts with Unique establish Defendant's place of business in the U.S. for the purposes of this contract.Plaintiff has failed to persuade the Court that Unique acted as the agent of Defendant. Plaintiff provides no legal support for this proposition. To the contrary, a distributor of goods for resale is normally not treated as an agent of the manufacturer. Restatement of the Law of Agency, 2d § 14J (1957) ("One who receives goods from another for resale to a third person is not thereby the other's agent in the transaction."); Stansifer v. Chrysler Motors Corp.,487 F.2d 59, 64-65 (9th Cir.1973) (holding that nonexclusive distributor was not agent of manufacturer where distributorship agreement expressly stated "distributor is not an agent"). Agency results "from the manisfestation of consent by one person to another that the other shall act on his behalf and subject to his control, and consent by the other so to act." Restatement of the Law of Agency, 2d, § 1 (1957). Plaintiff has produced no evidence of consent by Defendant to be bound by the acts of Unique. To the contrary, Defendant cites the distributorship agreement with Unique, which expressly states that the contract does not "allow Distributor to create or assume any obligation on behalf of [Defendant] for any purpose whatsoever." (Doucette Decl. Exh. M, ¶1.6(b).) Furthermore, while Unique may distribute Defendant's products, Plaintiff does not allege that Unique made any representations regarding technical specifications on behalf of Defendant. Indeed, Unique is not even mentioned in the Complaint. To the extent that representations were made regarding the technical specifications of the ASICs, and those specifications were not satisfied by the delivered goods, the relevant agreement is that between Plaintiff and Defendant. Accordingly, the Court finds that Unique is not an agent of Defendant in this dispute. Plaintiff's dealings with Unique do not establish Defendant's place of business in the United States.Plaintiff's claims concern breaches of representations made by Defendant from Canada. Moreover, the products in question are manufactured in Canada, and Plaintiff knew that Defendant was Canadian, having sent one purchase order directly to Defendant in Canada by fax. Plaintiff supports its position with the declaration of Anthony Contos, Plaintiff's Vice President of Finance and Administration, who states that Plaintiff's primary contact with Defendant "during the development and engineering of the ASICs at issue ... was with [Defendant's] facilities in Portland, Oregon." (Contos Amended Supplemental Decl. ¶ 3.) The Court concludes that these contacts are not sufficient to override the fact that most if not all of Defendant's alleged representations regarding the technical specifications of the products emanated from Canada. (See supra at 7:1-12.) Moreover, Plaintiff directly corresponded with Defendant at Defendant's Canadian address. (See Doucette Decl. ¶ 15.) Plaintiff relies on all of these alleged representations at length in its Complaint. (See supra at 7:1-12.) In contrast, Plaintiff has not identified any specific representation or correspondence emanating from Defendant's Oregon branch. For these reasons, the Court finds that Defendant's place of business that has the closest relationship to the contract and its performance is British Columbia, Canada. Consequently, the contract at issue in this litigation is between parties from two different Contracting States, Canada and the United States. This contract therefore implicates the CISG.C.T h e E f f e c t o f t h e Ch o i c e o f L a w C l a u s e sPlaintiff next argues that, even if the Parties are from two nations that have adopted the CISG, the choice of law provisions in the "Terms and Conditions" set forth by both Parties reflect the Parties' intent to "opt out" of application of the treaty.6 Article 6 of the CISG provides that "[t]he parties may exclude the application of the Convention or, subject to Article 12, derogate from or vary the effect of any of its provisions." 15 U.S.C.App., Art. 6. Defendant asserts that merely choosing the law of a jurisdiction is insufficient to opt out of the CISG, absent express exclusion of the CISG. The Court finds that the particular choice of law provisions in the "Terms and Conditions" of both parties are inadequate to effectuate an opt out of the CISG.Although selection of a particular choice of law, such as "the California Commercial Code" or the "Uniform Commercial Code"could amount to implied exclusion of the CISG, the choice of law clauses at issue here do not evince a clear intent to opt out of theCISG. For example, Defendant's choice of applicable law adopts the law of British Columbia, and it is undisputed that the CISG is the law of British Columbia. (International Sale of Goods Act ch. 236, 1996 S.B.C. 1 et seq. (B.C.).) Furthermore, even Plaintiff's choice of applicable law generally adopts the "laws of" the State of California, and California is bound by the Supremacy Clause to the treaties of the United States. U.S. Const. art. VI, cl. 2 ("This Constitution, and the laws of the United States which shall be made in pursuance thereof; and all treaties made, or which shall be made, under the authority of the United States, shall be the supreme law of the land.") Thus, under general California law, the CISG is applicable to contracts where the contracting parties are from different countries that have adopted the CISG. In the absence of clear language indicating that both contracting parties intended to opt out of the CISG, and in view of Defendant's Terms and Conditions which would apply the CISG, the Court rejects Plaintiff's contention that the choice of law provisions preclude the applicability of the CISG.D.F e d e r a l J u r i s d i c t i o n B a s e d U p o n t h e C I SG D o e s N o t V i o l a t e t h eW e l l-P l e a d e d C o m p l a i n t R u l eThe Court rejects Plaintiff's argument that removal is improper because of the well-pleaded complaint rule. The rule states that a cause of action arises under federal law only when the plaintiff's well-pleaded complaint raises issues of federal law. Gully v. First National Bank,299 U.S. 109, 112, 57 S.Ct. 96, 81 L.Ed. 70 (1936);Louisville & Nashville R. Co. v. Mottley,211 U.S. 149, 29 S.Ct. 42, 53 L.Ed. 126 (1908). Anticipation of a federal preemption defense, such as the defense that federal law prohibits the state claims, is insufficient to establish federal jurisdiction. Gully, 299 U.S. at 116, 57 S.Ct. 96. Even where both parties concede that determination of a federal question is the only issue in the case, removal is improper unless the plaintiff's complaint establishes that the case "arises under" federal law. Caterpillar, Inc. v. Williams,482 U.S. 386, 393, 107 S.Ct. 2425, 96 L.Ed.2d 318 (1987).It is undisputed that the Complaint on its face does not refer to the CISG. However, Defendants argue that the preemptive force of the CISG converts the state breach of contract claim into a federal claim. Indeed, Congress may establish a federal law that so completely preempts a particular area of law that any civil complaint raising that select group of claims is necessarily federal in character.Metropolitan Life Ins. Co. v. Taylor,481 U.S. 58, 62, 107 S.Ct. 1542, 95 L.Ed.2d 55 (1987) (holding that Employee Retirement Income Security Act (ERISA) preempts an employee's common-law contract and tort claims arising from employer's insurer's termination of disability benefits, establishing federal jurisdiction); Avco Corp. v. Aero Lodge No. 735, Int'l Ass'n. of Machinists,390 U.S. 557, 560, 88 S.Ct. 1235, 20 L.Ed.2d 126 (1968) (holding that section 301 of Labor Management Relations Act (LMRA) preempts any state cause of action for violation of contracts between an employer and a labor organization).It appears that the issue of whether or not the CISG preempts state law is a matter of first impression. In the case of federal statutes, "[t]he question of whether a certain action is preempted by federal law is one of congressional intent. The purpose of Congress is the ultimate touchstone." Pilot Life Ins. Co. v. Dedeaux,481 U.S. 41, 45, 107 S.Ct. 1549, 95 L.Ed.2d 39 (1987) (internal quotations and citations omitted). Transferring this analysis to the question of preemption by a treaty, the Court focuses on the intent of the treaty's contracting parties. See Husmann v. Trans World Airlines, Inc.,169 F.3d 1151, 1153 (8th Cir.1999) (finding Warsaw Convention preempts state law personal injury claim); Jack v. Trans World Airlines, Inc.,820 F.Supp. 1218, 1220 (N.D.Cal.1993) (finding removal proper because Warsaw Convention preempts state law causes of action).In the case of the CISG treaty, this intent can be discerned from the introductory text, which states that "the adoption of uniform rules which govern contracts for the international sale of goods and take into account the different social, economic and legal systems wouldcontribute to the removal of legal barriers in international trade and promote the development of international trade." 15 U.S.C.App. at 53. The CISG further recognizes the importance of "the development of international trade on the basis of equality and mutual benefit."Id. These objectives are reiterated in the President's Letter of Transmittal of the CISG to the Senate as well as the Secretary of State's Letter of Submittal of the CISG to the President. Id. at 70-72. The Secretary of State, George P. Shultz, noted:Sales transactions that cross international boundaries are subject to legal uncertainty-doubt as to which legal system will apply and the difficulty of coping with unfamiliar foreign law. The sales contract may specify which law will apply, but our sellers and buyers cannot expect that foreign trading partners will always agree on the applicability of United States law.... The Convention's approach provides an effective solution for this difficult problem. When a contract for an international sale of goods does not make clear what rule of law applies, the Convention provides uniform rules to govern the questions that arise in making and performance of the contract.Id. at 71. The Court concludes that the expressly stated goal of developing uniform international contract law to promote international trade indicates the intent of the parties to the treaty to have the treaty preempt state law causes of action.The availability of independent state contract law causes of action would frustrate the goals of uniformity and certainty embraced by the CISG. Allowing such avenues for potential liability would subject contracting parties to different states' laws and the very same ambiguities regarding international contracts that the CISG was designed to avoid. As a consequence, parties to international contracts would be unable to predict the applicable law, and the fundamental purpose of the CISG would be undermined. Based on very similar rationale, courts have concluded that the Warsaw Convention preempts state law causes of action. Husmann, 169 F.3d at 1153; Shah v. Pan American World Services, Inc.,148 F.3d 84, 97-98 (2d Cir. 1998); Potter v. Delta Air Lines,98 F.3d 881, 885 (5th Cir.1996); Boehringer-Mannheim Diagnostics v. Pan Am. World,737 F.2d 456, 459 (5th Cir.1984). The conclusion that the CISG preempts state law also comports with the view of academic commentators on the subject. See William S. Dodge, Teaching the CISG in Contracts,50 J. Legal Educ. 72, 72 (March 2000) ("As a treaty the CISG is federal law, which preempts state common law and the UCC."); David Frisch, Commercial Common Law, The United Nations Convention on the International Sale of Goods, and the Inertia of Habit, 74 Tul. L.Rev. 495, 503-04 (1999) ("Since the CISG has the preemptive force of federal law, it will preempt article 2 when applicable.").Furthermore, the Court has considered Plaintiff's arguments and finds them unpersuasive. Plaintiff argues that the CISG is incomparable to preemption under the Warsaw Convention, because "the CISG leaves open the possibility of other, concurrent causes of action." (Reply Brief at 9.) This argument merely begs the question by assuming that the state law causes of action asserted by Plaintiff are properly brought. Based on the proper applicable legal analysis discussed above, the Court concludes that the pleaded state law claims are preempted.Plaintiff next claims that the CISG does not completely supplant state law, because the CISG is limited in scope to the formation of the contract and the rights and obligations of the seller and buyer arising from the contract. (Id.) Plaintiff's correct observation that the CISG does not concern the validity of the contract or the effect which the contract may have on the property in the goods sold fails to support Plaintiff's conclusion that the CISG does not supplant any area of state contract law. Although the CISG is plainly limited in its scope (15 U.S.C.App., Art. 4.), the CISG nevertheless can and does preempt state contract law to the extent that the state causes of action fall within the scope of the CISG. Compare Franchise Tax Bd.,463 U.S. at 22-23, 103 S.Ct. 2841 (holding that ERISA did not preempt the state tax collection suit at issue, because the state causes of action did not fall within the scope of § 502(a) of ERISA) and Metropolitan Life Ins.。
微软Teams移动版用户指南说明书
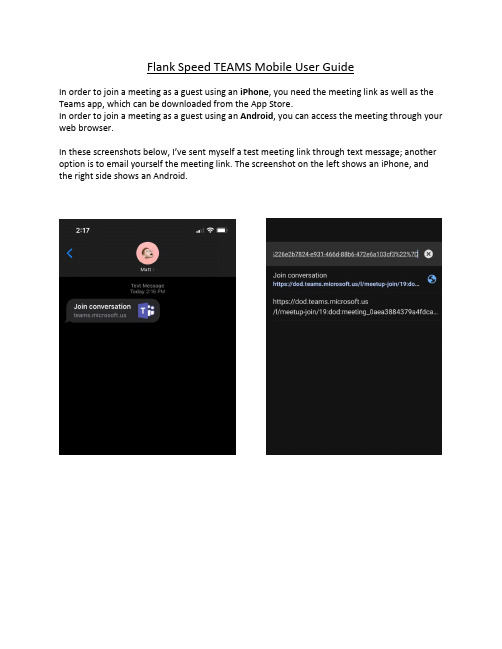
Flank Speed TEAMS Mobile User GuideIn order to join a meeting as a guest using an iPhone, you need the meeting link as well as the Teams app, which can be downloaded from the App Store.In order to join a meeting as a guest using an Android, you can access the meeting through your web browser.In these screenshots below, I’ve sent myself a test meeting link through te xt message; another option is to email yourself the meeting link. The screenshot on the left shows an iPhone, and the right side shows an Android.On iPhone - when you tap the link from your text messages or your email, you will go to the link in your browser. Your browser will automatically redirect to your Teams application, where you will get this screen:All you need to do o n this screen is hit the “Join as a guest” button, highlighted above.On Android, you’ll need to stay in your browser –so far, we’ve tested that the Edge browser works for this purpose –and use the “View desktop site” option, and then “Join on t he web instead”, like you would on a computer.When you get to this screen, type in your name as you’d like it to be displayed during the meeting. Keep in mind that you are joining a Navy meeting and you should actually write your first and last name so as to be identifiable. The meetin g will add “(Guest)” after your name.W hen you tap “Join meeting”, you wi ll be added in to the lobby, and someone will grant you access into the meeting.Once you’ve been added into the meeting, you can use all the same meeting options(mute/unmute, camera on/off, speakerphone, etc.) and you should be joined into the meeting, available on the go without a call-in number.As shown in the Android screenshot on the right – you will also have access to the meeting’s chat and participants list. If it doesn’t show up immediately, just tap the screen and the controls should show up.In lieu of personal email addresses, a member’s cell phone number as an email address can be utilized to send a Teams meeting invite. The link will appear in their respective text app vicethe personal email address app which will then take you either to the app (iPhone) or browser (Android) upon clicking the link.。
L'Amministrazione

CONVENZIONE SERVIZIO DI TESORERIATRAL’Amministrazione Comunale di Gattinara con sede in Gattinara, Corso Valsesia 119, in seguito denominata “Ente” rappresentata da …………………………. ........……............…………………………………....……...... dirigente del Settore Economico Finanziario del Comune di Gattinarae…..……………………………………………………………………………………indicazione della banca contraente (e della sua sede)in seguito denominato “Tesoriere” rappresentato/a da………………………… ……………………………………………............................... nella qualità di ................………………………………………………..………..……….premesso•che l’Ente è sottoposto alla disciplina di cui alla L. n. 720 del 29 ottobre 1984, come modificata dall’art.66, comma 11 della L.23.12.2000, n.388 e dall’art.77-quater, comma 7 del D.L.25.06.2008, n.112, da attuarsi con le modalità applicative di cui ai decreti del Ministro del tesoro del 26 luglio 1985 e del 22 novembre 1985;•che il Tesoriere, con riguardo alle disponibilità dell’Ente, deve effettuare, nella qualità di organo di esecuzione, le operazioni di incasso e di pagamento disposte dall’Ente;si conviene e si stipula quanto segueCAPO IDISPOSIZIONI GENERALIArt. 1Affidamento del servizio1. Il servizio di tesoreria viene svolto dal Tesoriere presso .…………………………..…….……......., nei giorni dal lunedì al venerdì e nel rispetto del seguente orario stabilito per tempo dal sistema bancario. Il servizio può essere dislocato in altro luogo solo previo specifico accordo con l'Ente.2. Il servizio di tesoreria, la cui durata è fissata dal successivo art. 3, viene svolto in conformità alla legge, agli statuti e ai regolamenti dell'Ente nonché ai patti di cui alla presente convenzione.Art. 2Oggetto e limiti della convenzione1. Il servizio di tesoreria di cui alla presente convenzione ha per oggetto il complesso delle operazioni inerenti la gestione finanziaria dell'Ente e, in particolare, la riscossione delle entrate ed il pagamento delle spese facenti capo all'Ente medesimo e dallo stesso ordinate, con l'osservanza delle norme contenute negli articoli che seguono, della normativa vigente, in particolare del D.Lgs. 267/2000; il servizio ha per oggetto, altresì, l'amministrazione di titoli e valori di cui al successivo art. 24 e le ulteriori attività definite agli articoli 25 e 26 della presente convenzione.2. Esula dall'ambito del presente accordo la riscossione delle "entrate patrimoniali e assimilate" nonché dei contributi di spettanza dell'Ente, affidata sulla base di apposita convenzione; è esclusa altresì la riscossione delle entrate tributarie affidata ai sensi dell’articolo 52 del D.Lgs. n. 446 del 15 dicembre 1997 la cui riscossione viene regolamentata da convenzione a latere, approvata in appendice e alle condizioni indicate in sede di offerta. In ogni caso, le entrate di cui al presente comma pervengono, nei tempi tecnici necessari, presso il conto di tesoreria.3. L’Ente può costituire in deposito presso il Tesoriere le disponibilità per le quali non è obbligatorio l’accentramento presso la Sezione di tesoreria provinciale dello Stato. A tal fine, presso il Tesoriere sono aperti appositi conti correnti bancari intestati all’Ente medesimo alle condizioni disciplinate dal successivo articolo 28.Art. 3Durata della convenzione1. La presente convenzione avrà durata dal 01/01/2010 al 31/12/2012Art. 4Esercizio finanziario1. L'esercizio finanziario dell'Ente ha durata annuale, con inizio il 1° gennaio e termine il 31 dicembre di ciascun anno; dopo tale termine non possono effettuarsi operazioni di cassa sul bilancio dell'anno precedente.CAPO IIORDINATIVI CARTACEIArt. 5Riscossioni1. Le entrate sono incassate dal Tesoriere in base ad ordinativi di incasso emessi dall'Ente su moduli appositamente predisposti, numerati progressivamente e firmati dal Dirigente del Servizio Finanziario o nel caso di assenza o impedimento, da persona abilitata a sostituirli ai sensi dei regolamenti vigenti dell’ente.2. Gli ordinativi di incasso devono contenere:•la denominazione dell'Ente;•la somma da riscuotere in cifre ed in lettere;•l'indicazione del debitore;•la causale del versamento;•la codifica di bilancio ( codice meccanografico, capitolo , articolo ), la voce economica ed il codice SIOPE;•il numero progressivo dell'ordinativo per esercizio finanziario, senza separazione tra conto competenza e conto residui;•l'esercizio finanziario e la data di emissione;•le indicazioni per l'assoggettamento o meno all'imposta di bollo di quietanza;•l'eventuale indicazione: "entrata vincolata". In caso di mancata indicazione, le somme introitate sono considerate libere da vincolo.3. A fronte dell'incasso il Tesoriere rilascia, in luogo e vece dell'Ente, regolari quietanze numerate in ordine cronologico per esercizio finanziario, compilate con procedure informatiche e moduli meccanizzati .4. Il Tesoriere accetta, anche senza autorizzazione dell'Ente, le somme che i terzi intendono versare, a qualsiasi titolo e causa, a favore dell'Ente stesso, rilasciando ricevuta contenente, oltre l'indicazione della causale del versamento, la clausola espressa “salvi i diritti dell'ente”. Tali incassi sono segnalati all'Ente stesso, il qualeemette i relativi ordinativi di riscossione entro quindici giorni e, comunque, entro il termine del mese in corso; detti ordinativi devono recare la seguente dicitura: "a copertura del sospeso n..………." o altra equivalente, rilevato dai dati comunicati dal Tesoriere.5. Con riguardo alle entrate affluite direttamente in contabilità speciale, il Tesoriere, appena in possesso dell'apposito tabulato consegnatogli dalla competente Sezione di tesoreria provinciale dello Stato, provvede a registrare la riscossione. In relazione a ciò l'Ente emette, nei termini di cui al precedente comma 4, i corrispondenti ordinativi a copertura.6. In merito alle riscossioni di somme affluite sui conti correnti postali intestati all'Ente e per i quali al Tesoriere è riservata la firma di traenza, il prelevamento dai conti medesimi è disposto esclusivamente dall'Ente mediante emissione di ordinativo cui è allegata copia dell'estratto conto postale comprovante la capienza del conto. Il Tesoriere esegue l'ordine di prelievo mediante emissione di assegno postale o tramite postagiro e accredita all’Ente l'importo corrispondente al lordo delle commissioni di prelevamento.Qualora il servizio postale lo consenta, i citati prelievi possono essere disposti nell’ambito del servizio “home-banking” offerto da bancoposta.In casi eccezionali e soprattutto al fine di evitare il ricorso da parte dell’Ente all’anticipazione di cassa, il Tesoriere è obbligato ad attivare su richiesta del Dirigente del Servizio Finanziario l’incasso delle somme disponibili su eventuali conti correnti postali, in difformità da quanto sopra esposto, semplicemente sulla base del saldo esistente sui suddetti c/c/p a una certa data, effettuando un unico movimento provvisorio in entrata che sarà cura dell’Ente regolarizzare nelle forme ordinarie entro i successivi 15 giorni.Il Tesoriere, comunque, anche in caso di mancato ordine di prelievo, provvede a cadenza quindicinale, al prelievo dai conti correnti postali delle somme sugli stessi depositati, dandone immediata comunicazione all’Ente per la regolarizzazione contabile.7. Le somme di soggetti terzi rivenienti da depositi in contanti effettuati da tali soggetti per spese contrattuali d’asta e per cauzioni provvisorie sono incassate dal Tesoriere contro rilascio di apposita ricevuta diversa dalla quietanza di tesoreria e trattenute su conto transitorio.8. Il Tesoriere non è tenuto ad accettare versamenti a mezzo di assegni di conto corrente bancario e postale nonché di assegni circolari non intestati al tesoriere. 9. Per le entrate riscosse senza ordinativo di incasso, le somme sono attribuite alla contabilità speciale fruttifera solo se dagli elementi in possesso del Tesoriere risulti evidente che trattasi di entrate proprie.10. Il Tesoriere, ai sensi di legge, non tiene conto di eventuali attribuzioni di valute da parte dell'Ente o di terzi.11. In alternativa alla soluzione descritta nei commi precedenti, l’Ente può, a sua richiesta, sostituire i titoli di entrata cartacei emessi dall' Ente per regolare le riscossioni di propria pertinenza con ordinativi informatici d’incasso denominati “reversali informatiche” che possiedono gli stessi contenuti degli ordinativi di riscossione emessi in forma cartacea. In tal caso si applicano anche le disposizioni contenute nel capo III della presente convenzione.Art. 6Pagamenti1. I pagamenti sono effettuati in base a mandati di pagamento, individuali o collettivi, emessi dall'Ente su moduli appositamente predisposti, numerati progressivamente per esercizio finanziario e firmati dal Dirigente del Servizio finanziario o nel caso di assenza o impedimento, da persona abilitata a sostituirli ai sensi dei vigenti regolamenti dell’ente.2. L'estinzione dei mandati ha luogo nel rispetto della legge e delle indicazioni fornite dall'Ente.3. I mandati di pagamento devono contenere:a)la denominazione dell'Ente;b)l'indicazione del creditore o dei creditori o di chi per loro è tenuto a rilasciarequietanza, con eventuale precisazione degli estremi necessari per l’individuazione dei richiamati soggetti nonché del codice fiscale o partita IVA ove richiesto. Qualora il beneficiario del mandato abbia costituito un procuratore per riscuotere o dar quietanza, l’atto di procura o la copia autenticata di esso dovrà essere rimesso al Settore Economico Finanziario dell’Ente cui spetta la predisposizione del mandato.I titoli di spesa dovranno essere intestati al creditore e recare l’indicazioneche sono pagabili con quietanza del creditore stesso o del suo procuratore.Nei mandati successivi si farà sempre menzione di quello a cui è stato unito l’atto di procura.Nel caso di assenza, minore età, interdizione, inabilitazione, fallimento o morte di un creditore tutta la documentazione relativa dovrà essere rimessa dagli interessati al Servizio dell’Ente che ha disposto la spesa. I titoli di spesa saranno intestati al rappresentante, al tutore, al curatore od all’erede del creditore unendo l’atto che attesti tale qualità al mandato di pagamento.L'atto stesso dovrà essere richiamato nei mandati successivi.c)l’ammontare della somma lorda - in cifre e in lettere - e netta da pagare;d)la causale del pagamento;e)la codifica di bilancio (codice meccanografico, capitolo e articolo), la voceeconomica, il codice SIOPE, nonché la corrispondente dimostrazionecontabile di disponibilità dello stanziamento sia in caso di imputazione alla competenza sia in caso di imputazione ai residui (castelletto);f)gli estremi del documento esecutivo in base al quale è stato emesso ilmandato di pagamento;g)il numero progressivo del mandato di pagamento per esercizio finanziario;h)l'esercizio finanziario e la data di emissione;i)l'eventuale indicazione della modalità agevolativa di pagamento prescelta dalbeneficiario con i relativi estremi;j)le indicazioni per l'assoggettamento o meno all'imposta di bollo di quietanza;k)l'annotazione, nel caso di pagamenti a valere su fondi a specifica destinazione: "Vincolato” o “pagamento da disporre con i fondi a specifica destinazione” o altra annotazione equivalente. In caso di mancata annotazione il Tesoriere non è responsabile ed è tenuto indenne dall'Ente in ordine alla somma utilizzata e alla mancata riduzione del vincolo medesimo;l)la data, nel caso di pagamenti a scadenza fissa il cui mancato rispetto comporti penalità, nella quale il pagamento deve essere eseguito;m)l'eventuale annotazione “esercizio provvisorio” oppure: “pagamento indilazionabile - gestione provvisoria”.4. Il Tesoriere, anche in assenza della preventiva emissione del relativo mandato, effettua i pagamenti derivanti da delegazioni di pagamento, da obblighi tributari, da somme iscritte a ruolo, da ordinanze di assegnazione - ed eventuali oneri conseguenti - emesse a seguito delle procedure di esecuzione forzata di cui all’art. 159 del D.Lgs. n. 267 del 2000, nonché gli altri pagamenti la cui effettuazione è imposta da specifiche disposizioni di legge; previa richiesta presentata di volta in volta e firmata dalle stesse persone autorizzate a sottoscrivere i mandati, la medesima operatività è adottata anche per i pagamenti relativi ad utenze, rate assicurative, altri pagamenti periodici o urgenti, al fine di evitare il pagamento di sanzioni ed interessi. Gli ordinativi a copertura di dette spese devono essere emessi entro quindici giorni e, comunque, entro il termine del mese in corso; devono, altresì, riportare l'annotazione: “a copertura del sospeso n. ................ “ o altra annotazione equivalente, rilevato dai dati comunicati dal Tesoriere.5. I beneficiari dei pagamenti sono avvisati direttamente dal Tesoriere dopo l'avvenuta consegna dei relativi mandati al Tesoriere stesso.6. Salvo quanto indicato al precedente comma 3, il Tesoriere esegue i pagamenti, per quanto attiene alla competenza, entro i limiti del bilancio ed eventuali variazioni approvate e rese esecutive nelle forme di legge e, per quanto attiene ai residui, entroi limiti delle somme risultanti da apposito elenco fornito dall'Ente.7. I mandati di pagamento emessi in eccedenza ai fondi stanziati in bilancio e, se approvato, nel PEG ed ai residui non devono essere ammessi al pagamento, non costituendo, in tal caso, titoli legittimi di discarico per il Tesoriere; il Tesoriere stesso procede alla loro restituzione all’Ente.8. I pagamenti sono eseguiti utilizzando i fondi disponibili ovvero utilizzando, con le modalità indicate al successivo art. 18, l'anticipazione di tesoreria deliberata e richiesta dall'Ente nelle forme di legge e libera da vincoli.9. Il Tesoriere non deve dar corso al pagamento di mandati che risultino irregolari, in quanto privi di uno qualsiasi degli elementi sopra elencati, non sottoscritti dalla persona a ciò tenuta, ovvero che presentino abrasioni o cancellature nell'indicazione della somma e del nome del creditore o discordanze fra la somma scritta in lettere e quella scritta in cifre. E' vietato il pagamento di mandati provvisori o annuali complessivi. Qualora ricorrano l'esercizio provvisorio o la gestione provvisoria, il Tesoriere esegue il pagamento solo in presenza delle relative annotazioni sul mandato o sulla distinta accompagnatoria degli ordinativi di incasso e dei mandati di pagamento.10. Il Tesoriere estingue i mandati secondo le modalità indicate dall'Ente specificando nella descrizione della ricevuta di pagamento sempre il numero e l’anno del documento contabile/fiscale quietanzato.In assenza di indicazione di una specifica modalità, il Tesoriere è autorizzato ad eseguire il pagamento ai propri sportelli o mediante l’utilizzo di altri mezzi equipollenti offerti dal sistema bancario. In caso di pagamenti da estinguersi con conto corrente postale non “premarcato” il Tesoriere è autorizzato ad eseguire bonifico sul conto corrente postale stesso per il tramite della rete interbancaria apponendo le relative commissioni.11. A comprova e discarico dei pagamenti effettuati, il Tesoriere raccoglie sul mandato o vi allega la quietanza del creditore, ovvero provvede ad annotare sui relativi mandati gli estremi delle operazioni effettuate, apponendo il timbro ‘pagato’. Il Tesoriere provvede, inoltre, ad annotare gli estremi del pagamento effettuato su documentazione meccanografica, da consegnare all'Ente unitamente ai mandati pagati, in allegato al proprio rendiconto.12. I mandati sono ammessi al pagamento, di norma, il primo giorno lavorativo bancabile successivo a quello della consegna al Tesoriere. In caso di pagamenti da eseguirsi in termine fisso indicato dall'Ente sull'ordinativo e per il pagamento delle retribuzioni al personale dipendente, l'Ente medesimo deve consegnare i mandati entro e non oltre il secondo giorno lavorativo bancabile precedente alla scadenza. 13. Il Tesoriere provvede ad estinguere i mandati di pagamento che dovessero rimanere interamente o parzialmente inestinti al 31 dicembre, commutandoli d'ufficio in assegni postali localizzati ovvero utilizzando altri mezzi equipollenti offerti dal sistema bancario o postale.14. L'Ente si impegna a non consegnare mandati al Tesoriere oltre la data del 15 dicembre, ad eccezione di quelli relativi ai pagamenti aventi scadenza perentoriasuccessiva a tale data e che non sia stato possibile consegnare entro la predetta scadenza del 15 dicembre.15. Eventuali commissioni, spese e tasse inerenti l'esecuzione di ogni pagamento ordinato dall'Ente ai sensi del presente articolo sono poste a carico dei beneficiari secondo quanto indicato nella offerta presentata dall’Istituto di credito, ad eccezione delle fattispecie disciplinate nel successivo articolo 7.Pertanto, il Tesoriere trattiene dall'importo nominale del mandato l'ammontare degli oneri in questione ed alla mancata corrispondenza fra le somme pagate e quella dei mandati medesimi sopperiscono formalmente le indicazioni - sui titoli, sulle quietanze o sui documenti equipollenti - degli importi dei suddetti oneri.16. Su richiesta dell'Ente, il Tesoriere fornisce gli estremi di qualsiasi pagamento eseguito, nonché la relativa prova documentale, entro il termine di giorni 2 (due). 17. Nel caso in cui i mandati siano da estinguersi mediante assegno circolare non trasferibile, il tesoriere dovrà, su richiesta scritta dell’Ente, rilasciare gli assegni circolari N.T. ( intestati ai beneficiari) nelle mani dell’incaricato da parte dell’Ente e il Tesoriere stesso rimarrà sollevato da qualsiasi responsabilità dovuta a smarrimento, mancata o errata consegna degli stessi da parte dell’Ente. La manleva di responsabilità dovrà essere esplicitamente indicata nella lettera di richiesta del Comune ove viene indicato l’incaricato al ritiro.18. Con riguardo ai pagamenti relativi ai contributi previdenziali, l'Ente si impegna,a produrre, contestualmente ai mandati di pagamento delle retribuzioni del proprio personale, anche quelli relativi al pagamento dei contributi suddetti, corredandoli della prevista distinta, debitamente compilata in triplice copia. Il Tesoriere, al ricevimento dei mandati, procede al pagamento degli stipendi ed accantona le somme necessarie per il pagamento dei corrispondenti contributi entro la scadenza di legge ovvero vincola l'anticipazione di tesoreria.19. Per quanto concerne il pagamento delle rate di mutuo garantite da delegazioni di pagamento, il Tesoriere, a seguito della notifica ai sensi di legge delle delegazioni medesime, effettua gli accantonamenti necessari, anche tramite apposizione di vincolo sull'anticipazione di tesoreria. Il Tesoriere è obbligato ad effettuare, alle scadenze, i pagamenti delle rate dei mutui, anche in assenza di mandato di pagamento, sulla base delle delegazioni di pagamento o degli avvisi che saranno tempestivamente trasmessi a cura del Servizio Finanziario.20. L’Ente, qualora intenda effettuare il pagamento mediante trasferimento di fondia favore di enti intestatari di contabilità speciale aperta presso la stessa Sezione di tesoreria provinciale dello Stato, deve trasmettere i mandati al Tesoriere entro e non oltre il primo giorno lavorativo bancabile precedente alla scadenza (con anticipo al secondo giorno ove si renda necessaria la raccolta di un ‘visto’ preventivo di altro pubblico ufficio), apponendo sui medesimi la seguente annotazione: “da eseguireentro il .……...………........ mediante giro fondi dalla contabilità di questo Ente a quella di ..……………….…................., intestatario della contabilità n.....…………..…..... presso la medesima Sezione di tesoreria provinciale dello Stato”.21. In alternativa alla soluzione descritta nei commi precedenti l’Ente può, a sua richiesta, sostituire i titoli di spesa cartacei emessi dall' Ente per regolare i pagamenti di propria pertinenza con ordinativi informatici di pagamento denominati “mandati informatici” che possiedono gli stessi contenuti degli ordinativi di pagamento emessi in forma cartacea. In tal caso si applicano anche le disposizioni contenute nel capo III della presente convenzione.Art. 7Particolari condizioni di incasso e di pagamento1.Il pagamento delle retribuzioni al personale dipendente dell’ente che abbia scelto come forma di pagamento l’accreditamento delle competenze stesse sia in conti correnti presso una qualsiasi filiale del Tesoriere, sia presso un Istituto di Credito diverso, verrà effettuato mediante una operazione di addebito al conto di tesoreria e di accredito ad ogni conto corrente con valuta compensata e senza alcuna spesa bancaria.I conti correnti in questione presso le filiali del Tesoriere potranno fruire, inoltre, di speciali condizioni definite in sede di gara.2.Gli accrediti a favore di terzi beneficiari su conti correnti bancari accesi su tutto il territorio nazionale presso il tesoriere non sono gravati da spese per bonifici. Gli accrediti a favore di terzi beneficiari su conti correnti bancari accesi su banche diverse dal tesoriere sono gravati da commissione nella misura contenuta nell’offerta dell’Istituto.Resta inteso:- che in caso di pagamenti plurimi nei confronti della stesso beneficiario, da eseguirsi nella stessa data, sarà addebitata una unica commissione.- che i pagamenti nei confronti di istituti scolastici ed altre Amministrazioni Pubbliche statali, regionali, provinciali o comunali sono esenti da commissioni.3.Il Tesoriere si impegna ad attivare la riscossione delle entrate patrimoniali dell’Ente a mezzo procedura R.I.D., cioè l’addebito diretto nel conto corrente dell’utente, anche presso istituti diversi da quello del Tesoriere. La procedura R.I.D. dovrà essere senza spese per l’Ente.La commissione R.I.D. per ogni singolo addebito è pari a 0 (zero).Art. 8Trasmissione di atti e documenti cartacei1. Gli ordinativi di incasso e i mandati di pagamento sono trasmessi dall'Ente al Tesoriere, accompagnati da distinta in doppia copia numerata progressivamente e debitamente sottoscritta dagli stessi soggetti abilitati alla firma degli ordinativi e dei mandati, di cui una, vistata dal Tesoriere, funge da ricevuta per l'Ente. La distinta deve contenere l'indicazione dell'importo dei documenti contabili trasmessi, con la ripresa dell'importo globale di quelli precedentemente consegnati.2. L’Ente, al fine di consentire la corretta gestione degli ordinativi di incasso e dei mandati di pagamento, comunica preventivamente le firme autografe, le generalità e qualifiche delle persone autorizzate a sottoscrivere detti ordinativi e mandati, nonché ogni successiva variazione. Il Tesoriere resta impegnato dal giorno lavorativo successivo al ricevimento della comunicazione.3. L’Ente trasmette al Tesoriere lo statuto e il regolamento di contabilità nonché le loro successive variazioni.4. All'inizio di ciascun esercizio, l'Ente trasmette al Tesoriere:a)il bilancio di previsione, il Piano esecutivo di Gestione, ove approvato e gliestremi delle delibere di approvazione e della loro esecutività;b)l'elenco dei residui attivi e passivi, sottoscritto dal dirigente del SettoreEconomico Finanziario ed aggregato per intervento.5. Nel corso dell'esercizio finanziario, l'Ente trasmette al Tesoriere:a)le deliberazioni esecutive relative a storni, prelevamenti dal fondo di riservaed ogni variazione di bilancio e del PEG, ove approvato;b)le variazioni apportate all'elenco dei residui attivi e passivi in sede diriaccertamento.CAPO IIIORDINATIVI INFORMATICIArticolo 9Ordinativo informatico1. L’ente può adottare l'ordinativo informatico, come definito dai successivi articoli,a tutti gli effetti di legge, in sostituzione degli ordinativi di riscossione e di pagamento cartacei, quale documento ufficiale per ordinare al Tesoriere la riscossione e il pagamento di somme iscritte nel proprio bilancio di previsione. In tal caso l'ordinativo informatico possiede gli stessi contenuti degli ordinativi di riscossione e di pagamento emessi in forma cartacea. Restano validetutte le disposizioni contenute nel precedente capo II in quanto compatibili con l’ordinativo informatico.2. Ai sensi dell'articolo 1 del decreto legislativo 7 marzo 2005, n. 82 e dell'articolo 10 del DPR 28 dicembre 2000, n. 445, gli ordinativi informatici sono documenti informatici che costituiscono la rappresentazione informatica di atti, fatti o dati giuridicamente rilevanti, soddisfano il requisito legale della forma scritta hanno efficacia probatoria ai sensi dell'articolo 2712 del Codice civile.3. L'ordinativo informatico è sottoscritto con firma digitale dal Dirigente del Servizio Finanziario o in sua assenza da persona abilitata a sostituirlo ai sensi dei vigenti regolamenti.4. Agli ordinativi informatici si applicano le disposizioni contenute nei DPR 28 dicembre 2000, n. 445, nel decreto legislativo 7 marzo 2005, n. 82 in quanto compatibili con le vigenti norme ed i principi dell'ordinamento contabile e finanziario.5. Gli ordinativi informatici possono essere individuali o collettivi, ossia ordinare la riscossione di somme nei confronti di uno o più soggetti ed ordinare il pagamento di somme a favore di uno o più soggetti.6. Gli ordinativi di riscossione sono denominati "reversali informatiche"; gli ordinativi di pagamento sono denominati "mandati informatici ''.Articolo 10Firma digitale1. Con l'apposizione della firma digitale può essere sottoscritto un singolo ordinativo informatico oppure più ordinativi informatici. In ogni caso, il sistema di gestione informatica dei documenti, come definito all'art 1 del Testo Unico approvato con Decreto del Presidente della Repubblica 28 dicembre 2000 n. 445, deve rappresentare senza ambiguità gli elementi di ciascun ordinativo informatico cui la firma si riferisce.2. Il complesso dei dati firmati riferiti a uno o più ordinativi informatici viene definito "flusso".3. Gli ordinativi informatici trasmessi al Tesoriere e le relative ricevute sono firmate con l'apposizione della firma digitale, come definita dal Decreto del Presidente della Repubblica 28 dicembre 2000, n. 445.4. La firma digitale può essere apposta esclusivamente mediante un dispositivo sicuro di firma contenente un certificato rilasciato da un soggetto che deve essere scelto tra i certificatori attivi ricompresi nell'Elenco pubblico conservato edaggiornato dal Centro Nazionale per l'informatica nella Pubblica Amministrazione (CNIPA).Articolo 11Trasmissione ordinativi informatici e rilascio ricevute1. Le modalità di scambio dei documenti informatici tra Ente e Tesoriere sono gestite avvalendosi di diversi strumenti e funzionalità. Tali strumenti possono prevedere:a)che più disposizioni e/o ricevute dei medesimi siano aggregate ai finitrasmissivi in flussi;b)che i flussi tra Ente e Tesoriere siano scambiati attraverso la Rete Internet.2. Gli ordinativi informatici firmati digitalmente dal Dirigente del Servizio Finanziario o in sua assenza da persona abilitata a sostituirlo ai sensi dei vigenti regolamenti, sono successivamente trasmessi al Tesoriere.3. Per ciascun flusso/documento trasmesso, il Tesoriere rilascia ricevuta di “conferma ricezione flusso/documento” attestante che il flusso/documento è arrivato nel perimetro della Banca. La procedura dovrà, inoltre, prevedere soluzioni riepilogative che permettano di visualizzare tutte le ricevute di “conferma ricezione flusso/documento”.4. Per ciascun ordinativo informatico contenuto in un flusso trasmessogli, il Tesoriere rilascia i messaggi di ritorno ed in particolare le seguenti ricevute:a)ricevuta attestante che l'ordinativo è stato acquisito dal Tesoriere ;b)ricevuta attestante che l'ordinativo è stato caricato in tesoreria;c)ricevuta attestante che l'ordinativo non è caricato in tesoreria,contenente l'indicazione del motivo del rifiuto;d)ricevuta attestante che l'ordinativo è stato eseguito da parte del Tesoriereed attesta l'avvenuto pagamento o riscossione;e)ricevuta attestante che l’ordinativo non è stato eseguito da parte delTesoriere, contenente l'indicazione del motivo del rifiuto.Dette comunicazioni dovranno essere visibili in allegato a ciascun ordinativo informatico ed accessibili da parte del Dirigente del Servizio Finanziario.5. L'elaborazione dei flussi da parte del Tesoriere e delle disposizioni in essi contenute, avviene ogni giorno lavorativo. Nel corso dell'elaborazione il Tesoriere predispone le ricevute di cui ai precedente comma 3 e le mette a disposizione dell’Ente secondo le modalità previste dal comma 4.Articolo 12Annullamento, variazione e rettifica ordinativo informatico。
PressCAD常用指令之快捷键

PressC AD常用指令之快捷键PRESSC AD绘图之绘图指令:A(arc)圆弧C(circle)圆D O(donut)圆环DT单行文字EL(ellips e)椭圆 H(hatch)剖面线L(line)直线ML(MLINE)多线MT(MTEXT)多行文本PL(pline)复线,多段线矩形P O(point)点REG(REGION)面域 POL(polygo n)正多边形PAR平行线REC/B(rectan g) RA Y射线SPL(SPLINE)样条曲线T(text)文字XL(XLINE)放射线PressC AD绘图之捕捉功能键:APPINT捕捉到外观交点CEN捕捉到圆心EXT捕捉到延长线END捕捉到端点FRO正交偏移捕捉FP圆角交点INT捕捉到交点INS捕捉到插入点MID捕捉到中点NOD捕捉到节点NEA捕捉到最近点NON无捕捉(禁用捕捉) OSNAP对象捕捉设置PER捕捉到垂足AR捕捉到平行线QUA捕捉到象限点TAN捕捉到切点ZNDP捕捉到端点SN(SNAP)捕捉栅格尺寸标注命令:D(dimsty le)标注样式DDI(DIMDIA METER)直径标注DA(dim arrows)标注箭头设定DAL(DIMALIGNED)对齐标注DAN(DIMANGULAR)角度标注DBA(DIMBASELINE)基线标注DCE(DIMCEN TER)中心标注DCO(DIMCON TINUE)连续标注DRA(DIMRAD IUS)半径标注DE调整尺寸线与文字的位置DLI(DIMLINEAR)线性标注D1/DL尺寸共线DOR(DIMORD INA TE)点标注DOV(DIMOVERRIDE)替换标注系统变量DED(DIMEDIT)编辑标注DG(dim gap)标注文字与标注线的距离DH(dim height)标注文字的高度ED修改标注XD坐标标注LE(QLEADER)快速引出标注ST(STYLE)文字样式TOL(TOLERA NCE)标注形位公差PRESSC AD绘图之编辑指令:AR(array)阵列AA(AREA)求面积周长AL(ALIGN)对齐A TT(A TTDEF)属性定义A TE(A TTEDIT)编辑属性ADC, *ADCENTER(设计中心“Ctrl+2”)BR(break)打断BO(BOUNDA RY)边界创建,包括创建闭合多段线和面域CO(copy)复制CHA(chamfe r)倒直角CH/MO(chang)/Ctrl+1修改特性(线性、文字高度等)DI(dist)测量距离(分析,非标注)D修改,调整 DIV(divide)等分(块)DS(DSETTINGS)设置极轴追踪 E(erase),DEL键删除ED(ddedit)文字编辑EXT(EXTEND)延伸EXIT(QUIT)退出EXP(EXPORT)输出其它格式文件 F(fillet)倒圆角 FF/PF(pfille t)快速倒圆角H(BHA TCH)填充HE编辑填充I(insert)插入图块MP(IMPORT)输入文件IN交集J合并直线(即合并前两直线必须在同一条直线上,合并后是直线,而非折线)LEN(length en)延长 LE(qleade r)快速引线LA (LAYER)图层操作LI(LIST)显示图形数据信息LT(LINETY PE)线形LTS(LTSCALE)线形比例LW(LWEIGH T)线宽MA(matchp rop)性质复制(相当于格式刷) ME等分M(move)移动MI(mirror)镜像OPTION S(自定义CAD设置)O(offset)偏移OS(OSNAP)设置捕捉模式O P,PR PRINT, *PLOT(打印)PU(PURGE)清除垃圾PE(PEDIT)编辑多边线PAN平移PRE(PREVIE W)打印预览 RO(rotate)旋转R(REDRAW)重新生成RE(regen)重生REN(RENAME)重命名REG面域REV二维旋转成三维SC(scale)比例缩放SU差集SKETCH徒手画线S(strech)拉展(单向伸缩,以交叉窗口或交叉多边形选择要拉伸的对象)TO(TOOLBA R)工具栏TR(trim)修剪UN(UNI)并集 X(explod e)炸开V(VIEW)命名视图UN(UNITS)图形单位W(WBLOCK)定义块文件3DPAN三维平移3DZOON三维缩放3DORBI T三维动态观察3DCORB IT三维连续观察PressC AD绘图之好用功能:AJ(autojo in)自动串接ADJ小数调整BF料表清单注解B创建临时图块CHL图层转换COL(COLOR)设置颜色CR(copy2)旋转复制CCW顺时针该逆时针CW逆时针改顺时针CP(ch_par t)零件处理CCT清楚标签CT(copy_t ags)标签复制CT2(ch_tag s)标签更改CT1(ch_tag1)尺寸标签更改CCC/EEE/MMM对各分离模板上的图元予以复制,删除,移动DF入子外形DM(pdel dim)删除尺寸DDD路径模拟DP图元分离ET(pdel text)删除文字EF删除图框E回车ALL回车全部删除FG对各分离模板上新增图元重新注解K(dup)删重复线II(In_Fra me)插图框LL(layer1_I)建模具ML(pcrosl in)模具中心线MF移动图框NC转程式OP(p_offe st)单边偏位PD(pdim)尺寸标注PD2(p_dim2)注解输入PW空间线整理PT串修PM(pchamf er)快速倒直角PX(PBOX)备料板设定QD快速修尺寸标注QS快速拉展QR尺寸反向QQ图层全开SM筛选SD查复线方向SCC比例缩放图框VER变更版本说明WID资料查询WN线割注解WD起割孔标注W创建永久图块UCS三维坐标ROTA TE3D三维旋转MIRROR3D三维镜像3A三维阵列SURFTA B曲面网格TXTEXP分解文字常用CTRL快捷键【CTRL】+1 *PROPER TIES(修改特性):【CTRL】+2 *ADCENTER(设计中心)【CTRL】+O *OPEN(打开文件)【CTRL】+N、M *NEW(新建文件)【CTRL】+P *PRINT(打印文件)【CTRL】+S *SA VE(保存文件)【CTRL】+Z *UNDO(放弃)【CTRL】+X *CUTCLIP(剪切)【CTRL】+C *COPYCLIP(复制)【CTRL】+V *PASTECLIP(粘贴)【CTRL】+B *SNAP(栅格捕捉)【CTRL】+F *OSNAP(对象捕捉)【CTRL】+G *GRID(栅格)【CTRL】+L *ORTHO(正交)【CTRL】+W *(对象追踪)【CTRL】+U *(极轴)【CTRL】+P *(打印)【CTRL】+Z *(撤销)=U回车。
2021-2022学年湖南省湘潭市全国计算机等级考试网络安全素质教育真题(含答案)

2021-2022学年湖南省湘潭市全国计算机等级考试网络安全素质教育真题(含答案) 学校:________ 班级:________ 姓名:________ 考号:________一、单选题(10题)1.计算机安全属性不包括()。
A.保密性B.完整性C.可用性服务和可审性D.语义正确性2.用来把主机连接在一起并在主机之间传送信息的设施,被称为()。
A.路由器B.资源子网C.通信子网D.主机3.在密钥的分类中,用于对传送的会话或文件密钥进行加密时所采用的密钥是()。
A.基本密钥B.密钥加密密钥C.会话密钥D.主机主密钥4.通过为系统的关键部件设置冗余备份、并在发生故障时通过自动功能隔离和自动功能转移使系统不间断地工作的计算机是()。
A.个人计算机B.容错计算机C.图形工作站D.家用计算机5.下面关于系统还原的说法错误的是()。
A.系统还原不是重新安装新的系统B.系统还原无法清除病毒C.系统还原点可以自动生成也可以由用户设定D.系统还原点必须事先设定6.下面专门用来防病毒的软件是()。
A.诺顿B.天网防火墙C.DebugD.整理磁盘7.手机发送的短信被让人截获,破坏了信息的()。
A.机密性B.完整性C.可用性D.真实性8.假冒破坏信息的()。
A.可靠性B.可用性C.完整性D.保密性9.下列选项中不属于网络安全的问题是()。
A.拒绝服务B.黑客恶意访问C.计算机病毒D.散布谣言10.使用大量垃圾信息,占用带宽(拒绝服务)的攻击破坏的是()。
A.保密性B.完整性C.可用性D.可靠性二、多选题(10题)11.虚拟专用网络(Virtual Private Network,VPN)是在公用网络上建立专用网络的技术,整个VPN网络的任意两个节点之间的连接并没有传统专网所需的端到端的物理链路,而是架构在公用网络服务商所提供的网络平台。
VPN的特点有:()。
A.安全性高B.服务质量保证C.成本高D.可扩展性12.国家对公共通信和信息服务、能源、交通、水利、金融、公共服务、电子政务等重要行业和领域,以及其他一旦遭到破坏、丧失功能或者数据泄露,可能严重危害()的关键信息基础设施,在网络安全等级保护制度的基础上,实行重点保护。
CA API Gateway 虚拟应用程序入门说明书

CA API Gateway – Virtual ApplianceGetting Started ContentsIntroduction (1)Requirements (2)Starting the Virtual Appliance (2)Configuring the Virtual Appliance (3)Installing the Gateway License (8)Next Steps (9)Getting Assistance (9)Troubleshooting Password Issues (9)IntroductionThe CA API Gateway – Virtual Appliance provides the power of the CA API Gatewayconventional hardware appliance with the flexibility of a software application.This document helps you get the Virtual Appliance up and running on your personalworkstation as quickly as possible.For complete information on using the Virtual Appliance and its accompanying PolicyManager, refer to the Gateway online documentation located at /Gatewayand download the CA API Gateway Administrators Manual from the CA APIManagement Customer Support site.If you require further assistance, send an email to ******************.Copyright © 2015 CA. All rights reserved. All trademarks, trade names, service marks and logos referenced herein belong to their respective companies. This document is for your informational purposes only. To the extent permitted by applicable law, CA provides this document “As Is” without warranty of any kind, including, without limitation, any implied warranties of merchantability or fitness for a particular purpose, or non-infringement. In no event will CA be liable for any loss or damage, direct or indirect, from the use of this document including, without limitation, lost profits, business interruption, goodwill or lost data, even if CA is expressly advised of such damages. Document last updated:RequirementsThe CA API Gateway Virtual Appliance will run under any recent version of VMware®Workstation or vSphere.For a complete list of requirements, refer to “Requirements and Compatibility” in theCA API Gateway online documentation located at: /Gateway. Starting the Virtual Appliance1.Follow the applicable instructions to start the Virtual Appliance:•To start the ESXi image: Select File> Deploy OVF Template and thennavigate to the Virtual Appliance image file (*.ova).•To start the Workstation image: Select File> Open and then navigate to theVirtual Appliance image file (*.ova).2.Verify the following settings:a.Select Edit virtual machine settings and then make sure the Hardware tab isvisible.b.Select Memory from the list and make sure the slider is showing at least 768MB.c.Select Network Adapter from the list and choose the appropriate option:•If the Gateway will be connected to a physical network or accessed fromexternal systems, choose Bridged.•If external access is not required or the host system is not connected toa network, select NAT or Host Only. Select NAT if you are running theVirtual Appliance for evaluative or training purposes.d.Click [OK].3.If using the ESXi Server, you must map the virtual network interface to theappropriate virtual network switch for your configuration.4.Click Power on this virtual machine to start the Virtual Appliance. Allow a fewmoments for the boot process to complete.Once the Virtual Appliance has started, proceed to Configuring the Virtual Appliancebelow.Technical Tip: If a “[FAILED]” message appears during the VMware Toolsinitialization process, check the irqbalance daemon.Configuring the Virtual ApplianceTip: The example settings shown are designed to get your Virtual Applianceup and running as quickly as possible for evaluation purposes. For use inother environments, see the CA API Gateway online documentation locatedat /Gateway.for a detailed description of each setting.Once the image boot process has completed, you can configure the Virtual Appliance.1.When prompted to log in, type ssgconfig for the user name and 7layer for thepassword (both are case sensitive).2.After your first login, you will be prompted to change the password for ssgconfig.Follow the prompts to create a new password. Tip: For evaluation purposes, youcan use L7Secure$0@ (“0” = zero).The Gateway main menu appears once you are successfully logged in.Welcome to the SecureSpan GatewayThis user account allows you to configure the applianceWhat would you like to do?1)Configure system settings2)Display Layer 7 Gateway configuration menu3)Use a privileged shell (root)4)Change the Master Passphrase5)Display Remote Management configuration menu6)Manage HSM7)Display Enterprise Service Manager configuration menu8)Display Patch Management MenuR)Reboot the SSG appliance (apply the new configuration)X)Exit (no reboot)Please make a selection: 1Figure 1: Gateway main menu3.Select 3 (Use a privileged shell). This opens a command prompt for root access.4.Type 7layer as the current password. Upon first access to this shell, you will beprompted to change the password for the root user. Create a new password thatadheres to “Password Rules” under “Troubleshooting Password Issues” in theGateway online documentation. Tip: You can use the same L7Secure$0@password as shown above.5.If evaluating the Virtual Appliance, you may want to reset the passwords back to7layer to make it easier to remember. Tip: For non-evaluation uses of theGateway, it is not advisable to weaken the password strength in this manner.To reset the root password:a.Type passwd.b.Type 7layer and ignore the “Bad Password” warning.c.Type 7layer again to confirm. The password is changed.To reset the ssgconfig password:a.Type passwd ssgconfig.b.Type 7layer and ignore the “Bad Password” warning.c.Type 7layer again to confirm. The password is changed.6.If evaluating the Virtual Appliance, type ifconfig and then make a note of theGateway’s dynamically assigned IP address on the NAT network and the subnet mask. See Figure 2.Figure 2: ifconfig outputNote: By default, the eth0 interface on the Gateway is configured forDHCP. For evaluation purposes, you will change eth0 to use a static IPaddress.7.If evaluating the Virtual Appliance, you must edit the hosts file to add the fullyqualified host name of the Gateway because the name will likely not beregistered with any configured DNS server.Tip: You must also modify the hosts file if you want the Gateway to connect to any other system by host name rather than IP address.a.Type vi /etc/hosts (space after “vi”) to load the hosts file into the editor.Table 1 lists some basic editing commands for the vi editor.Table 1: Basic vi commandsTo… Do this…Enter insert mode Press i.Create a new line Use the arrows to position the cursor at the endof the last line, and then press [Enter].Type content into the line Be sure to separate the IP address from the hostname and short name using one or more spaces(the actual number of spaces does not matter).Exit insert mode Press [Esc].Save and exit vi Type :wq and then press [Enter].Exit without saving Type :q! and then press [Enter].b.Add the IP address and hostname that you plan to assign to this gatewayduring network configuration (described later).For example, this inet address was noted in our example in step 6 above: 192.168.146.128 (dynamically assigned address)This means our static IP address must begin with “192.168.146”—in thisexample, we will use 192.168.146.200. Figure 3 shows a sample hosts filein the vi editor, using the fictitious hostname “” followed bythe short name “learn”.Figure 3: Editing /etc/hostsc.Save the changes and exit vi, and then type exit to return to the main menu.8.Select option 1 (Configure system settings) from the main menu9.Select option 1 (Configure networking and system time settings) to beginnetwork configuration.a.Enter 1 to configure the eth0 interface and then enter y to enable theinterface.b.Enter y to configure IPv4 networking.c.Under boot protocol, select static and then:•For the IPv4 address, type the IP address that was added to the/etc/hosts file in step 7b above. For example: 192.168.146.200.•For the default IPv4 gateway, type the VMware NAT network’s default IPv4 gateway. Normally this is the x.x.x.2 address on the NAT network.Although presented as optional, it is recommended that you enter one inthis environment as the default IPv4 address will also be used as theDNS server address later. For example: 192.168.146.2.Tip: Another way to locate the default Gateway is to run the “route –n”command. Look for the destination “0.0.0.0.” and the correspondingentry in the Gateway column is what you need.•For the netmask, type the VMware NAT network’s subnet mask that was noted in step 6 above. For example: 255.255.255.0.d.Enter n to skip configuring IPv6 networking.e.Enter n to skip configuring another interface.f.Enter n to skip configuring a default IPv4 gateway and interface.g.If prompted to configure a default IPv6 gateway and interface, type n.Tip: To learn more about default gateways, see “Determining Whether aDefault Gateway is Necessary” in the Layer 7 Installation and MaintenanceManual.h.Type the fully qualified hostname that was added to the Gateway’s/etc/hosts file. For example: .i.When prompted for the DNS server IP address, you may leave this blank ifyou wish to receive the name servers and search domains via DHCP.j.Enter y to configure the time zone, and then select your time zone from the lists presented.k.Enter n to skip synchronizing the Virtual Appliance with an NTP server.Tip: Time synchronization is an essential system setup step for clusteringand replay attack prevention, but it can be omitted for the purposes ofevaluating the Virtual Appliance. If you have an NTP server available, you cantype y and specify the NTP server IP addresses. The image comespreconfigured with the servers.l.Carefully review the configuration settings you are about to apply. If everything is correct, enter y to continue.If you are not ready to apply the settings, press < to return to a previous stepor type quit to exit the configurator.m.Review the results. You should see a message stating that the configuration was successfully applied. Press [Enter] to exit the configurator.10.When the network menu reappears, select option X to return to the main menu,select option R to reboot the Virtual Appliance, and type y to confirm. Rebooting may take a few minutes to complete.11.Log in as the ssgconfig user (see step 1), and then select option 2 (Display Layer7 Gateway configuration menu) from the main menu. The configuration menu inFigure 4 is displayed.This menu allows you to configure the Layer 7 Gateway application What would you like to do?1)Upgrade the Layer 7 Gateway database2)Create a new Layer 7 Gateway database3)Configure the Layer 7 Gateway4)Change the Layer 7 Gateway cluster password5)Delete the Layer 7 Gateway6)Display the current Layer 7 Gateway configuration7)Manage Layer 7 Gateway status8)Reset Admin passwordX)ExitPlease make a selection: 1Figure 4: Gateway configuration menu12.Select option 2 (Create a new Layer 7 Gateway database) and then follow Table2 to complete each step.Note: Once the new Gateway database is created, you can no longeruse option 2. To modify the configuration afterwards, select option 3(Configure the Layer 7 Gateway). To delete the Gateway configurationand start over, select option 5 (Delete the Layer 7 Gateway).Table 2: Creating a new Gateway databaseStep DescriptionSet Up the Gateway Database 1.Press [Enter] to set up the database connection.2.Press [Enter] to accept localhost as the hostname.3.Press [Enter] to accept the default port 3306.4.Press [Enter] to accept the default database name ssg.5.Press [Enter] to accept the default database username gateway.6.Type the password for the database user and then retype to confirm.7.Press [Enter] to accept the default administrative database username root.8.Type the administrative database password.Set Up the Gateway Failover Database •Press [Enter] to skip setting up a Gateway Failover Database.Note: Database failover connections are used in multi-Gateway clusters. For evaluation purposes, a single Gateway is deployed and failover does not apply.Set Up the Policy Manager Administration This step sets up the account for the Policy Manager administrator (i.e., the “super user”).1.Type the user name for the administrator. For example: admin.2.Type the password for the administrator and then retype to confirm. For example:7layer.Set Up the Gateway Cluster This step sets up the Gateway cluster. Note: This single Virtual Appliance isconsidered to be a “cluster” of one.1.Press [Enter] to accept the cluster hostname offered as the default. Note that thecluster host cannot be changed once entered.2.Type the passphrase to protect the cluster and then retype to confirm. Forexample: 7layer.Set Up the Gateway Node •Press [Enter] to enable the node. This activates the Virtual Appliance whenconfiguration is complete. Tip: It may take a few minutes for the node to be fullyup and running.Configuration Summary Carefully review the configuration settings you are about to apply. If everything iscorrect, press [Enter] to apply the settings.If you are not ready to apply the settings, press < to return to a previous step or typequit to exit the wizard.Configuration Results The configuration results show either:•Success: Press [Enter] to return to the Configure Layer 7 Gateway menu. Enter Xto exit to the main menu.•Errors encountered: Copy and paste the log messages from the command windowStep Descriptioninto a text file. Analyze the errors and run the wizard again. If you requireassistance, email ******************.13.Enter x to return to the Gateway main menu, then select option R to reboot theVirtual Appliance and then type y to confirm.You will now install the Gateway license using the Policy Manager. Installing the Gateway LicenseOnce the Virtual Appliance is configured, the next step is to install the license file.This is done using the CA API Gateway – Policy Manager, which provides a graphicalinterface for managing the Virtual Appliance.The Policy Manager is available in two form factors:•As a browser-based application that can run on any supported Web browser. Noinstallation or additional download are required if using this form factor.•As a desktop client for optimal performance. This form factor is a separatedownload. For installation instructions, see “Install and Upgrade the PolicyManager” in the CA API Gateway Administrators Guide.Note: The browser and desktop versions of the Policy Manager have nearlyidentical functionality. The differences between the two are summarizedunder “Policy Manager Browser Client” in the Gateway online documentationlocated at /Gateway.To install the Gateway license:1.Start the Policy Manager:•Browser client: Load the URL:https://<gatewayHostName>:8443/ssg/webadminwhere “<gatewayHostName>” is the hostname entered in the “Set Up theGateway Cluster” step of Table 2.Tip: You may see some security prompts when you start the PolicyManager for the first time in a browser. Both Internet Explorer andFirefox will present a series of warnings and authenticationchallenges. See “Start the Policy Manager” in the Gateway onlinedocumentation for detailed instructions on how to respond to theseprompts.•Desktop client:1)Run the Policy Manager. The Login dialog appears.2)For the User Name and Password, use the values in the “Set Up thePolicy Manager Administration” step of Table 2.3)For the Gateway, use the hostname entered in the “Set Up the GatewayCluster” step of Table 2.2.Click [Yes] when prompted to view the license manager.3.Click [Install License] and then locate the license file provide by Layer 7.4.Click [I Agree] at the License Agreement; it may take a moment for the license tofully register. The license is installed when you see “Valid” next to License Status.5.Click [Close] to return to the Policy Manager interface.Next StepsNow that the Gateway is installed and the Policy Manager is up and running, you canbegin to publish services and create policies. For more information, see “VirtualAppliance Tutorials” in the CA API Gateway online documentation located at:/Gateway.Getting AssistanceComplete documentation for the CA API Gateway and the Policy Manager is availablefrom any Web-enabled device by visiting /Gateway. For your convenience,any portion of the online documentation can be saved as ePUB or PDF files.If you require further assistance, email CA Support at .Troubleshooting Password IssuesMost common password difficulties can be resolved by following the steps under“Troubleshoot Password Issues” in the CA API Gateway online documentation locatedat /Gateway. If these steps do not resolve your issue, email CA Support.。
加密与CA证书的创建

加密与CA证书的创建1、在 CentOS7 中使⽤ gpg 创建 RSA ⾮对称密钥对#通过gpg --gen-key命令⽣成密钥对[root@localhost ~]# gpg --gen-keygpg (GnuPG) 2.0.22; Copyright (C) 2013 Free Software Foundation, Inc.This is free software: you are free to change and redistribute it.There is NO WARRANTY, to the extent permitted by law.Please select what kind of key you want:(1) RSA and RSA (default)(2) DSA and Elgamal(3) DSA (sign only)(4) RSA (sign only)Your selection?RSA keys may be between 1024 and 4096 bits long.What keysize do you want? (2048)Requested keysize is 2048 bitsPlease specify how long the key should be valid.0 = key does not expire<n> = key expires in n days<n>w = key expires in n weeks<n>m = key expires in n months<n>y = key expires in n yearsKey is valid for? (0) 3650Key expires at Wed 04 Sep 2030 05:16:47 PM CSTIs this correct? (y/N) yGnuPG needs to construct a user ID to identify your key.Real name: mageduEmail address: root@Comment:You selected this USER-ID:"magedu <root@>"Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? oYou need a Passphrase to protect your secret key.We need to generate a lot of random bytes. It is a good idea to performsome other action (type on the keyboard, move the mouse, utilize thedisks) during the prime generation; this gives the random numbergenerator a better chance to gain enough entropy.gpg: /root/.gnupg/trustdb.gpg: trustdb createdgpg: key FFC9AA26 marked as ultimately trustedpublic and secret key created and signed.gpg: checking the trustdbgpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust modelgpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1ugpg: next trustdb check due at 2030-09-04pub 2048R/FFC9AA26 2020-09-06 [expires: 2030-09-04]Key fingerprint = 9DED B2B6 51CC B789 163A CF14 539F 3228 FFC9 AA26uid magedu <root@>sub 2048R/37CA53C3 2020-09-06 [expires: 2030-09-04]#查看⽣成的公钥⽂件[root@localhost ~]# gpg --list-keys/root/.gnupg/pubring.gpg------------------------pub 2048R/FFC9AA26 2020-09-06 [expires: 2030-09-04]uid magedu <root@>sub 2048R/37CA53C3 2020-09-06 [expires: 2030-09-04]#导出公钥到liu.pubkey[root@localhost ~]# gpg -a --export -o liu.pubkey[root@localhost ~]# lsanaconda-ks.cfg liu.pubkey[root@localhost ~]# cat liu.pubkey-----BEGIN PGP PUBLIC KEY BLOCK-----Version: GnuPG v2.0.22 (GNU/Linux)mQENBF9UqScBCADpUEOg2Mt94JDSnvmci/i/zB7hflwM+jn+FlPCU4baRDqIkdteuwkF5CqItIU+IKvd8vjI2VNuNIYlrywwp2R7fd3tnnza2bbXcM5Z8Kci8xx4TeIJh13dwwE48CXaFWy1PcA01ZFNIChIdRgP8pUBeMg17auhwTPcHbOzEZlVHuJ2e/GMqZC147/7op7GSX+hVYY8hMyZyF/L5LTg6urDbgKGBcwrTxW3hNfAUO3D4EtcQw5p7jqWZxXqNcKfD88JQ7dgXrvrxrsPMnQ3RIywN9MfQvaMABy43YywBUZqCI9EC35b rqbDwvMEQVbjr08q+DNFwnbQPbbSjS5t8Q2zABEBAAG0GG1hZ2VkdSA8cm9vdEBt YWdlZHUub3JnPokBPwQTAQIAKQUCX1SpJwIbAwUJEswDAAcLCQgHAwIBBhUIAgkK CwQWAgMBAh4BAheAAAoJEFOfMij/yaomQeMH/iGm3Cod5yLEOpa4MLM3+SGzR9eYUyF4SbG0mBGrj24MUuVPN3YHEgEwPkj43V+EjdCPXIWQbqXCIbxfUf2PXLZ/SPd8Bu+CcB2ept/KJT0BHK6cWycAeVk8vXdj6hgLE2M3wVmopxHPTAlDfzmAuLBwQYFA2KK4yW6ab5Y0mF7+BvFS/rvkQu10Xkyn3+LbYEwDPfr752cezs+5qNIkZ19ZjtCGnSN9266aFLE+u8708GvFrzBGgVtIdp8K/pE5Gc8tpQOGYGBiRedAX7p4U1JkQTDMANr5E1zcg0339AdCZPunn9EuCkiwEU9b1IPu1zjQ3YVVhojshkmmOo+p7yy5AQ0EX1SpJwEIAK1DITDbUT9s17ZzT0XyIzNT2rBlybH57gF3sOsfuQk4M/iskcIcvEeYmTV9540Zk6ENZxxEXZU2nX9E4VbU39Z5qs67xjp9DLAVCaV04DZirZYI3ATQip/NXLNc3B27/qu4PyFx/J0Oys7ZweRfFHrVD1E3M9S6ah2htdjLQ4TBPPCXTRdkPb/4Fcyo2WZb5ojXzjarTaifN+EAdBsmGyCiGAtADPt6ElD5O8YwfHBbH+34ub9Gd771jfQv66RE/hng1qgRIEIa8QFPusxmeDW/cCkcr9ZH9RKaYH4U6qvKXyTN5AzYZI8o9NH8CS/t1PPK7ahyu+WkN7zxHOvd970AEQEAAYkBJQQYAQIADwUCX1SpJwIbDAUJ EswDAAAKCRBTnzIo/8mqJhZlCACqctMTytdseWA65EgXEDXNR8yOePyzewDVwnB6 qbiHyhAjldXUN1E4Ndb0OVytumsqjNA9Te6fTU6kukPjQex/XXl3K/UqYesV4TU0/kTENWWvX+olnxZig5B4BfjC7HmPu4DGlw78X7kuIxqUi2nwkhdrlEfG8GS5t0FyFgcl6TlyymlN04rFP30/xJ39kugkwN5bkR3GP5Q9QMVEHIR0iLdkWbDtX3n2nEKTal64Q9RE0P4FsroWbOzu7ZZLhSeE+ohloE2LHGnDtPbTsRseX7HNdVP/NfO7SOhUezg1HFzFYz+YoPEyyLWvOyK82j3Mvr+Xm7msjrcq551fvdyt=Hdfc-----END PGP PUBLIC KEY BLOCK-----2、将 CentOS7 导出的公钥,拷贝到 CentOS8 中,在 CentOS8 中使⽤ CentOS7 的公钥加密⼀个⽂件 #将公钥⽂件远程复制拷贝到centos8主机上[root@localhost ~]# scp liu.pubkey 10.0.0.8:root@10.0.0.8's password:liu.pubkey 100% 1723 2.2MB/s 00:00#在8主机上⽣成密钥对[root@localhost ~]# gpg --list-keysgpg: directory '/root/.gnupg' createdgpg: keybox '/root/.gnupg/pubring.kbx' createdgpg: /root/.gnupg/trustdb.gpg: trustdb created[root@localhost ~]# gpg --gen-keygpg (GnuPG) 2.2.9; Copyright (C) 2018 Free Software Foundation, Inc.This is free software: you are free to change and redistribute it.There is NO WARRANTY, to the extent permitted by law.Note: Use "gpg --full-generate-key" for a full featured key generation dialog.GnuPG needs to construct a user ID to identify your key.Real name: mageduEmail address: root@You selected this USER-ID:"magedu <root@>"Change (N)ame, (E)mail, or (O)kay/(Q)uit? oWe need to generate a lot of random bytes. It is a good idea to performsome other action (type on the keyboard, move the mouse, utilize thedisks) during the prime generation; this gives the random numbergenerator a better chance to gain enough entropy.We need to generate a lot of random bytes. It is a good idea to performsome other action (type on the keyboard, move the mouse, utilize thedisks) during the prime generation; this gives the random numbergenerator a better chance to gain enough entropy.gpg: key A8EB5216FA6980C8 marked as ultimately trustedgpg: directory '/root/.gnupg/openpgp-revocs.d' createdgpg: revocation certificate stored as '/root/.gnupg/openpgp-revocs.d/0CE5ACE751E9B662E435E7D8A8EB5216FA6980C8.rev' public and secret key created and signed.pub rsa2048 2020-09-06 [SC] [expires: 2022-09-06]0CE5ACE751E9B662E435E7D8A8EB5216FA6980C8uid magedu <root@>sub rsa2048 2020-09-06 [E] [expires: 2022-09-06]#在8主机上导⼊公钥[root@localhost ~]# gpg --list-keysgpg: checking the trustdbgpg: marginals needed: 3 completes needed: 1 trust model: pgpgpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1ugpg: next trustdb check due at 2022-09-06/root/.gnupg/pubring.kbx------------------------pub rsa2048 2020-09-06 [SC] [expires: 2022-09-06]0CE5ACE751E9B662E435E7D8A8EB5216FA6980C8uid [ultimate] magedu <root@>sub rsa2048 2020-09-06 [E] [expires: 2022-09-06]pub rsa2048 2020-09-06 [SC] [expires: 2030-09-04]9DEDB2B651CCB789163ACF14539F3228FFC9AA26uid [ unknown] magedu <root@>sub rsa2048 2020-09-06 [E] [expires: 2030-09-04]#⽤从7主机导⼊的公钥,加密8主机的/etc/fstab⽂件,会⽣成⼀个fatab.gpg⽂件[root@localhost ~]# gpg -e -r magedu /etc/fstab[root@localhost ~]# file /etc/fstab.gpg/etc/fstab.gpg: PGP RSA encrypted session key - keyid: B6110533 2823D626 RSA (Encrypt or Sign) 2048b .3、回到 CentOS7 服务器,远程拷贝 file.txt.gpg ⽂件到本地,使⽤ CentOS7的私钥解密⽂件#远程fstab.gpg⽂件拷贝到本机[root@localhost ~]# scp 10.0.0.8:/etc/fstab.gpg .root@10.0.0.8's password:fstab.gpg 100% 737 200.3KB/s 00:00#在本机上⽤⾃⼰的秘钥进⾏解密[root@localhost ~]# gpg -d fstab.gpg[root@localhost ~]# gpg -o fstab -d fstab.gpg4、在 CentOS7 中使⽤ openssl 软件创建 CA#进⼊CA⽬录⽣成CA私钥[root@localhost ~]# cd /etc/pki/CA/[root@localhost CA]# touch /etc/pki/CA/index.txt[root@localhost CA]# echo 01 > /etc/pki/CA/serial[root@localhost CA]# (umask 066;openssl genrsa -out private/cakey.pem 2048)Generating RSA private key, 2048 bit long modulus..........................+++ ......................................................................+++e is 65537 (0x10001)#⽣成CA⾃签名证书[root@localhost CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pemYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:beijingLocality Name (eg, city) [Default City]:beijingOrganization Name (eg, company) [Default Company Ltd]:mageduOrganizational Unit Name (eg, section) []:itCommon Name (eg, your name or your server's hostname) []:Email Address []:root@[root@localhost CA]# cat /etc/pki/CA/cacert.pem-----BEGIN CERTIFICATE-----MIID4zCCAsugAwIBAgIJAKmVhbF6f9HhMA0GCSqGSIb3DQEBCwUAMIGHMQswCQYD VQQGEwJDTjEQMA4GA1UECAwHYmVpamluZzEQMA4GA1UEBwwHYmVpamluZzEPMA0GA1UECgwGbWFnZWR1MQswCQYDVQQLDAJpdDEWMBQGA1UEAwwNY2EubWFnZWR1Lm9y ZzEeMBwGCSqGSIb3DQEJARYPcm9vdEBtYWdlZHUub3JnMB4XDTIwMDkwNjA5NTEz NVoXDTMwMDkwNDA5NTEzNVowgYcxCzAJBgNVBAYTAkNOMRAwDgYDVQQIDAdiZWlqaW5nMRAwDgYDVQQHDAdiZWlqaW5nMQ8wDQYDVQQKDAZtYWdlZHUxCzAJBgNVBAsM Aml0MRYwFAYDVQQDDA1jYS5tYWdlZHUub3JnMR4wHAYJKoZIhvcNAQkBFg9yb290QG1hZ2VkdS5vcmcwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC7bsED vhRsQlMYZ1yo8/W8+iGnUmFeKEn+XRXPMAPOS4CdysVOdXV/V9g1BxHObAoa8Gfsp18IOtOftS0LNjZF0iN/IN08Tj72Ju3h65mIC0WGSeumTGrm1ToQelQcGgfw1JXWCPTYKdOoX3fUwQKFAQC7EqpER2b/AD96L3wf6FFYBZbwAebaaKrM72MEVCrfPEciOK+DZztu4ni5YrV8ioo24nm9g+lihVzLoV1DqXovankJ8FQmjrE80QS1hePPx2tm6Gu+ki64sISCKs+VamgWA667w25TW84ySrLO5CSIyTfZgIvuwFwmfin/9EQGtjBtZdTheA0JqybG5l9VAgMBAAGjUDBOMB0GA1UdDgQWBBRgTeREskLWYFusJiS4tT3Y isppiDAfBgNVHSMEGDAWgBRgTeREskLWYFusJiS4tT3YisppiDAMBgNVHRMEBTADAQH/MA0GCSqGSIb3DQEBCwUAA4IBAQB8ES1o4IfNx2fhSW0EfbfCjYW8DT56sxDJRDD4arTpaDmkQFxPtG4SVYfLLKONjrbO4O99JWoT2x2foiiTqczKbZTVmkln8nI+vlj1o3do1QKHk6Zr6ZYA2a2TWfpOgnE9I8Bm9K+CgSurszZz5gYoUxUEJde5SbGkHS+0xYZT1a2ArDbEHAicJwkw/qKIEy5Jaip4p+6Rnbrrd1n1ln+ZF7KcJcriDz8S+moXJ0ECuQIftoTGHl66mcNHzCwNrLJlHxswFML7qsVe5fM5QqPJQCcv5t4AAc8IQPkjz5K8KlKwgDIiKY6/Ny2vnFqhJOA4Ltf62ibGp5MPvE/+8Y3t-----END CERTIFICATE-----5、在 CentOS7 中使⽤ openssl 软件创建⼀个证书申请请求⽂件,并使⽤上⾯的根证书对其进⾏签署 #⽤户⽣成私钥⽂件[root@localhost CA]# mkdir /data/app1 #创建⽤户⽬录[root@localhost CA]# (umask 066;openssl genrsa -out /data/app1/app1.key 2048)Generating RSA private key, 2048 bit long modulus.+++..................................+++e is 65537 (0x10001)[root@localhost CA]# cat /data/app1/app1.key-----BEGIN RSA PRIVATE KEY-----MIIEowIBAAKCAQEAw3c5Wa69bmAvSnLPqaPNxprIlI9dHLxreXLhXjvkK+eWxs3gw6YDmOkSuH8l9S5xPe39a6E1Vy4TNjkBtNTqgn+uaIwvWTyf4s+68WIa+GZ6oCgt2a1ak+TdNRkkrv7LDR5mooI5iyAn2VEB5EtUn+JI8VGosPzOS+/EvLIJBuDeM8KlSOLS5J4syt599M44QUV9UOYMAsEnPrFe1Vrv+NuKA/R+0tubGxqYQzmT8OGfmnWI6M/li4oQgUBKHAkOvZRj5MU8Hwi29rQd81dHbEeL+tbDYVr58u0+1GD2edHZaUmke3y1/9DM4ah2Y1d0oRgjnqEAmv694SGGA7jGaQIDAQABAoIBAHdEp1zer73KuPBvb+DuD2CRD7T+aW1gVx/rBjMOzmIv1KOH+g7HnMhP51lmVA3wAa8tKYXj/v0sIxLh4/WoOVPZft1SNI353QFziXlCSHyrY0WYXqnFClDVxFhi+CxDUji2BSBB38TRoR8MO+BGSuOoGqQNFKayC1rweZY9+B4WQ69BmhcIhwn5EgRCQ0BsTTF3B8pavNjTe0e/9II5XI9tM4+Md+TPhBmDNRGaSMgE1QmlraEc+UguRBYNxdOX/YP2+nq1MKX5CDnVK6T0cNgn3PHgKBipfnU8bU21iiwgmAHeLNv4sSiKgeh/QJEt3cRZT8wM8hOTYuKEPjGe3wECgYEA9ag8L9kj8rzip21i0sGH/3XJ7c47SF2I6ZYZEd13QdAI8AE6T3uiBuwCRG/0NjWRGtBJWgpy8awH44agcgWw7rxGHoGxehKb9IQf7inAsOko72Gu1KQ9sWK5Meus/LyzFqU0zQHUUSvojz5KfqIStMQN2wwk6k5T/beDvIGmFGECgYEAy7ICwm7M896SjmBx/7L6v1/IzxphBWTuXSW44+74+VSN+zDj47pNZjZ2JDq6QOCEg3E6dQ1sy2GGVctpjTDUWblB1gLeA1A9oOc5CQyyhSWUNHtRFVEgLsQT2JsR499aFCLBgV08oddpPWHOPCyZAoEfiVE6EJ/Kd+m07m2MbwkCgYEA4ZxhslwNPNimnLfEY+Uj3sUx7/pQzdRBcq3MVnD8HvBN1QZ7pBXap9rG9k2Pjt3BZ0vVoiEokbW6BQdWgYGijo9RIqFf+snuezGBFb044AEy/C7NXzN8CVau2R8mX3N6UpjllkZQ1T+rNSszRXvaDDRmuT89BAdt8f1BurWjbuECgYAPEWwC1g9zOtO8lIXaVHMYFQ3VxC3JKF45pcC3m8XvK8IVAtjYz79KAF1c8Ls2cWVcE9QvNH8HzH8TeailOSd8O6gTHMMvm4/zhydA9B+AmfcMqtKksQugagDN1SrNoIgZVTjbSPpjPnwaflGzQdlPxh1/GvMgp7FijXdE6/WngQKBgBZjLzmYqHbp7xKbcpU1DJGOru4NzEeqoHM8eGCwm6TkCvslXtvwk7v/crKK8NLnTB5pjeTfTiwfWXIXg/im/V8UrQxJATJM8EEoIrTlMI3PEC+KLxI0u746 GeaWUfmHyxosZ6GamVpseOndeQg2Yo2qt5BoorhYmzgjwNux++TC-----END RSA PRIVATE KEY-----#进⾏证书申请[root@localhost CA]# openssl req -new -key /data/app1/app1.key -out /data/app1/app1.csrYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [XX]:CNState or Province Name (full name) []:beijingLocality Name (eg, city) [Default City]:beijingOrganization Name (eg, company) [Default Company Ltd]:mageduOrganizational Unit Name (eg, section) []:itCommon Name (eg, your name or your server's hostname) []:Email Address []:app1@Please enter the following 'extra' attributesto be sent with your certificate requestA challenge password []:An optional company name []:#证书颁发[root@localhost ~]# openssl ca -in /data/app1/app1.csr -out /etc/pki/CA/certs/app1.crt -days 1000 Using configuration from /etc/pki/tls/fCheck that the request matches the signatureSignature okCertificate Details:Serial Number: 1 (0x1)ValidityNot Before: Sep 6 10:01:24 2020 GMTNot After : Jun 3 10:01:24 2023 GMTSubject:countryName = CNstateOrProvinceName = beijingorganizationName = mageduorganizationalUnitName = itcommonName = emailAddress = app1@X509v3 extensions:X509v3 Basic Constraints:CA:FALSENetscape Comment:OpenSSL Generated CertificateX509v3 Subject Key Identifier:91:A7:F3:0B:E4:C0:77:91:43:6C:AD:6D:CA:69:B6:8B:98:FA:F2:13X509v3 Authority Key Identifier:keyid:60:4D:E4:44:B2:42:D6:60:5B:AC:26:24:B8:B5:3D:D8:8A:CA:69:88Certificate is to be certified until Jun 3 10:01:24 2023 GMT (1000 days)Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]yWrite out database with 1 new entriesData Base Updated6、吊销已经签署成功的证书#吊销证书[root@localhost ~]# openssl ca -revoke /etc/pki/CA/newcerts/01.pemUsing configuration from /etc/pki/tls/fRevoking Certificate 01.Data Base Updated[root@localhost ~]# openssl ca -status 01Using configuration from /etc/pki/tls/f01=Revoked (R)#⽣成证书吊销列表[root@localhost ~]# echo 01 > //etc/pki/CA/crlnumber[root@localhost ~]# openssl ca -gencrl -out /etc/pki/CA/crl.pemUsing configuration from /etc/pki/tls/f[root@localhost ~]# cat /etc/pki/CA/crlnumber02[root@localhost ~]# cat /etc/pki/CA/crl.pem-----BEGIN X509 CRL-----MIIB9zCB4AIBATANBgkqhkiG9w0BAQsFADCBhzELMAkGA1UEBhMCQ04xEDAOBgNV BAgMB2JlaWppbmcxEDAOBgNVBAcMB2JlaWppbmcxDzANBgNVBAoMBm1hZ2VkdTEL MAkGA1UECwwCaXQxFjAUBgNVBAMMDWNhLm1hZ2VkdS5vcmcxHjAcBgkqhkiG9w0B CQEWD3Jvb3RAbWFnZWR1Lm9yZxcNMjAwOTA2MTAwNTU3WhcNMjAxMDA2MTAwNTU3 WjAUMBICAQEXDTIwMDkwNjEwMDI0OFqgDjAMMAoGA1UdFAQDAgEBMA0GCSqGSIb3 DQEBCwUAA4IBAQBbU7Q5nkHYzVNZuIPe9Q2G0lhiNEjgSxcotU8sYfNRpJ/DaCLY lPfvWQ4TGhGCpl8KMws/yhUU3Yk8x5Q5snaw4MTyE3VNoYkZfCGMLf3ovV4FS0rzem3o3DozohUiKLXFm9ES0QEaypMXPCXeiDpVGAhaotcL5oaFzgiBCZ657S14rmQ/CSy1VzTtFsZEcX5r8uMe+te1cwjOmRoKDFSXh0BL5f/Spv8pw9FF3WJryLiOWuxv5DHoOOK49ya9BWtmuyn99fB+qv4MDQoQmVMYiMTKbpthxmT6v8jpuAYHpZHSW5hluq5mdCr8YhM5RgJordrL+EEqBndoz/+zMIb+-----END X509 CRL-----。
各种文件的mime类型

各种⽂件的mime类型扩展名:absMIME类型:audio/x-mpeg扩展名:aiMIME类型:application/postscript扩展名:aifMIME类型:audio/x-aiff扩展名:aifcMIME类型:audio/x-aiff扩展名:aiffMIME类型:audio/x-aiff扩展名:aimMIME类型:application/x-aim扩展名:artMIME类型:image/x-jg扩展名:asfMIME类型:video/x-ms-asf扩展名:asxMIME类型:video/x-ms-asf扩展名:auMIME类型:audio/basic扩展名:aviMIME类型:video/x-msvideo扩展名:avxMIME类型:video/x-rad-screenplay扩展名:bcpioMIME类型:application/x-bcpio扩展名:binMIME类型:application/octet-stream扩展名:bmpMIME类型:image/bmp扩展名:bodyMIME类型:text/html扩展名:cdfMIME类型:application/x-cdf扩展名:cerMIME类型:application/x-x509-ca-cert扩展名:classMIME类型:application/java扩展名:cpioMIME类型:application/x-cpio扩展名:cshMIME类型:application/x-csh扩展名:dibMIME类型:image/bmp扩展名:docMIME类型:application/msword扩展名:dtdMIME类型:text/plain扩展名:dvMIME类型:video/x-dv扩展名:dviMIME类型:application/x-dvi扩展名:epsMIME类型:application/postscript扩展名:etxMIME类型:text/x-setext扩展名:exeMIME类型:application/octet-stream扩展名:gifMIME类型:image/gif扩展名:gtarMIME类型:application/x-gtar扩展名:gzMIME类型:application/x-gzip扩展名:hdfMIME类型:application/x-hdf扩展名:hqxMIME类型:application/mac-binhex40扩展名:htcMIME类型:text/x-component扩展名:htmMIME类型:text/html扩展名:htmlMIME类型:text/html扩展名:hqxMIME类型:application/mac-binhex40扩展名:iefMIME类型:image/ief扩展名:jadMIME类型:text/vnd.sun.j2me.app-descriptor 扩展名:jarMIME类型:application/java-archive扩展名:javaMIME类型:text/plain扩展名:jnlpMIME类型:application/x-java-jnlp-fileMIME类型:image/jpeg扩展名:jpegMIME类型:image/jpeg扩展名:jpgMIME类型:image/jpeg扩展名:jsMIME类型:text/javascript扩展名:jsfMIME类型:text/plain扩展名:jspfMIME类型:text/plain扩展名:karMIME类型:audio/x-midi扩展名:latexMIME类型:application/x-latex扩展名:m3uMIME类型:audio/x-mpegurl扩展名:macMIME类型:image/x-macpaint扩展名:manMIME类型:application/x-troff-man 扩展名:meMIME类型:application/x-troff-me 扩展名:midMIME类型:audio/x-midi扩展名:midiMIME类型:audio/x-midi扩展名:mifMIME类型:application/x-mif扩展名:movMIME类型:video/quicktime扩展名:movieMIME类型:video/x-sgi-movie扩展名:mp1MIME类型:audio/x-mpeg扩展名:mp2MIME类型:audio/x-mpeg扩展名:mp3MIME类型:audio/x-mpeg扩展名:mpaMIME类型:audio/x-mpeg扩展名:mpeMIME类型:video/mpeg扩展名:mpeg扩展名:mpegaMIME类型:audio/x-mpeg扩展名:mpgMIME类型:video/mpeg扩展名:mpv2MIME类型:video/mpeg2扩展名:msMIME类型:application/x-wais-source 扩展名:ncMIME类型:application/x-netcdf扩展名:odaMIME类型:application/oda扩展名:pbmMIME类型:image/x-portable-bitmap 扩展名:pctMIME类型:image/pict扩展名:pdfMIME类型:application/pdf扩展名:pgmMIME类型:image/x-portable-graymap 扩展名:picMIME类型:image/pict扩展名:pictMIME类型:image/pict扩展名:plsMIME类型:audio/x-scpls扩展名:pngMIME类型:image/png扩展名:pnmMIME类型:image/x-portable-anymap 扩展名:pntMIME类型:image/x-macpaint扩展名:ppmMIME类型:image/x-portable-pixmap 扩展名:psMIME类型:application/postscript扩展名:psdMIME类型:image/x-photoshop扩展名:qtMIME类型:video/quicktime扩展名:qtiMIME类型:image/x-quicktime扩展名:qtifMIME类型:image/x-quicktime扩展名:rgbMIME类型:image/x-rgb扩展名:rmMIME类型:application/vnd.rn-realmedia 扩展名:roffMIME类型:application/x-troff扩展名:rtfMIME类型:application/rtf扩展名:rtxMIME类型:text/richtext扩展名:shMIME类型:application/x-sh扩展名:sharMIME类型:application/x-shar扩展名:sitMIME类型:application/x-stuffit扩展名:smfMIME类型:audio/x-midi扩展名:sndMIME类型:audio/basic扩展名:srcMIME类型:application/x-wais-source扩展名:sv4cpioMIME类型:application/x-sv4cpio扩展名:sv4crcMIME类型:application/x-sv4crc扩展名:swfMIME类型:application/x-shockwave-flash 扩展名:tMIME类型:application/x-troff扩展名:tarMIME类型:application/x-tar扩展名:tclMIME类型:application/x-tcl扩展名:texMIME类型:application/x-tex扩展名:texiMIME类型:application/x-texinfo扩展名:texinfoMIME类型:application/x-texinfo扩展名:tifMIME类型:image/tiff扩展名:tiffMIME类型:image/tiff扩展名:tsvMIME类型:text/tab-separated-values扩展名:txtMIME类型:text/plain扩展名:ulwMIME类型:audio/basic扩展名:ustarMIME类型:application/x-ustar扩展名:xbmMIME类型:image/x-xbitmap扩展名:xmlMIME类型:text/xml扩展名:xpmMIME类型:image/x-xpixmap扩展名:xslMIME类型:text/xml扩展名:xwdMIME类型:image/x-xwindowdump扩展名:wavMIME类型:audio/x-wav扩展名:svgMIME类型:image/svg+xml扩展名:svgzMIME类型:image/svg+xml<!-- Wireless Bitmap -->扩展名:wbmpMIME类型:image/vnd.wap.wbmp<!-- WML Source -->扩展名:wmlMIME类型:text/vnd.wap.wml<!-- Compiled WML -->扩展名:wmlcMIME类型:application/vnd.wap.wmlc<!-- WML Script Source -->扩展名:wmlsMIME类型:text/vnd.wap.wmlscript<!-- Compiled WML Script -->扩展名:wmlscriptcMIME类型:application/vnd.wap.wmlscriptc 扩展名:wrlMIME类型:x-world/x-vrml扩展名:ZMIME类型:application/x-compress扩展名:zMIME类型:application/x-compress。
CA证书助手安装使用说明

CA证书助手安装使用说明1. 产品概述:CA证书助手系统是一个对客户端,网络等进行各项检测,同时把检测到的问题告知用户,方便客户发现问题、解决问题的软件系统。
1.1产品功能客户端进行检测并针对检测到的问题提供适当的建议解决办法;对无法解决的问题将检测报告发送到服务器端;检测网络环境;检测系统安装的CA签名控件是否存在并已注册、检测CA根证书是否已安装;检测各厂家Key驱动;检测Windows系统信息;检测系统安装的所有软件及版本;检测浏览器(只是IE)版本及补丁版本;系统自动升级功能;1.2运行环境支持Windows XP。
2. 软件安装CA证书助手安装步骤如下:步骤1:双击江苏CA证书助手1.0.exe文件,弹出江苏CA助手安装程序界面。
点击“下一步”。
步骤2:在许可协议界面选择“我同意”。
连续点击“下一步”,一直到出现“安装”按钮。
点击“安装”按钮,即可在默认路径下完成安装。
步骤3:安装过程中,弹出安装MICROSOFT VISUAL C++ 2005组件的对话框。
点击“是”,最后弹出完成的对话框,如下图:点击完成,即可完成安装。
3. 软件使用3.1 系统界面双击桌面的江苏CA证书助手的图标。
打开CA证书助手软件的界面,如下图:3.2 CA公司点击“CA公司”,界面显示CA最新动态,CA问题帮助,CA小贴士等资讯动态,如下图:打开链接可以看到具体内容,如下图;3.3 检测首先把需要检测的证书插入USB Token,导入数字证书。
点击“检测”按钮,界面如下图:点击“开始检测”,如果证书在其中一个检测中有错误的话,将会出现如下图:点击修复,可以修复该错误。
如果证书所有检测都正常,是否通过一栏中将全是绿色的勾。
如果通过以上的检测通过后,证书仍然无法使用,可以发送报告。
第一次发送报告需要设置个人信息。
点击“个人信息设置”,弹出如下对话框:输入城市,地区,单位,姓名,联系电话后,点击确定,该对话框消失。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Appendix B Sources of Experimental Datafor Code Validation Airfoil Data SourcesSome sources of airfoil geometry and experimental data for use in code evaluation are listed here. Note that rigorous validation of codes requires very careful analysis, and an understanding of possible experimental, as well as computational, error. See the junior Aerodynamic Lab notes for my comments on the issues involved in aerodynamic testing in wind tunnels. Hardcopies of the NACA reports are located in the Virginia Tech Library at DOCS Y3.N21/5:9 on the first floor.BooksAbbott and von Doenhoff, Theory of Airfoil Sections. Look in the references for the original NACA airfoil reports. Note that pressure distributions are fairly rare. See also NACA R 824.Riegels, Airfoil Sections, Butterworths, London, 1961. (English language version)NASA Low and Medium Speed AirfoilsMcGhee, Robert J., and Beasley, William D., “Low Speed Aerodynamic Characteristics of a 17-Percent-Thick Airfoil Section Designed for General Aviation Applications,” NASA TN D-7428, 1973.McGhee, Robert J., Beasley, William D., and Somers, Dan M., “Low Speed Aerodynamic Characteristics of a 13-Percent-Thick Airfoil Section Designed for General AviationApplications,” NASA TM X-72697, 1975.McGhee, Robert J., and Beasley, William D., “Effects of Thickness on the Aerodynamic Characteristics of an Initial Low-Speed Family of Airfoils for General AviationApplications,” NASA TM X-72843, 1976.McGhee, Robert J., and Beasley, William D., “Low-Speed Wind-Tunnel Results for aModified 13-Percent-Thick Airfoil,” NASA TM X-74018, 1977.Barnwell, Richard W., Noonan, Kevin W., and McGhee, Robert J., “Low SpeedAerodynamic Characteristics of a 16-Percent-Thick Variable Geometry Airfoil Designed for General Aviation Application,” NASA TP-1324, 1978.McGhee, Robert J., and Beasley, William D., “Wind-Tunnel Results for an Improved 21-Percent-Thick Low-Speed Airfoil Section,” NASA TM-78650, 1978.McGhee, Robert J., Beasley, William D., and Whitcomb, Richard T., “NASA Low- and Medium-Speed Airfoil Development “ NASA TM-78709, 1979.McGhee, Robert J., and Beasley, William D., “Low-Speed Aerodynamic Characteristics ofa 13-Percent-Thick Medium Speed Airfoil Designed for General Aviation Applications,”NASA TP-1498, 1979.McGhee, Robert J., and Beasley, William D., “Low Speed Aerodynamic Characteristics of a 17-Percent-Thick Medium Speed Airfoil Designed for General Aviation Applications,”NASA TP-1786, 1980McGhee, Robert J., and Beasley, William D., “Wind-Tunnel Results for a Modified 17-Percent Thick Low-Speed Airfoil Section, “ NASA TP-1919, 1981. (LS(1)-0417mod)Ferris, James D., McGhee, Robert J., and Barnwell, Richard W., “Low Speed Wind-Tunnel Results for Symmetrical NASA LS(1)-0013 Airfoil,” NASA TM-4003, 1987.B-2 Applied Computational AerodynamicsNASA Transonic AirfoilsWhitcomb, “Review of NASA Supercritical Airfoils,” ICAS Paper 74-10, August 1974(ICAS stands for International Council of the Aeronautical Sciences)Harris, C.D., “NASA Supercritical Airfoils,” NASA TP 2969, March 1990. See references contained in this report for sources of experimental data.Laminar Flow AirfoilsSomers, Dan M., “Design and Experimental Results for a Flapped Natural-Laminar-Flow Airfoil for General Aviation Applications,” NASA TP-1865, June 1981. (NLF(1)-0215F, Lancair and Wheeler express airfoil)McGhee, Robert J., Viken, Jeffrey K., and Pfenninger, Werner, D., “Experimental Results fora Flapped Natural-Laminar Flow Airfoil With High Lift/Drag Ratio,” NASA TM-85788,1984.Sewell, W.G., McGhee, R.J., Viken, J.K., Waggoner, E.G., Walker, B.S., and Miller, B.F.,“Wind Tunnel Results for a High-Speed, Natural Laminar Flow Airfoil Designed for General Aviation Aircraft,” NASA TM 87602, No. 1985.Other Low and Medium Speed Airfoils and Airfoil DataBeasley, William D., and McGhee, Robert J., “Experimental and Theoretical Low-Speed Aerodynamic Characteristics of the NACA 65(1)-213, a = 0.50, Airfoil,” NASA TMX-3160, Feb. 1975Hicks, Raymond M., “A Recontoured Upper Surface Designed to Increase the Maximum Lift Coefficient of a Modified NACA 65(0.82) (9.9) Airfoil Section,” NASA TM 85855, Feb.1984.Bingham, Gene J., and Chen, Allen Wen-shin, “Low Speed Aerodynamic Characteristics of an Airfoil Optimized for Maximum Lift Coefficient,” NASA TN D-7071, Dec. 1971.Stivers, “Effects of Subsonic Mach Number on the Forces and Pressure Distributions on Four 64A-Series Airfoil Sections at Angles of Attack as High as 28°,” NACA TN 3162, 1954.Also see TN 2096?Liebeck, R.H., “A Class of Airfoils Designed for High Lift in Incompressible Flow”, Journal of Aircraft, Oct. 1973, Vol. 10, No. 10, pp. 610-617Multi-element Airfoil DataWenzinger, C.J., and Delano, J., “Pressure Distribution Over an NACA 23012 Airfoil with a Slotted and Plain Flap,” NACA R-633, 1938.Harris, T.A., and Lowry, J.G., “Pressure Distribution over an NACA 23012 Airfoil with a Fixed Slot and a Slotted Flap,” NACA R 732, 1942.Axelson, J.A., and Stevens, G.L., “Investigation of a Slat in Several Different Positions on an NACA 64A010 Airfoil for a Wide Range of Subsonic Mach Numbers,” NACA TN 3129, March 1954.Weick, F.E., and Shortal, J.A., “The Effect of Multiple Fixed Slots and a Trailing-edge Flap on the Lift and Drag of a Clark Y Airfoil,” NACA R 427, 1932.Wentz, W.H., Jr., and Seetharam, H.C, “Development of a Fowler Flap System for a High Performance General Aviation Airfoil,” NASA CR-2443, 1974Seetharam, H.C., and Wentz, W.H., “Experimental Studies of Flow Separation and Stalling on a Two-Dimensional Airfoil at Low Speeds,” NASA CR-2560, 1975.Appendix B: Data Sources B-3Kelly, John A., and Hayter, N-L, F., “Lift and Pitching Moment at Low Speeds of the NACA 64A010 Airfoil Section Equipped with Various Combinations of Leading Edge Slat, Leading Edge Flap, Split Flap and Double-Slotter Flap,” NACA TN 3007, Sep. 1953. (no drag or pressure distributions)Other data sources:Bertin and Smith, 1st edition , page 102-102, NACA 4412, pressure distribution, 2nd edition: pg 201-202, 3rd edition: pg 221-222 (from Pinkerton, NACA R 563, 1936, but WATCH OUT! This data is not what you might think. See NACA R-646 for true 2-D data!)Hurley, F.X., Spaid, F.W., Roos, F.W., Stivers, L.S., Jr., and Bandettini, A., “Supercritical Airfoil Flowfield Measurements,” AIAA Paper No. 75-880, June 1975.Three-Dimensional Data SourcesElementary body geometries: There were many tests conducted by the NACA using geometries that are simple to model. Similar tests were also done in the early days of NASA. The NACA reports were classified at the time, but have been declassified. A sample of cases I’ve used are included here:Williams, C.V., “An Investigation of the Effects of a Geometric Twist on the Aerodynamic Loading Characteristics of a 45° Sweptback Wing-Body Configuration at Transonic Speeds,”NACA RM L54H18, 1954.Runckel, J.F., and Lee, E.E., Jr., “Investigation of Transonic Speeds of the Loading Over a 45° Sweptback Wing Having an Aspect Ratio of 3, Taper Ratio of 0.2, and NACA 65A004 Airfoil Sections,” NASA TN D-712, 1961.Loving, D.L., and Estabrooks, B.B., “Transonic Wing Investigation in the Langley Eight Foot High Speed Tunnel at High Subsonic Mach Numbers and at a Mach number of 1.2,”NACA RM L51F07, 1951.McDevitt, J.B., “An Experimental Investigation of Two Methods for Reducing Transonic Drag of Swept Wing and Body Combinations,” NACA RMA55B21, April 1955.Keener, E.R., “Pressure Measurements Obtained in Flight at Transonic Speeds for aConically Cambered Delta Wing,” NASA TM X-48, October 1959.The standard transonic test case: the ONERA M6 wing has been used in practically every transonic code validation calculation ever published. The data is contained in AGARD AR-138 cited below.Supercritical Wings:Harris, C.D., and Bartlett, D.W., “Tabulated Pressure Measurements on a NASASupercritical-Wing Research Airplane Model With and Without Fuselage Area-RuleAdditions at Mach 0.25 to 1.00,” NASA TM X-2634, 1972.Harris, C.D., “Wind-Tunnel Measurements of Aerodynamic Load Distribution on a NASA Supercritical-WIng Research Airplane Configuration,” NASA TM X-2469, 1972.Montoya, L.C., and Banner, R.D., “F-8 Supercritical Wing Flight Pressure, Boundary Layer and Wake Measurements and Comparisons with Wind Tunnel Data,” NASA TM X-3544, March 1977.Hinson, B.L., and Burdges, K.P., “Acquisition and Application of Transonic Wing and Far-Field Test Data for Three-Dimensional Computational Method Evaluation,” AFOSR-TR-80-0421, March 1980, available from DTIC as AD A085 258. These are the Lockheed Wings A, B, and C.Keener, E.R., “Pressure Distribution Measurements on a Transonic Low-Aspect RatioWing,” NASA TM 86683, 1985. (this is the so-called Lockheed Wing C)B-4 Applied Computational AerodynamicsKeener, E.R., “Boundary Layer Measurements on a Transonic Low-Aspect Ratio Wing,”NASA TM 88214, 1986. (this is the so-called Lockheed Wing C)Supersonic Wing Data:D.S. Miller,E.J. Landrum, J.C. Townsend, and W.H. Mason, “Pressure and Force Data for aFlat Wing and a Warped Conical Wing Having a Shockless Recompression at Mach 1.62,”NASA TP 1759, April 1981.J.L. Pittman, D.S. Miller, and W.H. Mason, “Fuselage and Canard Effects on an Attached Flow, Maneuver Wing at Mach 1.62,” NASA TP 2249, February 1984J.L. Pittman, D.S. Miller, and W.H. Mason, “Supersonic, Nonlinear, Attached-Flow Wing Design for High Lift with Experimental Validation,” NASA TP 2336, August 1984. AGARD Test CasesAGARD has selected test cases for CFD code validation. These cases are important because an attempt has been made to define the test conditions and any corrections required precisely enough for use in code validation work. This is not an easy job. This also means that the airfoil test coordinates and results are available in tabulated form in these reports. The reports include: AGARD AR-138, “Experimental Data Base for Computer Program Assessment,”May, 1979Two-dimensional test cases:(1) NACA 0012, over a range of subsonic Mach and angle of attack, both force andmoment and pressure distributions,(2) NLR QE 0.11-0.75-1.375, a symmetrical airfoil designed to be shock free at atransonic design point, Mach range from 0.30 to 0.85, all at zero angle of attack,(3) CAST 7, pressure distributions over a range of Mach from 0.40 to 0.80, from -2° to 5°, also boundary layer measurements. No force and moment data;(4) NLR7301, thick supercritical airfoil (16.5%), Mach from 0.30 to 0.85, a from -4°to + 4°, pressure, and force and moment;(5) SKF 1.1/with maneuver flap, (French), Mach number from 0.50 to 1.2, force andmoment and pressure over a limited range of angle of attack;(6) RAE 2822, surface pressure distribution, boundary layer and wake rake surveys,over a range of Mach and (this is one of the most complete sets of data in thereport),(7) NAE 75-036-13:2, Mach range from 0.5 to 0.84, from 0 to 4° at M = 0.75, 2°for other Machs.(8 )MBB-A3 NASA 10% supercritical, M from 0.6 to 0.80, from 0.5° to 2.5°.Three dimensional cases:(1) ONERA M6, pressure distributions,(2) ONERA AFV D, variable sweep wing,(3) MBB-AVA Pilot Model with supercritical wing,(4) RAE Wing A,(5) NASA Supercritical-Wing Research Airplane Model (actually the F-8, pressuredistributions only).Appendix B: Data Sources B-5Body alone configurations:(1) 1.5D Ogive Circular Cylinder Body, L/D = 21.5,(2) MBB Body of revolution No. 3,(3) 10° cone-cylinder at zero, M from 0.91 to 1.22,(4) ONERA calibration body model C5, M from 0.6 to 1.0, zero.AGARD AR-138-ADDENDUM, “ADDENDUM to AGARD AR No. 138, Experimental Data Base for Computer Program Assessment,” July, 1984Five additional three-dimensional data sets were identified and included in theADDENDUM(B-6)Lockheed-AFOSR Wing A: Semi-span wing, M 0.62-0.84,from -2° to 5°, RE on mac: 6 million(B-7)Lockheed-AFOSR Wing B: Semi-span wing, M: 0.70 to 0.94,from -2° to + 5°, Re on mac: 10 million(B-8)ARA M100 Wing/body, full model, M: 0.50-0.93,from -4° to +3°, Re on mac: 3.5 million(B-9)ARA M86 Wing/body, full model, M: 0.50-0.82,from 0° to +8°, Re on mac:2.8-3.7 million(B-10)FFA Aircraft (SAAB A32A Lansen), M: 0.40-0.89,from 0° to +10°, Re on mac: 10-30 millionAGARD R-702, “Compendium of Unsteady Aerodynamic Measurements,” Aug. 1982.Seven test cases are defined, five airfoils and two wings. The include:Airfoils:1. NACA 64006 with oscillating flap,2. NACA 64A010 with oscillatory pitching,3. NACA 0012 with oscillatory and transient pitching,4. NLR 7301 airfoil with (i) oscillatory pitching and oscillating flap at NLR and(ii)with oscillating pitching (NASA Ames).Wing data1. RAE Wing A with an oscillating flap2. NORA Model with oscillation about the swept axis.AGARD AR-211, “Test Cases for Inviscid Flowfield Methods,” May 1985.Two dimensional test casesNACA 0012 airfoil at (1) M = 0.80, = 1.25°,(2) M = 0.85, = 1°,(3) M = 0.95, = 0°,(4) M = 1.25, = 0°,(5) M = 1.25, = 7°,RAE 2822 airfoil at (6) M = 0.75, = 3°,B-6 Applied Computational AerodynamicsNLR 7301 airfoil at (7) M = 0.720957, = .194°, (theoretical data)Chiocchia-Nocilla at (8) M = 0.769, = 0°. (sharp le)2-D Cascade test cases:HOBSON-1(9) M = 0.476, a = 43.544°, Spacing, s/c = 1.0121HOBSON-2(10) M = 0.575, a = 46.123°, Spacing, s/c = 0.5259 Three-dimensional casesONERA M6 airfoil at (11) M = 0.84, = 3.06°,(12) M = 0.92, = 0°,Butler wing at (13) M = 2.50, = 0°,Dillner wing at (14) M = 1.50, = 15°,(15) M = 0.70, = 15°,NASA Ames swept wing at(16) M = 0.833, = 1.75°,AGARD B at (17) M = 1.5, = 0°,(18) M = 1.5, = 2°,(19) M = 2.0, = 0°,(20) M = 2.0, = 2°.AGARD AR-303, “A Selection of Experimental Test Cases for the Validation of CFD Codes,” Aug. 1994. (in two volumes)By now the data is much more elaborate, and there are many more cases.A - Airfoil cases (13)B - Wing-fuselage (6)C - Bodies (6)D - Delta wing class (5)E - Aero-Propulsion/Pylon/Store (9)The data is available on floppy disks. The Virginia Tech Library has this data in the media center. According to the report the data is available from the NASA Center for Aerospace Information, 800 Elkridge Landing Road, Linthicum Heights, MD 21090-2934. Contact: NASA Access Help Desk, (301) 621-0390, fax: (301) 621-0134. However, I’m not sure that this procedure actually worked when we tried it.。
