Software Tools Using CSRBFs for Processing Scattered Data
算法推荐安全评估工具

算法推荐安全评估工具
以下是一些常用的安全评估工具的算法推荐:
1. Nessus: 使用漏洞扫描技术来评估系统中的安全缺陷和漏洞。
它基于广泛的漏洞数据库和规则集,使用多种扫描技术来确定系统中的安全问题。
2. Nmap: 基于网络探测技术的安全评估工具。
它可以扫描目标系统上开放的端口和服务,并提供详细的服务信息和漏洞发现。
3. OpenVAS: 开源漏洞评估系统,用于扫描系统中的漏洞和安
全弱点。
它使用多种技术来检测各种类型的漏洞,并提供了强大的报告和跟踪功能。
4. Wireshark: 一个用于分析网络流量的工具,帮助发现潜在的
安全问题。
它可以捕捉和分析网络流量,从而揭示系统中的潜在安全问题。
5. Burp Suite: 一款广泛使用的Web应用程序安全测试工具。
它包括代理服务器、扫描器、拦截器等组件,可以帮助发现Web应用程序中的安全问题。
6. Metasploit: 一款用于开发和执行安全漏洞测试的框架。
它包
含了数百个漏洞利用模块,可以用于评估系统中的安全性,并执行各种渗透测试活动。
这些工具提供了不同类型的安全评估功能,可以根据具体需求
选择使用。
请注意,在使用这些工具时需要遵循合法合规的准则,并确保获得被测系统的合法授权。
气泡混合轻质土使用规程

目次1总则 (3)2术语和符号 (4)2.1 术语 (4)2.2 符号 (5)3材料及性能 (6)3.1 原材料 (6)3.2 性能 (6)4设计 (8)4.1 一般规定 (8)4.2 性能设计 (8)4.3 结构设计 (9)4.4 附属工程设计 (10)4.5 设计计算 (10)5配合比 (13)5.1 一般规定 (13)5.2 配合比计算 (13)5.3 配合比试配 (14)5.4 配合比调整 (14)6工程施工 (15)6.1 浇筑准备 (15)6.2 浇筑 (15)6.3 附属工程施工 (15)6.4 养护 (16)7质量检验与验收 (17)7.1 一般规定 (17)7.2 质量检验 (17)7.3 质量验收 (18)附录A 发泡剂性能试验 (20)附录B 湿容重试验 (22)附录C 适应性试验 (22)附录D 流动度试验 (24)附录E 干容重、饱水容重试验 (25)附录F 抗压强度、饱水抗压强度试验 (27)附录G 工程质量检验验收用表 (28)本规程用词说明 (35)引用标准名录 (36)条文说明 (37)Contents1.General provisions (3)2.Terms and symbols (4)2.1 Terms (4)2.2 Symbols (5)3. Materials and properties (6)3.1 Materials (6)3.2 properties (6)4. Design (8)4.1 General provisions (8)4.2 Performance design (8)4.3 Structure design (9)4.4 Subsidiary engineering design (9)4.5 Design calculation (10)5. Mix proportion (13)5.1 General provisions (13)5.2 Mix proportion calculation (13)5.3 Mix proportion trial mix (14)5.4 Mix proportion adjustment (14)6. Engineering construction (15)6.1 Construction preparation (15)6.2 Pouring .............................................................. .. (15)6.3 Subsidiary engineering construction (16)6.4 Maintenance (17)7 Quality inspection and acceptance (18)7.1 General provisions (18)7.2 Quality evaluate (18)7.3 Quality acceptance (19)Appendix A Test of foaming agent performance (20)Appendix B Wet density test (22)Appendix C Adaptability test (23)Appendix D Flow value test.................................................................................. .. (24)Appendix E Air-dry density and saturated density test (25)Appendix F Compressive strength and saturated compressive strength test (27)Appendix G Table of evaluate and acceptance for quality (28)Explanation of Wording in this code (35)Normative standard (36)Descriptive provision (37)1总则1.0.1为规范气泡混合轻质土的设计、施工,统一质量检验标准,保证气泡混合轻质土填筑工程安全适用、技术先进、经济合理,制订本规程。
ADuC8XX系列常见问题解答

ADuC8XX系列常见问题解答问题:ADUC8XX系列的开发方法和开发工具是怎样的?答案:ADuC8xx的开发方法是非常简便的。
ADUC8XX系列提供了评估板套件,以帮助用户熟悉ADuC8xx的开发方法和开发环境。
以ADUC831为例,EVAL- ADUC831QSZ套件包括评估板一块,下载线,9V电源和相应的软件光盘。
评估版套件中的光盘中包含了开发中用到的所有的软件,数据手册,应用笔记,评估板原理图、例子代码等信息。
如果没有购买评估板的用户想要得到此光盘, 可以联系800-810-1742或者发email至china.support@索取。
下面根据光盘中提供的各种开发软件对开发方法做一介绍。
1.Aspire它是一个集成开发环境。
可以编辑、编译、仿真及在线调试基于汇编语言和C语言的程序。
如果要使用在线调试功能,需要使用ACCUTRON公司的ACE仿真器。
这个ACE仿真器与PC的接口是USB,与芯片的接口只需一个管脚,所以称为单管脚调试。
2.Keil它是一个集成开发环境。
它支持编辑、编译、软件仿真。
目前最新版本的Keil C51支持UART口直接硬件在线调试,而不需仿真器(ACE)。
用户可在Keil的网站下载最新版本的软件。
3.WSD它是下载程序的工具。
当用Aspire或Keil编译生成*.hex文件后,可以用此软件把程序从PC上下载到芯片中。
PC与芯片之间的连接是通过串口实现的。
在两种评估板套件中,都包含了串口下载线。
如果没有购买评估板套件,您也可以自己在市场上买一根串口线。
但是需要在您的电路板上加入一颗RS232电平转换芯片。
如果您已经有ACE 仿真器,也可以不用WSD,而用ACE直接下载。
4.DEBUGV2它是在线调试汇编语言的工具。
也是通过串口来实现的。
不需要任何仿真器。
5.WASP它是用来评估ADuC8xx产品内部ADC性能的软件。
它也是通过串口与芯片通信。
不需要任何仿真器。
如需更加详细的软件使用方法,请参看光盘中的文档8XXGetStartedvx.x.pdf。
CSR调试入门

CSR8系列烧录程序步骤为,清空,写头文件,写系统文件,然后烧录配置文件。
----该方式针对空flash或者空的eepromcsr8系列修改步骤为:首先与USB转SPI转接器连接好,开机(机器必须处于开机状态才能与电脑连接),与电脑连接,打开PStool工具查看是否连接正常连接正常会显示连接样机的地址,即使是空的flash/eeprom也有地址无法连接或者连接异常会自动报警,检查连接顺序是否错误,或者样机的IC,晶振是不是坏的(如果连接电源发现开机之后有电流,松开开机键电流消失,可以一直长按开机键,通过烧写命令,把软件烧进去)通过PStool连接正常,先dump一个psr文件出来(dump.psr),作为备份和修改对比,之后打开config tool,open from device读取样机软件,在config tool 上修改软件的相关设置,然后write device写入机器中,通过pstool工具dump 一个psr文件出来(dump1.psr),与之前的psr文件(dump.psr)对比,将原先的(dump.psr里面的)// PSKEY_USR3复制到修改过的文件(dump1.psr)上,如果没有这个值,就不用管,有这个值就一定要恢复成原样将修改过的psr文件(dump1.psr)再通过pstool工具merge进样机中,然后reset BC就可以重启样机,之后就可以测试烧补丁,直接将补丁文件merge样机中即可,同样要reset BC补丁合集路径F:\yuanwenjian\lanya\bluetooth\CSR补丁合集——注:要及时更新最新的补丁,不然会出现问题,很容易影响生产文件夹中说明是每个补丁对应的作用(注:补丁不能打太多,一般不要超过7个,如果对应的功能样机中已存在,就不用打)注:改完软件最好就改一次地址,之后和手机重新配对测试CSR所有的相关文档,修改注意和修改方式文档凑在这个路径下F:\yuanwenjian\lanya\bluetooth\CSR文档csr8系列cmd烧写命令(直接在电脑dos后台用cmd命令完成,如下所示)首先打开命令提示符路径,即安装目录比如C:\Program Files (x86)\CSR\BlueSuite 2.5.8 这是我自己电脑的路径之后命令为: nvscmd dump "x:xx\xx\DUMP.XUV" -usb XXXXXXX 小写x为路径名称,大写X为usb转spi的转接口序列号(是一串数字,可通过PStool查看)之后回车即可完成读出文件操作之后的清空和烧录,将dump改为erase和burn即可发现的一个隐患,有时可能会烧录失败,软件没有烧录进去,或者烧录不完整,最好再烧录一次下图是我完整的打开烧录文件的截图输入nvscmd(e2cmd)会自动出现对应的命令字符和详解NORFLASH擦除烧写命令擦除nvscmd erase烧录nvscmd burn x:xx\xx\DUMP.XUV读取并保存nvscmd dump x:xx\xx\DUMP.XUVEEPROM擦除烧写命令擦除e2cmd fill 0xffff烧录e2cmd download d:\xx.dump读取并保存e2cmd dump d:\xx.dump注:NORFLASH和EEPROM的保存文件后缀不同,上面已表明CSR8系列的批量软件读取和保存有两种文件格式xuv文件和bin文件(flash)dump文件和bin文件(eeprom)xuv和dump文件的读取方式已在上面列出,不再做过多解释bin文件的读取方式很简单,确认样机中的软件是客户确认的批量软件,将flash/eeprom从样机上拆掉,放在底座cnv上,通过FlyPRO软件读取首选确认电脑和底座连接成功,然后选择芯片,点击读取,然后点击保存,标注好文件名,点击保存即可,如果不放心,可以拿一个空的flash/eeprom烧录进去,然后焊机器上测试一下注:flash的bin文件一般都是通过4033读取的,因为4033兼容性强,读取的bin文件可以在其他同样大小的flash中正常使用eeprom比较麻烦,因为必须首先确认批量用的eeprom大小,然后才能修改软件,因为软件大小如果比eeprom大或者小都会出现问题,所以确认好eeprom的大小之后再修改软件,之后和flash读取bin文件的方式相同,读取bin文件即可CSR8系列的2种烧录方式,具体如下:【方式一:软件烧录】电脑需要装好“BlueSuite 2.5.8”软件,和CSR量产软件V4,确认电脑与测试架或者样机连接好,打开CSR量产软件V4,勾选对应的USB转spi串口序列号,然后勾选对应的flash/eeprom,然后open file需要批量的软件,之后点击Erase,再点击Burn,最后点击SetAddr,完成烧录。
Arduino编程参考手册中文版(带目录适合打印)

! (逻辑非)
指针运算符
* 指针运算符
& 地址运算符
位运算
& (位与)
| (位或)
^ (位异或)
~ (位非)
<< (左移)
>> (右移)
复合运算符
++ (自加)
-- (自减)
+= (复合加)
-= (复合减)
*= (复合乘)
/= (复合除)
&= (复合与)
|= (复合或)
范围
HIGH | LOW
int checkSensor(){
if (analogRead(0) > 400) {
return 1;
else{
return 0;
}
}
return关键字对测试一段代码很方便,不需“注释掉”大段的可能是错误的代码。
void loop(){
//在此测试代码是个好想法
return;
// 这里是功能不正常的代码
for
for语句
描述
for语句用于重复执行被花括号包围的语句块。一个增量计数器通常被用来递增和终止循环。for语句对于任何需要重复的操作是非常有用的。常常用于与数组联合使用以收集数据/引脚。for循环的头部有三个部分:
for (初始化部分; 条件判断部分; 数据递增部分) {
//语句块
。。。
}
初始化部分被第一个执行,且只执行一次。每次通过这个循环,条件判断部分将被测试;如果为真,语句块和数据递增部分就会被执行,然后条件判断部分就会被再次测试,当条件测试为假时,结束循环。
示例:
for (x = 0; x < 255; x ++)
NIJ Standard 0101.04

Office of Justice ProgramsNational Institute of JusticeNational Institute of JusticeLaw Enforcement and Corrections Standards and Testing ProgramBallistic Resistance ofPersonal Body ArmorNIJ Standard–0101.04ABOUT THE LAW ENFORCEMENT AND CORRECTIONSSTANDARDS AND TESTING PROGRAMThe Law Enforcement and Corrections Standards and Testing Program is sponsored by the Office of Science and Technology of the National Institute of Justice (NIJ), U.S. Department of Justice. The program responds to the mandate of the Justice System Improvement Act of 1979, which directed NIJ to encourage research and development to improve the criminal justice system and to disseminate the results to Federal, State, and local agencies.The Law Enforcement and Corrections Standards and Testing Program is an applied research effort that determines the technological needs of justice system agencies, sets minimum performance standards for specific devices, tests commercially available equipment against those standards, and disseminates the standards and the test results to criminal justice agencies nationally and internationally.The program operates through:The Law Enforcement and Corrections Technology Advisory Council (LECTAC), consisting of nationally recognized criminal justice practitioners from Federal, State, and local agencies, which assesses technological needs and sets priorities for research programs and items to be evaluated and tested.The Office of Law Enforcement Standards (OLES) at the National Institute of Standards and Technology, which develops voluntary national performance standards for compliance testing to ensure that individual items of equipment are suitable for use by criminal justice agencies. The standards are based upon laboratory testing and evaluation of representative samples of each item of equipment to determine the key attributes, develop test methods, and establish minimum performance requirements for each essential attribute. In addition to the highly technical standards, OLES also produces technical reports and user guidelines that explain in nontechnical terms the capabilities of available equipment.The National Law Enforcement and Corrections Technology Center (NLECTC), operated by a grantee, which supervises a national compliance testing program conducted by independent laboratories. The standards developed by OLES serve as performance benchmarks against which commercial equipment is measured. The facilities, personnel, and testing capabilities of the independent laboratories are evaluated by OLES prior to testing each item of equipment, and OLES helps the NLECTC staff review and analyze data. Test results are published in Equipment Performance Reports designed to help justice system procurement officials make informed purchasing decisions.Publications are available at no charge through the National Law Enforcement and Corrections Technology Center. Some documents are also available online through the Internet/World Wide Web. To request a document or additional information, call 800–248–2742 or 301–519–5060, or write:National Law Enforcement and Corrections Technology CenterP.O. Box 1160Rockville, MD 20849–1160asknlectc@E-Mail:World Wide Web address: The National Institute of Justice is a component of the Officeof Justice Programs, which also includes the Bureau of JusticeAssistance, the Bureau of Justice Statistics, the Office ofJuvenile Justice and Delinquency Prevention, and the Office forVictims of Crime.U.S. Department of JusticeOffice of Justice ProgramsNational Institute of JusticeBallistic Resistance of PersonalArmorBodyNIJStandard–0101.04Supersedes NIJ Standard–0101.03, Ballistic Resistanceo f Police Body Armor dated April 1987Coordination by:Office of Law Enforcement StandardsNational Institute of Standards and TechnologyGaithersburg, MD 20899–8102Prepared for:National Institute of JusticeOffice of Science and TechnologyWashington, DC 205312000September183651NCJNational Institute of JusticeJulie E. SamuelsActing DirectorThe technical effort to develop this standard was conductedunder Interagency Agreement 94−IJ−R−004,Project No. 98−001CTT.This standard was formulated by the Office of Law Enforcement Standards (OLES) of the National Institute of Standards and Technology (NIST),Kathleen M. Higgins, Director. The participants in the researchand revision of this standard were: Carter K. Lord,Former Test Coordinator and Ballistics Range Manager, OLES,Steven L. Lightsey, President, The Tekne Group, Inc.,Ken Malley, National Technical Systems (NTS), Fredricksburg, VA,Nathaniel E. Waters, Engineering Technician, OLES,and the Staff of National Technical Systems (NTS), Camden, AR.The preparation of this standard was sponsored by the National Institute of Justice, Dr. David G. Boyd, Director, Office of Science and Technology.FOREWORDThis document, NIJ Standard−0101.04, “Ballistic Resistance of Personal Body Armor,” is an equipment standard developed by the Office of Law Enforcement Standards (OLES) of the National Institute of Standards and Technology (NIST). It is produced as part of the Law Enforcement and Corrections Standards and Testing Program of the National Institute of Justice (NIJ).This standard is a technical document that specifies the performance requirements that equipment should meet to satisfy the needs of criminal justice agencies for high quality service. While purchasers can use the test methods described in this standard to determine whether a particular piece of equipment meets the essential requirements, users are encouraged to have this testing conducted only in properly accredited laboratories. Procurement officials may also refer to this standard in their purchasing documents and require that equipment offered for purchase meet its requirements. Compliance with the requirements of this standard may be attested to by an independent laboratory or guaranteed by the vendor.Because this standard is designed as a procurement aid, it provides precise and detailed test methods. For those who seek general guidance concerning the selection and application of law enforcement and corrections equipment, user guides have also been published. The guides explain in nontechnical language how to select equipment capable of the level of performance required by a purchasing agency.NIJ STANDARD−0101.04 IS NOT INTENDED TO RESTRICT OROTHERWISE INFLUENCE THE PROCUREMENT AND USE OF NIJSTANDARD−0101.03 COMPLIANT BODY ARMORS. THEPUBLICATION AND USE OF THIS REVISION FOR NEW MODELCOMPLIANCE TESTING DOES NOT INVALIDATE OR RENDERUNSUITABLE ANY BODY ARMOR MODELS PREVIOUSLYDETERMINED TO BE COMPLIANT USING NIJ STANDARD−0101.03REQUIREMENTS.NIJ standards are subjected to continuing research, development, testing, change, and review. This standard and its successors will be reevaluated annually for success in achieving the technical goals of this revision. These reviews will be based on data collected through the Compliance Testing Program and its certified test laboratories, as well as from valid comments from the user and manufacturing communities. Technical comments and recommended revisions are welcome. Please send all written comments and suggestions to the Director, Office of Science and Technology, National Institute of Justice, U.S. Department of Justice, 810 7th St., NW, Washington, DC 20531.iiiBefore citing this or any other NIJ standard in a contract document, users should verify that the most recent edition of the standard is used. Write to the Director, Office of Law Enforcement Standards, National Institute of Standards and Technology, 100 Bureau Drive, Stop 8102, Gaithersburg, MD 20899−8102.Dr. David G. Boyd, DirectorandTechnologyScienceofOfficeofJusticeInstituteNationalivACKNOWLEDGMENTSThis standard has been reviewed and approved by the Weapons and Protective Systems Subcommittee and the Executive Committee of the Law Enforcement and Corrections Technology Advisory Council (LECTAC) and also by the National Armor Advisory Board (NAAB), currently comprised of representatives from:Accordis Fibers, Inc.American Body Armor and Equipment Co.California Department of CorrectionsChesterfield County Police Department, VirginiaDepartment of JusticeDHB Armor GroupDuPont Advanced Fiber SystemsFederal Bureau of InvestigationFraternal Order of PoliceGuardian Technologies, InternationalHexcel Schwebel High Performance FibersHoneywell/Allied Signal, Inc.International Association of Chiefs of PoliceInternational Brotherhood of Police OfficersNational Association of Police OrganizationsNational Sheriff’s AssociationOffice of Community Oriented Policing ServicesProtective Apparel Corporation of AmericaSafariland Ltd., Inc.U.S. Armor CorporationU.S. Secret Service, TSD/P&DvCONTENTSPage FOREWORD (iii)ACKNOWLEDGMENTS (v)SYMBOLS AND ABBREVIATIONS (ix)1. PURPOSE AND SCOPE (1)2. NIJ BODY ARMOR CLASSIFICATION (1)2.1 Type I (22 LR; 380 ACP) (2)2.2 Type IIA (9 mm; 40 S&W) (2)2.3 Type II (9 mm; 357 Magnum) (2)2.4 Type IIIA (High Velocity 9 mm; 44 Magnum) (2)2.5 Type III (Rifles) (2)2.6 Type IV (Armor Piercing Rifle) (3)2.7 Special Type (3)3. DEFINITIONS (3)4. REQUIREMENTS (8)4.1 Acceptance Criteria (8)4.2 Test Sequence (8)4.3 Workmanship (8)4.4 Traceability (8)4.5 Labeling (8)4.6 Ballistic Penetration and Backface Signature Criteria (12)4.7 Sampling (13)4.8 Armor Backing Material (14)4.9 Test Surveillance (14)pliance Test Documentation (15)5. TEST METHODS (15)5.1 Purpose (15)5.2 Sampling (15)5.3 References (15)5.4 Ballistic Penetration and Backface Signature Test (P-BFS) (16)5.5 Velocity Measurement Equipment (18)5.6 Wet Conditioning (19)5.7 Backing Material Fixture Preparation (20)5.8 Workmanship Examination (22)5.9 Armor Conditioning (22)5.10 Range Configuration (23)5.11 Test Preparation (24)5.12 Firing Sequence for Type I, IIA, II, and IIIA Armor (26)5.13 Firing Sequence for Type III Armor (30)5.14 Firing Sequence for Type IV Armor (31)vii5.15 P-BFS Test (Special Type) (33)5.16 P-BFS Test for Groin and Coccyx Protectors (33)5.17 Baseline Ballistic Limit Determination Test (33)5.18 Ballistic Limit Testing Equipment (34)5.19 Ballistic Limit Test Preparation (35)5.20 Ballistic Limit Firing Sequence (36)5.21 Ballistic Limit Determination (37)5.22 Ballistic Limit Retesting of Compliant Armor (37)6. DATA COLLECTION AND REPORTING (38)APPENDIX A–Compliance Test Report Form (39)APPENDIX B–Modified Langlie Method of Ballistic Limit Firing (53)APPENDIX C–Body Armor Selection (55)APPENDIX D–Acceptable Bullets for Handloading (56)TABLESTable 1. NIJ Standard–0101.04 P-BFS performance test summary (17)Table 2. NIJ baseline Ballistic Limit determination test summary (34)FIGURESFigure 1. Angle of incidence (3)Figure 2. Sample ballistic panel label (10)Figure 3. Sample carrier label (11)Figure 4. Sample label locations (12)Figure 5. General pretest drop locations (21)Figure 6. Test range configuration (24)Figure 7. General armor panel impact locations (front and back) (25)Figure 8. Acceptable strapping methods (26)Figure 9. Impact locations for baseline BL determination testing – Type Ithrough IIIA (35)viiiSTANDARD SPECIFIC ABBREVIATIONSACP = Automatic Colt PistolANSI = American National Standards Institute AP = Armor Piercing BFS = Backface Signature BL = Ballistic LimitBMF = Backing Material Fixture CP = Complete PenetrationCPO = Compliance Program Office CTP = Compliance Testing Program CTR = Compliance Test Report FMJ = Full Metal JacketJHP = Jacketed Hollow Point JSP =Jacketed Soft PointLR = Long RifleLRN = Lead Round NoseNLECTC = National Law Enforcement and Corrections Technology CenterP-BFS = Penetration and Backface Signature PP = Partial Penetration RN = Round Nose S&W = Smith & WessonSAAMI = Sporting Arms and Ammunition Manufacturers InstituteSJHP = Semi Jacketed Hollow Point SJSP = Semi Jacketed Soft PointCOMMONLY USED SYMBOLS AND ABBREVIATIONSA ampere H henry nm nanometer ac alternating current h hour No. number AM amplitude modulation hf high frequency o.d. outside diameter cd candela Hz hertz Ω ohm cm centimeter i.d. inside diameter p. page CP chemically pure in inch Pa pascal c/s cycle per second IR infrared pe probable error d day J joule pp. pages dB decibel L lambert ppm parts per million dc direct current L liter qt quart °C degree Celsius lb pound rad radian °F degree Fahrenheit lbf pound-force rf radio frequency diam diameter lbf in pound-force inch rh relative humidity emf electromotive force lm lumen s second eq equation ln logarithm (base e) SD standard deviation F farad log logarithm (base 10) sec. section fc footcandle M molar SWR standing wave ratio fig. figure m meter uhf ultrahigh frequency FM frequency modulation min. minute UV ultraviolet ft foot mm millimeter V volt ft/s foot per second mph miles per hour vhf very high frequency g acceleration m/s meter per second W watt g gram N newton λ wavelength gr grain N m newton meter wt weightarea=unit 2(e.g., ft 2, in 2, etc.); volume=unit 3 (e.g., ft 3, m 3, etc.) PREFIXES COMMON CONVERSIONS(See ASTM E380)d deci (10-1) da deka (10) 0.30480 m = 1 ft4.448222 N = 1 lbfc centi (10-2) hhecto (102) 2.54 cm = 1 in 1.355818 J = 1 ft lbf m milli (10-3)k kilo (103) 0.4535924 kg = 1 lb 0.1129848 N m = 1 lbf in µ micro (10-6)M mega (106) 0.06479891g = 1 gr 14.59390 N/m = 1 lbf/ft n nano (10-9) G giga (109) 0.9463529 L = 1 qt6894.757 Pa = 1 lbf/in 2 p pico (10-12)T tera (1012) 3600000 J = 1 kW hr 1.609344 km/h = 1 mphTemperature: T °C = (T °F -32)×5/9 Temperature: T °F = (T °C ×9/5)+32NIJ Standard−0101.04NIJ STANDARDFORBALLISTIC RESISTANCE OF PERSONAL BODY ARMOR1. PURPOSE AND SCOPEThe purpose of this standard is to establish minimum performance requirements and test methods for the ballistic resistance of personal body armor intended to protect the torso against gunfire. This standard is a general revision of NIJ Standard−0101.03, dated April 1987, updating the labeling requirements, acceptance criteria, test ammunition, procedures, and other items throughout the standard.The scope of the standard is limited to ballistic resistance only; this standard does not address threats from knives and sharply pointed instruments, which are different types of threat.2. NIJ BODY ARMOR CLASSIFICATIONPersonal body armors covered by this standard are classified into seven classes, or types, by level of ballistic performance. The ballistic threat posed by a bullet depends, among other things, on its composition, shape, caliber, mass, angle of incidence, and impact velocity. Because of the wide variety of bullets and cartridges available in a given caliber and because of the existence of handloaded ammunition, armors that will defeat a standard test round may not defeat other loadings in the same caliber. For example, an armor that prevents complete penetration by a 40 S&W test round may or may not defeat a 40 S&W round with higher velocity. In general, an armor that defeats a given lead bullet may not resist complete penetration by other bullets of the same caliber of different construction or configuration. The test ammunition specified in this standard represent general, common threats to law enforcement officers.As of the year 2000, ballistic resistant body armor suitable for full time wear throughout an entire shift of duty is available in classification Types I, IIA, II, and IIIA, which provide increasing levels of protection from handgun threats. Type I body armor, which was first issued during the NIJ demonstration project in 1975, is the minimum level of protection that any officer should have. Officers seeking protection from lower velocity 9 mm and 40 S&W ammunition typically wear Type IIA body armor. For protection against high velocity 357 Magnum and higher velocity 9 mm ammunition, officers traditionally select Type II body armor. Type IIIA body armor provides the highest level of protection available in concealable body armor and provides protection from high velocity 9 mm and 44 Magnum ammunition.Type IIIA armor is suitable for routine wear in many situations; however, departments located in hot, humid climates may need to carefully evaluate their use of Type IIIA body armor for their officers. Types III and IV armor, which protect against high powered rifle rounds, areclearly intended for use only in tactical situations when the threat warrants such protection (see app. C).The classification of an armor panel that provides two or more levels of NIJ ballistic protection at different locations on the ballistic panel shall be that of the minimum ballistic protection provided at any location on the panel.2.1 Type I (22 LR; 380 ACP)This armor protects against .22 caliber Long Rifle Lead Round Nose (LR LRN) bullets, with nominal masses of 2.6 g (40 gr) impacting at a minimum velocity of 320 m/s (1050 ft/s) or less, and 380 ACP Full Metal Jacketed Round Nose (FMJ RN) bullets, with nominal masses of 6.2 g (95 gr) impacting at a minimum velocity of 312 m/s (1025 ft/s) or less.2.2 Type IIA (9 mm; 40 S&W)This armor protects against 9 mm Full Metal Jacketed Round Nose (FMJ RN) bullets, with nominal masses of 8.0 g (124 gr) impacting at a minimum velocity of 332 m/s (1090 ft/s) or less, and 40 S&W caliber Full Metal Jacketed (FMJ) bullets, with nominal masses of 11.7 g (180 gr) impacting at a minimum velocity of 312 m/s (1025 ft/s) or less. It also provides protection against the threats mentioned in section 2.1.2.3 Type II (9 mm; 357 Magnum)This armor protects against 9 mm Full Metal Jacketed Round Nose (FMJ RN) bullets, with nominal masses of 8.0 g (124 gr) impacting at a minimum velocity of 358 m/s (1175 ft/s) or less, and 357 Magnum Jacketed Soft Point (JSP) bullets, with nominal masses of 10.2 g (158 gr) impacting at a minimum velocity of 427 m/s (1400 ft/s) or less. It also provides protection against the threats mentioned in sections 2.1 and 2.2.2.4 Type IIIA (High Velocity 9 mm; 44 Magnum)This armor protects against 9 mm Full Metal Jacketed Round Nose (FMJ RN) bullets, with nominal masses of 8.0 g (124 gr) impacting at a minimum velocity of 427 m/s (1400 ft/s) or less, and 44 Magnum Jacketed Hollow Point (JHP) bullets, with nominal masses of 15.6 g (240 gr) impacting at a minimum velocity of 427 m/s (1400 ft/s) or less. It also provides protection against most handgun threats, as well as the threats mentioned in sections 2.1, 2.2, and 2.3.2.5 Type III (Rifles)This armor protects against 7.62 mm Full Metal Jacketed (FMJ) bullets (U.S. Military designation M80), with nominal masses of 9.6 g (148 gr) impacting at a minimum velocity of 838 m/s (2750 ft/s) or less. It also provides protection against the threats mentioned in sections 2.1, 2.2, 2.3, and 2.4.2.6 Type IV (Armor Piercing Rifle)This armor protects against .30 caliber armor piercing (AP) bullets (U.S. Militarydesignation M2 AP), with nominal masses of 10.8 g (166 gr) impacting at a minimum velocity of 869 m/s (2850 ft/s) or less. It also provides at least single hit protection against the threats mentioned in sections 2.1, 2.2, 2.3, 2.4, and 2.5.2.7 Special TypeA purchaser having a special requirement for a level of protection other than one of the above standard types and threat levels should specify the exact test round(s) and minimum reference impact velocities to be used, and indicate that this standard shall govern in all other aspects.3. DEFINITIONS3.1 Angle of Incidence The angle between the line of flight of the bullet and the perpendicular to the front surface of the backing material fixture as shown in figure 1.Figure 1. Angle of incidence3.2 Armor CarrierA component of the armor sample or armor panel whose primary purpose is to retain the ballistic panel and provide a means of supporting and securing the armor garment to the user. These carriers are not generally ballistic resistant.3.3 Armor PanelThe portion of an armor sample that generally consists of an external carrier and its internal ballistic protective component(s) (e.g., the front and back panels).3.4 Armor SampleBULLET LINE OF FLIGHTANGLE OF INCIDENCEBACKING MATERIAL FIXTUREARMOR SAMPLEPERPENDICULAR TO FRONTSURFACE OF BACKING MATERIALFRONT SURFACE OF BACKING MATERIALOne complete armor garment comprised of a single wraparound style jacket, or a set (two) of front and back armor panels.3.5 Backface Signature (BFS)The depth of the depression made in the backing material, created by a nonpenetrating projectile impact, measured from the plane defined by the front edge of the backing material fixture. For armor tested on built up or curved backing material, the BFS is measured from the plane defined by the top edges of the depression or crater formed by the impact.Material3.6 BackingA homogenous block of nonhardening, oil base modeling clay, placed in contact with the back of the armor panel during ballistic testing.3.7 Backing Material FixtureA box fixture containing the backing material, typically comprised of a rigid frame constructed of wood or metal with a removable wooden back. The wooden back is not used during Ballistic Limit testing.3.8 Baseline Ballistic LimitThe experimentally derived, statistically calculated impact velocity at which a projectile is expected to completely penetrate an armor component (sample, panel or ballistic panel) 50 % of the time (V50). This velocity is also the velocity at which a projectile is expected to be stopped by the armor 50 % of the time (V50).Panel3.9 BallisticThe protective component of an armor sample or panel, primarily consisting of ballistic resistant materials, usually enclosed in a nonremovable cover. The ballistic panel is normally retained within the armor sample or panel by a separate fabric carrier, and may be removable from the carrier.3.10 Certification of ComplianceManufacturer’s affidavit (certification) that a production unit of body armor meets (complies with) all of the requirements of this standard (sec. 4.0) for the labeled protection classification (sec. 2.0).3.11 ComplianceNIJ approval, after successful ballistic performance testing to this standard, of a body armor model submitted to the NIJ Compliance Testing Program (CTP).3.12 Compliance Test GroupA group of armor samples, either six, four, or nine complete garments, submitted to the NIJ CTP for testing according to this standard (sec. 4.7).3.13 DeformationThe maximum momentary displacement of the rear surface of an armor panel, caused by a fair hit that does not penetrate the armor, when the armor is in initial contact with the backing material.3.14 Fair HitA bullet that impacts the armor sample or panel at an angle of incidence no greater than ± 5° from the intended angle of incidence, no closer to the edge of the ballistic panel than 76 mm (3.0 in) and no closer to a prior hit than 51 mm (2.0 in), at an impact velocity within ± 9.1 m/s(30 ft/s) of the required reference test velocity.A bullet that impacts the armor sample or panel at an angle of incidence no greater than ± 5° from the intended angle of incidence, no closer to the edge of the ballistic panel than 76 mm (3.0 in) and no closer to a prior hit than 51 mm (2.0 in), at an impact velocity less than 7.6 m/s (30 ft/s) below the required reference test velocity which produces a penetration or an excessive backface signature.A bullet that impacts the armor sample or panel at an angle of incidence no greater than ± 5° from the intended angle of incidence, no closer to the edge of the ballistic panel than 76 mm (3.0 in) and no closer to a prior hit than 51 mm (2.0 in), at an impact velocity more than 7.6 m/s (30 ft/s) above the required reference test velocity which does not produce a penetration or an excessive backface signature.3.15 Full Metal Jacketed Bullet (FMJ)A bullet consisting of a lead core completely covered, except for the base, with copper alloy (approximately 90 % copper and 10 % zinc). “Total Metal Jacket (TMJ),” “Totally Enclosed Metal Case (TEMC),” and other commercial terminology for bullets with electro deposited copper and copper alloy coatings have been tested and are considered comparable to Full Metal Jacketed (FMJ) bullets for this standard.3.16 InsertA removable or nonremovable unit of ballistic material which can be part of either the armor or ballistic panel, which is utilized to enhance the ballistic performance of an armor in a specific area (also known as “trauma packs” or “trauma plates”).3.17 Jacketed Hollow Point Bullet (JHP)A bullet consisting of a lead core which has a hollow cavity or hole located in the nose of the bullet and is completely covered except for the hollow point with a copper alloy (approximately 90 % copper and 10 % zinc) jacket.3.18 Jacketed Soft Point Bullet (JSP)A lead bullet, also known as a Semi Jacketed Soft Point (SJSP), completely covered, except for the point, with copper alloy (approximately 90 % copper and 10 % zinc) jacket.3.19 Lead BulletA bullet made entirely of lead, which may be alloyed with hardening agents.3.20 Minimum VelocityThe designated NIJ Standard−0101.04 reference impact velocity (sec.5.4, table 1) less 9.1 m/s (30 ft/s).3.21 ModelA manufacturer’s designation (name, number, or other description) that serves to uniquely identify a specific configuration of body armor based upon the details of the ballistic panel construction (i.e., the number of layers of one or more types of ballistic resistant material assembled in a specific manner or the manner in which the armor is held in place upon the torso).NIJ verifies the ballistic resistance of a model based on ballistic testing of model samples in accordance with this standard. As an example, differences in stitching (e.g., box stitch versus quilt stitch) would make the ballistic panels different models. If a model of armor fails compliance testing, the manufacturer may never resubmit any armor under that model designation.3.22 ObliquityThe same determination of striking condition as “angle of incidence” (sec. 3.1).3.23 PenetrationComplete Penetration (CP): The complete perforation of an armor sample or panel by a test bullet or by a fragment of the bullet or armor sample itself, as evidenced by the presence of that bullet or fragment (armor or bullet) in the backing material, or by a hole which passes through the armor and/or backing material.Partial Penetration (PP):Any impact that is not a complete penetration is considered a partial penetration.3.24 Reference Bullet VelocityThe designated impact velocity of NIJ Standard−0101.04 test threat ammunition (sec. 5.4, table 1), obtained using specified ANSI/SAAMI unvented velocity test barrels.3.25 RetestThe NIJ CTP procedure for resolving ballistic performance issues with NIJ Standard−0101.04 compliant body armor models (sec. 5.22).3.26 Round Nose Bullet (RN)A bullet with a blunt or rounded nose. A bullet with a generally blunt or rounded nose or tip, which possesses a small flat surface at the tip of the bullet shall also be considered a round nose bullet for this standard.3.27 Semi Jacketed Hollow Point Bullet (SJHP)A bullet consisting of a lead core with a copper alloy (approximately 90 % copper and10 % zinc) jacket covering the base and bore riding surface (major diameter), which leaves some portion of the lead core exposed, thus forming a lead nose or tip, which has a hollow cavity or hole located in the nose or tip of the bullet.3.28 Semi Jacketed Soft Point Bullet (SJSP)A bullet, also known as a Jacketed Soft Point (JSP), consisting of a lead core with a copper alloy (approximately 90 % copper and 10 % zinc) jacket covering the base and bore riding surface (major diameter), which leaves some portion of the lead core exposed, thus forming a lead nose or tip.3.29 Strike FaceThe surface of an armor sample or panel, designated by the manufacturer, as the surface that should face the incoming ballistic threat.3.30 Wear FaceThe surface of an armor sample or panel, designated by the manufacturer, as the surface that should be worn against the body.3.31 YawThe angular deviation of the longitudinal axis of the projectile from its line of flight, measured as close to the target as practical.。
CE6.0主板文件备份工具bfs使用说明
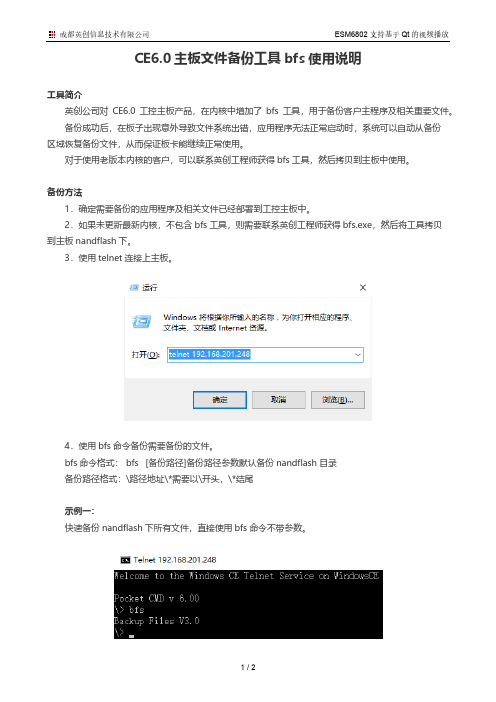
CE6.0主板文件备份工具bfs使用说明
工具简介
英创公司对CE6.0工控主板产品,在内核中增加了bfs工具,用于备份客户主程序及相关重要文件。
备份成功后,在板子出现意外导致文件系统出错,应用程序无法正常启动时,系统可以自动从备份
区域恢复备份文件,从而保证板卡能继续正常使用。
对于使用老版本内核的客户,可以联系英创工程师获得bfs工具,然后拷贝到主板中使用。
备份方法
1.确定需要备份的应用程序及相关文件已经部署到工控主板中。
2.如果未更新最新内核,不包含bfs工具,则需要联系英创工程师获得bfs.exe,然后将工具拷贝
到主板nandflash下。
3.使用telnet连接上主板。
4.使用bfs命令备份需要备份的文件。
bfs命令格式: bfs [备份路径]备份路径参数默认备份nandflash目录
备份路径格式:\路径地址\*需要以\开头,\*结尾
示例一:
快速备份nandflash下所有文件,直接使用bfs命令不带参数。
备份完成后DEBUG串口会打印备份内容及最后succeed信息。
示例二:
备份U盘目录下文件。
示例三:
当路径参数格式不对时(示例中未以*结尾),备份失败,提示信息如下
注意:
1.重复备份生效的是最后次备份内容。
升级应用程序后再次执行bfs命令即可重新备份。
2.bfs命令只备份命令路径下的文件,并不包括路径下的文件夹及文件夹内的内容。
3.测试该功能,可以在备份完成后,删除备份的应用程序,然后在运行模式下重启。
(重启后系统检测到没有应用程序,启动失败,会自动从备份区域恢复备份文件)。
ARTISAN TECHNOLOGY GROUP 质量用途设备来源说明书

DL205PLC User Manual Volume1of2Manual Number:D2-USER-MNotesDL205 PLC USER MANUALNotesVolume One: Table of Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .iVolume Two: Table of Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .xiChapter 1: Getting Started . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–2 The Purpose of this Manual . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–2 Where to Begin . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–2 Supplemental Manuals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–2 Technical Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–2 Conventions Used . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–3 Key Topics for Each Chapter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–3 DL205 System Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–4 CPUs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–4 Bases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–4 I/O Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–4 I/O Modules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–4 DL205 System Diagrams . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–5 Programming Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–7 Direct SOFT Programming for Windows. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–7 Handheld Programmer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–7 Direct LOGIC™ Part Numbering System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–8 Quick Start for PLC Validation and Programming . . . . . . . . . . . . . . . . . . . . . . . . .1–10 Steps to Designing a Successful System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .1–13Chapter 2: Installation, Wiring and Specifications . . . . . . . . . . . . . . .2–1 Safety Guidelines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–2Table of ContentsPlan for Safety . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–2 Three Levels of Protection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–3 Emergency Stops . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–3 Emergency Power Disconnect . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–4 Orderly System Shutdown . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–4 Class 1, Division 2, Approval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–4Mounting Guidelines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–5 Base Dimensions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–5 Panel Mounting and Layout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–6 Enclosures . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–7 Environmental Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–8 Power . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–8 Marine Use . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–9 Agency Approvals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–924 VDC Power Bases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–9Installing DL205 Bases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–10 Choosing the Base Type . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–10 Mounting the Base . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–10 Using Mounting Rails . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–11Installing Components in the Base . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–12Base Wiring Guidelines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–13 Base Wiring . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–13I/O Wiring Strategies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–14 PLC Isolation Boundaries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–14 Powering I/O Circuits with the Auxiliary Supply . . . . . . . . . . . . . . . . . . . . . . . . . . .2–15 Powering I/O Circuits Using Separate Supplies . . . . . . . . . . . . . . . . . . . . . . . . . . .2–16 Sinking / Sourcing Concepts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–17 I/O “Common” Terminal Concepts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–18 Connecting DC I/O to “Solid State” Field Devices . . . . . . . . . . . . . . . . . . . . . . . . .2–19 Solid State Input Sensors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–19 Solid State Output Loads . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–19 Relay Output Guidelines . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–21 Surge Suppression For Inductive Loads . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–21I/O Modules Position, Wiring, and Specification . . . . . . . . . . . . . . . . . . . . . . . . . .2–25 Slot Numbering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–25 Module Placement Restrictions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–25Table of ContentsSpecial Placement Considerations for Analog Modules . . . . . . . . . . . . . . . . . . . . .2–26 Discrete Input Module Status Indicators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–26 Color Coding of I/O Modules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–26 Wiring the Different Module Connectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–27 I/O Wiring Checklist . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–28D2-08ND3, DC Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–29D2-16ND3-2, DC Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–29D2–32ND3, DC Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–30D2–32ND3–2, DC Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–31D2-08NA-1, AC Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–32D2-08NA-2, AC Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–33D2-16NA, AC Input . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–34F2-08SIM, Input Simulator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–34D2-04TD1, DC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–35D2–08TD1, DC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–36D2–08TD2, DC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–36D2–16TD1–2, DC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–37D2–16TD2–2, DC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–37F2–16TD1(2)P, DC Output With Fault Protection . . . . . . . . . . . . . . . . . . . . . . . . .2–38F2–16TD1P, DC Output With Fault Protection . . . . . . . . . . . . . . . . . . . . . . . . . . .2–39F2–16TD2P, DC Output with Fault Protection . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–40D2–32TD1, DC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–41D2–32TD2, DC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–41F2–08TA, AC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–42D2–08TA, AC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–42D2–12TA, AC Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–43D2–04TRS, Relay Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–44D2–08TR, Relay Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–45F2–08TR, Relay Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–46F2–08TRS, Relay Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–47D2–12TR, Relay Output . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–48 D2–08CDR 4 pt., DC Input / 4pt., Relay Output . . . . . . . . . . . . . . . . . . . . . . . . . .2–49 Glossary of Specification Terms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .2–50Chapter 3: CPU Specifications and Operations . . . . . . . . . . . . . . . . . .3–1 CPU Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–2 General CPU Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–2 DL230 CPU Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–2 DL240 CPU Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–2 DL250–1 CPU Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–3 DL260 CPU Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–3CPU General Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–4 CPU Base Electrical Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–5 CPU Hardware Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–6 Communication Port Pinout Diagrams . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–6 Port 1 Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–7 Port 2 Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–8 Selecting the Program Storage Media . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–9 Built-in EEPROM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–9 EEPROM Sizes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–9 EEPROM Operations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–9 Installing the CPU . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–10 Connecting the Programming Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–10 CPU Setup Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–11 Status Indicators . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–12 Mode Switch Functions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–12 Changing Modes in the DL205 PLC . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–13 Mode of Operation at Power-up . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–13Using Battery Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–14 DL230 and DL240 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–14 DL250-1 and DL260 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–14 Battery Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–14 Auxiliary Functions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–15 Clearing an Existing Program . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–16 Initializing System Memory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–16Setting the Clock and Calendar . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–16 Setting the CPU Network Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–17 Setting Retentive Memory Ranges . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–17 Using a Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–18 Setting the Analog Potentiometer Ranges . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–19 CPU Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–21 CPU Operating System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–21 Program Mode Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–22 Run Mode Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–22 Read Inputs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–23 Read Inputs from Specialty and Remote I/O . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–23 Service Peripherals and Force I/O . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–23 CPU Bus Communication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–24 Update Clock, Special Relays and Special Registers . . . . . . . . . . . . . . . . . . . . . . . .3–24 Solve Application Program . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–25 Solve PID Loop Equations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–25 Write Outputs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–25 Write Outputs to Specialty and Remote I/O . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–26 Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–26 I/O Response Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–27 Is Timing Important for Your Application? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–27 Normal Minimum I/O Response . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–27 Normal Maximum I/O Response . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–27 Improving Response Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–28 CPU Scan Time Considerations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–29 Initialization Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–30 Reading Inputs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–30 Reading Inputs from Specialty I/O . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–31 Service Peripherals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–31 CPU Bus Communication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–32 Update Clock/Calendar, Special Relays, Special Registers . . . . . . . . . . . . . . . . . . . .3–32 Writing Outputs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–32 Writing Outputs to Specialty I/O . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–33 Diagnostics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–33 Application Program Execution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–34 PLC Numbering Systems . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–35PLC Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–35 V–Memory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–36 Binary-Coded Decimal Numbers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–36 Hexadecimal Numbers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–36Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–37 Octal Numbering System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–37 Discrete and Word Locations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–37 V–Memory Locations for Discrete Memory Areas . . . . . . . . . . . . . . . . . . . . . . . . . .3–37 Input Points (X Data Type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–38 Output Points (Y Data Type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–38 Control Relays (C Data Type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–38 Timers and Timer Status Bits (T Data type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–38 Timer Current Values (V Data Type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–39 Counters and Counter Status Bits (CT Data type) . . . . . . . . . . . . . . . . . . . . . . . . .3–39 Counter Current Values (V Data Type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–39 Word Memory (V Data Type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–39 Stages (S Data type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–40 Special Relays (SP Data Type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–40 Remote I/O Points (GX Data Type) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–40DL230 System V-memory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–41DL240 System V-memory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–43DL250–1 System V-memory (DL250 also) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–46DL260 System V-memory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–49DL205 Aliases . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–52DL230 Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–53DL240 Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–54DL250–1 Memory Map (DL250 also) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–55DL260 Memory Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–56X Input/Y Output Bit Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–57Control Relay Bit Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–59Stage Control/Status Bit Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–63Timer and Counter Status Bit Maps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–65Remote I/O Bit Map . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .3–66Chapter 4: System Design and Configuration . . . . . . . . . . . . . . . . . . .4–1DL205 System Design Strategies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–2 I/O System Configurations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–2 Networking Configurations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–2Module Placement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–3 Slot Numbering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–3 Module Placement Restrictions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–3 Automatic I/O Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–4 Manual I/O Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–4 Removing a Manual Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–5 Power–On I/O Configuration Check . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–5 I/O Points Required for Each Module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–6Calculating the Power Budget . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–7 Managing your Power Resource . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–7 CPU Power Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–7 Module Power Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–7 Power Budget Calculation Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–9 Power Budget Calculation Worksheet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–10 Local Expansion I/O . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–11 D2–CM Local Expansion Module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–11 D2–EM Local Expansion Module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–12 D2–EXCBL–1 Local Expansion Cable . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–12 DL260 Local Expansion System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–13 DL250–1 Local Expansion System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–14 Expansion Base Output Hold Option . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–15 Enabling I/O Configuration Check using Direct SOFT . . . . . . . . . . . . . . . . . . . . . . .4–16 Expanding DL205 I/O . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–17 I/O Expansion Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–17 Ethernet Remote Master, H2-ERM(-F) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–17 Ethernet Remote Master Hardware Configuration . . . . . . . . . . . . . . . . . . . . . . . . .4–18 Installing the ERM Module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–19 Ethernet Base Controller, H2-EBC(100)(-F) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–22 Install the EBC Module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–23 Set the Module ID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–23 Insert the EBC Module . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–23 Network Cabling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–2410BaseFL Network Cabling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–25 Maximum Cable Length . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–25 Add a Serial Remote I/O Master/Slave Module . . . . . . . . . . . . . . . . . . . . . . . . . . .4–26 Configuring the CPU’s Remote I/O Channel . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–27 Configure Remote I/O Slaves . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–29 Configuring the Remote I/O Table . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–29 Remote I/O Setup Program . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–30 Remote I/O Test Program . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–31 Network Connections to Modbus and Direct Net . . . . . . . . . . . . . . . . . . . . . . . . . .4–32 Configuring Port 2 For Direct Net . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–32 Configuring Port 2 For Modbus RTU . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–32 Modbus Port Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–33 Direct NET Port Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–34 Network Slave Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–35 Modbus Function Codes Supported . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–35 Determining the Modbus Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–35 If Your Host Software Requires the Data Type and Address . . . . . . . . . . . . . . . . . .4–35 If Your Modbus Host Software Requires an Address ONLY . . . . . . . . . . . . . . . . . . .4–38 Example 1: V2100 584/984 Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–40 Example 2: Y20 584/984 Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–40 Example 3: T10 Current Value 484 Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–40 Example 4: C54 584/984 Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–40 Determining the Direct NET Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–40 Network Master Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–41 Communications from a Ladder Program . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–44 Multiple Read and Write Interlocks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–44 Network Modbus RTU Master Operation (DL260 only) . . . . . . . . . . . . . . . . . . . .4–45 Modbus Function Codes Supported . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–45 Modbus Port Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–46 RS–485 Network (Modbus only) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–47 RS–232 Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–47 Modbus Read from Network (MRX) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–48 MRX Slave Memory Address . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–49 MRX Master Memory Addresses . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–49 MRX Number of Elements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–49 MRX Exception Response Buffer . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–49 Modbus Write to Network (MWX) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .4–50。
HP ProtectTools Security Manager用户指南说明书

Customer concernsAs computers become increasingly mobile and better connected, threats to data security are increasing in magnitude as well as complexity. Business customers, for whom data security can have a direct impact on the health of their business, are becoming increasingly concerned about this problem.Taking a holistic approach to security, HP has developed the HP ProtectTools Security Manager to bring many technology areas together in a way that ensures not only protection for client devices, but also ensures that client devices themselves do not become points of vulnerability that could be used to threaten the entire IT infrastructure. Security solutionsHP ProtectTools Security Manager addresses the four challenges that are keeping security features from being widely deployed and used. These are:ability — HP ProtectTools Security Manger offersa single client console that unifies security capabilities under an easy to use common user interface.2.Manageability— The modular architecture of the HP ProtectTools Security Manger enables add-on modules to be selectively installed by the end user or IT administrator, providing a high degree of flexibility to customize HP ProtectTools depending on need or underlying hardware configuration.3.Interoperability— HP ProtectTools Security Manger is built to industry standards on underlying hardware security building blocks such as embedded security chips designed to the Trusted Computing Group (TCG) standard and Smart Card technology.4.Extensibility— By using add-on software modules, HP ProtectTools Security Manager can easily grow to handle new threats and offer new technologies as they become available.The flexible plug-in software modules of HP ProtectTools Security Manager allow customers to choose the level of security that is right for their business. A number of modules are being introduced that provide better protection against unauthorized access to the PC, while making accessing the PC and network resources simple and convenient for authorized users.HP ProtectTools features guideModule Key FeaturesEmbedded Security for HP ProtectToolsprovides important client security functionality using a TPM embedded security chip to help protect against unauthorized access to sensitive user data or credentials. BIOS Configuration for HP ProtectTools*provides access to power-on user and administrator password management, easy configuration of pre-boot authentication features, such as Smart Card, power-on password and the TPM embedded security chip.Smart Card Security for HP ProtectToolsallows customers to work with the BIOS to enable optional Smart Card authentication in a pre-boot environment, and to configure separate Smart Cards for an administrator and a user. Customers can also set and change the password used to authenticate users to the Smart Card, and backup and restore credentials stored onthe Smart Card.Credential Manager for HP ProtectToolsacts as a personal password vault that makes accessing protected information more secure and convenient. Credential Manager provides enhanced protection against unauthorized access to a notebook, desktop or workstation, including alternatives to passwords when logging on to Microsoft Windows and single sign-on capability that automatically remembers credentials for websites, applications, and protected network resources. •TPM embedded security chips are designed to work with a growing number of third party software solutions while providing a platform to support future hardware and operating system architectures.•Enhances a broad range of existing applications and solutions that take advantage of supported industry standard software interfaces.•Helps protect sensitive user data stored locallyon a PC.•Provides an easier to use alternative to the pre-boot BIOS configuration utility known as F10 Setup.•Helps protect the system from the moment power is turned on.•Embedded security chip enhanced Drivelock* helps protect a hard drive from authorized access even if removed from a system without requiring the user to remember any additional passwords beyond the embedded security chip user passphrase.•User interface is fully integrated with other security software modules for HP ProtectTools.•Configures the HP ProtectTools Smart Card for user authentication before the operating system loads, providing an additional layer of protection against unauthorized use of the PC.•Provides users with the ability to back up and restore credentials stored on their Smart Card.•Users no longer need to remember multiple passwords for various password protected websites, applications and network resources.•Single sign-on works with multifactor authentication capabilities to add additional protection, requiring users to use combinations of different security technologies, such as a Smart Card and biometric, when authenticating themselves to the PC.•Password store is protected via encryption and can be hardened through the use of TPM embedded security chip and/or security device authentication, such as Smart Cards or biometrics.The table below details the key customer features and benefits of the newHP ProtectTools offerings:Customer ScenariosScenario 1 — Targeted TheftA notebook containing confidential data and customer information is stolen in a targeted theft incident at an airport security checkpoint.HP ProtectTools technologies and solutions:•Pre-boot authentication feature, if enabled, helps prevent access to the operating system.•Drivelock* helps ensure that data cannot be accessed even if the hard drive is removed and installed into an unsecured system.•Personal Secure Drive feature, provided by the Embedded Security for HP ProtectTools module, encrypts sensitive data to help ensure it cannot be accessed without authentication.Scenario 2 — Unauthorized access from internal or external locationA PC containing confidential data and customer information is accessed from an internal or externallocation. Unauthorized users may be able to gain entry to corporate network resources or data from financial services, an executive, R&D team, or private information such as patient records or personal financial data.HP ProtectTools technologies and solutions:•Pre-boot authentication feature, if enabled, helps prevent access to the operating system.•Embedded Security for ProtectTools helps ensure that data cannot be accessed even if the hard drive is removed and installed into an unsecured system.•Credential Manager for ProtectTools helps ensure that even if an unauthorized user gains access to the PC, they cannot get passwords or access to password protected applications.•Personal Secure Drive feature, provided by the Embedded Security for HP ProtectTools module, encrypts sensitive data to help ensure it cannot be accessed without authentication.Scenario 3 — Strong Password PoliciesA legislative mandate goes into effect that requires the use of strong password policy for dozens of Web based applications and databases.HP ProtectTools technologies and solutions:•Credential Manager for HP ProtectTools provides a protected repository for passwords and single sign-on convenience.•Embedded Security for HP ProtectTools protects the cache of usernames and passwords, which allows users to maintain multiple strong passwords without having towrite them down or try to remember them.HP ProtectTools technologies and solutionsFor more information:HP ProtectTools Security Solutions/hps/security/productsHP Business PC Security Solutions/products/securityHP Business PC Security Solutions/products/securityHP ProtectTools white paper/bc/docs/support/SupportManual/c00264970/c00264970.pdf*Available on select HP Business notebook computers.© 2005 Hewlett-Packard Development Company, L.P. The information contained herein is subject to changewithout notice. The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additionalwarranty. HP shall not be liable for technical or editorial errors or omissions contained herein.For more information about HP products and services, visit 。
BU_61580寄存器说明中文版

目录
1 SOFTWARE INTERFACE 软件接口 ....................................................................................................................... 1 1.1. POWER TURN-ON/INITIALIZATION STATE 上电/初始化状态 .................................................................... 1 1.2. OVERALL ADDRESS MAPPING: WORDS VS. BYTES 整体地址映射:字 和 位 ........................................ 2 1.3. SOFTWARE INTERFACE: INTERNAL RAM 软件接口:内部 RAM .............................................................. 3 1.4. INTERNAL REGISTERS ADDRESS AND BIT MAPPING 内部寄存器地址和位映射 ..................................... 3 1.5. INTERRUPT MASK REGISTER 中断屏蔽寄存器 ........................................................................................ 6 1.5.1. RAM PARITY ERROR RAM 校验错误..................................
CKD EBS-M G系列滑块EBR-M G系列杆带内置导轨INDEX ECR系列ECG系列控制器控

EBS Series Conventional
Conventional product
Body width
64 mm
Static
MP 25.7 N·m
allowable MY 25.7 N·m
moment
MR
58 N·m
EBS-05 54 mm 103 N·m 103 N·m
144 N·m
For press fitting and hoisting
to return to origin when the power is
Origin
ห้องสมุดไป่ตู้
turned ON, and there is no need to install an origin sensor. This allows quick recovery from an emergency stop
EBR-M/G Series
47
Series variation ......................................................... 48 EBR-04M/G............................................................... 52 EBR-05M/G............................................................... 62 EBR-08M/G............................................................... 72 Technical data .......................................................... 82
XRD分析软件

Siroquant Version 3 User ManualPublished by:Sietronics Pty LimitedUnit 3/22 Walder StPO Box 3066Belconnen ACT 2616Email: spl@.auWeb: .auCopyright © 2007 Sietronics Pty Limited. All rights reserved. First edition: December 2006, minor revisions, March 2007.Siroquant Version 3 User ManualTable of Contents Introduction (1)Manual Overview: (1)Manual Conventions: (1)1.Siroquant Overview (2)1.1Software Description (2)1.2Siroquant Objectives (2)1.3.Software License, Trademark and Copyrights (2)1.4Computer Specifications (2)1.5Installation Instructions (3)1.6Folders (4)2.Siroquant Files (5)2.1Task Files (*.TSK files) (5)2.2Task Option File (5)2.3Data Files (various types) (5)2.4Databases and Databanks (6)2.4HKL files (6)3.Siroquant User Interface (9)3.1Main Application Window (9)3.2Task Display (10)3.3Main Application ToolBar (12)4.Basic Level Operations (16)4.1Preparing Calculated *.HKL Files (16)4.2Preparation of An Analytical Task (18)4.3Task Parameters Dialog (21)4.4Phase Dependent Parameters Dialog (23)4.5Stage Control and Refinement dialog (26)4.6Background Refinement dialog (28)4.7Background Subtract dialog (29)4.8Excluded Regions form (31)4.9Calibration form (32)4.10Advanced Halfwidths (33)4.11Editing the Current Task (35)4.12Starting a refinement (38)4.13Displaying hkl Bars (38)4.14HKL Bar Palette (39)4.15Quantitation Results (40)4.16Quantitation Charts (41)4.17Refinement Statistics χ² (42)4.18Overview of Intermediate level features (43)4.19Overview of Advanced level features (44)5.Intermediate Level Operations (45)5.1Extra Display Features (45)5.2Template Tasks (46)5.3New Task Wizard (48)5.4Phase Status (52)5.5Phase Preview (52)5.6Print Out (54)5.7Calculate Menu Functions (56)5.8Long Results Dialog (58)5.9Phase Profiles (58)5.10Information Menu (59)5.11Options (61)5.12Verify Task Phases (64)6.Advanced Level Operations (65)6.1Tools Menu (65)6.2Advanced hkl Preparation (65)6.3Refinement History (65)6.4Overlay Scan (66)6.5Refinement Extras (66)6.6Search Match (67)6.7Composition Analysis (67)6.8Brindley Trials (67)7. A step by step guide to quantifying a sample: (69)IntroductionSiroquant Version 3.0 is an integrated 32-bit program for use with 32 bit Windows operating systems and modern PCs. All the elements of the previous 16 bit Windows interface and the Fortran calculation programs have been merged into a single application and the entire program has been rewritten into a new programming language.Siroquant Version 3.0 incorporates new features requested previously but which could not be incorporated because of programming language constraints. It also has new ways of doing some operations, mainly because it is now a fully integrated program and better software controls are now available. There are more user settable options in version 3 than were previously available. The initial default values for these are consistent with version 2.5 as far as practical.Manual Overview:This manual is divided into seven chapters:• Chapter 1 contains basic information on the program, copyright and installation instructions.• Chapter 2 contains information on the various files used by the program.• Chapter 3 contains information on the user interface.• Chapter 4 has a description of the basic operations needed to use version 3 effectively.• Chapter 5 contains a detailed description of the intermediate operations of Siroquant.• Chapter 6 contains a detailed description of the advanced operations of Siroquant. • Chapter 7 contains a description of the process of analyzing a sample using the quartz/zincite demo scan.Manual Conventions:Icons are used in this manual to identify various types of information as follows:Significant differences between version 3 and previous versions withan explanation of the difference between the versions for the benefit ofSiroquant users familiar with previous versions.Useful hints1. Siroquant Overview1.1 SoftwareDescription Siroquant Version 3.0 is written for Quantitative Phase Analysis from X-ray Powder Diffraction Patterns of mixtures of solid phases such as found in many scientific and industrial applications. It is compatible with Microsoft Windows XP, 2000 and NT. Version 3.0 is a fully integrated 32-bit application (or program) with a Multi Document Interface (MDI) style user interface. The application has been written in Delphi 6 and uses the TeeChart control for all graphics support.The software principally uses the “Rietveld” technique. The 32 bit extended DOS programs TRACSCAL, PREP & STRUCT and the 16-bit SQWIN interface have now been integrated into one 32-bit program.The MDI style interface now allows more than one task to be open atthe same time. Working files are handled very differently to earlierversions. 1.2 Siroquant ObjectivesSietronics is committed to the long-term development and support of Siroquant. Our objective is to continue to develop the software to be as scientifically accurate as the powder XRD technique will allow, while retaining its user-friendliness and suitability for accurate solid phase analysis.1.3. Software License, Trademark and CopyrightsThe use of copies of the Siroquant™ software is limited to purchasers of copies with the WIBU protection device that is required to operate the software.Windows is the registered trademark of Microsoft Corporation. Copyright (c) 1985-2007 Microsoft Corp.WIBU is the registered trademark of WIBU Systems AG. Copyright © 2007 Wibu Systems AG.Siroquant™ is the registered trademark of CSIRO Australia.Delphi is a registered trademark of Borland Software Corporation.TeeChart is a registered trademark of Steema Software.Adobe Acrobat is the registered trademark of Adobe Systems Incorporated.Manual Contents Copyright (c) 1988-2007 Sietronics Pty Ltd. All Rights Reserved.1.4 Computer SpecificationsA Pentium III PC with at least 256 megabytes of RAM, recommended is a Pentium IV 2 GHz (or better) with 512 megabytes of RAM. Extra memory may be needed if multiple tasks analyzing patterns with many step points or with many phases are open at the same time. Windows 98, NT, 2000 or XP are required for operation. The minimum screen resolution required is 800 X 600 (1024 x 768 or better is recommended) and a CD-ROM drive is required for the installation of the software. The computer must have either a spare USB port or a parallel port for the dongle.The program is compatible with dual monitor displays (e.g. 1600 x 600). The program can also take advantage of computers with multiple processors, dual core processors or single processors with hyper-threading.Important notes:•If you are using the Windows XP, 2000 or Windows NT operating systems, you willneed to be logged in with administrative privileges to install the dongle driver. • If you are using the Windows NT or Windows 98 operating systems, you may need toinstall the ADO driver to utilize the database. Please check the Microsoft website () and search for the “MDAC Redistributable” for the latestrelease and install this.• If you have an Iomega Zip drive located on the parallel port, place the dongle after the zip drive. You should also not try to access Siroquant files (task, scan or HKL files) from the Zip drive, as the dongle will not work properly under thesecircumstances.•If you have a printer attached to the PC working in bi-directional mode, you may need to have this printer switched on for the dongle to operate correctly. 1.5.2 WIBU DongleA correct dongle must be present at all times on the computer on which Siroquant Version 3 is running. The program will not start without the dongle present and if the dongle is removed while the program is running, the program may terminate. Siroquant v3 may be installed on as many computers as desired but only one computer can run it at any one time with only one dongle. If additional licenses are required, please contact Sietronics.If you do use more than one computer with one dongle ensure thatSiroquant v3 is closed before removing the dongle. It may be easier toconnect USB dongles via an extension cable on each computer.1.5.3 Manuals on CD-ROMThe full text of the manuals is available on the installation CD-ROM in the “Manuals”folder. The manuals include this manual, Technical, Clay and File Formats manuals. The latest version of the Adobe Acrobat ® reader software is also available on the CD-ROM. The manuals can also be viewed from inside the program’s user interface as well.1.5.4 Siroquant UpdatesAn Internet web page has also been established for the download of program updates. This is designed to ensure that users keep up to date with the latest version of the program. The web address is:.au/siroquantThe Internet address for updates can also be called from the Help Menu within Siroquant.1.6 FoldersDepending on the installation parameters used, the installation program will have created a directory structure similar to that shown below. The default installation folder is “C:\Program Files\Siroquant\v3” and is recommended. An alternative folder may bespecified when installing Siroquant. The main installation folder has various subfolders. These folder names must not be changed or deleted.Note: The terms ‘folder’ and ‘directory’ are the same in Siroquant the former being thelatest used by Microsoft.Because Version 3.0 is a 32 bit application it fully supports long filenames including folder names. Users should avoid the use ofextensions in folder names or file names with more than oneextension, that is two or more periods. 1.6.1 \DatabaseThis folder holds the registered database including the Standard database “Quantlib v3.mdb”. User databases are pairs of database (.mdb) and databank (.dat) files. An example user database Quantv3.mdb & Quantv3.dat is supplied. The subfolder “\Templates ” contains an Access database file that is used as a template for userdatabases and “\Removed ” contains any user database removed from the parent folder (under control of supplied software).1.6.2 \Output TemplatesThis folder contains text template files for formatting output when printing results.1.6.3 \ManualsThis folder holds the manuals as .pdf files.1.6.4 \Display SettingsThis folder is not currently used.1.6.5 \ExamplesThis folder and its subfolders contain various examples for use with version 3. The user should create their own folders for storage of user task files and HKL files.2. Siroquant Files2.1 Task Files (*.TSK files)Task files are the ‘document’ files of Siroquant. After installation ‘opening’ a task file inExplorer will open Siroquant and the task file just like opening a .doc file opens Microsoft Word. Task files contain information necessary for the analytical task, most importantly the scan to be analysed, the phases to be quantified and refinement data. Task files are text files arranged in a similar way to an .ini type file. Long file names are allowed for tasks. The characters ampersand (‘&’) and hash (#) should be avoided in task file names as they are for special use in Siroquant. Tasks have a version number that is found on the first line of the task and for version 3 it is 10005.Task files in version 3 have a different format to earlier versions(10003 & 10004). When version 2.0 and Version 2.5 task files areopened they will be automatically converted to Version 3 task files and‘v3’ will be added to their name part of the file name. 2.1.1 Template tasksTemplate tasks can be set up to provide a common starting point for similar analyses. They have the same format as a task file but their extension is .tmk and version number is 20005. A task file and a template task file must not have the same name in a folder. Template tasks are further discussed in Section 5.2.2.1.2 Ancillary Task Files Tasks will have extra files associated with them for extra information associated with a task. These are described in detail in the File Formats manual and they will be mentioned elsewhere in this manual. They have extensions .cps, .cpd, .cpk and .nnn where n is 0 to 9. They are always placed in the same folder as the task.In earlier versions of Siroquant various intermediate files weregenerated during a refinement and were overwritten by everyrefinement whether it was the same or different task. The equivalentof some of these are now included in the ancillary files. Also thecalculated pattern, the background profile and the difference pattern files now have the same name as the task and not necessarily the same as the pattern. This is all a consequence of Siroquant v3’s being able to have open and refine more than one task at a time. 2.2 Task Option File One of the ancillary files is an .ini type file (extension .998) that is used to save various information and options related to the task. What is saved and how it is used can depend on how options have been set.An example of one these options is that every task maintains its ownhkl options and hkl colors. 2.3 Data Files (various types)XRD analysis begins with an XRD pattern collected as (preferably) a step scan from an automated XRD instrument. The raw data files from most common diffractometer software packages can be read by SQv3. When a task is set up the raw data file isspecified into the task and, if necessary, is converted into a ‘.cpi format. This is called the ‘original’ pattern.The original pattern may be calibrated and can have the background subtracted. These result in the ‘active’ pattern with extensions of either .cpc or .cpb. An alternative to subtracting the background is to use background refinement; either method may be appropriate depending on the pattern type. The ‘active’ pattern is the pattern used forrefinement.In earlier versions all raw data files were automatically converted to*.cpi format (which is easy to read or edit) but in Version 3 this is onlydone if the raw data file has or is capable of storing more than onepattern or if extra information not present in the raw data file isrequired. A cpi format file can be saved by selecting the Save Scanaction and then ‘Original Scan’.The term ‘active scan’ in version 3 refers to the scan that is used in therefinement. 2.4 Databases and DatabanksDatabanks are files (.dat) that hold crystallographic data for phases. Phases are the components of a sample that will be will quantified. Microsoft Access databases (.mdb) are used to hold further information about the phases. These databases are used by Siroquant for the selection of the phases to form part of the task.2.4.1 Standard DatabaseA Standard Database (“C:\Program Files\Siroquant\v3\Database\Quantlib v3.mdb”) with over 1500 phases is provided as part of Siroquant v3. There is no correspondingdatabank file (.dat) because the crystallographic data is stored inside the database itself.Version 2.0 and 2.5 databases can be converted using “ConvertToV3.exe”. This program can also be started from the Toolmenu using the “Convert v2 & v2.5 Database to v3” menu item.2.4.3 Example User DatabaseThe files “Quant v3.mdb” and “Quant v3.dat” contain the first 300 phases of the standarddatabank. This is the databank that was available with version 2.0.database can be specified directly in the task in which case the equivalent of an hkl file isgenerated each time the task is opened*. HKL files are text based files. The version 3 hklfile (10005) is in an .ini style format. Version 2 & 2.5 hkl file (other than the Clay Packfiles) are compatible. HKL files basically consist of phase parameters and the reflectionsfor the phase.* This has been made possible by the integration of the previous DOS programs and byfaster modern computers.2.4.1 Observed HKL FilesSiroquant is able to substitute F o (hkl) for F c (hkl) in the Rietveld calculation allowingquantification of phases for which there is no published crystal structure. Observed *.hklfiles have been prepared for many common clays which have very disordered and ill-defined structures. These are included in the Standard database and are specified in thecompanion “Clay Package Manual”. The Siroquant user cannot prepare (hkl) files fromthe structure database for these structurally disordered mineral phases; these are alreadysupplied for use with Siroquant. In version 3 supplied observed HKL files are included inthe Standard database. Also non-Clay Pack observed phases are supplied as hkl filesinstalled with the program.Supplied observed hkl files are included in the Standard database andhave a reference ID > 5000 and are also supplied as disk HKL filesexcept for the Clay or any other special package files. These fileshave a reference ID number > 8000. The non-clay phases for which no crystal structure data could be found also haveobserved (hkl) files and are listed below. These are located, for the standard setup, in thedirectory “C:\Program Files\Siroquant\v3 \Observed”. Special Phase(No Crystal Structure Data)Standard Database Serial #Name of “Observed” (hkl) File para-Spurrite 5197 pspurr1.hkl Pyrrhotite-5c 5199 pyrr5c_1.hklCaSiF6 5235 CaSiF61.hkl Theta-alumina 5299 thal1.hkl Talc, disordered 5320 talb1.hkl2.4.2 Clay Pack Observed hklClays often have very disordered and ill-defined structures - many common types of claylisted below have been included in the databank and these are also specified in thecompanion “Clay Package Manual”.Clay phases with imperfect or unknown crystal structures are included in SiroquantVersion 3.0: When a Clay Pack phase is added to a task it must be specified directly fromthe Standard database. HKL files in Version 3 are not supplied separately for Clay Packphases but included in the Standard database.Do not use Clay Pack files from previous versions of Siroquant as theyare no longer valid in version 3. When an earlier version task isconverted any Clay Pack, observed hkl files are automaticallyreferenced to the Standard database.The Clay Pack phases are:Clay Mineral in Siroquant Clay Package Crystal Structure Status Clay PackageDemonstration TaskFilenamesRef. IDNumberAntigorite Modulatedstructure (unknown) Antig, Antig18 8237Halloysite Curved lattice (unknown) Halloy, Halloy18 8161Illite Mica-like(unknown) Illite,Illite208146Moderately Ordered 1Tc Kaolin, No 1. Unknown Kaoord,Kaoord138240Moderately Ordered 1Tc Kaolin No 2 Unknown Kaodis1,Kaodi1208440Disordered 1Tc Kaolinproduced by grindingKaolin No 2Unknown Kaodis2, Kaodi220 8441Highly Disordered 1Tc Kaolin Unknown Kaodisor,Kaodis508442Highly Disordered 1Md Kaolin Unknown Kao1Md,Kao1Md368239Montmorillonite Poorly Known Mont, Mont24 8137 Amorphous Opal,Tridymite-basedAmorphous, Tridymite-like regions SI02FUM 8101 Palygorskite (Attapulgite) Poorly Known Paly, Paly27 8237Mixed-Layer Illite- Smectite Unknown Mixlayer,Mixlay188236Meta-Kaolin Unknown Metako,Metako3082743.Siroquant User InterfaceTo effective utilize this part of the manual you should have Siroquant v3 installed and the dongle attached. There may be slight inconsequential differences between what may be shown on your computer screen and what is shown in the text. Some differences may be due to how Windows is set up. There may also be some color differences to the default setup.3.1 Main Application WindowThe main Siroquant application window is a multiple document interface (MDI) application. It features (from the top):CaptionThe number in the brackets is the session number. This is incremented for a user each time Siroquant v3 is started. Main MenuShows the menu commands available when no tasks are opened. Tool Bar Siroquant for Windows allows shortcuts for frequently used functions viaa tool bar (button bar). If no tasks are open very few buttons areenabled. Some buttons have a drop down menu for additional actions.The top most item of the drop down menu is the same action as thebutton itself.Client Area The main area of the application window is the client area where the childwindows of the MDI are placed. The only type of child window in is thedialog that displays each open task.Status Bar The bottom most part is the status bar. It is divided into four panels:1. Hint for a selected action from the main menu and toolbar.2. Identifies whether the active task is saved or not.3.Identifies the active task. Each task is identified by a letter enclosed in square brackets (e.g. [A]). Every open window or dialog associated with the task has its caption preceded by this identification. 4. The folder (directory) where the active task resides and therefore the current directory.In earlier versions of Siroquant the current directory wasthe Siroquant directory. In v3, no working files need to beplaced in the program directory.3.2 Task DisplayFor the following example open the task (press Ctrl-O) and open the following task:“C:\Program Files\Siroquant\v3\Examples\Manual Demos\ Demo Task Display.tsk”.The above shows the task window maximized in the MDI client area. The captions for themain application window and the task window have been combined.There are significant differences in operation between version 3 andearlier versions. The following should be read by users of earlierversions of Siroquant. The display of hkl bars is discussed in Section 4.13. Extra display features are discussed in section 5.1.3.2.1 General DescriptionThe plot above is what is displayed after a refinement. The calculated pattern (red) is overlaid on the active pattern (yellow). The difference pattern (blue) is shown below the other plots. The difference trace is the active trace with the calculated trace subtracted. Also shown is a magenta trace for the background profile because background refinement was included.The first four panels of the status bar show the position of the last left mouse click. Two more panels indicate the status of the keyboard Ctrl, Alt and Shift keys.3.2.2 Zooming & UnzoomingTo zoom a section of the plot, draw a rectangle from the top-left to the bottom-right by holding down the left mouse button. The plot may be further zoomed in the samemanner. To unzoom reverse the operation, that is draw a rectangle anywhere from thebottom left to the top right.The plot returns to the original, not to the previous zoom operation.The difference trace is not zoomable. 3.2.3 ScrollingThere are two methods of scrolling. Firstly: you will notice that on a zoomed plot red arrows appear at each end on the two-theta axis. The left most shifts the current scan graph to the left (displaying lower 2θ angles) and the right most shifts the current scan graph to the right (higher 2θ angles). The range of the intensity values is not affected. Secondly: hold the middle mouse button (or scroll wheel) down and move the mouse. Torecover from scrolling unzoom the display (i.e. draw a rectangle from the bottom left to top right while holding down the left mouse button).3.2.4 Reading the Position Points on the Plot and TracesWhen certain actions are executed the first four panels of the status bar at the bottom of the task display window show the two-theta angle, d-spacing, reading and the relative intensity to either of the active, calculated or difference traces. The various types are:A. Any point on the plot area.Click the left mouse button on the plot: The x-values of the angle and d-spacing will always be shown. The y-value shown depends on which zone of the plot area is clicked. The relative intensity is either relative to the active trace or the difference trace. If the shift key on the keyboard is held down the calculated trace, if present, will be used instead of the active trace.B. Points on a Trace.If you hold down the Ctrl key and click the left mouse button or move the mouse a point on the active or difference trace will have a small circle drawn around it and its coordinates will be shown in the status bar. If the Shift key is also held down then the calculated trace, if present, is used instead of the active trace. In thesecircumstances no zoom box can be drawn unless the Alt key is held down as well.The above emulates facilities available in the earlier versions ofSiroquant. The right mouse button in v3 is used for other purposes(usually to show a popup menu) and there is no ‘active’ trace selectionin the pre v3 style. 3.2.5 Chart Popup MenuIf the mouse is right clicked over the chart area a popup menu related to the chart isdisplayed. Access to the OEM (original equipment manufacturer) controls is supplied on an ‘as is’ basis. They are beyond the control of Sietronics and limited assistance can beprovided in their use.3.2.5.1 Popup Menu item: EditThis is an OEM chart editing tool supplied by TeeChart. It can be used to edit various chart features. Changes made are not remembered and could be lost when the chart is redrawn. Care should also be taken as some deletions could cause program exceptions. The principle use would be to ready the chart for print out.3.2.5.2 Popup Menu item: PrintThis is an OEM print preview tool supplied by TeeChart. It can be used to print out the chart as it is currently displayed as. The user should experiment with the various controls on the print preview dialog for best results. See also Print Colors below.3.2.5.3 Popup Menu item: ExportThis brings up the part of the OEM chart editor related to export of the chart and its data.3.2.5.4 Popup Menu item: Print ColorsClicking this item changes the colors to those suitable for printing. Clicking the item a second time reverts to the original colors. The print colors can be edited in the main menu item Options/Main Display & Colors/Print set page.3.2.5.5 Popup Menu item: hkl Bar OptionsThis is equivalent to the main menu item Display/hkl Bar Options. Note that changes to these options only affect the active task window and other tasks are unaffected.3.2.5.6 Popup Menu item: Cross HairsCross hairs can be displayed on the main of difference plots with the coordinates of the cross hairs being displayed on the Task Window’s status bar. Cross hairs commands are:Off No cross hairs are displayedOn Active The Relative Intensity will be with respect to the active trace.On Calculated The Relative Intensity will be with respect to the calculated trace.On Diff.The cross hairs will be displayed on the difference trace and therelative intensities will be with respect to that trace.Stick to Trace If selected the cross hairs will stay on the trace as determinedabove.3.2.5.7 Popup Menu item: Add AnnotationAnnotations can be added to the plot. These are stored and are redisplayed each time the task is opened. As annotations are labels for one series they are the same font and color. The following dialog is brought up:The initial coordinates are those of the last left mouse click on the chart. Annotations can be edited with the Main Menu Command Display/Annotation List. See Section 5.1.1. 3.3 Main Application ToolbarIn earlier versions, this was referred to as the button bar. Version 3uses smaller buttons similar to standard Windows applications.The toolbar has short cuts for the most frequently used functions in Version 3. The toolbar is not customizable. Some buttons have a drop down menu for additional actions. Thetop most item of the drop down menu is the same action as the button itself.。
IBM SPSS Amos 安装说明(站点许可证)说明书

IBM SPSS Amos Installation Instructions(Site License)The following instructions are for installing IBM®SPSS®Amos™version21using a site license.This document is for end users who are installing IBM SPSS Amos on their desktop computers.If you are a site administrator,see the Site License Administrators Guide for information aboutdistributing the installation to end users.During installation,you will be prompted for the following information.Contact your siteadministrator if you do not have the following information.Name:Organization:Authorization Code:System Requirements for IBM SPSS AmosThe minimum hardware and software requirements for IBM®SPSS®Amos™are as follows:Operating system and software⏹Microsoft Windows XP(32-bit version),Windows Vista(32-bit and64-bit versions),orWindows7(32-bit and64-bit versions).⏹ Framework4.0Configuration⏹Intel or AMD processor⏹256megabytes(MB)of RAM or more⏹125MB of available hard-disk space⏹If using physical installation media,DVD/CD drive⏹Super VGA(800x600)or a higher-resolution monitorAuthorization CodeYou will also need your authorization code(s).You should have received your authorizationcode(s)from your administrator.The authorization code enables you to obtain a license for IBMSPSS Amos.If you cannot find your authorization code,contact your administrator.In somecases,you might have multiple codes.You will need all of them.Note:You cannot run IBM SPSS Amos remotely via Windows Terminal Services or Citrix with asite license.©Copyright IBM Corp.1995,201212IBM SPSS Amos Installation Instructions(Site License)Installing IBM SPSS AmosYour administrator might have given you an installation disk or identified a network locationfrom which to install.Check with your administrator if you do not know how you are supposedto install IBM®SPSS®Amos™.Note:To install IBM SPSS Amos,you must be logged on to your computer with administratorprivileges.Installing from a Downloaded FileWindows XPE Double-click the file that you downloaded and extract the files to some location on your computer.E Using Windows Explorer,browse to the location where you extracted the files and double-clicksetup.exe.E Follow the instructions that appear on the screen.See Notes for Installation on p.3for anyspecial instructions.Windows Vista or Windows7You must run the installer as administrator:E Double-click the file that you downloaded and extract all the files to some location on yourcomputer.E Using Windows Explorer,browse to the location where you extracted the files.E Right-click setup.exe and choose Run as Administrator.E Follow the instructions that appear on the screen.See Notes for Installation on p.3for anyspecial instructions.Installing from the DVD/CDWindows XPE Insert the DVD/CD into your DVD/CD drive.The AutoPlay feature presents a menu.E On the AutoPlay menu,click Install IBM SPSS Amos,and then follow the instructions that appearon the screen.See Notes for Installation for any special instructions.Windows Vista or Windows7You must run the AutoPlay as administrator:E Close the AutoPlay window that automatically appeared when you inserted the DVD/CD intoyour DVD/CD drive.3IBM SPSS Amos Installation Instructions(Site License)E Using Windows Explorer,browse to the DVD/CD drive.E Right-click setup.exe in the Windows subfolder and choose Run as Administrator.E On the AutoPlay menu,click Install IBM SPSS Amos,and then follow the instructions that appearon the screen.See Notes for Installation for any special instructions.Installing from a Network LocationE Using Windows Explorer,browse to the location that your administrator provided for the setup.exefile.E If your computer is running Windows Vista or7,right-click setup.exe and choose Run asAdministrator.Otherwise,double-click the file.E On the AutoPlay menu,click Install IBM SPSS Amos,and then follow the instructions that appearon the screen.See Notes for Installation for any special instructions.Notes for InstallationThis section contains special instructions for this installation.License type.Be sure to select Site License.Licensing Your ProductAfter the main part of the installation is complete,click OK to launch the License AuthorizationWizard.The License Authorization Wizard allows you to obtain a license for IBM®SPSS®Amos™.If you do not get a license now,you can enable IBM SPSS Amos to be used for a temporary usageperiod.After the temporary usage period has completed—and which begins when the product isfirst used—IBM SPSS Amos will no longer run.Therefore,it is recommended that you obtain alicense as soon as possible.You must either obtain a license or enable for temporary usage touse IBM SPSS Amos.Note:Licenses are tied to your computer’s hardware with a lock code.If you replace yourcomputer or its hardware,you will have a new lock code and will need to repeat the authorizationprocess.This is also true if you re-image your computer.If you find out that you exceeded theallowable number of authorizations specified in the license agreement,contact your administrator.Warning:The license is sensitive to time changes.If you must change the system time and thencannot run the product,contact your administrator.Using the License Authorization WizardE If you don’t launch the License Authorization Wizard during installation or cancel the LicenseAuthorization Wizard before obtaining a license,you can launch it by choosing LicenseAuthorization Wizard in the Windows Start menu program group for IBM®SPSS®Amos™.On4IBM SPSS Amos Installation Instructions(Site License)Windows Vista or7,you must run as administrator.Right-click the License Authorization Wizardshortcut and choose Run As Administrator.E When prompted,choose License my product now.If you want to enable for temporary usageinstead,refer to Enabling for Temporary Usage on p.4.E When prompted,enter one or more authorization codes.You should have received theauthorization code(s)from your administrator.The License Authorization Wizard sends your authorization code over the Internet to IBM Corp.and automatically retrieves your license.If your computer is behind a proxy,click Configureproxy settings and enter the appropriate settings.If the authorization process fails,you will be prompted to send an e-mail message.Choosewhether you want to send the e-mail message through your desktop e-mail program or through aWeb-based e-mail application.⏹If you choose the desktop option,a new message with the appropriate information will becreated automatically.⏹If you choose the Web-based option,you must first create a new message in your Web-basede-mail program.Then copy the message text from the License Authorization Wizard andpaste it into your e-mail application.Send the e-mail message and respond to the prompt in the License Authorization Wizard.Thee-mail message will be processed almost instantaneously.You can click Enter License Code(s)to enter any license code(s)that you receive.If you already closed the License AuthorizationWizard,restart it and select License my product now.On the Enter Codes panel,add the licensecode that you received and click Next to complete the process.Enabling for Temporary UsageYou can enable for temporary usage instead of installing the regular license.E Launch the License Authorization Wizard.E When prompted,choose Enable for temporary usage.E On the next screen,click the browse button to locate the temporary usage file in the productinstallation directory(typically temp.txt).Viewing Your LicenseYou can view the license by relaunching the License Authorization Wizard.The first paneldisplays the licensing information.Click Cancel when done,and click Y es when prompted aboutcancelling.5IBM SPSS Amos Installation Instructions(Site License) Uninstalling IBM SPSS AmosTo completely uninstall IBM®SPSS®Amos™:E Use the Windows Control Panel to remove IBM SPSS Amos.Updating,Modifying,and Renewing IBM SPSS AmosIf you renew your license,you will receive a new authorization code(or codes).For instructionson using the authorization code(s),see Licensing Your Product on p.3.。
A Survey of Software Refactoring

A Survey of Software RefactoringTom Mens,Tom Tourw´eAbstract—This paper provides an extensive overview of existing research in thefield of software refactoring.This re-search is compared and discussed based on a number of dif-ferent criteria:the refactoring activities that are supported; the specific techniques and formalisms that are used for sup-porting these activities;the types of software artifacts that are being refactored;the important issues that need to be taken into account when building refactoring tool support; and the effect of refactoring on the software process.A run-ning example is used throughout the paper to explain and illustrate the main concepts.Keywords—D.2.3Coding Tools and Techniques;D.2.6Programming Environments/Construction Tools;D.2.7.m Restructuring,reverse engineering,and reengi-neeringI.IntroductionA N intrinsic property of software in a real-world envi-ronment is its need to evolve.As the software is en-hanced,modified and adapted to new requirements,the code becomes more complex and drifts away from its orig-inal design,thereby lowering the quality of the software. Because of this,the major part of the total software de-velopment cost is devoted to software maintenance[1],[2], [3].Better software development methods and tools do not solve this problem,because their increased capacity is used to implement more new requirements within the same time frame[4],making the software more complex again.To cope with this spiral of complexity there is an urgent need for techniques that reduce software complexity by in-crementally improving the internal software quality.The research domain that addresses this problem is referred to as restructuring[5],[79]or,in the specific case of object-oriented software development,refactoring[6],[7]. According to the taxonomy of Chikofsky and Cross[8], restructuring is defined as“the transformation from one representation form to another at the same relative abstrac-tion level,while preserving the subject system’s external behaviour(functionality and semantics).A restructuring transformation is often one of appearance,such as alter-ing code to improve its structure in the traditional sense of structured design.While restructuring creates new versions that implement or propose change to the subject system,it does not normally involve modifications because of new re-quirements.However,it may lead to better observations of the subject system that suggest changes that would improve aspects of the system.”The term refactoring was originally introduced by William Opdyke in his PhD dissertation[6].Refactoring is basically the object-oriented variant of restructuring:“the Tom Mens(tom.mens@umh.ac.be),Universit´e de Mons-Hainaut, Avenue du Champ de Mars6,B7000Mons,Belgium.Tom Tourw´e(tom.tourwe@cwi.nl),Centrum voor Wiskunde en Informatica,P.O.Box94079,NL1090GB Amsterdam,The Nether-lands.process of changing a[object-oriented]software system in such a way that it does not alter the external behaviour of the code,yet improves its internal structure”[7].The key idea here is to redistribute classes,variables and methods across the class hierarchy in order to facilitate future adap-tations and extensions.In the context of software evolution,restructuring and refactoring are used to improve the quality of the soft-ware(e.g.,extensibility,modularity,reusability,complex-ity,maintainability,efficiency).Refactoring and restruc-turing are also used in the context of reengineering[9], which is the examination and alteration of a subject sys-tem to reconstitute it in a new form and the subsequent implementation of the new form[8].In this context,re-structuring is needed to convert legacy code or deteriorated code into a more modular or structured form[10],or even to migrate code to a different programming language or even language paradigm[11].The remainder of this paper is structured as follows.Sec-tion II explains general ideas of refactoring by means of an illustrative example.Section III identifies and explains the different refactoring activities.Section IV provides an overview of various formalisms and techniques that can be used to support these refactoring activities.Section V sum-marises different types of software artifacts for which refac-toring support has been provided.Section VI discusses essential issues that have to be considered in developing refactoring tools.Section VII discusses how refactoring fits in the software development process.Finally,Section VIII concludes.II.Running exampleIn this section we introduce a running example that will be used throughout the paper.The example illustrates a typical non-trivial refactoring of an object-oriented de-sign.The initial design depicted in Figure1represents an object-oriented class hierarchy.It shows a Document class that is refined into three specific subclasses ASCIIDoc,PS-Doc and PDFDoc.A document provides preview and print facilities,which are realised by invoking the appropriate methods in the associated Previewer and Printer classes, respectively.Before these methods can be invoked,some preprocessing or conversion needs to be done,which is re-alized differently for each of the Document subclasses.In Figure1this is represented by the different code fragments A,B,C and X,Y,Z,respectively.This design is not optimal because different function-alities of the Document class are distributed over all the subclasses.In order to add a new functionality to the Doc-ument class,such as a text search or a spell checker,we need to change every subclass of Document and we need to define the appropriate helper classes.Moreover,manyFig.1.Document class hierarchy and helper classessuch evolutions increase the complexity and reduce the un-derstandability of the design,because the Document class has many associations and no explicit relationship between all helper classes exists,although their roles are similar. To overcome these problems,the design needs to be refactored.By introducing a so-called Visitor design pat-tern[12],the same functionality can be achieved in a more localised fashion,while at the same time the understand-ability of the design is improved.This is illustrated in Figure2.The idea is to introduce a Visitor class hierar-chy,that groups all helper classes and defines a common interface for them(the visit*methods).At the same time, a generic accept method is implemented in all classes of the Document hierarchy.The accept method in each subclass calls a method,specifically defined for that subclass,of the Visitor hierarchy interface.In this refactored design model,new functionality can be added by simply creating a new subclass of Visitor,and implementing the visit*methods appropriately.As can be seen in Figure2,the implementations of the print and pre-view methods previously in subclasses of Document(i.e., A,B,C,X,Y,Z)have been moved to the visit*meth-ods of the Printer and Previewer classes(i.e.,A’,B’,C’, X’,Y’,Z’).Although the above example is relatively simple,it al-ready requires over twenty primitive refactorings to intro-duce the Visitor design pattern:1.The print method in each Document subclass(3occur-rences)is moved to class Printer using a MoveMethod refactoring2.To avoid name conflicts,each of the3moved print meth-ods needs to be renamedfirst to a visit*method using a RenameMethod refactoring3.The preview method in each Document subclass (3occurrences)is moved to class Previewer using a MoveMethod refactoring4.To avoid name conflicts,each of the3moved preview methods needs to be renamedfirst to a visit*method usinga RenameMethod refactoring5.An abstract Visitor class is introduced as superclass for Printer and Previewer using an AddClass refactoring6.Three abstract visit*methods are introduced in the new Visitor class using an AddMethod refactoring7.An accept method is introduced in all three subclasses of Document by extracting it from the print method and preview methods,using an ExtractMethod refactoring 8.All preview and print methods now call the accept method with an instance of the appropriate Visitor sub-class.Therefore,their definition can be pulled up to the Document class,by using a PullUpMethod refactoring. The refactorings in the above list are referred to as primitive refactorings.They are elementary behaviour-preserving transformations that can be used as building blocks to create the so-called composite refactorings[6],[13].These composite refactorings are usually defined asa sequence of primitive refactorings,and reflect more com-plex behaviour-preserving transformations that are more meaningful to the user.For example,the six refactorings in steps1and2of the above enumeration can be combined into the single composite refactoring MoveMethodsTo-Visitor shown in Figure3.In a similar way,steps3and 4in the above enumeration can be combined into a single composite refactoring.posite refactoring for renaming and moving print meth-ods from the Document subclasses to the Printer classIII.Refactoring activitiesThe refactoring process consists of a number of distinct activities:1.Identify where the software should be refactored;2.Determine which refactoring(s)should be applied to the identified places;3.Guarantee that the applied refactoring preserves be-haviour;4.Apply the refactoring;5.Assess the effect of the refactoring on quality character-istics of the software(e.g.,complexity,understandability, maintainability)or the process(e.g.,productivity,cost,ef-fort);6.Maintain the consistency between the refactored pro-gram code and other software artifacts(such as documen-tation,design documents,requirements specifications,tests and so on)As will be illustrated below,each of these activities can be supported by different tools,techniques or formalisms.Fig.2.Refactored design model for the Document class hierarchyA.Identifying where to apply which refactoringsAfirst decision that needs to be made here is to deter-mine the appropriate level of abstraction to apply the refac-toring.Should the refactorings be applied to the program itself(i.e.,the source code),or to more abstract software artifacts such as design models or requirements documents, for example?1We will tackle this particular question in de-tail in Section V,and restrict ourselves to the subdomain of program refactoring here.In this subdomain,the activity of identifying the parts of the program that require refac-toring(activity1),and proposing refactorings that should be applied to these(activity2),are usually combined. Kataoka et al.implemented the Daikon tool to indicate where refactorings might be applicable by automatically detecting program invariants[14].One invariant may be that a certain parameter of a method is always constant, or is a function of the other parameters of a method.In that case,it might be possible to apply a removeParameter refactoring.The main problem with this approach is that it requires dynamic analysis of the runtime behaviour:the application needs to be executed to infer the program in-variants.To this extent,the tool uses a representative set of test suites.It is however impossible to guarantee that a test suite covers all possible runs of a program.Therefore, the invariants may not hold in general.Nonetheless,very good results have been obtained in practice.Moreover,the approach is complementary to other approaches that rely on static information.Probably the most widespread approach to detect pro-gram parts that require refactoring is the identification of bad smells.According to Kent Beck,bad smells are“struc-tures in the code that suggest(sometimes scream for)the possibility of refactoring”[7].As a concrete example of a bad smell,reconsider the Document class hierarchy design in Figure1of Section II.By analysing the code fragments A,B,C and X,Y,Z,respectively,it is very likely that one can detect a significant amount of code duplication.This 1As a terminological side note,when we use to term program in the remainder of this paper,we specifically refer to the source code or executable code.In contrast,when we use the term software,we refer to any type of software artifact(including code,design models, requirements specifications,and so on).is a typical example of a bad smell,since code duplication should be avoided,as it decreases maintainability.Balazin-ska et e a clone analysis tool to identify duplicated code that suggests candidates for refactoring[15].Ducasse et al.sketch an approach to detect duplicated code in soft-ware and propose refactorings that can eliminate this du-plication[16].The approach is based on an object-oriented meta model of the source code and a tool that is capable of detecting duplication in code.The proposed refactor-ings consist of removing duplicated methods,extracting duplicated code from within a method and inserting an intermediate subclass to factor out the common code. Martin Fowler informally links bad smells to refactor-ings[7].Tourw´e and Mens use a semi-automated approach based on logic meta programming to formally specify and detect these bad smells,and to propose refactoring oppor-tunities that remove these bad smells[17].A more ad hoc approach to detect structural weaknesses in object-oriented source code and solve them by refactorings is proposed by Dudziak and Wloka[19].van Emden and Moonen com-bine the detection of bad smells in Java with a visuali-sation mechanism[18].Simon et e object-oriented metrics to identify bad smells and propose adequate refac-torings[20].They focus on use relations to propose move method/attribute and extract/inline class refactorings.The key underlying concept is the distance-based cohesion met-ric,which measures the degree to which methods and vari-ables of a class belong together.Especially in combination with software visualisation,the use of object-oriented met-rics seems well suited to detect places in the source code that are in need of refactoring[20],[21].Afinal but important issue is that identification of which refactorings to apply can be highly dependent on the par-ticular application domain.If we restrict ourselves to,for example,web-based software the question of“where and why”to refactor is partially answered by the high-level refactorings from[22].B.Guaranteeing that the refactoring preserves software be-haviourBy definition,a refactoring should not alter the be-haviour of the software.Unfortunately,a precise definitionof behaviour is rarely provided,or may be inefficient to bechecked in practice.The original definition of behaviour preservation as sug-gested by Opdyke[6]states that,for the same set ofinput values,the resulting set of output values shouldbe the same before and after the refactoring.Opdykesuggests to ensure this particular notion of behaviourpreservation by specifying refactoring preconditions.Asa concrete example of such a refactoring precondition,reconsider the primitive refactorings in the running ex-ample of Section II.Thefirst refactoring suggestedis MoveMethod(print,ASCIIDoc,Printer).It has anumber of necessary preconditions:the classes ASCIIDocand Printer should be defined;the method print shouldbe implemented in ASCIIDoc;the method signature ofprint should not be present in class Printer.As can beseen in Figure1,the third precondition is not satisfied,which is precisely why the refactoring RenameMethod(print,ASCIIDoc,visitASCII)was suggested to avoidthe method signature conflict.In many application domains,requiring the preservationof input-output behaviour is insufficient,since many otheraspects of the behaviour may be relevant as well.This im-plies that we need a wider range of definitions of behaviourthat may or may not be preserved by a refactoring,de-pending on domain-specific or even user-specific concerns:•For real-time software,an essential aspect of the be-haviour is the execution time of certain(sequences of)op-erations.In other words,refactorings should preserve allkinds of temporal constraints;•For embedded software,memory constraints and power consumption are also important aspects of the behaviour that may need to be preserved by a refactoring;•For safety-critical software,there are concrete notions of safety(e.g.,liveness)that need to be preserved by a refactoring.One may deal with behaviour preservation in a very prag-matic way,for example by means of a rigorous testing disci-pline.If we have an extensive set of test cases,and all thesetests still pass after the refactoring,there is a good evidencethat the refactoring preserves the program behaviour.Un-fortunately,some refactorings will invalidate existing tests,even if the refactoring does no alter the behaviour[23],[24].The reason for this is that the tests may rely on theprogram structure that is modified by the refactoring.Another pragmatic,but slightly more formal,approachis to adopt a weaker notion of behaviour preservation thatis insufficient to formally guarantee the full preservationof program semantics,but that works well in many prac-tical situations.For example,we can define a notion ofcall preservation,which guarantees that all method callsare preserved by the refactoring[25].In the presence ofa type system,one can show that a refactoring preservestype correctness[26].A more fundamental approach is to formally prove that refactorings preserve the full program semantics.For a lan-guage with a simple and formally defined semantics,such as the logic programming language Prolog,one can prove that some refactorings that improve the efficiency actually preserve the program semantics[27].For more complex languages such as C++,where a formal semantics is ex-tremely difficult to define,we typically have to put restric-tions on the allowed language constructs or refactorings, and the applicability of a refactoring tool may be limited to a particular version of a particular compiler[28].C.Assessing the effect of refactoring on qualityFor any piece of software we can specify its external qual-ity attributes(such as robustness,extensibility,reusability, performance).Refactorings can be classified according to which of these quality attributes they affect.This allows us to improve the quality of software by applying the rele-vant refactorings at the right places.To achieve this,each refactoring has to be analysed according to its particular purpose and effect.Some refactorings remove code redun-dancy,some raise the level of abstraction,some enhance the reusability,and so on.This efffect can be estimated to a certain extent by expressing the refactorings in terms of the internal quality attributes they affect(such as size, complexity,coupling and cohesion).An important software quality characteristic that can be affected by refactoring is performance.It is a common misconception that improving the program structure has a negative effect on the program performance.In the context of logic and functional programs,restructuring transforma-tions typically have the goal to improve program perfor-mance while preserving the program semantics[27],[29]. In the context of object-oriented programs,Demeyer[30] investigated the effect of refactorings that replace condi-tional logic by polymorphism.He concludes that the pro-gram performance gets better after the refactoring,because of the efficient way in which current compiler technology optimises polymorphic methods.To measure or estimate the impact of a refactoring on quality characteristics,many different techniques can be used.Examples include,but are not limited to,software metrics,empirical measurements,controlled experiments and statistical techniques.Kataoka et al.propose cou-pling metrics as an evaluation method to determine the effect of refactoring on the maintainability of the program [31].Tahvildari et al.encode design decisions as soft-goal graphs to guide the application of the transformation pro-cess[32].These soft-goal graphs describe correlations be-tween quality attributes.The association of refactorings with a possible effect on soft-goals addresses maintainabil-ity enhancements through primitive and composite refac-torings.Tahvildari et e a catalogue of object-oriented metrics as indicator to detect automatically where a par-ticular refactoring can be applied to improve the software quality[33].This is achieved by analysing the impact of each refactoring on these object-oriented metrics.D.Maintaining consistency of refactored software Typically,software development involves a wide range of software artifacts such as requirements specifications, software architectures,design models,source code,docu-mentation,test suites,and so on.If we refactor any of these software artifacts,we need mechanisms to maintain their consistency.Since the activity of inconsistency man-agement is a research area in its own right[34],[35],[36], we will not treat it in detail here.We only discuss a few approaches that relate consistency maintenance to refac-toring.Bottoni et al.propose to maintain consistency between the program and design models by describing refactoring as coordinated graph transformation schemes[37].These schemes have to be instantiated according to the specific code modification and applied to the design models affected by the change.Within the same level of abstraction,there is also a need to maintain consistency.For example,if we want to refac-tor source code,we have to ensure that the corresponding unit tests are kept consistent[23].Similarly,if we have different kinds of UML design models,and any of these is being refactored,the others have to be kept consistent. Van Der Straeten et al.suggest to do this by means of logic rules[39].Rajlich uses the technique of change propagation to cope with inconsistencies between different software artifacts [38].This technique deals with the phenomenon that,when one part of a software is changed,dependent parts of the software may need to be changed as well.IV.Refactoring techniques and formalismsA wide variety of formalisms and techniques have been proposed and used to deal with one or more refactoring activities.We discuss two such techniques in detail:the use of assertions(preconditions,postconditions and invari-ants)and the use of graph transformation.Next,we discuss how formalisms can help us to guarantee program correct-ness and preservation in the context of refactoring.Finally, we provide an indicative,but inevitably incomplete,list of other useful techniques to support refactoring activities.A.Invariants,pre-and postconditionsA refactoring’s definition often includes invariants that should remain satisfied and pre-and postconditions that should hold before and after the refactoring has been applied.These constitute a lightweight and automati-cally verifiable means to ensure that(certain parts of) the behaviour of the software is preserved by the refac-toring.A concrete example of the use of preconditions was already presented for the refactoring MoveMethod (print,ASCIIDoc,Printer)in Section III-B.A set of postconditions for the same refactoring would be:(1)the print method must be implemented in Printer after the refactoring;(2)the method signature of print does not ex-ist in ASCIIDoc after the refactoring.An example of an invariant is the fact that classes ASCIIDoc and Printer are defined before and after the refactoring.The use of preconditions and invariants has been sug-gested repeatedly in research literature as a way to address the problem of behaviour preservation when restructuring or refactoring software artifacts.In the context of object-oriented database schemas(which are similar to UML class diagrams),Banerjee and Kim identified a set of invariants that preserve the behaviour of these schemas[40].Opdyke adopted this approach to object-oriented programs,and additionally provided preconditions or enabling conditions for each refactoring[6].He argued that these preconditions preserve the invariants.Roberts usedfirst order predicate calculus to specify these preconditions in a formal way[41]. The notion of preconditions or applicability conditions is also available in the formal restructuring approach of Ward and Bennett,using the formal language WSL[42]. Preconditions may vary depending on the complexity of the language studied.More complex languages typically re-quire more preconditions on the refactoring in order to pre-serve the invariants.Unfortunately,there are some prac-tical problems with preconditions.One problem is that the static checking of some preconditions may require very expensive analysis,or may even be impossible.Another problem is that the preconditions do not consider the size or structure of the program[6].For example,C++pro-grams may perform integer arithmetic with the address of a variable in a class,which is problematic if the refactoring changes the physical ordering of the variables in that class.A number of suggestions have been made to overcome the above problems with preconditions.Tip et al.suggest to use type constraints to efficiently verify preconditions that depend on interprocedural relationships between vari-able types[26].This is particularly useful for refactorings that are concerned with generalisation.Roberts suggests to augment refactorings with postconditions[41].These postconditions are particularly useful for those invariants that rely on dynamic information that is difficult to ex-press,or expensive to check statically,with preconditions. Postconditions can also be used to increase the efficiency of a refactoring tool.From a theoretical point of view it can be shown that a set of postconditions can be trans-lated into an equivalent set of preconditions[43].Roberts provided an algorithm to perform this translation for se-quences of program transformations.´O Cinn´e ide extended this algorithm to deal with iteration and conditional con-structs[13].B.Graph transformationTraditionally,refactorings are specified as parameterized program transformations along with a set of pre-and post-conditions that guarantee behavior preservation if satisfied [6],[44].If we adopt this view,there is a direct corre-spondence between refactorings and graph transformations. Programs(or other kinds of software artifacts)can be ex-pressed as graphs,refactorings correspond to graph pro-duction rules,the application of a refactoring corresponds to a graph transformation,refactoring pre-and postcondi-tions can be expressed as application pre-and postcondi-tions[43],[45].Table I summarises some formal properties of graph transformation that may be used to address im-portant issues in refactoring.TABLE ICorrespondence between refactoring and graphtransformationRefactoring Graph transformation software artifact graphrefactoring graph production composite refactoring composition of graph pro-ductionsrefactoring application graph transformation refactoring precondition application precondition refactoring postcondition application postcondition(in)dependence between refactorings in a sequence parallel or sequential (in)dependenceconflict between refactor-ings applied in parallel to the same software artifact confluency and critical pair analysisHence,it is not surprising that the theory of graph trans-formations has been used to provide more formal support for software refactoring.Mens et e the graph rewrit-ing formalism to prove that refactorings preserve certain kinds of relationships(updates,accesses and invocations) that can be inferred statically from the source code[25]. Bottoni et al.describe refactorings as coordinated graph transformation schemes in order to maintain consistency between a program and its design when any of them evolves by means of a refactoring[37].Heckel[43]uses graph trans-formations to formally prove the claim(and correspond-ing algorithm)of Roberts[41]that any set of refactoring postconditions can be translated into an equivalent set of preconditions.Van Eetvelde and Janssens[46]propose a hierarchical graph transformation approach to be able to view and manipulate the software and its refactorings at different levels of detail.The properties of sequential and parallel(in)dependence of graph transformations are also extremely suitable to rea-son about the dependence between refactorings.Two refac-torings are independent if they can be applied in any order, i.e.,the order in which they are applied does not affect the end result.This gives rise to a whole range of useful appli-cation scenarios.One scenario is the serialisation of refactorings that have been applied in parallel to the same software artifact[102]. During this serialisation process,it is possible that conflicts arise because the refactorings make incompatible changes. To detect and resolve such conflicts,one can rely on existing results about parallelism and confluence[110]and critical pair analysis[111].Analysis of sequential dependencies can also be used to reorder a given sequence of refactorings,for example,to normalise the sequence,to identify refactorings that an-nihilate each other’s effect,to regroup subsequences into predefined composite refactorings,and so on.When building composite refactorings it is useful to de-termine which refactorings have to be applied sequentially and which refactorings are mutually independent[41].For example,the composite refactoring shown in Figure3of Section II consists of a sequence of6primitive refactorings, but there are only3sequential dependencies(represented by straight arrows):each MoveMethod refactoring has to be preceded by a Rename refactoring.The order in which the three(Rename,MoveMethod)pairs have to be applied,however,is irrelevant.This is represented by dashed arrows.This means that,to increase the efficiency of the refactoring,one may decide to apply these3pairs of primitive refactorings in parallel.C.Formalisms for program correctness and preservation Formal approaches are needed to guarantee that certain program properties remain invariant to a program transfor-mation.We will make a distinction between the property of program correctness and the property of preservation.2 Program correctness is the property that a program will work without errors.The preservation property of a pro-gram transformation guarantees that(some aspect of)the program behaviour is preserved by the transformation. Obviously,any program transformation should preserve the syntactic rules(or well-formedness rules)of the pro-gramming language.After the transformation,the soft-ware should still be syntactically correct.This can be checked by using a scanner and a parser.The semantics of the program should also remain correct,i.e.,the program should not give rise to run-time errors.Unfortunately,the correctness property is in general undecidable.Gupta et al.showed that we cannot prove,for an arbitrary running program and an arbitrary update to it,that the update is valid in the sense that it will eventually result in a reach-able program state of the newly added program code[63]. Because of the undecidability of this property,we can only take a conservative approach.For example,if we only con-sider restructurings of the same algorithm(as opposed to changes to program functionality),a syntactic analysis of the old and new program code can identify program points that preserve update validity.The preservation property can either be checked stati-cally or dynamically.The checking of refactoring precon-ditions[6],[41]can be considered as a static approach. However,the preconditions that are expressed infirst-order predicate logic are only a conservative approximation,and hence rule out many legal refactorings.Mens et al.sug-gest other notions of behaviour preservation that can be checked statically and show how this can be realised using a graph transformation formalism[25].Access preserva-tion means that all variable accesses should be preserved by the refactoring.Update preservation means that all vari-able updates should be preserved by the refactoring.Call 2This distinction is not made in the domain of program transforma-tion for functional languages[29].In this domain,the term correct-ness is used to indicate that a program transformation preserves the extensional meaning of programs.We will not use correctness in this sense,because it leads to confusion with the more widely accepted definition of program correctness.。
ebpf 环境准备 -回复

ebpf 环境准备-回复EBPF环境准备EBPF(Extended Berkeley Packet Filter)是一种内核扩展技术,它允许开发人员在内核中注入小型的程序以实现高效的包处理和网络分析。
EBPF 已经成为在现代操作系统中进行网络和系统跟踪的重要工具,因其高性能和安全性而受到广泛关注。
本文将向您介绍如何准备EBPF环境并开始使用它。
步骤一:安装所需工具和库在开始之前,我们需要安装一些必要的工具和库。
首先,我们需要安装LLVM和Clang,它们是EBPF编译器和工具链的一部分。
我们可以使用包管理器来安装它们,例如在Ubuntu上,我们可以运行以下命令:sudo apt-get install llvm clang接下来,我们需要安装libbpf库,它是EBPF的运行时库。
您可以从GitHub 上的libbpf存储库中获取它,并按照其文档中的说明进行安装。
例如,您可以运行以下命令:git clonecd libbpfmakesudo make install步骤二:编写和编译EBPF程序一旦我们安装了所需的工具和库,我们就可以开始编写和编译我们的第一个EBPF程序了。
EBPF程序可以使用C语言编写,因此我们可以使用任何支持C语言的文本编辑器来编写它。
在本例中,我们将创建一个简单的EBPF程序来统计收到的数据包数量。
首先,我们需要创建一个名为`packet_counter.c`的文件,并在其中编写以下代码:c#include <linux/bpf.h>SEC("socket")int packet_counter(struct __sk_buff *skb){int key = 0;__u64 *value;value = bpf_map_lookup_elem(&packet_map, &key);if (value)*value += 1;return XDP_PASS;}在这个简单的EBPF程序中,我们首先定义了一个名为`packet_counter`的函数,它接收一个名为`skb`的数据包作为参数。
CSRFScanner——打造全自动检测CSRF漏洞利器脚本安全电脑资料

CSRFScanner——打造全自动检测CSRF破绽利器脚本平安电脑资料1.CSRF破绽的介绍和危害性图1-1 csrf破绽的攻击过程CSRF(Cross-site request forgery跨站恳求伪造)通常缩写为CSRF或者XSRF,攻击通过在授权用户访问的页面中包含链接或者脚本的方式工作。
举一个简单的例子,例如:用户A在自己的博客站点中写了一篇文章C,用户B在回复中贴了一张图,在贴图的URL中写入删除文章C 的链接,当A看见这张图片的时候,文章C便被不知不觉间删除了。
这就是CSRF攻击了。
2.业界现有CSRF检测技术2.1业界现有的技术方案目前对于csrf的检测,业界还没有成熟有效的工具,唯一的一款比较有名的检测工具是由开放式Web应用程序平安工程(OWASP,Open Web Application Security Project)的Csrftester,该工具仅支持简单的对页面所提交的表单信息进展抓取,然后由用户人工地进展修改该数据来确定是否存在csrf破绽,效率低下,无法适应互联网海量CGI破绽检测的需求。
而其他的扫描器只能半自动发现,但误报极高,例如著名的awvs对csrf扫描的逻辑就比较简单,导致误报率很高。
所以,业界一直缺少一个自动的和高准确率的csrf检测工具。
2.2业界现有技术的缺点1)、不支持自动csrf破绽检测;2)、误报率很高。
3.创新的CSRF检测技术针对近期外部的大量csrf破绽,为快速地解决当前面临的问题,腾讯平安团队自研了一款全自动检测csrf破绽的工具——CsrfScanner,主要检测根底数据库中的存在的破绽。
csrf产生危险的核心就是利用的别人的cookie来进展有敏感的操作,区别对待带cookie和不带cookie两种情况是扫描器的检测逻辑的关键点。
CsrfScanner的检测步骤如下:1)、不带cooie访问页面得到表单form1。
2)、带cookie访问页面得到表单form2。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Software Tools Using CSRBFs for ProcessingScattered DataNikita Kojekine a,Ichiro Hagiwara a,Vladimir Savchenko ba Hagiwara’s Laboratory,Department of Mechanical Sciences and Engineering,Faculty ofEngineering,Tokyo Institute of Technology,2-12-1,O-okayama,Meguro-ku,Tokyo,152-8552,Japan.b Faculty of Computer and Information Sciences,Hosei University,3-7-2,Kajino-cho,Koganei-shi,Tokyo,184-8584,Japan.1IntroductionMany practical surface reconstruction techniques based on measured data points require the solution of optimization problems in thefitting of surface data,as,for example,in restoration design or reverse engineering tasks.One of the applications considered in this paper,namely,reconstruction of volume geometric models,is anattractive research direction:it makes possible to speed up the solution of reverse engineering problems by using scattered measured data,and addresses the demand for the reconstruction of volume models that allow a rich set of operations to be ap-plied.Recently,many researchers have paid attention to possibilities opened by us-ing radial basis functions(RBFs)for surface reconstruction of functionaly defined objects.Traditionally,constructive solid geometry(CSG)modeling uses simple ge-ometric objects for a base model,which can be further manipulated by implement-ing a certain collection of operations such as set-theoretic operations,blending,or offsetting.The operations mentioned above and many others have found quite gen-eral descriptions or solutions for geometric solids represented as points x y z in space satisfying f x y z0for a continuous function f.Such a representation is usually called a function representation.Set-theoretic solids have been successfully included in this type of representation with the application of R-functions and their modifications(see[1],[2]).A vast volume of literature is devoted to the subject of scattered data reconstruc-tion and interpolation.In most applications,Delaunay triangulation is used for3D reconstruction.The main idea of Delaunay decomposition is to reconstruct a sur-face from non-uniform samples by connecting a subset of points that are natural neighbors in a triangulated mesh.This approach(see,for example,[3])performs efficient Delaunay triangulation of different shape types reconstructed from their cross-sections[4].A comprehensive overview of related studies,problems,and limitations can be found in[6],which addresses these problems and introduces a fast algorithm for constructing C2-continuous interpolation functions.Another approach to surface reconstruction is skeletal.An implicit surface generated by point skeletons may be fitted to a set of surface points[7],but this method is rather time-consuming. One other approach is to use methods of scattered data interpolation,based on minimum-energy properties[8],[9],[10].These methods are widely discussed in mathematical literature(see[11],[12]).The benefits of modeling3D surfaces with the help of RBFs have been recognized in[13]for Phobos reconstruction.RBFs were adopted for computer animation[14],[5]and medical applications[15],[16], and werefirst applied to implicit surfaces by Savchenko et al.[17].However,the work required is proportional to the number of the grid nodes and the number of scattered data points.The amount of computation becomes significant,even for a moderate number of nodes.Special methods for reducing the processing time were developed for thin-plate splines[18].Theoretical aspects of using radial functions in compact domains were discussed by Light in[19].Carr et al.[20]have also recently worked on surface reconstruction of implicitly defined3D objects based on the use of non-compact supported RBFs and a"both-side"approach,which has been proposed in[21].Unfortunately,the authors of that paper did not describe their algorithm in detail.The approach taken by Turk and O’Brien in[21]of using points specified on both sides of the surface will provide successful restoration of a2surface arbitrary topology,but it involves drawbacks that lead one to suppose that it would be inefficient for applying RBFs in volume reconstruction.It is beyond the scope of this paper to discuss all these matters;let us note,however,that there is a problem of constructing or specifying off-surface points along a surface normal that also leads to a doubling of the given number of surface points.The"both-sides" approach also has a problem with surface extraction:a surface extractor can jump outside the band of non-zero points.Methods exploiting RBFs can be divided into three groups.Thefirst group is "naive"methods,which are restricted to small problems,but they work quite well in applications,dealing with shape transformation(see,for example,[22]).The second group is fast methods forfitting and evaluating RBFs,which allow large data sets to be modeled[23],[18].The third and last group is compactly supported RBFs[24].In spite of significant progress in thefield of implementing RBFs and CSRBFs[25],for reconstruction purposes,it is still an open question whether it is possible to handle realistic amounts of data in real time.We suppose that RBFs and CSRBFs are suitable for moderately sized3D data sets;for instance,the execution time is about300seconds for36000points,without time costs for surface extrac-tion,as reported in[23],where the authors used commercial software for SLAE solution and employed the"both-sides"approach to reconstruct implicitly defined objects.Nevertheless,RBFs possess many features that make them very attractive for CG applications dealing with modification of geometric objects.In the simplest case,when we use sphere as a carrier solid(see the description of our surface ex-traction algorithm given later in section4)to generate CSG objects we restrict our applications to the restoration of objects close to a sphere.However,using other carrier solids or dividing the point data in parts and modeling the whole object by boolean combination of the different CSRBF function,it is possible to model any type of geometry,but it can be very difficult to select appropriate carrier solid or division for the dataset.Our software toolkit can be used both with carrier solid and"both-sides"approaches and we demonstrate some examples of restoration using both approaches later in section4.Nevertheless,generally we avoid using"both-sides"approach because it is not sufficiently clear how to define right normal vectors for scattered data sets. Actually,we noticed in our experiments that the results of restorations heavily de-pend on the normal vectors.In practice,reconstruction with RBFs consists of the following steps:sorting the data,constructing the system of linear algebraic equations(SLAE),solving the SLAE,and evaluating the functions.In fact,while the solution of the system is the limiting step,constructing the matrix and evaluating the functions to extract the isosurface may also be computationally expensive.In this paper,we attempt to solve the reconstruction problem according to the above-mentioned steps.Thus,the main goal of the ongoing project is to develop an effective library of C++classes that can be successfully applied to computationally intensive problems of surface3reconstruction and deformation using RBF splines.The key point of the software tools we developed is the efficient octree algorithm proposed in this study:the resulting matrix is a band-diagonal matrix that permits handling of large data sets in a reasonable time.This work is a considerably extended and improved version of a presentation we made[26].The paper is organized as follows.In Section2we describe a method of surface reconstruction from a set of unorganized(scattered)points by means of radial basis functions.Our algorithms give such a reconstruction(Section3)in two steps:sorting of data and solution of the SLAE.Section4gives examples of surface construction as one of the applications of our toolkit.Section5summarizes the results described in the paper.2RBF splinesFor a three-dimensional arbitrary areaΩ,the thin-plate interpolation is the varia-tional solution that defines a linear operator T when the following minimum con-dition is used:Ω∑αmm!α!Dαf2dΩminwhere m is a parameter of the variational functional andαis a multi-index.It is equivalent to using the radial basis functionsφr r1or r3for m2and3,re-spectively,where r is the Euclidean distance between two points.Since the function φr is not compactly supported,the corresponding system of linear algebraic equa-tions(SLAE)is not sparse or bounded.Storing the lower triangle matrix requires O N2real numbers,and the computational complexity of a matrix factorization is O N3.Thus,the amount of computation becomes significant,even for a moderate number of points.Wendland in[24]constructed a new class of positive definite and compactly sup-ported radial functions for1D,3D,and5D spaces of the formφr P r0r1 0r1whose radius of support is equal to1.The functionφr1r2,which is an in-terpolated function that supports only C0continuity,is used.This function provides positive defined and nonsingular systems of equations.However,it may be possible to apply functions that support a higher continuity,this is a matter for further re-search.An investigation[27]of the smoothness of this family of polynomial basis functions shows that each memberφr possesses an even number of continuous derivatives.4The volume spline f P having values h i at N points P i is the functionf PN∑j1λjφP P j p P(1)where p v0v1x v2y v3z is a degree one polynomial.To solve for the weights λj we have to satisfy the constraints h i by substituting the right part of equation1, which givesh iN∑j1λjφP i P j p P iSolving for the weightsλj and v0,v1,v2,v3it follows that in the most common case there is a doubly bordered matrix T,which consist of three blocks,square sub-matrices A and D of size N N and44,respectively,and B,which is not necessarily square and has the size N 4.Heights h i,are not necessarily values of a function defining a selected carrier solid. Arbitrary points in the Euclidean space E n(more precisely,vectors of deviations of some defined3D points)can also be used.3Algorithm3.1Sorting of scattered dataSpace-recursive subdivision is an elegant and popular way of sorting scattered3D data.We propose an efficient approach based on the use of variable-depth octal trees for space subdivision,which allows us to obtain the resulting matrix as a band-diagonal matrix that reduces the computational complexity.Ourfirst goal is to build an octal tree[28]data structure from the original point data.For each node of the tree,we need to store the following:a pointer to the parent node,8pointers to child nodes,a pointer to the list of points(empty,if this node is not a leaf).The total amount of memory needed to store such a tree is(memory for each node) (number of nodes)(memory needed to store points)N.In our software implementation,we employ a standard approach for creating the tree from an initial point data set with an additional required parametric value K,which denotes the maximum number of points in the leaf.For the sake of convenience,we scale all N points in a unit cube.Afterwards we divide this cube into8equal sub-cubes.All5points are shared among these sub-cubes.The root of the tree corresponds to the initial cube,and the8sub-cubes correspond to8nodes linked with the root of the tree.This procedure is applied to each cube,until all K points lie in their own small cubes.If one of the8cubes does not contain points in the current step we should not build a sub-tree in that direction.Afterwards we can use this tree to search for neighbors of any given point from the given N points.The neighbors are points of a sphere of radius r,whose center is located at the given point.We call this sphere an r-sphere.To accelerate the search,the tree is simplified after creation by removing unneces-sary nodes.If the node A has only one sub-node B,we can remove node the A node and replace it with B.For example,see Fig.1(numerals represent node numbers).This procedure is reasonable to use only if K is small.For instance,for data in the example(a)(see Table1)if K is set equal to1,applying of this procedure results in removing113nodes from the initially created2427nodes.An application-programming library was developed and contains7main C++classes:The CDataList class defines a stack,which we use in our implementation,instead of a list,The CDataListItem class represents an element of the stack,The CGetFunctions class defines the interface for functions depending on the data storage technology,The CPointFunctions class inherited from CGetFunctions class contains func-tions connecting a COctupleTree class with the array of points,and also the condition that points in space belong to the same r-sphere,The CNodeNumber class serves to describe the node’s number in the tree,The COctupleTree class defining the octal tree contains the main functions,The COctupleTreeNode class serves to represent the node in the octal tree.The complexity of creation and searching using an octal tree strongly depends on the initial data and the parameter K.The depth of the tree depends on the length of the cube edge corresponding to the leaf.This length is equal to12M,where M is the depth of the tree and depends on the original data.If the initial points are distributed more or less uniformly,then the tree will have sufficiently uniform filling and will be symmetric.If K1,at that time the tree will be close to a full octal tree with N leaves.The maximum complexity of searching the tree will be proportional to the depth of the tree,that is,log8N.A more detailed account of these algorithms,including a C++library description,can be found in[29].The procedure of searching for the neighbors of a point in a given r-sphere is ap-plied several times in the application.For example,it is used in the calculation of the function1to sum up only the points that are neighbors of the specified point with coordinates x y z.However,thefirst application is the construction of the6band diagonal sub-matrixφP P i,which accounts for a significant portion of the computational cost.Band-diagonal systems haveα11of nonzero elements to the left of the diagonal andα21of nonzero elements to its right.In our case, these numbers are equal,because our matrix is symmetric.In our application,to store the band-diagonal matrix,we use a so-called profile form or a slightly modi-fied Jennings envelope scheme[30].To store the matrix A,an array can be used for diagonal elements;values of non-diagonal elements and correspondent indices of thefirst non-zero elements in the matrix lines are placed in two additional arrays. To make our sub-matrix band diagonal,we need to re-enumerate the initial points in a special way.We propose the following algorithm,named"Sorting data using an octal tree"(see the pseudo-code in Fig.2):Take a point from the initial data and put it in the list.Go through the list and for each point in the list search for the neighbors in the initial data.When new points are found,add them to the list.Remove from the initial array points that have been placed in the list.If there are no more points in the list(that is,if all points were appended in the second step),then take thefirst point remaining in the initial array and repeat the above steps.As a result of this algorithm,a band with maximum sizeα1,that is,the maximum number of the neighbors of a point,is obtained.The maximum complexity of this algorithm is the complexity of searching for neighbors through the octal tree for each point,that is,N(the maximum complexity of the searching algorithm).The maximum complexity of this algorithm is the complexity of searching for neigh-bors through the octal tree for each point,i.e.,N(the maximum complexity of the searching algorithm).We can reduce our computational outlays by calculating the matrix and ordering of the points simultaneously.In thefirst step of sorting al-gorithm,we have thefirst point and a list of its neighbors.This means that we can calculate one row(and one column)of the band-diagonal sub-matrix.In the next step,we take the second point and calculate the next row of the matrix,and so on, until we have calculated the entire matrix.After sorting we have a banded matrix as illustrated in Fig.3;that is,the matrix has the maximum number of nonzero elements for some point.Naturally,the re-sults of matrix construction depend on the appropriate selection of the radius of the r-sphere.Note that the special order prescribed by a sparse matrix to minimize fill-ins is not important.Note also that the half-width for the selected r cannot be decreased.Considering the following unlikely event will clarify this concept.If we connect all neighboring points,we will obtain a graph,and if this graph has a cycle, then the maximum size we will get is less than or equal to the cycle length.Thus, if the radius is quite large,then the cycle will include nearly all the points from the input data.In this case,the maximum size of the band will also be large,and we7will have an expansion of the band at some point.The position of the expansion isnot important for our implementation.3.2SLAE solutionNote that goals in solving any sparse system are to save time and space.Accordingto theoretical estimation and our own practical experience with the reconstructionof surfaces based on using RBFs splines,the best method of solution is the House-holder method[31].However,this method is time-consuming,which becomes acrucial drawback in practical reconstruction problems.The attractiveness of usingimplicit methods such as conjugate gradient methods for large sparse systems hasbeen well recognized in various applications.If T is positive definite and symmet-ric,the algorithm cannot break down,in theory[32].Conjugate gradient methodswork well for matrices that are well-conditioned.In practical applications,this re-striction can limit the accuracy with which a solution can be obtained,and thus weprefer to use explicit SLAE solution methods for matrices stored in profile form.The advantage of Gaussian LU decomposition[33]has been well recognized andmany software routines have been developed.For a symmetric and positive definitematrix,a special factorization,called Cholesky decomposition[31],is about twiceas fast as alternative methods for solving linear equations.In our case,we have an SLAE in the form T x b,where symmetric matrix Tconsists of four blocks:A,B,C,and C T.Sub-matrices A,B,and C have sizes N N,k k,and N k,respectively.A is a band-diagonal matrix,k4for3D case,B0.A combination of block Gaussian solution and Cholesky decompositionwas proposed by George and Liu in[32],and in our software tools we follow theirproposal.4Surface evaluation and extractionThe surfacefitted to a set of surface data point forms a volume model of a geo-metric object.The general idea of our algorithm[17]is to introduce a carrier solidwith a defining function f c and to construct a volume spline f P interpolatingvalues of the function f c in the points P i.The algebraic difference between f Pand f c describes the reconstructed solid.The algorithm consists of two steps.Inthefirst step,we introduce a carrier solid object,which is an initial approxima-tion of the object being searched for.In the simplest case,it can be a sphere sothat f c P i P2i x P2i y P2i z 1.Then the data set r associated with the points r i f c P i:i12N is calculated at all given points.In the second step,these values are approximated by a volume spline derived for random or unorganizedpoints.8Calculation of the resulting spline function is accelerated in our algorithm by using previously created octal tree.This also makes the rendering time very small(see Table1).This surface can be visualized directly using an implicit ray-tracer,and can be voxelized or polygonized to extract a mesh of polygons.For the visualization of reconstructed volumes we use an implicit function modeler tool[34],[35]. Visual inspection(images in Fig.4)allows us to judge the interpolation features of the algorithm we have discussed.We would like to note that visual inspection of different restorations shows a dependency of the accuracy of restoration on the choice of the radius of support.Actually,there is some trade-off between the effi-ciency of computation and the restoration quality.Visual evaluation of the result is not sufficient for an appraisal of the algorithm,especially for CAGD applications, where numerical error estimation is very important for comparison of various scat-tered data interpolants.To compare,some numerical measure of the error of the approximation found for a test function is needed.In practice,the root mean square measure(RMS)of the error for the test function and the maximal deviation be-tween the reconstructed and test functions can be used.For the2D case in[17] we have evaluated the error of approximation by RBFs for a"noisy"function.The RMS error is equal to002for the z-coordinates of469random points.However, we have to state that a small RMS does not guarantee correct reconstruction results. In our experience,the results of reconstruction heavily depend on the uniformity of data distribution,and in the case of reconstruction with CSRBFs they depend also on appropriate choice of the radius of support.Thus,how to evaluate the accuracy of restoration is an open question.Nevertheless,we suppose that RBFs provide sufficiently good interpolation features,and here we illustrate visually(see Fig.5) the accuracy of reconstruction as the boolean difference between RBF and CSRBF solutions for the same dataset"head"that we have already used as an example in this section(see Fig.4(a)and Table1).Fig.5shows an increasing white area(difference that can be observed on the right-hand side of the reconstructed"head")caused by an inappropriate choice of the radius of support.Let us note that we have a lack of data in the lower part of the"head".Increasing the radius of support provides better reconstruction results. However,the work required for correct reconstruction of the object becomes nearly proportional to the total number of all scattered data points(see Table2).Note that the approach of3D surface reconstruction taken in this study does not guarantee restoration of highly topologically complex volume objects.As noted in[36],the accuracy of the restoration strongly depends on the uniformity of the distribution of data.Moreover,RBFs demonstrate excessive blending features that lead to undesirable smoothing effects.For3D reconstruction using cross-sectional data,in[36]it is proposed that,for m different contours in one slice,m different function descriptions of separate contours must be used and that union of the m carrier functions defines the description of the reconstructed2D object.That is, introducing m carrier functions allows us to localize different contours situated9in one slice to avoid an excessive blending or"spilling"of contours.For the3D case such an approach looks exceedingly complicated.Nevertheless,we have to notice that the results of reconstruction do not depend on the choice of the carrier functions.Naturally,the approach taken by Turk and O’Brien in[21]of using points specified on both sides of the surface can be applied(see Fig.6(c)).5ConclusionsIn this paper,we thoroughly investigated the problem of development C++tools based on the use of CSRBFs splines for implementation in various CG applica-tions.The main goal of the ongoing project is to understand the processing char-acteristics and capabilities of RBFs and their visualization aspects.Thanks to our efficient octal tree algorithm,the resulting matrix is a band-diagonal matrix(not simply a sparse one)that reduces computational complexity,allows the applica-tion of a simple and direct SLAE solver,and permits the exploration of sufficiently large data sets.C++language was used to create reusable,extensible,and reliable components,which can be used in later research.The toolkit we have created can be used in conjunction with other algorithms to create animated applications.Our second goal was very clear:to develop an application for introductory university-level courses for students with no programming and CG experience.Students can download our software binaries(Linux and Windows versions)from[29].On this page,we have also established an online reconstruction server,where they can in-put a datafile and get a visualization of a VRML object in their browser(Netscape Communicator4.x is recommended).6AcknowledgmentsWe would like to thank our anonymous reviewers for the comments,which were very helpful and important for our current and further research.References[1]V.Shapiro,Real Functions for Representation of Rigid solids,Computer AidedGeometric Design,11(2):153-175,1994.[2] A.Pasko,V.Adzhiev, A.Sourin and V.Savchenko,Function Representationin Geometric Modeling:Concepts,Implementation and Applications,The Visual Computer,11(6):429-446,1995.10[3]http://www-sop.inria.fr/prisme/fiches/Reconstruction/[4] B.Geiger,Three-dimensional modeling of human organs and its application todiagnosis and surgical planning,TR2105,INRIA,France,Dec1993.[5]V.Savchenko,A.Pasko,T.L.Kunii and A.Savchenko,Feature Based Sculpting ofFunctionally Defined3D Geometric Objects,Proceedings of the Multimedia Modeling Conference,Singapore,14-17Nov.,T.T.Chua et al.(eds.),World Scientific Pub.,341-34,1995.[6]S.Lee,G.Wolberg,and S.Y.Shin,Scattered Data Interpolation with Multilevel B-Splines,IEEE Transaction on Visualization and Computer Graphics,3(3),228-244, 1997.[7]S.Muraki,V olumetric Shape Description of Range Data Using"Blobby Model",Computer Graphics(Proceedings of SIGGRAPH),25(4),227-235,1991.[8]J.H.Ahlberg,E.N.Nilson,J.L.Walsh,The Theory of Splines and Their Applications,Academic Press,New York,1967.[9]J.Dushon,Splines Minimizing Rotation Invariants Semi-Norms in Sobolev Spaces,Constructive Theory of Functions of Several Variables,W.Schempp and K.Zeller (eds.),Springer-Verlag,85-100,1976.[10]V.A.Vasilenko,Spline-functions:Theory,Algorithms,Programs,Novosibirsk,NaukaPublishers,1983.[11]R.M.Bolle and B.C.Vemuri,On Three-Dimensional Surface ReconstructionMethods,IEEE Transactions on Pattern Analysis and Machine Intelligence,13(1), 1-13,1991.[12]G.Greiner,Surface Construction Based on Variational Principles,Wavelets,Imagesand Surface Fitting,urent et al.(eds.),AL Peters Ltd.,277-286,1994. [13]V.Savchenko and V.Vishnjakov,The Use of the"Serialization"Approach in theDesign of Parallel Programs Exemplified by Problems in Applied Celestial Mechanics, Performance Evaluation of Parallel Systems,Proceedings PEPS,University of Warwick,Coventry,UK,29-30Nov.,126-133,1993.[14]P.Litwinovicz and L.Williams,Animating Images with Drawing,Computer Graphics(Proceedings of SIGGRAPH),409-412,1994.[15]J.C.Carr,W.R.Fright and R.K.Beatson,Surface Interpolation with Radial BasisFunctions for Medical Imaging,IEEE Transaction on Medical Imaging,16(1),96-107,1997.[16]F.L.Bookstein,Principal Warps:Thin Plate Splines and the Decomposition ofDeformations,IEEE Transactions on Pattern Analysis and Machine Intelligence, 11(6),567-585,1989.[17]V.Savchenko,A.Pasko,O.Okunev and T.L.Kunii,Function Representation of SolidsReconstructed from Scattered Surface Points and Contours,Computer Graphics Forum,14(4),181-188,1995.11。
