Software performance antipatterns - Common performance problems and their solutions (2001)
FortiGate 系列产品说明书

Real Time Network Protectionfor SOHO/Branch Office/100FortiGate™ Antivirus Firewalls are dedicated, hardware-based unitsthat deliver complete, real-time network protection services at thenetwork edge. Based on Fortinet’s revolutionary FortiASIC™ Content Processor chip,the FortiGate platforms are the only systems that can detect and eliminate viruses,worms, and other content-based threats without reducing network performance —even for real-time applications like Web browsing. FortiGate systems also includeintegrated firewall, content filtering, VPN, intrusion detection and prevention, and traffic shaping functions, makingthem the most cost effective, convenient, and powerful network protection solutions available.Tailored for the needs of smaller offices, the FortiGate-50A and FortiGate-100 systems deliver the same enterprise class, network-based antivirus, content filtering, firewall, VPN, and network-based intrusion detection/prevention featured inall FortiGate models. Both the FortiGate-50A and FortiGate-100 support an unlimited number of users, and are ideally suited for small businesses, remote offices, retail stores, broadband telecommuter sites, and many other applications.The capabilities and speed of the FortiGate-50A are unmatched by comparable devices in its class. The FortiGate-100 includes all of the capabilities of the FortiGate-50A and adds a DMZ port, traffic shaping, and increased throughput. The FortiGate-50A and FortiGate-100 are kept up to date automatically by Fortinet’s FortiProtect Network, which provides continuous updates that ensure protection against the latest viruses, worms, Trojans, intrusions and other threats —around the clock, and around the world.Product Highlights• Provides complete real-time network protection through a combination of network-based antivirus, web content filtering, firewall, VPN, network-based intrusion detection and prevention, traffic shaping, and anti-spam• Eliminates viruses and worms from email, file transfer, and real-time (Web) traffic without degrading network performance• Easy to use and deploy – quick and easy configuration wizard walks administrators through initial setup with graphical user interface• Reduces exposure to threats by detecting and preventing over 1300 different intrusions, including DoS and DDoS attacks• Boasts the best combination of price, performance, and value relative to all other products on the market • Delivers superior performance and reliability from hardware accelerated, ASIC-based architecture• Automatically downloads the latest virus and attack database and can accept instant “push” updates from the FortiProtect Network• Manage thousands of FortiGate units through the FortiManager™ central management tool• Underlying FortiOS™ operating system is ICSA-certified for Antivirus, Firewall, IPSec VPN, and Intrusion Detection• Virus quarantine enables easy submission of attack sample to Fortinet Threat Response Team• Web-based graphical user interface and content filteringsupports multiple languages/100System SpecificationsPowerLightStatusLight PowerConnectionRS-232SerialConnectionExternalInterfaceInternalInterface ExternalInterfaceInternalInterfacePowerLightStatusLightPowerConnectionRS-232SerialConnectionExternalInterfaceInternalInterfaceExternalInterfaceInternalInterfaceDMZInterfaceDMZInterfaceNetwork-based Antivirus(ICSA Certified)AV-VPNFirewall(ICSA Certified)Web Content FilteringVPN(ICSA Certified)Dynamic IntrusionDetection and Prevention(ICSA Certified)Remote AccessKey Features & BenefitsDescriptionDetects and eliminates viruses and worms in real-time. Scans incoming and outgoing emailattachments (SMTP, POP3, IMAP) and Web(HTTP) and file transfer (FTP) traffic — withoutdegrading Web performanceScans and eliminates viruses and worms found inencrypted VPN tunnelsIndustry standard stateful inspection firewallProcesses Web content to block inappropriatematerial and malicious scripts via URL blockingand keyword/phrase blockingIndustry standard PPTP, L2TP, and IPSec VPNsupportDetection and prevention of over 1300 intrusionsand attacks, including DoS and DDoS attacks,based on user-configurable thresholds. Auto-matic updates of IPS signatures from FortiProtectNetworkSupports secure remote access from any PCequipped with Fortinet Remote VPN ClientBenefitCloses the vulnerability window by stoppingviruses and worms before they enter the networkPrevents infection by remote users and partnersCertified protection, maximum performanceand scalabilityAssures improved productivity and regulatorycomplianceLower costs by using the public Internet forprivate site-to-site and remote accesscommunicationsStops attacks that evade conventional antivirusproducts, with real-time response to fast-spreading threatsLow cost, anytime, anywhere access for mobileand remote workers and telecommuters FortiGate-50AFortiGate-100USBPortsFortiGate-50AFortiGate-100/100SpecificationsInterfaces10/100 Ethernet Ports 23DMZ port•System Performance Concurrent sessions 25,000200,000New sessions/second10004,000Firewall throughput (Mbps)5095168-bit Triple-DES throughput (Mbps)1025Users UnrestrictedUnrestrictedPolicies 5001000Schedules256256Antivirus, Worm Detection & Removal Automatic virus database update from FortiProtect Network••Scans HTTP, SMTP, POP3, IMAP, FTP and encrypted VPN Tunnels ••Block by file size••Firewall Modes and Features NAT, PAT, Transparent (bridge)••Routing mode (RIPv1, v2)••Virtual domains22VLAN tagging (802.1q)••User Group-based authentication ••H.323 NAT Traversal ••WINS support••VPNPPTP, L2TP, and IPSec ••Dedicated tunnels2080Encryption (DES, 3DES, AES)••SHA-1 / MD5 authentication••Supports Fortinet Remote VPN Client ••PPTP, L2TP, VPN client pass though ••Hub and Spoke VPN support••IKE certificate authentication (X.509)••Manual key and Auto key IKE ••IPSec NAT Traversal ••Aggressive mode ••Replay protection ••Remote access VPN••Interoperability with major VPN vendors ••Content FilteringURL/keyword/phrase block ••URL Exempt List ••Protection profiles3232Blocks Java Applet, Cookies, Active X ••FortiGuard™ web filtering support••Dynamic Intrusion Detection and Prevention Intrusion prevention for over 1300 attacks ••Automatic real-time updates from FortiProtect Network ••Customizable detection signature list ••Anti-SpamReal-time Blacklist/Open Relay Database Server ••MIME header check••Keyword/phrase filtering••IP address blacklist/exempt list••Logging/MonitoringLog to remote Syslog/WELF server ••SNMP••Graphical real-time and historical monitoring ••Email notification of viruses and attacks ••VPN tunnel monitor ••NetworkingMultiple WAN link support •PPPoE client ••DHCP client••DHCP server (Internal)••Policy-based routing••System Management Console interface (RS-232)••WebUI (HTTPS)••Multi-language support ••Command line interface••Secure Command Shell (SSH)••FortiManager System••AdministrationMultiple administrators and user levels ••Upgrades & changes via TFTP & WebUI ••System software rollback••User Authentication Internal database••External LDAP/RADIUS database support ••RSA SecurID••IP/MAC address binding••Xauth over RADIUS support for IPSec VPN ••Traffic Management DiffServ setting••Policy-based traffic shaping••Guaranteed/Maxiumum/Priority bandwidth ••Dimensions Height 1.38 inches 1.75 inches Width 8.63 inches 10.25 inches Length 6.13 inches 6.13 inches Weight1.5 lb (0.68 kg)1.75 lb (0.8 kg)PowerDC input voltage 12V 12V DC input current 3A5AEnvironmentalOperating Temperature 32 to 104 °F 32 to 104 °F (0 to 40 °C)(0 to 40 °C)Storage Temperature-13 to 158 °F -13 to 158 °F (-25 to 70 °C)(-25 to 70 °C)Humidity5 to 95% 5 to 95%non-condensing non-condensingCompliance & Certifications FCC Class A Part 15••CE ••UL•ICSA Antivirus, Firewall, IPSec, NIDS••FortiGate-50AFortiGate-100/100Specifications subject to change without notice. Copyright 2004 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiASIC, FortiGuard, FortiOS and FortiProtect are trademarks of Fortinet, Inc. DAT1150409AustraliaLevel 17, 201 Miller StreetNorth Sydney 2060AustraliaTel: +61-2-8923-2555Fax: +61-2-8923-2525ChinaCyber Tower, Suite B-9032 Zhongguancun Nan Ave.Hai Dian, Beijing 100086ChinaTel: +8610-8251-2622Fax: +8610-8251-2630France69 rue d’Aguesseau92100 Boulogne BillancourtFranceTel: +33-1-4610-5000Tech Support: +33-4-9300-8810Fax: +33-1-4610-5025GermanyFeringaparkFeringastrasse 685774 München-UnterföhringGermanyTel: +49-(0)-89-99216-300Fax: +49-(0)-89-99216-200Hong KongRoom 3206, 32/FConvention Plaza - Office Tower1 Harbour Road, WanChaiHong KongTel: +852-3171-3000Fax: +852-3171-3008JapanKokusai Tameike Building 6F2-12-10 Akasaka, Minato-kuTokyo 107-0052JapanTel: +81-3-5549-1640Fax: +81-3-5549-1641Korea27th FloorKorea World Trade Center159 Samsung-DongKangnam-KuSeoul 135-729KoreaTel: +82-2-6007-2007Fax: +82-2-6007-2703Taiwan18F-1, 460 SEC.4Xin-Yi RoadTaipei, Taiwan, R.O.C.Tel: +886-2-8786-0966Fax: +886-2-8786-0968United Kingdom1 Farnham RoadGuildford, Surrey GU2 4RGUnited KingdomTel: +44-(0)-1483-549061Fax: +44-(0)-1483-549165United States920 Stewart DriveSunnyvale, CA 94085USATel: +1-408-235-7700Fax: +1-408-235-7737Email:******************。
JOLT获奖图书

软件业的奥斯卡:Jolt奖Jolt大奖素有“软件业界的奥斯卡”之美誉,共设通用类图书、技术类图书、语言和开发环境、框架库和组件、开发者网站等十余个分类,每个分类设有一个“震撼奖”(Jolt Award)和三个“生产力奖”(Productivity Award)。
一项技术产品只有在获得了Jolt奖之后才能真正成为行业的主流,一本技术书籍只有在获得了Jolt奖之后才能真正奠定经典的地位。
JOLT大奖共设有:通用图书、技术图书、配置管理、协作工具、数据库引擎/数据库工具、设计工具/建模、开发环境、企业工具、库/框架、移动开发工具、项目管理工具、安全工具、测试、测试、工具、Web开发工具、Web网站/开发者网络等分类。
JOLT获奖图书年份类别书名作者1990图书震撼奖Annotated C++Reference Manual Margaret Ellis and BjarneStroustrup图书生产力奖The Art of Human-Computer Interface Design Brenda LaurelProgramming Windows,2nd Ed Charles PetzoldTurbo C++DiskTutor Greg Voss1991图书震撼奖Object-Oriented Design with Applications Grady Booch图书生产力奖Advanced C++:Programming Styles and Idioms James CoplienObject-Oriented Modeling and Design James rumbaughObject Lifecycles:Modeling the World in States Sally Shlaer1992图书震撼奖Undocumented Windows Andrew SchulmanDecline and Fall of the American Programmer Ed Yourdon图书生产力奖Object-Oriented Software Engineering:A Use-Case Driven Approach Ivar JacobsonLiter Programming Donald KnuthEffective C++Scott Meyers1993图书震撼奖Code Complete Steve McConnellObject-Oriented Design and Analysis with Applications,2nd Edition图书生产力奖Applied Cryptography Bruce SchneierProgramming on Purpose,Vols.I and II P.J.PlaugerWriting Solid Code,Steve Maguire11994图书震撼奖Essential Client/Server Survival Guide Robert Orfali图书生产力奖Debugging the Development Process Steve MaguireDesign Patterns GofThe Design and Evolution of C++Bjarne Stroustrup1995图书震撼奖Thinking in C++Bruce Eckel图书生产力奖About Face:The Essentials of User Interface Design Alan CooperA Discipline for Software Engineering Watts HumphreyWhat Every Programmer Should Know About Object-Oriented Design Meilir Page-Jones1996图书震撼奖Rapid Development Steve McConnell 图书生产力奖Creating a Software Engineering Culture Karl WeigersPattern-Oriented Software Architecture Frank BuschmannThe Essential Distributed Objects Survival Guide Robert Orfali1997图书震撼奖Object-oriented Software Construction Bertrand Meyer 图书生产力奖The Deadline:A Novel about Project Management Tom DeMarcoUML DistilledBuilding Object Applications That Work,Scott Ambler1998图书震撼奖Component Software—Beyond Object-Oriented Programming Clemens Szyperski 图书生产力奖Anti-Patterns:Refactoring Software,Architectures,and Projects in Crisis William J.BrownSoftware Architecture in Practice Paul ClementsThinking in Java Bruce Eckel1999图书震撼奖Software for Use:A Practical Guide to the Models and Methods of UsageCentered DesignLarry Constantine 图书生产力奖xtreme Programming Explained:Embrace Change Kent BeckSoftware Requirements Karl E.WiegersAfter the Gold Rush:Creating a True Profession of Software Engineering Steve M.McConnell2000图书震撼奖Adaptive Software Development JamesA.Highsmith 图书生产力奖Don't Make Me Think!A Common Sense Approach to Web Usability Steve KrugSecrets and Lies Bruce SchneierWriting Effective Use Cases Alistair Cockburn22001图书震撼奖Effective Java Joshua Bloch图书生产力奖Agile Software Development Alistair CockburnSoftware Craftmanship Pete McBreenUnder Press and On Time Ed Sullivan2002通用图书震撼奖Agile Software Development:Principles,Patterns and Processes敏捷软件开发--原则、模式与实践Robert C.Martin 通用图书生产力奖Documenting Software Architectures:Views and Beyond软件构架编档Paul ClementsPatterns of Enterprise Application Architecture企业应用架构模式Martin FowlerTest-Driven Development:By Example测试驱动开发Kent Beck技术图书震撼奖Thinking in Java(3rd edition)Java编程思想Bruce Eckel技术图书生产力奖Core Java2,Vol.1:Fundamentals(6th edition)最新Java2核心技术卷I:原理Cay HorstmannPHP and MySQL Web DevelopmentPHP和MySQL Web开发Luke WellingUnderstanding Web Services Eric Newcomer2003通用图书震撼奖Waltzing with Bears:Managing Risk on Software Projects与熊共舞:软件项目风险管理Tom DeMarco通用图书生产力奖The Art of UNIX ProgrammingUNIX编程艺术Eric S.RaymondLean Software Development:An Agile Toolkit敏捷软件开发工具--精益开发方法Mary PoppendieckPragmatic Starter Kit程序员修炼Dave Thomas技术图书震撼奖Test-Driven Development:A Practical Guide测试驱动开发:实用指南David Astels3技术图书生产力奖About Face2.0Alan Cooper Agile Database Techniques:Effective Strategies for the Agile SoftwareDeveloper敏捷数据Scott W.AmblerCode Reading:The Open Source Perspective代码阅读方法与实践Diomidis Spinellis2004通用图书震撼奖Head First Design Patterns深入浅出设计模式Elisabeth Freeman,通用图书生产力奖Joel on SoftwareJoel说软件Joel SpolskyRefactoring to Patterns重构与模式Joshua erievskySoftware Factories:Assembling Applications with Patterns,Models,Frameworks,and Toolsack Greenfield,技术图书震撼奖Better,Faster,Lighter Java轻快好的JavaBruce A.Tate技术图书生产力奖C++Coding Standards:101Rules,Guidelines,and Best PracticesC++编程规范Herb SutteHibernate:A Developer's NotebookHibernate:程序高手秘笈James ElliottJava Developer's Guide to Eclipse,Second EditionEclipse权威开发指南Jim D'Anjou2005通用图书震撼奖Prefactoring软件预构艺术Ken Pugh通用图书生产力奖Innovation Happens Elsewhere:Open Source as Business Strategy Ron Goldman,Richard P.GabrielProducing Open Source Software:How to Run a Successful Free SoftwareProjectKarl FogelThe Art of Project Management Scott Berkun4项目管理艺术技术图书震撼奖Agile Web Development with Rails应用Rails进行敏捷Web开发Dave Thomas技术图书生产力奖Framework Design Guidelines:Conventions,Idioms,and Patterns for LibrariesNET设计规范KrzysztofPractical Common Lisp Peter Seibel Why Programs Fail:A Guide to Systematic Debugging Andreas Zeller2006通用图书震撼奖Agile Software Development Alistair Cockburn通用图书生产力奖atastrophe Disentanglement E.M.BennatanPractices of an Agile Developer V.SubramaniamSoftware Estimation Demystifying the Black Art Steve McConnell技术图书震撼奖Head First Object-Oriented Analysis&Design深入浅出面向对象的分析与设计B.McLaughlin技术图书生产力奖Code Quality Diomidis SpinellisRefactoring Databases数据库重构Scott W.AmblerCSS:The Missing ManualCSS实战手册David Sawyer McFarland2007通用图书震撼奖Beautiful Code代码之美Andy Oram通用图书生产力奖Manage It!Your Guide to Modern Pragmatic Project Management项目管理修炼之道Johanna RothmanThe Myths of Innovation Scott BerkunRelease It!Design and Deploy Production-Ready Software Michael T.Nygard 技术图书震撼奖Continuous Integration:Improving Software Quality and Reducing Risk持续集成:软件质量改进和风险降低之道Paul Duvall技术图书生产力奖xUnit Test Patterns:Refactoring Test Code Gerard MeszarosHead First SQL:Your Brain on SQL—A Learner's Guide Lynn Beighley5深入浅出SQLThe Rails Way Obie Fernandez2008通用图书震撼奖Adrenaline Junkies and Template Zombies:Understanding Patterns ofProject Behavior通用图书生产力奖Emergent Design:The Evolutionary Nature of Professional SoftwareDevelopment自然发生的设计Intellectual Property and Open Source:A Practical Guide to ProtectingCode知识产权和开放源码:保护代码实用指南技术图书震撼奖Real World HaskellHaskell是一种纯函数式程式语言,此书获奖,看来函数编程开发的新趋势在未来将有更大的发展空间。
基于反模式的中间件应用系统性能优化

ISSN 1000-9825, CODEN RUXUEW E-mail: jos@Journal of Software, Vol.19, No.9, September 2008, pp.2167−2180 DOI: 10.3724/SP.J.1001.2008.02167 Tel/Fax: +86-10-62562563© 2008 by Journal of Software. All rights reserved.∗基于反模式的中间件应用系统性能优化兰灵, 黄罡+, 王玮琥, 梅宏(北京大学信息科学技术学院软件研究所,北京 100871)Anti-Pattern Based Performance Optimization for Middleware ApplicationsLAN Ling, HUANG Gang+, WANG Wei-Hu, MEI Hong(Institute of Software, School of Electronics Engineering and Computer Science, Peking University, Beijing 100871, China)+ Corresponding author: E-mail: huanggang@Lan L, Huang G, Wang WH, Mei H. Anti-Pattern based performance optimization for middlewareapplications. Journal of Software, 2008,19(9):2167−2180. /1000-9825/19/2167.htmAbstract: This paper presents an approach to optimizing performance of middleware applications based onanti-pattern. This approach has three major features: First, a meta-model is offered to build more understandable andformalized representation of anti-patterns; second, the detection of anti-patterns is based on both the static and thedynamic information, which is retrieved at runtime; third, refactorings operate without interrupt the running systems,and is completed in an automated way with the help of the middleware. A prototype based on J2EE has beendeveloped and an e-bookstore is used as a running example to illustrate the ideas introduced in this approach.Key words: anti-pattern; middleware; performance optimization; detection; refacotring摘要: 提出了一种基于反模式的中间件应用系统的性能优化方法.该方法的主要特点包括:建立了反模式元模型以使得反模式的表示更加准确;综合利用系统的静态信息和动态信息以检测运行系统中存在的反模式;系统重构在不中断应用系统运行的前提下在线执行,并在中间件的辅助下自动/半自动地完成.在J2EE平台上实现了支持该方法的原型系统,并通过网上书店的实例展示了该方法的有效性.关键词: 反模式;中间件;性能优化;检测;重构中图法分类号: TP391文献标识码: A模式是人们所熟知的一种经验的总结,它描述了对一些可重复出现问题的有效解决方案[1].作为对模式概念的一种扩展,反模式描述的是一个普遍采用的不良解决方案,该方案将会给应用系统带来负面的影响[2].为了去除反模式导致的负面影响,通常需要对应用系统进行重构,即在不改变系统行为的前提下,改变系统内部结构[3].完整的反模式描述中,最重要的部分是两个解决方案:会带来负面影响的反模式解决方案;相应的重构方案.反模式可以指导人们提高软件的质量属性,包括可扩展性、可维护性以及软件性能等.特别地,它可以帮助人们查找系统中导致性能低下的根源并提供相应的优化方案.文献[4−8]介绍了一些与性能相关的反模式.∗ Supported by the National Natural Science Foundation of China under Grant Nos.90612011, 90412011, 60403030 (国家自然科学基金); the National Basic Research Program of China under Grant No.2005CB321800 (国家重点基础研究发展计划(973)); the Fok YingTong Education Foundation (霍英东教育基金)Received 2007-03-26; Accepted 2007-06-302168 Journal of Software软件学报 V ol.19, No.9, September 2008目前,对于反模式的研究主要停留在反模式的收集和整理阶段,缺少有效的方法或者工具来指导或帮助人们正确、高效地使用反模式.人们一般按照如下的步骤检测反模式并重构应用系统:首先,通过对源代码以及设计文档的分析,检测出应用系统中存在的反模式;然后,确定重构方案;最后,修改应用系统的源代码,并重新编译、部署应用以使得重构生效.然而,通过上述的步骤对应用系统进行性能优化时,会存在如下一些问题: •反模式的检测与系统重构仅仅依赖于源代码.首先,在对应用系统的维护与优化过程中,并不能够保证得到源代码.在目前的方法中,没有源代码将很难检测到应用系统中的反模式或者对应用系统进行重构.但是随着软件构件技术的发展,目前的许多应用系统都采用了基于构件的开发技术,并通过组装不同厂商提供的商用构件(commercial off-the-shelf,简称COTS)进行开发.这意味着获得应用系统完整的源代码或者设计文档非常困难.其次,仅限于对源代码的分析将无法检测到许多目前已知的性能反模式.从性能优化的角度来看,由于软件性能是一个运行时刻的概念,因此,大部分性能相关反模式的检测都需要考察某些运行时刻的信息,如构件之间的交互频率、构件实例消耗的内存等.然而,这些运行时刻信息无法通过分析源代码得到;最后,基于源代码的重构可能会引发其他问题.一般来说,性能优化会使应用系统变得更加复杂,使其更难以理解,在提高性能的同时导致应用系统其他质量属性降低.•系统重构往往是离线执行的.目前的重构是修改源代码,而不是直接修改运行时刻的应用系统,要使重构生效,应用系统需要经过“停止-更新-重启”的步骤,我们称这样的重构方式为离线重构.对于目前具有高可用性的应用系统而言,能够提供7(天)×24(小时)的不中断服务已经成为很普遍的需求.然而,由于对应用系统的离线重构将不得不中断应用系统的正常运行,因此无法满足应用系统的高可用需求.•系统重构需手工完成.在确定重构方案以后,需要系统开发或管理人员手工地完成重构工作.尽管目前有一些开发工具能够在一定程度上减少手工重构的工作量,但重构依然会给开发管理人员带来不小的负担.此外,已经进行的重构并不能持续保证正确有效.由于管理人员的失误,也许会实施不合适的重构方案;或者由于运行环境或者用户需求的变化,以前进行的重构方案已经不再适合当前的具体情况.在这种情况下,可能需要对重构进行回滚,即让应用系统恢复到该次重构以前的状态.但是对于手工进行的重构而言,要进行重构回滚会非常困难.综上所述,软件性能的特性以及目前应用系统的实际需求要求能够在系统的运行时刻应用反模式:对反模式的检测不应该仅依赖于源代码的分析,而应该更多地考虑运行时刻的信息;对应用系统的重构,应该在不中断正常运行的前提下完成,即实现运行时刻的在线重构.为了满足上述需求,底层平台需要提供相关的支持,以监测应用系统的状态并且在线调整其行为.在目前大型分布式应用系统的开发过程中,将应用系统搭建在中间件之上已经成为一种最普遍的解决方案,中间件主要解决的是分布式通信以及屏蔽底层平台的异构性问题.而随着中间件技术的发展,现在的中间件除了完成其基本功能外,还能够在运行时刻提供应用系统的动态信息,并在一定程度上调整其行为.由此可见,中间件可以作为运行时刻应用反模式的支撑机制.针对目前方法的局限性,本文将中间件技术引入到反模式应用中,提出了一种运行时刻基于反模式的中间件应用系统性能的优化方法,并在J2EE应用服务器PKUAS[9]上实现了一个原型系统.与传统的反模式应用方式相比,该方法主要有3点改进:1) 通过分析运行时刻的信息而不是仅仅分析源代码来检测应用系统中的反模式;2) 由中间件在运行时刻进行系统在线重构,无须修改应用系统,由此也不会导致中断应用系统的正常运行;3) 反模式的检测和系统重构由中间件自动/半自动地完成.本文第1节概述整个方法框架.第2节介绍反模式检测.第3节介绍应用系统的在线重构.第4节演示该方法的使用以及性能优化效果.第5节与相关工作进行比较.最后一节总结全文并展望将来的工作.1 基于反模式的性能优化过程图1展示了该方法的过程图.该方法一共包括两个子过程:一个是管理反模式的过程,另一个是进行性能优化的过程.兰灵等:基于反模式的中间件应用系统性能优化2169Antipattern evaluation andmodificationFig.1 Processes of anti-pattern based optimization图1 基于反模式的性能优化过程本节首先介绍反模式的管理过程,它主要分为两个步骤:1. 反模式注册:为了检测应用系统中存在的反模式并根据该反模式提供的重构方案对系统进行重构,首先必须注册这些待检的反模式.对一个反模式的定义需要包括如下一些部分:判断规则,用于检测运行系统中指定的反模式;重构方案,用于指导系统的重构工作以提高性能.这些反模式定义将被保存在一个反模式库中,以便在进行性能优化过程中使用或更新.2. 在线重构方案注册:在第1个步骤中注册的重构方案是离线的重构方案,通过对应用本身的调整来完成重构,该步骤一般是由领域专家来完成的.我们的方法不仅支持运行时刻的反模式检测,还支持运行时刻的系统在线重构.与离线重构相比,在线重构直接作用在运行系统之上,而不是作用在源代码之上,这些重构工作大部分可以在中间件的帮助下自动或者半自动地完成.在线重构模型应该由对中间件熟悉的专家完成,并添加到反模式库中.该方法中第2个过程是基于反模式的性能优化过程,它分为如下几个步骤:(1) 反模式激活:在实际的性能优化过程中,考虑到反模式检测的代价,如采集运行时刻信息导致的系统资源消耗等,我们的方法并不会尝试去检测所有已经注册的反模式.在反模式库中,反模式有两种状态:激活与去活状态.注册的反模式的默认状态是去活状态,用户可以设置反模式在这两种状态之间进行切换.在之后的反模式检测步骤中,系统只会尝试去检测已激活的反模式.在这个步骤中,用户的任务就是选择需要检测的反模式.用户可以根据系统当前的运行状态或者工作负载来决定需要检测哪些反模式.举例来说,我们可以在工作负载很低、系统空闲的情况下,对所有的反模式进行检测.(2) 运行时刻信息采集:在对应用系统的维护与优化过程中,并不能保证得到完整的源代码以及设计文档.2170 Journal of Software软件学报 V ol.19, No.9, September 2008因此,本方法中的反模式检测综合分析了静态信息与运行时刻的动态信息.静态信息主要是指应用部署包中的一些部署描述信息.运行时刻的动态信息包括构件之间的方法调用、远程客户端的IP地址等.这些信息可以在不修改应用系统的前提下,由中间件自动地进行采集.(3) 反模式检测:在采集到足够的信息以后,就可以根据反模式库中的反模式定义进行反模式检测了.在检测之前,已经采集到的原始运行信息需要进行一定的预处理.与已激活的反模式相关的信息需要进行萃取与重新组织.反模式检测的相关内容将在第2节进行更详细的介绍.(4) 重构规划:在反模式被检测出来以后,并不是马上就进行系统重构,在此之前还需要进行一些权衡工作.一些情况下,一个反模式可能有不止一种重构方案,此时,我们就应该根据一些因素,比如重构方案的代价、用户的具体需求来选择最适合的重构方案.另外,在同一个运行系统中,如果同时检测到多个反模式,这些反模式的重构方案之间可能会存在冲突.在这种情况下,我们需要在这些反模式以及与它们相关的重构方案作一个权衡,以得到尽量优化的解决方案.(5) 运行时刻系统重构:通过中间件可以在一定程度上调整应用系统的行为,我们的方法支持的是通过中间件的帮助,在运行时刻对应用系统进行重构.重构完成后,通过对当前应用系统的运行情况监测,有可能会进行重构回滚,使应用系统恢复到重构之前的状态.关于重构相关的内容将在第3节进行更详细的介绍.(6) 反模式评估和修正:在重构完成以后,性能优化的过程并没有结束,需要通过系统重构前后的性能比较,对反模式库中的反模式以及重构模型进行评估,并在需要的情况下进行修正,使以后的性能优化达到更好的效果.2 反模式检测2.1 反模式模型一个完整记录的反模式应该包含如下一些内容:应用系统的状态、造成该状态的原因、该状态引发的不良后果、相应的重构方案等.在进行反模式检测时,需要检查当前应用系统的状态是否与反模式定义的状态一致,从而确定该应用系统中是否存在该反模式.我们通过对目前已知的性能相关的反模式进行调研,将检测反模式所需的应用系统状态信息分为如下3类:•件信息:包括构件类型(如EJB/Servlet/POJO等)、构件方法(如方法名称、方法个数等)、构件配置(如实例池大小等)、构件操作(如构件回调方法等);•件交互信息:包括方法调用类型(如同步/异步调用等)、方法调用参数(如参数大小等)、方法调用序列;•境信息:包括中间件服务配置信息(如事务过期时间、线程池大小等)与底层硬件信息(如内存使用情况、网络拓扑结构等).在上述信息中,除了某些与应用逻辑相关的构件操作以外,其余信息都是可以由中间件自动获取的,因此,大部分的反模式都可以自动检测.但是,目前的反模式几乎都是使用自然语言来描述的.使用这种描述方法使得人们很难精确地表示它,更不可能实现自动化检测.我们给出了一个基于MOF[10]的元模型,它可以表示上述这3类的应用状态信息.与自然语言相比,使用这个元模型可以更加准确地表示反模式.而且,用户可以使用图形化的方式对反模式模型进行定义、编辑,使得记录反模式更加方便,图形化的反模式模型也更利于理解.图2展示了该元模型的简化版本,它一共包含5类实体,其中:Component代表构件;Call代表构件之间的调用关系;Method 代表调用的方法;Service代表中间件服务;Host代表物理主机.这5类实体还包含若干相应的属性,而实体之间可能存在着各种关联关系,由于篇幅所限,这里不再进行详述.目前,我们提供的反模式元模型可以描述J2EE领域的反模式.兰灵等:基于反模式的中间件应用系统性能优化2171Fig.2 Meta-Model of anti-pattern图2 反模式元模型2.2 反模式检测在进行反模式检测之前,需要先采集应用系统相关的信息,包括静态信息与运行时刻的动态信息.用户将根据待检测的反模式模型来确定需要采集当前应用系统的哪些状态信息.应用的静态信息,比如构件名称、构件类型等可以从部署描述符里得到.而应用的运行时刻信息,我们通过给中间件添加截取器的方式来进行采集.截取器会把用户关心的运行时刻信息写到日志文件中.这些截取器实现了分布式系统中常见的截取器模式[11],可以在不被应用感知的情况下添加/删除,而且可以动态地触发.通过这种方式,我们就可以很方便地定制采集的信息量以及时间段.在采集到应用系统信息之后,就可以进行反模式的检测工作:将应用系统信息与反模式模型进行匹配,以检测出当前运行系统中存在的反模式.对于构件信息与环境信息的匹配,可以通过简单的遍历来查找与模型匹配的状态信息,比如,为了找出public方法个数少于2个的EJB,可以通过遍历所有的构件完成.而对于构件交互信息匹配,比如找出存在指定调用序列的两个构件,由于一般情况下构件之间的调用数目都很庞大,无法通过遍历来完成反模式检测,因此我们采用了数据挖掘技术来完成这项任务.通过使用相关规则算法[12],可以查找出符合一定条件的调用序列,从而完成此类反模式的检测[13].3 系统重构3.1 系统重构模型与检测反模式时所需的状态信息类似,反模式对应的重构动作也可以分为如下3类:• 构件重构:包括添加/删除构件、修改构件属性、修改构件类型等;• 构件交互重构:包括修改调用类型、修改调用参数、重构调用序列等;• 环境重构:包括修改中间件服务属性等.系统重构模型同样使用第 2.1节中介绍的元模型进行构建,它描述了系统经过重构后的状态.用户需要定义一组重构操作从反模式模型演化为重构模型.重构操作可以分为两类:一类是原子操作,包括ADD,DEL,MOD 这3个基本的重构操作,它表示对模型中的实体或者实体之间的关系进行添加或删除,以及实体属性的修改,比如添加一个构件、删除两个构件之间的调用、修改服务的配置等;另一类是复合操作,它由一组预设的原子操作组成,而通过这一组原子操作可以为系统中引入一些可以提高性能的模式.此外,针对一些重构操作,我们给2172 Journal of Software软件学报 V ol.19, No.9, September 2008出了重构约束以保证这些操作的正确性.重构约束分为前置条件与后置条件两类,分别对系统重构前后的状态进行约束,只有满足这些条件,重构操作才可以执行.上述的重构模型是离线的重构模型,它可以用于指导用户对应用系统进行重构.但是,该类重构需要应用系统通过“停止-更新-重启”的步骤才能使所做的重构生效.为了达到不中断应用系统运行的目的,需要底层机制支持进行在线的重构.目前的中间件不仅为应用系统提供了一个运行平台,而且还提供了调整机制来完成应用系统的某些重构工作,它可以为在线重构提供支持.但是,由于重构模型中的重构动作是对应用自身的调整,而中间件的调整机制是在不修改应用的前提下对包括中间件在内的整个系统进行调整,因此,这二者并不是完全一致的.为了使重构模型指导中间件完成重构,需要将模型重构动作映射为中间件调整机制,生成在线重构模型.在线重构模型会根据底层的具体调整机制,引入一些中间件特定的实体与关系.由于不同的中间件会拥有不同的调整机制,因此,在线重构模型是基于特定中间件产品的,我们目前提供了基于J2EE应用服务器PKUAS的在线重构模型.3.2 重构规划在检测出反模式以后,需要确定如何进行重构.一般来说,每个反模式都有对应的重构方案,但是在具体的应用系统中,是否进行重构、如何重构,都需要进行事先的规划,才能保证性能优化效果尽可能地好,而进行重构的代价也尽可能地小.我们给出了一组指导原则,通过这些原则,能够指导如何进行系统重构工作(AP表示检测出来的反模式,R 表示重构方案):• AP→R:如果一个系统中只检测出一个反模式且该反模式只对应一个重构方案,则选择该重构方案.• AP→{R1,R2,…,R n}:如果一个反模式对应多个重构方案,则从中选择一个重构代价最小的方案.• AP1→R1,AP2→R2,…,AP n→R n:如果系统中存在不止一个反模式,而它们对应的重构方案之间又存在着冲突.则应该综合考虑反模式对性能的影响程度以及重构方案的代价,找出最适合的重构方案.反模式对性能的影响主要需要从以下几个方面考虑:1) 性能影响程度:不同的反模式对于应用系统的性能影响也不同,应该优先考虑去除对性能影响严重的反模式;2) 影响条件:某些系统虽然存在反模式,但是只有在特定条件下才会对性能造成影响.例如,某些反模式消耗了过多的系统资源,但是只会在系统负载较重的情况下才会造成应用系统的性能降低,而在轻载时不会影响性能.对于此类反模式,应根据应用系统的实际运行情况来判断是否去除;3) 出现频率:某些反模式虽然存在,但出现的次数很少.例如,某反模式造成了某方法调用的响应时间增大,但是在实际运行中,如果该方法很少被调用,那么,该反模式对应用系统的影响也很小.重构时应优先考虑去除出现更为频繁的反模式.重构方案代价需要从以下两方面考虑:1) 平台限制:一些重构操作虽然满足重构约束,但是,由于底层平台的限制导致实际无法执行.例如,某重构操作需要增大一个EJB的实例池大小以应对频繁的并发访问,但是,如果该EJB的实例池大小已经达到底层平台规定的上限,那么,该重构操作将无法执行.在进行规划的过程中,应该去除这一类的重构方案;2) 重构开销:任意一个重构操作都需要消费一定的时间,而对于在线重构来说,重构消费的时间越多,对运行中的应用系统影响也就越大.因此,应该尽量选择重构开销比较小的方案.对于重构规划中的影响因素,包括反模式对性能的影响以及重构方案代价,我们根据不同的反模式以及重构动作都给出了默认值,使得重构规划可以自动完成.用户也可以根据具体的情况为这些因素进行赋值,实现对重构规划的定制.兰灵 等:基于反模式的中间件应用系统性能优化21733.3 重构执行 在确定了重构方案以后,就可以根据重构模型进行应用系统重构.我们将目前的重构分为3个类别,分别是: • 自动重构:该重构可以由中间件自动完成,不需要用户过多的参与.自动重构包括环境重构以及部分对构件的重构,这些重构主要是修改构件或者环境的属性值,中间件可以在运行时刻自动完成这些修改,将属性值调整为重构方案中预设的值;• 半自动重构:这类重构也可以在中间件的帮助下完成,但需要用户进行一些工作;构件交互的重构一般属于该类别,它通常需要用户添加一些应用特定的辅助类,再由中间件借助这些辅助类完成重构工作; • 手工重构:对此类重构,我们的方法只能给出重构方案,而所有的重构工作将由用户自己完成,中间件无法提供更多的帮助.部分构件重构属于该类,这些重构牵涉到修改构件内部的应用逻辑,这类重构必须通过修改应用源代码才可能完成,因此需要用户全手工完成.在重构执行的过程中,将不可避免地对正在运行的应用系统造成一定的影响,需要尽可能地将这类影响降到最低.重构有可能影响到正在进行的应用系统行为,包括正在处理客户请求的构件或中间件服务需要重构,以及正在执行的调用需要进行重构.为了保证应用逻辑的一致性,不应该对这些正在进行的应用系统行为进行重构.因此,本方法中采用的在线重构只针对重构开始执行后的应用系统行为,包括构件或中间件服务接收到的新请求、构件之间新发起的调用.4 实例研究4.1 反模式描述为了更好地演示如何检测J2EE 应用中存在的反模式并进行相应的重构,我们开发了一个存在反模式的应用系统.该应用系统是一个网上书店的部分实现,主要用于客户端从服务器端获取图书的信息,并将这些信息显示在Web 页面上.该应用主要包括一个叫BookEJB 的实体bean 以及一些Web 端的构件,它们被部署在不同的机器上.该应用中存在着这样一个反模式:如图3所示,当客户端需要从服务器端获取一本书的包括书名、作者、价格在内的一组信息时,需要对服务器端的BookEJB 执行一系列的方法调用.由于客户端和服务器部署在不同的机器上,因此,这些调用都必须通过网络,调用参数与返回值都需要进行序列化与反序列化的操作,而且还会花费大量的时间通过网络传输数据.这种采用过多次远程调用获取一组属性值的方法会极大地降低性能,是应用中存在的一个性能反模式.它是反模式“细粒度远程调用(fine-grained remote calls)”[5]中的一种.Fig.3 Anti-Pattern of fine-grained remote calls and the refactoring图3 “细粒度远程调用”反模式及重构示意图为了去除该反模式带来的性能影响,需要对网上书店系统进行重构.一种重构方案是通过一次远程调用就Network。
FortiADC 产品数据表说明书

DATA SHEETFortiADC ™FortiADC 60F , 100F , 200F , 300F , 400F , 1000F , 2000F , 4000F , 5000F and VMHighlights§Comprehensive server load balancing for 99.999% application uptime §Server offloading for improved application acceleration, scale and TCO§Intelligent traffic management for optimized application delivery and availability§Web Application Firewall with Integrated vulnerability scanner §Hardware-based SSL Offloading, Forward Proxy, and Visibility §Advanced User Authentication §Included Global Server Load Balancing§Included Link Load Balancing and WAN Optimization §Scripting for Custom Load Balancing, Health Check and Content RewritingApplication Delivery without any limits.The FortiADC Application Delivery Controllers (ADC) optimize the availability, user experience, performance and application security. The FortiADC family of physical and virtual appliances delivers fast, secure and intelligent acceleration and distribution of demanding applications in the enterprise.Acceleration and PerformanceMulti-core processor technology, combined with hardware-based SSL offloading to accelerate application performance.Application Availability24x7 application availability through automatic failover, global server load balancing, and link load balancing to optimize WAN connectivity.Application ProtectionAdvanced Web Application Firewall protection from the OWASP top 10 and threat detection with Fortinet Security Fabric.DATA SHEET | FortiADC ™2HighlightsHardware-Based SSL Offloading, SSL Inspection, and VisibilityFortiADC offloads server-intensive SSL processing with support for 4096-bit keys, TCP connection management, data compression and HTTP request processing from servers. This speeds up response times, reduces load on the backend servers, allowing them to serve more users.SSL Forward Proxy utilizes FortiADC’s high-capacity decryption and encryption to allow other devices, such as a FortiGate firewall, to easily inspect traffic for threats. An inline pair of FortiADCs at the front end and back end of a firewall remove all encryption so that the firewall isn’t taxed with the additional load of SSL processing. FortiADC ensures seamless re-encryption with certificates intact with no user disruptions.FortiADC’s Transparent HTTP/S and TCP/S Mirroring Capabilities decrypt secure traffic for inspection and reporting. Copies of clear traffic can be sent for analysis by FortiGate or other third-party solutions for an indepth view of threats that may be hidden in encrypted traffic while FortiADC continues to perform its application delivery functions.FortiADC integrates with Gemalto’s SafeNet Enterprise Hardware Security Modules (HSMs) to use the advanced security certificates managed by the HSM for the encryption and decryption of secure application traffic. This lets organizations that use Gemalto’s SafeNet HSMs deploy a high-performance ADC solution using a strong, centrally-managed set of certificates and encryption keys.Disaster Recovery with Global Server Load BalancingFortiADC’s included Global Server Load Balancing (GSLB) makes your network reliable and available by scaling applications across multiple data centers for disaster recovery or to improve application response times. Administrators can set up rules that direct traffic based on site availability, data center performance and network latency.Web Application FirewallFortiADC offers multiple levels of protection to defend against attacks that target your web applications. FortiADC Web Application Firewall can detect a zero day attack and protect from OWASP top-10 and many other threats with multi-vector protection such as SQLi and XSS Protection, Web Scraping, Brute Force, Web Defacement, Protocol Validation (HTTP RFC) and Web Attack Signature using FortiGuard WAF Security Services for layer 7 attacks (subscription required). Also, FortiADC WAF provides full Web Vulnerability Scanning for your website to detect and alert against known attacks.Optimize Performance with PageSpeed, Caching, and CompressionFortiADC provides multiple services that speed the delivery of applications to users. The PageSpeed suite of website performance enhancement tools can automatically optimize HTTP , CSS, Javascript and image delivery to application users. Caching on FortiADC dynamically stores popular application content such as images, videos, HTML files and other file types to alleviate server resources and accelerate overall application performance. HTTP Compression employs GZIP and DEFLATE to intelligently compress many content types used by today’s latest web-based applications to reduce bandwidth needs and improve the user application experience.Deep Integration into the Fortinet Security FabricAs the threat landscape evolves, many new threats require a multi-pronged approach for protecting applications. Advanced Persistent Threats that target users can take many different forms than traditional single-vector attack types and can evadeprotections offered only by a single device. FortiADC’s antivirus and integration with FortiSandbox extend basic security protections toscan file attachments for known and unknown threats.DDoS Application, Web Filtering, IPS, Geo-IP and IP Reputation for Enhanced SecurityFortiGuard Web Filtering works with FortiADC’s SSL Forward Proxy feature to simplify the process of managing exceptions for secure traffic inspection. Instead of manually configuring single URLs, Web Filtering gives administrators the ability to choose websitesDATA SHEET | FortiADC™HighlightsAdvanced Layer 7 Load Balancing Intuitive L7 policy-based routing to dynamically rewrite content to support complex applications andserver configurations.Web Application Firewall Advanced Web Application Firewall that protects applications with Web Application Attack Signatures,Protocol Validation, Web Vulnerability Scanner, Bot Detection, DLP and File Restriction.SSL Offloading, Forward Proxy,and VisiblityHardware and software-based SSL offloading reduces the performance impact on your server infrastructure.Also provides SSL visibility, decryption and re-encryption for FortiGate to easily inspect traffic for threats.Application Optimization Speed up web application delivery with Compression, Caching, HTTP 2.0, and HTTP Page Speed-UP forimproved network and web server utilization.Global Server Load Balancing Included Global Server Load Balancing distributes traffic across multiple geographical locations for disaster Key Features and Benefitsby category type to enable or disable SSL traffic inspection as agroup instead of on a site by site basis. FortiADC also supports ourFortiGuard which provides multi services such as: IPS, Antivirusand IP Reputation service (subscription required) that protectsyou from sources associated with DoS/DDoS attacks, phishingschemes, spammers, malicious software and botnets.Scripting to Extend Built-in FeaturesFortiADC’s Lua-based scripting language gives you the flexibilityto create custom, event-driven rules using predefined commands,variables and operators. Using easy-to-create scripts, you get theflexibility you need to extend your FortiADC with specializedbusiness rules that give you almost unlimited possibilities for serverload balancing, health checks, application validation, content routing,and content rewriting to meet the needs of your organization.Link Load BalancingBuilt-in Link Load Balancing (LLB) gives you the option to connectyour FortiADC to two or more WAN links to reduce the risk ofoutages or to add additional bandwidth to relieve traffic congestion.FortiADC supports inbound and outbound Link Load Balancing tomanage traffic leaving or entering the device. Using policy routing,FortiADC can support complex NAT and routing requirements toaddress almost any network LLB architecture. With Tunnel Routingyou get high-speed, reliable site-to-site connectivity without theneed to lease expensive WAN links. It aggregates multiple linksto create a virtual tunnel to a remote data center that ensuresavailability especially for applications that are time sensitive andrequire large single-session bandwidth such as video conferencing.Analytics and VisibilityFortiADC offers real-time and historical information about yourappliance, which includes the logical topology of real-server pools,user/application data-analytics, security threats, attack maps andsome other system events and alerts.FortiADC DashboardVM and Public Cloud OptionsFortiADC provides maximum flexibility in supporting your virtual andhybrid environments. The virtual versions of FortiADC support all thesame features as our hardware-based devices and can be deployedin VMware, Microsoft Hyper-V, Citrix XenServer, Open Source Xen,and KVM platforms. FortiADC is also available for Amazon WebServices, Microsoft Azure, Google Cloud and Oracle Cloud.DATA SHEET | FortiADC™4Global Server Load Balancing (GSLB)§Global data center DNS-based failover of web applications§Delivers local and global load balancing between multi-site SSL VPN deployments§DNSSEC§DNS Access Control Lists§GSLB setup wizardDeployment Modes§One arm-mode (Proxy with X-forwarded for support)§Router mode§Transparent mode (switch)§High Availability (AA/AP Failover)Web Application FirewallApplication Protection§OWASP Top 10§Web Attack Signature§Bot Detection§Web Vulnerability Scanner§HTTP RFC complianceSecurity Services§SQLi/XSS Injection Detection§Web Scraping§CSRF Protection§Brute Force Protection§Web Defacement Protection§Data Leak Prevention§File Restriction§Cookie Security§XML/JSON/SOAP Validation§HTTP Header SecurityApplication AvailabilityEasy to use and configure Layer 4/7 policy andgroup management§Virtual service definition with inherited persistence, load balancing method and pool members§Static, default and backup policies and groups§Layer 4/7 application routing policy§Layer 4/7 server persistence§Application load balancing based on round robin, weighted round robin, least connections, shortest response§Granular real server control including warm up rate limiting and maintenance mode with session ramp down§Custom Scripting for SLB and Content Rewriting§Application Templates for Microsoft Applications including SharePoint, Exchange and Windows Remote Desktop§Application and script health checks§Clone Traffic PoolsLayer 4 Application Load Balancing§TCP, UDP stateless protocols supported§Round robin, weighted round robin, least connections, shortest response§L4 dynamic load balancing based on server parameters (CPU, Memory and disk)§Persistent IP, has IP/port, hash header, persistent cookie, hash cookie, destination IP hash, URI hash, full URI hash, host hash, host domain hashLayer 7 Application Load Balancing§DNS, HTTP, HTTPS, HTTP 2.0 GW, FTP, SIP, RDP, RADIUS, MySQL, RTMP, RTSP supported§L7 content switching– HTTP Host, HTTP Request URL, HTTP Referrer– Source IP Address§URL Redirect, HTTP request/response rewrite (includes HTTP body)§Layer 7 DNS load balancing, security, and caching§403 Forbidden Rewrite§Content rewritingLink Load Balancing§Inbound and outbound LLB§Support for Policy Route and SNAT§Multiple health check target support§Configurable intervals, retries and timeouts§Tunnel RoutingFeaturesDATA SHEET | FortiADC ™5FeaturesApplication AccelerationSSL Offloading and Acceleration§Offloads HTTPS and TCPS processing while securing sensitive data§Full certificate management features§SSL Forward Proxy for secure traffic inspection §HTTP/S Mirroring for traffic analysis and reporting §Support TLS 1.3HTTP and TCP Optimization§100x acceleration by off-loading TCP processing§Connection pooling and multiplexing for HTTP and HTTPS §HTTP Page Speed-UP for Web Server Optimization and Acceleration §TCP buffering§HTTP Compression and Decompression §HTTP Caching (static and dynamic objects) §Bandwidth allocation with Quality of Service (QoS) §HTTP and Layer 4 Rate Limiting Authentication Offloading §Local §LDAP §RADIUS §Kerberos§SAML 2.0 (SP & Idp)§Two-Factor Authentication — FortiToken and Google AuthenticationNetworking§NAT for maximum flexibility and scalability §VLAN and port trunking support§Cisco ACI, Nutanix, OpenStack and Ansible §NVGRE and VXLAN Support§BGP and OSPF with Route Health Inspection (RHI) §IPv6 Support §IPv6 routing §IPv6 firewall rulesApplication Security§FortiGuard Antivirus and FortiSandbox integration §GEO IP security and logs (subscription required) §Stateful firewall§Web Filtering (subscription required) §IP Reputation (subscription required) §IPv4 and 6 firewall rules§Granular policy-based connection limiting §Syn Cookie Protection §Connection Limits§Intrusion Prevention System (subscription required) §Application DDoS Protection §DNS SecurityManagement§Single point of cluster management§CLI Interface for configuration and monitoring §Secure SSH remote network management §Secure Web UI access§Central management for multiple FortiADC devices §RESTful API§SNMP with private MIBs with threshold-based traps §Real-time Data Analytics §Syslog support§Role-based administration §In-build diagnostic utilities §Real-time monitoring graphs §Built-in reporting§FortiView Integration §Data Analytics§Getting Started wizard for first-time login §Virtual Domains (VDOMs)DATA SHEET | FortiADC ™6SpecificationsHeight x Width x Length (mm)38 x 216 x 16044 x 440 x 26844 x 432 x 301.4Weight2.2 lbs (1 kg)9.9 lbs (4.5 kg)10.98 lbs (4.98 kg)All performance values are “up to” and vary depending on the system configuration.* Layer 7 CPS — measures number of new HTTP connections (1 HTTP request per TCP connection)** Tested with 1 HTTP request per SSL connection; SSL Ciphers=AES256-SHA; 2K KeysFortiADC 100FFortiADC 200FFortiADC 60FDATA SHEET | FortiADC ™7SpecificationsHeight x Width x Length (mm)44 x 438 x 41644 x 438 x 41644 x 438 x 530 Weight20 lbs (9.07 kg)20 lbs (9.07 kg)22.6 lbs (10.3 kg)All performance values are “up to” and vary depending on the system configuration.* Layer 7 CPS — measures number of new HTTP connections (1 HTTP request per TCP connection) ** Tested with 1 HTTP request per SSL connection; SSL Ciphers=AES256-SHA; 2K KeysFortiADC 1000FFortiADC 400FFortiADC 300FDATA SHEET | FortiADC ™8Height x Width x Length (mm)44 x 438 x 530 88 x 438 x 53080.6 x 436.9 x 777.2Weight22.6 lbs (10.3 kg)27 lbs (12.25 kg)68.3 lbs (31 kg)All performance values are “up to” and vary depending on the system configuration.* Layer 7 CPS — measures number of new HTTP connections (1 HTTP request per TCP connection) ** Tested with 1 HTTP request per SSL connection; SSL Ciphers=AES256-SHA; 2K Keys *** Subject to availabilitySpecificationsFortiADC 2000FFortiADC 4000FFortiADC 5000FDATA SHEET | FortiADC™SpecificationsHardware SpecificationsHypervisor Support VMware ESX/ESXi, Citrix XenServer, Open Source Xen, Microsoft Hyper-V, KVM, AWS, Azure, Google Cloud, Oracle Cloud. Please see the FortiADC-VM Install Guide for thelatest hypervisor versions supported.L4 Throughput* 1 Gbps 2 Gbps 4 Gbps10 Gbps16 Gbps24 GbpsVirtual Domains005101520vCPU Support (Maximum)12481632Memory Support (Maximum) 4 GB 4 GB8 GB16 GB32 GB64 GBNetwork Interface Support (Maximum)101010101010Storage Support (Minimum / Maximum)50 MB / 1 TB50 MB / 1 TB50 MB / 1 TB50 MB / 1 TB50 MB / 1 TB50 MB / 1 TB Throughput Hardware Dependent Hardware Dependent Hardware Dependent Hardware Dependent Hardware Dependent Hardware Dependent Management HTTPS, SSH CLI, Direct Console DB9 CLI, SNMP*********************************************************************************************************************************************************************************.5.Order Information Copyright © 2019 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, FortiCare® and FortiGuard®, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.FST-PROD-DS-ADC3FAD-DAT-R36-201908。
低频活动漂浮潜水船声探测系统(LFATS)说明书

LOW-FREQUENCY ACTIVE TOWED SONAR (LFATS)LFATS is a full-feature, long-range,low-frequency variable depth sonarDeveloped for active sonar operation against modern dieselelectric submarines, LFATS has demonstrated consistent detection performance in shallow and deep water. LFATS also provides a passive mode and includes a full set of passive tools and features.COMPACT SIZELFATS is a small, lightweight, air-transportable, ruggedized system designed specifically for easy installation on small vessels. CONFIGURABLELFATS can operate in a stand-alone configuration or be easily integrated into the ship’s combat system.TACTICAL BISTATIC AND MULTISTATIC CAPABILITYA robust infrastructure permits interoperability with the HELRAS helicopter dipping sonar and all key sonobuoys.HIGHLY MANEUVERABLEOwn-ship noise reduction processing algorithms, coupled with compact twin line receivers, enable short-scope towing for efficient maneuvering, fast deployment and unencumbered operation in shallow water.COMPACT WINCH AND HANDLING SYSTEMAn ultrastable structure assures safe, reliable operation in heavy seas and permits manual or console-controlled deployment, retrieval and depth-keeping. FULL 360° COVERAGEA dual parallel array configuration and advanced signal processing achieve instantaneous, unambiguous left/right target discrimination.SPACE-SAVING TRANSMITTERTOW-BODY CONFIGURATIONInnovative technology achievesomnidirectional, large aperture acousticperformance in a compact, sleek tow-body assembly.REVERBERATION SUPRESSIONThe unique transmitter design enablesforward, aft, port and starboarddirectional transmission. This capabilitydiverts energy concentration away fromshorelines and landmasses, minimizingreverb and optimizing target detection.SONAR PERFORMANCE PREDICTIONA key ingredient to mission planning,LFATS computes and displays systemdetection capability based on modeled ormeasured environmental data.Key Features>Wide-area search>Target detection, localization andclassification>T racking and attack>Embedded trainingSonar Processing>Active processing: State-of-the-art signal processing offers acomprehensive range of single- andmulti-pulse, FM and CW processingfor detection and tracking. Targetdetection, localization andclassification>P assive processing: LFATS featuresfull 100-to-2,000 Hz continuouswideband coverage. Broadband,DEMON and narrowband analyzers,torpedo alert and extendedtracking functions constitute asuite of passive tools to track andanalyze targets.>Playback mode: Playback isseamlessly integrated intopassive and active operation,enabling postanalysis of pre-recorded mission data and is a keycomponent to operator training.>Built-in test: Power-up, continuousbackground and operator-initiatedtest modes combine to boostsystem availability and accelerateoperational readiness.UNIQUE EXTENSION/RETRACTIONMECHANISM TRANSFORMS COMPACTTOW-BODY CONFIGURATION TO ALARGE-APERTURE MULTIDIRECTIONALTRANSMITTERDISPLAYS AND OPERATOR INTERFACES>State-of-the-art workstation-based operator machineinterface: Trackball, point-and-click control, pull-down menu function and parameter selection allows easy access to key information. >Displays: A strategic balance of multifunction displays,built on a modern OpenGL framework, offer flexible search, classification and geographic formats. Ground-stabilized, high-resolution color monitors capture details in the real-time processed sonar data. > B uilt-in operator aids: To simplify operation, LFATS provides recommended mode/parameter settings, automated range-of-day estimation and data history recall. >COTS hardware: LFATS incorporates a modular, expandable open architecture to accommodate future technology.L3Harrissellsht_LFATS© 2022 L3Harris Technologies, Inc. | 09/2022NON-EXPORT CONTROLLED - These item(s)/data have been reviewed in accordance with the InternationalTraffic in Arms Regulations (ITAR), 22 CFR part 120.33, and the Export Administration Regulations (EAR), 15 CFR 734(3)(b)(3), and may be released without export restrictions.L3Harris Technologies is an agile global aerospace and defense technology innovator, delivering end-to-endsolutions that meet customers’ mission-critical needs. The company provides advanced defense and commercial technologies across air, land, sea, space and cyber domains.t 818 367 0111 | f 818 364 2491 *******************WINCH AND HANDLINGSYSTEMSHIP ELECTRONICSTOWED SUBSYSTEMSONAR OPERATORCONSOLETRANSMIT POWERAMPLIFIER 1025 W. NASA Boulevard Melbourne, FL 32919SPECIFICATIONSOperating Modes Active, passive, test, playback, multi-staticSource Level 219 dB Omnidirectional, 222 dB Sector Steered Projector Elements 16 in 4 stavesTransmission Omnidirectional or by sector Operating Depth 15-to-300 m Survival Speed 30 knotsSize Winch & Handling Subsystem:180 in. x 138 in. x 84 in.(4.5 m x 3.5 m x 2.2 m)Sonar Operator Console:60 in. x 26 in. x 68 in.(1.52 m x 0.66 m x 1.73 m)Transmit Power Amplifier:42 in. x 28 in. x 68 in.(1.07 m x 0.71 m x 1.73 m)Weight Winch & Handling: 3,954 kg (8,717 lb.)Towed Subsystem: 678 kg (1,495 lb.)Ship Electronics: 928 kg (2,045 lb.)Platforms Frigates, corvettes, small patrol boats Receive ArrayConfiguration: Twin-lineNumber of channels: 48 per lineLength: 26.5 m (86.9 ft.)Array directivity: >18 dB @ 1,380 HzLFATS PROCESSINGActiveActive Band 1,200-to-1,00 HzProcessing CW, FM, wavetrain, multi-pulse matched filtering Pulse Lengths Range-dependent, .039 to 10 sec. max.FM Bandwidth 50, 100 and 300 HzTracking 20 auto and operator-initiated Displays PPI, bearing range, Doppler range, FM A-scan, geographic overlayRange Scale5, 10, 20, 40, and 80 kyd PassivePassive Band Continuous 100-to-2,000 HzProcessing Broadband, narrowband, ALI, DEMON and tracking Displays BTR, BFI, NALI, DEMON and LOFAR Tracking 20 auto and operator-initiatedCommonOwn-ship noise reduction, doppler nullification, directional audio。
IGLOO2 FPGAs商品说明书

IGLOO®2 FPGAsThe Industry’s Lowest-Power FPGAs/FPGA2IGLOO ®2 FPGAsIGLOO ®2 FPGAs Offer More Resources in Low-Density Devices With the Lowest Power, Proven Security and Exceptional ReliabilityIGLOO2 FPGAs are ideal for general-purpose functions such as Gigabit Ethernet or dual-PCI Express control planes, bridgingfunctions, (I/O) expansion and conversion, video/image processing, system management and secure connectivity. FPGAs are used in communications, industrial, medical, defense and aviation markets.IGLOO2 FeaturesMore Resources in Low-Density Devices• PCIe ® Gen 2 support in 10K LE• High-performance memory subsystem • Highest I/O densityWith Clear Advantages• Lowest power• Reduces total power by up to 50% • 70 mW per 5G SERDES (PCIe Gen 2) • Proven security• Protection from overbuilding and cloning • Secure boot for FPGA and processors • Exceptional reliability• SEU immune zero FIT Flash FPGA configuration •Reliable safety-critical and mission-critical systemsIGLOO2 FPGA ArchitectureIGLOO2 FPGAs offer 5K–150K LEs with a high-performance memory subsystem, up to 512 KB embedded Flash, 2 × 32 KB embedded SRAM, two Direct Memory Access (DMA) engines and two Double Data Rate (DDR) memory controllers. Architecture highlights include:• Up to 16× transceiver lanes • PCIe Gen 2, XAUI/XGXS+, generic ePCS mode at 3.2G • Up to 150K LEs, 5 Mbits SRAM, 4 Mbits eNVM• Hard 667 Mbps DDR2/3 controllers• Integrated DSP processing blocks• Power as low as 7 mW standby, typical• DPA-hardened, AES256, SHA256, on-demand NVM dataintegrity check • SEU-protected/tolerant memories: eSRAMs, DDR bridgesPCI ExpressDDR3 ControllerSecure FlashIGLOO2 FPGAs3PCIe 1G Control Plane• PCIe Gen 2 in 10K LE devices With I/O expansionMulti-Axis Motor Control• Deterministic and secure multi-axis/high-RPM solutions • Motor control IP and development kitAudio Processing, Storage, and Retrieval• I 2S-to-SPI bridge allows multiple audio recordings and playbacks/FPGA4Bridging and Co-Processing• SERDES to bridge CPRI, ADC/DACSecure Connectivity• Best-in-class security data communications and anti-tamper • Ultra-low static power for portabilityBoard Initialization• PMBus, instant-onIGLOO2 FPGAs5IGLOO2 FPGA FeaturesHigh-Performance Memory Subsystem• 64 KB embedded SRAM (eSRAM)• Up to 512 KB embedded nonvola -tile memory (eNVM)• One SPI/COMM_BLK• DDR bridge (2 port) with 64-bit AXI interface• Non-blocking, multi-layer AHB bus matrix allowing multi-master scheme supporting 4 masters and 8 slaves• Two AHB/APB interfaces to FPGA fabric (master/slave capable)• Two DMA controllers to offload data transactions• 8-channel peripheral DMA (PDMA) for data transfer between softperipherals in fabric and embedded eSRAMs, as well as support for memory-to-memory transfers• eSRAM and external DDR memory for efficient data movement between embedded real-time memoriesIGLOO2 FPGA SERDES• Up to 16 lanes at up to 5 Gbps • Dual-based reference clocks with single-lane rate granularity• Tx and Rx PLLs programmable for each lane• Reference clock is shared by groups of two lanes• Transmitter features• Programmable pre/post-emphasis • Programmable impedance • Programmable amplitude• Receiver features • Programmable termination• Programmable linear equalization• Built-in system debug features• PRBS gen/chk • Constant patterns • LoopbacksIGLOO2 FPGA Math Block• High-performance and power-optimized multiplication operations • Supports 18 × 18-signed multiplica -tion (natively)• Supports 17×17 unsigned multiplication• Supports dot product: the multi-plier computes (A[8:0] × B[17:9] + A[17:9] × B[8:0]) × 29 independent third input C with data width 44-bits completely registered• Supports both registered and unregistered inputs and outputs• Internal cascade signals(44-bit CDIN and CDOUT)enable cascading of the Math Blocks to supportlarger accumulator, adder,and subtractor withoutextra logic • Supports loopback capability• Adder support: (A×B) + C or (A×B) +D or (A×B) + C + D • Clock-gated inputand output registers for poweroptimizationsSUBA [17:0]B [17:0]C [43:0]CARRYIN ARSHFT17CDSELFDBKSELIGLOO2 FPGA Logic Element• A fully permutable 4-input LUT • A dedicated carry chain based on the carry look-ahead technique• A separate flip-flop that can be used independently from the LUT • Clock-gated input and output registers for power optimizationsA B C D CINLUT_BYPENSYNC_SRCLK RSTCO LORO/FPGA6Design ResourcesLibero ® SoC Design SoftwareLibero SoC Design Suite offers high productivity with its comprehensive, easy-to-learn, easy-to-adopt development tools that are used for designing with Microchip’s power-efficient Flash-based IGLOO2 devices. The suite integrates industry-standard Synopsys Synplify Pro synthesis and Mentor Graphics ModelSim simulation with best-in-class constraints management, debug capabilities, timing analysis, power analysis, secure production programming and push button design flow.This comprehensive suite features an intuitive design flow with GUI wizards to guide the design process. Its easy-to-adopt single-click synthesis to programming flow integrates industry-standard third-party tools, a rich IP library of DirectCores and Companion -Cores and supports complete reference designs and development kits.https:///product-directory/design-resources/1750-libero-socIGLOO2 Evaluation Kit• Gives designers access to IGLOO2 FPGAs that offer leadership in I/O density, security, reliability and low power for mainstream applications • Supports industry-standard interfaces including Gigabit Ethernet, USB 2.0 OTG, SPI, I 2C and UART• Can be powered by a 12V power supply or the PCIe connector and includes a FlashPro4 programmerBoard features• IGLOO2 FPGA in the FGG484 package (M2GL010T -1FGG484)• JTAG/SPI programming interface• Gigabit Ethernet PHY and RJ45 connector • USB 2.0 OTG interface connector • 1 GB LPDDR, 64 MB SPI Flash • Headers for I 2C, UART, SPI, GPIOs • ×1 Gen2 PCIe edge connector •Tx/Rx/Clk SMP pairs/existing-parts/parts/143976Intellectual PropertyMicrochip enhances your design productivity by providing an extensive suite of proven and optimized IP cores for use with FPGAs. Our extensive suite of IP cores covers all key markets and applications. Our cores are organized as either Microchip-developed DirectCores or third-party-developed CompanionCores. Most DirectCores are available for free within our Libero tool suite and include common communications interfaces, peripherals, and processing elements.Below are a few key DirectCores and CompanionCores. Click the below link for more details on IP Cores./product-directory/design-resources/5092-ip-coresIGLOO2 FPGA Product Family*Feature availablility is package dependent.Highlighted devices can migrate vertically in the same packageIGLOO2 FPGAs7SupportMicrochip is committed to supporting its customers in de-veloping products faster and more efficiently. We maintain a worldwide network of field applications engineers and technical support ready to provide product and system assistance. For more information, please visit :• Technical Support: /support • Evaluation samples of any Microchip device: /sample • Knowledge base and peer help: /forums• Sales and Global Distribution: /salesTrainingIf additional training interests you, Microchip offers several resources including in-depth technical training and reference material, self-paced tutorials and significant online resources.• Overview of Technical Training Resources: /training • MASTERs Conferences: /masters • Developer Help Website:/developerhelp • Technical Training Centers: /seminarsMicrochip Technology Inc. | 2355 W. Chandler Blvd. | Chandler AZ, 85224-6199Sales Office ListingAMERICASAtlanta, GATel: 678-957-9614Austin, TXTel: 512-257-3370Boston, MATel: 774-760-0087Chandler, AZ (HQ) Tel: 480-792-7200Chicago, ILTel: 630-285-0071Dallas, TXTel: 972-818-7423Detroit, MITel: 248-848-4000Houston, TXTel: 281-894-5983Indianapolis, IN Tel: 317-773-8323 Tel: 317-536-2380Los Angeles, CA Tel: 949-462-9523 Tel: 951-273-7800Raleigh, NCTel: 919-844-7510New York, NY Tel: 631-435-6000San Jose, CA Tel: 408-735-9110 Tel: 408-436-4270Canada - Toronto Tel: 905-695-1980EUROPEAustria - WelsTel: 43-7242-2244-39Denmark - Copenhagen Tel: 45-4450-2828Finland - Espoo Tel: 358-9-4520-820France - ParisTel: 33-1-69-53-63-20Germany - Garching Tel: 49-8931-9700Germany - HaanTel: 49-2129-3766-400Germany - Heilbronn Tel: 49-7131-67-3636Germany - Karlsruhe Tel: 49-721-62537-0Germany - Munich Tel: 49-89-627-144-0Germany - Rosenheim Tel: 49-8031-354-560EUROPEIsrael - Ra’anana Tel: 972-9-744-7705Italy - MilanTel: 39-0331-742611Italy - PadovaTel: 39-049-7625286Netherlands - Drunen Tel: 31-416-690399Norway - Trondheim Tel: 47-7289-7561Poland - Warsaw Tel: 48-22-3325737Romania - Bucharest Tel: 40-21-407-87-50Spain - MadridTel: 34-91-708-08-90Sweden - Gothenberg Tel: 46-31-704-60-40Sweden - Stockholm Tel: 46-8-5090-4654UK - Wokingham Tel: 44-118-921-5800ASIA/PACIFICAustralia - Sydney Tel: 61-2-9868-6733China - BeijingTel: 86-10-8569-7000China - Chengdu Tel: 86-28-8665-5511China - Chongqing Tel: 86-23-8980-9588China - Dongguan Tel: 86-769-8702-9880China - Guangzhou Tel: 86-20-8755-8029China - Hangzhou Tel: 86-571-8792-8115China - Hong Kong SAR Tel: 852-2943-5100China - NanjingTel: 86-25-8473-2460China - QingdaoTel: 86-532-8502-7355China - Shanghai Tel: 86-21-3326-8000China - Shenyang Tel: 86-24-2334-2829China - Shenzhen Tel: 86-755-8864-2200China - SuzhouTel: 86-186-6233-1526China - WuhanTel: 86-27-5980-5300China - Xiamen Tel: 86-592-2388138China - XianTel: 86-29-8833-7252ASIA/PACIFICChina - ZhuhaiTel: 86-756-321-0040India - Bangalore Tel: 91-80-3090-4444India - New Delhi Tel: 91-11-4160-8631India - PuneTel: 91-20-4121-0141Japan - Osaka Tel: 81-6-6152-7160Japan - TokyoTel: 81-3-6880-3770Korea - Daegu Tel: 82-53-744-4301Korea - Seoul Tel: 82-2-554-7200Malaysia - Kuala Lumpur Tel: 60-3-7651-7906Malaysia - Penang Tel: 60-4-227-8870Philippines - Manila Tel: 63-2-634-9065SingaporeTel: 65-6334-8870Taiwan - Hsin Chu Tel: 886-3-577-8366Taiwan - Kaohsiung Tel: 886-7-213-7830Taiwan - TaipeiTel: 886-2-2508-8600Thailand - Bangkok Tel: 66-2-694-1351Vietnam - Ho Chi Minh Tel: 84-28-5448-21005/15/19The Microchip name and logo, the Microchip logo, IGLOO and Libero are registered trademarks of Microchip Technology Incorporated in the U.S.A. and other countries. All other trademarks mentioned herein are property of their respective companies.© 2019, Microchip Technology Incorporated. All Rights Reserved. 11/19 DS00003294A。
毛驴AWK-1137C系列工业无线客户端说明书

AWK-1137C SeriesIndustrial802.11a/b/g/n wireless clientFeatures and Benefits•IEEE802.11a/b/g/n compliant client•Comprehensive interfaces with one serial port and two Ethernet LAN ports•Millisecond-level Client-based Turbo Roaming1•2x2MIMO future-proof technology•Integrated robust antenna and power isolation•Anti-vibration design•Compact size for your industrial applications•Easy setup and deployment with AeroMagCertificationsIntroductionThe AWK-1137C is an ideal client solution for industrial wireless mobile applications.It enables WLAN connections for both Ethernet and serial devices,and is compliant with industrial standards and approvals covering operating temperature,power input voltage,surge,ESD,and vibration. The AWK-1137C can operate on either the2.4or5GHz bands,and is backwards-compatible with existing802.11a/b/g deployments to future-proof your wireless investments.Industrial Ruggedness•Integrated antenna and power isolation designed to provide500V insulation protection against external electrical interference•-40to75°C wide operating temperature models(-T)available for smooth wireless communication in harsh environmentsMobility-Oriented Design•Client-based Turbo Roaming1for<150ms roaming recovery time between APs•MIMO technology to ensure transmitting and receiving capability while on the move•Anti-vibration performance(with reference to IEC60068-2-6)Easy Integration•Semi-automatically configurable to reduce deployment cost•AeroMag support for error-free setup of your industrial applications’basic WLAN settings•Various communication interfaces for connecting to different types of devices•One-to-many NAT to simplify your machine setupSpecificationsWLAN InterfaceWLAN Standards802.11a/b/g/n802.11i Wireless SecurityModulation Type DSSSMIMO-OFDMOFDMFrequency Band for US(20MHz operating channels) 2.412to2.462GHz(11channels)5.180to5.240GHz(4channels)5.260to5.320GHz(4channels)21.The Turbo Roaming recovery time indicated herein is an average of test results documented,in optimized conditions,across APs configured with interference-free20-MHz RF channels,WPA2-PSK security,and default Turbo Roaming parameters.The clients are configured with3-channel roaming at100Kbps traffic load.Other conditions may also impact roaming performance.For more information about Turbo Roaming parameter settings,refer to the product manual.5.500to5.700GHz(11channels)35.745to5.825GHz(5channels)Frequency Band for EU(20MHz operating channels) 2.412to2.472GHz(13channels)5.180to5.240GHz(4channels)5.260to5.320GHz(4channels)35.500to5.700GHz(11channels)3Frequency Band for JP(20MHz operating channels) 2.412to2.484GHz(14channels)5.180to5.240GHz(4channels)5.260to5.320GHz(4channels)35.500to5.700GHz(11channels)3Wireless Security WEP encryption(64-bit and128-bit)WPA/WPA2-Enterprise(IEEE802.1X/RADIUS,TKIP,AES)WPA/WPA2-PersonalTransmission Rate802.11b:1to11Mbps802.11a/g:6to54Mbps802.11n:6.5to300MbpsTransmitter Power for802.11a23±1.5dBm@6to24Mbps21±1.5dBm@36Mbps20±1.5dBm@48Mbps18±1.5dBm@54MbpsTransmitter Power for802.11b26±1.5dBm@1Mbps26±1.5dBm@2Mbps26±1.5dBm@5.5Mbps25±1.5dBm@11MbpsTransmitter Power for802.11g23±1.5dBm@6to24Mbps22±1.5dBm@36Mbps20±1.5dBm@48Mbps19±1.5dBm@54MbpsTransmitter Power for802.11n(2.4GHz)23±1.5dBm@MCS0/820MHz17±1.5dBm@MCS7/1520MHz23±1.5dBm@MCS0/840MHz17±1.5dBm@MCS7/1540MHzTransmitter Power for802.11n(5GHz)23±1.5dBm@MCS0/820MHz18±1.5dBm@MCS7/1520MHz23±1.5dBm@MCS0/840MHz18±1.5dBm@MCS7/1540MHzTransmitter Power2.4GHz26dBm18dBm18dBm5GHz(UNII-1)23dBm23dBm23dBm5GHz(UNII-2)23dBm23dBm23dBm5GHz(UNII-2e)23dBm23dBm23dBm5GHz(UNII-3)23dBm––Note:Based on regional regulations,the maximum transmission power allowed onthe UNII bands is restricted in the firmware,as indicated above.Receiver Sensitivity for802.11a-90dBm@6Mbps-88dBm@9Mbps-87dBm@12Mbps-85dBm@18Mbps-81dBm@24Mbps-78dBm@36Mbps-74dBm@48Mbps-73dBm@54MbpsReceiver Sensitivity for802.11b-89dBm@1Mbps-89dBm@2Mbps-89dBm@5.5Mbps-88dBm@11MbpsReceiver Sensitivity for802.11g-88dBm@6Mbps-88dBm@9Mbps-88dBm@12Mbps-87dBm@18Mbps-84dBm@24Mbps-81dBm@36Mbps-77dBm@48Mbps-75dBm@54MbpsReceiver Sensitivity for802.11n(2.4GHz)-70dBm@MCS720MHz-70dBm@MCS1520MHz-64dBm@MCS740MHz-65dBm@MCS1540MHzReceiver Sensitivity for802.11n(5GHz)-69dBm@MCS720MHz-70dBm@MCS1520MHz-64dBm@MCS740MHz-66dBm@MCS1540MHzWLAN Operation Mode Client,Client-Router,Slave,SnifferAntenna External,2/2dBi,Omni-directional,2RP-SMA maleAntenna Connectors2RP-SMA femaleEthernet Interface10/100BaseT(X)Ports(RJ45connector)2Standards IEEE802.1Q for VLAN TaggingIEEE802.3for10BaseTIEEE802.3u for100BaseT(X)Ethernet Software FeaturesManagement DHCP Server/Client,HTTP,IPv4,LLDP,SMTP,SNMPv1/v2c/v3,Syslog,TCP/IP,Telnet,UDP,Proxy ARP,Wireless Search Utility,VLAN,MXview,MXconfigSecurity HTTPS/SSL,RADIUS,SSHTime Management NTP Client,SNTP ClientFirewallFilter ICMP,MAC address,IP protocol,Port-basedSerial InterfaceConnector DB9maleSerial Standards RS-232,RS-422/485,RS-232/422/485Operation Modes Disabled,Real COM,RFC2217,TCP Client,TCP Server,UDPData Bits5,6,7,8Stop Bits1,1.5,2Parity None,Even,Odd,Space,MarkFlow Control None,RTS/CTS,XON/XOFFBaudrate75bps to921.6kbpsSerial Data Log256KBSerial SignalsRS-232TxD,RxD,RTS,CTS,DCD,GND,DTR,DSRRS-422Tx+,Tx-,Rx+,Rx-,GNDRS-485-2w Data+,Data-,GNDRS-485-4w Tx+,Tx-,Rx+,Rx-,GNDLED InterfaceLED Indicators SYS,LAN1,LAN2,WLAN,SerialInput/Output InterfaceButtons Reset buttonPhysical CharacteristicsHousing MetalIP Rating IP30Dimensions77.1x115.5x26mm(3.035x4.55x1.024in)Weight470g(1.03lb)Installation DIN-rail mounting,Wall mounting(with optional kit)Power ParametersInput Voltage9to30VDCPower Connector1removable3-contact terminal block(s)Power Consumption11.7W(max.)Reverse Polarity Protection SupportedEnvironmental LimitsOperating Temperature Standard Models:0to60°C(32to140°F)Wide Temp.Models:-40to75°C(-40to167°F)Storage Temperature(package included)-40to85°C(-40to185°F)Ambient Relative Humidity5to95%(non-condensing)Standards and CertificationsEMC EN61000-6-2/-6-4,EN55032/24EMI CISPR22,FCC Part15B Class AEMS IEC61000-4-2ESD:Contact:8kV;Air:15kVIEC61000-4-3RS:80MHz to1GHz:10V/mIEC61000-4-4EFT:Power:2kV;Signal:1kVIEC61000-4-5Surge:Power:2kV;Signal:1kVIEC61000-4-6CS:10VIEC61000-4-8PFMFRadio ANATEL,EN300328,EN301489-1/17,EN301893,FCC ID SLE-1137C,MIC,NCC,SRRC,WPC,KC,RCMSafety EN60950-1,UL60950-1Vibration IEC60068-2-6MTBFTime1,125,942hrsStandards Telcordia SR332WarrantyWarranty Period5yearsDetails See /warranty Package ContentsDevice1x AWK-1137C Series wireless client Antenna2x2.4/5GHz antennaInstallation Kit1x DIN-rail kitDocumentation1x quick installation guide1x warranty card DimensionsOrdering InformationAWK-1137C-EU EU802.11a/b/g/n0to60°C AWK-1137C-EU-T EU802.11a/b/g/n-40to75°C AWK-1137C-JP JP802.11a/b/g/n0to60°C AWK-1137C-JP-T JP802.11a/b/g/n-40to75°C AWK-1137C-US US802.11a/b/g/n0to60°C AWK-1137C-US-T US802.11a/b/g/n-40to75°C Accessories(sold separately)AntennasANT-WDB-ANF-0407 2.4/5GHz,omni-directional antenna,4/7dBi,N-type(male)ANT-WDB-ANF-0609 2.4/5GHz,omni-directional antenna,6/9dBi,N-type(female)ANT-WDB-ANM-0306 2.4/5GHz,omni-directional antenna,3/6dBi,N-type(male)ANT-WDB-ANM-0407 2.4/5GHz,dual-band omni-directional antenna,4/7dBi,N-type(male)ANT-WDB-ANM-0502 2.4/5GHz,omni-directional antenna,5/2dBi,N-type(male)ANT-WDB-ANM-0609 2.4/5GHz,omni-directional antenna,6/9dBi,N-type(male)ANT-WDB-ARM-02 2.4/5GHz,omni-directional rubber duck antenna,2dBi,RP-SMA(male)ANT-WDB-ARM-0202 2.4/5GHz,panel antenna,2/2dBi,RP-SMA(male)ANT-WDB-PNF-1518 2.4/5GHz,panel antenna,15/18dBi,N-type(female)MAT-WDB-CA-RM-2-0205 2.4/5GHz,ceiling antenna,2/5dBi,MIMO2x2,RP-SMA-type(male)MAT-WDB-DA-RM-2-0203-1m 2.4/5GHz,desktop antenna,2/3dBi,MIMO2x2,RP-SMA-type(male),1m cableMAT-WDB-PA-NF-2-0708 2.4/5GHz,panel antenna,7/8dBi,MIMO2x2,N-type(female)ANT-WSB5-ANF-125GHz,omni-directional antenna,12dBi,N-type(female)ANT-WSB5-PNF-185GHz,directional panel antenna,18dBi,N-type(female)ANT-WSB-ANF-09 2.4GHz,omni-directional antenna,9dBi,N-type(female)ANT-WSB-PNF-12 2.4GHz,directional panel antenna,12dBi,N-type(female)ANT-WSB-PNF-18 2.4GHz,directional panel antenna,18dBi,N-type(female)ANT-WSB-AHRM-05-1.5m 2.4GHz,omni-directional/dipole antenna,5dBi,RP-SMA(male),1.5m cableWireless AdaptorsA-ADP-RJ458P-DB9F-ABC01DB9female to RJ45connector for the ABC-01Wireless Antenna CableA-CRF-RFRM-R4-150RF magnetic stand,RP-SMA(male)to RP-SMA(female),RG-174/U cable,1.5mA-CRF-RFRM-S2-60SS402cable,RP-SMA(male)to RP-SMA(female)A-CRF-RMNM-L1-300N-type(male)to RP SMA(male),LMR-195Lite cable,3mA-CRF-RMNM-L1-600N-type(male)to RP SMA(male),LMR-195Lite cable,6mA-CRF-RMNM-L1-900N-type(male)to RP SMA(male),LMR-195Lite cable,9mCRF-N0117SA-3M N-type(male)to RP SMA(male),CFD200cable,3mSurge ArrestorA-SA-NFNF-01Surge arrestor,N-type(female)to N-type(female)Wireless Terminating ResistorA-TRM-50-RM Termination resistor,50ohms,N-type maleWall-Mounting KitsWK-35-01Wall-mounting kit,2plates,6screws,35x44x2.5mm©Moxa Inc.All rights reserved.Updated Apr30,2019.This document and any portion thereof may not be reproduced or used in any manner whatsoever without the express written permission of Moxa Inc.Product specifications subject to change without notice.Visit our website for the most up-to-date product information.。
网络信息安全英语练习题

网络信息安全英语练习题网络信息安全是现代社会中一个非常重要的议题,它涉及到保护数据不被未授权访问、修改、破坏或泄露。
以下是一些英语练习题,旨在帮助学生更好地理解和掌握网络信息安全的相关概念。
1. Multiple Choice Questions (选择题)Choose the correct answer from the options provided.a) What does "cybersecurity" refer to?- A) The study of cybernetics- B) The practice of protecting information systems from theft or damage- C) The design of computer networks- D) The creation of cyberspaceb) Which of the following is a common method used by hackers to gain unauthorized access to a system?- A) Social engineering- B) Social networking- C) Social media marketing- D) Social sciencec) What is a "firewall"?- A) A physical barrier to prevent fire from spreading- B) A software or hardware that monitors and controlsincoming and outgoing network traffic- C) A type of antivirus software- D) A network protocold) What is the purpose of "encryption" in cybersecurity?- A) To make data unreadable to unauthorized users- B) To increase the speed of data transmission- C) To reduce the size of data files- D) To improve the quality of network connections2. Fill in the Blanks (填空题)Fill in the blanks with the appropriate words from the list provided.- breach, protocol, phishing, malware, vulnerabilitya) A computer virus is a type of _______ that can cause damage to a system or steal information.b) An email that appears to be from a legitimate source butis actually designed to trick the recipient into revealing sensitive information is known as _______.c) A _______ is a set of rules governing the format and transmission of data over a network.d) A _______ in a system is a weakness that can be exploited by an attacker.e) A _______ of data security occurs when unauthorized accessis gained, often resulting in data loss or corruption.3. True or False (判断题)Determine whether the statements below are true or false.a) Two-factor authentication is a security measure that requires two different methods of verification to access a system. (True / False)b) Public Wi-Fi networks are always secure and safe to usefor online banking. (True / False)c) A strong password should include a mix of upper and lower case letters, numbers, and special characters. (True / False)d) It is not necessary to update software regularly because updates are only for new features. (True / False)e) VPNs (Virtual Private Networks) can provide an extra layer of security by encrypting internet traffic. (True / False)4. Short Answer Questions (简答题)Answer the following questions in a few sentences.a) What is the significance of using strong passwords?b) Explain the concept of "zero-day" vulnerabilities.c) How can users protect themselves from phishing attacks?d) What are some best practices for maintaining network security at home?e) Describe the role of a cybersecurity analyst.These exercises are designed to test and reinforce knowledge on various aspects of network information security. By practicing with these questions, students can enhance their understanding of the subject and be better prepared to tackle real-world cybersecurity challenges.。
SimpleWare软件系列介绍(简化版)说明书

Follow us:/simplewareWhy Simpleware Software?Simpleware TM software offers a fast, easy-to-use solution for processing medical image data into 3D models for pre-surgical planning and 3D printing. Use the software to generate watertight STLs for 3D printing applications. Get more from patient-specific images by combining image and CAD data for evaluating implant positions. Take advantage of tools for visualizing and measuring image data, as well as for exporting meshes suitable for FE/CFD simulation.Intuitive and Customizable We pride ourselves on the ease-of-use of Simpleware software. Users new to the software can start processing clinical images within a short time frame, and very quickly visualize and identify anatomical regions of interest. Our range of fully automated, semi-automated and interactive segmentation tools allow even the most challenging image datasets to be processed efficiently. The software also offers scripting tools and plug-ins for users to customize the software and automate repetitive tasks without compromising on accuracy.Dedicated Support and TrainingOur expert technical support team are here to help you get the most out of thesoftware, including step-by-step guidance and personalized support. We alsoregularly offer classroom training courses at our offices, or you can arrangecustomized training sessions online or at your site.Key Benefits• F DA 510(k) Cleared• I ntuitive, User-Friendly Interface• Q uick and Accurate Segmentation• A dvanced 3D Image Processing• D evelop Automated Workflows• E xpert Technical Support Key Features• I mport Clinical Images• C o-Register Image Data Sets• M ultiplanar Reconstruction (MPR)• I ntegrate CAD Implants with Scan Data• M easurements and Statistics• E xport to 3D Printing or 3D PDF©360 Knee SystemsImproving Patient Outcomes with 3D Surgical Planning Corin OPS™ (Optimized Positioning System), AustraliaCorin’s OPS™ technology enables surgeons to understand the individual motion profileof each patient before surgery. This gives surgeons the information required to identify, customize and deliver a personalized total hip replacement. The system provides the surgeon with an accurate laser-guided alignment system allowing the patient-specific implant orientation to be reliably achieved during surgery. 3D printed guides are created to enable the surgeon to achieve these positions as planned. Thanks to Simpleware software, the guides fit accurately to the patient’s individual geometry, giving the surgeon confidence that the planned implant position will be achieved intraoperatively.Patient-Specific Knee Guide DevelopmentW. Theodore, 360 Knee Systems, Australia360 Knee Systems develops a system for customized preoperative plans and guides for optimal placement of knee implants. 3D models generated in Simpleware ScanIP are used to create patient-specific guides for surgeons. Each guide is tailored to the specific bone geometry of a patient, and is designed to help make appropriate cuts for surgery. 360 Knee Systems use these models to provide preoperative plans of the optimal placement of knee implants and the patient’s bone geometry that surgeons can familiarize themselves with prior to surgery. 3D printed guides provide accurate cutting positions for the patella, femur and tibia components of the implant for each patient.Production of High-Fidelity Patient-Specific 3D ModelsB. Chanin, Mediprint, USAMediprint offer 3D reconstruction and printing services to produce patient-specific anatomical replicas, with a focus on accuracy and efficiency for different uses. In orderto equip their certified and registered radiological technologists with an FDA compliant tool, they turned to Simpleware ScanIP for producing high-fidelity 3D models. Colorfullife-sized models give surgeons a hands-on feel for the scale and scope of their procedure before entering the operating room. Being able to hold the pathology, turn it in their hands to inspect, and discuss it with their peers reflects a paradigm shift in the way medical imaging is implemented in the approach to surgery.3D Printed Model used for Kidney Stone Removal SurgeryJ. Cousins, isodo3D, UKThe potential of 3D printing to aid pre-surgical planning has been shown in this example of a kidney operation. Entrepreneur John Cousins used the opportunity of his kidney stone removal operation to create a 3D model from the CT scan of the kidney stone. Cousins used Simpleware ScanIP to segment the kidney and stone prior to 3D printinga physical replica. Surgeons at Southampton General Hospital were able to use the printed model as an additional reference during the procedure. The successful operation shows the potential of improving pre-surgical planning through working with an accuratereference model.THR templating based on3D imaging3D printedsurgical guides3D printed model of the kidney (green, red and yellow parts) with a ‘stag head’ kidney stone (blue)Preoperative planning of knee implants anddevelopment of placement guide3D printed replica of a klatskin tumor provided surgeons with the scale and scope before surgery。
日式品牌的电子静电模拟仪器产品说明书

1w w w.n o i s e k e n.c o mThe electrostatic simulator you always use is renewed now. The new main unit and discharge gun in sale now are `ESS-S3011A`, ` ESS-B3011A` and `GT-30RA`.For repair maintenance in our company, we discontinue repair support 8 years after delivery according to warranty and 5 years after sales termination. For those electrostatic simulators whose repair support is terminated, we may decline to repair. For discharge gun 'TC-815 series', as there are many discontinued parts, it is difficult to continue to support it. We plan to terminate the repair support as the following schedule.ESD SimulatorESS-S3011A & GT-30RASmart model equipped high function & extendibilityInformation on successive model (current model)Repair support termination schedule:discharge gunModelRepair service and support statussuccessive modelTC-815C terminated GT-30RA TC-815D terminated GT-30RA TC-815D(F)terminated GT-30RA TC-815P terminated GT-30RA TC-815R terminatedGT-30RA TC-815RE22020年(scheduled)GT-30RA TC-815S2020年(scheduled)GT-30RA TC-815-330/2K2020年(scheduled)GT-30R3302KA※Old standard:IEC61000-4-2 Ed1 compliant (new standard incompliant)Repair support termination schedule noticeModelRepair service and support status successive modelESS-630 series terminated ESS-B3011A ESS-200AX terminated ESS-S3011A ESS-100L terminated ESS-B3011A ESS-100LA terminated ESS-B3011A ESS-2000terminated ESS-S3011A ESS-2002terminated ESS-B3011A ESS-2000AX terminated ESS-S3011A ESS-2002EXterminatedESS-B3011AFor the customers who above have electrostatic simulators and discharge gun, please consider to buy the successive model(current model) as replacement.ESS-630A ESS-200AX ESS-100L ESS-2000ESS-2002ESS-2000AX/2002EXEMC test equipment to evaluate the resistibility of electronic equipments when en-ergy charged on a human body or object is discharged to the electronic equipment.This can be available for evaluating malfunctions or functions declines of electronic equipment against the ESD.Programmable simulator to ease some complicated tests. The output voltage is up to 30kV and performable IEC61000-4-2 & ISO 10605 Standardscompliant tests.●“3 pre-checking function” to make sure the more confirmable test ●“CR constant indicator” to make sure the correct unit attachment ●One-touch exchange of gun head and CR unit realized ●“Ten-key & Rotary knob” to ease the setting.●“Discharge Detecting Function” to realize the air-discharge confirmation.●“Lightest discharge gun in the market” to lighten the continuous operation (Excluding the cable and connector)●“White LED Irradiator” to facilitate the visualization of the discharging areas.●“ Control Software” to enable the test result reporting and control with PC.Provided by:Advanced Test Equipment Corp .® (800) 404-ATECRentals • Sales • Calibration • ServiceESD SimulatorESS-B3011A & GT-30RACost-oriented basic model ESD Simulator the light weight discharge gun attach-able.The output voltage can be selected either max. 30kV (B3011A) or max.16kV (L1611A) and compliant to both EN/IEC61000-4-2 Standard (both B3011A and L1611A) and ISO10605 Standard (only B3011A).Cost-oriented Basic modelsESS-S3011A & GT-30RAParameter Specification Polarity Positive / Negative Output voltage 0.20kV ~ 30.0kV±5% (30.5kVmax) ~10.0kV : 0.01kV step ~30.0kV : 0.1kV step Repetition cycle 0.05s ~ 600s±10% / Manual Set step : 0.01s (0.05 ~ 9.99s), 0.10s (10.0 ~ 600.0s)No. of time of discharge 1~60,000 times, Preset 1 time step or continuous preset Discharge mode Contact discharge / Air discharge Radiation level mode NORMAL mode / EXTRA mode Trigger mode Gun trigger / Main trigger / External trigger Operation panel Color LCD / Push-buttons (Partially lighting)Gun holder Standard attached (to hold the discharge gun Model GT-30RA)Radiation mode select switch Extra / Normal switching function built-inDischarge detection Discharge detection function in air-discharge equipped Pre-checking function Following 3 steps function equipped (by user operation. Not the calibration but just checking) SETP1 : High voltage output checking STEP2 : Withstanding voltage checking STEP3 : Discharge relay operation checking CR & Gun head checking CR constant and gun head recognizable (with an indicator to prevent the wrong combination)Parameter Specification"IEC STANDARD" Contact discharge mode : 2.0kV, 4.0kV, 6.0kV and 8.0kV step test mode Air discharge mode : 2.0kV, 4.0kV, 8.0kV and 15.0kV step "MANUAL" Contact / Air discharge mode, Arbitrary setting during 0.2kV~30.0kV test mode Sweeping function built-in, Recordable up to 99 units "SEQUENCE" Enables to operate units set in MANUAL mode continuously.test mode Max. 22 steps / 1 program and the programs recordable up to 20.Warning lamp Lighting at voltage output from the generator. Blinking at electro-static dischargingCharge capacitor / resistor 150pF±10%, 330Ω±10%(Built-in CR unit for discharge gun GT-30RA)Charge resistor in generator 10MΩ(Totally 53Ω in combination with 43MΩ in discharge gun)*AUX connector D-SUB 15pins female connector (for connecting to patolight, automated ESD eliminator, external interlock input, external trigger input terminal)Optical communication Optical connector (serial interface) for connecting to PC connector Power supply / consumption AC100V~AC240V 50Hz / 60Hz ±10% 75VA Dimension Generator : (W)392mm X (H)312mm X (D)295.3mm (including gun holder) Discharge gun : (W)83.3mm X (H)217.2mm X (D)229.3mm Mass Generator : Approx. 7.5kg Discharge gun : Approx. 800g (excluding cable and connector)* The constant depends on combination with CR unit for the discharge gun● “Pre-checking function” taking the confirmable test into the account ● “Discharge Detecting Function” to realize the air-discharge confirmation.● “Lightest Discharge Gun in the market” to lighten the continual operation"● “White LED Irradiator” to facilitate the visualization of the discharging area.● “CR constant checking function” (No indicator) to make the correct unit attachment sure"● One-touch exchange of gun head and CR unit realizedParameter Specification Output voltage 0.20kV~30.0kV±5%(30.5kVmax) ESS-L1611A is 16kVmax Polarity Positive / Negative Repetition cycle 0.05s~9.99s±10%, 0.01s step / ManualNo. of time of discharge 1~999 times, Preset 1 time step or continuous preset Discharge mode Contact discharge / Air discharge Trigger mode Gun trigger / Main trigger Operation panel Indicator : 5X7 Dot matrix LED / Operation : Push buttons Radiation mode select switch Extra / Normal switching function built-inDischarge detection Discharge detection function in air-discharge equipped.Pre-checking function High voltage output checking function (by user operation. Not the calibration but just checking)CR & Gun head CR constant and gun head recognizable checking (to prevent the wrong combination without indicator)IEC LEVELContact discharge mode : 2.0kV, 4.0kV, 6.0kV and 8.0kV step Switching function Air discharge mode : 2.0kV, 4.0kV, 8.0kV and 15.0kV step)Parameter SpecificationWarning lamp Lighting at voltage output from the generator. Blinking at electro-static discharging Charge capacitor / resistor 150pF±10%, 330Ω±10% (Built-in CR unit for discharge gun GT-30RA)Charge resistor in generator 10MΩ (Totally 53Ω in combination with 43MΩ in discharge gun)*Power supply / consumption AC100V~AC240V ±10% 50Hz / 60Hz 62VA Dimension Generator : (W)270 X (H)263 X (D)200mm Discharge gun : (W)83.3 X (H)217.2 X (D)229.3mm Mass Generator : Approx. 4.8kg Discharge gun : Approx. 800g (excluding cable and connector)* Remote control function not built-in.* The constant depends on combination with CR unit for the discharge gun。
Dell SonicWALL NSA系列下一代防火墙用户手册说明书

Organizations of all sizes depend on their networks to access internal and external mission-critical applications. As advances in networking continueto provide tremendous benefits, organizations are increasingly challenged by sophisticated and financially-motivated attacks designed to disrupt communication, degrade performance and compromise data. Malicious attacks penetrate outdated stateful packet inspection firewalls with advanced application layer exploits. Point products add layers of security, but are costly, difficult to manage, limited in controlling network misuse and ineffective against the latest multipronged attacks.By utilizing a unique multi-core design and patented Reassembly-Free Deep Packet Inspection® (RFDPI) technology*, the Dell™ SonicWALL™ Network Security Appliance (NSA) Series of Next-Generation Firewalls offers complete protection without compromising network performance. The low latency NSA Series overcomes the limitations of existing security solutions by scanning the entirety of each packet for current internal and external threats in real-time. The NSA Series offers intrusion prevention, malware protection, and application intelligence, control and visualization, while delivering breakthrough performance. With advanced routing, stateful high-availability and high-speed IPSec and SSL VPN technology, the NSA Series adds security, reliability, functionality and productivity to branch offices, central sites and distributed mid-enterprise networks, while minimizing cost and complexity.Comprised of the Dell SonicWALL NSA 220, NSA 220 Wireless-N, NSA 250M, NSA 250M Wireless-N, NSA 2400, NSA 3500 and NSA 4500, the NSA Series offers a scalable range of solutions designed to meet the network security needs of any organization.Network SecurityAppliance SeriesNext-Generation Firewall• Next-Generation Firewall• Scalable multi-core hardware andReassembly-Free Deep PacketInspection• Application intelligence, controland visualization• Stateful high availability and loadbalancing• High performance and loweredtco• Network productivity• Advanced routing services andnetworking• Standards-based Voice over IP(VoIP)• Dell Sonicwall clean Wireless• onboard Quality of Service (QoS)• Integrated modules support• Border Gateway Protocol (BGP)support• More concurrent SSL VPN sessionsFeatures and benefitsNext-Generation Firewall features integrate intrusion prevention, gateway anti-virus, anti-spyware and URL filtering with application intelligence and control, and SSL decryption to block threats from entering the network and provide granular application control without compromising performance.Scalable multi-core hardware and Reassembly-Free Deep Packet Inspection scans and eliminates threats of unlimited file sizes, with near-zero latency across thousands of connections at wire speed.Application intelligence, control and visualization provides granular control and real-time visualization of applications to guarantee bandwidth prioritization and ensure maximum network security and productivity. Stateful high availability and load balancing features maximize total network bandwidth and maintain seamless network uptime, delivering uninterrupted access to mission-critical resources, and ensuring that VPN tunnels and other network traffic will not be interrupted in the event of a failover. High performance and lowered tcoare achieved by using the processingpower of multiple cores in unison todramatically increase throughput andprovide simultaneous inspectioncapabilities, while lowering powerconsumption.Network productivity increases becauseIT can identify and throttle or blockunauthorized, unproductive andnon-work related applications and websites, such as Facebook® or YouTube®,and can optimize WAN traffic whenintegrated with Dell SonicWALL WANAcceleration Appliance (WXA) solutions.Advanced routing services andnetworking features incorporate 802.1qVLANs, multi-WAN failover, zone andobject-based management, loadbalancing, advanced NAT modes, andmore, providing granular configurationflexibility and comprehensive protectionat the administrator’s discretion.Standards-based Voice over IP (VoIP)capabilities provide the highest levels ofsecurity for every element of the VoIPinfrastructure, from communicationsequipment to VoIP-ready devices suchas SIP Proxies, H.323 Gatekeepers andCall Servers.Dell SonicWALL clean Wirelessoptionally integrated into dual-bandwireless models or via Dell SonicWALLSonicPoint wireless access pointsprovides powerful and secure 802.11a/b/g/n 3x3 MIMO wireless, and enablesscanning for rogue wireless accesspoints in compliance with PCI DSS.onboard Quality of Service (QoS)features use industry standard 802.1pand Differentiated Services Code Points(DSCP) Class of Service (CoS)designators to provide powerful andflexible bandwidth management that isvital for VoIP, multimedia content andbusiness-critical applications.Integrated modules support on NSA250M and NSA 250M Wireless-Nappliances reduce acquisition andmaintenance costs through equipmentconsolidation, and add deploymentflexibility.Border Gateway Protocol (BGP)support enables alternate networkaccess paths (ISPs) if one path fails.More concurrent SSL VPN sessions addscalability, while extending End PointControl to Microsoft® Windows® devicesensures anti-malware and firewalls areup-to-date.Best-in-class threat protection Dell SonicWALL deep packetinspection protects against network risks such as viruses, worms, Trojans, spyware, phishing attacks, emerging threats and Internet misuse. Application intelligence and control adds highly controls to prevent data leakage and manage bandwidth at the application level.The Dell SonicWALL Reassembly-Free Deep Packet Inspection (RFDPI) technology utilizes Dell SonicWALL’s multi-corearchitecture to scan packets in real-time without stalling traffic in memory.This functionality allows threats to be identified and eliminated over unlimited file sizes and unrestricted concurrent connections, without interruption.The Dell SonicWALL NSA Series provides dynamic network protection through continuous, automated security updates, protecting against emerging and evolving threats, without requiring any administrator intervention.Dynamic security architectureand managementMobile users32Application intelligence and control Dell SonicWALL Application Intelligence and Control provides granular control, data leakage prevention, and real-time visualization of applications to guarantee bandwidth prioritization and ensure maximum network security and productivity. An integrated feature of Dell SonicWALL Next-Generation Firewalls, it uses Dell SonicWALL RFDPItechnology to identify and control applications in use with easy-to-use pre-defined application categories (such as social media or gaming)—regardless of port or protocol. Dell SonicWALL Application Traffic Analytics provides real-time and indepth historical analysis of data transmitted through the firewall including application activities by user.1Dell SonicWALL clean VPNDell SonicWALL Clean VPN™ secures the integrity of VPN access for remote devices including those running iOS or Android by establishing trust for remote users and these endpoint devices and applying anti-malware security services, intrusion prevention and application intelligence and control to eliminate the transport of malicious threats• The SonicWALL NSA 2400 is ideal for branch office and small- to medium-sized corporate environments concerned about throughput capacity and performance • The SonicWALL NSA 220, NSA 220 Wireless-N, NSA 250M and NSA 250M Wireless-N are ideal for branch office sites in distributed enterprise, small- to medium-sizedbusinesses and retail environmentscentralized policy managementThe Network Security Appliance Series can be managed using the SonicWALL Global Management System, which provides flexible, powerful and intuitive tools to manage configurations, viewreal-time monitoring metrics andintegrate policy and compliancereporting and application traffic analytics,all from a central location.Server Anti-Virusand Anti-SpywareServers anti-threatprotectionVPNVPNClientRemoteAccessUpgradeServiceWeb siteand contentusage control Enforced ClientAnti-Virusand Anti-SpywareClient PCs anti-threat protectionFlexible, customizable deployment options –NSA Series at-a-glanceEvery SonicWALL Network Security Appliance solution delivers Next-Generation Firewall protection, utilizing a breakthrough multi-core hardware design and Reassembly-Free Deep Packet Inspection for internal and external network protection without compromising network performance. Each NSA Series product combineshigh-speed intrusion prevention, file and content inspection, and powerful application intelligence and controlwith an extensive array of advanced networking and flexible configuration features. The NSA Series offers an accessible, affordable platform that is easy to deploy and manage in a wide variety of corporate, branch office and distributed network environments.• The SonicWALL NSA 4500 is ideal for large distributed and corporate central-site environments requiring high throughput capacity and performance • The SonicWALL NSA 3500 is idealfor distributed, branch office and corporate environments needing significant throughput capacity and performanceSecurity services andupgradesGateway Anti-Virus,Anti-Spyware, IntrusionPrevention and ApplicationIntelligence and controlService delivers intelligent,real-time network security protectionagainst sophisticated application layerand content-based attacks includingviruses, spyware, worms, Trojans andsoftware vulnerabilities such as bufferoverflows. Application intelligence andcontrol delivers a suite of configurabletools designed to prevent data leakagewhile providing granular application-level controls along with tools enablingvisualization of network traffic.Enforced client Anti-Virusand Anti-spyware (McAfee)working in conjunction withDell SonicWALL firewalls,guarantees that allendpoints have the latest versions ofanti-virus and anti-spyware softwareinstalled and active.content Filtering Serviceenforces protection andproductivity policies byemploying an innovativerating architecture, utilizingadynamic database to block up to 56categories of objectionable webcontent.Analyzer is a flexible, easyto use web-basedapplication traffic analyticsand reporting tool thatprovides powerful real-time andhistorical insight into the health,performance and security of the network.Virtual Assist is a remotesupport tool that enablesa technician to assumecontrol of a PC or laptopfor the purpose of providingremote technical assistance. Withpermission, the technician can gaininstant access to a computer using aweb browser, making it easy to diagnoseand fix a problem remotely without theneed for a pre-installed “fat” client.Dynamic Support Servicesare available 8x5 or 24x7depending on customerneeds. Features includeworld-class technicalsupport, crucial firmware updates andupgrades, access to extensive electronictools and timely hardware replacementto help organizations get the greatestreturn on their Dell SonicWALLinvestment.Global VPN clientUpgrades utilize a softwareclient that is installed onWindows-based computersand increase workforce productivity byproviding secure access to email, files,intranets, and applications for remoteusers.provide clientlessLinux-based systems. With integratedSSL VPN technology, Dell SonicWALLfirewall appliances enable seamless andsecure remote access to email, files,intranets, and applications from a varietyof client platforms via NetExtender, alightweight client that is pushed onto theuser’s machine.SonicWALL Mobile connect™,a single unified client app forApple® iOS and Google®Android™, provides smartphone andtablet users superior network-levelaccess to corporate and academicresources over encrypted SSL VPNconnections.comprehensive Anti-SpamService (CASS) offerssmall- to medium-sizedbusinesses comprehensiveprotection from spam andviruses, with instant deployment overexisting Dell SonicWALL firewalls. CASSspeeds deployment, eases administrationand reduces overhead by consolidatingsolutions, providing one-click anti-spamservices, with advanced configuration injust ten minutes.Deep Packet Inspection for of SSL-Encrypted traffic (DPI-SSL) transparentlydecrypts and scans both inbound andoutbound HTTPS traffic for threats usingDell SonicWALL RFDPI. The traffic is thenre-encrypted and sent to its originaldestination if no threats or vulnerabilitiesare discovered.Denial of Service attack prevention 22 classes of DoS, DDoS and scanning attacksKey exchange K ey Exchange IKE, IKEv2, Manual Key, PKI (X.509), L2TP over IPSec Route-based VPN Yes (OSPF, RIP)Certificate support Verisign, Thawte, Cybertrust, RSA Keon, Entrust, and Microsoft CA for Dell SonicWALL-to-Dell SonicWALL VPN, SCEP Dead peer detection Yes DHCP over VPN Yes IPSec NAT TraversalYes Redundant VPN gatewayYesGlobal VPN client platforms supported Microsoft Windows 2000, Windows XP, Microsoft Vista 32/64-bit, Windows 7 32/64-bitSSL VPN platforms supportedMicrosoft Windows 2000 / XP / Vista 32/64-bit / Windows 7, Mac 10.4+, Linux FC 3+ / Ubuntu 7+ / OpenSUSEMobile Connect platforms supported iOS 4.2 and higher, Android 4.0 and higherSecurity servicesDeep Packet Inspection Service Gateway Anti-Virus, Anti-Spyware, Intrusion Prevention and Application Intelligence and Control Content Filtering Service (CFS) HTTP URL,HTTPS IP, keyword and content scanning ActiveX, Java Applet, and cookie blocking bandwidth management on filtering categories, allow/forbid lists Gateway-enforced Client Anti-Virus and Anti-Spyware McAfee Comprehensive Anti-Spam Service Supported Application Intelligence Application bandwidth management and control, prioritize or block application and Control by signatures, control file transfers, scan for key words or phrasesDPI SSL Provides the ability to decrypt HTTPS traffic transparently, scan this traffic for threats using Dell SonicWALL’s Deep Packet Inspection technology (GAV/AS/IPS/ Application Intelligence/CFS), then re-encrypt the traffic and send it to its destination if no threats or vulnerabilities are found. This feature works for both clients and workingIP Address assignment Static, (DHCP, PPPoE, L2TP and PPTP client), Internal DHCP server, DHCP relay NAT modes1:1, 1:many, many:1, many:many, flexible NAT (overlapping IPs), PAT, transparent modeVLAN interfaces (802.1q) 25352550200Routing OSPF, RIPv1/v2, static routes, policy-based routing, MulticastQoS Bandwidth priority, maximum bandwidth, guaranteed bandwidth, DSCP marking, 802.1pIPv6Yes AuthenticationXAUTH/RADIUS, Active Directory, SSO, LDAP, Novell, internal user database, Terminal Services, Citrix Internal database/single sign-on users 100/100 Users150/150 Users250/250 Users300/500 Users1,000/1,000 UsersVoIPFull H.323v1-5, SIP, gatekeeper support, outbound bandwidth management, VoIP over WLAN, deep inspection security, full interoperability with most VoIP gateway and communications devicesSystemZone security Yes SchedulesOne time, recurring Object-based/group-based management Yes DDNSYesManagement and monitoring Web GUI (HTTP, HTTPS), Command Line (SSH, Console), SNMP v3: Global management with Dell SonicWALL GMSLogging and reporting Analyzer, Local Log, Syslog, Solera Networks, NetFlow v5/v9, IPFIX with extensions, real-time visualizationHigh availabilityOptional Active/Passive with State SyncLoad balancing Yes, (Outgoing with percent-based, round robin and spill-over); (Incoming with round robin,random distribution, sticky IP, block remap and symmetrical remap)StandardsTCP/IP, UDP, ICMP, HTTP, HTTPS, IPSec, ISAKMP/IKE, SNMP, DHCP, PPPoE, L2TP, PPTP, RADIUS, IEEE 802.3Wireless standards802.11 a/b/g/n, WPA2, WPA, TKIP, 802.1x, EAP-PEAP, EAP-TTLS WAN acceleration supportYesFlash memory32 MB compact Flash 512 MB compact Flash3G wireless/modem * With 3G/4G USB adapter or modem — With 3G/4G USB adapter or modemPower supply 36W external Single 180W ATX power supplyFansNo fan/1 internal fan 2 internal fans 2 fansPower input10-240V, 50-60Hz Max power consumption 11W/15W 12W/16W 42W 64W 66W Total heat dissipation 37BTU/50BTU 41BTU/55BTU 144BTU 219BTU 225BTUCertificationsVPNC, ICSA Firewall 4.1 EAL4+, FIPS 140-2 Level 2, VPNC, ICSA Firewall 4.1, IPv6 Phase 1, IPv6 Phase 2Certifications pending EAL4+, FIPS 140-2 Level 2, IPv6 Phase 1, IPv6 Phase 2 —Form factor 1U rack-mountable/ 1U rack-mountable/ 1U rack-mountable/ and dimensions 7.125 x 1.5 x 10.5 in/ 17 x 10.25 x 1.75 in/ 17 x 13.25 x 1.75 in/18.10 x 3.81 x 26.67 cm 43.18 x 26 x 4.44 cm 43.18 x 33.65 x 4.44 cmWeight 1.95 lbs/0.88 kg/ 3.05 lbs/1.38 kg/ 8.05 lbs/ 3.65 kg 11.30 lbs/ 5.14 kg2.15 lbs/0.97 kg3.15 lbs/1.43 kg WEEE weight V 3.05 lbs/1.38 kg/4.4 lbs/2.0kg/ 8.05 lbs/ 3.65 kg 11.30 lbs/5.14 kg3.45 lbs/1.56 kg4.65 lbs/2.11 kgMajor regulatoryF CC Class A, CES Class A, CE, C-Tick, VCCI, Compliance MIC, UL, cUL, TUV/GS, CB, NOM, RoHS, WEEE Environment 40-105° F, 0-40° C 40-105° F, 5-40° CMTBF 28 years/15 years 23 years/14 years 14.3 years 14.1 years 14.1 yearsHumidity5-95% non-condensing 10-90% non-condensingcertificationsSpecificationsTesting methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services. Full DPI Performance/Gateway AV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs. Actual maximum connection counts are lower when Next-Generation Firewall services are enabled. VPN throughput measured using UDP traffic at 1280 byte packet size adhering to RFC 2544. Supported on the NSA 3500 and higher. Not available on NSA 2400. *USB 3G card and modem are not included. See http://www.Dell /us/products/cardsupport.html for supported USB devices. The Comprehensive Anti-Spam Service supports an unrestricted number of users but is recommended for 250 users or less. With Dell SonicWALL WXA Series Appliance.Network Security Appliance 3500 01-SSC-7016NSA 3500 TotalSecure* (1-year) 01-SC-7033Network Security Appliance 450001-SSC-7012NSA 4500 TotalSecure* (1-year) 01-SC-7032Network Security Appliance 2400 01-SSC-7020NSA 2400 TotalSecure* (1-year) 01-SC-7035Network Security Appliance 250M 01-SSC-9755Network Security Appliance 250M Wireless-N 01-SSC-9757 (US/Canada)Network Security Appliance 250M TotalSecure* 01-SSC-9747Network Security Appliance 250M Wireless-N TotalSecure*01-SSC-9748 (US/Canada)Network Security Appliance 220 01-SSC-9750Network Security Appliance 220 Wireless-N 01-SSC-9752 (US/Canada)Network Security Appliance 220 TotalSecure* 01-SSC-9744Network Security Appliance 220 Wireless-N TotalSecure*01-SSC-9745 (US/Canada)For more information on Dell SonicWALL network security solutions, please visit .*Includes one-year of Gateway Anti-Virus, Anti-Spyware, Intrusion Prevention, andApplication Intelligence and Control Service, Content Filtering Service and Dynamic Support 24x7.Security Monitoring Services from Dell SecureWorks are available for thisappliance Series. For more information, visit /secureworks。
Silicon Labs 芯片评估板 套件说明书
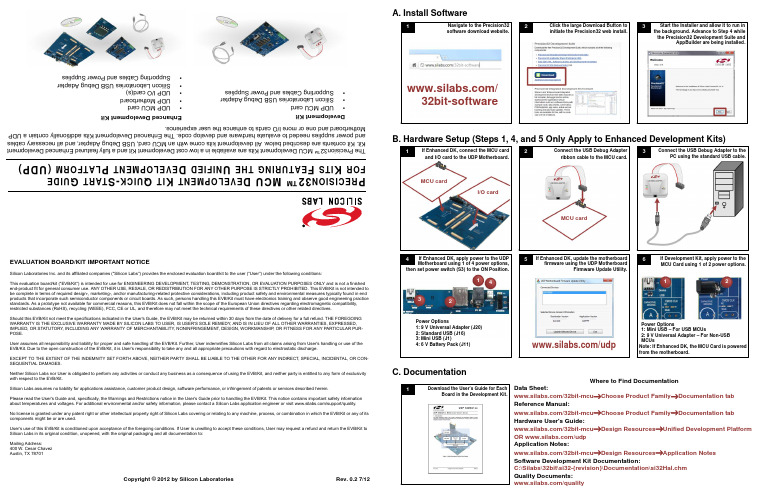
EVALUATION BOARD/KIT IMPORTANT NOTICESilicon Laboratories Inc. and its affiliated companies ("Silicon Labs") provides the enclosed evaluation board/kit to the user ("User") under the following conditions:This evaluation board/kit ("EVB/Kit") is intended for use for ENGINEERING DEVELOPMENT, TESTING, DEMONSTRATION, OR EVALUATION PURPOSES ONLY and is not a finished end-product fit for general consumer use. ANY OTHER USE, RESALE, OR REDISTRIBUTION FOR ANY OTHER PURPOSE IS STRICTLY PROHIBITED. This EVB/Kit is not intended to be complete in terms of required design-, marketing-, and/or manufacturing-related protective considerations, including product safety and environmental measures typically found in end products that incorporate such semiconductor components or circuit boards. As such, persons handling this EVB/Kit must have electronics training and observe good engineering practice standards. As a prototype not available for commercial reasons, this EVB/Kit does not fall within the scope of the European Union directives regarding electromagnetic compatibility, restricted substances (RoHS), recycling (WEEE), FCC, CE or UL, and therefore may not meet the technical requirements of these directives or other related directives.Should this EVB/Kit not meet the specifications indicated in the User's Guide, the EVB/Kit may be returned within 30 days from the date of delivery for a full refund. THE FOREGOING WARRANTY IS THE EXCLUSIVE WARRANTY MADE BY SILICON LABS TO USER, IS USER'S SOLE REMEDY , AND IS IN LIEU OF ALL OTHER WARRANTIES, EXPRESSED, IMPLIED, OR STATUTORY , INCLUDING ANY WARRANTY OF MERCHANTABILITY , NONINFRINGEMENT, DESIGN, WORKMANSHIP , OR FITNESS FOR ANY PARTICULAR PUR-POSE.User assumes all responsibility and liability for proper and safe handling of the EVB/Kit. Further, User indemnifies Silicon Labs from all claims arising from User's handling or use of the EVB/Kit. Due to the open construction of the EVB/Kit, it is User's responsibility to take any and all appropriate precautions with regard to electrostatic discharge.EXCEPT TO THE EXTENT OF THE INDEMNITY SET FORTH ABOVE, NEITHER PARTY SHALL BE LIABLE TO THE OTHER FOR ANY INDIRECT, SPECIAL, INCIDENTAL, OR CON-SEQUENTIAL DAMAGES.Neither Silicon Labs nor User is obligated to perform any activities or conduct any business as a consequence of using the EVB/Kit, and neither party is entitled to any form of exclusivity with respect to the EVB/Kit.Silicon Labs assumes no liability for applications assistance, customer product design, software performance, or infringement of patents or services described herein.Please read the User's Guide and, specifically, the Warnings and Restrictions notice in the User's Guide prior to handling the EVB/Kit. This notice contains important safety information about temperatures and voltages. For additional environmental and/or safety information, please contact a Silicon Labs application engineer or visit /support/quality.No license is granted under any patent right or other intellectual property right of Silicon Labs covering or relating to any machine, process, or combination in which the EVB/Kit or any of its components might be or are used.User's use of this EVB/Kit is conditioned upon acceptance of the foregoing conditions. If User is unwilling to accept these conditions, User may request a refund and return the EVB/Kit to Silicon Labs in its original condition, unopened, with the original packaging and all documentation to:Mailing Address:400 W. Cesar Chavez Austin, TX 78701Copyright © 2012 by Silicon Laboratories Rev. 0.2 7/12P R E C I S I O N 32™ M C U D E V E L O P M E N T K I T Q U I C K -S T A R T G U I D E F O R K I T S F E A T U R I N G T H E U N I F I E D D E V E L O P M E N T P L A T F O R M (U D P )T h e P r e c i s i o n 32™ M C U D e v e l o p m e n t K i t s a r e a v a i l a b l e i n a l o w c o s t D e v e l o p m e n t K i t a n d a f u l l y f e a t u r e d E n h a n c e d D e v e l o p m e n t K i t . K i t c o n t e n t s a r e d e s c r i b e d b e l o w . A l l d e v e l o p m e n t k i t s c o m e w i t h a n M C U c a r d , U S B D e b u g A d a p t e r , a n d a l l n e c e s s a r y c a b l e s a n d p o w e r s u p p l i e s n e e d e d t o e v a l u a t e h a r d w a r e a n d d e v e l o p c o d e . T h e E n h a n c e d D e v e l o p m e n t K i t s a d d i t i o n a l l y c o n t a i n a U D PM o t h e r b o a r d a n d o n e o r m o r e I /O c a r d s t o e n h a n c e t h e u s e r e x p e r i e n c e .D e v e l o p m e n t K i t•U D P M C U c a r d•S i l i c o n L a b o r a t o r i e s U S B D e b u g A d a p t e r •S u p p o r t i n g C a b l e s a n d P o w e r S u p p l i esE n h a n c e d D e v e l o p m e n t K i t•U D P M C U c a r d•U D P M o t h e r b o a r d •U D P I /O c a r d (s )•S i l i c o n L a b o r a t o r i e s U S B D e b u g A d a p t e r •S u p p o r t i n g C a b l e s a n d P o w e r S u p p l i e sA. Install SoftwareB. Hardware Setup (Steps 1, 4, and 5 Only Apply to Enhanced Development Kits)C. Documentation12Click the large Download Button to initiate the Precision32 web install.Navigate to the Precision32 software download website.3Start the Installer and allow it to run in the background. Advance to Step 4 while the Precision32 Development Suite andAppBuilder are being installed./32bit-software1Connect the USB Debug Adapter ribbon cable to the MCU card.2Connect the USB Debug Adapter to thePC using the standard USB cable.I/O cardMCU card45If Enhanced DK, apply power to the UDP Motherboard using 1 of 4 power options,Power Options1: 9 V Universal Adapter (J20)2: Standard USB (J16) 3: Mini USB (J1)4: 6 V Battery Pack (J11)then set power switch (S3) to the ON Position.If Development Kit, apply power to the MCU Card using 1 of 2 power options.Power Options1: Mini USB – For USB MCUs2: 9 V Universal Adapter – For Non-USB MCUsIf Enhanced DK, update the motherboardfirmware using the UDP MotherboardFirmware Update Utility./udpMCU card321412Note: If Enhanced DK, the MCU Card is powered from the motherboard.36If Enhanced DK, connect the MCU card and I/O card to the UDP Motherboard.1Download the User’s Guide for EachBoard in the Development Kit.Where to Find DocumentationData Sheet:/32bit-mcu →Choose Product Family →Documentation tab Reference Manual:/32bit-mcu →Choose Product Family →Documentation tab Hardware User's Guide:/32bit-mcu →Design Resources →Unified Development Platform OR /udp Application Notes:/32bit-mcu →Design Resources →Application Notes Software Development Kit Documentation:C:\Silabs\32bit\si32-{revision}\Documentation\si32Hal.chm Quality Documents:/qualityE . U s i n g t h e P r e c i s i o n 32 D e v e l o p m e n t S u i t eT h e P r e c i s i o n 32 D e v e l o p m e n t S u i t e i s a c o m p l e t e d e v e l o p m e n t s y s t e m f o r S i l i c o n L a b s 32-b i t M C U s . T h e D e v e l o p m e n t S u i t e c o n s i s t s o f t h r e e p a r t s : t h e U n i f i e d D e v e l o p m e n t P l a t f o r m (U D P ) h a r d w a r e , t h e S o f t w a r e D e v e l o p m e n t K i t (S D K ), a n d t h e P C d e v e l o p m e n t t o o l s i n c l u d i n g A p p B u i l d e r a n d t h e I n t e g r a t e d D e v e l o p m e n t E n v i r o n m e n t (I D E ). S e e t h e a p p l i c a t i o n n o t e s l i s t e d b e l o wf o r c o m p l e t e d e t a i l s .t h e p r o g r a m . T h e L E D b l i n k . P a u s e p r o g r a R u nl i n e s o f c o d e a n d s e l e c t T o g B r e a k p o i n t t o a d d a b r e a k p o T h e n p r e s s R u n t o r u n t o b r e a k p o i c o d e .S t e p I n t o o r S t e p O v e r V i e w o r m o d i f y P e r i p h e r a R e g i s t e r s , o r M e m o i a b l e , r i g h t -c l i a n d s e l e c t A d d W a t c h E x p r e t o a d d i t t o t h e E x p r e s s i o n s w A p p B u i l d e r I D E•A N 675: P r e c i s i o n 32 D e v e l o p m e n t S u i t e O v e r v i e w•A N 667: G e t t i n g S t a r t e d w i t h t h e S i l i c o n L a b s P r e c i s i o n 32 I D E•A N 670: G e t t i n g S t a r t e d w i t h t h e S i l i c o n L a b s P r e c i s i o n 32 A p p B u i l d e r•A N 678: P r e c i s i o n 32 s i 32F l a s h U t i l i t y C o m m a n d -L i n e P r o g r a m m e r U s e r 's G u i d e•A N 719: P r e c i s i o n 32 I D E a n d A p p B u i l d e r D e t a i l e d T u t o r i a l a n d W a l k t h r o u g hW h e r e t o F i n d S u p p o r tM C U K n o w l e d g e B a s e :w w w .s i l a b s .c o m →S u p p o r t →K n o w l e d g e B a s eV i d e o T r a i n i n g M o d u l e s :w w w .s i l a b s .c o m →S u p p o r t →T r a i n i n g a n d R e s o u r c e sC o n t a c t a n A p p l i c a t i o n s E n g i n e e r :w w w .s i l a b s .c o m →S u p p o r t →C o n t a c t T e c h n i c a l S u p p o r tD . U s i n g t h e P r e c i s i o n 32 I DE f o r t h eF i r s t T i m e2R e g i s t e r t h e I D E u s i n g t h e s t e p s l i s t e d o n t h e W e l c o m e p a g e .1O p e n t h e P r e c i s i o n 32 I D E a n d s e l e c t t h e p r o j e c t w o r k s p a c e .313456S e l e c t j u s t t h e s i m x x x x x _B l i n k y c h e c k b o x ,e n s u r e C o p y p r o j e c t s i n t o w o r k s p a c e i s s e l e c t e d , a n d p r e s s F i n i s h .S e l e c t t h e I m p o r t S I 32 S D Ke x a m p l e (s ) l i n k i n t h e Q u i c k s t a r t w i n d o w .S e l e c t t h e s i m x x x x x _B l i n k yp r o j e c t i n t h e P r o j e c t E x p l o r e r a n d p r e s s B u i l d ‘B l i n k y ’ [D e b u g ] i n t h e Q u i c k s t a r t w i n d o w .S t a r t a D e b u g s e s s i o n b yc l i c k i n g D e b u g ‘B l i n k y ’ [D e b u g ] i n t h e Q u i c k s t a r t w i nd o w .。
Autodesk Fusion 360高性能设计优化教程说明书

High-Performing Design AlternativesFusion 360, Generative Design, and SimulationGilberto FernandezDesignated Support Specialist, CSOAbout the speakerGilberto FernandezGilberto Fernandez is a Designated Support Specialist within the Autodesk Customer Services organization. Having an engineering background,he has vast experience in the field of Simulation and Computational Fluid Dynamics.Mainly Gilberto's role is to lead the way technically with Autodesk Premium Customers,in terms of Simulation solutions.He is based in Barcelona,and is heavily focused now in Design Optimization through SimulationSummaryGenerative design is a process of iterative design that uses the power of computing to give a designer a very large number of permutations and possibilities we can fine-tune with several constraints to get an high-performing design.This class will show how we can use Fusion360tools to optimize designs,fulfilling the whole process from a raw CAD model to a high-performance design model that we can use in our simulation studies.Software involved will be Fusion360and Autodesk CFD.The class can be used as a reference to get familiar with these tools as well to get to optimum performance in simulation studies.Agenda SUMMARYINTRODUCTION TO GENERATIVE DESIGN •Why do we care?•What is Gen Design•Where does it impact?•What makes it different? GENERATIVE DESIGN WORKFLOW•General workflow•Performance curves•Workflow detail:•CAD-Geometry•Define set up•Generate•Explore EXPLORATION OF OPTIONS•Outcomes and comparison•Candidate selection•ExportCOMBINING IT WITH SIM TOOLS •Fusion Simulation•CFD studies•Decision Centre LOOKING INTO THE FUTURE ADDITIONAL RESOURCESQ&ADesign is thinking made visual SAUL BASS (1920-1996)Introduction to Generative DesignWhat is Autodesk Generative Design?Autodesk generative design is a design exploration technology.Simultaneously generate multiple CAD-ready solutions based on real-word manufacturing constraints and product performance requirements.Why do we care?Making wheelchairs more versatile, customizable and a fashion itemTailored to unique persons measurements Interchangeable parts based on needsPart consolidation is a twofold motivatorOptimize for massReduce supply-chain costs associated with each part and its unique supplierHow is Autodesk Generative Design different?Where does Generative Design apply?1 | New Product Design Creation•Use Generative result as design guide. Where ismaterial needed?•What type of material and how much?•Use Generative result, manipulate for production2 | Part Consolidation•Explore costly, or hard to manufactureassemblies –how can multiple parts beconsolidated to one?3 | Part Enhancement•Enhance existing parts to improve strength-to-weight ratio, reduce material cost, improvemanufacturability•Am I using the correct material?Engineering OutcomesThe ultimate goal for any engineering activity is to strike the right balance between performance and cost to produce for a given design challenge or market opportunity.Engineers are limited in the time and energy they can spend on any design problem to fully explore the options that encompass the design space.Low Cost/Low PerformanceHigh Cost/High PerformanceCost to ProduceP e r f o r m a n c eCost to Produce P e r f o r m a n c eGenerative Design WorkflowAutodesk Generative Design -Workflow1.In CAD model appropriate Preserve andAvoidance Regions2.Start Project in Generative Design3.Import Geometry4.Setup Study -Geometry, Constraints, Loads, etc5.Generate Outcomes6.Explore Outcomes7.Export desired outcomes for useAutodesk Generative DesignAutodesk Generative Design enables the rapid creation and exploration of design options, empowering design teams to determine the tradeoffs they want to make along theprice/performance curve.Demohttps:///community/article/270191Free Generative Design Until 2020Autodesk has teamed up with AWS and NVIDIA to offer unlimited generative design in Fusion 360 from November 18th through December 31, 2019.Learn more/free-generative-designSponsorsGenerative Design WorkflowDetailsImage caption goes hereGenerative Design User InterfacePreserve Geometry-Entities will be included in the final shape -Entities will be connected (ONE PIECE)-Critical parts for mounting-Loads and constraints will be applied-Entities will NOT be included in the final shape-Barrier or obstacles-mounting or tools, we need the spaceObstacle GeometryDesign SpaceStarting Shape-Initial shape to be modified-not needed (optional)-Auto-EnvelopeStructural Constraints-Fixed/Pin/Frictionless-Faces of Preserved Geometry-Pressure –Force –Moment-Bearing-Set to geometry -preservedStructural Loads Design ConditionsObjectives -Limits-Optimization goals and limits-Mass target-for Maximize stiffness-sets limits-Specifies manufacturing methods and constraints-You can use to filter, according to your current tools-optimize useManufacturingDesign CriteriaMaterial Selection-Selection of multiple materials-This will be part of the multi-option simulation-Copy materials into custom libraries-Editable appearance and propertiesMaterial Browser Study MaterialsGenerate-Check –warnings of needed parameters -Previewer –sanity checks-Cloud credits requiredExploring first iterationsExploration of OptionsExplore outcomesConverged vs CompletedConverged and Completed –Iteration exploration https://autode.sk/2Q93SRcFor every outcome, the iterations within it can be explored, and set to any of the intermediate results. This can apply to the “completed” ones a little more -ComparisonsDisplaying and exploring propertiesDisplaying and exploring properties -Table formatDisplaying and exploring properties -Scatter plot-Every dot is an outcome-Colour code marks materials-Axis values can be changedand customized-Filters do apply-Decision Centre-Options-:-Create new Design-Create new Mesh Design from Outcome-Cloud Credits required-If for some reason it does not get generated, credits are returned Export design from outcomeBack to design with winning outcomeVideo link : https://autode.sk/32LyrixCombine with Sim ToolsOutcome into CFD -Launch•Once with model –go to Simulation > Simplify > Tools•Get the rest of assembly on topOutcome into CFD•Challenge will be the mesh for additive manufacturing•Great tool in decision Centre environmentOutcome to CFD-Example -Fusion initial modelAlternatives for housingCFD Model –Launching new geometryhttps://autode.sk/2plkwloComparison of performance –Multiple designs。
软件测试中英文术语对照表

Criterio n)的要求
Bebuggi ng
错误散播
Error Seedi ng
Behavior
行为
组件或系统对输入值的预置条件的反应
Ben chmark Test
基准测试
(1)为使系统或组件能够进行度量和比较而制 定的一种测试标准;(2)用于组件或系统之间 进行的比较,或和(1)中提到的标准进行比较 的测试(与IEEE610—致)
Analysis)、编译(Compilation)、软件产品或应 用文档的使用等。参见Defect、Deviation、
Error、Fault、Failure、Incident、Problem
Arc Test ing
弧测试
Branch Test ing
Attractive ness
吸引力
软件产品吸引用户的能力(ISO9126)。参见
Bespoke Software
定制软件
为特定的用户定制开发的软件。与之对比的是现
货软件(Off-The-Shlf Software)
Best Practice
最佳实践
在界定范围内,帮助提高组织能力的有效方法或 创新实践,通常被同行业组织视为最佳的方法或
实践
Beta Testi ng
Beta测试
用户在开发组织外,没有开发人员参与的情况下 进行的测试,检验软件是否满足客户及业务需 求。这种测试是软件产品获得市场反馈进行验收
Big-Ba ng Test ing
大爆炸测试
非增量集成测试的一种方法,测试的时候将软件 单兀、硬件单兀或者两者同时(而不是阶段性的) 集成到组件或者整个系统中去进行测试(与IEEE
Antivirus Software

Antivirus SoftwareCognex recognizes the need for antivirus software in today’s computing environment. The antivi-rus software used will vary from plant to plant, depending on vendor preferences, IT management philosophy, and other factors. Our experience is that ownership and maintenance of virus-scan-ning software is best left to the local plant IT group, and for this reason we do not supply any virus-scanning software on our systems. We do expect that our customers will install virus scanning on systems shipped to them.Internally, Cognex uses the Symantec Antivirus Corporate Edition antivirus software program. This program is installed on all internal computers and servers and is also installed on all field service laptops. The virus definition is updated automatically using the live update engine. This should not be considered an endorsement or recommendation of the Symantec software. It is simply the soft-ware that we have chosen to prevent our systems from being infected by computer viruses and, in turn, preventing their spread to customer systems.Configuration of Antivirus SoftwareSmartView system software is compatible with antivirus software. However, it is important to remember that virus-scanning programs can use a lot of system resources and can interfere with the operation of a real-time inspection system if not configured correctly.It is important to ensure that the virus scanning is set up so that it only occurs at a definite, sched-uled time. Real-time scanning should be disabled. This way, if problems or conflicts are caused by the virus-scanning software, they can easily be identified by the time of day.Because the antivirus software uses a lot of resources, it should be set to scan during a time when the system is not inspecting, if that is possible. It is also important to consider the schedule of other resource-intensive system tasks, such as Retrospect archive jobs or automatic file move/delete tasks. The antivirus software should be scheduled so that it does not occur at the same time as one of these other tasks, as this can create system-resource issues.Technical Note 170-114809 Revision 2.0 21 May 091©2009–2009 Cognex CorporationAntivirus Software• Trademarks, Copyright, and Confidentiality •Our recommendations for configuring virus-scanning software are•File system real-time protection should be disabled. The automatic enabler (advanced option) should also be turned off.•.SSD, .SSF, and .SST files should be excluded.•Network drives should not be scanned.•The virus scan can be configured to happen at startup.•The schedule should be set to no more frequently than once per day.Cognex may request that virus-scanning programs be disabled for up to one week if it is sus-pected that the virus-scan program is resulting in a conflict or excessive use of system resources.Trademarks, Copyright, and ConfidentialityCognex and SmartView are registered trademarks of Cognex Corporation. All other brand names, service marks, and trademarks (whether or not registered) referenced in this document are the property of their respective owners.© 2004–2009 Cognex Corporation. This document is copyrighted with all rights reserved. No part of this document may be reproduced in whole or in part without the prior written consent of Cognex Corporation.The information contained in this document is proprietary and confidential. It is intended for use by Cognex and Cognex customers.Technical Note 170-114809 Revision 2.0 21 May 092©2009–2009Cognex Corporation。
工程样件 OTS 概述

批量试生产
试制协议 质量保证协议 产品工程样件性能检查认可 采购认可 试制/批量的认可 计划认可 技术资料汇编 要求汇总书 责任汇总书 市场导入 管理信息系统 零批量 新零件质量提高计划
SOP
QSR APQP PPAP QSA MSA FMEA SPC 2TP ES
Start Of Production
OTS off tooling samples,用和量产相同的工装制造 出来的样件,即“工装样件”。 它必须是以后量产时要用的工装,只不过在制造 工装样件时在操作者,地点等方面可以与量产时 有所不同。OTS即全工装状态下非节拍生产条件下 制造出来的样件。(off tooling 就是不用手工工具 的意思,即非手工样件) 新产品开发顺序为 Prototype->OTS->PPAP->SOP OTS是APQP得第二阶段,手工样件后的样件提交。 是使用正常的工装设备生产的样件,目的是验证 工装;后续就是PPAP产品批准。 OTS在产品开发过程中,处于设计阶段的后半程。 DV阶段以后,由于设计的零件基本已经确定, OTS主要用于性能、制造可行性及品质可行性方面 的评价,目的就是验证大规模生产零件供应商的 硬工装的能力(主要是模具和夹具方面),只是没 有将生产节拍纳入考量。OTS件是指完全正式生产 用的工装模具生产出的样件,所以软模件不属于 OTS件。 OTS通常是由工程部门负责认可。然后会有个PVS 首批样件(PVS:生产试制批量)主要是对生产节拍及 产品批量稳定性的评价。PVS是质量部门负责。再 接下来的时2TP/2天试生产验收,主要是验证供应 商的批量供货能力。OS(零批量),是批量生产前 的总演习,批量的全面验证;接下来就是SOP, 即正式订单及批量生产。
OTS
SonicWall NSA系列网络安全应用机产品说明说明书

The SonicWall Network Security Appliance (NSA) series providesmid-sized networks, branch offices and distributed enterprises with advanced threat prevention in a high-performance security platform. Combining next-generation firewall technology withour patented* Reassembly-Free Deep Packet Inspection (RFDPI) engine on a multi-core architecture, the NSA series offers the security, performance and control organizations require. Superior threat prevention and performanceNSA series next-generation firewalls (NGFWs) integrate advanced security technologies to deliver superior threat prevention. Our patented single-pass RFDPI threat prevention engine examines every byte of every packet, inspecting both inbound and outbound traffic simultaneously. The NSA series leverages on-box capabilities including intrusion prevention, anti-malware and web/URL filtering in addition to cloud-based SonicWall Capture multi-engine sandboxing service to block zero-day threats at the gateway. Unlike other security products that cannot inspect large files for hidden threats, NSA firewalls scan files of any size acrossall ports and protocols. The security architecture in SonicWall NGFWs has been validated as one of the industry’s best for security effectiveness by NSS Labs for five consecutive years. Further, SonicWall NGFWs provide complete protection by performingfull decryption and inspection of TLS/SSL and SSH encrypted connections as well as non-proxyable applications regardless of transport or protocol. The firewall looks deep inside every packet (the header and data) searching for protocol non-compliance, threats, zero-days, intrusions, and even defined criteria to detect and prevent hidden attacks that leverage cryptography, block encrypted malware downloads, cease the spread of infections, and thwart command and control (C&C) communications and data exfiltration. Inclusion and exclusion rules allow total control to customize which traffic is subjected to decryption and inspection based on specific organizational compliance and/or legal requirements. When organizations activate deep packet inspection functions such as intrusion prevention, anti-virus, anti-spyware, TLS/SSL decryption/inspection and others on their firewalls, network performance often slows down, sometimes dramatically. NSA series firewalls, however, feature a multi-core hardware architecture that utilizes specialized security microprocessors. Combined with our RFDPI engine,this unique design eliminates the performance degradation networks experience with other firewalls.In today’s security environment, it’s not enough to rely on solely on outside parties for threat information. That’s why SonicWall formed its own in-house Capture Labs threat research team more than 15 years ago. This dedicated team gathers, analyzes and vets data from over one million sensors in itsSonicWall Network SecurityAppliance (NSA) seriesIndustry-validated security effectiveness and performance formid-sized networksBenefits:Superior threat preventionand performance• Patented reassembly-free deeppacket inspection technology• On-box and cloud-based threatprevention• TLS/SSL decryption and inspection• Industry-validated securityeffectiveness• Multi-core hardware architecture• Dedicated Capture Labs threatresearch teamNetwork control and flexibility• Powerful SonicOS operating system• Application intelligence and control• Network segmentation with VLANs• High-speed wireless securityEasy deployment, setup andongoing management• Tightly integrated solution• Centralized management• Scalability through multiplehardware platforms• Low total cost of ownershipCapture Threat Network. SonicWall also participates in industry collaboration efforts and engages with threat research communities to gather and share samples of attacks and vulnerabilities. This shared threat intelligence is usedto develop real-time countermeasures that are automatically deployed to our customers’ firewalls.Network control and flexibilityAt the core of the NSA series is SonicOS, SonicWall’s feature-rich operating system. SonicOS provides organizations with the network control and flexibility they require through application intelligence and control, real-time visualization, an intrusion prevention system (IPS) featuring sophisticated anti-evasion technology, high-speed virtual private networking (VPN) and other robust security features.Using application intelligence and control, network administrators can identify and categorize productive applications from those that are unproductive or potentially dangerous, and control that traffic through powerful application-level policies on both a per-user and a per-group basis (along with schedules and exception lists). Business-critical applications can be prioritizedand allocated more bandwidthwhile non-essential applications arebandwidth-limited. Real-time monitoringand visualization provides a graphicalrepresentation of applications, users andbandwidth usage for granular insightinto traffic across the network.For organizations requiring advancedflexibility in their network design,SonicOS offers the tools to segmentthe network through the use of virtualLANs (VLANs). This enables networkadministrators to create a virtualLAN interface that allows for networkseparation into one or more logicalgroups. Administrators create rules thatdetermine the level of communicationwith devices on other VLANs.Built into every NSA series firewall is awireless access controller that enablesorganizations to extend the networkperimeter securely through the use ofwireless technology. Together, SonicWallfirewalls and SonicWave 802.11ac Wave2 wireless access points create a wirelessnetwork security solution that combinesindustry-leading next-generation firewalltechnology with high-speed wireless forenterprise-class network security andperformance across the wireless network.Easy deployment, setup andongoing managementLike all SonicWall firewalls, the NSAseries tightly integrates key security,connectivity and flexibility technologiesinto a single, comprehensive solution.This includes SonicWave wirelessaccess points and the SonicWall WANAcceleration Appliance (WXA) series,both of which are automatically detectedand provisioned by the managingNSA firewall. Consolidating multiplecapabilities eliminates the need topurchase and install point products thatdon’t always work well together. Thisreduces the effort it takes to deploy thesolution into the network and configureit, saving both time and money.Ongoing management and monitoringof network security are handled centrallythrough the firewall or through theSonicWall Global Management System(GMS), providing network administratorswith a single pane of glass from whichto manage all aspects of the network.Together, the simplified deploymentand setup along with the ease ofmanagement enable organizations tolower their total cost of ownership andrealize a high return on investment.SonicWallSonicWave 432iSonicWall NSA 5600The SonicWall NSA 2600 is designed to address the needs of growing small organizations, branch offices and school campuses.The SonicWall NSA 3600 is ideal for branch office and small- to medium-sized corporate environments concerned aboutthroughput capacity and performance.Dual fansPower8 x 1GbEports1GbEmanagementConsoleDualDual fansPower2 x 10GbE12 x 1GbE1GbEmanagement4 x 1GbESFP portsConsoleDualDual fansPower2 x 10GbE 12 x 1GbE1GbEmanagement 4 x 1GbESFP portsConsoleDual The SonicWall NSA 4600 secures growing medium-sizedorganizations and branch office locations with enterprise-class features and uncompromising performance.The SonicWall NSA 5600 is ideal for distributed, branch office and corporate environments needingsignificant throughput.Dual fansPower2 x 10GbE12 x 1GbE 1GbEmanagement4 x 1GbE SPF portsConsole DualNetwork Security Appliance 6600The SonicWall NSA 6600 is ideal for large distributed andcorporate central site environments requiring high throughputcapacity and performance.Dual hotswappable fansPower4 x 10GbE8 x 1GbE 1GbEmanagement 8 x 1GbE SFP ports ConsoleDualReassembly-Free Deep Packet Inspection engineThe SonicWall Reassembly-Free Deep Packet Inspection (RFDPI) is a single-pass, low latency inspection system that performs stream-based, bi-directional traffic analysis at high speed without proxying or buffering to effectivelyuncover intrusion attempts and malwaredownloads while identifying application traffic regardless of port and protocol. This proprietary engine relies onstreaming traffic payload inspection to detect threats at Layers 3-7, and takesnetwork streams through extensive andrepeated normalization and decryption in order to neutralize advanced evasion techniques that seek to confusedetection engines and sneak malicious code into the network.Once a packet undergoes thenecessary pre-processing, including SSL decryption, it is analyzedagainst a single, proprietary memory representation of three signature databases: intrusion attacks, malware and applications. The connection state is then advanced to represent the positionof the stream relative to these databases until it encounters a state of attack, or other “match” event, at which point a pre-set action is taken.In most cases, the connection is terminated and proper logging andnotification events are created. However, the engine can also be configured for inspection only or, in case of application detection, to provide Layer 7 bandwidth management services for the remainder of the application stream as soon as the application is identified.Flexible, customizable deployment options – NSA series at-a-glanceEvery SonicWall NSA firewall utilizes a breakthrough, multi-core hardware design and RFDPI for internal and external network protection without compromising network performance. NSA series NGFWs combine high-speed intrusion prevention, file and content inspection, and powerful application intelligence and control with anextensive array of advanced networking and flexible configuration features. The NSA series offers an affordable platform that is easy to deploy and manage in a wide variety of large, branch office and distributed network environments.NSA series as central-site gatewayNSA series as in-line NGFW solutionPacket Packet assembly-based processSonicWall stream-based architectureCompetitive proxy-based architecture When proxy becomes full or content too large,files bypass scanning.Reassembly-free Deep Packet Inspection (RFDPI)Reassembly-free packet scanning eliminates proxy and content size limitations.Inspection timeLessMoreInspection capacityMinMaxCapture LabsThe dedicated, in-house SonicWall Capture Labs threat research team researches and develops counter-measures to deploy to customer firewalls for up-to-date protection. The team gathers data on potential threats from several sources including our award-winning network sandboxing service, Capture Advanced Threat Protection, as well as more than 1 million SonicWall sensors located around the globe that monitor traffic for emerging threats. Itis analyzed via machine learning using SonicWall's Deep Learning Algorithmsto extract the DNA from the code to see if it is related to any known forms of malicious code.SonicWall NGFW customers benefit from continuously updated threat protection around the clock. New updates take effect immediately without reboots or interruptions. The signatures resident on the appliances are designed to protect against wide classes of attacks, covering tens of thousands of individual threats with a single signature.In addition to the countermeasureson the appliance, NSA appliances alsohave access to SonicWall CloudAV,which extends the onboard signatureintelligence with over 20 millionsignatures. This CloudAV database isaccessed by the firewall via a proprietary,light-weight protocol to augment theinspection done on the appliance. WithCapture Advanced Threat Protection,a cloud-based multi-engine sandbox,organizations can examine suspiciousfiles and code in an isolated environmentto stop advanced threats such as zero-day attacks.Advanced threat protection SonicWall Capture Advanced Threat Protection Service is a cloud-based multi-engine sandbox that extends firewall threat protection to detect and prevent zero-day threats. Suspicious files are sent to the cloud for analysis with the option to hold them at the gateway until a verdict is determined. Themulti-engine sandbox platform, which includes virtualized sandboxing, full system emulation and hypervisor level analysis technology, executes suspicious code and analyzes behavior. When afile is identified as malicious, a hash is immediately created within Capture and later a signature is sent to firewalls to prevent follow-on attacks.The service analyzes a broad rangeof operating systems and file types, including executable programs, DLL, PDFs, MS Office documents, archives, JAR and APK.Capture provides an at-a-glance threatanalysis dashboard and reports, whichdetail the analysis results for files sent tothe service, including source, destinationand a summary plus details of malwareaction once detonated.ProtectionCollectionClassificationCountermeasureL A B SGlobal management and reporting For highly regulated organizations wanting to achieve a fully coordinated security governance, compliance and risk management strategy, SonicWall Global Management System (GMS®) provides administrators a unified, secure and extensible platform to manage SonicWall firewalls, wireless access points and Dell X-Series switches through a correlated and auditable workstream process. GMS enables enterprises to easily consolidate the management of security appliances, reduce administrativeand troubleshooting complexities,and govern all operational aspects ofthe security infrastructure, includingcentralized policy management andenforcement; real-time event monitoring;user activities; application identifications;flow analytics and forensics; complianceand audit reporting; and more. GMS alsomeets the firewall’s change managementrequirements of enterprises through aworkflow automation feature. With GMSworkflow automation, all enterprises willgain agility and confidence in deployingthe right firewall policies, at the righttime and in conformance to complianceregulations. Available in software, cloudand virtual appliance options, GMSprovides a coherent way to managenetwork security by business processesand service levels, dramaticallysimplifying lifecycle management of youroverall security environments comparedto managing on a device-by-devicebasis.Port Expansion Scalability SonicWall GMS Secure Compliance EnforcementFeaturesAround-the-clock security updates New threat updates are automatically pushed to firewalls in the field with active security services, and take effectimmediately without reboots or interruptions.Bi-directional raw TCP inspection The RFDPI engine is capable of scanning raw TCP streams on any port bi-directionally preventing attacks that they tosneak by outdated security systems that focus on securing a few well-known ports.Extensive protocol support Identifies common protocols such as HTTP/S, FTP, SMTP, SMBv1/v2 and others, which do not send data in raw TCP, anddecodes payloads for malware inspection, even if they do not run on standard, well-known ports.Firewall• Stateful packet inspection• Reassembly-Free Deep PacketInspection• DDoS attack protection (UDP/ICMP/SYNflood)• IPv4/IPv6 support• Biometric authentication for remoteaccess• DNS proxy• Threat APISSL/SSH decryption and inspection1• Deep packet inspection for TLS/SSL/SSH • Inclusion/exclusion of objects, groups orhostnames• SSL ControlCapture advanced threat protection1• Cloud-based multi-engine analysis• Virtualized sandboxing• Hypervisor level analysis• Full system emulation• Broad file type examination• Automated and manual submission• Real-time threat intelligence updates • Auto-block capabilityIntrusion prevention1• Signature-based scanning• Automatic signature updates• Bidirectional inspection• Granular IPS rule capability• GeoIP enforcement• Botnet filtering with dynamic list• Regular expression matchingAnti-malware1• Stream-based malware scanning• Gateway anti-virus• Gateway anti-spyware• Bi-directional inspection• No file size limitation• Cloud malware database Application identification1• Application control• Application traffic visualization• Application component blocking• Application bandwidth management• Custom application signature creation• Data leakage prevention• Application reporting over NetFlow/IPFIX• User activity tracking (SSO)• Comprehensive application signaturedatabaseWeb content filtering1• URL filtering• Anti-proxy technology• Keyword blocking• Bandwidth manage CFSrating categories• Unified policy model with app control• Content Filtering ClientVPN• Auto-provision VPN• IPSec VPN for site-to-site connectivity• SSL VPN and IPSec client remote access• Redundant VPN gateway• Mobile Connect for iOS, Mac OSX, Windows, Chrome, Android andKindle Fire• Route-based VPN (OSPF, RIP, BGP)Networking• PortShield• Jumbo frames• IPv6• Path MTU discovery• Enhanced logging• VLAN trunking• RSTP (Rapid Spanning Tree protocol)• Port mirroring• Layer-2 QoS• Port security• Dynamic routing (RIP/OSPF/BGP)• SonicWall wireless controller• Policy-based routing (ToS/metric andECMP)• NAT• DHCP server• Bandwidth management• Link aggregation (static and dynamic)• Port redundancy• A/P high availability with state sync• A/A clustering• Inbound/outbound load balancing• L2 bridge, wire/virtual wire mode,tap mode• 3G/4G WAN failover• Asymmetric routing• Common Access Card (CAC) supportWireless• MU-MIMO• Floor plan view• Topology view• Band steering• Beamforming• AirTime fairness• MiFi extender• Guest cyclic quotaVoIP• Granular QoS control• Bandwidth management• DPI for VoIP traffic• H.323 gatekeeper and SIP proxy supportManagement and monitoring• Web GUI• Command line interface (CLI)• SNMPv2/v3• Centralized management and reporting• Logging• Netflow/IPFix exporting• Cloud-based configuration backup• BlueCoat Security Analytics Platform• Application and bandwidth visualization• IPv4 and IPv6 Management• Dell X-Series switch managementincluding cascaded switches1Requires added subscription.Testing Methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services.Threat Prevention/GatewayAV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs. Threat Prevention throughput measured with Gateway AV, Anti-Spyware, IPS and Application Control enabled.VPN throughput measured using UDP traffic at 1280 byte packet size adhering to RFC 2544. All specifications, features and availability are subject to change.For every 125,000 DPI connections reduced, the number of available DPI SSL connections increases by 750.Active/Active Clustering and Active/Active DPI with State Sync require purchase of Expanded License.Performance optimized mode can provide significant increases in performance without major impact to threat prevention efficacy.*Future use. All specifications, features and availability are subject to change.NSA series ordering information*Please consult with your local SonicWall reseller for a complete list of supported SFP and SFP+ modules© 2018 SonicWall Inc. ALL RIGHTS RESERVED. SonicWall is atrademark or registered trademark of SonicWall Inc. and/or its affiliates SonicWall, Inc.1033 McCarthy Boulevard | Milpitas, CA 95035 Regulatory model numbers:NSA 2600–1RK29-0A9NSA 3600–1RK26-0A2NSA 4600–1RK26-0A3NSA 5600–1RK26-0A4NSA 6600–1RK27-0A5About UsSonicWall has been fighting the cyber-criminal industry for over 25 years, defending small, medium size businesses and enterprises worldwide. Our combination of products and partners has enabled a real-time cyber defense solution tuned to the specific needs of the more than 500,000 businesses in over 150 countries, so you can do more business with less fear.。
Sophos系列产品介绍

21
Network firewall
Free Firewall for business use
• 基于对象的防火墙规则 • 状态包检测 • 部署在网络中的任何地方 • 桥接 • IPv6 支持 • 网络地址伪装/NAT • PPTP, L2TP 远程接入 • Amazon Virtual Private Cloud Connector • 基本的日志和报告 New in UTM 9.2 • 双因素认证(一次性密码解决方案)
X
X
!!
X
!
X
3
拦截网络攻击
防火墙与全新优化的IPS系统 可以在网关位置拦截网络攻击 与防止破坏行为。
4
拦截自动回联
DNS、应用程序控制与Web代 理与ATP模块协同工作,识别 连接C&C的数据流并拦截它们。
5
识别感染系统
ATP模块可以在内部主机试图 与C&C联络时立刻识别并控制 通讯。
27
双因数认证
样本 自动遥测 蜜罐技术
SOPHOSLABS
人工判定 自动学习 & 自动记录 BIG DATA 分析
动态 & 静态
AT HOME ON THE MOVE REMOTE OFFICE
HEADQUARTERS
15
SophosLabs–云技术实现主动保护
更好,更快,实时保护化繁为简
Malware Data
22
Sophos UTM
—— 模块化设计
基础的防火墙 • 状态监测防火墙 • 灵活的NAT、DHCP • PPTP/L2TP远程访问
AntiPatterns.ppt

What are AntiPatterns?
Recall Design Patterns. AntiPatterns are observable phenomena that are signs of development problems. The purpose of cataloguing antiPatterns is so they can be recognized and remedied (“refactored”).
AntiPattern: Cut-and-Paste
Scale: Application Symptoms:
Over 10000 lines of code in a week Having to make multiple identical edits to correct a single problem
Software can have its own antiPatterns, also referred to as “design flaws”:
fascist features dancing baloney gratuitous sound effects unnecessary font transformations
Cause: too much reliance on components Refactored Solution:
Use abstraction to coalesce components. Use layered architecture, use common interfaces.
AntiPattern: Vendor Lock-in
as in the product I’m using right now.
NTT Ltd.和Fortinet保护重要基础设施和资产免受恶意网络攻击的挑战说明书

NTT Ltd. and FortinetFortifying and Protecting Valuable Infrastructure and Assets from Malicious Cybersecurity AttacksChallengesAccording to FBI reports, cybercrime losses have doubled in recent years, reaching over $3.5 billion.1 Account Takeover (ATO) losses have tripled, and fraudhas doubled.2 Ponemon Institute, a leading security research firm, notes thatthe average cost of a security breach is now almost $4 million.3 Moreover, digital transformation (DX) now accounts for over 40 percent of most IT budgets andhas expanded security requirements and boundaries.4 Enforcing cybersecurity protection across physical and virtual environments has become more complicated and expensive for most global enterprises.Given these extraordinary challenges, IT departments must spend tremendous time and resources protecting their organizations from attack. In addition, governments and other regulatory agencies have implemented a variety of compliance mandates to protect valuable assets that may include Personally Identifiable Information (PII) or intellectual property. Information security professionals are stretched thin and most organizations have difficulty meeting these demands. Solving these challenges requires a modern approach, purpose-built for advanced security and networking needs.The Fortinet Security FabricFortinet’s fast, secure, and global cybersecurity solutions provide broad, high-performance protection against dynamic security threats while simplifying IT infrastructures. Fortinet’s solutions are fortified by the industry’s highest levelof threat research, intelligence, and analytics. The Fortinet Security Fabric and solutions, combined with NTT’s comprehensive portfolio of cloud and managed security services, offer organizations the advanced security controls and unified management required to protect their data from malicious attacks. Enhanced by NTT’s integration, support, and managed security services expertise, our global partnership provides you with high-quality and cost-efficient security solutions that deliver multiple layers of threat protection and management, increased deployment flexibility, and the ability to scale your business.More than 465,000 customers worldwide, including some of the largest and most complex organizations, trust Fortinet to protect their firms’ most valuable assets. The Fortinet Security Fabric enables organizations to implement DX initiatives without compromise by delivering a complete cybersecurity platform that provides: nn Broad visibility across the entire digital attack surface to better manage risksnn Integrated solutions that reduce the complexity of supporting multiple point products nn Automated workflows to increase the speed and efficiency operations and responses Global Technology Leader The NTT Group is the largest ICT company in the world by revenue.Keeping You Secure We mitigate 2 billion securitythreats every year.Global ImplementationThe NTT group invests USD3.6 billion in research anddevelopment.Global Scale40,000 people acrossfive continents.NTT Services and SolutionsNTT is a leading Global Technology Integrator that understands your need to be resilient, yet agile, and innovative for the future of your intelligent business. Therefore, knowing the security risks you face and being prepared to address them amidst constant change is crucial. We work with you to identify the technologies and services you need to create, build, deliver, and manage a cybersecurity posture that keeps you secure while you transform.NTT offers proven business and technology advisory services, delivered by experts with advanced cybersecurity knowledge. We have both vertical-specific and regional expertise that enables you to evaluate the most appropriate activities to prepare effectively. NTT security experts provide the help you need to identify the technologies required, assist in implementation, and monitor systems for ongoing security and integrity from our security operations center (SOC).The NTT and Fortinet PartnershipNTT and Fortinet can help protect your firm from cyberattacks as your organization expands from data centers to endpoints and the cloud, well beyond traditional boundaries. Our goal is to help you build a comprehensive security platform that provides multiple layers of threat protection and management, increased deployment flexibility, and the ability to scale with business requirements, while maximizing your existing IT investment. With cybersecurity at the core of our strategy and digital programs, NTT has partnered with Fortinet to help enterprise firms create a digital business infrastructure that is secure by design. With our combined threat intelligence, we help identify, predict, detect, and respond to cyberthreats while supporting business innovation and managing risk. Unlike others in the security industry, we support your team across the full cybersecurity lifecycle, including:nn Consultative advice on the emerging threats and the best practice security posture needed to enable your business goalsn Designing, architecting, and implementing the best solutions globally by aligning controls that best suit your environmentnn Managed service on a global basis to help overcome resource gaps and implement and manage best-in-class security technologies nA Comprehensive ApproachNTT’s extensive global experience, combined with our Fortinet Technical Professional Certifications, ensure our ability to help your team plan and build defensible infrastructures that incorporate solutions from Fortinet. Implementations will always exceed business requirements and create fortified foundations for a secure infrastructure. The NTT and Fortinet global partnership offers you a consistent level of service and support, as well as the latest solutions needed to remain secure. NTT’s proactive teams monitor and maintain security devices through our six Global Security Operations Centers using ITIL-aligned Global Services Operating Architecture Service capabilities, which include 24x7 technical support, product education, and professional integration services.By leveraging the ISA99/IEC 62443 standard and integrating with third-party partners, NTT Security experts and the Fortinet Security Fabric deliver a comprehensive security approach that implements a progressive strategy across three major phases: Phase I: ReconnaissanceNTT begins by passively observing and monitoring your network. We then create an updated and comprehensive inventory of every network segment, device, application version, connectivity detail, and security score. We also perform real-time behavioral analytics that identify normal and abnormal activities. This provides a visibility overview to adequately plan the best tactics and strategies and provide the appropriate security solutions and services.Phase II: RisksNTT Security experts identify your security vulnerabilities and map the risks to the operational level. We use a variety of common benchmarks including the National Institute of Standards and Technology (NIST) framework, the EU’s Directive on Security of Network and Information Systems (NIS Directive), and IEC 62443 to identify risks and how they relate to your organization’s infrastructure, business, and operational goals. Benchmarks and identified risks are used to guide your firm and prioritize the fortifications, weapons, and armor needed reduce risks and maintain operational uptime.Phase III: ResponseResponding to threats in today’s dynamically changing environment requires a more proactive rather than reactive approach. NTT’s Security Division can help you identify potential threats and attackers before they invade. To help with this, we employ the most appropriate Fortinet solutions and Security Fabric, based on the insights and recommendations obtained from the previous two phases, to help fortify your firm against attacks. The Fortinet Security Fabric and solutions offer some of the most comprehensive and proven solutions in the industry that include:1. An Integrated Platform: Fortinet delivers a flexible platform and next-generation firewall (NGFW) technology for buildingan end-to-end, integrated security architecture. From the data center to the endpoint to multiple clouds, Fortinet offers an integrated Security Fabric. Also, an open application programming interface (API) and Fabric Connectors that can help you integrate third-party tools to leverage prior investments.2. Remote Location Security: Fortinet offers a comprehensive software-defined wide-area network (SD-WAN) and securenetworking for remote locations. This eliminates the need for expensive multiprotocol label switching (MPLS) bandwidth, provides optimal security, and improves network performance.3. Networking, Cybersecurity, and Physical Security: Fortinet delivers the ability to consolidate networking, cybersecurity,and surveillance functions into a single pane of glass—whether at a main site or remote branch.4. Insider Threat Protection: Fortinet delivers a comprehensive and multilayered solution to guard against accidental anddeliberate insider threats with identity and access management supplemented by network access control (NAC), intent-based segmentation, deception technology, and user and entity behavior analytics (UEBA)—all integrated for centralized visibility and control.5. Robust Threat Intelligence: FortiGuard Labs delivers comprehensive intelligence from a large global network of firewallsand an artificial intelligence (AI)-powered self-evolving detection system (SEDS) that has refined its algorithms using machine learning (ML) for nearly eight years. This has resulted in extremely accurate, real-time identification of zero-day, and unknown threats.6. Industry Leadership: Fortinet is recognized as a Leader in the Gartner Magic Quadrant for Network Firewalls, achieved thebest score in the NGFW Security Value Map from NSS Labs, and has achieved nine “Recommended” ratings from NSS Labs.FortiGate Firewall Use CaseA financial services company used multiple legacy vendors to meet firewall, NAC, endpoint protection, and WAN edge router requirements. They managed these devices in-house and maintained separate relationships with each vendor. When a new CISO joined the firm, he asked his team to review the entire Fortinet Fabric solution across all areas including switching and wireless infrastructure. NTT Managed Security Services offered the ability to manage all aspects of the Fortinet Fabric with a single vendor, thereby lowering efforts and costs. NTT helped improve the customer’s overall security posture and increase the performance of the WAN edge branch network through a fully-integrated solution.Secure Edge/SD-WAN Use CaseA large foods manufacturing and processing company based in the United States had invested in Fortinet FortiGates for their data centers and DMZ, which was fully managed by the NTT Managed Security Services team. When the company decidedto transform their edge branch deployments by implementing SD-WAN technology, NTT recommended a security-focused approach that leveraged the existing FortiGate infrastructure. Having the SD-WAN feature native within a security appliance allowed seamless, automated, and preemptive failover capabilities for the network and the defined applications. Continuous health monitoring is performed on the FortiGate appliances, and if connectivity becomes an issue, the FortiGate will fail overto another node before network performance is impacted. This can be enhanced by assigning roles to critical applicationsthat prioritize connectivity. The customer now benefits from consistent security policies across the core and branch network, application awareness at the edge, and lower Total Cost of Ownership (TCO). In managed Fortinet environments, NTT clients have consistently relied on NTT to manage global rule sets and security policies, and enable SD-WAN features. NTT ensures that the edge is secure while maintaining the integrity of the wider network.OT Use CaseA municipal water & wastewater systems operator in the United States had difficulty balancing limited resources against OT security needs to keep critical Water sites operational, as well as reduce operational cyber risks while meeting corporate guidelines. The company had not yet implemented an OT cybersecurity roadmap to address cybersecurity requirements or focus IT budgets on high impact OT assets. The NTT Security Consulting team helped the customer build a comprehensiveOT cybersecurity roadmap. NTT worked collaboratively with Fortinet to provide a complete solution to address all OT security requirements including perimeter protection and systems baselining. The Fortinet-NTT solution proactively limited OT network risks through dynamic network segmentation and enforced security policies across all OT devices. The solutions also analyzed traffic for ongoing threats and vulnerabilities.Teleworker Use CaseRecent research revealed that 84 percent of firms plan to continue supporting more teleworkers but less than 30 percentare ready to ensure adequate security.5 Remote work is the new norm where the current environment requires employeesto complete work-related tasks through remote internet connections. The Fortinet Security Fabric addresses remote worker scenarios with three primary levels of connectivity. NTT Managed Security Services provides deployment and managed services for all these elements of the Fortinet Security Fabric, to ensure the most cost-effective and reliable solutions available for remote workers. FortiGate with the FortiClient Fabric Agent provides a VPN tunnel back to a primary office, to ensure that communications stay private while traveling across open networks. FortiAuthenticator and FortiToken provide multi-factor authentication (MFA) to verify user identities.And for individuals handling company confidential communications, deploying a FortiGate NGFW at a remote office provides key personnel with the highest levels of security and performance available for remote locations. With secure traffic tunnels,as well as application control and traffic inspection, a low-end FortiGate NGFW provides an economical and powerful solution with several levels of protection, backed by artificial intelligence (AI) security processes. By deploying the Remote Work solution from Fortinet and NTT, firms can benefit from the agility required to support remote workers, thereby increasing employee productivity, morale, and retention.ConclusionAvoiding the serious consequences of ransomware or other malicious cybersecurity attacks, or compliance-related finesor lawsuits, now requires more advanced and effective network security technologies, expertise, and services. Rather than complex and costly point solutions or services, IT and security teams need augmentation from trained security experts combined with the latest security solutions that seamlessly integrate into networks and simplify and automate security tasks. Organizations need to identify risks and how they relate to infrastructure, business, and operational goals, and then implement a Security Fabric, solutions, and managed services to mitigate attacks while creating seamless and frictionless user experiences. To accomplish this, firms require transparent visibility and real-time security workflows underscored by global threat intelligence. In today’s dynamic, remote, and risk-filled environment, protecting valuable assets requires the right combination of security solutions and services provided by NTT and Fortinet.Figure 1: Fortinet Security Fabric diagram.The Security FabricThe Fortinet Security Fabric platform provides true integration and automation across an organization’s security infrastructure, delivering unparalleled protection and visibility to every network segment, device, and appliance, whether virtual, in the cloud, or on-premises.Contact Information, Trademarks, and CopyrightsReferences1https:///news/stories/2019-internet-crime-report-released-0211202https:///press-release/identity-fraud-hits-all-time-high-167-million-us-victims-2017-according-new-javelin3https:///posts/whats-new-in-the-2019-cost-of-a-data-breach-report/4https:///getdoc.jsp?containerId=prUS456124195https:///press-releases/bitglass-report-84-of-organizations-will-continue-to-support-remote-work-but-most-arent-equipped-to-do-so-securely Copyright © 2021 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare and FortiGuard, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.May 2, 2021 3:09 AM。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1.0 I NTRODUCTIONA pattern is a common solution to a problem that occurs in many different contexts [Gamma et al. 1995]. It provides a general solution that may be specialized for a given context. Patterns capture expert knowledge about “best practices” in software design in a form that allows that knowledge to be reused and applied in the design of many different types of software.Patterns address the problem of “reinventing the wheel.” Over the years, software developers have solved essentially the same problem, albeit in different contexts, over and over again. Some of these solutions have stood the test of time while others have not. Pat-terns capture these proven solutions and package them in a way that allows software designers to look-up and reuse the solution in much the same fashion as engineers in other fields use design handbooks.The use of patterns in software development has its roots in the work of Christopher Alexander, an archi-tect. Alexander developed a pattern language for plan-ning towns and designing the buildings within them [Alexander et al. 1977]. A pattern language is a collec-tion of patterns that may be combined to solve a range of problems within a given application domain, such as architecture or software development. Alexander’swork codified much of what was, until then, implicit in the field of architecture and required years of experi-ence to learn.In addition to capturing design expertise and providing solutions to common design problems, patterns are valuable because they identify abstractions that are at a higher level than individual classes and objects. Now, instead of discussing software construction in terms of building blocks such as lines of code, or individual objects, we can talk about structuring software using patterns. For example, when we discuss using the Proxy pattern [Gamma et al. 1995] to solve a problem, we are describing a building block that includes several classes as well as the interactions among them.Patterns have been described for several different cate-gories of software development problems and solu-tions, including software architecture, design, and the software development process itself.Recently, software practitioners have also begun to document antipatterns . Antipatterns [Brown et al. 1998]are conceptually similar to patterns in that they docu-ment recurring solutions to common design problems. They are known as anti patterns because their use (or misuse) produces negative consequences. Antipat-terns document common mistakes made during soft-Software Performance AntiPatterns:Common Performance Problems and Their SolutionsA pattern is a common solution to a problem that occurs in many different contexts. Pat-terns capture expert knowledge about “best practices” in software design in a form that allows that knowledge to be reused and applied in the design of many different types of software. Antipatterns are conceptually similar to patterns in that they document recurring solutions to common design problems. They are known as antipatterns because their use (or misuse) produces negative consequences. Antipatterns document common mistakes made during software development as well as their solutions.While both patterns and antipatterns can be found in the literature, they typically do not explicitly consider performance consequences. This paper explores antipatterns from a performance perspective. We propose four new performance antipatterns that often occur in software systems.Connie U. SmithPerformance Engineering ServicesPO Box 2640Santa Fe, New Mexico, 87504-2640(505) 988-3811/Lloyd G. WilliamsSoftware Engineering Research264 Ridgeview Lane Boulder, Colorado 80302(303) 938-9847boulderlgw@Copyright © 2002, Performance Engineering Services and Software Engineering Research. All rights reserved.ware development as well as their solutions. Thus, antipatterns tell you what to avoid and how to fix the problem when you find it. Antipatterns address soft-ware architecture and design as well as the software development process itself.Antipatterns are refactored (restructured or reorga-nized) to overcome their negative consequences. A refactoring is a correctness-preserving transformation that improves the quality of the software. For example a set of classes might be refactored to improve reusabil-ity by moving common properties to an abstract super-class. The transformation does not alter the semantics of the application but it may improve overall reusability. Refactoring may be used to enhance many different quality attributes of software, including: reusability, maintainability, and, of course, performance. Refactor-ing is discussed in detail in [Fowler 1999].Our experience is that developers find antipatterns useful because they make it possible to identify a bad situation and provide a way to rectify the problem. This is particularly true for performance because good per-formance is the absence of problems. Thus, by illustrat-ing performance problems and their causes, performance antipatterns help build performance intu-ition in developers. Patterns, which do not contain per-formance problems, may be less useful for building performance intuition, especially if their performance characteristics are not discussed (as is typically the case).While both patterns and antipatterns can be found in the literature, they typically do not explicitly consider performance consequences. It is important to docu-ment both design patterns that lead to systems with good performance and to point out common perfor-mance mistakes and how to avoid them. This is a sup-plement to software performance engineering that will improve the architectures and designs of software developers.This paper explores antipatterns from a performance perspective. We propose four new performance anti-patterns that often occur in software systems.While their emphasis is different, both patterns and antipatterns address common software problems and their solutions. The emphasis in the patterns commu-nity, however, is on quality attributes, such as reusabil-ity or maintainability, other than performance. As the use of patterns and antipatterns becomes more wide-spread, it is vital to also identify those that are likely to have good performance characteristics. We propose antipatterns for performance problems that we encoun-ter in many different contexts but have the same under-lying pathology. Because we find them so often, it is important to document these antipatterns so develop-ers will be able to recognize them before they occur, and select appropriate alternatives.2.0 R ELATED W ORKAntipatterns are derived from work on patterns. As noted in the introduction, this work is aimed at captur-ing expert software design knowledge. There is a large body of published work on patterns including [Gamma et al. 1995], [Buschmann et al. 1996], and the proceed-ings of the Pattern Languages of Program Design (PLoP) conferences. While there is occasional mention of performance considerations in the work on patterns, the principal focus is on other quality attributes, such as modifiability and maintainability.Meszaros [Meszaros 1996] presents a set of patterns that address capacity and reliability in reactive systems such as telephony switches. Petriu and Somadder [Pet-riu and Somadder 1997] extend these patterns for use in identifying and correcting performance problems in distributed layered client-server systems with multi-threaded servers.Smith [Smith 1988] presents a set of principles for con-structing responsive software systems. While they were published before the work on software patterns began and presented with a different focus, they serve as the basis for performance patterns.Antipatterns extend the notion of patterns to capture common design errors and their solution. The most extensive work on this topic is by Brown, et al. [Brown et al. 1998]. Their work, like the work on patterns how-ever, focuses principally on quality attributes other than performance.This paper extends the work on antipatterns to explic-itly address the performance of software architectures and designs. It presents four common performance mistakes made in software architectures. They may also have other negative impacts on other quality attributes, but they are not addressed here. Additional performance patterns and antipatterns appear in a new book by the authors [Smith and Williams 2001].Each of the antipatterns is defined in the following sec-tions using this standard template:•Name: the section title•Problem: What is the recurrent situation that causes negative consequences?•Solution: How do we avoid, minimize or refactor the antipattern?3.0 E XCESSIVE D YNAMIC A LLOCATIONWith dynamic allocation, objects are created when they are first accessed (a sort of “just-in-time” approach)and then destroyed when they are no longer needed. This can often be a good approach to structuring a sys-tem, providing flexibility in highly dynamic situations. For example, in a graphics editor, it may be a very use-ful approach to create an instance of a shape (such as a circle or rectangle) when it is drawn, and destroy the instance when the shape is deleted. Excessive Dynamic Allocation, however, addresses frequent, unnecessary creation and destruction of objects of the same class.3.1 ProblemDynamic allocation is expensive. Riel [Riel 1996]describes an object-oriented approach to designing a gas station in which, when your car needs gasoline, you pull over to the side of the road, buy a piece of land, build a gas station (which, in turn builds pumps, and so on), and fill the tank. When you’re done, you destroy the gas station and return the land to its origi-nal state. Clearly, this approach only works for the wealthy (and patient!). Y ou certainly do not want to use this approach if you need gas frequently.The situation is similar in object-oriented software sys-tems. When an object is created, the memory to con-tain it (and any objects that it contains) must be allocated from the heap, and any initialization code for the object and the contained objects must be executed. When the object is no longer needed, necessary clean-up must be performed, and the reclaimed memory must be returned to the heap to avoid “memory leaks.” While the overhead for creating and destroying a single object may be small, the performance impact may be significant when a large number of objects are fre-quently created and then destroyed.The sequence diagram in Figure 1 illustrates Excessive Dynamic Allocation. This example is drawn from a call-processing application in which, when a customer lifts the telephone handset (an offHook event), the switch creates a Call object to manage the call. When the call is completed (an onHook event), the Call object is destroyed. (Details of the call processing are provided in the sequence diagram referenced by handleCall , which is not shown here.)Figure 1: Excessive Dynamic AllocationWhile constructing a single Call object may not seem excessive, a Call is a complex object that contains sev-eral other objects that must also be created. In addi-tion, a switch can receive hundreds of thousands of offHook events each hour. In a case like this, the over-head for dynamically allocating call objects adds sub-stantial delays to the time needed to complete a call.The cost of dynamic allocation, C , is:C N s c s d +()depth∑×=where N is the number of calls, depth is the number of contained objects that must be created when the class is created, and s c and s d are the service time to create and to destroy the object, respectively.Figure 2 shows the cost of Excessive Dynamic Alloca-tion for some typical values of depth and S , the sum ofthe creation and destruction time. The figure shows how the overhead for dynamic allocation increases as the number of calls increases. Note that the graph shows the total service time for dynamic allocation, regardless of the number of processes handling these calls. Calls are multi-processed, so the response time depends on the number of processes and on conten-tion delays among them. Reducing the service time, however, also reduces the response time.3.2 SolutionThere are two possible solutions to problems intro-duced by Excessive Dynamic Allocation.The first is to “recycle” objects rather than create new ones each time they are needed. This approach pre-allocates a “pool” of objects and stores them in a col-lection. New instances of the object are requested from the pool, and unneeded instances are returned to it.Figure 2: Cost of Excessive Dynamic AllocationThis approach is useful for systems that continually need many short-lived objects (like the call processing application). Y ou pay for pre-allocating the objects at system initialization but reduce the run-time overhead to simply passing a pointer to the pre-allocated object. This is an application of the Processing versus Fre-quency principle—we minimize the product of the amount of processing times the frequency that it is per-formed. Returning unused objects to the pool elimi-nates garbage collection overhead and possible memory leaks.Another way to refactor the Excessive Dynamic Alloca-tion antipattern is to share objects rather than create new ones.An example of this approach is the use of the Flyweight pattern [Gamma et al. 1995] to allow all clients to share a single instance of the object.The first improvement approach affects the cost in Fig-ure 2 by reducing the service time, S, to the time to allocate/return an object from the pool, and changing the depth to 1 because the pre-allocated objects have already created the subordinate objects. The improve-ment for the second approach is similar.4.0 C IRCUITOUS T REASURE H UNTDo you remember the child’s treasure hunt game which starts with a clue that leads to a location where the next clue is hidden and so on, until the “treasure” is finally located? The antipattern analogy is typically found in database applications. Software retrieves data from a first table, uses those results to search a second table, retrieves data from that table, and so on, until the “ulti-mate results” are obtained.4.1 ProblemThe impact on performance is the large amount of database processing required each time the “ultimate results” are needed. It is especially problematic when the data is on a remote server, and each access requires transmitting all the intermediate queries and their results via a network, and perhaps through mid-dleware and other servers in a multi-tier environment. The ICAD application originally described in [Williams and Smith 1998] and also discussed in [Smith and Will-iams 2001] illustrates this antipattern. The application allows engineers to construct and view drawings that model structures, such as aircraft wings. A model is stored in a relational database, and several versions of the model may exist within the database.Figure 3 shows a portion of the ICAD class diagram with the relevant classes. A model consists of elements that may be: beams, which connect two nodes; trian-gles, which connect three nodes; or plates, which con-nect four or more nodes. A node is defined by its position in three-dimensional space (x, y, z). Additional data is associated with each type of element to allow solution of the engineer’s model.This example focuses on the DrawMod scenario in which a model is retrieved from the database and drawn on the screen. Figure 4 shows a sequence dia-gram for this scenario. A typical model consists of 2,000 beams and 1,500 nodes (a single node may be connected to as many as four beams). The software first finds the model ID, then uses it to find the beams, and repeats the sequence of steps to retrieve each beam row, using the node number from the beam row to find and then retrieve the node row ((which contains the “ultimate results”—the node coordinates). ThisFigure 3: ICAD Classes and Associationsinformation is then used to draw the model. For a typi-cal DrawMod scenario, there are 6,001 database calls: 1 for the model, 2,000 for the beams, and 4,000 for the nodes.Figure 4: DrawMod Example of Circuitous Treasure HuntA large number of database calls causes the most seri-ous performance problems in systems with remote database accesses, due to the cost of the remote access, the processing of the query, and the network transfer of all the intermediate results.Another instance of the antipattern is also found in object-oriented systems, where operations have large “response sets.” In this case, one object invokes an operation in another object, that object then invokes an operation in another object, and so on, until the “ulti-mate result” is achieved. Then each operation returns, one by one, to the object that made the original call.The performance impact is the extra processing required to identify the final operation to be called andinvoking it, especially in distributed object systems where objects may reside in other processes and on other processors. When the invocation causes the intermediate objects to be created and destroyed, the performance impact is even greater. This behavior also has poor memory locality because each context switch may cause the working set of the called object to be loaded. The working sets of intermediate objects may need to be reloaded later when the return executes.The class diagram in Figure 3 shows a simple example.Suppose that the model data has been retrieved from the database and is now contained within each object. Then the Model object must determine each Beam object to call (from the association to Beam , probably a table of pointers), and each Beam must determinewhich Node objects to call (from the association to Nodes ). The Model calls the first Beam operation, then the Beam calls two Node operations, and so on.4.2 SolutionIf you find the database access problem early in devel-opment, you may have the option of selecting a differ-ent data organization. For example, the DrawMod database could store the node coordinates (x, y, z ) in the beam table. The sequence diagram for the alterna-tive database design appears in Figure 5. With the node coordinates in the beam row, the database call to find and retrieve nodes is unnecessary and is omitted. For a typical DrawMod scenario with 2,000 beams, there will be 4,000 fewer database calls.Figure 5: Refactored DrawMod ScenarioIn general the number of calls saved will be:C s a jj rootpath∈∏=where c s is the total number of calls saved, a j is the number of associated objects in the level below for each object in this level—for every object j between the object originally containing the “ultimate result” (the leaf class), and the object containing the “first clue” (the root class). For example, for the leaf class (Node ) a j is two nodes per beam, and for the intermediate class (Beam ) a j is 2,000 beams per model, so c s is 4,000.There are some potential disadvantages to reorganiz-ing the DrawMod data in this way. Optimizing the data organization for one scenario may degrade the perfor-mance of other scenarios. To determine the appropri-ateness of each alternative, the performance engineer will need to analyze the performance impact on other scenarios that use the database. It is unwise to opti-mize the database organization for a single scenario if it has a detrimental affect on all other scenarios; instead you want the “globally optimal” solution for the key performance scenarios. To do so, you evaluate the overall performance by revising each scenario that is affected by the change, and comparing the model solu-tions.For distributed systems, if you cannot change the data-base organization, you can reduce the number of remote database calls by using the Adapter pattern [Gamma et al. 1995] to provide a more reasonable interface for remote calls. The Adapter would thenmake all the other (local) database calls required to retrieve the “ultimate result,” and return only those results to the remote caller. This reduces the number of remote calls and the amount of data transferred, but does not reduce the database processing.For designs with large response sets, an alternative is to create a new association that leads directly to the “ultimate result.” For example, in Figure 3 we would add an association between the Model class and the Node class. In the DrawMod scenario, this would reduce the number of operations called from 6,000 (2000 Beam calls plus 4,000 Node calls) to 1,500 (the number of Nodes per Model). The performance impact is substan-tial if these are remote calls that are made via middle-ware such as CORBA or DCOM.5.0 T HE O NE-L ANE B RIDGEOn the south island of New Zealand there is a highway with many one-lane bridges; one of them is even shared with a train. This isn’t a problem in New Zealand because there is light traffic in that part of the country. It would be a problem, though, if it were in Los Angeles. 5.1 ProblemThe problem with a One-Lane Bridge is that traffic may only travel in one direction at a time, and, if there are multiple lanes of traffic all moving in parallel, they must merge and proceed across the bridge; one vehicle at a time.This increases the time required to get a given number of vehicles across the bridge, and can also cause long backups.The software analogy to the One-Lane Bridge is a point in the execution where one, or only a few, processes may continue to execute concurrently. All other pro-cesses must wait. It frequently occurs in applications that access a database. Here, a lock ensures that only one process may update the associated portion of the database at a time. It may also occur when a set of pro-cesses make a synchronous call to another process that is not multi-threaded; all of the processes making synchronous calls must take turns “crossing the bridge.”The sequence diagram in Figure 6 illustrates the data-base variant of the One-Lane Bridge antipattern. Each order requires a database update for each item ordered. The structure selected for the database assigns a new order item number to each item, and inserts all items at the end of the table. If every new update must go to the same physical location, and all new items are “inserted,” then the update behaves like a One-Lane Bridge because only one insert may pro-ceed at a time; all others must wait. There is also a second problem in that these inserts are costly because they must update a database index for each key on the table.Figure 6: Database Contention ProblemSimilar problems occur when the database key is a date-time stamp for an entity, or any key that increases monotonically. We have also seen this problem for peri-odic archives, where processing must halt while state information is transferred to long-term storage.5.2 SolutionWith vehicular traffic, you alleviate the congestion caused by a One-Lane Bridge by constructing multiple lanes, constructing additional bridges (or other alterna-tives), or rerouting traffic.The analogous solutions in the database update exam-ple above would be:•Use an algorithm for assigning new database keys which results in a “random” location for inserts,•Use multiple tables that may be consolidated later, or•Use another alternative such as pre-loading “empty” database rows, and selecting a location to update that minimizes conflicts.For example, an alternative for assigning date-time keys is to use multiple “buckets” for inserts, and use a hashing algorithm to assign new inserts to the “buck-ets.”Reducing the amount of time required to cross the bridge also helps relieve congestion. One way to do this is to find alternatives for performing the update. For example, if the update must change multiple tables, it would be better to select a different data organization in which the update could be processed in a single table.For the database example above, the magnitude of the improvement depends on the intensity of new item orders, and the service time for performing updates. The relationship is:RT S1XS–-----------------=where RT is the residence time (elapsed time for per-forming the update), S is the service time for perform-ing updates, and X is the arrival rate.Figure 7 shows a comparison of the residence time for various arrival rates for two different service times. The first curve assumes the service time for the update is 10 milliseconds (thus the arrival rate of update requests must be less than 100 requests per second), and shows how the residence time increases as the arrival rate approaches the maximum. The second curve shows the improvement if the update service time is reduced by 1 millisecond! The figure illustrates the improvement achievable by reducing the service time (the time required to cross the bridge).Figure 7: Performance Impact of the One-Lane BridgeIf youchange the structure of the database so that you update in multiple locations (so fewer processes wait for each update), this is equivalent to reducing the arrival rate—and the figure also shows the relative ben-efit of this alternative.Figure 7 also illustrates the relative importance of the One-Lane Bridge antipattern: If the intensity of requests for the service is high, it may be a significant barrier to achieving responsiveness and scalability requirements.This solution to the One-Lane Bridge problem embod-ies the Shared Resources principle, because respon-siveness improves when we minimize the schedulingtime plus the holding time. Holding time is reduced by reducing the service time for the One-Lane Bridge, and by rerouting the work.6.0 T RAFFIC J AMHave you ever been stuck in a traffic jam on a highway where traffic initially inches along, then goes slightly faster, and then inches along again? Suddenly you notice that traffic ahead is moving at normal speeds, and there is no sign of the original problem that caused the jam. It is long gone. This same antipattern occurs in software systems. It is often caused by the One-Lane Bridge, but there are other sources as well.6.1 ProblemThe performance impact of the Traffic Jam is the tran-sient behavior that produces wide variability in response time. Sometimes it is fine, but at other times, it is unacceptably long. The cause of the problem is sel-dom visible to users who thus find it even more frustrat-ing.The problem often occurs when the One-Lane Bridge, or some other cause, produces a large backlog in jobs waiting for service, whereupon it takes a long time to return to “normal” operating conditions. The problem also occurs when a large amount of work is scheduled within a relatively small interval. It occurs, for example, when every user needs a report at approximately the same time, or when stock market activity triggers a sudden surge in trading activity. There are many other, similar circumstances.6.2 SolutionIf the problem is caused by the One-Lane Bridge, the solution to that antipattern will reduce the effect of the Traffic Jam.If the problem is caused by periodic high demand, you should seek alternatives that spread the load, or han-dle the demand in a different manner. Y ou can accom-plish this by using either the Alternative Routes pattern or the Flex-Time pattern.For example, if users select the time for a report to be generated, change the selection options so that they select a time interval rather than selecting a specific time. This gives the software more flexibility in schedul-ing the reports to reduce contention. If that isn’t possi-ble, make sure that the user interface doesn’t encourage everyone to select the same default value. Y ou can do this by generating a random number for the default time (e.g., instead of always displaying 7:00 a.m., generate a random time between 6:50 a.m. and 7:10 a.m. and display this as the default value).If the problem is caused by external factors such as stock market behavior, there isn’t much that you can do in the software other than use SPE techniques to iden-tify the most important workloads, and streamline their processing as much as possible. Use the models to determine the size of the platforms and network that will be required to support the worst-case workload intensity. For extremely important workloads, you may need to size the execution environment so that it is lightly used under normal conditions.7.0 S UMMARY AND C ONCLUSIONSThis paper has explored antipatterns from a perfor-mance perspective. We introduce four new antipatterns with negative performance consequences, and quantify their impact on performance.The value of both antipatterns and their predecessor, patterns, is that they capture expert software design knowledge. This value has been amply demonstrated by their acceptance within the development community. One serious shortcoming of both patterns and antipat-terns has been their lack of focus on performance issues. While some authors focused on performance [Meszaros, 1996; Petriu and Somadder, 1997], most have considered it as an afterthought, if at all. Demon-strating the performance characteristics of patterns and antipatterns is vital so that developers using them in designing software can select alternatives that will meet their performance goals.The work presented here goes beyond merely describ-ing the characteristics of architectural or design antipat-terns, however. The Excessive Dynamic Allocation, Circuitous Treasure Hunt, One Lane Bridge, and Traffic Jam antipatterns document common performance mis-takes and provide solutions for them. While these anti-patterns may manifest themselves in a variety of ways (for example the One Lane Bridge problem may be caused by either database collisions or synchronization delays) the manifestations have a common underlying cause.The solutions to these antipatterns embody sound, well-accepted performance principles [Smith, 1988; Smith, 1990; Smith, 2001]. These principles are similar to patterns in that they provide guidelines for creating responsive software. The antipatterns presented here provide a complement to the performance principles by illustrating what not to do and how to fix a problem when you find it. A simple analogy from electrical engi-neering would be using examples of series and parallel circuits (i.e., patterns) to illustrate how to build proper circuits and an example of a short circuit (i.e., an anti-pattern) to show what to avoid. Feedback from stu-dents in our classes indicates that both types of example are needed to instill performance intuition. More work is needed on both patterns and antipatterns that includes their impact on performance as well as other quality attributes. We are continuing to identify other performance-related patterns and antipatterns. They are described in a new book [Smith and Williams 2001].。
