Regularization networks and support vector machines
(中英对照)网络空间命运共同体-政府报告参考译文-任务篮子话题积累第一次汉译英练习

(中英对照)网络空间命运共同体-政府报告参考译文-任务篮子话题积累第一次汉译英练习高斋翻译TransElegant整理的CATTI和MTI备考资料网络空间是人类共同的活动空间,网络空间前途命运应由世界各国共同掌握。
各国应该加强沟通、扩大共识、深化合作,共同构建网络空间命运共同体。
这一段时间以来,我非常愿意使用“命运共同体”这个词。
对此,我愿提出5点主张。
Cyberspace is a common space of activities for mankind. The future of cyberspace should be in the hands of all countries. Countries should step up communications, broaden consensus and deepen cooperation to jointly build a community of shared future in cyberspace. Recently, I have used this phrase “Community of shared future” on quite a number of occasions. To this end, I wish to put forward five proposals.第一,加快全球网络基础设施建设,促进互联互通。
网络的本质在于互联,信息的价值在于互通。
只有加强信息基础设施建设,铺就信息畅通之路,不断缩小不同国家、地区、人群间的信息鸿沟,才能让信息资源充分涌流。
中国正在实施“宽带中国”战略,预计到2020年,中国宽带网络将基本覆盖所有农村,打通网络基础设施“最后一公里”,让更多人用上互联网。
中国愿同各方一道,加大资金投入,加强技术支持,共同推动全球网络基础设施建设,让更多发展中国家和人民共享互联网带来的发展机遇。
深度学习系列(11):神经网络防止过拟合的方法

过拟合(overfitting )是指在模型参数拟合过程中的问题,由于训练数据包含抽样误差,训练时,复杂的模型将抽样误差也考虑在内,将抽样误差也进⾏行行了了很好的拟合。
具体表现就是最终模型在训练集上效果好,⽽而在测试集上的效果很差,模型的泛化能⼒力力⽐比较弱。
那为什什么要解决过拟合现象呢?这是因为我们拟合的模型⼀一般是⽤用来预测未知的结果(不不在训练集内),过你个虽然在训练集上效果很好,但在实际使⽤用时(测试集)效果很差。
同时,在很多问题上,我们⽆无法穷尽所以状态,不不可能将所有情况都包含在训练集上。
所以,必须要解决过拟合问题。
之所以过拟合在机器器学习中⽐比较常⻅见,就是因为机器器学习算法为了了满⾜足尽可能复杂的任务,其模型的拟合能⼒力力⼀一般远远⾼高于问题复杂度,也就是说,机器器学习算法有“拟合出正确规则的前提下,进⼀一步拟合噪声”的能⼒力力。
过拟合主要是有两个原因造成的:数据太少+模型太复杂。
所以,我们可以通过使⽤用合适复杂度的模型来防⽌止过拟合问题,让其⾜足够拟合真正的规则,同时⼜又不不⾄至于拟合太多抽样误差。
深度学习系列列(11):神经⽹网络防⽌止过拟合的⽅方法通过上图可以看出,随着模型训练的进⾏行行,模型的复杂度会增加,此时模型在训练数据集上的训练误差会逐渐减⼩小,但是在模型的复杂度达到⼀一定程度时,模型在验证集上的误差反⽽而随着模型的复杂度增加⽽而增⼤大。
此时便便发⽣生了了过拟合,即模型的复杂度升⾼高,但是该模型在除训练集之外的数据集上却不不work。
为了了防⽌止过拟合,我们需要⽤用到⼀一些⽅方法,如下所示:⼀一、获取更更多的数据所有的过拟合⽆无⾮非就是训练样本的缺乏和训练参数的增加。
⼀一般要想获得更更好的模型,需要⼤大量量的训练参数,这也是为什什么CNN⽹网络越来越深的原因之⼀一,⽽而如果训练样本缺乏多样性,那再多的训练参数也毫⽆无意义,因为这造成了了过拟合,训练的模型泛化能⼒力力相应也会很差。
deep learning英语作文

deep learning英语作文篇1Deep learning is an amazing and revolutionary field that has transformed the way we think about technology and problem-solving! It's like a magic key that unlocks countless possibilities. So, what exactly is deep learning? Well, it's a branch of artificial intelligence that involves training complex neural networks to learn and make predictions based on large amounts of data. Let's take the example of self-driving cars. How do they navigate the roads safely and recognize traffic signals? It's all thanks to deep learning! The system is trained on countless images and data related to roads and traffic, enabling it to make split-second decisions. Or think about image recognition software. How can it accurately distinguish between different objects? Again, deep learning plays a crucial role. It analyzes patterns and features in the images, allowing it to classify and identify with astonishing accuracy. Isn't it mind-blowing? Deep learning is not just a buzzword; it's a powerful tool that is changing our lives in so many ways. It makes us wonder what else it will enable us to achieve in the future. The potential is truly limitless!篇2Deep learning is undoubtedly one of the most revolutionary technologies of our time! How will it shape the future of our society? Let'sexplore this fascinating topic.In the field of healthcare, deep learning has brought about remarkable changes. It can analyze vast amounts of medical data with astonishing accuracy, helping doctors diagnose diseases that were once difficult to identify. Isn't this a huge leap forward? But wait, there are also challenges. For instance, the widespread application of deep learning could lead to significant changes in the employment structure. Many routine jobs might be replaced by automated systems based on this technology. Will this cause widespread unemployment? That's a big question mark!However, we should not be overly pessimistic. New opportunities will arise. People can focus on more creative and strategic roles that require human intelligence and emotional intelligence. Isn't it exciting to think about the potential for innovation and progress that deep learning can bring?In conclusion, deep learning holds both great promise and potential challenges for the future of our society. How we navigate and adapt to these changes will determine whether we can fully leverage its benefits and minimize the negative impacts. So, let's embrace this technological wave with optimism and caution!篇3When I embarked on the journey of learning deep learning, it was like stepping into a vast and mysterious forest. At the beginning, I was completely lost and confused. The complex theories and algorithmsseemed like an insurmountable mountain in front of me! How could I understand them? But I didn't give up. I spent countless hours reading books and online materials, trying to make sense of this challenging field.There were times when I faced problems that made me want to throw in the towel. For instance, when dealing with neural networks and backpropagation, I just couldn't get it right. However, I kept telling myself, "I mustn't give up! I can do this!" And so, I sought help from online forums and asked for advice from experts. Little by little, I started to see the light.When I finally solved those difficult problems and saw my progress, oh my goodness, the joy in my heart was indescribable! It was like finding a precious treasure. I realized that as long as I persisted and was willing to learn, nothing could stop me. Now, looking back on this journey, I'm so glad that I had the courage and determination to keep going. Deep learning has not only broadened my knowledge but also taught me the value of perseverance.篇4Deep learning has emerged as a revolutionary force in the field of artificial intelligence! How significant is it? Well, let's take a look. Consider the common voice assistants we use daily. They can understand our speech and respond accurately, all thanks to deep learning. Through complex neural networks, these systems learn to recognize patterns in human language and provide useful answers. Isn't that amazing? Anothergreat example is the recommendation systems. They use deep learning to analyze our preferences and behaviors. How? By processing vast amounts of data, they can suggest products, movies, or music that are tailored just for us. This personalized service has transformed our online experiences. But it doesn't stop there! In healthcare, deep learning helps diagnose diseases more accurately. In finance, it predicts market trends. The list goes on and on. So, it's clear that deep learning is not just an important part of artificial intelligence, it's the key that unlocks countless possibilities and innovations. How can we not be excited about its potential?篇5Deep learning has emerged as a revolutionary force in the field of technology, but it is not without its challenges! One significant concern is the issue of data privacy. In the process of deep learning, vast amounts of data are collected and analyzed. How can we ensure that this data remains confidential and protected? It's a crucial question that demands immediate attention. Another challenge is the overfitting phenomenon of deep learning models. Sometimes, these models become too tailored to the training data, resulting in poor generalization to new, unseen data. So, what can be done to address this? Well, one possible solution could be to increase the size and diversity of the training dataset. Additionally, regularization techniques such as L1 and L2 regularization can be employed to prevent overfitting. Moreover, early stopping during the training process can alsohelp. Isn't it fascinating how we need to constantly think and innovate to overcome these hurdles? The future of deep learning depends on our ability to find effective solutions to these challenges. Let's keep exploring and working towards a more advanced and reliable deep learning landscape!。
support-vecttor+networks-翻译

支持向量网络Corinna Cortes and Vladimir VapnikAT&T Labs-Research, USA摘要. 支持向量网络是一种针对两类问题的新学习机器.它的实现基于以下思想:将输入向量非线性地映射到一个很高维的特征空间.并在该特征空间中构造一个线性决策平面.该决策平面的特殊性质保证了学习机器具有很好的推广能力.支持向量网络的思想已在完全可分的训练数据集上得以实现,这里我们将它扩展到不完全可分的训练数据集.利用多项式输入变换的支持向量网络被证明具有很好的推广能力.我们以光学字体识别为实验将支持向量网络和其他不同的经典学习算法进行了性能比较.关键词:模式识别, 有效的学习算法, 神经网路, 径向基函数分类器, 多项式分类器1 介绍60多年前,R.A.Fisher[7]提出了模式识别领域的第一个算法.该模型考虑n 维向量x 正态分布N(m 1,∑1)和N(m 2,∑2), m 1 和m 2为各个分布的均值向量, ∑1和∑2为各个分布的协方差矩阵,并给出最优解为如下二次决策函数:2111112221|11||()[()()()()ln ]22|T T sq F x sign x m x m x m x m --∑=-∑---∑-+∑ . (1) 当∑1 = ∑2 = ∑时该二次决策函数(1)退化为一个线性函数:1111211221()[()()]2T T T lin F x sign m m x m m m m ---=-∑-∑-∑ . (2) 评估二次决策函数需要确定n(n+3)/2个自由参数,而评估线性函数只需要n 个自由参数.在观测数目较小(小于10n 2)的情况下评估O(n 2)个参数是不可靠的.Fisher 因此提出以下建议,在∑1 ≠∑2 时也采用线性判别函数(2),其中的∑采用如下形式:12(1)ττ∑=∑+-∑ , (3) 这里τ是某个常数.Fisher 也对两个非正态分布的线性决策函数给出了建议.因此模式识别的算法最开始是和构建线性决策平面相关联的.1962年,Rosenblatt[11]提出了一种不同的学习机器:感知器(或神经网络).感知器由相关联的神经元构成,每个神经元实现一个分类超平面,因此整个感知器完成了一个分段线性分类平面.如图1.Fig 1: A simple feed-forward perceptron with 8 input units, 2 layers of hidden units, and 1 output unit. The gray-shading of the Vector entries reflects their numeric value.Rosenblatt 没有提出通过调整网络的所有权值来最小化向量集上误差的算法,而提出了一种自适应仅仅改变输出节点上的权值的方法.由于其他权值都是固定的,输入向量被非线性地映射到最后一层节点的特征空间Z.在该空间的线性决策函数如下:()(())i iiI x sign z x α=∑ (4) 通过调整第i 个节点到输出节点的权值i α来最小化定义在训练集上的某种误差.Rosenblatt 的方法,再次将构建决策规则归结为构造某个空间的线性超平面.1986年,针对模式识别问题出现了通过调整神经网络所有权值来局部最小化向量集上误差的算法[12,13,10,8],即后向传播算法.算法对神经网络的数学模型有微小的改动.至此,神经网络实现了分段线性决策函数.本文提出了一种全新的学习机器,支持向量网络.它基于以下思想:通过事先选择的非线性映射将输入向量映射到一个高维特征空间Z.在空间Z 里构建一个线性决策面,该决策面的一些性质保证支持向量网络具有好的推广能力.例如:要构造一个与二阶多项式对应的决策面,我们可以构造一个特征空间Z,它有如下的N=n(n+3)/2个坐标:11,,n n z x z x == , n coordinates,22112,,n n n z x z x +== , n coordinates,21121,,n N n n z x x z x x +-== , n(n-1)/2 coordinates ,其中,x = 1(,,)n x x .分类超平面便是在该空间中构造的.以上方法存在两个问题:一个是概念上的,另一个是技术上的.(1)概念上的问题:怎样找到一个推广性很好的分类超平面?特征空间的维数将会很高,能将数据分开的超平面不一定都具有很好的推广性.(2)技术上的问题:怎样在计算上处理如此高维的空间?要在一个200维的空间中构建一个4或5阶的多项式,需要构造一个上十亿的特征空间.概念上的问题在1965年[14]通过完全可分情况下的最优超平面得以解决.最优超平面是指使两类向量具有最大间隔的线性决策函数,如图2所示.可以发现,构造最优超平面只需考虑训练集中决定分类隔间的少量数据,即所谓的支持向量.如果训练集被最优超平面完全无错地分开,则一个测试样例被错判的期望概率以支持向量的期望数目与训练集向量数目比值为上界,即: [number of support vectors][Pr()]number of training vectorsE E error ≤. (5) 注意,这个界与分类空间的维数无关.并且由此可知,如果支持向量的个数相对与整个训练集很小,则构建出来的分类超平面将具有很好的推广性,即便是在一个无限维空间.第5节中,通过实际问题我们验证了比值(5)能够小到0.03而相应的最优超平面在一个十亿的特征空间依然具有很好的推广能力.Fig 2. An example of a separable problem in a 2 dimensional space. The support vectors, marked with grey squares, define the margin of largest separation between the two classes.令000b ⋅+=w z为特征空间里的最优超平面.我们将看到,特征空间中最优超平面的权值0w 可以写成支持向量的某个线性组合0support vectors i i α=∑w z . (6)从而特征空间里的线性决策函数I(z )为如下形式:0support vectors ()sign()i i I b α=⋅+∑z z z , (7)其中i z ⋅z 表示支持向量i z 和向量z 在特征空间里的内积.因此,该决策函数可以通过一个两层的网络来描述.如图3.尽管最优超平面保证了好的推广性,但如何处理高维特征空间这个技术上的问题依然存在.1992年,在文献[3]中证明构造决策函数的步骤可以交换顺序:不必先将输入向量通过某种非线性变换映射到特征空间再与特征空间中的支持向量做内积;而可以先在输入空间通过内积或者某种别的距离进行比较,再对比较的值进行非线性变化.如图4.这就允许我们构造足够好的分类决策面,比如任意精度的多项式决策面.称这种类型的学习机器为支持向量网络.支持向量网络的技术首先针对能够完全无错地分开的数据集.本文我们将支持向量网络推广到不能完全无错分类的数据集.通过该扩展,作为一种全新的学习机器的支持向量网络将和神经网络一样的强大和通用.第5节将展示它在256维的高维空间中针对高达7阶的多项式决策面的推广性.并将它和其他经典的算法比如线性分类器、k 近邻分类器和神经网络做了性能上的比较.第2、3、4节着重引出算法并讨论了算法的一些性质.算法的一些重要细节参见附录.Fig 3. Classification by a support-vector network of an unknown pattern is conceptually done by first transforming the pattern into some high-dimensional feature space. An optimal hyperplane constructed in this feature space determines the output. The similarity to a two-layer perceptron can be seen by comparison to Fig 1.Fig 4. Classification of an unknown pattern by a support-vector network. The pattern is in input space compared to support vectors. The resulting values are non-linearly transformed. A linear function of these transformed values determines the output of the classifier.2 最优超平面本节回顾文献[14]中针对能被完全无错分开的训练数据的最优超平面方法.下一节介绍软间隔的概念,用来处理训练集不完全可分情况下的学习问题.2.1 最优超平面算法训练样本集11(,),,(,)l l y y x x , {1,1}i y ∈- (8) 是线性可分的。
人工智能词汇

常用英语词汇 -andrew Ng课程average firing rate均匀激活率intensity强度average sum-of-squares error均方差Regression回归backpropagation后向流传Loss function损失函数basis 基non-convex非凸函数basis feature vectors特点基向量neural network神经网络batch gradient ascent批量梯度上涨法supervised learning监察学习Bayesian regularization method贝叶斯规则化方法regression problem回归问题办理的是连续的问题Bernoulli random variable伯努利随机变量classification problem分类问题bias term偏置项discreet value失散值binary classfication二元分类support vector machines支持向量机class labels种类标记learning theory学习理论concatenation级联learning algorithms学习算法conjugate gradient共轭梯度unsupervised learning无监察学习contiguous groups联通地区gradient descent梯度降落convex optimization software凸优化软件linear regression线性回归convolution卷积Neural Network神经网络cost function代价函数gradient descent梯度降落covariance matrix协方差矩阵normal equations DC component直流重量linear algebra线性代数decorrelation去有关superscript上标degeneracy退化exponentiation指数demensionality reduction降维training set训练会合derivative导函数training example训练样本diagonal对角线hypothesis假定,用来表示学习算法的输出diffusion of gradients梯度的弥散LMS algorithm “least mean squares最小二乘法算eigenvalue特点值法eigenvector特点向量batch gradient descent批量梯度降落error term残差constantly gradient descent随机梯度降落feature matrix特点矩阵iterative algorithm迭代算法feature standardization特点标准化partial derivative偏导数feedforward architectures前馈构造算法contour等高线feedforward neural network前馈神经网络quadratic function二元函数feedforward pass前馈传导locally weighted regression局部加权回归fine-tuned微调underfitting欠拟合first-order feature一阶特点overfitting过拟合forward pass前向传导non-parametric learning algorithms无参数学习算forward propagation前向流传法Gaussian prior高斯先验概率parametric learning algorithm参数学习算法generative model生成模型activation激活值gradient descent梯度降落activation function激活函数Greedy layer-wise training逐层贪心训练方法additive noise加性噪声grouping matrix分组矩阵autoencoder自编码器Hadamard product阿达马乘积Autoencoders自编码算法Hessian matrix Hessian矩阵hidden layer隐含层hidden units隐蔽神经元Hierarchical grouping层次型分组higher-order features更高阶特点highly non-convex optimization problem高度非凸的优化问题histogram直方图hyperbolic tangent双曲正切函数hypothesis估值,假定identity activation function恒等激励函数IID 独立同散布illumination照明inactive克制independent component analysis独立成份剖析input domains输入域input layer输入层intensity亮度/灰度intercept term截距KL divergence相对熵KL divergence KL分别度k-Means K-均值learning rate学习速率least squares最小二乘法linear correspondence线性响应linear superposition线性叠加line-search algorithm线搜寻算法local mean subtraction局部均值消减local optima局部最优解logistic regression逻辑回归loss function损失函数low-pass filtering低通滤波magnitude幅值MAP 极大后验预计maximum likelihood estimation极大似然预计mean 均匀值MFCC Mel 倒频系数multi-class classification多元分类neural networks神经网络neuron 神经元Newton’s method牛顿法non-convex function非凸函数non-linear feature非线性特点norm 范式norm bounded有界范数norm constrained范数拘束normalization归一化numerical roundoff errors数值舍入偏差numerically checking数值查验numerically reliable数值计算上稳固object detection物体检测objective function目标函数off-by-one error缺位错误orthogonalization正交化output layer输出层overall cost function整体代价函数over-complete basis超齐备基over-fitting过拟合parts of objects目标的零件part-whole decompostion部分-整体分解PCA 主元剖析penalty term处罚因子per-example mean subtraction逐样本均值消减pooling池化pretrain预训练principal components analysis主成份剖析quadratic constraints二次拘束RBMs 受限 Boltzman 机reconstruction based models鉴于重构的模型reconstruction cost重修代价reconstruction term重构项redundant冗余reflection matrix反射矩阵regularization正则化regularization term正则化项rescaling缩放robust 鲁棒性run 行程second-order feature二阶特点sigmoid activation function S型激励函数significant digits有效数字singular value奇怪值singular vector奇怪向量smoothed L1 penalty光滑的L1 范数处罚Smoothed topographic L1 sparsity penalty光滑地形L1 稀少处罚函数smoothing光滑Softmax Regresson Softmax回归sorted in decreasing order降序摆列source features源特点Adversarial Networks抗衡网络sparse autoencoder消减归一化Affine Layer仿射层Sparsity稀少性Affinity matrix亲和矩阵sparsity parameter稀少性参数Agent 代理 /智能体sparsity penalty稀少处罚Algorithm 算法square function平方函数Alpha- beta pruningα - β剪枝squared-error方差Anomaly detection异样检测stationary安稳性(不变性)Approximation近似stationary stochastic process安稳随机过程Area Under ROC Curve/ AUC Roc 曲线下边积step-size步长值Artificial General Intelligence/AGI通用人工智supervised learning监察学习能symmetric positive semi-definite matrix Artificial Intelligence/AI人工智能对称半正定矩阵Association analysis关系剖析symmetry breaking对称无效Attention mechanism注意力体制tanh function双曲正切函数Attribute conditional independence assumptionthe average activation均匀活跃度属性条件独立性假定the derivative checking method梯度考证方法Attribute space属性空间the empirical distribution经验散布函数Attribute value属性值the energy function能量函数Autoencoder自编码器the Lagrange dual拉格朗日对偶函数Automatic speech recognition自动语音辨别the log likelihood对数似然函数Automatic summarization自动纲要the pixel intensity value像素灰度值Average gradient均匀梯度the rate of convergence收敛速度Average-Pooling均匀池化topographic cost term拓扑代价项Backpropagation Through Time经过时间的反向流传topographic ordered拓扑次序Backpropagation/BP反向流传transformation变换Base learner基学习器translation invariant平移不变性Base learning algorithm基学习算法trivial answer平庸解Batch Normalization/BN批量归一化under-complete basis不齐备基Bayes decision rule贝叶斯判断准则unrolling组合扩展Bayes Model Averaging/ BMA 贝叶斯模型均匀unsupervised learning无监察学习Bayes optimal classifier贝叶斯最优分类器variance 方差Bayesian decision theory贝叶斯决议论vecotrized implementation向量化实现Bayesian network贝叶斯网络vectorization矢量化Between-class scatter matrix类间散度矩阵visual cortex视觉皮层Bias 偏置 /偏差weight decay权重衰减Bias-variance decomposition偏差 - 方差分解weighted average加权均匀值Bias-Variance Dilemma偏差–方差窘境whitening白化Bi-directional Long-Short Term Memory/Bi-LSTMzero-mean均值为零双向长短期记忆Accumulated error backpropagation积累偏差逆传Binary classification二分类播Binomial test二项查验Activation Function激活函数Bi-partition二分法Adaptive Resonance Theory/ART自适应谐振理论Boltzmann machine玻尔兹曼机Addictive model加性学习Bootstrap sampling自助采样法/可重复采样Bootstrapping自助法Break-Event Point/ BEP 均衡点Calibration校准Cascade-Correlation级联有关Categorical attribute失散属性Class-conditional probability类条件概率Classification and regression tree/CART分类与回归树Classifier分类器Class-imbalance类型不均衡Closed -form闭式Cluster簇/ 类/ 集群Cluster analysis聚类剖析Clustering聚类Clustering ensemble聚类集成Co-adapting共适应Coding matrix编码矩阵COLT 国际学习理论会议Committee-based learning鉴于委员会的学习Competitive learning竞争型学习Component learner组件学习器Comprehensibility可解说性Computation Cost计算成本Computational Linguistics计算语言学Computer vision计算机视觉Concept drift观点漂移Concept Learning System /CLS观点学习系统Conditional entropy条件熵Conditional mutual information条件互信息Conditional Probability Table/ CPT 条件概率表Conditional random field/CRF条件随机场Conditional risk条件风险Confidence置信度Confusion matrix混杂矩阵Connection weight连结权Connectionism 连结主义Consistency一致性/相合性Contingency table列联表Continuous attribute连续属性Convergence收敛Conversational agent会话智能体Convex quadratic programming凸二次规划Convexity凸性Convolutional neural network/CNN卷积神经网络Co-occurrence同现Correlation coefficient有关系数Cosine similarity余弦相像度Cost curve成本曲线Cost Function成本函数Cost matrix成本矩阵Cost-sensitive成本敏感Cross entropy交错熵Cross validation交错考证Crowdsourcing众包Curse of dimensionality维数灾害Cut point截断点Cutting plane algorithm割平面法Data mining数据发掘Data set数据集Decision Boundary决议界限Decision stump决议树桩Decision tree决议树/判断树Deduction演绎Deep Belief Network深度信念网络Deep Convolutional Generative Adversarial NetworkDCGAN深度卷积生成抗衡网络Deep learning深度学习Deep neural network/DNN深度神经网络Deep Q-Learning深度Q 学习Deep Q-Network深度Q 网络Density estimation密度预计Density-based clustering密度聚类Differentiable neural computer可微分神经计算机Dimensionality reduction algorithm降维算法Directed edge有向边Disagreement measure不合胸怀Discriminative model鉴别模型Discriminator鉴别器Distance measure距离胸怀Distance metric learning距离胸怀学习Distribution散布Divergence散度Diversity measure多样性胸怀/差别性胸怀Domain adaption领域自适应Downsampling下采样D-separation( Directed separation)有向分别Dual problem对偶问题Dummy node 哑结点General Problem Solving通用问题求解Dynamic Fusion 动向交融Generalization泛化Dynamic programming动向规划Generalization error泛化偏差Eigenvalue decomposition特点值分解Generalization error bound泛化偏差上界Embedding 嵌入Generalized Lagrange function广义拉格朗日函数Emotional analysis情绪剖析Generalized linear model广义线性模型Empirical conditional entropy经验条件熵Generalized Rayleigh quotient广义瑞利商Empirical entropy经验熵Generative Adversarial Networks/GAN生成抗衡网Empirical error经验偏差络Empirical risk经验风险Generative Model生成模型End-to-End 端到端Generator生成器Energy-based model鉴于能量的模型Genetic Algorithm/GA遗传算法Ensemble learning集成学习Gibbs sampling吉布斯采样Ensemble pruning集成修剪Gini index基尼指数Error Correcting Output Codes/ ECOC纠错输出码Global minimum全局最小Error rate错误率Global Optimization全局优化Error-ambiguity decomposition偏差 - 分歧分解Gradient boosting梯度提高Euclidean distance欧氏距离Gradient Descent梯度降落Evolutionary computation演化计算Graph theory图论Expectation-Maximization希望最大化Ground-truth实情/真切Expected loss希望损失Hard margin硬间隔Exploding Gradient Problem梯度爆炸问题Hard voting硬投票Exponential loss function指数损失函数Harmonic mean 调解均匀Extreme Learning Machine/ELM超限学习机Hesse matrix海塞矩阵Factorization因子分解Hidden dynamic model隐动向模型False negative假负类Hidden layer隐蔽层False positive假正类Hidden Markov Model/HMM 隐马尔可夫模型False Positive Rate/FPR假正例率Hierarchical clustering层次聚类Feature engineering特点工程Hilbert space希尔伯特空间Feature selection特点选择Hinge loss function合页损失函数Feature vector特点向量Hold-out 留出法Featured Learning特点学习Homogeneous 同质Feedforward Neural Networks/FNN前馈神经网络Hybrid computing混杂计算Fine-tuning微调Hyperparameter超参数Flipping output翻转法Hypothesis假定Fluctuation震荡Hypothesis test假定考证Forward stagewise algorithm前向分步算法ICML 国际机器学习会议Frequentist频次主义学派Improved iterative scaling/IIS改良的迭代尺度法Full-rank matrix满秩矩阵Incremental learning增量学习Functional neuron功能神经元Independent and identically distributed/独Gain ratio增益率立同散布Game theory博弈论Independent Component Analysis/ICA独立成分剖析Gaussian kernel function高斯核函数Indicator function指示函数Gaussian Mixture Model高斯混杂模型Individual learner个体学习器Induction归纳Inductive bias归纳偏好Inductive learning归纳学习Inductive Logic Programming/ ILP归纳逻辑程序设计Information entropy信息熵Information gain信息增益Input layer输入层Insensitive loss不敏感损失Inter-cluster similarity簇间相像度International Conference for Machine Learning/ICML国际机器学习大会Intra-cluster similarity簇内相像度Intrinsic value固有值Isometric Mapping/Isomap等胸怀映照Isotonic regression平分回归Iterative Dichotomiser迭代二分器Kernel method核方法Kernel trick核技巧Kernelized Linear Discriminant Analysis/KLDA核线性鉴别剖析K-fold cross validation k折交错考证/k 倍交错考证K-Means Clustering K–均值聚类K-Nearest Neighbours Algorithm/KNN K近邻算法Knowledge base 知识库Knowledge Representation知识表征Label space标记空间Lagrange duality拉格朗日对偶性Lagrange multiplier拉格朗日乘子Laplace smoothing拉普拉斯光滑Laplacian correction拉普拉斯修正Latent Dirichlet Allocation隐狄利克雷散布Latent semantic analysis潜伏语义剖析Latent variable隐变量Lazy learning懒散学习Learner学习器Learning by analogy类比学习Learning rate学习率Learning Vector Quantization/LVQ学习向量量化Least squares regression tree最小二乘回归树Leave-One-Out/LOO留一法linear chain conditional random field线性链条件随机场Linear Discriminant Analysis/ LDA 线性鉴别剖析Linear model线性模型Linear Regression线性回归Link function联系函数Local Markov property局部马尔可夫性Local minimum局部最小Log likelihood对数似然Log odds/ logit对数几率Logistic Regression Logistic回归Log-likelihood对数似然Log-linear regression对数线性回归Long-Short Term Memory/LSTM 长短期记忆Loss function损失函数Machine translation/MT机器翻译Macron-P宏查准率Macron-R宏查全率Majority voting绝对多半投票法Manifold assumption流形假定Manifold learning流形学习Margin theory间隔理论Marginal distribution边沿散布Marginal independence边沿独立性Marginalization边沿化Markov Chain Monte Carlo/MCMC马尔可夫链蒙特卡罗方法Markov Random Field马尔可夫随机场Maximal clique最大团Maximum Likelihood Estimation/MLE极大似然预计/极大似然法Maximum margin最大间隔Maximum weighted spanning tree最大带权生成树Max-Pooling 最大池化Mean squared error均方偏差Meta-learner元学习器Metric learning胸怀学习Micro-P微查准率Micro-R微查全率Minimal Description Length/MDL最小描绘长度Minimax game极小极大博弈Misclassification cost误分类成本Mixture of experts混杂专家Momentum 动量Moral graph道德图/正直图Multi-class classification多分类Multi-document summarization多文档纲要One shot learning一次性学习Multi-layer feedforward neural networks One-Dependent Estimator/ ODE 独依靠预计多层前馈神经网络On-Policy在策略Multilayer Perceptron/MLP多层感知器Ordinal attribute有序属性Multimodal learning多模态学习Out-of-bag estimate包外预计Multiple Dimensional Scaling多维缩放Output layer输出层Multiple linear regression多元线性回归Output smearing输出调制法Multi-response Linear Regression/ MLR Overfitting过拟合/过配多响应线性回归Oversampling 过采样Mutual information互信息Paired t-test成对 t查验Naive bayes 朴实贝叶斯Pairwise 成对型Naive Bayes Classifier朴实贝叶斯分类器Pairwise Markov property成对马尔可夫性Named entity recognition命名实体辨别Parameter参数Nash equilibrium纳什均衡Parameter estimation参数预计Natural language generation/NLG自然语言生成Parameter tuning调参Natural language processing自然语言办理Parse tree分析树Negative class负类Particle Swarm Optimization/PSO粒子群优化算法Negative correlation负有关法Part-of-speech tagging词性标明Negative Log Likelihood负对数似然Perceptron感知机Neighbourhood Component Analysis/NCA Performance measure性能胸怀近邻成分剖析Plug and Play Generative Network即插即用生成网Neural Machine Translation神经机器翻译络Neural Turing Machine神经图灵机Plurality voting相对多半投票法Newton method牛顿法Polarity detection极性检测NIPS 国际神经信息办理系统会议Polynomial kernel function多项式核函数No Free Lunch Theorem/ NFL 没有免费的午饭定理Pooling池化Noise-contrastive estimation噪音对照预计Positive class正类Nominal attribute列名属性Positive definite matrix正定矩阵Non-convex optimization非凸优化Post-hoc test后续查验Nonlinear model非线性模型Post-pruning后剪枝Non-metric distance非胸怀距离potential function势函数Non-negative matrix factorization非负矩阵分解Precision查准率/正确率Non-ordinal attribute无序属性Prepruning 预剪枝Non-Saturating Game非饱和博弈Principal component analysis/PCA主成分剖析Norm 范数Principle of multiple explanations多释原则Normalization归一化Prior 先验Nuclear norm核范数Probability Graphical Model概率图模型Numerical attribute数值属性Proximal Gradient Descent/PGD近端梯度降落Letter O Pruning剪枝Objective function目标函数Pseudo-label伪标记Oblique decision tree斜决议树Quantized Neural Network量子化神经网络Occam’s razor奥卡姆剃刀Quantum computer 量子计算机Odds 几率Quantum Computing量子计算Off-Policy离策略Quasi Newton method拟牛顿法Radial Basis Function/ RBF 径向基函数Random Forest Algorithm随机丛林算法Random walk随机闲步Recall 查全率/召回率Receiver Operating Characteristic/ROC受试者工作特点Rectified Linear Unit/ReLU线性修正单元Recurrent Neural Network循环神经网络Recursive neural network递归神经网络Reference model 参照模型Regression回归Regularization正则化Reinforcement learning/RL加强学习Representation learning表征学习Representer theorem表示定理reproducing kernel Hilbert space/RKHS重生核希尔伯特空间Re-sampling重采样法Rescaling再缩放Residual Mapping残差映照Residual Network残差网络Restricted Boltzmann Machine/RBM受限玻尔兹曼机Restricted Isometry Property/RIP限制等距性Re-weighting重赋权法Robustness稳重性 / 鲁棒性Root node根结点Rule Engine规则引擎Rule learning规则学习Saddle point鞍点Sample space样本空间Sampling采样Score function评分函数Self-Driving自动驾驶Self-Organizing Map/ SOM自组织映照Semi-naive Bayes classifiers半朴实贝叶斯分类器Semi-Supervised Learning半监察学习semi-Supervised Support Vector Machine半监察支持向量机Sentiment analysis感情剖析Separating hyperplane分别超平面Sigmoid function Sigmoid函数Similarity measure相像度胸怀Simulated annealing模拟退火Simultaneous localization and mapping同步定位与地图建立Singular Value Decomposition奇怪值分解Slack variables废弛变量Smoothing光滑Soft margin软间隔Soft margin maximization软间隔最大化Soft voting软投票Sparse representation稀少表征Sparsity稀少性Specialization特化Spectral Clustering谱聚类Speech Recognition语音辨别Splitting variable切分变量Squashing function挤压函数Stability-plasticity dilemma可塑性 - 稳固性窘境Statistical learning统计学习Status feature function状态特点函Stochastic gradient descent随机梯度降落Stratified sampling分层采样Structural risk构造风险Structural risk minimization/SRM构造风险最小化Subspace子空间Supervised learning监察学习/有导师学习support vector expansion支持向量展式Support Vector Machine/SVM支持向量机Surrogat loss代替损失Surrogate function代替函数Symbolic learning符号学习Symbolism符号主义Synset同义词集T-Distribution Stochastic Neighbour Embeddingt-SNE T–散布随机近邻嵌入Tensor 张量Tensor Processing Units/TPU张量办理单元The least square method最小二乘法Threshold阈值Threshold logic unit阈值逻辑单元Threshold-moving阈值挪动Time Step时间步骤Tokenization标记化Training error训练偏差Training instance训练示例/训练例Transductive learning直推学习Transfer learning迁徙学习Treebank树库algebra线性代数Tria-by-error试错法asymptotically无症状的True negative真负类appropriate适合的True positive真切类bias 偏差True Positive Rate/TPR真切例率brevity简洁,简洁;短暂Turing Machine图灵机[800 ] broader宽泛Twice-learning二次学习briefly简洁的Underfitting欠拟合/欠配batch 批量Undersampling欠采样convergence收敛,集中到一点Understandability可理解性convex凸的Unequal cost非均等代价contours轮廓Unit-step function单位阶跃函数constraint拘束Univariate decision tree单变量决议树constant常理Unsupervised learning无监察学习/无导师学习commercial商务的Unsupervised layer-wise training无监察逐层训练complementarity增补Upsampling上采样coordinate ascent同样级上涨Vanishing Gradient Problem梯度消逝问题clipping剪下物;剪报;修剪Variational inference变分推测component重量;零件VC Theory VC维理论continuous连续的Version space版本空间covariance协方差Viterbi algorithm维特比算法canonical正规的,正则的Von Neumann architecture冯· 诺伊曼架构concave非凸的Wasserstein GAN/WGAN Wasserstein生成抗衡网络corresponds相切合;相当;通讯Weak learner弱学习器corollary推论Weight权重concrete详细的事物,实在的东西Weight sharing权共享cross validation交错考证Weighted voting加权投票法correlation互相关系Within-class scatter matrix类内散度矩阵convention商定Word embedding词嵌入cluster一簇Word sense disambiguation词义消歧centroids质心,形心Zero-data learning零数据学习converge收敛Zero-shot learning零次学习computationally计算(机)的approximations近似值calculus计算arbitrary任意的derive获取,获得affine仿射的dual 二元的arbitrary任意的duality二元性;二象性;对偶性amino acid氨基酸derivation求导;获取;发源amenable 经得起查验的denote预示,表示,是的标记;意味着,[逻]指称axiom 公义,原则divergence散度;发散性abstract提取dimension尺度,规格;维数architecture架构,系统构造;建筑业dot 小圆点absolute绝对的distortion变形arsenal军械库density概率密度函数assignment分派discrete失散的人工智能词汇discriminative有辨别能力的indicator指示物,指示器diagonal对角interative重复的,迭代的dispersion分别,散开integral积分determinant决定要素identical相等的;完整同样的disjoint不订交的indicate表示,指出encounter碰到invariance不变性,恒定性ellipses椭圆impose把强加于equality等式intermediate中间的extra 额外的interpretation解说,翻译empirical经验;察看joint distribution结合概率ennmerate例举,计数lieu 代替exceed超出,越出logarithmic对数的,用对数表示的expectation希望latent潜伏的efficient奏效的Leave-one-out cross validation留一法交错考证endow 给予magnitude巨大explicitly清楚的mapping 画图,制图;映照exponential family指数家族matrix矩阵equivalently等价的mutual互相的,共同的feasible可行的monotonically单一的forary首次试试minor较小的,次要的finite有限的,限制的multinomial多项的forgo 摒弃,放弃multi-class classification二分类问题fliter过滤nasty厌烦的frequentist最常发生的notation标记,说明forward search前向式搜寻na?ve 朴实的formalize使定形obtain获取generalized归纳的oscillate摇动generalization归纳,归纳;广泛化;判断(依据不optimization problem最优化问题足)objective function目标函数guarantee保证;抵押品optimal最理想的generate形成,产生orthogonal(矢量,矩阵等 ) 正交的geometric margins几何界限orientation方向gap 裂口ordinary一般的generative生产的;有生产力的occasionally有时的heuristic启迪式的;启迪法;启迪程序partial derivative偏导数hone 怀恋;磨property性质hyperplane超平面proportional成比率的initial最先的primal原始的,最先的implement履行permit同意intuitive凭直觉获知的pseudocode 伪代码incremental增添的permissible可同意的intercept截距polynomial多项式intuitious直觉preliminary预备instantiation例子precision精度人工智能词汇perturbation不安,搅乱theorem定理poist 假定,假想tangent正弦positive semi-definite半正定的unit-length vector单位向量parentheses圆括号valid 有效的,正确的posterior probability后验概率variance方差plementarity增补variable变量;变元pictorially图像的vocabulary 词汇parameterize确立的参数valued经估价的;可贵的poisson distribution柏松散布wrapper 包装pertinent有关的总计 1038 词汇quadratic二次的quantity量,数目;重量query 疑问的regularization使系统化;调整reoptimize从头优化restrict限制;限制;拘束reminiscent回想旧事的;提示的;令人联想的( of )remark 注意random variable随机变量respect考虑respectively各自的;分其他redundant过多的;冗余的susceptible敏感的stochastic可能的;随机的symmetric对称的sophisticated复杂的spurious假的;假造的subtract减去;减法器simultaneously同时发生地;同步地suffice知足scarce罕有的,难得的split分解,分别subset子集statistic统计量successive iteratious连续的迭代scale标度sort of有几分的squares 平方trajectory轨迹temporarily临时的terminology专用名词tolerance容忍;公差thumb翻阅threshold阈,临界。
-bpin结构式 -回复

-bpin结构式-回复Bolivian Power Integration Network: An Analysis of its Structural Design and Implications[Introduction]The Bolivian Power Integration Network, known as BPIN, is a bold venture undertaken by Bolivia to strengthen and improve its power infrastructure. This article aims to delve into the structural design of BPIN, examining its goals, components, and the implications of such an ambitious project. In doing so, we will walk through the creation and implementation of BPIN, dissecting each step to gain a comprehensive understanding of this innovative initiative.[Background and Goals]At its core, BPIN seeks to enhance Bolivia's power sector by improving the efficiency, reliability, and affordability of electricity supply. With its rich natural resources, specifically in the hydroelectric sector, Bolivia aims to leverage its potential as a power exporter to foster economic growth and regional cooperation. This project's goals are two-fold: boost Bolivia'sdomestic power supply and establish cross-border connections for energy exchange with neighboring countries.[Components of BPIN]1. Generation Facilities: The first key component of BPIN lies in the construction and expansion of hydroelectric power plants. These facilities are strategically situated at various locations across Bolivia to harness the potential of its rivers, ensuring a stable and renewable power supply. Notable examples include the San Joséand Rositas hydroelectric projects, which are expected to contribute significantly to BPIN's overall generation capacity.2. Transmission Lines: To facilitate the distribution of electricity generated by the new power plants, BPIN incorporates the installation of a network of high-voltage transmission lines. This complex web allows for efficient and reliable power transmission, connecting the generation facilities to distribution centers and facilitating cross-border energy exchange with neighboring countries. The transmission lines serve as the backbone of BPIN, enabling the project to tap into regional markets.3. Substations and Distribution Networks: As electricity flows through the transmission lines, substations act as intermediaries, ensuring voltage regularization and enabling the transition from high-voltage to low-voltage distribution. In addition to the substations, BPIN also focuses on improving the existing distribution networks to minimize energy losses and optimize the electricity supply to consumers.[Implementation Process]1. Feasibility Studies and Planning: Prior to BPIN's implementation, extensive feasibility studies were conducted to analyze the potential hydroelectric sites and assess their economic viability. This stage involved geological surveys, environmental impact assessments, and cost-benefit analyses. Based on these studies, the project's blueprint was formulated, taking into account technical specifications, financial considerations, and the environmental implications of each development.2. Financing and Partnerships: To fund the ambitious project, Bolivia sought financial assistance from various sources, including national and international development banks, private investors,and bilateral agreements with neighboring countries. These partnerships not only provided the necessary capital for BPIN but also facilitated the connection of Bolivia's grid with those of other countries, enabling energy trade and cross-border collaboration.3. Construction and Commissioning: The construction phase of BPIN involved the simultaneous development of multiple hydroelectric power plants, transmission lines, substations, and distribution networks. Construction sites were carefully selected, considering factors such as proximity to water sources, geological stability, and minimal environmental impact. Upon completion of each component, commissioning tests were conducted to ensure functionality and reliability.4. Operation and Maintenance: As BPIN became operational, a dedicated team was established to oversee its day-to-day operations and maintenance. Regular inspections, maintenance work, and system upgrades are crucial to ensure the longevity and efficiency of BPIN. Diagnostic tools and monitoring systems are employed to detect any technical glitches or performance issues, allowing the team to address them promptly and minimize downtime.[Implications and Future Outlook]BPIN has significant implications for Bolivia's power sector and the wider regional energy landscape. By expanding the country's power generation capacity and establishing cross-border connections, BPIN strengthens Bolivia's position as a regional power player. The project facilitates energy exchange with neighboring countries, fostering economic integration, regional stability, and renewable energy utilization. Moreover, BPIN's improved power infrastructure paves the way for attracting foreign investments, enabling sustainable economic growth in Bolivia.In conclusion, the Bolivian Power Integration Network, with its comprehensive structural design, represents a remarkable initiative aimed at transforming Bolivia's power infrastructure. From hydroelectric power plant construction to the development of transmission lines and distribution networks, BPIN fosters regional integration, renewable energy deployment, and economic growth. While the project's successful implementation requires diligentplanning, efficient financing, and ongoing maintenance, the long-term benefits it offers make BPIN a vital step forward for Bolivia and its aspirations in the power sector.。
机器学习英语词汇

目录第一部分 (3)第二部分 (12)Letter A (12)Letter B (14)Letter C (15)Letter D (17)Letter E (19)Letter F (20)Letter G (21)Letter H (22)Letter I (23)Letter K (24)Letter L (24)Letter M (26)Letter N (27)Letter O (29)Letter P (29)Letter R (31)Letter S (32)Letter T (35)Letter U (36)Letter W (37)Letter Z (37)第三部分 (37)A (37)B (38)C (38)D (40)E (40)F (41)G (41)H (42)L (42)J (43)L (43)M (43)N (44)O (44)P (44)Q (45)R (46)S (46)U (47)V (48)第一部分[ ] intensity 强度[ ] Regression 回归[ ] Loss function 损失函数[ ] non-convex 非凸函数[ ] neural network 神经网络[ ] supervised learning 监督学习[ ] regression problem 回归问题处理的是连续的问题[ ] classification problem 分类问题处理的问题是离散的而不是连续的回归问题和分类问题的区别应该在于回归问题的结果是连续的,分类问题的结果是离散的。
[ ]discreet value 离散值[ ] support vector machines 支持向量机,用来处理分类算法中输入的维度不单一的情况(甚至输入维度为无穷)[ ] learning theory 学习理论[ ] learning algorithms 学习算法[ ] unsupervised learning 无监督学习[ ] gradient descent 梯度下降[ ] linear regression 线性回归[ ] Neural Network 神经网络[ ] gradient descent 梯度下降监督学习的一种算法,用来拟合的算法[ ] normal equations[ ] linear algebra 线性代数原谅我英语不太好[ ] superscript上标[ ] exponentiation 指数[ ] training set 训练集合[ ] training example 训练样本[ ] hypothesis 假设,用来表示学习算法的输出,叫我们不要太纠结H的意思,因为这只是历史的惯例[ ] LMS algorithm “least mean squares” 最小二乘法算法[ ] batch gradient descent 批量梯度下降,因为每次都会计算最小拟合的方差,所以运算慢[ ] constantly gradient descent 字幕组翻译成“随机梯度下降” 我怎么觉得是“常量梯度下降”也就是梯度下降的运算次数不变,一般比批量梯度下降速度快,但是通常不是那么准确[ ] iterative algorithm 迭代算法[ ] partial derivative 偏导数[ ] contour 等高线[ ] quadratic function 二元函数[ ] locally weighted regression局部加权回归[ ] underfitting欠拟合[ ] overfitting 过拟合[ ] non-parametric learning algorithms 无参数学习算法[ ] parametric learning algorithm 参数学习算法[ ] other[ ] activation 激活值[ ] activation function 激活函数[ ] additive noise 加性噪声[ ] autoencoder 自编码器[ ] Autoencoders 自编码算法[ ] average firing rate 平均激活率[ ] average sum-of-squares error 均方差[ ] backpropagation 后向传播[ ] basis 基[ ] basis feature vectors 特征基向量[50 ] batch gradient ascent 批量梯度上升法[ ] Bayesian regularization method 贝叶斯规则化方法[ ] Bernoulli random variable 伯努利随机变量[ ] bias term 偏置项[ ] binary classfication 二元分类[ ] class labels 类型标记[ ] concatenation 级联[ ] conjugate gradient 共轭梯度[ ] contiguous groups 联通区域[ ] convex optimization software 凸优化软件[ ] convolution 卷积[ ] cost function 代价函数[ ] covariance matrix 协方差矩阵[ ] DC component 直流分量[ ] decorrelation 去相关[ ] degeneracy 退化[ ] demensionality reduction 降维[ ] derivative 导函数[ ] diagonal 对角线[ ] diffusion of gradients 梯度的弥散[ ] eigenvalue 特征值[ ] eigenvector 特征向量[ ] error term 残差[ ] feature matrix 特征矩阵[ ] feature standardization 特征标准化[ ] feedforward architectures 前馈结构算法[ ] feedforward neural network 前馈神经网络[ ] feedforward pass 前馈传导[ ] fine-tuned 微调[ ] first-order feature 一阶特征[ ] forward pass 前向传导[ ] forward propagation 前向传播[ ] Gaussian prior 高斯先验概率[ ] generative model 生成模型[ ] gradient descent 梯度下降[ ] Greedy layer-wise training 逐层贪婪训练方法[ ] grouping matrix 分组矩阵[ ] Hadamard product 阿达马乘积[ ] Hessian matrix Hessian 矩阵[ ] hidden layer 隐含层[ ] hidden units 隐藏神经元[ ] Hierarchical grouping 层次型分组[ ] higher-order features 更高阶特征[ ] highly non-convex optimization problem 高度非凸的优化问题[ ] histogram 直方图[ ] hyperbolic tangent 双曲正切函数[ ] hypothesis 估值,假设[ ] identity activation function 恒等激励函数[ ] IID 独立同分布[ ] illumination 照明[100 ] inactive 抑制[ ] independent component analysis 独立成份分析[ ] input domains 输入域[ ] input layer 输入层[ ] intensity 亮度/灰度[ ] intercept term 截距[ ] KL divergence 相对熵[ ] KL divergence KL分散度[ ] k-Means K-均值[ ] learning rate 学习速率[ ] least squares 最小二乘法[ ] linear correspondence 线性响应[ ] linear superposition 线性叠加[ ] line-search algorithm 线搜索算法[ ] local mean subtraction 局部均值消减[ ] local optima 局部最优解[ ] logistic regression 逻辑回归[ ] loss function 损失函数[ ] low-pass filtering 低通滤波[ ] magnitude 幅值[ ] MAP 极大后验估计[ ] maximum likelihood estimation 极大似然估计[ ] mean 平均值[ ] MFCC Mel 倒频系数[ ] multi-class classification 多元分类[ ] neural networks 神经网络[ ] neuron 神经元[ ] Newton’s method 牛顿法[ ] non-convex function 非凸函数[ ] non-linear feature 非线性特征[ ] norm 范式[ ] norm bounded 有界范数[ ] norm constrained 范数约束[ ] normalization 归一化[ ] numerical roundoff errors 数值舍入误差[ ] numerically checking 数值检验[ ] numerically reliable 数值计算上稳定[ ] object detection 物体检测[ ] objective function 目标函数[ ] off-by-one error 缺位错误[ ] orthogonalization 正交化[ ] output layer 输出层[ ] overall cost function 总体代价函数[ ] over-complete basis 超完备基[ ] over-fitting 过拟合[ ] parts of objects 目标的部件[ ] part-whole decompostion 部分-整体分解[ ] PCA 主元分析[ ] penalty term 惩罚因子[ ] per-example mean subtraction 逐样本均值消减[150 ] pooling 池化[ ] pretrain 预训练[ ] principal components analysis 主成份分析[ ] quadratic constraints 二次约束[ ] RBMs 受限Boltzman机[ ] reconstruction based models 基于重构的模型[ ] reconstruction cost 重建代价[ ] reconstruction term 重构项[ ] redundant 冗余[ ] reflection matrix 反射矩阵[ ] regularization 正则化[ ] regularization term 正则化项[ ] rescaling 缩放[ ] robust 鲁棒性[ ] run 行程[ ] second-order feature 二阶特征[ ] sigmoid activation function S型激励函数[ ] significant digits 有效数字[ ] singular value 奇异值[ ] singular vector 奇异向量[ ] smoothed L1 penalty 平滑的L1范数惩罚[ ] Smoothed topographic L1 sparsity penalty 平滑地形L1稀疏惩罚函数[ ] smoothing 平滑[ ] Softmax Regresson Softmax回归[ ] sorted in decreasing order 降序排列[ ] source features 源特征[ ] sparse autoencoder 消减归一化[ ] Sparsity 稀疏性[ ] sparsity parameter 稀疏性参数[ ] sparsity penalty 稀疏惩罚[ ] square function 平方函数[ ] squared-error 方差[ ] stationary 平稳性(不变性)[ ] stationary stochastic process 平稳随机过程[ ] step-size 步长值[ ] supervised learning 监督学习[ ] symmetric positive semi-definite matrix 对称半正定矩阵[ ] symmetry breaking 对称失效[ ] tanh function 双曲正切函数[ ] the average activation 平均活跃度[ ] the derivative checking method 梯度验证方法[ ] the empirical distribution 经验分布函数[ ] the energy function 能量函数[ ] the Lagrange dual 拉格朗日对偶函数[ ] the log likelihood 对数似然函数[ ] the pixel intensity value 像素灰度值[ ] the rate of convergence 收敛速度[ ] topographic cost term 拓扑代价项[ ] topographic ordered 拓扑秩序[ ] transformation 变换[200 ] translation invariant 平移不变性[ ] trivial answer 平凡解[ ] under-complete basis 不完备基[ ] unrolling 组合扩展[ ] unsupervised learning 无监督学习[ ] variance 方差[ ] vecotrized implementation 向量化实现[ ] vectorization 矢量化[ ] visual cortex 视觉皮层[ ] weight decay 权重衰减[ ] weighted average 加权平均值[ ] whitening 白化[ ] zero-mean 均值为零第二部分Letter A[ ] Accumulated error backpropagation 累积误差逆传播[ ] Activation Function 激活函数[ ] Adaptive Resonance Theory/ART 自适应谐振理论[ ] Addictive model 加性学习[ ] Adversarial Networks 对抗网络[ ] Affine Layer 仿射层[ ] Affinity matrix 亲和矩阵[ ] Agent 代理/ 智能体[ ] Algorithm 算法[ ] Alpha-beta pruning α-β剪枝[ ] Anomaly detection 异常检测[ ] Approximation 近似[ ] Area Under ROC Curve/AUC Roc 曲线下面积[ ] Artificial General Intelligence/AGI 通用人工智能[ ] Artificial Intelligence/AI 人工智能[ ] Association analysis 关联分析[ ] Attention mechanism 注意力机制[ ] Attribute conditional independence assumption 属性条件独立性假设[ ] Attribute space 属性空间[ ] Attribute value 属性值[ ] Autoencoder 自编码器[ ] Automatic speech recognition 自动语音识别[ ] Automatic summarization 自动摘要[ ] Average gradient 平均梯度[ ] Average-Pooling 平均池化Letter B[ ] Backpropagation Through Time 通过时间的反向传播[ ] Backpropagation/BP 反向传播[ ] Base learner 基学习器[ ] Base learning algorithm 基学习算法[ ] Batch Normalization/BN 批量归一化[ ] Bayes decision rule 贝叶斯判定准则[250 ] Bayes Model Averaging/BMA 贝叶斯模型平均[ ] Bayes optimal classifier 贝叶斯最优分类器[ ] Bayesian decision theory 贝叶斯决策论[ ] Bayesian network 贝叶斯网络[ ] Between-class scatter matrix 类间散度矩阵[ ] Bias 偏置/ 偏差[ ] Bias-variance decomposition 偏差-方差分解[ ] Bias-Variance Dilemma 偏差–方差困境[ ] Bi-directional Long-Short Term Memory/Bi-LSTM 双向长短期记忆[ ] Binary classification 二分类[ ] Binomial test 二项检验[ ] Bi-partition 二分法[ ] Boltzmann machine 玻尔兹曼机[ ] Bootstrap sampling 自助采样法/可重复采样/有放回采样[ ] Bootstrapping 自助法[ ] Break-Event Point/BEP 平衡点Letter C[ ] Calibration 校准[ ] Cascade-Correlation 级联相关[ ] Categorical attribute 离散属性[ ] Class-conditional probability 类条件概率[ ] Classification and regression tree/CART 分类与回归树[ ] Classifier 分类器[ ] Class-imbalance 类别不平衡[ ] Closed -form 闭式[ ] Cluster 簇/类/集群[ ] Cluster analysis 聚类分析[ ] Clustering 聚类[ ] Clustering ensemble 聚类集成[ ] Co-adapting 共适应[ ] Coding matrix 编码矩阵[ ] COLT 国际学习理论会议[ ] Committee-based learning 基于委员会的学习[ ] Competitive learning 竞争型学习[ ] Component learner 组件学习器[ ] Comprehensibility 可解释性[ ] Computation Cost 计算成本[ ] Computational Linguistics 计算语言学[ ] Computer vision 计算机视觉[ ] Concept drift 概念漂移[ ] Concept Learning System /CLS 概念学习系统[ ] Conditional entropy 条件熵[ ] Conditional mutual information 条件互信息[ ] Conditional Probability Table/CPT 条件概率表[ ] Conditional random field/CRF 条件随机场[ ] Conditional risk 条件风险[ ] Confidence 置信度[ ] Confusion matrix 混淆矩阵[300 ] Connection weight 连接权[ ] Connectionism 连结主义[ ] Consistency 一致性/相合性[ ] Contingency table 列联表[ ] Continuous attribute 连续属性[ ] Convergence 收敛[ ] Conversational agent 会话智能体[ ] Convex quadratic programming 凸二次规划[ ] Convexity 凸性[ ] Convolutional neural network/CNN 卷积神经网络[ ] Co-occurrence 同现[ ] Correlation coefficient 相关系数[ ] Cosine similarity 余弦相似度[ ] Cost curve 成本曲线[ ] Cost Function 成本函数[ ] Cost matrix 成本矩阵[ ] Cost-sensitive 成本敏感[ ] Cross entropy 交叉熵[ ] Cross validation 交叉验证[ ] Crowdsourcing 众包[ ] Curse of dimensionality 维数灾难[ ] Cut point 截断点[ ] Cutting plane algorithm 割平面法Letter D[ ] Data mining 数据挖掘[ ] Data set 数据集[ ] Decision Boundary 决策边界[ ] Decision stump 决策树桩[ ] Decision tree 决策树/判定树[ ] Deduction 演绎[ ] Deep Belief Network 深度信念网络[ ] Deep Convolutional Generative Adversarial Network/DCGAN 深度卷积生成对抗网络[ ] Deep learning 深度学习[ ] Deep neural network/DNN 深度神经网络[ ] Deep Q-Learning 深度Q 学习[ ] Deep Q-Network 深度Q 网络[ ] Density estimation 密度估计[ ] Density-based clustering 密度聚类[ ] Differentiable neural computer 可微分神经计算机[ ] Dimensionality reduction algorithm 降维算法[ ] Directed edge 有向边[ ] Disagreement measure 不合度量[ ] Discriminative model 判别模型[ ] Discriminator 判别器[ ] Distance measure 距离度量[ ] Distance metric learning 距离度量学习[ ] Distribution 分布[ ] Divergence 散度[350 ] Diversity measure 多样性度量/差异性度量[ ] Domain adaption 领域自适应[ ] Downsampling 下采样[ ] D-separation (Directed separation)有向分离[ ] Dual problem 对偶问题[ ] Dummy node 哑结点[ ] Dynamic Fusion 动态融合[ ] Dynamic programming 动态规划Letter E[ ] Eigenvalue decomposition 特征值分解[ ] Embedding 嵌入[ ] Emotional analysis 情绪分析[ ] Empirical conditional entropy 经验条件熵[ ] Empirical entropy 经验熵[ ] Empirical error 经验误差[ ] Empirical risk 经验风险[ ] End-to-End 端到端[ ] Energy-based model 基于能量的模型[ ] Ensemble learning 集成学习[ ] Ensemble pruning 集成修剪[ ] Error Correcting Output Codes/ECOC 纠错输出码[ ] Error rate 错误率[ ] Error-ambiguity decomposition 误差-分歧分解[ ] Euclidean distance 欧氏距离[ ] Evolutionary computation 演化计算[ ] Expectation-Maximization 期望最大化[ ] Expected loss 期望损失[ ] Exploding Gradient Problem 梯度爆炸问题[ ] Exponential loss function 指数损失函数[ ] Extreme Learning Machine/ELM 超限学习机Letter F[ ] Factorization 因子分解[ ] False negative 假负类[ ] False positive 假正类[ ] False Positive Rate/FPR 假正例率[ ] Feature engineering 特征工程[ ] Feature selection 特征选择[ ] Feature vector 特征向量[ ] Featured Learning 特征学习[ ] Feedforward Neural Networks/FNN 前馈神经网络[ ] Fine-tuning 微调[ ] Flipping output 翻转法[ ] Fluctuation 震荡[ ] Forward stagewise algorithm 前向分步算法[ ] Frequentist 频率主义学派[ ] Full-rank matrix 满秩矩阵[400 ] Functional neuron 功能神经元Letter G[ ] Gain ratio 增益率[ ] Game theory 博弈论[ ] Gaussian kernel function 高斯核函数[ ] Gaussian Mixture Model 高斯混合模型[ ] General Problem Solving 通用问题求解[ ] Generalization 泛化[ ] Generalization error 泛化误差[ ] Generalization error bound 泛化误差上界[ ] Generalized Lagrange function 广义拉格朗日函数[ ] Generalized linear model 广义线性模型[ ] Generalized Rayleigh quotient 广义瑞利商[ ] Generative Adversarial Networks/GAN 生成对抗网络[ ] Generative Model 生成模型[ ] Generator 生成器[ ] Genetic Algorithm/GA 遗传算法[ ] Gibbs sampling 吉布斯采样[ ] Gini index 基尼指数[ ] Global minimum 全局最小[ ] Global Optimization 全局优化[ ] Gradient boosting 梯度提升[ ] Gradient Descent 梯度下降[ ] Graph theory 图论[ ] Ground-truth 真相/真实Letter H[ ] Hard margin 硬间隔[ ] Hard voting 硬投票[ ] Harmonic mean 调和平均[ ] Hesse matrix 海塞矩阵[ ] Hidden dynamic model 隐动态模型[ ] Hidden layer 隐藏层[ ] Hidden Markov Model/HMM 隐马尔可夫模型[ ] Hierarchical clustering 层次聚类[ ] Hilbert space 希尔伯特空间[ ] Hinge loss function 合页损失函数[ ] Hold-out 留出法[ ] Homogeneous 同质[ ] Hybrid computing 混合计算[ ] Hyperparameter 超参数[ ] Hypothesis 假设[ ] Hypothesis test 假设验证Letter I[ ] ICML 国际机器学习会议[450 ] Improved iterative scaling/IIS 改进的迭代尺度法[ ] Incremental learning 增量学习[ ] Independent and identically distributed/i.i.d. 独立同分布[ ] Independent Component Analysis/ICA 独立成分分析[ ] Indicator function 指示函数[ ] Individual learner 个体学习器[ ] Induction 归纳[ ] Inductive bias 归纳偏好[ ] Inductive learning 归纳学习[ ] Inductive Logic Programming/ILP 归纳逻辑程序设计[ ] Information entropy 信息熵[ ] Information gain 信息增益[ ] Input layer 输入层[ ] Insensitive loss 不敏感损失[ ] Inter-cluster similarity 簇间相似度[ ] International Conference for Machine Learning/ICML 国际机器学习大会[ ] Intra-cluster similarity 簇内相似度[ ] Intrinsic value 固有值[ ] Isometric Mapping/Isomap 等度量映射[ ] Isotonic regression 等分回归[ ] Iterative Dichotomiser 迭代二分器Letter K[ ] Kernel method 核方法[ ] Kernel trick 核技巧[ ] Kernelized Linear Discriminant Analysis/KLDA 核线性判别分析[ ] K-fold cross validation k 折交叉验证/k 倍交叉验证[ ] K-Means Clustering K –均值聚类[ ] K-Nearest Neighbours Algorithm/KNN K近邻算法[ ] Knowledge base 知识库[ ] Knowledge Representation 知识表征Letter L[ ] Label space 标记空间[ ] Lagrange duality 拉格朗日对偶性[ ] Lagrange multiplier 拉格朗日乘子[ ] Laplace smoothing 拉普拉斯平滑[ ] Laplacian correction 拉普拉斯修正[ ] Latent Dirichlet Allocation 隐狄利克雷分布[ ] Latent semantic analysis 潜在语义分析[ ] Latent variable 隐变量[ ] Lazy learning 懒惰学习[ ] Learner 学习器[ ] Learning by analogy 类比学习[ ] Learning rate 学习率[ ] Learning Vector Quantization/LVQ 学习向量量化[ ] Least squares regression tree 最小二乘回归树[ ] Leave-One-Out/LOO 留一法[500 ] linear chain conditional random field 线性链条件随机场[ ] Linear Discriminant Analysis/LDA 线性判别分析[ ] Linear model 线性模型[ ] Linear Regression 线性回归[ ] Link function 联系函数[ ] Local Markov property 局部马尔可夫性[ ] Local minimum 局部最小[ ] Log likelihood 对数似然[ ] Log odds/logit 对数几率[ ] Logistic Regression Logistic 回归[ ] Log-likelihood 对数似然[ ] Log-linear regression 对数线性回归[ ] Long-Short Term Memory/LSTM 长短期记忆[ ] Loss function 损失函数Letter M[ ] Machine translation/MT 机器翻译[ ] Macron-P 宏查准率[ ] Macron-R 宏查全率[ ] Majority voting 绝对多数投票法[ ] Manifold assumption 流形假设[ ] Manifold learning 流形学习[ ] Margin theory 间隔理论[ ] Marginal distribution 边际分布[ ] Marginal independence 边际独立性[ ] Marginalization 边际化[ ] Markov Chain Monte Carlo/MCMC 马尔可夫链蒙特卡罗方法[ ] Markov Random Field 马尔可夫随机场[ ] Maximal clique 最大团[ ] Maximum Likelihood Estimation/MLE 极大似然估计/极大似然法[ ] Maximum margin 最大间隔[ ] Maximum weighted spanning tree 最大带权生成树[ ] Max-Pooling 最大池化[ ] Mean squared error 均方误差[ ] Meta-learner 元学习器[ ] Metric learning 度量学习[ ] Micro-P 微查准率[ ] Micro-R 微查全率[ ] Minimal Description Length/MDL 最小描述长度[ ] Minimax game 极小极大博弈[ ] Misclassification cost 误分类成本[ ] Mixture of experts 混合专家[ ] Momentum 动量[ ] Moral graph 道德图/端正图[ ] Multi-class classification 多分类[ ] Multi-document summarization 多文档摘要[ ] Multi-layer feedforward neural networks 多层前馈神经网络[ ] Multilayer Perceptron/MLP 多层感知器[ ] Multimodal learning 多模态学习[550 ] Multiple Dimensional Scaling 多维缩放[ ] Multiple linear regression 多元线性回归[ ] Multi-response Linear Regression /MLR 多响应线性回归[ ] Mutual information 互信息Letter N[ ] Naive bayes 朴素贝叶斯[ ] Naive Bayes Classifier 朴素贝叶斯分类器[ ] Named entity recognition 命名实体识别[ ] Nash equilibrium 纳什均衡[ ] Natural language generation/NLG 自然语言生成[ ] Natural language processing 自然语言处理[ ] Negative class 负类[ ] Negative correlation 负相关法[ ] Negative Log Likelihood 负对数似然[ ] Neighbourhood Component Analysis/NCA 近邻成分分析[ ] Neural Machine Translation 神经机器翻译[ ] Neural Turing Machine 神经图灵机[ ] Newton method 牛顿法[ ] NIPS 国际神经信息处理系统会议[ ] No Free Lunch Theorem/NFL 没有免费的午餐定理[ ] Noise-contrastive estimation 噪音对比估计[ ] Nominal attribute 列名属性[ ] Non-convex optimization 非凸优化[ ] Nonlinear model 非线性模型[ ] Non-metric distance 非度量距离[ ] Non-negative matrix factorization 非负矩阵分解[ ] Non-ordinal attribute 无序属性[ ] Non-Saturating Game 非饱和博弈[ ] Norm 范数[ ] Normalization 归一化[ ] Nuclear norm 核范数[ ] Numerical attribute 数值属性Letter O[ ] Objective function 目标函数[ ] Oblique decision tree 斜决策树[ ] Occam’s razor 奥卡姆剃刀[ ] Odds 几率[ ] Off-Policy 离策略[ ] One shot learning 一次性学习[ ] One-Dependent Estimator/ODE 独依赖估计[ ] On-Policy 在策略[ ] Ordinal attribute 有序属性[ ] Out-of-bag estimate 包外估计[ ] Output layer 输出层[ ] Output smearing 输出调制法[ ] Overfitting 过拟合/过配[600 ] Oversampling 过采样Letter P[ ] Paired t-test 成对t 检验[ ] Pairwise 成对型[ ] Pairwise Markov property 成对马尔可夫性[ ] Parameter 参数[ ] Parameter estimation 参数估计[ ] Parameter tuning 调参[ ] Parse tree 解析树[ ] Particle Swarm Optimization/PSO 粒子群优化算法[ ] Part-of-speech tagging 词性标注[ ] Perceptron 感知机[ ] Performance measure 性能度量[ ] Plug and Play Generative Network 即插即用生成网络[ ] Plurality voting 相对多数投票法[ ] Polarity detection 极性检测[ ] Polynomial kernel function 多项式核函数[ ] Pooling 池化[ ] Positive class 正类[ ] Positive definite matrix 正定矩阵[ ] Post-hoc test 后续检验[ ] Post-pruning 后剪枝[ ] potential function 势函数[ ] Precision 查准率/准确率[ ] Prepruning 预剪枝[ ] Principal component analysis/PCA 主成分分析[ ] Principle of multiple explanations 多释原则[ ] Prior 先验[ ] Probability Graphical Model 概率图模型[ ] Proximal Gradient Descent/PGD 近端梯度下降[ ] Pruning 剪枝[ ] Pseudo-label 伪标记[ ] Letter Q[ ] Quantized Neural Network 量子化神经网络[ ] Quantum computer 量子计算机[ ] Quantum Computing 量子计算[ ] Quasi Newton method 拟牛顿法Letter R[ ] Radial Basis Function/RBF 径向基函数[ ] Random Forest Algorithm 随机森林算法[ ] Random walk 随机漫步[ ] Recall 查全率/召回率[ ] Receiver Operating Characteristic/ROC 受试者工作特征[ ] Rectified Linear Unit/ReLU 线性修正单元[650 ] Recurrent Neural Network 循环神经网络[ ] Recursive neural network 递归神经网络[ ] Reference model 参考模型[ ] Regression 回归[ ] Regularization 正则化[ ] Reinforcement learning/RL 强化学习[ ] Representation learning 表征学习[ ] Representer theorem 表示定理[ ] reproducing kernel Hilbert space/RKHS 再生核希尔伯特空间[ ] Re-sampling 重采样法[ ] Rescaling 再缩放[ ] Residual Mapping 残差映射[ ] Residual Network 残差网络[ ] Restricted Boltzmann Machine/RBM 受限玻尔兹曼机[ ] Restricted Isometry Property/RIP 限定等距性[ ] Re-weighting 重赋权法[ ] Robustness 稳健性/鲁棒性[ ] Root node 根结点[ ] Rule Engine 规则引擎[ ] Rule learning 规则学习Letter S[ ] Saddle point 鞍点[ ] Sample space 样本空间[ ] Sampling 采样[ ] Score function 评分函数[ ] Self-Driving 自动驾驶[ ] Self-Organizing Map/SOM 自组织映射[ ] Semi-naive Bayes classifiers 半朴素贝叶斯分类器[ ] Semi-Supervised Learning 半监督学习[ ] semi-Supervised Support Vector Machine 半监督支持向量机[ ] Sentiment analysis 情感分析[ ] Separating hyperplane 分离超平面[ ] Sigmoid function Sigmoid 函数[ ] Similarity measure 相似度度量[ ] Simulated annealing 模拟退火[ ] Simultaneous localization and mapping 同步定位与地图构建[ ] Singular Value Decomposition 奇异值分解[ ] Slack variables 松弛变量[ ] Smoothing 平滑[ ] Soft margin 软间隔[ ] Soft margin maximization 软间隔最大化[ ] Soft voting 软投票[ ] Sparse representation 稀疏表征[ ] Sparsity 稀疏性[ ] Specialization 特化[ ] Spectral Clustering 谱聚类[ ] Speech Recognition 语音识别[ ] Splitting variable 切分变量[700 ] Squashing function 挤压函数[ ] Stability-plasticity dilemma 可塑性-稳定性困境[ ] Statistical learning 统计学习[ ] Status feature function 状态特征函[ ] Stochastic gradient descent 随机梯度下降[ ] Stratified sampling 分层采样[ ] Structural risk 结构风险[ ] Structural risk minimization/SRM 结构风险最小化[ ] Subspace 子空间[ ] Supervised learning 监督学习/有导师学习[ ] support vector expansion 支持向量展式[ ] Support Vector Machine/SVM 支持向量机[ ] Surrogat loss 替代损失[ ] Surrogate function 替代函数[ ] Symbolic learning 符号学习[ ] Symbolism 符号主义[ ] Synset 同义词集Letter T[ ] T-Distribution Stochastic Neighbour Embedding/t-SNE T –分布随机近邻嵌入[ ] Tensor 张量[ ] Tensor Processing Units/TPU 张量处理单元[ ] The least square method 最小二乘法[ ] Threshold 阈值[ ] Threshold logic unit 阈值逻辑单元[ ] Threshold-moving 阈值移动[ ] Time Step 时间步骤[ ] Tokenization 标记化[ ] Training error 训练误差[ ] Training instance 训练示例/训练例[ ] Transductive learning 直推学习[ ] Transfer learning 迁移学习[ ] Treebank 树库[ ] Tria-by-error 试错法[ ] True negative 真负类[ ] True positive 真正类[ ] True Positive Rate/TPR 真正例率[ ] Turing Machine 图灵机[ ] Twice-learning 二次学习Letter U[ ] Underfitting 欠拟合/欠配[ ] Undersampling 欠采样[ ] Understandability 可理解性[ ] Unequal cost 非均等代价[ ] Unit-step function 单位阶跃函数[ ] Univariate decision tree 单变量决策树[ ] Unsupervised learning 无监督学习/无导师学习[ ] Unsupervised layer-wise training 无监督逐层训练[ ] Upsampling 上采样Letter V[ ] Vanishing Gradient Problem 梯度消失问题[ ] Variational inference 变分推断[ ] VC Theory VC维理论[ ] Version space 版本空间[ ] Viterbi algorithm 维特比算法[760 ] Von Neumann architecture 冯· 诺伊曼架构Letter W[ ] Wasserstein GAN/WGAN Wasserstein生成对抗网络[ ] Weak learner 弱学习器[ ] Weight 权重[ ] Weight sharing 权共享[ ] Weighted voting 加权投票法[ ] Within-class scatter matrix 类内散度矩阵[ ] Word embedding 词嵌入[ ] Word sense disambiguation 词义消歧Letter Z[ ] Zero-data learning 零数据学习[ ] Zero-shot learning 零次学习第三部分A[ ] approximations近似值[ ] arbitrary随意的[ ] affine仿射的[ ] arbitrary任意的[ ] amino acid氨基酸[ ] amenable经得起检验的[ ] axiom公理,原则[ ] abstract提取[ ] architecture架构,体系结构;建造业[ ] absolute绝对的[ ] arsenal军火库[ ] assignment分配[ ] algebra线性代数[ ] asymptotically无症状的[ ] appropriate恰当的B[ ] bias偏差[ ] brevity简短,简洁;短暂[800 ] broader广泛[ ] briefly简短的[ ] batch批量C[ ] convergence 收敛,集中到一点[ ] convex凸的[ ] contours轮廓[ ] constraint约束[ ] constant常理[ ] commercial商务的[ ] complementarity补充[ ] coordinate ascent同等级上升[ ] clipping剪下物;剪报;修剪[ ] component分量;部件[ ] continuous连续的[ ] covariance协方差[ ] canonical正规的,正则的[ ] concave非凸的[ ] corresponds相符合;相当;通信[ ] corollary推论[ ] concrete具体的事物,实在的东西[ ] cross validation交叉验证[ ] correlation相互关系[ ] convention约定[ ] cluster一簇[ ] centroids 质心,形心[ ] converge收敛[ ] computationally计算(机)的[ ] calculus计算D[ ] derive获得,取得[ ] dual二元的[ ] duality二元性;二象性;对偶性[ ] derivation求导;得到;起源[ ] denote预示,表示,是…的标志;意味着,[逻]指称[ ] divergence 散度;发散性[ ] dimension尺度,规格;维数[ ] dot小圆点[ ] distortion变形[ ] density概率密度函数[ ] discrete离散的[ ] discriminative有识别能力的[ ] diagonal对角[ ] dispersion分散,散开[ ] determinant决定因素[849 ] disjoint不相交的E[ ] encounter遇到[ ] ellipses椭圆[ ] equality等式[ ] extra额外的[ ] empirical经验;观察[ ] ennmerate例举,计数[ ] exceed超过,越出[ ] expectation期望[ ] efficient生效的[ ] endow赋予[ ] explicitly清楚的[ ] exponential family指数家族[ ] equivalently等价的F[ ] feasible可行的[ ] forary初次尝试[ ] finite有限的,限定的[ ] forgo摒弃,放弃[ ] fliter过滤[ ] frequentist最常发生的[ ] forward search前向式搜索[ ] formalize使定形G[ ] generalized归纳的[ ] generalization概括,归纳;普遍化;判断(根据不足)[ ] guarantee保证;抵押品[ ] generate形成,产生[ ] geometric margins几何边界[ ] gap裂口[ ] generative生产的;有生产力的H[ ] heuristic启发式的;启发法;启发程序[ ] hone怀恋;磨[ ] hyperplane超平面L[ ] initial最初的[ ] implement执行[ ] intuitive凭直觉获知的[ ] incremental增加的[900 ] intercept截距[ ] intuitious直觉[ ] instantiation例子[ ] indicator指示物,指示器[ ] interative重复的,迭代的[ ] integral积分[ ] identical相等的;完全相同的[ ] indicate表示,指出[ ] invariance不变性,恒定性[ ] impose把…强加于[ ] intermediate中间的[ ] interpretation解释,翻译J[ ] joint distribution联合概率L[ ] lieu替代[ ] logarithmic对数的,用对数表示的[ ] latent潜在的[ ] Leave-one-out cross validation留一法交叉验证M[ ] magnitude巨大[ ] mapping绘图,制图;映射[ ] matrix矩阵[ ] mutual相互的,共同的[ ] monotonically单调的[ ] minor较小的,次要的[ ] multinomial多项的[ ] multi-class classification二分类问题N[ ] nasty讨厌的[ ] notation标志,注释[ ] naïve朴素的O[ ] obtain得到[ ] oscillate摆动[ ] optimization problem最优化问题[ ] objective function目标函数[ ] optimal最理想的[ ] orthogonal(矢量,矩阵等)正交的[ ] orientation方向[ ] ordinary普通的[ ] occasionally偶然的P[ ] partial derivative偏导数[ ] property性质[ ] proportional成比例的[ ] primal原始的,最初的[ ] permit允许[ ] pseudocode伪代码[ ] permissible可允许的[ ] polynomial多项式[ ] preliminary预备[ ] precision精度[ ] perturbation 不安,扰乱[ ] poist假定,设想[ ] positive semi-definite半正定的[ ] parentheses圆括号[ ] posterior probability后验概率[ ] plementarity补充[ ] pictorially图像的[ ] parameterize确定…的参数[ ] poisson distribution柏松分布[ ] pertinent相关的Q[ ] quadratic二次的[ ] quantity量,数量;分量[ ] query疑问的R[ ] regularization使系统化;调整[ ] reoptimize重新优化[ ] restrict限制;限定;约束[ ] reminiscent回忆往事的;提醒的;使人联想…的(of)[ ] remark注意[ ] random variable随机变量[ ] respect考虑[ ] respectively各自的;分别的[ ] redundant过多的;冗余的S[ ] susceptible敏感的[ ] stochastic可能的;随机的[ ] symmetric对称的[ ] sophisticated复杂的[ ] spurious假的;伪造的[ ] subtract减去;减法器[ ] simultaneously同时发生地;同步地[ ] suffice满足[ ] scarce稀有的,难得的[ ] split分解,分离[ ] subset子集[ ] statistic统计量[ ] successive iteratious连续的迭代[ ] scale标度[ ] sort of有几分的[ ] squares平方T[ ] trajectory轨迹[ ] temporarily暂时的[ ] terminology专用名词[ ] tolerance容忍;公差[ ] thumb翻阅[ ] threshold阈,临界[ ] theorem定理[ ] tangent正弦U[ ] unit-length vector单位向量V[ ] valid有效的,正确的[ ] variance方差[ ] variable变量;变元[ ] vocabulary词汇[ ] valued经估价的;宝贵的[ ] W [1038 ] wrapper包装。
迭代吉洪诺夫正则化的FCM聚类算法

迭代吉洪诺夫正则化的FCM聚类算法蒋莉芳;苏一丹;覃华【摘要】模糊C均值聚类算法(fuzzy C-means,FCM)存在不适定性问题,数据噪声会引起聚类失真.为此,提出一种迭代Tikhonov正则化模糊C均值聚类算法,对FCM的目标函数引入正则化罚项,推导最优正则化参数的迭代公式,用L曲线法在迭代过程中实现正则化参数的寻优,提高FCM的抗噪声能力,克服不适定问题.在UCI 数据集和人工数据集上的实验结果表明,所提算法的聚类精度较传统FCM高,迭代次数少10倍以上,抗噪声能力更强,用迭代Tikhonov正则化克服传统FCM的不适定问题是可行的.%FCM algorithm has the ill posed problem.Regularization method can improve the distortion of the model solution caused by the fluctuation of the data.And it can improve the precision and robustness of FCM through solving the error estimate of solution caused by ill posed problem.Iterative Tikhonov regularization function was introduced into the proposed problem (ITR-FCM),and L-curve method was used to select the optimal regularization parameter iteratively,and the convergence rate of the algorithm was further improved using the dynamic Tikhonov method.Five UCI datasets and five artificial datasets were chosen for the test.Results of tests show that iterative Tikhonov is an effective solution to the ill posed problem,and ITR-FCM has better convergence speed,accuracy and robustness.【期刊名称】《计算机工程与设计》【年(卷),期】2017(038)009【总页数】5页(P2391-2395)【关键词】模糊C均值聚类;不适定问题;Tikhonov正则化;正则化参数;L曲线【作者】蒋莉芳;苏一丹;覃华【作者单位】广西大学计算机与电子信息学院,广西南宁 530004;广西大学计算机与电子信息学院,广西南宁 530004;广西大学计算机与电子信息学院,广西南宁530004【正文语种】中文【中图分类】TP389.1模糊C均值算法已广泛地应用于图像分割、模式识别、故障诊断等领域[1-6]。
数字鸿沟产生的原因及解决办法英语作文

数字鸿沟产生的原因及解决办法英语作文全文共3篇示例,供读者参考篇1The digital divide refers to the gap between those who have access to digital technology and those who do not. This divide is becoming increasingly important as technology plays anever-growing role in society. There are several reasons why the digital divide exists and various ways to bridge this gap.One of the main reasons for the digital divide is socioeconomic status. Those from lower-income backgrounds may not be able to afford the latest technology or internet access, therefore creating a barrier to participation in the digital world. Additionally, education plays a significant role in the digital divide. Those who are more educated are more likely to have the skills and knowledge to navigate technology effectively, while those with less education may struggle to keep up.Geographical location is another factor that contributes to the digital divide. Rural areas may not have the same access to high-speed internet as urban areas, creating a disparity in digital opportunities. Furthermore, age can also play a role in the digitaldivide. Older individuals may be less comfortable with technology and therefore less likely to engage with it.To bridge the digital divide, various solutions can be implemented. One approach is to provide affordable or even free access to technology and internet services for those in lower-income brackets. This could involve government subsidies or community initiatives to ensure that everyone has access to the necessary tools.Education is another crucial aspect of bridging the digital divide. By providing digital literacy classes and training programs, individuals can develop the skills needed to effectively use technology. Schools can also play a role in reducing the digital divide by ensuring that all students have access to technology and are taught how to use it effectively.Improving infrastructure is also key to bridging the digital divide. This may involve expanding high-speed internet access to rural areas and ensuring that all communities have access to reliable technology services. Companies and governments can work together to invest in infrastructure improvements to ensure that everyone has equal access to technology.In conclusion, the digital divide is a significant issue that must be addressed in order to create a more equitable society.By understanding the reasons for the divide and implementing solutions to bridge it, we can ensure that everyone has access to the benefits of digital technology. By working together, we can create a more connected and inclusive world for all.篇2The Digital Divide: Causes and SolutionsIntroductionThe digital divide refers to the gap between those who have access to technology and the internet, and those who do not. This gap is widening as technology becomes increasingly essential in our daily lives. In this essay, we will explore the causes of the digital divide and propose solutions to bridge this gap.Causes of the Digital Divide1. Economic DisparitiesOne of the main reasons for the digital divide is economic disparities. People from lower-income households may not be able to afford computers or internet access. In many developing countries, the cost of technology is prohibitively high for the average citizen, leading to disparities in access.2. Geographic LocationGeographic location also plays a role in the digital divide. Rural areas often lack the necessary infrastructure for reliable internet connection, making it difficult for residents to access the internet. This lack of access hinders their ability to participate in the digital world.3. Lack of Digital LiteracyAnother factor contributing to the digital divide is the lack of digital literacy. Many people, especially in older generations, lack the skills and knowledge to use technology effectively. This hinders their ability to take advantage of the opportunities offered by the internet.Solutions to Bridge the Digital Divide1. Affordable Access ProgramsTo address the economic disparities that contribute to the digital divide, governments and non-profit organizations can provide affordable access programs. These programs can offer subsidized computers and internet access to low-income families, ensuring that everyone has the opportunity to connect to the digital world.2. Infrastructure DevelopmentImproving infrastructure in rural areas is essential to bridging the digital divide. Governments can invest in expanding broadband networks to underserved areas, providing residents with access to high-speed internet. This will help to level the playing field and ensure that everyone has equal access to technology.3. Digital Literacy TrainingPromoting digital literacy is key to bridging the digital divide. Schools, community centers, and other organizations can offer digital skills training programs to help people of all ages become more proficient in using technology. This will empower individuals to navigate the digital world more effectively and take advantage of the opportunities it offers.ConclusionThe digital divide is a significant challenge that must be addressed to ensure that everyone has equal access to technology and the internet. By tackling the root causes of the divide and implementing solutions such as affordable access programs, infrastructure development, and digital literacy training, we can bridge the gap and create a more inclusive digital society. It is crucial that we work together to overcome this divide and create a more equitable future for all.篇3The Digital Divide: Causes and SolutionsIn our rapidly advancing digital age, there is a growing concern about the digital divide - the gap between those who have access to and knowledge of digital technologies and those who do not. This issue affects not only individuals but also communities and countries as a whole. In this essay, we will explore the causes of the digital divide and propose possible solutions to bridge this gap.Causes of the Digital DivideOne of the main causes of the digital divide is socioeconomic inequality. People from lower-income households may not have the financial means to access digital technologies such as computers, smartphones, and the internet. Without these tools, they are at a disadvantage when it comes to education, job opportunities, and staying connected with others.Another factor contributing to the digital divide is geographical location. In rural and remote areas, there may be a lack of infrastructure for internet access, making it difficult for residents to get online. This disparity in access to digitaltechnologies can further isolate these communities and hinder their social and economic development.Furthermore, digital literacy plays a significant role in widening the digital divide. Those who are not familiar with digital technologies may struggle to use them effectively, leading to a lack of skills necessary to thrive in today's digital world. Without adequate training and support, these individuals may fall behind in terms of education, employment, and overall quality of life.Solutions to the Digital DivideTo address the digital divide, we must take a multi-faceted approach that tackles the root causes of this issue. One potential solution is to invest in infrastructure improvements to expand internet access to underserved areas. By building a reliable network of high-speed internet connections, we can ensure that all communities have equal opportunities to access digital technologies.Additionally, we need to provide affordable devices and internet services to those who cannot afford them. Government subsidies and private sector partnerships can help make digital technologies more accessible to low-income households, narrowing the gap between the haves and the have-nots.Moreover, promoting digital literacy programs is essential in bridging the digital divide. By offering training and educational resources on how to use digital technologies effectively, we can empower individuals to navigate the digital world with confidence and competence. Schools, community centers, and libraries can serve as hubs for these programs, reaching out to those who need them most.In conclusion, the digital divide is a complex issue withfar-reaching implications for society. By understanding the causes of this gap and implementing targeted solutions, we can work towards a more equitable and inclusive digital future where everyone has the opportunity to benefit from the advantages of technology. It is up to all of us to collectively bridge the digital divide and ensure that no one is left behind in the digital age.。
电缆通道AR巡视辅助系统

电缆通道AR巡视辅助系统摘要:针对目前电缆巡视作业中广泛存在的效率低、准确性低、监督不严的问题,本文提出了一种将智能穿戴设备(AR眼镜)运用于电缆通道巡视的方法。
该方法通过GPS实时定位,结合AR眼镜实现了智能巡检指导,并可对巡检过程数据做记录和分析。
关键词:智能可穿戴设备;电力行业;智能巡检合智能可穿戴设备和后台监控端的全新巡检指导模式。
3.1 通信方式本系统使用中,任务需要从后台端下载到眼镜端,并从眼镜端回传到后台端。
眼镜端应用使用C#语言和Unity进行开发,客户端和服务端之间的通信基于Http协议P2P模式,因此要求客户端和服务器处于同一网络(外网.局域网均可)。
服务端创建工作任务后[3],通过Http协议向眼镜端发送加密信息。
眼镜端通过Http协议获得加密任务信息,解密后获得任务信息并生成巡检人员需要执行的实际任务内容。
任务结束后,眼镜端自动判断当前是否是有效网络环境(是否能连接服务端)。
若处于无效网络环境,任务仍然保留在眼镜端本地不做上传处理。
若处于有效网络环境下,系统首先通过递归算法对图像文件进行ZIP格式压缩处理之后对操作信息进行加密处理,处理结束后文件将通过HTTP断点传输文件的方式上传到服务器。
3.2 语音实现方式本系统使用科大讯飞windows系统语音插件进行交互,包含语音合成,语音唤醒和语音读写三大模块。
其中语音听写的使用需要网络支持下使用[4]。
使用C++语言封装讯飞官方windows语音库,Unity调用封装好的Dll动态链接库。
通过对Dll动态库文件方法的再次封装,使用观察者模式管理所有需要通过语音调用的功能函数。
4 结论AR技术结合电缆通道巡视辅助,有效解决了目前电缆通道巡检中流程繁琐,无法监控等问题。
本文提出的电缆通道AR巡视辅助系统,结合可穿戴智能设备AR眼镜,可以实现对巡检过程的监控、指导、数据电子化,确保巡检的准确无误,推动巡检工作的标准化,提高巡检结果的可靠性和巡检人员的工作效率。
人工智能专用名词

人工智能专用名词1. 机器学习 (Machine Learning)2. 深度学习 (Deep Learning)3. 神经网络 (Neural Network)4. 自然语言处理 (Natural Language Processing)5. 计算机视觉 (Computer Vision)6. 强化学习 (Reinforcement Learning)7. 数据挖掘 (Data Mining)8. 数据预处理 (Data Preprocessing)9. 特征工程 (Feature Engineering)10. 模型训练 (Model Training)11. 模型评估 (Model Evaluation)12. 监督学习 (Supervised Learning)13. 无监督学习 (Unsupervised Learning)14. 半监督学习 (Semi-Supervised Learning)15. 迁移学习 (Transfer Learning)16. 生成对抗网络 (Generative Adversarial Networks, GANs)17. 强化学习 (Reinforcement Learning)18. 聚类 (Clustering)19. 分类 (Classification)20. 回归 (Regression)21. 泛化能力 (Generalization)22. 正则化 (Regularization)23. 自动编码器 (Autoencoder)24. 支持向量机 (Support Vector Machine, SVM)25. 随机森林 (Random Forest)26. 梯度下降 (Gradient Descent)27. 前向传播 (Forward Propagation)28. 反向传播 (Backpropagation)29. 混淆矩阵 (Confusion Matrix)30. ROC曲线 (Receiver Operating Characteristic Curve, ROC Curve)31. AUC指标 (Area Under Curve, AUC)32. 噪声 (Noise)33. 过拟合 (Overfitting)34. 欠拟合 (Underfitting)35. 超参数 (Hyperparameters)36. 网格搜索 (Grid Search)37. 交叉验证 (Cross Validation)38. 降维 (Dimensionality Reduction)39. 卷积神经网络 (Convolutional Neural Network, CNN)40. 循环神经网络 (Recurrent Neural Network, RNN)。
soft actor-critic 的解释 -回复

soft actor-critic 的解释-回复Soft Actor-Critic (SAC) is a reinforcement learning algorithm that combines the actor-critic framework with maximum entropy reinforcement learning. It is designed to learn policies for continuous action spaces, facilitating robust and flexible control in complex environments. In this article, we will step by step explore the key principles and components of the SAC algorithm.1. Introduction to Reinforcement Learning:Reinforcement learning is a branch of machine learning that focuses on enabling an agent to learn how to make decisions based on its interaction with an environment. The agent receives feedback in the form of rewards or penalties and learns to maximize the cumulative reward over time through trial and error.2. Actor-Critic Framework:The actor-critic framework is a popular approach in reinforcement learning. It combines the advantages of both value-based and policy-based methods. The actor, also known as the policy network, learns to select actions based on the current state of the environment. The critic, on the other hand, estimates the value function or the state-action value function, providing feedback tothe actor's policy learning process.3. Continuous Action Spaces:Many real-world problems, such as robotics control or autonomous driving, involve continuous action spaces. In contrast to discrete action spaces where there are a finite number of actions to choose from, continuous action spaces allow for an infinite number of actions within a specific range. Traditional policy-based methods struggle with continuous actions due to the curse of dimensionality.4. Maximum Entropy Reinforcement Learning:Maximum entropy reinforcement learning aims to learn policies that are not only optimal but also stochastic. Introducing stochasticity in the policy allows for exploration and probabilistic decision-making, enabling the agent to handle uncertainties in the environment. This approach helps prevent the agent from getting trapped in local optima.5. Soft Q-Learning:Soft Q-learning is a variant of the Q-learning algorithm that leverages maximum entropy reinforcement learning principles. Itseeks to learn a soft state-action value function, which combines the typical expected reward with an entropy term. The entropy term encourages exploration by discouraging over-reliance on deterministic policies.6. Policy Optimization with Soft Actor-Critic:In SAC, the actor is responsible for learning the policy distribution, parametrized by a neural network. The critic learns the Q-function, estimating the state-action values. The training procedure consists of sampling actions based on the current policy, collecting trajectories or episodes, and using these samples to update the policy and Q-function.7. Entropy Regularization:SAC utilizes entropy regularization to ensure exploration and stochastic decision-making. The entropy term acts as a regularizer added to the objective function during policy optimization. By maximizing the entropy, the agent strives to maintain a diverse set of actions and explore the full action space.8. Soft Actor-Critic Architecture:The SAC architecture involves three main components: the actornetwork, the critic network, and target networks. The actor network is responsible for learning the policy distribution, while the critic network estimates the Q-function for value estimation. Target networks are used to stabilize the learning process by providing temporally consistent value estimates.9. Experience Replay:Experience replay is a technique employed in SAC to improve sample efficiency and mitigate potential non-stationarity issues. Instead of updating the policy and value function using immediate samples, experience replay stores and replays past experiences. This approach enables the agent to learn from a diverse range of experiences, leading to more robust policy learning.10. Exploration Strategies:Exploration is critical for reinforcement learning, as it allows the agent to discover new and potentially better policies. SAC employs a combination of exploration strategies, including adding noise to the policy parameters or actions. This noise injection encourages the agent to explore different solutions, improving the chance of finding the optimal policy.In conclusion, Soft Actor-Critic is a powerful reinforcement learning algorithm for continuous action spaces. By incorporating maximum entropy reinforcement learning principles, SAC enables robust and flexible control in complex environments. Its actor-critic framework, with entropy regularization, allows for policy optimization and exploration, making it well-suited for real-world problems. Additionally, the use of experience replay and exploration strategies enhances the learning process, leading to better performance and more efficient policy learning.。
08-正则化网络

第八章正则化网络8.0 引言8.1 正则化理论(Regularization Theory)8.2 Reproducing Kernel Hilbert Space (RKHS)8.3 正则化网络(Regularization Networks)、SVM 和SRM8.0 引言模式识别中的“学习”的过程通常是ill-posed 问题:一般没有唯一解;复杂程度高的解很多时候是不稳定的(overfitting)。
8.0 引言解决的办法:Ockham’s razor (定性);正则化方法(定量):对函数集的复杂度加惩罚(与SVM 的思想类似)。
人工神经网络的学习就是ill-posed 问题:正则化网络能够在一定程度上克服overfitting 问题。
8.1 正则化理论简介8.1 正则化理论简介问题的提出:解方程:解的稳定性:y 的小扰动,是否对应x 的小扰动?,y Ax =.X x ∈.Y y ∈.:Y X A →算子赋范空间.)(y y x x A ∆+=∆+小小?8.1 正则化理论简介上述问题可表示为,求:一般的有逆问题求f :yy A A =−)(11−A YF A Hibert Y F Y y F f y Af →∈∈=:,,算子空间是和逆问题Well-posed 与ill-posed :Hadamard 关于well-posed 问题的定义: 存在性:对每个方程都有解f 。
唯一性:保证对每个方程都有唯一解f 。
稳定性:是连续映射,保证了解的稳定性。
y 的小扰动,对应f 的小扰动。
Y y ∈Y y ∈1−A 不是well-posed 就称为ill-posed 。
Hadamard :y 总会有误差,ill-posed 问题不可解。
正则化理论(Tikhonov 1943,1963):有一大类问题,在Hadamard 意义下是ill-posed 问题,但可以找出一个稳定的近似解。
Tikhonov 的思想:不在整个空间上求解,把解限制在一个子集上求解,可能得到稳定解。
R包的分类介绍

R的包分类介绍1.空间数据分析包1)分类空间数据(Classes for spatial data)2)处理空间数据(Handling spatial data)3)读写空间数据(Reading and writing spatial data)4)点格局分析(Point pattern analysis)5)地质统计学(Geostatistics)6)疾病制图和地区数据分析(Disease mapping and areal dataanalysis)7)生态学分析(Ecological analysis)2.机器学习包1)神经网络(Neural Networks)2)递归拆分(Recursive Partitioning)3)随机森林(Random Forests)4)Regularized and Shrinkage Methods5)Boosting6)支持向量机(Support Vector Machines)7)贝叶斯方法(Bayesian Methods)8)基于遗传算法的最优化(Optimization using Genetic Algorithms)9)关联规则(Association Rules)10)模型选择和确认(Model selection and validation)11)统计学习基础(Elements of Statistical Learning)3.多元统计包1)多元数据可视化(Visualising multivariate data)2)假设检验(Hypothesis testing)3)多元分布(Multivariate distributions)4)线形模型(Linear models)5)投影方法(Projection methods)6)主坐标/尺度方法(Principal coordinates / scaling methods)7)无监督分类(Unsupervised classification)8)有监督分类和判别分析(Supervised classification anddiscriminant analysis)9)对应分析(Correspondence analysis)10)前向查找(Forward search)11)缺失数据(Missing data)12)隐变量方法(Latent variable approaches)13)非高斯数据建模(Modelling non-Gaussian data)14)矩阵处理(Matrix manipulations)15)其它(Miscellaneous utitlies)4.药物(代谢)动力学数据分析5.计量经济学1)线形回归模型(Linear regression models)2)微观计量经济学(Microeconometrics)3)其它的回归模型(Further regression models)4)基本的时间序列架构(Basic time series infrastructure)5)时间序列建模(Time series modelling)6)矩阵处理(Matrix manipulations)7)放回再抽样(Bootstrap)8)不平等(Inequality)9)结构变化(Structural change)10)数据集(Data sets)1.R分析空间数据(Spatial Data)的包主要包括两部分:1)导入导出空间数据2)分析空间数据功能及函数包:1)分类空间数据(Classes for spatial data):包sp(/web/packages/sp/index.html)为不同类型的空间数据设计了不同的类,如:点(points),栅格(grids),线(lines),环(rings),多边形(polygons)。
解读TheBenefitsofRegularNetworking

解读TheBenefitsofRegularNetworkingThe Benefits of Regular NetworkingIn today's fast-paced and interconnected world, networking has become an essential tool for professionals in all industries. Regular networking, which involves actively seeking and nurturing professional relationships, can offer numerous benefits that can greatly enhance one's career trajectory and personal growth. In this article, we will explore the various advantages of regular networking and discuss how individuals can leverage these benefits to achieve professional success.1. Access to OpportunitiesOne of the most significant benefits of regular networking is the access it provides to a wide range of opportunities. By building and maintaining connections with professionals in different fields, individuals can gain insights into job openings, industry trends, and emerging markets. Networking enables professionals to tap into the hidden job market, where many positions are filled through referrals and recommendations rather than traditional job postings. Through regular networking, individuals can discover new career prospects that they may have otherwise missed.2. Knowledge Sharing and LearningNetworking is not just about professional advancement; it is also a gateway to continuous learning and knowledge sharing. When individuals interact with professionals from diverse backgrounds, they can exchange ideas, insights, and best practices. By engaging in meaningful conversations, attending industry conferences, or participating in online communities,individuals can broaden their perspectives and expand their knowledge base. Regular networking facilitates a culture of learning that can help professionals stay updated with the latest developments in their respective fields.3. Building a Supportive NetworkRegular networking allows individuals to create and nurture a strong support system of like-minded professionals. In today's competitive and ever-changing professional landscape, having a supportive network is invaluable. These connections can provide emotional support, guidance, and mentorship when faced with challenges or when seeking advice. Networking also enables individuals to collaborate and form partnerships with others who share similar goals and aspirations. The sense of belonging and camaraderie that comes from a supportive network can significantly contribute to personal and professional growth.4. Enhancing Visibility and Personal BrandingEffective networking can greatly enhance one's visibility in the industry and establish a strong personal brand. Regularly interacting with professionals from different companies and sectors allows individuals to showcase their expertise, skills, and accomplishments. As individuals become known and respected within their network, they increase their chances of gaining recognition and attracting new opportunities. By actively participating in industry forums, sharing valuable insights, and contributing to relevant discussions, professionals can differentiate themselves from their peers and enhance their personal brand image.5. Strengthening Communication and Interpersonal SkillsNetworking is not just about exchanging business cards or connecting online; it is about building genuine connections with others. Regular networking provides ample opportunities to practice and refine communication and interpersonal skills. By engaging in conversations, individuals can improve their ability to articulate their ideas, actively listen, and build rapport with others. These skills are not only crucial for professional success but also for personal relationships and leadership development.In conclusion, regular networking offers countless benefits that can significantly impact one's professional growth and career advancement. From accessing new opportunities to acquiring knowledge, building a support system, enhancing visibility, and strengthening communication skills, networking plays a crucial role in today's business world. By actively investing time and effort into networking, individuals can unlock new doors, expand their horizons, and pave the way for long-lasting success.。
gru的超参数

gru的超参数Gru是一种常用的循环神经网络(RNN)的变体,具有门控循环单元(GRU)的结构。
GRU通过引入门控机制,能够更好地捕捉长期依赖的特征,并且相较于传统的循环神经网络,其参数较少,计算效率更高。
在使用GRU模型时,有一些超参数需要进行调整,以便获得更好的模型性能。
下面将详细介绍GRU的一些常见超参数及其相关参考内容。
1. 隐藏层维度(hidden_size):隐藏层维度是决定GRU模型中隐藏状态的维度大小,这个参数直接影响着模型能够学习到的特征数量。
在选择隐藏层维度时,需要考虑输入数据的复杂度以及训练数据集的大小。
如果输入数据较复杂或训练数据集较大,可以选择较大的隐藏层维度来增加模型的表达能力。
参考内容:《On the Propertiesof Neural Machine Translation: Encoder-Decoder Approaches》2. 层数(num_layers):GRU可以堆叠多个循环层以增加模型的深度,这有助于提取更高级的特征。
在选择层数时,需要平衡模型表达能力和计算复杂度。
增加层数可以提高模型的表达能力,但也会增加计算负担。
参考内容:《Recurrent Neural Network Regularization》3. 学习率(learning_rate):学习率是控制模型在每次迭代中更新参数的步长,直接决定着模型参数的收敛速度。
通常情况下,较小的学习率可以使模型训练更加稳定,但可能导致训练过程收敛较慢;而较大的学习率可能导致模型在局部最优点附近震荡无法收敛。
选择合适的学习率需要进行实验调整,可以逐渐减小学习率,观察模型性能的变化。
参考内容:《A Gentle Introduction to Optimization》4. 批量大小(batch_size):批量大小是指每次迭代模型更新时,用于计算损失函数的数据样本数量。
较大的批量大小可以提高模型的收敛速度,但也会带来一定的计算开销;较小的批量大小则可以更好地利用梯度信息,但也可能导致训练过程受到噪声的影响。
normalization和regularization

normalization和regularizationNormalization and RegularizationNormalizationNormalization is the process of adjusting values of different columns in a data set to a common scale, primarily to reduce the amount of bias in the data. It's an important pre-processing step in any data analysis and machine learning task. Normalization can be achieved in various ways, including scaling values to range, standardizing, re-scaling, and many more.Normalization is a critical step when preparing data for various machine learning algorithms, as a good data normalization can greatly improve the performance of certain algorithms, especially those that depend on distance measures such as K-Nearest Neighbors or Support Vector Machines. It also helps reduce the overall complexity of training complex models, enabling faster training times.RegularizationRegularization is a technique used to improve the generalization of a model on unseen data, by controlling overfitting on a dataset. It's a very important tool for model training, and can be used to reduce the complexity of a model,and hence increase its accuracy.Common regularization methods include adding penalty terms to the loss function, or limiting the size or magnitude of the weights used in the model. Regularization can also be done implicitly by using techniques such as dropout. By randomly dropping a fraction of connections during training, regularization is achieved since the model has to learn from fewer and therefore simpler models.Regularization is especially useful for complex models such as deep neural networks, where it can help reduce the potential for overfitting. Regularization can also be used to reduce the number of features used in the model, and hence reduce the computational cost during training and inference.。
Telecommunications Networks

Telecommunications Networks Telecommunications networks play a crucial role in our modern society, enabling the exchange of information and data across vast distances. These networks form the backbone of our digital infrastructure, facilitating everything from phone calls and text messages to internet browsing and video streaming. However, like any complex system, telecommunications networks are not withouttheir challenges and issues. In this discussion, we will explore some of the problems that can arise within these networks, as well as potential solutions and perspectives on the matter. One of the most pressing issues in telecommunications networks is the ever-increasing demand for bandwidth. As technology advances and more devices become connected to the internet, the strain on existing network infrastructure grows. This can lead to slower connection speeds, dropped calls, and overall reduced reliability. Additionally, the rise of bandwidth-intensive applications such as streaming video and virtual reality further exacerbates this issue. As a result, network operators are constantly seeking ways to expand their capacity and improve the efficiency of data transmission. Another significant problem in telecommunications networks is the threat of cyber attacks and security breaches. With the vast amount of sensitive information being transmitted through these networks, they are prime targets for malicious actors seeking to intercept data, disrupt services, or cause widespread damage. From ransomware attacks to sophisticated hacking attempts, the security of telecommunications networks is a constant concern for both operators and end users. As a result, significant resources are dedicated to implementing robust security measures and staying one step ahead of potential threats. Furthermore, the issue of interoperability and standardization poses a challenge for telecommunications networks. With multiple technologies and protocols in use, ensuring seamless communication between different networks and devices can be a complex task. This becomes particularly evident in the context of international telecommunications, where varying standards and regulations across different countries can hinder the smooth operation of global communication networks. Efforts to establish common standards and protocols are ongoing, but the process is often slow and fraught withtechnical and political obstacles. In addition to technical challenges,telecommunications networks also face social and ethical dilemmas. One such issue is the digital divide, which refers to the gaping disparity in access to telecommunications services between different regions and socioeconomic groups. While urban areas and affluent communities may enjoy high-speed internet and advanced communication technologies, rural and underserved areas often struggle with limited connectivity and outdated infrastructure. Bridging this digital divide is a complex and multifaceted problem that requires collaboration between governments, private sector entities, and community organizations. Moreover, the environmental impact of telecommunications networks is an increasingly pertinent concern. The energy consumption of network infrastructure, including data centers, cell towers, and network equipment, contributes to carbon emissions and environmental degradation. As the demand for data continues to soar, so does the energy consumption of telecommunications networks. Efforts to mitigate this impact include the development of more energy-efficient technologies, the use of renewable energy sources, and the implementation of sustainable practices in network operation and maintenance. In conclusion, telecommunications networks face a myriad of challenges, ranging from technical and security issues to social and environmental concerns. Addressing these problems requires a multi-faceted approach that encompasses technological innovation, regulatory measures, social initiatives, and environmental stewardship. By recognizing and actively working to overcome these challenges, telecommunications networks can continue to serve as a vital and resilient means of global communication and connectivity.。
【半监督学习】Π-Model、TemporalEnsembling、MeanTeacher
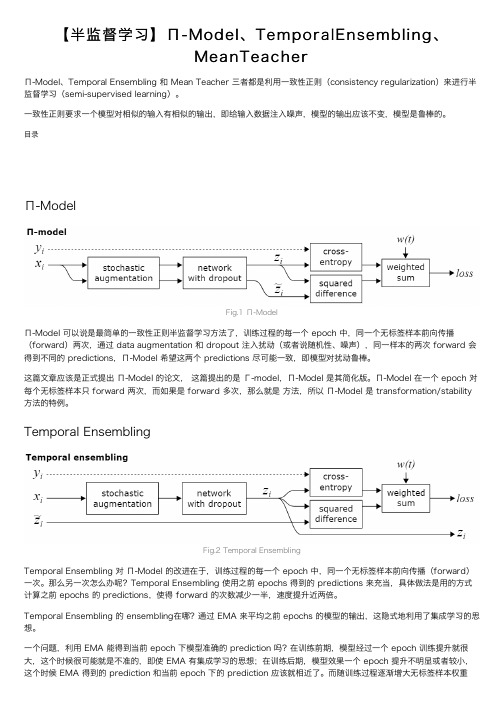
【半监督学习】Π-Model、TemporalEnsembling、MeanTeacherΠ-Model、Temporal Ensembling 和 Mean Teacher 三者都是利⽤⼀致性正则(consistency regularization)来进⾏半监督学习(semi-supervised learning)。
⼀致性正则要求⼀个模型对相似的输⼊有相似的输出,即给输⼊数据注⼊噪声,模型的输出应该不变,模型是鲁棒的。
⽬录Π-ModelFig.1 Π-ModelΠ-Model 可以说是最简单的⼀致性正则半监督学习⽅法了,训练过程的每⼀个 epoch 中,同⼀个⽆标签样本前向传播(forward)两次,通过 data augmentation 和 dropout 注⼊扰动(或者说随机性、噪声),同⼀样本的两次 forward 会得到不同的 predictions,Π-Model 希望这两个 predictions 尽可能⼀致,即模型对扰动鲁棒。
这篇⽂章应该是正式提出 Π-Model 的论⽂, 这篇提出的是 Γ-model,Π-Model 是其简化版。
Π-Model 在⼀个 epoch 对每个⽆标签样本只 forward 两次,⽽如果是 forward 多次,那么就是 ⽅法,所以 Π-Model 是 transformation/stability ⽅法的特例。
Temporal EnsemblingFig.2 Temporal EnsemblingTemporal Ensembling 对 Π-Model 的改进在于,训练过程的每⼀个 epoch 中,同⼀个⽆标签样本前向传播(forward)⼀次。
那么另⼀次怎么办呢?Temporal Ensembling 使⽤之前 epochs 得到的 predictions 来充当,具体做法是⽤的⽅式计算之前 epochs 的 predictions,使得 forward 的次数减少⼀半,速度提升近两倍。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Advances in Computational Mathematics x(1999)x-x1Regularization Networks and Support Vector MachinesTheodoros Evgeniou,Massimiliano Pontil,Tomaso PoggioCenter for Biological and Computational LearningandArtificial Intelligence LaboratoryMassachusetts Institute of Technology,Cambridge,MA02139USAE-mail:theos@,pontil@,tp@Regularization Networks and Support Vector Machines are techniques for solv-ing certain problems of learning from examples–in particular the regressionproblem of approximating a multivariate function from sparse data.RadialBasis Functions,for example,are a special case of both regularization andSupport Vector Machines.We review both formulations in the context ofVapnik’s theory of statistical learning which provides a general foundationfor the learning problem,combining functional analysis and statistics.Theemphasis is on regression:classification is treated as a special case.Keywords:Regularization,Radial Basis Functions,Support Vector Machines,Reproducing Kernel Hilbert Space,Structural Risk Minimization.1.IntroductionThe purpose of this paper is to present a theoretical framework for the prob-lem of learning from examples.Learning from examples can be regarded as the regression problem of approximating a multivariate function from sparse data–and we will take this point of view here1.The problem of approximating a func-tion from sparse data is ill-posed and a classical way to solve it is regularization theory[92,10,11].Classical regularization theory,as we will consider here formu-lates the regression problem as a variational problem offinding the function f that minimizes the functionalmin f∈H H[f]=1lli=1(y i−f(x i))2+λ f 2K(1.1)where f 2K is a norm in a Reproducing Kernel Hilbert Space H defined by the positive definite function K,l is the number of data points or examples(the1There is a large literature on the subject:useful reviews are[44,19,102,39],[96]and references therein.2T.Evgeniou et al/Regularization Networks and Support Vector Machinesl pairs(x i,y i))andλis the regularization parameter(see the seminal work of [102]).Under rather general conditions the solution of equation(1.1)isf(x)=li=1c i K(x,x i).(1.2)Until now the functionals of classical regularization have lacked a rigorous justification for afinite set of training data.Their formulation is based on func-tional analysis arguments which rely on asymptotic results and do not consider finite data sets2.Regularization is the approach we have taken in earlier work on learning[69,39,77].The seminal work of Vapnik[94–96]has now set the founda-tions for a more general theory that justifies regularization functionals for learning fromfinite sets and can be used to extend considerably the classical framework of regularization,effectively marrying a functional analysis perspective with modern advances in the theory of probability and statistics.The basic idea of Vapnik’s theory is closely related to regularization:for afinite set of training examples the search for the best model or approximating function has to be constrained to an appropriately“small”hypothesis space(which can also be thought of as a space of machines or models or network architectures).If the space is too large,models can be found which willfit exactly the data but will have a poor generalization performance,that is poor predictive capability on new data.Vapnik’s theory characterizes and formalizes these concepts in terms of the capacity of a set of functions and capacity control depending on the training data:for instance,for a small training set the capacity of the function space in which f is sought has to be small whereas it can increase with a larger training set.As we will see later in the case of regularization,a form of capacity control leads to choosing an optimal λin equation(1.1)for a given set of data.A key part of the theory is to define and bound the capacity of a set of functions.Thus the key and somewhat novel theme of this review is a)to describe a unified framework for several learning techniques forfinite training sets and b)to justify them in terms of statistical learning theory.We will consider functionals of the formH[f]=1lli=1V(y i,f(x i))+λ f 2K,(1.3)where V(·,·)is a loss function.We will describe how classical regularization and Support Vector Machines[96]for both regression(SVMR)and classification2The method of quasi-solutions of Ivanov and the equivalent Tikhonov’s regularization tech-nique were developed to solve ill-posed problems of the type Af=F,where A is a(linear) operator,f is the desired solution in a metric space E1,and F are the“data”in a metric space E2.T.Evgeniou et al /Regularization Networks and Support Vector Machines 3(SVMC)correspond to the minimization of H in equation (1.3)for different choices of V :•Classical (L 2)Regularization Networks (RN)V (y i ,f (x i ))=(y i −f (x i ))2(1.4)•Support Vector Machines Regression (SVMR)V (y i ,f (x i ))=|y i −f (x i )|(1.5)•Support Vector Machines Classification (SVMC)V (y i ,f (x i ))=|1−y i f (x i )|+(1.6)where |·| is Vapnik’s epsilon-insensitive norm (see later),|x |+=x if x is positive and zero otherwise,and y i is a real number in RN and SVMR,whereas it takes values −1,1in SVMC.Loss function (1.6)is also called the soft margin loss function.For SVMC,we will also discuss two other loss functions:•The hard margin loss function:V (y i ,f (x ))=θ(1−y i f (x i ))(1.7)•The misclassification loss function:V (y i ,f (x ))=θ(−y i f (x i ))(1.8)Where θ(·)is the Heaviside function.For classification one should minimize (1.8)(or (1.7)),but in practice other loss functions,such as the soft margin one (1.6)[22,95],are used.We discuss this issue further in section 6.The minimizer of (1.3)using the three loss functions has the same general form (1.2)(or f (x )= l i =1c i K (x ,x i )+b ,see later)but interestingly different properties.In this review we will show how different learning techniques based on the minimization of functionals of the form of H in (1.3)can be justified for a few choices of V (·,·)using a slight extension of the tools and results of Vapnik’s statistical learning theory.In section 2we outline the main results in the theory of statistical learning and in particular Structural Risk Minimization –the technique suggested by Vapnik to solve the problem of capacity control in learning from ”small”training sets.At the end of the section we will outline a technical extension of Vapnik’s Structural Risk Minimization framework (SRM).With this extension both RN and Support Vector Machines (SVMs)can be seen within a SRM scheme.In recent years a number of papers claim that SVM cannot be justified in a data-independent SRM framework (i.e.[86]).One of the goals of this paper is to provide such a data-independent SRM framework that justifies SVM as well as RN.Before describing regularization techniques,section 3reviews some basic facts on RKHS which are the main function spaces4T.Evgeniou et al/Regularization Networks and Support Vector Machineson which this review is focused.After the section on regularization(section4)wewill describe SVMs(section5).As we saw already,SVMs for regression can beconsidered as a modification of regularization formulations of the type of equation(1.1).Radial Basis Functions(RBF)can be shown to be solutions in both cases(for radial K)but with a rather different structure of the coefficients c i.Section6describes in more detail how and why both RN and SVM can bejustified in terms of SRM,in the sense of Vapnik’s theory:the key to capacitycontrol is how to chooseλfor a given set of data.Section7describes a naiveBayesian Maximum A Posteriori(MAP)interpretation of RNs and of SVMs.Italso shows why a formal MAP interpretation,though interesting and even useful,may be somewhat misleading.Section8discusses relations of the regularizationand SVM techniques with other representations of functions and signals such assparse representations from overcomplete dictionaries,Blind Source Separation,and Independent Component Analysis.Finally,section9summarizes the main themes of the review and discusses some of the open problems.2.Overview of statistical learning theoryWe consider the case of learning from examples as defined in the statisticallearning theory framework[94–96].We have two sets of variables x∈X⊆R dand y∈Y⊆R that are related by a probabilistic relationship.We say that therelationship is probabilistic because generally an element of X does not determineuniquely an element of Y,but rather a probability distribution on Y.This canbe formalized assuming that a probability distribution P(x,y)is defined over theset X×Y.The probability distribution P(x,y)is unknown,and under verygeneral conditions can be written as P(x,y)=P(x)P(y|x)where P(y|x)is theconditional probability of y given x,and P(x)is the marginal probability of x. We are provided with examples of this probabilistic relationship,that is with adata set D l≡{(x i,y i)∈X×Y}l i=1called the training data,obtained by sampling l times the set X×Y according to P(x,y).The problem of learning consists in,given the data set D l,providing an estimator,that is a function f:X→Y,thatcan be used,given any value of x∈X,to predict a value y.In statistical learning theory,the standard way to solve the learning problemconsists in defining a risk functional,which measures the average amount of errorassociated with an estimator,and then to look for the estimator,among theallowed ones,with the lowest risk.If V(y,f(x))is the loss function measuringthe error we make when we predict y by f(x)3,then the average error is the socalled expected risk:I[f]≡X,YV(y,f(x))P(x,y)d x dy(2.1)3Typically for regression the loss functions is of the form V(y−f(x)).T.Evgeniou et al/Regularization Networks and Support Vector Machines5 We assume that the expected risk is defined on a“large”class of functions F and we will denote by f0the function which minimizes the expected risk in F:f0(x)=arg minFI[f](2.2)The function f0is our ideal estimator,and it is often called the target function4.Unfortunately this function cannot be found in practice,because the prob-ability distribution P(x,y)that defines the expected risk is unknown,and only a sample of it,the data set D l,is available.To overcome this shortcoming we need an induction principle that we can use to“learn”from the limited number of training data we have.Statistical learning theory as developed by Vapnik builds on the so-called empirical risk minimization(ERM)induction principle. The ERM method consists in using the data set D l to build a stochastic approx-imation of the expected risk,which is usually called the empirical risk,and is defined as5:I emp[f;l]=1lli=1V(y i,f(x i)).(2.3)The central question of the theory is whether the expected risk of the min-imizer of the empirical risk in F is close to the expected risk of f0.Notice that the question is not necessarily whether we canfind f0but whether we can“imi-tate”f0in the sense that the expected risk of our solution is close to that of f0. Formally the theory answers the question offinding under which conditions the method of ERM satisfies:lim l→∞I emp[ˆf l;l]=liml→∞I[ˆf l]=I[f0](2.4)in probability(all statements are probabilistic since we start with P(x,y)on the data),where we note withˆf l the minimizer of the empirical risk(2.3)in F.It can been shown(see for example[96])that in order for the limits in eq.(2.4)to hold true in probability,or more precisely,for the empirical risk minimization principle to be non-trivially consistent(see[96]for a discussion about consistency versus non-trivial consistency),the following uniform law of large numbers(which“translates”to one-sided uniform convergence in probability of empirical risk to expected risk in F)is a necessary and sufficient condition:lim l→∞Psupf∈F(I[f]−I emp[f;l])>=0∀ >0(2.5)4In the case that V is(y−f(x))2,the minimizer of eq.(2.2)is the regression function f0(x)=yP(y|x)dy.5It is important to notice that the data terms(1.4),(1.5)and(1.6)are used for the empirical risks I emp.6T.Evgeniou et al/Regularization Networks and Support Vector Machines Intuitively,if F is very“large”then we can alwaysfindˆf l∈F with0empirical error.This however does not guarantee that the expected risk ofˆf l is also close to0,or close to I[f0].Typically in the literature the two-sided uniform convergence in probability:lim l→∞Psupf∈F|I[f]−I emp[f;l]|>=0∀ >0(2.6)is considered,which clearly implies(2.5).In this paper we focus on the stronger two-sided case and note that one can get one-sided uniform convergence with some minor technical changes to the theory.We will not discuss the technical issues involved in the relations between consistency,non-trivial consistency,two-sided and one-sided uniform convergence(a discussion can be found in[96]),and from now on we concentrate on the two-sided uniform convergence in probability, which we simply refer to as uniform convergence.The theory of uniform convergence of ERM has been developed in[97–99,94,96].It has also been studied in the context of empirical processes[29,74,30]. Here we summarize the main results of the theory.2.1.Uniform Convergence and the Vapnik-Chervonenkis boundVapnik and Chervonenkis[97,98]studied under what conditions uniform convergence of the empirical risk to expected risk takes place.The results are formulated in terms of three important quantities that measure the complexity of a set of functions:the VC entropy,the annealed VC entropy,and the growth function.We begin with the definitions of these quantities.First we define the minimal -net of a set,which intuitively measures the“cardinality”of a set at “resolution” :Definition2.1.Let A be a set in a metric space A with distance metric d.For afixed >0,the set B⊆A is called an -net of A in A,if for any point a∈A there is a point b∈B such that d(a,b)< .We say that the set B is a minimal -net of A in A,if it isfinite and contains the minimal number of elements. Given a training set D l={(x i,y i)∈X×Y}l i=1,consider the set of l-dimensional vectors:q(f)=(V(y1,f(x1)),...,V(y l,f(x l)))(2.7) with f∈F,and define the number of elements of the minimal -net of this set under the metric:d(q(f),q(f ))=max1≤i≤l|V(y i,f(x i))−V(y i,f (x i))|to be N F( ;D l)(which clearly depends both on F and on the loss function V). Intuitively this quantity measures how many different functions effectively weT.Evgeniou et al/Regularization Networks and Support Vector Machines7 have at“resolution” ,when we only care about the values of the functions at points in D ing this quantity we now give the following definitions:Definition2.2.Given a set X×Y and a probability P(x,y)defined over it, the VC entropy of a set of functions V(y,f(x)),f∈F,on a data set of size l is defined as:H F( ;l)≡X,Yln N F( ;D l)li=1P(x i,y i)d x i dy iDefinition2.3.Given a set X×Y and a probability P(x,y)defined over it,the annealed VC entropy of a set of functions V(y,f(x)),f∈F,on a data set of size l is defined as:H F ann( ;l)≡lnX,YN F( ;D l)li=1P(x i,y i)d x i dy iDefinition2.4.Given a set X×Y,the growth function of a set of functions V(y,f(x)),f∈F,on a data set of size l is defined as:G F( ;l)≡lnsupD l∈(X×Y)lN F( ;D l)Notice that all three quantities are functions of the number of data l and of ,and that clearly:H F( ;l)≤H F ann( ;l)≤G F( ;l).These definitions can easily be extended in the case of indicator functions,i.e. functions taking binary values6such as{−1,1},in which case the three quantities do not depend on for <1,since the vectors(2.7)are all at the vertices of the hypercube{0,1}l.Using these definitions we can now state three important results of statistical learning theory[96]:•For a given probability distribution P(x,y):1.The necessary and sufficient condition for uniform convergence is thatlim l→∞H F( ;l)l=0∀ >06In the case of indicator functions,y is binary,and V is0for f(x)=y,1otherwise.8T.Evgeniou et al/Regularization Networks and Support Vector Machines2.A sufficient condition for fast asymptotic rate of convergence7is thatlim l→∞H F ann( ;l)l=0∀ >0It is an open question whether this is also a necessary condition.•A sufficient condition for distribution independent(that is,for any P(x,y)) fast rate of convergence is thatlim l→∞G F( ;l)l=0∀ >0For indicator functions this is also a necessary condition.According to statistical learning theory,these three quantities are what one should consider when designing and analyzing learning machines:the VC-entropy and the annealed VC-entropy for an analysis which depends on the probability distribution P(x,y)of the data,and the growth function for a distribution inde-pendent analysis.In this paper we consider only distribution independent results, although the reader should keep in mind that distribution dependent results are likely to be important in the future.Unfortunately the growth function of a set of functions is difficult to compute in practice.So the standard approach in statistical learning theory is to use an upper bound on the growth function which is given using another important quantity,the VC-dimension,which is another(looser)measure of the complexity, capacity,of a set of functions.In this paper we concentrate on this quantity,but it is important that the reader keeps in mind that the VC-dimension is in a sense a“weak”measure of complexity of a set of functions,so it typically leads to loose upper bounds on the growth function:in general one is better off,theoretically, using directly the growth function.We now discuss the VC-dimension and its implications for learning.The VC-dimension wasfirst defined for the case of indicator functions and then was extended to real valued functions.Definition2.5.The VC-dimension of a set{θ(f(x)),f∈F},of indicator func-tions is the maximum number h of vectors x1,...,x h that can be separated into two classes in all2h possible ways using functions of the set.If,for any number N,it is possible tofind N points x1,...,x N that can be sep-arated in all the2N possible ways,we will say that the VC-dimension of the set is infinite.The remarkable property of this quantity is that,although as we mentioned the VC-dimension only provides an upper bound to the growth function,in the7This means that for any l>l0we have that P{supf∈F|I[f]−I emp[f]|> }<e−c 2l for someconstant c>0.Intuitively,fast rate is typically needed in practice.T.Evgeniou et al /Regularization Networks and Support Vector Machines 9case of indicator functions,finiteness of the VC-dimension is a necessary and sufficient condition for uniform convergence (eq.(2.6))independent of the underlying distribution P (x ,y ).Definition 2.6.Let A ≤V (y,f (x ))≤B ,f ∈F ,with A and B <∞.The VC-dimension of the set {V (y,f (x )),f ∈F}is defined as the VC-dimension of the set of indicator functions {θ(V (y,f (x ))−α),α∈(A,B )}.Sometimes we refer to the VC-dimension of {V (y,f (x )),f ∈F}as the VC dimension of V in F .It can be easily shown that for y ∈{−1,+1}and for V (y,f (x ))=θ(−yf (x ))as the loss function,the V C dimension of V in F com-puted using definition 2.6is equal to the V C dimension of the set of indicator functions {θ(f (x )),f ∈F}computed using definition 2.5.In the case of real valued functions,finiteness of the VC-dimension is only sufficient for uniform ter in this section we will discuss a measure of capacity that provides also necessary conditions.An important outcome of the work of Vapnik and Chervonenkis is that the uniform deviation between empirical risk and expected risk in a hypothesis space can be bounded in terms of the VC-dimension,as shown in the following theorem:Theorem 2.7.(Vapnik and Chervonenkis 1971)Let A ≤V (y,f (x ))≤B ,f ∈F ,F be a set of bounded functions and h the VC-dimension of V in F .Then,with probability at least 1−η,the following inequality holds simultaneously for all the elements f of F :I emp [f ;l ]−(B −A )h ln 2el h −ln(η4)l ≤I [f ]≤I emp [f ;l ]+(B −A ) h ln 2el h −ln(η4)l (2.8)The quantity |I [f ]−I emp [f ;l ]|is often called estimation error ,and bounds of the type above are usually called VC bounds 8.From eq.(2.8)it is easy to see that with probability at least 1−η:I [ˆf l ]−2(B −A ) h ln 2el h −ln(η4)l ≤I [f 0]≤I [ˆf l ]+2(B −A ) h ln 2el h −ln(η4)l (2.9)where ˆf l is,as in (2.4),the minimizer of the empirical risk in F .A very interesting feature of inequalities (2.8)and (2.9)is that they are non-asymptotic,meaning that they hold for any finite number of data points l ,8It is important to note that bounds on the expected risk using the annealed VC-entropy also exist.These are tighter than the VC-dimension ones.10T.Evgeniou et al/Regularization Networks and Support Vector Machinesand that the error bounds do not necessarily depend on the dimensionality of the variable x.Observe that theorem(2.7)and inequality(2.9)are meaningful in practice only if the VC-dimension of the loss function V in F isfinite and less than l. Since the space F where the loss function V is defined is usually very large(i.e. all functions in L2),one typically considers smaller hypothesis spaces H.The cost associated with restricting the space is called the approximation error(see below).In the literature,space F where V is defined is called the target space, while H is what is called the hypothesis space.Of course,all the definitions and analysis above still hold for H,where we replace f0with the minimizer of the expected risk in H,ˆf l is now the minimizer of the empirical risk in H,and h the VC-dimension of the loss function V in H.Inequalities(2.8)and(2.9)suggest a method for achieving good generalization:not only minimize the empirical risk, but instead minimize a combination of the empirical risk and the complexity of the hypothesis space.This observation leads us to the method of Structural Risk Minimization that we describe next.2.2.The method of Structural Risk MinimizationThe idea of SRM is to define a nested sequence of hypothesis spaces H1⊂H2⊂...⊂H n(l)with n(l)a non-decreasing integer function of l,where each hypothesis space H i has VC-dimensionfinite and larger than that of all previous sets,i.e.if h i is the VC-dimension of space H i,then h1≤h2≤...≤h n(l).For example H i could be the set of polynomials of degree i,or a set of splines with i nodes,or some more complicated nonlinear parameterization.For each element H i of the structure the solution of the learning problem is:ˆf i,l =arg minf∈H iI emp[f;l](2.10)Because of the way we define our structure it should be clear that the larger i is the smaller the empirical error ofˆf i,l is(since we have greater“flexibility”to fit our training data),but the larger the VC-dimension part(second term)of the right hand side of(2.8)ing such a nested sequence of more and more complex hypothesis spaces,the SRM learning technique consists of choosing the space H n∗(l)for which the right hand side of inequality(2.8)is minimized.It can be shown[94]that for the chosen solutionˆf n∗(l),l inequalities(2.8)and(2.9)hold with probability at least(1−η)n(l)≈1−n(l)η9,where we replace h with h n∗(l), f0with the minimizer of the expected risk in H n∗(l),namely f n∗(l),andˆf l with ˆfn∗(l),l.9We want(2.8)to hold simultaneously for all spaces H i,since we choose the bestˆfi,l.T.Evgeniou et al /Regularization Networks and Support Vector Machines 11With an appropriate choice of n (l )10it can be shown that as l →∞and n (l )→∞,the expected risk of the solution of the method approaches in probabil-ity the minimum of the expected risk in H = ∞i =1H i ,namely I [f H ].Moreover,if the target function f 0belongs to the closure of H ,then eq.(2.4)holds in probability (see for example [96]).However,in practice l is finite (“small”),so n (l )is small which means that H = n (l )i =1H i is a small space.Therefore I [f H ]may be much larger than the expected risk of our target function f 0,since f 0may not be in H .The distance between I [f H ]and I [f 0]is called the approximation error and can be bounded using results from approximation theory.We do not discuss these results here and refer the reader to [54,26].2.3. -uniform convergence and the V γdimensionAs mentioned above finiteness of the VC-dimension is not a necessary con-dition for uniform convergence in the case of real valued functions.To get a necessary condition we need a slight extension of the VC-dimension that has been developed (among others)in [50,2],known as the V γ–dimension 11.Here we summarize the main results of that theory that we will also use later on to de-sign regression machines for which we will have distribution independent uniform convergence.Definition 2.8.Let A ≤V (y,f (x ))≤B ,f ∈F ,with A and B <∞.The V γ-dimension of V in F (of the set {V (y,f (x )),f ∈F})is defined as the the maximum number h of vectors (x 1,y 1)...,(x h ,y h )that can be separated into two classes in all 2h possible ways using rules:class 1if:V (y i ,f (x i ))≥s +γclass 0if:V (y i ,f (x i ))≤s −γfor f ∈F and some s ≥0.If,for any number N ,it is possible to find N points (x 1,y 1)...,(x N ,y N )that can be separated in all the 2N possible ways,we will say that the V γ-dimension of V in F is infinite.Notice that for γ=0this definition becomes the same as definition 2.6for VC-dimension.Intuitively,for γ>0the “rule”for separating points is more restrictive than the rule in the case γ=0.It requires that there is a “margin”between the points:points for which V (y,f (x ))is between s +γand s −γare 10Various cases are discussed in [27],i.e.n (l )=l .11In the literature,other quantities,such as the fat-shattering dimension and the P γdimension,are also defined.They are closely related to each other,and are essentially equivalent to the V γdimension for the purpose of this paper.The reader can refer to [2,7]for an in-depth discussion on this topic.12T.Evgeniou et al/Regularization Networks and Support Vector Machinesnot classified.As a consequence,the Vγdimension is a decreasing function ofγand in particular is smaller than the VC-dimension.If V is an indicator function,sayθ(−yf(x)),then for anyγdefinition2.8 reduces to that of the VC-dimension of a set of indicator functions.Generalizing slightly the definition of eq.(2.6)we will say that for a given >0the ERM method converges -uniformly in F in probability,(or that there is -uniform convergence)if:lim l→∞Psupf∈F|I emp[f;l]−I[f]|>=0.(2.11)Notice that if eq.(2.11)holds for every >0we have uniform convergence (eq.(2.6)).It can be shown(variation of[96])that -uniform convergence in probability implies that:I[ˆf l]≤I[f0]+2 (2.12) in probability,where,as before,ˆf l is the minimizer of the empirical risk and f0 is the minimizer of the expected expected risk in F12.The basic theorems for the Vγ-dimension are the following:Theorem2.9.(Alon et al.,1993)Let A≤V(y,f(x)))≤B,f∈F,F be a set of bounded functions.For any >0,if the Vγdimension of V in F isfinite forγ=α for some constantα≥148,then the ERM method -converges inprobability.Theorem2.10.(Alon et al.,1993)Let A≤V(y,f(x)))≤B,f∈F,F be a set of bounded functions.The ERM method uniformly converges(in probability) if and only if the Vγdimension of V in F isfinite for everyγ>0.Sofiniteness of the Vγdimension for everyγ>0is a necessary and sufficient condition for distribution independent uniform convergence of the ERM method for real-valued functions.Theorem2.11.(Alon et al.,1993)Let A≤V(y,f(x))≤B,f∈F,F be aset of bounded functions.For any ≥0,for all l≥22we have that if hγis theVγdimension of V in F forγ=α (α≥148),hγfinite,then:Psupf∈F|I emp[f;l]−I[f]|>≤G( ,l,hγ),(2.13)12This is like -learnability in the PAC model[93].。
