ASA5520 C2800
asa5520防火墙透明模式的配置例子

asa5520防火墙透明模式的配置例子ciscoasa# sh run: Saved:ASA Version 7.2(3)!firewall transparenthostname ciscoasadomain-name default.domain.invalidenable password 8Ry2YjIyt7RRXU24 encryptednames!interface GigabitEthernet0/0nameif outsidesecurity-level 0!interface GigabitEthernet0/1nameif insidesecurity-level 100!interface GigabitEthernet0/2shutdownno nameifno security-level!interface GigabitEthernet0/3shutdownno nameifno security-level!interface Management0/0nameif managementsecurity-level 100ip address 192.168.1.1 255.255.255.0management-only!passwd 2KFQnbNIdI.2KYOU encryptedftp mode passivedns server-group DefaultDNSdomain-name default.domain.invalidaccess-list acl_inside extended permit ip any any access-list acl_inside extended permit icmp any anyaccess-list acl_outside extended permit tcp any any eq 3306access-list acl_outside extended permit tcp any any eq wwwaccess-list acl_outside extended permit tcp any any eq 8080access-list acl_outside extended permit tcp any any eq httpsaccess-list acl_outside extended permit tcp any any eq sqlnetaccess-list acl_outside extended permit tcp any any eq ftpaccess-list acl_outside extended permit tcp any any eq 1433access-list acl_outside extended permit esp any anyaccess-list acl_outside extended permit udp any any eq isakmpaccess-list acl_outside extended permit tcp any any eq pop3access-list acl_outside extended permit tcp any any eq smtpaccess-list acl_outside extended permit icmp any anypager lines 24mtu outside 1500mtu inside 1500mtu management 1500ip address 172.16.177.208 255.255.255.0no failovericmp unreachable rate-limit 1 burst-size 1asdm image disk0:/ASDM-523.BINno asdm history enablearp timeout 14400access-group acl_outside in interface outsideaccess-group acl_inside in interface insidetimeout xlate 3:00:00timeout conn 0:20:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout uauth 0:05:00 absolutehttp server enablehttp 192.168.1.0 255.255.255.0 managementhttp 0.0.0.0 0.0.0.0 insideno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstarttelnet timeout 5ssh timeout 5console timeout 0!class-map inspection_defaultmatch default-inspection-traffic!!policy-map type inspect dns preset_dns_mapparametersmessage-length maximum 512policy-map global_policyclass inspection_defaultinspect dns preset_dns_mapinspect ftpinspect h323 h225inspect h323 rasinspect rshinspect rtspinspect esmtpinspect sqlnetinspect skinnyinspect sunrpcinspect xdmcpinspect sipinspect netbiosinspect tftpinspect pptp!service-policy global_policy globalusername cisco password 3USUcOPFUiMCO4Jk encryptedprompt hostname contextCryptochecksum:4682fd668f251c28d32a0cb82a3ac5f3: endciscoasa#注意点:语句ip address 172.16.177.208 255.255.255.0是在interface GigabitEthernet0/0下配的,自己跑到外面来了,如果不配这个,好像ping不通。
ASA5500系列防火墙

ASA IDS 模块ASA 防病毒模块ASA5500 产品订货编号产品名称 产品编号Cisco ASA 5510设备(3个快速以太网端口,50个VPN对,三重数 字加密标准/高级加密标准〔3DES/AES〕) Cisco ASA 5510设备,带AIP-SSM-10(3个快速以太网端口,50个 VPN对,AIP-SSM-10,3DES/AES) Cisco ASA 5510安全增强设备(5个快速以太网端口,150个VPN 对,3DES/AES)ASA5510-BUN-K9 ASA5510-AIP10-K9 ASA5510-SEC-BUNK9Cisco ASA 5520设备(4个千兆以太网端口+1个快速以太网端口, ASA5520-BUN-K9 300个VPN对,3DES/AES) Cisco ASA 5520设备,带AIP-SSM-10(4个千兆以太网端口+1个 快速以太网端口,300个VPN对,AIP-SSM-10,3DES/AES) Cisco ASA 5520设备,带AIP-SSM-20(4个千兆以太网端口+1个 快速以太网端口,300个VPN对,AIP-SSM-20,3DES/AES) ASA5520-AIP10-K9 ASA5520-AIP20-K9Cisco ASA 5540设备(4个千兆以太网端口+1个快速以太网端口, ASA5540-BUN-K9 500个VPN对,3DES/AES) Cisco ASA 5540设备,带AIP-SSM-20(4个千兆以太网端口+1个 快速以太网端口,500个VPN对,AIP-SSM-20,3DES/AES) ASA5540-AIP20-K9ASA IPS bundle 订货编号ASA5510-AIP10-K9 ASA5520-AIP10-K9 ASA5520-AIP20-K9 ASA5540-AIP20-K9 ASA 5510 Appliance with AIP-SSM-10, SW, 3FE, 3DES/AES ASA 5520 Appliance w/ AIP-SSM-10, SW, HA, 4GE+1FE, 3DES/AES ASA 5520 Appliance w/ AIP-SSM-20, SW, HA, 4GE+1FE, 3DES/AES ASA 5540 Appliance w/ AIP-SSM-20, SW, HA, 4GE+1FE, 3DES/AES B B B B $12,7 92 $18,7 43 $23,9 93 $49,9 90ASA Anti-X bundle 订货编号ASA5510-CSC10-K9 ASA5510-CSC20-K9 ASA5520-CSC10-K9 ASA5520-CSC20-K9 ASA 5510 Appl w/ CSC10, SW, 50 Usr AV/Spy, 1 YR Subscript ASA 5510 Appl w/ CSC20, SW, 500 Usr AV/Spy, 1 YR Subscript ASA 5520 Appl w/ CSC10, SW, 50 Usr AV/Spy, 1 YR Subscript ASA 5520 Appl w/ CSC20, SW, 500 Usr AV/Spy, 1 YR Subscript N/A N/A N/A N/A $14,3 90 $25,1 90 $22,3 90 $33,1 90ASA Anti-X 模块扩展 订货编号ASA-CSC10-PLUS ASA-CSC10-PLUS= ASA-CSC20-PLUS ASA-CSC10-USR-100 ASA-CSC10-USR-100= ASA-CSC10-USR-250 ASA-CSC10-USR-250= ASA-CSC10-USR-500 ASA-CSC10-USR-500= ASA-CSC20-USR-750 ASA-CSC20-USR-750= ASA-CSC20-USR-1K ASA-CSC20-USR-1K= ASA-CSC10-100-250= ASA 5500 CSC SSM10 Plus Lic. (Spam/URL/Phish, 1Yr Subscript) ASA 5500 CSC SSM10 Plus Lic. (Spam/URL/Phish, 1Yr Subscript) ASA 5500 CSC SSM20 Plus Lic. (Spam/URL/Phish, 1Yr Subscript) ASA 5500 Content Security SSM-10 100 User License ASA 5500 Content Security SSM-10 100 User License ASA 5500 Content Security SSM-10 250 User License ASA 5500 Content Security SSM-10 250 User License ASA 5500 Content Security SSM-10 500 User License ASA 5500 Content Security SSM-10 500 User License ASA 5500 Content Security SSM-20 750 User License ASA 5500 Content Security SSM-20 750 User License ASA 5500 Content Security SSM-20 1000 User License ASA 5500 Content Security SSM-20 1000 User License ASA 5500 Content Security SSM-10 100 to 250 User License Upg N/A N/A N/A N/A N/A N/A N/A N/A N/A N/A N/A N/A N/A N/A $3,15 0 $3,15 0 $6,30 0 $1,050 $1,050 $3,150 $3,150 $10,50 0 $10,50 0 $6,300 $6,300 $12,60 0 $12,60 0 $2,520ASA FireWall 技术简介ASA IPS 技术简介如何防御攻击?• 防火墙不能有效检测 并阻断夹杂在正常流 量中的攻击代码 IDS由于旁路部署,无 法阻断攻击,亡羊补 牢,侧重安全状态监控入侵检 测系统 IDS••IPS在线部署,主动防 御,实时阻断攻击入侵保护 系统IPS IDSIPSIDS &IPS 区别IDS : Intrusion Detection system入侵检测系统IPS : Intrunsion Prevention System 入侵防御系统 IPS 产品和IDS产品最大的不同: IPS产品通常串接在防火墙和交换机之间,这点和以前 基于网络的IDS不同,串联在防火墙后面的IPS检查所 有进出的数据包,并且根据特征检测来识别攻击的数据 包,在数据包到达目标之前就会被IPS产品中途截获, 并且采取丢弃数据包、中止会话、同时修改防火墙策 略,进行报警和日志的记录等动作,达到“防御”的目的。
asa5520防火墙透明模式的配置例子
asa5520防火墙透明模式的配置例子ciscoasa# sh run: Saved:ASA Version (3)!firewall transparenthostname ciscoasadomain-nameenable password 8Ry2YjIyt7RRXU24 encrypted names!interface GigabitEthernet0/0nameif outsidesecurity-level 0!interface GigabitEthernet0/1nameif insidesecurity-level 100!interface GigabitEthernet0/2shutdownno nameifno security-level!interface GigabitEthernet0/3shutdownno nameifno security-level!interface Management0/0nameif managementsecurity-level 100ip addressmanagement-only!passwd encryptedftp mode passivedns server-group DefaultDNSdomain-nameaccess-list acl_inside extended permit ip any anyaccess-list acl_inside extended permit icmp any anyaccess-list acl_outside extended permit tcp any any eq 3306 access-list acl_outside extended permit tcp any any eq www access-list acl_outside extended permit tcp any any eq 8080 access-list acl_outside extended permit tcp any any eq https access-list acl_outside extended permit tcp any any eq sqlnetaccess-list acl_outside extended permit tcp any any eq ftpaccess-list acl_outside extended permit tcp any any eq 1433access-list acl_outside extended permit esp any anyaccess-list acl_outside extended permit udp any any eq isakmpaccess-list acl_outside extended permit tcp any any eq pop3access-list acl_outside extended permit tcp any any eq smtpaccess-list acl_outside extended permit icmp any anypager lines 24mtu outside 1500mtu inside 1500mtu management 1500ip addressno failovericmp unreachable rate-limit 1 burst-size 1asdm image disk0:/no asdm history enablearp timeout 14400access-group acl_outside in interface outsideaccess-group acl_inside in interface insidetimeout xlate 3:00:00timeout conn 0:20:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout uauth 0:05:00 absolutehttp server enablehttp managementhttp insideno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstart telnet timeout 5ssh timeout 5console timeout 0!class-map inspection_defaultmatch default-inspection-traffic!!policy-map type inspect dns preset_dns_mapparametersmessage-length maximum 512policy-map global_policyclass inspection_defaultinspect dns preset_dns_mapinspect ftpinspect h323 h225inspect h323 rasinspect rshinspect rtspinspect esmtpinspect sqlnetinspect skinnyinspect sunrpcinspect xdmcpinspect sipinspect netbiosinspect tftpinspect pptp!service-policy global_policy globalusername cisco password 3USUcOPFUiMCO4Jk encryptedprompt hostname contextCryptochecksum:4682fd668f251c28d32a0cb82a3ac5f3: endciscoasa#注意点:语句ip address 是在interface GigabitEthernet0/0下配的,自己跑到外面来了,如果不配这个,好像ping不通。
ASA型号及配置命令

ASA型号及配置命令asa复习笔记一、cisco防火墙1.软件防火墙它用于基于IOS软件的设备。
一般来说,客户端上具有应用层智能的状态检测防火墙引擎占CPU和内存资源的2.5%(可以定期欣赏)硬件防火墙(更多优势)应用在一般企业外部网络:pix500系列安全设备、asa5500系列自适应安全设备、catalyst6500系列交换机和cisco7600系列路由器的防火墙服务模块(不可以定期升值)二、 Ciscosa1常见型号:型号asa5505asa5510asa5520asa5540asa5550asa5580规模作用交换机接小型企业、分公司和企业设备成本低,易于部署、集成8个10/100端口快速口远程办公环境以太网交换机中型企业、分公司企业环设备成本低,易于部署,具有高级安全和网络服务境中型企业具有模块化、高性能网络中的高可用性主动/主动服路(小凡模拟器)务,并能连接千兆以太网设备由大中型企业,服务提供商提供高密度,主动/主动高可用性服务和千兆以太网连器接,设备具有高可靠性和高性能接大型企业、服务提供商网千兆级提供高达1.2gb/s的防火墙吞吐量,具有主动口络的高性能设备/主动高可用性服务、光纤和千兆位以太网连接性大型企业、数据中心、和提供王兆位以太网连接运营商网络型号为asa5580-20、asa5580-402.基本配置配置主机名:ciscoasa>enciscoasa#cinft思科ASA(配置)#主机名ASA802域名:asa802(config)#enablepassword123telnet或ssh密码:Asa802(配置)#passwdciscoasa接口名称和安全级别asa802(config-if)#nameifinside(不起名,ping不通)Asa802(如果配置)#安全级别100(值为0-100,值越大,安全级别越高)//默认情况下,outside口安全级别为0,inside口安全级别为100,防火墙允许数据从高安全级别流向低安全级别的接口,但不允许流量从低安全级别流向高安全级别的接口,若要放行,必须做策略,acl放行;若接口的安全级别相同,那么它们之间不允许通信,绝对不允许,但有时有这个需要,故意把它们设成一样。
国内外主流防火墙厂商竞争分析

产品线介绍-UTM产品线
定位
千兆 高端
千兆 中端
百兆 高端 百兆 中端
桌面
天融信型号 黒:X86 红:多核 绿:NP 蓝:ASIC
TG-57K2
TG-562A
TG-5544
TG-440A
TG-330S
TG-3105
裸机 列表价
对应型号
108万 3016B
61.8万 54.8万
1000A FA2
800F
市场销量分析
至08年,销售收入达3.8亿人民币 防火墙与UTM产品的销售收入仍然是占总体75%以上。
40000 35000 30000 25000 20000 15000 10000
5000 0
2006
2007
2008
其他产品销售额 fw销售额 utm销售额
| Hillstone Confidential 7
银川33人
南京分公司 26人
昆明办事处 6人
海南办事处 2人
武汉分公司 16人
山东分公司 40人
天津办事处 7人
北京办事处 6人
行业人
军队军工 13
电信 5人
能源交通 6
金融制造 15
政府 11
中小企业 38人
| Hillstone Confidential 6
|
53H00ilBBlstone
USG-50
Confidential 3
华为华赛 H3C
总纲
天融信 联想网御
Fortinet
网御神州
Juniper Cisco
东软
启明星辰
绿盟
| Hillstone Confidential 4
ASA5520的双机A-A方式配置

拓朴图如下,现有点不明白怎么样将防火墙的接口怎样分配IP ,两个context中的路由指向同一个IP 网关,
原来防火墙的OUTSIDE :10。180。48。253 INS做成两个context a.contextb 两个接口的IP 该怎样做?????
ASA5520/test1(config-if)# ip address 192.168.10.1 255.255.255.0 standby
192.168.10.2
ASA5520(config)# failover //全局模式下面开始failover
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------在第二台ASA5520设备上配置
failover
剩下的ASA会自动同步它的配置
两个5520实现双A,非常好的方案啊,而且这个配置绝对可行,前几天刚刚做过实验了,我觉得八楼的兄弟把中文解释都写出来了,
值得借鉴啊,等有空的时候,我也把做双A的完整配置写出来的
用透明模式完成比较好
在65上起两个VLAN
能給一份完整的配置嗎。特別是兩臺FIREWALL都在透明模式下的,如何做A/A,謝謝!!
ASA5520(config-fover-group)# preempt //配置抢占参数
ASA5520(config-fover-group)# replication http
ASA5520配置

一般网络机构来理解asa5520外网-----asa5520----分别是内网和dmzasa配置都在全局模式下配置,很多跟cisco路由交换的一样(大同小异)第一次连接防火墙时有个初始化配置主要有配置密码,时间,内部ip,和管理ip1、配置主机名、域名、和密码主机名:ciscoasa5520(config)#hostname 5520域名:5520(config)#domain—name 密码:5520(config)#enable password asa5520 (特权密码)5520(config)#password cisco (telnet密码)2、配置接口名字、安全级别5520(config)#int f0/15520(config)#nameif inside (内网,dmz,outside)5520(config)#security-level 100 (安全级别为100,dmz:50,outside:0)5520(config)#ip add 192.168.1.1 255.255.255.0 (配置ip地址)5520(config)#no shut5520(config)#exit查看接口show interface ipbriefshow interface f/03、配置路由5520(config)#route 接口名目标网段掩码下一跳例上网的缺省路由5520(config)#route outside 0.0.0.0 0.0.0.0 61.232.14.815520(config)#route inside 192.168.0.0 0.0.255.255 192.168.1.254查看路由show route4、管理(启用telnet或者ssh)5520(config)#telnet ip或网段掩码接口例:5520(config)#telnet 192.168.2.20 255.255.255.0 inside(表示只允许这个ip地址telnet asa)5520(config)#telnet 192.168.2.0 255.255.255.0 inside (表示允许这个ip段telnet asa)设置telnet超时5520(config)#telnet timeout 30 单位为分ssh为密文传送(RSA密钥对)5520(config)#cryto key generate rsa modulus 1024连接5520(config)#ssh 192.168.2.0 255.255.255.0 inside5520(config)#ssh 0 0 outside 允许外网任意ip连接配置空闲超时ssh timeout 30ssh version 25、远程接入ASDM(cisco的自适应安全管理器)客户端可以用cisco自带的软件也可以装jre走https启用https服务器功能5520(config)#http server enable 端口号(越大越好)设置允许接入网段5520(config)#http 网段|ip 掩码接口名(http 0 0 outside 外网任何ip接入)指定ASDM的映像位置5520(config)#asdm image disk0:/asdmfilse(这个一般用show version产看版本号)配置客户端登录使用的用户名和密码5520(config)# username 用户名password 密码privilege 156、nat的配置(这个好像与pix类似)5520(config)# nat (interface-名)nat-id 本地ip 掩码5520(config)#global (接口名)nat-id 全局ip、网段或接口例:5520(config)#nat-control (启用nat)5520(config)#nat(inside)1 0 0 (可以指定一个网段或者全部)5520(config)#global (outside)1 interface (这就称了pat,当然也可以写一个ip段或者一个ip)5520(config)# global(dmz)1 172.16.1.100-172.16.1.110 意思与上差不多这里要注意:内网到dmz区域都应是nat如果内网到dmz用路由的话,这样可能导致黑客先攻击dmz,然后长区直入到内网。
ASA5520防火墙双机配置
ASA5520防火墙的安装配置说明一、通过超级终端连接防火墙。
先将防火墙固定在机架上,接好电源;用随机带来的一根蓝色的线缆将防火墙与笔记本连接起来。
注意:该线缆是扁平的,一端是RJ-45接口,要接在防火墙的console端口;另一端是串口,要接到笔记本的串口上.建立新连接,给连接起个名字。
选择COM口,具体COM1还是COM3应该根据自己接的COM来选择,一般接COM1就可以。
选择9600,回车就可以连接到命令输入行。
二、防火墙提供4种管理访问模式:1.非特权模式。
防火墙开机自检后,就是处于这种模式。
系统显示为firewall> 2.特权模式。
输入enable进入特权模式,可以改变当前配置。
显示为firewall# 3.配置模式。
在特权模式下输入configure terminal进入此模式,绝大部分的系统配置都在这里进行。
显示为firewall(config)#4.监视模式。
PIX防火墙在开机或重启过程中,按住Escape键或发送一个“Break”字符,进入监视模式。
这里可以更新操作系统映象和口令恢复。
显示为monitor>三、基本配置步骤在PC机上用串口通过cisco产品控制线连接防火墙的Console口(9600-N-8-1),使用超级终端连接。
在提示符的后面有一个大于号“>”,你处在asa用户模式。
使用en或者enable命令修改权限模式。
asafirewall> en //输入en 或 enable 回车Password: //若没有密码则直接回车即可asafirewall# //此时便拥有了管理员模式,此模式下可以显示内容但不能配置,若要配置必须进入到通用模式asafirewall# config t // 进入到通用模式的命令asafirewall(config)# hostname sjzpix1 //设置防火墙的名称Sjzpix1(config)# password zxm10 //设置登陆口令为zxm10Sjzpix1(config)# enable password zxm10 //设置启动模式口令,用于获得管理员模式访问1.配置各个网卡Sjzpix1(config)# interface GigabitEthernet0/0 //配置防火墙的E0 端口Sjzpix1(config-if)# security-level 0 //设置成最低级别Sjzpix1(config-if)# nameif outside //设置E0 端口为外部端口Sjzpix1(config-if)# speed auto //设置成自动设置网口速率Sjzpix1(config-if)# ip address 10.0.1.50 255.255.255.0 standby 10.0.1.51// 10.0.1.50 为该防火墙分配的公网IP,255.255.255.0为该防火墙公网IP对应的掩码,若该防火墙没有主备用方式则配置命令中的红色字体部分不需要配置。
ASA 5520

4.1.6.1 C ISCO ASA5520-K8Cisco ASA 5500 系列在单一平台中提供了多种市场成熟技术的强大组合,从而从运营角度和经济角度来说,都能向更多地点部署全面的安全服务。
它是一款多功能的安全设备,借此既可以实现强大的安全保护,又可以避免在多个地点运行多个设备的高运行成本,因而不必在两者间进行困难的、高风险的权衡。
Cisco ASA 5500 系列针对中小型企业(SMB)、大型企业和电信运营商的特别需求提供了定制产品包。
这样即可通过ASA 5500 系列平台实现标准化,从而降低管理、培训和备件的成本。
它能为网络中的地点提供适合的服务,以实现出色的保护。
此外,它提供了预打包的各地点专用安全解决方案,借此简化了设计和部署。
这些预打包的解决方案有四种类型:Cisco ASA 5500 系列防火墙、IPS、Anti-X 和VPN 捆绑。
产品特性:用户/ 节点数目无限制防火墙吞吐率最高 450 Mbps并发威胁防御吞吐率AIP-SSM-10:最高 225 Mbps AIP-SSM-20:最高375 Mbps3DES/AES VPN 吞吐率最高225 MbpsIPSec VPN 设备对1 750并发进程280,000集成网络端口 4 个千兆以太网端口,1 个快速以太网端口虚拟接口(VLAN)基本系统: 100安全环境(包括/ 最大) 2/10SSM 扩展插槽 1USB 2.0 端口 2RAM 512 Mb闪存64 Mb规格 1 RU许可证类型7 个许可证:ASA 5500 SSL VPN 10、25、50、100 250 个设备对许可证关键特性:●成熟的安全和VPN 性能——特性全面的高性能防火墙、IPS、Anti-X 以及IPSec 和SSL VPN 技术,提供了强大的应用安全、基于用户和应用的访问控制、蠕虫和病毒防御、恶意软件防御、防网络钓鱼和防垃圾邮件、URL 阻拦和过滤,以及远程用户/ 地点连接。
ASA 5520 IOS 恢复步骤

ASA 5520 IOS 恢复步骤(已验证)1、首先做一下说明,恢复过程中用到的是ASA 5520上的千兆以太网端口(GE),1个快速以太网端口(MGMT),一个Console口,使用3CDaemon 软件,一台PC,备份的asa708-k8.bin和asdm-508.bin,Console线,普通网线。
2、下面是步骤及配置信息开启5520电源,开机会有如下提示:Use BREAK or ESC to interrupt boot.Use SPACE to begin boot immediately.然后按“ESC”键进入监控模式。
3、在监控模式下可以用“?”或“help”获得命令帮助,下面是用“?”或“help”后提示的恢复命令。
rommon #0>?Variables: Use "sync" to store in NVRAMADDRESS= <addr> local IP addressCONFIG= <name> config file path/nameGATEWAY= <addr> gateway IP addressIMAGE= <name> image file path/nameLINKTIMEOUT= <num> Link UP timeout (seconds)PKTTIMEOUT= <num> packet timeout (seconds)PORT= <name> ethernet interface portRETRY= <num> Packet Retry Count (Ping/TFTP)SERVER= <addr> server IP addressVLAN= <num> enable/disable DOT1Q tagging on the selected port。
ASA 5520长连接解决方案
C H A P T E R 52-1Cisco ASA 5500 Series Configuration Guide using the CLI52Configuring Connection SettingsThis chapter describes how to configure connection settings for connections that go through the ASA,or for management connections, that go to the ASA. Connection settings include:•Maximum connections (TCP and UDP connections, embryonic connections, per-client connections)•Connection timeouts •Dead connection detection •TCP sequence randomization •TCP normalization customization •TCP state bypass •Global timeoutsThis chapter includes the following sections:•Information About Connection Settings, page 52-1•Licensing Requirements for Connection Settings, page 52-4•Guidelines and Limitations, page 52-5•Default Settings, page 52-5•Configuring Connection Settings, page 52-6•Monitoring Connection Settings, page 52-14•Configuration Examples for Connection Settings, page 52-14•Feature History for Connection Settings, page 52-16Information About Connection SettingsThis section describes why you might want to limit connections and includes the following topics:•TCP Intercept and Limiting Embryonic Connections, page 52-2•Disabling TCP Intercept for Management Packets for Clientless SSL Compatibility, page 52-2•Dead Connection Detection (DCD), page 52-2•TCP Sequence Randomization, page 52-3•TCP Normalization, page 52-3•TCP State Bypass, page 52-3Chapter52 Configuring Connection Settings Information About Connection SettingsTCP Intercept and Limiting Embryonic ConnectionsLimiting the number of embryonic connections protects you from a DoS attack. The ASA uses theper-client limits and the embryonic connection limit to trigger TCP Intercept, which protects insidesystems from a DoS attack perpetrated by flooding an interface with TCP SYN packets. An embryonicconnection is a connection request that has not finished the necessary handshake between source anddestination. TCP Intercept uses the SYN cookies algorithm to prevent TCP SYN-flooding attacks. ASYN-flooding attack consists of a series of SYN packets usually originating from spoofed IP addresses.The constant flood of SYN packets keeps the server SYN queue full, which prevents it from servicingconnection requests. When the embryonic connection threshold of a connection is crossed, the ASA actsas a proxy for the server and generates a SYN-ACK response to the client SYN request. When the ASAreceives an ACK back from the client, it can then authenticate the client and allow the connection to theserver.Note When you use TCP SYN cookie protection to protect servers from SYN attacks, you must set the embryonic connection limit lower than the TCP SYN backlog queue on the server that you want toprotect. Otherwise, valid clients can nolonger access the server during a SYN attack.To view TCP Intercept statistics, including the top 10 servers under attack, see Chapter55, “ConfiguringThreat Detection.”Disabling TCP Intercept for Management Packets for Clientless SSL CompatibilityBy default, TCP management connections have TCP Intercept always enabled. When TCP Intercept isenabled, it intercepts the 3-way TCP connection establishment handshake packets and thus deprives theASA from processing the packets for clientless SSL. Clientless SSL requires the ability to process the3-way handshake packets to provide selective ACK and other TCP options for clientless SSLconnections. To disable TCP Intercept for management traffic, you can set the embryonic connectionlimit; only after the embryonic connection limit is reached is TCP Intercept enabled.Dead Connection Detection (DCD)DCD detects a dead connection and allows it to expire, without expiring connections that can still handletraffic. You configure DCD when you want idle, but valid connections to persist.When you enable DCD, idle timeout behavior changes. With idle timeout, DCD probes are sent to eachof the two end-hosts to determine the validity of the connection. If an end-host fails to respond afterprobes are sent at the configured intervals, the connection is freed, and reset values, if configured, aresent to each of the end-hosts. If both end-hosts respond that the connection is valid, the activity timeoutis updated to the current time and the idle timeout is rescheduled accordingly.Enabling DCD changes the behavior of idle-timeout handling in the TCP normalizer. DCD probingresets the idle timeout on the connections seen in the show conn command. To determine when aconnection that has exceeded the configured timeout value in the timeout command but is kept alive dueto DCD probing, the show service-policy command includes counters to show the amount of activityfrom DCD.Cisco ASA 5500 Series Configuration Guide using the CLIChapter52 Configuring Connection SettingsInformation About Connection SettingsTCP Sequence RandomizationEach TCP connection has two ISNs: one generated by the client and one generated by the server. TheASA randomizes the ISN of the TCP SYN passing in both the inbound and outbound directions.Randomizing the ISN of the protected host prevents an attacker from predecting the next ISN for a newconnection and potentially hijacking the new session.TCP initial sequence number randomization can be disabled if required. For example:•If another in-line firewall is also randomizing the initial sequence numbers, there is no need for both firewalls to be performing this action, even though this action does not affect the traffic.•If you use eBGP multi-hop through the ASA, and the eBGP peers are using MD5. Randomization breaks the MD5 checksum.•You use a WAAS device that requires the ASA not to randomize the sequence numbers ofconnections.TCP NormalizationThe TCP normalization feature identifies abnormal packets that the ASA can act on when they aredetected; for example, the ASA can allow, drop, or clear the packets. TCP normalization helps protectthe ASA from attacks. TCP normalization is always enabled, but you can customize how some featuresbehave.The TCP normalizer includes non-configurable actions and configurable actions. Typically,non-configurable actions that drop or clear connections apply to packets that are always bad.Configurable actions (as detailed in “Customizing the TCP Normalizer with a TCP Map” section onpage52-6) might need to be customized depending on your network needs.See the following guidelines for TCP normalization:•The normalizer does not protect from SYN floods. The ASA includes SYN flood protection in other ways.•The normalizer always sees the SYN packet as the first packet in a flow unless the ASA is in loose mode due to failover.TCP State BypassBy default, all traffic that goes through the ASA is inspected using the Adaptive Security Algorithm andis either allowed through or dropped based on the security policy. The ASA maximizes the firewallperformance by checking the state of each packet (is this a new connection or an establishedCisco ASA 5500 Series Configuration Guide using the CLICisco ASA 5500 Series Configuration Guide using the CLI Chapter52 Configuring Connection SettingsLicensing Requirements for Connection Settings52-4Chapter52 Configuring Connection SettingsGuidelines and LimitationsGuidelines and LimitationsThis section includes the following guidelines and limitations:•TCP State Bypass Guidelines and Limitations, page52-5TCP State Bypass Guidelines and LimitationsContext Mode GuidelinesSupported in single and multiple context mode.Firewall Mode GuidelinesSupported in routed and transparent mode.Failover GuidelinesFailover is supported.Unsupported FeaturesThe following features are not supported when you use TCP state bypass:•Application inspection—Application inspection requires both inbound and outbound traffic to go through the same ASA, so application inspection is not supported with TCP state bypass.•AAA authenticated sessions—When a user authenticates with one ASA, traffic returning via the other ASA will be denied because the user did not authenticate with that ASA.•TCP Intercept, maximum embryonic connection limit, TCP sequence number randomization—The ASA does not keep track of the state of the connection, so these features are not applied.•TCP normalization—The TCP normalizer is disabled.•SSM and SSC functionality—You cannot use TCP state bypass and any application running on an SSM or SSC, such as IPS or CSC.NAT GuidelinesBecause the translation session is established separately for each ASA, be sure to configure static NATon both ASAs for TCP state bypass traffic; if you use dynamic NAT, the address chosen for the sessionon ASA 1 will differ from the address chosen for the session on ASA 2.Default SettingsTCP State BypassTCP state bypass is disabled by default.TCP NormalizerThe default configuration includes the following settings:no check-retransmissionno checksum-verificationCisco ASA 5500 Series Configuration Guide using the CLIChapter52 Configuring Connection Settings Configuring Connection Settingsexceed-mss allowqueue-limit 0 timeout 4reserved-bits allowsyn-data allowsynack-data dropinvalid-ack dropseq-past-window droptcp-options range 6 7 cleartcp-options range 9 255 cleartcp-options selective-ack allowtcp-options timestamp allowtcp-options window-scale allowttl-evasion-protectionurgent-flag clearwindow-variation allow-connectionConfiguring Connection SettingsThis section includes the following topics:•Customizing the TCP Normalizer with a TCP Map, page52-6•Configuring Connection Settings, page52-10Task Flow For Configuring Configuration Settings (Except Global Timeouts) Step1For TCP normalization customization, create a TCP map according to the “Customizing the TCP Normalizer with a TCP Map” section on page52-6.Step2For all connection settings except for global timeouts, configure a service policy according to Chapter32, “Configuring a Service Policy Using the Modular Policy Framework.”Step3Configure connection settings according to the “Configuring Connection Settings” section on page52-10.Customizing the TCP Normalizer with a TCP MapTo customize the TCP normalizer, first define the settings using a TCP map.Detailed StepsStep1To specify the TCP normalization criteria that you want to look for, create a TCP map by entering the following command:hostname(config)# tcp-map tcp-map-nameFor each TCP map, you can customize one or more settings.Step2(Optional) Configure the TCP map criteria by entering one or more of the following commands (see Table52-1). If you want to customize some settings, then the defaults are used for any commands youdo not enter.Cisco ASA 5500 Series Configuration Guide using the CLIChapter52 Configuring Connection SettingsConfiguring Connection SettingsT able52-1tcp-map CommandsCommand Notescheck-retransmission Prevents inconsistent TCP retransmissions.checksum-verification Verifies the checksum.exceed-mss {allow | drop}Sets the action for packets whose data length exceeds the TCPmaximum segment size.(Default) The allow keyword allows packets whose data lengthexceeds the TCP maximum segment size.The drop keyword drops packets whose data length exceeds theTCP maximum segment size.invalid-ack {allow | drop}Sets the action for packets with an invalid ACK. You might seeinvalid ACKs in the following instances:•In the TCP connection SYN-ACK-received status, if the ACKnumber of a received TCP packet is not exactly same as thesequence number of the next TCP packet sending out, it is aninvalid ACK.•Whenever the ACK number of a received TCP packet isgreater than the sequence number of the next TCP packetsending out, it is an invalid ACK.The allow keyword allows packets with an invalid ACK.(Default) The drop keyword drops packets with an invalid ACK.Note TCP packets with an invalid ACK are automaticallyallowed for WAAS connections.Cisco ASA 5500 Series Configuration Guide using the CLICisco ASA 5500 Series Configuration Guide using the CLI Chapter 52 Configuring Connection SettingsConfiguring Connection Settings queue-limit pkt_num[timeout seconds ]Sets the maximum number of out-of-order packets that can be buffered and put in order for a TCP connection, between 1 and 250packets. The default is 0, which means this setting is disabled andthe default system queue limit is used depending on the type oftraffic:•Connections for application inspection (the inspectcommand), IPS (the ips command), and TCPcheck-retransmission (the TCP map check-retransmissioncommand) have a queue limit of 3 packets. If the ASAreceives a TCP packet with a different window size, then thequeue limit is dynamically changed to match the advertisedsetting.•For other TCP connections, out-of-order packets are passedthrough untouched.If you set the queue-limit command to be 1 or above, then thenumber of out-of-order packets allowed for all TCP traffic matchesthis setting. For example, for application inspection, IPS, and TCPcheck-retransmission traffic, any advertised settings from TCPpackets are ignored in favor of the queue-limit setting. For otherTCP traffic, out-of-order packets are now buffered and put in orderinstead of passed through untouched.The timeout seconds argument sets the maximum amount of timethat out-of-order packets can remain in the buffer, between 1 and20 seconds; if they are not put in order and passed on within thetimeout period, then they are dropped. The default is 4 seconds.You cannot change the timeout for any traffic if the pkt_numargument is set to 0; you need to set the limit to be 1 or above forthe timeout keyword to take effect.reserved-bits {allow | clear |drop }Sets the action for reserved bits in the TCP header.(Default) The allow keyword allows packets with the reserved bitsin the TCP header.The clear keyword clears the reserved bits in the TCP header andallows the packet.The drop keyword drops the packet with the reserved bits in theTCP header.seq-past-window {allow | drop }Sets the action for packets that have past-window sequencenumbers, namely the sequence number of a received TCP packetis greater than the right edge of the TCP receiving window.The allow keyword allows packets that have past-windowsequence numbers. This action is only allowed if the queue-limitcommand is set to 0 (disabled).(Default) The drop keyword drops packets that have past-windowsequence numbers.T able 52-1tcp-map Commands (continued)CommandNotesCisco ASA 5500 Series Configuration Guide using the CLIChapter 52 Configuring Connection SettingsConfiguring Connection Settings synack-data {allow | drop }Sets the action for TCP SYNACK packets that contain data.The allow keyword allows TCP SYNACK packets that containdata.(Default) The drop keyword drops TCP SYNACK packets thatcontain data.syn-data {allow | drop }Sets the action for SYN packets with data.(Default) The allow keyword allows SYN packets with data.The drop keyword drops SYN packets with data.tcp-options {selective-ack |timestamp | window-scale }{allow | clear }Ortcp-options range lower upper{allow | clear | drop }Sets the action for packets with TCP options, including the selective-ack, timestamp, or window-scale TCP options. (Default) The allow keyword allows packets with the specified option.(Default for range ) The clear keyword clears the option and allows the packet.The drop keyword drops the packet with the specified option.The selective-ack keyword sets the action for the SACK option.The timestamp keyword sets the action for the timestamp option.Clearing the timestamp option disables PAWS and RTT.The widow-scale keyword sets the action for the window scalemechanism option.The range keyword specifies a range of options. The lowerargument sets the lower end of the range as 6, 7, or 9 through 255.The upper argument sets the upper end of the range as 6, 7, or 9through 255.ttl-evasion-protection Disables the TTL evasion protection. Do not enter this commandit you want to prevent attacks that attempt to evade security policy.For example, an attacker can send a packet that passes policy witha very short TTL. When the TTL goes to zero, a router between theASA and the endpoint drops the packet. It is at this point that theattacker can send a malicious packet with a long TTL that appearsto the ASA to be a retransmission and is passed. To the endpointhost, however, it is the first packet that has been received by theattacker. In this case, an attacker is able to succeed withoutsecurity preventing the attack.T able 52-1tcp-map Commands (continued)CommandNotesCisco ASA 5500 Series Configuration Guide using the CLI Chapter 52 Configuring Connection SettingsConfiguring Connection Settings Configuring Connection SettingsTo set connection settings, perform the following steps.Detailed Stepsurgent-flag {allow | clear }Sets the action for packets with the URG flag. The URG flag isused to indicate that the packet contains information that is ofhigher priority than other data within the stream. The TCP RFC isvague about the exact interpretation of the URG flag, therefore endsystems handle urgent offsets in different ways, which may makethe end system vulnerable to attacks.The allow keyword allows packets with the URG flag.(Default) The clear keyword clears the URG flag and allows thepacket.window-variation {allow | drop }Sets the action for a connection that has changed its window sizeunexpectedly. The window size mechanism allows TCP toadvertise a large window and to subsequently advertise a muchsmaller window without having accepted too much data. From theTCP specification, “shrinking the window” is stronglydiscouraged. When this condition is detected, the connection canbe dropped.(Default) The allow keyword allows connections with a windowvariation.The drop keyword drops connections with a window variation.T able 52-1tcp-map Commands (continued)CommandNotes CommandPurpose Step 1class-map name Example:hostname(config)# class-map bypass_trafficCreates a class map to identify the traffic for which you want todisable stateful firewall inspection.Step 2match parameter Example:hostname(config-cmap)# match access-listbypassSpecifies the traffic in the class map. See the “Identifying Traffic(Layer 3/4 Class Maps)” section on page 32-12 for moreinformation.Configuring Connection SettingsStep3policy-map nameExample:hostname(config)# policy-maptcp_bypass_policy Adds or edits a policy map that sets the actions to take with the class map traffic.Step4class nameExample:hostname(config-pmap)# classbypass_trafficIdentifies the class map created in Step1Step5Do one or more of the following:Command PurposeCisco ASA 5500 Series Configuration Guide using the CLIConfiguring Connection Settingsset connection {[conn-max n ][embryonic-conn-max n ][per-client-embryonic-max n ][per-client-max n ] [random-sequence-number{enable | disable }]}Example:hostname(config-pmap-c)# set connection conn-max 256 random-sequence-number disable Sets maximum connection limits or whether TCP sequence randomization is enabled.The conn-max n argument sets the maximum number of simultaneous TCP and/or UDP connections that are allowed,between 0 and 65535. The default is 0, which allows unlimitedconnections.If two servers are configured to allow simultaneous TCP and/orUDP connections, the connection limit is applied to eachconfigured server separately.When configured under a class, this argument restricts themaximum number of simultaneous connections that are allowedfor the entire class. In this case, one attack host can consume allthe connections and leave none of the rest of the hosts matched inthe access list under the class.The embryonic-conn-max n argument sets the maximum numberof simultaneous embryonic connections allowed, between 0 and65535. The default is 0, which allows unlimited connections.The per-client-embryonic-max n argument sets the maximumnumber of simultaneous embryonic connections allowed perclient, between 0 and 65535. The default is 0, which allowsunlimited connections.The per-client-max n argument sets the maximum number ofsimultaneous connections allowed per client, between 0 and65535. The default is 0, which allows unlimited connections.When configured under a class, this argument restricts themaximum number of simultaneous connections that are allowedfor each host that is matched through an access list under theclass.The random-sequence-number {enable | disable } keywordenables or disables TCP sequence number randomization. See the“TCP Sequence Randomization” section on page 52-3 section formore information.You can enter this command all on one line (in any order), or youcan enter each attribute as a separate command. The ASAcombines the command into one line in the running configuration.Note For management traffic, you can only set the conn-maxand embryonic-conn-max keywords.CommandPurposeCisco ASA 5500 Series Configuration Guide using the CLI Configuring Connection Settingsset connection timeout {[embryonichh :mm :ss ] {idle hh :mm :ss [reset ]][half-closed hh :mm :ss ] [dcd hh :mm :ss[max_retries ]]}Example:hostname(config-pmap-c)# set connection timeout idle 2:0:0 embryonic 0:40:0 half-closed 0:20:0 dcd Sets connection timeouts.The embryonic hh :mm :ss keyword sets the timeout period until a TCP embryonic (half-open) connection is closed, between 0:0:5and 1193:00:00. The default is 0:0:30. You can also set this valueto 0, which means the connection never times out.The idle hh :mm :ss keyword sets the idle timeout for all protocolsbetween 0:5:0 and 1193:00:00. The default is 1:0:0. You can alsoset this value to 0, which means the connection never times out.For TCP traffic, the reset keyword sends a reset to TCP endpointswhen the connection times out.The half-closed hh :mm :ss keyword sets the idle timeout between0:5:0 and 1193:00:00. The default is 0:10:0. Half-closedconnections are not affected by DCD. Also, the ASA does notsend a reset when taking down half-closed connections.The dcd keyword enables DCD. DCD detects a dead connectionand allows it to expire, without expiring connections that can stillhandle traffic. You configure DCD when you want idle, but validconnections to persist. After a TCP connection times out, the ASAsends DCD probes to the end hosts to determine the validity of theconnection. If one of the end hosts fails to respond after themaximum retries are exhausted, the ASA frees the connection. Ifboth end hosts respond that the connection is valid, the ASAupdates the activity timeout to the current time and reschedulesthe idle timeout accordingly. The retry-interval sets the timeduration in hh :mm :ss format to wait after each unresponsive DCDprobe before sending another probe, between 0:0:1 and 24:0:0.The default is 0:0:15. The max-retries sets the number ofconsecutive failed retries for DCD before declaring theconnection as dead. The minimum value is 1 and the maximumvalue is 255. The default is 5.The default tcp idle timeout is 1 hour.The default udp idle timeout is 2 minutes.The default icmp idle timeout is 2 minutes.The default esp and ha idle timeout is 30 seconds.For all other protocols, the default idle timeout is 2 minutes.To never time out, enter 0:0:0.You can enter this command all on one line (in any order), or youcan enter each attribute as a separate command. The command iscombined onto one line in the running configuration.Note This command is not available for management traffic.CommandPurposeMonitoring Connection Settings Monitoring Connection SettingsThis section includes the following topics:•Monitoring TCP State Bypass, page 52-14Monitoring TCP State BypassTo monitor TCP state bypass, perform one of the following tasks:Configuration Examples for Connection SettingsThis section includes the following topics:•Configuration Examples for Connection Limits and Timeouts, page 52-15•Configuration Examples for TCP State Bypass, page 52-15•Configuration Examples for TCP Normalization, page 52-15set connection advanced-optionstcp-map-name Example:hostname(config-pmap-c)# set connectionadvanced-options tcp_map1Customizes the TCP normalizer. See the “Customizing the TCP Normalizer with a TCP Map” section on page 52-6 to create aTCP map.set connection advanced-optionstcp-state-bypass Example:hostname(config-pmap-c)# set connectionadvanced-options tcp-state-bypassEnables TCP state bypass.Step 6service-policy policymap_name {global |interface interface_name }Example:hostname(config)# service-policytcp_bypass_policy outside Activates the policy map on one or more interfaces. global applies the policy map to all interfaces, and interface applies the policy to one interface. Only one global policy is allowed. You can override the global policy on an interface by applying a service policy to that interface. You can only apply one policy map to each interface.CommandPurpose CommandPurpose show conn If you use the show conn command, the display for connections that useTCP state bypass includes the flag “b.”Configuration Examples for Connection SettingsConfiguration Examples for Connection Limits and TimeoutsThe following example sets the connection limits and timeouts for all traffic:hostname(config)# class-map CONNShostname(config-cmap)# match anyhostname(config-cmap)# policy-map CONNShostname(config-pmap)# class CONNShostname(config-pmap-c)# set connection conn-max 1000 embryonic-conn-max 3000hostname(config-pmap-c)# set connection timeout tcp 2:0:0 embryonic 0:40:0 half-closed0:20:0 dcdhostname(config-pmap-c)# service-policy CONNS interface outsideYou can enter set connection commands with multiple parameters or you can enter each parameter as aseparate command. The ASA combines the commands into one line in the running configuration. Forexample, if you entered the following two commands in class configuration mode:hostname(config-pmap-c)# set connection conn-max 600hostname(config-pmap-c)# set connection embryonic-conn-max 50the output of the show running-config policy-map command would display the result of the twocommands in a single, combined command:set connection conn-max 600 embryonic-conn-max 50Configuration Examples for TCP State BypassThe following is a sample configuration for TCP state bypass:hostname(config)# access-list tcp_bypass extended permit tcp 10.1.1.0 255.255.255.224 anyhostname(config)# class-map tcp_bypasshostname(config-cmap)# description "TCP traffic that bypasses stateful firewall"hostname(config-cmap)# match access-list tcp_bypasshostname(config-cmap)# policy-map tcp_bypass_policyhostname(config-pmap)# class tcp_bypasshostname(config-pmap-c)# set connection advanced-options tcp-state-bypasshostname(config-pmap-c)# service-policy tcp_bypass_policy outsidehostname(config-pmap-c)# static (inside,outside) 209.165.200.224 10.1.1.0 netmask255.255.255.224Configuration Examples for TCP NormalizationFor example, to allow urgent flag and urgent offset packets for all traffic sent to the range of TCP portsbetween the well known FTP data port and the Telnet port, enter the following commands:hostname(config)# tcp-map tmaphostname(config-tcp-map)# urgent-flag allowhostname(config-tcp-map)# class-map urg-classhostname(config-cmap)# match port tcp range ftp-data telnethostname(config-cmap)# policy-map pmaphostname(config-pmap)# class urg-classhostname(config-pmap-c)# set connection advanced-options tmaphostname(config-pmap-c)# service-policy pmap globalCisco ASA 5500 Series Configuration Guide using the CLI。
防火墙价格,最新全国防火墙规格型号价格大全

全国各规格型号防火墙价格大全来源:造价通工程造价信息网概述:造价通工程造价信息网为您实时提供全国各省市地区各种规格/型号防火墙价格查询。
标签:防火墙价格,防火墙价格表,防火墙规格,防火墙型号,最新防火墙价格,防火墙报价,防火墙价格查询,防火墙市场价编者按:造价通——是中华人民共和国国家标准《建设工程人工材料设备机械数据标准》(GB/T 50851-2013)的参编单位和唯一数据提供方。
材料名规格/型号单位品牌省份城市查询账号账号密码防火墙H3C¡ÁNS-SecPathF100-S-ACH3C 浙江杭州市misschen1988 lzl639528417防火墙H3C¡ÁNS-SecPathF100-A-SI-ACH3C 浙江杭州市misschen1988 lzl639528417防火墙H3C¡ÁNS-SecPathF100-C-EIH3C 浙江杭州市misschen1988 lzl639528417防火墙H3C¡ÁNS-SecPathF100-C-ACH3C 浙江杭州市misschen1988 lzl639528417防火墙H3C¡ÁNS-SecPathF100-M-ACH3C 浙江杭州市misschen1988 lzl639528417防火墙ASA5505-K8 1.0 思科浙江杭州市misschen1988 lzl639528417 防火墙ASA5520-K8 1.0 思科浙江杭州市misschen1988 lzl639528417 防火墙ASA5505-UL-BUN-K8 1.0 思科浙江杭州市misschen1988 lzl639528417 防火墙ASA5520-BUN-K9 1.0 思科浙江杭州市misschen1988 lzl639528417 防火墙ASA5510-K8 1.0 思科浙江杭州市misschen1988 lzl639528417 防火墙ASA5510-BUN-K9 1.0 思科浙江杭州市misschen1988 lzl639528417 防火墙ASA5505-UL-BUN-K9 1.0 思科浙江杭州市misschen1988 lzl639528417 防火墙ASA5505-50-BUN-K9 1.0 思科浙江杭州市misschen1988 lzl639528417 防火墙ASA5505-50-BUN-K8 1.0 思科浙江杭州市misschen1988 lzl639528417防火墙ZXSEC US2640 台中兴广东广州市misschen1988 lzl639528417 防火墙Eudemon 1000 个华为广东广州市misschen1988 lzl639528417 防火墙USG5310 台华为广东广州市misschen1988 lzl639528417 防火墙NS-SecPath F1000-E-AC 台H3C 广东深圳市misschen1988 lzl639528417 防火墙NS-SecPath F1000-E-AC 台华为广东广州市misschen1988 lzl639528417防火墙DFL-800 中小企业级防火墙 (120M bps 防火墙性能)套清华同方广东广州市misschen1988 lzl639528417防火墙LFWEVSYS01 5虚拟防火墙套壹软广东广州市misschen1988 lzl639528417 防火墙LFWEVSYS02 10虚拟防火墙套壹软广东广州市misschen1988 lzl639528417 防火墙LFWEVSYS03 25虚拟防火墙套壹软广东广州市misschen1988 lzl639528417 防火墙LFWEVSYS04 50虚拟防火墙套壹软广东广州市misschen1988 lzl639528417防火墙LFWEVSYS05 100虚拟防火墙套壹软广东广州市misschen1988 lzl639528417防火墙ADD 10 VPN Tunnel VPN隧道数(10 隧道)套壹软广东广州市misschen1988 lzl639528417防火墙ADD 100 VPN Tunnel VPN隧道数(100 隧道)套壹软广东广州市misschen1988 lzl639528417防火墙ADD 500 VPN Tunnel VPN隧道数(500 隧道)套壹软广东广州市misschen1988 lzl639528417防火墙ADD 1000 VPN Tunnel VPN隧道数(1000 隧道)套壹软广东广州市misschen1988 lzl639528417防火墙ADD 2000 VPN Tunnel VPN隧道数(2000 隧道)套壹软广东广州市misschen1988 lzl639528417防火墙ADD 5000 VPN Tunnel VPN隧道数(5000 隧道)套壹软广东广州市misschen1988 lzl639528417防火墙ADD 10000 VPN Tunnel VPN隧道数(10000 隧道)套壹软广东广州市misschen1988 lzl639528417防火墙ADD 10 VPN Tunnel VPN隧道数(10 隧道) 默认VPN隧道数为0套壹软广东广州市misschen1988 lzl639528417防火墙ADD 100 VPN Tunnel VPN隧道数(100 隧道) 默认VPN隧道数为0套壹软广东广州市misschen1988 lzl639528417防火墙ADD 500 VPN Tunnel VPN隧道数(500 隧道) 默认VPN隧道数为0套壹软广东广州市misschen1988 lzl639528417防火墙ADD 1000 VPN Tunnel VPN隧道数(1000 隧道) 默认VPN隧道数为0套壹软广东广州市misschen1988 lzl639528417防火墙ADD 2000 VPN Tunnel VPN隧道数(2000 隧道) 默认VPN隧道数为0套壹软广东广州市misschen1988 lzl639528417防火墙ADD 5000 VPN Tunnel VPN隧道数(5000 隧道) 默认VPN隧道数为0套壹软广东广州市misschen1988 lzl639528417防火墙ADD 10000 VPN Tunnel VPN隧道数(10000 隧道) 默认VPN隧道数为0套壹软广东广州市misschen1988 lzl639528417防火墙ASA5505-K8 ASA 5505Appliance with SW, 10Users, 8 ports, DES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5505-BUN-K9 ASA 5505Appliance with SW, 10Users, 8 ports, 3DES/AES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5505-50-BUN-K8 ASA5505 Appliance with SW,50 Users, 8 ports, DES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5505-UL-BUN-K8 ASA5505 Appliance with SW,UL Users, 8 ports, DES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5505-SEC-BUN-K8 ASA5505 Sec Plus Appliancewith SW, UL Users, HA, DES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5505-50-BUN-K9 ASA5505 Appliance with SW,套壹软广东广州市misschen1988 lzl63952841750 Users, 8 ports,3DES/AES防火墙ASA5505-UL-BUN-K9 ASA5505 Appliance with SW,UL Users, 8 ports,3DES/AES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5505-SEC-BUN-K9 ASA5505 Sec Plus Appliancewith SW, UL Users, HA,3DES/AES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5510-K8 ASA 5510Appliance with SW, 3FE,DES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5510-BUN-K9 ASA 5510Appliance with SW, 3FE,3DES/AES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5510-DC-K8 ASA 5510Appliance with DC power,SW, 3FE, DES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5510-SEC-BUN-K9 ASA5510 Security PlusAppliance with SW, HA,5FE, 3DES/AES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5520-K8 ASA 5520Appliance with SW, HA,4GE+1FE, DES套壹软广东广州市misschen1988 lzl639528417防火墙ASA5520-BUN-K9 ASA 5520Appliance with SW, HA,4GE+1FE, 3DES/AES套壹软广东广州市misschen1988 lzl639528417防火墙型号:SE-FW-01HASA5520-K8,Cisco防火墙,4个GE+1个FE,并发数280000,并发VPN 750,吞吐量450Mbit/s 每套SmartEye系统部署一台套广东深圳市misschen1988 lzl639528417防火墙型号:SE-FW-02HASA5550-K8,Cisco防火墙,8个GE+1个FE,并发数650000,并发VPN 5000,吞吐量1.2Gbit/s 每套SmartEye系统部署一台套广东深圳市misschen1988 lzl639528417结后语:完整版防火墙价格全国各地区加起来有共有数百页,因受限于百度文库文件上传大小、篇幅限制以及价格时效性原因,故而只上传了一部分。
cisco ASA5520 详细配置

nat (inside) 0 access-list No-nat
(anyconnect ssl-vpn)
webvpn
enable outside
username sxwz008 password 1234567
username sxwz009 password 1234567
username sxwz010 password 1234567
username sxwz011 password 1234567
username sxwz012 password 1234567
username sxwz013 password 1234567
username sxwz014 password 1234567
username sxwz015 password 1234567
(IPsecDynamicLAN-to-LAN VPN 动态VPN)
isakmp enable outside
nat-con
nat (inside) 1 0 0
global (outside) 1 interface
(开启ASDM)
http server enable 443
http 0 0 inside
http 0 0 outside
username sxwz password cisco privilege 15
group-policy SSLCLientPolicy internal
思科防火墙ASA5520配置

思科防火墙ASA5520配置博客分类:网络思科防火墙ASA5520配置:目的:1、内网可以上网2、内网可以访问DMZ区域的服务器3、外网可以通过公网IP访问DMZ区域的服务器要求:1、内网的网段192.168.10.02、DMZ的网段192.168.5.03、外网IP地址:200.200.200.82 200.200.200.83 网关255.255.255.248(这个地址一般是运营商提供)4、外网路由:200.200.200.815、DMZ区域的服务器IP地址:192.168.5.2步骤1:配置接口inside、outside和dmzinterface g0/0speed autoduplex autonameif insideSecurity-level 100ip address 192.168.10.1 255.255.255.0no shutexitinterface g0/1speed autoduplex autonameif outsideSecurity-level 0ip address 200.200.200.82 255.255.255.248 no shutexitinterface g0/2speed autoduplex autonameif dmzSecurity-level 50ip address 192.168.5.1 255.255.255.0no shutexit步骤2、添加外网路由route outside 0 0 200.200.200.81步骤3、做nat转换,使得内网可以上网,同时内网可以访问dmz区域的服务器nat-controlnat (inside) 1 192.168.10.0 255.255.255.0global (outside) 1 interfaceglobal (dmz) 1 interface步骤4、做静态nat,将对外网IP的访问转换到dmz区域的服务器static (dmz,outside) 200.200.200.83 192.168.5.2 netmask255.255.255.255 dns注意:这里的外网IP不是outside的接口地址,是另外一个公网IP步骤5、配置ACL规则,允许外网访问DMZ服务器access-list out_dmz extended permit tcp any host 200.200.200.83 eq wwwaccess-group out_dmz in interface outside到此配置结束,正常情况下上面的要求都可以实现了,但是可能由于每个机房的环境不一样,结果会有一些错误。
ASA5520的硬件介绍及相关配置

ASA5520的硬件介绍及相关配置Cisco ASA55201 Cisco ASA5500系列介绍:Cisco ASA 5500 系列⾃适应安全设备是思科专门设计的解决⽅案,能够将最⾼的安全性和VPN服务与全新的⾃适应识别和防御(AIM)架构有机地结合在⼀起。
作为思科⾃防御⽹络的关键组件,Cisco ASA 5500系列能够提供主动威胁防御,在⽹络受到威胁之前就能及时阻挡攻击,控制⽹络⾏为和应⽤流量,并提供灵活的VPN连接。
思科提供的强⼤多功能⽹络安全设备系列不但能为保护中⼩企业和⼤型企业⽹络提供⼴泛⽽深⼊的安全功能,还能降低与实现这种安全性相关的总体部署和运营成本及复杂性。
Cisco ASA 5500 系列能够在⼀个平台中提供多种已经过市场验证的技术,⽆论从技术⾓度还是从经济⾓度看,都能够为多个地点部署各种安全服务。
利⽤其多功能安全组件,企业⼏乎不需要作任何两难选择,既可以提供强有⼒的安全保护,⼜可以降低在多个地点部署多台设备的运营成本。
Cisco ASA 5500 系列能够通过以下关键组件帮助企业更有效地管理⽹络并提供出⾊的投资保护:●作⽤全特性、⾼性能的防⽕墙,⼊侵防范(IPS), ⽹络防病毒和IPSec/SSL VPN 技术提供了强⼤的应⽤安全性,基于⽤户和应⽤的访问控制,蠕⾍与病毒抑制,恶意代码防护以及远程⽤户/站点连接。
●⽬的利⽤⾼度可定制的针对流的安全策略,企业能够适应和扩展Cisco ASA 5500系列的安全服务组合。
安全策略允许企业根据应⽤要求定制安全需求,并通过⽤户可安装的安全服务模块(SSM)提供性能和安全服务可扩展性。
这种多功能的设备可实现平台、配置和管理的标准化,从⽽降低部署与⽇常运营成本。
Cisco ASA 5500系列包括Cisco ASA 5510, 5520和5540 ⾃适应安全设备——这三种专门设计的⾼性能安全解决⽅案提供了多功能的单机架(1RU) 设计,⼀个⽤于提供安全服务可扩展性的扩展插槽以及可提⾼部署灵活性的多个⽹络接⼝。
ASA5525翻译
1、基础配置类(1、接口配置)interface GigabitEthernet0/0nameif outsidesecurity-level 0ip address 192.168.4.254 255.255.255.0!interface GigabitEthernet0/1nameif insidesecurity-level 100ip address ASA5520 255.255.255.0!interface GigabitEthernet0/2nameif outside2security-level 0ip address 116.247.109.13 255.255.255.248 !interface Management0/0 management-onlynameif managementsecurity-level 100ip address 192.168.1.1 255.255.255.0配置解析:总共有2个外网,一个outside(私网),一个Outside2(公网地址),一个内网网段(Inside),一个管理接口(management),值得注意的是,这里内网网段配置是ip address ASA5520 255.255.255.0,这个ASA5520,对应192.168.2.254,为什么是这个,下面有说明。
(2、names)namesname 192.168.5.0 VPN-networkname 172.19.0.0 MFC-networkname 172.18.0.0 Office-networkname 172.18.2.0 local-guestname 172.100.0.0 wireless-guestname 172.99.0.0 wireless-username 192.168.2.1 core-switchname 192.168.2.253 cpcnet-gatewayname 172.20.0.0 complex-networkname 192.168.2.248 email-servername 192.168.2.254 ASA5520name 172.22.0.0 telephonename 172.22.1.249 welltech-servername 192.168.4.1 Ascanlinkname 192.168.2.251 ftp-servername 192.168.2.230 db-servername 172.18.3.249 edge95name 192.168.2.231 report-servername 192.168.2.233 terminalserver1name 192.168.2.234 terminalserver2name 192.168.2.235 terminalserver3name 192.168.2.236 terminalserver4name 192.168.2.250 web-servername 192.168.2.2 testservername 192.168.2.42 File_Servername 192.168.2.33 HR_Servername 192.168.2.32 ComexServername 192.168.2.152 Yikename 172.19.1.245 c20name 192.168.2.6 VSVN-Server description VSVN-Server配置解析:这个就是把一个IP地址对应一个名称,方便记忆,name 192.168.2.254 ASA5520,这个就是之前地址直接配置的ASA5520的名称,直接对应192.168.2.254(3、路由部分)route outside 0.0.0.0 0.0.0.0 Ascanlink 70route outside2 5.158.151.28 255.255.255.255 116.247.109.9 1route outside2 12.145.28.178 255.255.255.255 116.247.109.9 1route outside2 12.145.28.185 255.255.255.255 116.247.109.9 1route outside2 50.136.199.58 255.255.255.255 116.247.109.9 1 route outside 116.247.109.9 255.255.255.255 Ascanlink 1 route outside 116.247.109.10 255.255.255.255 Ascanlink 1 route outside 116.247.109.11 255.255.255.255 Ascanlink 1 route outside 116.247.109.12 255.255.255.255 Ascanlink 1 route inside 172.0.0.0 255.0.0.0 core-switch 1route outside2 172.16.0.0 255.255.255.0 116.247.109.9 1 route outside2 172.16.2.0 255.255.255.0 116.247.109.9 1 route outside2 172.16.4.0 255.255.255.0 116.247.109.9 1 route outside2 172.16.6.0 255.255.255.0 116.247.109.9 1 route outside2 172.16.9.0 255.255.255.0 116.247.109.9 1 route outside2 172.16.13.0 255.255.255.0 116.247.109.9 1 route outside2 172.16.15.0 255.255.255.0 116.247.109.9 1 route outside2 172.16.19.0 255.255.255.0 116.247.109.9 1 route outside2 172.16.32.0 255.255.252.0 116.247.109.9 1 route outside2 172.16.52.0 255.255.252.0 116.247.109.9 1 route outside2 172.16.200.0 255.255.252.0 116.247.109.9 1 route outside2 172.27.6.0 255.255.255.0 116.247.109.9 1 route inside VPN-network 255.255.255.0 core-switch 1route outside2 192.168.6.0 255.255.255.0 116.247.109.9 1 route outside2 192.168.9.0 255.255.255.0 116.247.109.9 1 route outside2 192.168.10.0 255.255.255.0 116.247.109.9 1route outside2 192.168.11.0 255.255.255.0 116.247.109.9 1route outside2 192.168.49.0 255.255.255.0 116.247.109.9 1route outside2 192.168.158.0 255.255.255.0 116.247.109.9 1route outside2 192.168.159.0 255.255.255.0 116.247.109.9 1route outside2 192.168.160.0 255.255.255.0 116.247.109.9 1route outside2 192.168.161.0 255.255.255.0 116.247.109.9 1route outside2 192.168.162.0 255.255.255.0 116.247.109.9 1route outside2 192.168.163.0 255.255.255.0 116.247.109.9 1route outside2 192.168.164.0 255.255.252.0 116.247.109.9 1route outside2 203.66.1.189 255.255.255.255 116.247.109.9 1route inside 203.70.94.0 255.255.255.0 core-switch 1route outside2 209.118.175.5 255.255.255.255 116.247.109.9 1配置解析:这里路由有3类,一个去往outside的,一个去往outside2的,一个去往内网inside的,去往内网的写回程路由,让数据包能够返回,外网由于有2条线路,ASA 9.4版本之前都不支持PBR,所以,只支持一条默认路由,另外一条写明细路由,从配置来看,outside2 作为VPN的线路来用(也就是VPN的流量都走outside2),而outside作为上网用,所以写了默认路由route outside 0.0.0.0 0.0.0.0 Ascanlink 702、ACL与NAT相关(1、object配置)object network FTP-Serverhost 192.168.2.251object network CORE-Switch host 192.168.2.1object network TERminalserver1 host 192.168.2.233object network TERminalserver2 host 192.168.2.234object network TERminalserver3 host 192.168.2.235object network TERminalserver4 host 192.168.2.236object network EMAil-server host 192.168.2.248object network REPort-server host 192.168.2.231object network EDGe95host 172.18.3.249object network DB-serverhost 192.168.2.230object network WEB-server host 192.168.2.250object network C20host 172.19.1.245object network H192.168.2.22 host 192.168.2.22object network H192.168.2.142 host 192.168.2.142object network hr_serverhost 192.168.2.33object network file_server host 192.168.2.42object network H172.20.3.36 host 172.20.3.36object network cOMexServer host 192.168.2.32object network H192.168.2.25 host 192.168.2.25object network yIKEhost 192.168.2.152object network H192.168.2.81 host 192.168.2.81object network H192.168.2.82 host 192.168.2.82object network asa5520host 192.168.2.254object network WELLTech-server host 172.22.1.249object network vsvn-serverhost 192.168.2.6object network 192.168.158.0 subnet 192.168.158.0 255.255.255.0 description 192.168.158.0object network 192.168.159.0 subnet 192.168.159.0 255.255.255.0 description 192.168.159.0object network 192.168.160.0 subnet 192.168.160.0 255.255.255.0 description 192.168.160.0object network 172.27.199.0 subnet 172.27.199.0 255.255.255.0 description AATI-Phoneobject network 192168_2subnet 192.168.2.0 255.255.255.0 object network WiFi6subnet 172.27.6.0 255.255.255.0 object network 192.168.161.0 subnet 192.168.161.0 255.255.255.0object network 192.168.162.0subnet 192.168.162.0 255.255.255.0 description 192.168.162.0object network 192.168.163.0subnet 192.168.163.0 255.255.255.0 description 192.168.163.0object network 192.168.164.0subnet 192.168.164.0 255.255.252.0 description 192.168.164.0object-group service udp_gt_8000 udpport-object range 7999 65000object-group network zhangjiangnetwork-object Office-network 255.255.0.0 network-object MFC-network 255.255.0.0 network-object complex-network 255.255.0.0 network-object wireless-user 255.255.0.0 network-object VPN-network 255.255.255.0 network-object 192.168.2.0 255.255.255.0 object-group service tcp-normal tcpport-objecteq echoport-objecteq ftpport-objecteq wwwport-objecteq httpsport-objecteq pop3port-objecteqsmtpport-object range 3000 4000port-objecteq 16000port-objecteq 8080port-objecteq ftp-dataobject-group service tcpudp-normal tcp-udp port-objecteq domainport-objecteq echoport-objecteq wwwobject-group service udp-normal udpport-objecteq echoport-objecteq wwwport-objecteqtftpport-objecteq 1863port-objecteq 4000port-object range 6891 6900port-objecteq timeobject-group service tcp_gt_10000 tcpport-object range 10000 65535object-group protocol TCPUDPprotocol-objecttcpobject-group service QQdescription QQservice-objecttcp destination eq 8000 service-objecttcp destination eq 8001object-group service rdptcpport-objecteq 3389object-group network DM_INLINE_NETWORK_1 network-object host report-servernetwork-object host terminalserver1network-object host terminalserver3network-object host terminalserver4network-object host terminalserver2network-object host HR_Servernetwork-object host 192.168.2.81object-group service DM_INLINE_TCP_1 tcp port-objecteq 10000port-objecteq pop3port-objecteqsmtpport-objecteq 8080port-objecteq imap4object-group service tcp-10000 tcpport-objecteq 1000group-objectrdpobject-group service DM_INLINE_TCP_2 tcp port-objecteq ftpport-objecteq ftp-dataport-objecteqsshport-objecteq 990object-group network DM_INLINE_NETWORK_3 network-object 192.168.200.0 255.255.255.0 network-object host 192.168.2.49network-object telephone 255.255.0.0 network-object host 172.16.13.224object-group service VideoConf descriptionVideoConfservice-objecttcp-udp destination eq sip service-objecttcp-udpobject-group network DM_INLINE_NETWORK_4 network-object host web-servernetwork-object host ftp-serverobject-group network DM_INLINE_NETWORK_5network-object host edge95network-object host c20object-group service sipphoneudp description sip-phoneport-objecteq 10087port-objecteq 8088port-objecteq sipport-object range 15000 30000object-group network DM_INLINE_NETWORK_6 network-object host edge95network-object host c20object-group protocol DM_INLINE_PROTOCOL_0 protocol-objectudpprotocol-objecttcpobject-group service DM_INLINE_TCP_3 tcp port-objecteq 8080port-objecteq wwwobject-group service DNSdescriptiondnsservice-objecttcp-udp destination eq domain object-group protocol DM_INLINE_PROTOCOL_1 protocol-objectudpobject-group protocol DM_INLINE_PROTOCOL_2 protocol-objectudpprotocol-objecttcpobject-group network DM_INLINE_NETWORK_7 network-object host web-servernetwork-object host File_Serverobject-group service 4433 tcpdescription 4433port-objecteq 4433object-group network SHANGHAI-LAN network-object 192.168.2.0 255.255.255.0 network-object VPN-network 255.255.255.0 network-object Office-network 255.255.0.0 network-object MFC-network 255.255.0.0 network-object wireless-user 255.255.0.0 network-object telephone 255.255.0.0 network-object complex-network 255.255.0.0 object-group network GERMANY-LAN network-object 192.168.49.0 255.255.255.0 object-group service DM_INLINE_TCP_4 tcp group-object 4433object-group network TW-LANnetwork-object 172.16.13.0 255.255.255.0 network-object 172.16.15.0 255.255.255.0 network-object 172.16.2.0 255.255.255.0 network-object 172.16.4.0 255.255.255.0 network-object 172.16.9.0 255.255.255.0 network-object 192.168.10.0 255.255.255.0 network-object 192.168.11.0 255.255.255.0 network-object 192.168.4.0 255.255.255.0 network-object 192.168.6.0 255.255.255.0 network-object 192.168.9.0 255.255.255.0 network-object 203.70.94.0 255.255.255.0 network-object 172.16.19.0 255.255.255.0 network-object 172.16.0.0 255.255.255.0 network-object 172.16.6.0 255.255.255.0 network-object 172.16.32.0 255.255.252.0 network-object 172.16.200.0 255.255.252.0 network-object 172.16.52.0 255.255.252.0 object-group network DM_INLINE_NETWORK_9 network-object telephone 255.255.0.0 network-object host welltech-serverobject-group service DM_INLINE_TCP_5 tcp port-objecteq 3309port-objecteq 3443port-objecteq 5443port-objecteq 1433port-objecteq 3080object-group network DM_INLINE_NETWORK_10 network-object host 211.78.82.113network-object host 60.250.154.133network-object host 210.65.220.246network-object host 222.73.42.138object-group service 4500 tcp-udp description 4500port-objecteq 4500object-group network AATI_LANdescription AATInetwork-object object 192.168.158.0network-object object 192.168.159.0network-object object 192.168.160.0network-object object 172.27.199.0network-object object 192.168.161.0network-object object 192.168.162.0network-object object 192.168.163.0network-object object 192.168.164.0object-group network DM_INLINE_NETWORK_12 network-object 192.168.49.0 255.255.255.0 group-object AATI_LANobject-group network USA-LANnetwork-object 192.168.158.0 255.255.255.0 network-object 192.168.159.0 255.255.255.0 network-object 172.27.199.0 255.255.255.192 network-object 192.168.160.0 255.255.248.0 object-group network CN-LANdescription all China networknetwork-object wireless-guest 255.255.0.0 network-object Office-network 255.255.0.0 network-object MFC-network 255.255.0.0 network-object complex-network 255.255.0.0 network-object telephone 255.255.0.0network-object wireless-user 255.255.0.0 network-object 192.168.0.0 255.255.255.0 network-object 192.168.10.0 255.255.255.0 network-object 192.168.11.0 255.255.255.0 network-object 192.168.2.0 255.255.255.0network-object 192.168.6.0 255.255.255.0network-object 192.168.21.0 255.255.255.0配置解析:关于object的作用就是定义一个对象与多个的对象匹配,比如匹配192.168.0.0 255.255.0.0,或者可以写多个object,把需要的匹配出来,最终以一个object-group调用这些object,等于是一个合集,这样我们在配置ACL的时候,可以简化配置,直接一次性调用需要调用的内容了。
ASA防火墙疑难杂症与CiscoASA5520防火墙配置

ASA防火墙疑难杂症解答ASA防火墙疑难杂症解答1...............................内部网络不能ping通internet2........................内部网络不能使用pptp拨入vpn服务器3....................内部网络不能通过被动Mode访问ftp服务器4.................................内部网络不能进行ipsec NAT5...................................内网不能访问DMZ区服务器6................................内网用户不能ping web服务器1. 内部网络不能ping通internet对于ASA5510,只要策略允许,则是可以Ping通的,对于ASA550,部分IOS可以ping,如果所以流量都允许还是不能Ping的话,则需要做inspect,对icmp协议进行检查即可2. 内部网络不能使用pptp拨入vpn服务器因pptp需要连接TCP 1723端口,同时还需要GRE协议,如果防火墙是linux的Iptables,则需要加载:modprobe ip_nat_pptp modprobe ip_conntrack_proto_gre如果防火墙是ASA,则需要inspect pptp。
3. 内部网络不能通过被动Mode访问ftp服务器同样需要inspect ftp,有些还需要检查相关参数policy-map type inspect ftp ftpaccessparametersmatch request-command appe cdup help get rnfr rnto put stou sitedele mkd rmd4. 内部网络不能进行ipsec NAT这种情况不多用,如查进行ipsect :IPSec Pass Through5. 内网不能访问DMZ区服务器增加NAT规则,即DMZ到内网的规则6. 内网用户不能ping web服务器如果内网中有一台web服务器,且已经配置了NAT,使用internet用户可以通过外部IP访问这台web服务器。
Cisco二级测评指导书
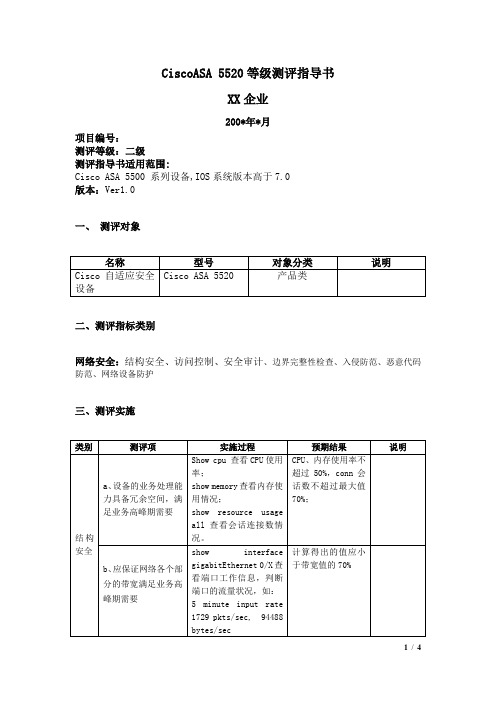
CiscoASA 5520等级测评指导书XX企业200*年*月项目编号:测评等级:二级测评指导书适用范围:Cisco ASA 5500 系列设备,IOS系统版本高于7.0版本:Ver1.0一、测评对象名称型号对象分类说明Cisco自适应安全设备Cisco ASA 5520 产品类二、测评指标类别网络安全:结构安全、访问控制、安全审计、边界完整性检查、入侵防范、恶意代码防范、网络设备防护三、测评实施类别测评项实施过程预期结果说明结构安全a、设备的业务处理能力具备冗余空间,满足业务高峰期需要Show cpu 查看CPU使用率;show memory查看内存使用情况;show resource usageall查看会话连接数情况。
CPU、内存使用率不超过50%,conn会话数不超过最大值70%;b、应保证网络各个部分的带宽满足业务高峰期需要show interfacegigabitEthernet 0/X查看端口工作信息,判断端口的流量状况,如:5 minute input rate1729 pkts/sec, 94488bytes/sec计算得出的值应小于带宽值的70%5 minute output rate 3884 pkts/sec, 4987242 bytes/secc、应绘制与当前运行情况相符的网络拓扑结构图;检查网络拓扑图看是否当前允许情况一致网络拓扑图与当前允许情况一致d、应根据各部门的工作职能、重要性和所涉及信息的重要程度等因素,划分不同的子网或网段,并按照方便管理和控制的原则为各子网、网段分配地址段show running-config查看各个接口是否配置IP地址;show interfacegigabitEthernet 0/X查看端口工作是否正常针对不同业务接口配置不同网段;各个接口工作状态正常,收发包数量在合理范围内访问控制a、应在网络边界部署访问控制设备,启用访问控制功能show access-list查看是否配置访问控制列表部署有访问控制列表,控制网络间的网络访问b、应能根据会话状态信息为数据流提供明确的允许/拒绝访问的能力,控制粒度为网段级show running-config查看配置有NAT地址转换配置;show access-list每条策略是否有明确的源IP、目的IP及协议等配置有NAT配置;每条策略有明确的源IP、目的IP、协议及端口c、应按用户和系统之间的允许访问规则,决定允许或拒绝用户对受控系统进行资源访问,控制粒度为单个用户show access-list查看是否配置访问控制列表部署有访问控制列表,控制各个网段间的网络访问d、应限制具有拨号访问权限的用户数量show version查看系统的授权信息;show running-config查看系统配置信息,确认拨号用户数的数量配置通过配置拨号用户获得IP地址的数量来限制用户数安全审计a、应对网络系统中的网络设备运行状况、网络流量、用户行为等进行日志记录Show logging;Show local-host;show resource usageall;show cpu;show menoryShow nat或者通过ASDM登陆ASA设备查看能查看系统运行状况,系统保留日志及用户行为记录,以及系统的运行状况相关信息b、审计记录应包括事件的日期和时间、用户、事件类型、事件是否成功及其他与审计相关的信息Show logging;Show local-host;show resource usageall;能查看系统运行状况,系统保留日志及用户行为记录,以及系统的运行状况边界完整性检查a、应能够对内部网络中出现的内部用户未通过准许私自联到外部网络的行为进行检查此设备不具备此功能,此项为不适应项恶意代码防范a、应在网络边界处监视以下攻击行为:端口扫描、强力攻击、木马后门攻击、拒绝服务攻击、缓冲区溢出攻击、IP碎片攻击和网络蠕虫攻击等通过端口扫描工具等测试工具判断此项能监视端口扫描、强力攻击、木马后门攻击、拒绝服务攻击、缓冲区溢出攻击、IP碎片攻击和网络蠕虫攻击功能网络设备防护a、应对登录网络设备的用户进行身份鉴别show running-config查看用户名密码机认证配置如:username adminpasswordfMQ/rjnxl9Vwe9mvencrypted privilege15;aaa authenticationtelnet console LOCALaaa authenticationssh console LOCALaaa authenticationenable console LOCAL有配置用户名及密码,对console、telnet、ssh、web已开启认证b、应对网络设备的管理员登录地址进行限制show access-lis查看是否有控制列表对管理员登陆进行控制;show runtelnet 0.0.0.00.0.0.0 insidessh 0.0.0.0 0.0.0.0Outside确定有控制列表或登陆设置对登陆的地址进行限制c、网络设备用户的标识应唯一Show run 查看系统配置确认设备用户的标识是唯一d、身份鉴别信息应具有不易被冒用的特点,口令应有复杂度要求并定期更换通过访谈检查设备的用户、口令信息及是否定期更换Show run 查看系统配置用户名口令复杂度高,密码定期更换e、应具有登录失败处理功能,可采取结束会话、限制非法登录次数和当网络登录连接超时自动退出等措施登陆测试登录失败时系统采取结束会话、限制非法登录次数和当网络登录连接超时自动退出f、当对网络设备进行远程管理时,应采取必要措施防止鉴别信息在网络传输过程中被窃听Show run查看配置是否开启ssh,如aaa authenticationssh console LOCAL配置中有此项配置。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
下列是路由器配置
inte**ce GigabitEthernet0/0
ip address 222.166.2.82 255.255.255.240
ip nat outside
no ip virtual-reassembly
duplex auto
speed auto
media-type rj45
!
inte**ce GigabitEthernet0/1
ip address 172.17.1.254 255.255.255.252
ip nat inside
no ip virtual-reassembly
duplex auto
speed auto
media-type rj45
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 222.166.2.81 这条指向互联网
ip route 172.17.0.0 255.255.0.0 172.17.1.253 这条指向内部,注意看子网掩码
!
!
ip http server
ip http authentication local
ip nat inside source list 100 inte**ce GigabitEthernet0/0 overload 内部计算机上互联网做的NAT
ip nat inside source static tcp 172.18.1.4 3389 222.166.2.82 3389 extendable
ip nat inside source static tcp 172.18.1.4 8090 222.166.2.82 8090 extendable
ip nat inside source static tcp 172.18.1.4 23 222.166.2.82 23 extendable
172.18.1.4为dmz去的内部服务器,我分别映射3389,8090,23三个端口
!
access-list 100 permit ip any any
允许所有用户做地址转换
!
!
control-plane
!
!
line con 0
line aux 0
line vty 0 4
password admin
login
!
scheduler allocate 20000 1000
!
end
往下是asa的配置
inte**ce GigabitEthernet0/0
nameif outside
security-level 0
ip address 172.17.1.253 255.255.255.252
以上这个为接路由器接口
!
inte**ce GigabitEthernet0/1
nameif inside
security-level 50
ip address 172.17.2.254 255.255.255.252
这个是到交换机接口
!
inte**ce GigabitEthernet0/2
nameif DMZ
security-level 50
ip address 172.18.1.254 255.255.255.0
这个为接服务器
!
inte**ce GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
inte**ce Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0 management-only
!
ftp mode passive
access-list outside extended permit ip any any access-list outside extended permit icmp any any access-list dmz extended permit ip any any access-list dmz extended permit icmp any any
我允许所有ip与ICMP通过
pager lines 24
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu management 1500
no failover
icmp permit any outside
icmp permit any inside
no asdm history enable
arp timeout 14400
static (inside,outside) 172.17.2.0 172.17.2.0 netmask 255.255.255.0 static (inside,outside) 172.17.3.0 172.17.3.0 netmask 255.255.255.0 static (dmz,outside) 172.18.1.0 172.18.1.0 netmask 255.255.255.0
以上三条为dmz,inside,outside之间的互相访问
access-group outside in inte**ce outside 绑定访问控制列表到outside access-group dmz in inte**ce dmz 绑定访问控制列表到dmz
route outside 0.0.0.0 0.0.0.0 172.17.1.254 1 指向路由器的路由
以下三条到内网交换机上的用户段
route inside 172.17.5.0 255.255.255.0 172.17.2.253 1
route inside 172.17.4.0 255.255.255.0 172.17.2.253 1
route inside 172.17.3.0 255.255.255.0 172.17.2.253 1。
