Chapter 6. Interfaces and Inner Classes
容器技术智慧树知到期末考试章节课后题库2024年山东劳动职业技术学院

容器技术智慧树知到期末考试答案章节题库2024年山东劳动职业技术学院1.Docker Swarm需要网络的支持,但不依赖于特定的网络组件。
()答案:错2.Rancher的用户可以利用“应用商店”来部署各种应用,并可以在应用有新版本时实现自动升级。
()答案:对3.在Kubernetes配置文件中,可以使用nodeSelector来指定容器运行在特定的节点上。
()答案:对4.在Kubernetes配置文件中,可以使用securityContext来设置容器的安全策略。
()答案:对5.使用kubectl get命令可以获取集群中所有资源的信息。
()答案:对6.虚拟化技术是基于系统的隔离,容器技术是基于程序的隔离。
()答案:对7.Kubernetes配置文件只支持YAML格式。
()答案:错8.在docker swarm中,节点分为管理节点和工作节点两种类型。
()答案:对9.使用kubectl describe命令可以获取资源的详细信息,包括资源的历史、事件等。
()答案:对10.使用docker-compose stop命令只会停止应用,但不会删除容器。
()答案:对11.使用docker-compose up命令可以在后台启动应用。
()答案:对12.Docker镜像只能包含一个应用。
()答案:错13.使用docker node rm命令可以从docker swarm中删除一个节点,但该节点必须先离开swarm。
()答案:对14.Docker Compose文件可以用于部署到生产环境。
()答案:对15.Docker镜像的层可以合并成一个单独的镜像。
()答案:对16.docker CE是社区版Docker。
()答案:对17.在docker swarm中,一个节点只能同时担任管理节点和工作节点的角色。
()答案:错18.Rancher的组成主要包括基础设施编排、容器编排与调度、应用商店和企业级权限管理。
()答案:对19.使用docker-compose rm命令可以删除已停止的Compose应用,包括容器和网络,但不会删除卷和镜像。
Chapter06_PPT
10
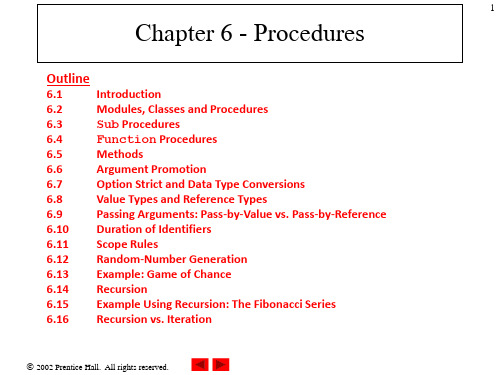
6.3 Sub Procedures
• Format of a procedure definition
Sub procedure-name(parameter-list) declarations and statements End Sub
• Procedure header
– The first line is known as the procedure header
6.18
2002 Prentice Hall. All rights reserved.
3
6.1 Introduction
• Divide and Conquer
– The best way to develop and maintain a large program is to construct it from small, manageable pieces.
Number 1 2 3 4 5 6 7 8 9 10
Square 1 4 9 16 25 36 49 64 81 100
Outline
13
SquareInteger.vb Program Output
2002 Prentice Hall.
All rights reserved.
14
6.4 Function Procedures
• Procedure-name
– Directly follows the Sub keyword – Can be any valid identifier – It is used to call this Sub procedure within the program
• Procedure body
密码编码学与网络安全(第五版)答案

Chapter 1: Introduction (5)Chapter 2: Classical Encryption Techniques (7)Chapter 3: Block Ciphers and the Date Encryption Standard (13)Chapter 4: Finite Fields (21)Chapter 5: Advanced Encryption Standard (28)Chapter 6: More on Symmetric Ciphers (33)Chapter 7: Confidentiality Using Symmetric Encryption (38)Chapter 8: Introduction to Number Theory (42)Chapter 9: Public-Key Cryptography and RSA (46)Chapter 10: Key Management; Other Public-Key Cryptosystems (55)Chapter 11: Message Authentication and Hash Functions (59)Chapter 12: Hash and MAC Algorithms (62)Chapter 13: Digital Signatures and Authentication Protocols (66)Chapter 14: Authentication Applications (71)Chapter 15: Electronic Mail Security (73)Chapter 16: IP Security (76)Chapter 17: Web Security (80)Chapter 18: Intruders (83)Chapter 19: Malicious Software (87)Chapter 20: Firewalls (89)A NSWERS TO Q UESTIONS1.1The OSI Security Architecture is a framework that provides a systematic way of definingthe requirements for security and characterizing the approaches to satisfying thoserequirements. The document defines security attacks, mechanisms, and services, and the relationships among these categories.1.2 Passive attacks have to do with eavesdropping on, or monitoring, transmissions.Electronic mail, file transfers, and client/server exchanges are examples oftransmissions that can be monitored. Active attacks include the modification of transmitted data and attempts to gain unauthorized access to computer systems.1.3 Passive attacks: release of message contents and traffic analysis. Active attacks:masquerade, replay, modification of messages, and denial of service.1.4 Authentication: The assurance that the communicating entity is the one that it claims to be.Access control: The prevention of unauthorized use of a resource (i.e., this service controls who can have access to a resource, under what conditions access can occur, and what those accessing the resource are allowed to do).Data confidentiality: The protection of data from unauthorized disclosure.Data integrity: The assurance that data received are exactly as sent by an authorized entity(i.e., contain no modification, insertion, deletion, or replay).Nonrepudiation: Provides protection against denial by one of the entities involved in a communication of having participated in all or part of the communication.Availability service: The property of a system or a system resource being accessible and usable upon demand by an authorized system entity, according to performancespecifications for the system (i.e., a system is available if it provides services according to the system design whenever users request them).1.5 See Table 1.3.C HAPTER 2C LASSICAL E NCRYPTION T ECHNIQUESR2.1 Plaintext, encryption algorithm, secret key, ciphertext, decryption algorithm.2.2 Permutation and substitution.2.3 One key for symmetric ciphers, two keys for asymmetric ciphers.2.4 A stream cipher is one that encrypts a digital data stream one bit or one byte at atime. A block cipher is one in which a block of plaintext is treated as a whole and used to produce a ciphertext block of equal length.2.5 Cryptanalysis and brute force.2.6 Ciphertext only. One possible attack under these circumstances is the brute-forceapproach of trying all possible keys. If the key space is very large, this becomesimpractical. Thus, the opponent must rely on an analysis of the ciphertext itself, generally applying various statistical tests to it. Known plaintext. The analyst may be able to capture one or more plaintext messages as well as their encryptions.With this knowledge, the analyst may be able to deduce the key on the basis of the way in which the known plaintext is transformed. Chosen plaintext. If the analyst is able to choose the messages to encrypt, the analyst may deliberately pickpatterns that can be expected to reveal the structure of the key.2.7 An encryption scheme is unconditionally secure if the ciphertext generated by thescheme does not contain enough information to determine uniquely thecorresponding plaintext, no matter how much ciphertext is available. Anencryption scheme is said to be computationally secure if: (1) the cost of breaking the cipher exceeds the value of the encrypted information, and (2) the timerequired to break the cipher exceeds the useful lifetime of the information.2.8 The Caesar cipher involves replacing each letter of the alphabet with the letterstanding k places further down the alphabet, for k in the range 1 through 25.2.9 A monoalphabetic substitution cipher maps a plaintext alphabet to a ciphertextalphabet, so that each letter of the plaintext alphabet maps to a single unique letter of the ciphertext alphabet.2.10 The Playfair algorithm is based on the use of a 5 5 matrix of letters constructedusing a keyword. Plaintext is encrypted two letters at a time using this matrix.2.11 A polyalphabetic substitution cipher uses a separate monoalphabetic substitutioncipher for each successive letter of plaintext, depending on a key.2.12 1. There is the practical problem of making large quantities of random keys. Anyheavily used system might require millions of random characters on a regularbasis. Supplying truly random characters in this volume is a significant task.2. Even more daunting is the problem of key distribution and protection. For everymessage to be sent, a key of equal length is needed by both sender and receiver.Thus, a mammoth key distribution problem exists.2.13 A transposition cipher involves a permutation of the plaintext letters.2.14 Steganography involves concealing the existence of a message.2.1 a. No. A change in the value of b shifts the relationship between plaintext lettersand ciphertext letters to the left or right uniformly, so that if the mapping isone-to-one it remains one-to-one.b. 2, 4, 6, 8, 10, 12, 13, 14, 16, 18, 20, 22, 24. Any value of a larger than 25 isequivalent to a mod 26.c. The values of a and 26 must have no common positive integer factor other than1. This is equivalent to saying that a and 26 are relatively prime, or that thegreatest common divisor of a and 26 is 1. To see this, first note that E(a, p) = E(a,q) (0 ≤ p≤ q < 26) if and only if a(p–q) is divisible by 26. 1. Suppose that a and26 are relatively prime. Then, a(p–q) is not divisible by 26, because there is noway to reduce the fraction a/26 and (p–q) is less than 26. 2. Suppose that a and26 have a common factor k > 1. Then E(a, p) = E(a, q), if q = p + m/k≠ p.2.2 There are 12 allowable values of a (1, 3, 5, 7, 9, 11, 15, 17, 19, 21, 23, 25). There are 26allowable values of b, from 0 through 25). Thus the total number of distinct affine Caesar ciphers is 12 26 = 312.2.3 Assume that the most frequent plaintext letter is e and the second most frequentletter is t. Note that the numerical values are e = 4; B = 1; t = 19; U = 20. Then we have the following equations:1 = (4a + b) mod 2620 = (19a + b) mod 26Thus, 19 = 15a mod 26. By trial and error, we solve: a = 3.Then 1 = (12 + b) mod 26. By observation, b = 15.2.4 A good glass in the Bishop's hostel in the Devil's seat—twenty-one degrees andthirteen minutes—northeast and by north—main branch seventh limb east side—shoot from the left eye of the death's head— a bee line from the tree through the shot fifty feet out. (from The Gold Bug, by Edgar Allan Poe)2.5 a.The first letter t corresponds to A, the second letter h corresponds to B, e is C, sis D, and so on. Second and subsequent occurrences of a letter in the keysentence are ignored. The resultciphertext: SIDKHKDM AF HCRKIABIE SHIMC KD LFEAILAplaintext: basilisk to leviathan blake is contactb.It is a monalphabetic cipher and so easily breakable.c.The last sentence may not contain all the letters of the alphabet. If the firstsentence is used, the second and subsequent sentences may also be used untilall 26 letters are encountered.2.6The cipher refers to the words in the page of a book. The first entry, 534, refers topage 534. The second entry, C2, refers to column two. The remaining numbers are words in that column. The names DOUGLAS and BIRLSTONE are simply words that do not appear on that page. Elementary! (from The Valley of Fear, by Sir Arthur Conan Doyle)2.7 a.2 8 10 7 9 63 14 54 2 8 1056 37 1 9ISRNG BUTLF RRAFR LIDLP FTIYO NVSEE TBEHI HTETAEYHAT TUCME HRGTA IOENT TUSRU IEADR FOETO LHMETNTEDS IFWRO HUTEL EITDSb.The two matrices are used in reverse order. First, the ciphertext is laid out incolumns in the second matrix, taking into account the order dictated by thesecond memory word. Then, the contents of the second matrix are read left toright, top to bottom and laid out in columns in the first matrix, taking intoaccount the order dictated by the first memory word. The plaintext is then read left to right, top to bottom.c.Although this is a weak method, it may have use with time-sensitiveinformation and an adversary without immediate access to good cryptanalysis(e.g., tactical use). Plus it doesn't require anything more than paper and pencil,and can be easily remembered.2.8 SPUTNIK2.9 PT BOAT ONE OWE NINE LOST IN ACTION IN BLACKETT STRAIT TWOMILES SW MERESU COVE X CREW OF TWELVE X REQUEST ANYINFORMATION2.10 a.b.2.11 a. UZTBDLGZPNNWLGTGTUEROVLDBDUHFPERHWQSRZb.UZTBDLGZPNNWLGTGTUEROVLDBDUHFPERHWQSRZc. A cyclic rotation of rows and/or columns leads to equivalent substitutions. Inthis case, the matrix for part a of this problem is obtained from the matrix ofProblem 2.10a, by rotating the columns by one step and the rows by three steps.2.12 a. 25! ≈ 284b. Given any 5x5 configuration, any of the four row rotations is equivalent, for atotal of five equivalent configurations. For each of these five configurations,any of the four column rotations is equivalent. So each configuration in factrepresents 25 equivalent configurations. Thus, the total number of unique keysis 25!/25 = 24!2.13 A mixed Caesar cipher. The amount of shift is determined by the keyword, whichdetermines the placement of letters in the matrix.2.14 a. Difficulties are things that show what men are.b. Irrationally held truths may be more harmful than reasoned errors.2.15 a. We need an even number of letters, so append a "q" to the end of the message.Then convert the letters into the corresponding alphabetic positions:The calculations proceed two letters at a time. The first pair:The first two ciphertext characters are alphabetic positions 7 and 22, whichcorrespond to GV. The complete ciphertext:GVUIGVKODZYPUHEKJHUZWFZFWSJSDZMUDZMYCJQMFWWUQRKRb. We first perform a matrix inversion. Note that the determinate of theencryption matrix is (9 ⨯ 7) – (4 ⨯ 5) = 43. Using the matrix inversion formulafrom the book:Here we used the fact that (43)–1 = 23 in Z26. Once the inverse matrix has beendetermined, decryption can proceed. Source: [LEWA00].2.16 Consider the matrix K with elements k ij to consist of the set of column vectors K j,where:andThe ciphertext of the following chosen plaintext n-grams reveals the columns of K:(B, A, A, …, A, A) ↔ K1(A, B, A, …, A, A) ↔ K2:(A, A, A, …, A, B) ↔ K n2.17 a.7 ⨯ 134b.7 ⨯ 134c.134d.10 ⨯ 134e.24⨯ 132f.24⨯(132– 1) ⨯ 13g. 37648h.23530i.1572482.18 key: legleglegleplaintext: explanationciphertext: PBVWETLXOZR2.19 a.b.2.20your package ready Friday 21st room three Please destroy this immediately.2.21 y the message out in a matrix 8 letters across. Each integer in the key tellsyou which letter to choose in the corresponding row. Result:He sitteth between the cherubims. The isles may be gladthereof. As the rivers in the south.b.Quite secure. In each row there is one of eight possibilities. So if the ciphertextis 8n letters in length, then the number of possible plaintexts is 8n.c. Not very secure. Lord Peter figured it out. (from The Nine Tailors)3.1 Most symmetric block encryption algorithms in current use are based on the Feistelblock cipher structure. Therefore, a study of the Feistel structure reveals theprinciples behind these more recent ciphers.3.2 A stream cipher is one that encrypts a digital data stream one bit or one byte at atime. A block cipher is one in which a block of plaintext is treated as a whole and used to produce a ciphertext block of equal length.3.3 If a small block size, such as n = 4, is used, then the system is equivalent to aclassical substitution cipher. For small n, such systems are vulnerable to a statistical analysis of the plaintext. For a large block size, the size of the key, which is on the order of n 2n, makes the system impractical.3.4 In a product cipher, two or more basic ciphers are performed in sequence in such away that the final result or product is cryptographically stronger than any of the component ciphers.3.5 In diffusion, the statistical structure of the plaintext is dissipated into long-rangestatistics of the ciphertext. This is achieved by having each plaintext digit affect thevalue of many ciphertext digits, which is equivalent to saying that each ciphertext digit is affected by many plaintext digits. Confusion seeks to make the relationship between the statistics of the ciphertext and the value of the encryption key ascomplex as possible, again to thwart attempts to discover the key. Thus, even if the attacker can get some handle on the statistics of the ciphertext, the way in which the key was used to produce that ciphertext is so complex as to make it difficult todeduce the key. This is achieved by the use of a complex substitution algorithm. 3.6 Block size: Larger block sizes mean greater security (all other things being equal)but reduced encryption/decryption speed. Key size: Larger key size means greater security but may decrease encryption/decryption speed. Number of rounds: The essence of the Feistel cipher is that a single round offers inadequate security but that multiple rounds offer increasing security. Subkey generation algorithm:Greater complexity in this algorithm should lead to greater difficulty ofcryptanalysis. Round function: Again, greater complexity generally means greater resistance to cryptanalysis. Fast software encryption/decryption: In many cases, encryption is embedded in applications or utility functions in such a way as topreclude a hardware implementation. Accordingly, the speed of execution of the algorithm becomes a concern. Ease of analysis: Although we would like to make our algorithm as difficult as possible to cryptanalyze, there is great benefit inmaking the algorithm easy to analyze. That is, if the algorithm can be concisely and clearly explained, it is easier to analyze that algorithm for cryptanalyticvulnerabilities and therefore develop a higher level of assurance as to its strength.3.7 The S-box is a substitution function that introduces nonlinearity and adds to thecomplexity of the transformation.3.8 The avalanche effect is a property of any encryption algorithm such that a smallchange in either the plaintext or the key produces a significant change in theciphertext.3.9 Differential cryptanalysis is a technique in which chosen plaintexts with particularXOR difference patterns are encrypted. The difference patterns of the resultingciphertext provide information that can be used to determine the encryption key.Linear cryptanalysis is based on finding linear approximations to describe thetransformations performed in a block cipher.3.1 a. For an n-bit block size are 2n possible different plaintext blocks and 2n possibledifferent ciphertext blocks. For both the plaintext and ciphertext, if we treat theblock as an unsigned integer, the values are in the range 0 through 2n– 1. For amapping to be reversible, each plaintext block must map into a uniqueciphertext block. Thus, to enumerate all possible reversible mappings, the blockwith value 0 can map into anyone of 2n possible ciphertext blocks. For anygiven mapping of the block with value 0, the block with value 1 can map intoany one of 2n– 1 possible ciphertext blocks, and so on. Thus, the total numberof reversible mappings is (2n)!.b. In theory, the key length could be log2(2n)! bits. For example, assign eachmapping a number, from 1 through (2n)! and maintain a table that shows themapping for each such number. Then, the key would only require log2(2n)! bits, but we would also require this huge table. A more straightforward way todefine the key is to have the key consist of the ciphertext value for eachplaintext block, listed in sequence for plaintext blocks 0 through 2n– 1. This iswhat is suggested by Table 3.1. In this case the key size is n⨯ 2n and the hugetable is not required.3.2 Because of the key schedule, the round functions used in rounds 9 through 16 aremirror images of the round functions used in rounds 1 through 8. From this fact we see that encryption and decryption are identical. We are given a ciphertext c.Let m' = c. Ask the encryption oracle to encrypt m'. The ciphertext returned by the oracle will be the decryption of c.3.3 a.We need only determine the probability that for the remaining N – t plaintextsP i, we have E[K, P i] ≠ E[K', P i]. But E[K, P i] = E[K', P i] for all the remaining P iwith probability 1 – 1/(N–t)!.b.Without loss of generality we may assume the E[K, P i] = P i since E K(•) is takenover all permutations. It then follows that we seek the probability that apermutation on N–t objects has exactly t' fixed points, which would be theadditional t' points of agreement between E(K, •) and E(K', •). But apermutation on N–t objects with t' fixed points is equal to the number of wayst' out of N–t objects can be fixed, while the remaining N–t–t' are not fixed.Then using Problem 3.4 we have thatPr(t' additional fixed points) = ⨯Pr(no fixed points in N – t – t' objects)=We see that this reduces to the solution to part (a) when t' = N–t.3.4Let be the set of permutations on [0, 1, . . ., 2n– 1], which is referredto as the symmetric group on 2n objects, and let N = 2n. For 0 ≤ i≤ N, let A i be all mappings for which π(i) = i. It follows that |A i| = (N– 1)! and= (N–k)!. The inclusion-exclusion principle states thatPr(no fixed points in π)=== 1 – 1 + 1/2! – 1/3! + . . . + (–1)N⨯ 1/N!= e–1 +Then since e–1≈ 0.368, we find that for even small values of N, approximately37% of permutations contain no fixed points.3.53.6 Main key K = 111…111 (56 bits)Round keys K1 = K2=…= K16 = 1111..111 (48 bits)Ciphertext C = 1111…111 (64 bits)Input to the first round of decryption =LD0RD0 = RE16LE16 = IP(C) = 1111...111 (64 bits)LD0 = RD0 = 1111...111 (32 bits)Output of the first round of decryption = LD1RD1LD1 = RD0= 1111…111 (32 bits)Thus, the bits no. 1 and 16 of the output are equal to ‘1’.RD1 = LD0 F(RD0, K16)We are looking for bits no. 1 and 16 of RD1 (33 and 48 of the entire output).Based on the analysis of the permutation P, bit 1 of F(RD0, K16) comes from thefourth output of the S-box S4, and bit 16 of F(RD0, K16) comes from the second output of the S-box S3. These bits are XOR-ed with 1’s from the correspondingpositions of LD0.Inside of the function F,E(RD0) ≈ K16= 0000…000 (48 bits),and thus inputs to all eight S-boxes are equal to “000000”.Output from the S-box S4 = “0111”, and thus the fourth output is equal to ‘1’,Output from the S-box S3 = “1010”, and thus the second output is equal to ‘0’.From here, after the XOR, the bit no. 33 of the first round output is equal to ‘0’, and the bit no. 48 is equal to ‘1’.3.7 In the solution given below the following general properties of the XOR functionare used:A ⊕ 1 = A'(A ⊕ B)' = A' ⊕ B = A ⊕ B'A' ⊕ B' = A ⊕ BWhere A' = the bitwise complement of A.a. F (R n, K n+1) = 1We haveL n+1 = R n; R n+1 = L n⊕ F (R n, K n+1) = L n⊕ 1 = L n'ThusL n+2 = R n+1 = L n' ; R n+2 = L n+1 = R n'i.e., after each two rounds we obtain the bit complement of the original input,and every four rounds we obtain back the original input:L n+4 = L n+2' = L n ; R n+2 = R n+2' = R nTherefore,L16 = L0; R16 = R0An input to the inverse initial permutation is R16 L16.Therefore, the transformation computed by the modified DES can berepresented as follows:C = IP–1(SWAP(IP(M))), where SWAP is a permutation exchanging the positionof two halves of the input: SWAP(A, B) = (B, A).This function is linear (and thus also affine). Actually, this is a permutation, the product of three permutations IP, SWAP, and IP–1. This permutation ishowever different from the identity permutation.b. F (R n, K n+1) = R n'We haveL n+1 = R n; R n+1 = L n⊕ F(R n, K n+1) = L n⊕ R n'L n+2 = R n+1 = L n⊕ R n'R n+2 = L n+1⊕ F(R n+1, K n+2) = R n≈ (L n⊕ R n')' = R n⊕ L n⊕ R n'' = L nL n+3 = R n+2 = L nR n+3 = L n+2⊕ F (R n+2, K n+3) = (L n≈ R n') ⊕ L n' = R n' ⊕1 = R ni.e., after each three rounds we come back to the original input.L15 = L0; R15 = R0andL16 = R0(1)R16 = L0⊕ R0' (2)An input to the inverse initial permutation is R16 L16.A function described by (1) and (2) is affine, as bitwise complement is affine,and the other transformations are linear.The transformation computed by the modified DES can be represented asfollows:C = IP–1(FUN2(IP(M))), where FUN2(A, B) = (A ⊕ B', B).This function is affine as a product of three affine functions.In all cases decryption looks exactly the same as encryption.3.8 a. First, pass the 64-bit input through PC-1 (Table 3.4a) to produce a 56-bit result.Then perform a left circular shift separately on the two 28-bit halves. Finally,pass the 56-bit result through PC-2 (Table 3.4b) to produce the 48-bit K1.:in binary notation: 0000 1011 0000 0010 0110 01111001 1011 0100 1001 1010 0101in hexadecimal notation: 0 B 0 2 6 7 9 B 4 9 A 5b. L0, R0 are derived by passing the 64-plaintext through IP (Table 3.2a):L0 = 1100 1100 0000 0000 1100 1100 1111 1111R0 = 1111 0000 1010 1010 1111 0000 1010 1010c. The E table (Table 3.2c) expands R0 to 48 bits:E(R0) = 01110 100001 010101 010101 011110 100001 010101 010101d. A = 011100 010001 011100 110010 111000 010101 110011 110000e. (1110) = (14) = 0 (base 10) = 0000 (base 2)(1000) = (8) = 12 (base 10) = 1100 (base 2)(1110) = (14) = 2 (base 10) = 0010 (base 2)(1001) = (9) = 1 (base 10) = 0001 (base 2)(1100) = (12) = 6 (base 10) = 0110 (base 2)(1010) = (10) = 13 (base 10) = 1101 (base 2)(1001) = (9) = 5 (base 10) = 0101 (base 2)(1000) = (8) = 0 (base 10) = 0000 (base 2)f. B = 0000 1100 0010 0001 0110 1101 0101 0000g. Using Table 3.2d, P(B) = 1001 0010 0001 1100 0010 0000 1001 1100h. R1 = 0101 1110 0001 1100 1110 1100 0110 0011i. L1 = R0. The ciphertext is the concatenation of L1 and R1. Source: [MEYE82]3.9The reasoning for the Feistel cipher, as shown in Figure 3.6 applies in the case ofDES. We only have to show the effect of the IP and IP–1 functions. For encryption, the input to the final IP–1 is RE16|| LE16. The output of that stage is the ciphertext.On decryption, the first step is to take the ciphertext and pass it through IP. Because IP is the inverse of IP–1, the result of this operation is just RE16|| LE16, which isequivalent to LD0|| RD0. Then, we follow the same reasoning as with the Feistel cipher to reach a point where LE0 = RD16 and RE0 = LD16. Decryption is completed by passing LD0|| RD0 through IP–1. Again, because IP is the inverse of IP–1, passing the plaintext through IP as the first step of encryption yields LD0|| RD0, thusshowing that decryption is the inverse of encryption.3.10a.Let us work this from the inside out.T16(L15|| R15) = L16|| R16T17(L16|| R16) = R16|| L16IP [IP–1 (R16|| L16)] = R16|| L16TD1(R16|| L16) = R15|| L15b.T16(L15|| R15) = L16|| R16IP [IP–1 (L16|| R16)] = L16|| R16TD1(R16 || L16) = R16|| L16 f(R16, K16)≠ L15|| R153.11PC-1 is essentially the same as IP with every eighth bit eliminated. This wouldenable a similar type of implementation. Beyond that, there does not appear to be any particular cryptographic significance.3.13a.The equality in the hint can be shown by listing all 1-bit possibilities:We also need the equality A ⊕ B = A' ⊕ B', which is easily seen to be true. Now, consider the two XOR operations in Figure 3.8. If the plaintext and key for anencryption are complemented, then the inputs to the first XOR are alsocomplemented. The output, then, is the same as for the uncomplementedinputs. Further down, we see that only one of the two inputs to the secondXOR is complemented, therefore, the output is the complement of the outputthat would be generated by uncomplemented inputs.b.In a chosen plaintext attack, if for chosen plaintext X, the analyst can obtain Y1= E[K, X] and Y2 = E[K, X'], then an exhaustive key search requires only 255rather than 256 encryptions. To see this, note that (Y2)' = E[K', X]. Now, pick atest value of the key T and perform E[T, X]. If the result is Y1, then we knowthat T is the correct key. If the result is (Y2)', then we know that T' is the correctkey. If neither result appears, then we have eliminated two possible keys withone encryption.3.14 The result can be demonstrated by tracing through the way in which the bits areused. An easy, but not necessary, way to see this is to number the 64 bits of the key as follows (read each vertical column of 2 digits as a number):2113355-1025554-0214434-1123334-0012343-2021453-0202435-0110454- 1031975-1176107-2423401-7632789-7452553-0858846-6836043-9495226-The first bit of the key is identified as 21, the second as 10, the third as 13, and so on.The eight bits that are not used in the calculation are unnumbered. The numbers 01 through 28 and 30 through 57 are used. The reason for this assignment is to clarify the way in which the subkeys are chosen. With this assignment, the subkey for the first iteration contains 48 bits, 01 through 24 and 30 through 53, in their naturalnumerical order. It is easy at this point to see that the first 24 bits of each subkey will always be from the bits designated 01 through 28, and the second 24 bits of each subkey will always be from the bits designated 30 through 57.3.15 For 1 ≤ i ≤ 128, take c i∈ {0, 1}128 to be the string containing a 1 in position i andthen zeros elsewhere. Obtain the decryption of these 128 ciphertexts. Let m1,m2, . . . , m128 be the corresponding plaintexts. Now, given any ciphertext c which does not consist of all zeros, there is a unique nonempty subset of the c i’s which we can XOR together to obtain c. Let I(c) ⊆ {1, 2, . . . , 128} denote this subset.ObserveThus, we obtain the plaintext of c by computing . Let 0 be the all-zerostring. Note that 0 = 0⊕0. From this we obtain E(0) = E(0⊕0) = E(0) ⊕ E(0) = 0.Thus, the plaintext of c = 0 is m = 0. Hence we can decrypt every c ∈ {0, 1}128.3.16a. This adds nothing to the security of the algorithm. There is a one-to-onereversible relationship between the 10-bit key and the output of the P10function. If we consider the output of the P10 function as a new key, then thereare still 210 different unique keys.b. By the same reasoning as (a), this adds nothing to the security of the algorithm.3.17s = wxyz + wxy + wyz + wy + wz + yz + w + x + zt = wxz + wyz + wz + xz + yz + w + y3.18OK4.1 A group is a set of elements that is closed under a binary operation and that isassociative and that includes an identity element and an inverse element.4.2 A ring is a set of elements that is closed under two binary operations, addition andsubtraction, with the following: the addition operation is a group that iscommutative; the multiplication operation is associative and is distributive over the addition operation.C HAPTER 4F INITE F IELDS。
java typereference 二层嵌套 -回复

java typereference 二层嵌套-回复Java中的嵌套类型(Nested Types)是指在一个类中定义另一个类。
这种二层嵌套类型可以是内部类(Inner Class),也可以是静态嵌套类(Static Nested Class)。
在本文中,我们将探讨Java中的二层嵌套类型,并深入了解它们的使用和作用。
首先,让我们从内部类开始。
内部类是指在另一个类内部定义的类。
这种定义方式使得内部类可以直接访问外部类的成员变量和方法,而不需要使用实例变量。
内部类有四种类型:成员内部类(Member Inner Class)、局部内部类(Local Inner Class)、匿名内部类(Anonymous Inner Class)和静态内部类(Static Inner Class)。
成员内部类是最常见的内部类类型,它是在外部类的成员位置上定义的。
下面是一个例子:javapublic class Outer {private int outerField;成员内部类public class Inner {public void printField() {System.out.println("外部类的成员变量outerField 的值是:" + outerField);}}}在这个例子中,类`Inner`是类`Outer`的成员内部类。
它可以直接访问外部类`Outer`的成员变量`outerField`。
为了创建内部类的实例,我们需要先创建外部类的实例,然后使用外部类的对象来创建内部类的对象,如下所示:javapublic class Main {public static void main(String[] args) {Outer outer = new Outer();Outer.Inner inner = outer.new Inner();inner.printField();}}在上面的示例中,我们首先创建外部类`Outer`的实例`outer`,然后使用`outer`来创建内部类`Inner`的实例`inner`。
解析JAVA程序设计第六章课后答案

第6章习题解答1.简述Java中设计图形用户界面程序的主要步骤。
对于设计图形用户界面程序而言,一般分为两个步骤:第一步,设计相应的用户界面,并根据需要对相关的组件进行布局;第二步,添加相关的事件处理,如鼠标、菜单、按钮和键盘等事件。
2.试说明容器与组件之间的关系。
组件(component)是图形用户界面中的各种部件(如标签、按钮、文本框等等),所有的组件类都继承自JComponent类。
容器(container)是用来放置其他组件的一种特殊部件,在java中容器用Container类描述。
3.阅读下面程序,说明其运行结果和功能。
//filename:MyFrame.javaimport java.awt.*;import java.awt.event.*;import javax.swing.*;public class MyFrame{public static void main(String agrs[]){JFrame f=new JFrame("简单窗体示例");f.setDefaultCloseOperation(JFrame.EXIT_ON_CLOSE);JLabel l=new JLabel("习题1");f.getContentPane().add(l,BorderLayout.CENTER);f.pack();f.setVisible(true);}}程序的运行结果如下:4.阅读下面程序,说明其运行结果和功能。
//filename:TestButton.javaimport java.awt.*;import javax.swing.*;public class TestButton extends JFrame{JButton b1,b2;TestButton(String s){super(s);b1=new JButton("按钮1");b2=new JButton("按钮2");setLayout(new FlowLayout());add(b1);add(b2);setSize(300,100);setVisible(true);}public static void main(String args[]){ TestButton test;test=new TestButton("测试按钮"); }}程序的运行结果如下:5.阅读下面程序,说明其运行结果和功能。
系统与要素的关系英语作文

系统与要素的关系英语作文In the realm of systems theory, the relationship between a system and its elements is a fundamental concept that underpins the understanding of complex structures and processes. A system can be defined as a set of interrelated components that work together to achieve a common goal or function. The elements, on the other hand, are the individual parts or units that make up the system.The relationship between a system and its elements is characterized by interdependence and interaction. Eachelement plays a specific role within the system, contributing to its overall functionality. The performance of the systemis not just a sum of its parts but is also influenced by the way these parts interact with each other.Take, for example, a computer system. It consists of various elements such as the central processing unit (CPU), memory, storage devices, and input/output devices. Each of these elements has a distinct role: the CPU processes data, memory stores it temporarily, and storage devices retain it forlong-term use. Input/output devices allow for the interaction with the user. However, the computer's performance is not solely determined by the quality of its individual components. The efficiency of the system also depends on how well these components communicate and work in unison.Moreover, the relationship between a system and its elementsis dynamic. Changes in one element can have cascading effects on the rest of the system. For instance, an upgrade in the CPU can lead to increased processing speed, but if the memory is not upgraded accordingly, it may become a bottleneck, limiting the overall performance of the system.In conclusion, the relationship between a system and its elements is one of mutual influence and synergy. Understanding this relationship is crucial for effective system design, management, and optimization. It is through the harmonious interaction of its elements that a system can achieve its full potential and fulfill its intended purpose.。
Inner classes

Because its instances may exist after the method exits, code in the local class cannot access variables declared in the method unless they are declared final
new Interface (args) { body } b.addActionListener (new ActionListener( ) { public void actionPerformed (ActionEvent e) { System.out.println (“Ouch!”); }});
6
Example anonymous inner class
An ActionListener is a Java-supplied interface for listening to Buttons and some other things The format (from the previous slide) is
Local classes
Defined within a method Can access final variables in the enclosing class
10
The End
11
3
Member classes
A member class is an “ordinary” inner class
class Outer { int n; class Inner { int ten = 10; void setNToTen( ) { n = ten; } } void setN ( ) { new Inner( ).setNToTen( ); } }
oc中英文对照

oc中英文对照Objective-C中英文对照Objective-C是一种面向对象的编程语言,广泛用于iOS和macOS 应用程序的开发。
它将C语言与面向对象编程相结合,提供了丰富的功能和特性。
下面是一份Objective-C中的常用词汇对照表,其中包含了中文和英文的对应词汇,以帮助开发者更好地理解和使用Objective-C。
1. 关键字(Keywords)关键字是在Objective-C中具有特殊含义的单词,用于表示语言的各种语法结构和功能。
- 类定义:Class- 继承:Inheritance- 实例变量:Instance Variables- 方法:Methods- 属性:Properties- 协议:Protocol- 实现:Implementation- 接口:Interface- 静态:Static- 共有:Public- 私有:Private- 受保护:Protected- 抽象:Abstract- 选择器:Selector- 异步:Asynchronous- 同步:Synchronous2. 类与对象(Classes and Objects)Objective-C是一种面向对象的编程语言,类与对象是其核心概念。
- 类:Class- 对象:Object- 实例变量:Instance Variable- 类方法:Class Method- 对象方法:Instance Method- 初始化:Initialization- 实例化:Instantiation- 继承:Inheritance- 多态:Polymorphism- 封装:Encapsulation- 抽象类:Abstract Class- 类别:Category- 选择器:Selector- 代理:Delegate- 消息发送:Message Sending- 内存管理:Memory Management3. 数据类型(Data Types)Objective-C支持各种常见的数据类型,用于存储和操作数据。
java嵌套类(Nested Classes)总结

java嵌套类(Nested Classes)总结Nested Classes定义在java语言规范里面,嵌套类(Nested Classes)定义是:A nested class is any class whose declaration occurs within the body of another class or interface. A top level class is a class that is not a nested class.说的简单一点,就是定义在类里面的类。
一般把定义内部类的外围类成为包装类(enclosing class)或者外部类嵌套类分类根据nested class定义的地方,可以分为member nested class,local nestedclass , anonymous nested classmember nested class(成员嵌套类):成员嵌套类作为 enclosing class 的成员定义的,成员嵌套类有enclosing class属性local nested class (局部嵌套类): 局部嵌套类定义在 enclosing class 的方法里面,局部嵌套类有enclosing class 属性和enclosing method 属性anonymous nested class(匿名嵌套类):匿名嵌套类没有显示的定义一个类,直接通过new 的方法创建类的实例。
一般回调模式情况下使用的比较多member nested class 可以使用public,private,protected访问控制符,也可以用static,final关键字local nested class 可以使用final关键字anonymous nested class 不使用任何关键字和访问控制符见下面的代码public class EnclosingClass {public static final class NestedMemberClass{}public void nestedLocalClass() {final class NestedLocalClass {}}public void nestedAnonymousClass() {new Runnable() {@Overridepublic void run() {}};}}在大多数情况下,一般把nested classes 分为两种:Static Nested Classes(静态嵌套类): 就是用static修饰的成员嵌套类InnerClass:静态嵌套类之外所有的嵌套类的总称,也就是没有用static定义的nestedclasses,Inner Classes 不能定义为static,不能有static方法和static初始化语句块。
编译原理英文版

Compiler Principles (English Version)BackgroundCompiler theory is a fundamental subject in computer science that focuses on the study of how programming languages are translated into machine code. It plays a crucial role in software development by enabling programmers to write in high-level languages and have their code executed by machines. This document provides an overview of the key concepts and principles of compiler theory.1. IntroductionThe field of compiler theory deals with the design and implementation of compilers. A compiler is a software tool that translates source code written in a programming language into an equivalent program in another language, typically machine code. The process of compilation involves multiple stages, which are executed sequentially. These stages include lexical analysis, syntax analysis, semantic analysis, code generation, and optimization.2. Lexical AnalysisLexical analysis is the initial stage of the compilation process. It involves breaking down the source code into a sequence of tokens. Tokens are the smallest units of meaning in a programming language. The lexer, also known as the scanner, reads the source code character by character and identifies the tokens based on predefined rules.3. Syntax AnalysisOnce the tokens have been identified, the next stage is syntax analysis. This stage involves checking the sequence of tokens against the grammar rules of the programming language. The parser analyzes the tokens and constructs a parse tree, which represents the structure of the source code according to the grammar rules.4. Semantic AnalysisSemantic analysis is performed after the syntax analysis stage. It focuses on the meaning of the source code. The semantic analyzer checks for semantic errors andenforces the language-specific rules. It also builds the symbol table, which keeps track of the variables, functions, and other program entities declared in the source code.5. Code GenerationCode generation is the process of translating the source code into executable machine code or an intermediate representation. The target of code generation depends on the intended execution environment. It could be machine code for a particular processor, bytecode for a virtual machine, or an intermediate representation like LLVM IR.6. OptimizationOptimization is an important part of the compilation process. It aims to improve the performance of the generated code by applying various optimization techniques. The common types of optimizations include constant folding, loop optimization, register allocation, and code motion. These optimizations are performed on the intermediate representation or the generated machine code.7. ConclusionCompiler principles are essential for understanding how programming languages are translated into machine code. This document has provided an overview of the key concepts and stages of the compilation process. By understanding these principles, developers can write efficient and high-quality code. The field of compiler theory continues to advance, with new techniques and optimizations being developed to improve the performance of compilers.。
计算机英语考试题及答案

计算机英语考试题及答案一、选择题(每题2分,共20分)1. Which of the following is not a type of computer hardware?A. CPUB. RAMC. SoftwareD. Hard Disk答案:C2. What does the acronym "USB" stand for?A. Universal Serial BusB. User System BusC. User Storage BusD. Universal Storage Bus答案:A3. What is the primary function of a router in a computer network?A. To store dataB. To process dataC. To connect multiple devicesD. To print documents答案:C4. Which of the following is a programming language?A. HTMLB. CSSC. JavaScriptD. All of the above答案:D5. What does "RAM" stand for in computer terminology?A. Random Access MethodB. Random Access MemoryC. Remote Access MemoryD. Rapid Access Memory答案:B6. What is the term for a collection of data stored on a computer?A. FileB. FolderC. DatabaseD. Memory答案:A7. Which of the following is a type of computer virus?A. WormB. TrojanC. Both A and BD. None of the above答案:C8. What is the purpose of a firewall in a computer system?A. To prevent unauthorized accessB. To speed up internet connectionsC. To store dataD. To print documents答案:A9. What does "GUI" stand for in the context of computer systems?A. Graphical User InterfaceB. General User InterfaceC. Global User InterfaceD. Graphical Universal Interface答案:A10. What is the term for a small computer program that performs a specific task?A. ApplicationB. SoftwareC. UtilityD. Script答案:D二、填空题(每题2分,共20分)1. The basic unit of data in a computer is called a____________.答案:bit2. A computer's operating system is an example of______________.答案:system software3. The process of converting data into a form that can be understood by a computer is called ______________.答案:encoding4. The term used to describe the speed of a computer's processor is ______________.答案:clock speed5. A computer network that spans a large geographical area is known as a ______________.答案:WAN (Wide Area Network)6. The process of recovering lost data is called______________.答案:data recovery7. A computer program that is designed to disrupt or damage a computer system is known as a ______________.答案:malware8. The primary storage medium for a computer's operating system and most frequently used programs is the______________.答案:hard drive9. The term used to describe the process of transferring data from one computer to another is ______________.答案:data transfer10. A computer that is part of a network and shares its resources with other computers is called a ______________.答案:server三、简答题(每题10分,共40分)1. What are the main components of a computer system?答案:The main components of a computer system include the central processing unit (CPU), memory (RAM), storage devices (hard disk, solid-state drive, etc.), input devices (keyboard, mouse, etc.), output devices (monitor, printer, etc.), andthe operating system.2. Explain the difference between hardware and software in a computer system.答案:Hardware refers to the physical components of a computer, such as the CPU, memory, and storage devices. Software, on the other hand, comprises the programs and instructions that run on the hardware, including theoperating system, applications, and utilities.3. What is the role of a firewall in a computer network?答案:A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks,such as the Internet, to prevent unauthorized access and protect the internal network from potential threats.4. Describe the process of data encryption and its importance in computer security.答案:Data encryption is the process of converting readable data into an unreadable format, called ciphertext, using an algorithm and a key. This process ensures that only authorized parties with the correct key can access and decrypt the data. Encryption is crucial for protecting sensitive information from unauthorized access, ensuring data privacy and security in computer systems and networks.。
编译原理英文

Compilation PrinciplesPlease note: This document aims to introduce the core concepts of compilation principles in a simplified manner.IntroductionCompilation principles form the foundation of modern computing. It is a field that deals with the transformation of source code into executable programs. A compiler, which is a software tool, plays a crucial role in this process. In this document, we will explore the key components and stages involved in the compilation process.Lexical AnalysisLexical analysis, also known as scanning, is the initial stage of the compilation process. It deals with the analysis of individual characters or lexical units and divides the source code into meaningful tokens. Tokens can be identifiers, keywords, constants, or operators. The lexer, a component of the compiler, is responsible for this task.For example, in the source code int x = 5;, the lexer will identify the tokens as int, x, =, and 5.Syntax AnalysisSyntax analysis, also known as parsing, follows the lexical analysis stage. This stage checks whether the arrangement of tokens adheres to the rules of the programming language’s grammar. It involves the generation o f a parse tree or an abstract syntax tree (AST) that represents the structure of the program.The parser, another component of the compiler, ensures that the source code contains the correct syntax and detects any grammar errors.For example, the parser will verify that the expression x = y + z adheres to the grammar rule for assignment statements.Semantic AnalysisSemantic analysis, a crucial stage in the compilation process, focuses on the meaning associated with the source code. It verifies rules that cannot be checked by syntax analysis alone. The semantic analyzer examines the type compatibility, variable declarations, function calls, and scoping rules within the source code.For instance, the semantic analyzer will identify if a variable is being used without prior declaration or if an integer is assigned to a string variable.Intermediate Code GenerationIntermediate code generation involves the transformation of the parsed source code into an intermediate representation. This representation is usually closer to the target machine language code and allows for easier optimization and translation into executable code.The intermediate code acts as a bridge between the source code and the target code. It simplifies the complexity of translating code for different architectures, making it easier to develop compilers for various platforms.Code OptimizationCode optimization aims to improve the efficiency of the generated target code. This stage involves analyzing and transforming the intermediate code to produce more efficient code while retaining the same functionality.Various optimization techniques, such as constant folding, loop optimization, and register allocation, can be applied to reduce execution time or improve memory usage.Code GenerationCode generation involves the translation of the optimized intermediate code into the target machine language. The target machine language can be assembly language or directly executable binary code.The code generator performs the mapping of intermediate code instructions to the target machine’s specific instructions. It ensures that the instructions are generated in the correct sequence and employ appropriate memory allocation strategies.ConclusionIn conclusion, compilation principles form the backbone of modern programming. Understanding the various stages involved in the compilation process enables programmers to write efficient and optimized code. While this document provides an overview of the key components, each stage can be explored in much greater detail. Happy coding!。
classNode(学习资料)

Inner ClassesMark Allen WeissCopyright 20009/26/001Outlineq History of inner classesq Nested (static inner) classesq The instance inner class and iterator patternq Inner classes inside of functionsq Anonymous inner classesTuesday, September 26, 2000Copyright 2000, M. A. Weiss2Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 3History LessonqJava design removes fringe C++ features q C++ has nested classes to hide types:class List{...private:class Node{public:int data;Node *next;Node( int d = 0, Node *n = NULL ): data( d ), next( n ) { }};};Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 4Java 1.0qNo nested classes in Java 1.0q C++ nesting style achieved with packages –Can make Node class package privateq Speculation was that nested classes would needlessly complicate languageTuesday, September 26, 2000Copyright 2000, M. A. Weiss 5Java 1.1qIn Java 1.1, nested classes were added qNeeded especially to implement patterns associated with AWT event handling qAlso useful for several other patterns q Designers went crazy and added lots of features Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 6What’s AddedqNested classes (static inner classes), mimic C++style of nesting a type inside of type qInner classes (new in Java), allows classes inside of classes and implies an association of objects of the inner class with an object of the outer class qClasses inside of functions qClasses inside of expressions q Classes with no namesTuesday, September 26, 2000Copyright 2000, M. A. Weiss 7Language Changes Required q Added lots of syntax for inner classes –lots of syntax rules for corner cases and silly code q In addition to direct inner class syntax, added some new syntax as a result–final local variables–final parameters–instance initializersq Java 1.1 compiler generates code for inner classes that can be run on a Java 1.0 VMTuesday, September 26, 2000Copyright 2000, M. A. Weiss 8TerminologyqUse terms outer and inner class to refer to the two classes qNested classes are (static) inner classes q Can have classes inside of classes inside of classes if we wantVisibility Rulesq Inner classes are members of the outer class –can be declared with any visibility–can see all members of the outer class–is in same package as outer class: implies that outerclass can access non-private inner class members–class name isq Inner (from outer class)q Outer.Inner (if visible, from rest of world)q Typical pattern:–declare inner class private–declare inner class members public or packagevisibleTuesday, September 26, 2000Copyright 2000, M. A. Weiss9Linked Listq Hide the Node class inside of MyList class public class MyList{private Node front = null;...private static class Node{Object data;Node next;Node( Object d, Node n ){ data = d; next = n; }}}Tuesday, September 26, 2000Copyright 2000, M. A. Weiss10Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 11Public Nested Classq Occasionally nested class is public –Done just for convenience–Example is java.io.ObjectInputStream.GetField qConvention of lower case for package and upper case for classes makes it easy to see what class and package are q If nested class has public constructor, can create withOuter.Inner in = new Outer.Inner( ... );–Often created via factory method instead Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 12Access of Outer Class Members q Static inner class objects can–access static members of the outer class –access instance members of the outer class only through a reference to the outer class–rules similar to what static methods can access q If inner and outer class have name clash –closest class name wins–access outer member explicitly with Outer.member or Inner.memberTuesday, September 26, 2000Copyright 2000, M. A. Weiss 13Instance Inner Class Motivation q Consider container/iterator interaction package pack;public class MyContainer{Object[] items;public Iterator iterator( ){ return new MyContainerIterator( this ); }...}class MyContainerIterator implements Iterator{private int current = 0;private MyContainer container;public MyContainerIterator( MyContainer c ){ container = c; }public boolean hasNext( ){ return current < container.items.length; }...}Tuesday, September 26, 2000Copyright 2000, M. A. Weiss14Using The Container/Iterator import pack.MyContainer;public class Demo {public static void main( String[] args ) {MyContainer c = new MyContainer( );... // populate c via addsIterator itr1 = c.iterator( );Iterator itr2 = c.iterator( );while( itr1.hasNext( ) )System.out.println( itr1.next( ) );}}c itr1container =current = 3items: 13, 76, 12itr2container =current = 0Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 15Observationsqitems array in MyContainer is not private qMyContainerIterator is really part of MyContainer qMyContainerIterator is package visible;private would be better; only use interface qFollowing the container reference in MyContainerIterator is a little sloppy q Every instance of MyContainerIterator is associated with exactly one MyContainer Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 16Revised With Inner Classes package pack;public class MyContainer{private Object[] items;public Iterator iterator( ){ return new MyContainerIterator( ); }...private class MyContainerIterator implements Iterator {private int current = 0;public MyContainerIterator( ){ }public boolean hasNext( ){ return current < items.length; }...}}Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 17Benefitsqitems array is now private qMyContainerIterator is now private qCode is cleaner because container reference has mysteriously vanished and it appears we can access outer class members directly q But what happened to that reference?Tuesday, September 26, 2000Copyright 2000, M. A. Weiss18Implicit Outer Referenceq Instance inner class objects always have an implicit reference to the outer class object that caused its creation–Name is Outer.this–Can be omitted if no conflict with inner namec itr1MyContainer.this =current = 3items: 13, 76, 12itr2MyContainer.this =current = 0Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 19Consequences of Implicit Outer Ref qGarbage collector will not reclaim an outer object if an inner object is around q If an inner instance class is public enough, the following would not work:MyContainer.MyContainerIterator obj = new MyContainer.MyContainerIterator();–even though constructor appears to exist –no way to initialize outer reference in this code q Cannot create inner instance class from static outer class method:// Cannot do this inside static method of MyContainer MyContainerIterator obj = new MyContainerIterator();Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 20Inner Classes Complicate Things q Previous slide illustrates problem –Need syntax to create inner class from outside outer class–Have to be able to propagate a reference to some outer object–Code is stupidqCase 1: inner class should have been private and this wouldn’t be an issue q Case 2: use an instance method–But language designers need a rule for all casesTuesday, September 26, 2000Copyright 2000, M. A. Weiss 21The Ugly Solutionsq Outer reference invokes new as if it were a method:MyCollection c = new MyCollection( );...MyCollection.MyCollectionIterator = c.new MyCollectionIterator( );q Similar nonsense for extending an inner instance class:class Stupid extends Inner.Outer // Inner.Outer is instance inner class {public Stupid( Outer obj ){obj.super( );...}}Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 22Inner Classes With Factory Classes q If factory objects can never be created, inner classes and methods must of course be static:public interface Foo { ... }public class FooFactory{private static FooImpl { ... }private static FooProxy { ... }public static Foo allocateFoo( ){ return new FooProxy( new FooImpl( ) ); } private FooFactory( ) { } // No FooFactory objects }Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 23Inner ClassesqCan be static (of course)qCan be final (not legal to extend)qCan be abstract qCan be interfaces q Can define static final fields but no other statics Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 24Interfaces and Inner Classes qSame Outer.Inner used qInner interfaces of a class are legal qInner interfaces are always implicitly static qInner classes of an interface are legal q Inner classes of an interface are always implicitly staticTuesday, September 26, 2000Copyright 2000, M. A. Weiss 25Inner Class Filesq Compiler:–generates a unique class file for each inner class.–Generally uses Outer$Inner.class as the class file –Internally generates a hidden implicit reference to outer class–Generates package private wrappers to access each accessed private member of the outer class qnames such as access$001 (convention changed in Java 1.3)qcan invoke with reflection q VM can verify that method only invoked from outer class,but doesn’t right nowTuesday, September 26, 2000Copyright 2000, M. A. Weiss 26Classes Inside of MethodsqCan declare classes inside of methods q Cannot use static–class is static if method is static–class is instance if method is instanceq Cannot use private–meaningless; class is not visible outside of the functionq Can also access the parameters of the enclosing method and local variables that are in scope –variables must be finalTuesday, September 26, 2000Copyright 2000, M. A. Weiss 27Final Local VariablesqAdded in Java 1.1qValue cannot change (for references, only value of reference can’t change; object state can)qCan only be initialized once (parameters already are); compiler does usual flow analysis q Final variables (primitives and references) not reclaimed by GC until all anonymous inner objects in the method are reclaimed.–Implies that these variables are not on the stack –So not all local variables are on the stackTuesday, September 26, 2000Copyright 2000, M. A. Weiss 28Anonymous Inner ClassesqCan create a class with no name qClass implements an interface or extends an existing class qBrutal syntax q Useful for implementing short function objectsOriginal Example From InterfacesModule With Function Objectclass OrderRectByWidth implements Comparator {public int compare( Object obj1, Object obj2 ) {Rectangle r1 = (Rectangle) obj1;Rectangle r2 = (Rectangle) obj2;return( r1.getWidth() - r2.getWidth() );}}class Demo {public static void main( String [] args ) {Object [ ] rects = new Rectangle[ ] { ... };Object max = findMax( rects, new OrderRectByWidth( ) ) );Rectangle widest = (Rectangle) max;...}}Tuesday, September 26, 2000Copyright 2000, M. A. Weiss29With Static Inner Classclass Demo {private static class OrderRectByWidth implements Comparator { public int compare( Object obj1, Object obj2 ) {Rectangle r1 = (Rectangle) obj1;Rectangle r2 = (Rectangle) obj2;return( r1.getWidth() - r2.getWidth() );}}public static void main( String [] args ) {Object [ ] rects = new Rectangle[ ] { ... };Object max = findMax( rects, new OrderRectByWidth( ) ) );Rectangle widest = (Rectangle) max;...}}Tuesday, September 26, 2000Copyright 2000, M. A. Weiss30With Class Inside Of Methodclass Demo {public static void main( String [] args ) {Object [ ] rects = new Rectangle[ ] { ... };class OrderRectByWidth implements Comparator {public int compare( Object obj1, Object obj2 ) {Rectangle r1 = (Rectangle) obj1;Rectangle r2 = (Rectangle) obj2;return( r1.getWidth() - r2.getWidth() );}}Object max = findMax( rects, new OrderRectByWidth( ) ) ); Rectangle widest = (Rectangle) max;...}}Tuesday, September 26, 2000Copyright 2000, M. A. Weiss31With Anonymous Inner Classclass Demo {public static void main( String [] args ) {Object [ ] rects = new Rectangle[ ] { ... };Object max = findMax( rects, new Comparator( ) {public int compare( Object obj1, Object obj2 ) {Rectangle r1 = (Rectangle) obj1;Rectangle r2 = (Rectangle) obj2;return( r1.getWidth() - r2.getWidth() );}}) );Rectangle widest = (Rectangle) max;...}}Tuesday, September 26, 2000Copyright 2000, M. A. Weiss32Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 33Anonymous Inner Class Hints q Classic signature will have lots of parentheses,semicolons, braces at the end–very hard to typeqWrite the class outside first.qAfter the () after the call to new , add some blank lines qReplace new Implementation with new Interface q Cut and paste the class declaration after the ()that follow the call to new , and indent a littleTuesday, September 26, 2000Copyright 2000, M. A. Weiss 34Anonymous Class DesignqUseful for class that adds one short function qAdding lots of stuff defeats readability q Useful for accessing local variables that would be impossible without inner classesTuesday, September 26, 2000Copyright 2000, M. A. Weiss 35Anonymous Class NamesqCompiler uses Outer$1.class, Outer$2.class qInner class declared in method gets Outer$1$Inner.class q Can access inner classes -- even anonymous ones with reflection and Class.forName qHowever, hard to know how compiler has numbered classes Tuesday, September 26, 2000Copyright 2000, M. A. Weiss 36Anonymous Class Initialization q QUESTION: If an anonymous class is a class,how do you write its constructor?–Constructor has same name as the class q ANSWER: You can’t. So the language designers invented the initializer block –modeled to look like a static initializer block –almost never worth using, but more language complications–implies that you can only call a constructor defined in class that anonymous class extends or zero-parameter constructor if implementing an interfaceTuesday, September 26, 2000Copyright 2000, M. A. Weiss 37Inner Class Patterns qStatic inner class is private with public/package data qInner class is private (possibly static), with public/package data and implements a public interface. Outer class has factory method that returns inner class instances using the interface type qBoth patterns used in linked lists and other data structures q Other pattern is to use anonymous inner classes for function objectsTuesday, September 26, 2000Copyright 2000, M. A. Weiss 38Class Relationships q Nested (static inner) relates TYPES –inner class type related to outer class type q (Instance) Inner relates OBJECTS –Objects of the inner class type always associated with exactly one object of the outer typeSummaryq The speculation was correct: adding inner classes complicates the languageq Static inner classes (nested classes) just likeC++ nested classesq Instance inner class objects always have reference to outer objectq Inner classes generally private, so syntax okq Classes inside of functions can access final local variables and can even have no nameq Use anonymous classes judiciouslyTuesday, September 26, 2000Copyright 2000, M. A. Weiss39。
计算机专业英语第二版课后翻译答案

Unite 1Section A: 1、artificial intelligence 人工智能2、paper-tape reader 纸带阅读器3、Optical computer 光学计算机4、Neural network 神经网络5、Instruction set 指令集6、Parallel processing 并行处理器7、Difference engine差分机8、Versatile logical element 多用途逻辑元件9、Silicon substrate 硅衬底10、Vaccum tube 真空管11、数据的存储与管理the storage and management of data12、超大规模集成电路large-scale integrated circuit13、中央处理器central processing unit14、个人计算机personal computer15、模拟计算机analog computer16、数字计算机digital computer17、通用计算机general purpose computer18、处理器芯片processor chip19、操作指令operating instructions20、输入设备input devicesSection B1、artificial neural network 人工智能神经网络2、Computer architecture 计算机体系结构3、Robust computer program 健壮的计算机程序4、Human-computer interface 人机接口5、Knowledge representation 知识代表6、数值分析numerical analysis7、程序设计环境programming environment8、数据结构data structure9、存储和检索信息store and retrieve information10、虚拟现实virtual realityUnit 2Section A:1、function key 功能键2、V oice recognition module 声音识别调制器3、Touch-sensitive region 触敏扫描仪4、Address bus 地址总线5、Flatbed scanner 平板扫描仪6、Dot-matrix printer 矩阵式打印机7、Parallel connection 并行连接8、Cathode ray tube 阴极射线管9、Video game 电子游戏10、Audio signal 音频信号11、操作系统operating system12、液晶显示liquid crystal display13、喷墨打印机inkjet printer14、数据总线data bus15、串行连接serial connection16、易失性存储器volatile memory17、激光打印机laser printer18、磁盘存储器floppy disc19、基本输入输出系统basic input/output system20、视频显示器video displaySection B:1、interrupt handler 中断处理程序2、Virtual memory 虚拟内存3、Context switch 上下文转换4、Main memory 主存5、Bit pattern 位模式6、外围设备peripheral device7、进程表process table8、时间片time slice9、图形用户界面graphics user interface10、海量存储器mass storageUnit 3Section A:1、storage register 存储寄存器2、Function statement 函数语句3、Program statement 程序语句4、Object-oriented language 面向对象语言5、Assembly language 汇编语言6、Intermediate language 中间语言7、Relational language 关系语言8、Artificial language 人工语言9、Data declaration 数据声明10、SQL 结构化查询语言11、可执行程序executable program12、程序模块program module13、条件语句conditional statement14、赋值语句assignment statement15、逻辑语言logic statement16、机器语言machine language17、函数式语言functional language18、程序设计语言programming language19、运行计算机程序run a omputer program20、计算机程序员computer programmerSection B1、native code 本机代码2、Header file 头文件3、Multithreaded program 多线程程序4、Java-enabled browser 支持Java的浏览器5、Mallicious code6、机器码machine code7、汇编码assembly code8、特洛伊木马程序trojan9、软件包software package10、类层次class hierarchyUnit 4Section A1、inference engine 推理机2、System call 系统调用3、Compiled language 编译执行的语言4、Parellel computing 并行计算5、Pattern matching 模式匹配6、Memory location 存储单元7、Interpreter program 解释程序8、Library routine 库程序9、Intermediate program 中间程序10、Source file 源文件11、解释执行的语言interpreted language12、设备驱动程序device driver13、源程序source program14、调试程序debugger15、目标代码object code16、应用程序application program17、实用程序utility program18、逻辑程序logic program19、黑盒ink cartridge20、程序的存储与执行storage and execution of program Section B1、Messaging model 通信模式2、Common language runtime 通用语言运行时刻(环境)3、Hierarchical namespace 分层的名称空间4、Development community 开发社区5、CORBA 公共对象请求代理体系结构6、基本组件basic components7、元数据标记metadata token8、虚拟机VM virtual machine9、集成开发环境IDE(intergrated development environment)10、简单对象访问协议SOAP(simple object access protocol) Unit 5Section A1、system specification 系统规范2、Unit testing 单元测试3、Software life cycle 软件的生命周期4、System validation process 系统验证过程5、Evolutionary development process 进化发展过程6、Simple linear model 简单线性模型7、Program unit 程序单元8、Throwaway prototype 一次性使用原型9、Text formatting 文本格式10、System evolution 系统演变11、系统设计范例paradigm for system design12、需求分析与定义Requirements analysis and definition13、探索式编程方法exploratory programming approach14、系统文件编制system documentation15、瀑布模型waterfall model16、系统集成system integration17、商用现成软件commercial off-the-shelf software18、基于组件的软件工程component-based software engineering19、软件维护工具software maintenance tool20、软件复用software reuseSection B1、check box 复选框2、Structured design 结构化设计3、Building block 构建模块4、Database schema 数据库模式5、Radio button 单选按钮6、系统建模技术system modeling techniques7、模型驱动开发MDD(model-driven development)8、数据流程图data flow diagram9、下拉式菜单drop-down10、滚动条scroll barUnit 6Section A1、end user 终端用户2、Atomic operation 原子操作3、Database administrator 数据库管理员4、Relational database model 关系数据库模型5、Local data 本地数据6、Object-oriented database 面向对象的数据库7、Database management system 数据库管理系统8、Entity-relationship model 实体关系模型9、Distributed database 分布式数据库10、Flat file 展开文件11、二维表two-dimensional table12、数据属性data attributes13、数据库对象database object14、存储设备storage device15、数据类型data type16、数据插入与删除insertion and deletion17、层次数据库模型hierarchical18、数据库体系结构database architecture19、关系数据库管理系统ralational database management system20、全局控制总线global control busSection B1、nonvolatile storage system 易失性存储系统2、Equitment malfunction 设备故障3、Wound-wait protocol 损伤等待协议4、Exclusive lock 排它锁5、Database integrity 数据库完整性6、共享锁shared lock7、数据库实现database implementation8、级联回滚cascading rollback9、数据项data item10、分时操作系统time sharing operating system ;Unit 7Section A1、microwave radio 微波无线电2、digital television 数字电视3、DSL 数字用户线路4、analog transmission 模拟传输5、on-screen pointer 屏幕上的指针6、computer terminal 计算机终端7、radio telephone 无线电话8、cellular telephone 蜂窝电话,移动电话,手机9、decentralized network 分散型网络10、wire-based internal network 基于导线的内部网络,有线内部网11、光缆fiber-optic cable12、传真机fax machine13、线通信wireless communications14、点对点通信point-to-point communications15、调制电脉冲modulated electrical impulse16、通信卫星communication(s) satellite17、电报电键telegraph key18、传输媒体transmission medium (或media)19、无绳电话cordless telephone20、金属导体metal conductorSection B1、bit map 位图2、parallel port 并行端口3、direct memory access (DMA) 直接存储器存取4、universal serial bus 通用串行总线5、general-purpose register 通用寄存器6、电路板circuit board7、串行通信serial communication8、数码照相机digital camera9、存储映射输入/输出memory-mapped I/O10、有线电视cable televisionUnit 8Section A1、file server 文件服务器2、carrier sense 载波检测3、Protocol suite 协议族4、Peer-to-peer model 点对点模型5、bus topology network 总线拓扑网络6、inter-machine cooperation 计算机间合作7、Ethernet protocol collection 以太网协作集8、Proprietary network 专有网络9、utility package 实用软件包10、star network 星形网络11、局域网local area network (LAN)12、令牌环token ring13、无线网络wireless network14、封闭式网络closed network15、环形拓扑网络ring topology16、客户/服务机模型client/server model17、网络应用程序network application18、进程间通信interprocess communication19、打印服务机printer server20、广域网wide area networkSection B1、routing path 路由选择通路2、dual-ring topology 双环形拓扑结构3、extended star topology 扩展星形拓扑结构4、backbone network 基干网,骨干网5、mesh topology网络拓扑结构6、同轴电缆coaxial cable7、逻辑拓扑结构logical topology8、无冲突连网环境collision-free networking environment9、树形拓扑结构tree topology10、目的地节点destination nodeUnit 9Section A1、cell phone 蜂窝电话,移动电话,手机2、IP address 网际协议地址,IP地址3、autonomous system 自主系统4、dial-up connection 拨号连接5、network identifier 网络标识符6、binary notation 二进制记数法7、mnemonic name 助记名,缩写名8、Internet-wide directory system 因特网范围的目录系统9、name server 名称服务器10、Internet infrastructure 因特网基础结构11、助记地址mnemonic address12、网吧cyber cafe13、宽带因特网访问broadband Internet access14、顶级域名top-level domain (TLD)15、因特网编址Internet addressing16、点分十进制记数法dotted decimal notation17、因特网服务提供商Internet service provider (ISP)18、专用因特网连接dedicated Internet connection19、主机地址host address20、硬件与软件支持hardware and software support Section B1、incoming message 来报,到来的报文2、application layer 应用层3、utility software 实用软件4、sequence number (顺)序号,序列号5、remote login capabilities 远程登录能力6、端口号port number7、软件例程software routine8、传输层transport layer9、文件传送协议FTP(File Transfer Protocol)10、万维网浏览器Web browserUnit 10Section A1、mailing list 邮件发送清单,邮件列表2、proprietary software 专有软件3、cc line 抄送行4、bcc line 密送行5、forwarded e-mail messages 转发的电子邮件6、e-mail convention 电子邮件常规7、click on an icon 点击图标8、confidential document 密件,秘密文件9、classified information 密级信息10、recovered e-mail message 恢复的电子邮件11、常用情感符commonly used emoticon12、已删除电子邮件deleted e-mail13、电子系统electronic system14、附件行Attachments line15、版权法copyright law16、电子邮件网规e-mail netiquette17、信息高速公路information superhighway18、签名文件signature file19、电子数据表程序spreadsheet program20、文字处理软件word processorSection B1、web-authoring software 网络写作软件2、template generator 模版生成程序3、navigation page 导航页面4、corporate logo 公司标识5、splash page 醒目页面,过渡页6、导航条navigation bar7、节点页面node page8、网站地图site map9、可用性测试usability testing10、图形交换格式gif(Graphics Interchange Format)Unit 11Section A1、customized marketing strategy 定制的营销策略2、B2G transaction 企业对政府交易3、mobile telephone 移动电话4、dot-com bust 网络不景气5、smart card 智能卡,灵巧卡6、digital piracy 数字盗版7、dot-com boom 网络繁荣8、C2C transaction 消费者对消费者交易9、Web auction site 拍卖网站10、fingerprint reader 指纹读取器11、射频识别装置radio-frequency identification (RFID) device12、电子数据交换electronic data interchange (EDI)13、库存管理技术inventory management technology14、知识产权intellectual property15、条形码bar code16、货币兑换currency conversion17、电子图书electronic book18、视网膜扫描仪retina scanner19、个人数字助理personal digital assistant (PDA)20、企业对企业电子商务B2B electronic commerceSection B1、software suite 软件套件2、text box 文本框3、virtual checkout counter 虚拟付款台4、static catalog 静态目录5、browser session 浏览器会话期6、动态目录dynamic catalog7、购物车软件shopping cart software8、供应链supply chain9、企业资源计划软件enterprise resource planning (ERP) software10、税率tax rateUnit 12Section A1、encryption program 加密程序2、deletion command 删除命令3、authorized user 授权的用户4、backup copy 备份5、voltage surge 电压浪涌6、circuit breaker 断路器7、electronic component 电子元件(或部件)8、data-entry error 数据输入错误9、electronic break-in 电子入侵10、power line 电力线,输电线11、检测程序detection program12、电源power source13、破坏性计算机程序destructive computer program14、计算机病毒computer virus15、软件侵权software piracy16、硬盘驱动器hard-disk drive17、病毒检查程序virus checker18、主存储器primary storage19、电子公告板electronic bulletin board20、浪涌电压保护器surge protectorSection B1、phishing attack 网络钓鱼攻击2、graphics card 显(示)卡3、heuristic analysis 试探性分析4、infected file 被感染文件5、virus dictionary 病毒字典6、数据捕获data capture7、恶意软件malicious software8、病毒特征代码virus signature9、防病毒软件antivirus software10、内存驻留程序memory-resident program。
10 yesInner classes3

Inner classes
• • • • • • • •
Creating inner classes Link to the outer class Using .this and .new Inner classes and upcasting Inner classes in methods and scopes Anonymous inner classes Nested classes Classes inside interfaces
class MNA { private void f() {} class A { private void g() {} public class B { void h() { g(); //A.this.g() f(); //MNA.this.f(); }}}}
Multiply nested class
See example DotNew
Inner classes and upcasting
Come into inner class by starting upcasting to a base class, and in particular to an interface.(Example TestParcel)
public static Destination destination(String s) { return new ParcelDestination(s); } public static Contents contents() { return new ParcelContents(); } public static void main(String[] args) { Contents c = contents(); Destination d = destination("Tasmania"); } } ///:~
科技英语翻译的基本技巧

Part of speech conversion
Common problems in translating scientific English
03
Summary: In scientific English translation, semantic comprehension errors are one of the most common problems.
要点一
要点二
Long senses
In contrast to general English, Technology English often uses long and complex senses to describe complex technical processes and concepts in detail
Example: In the field of computer science, the term "algorithm" is often translated as "algorithm", but in some contexts, it may be more accurately translated as "computational process" or "computational method".
New words
With the rapid development of technology, new words are consistently emerging in Technology English to describe new concepts and products, such as "artistic intelligence" and "virtual reality."
编译原理 英文

编译原理英文Compiler Principle。
Compiler principle is a fundamental subject in thefield of computer science. It plays a crucial role in the development of programming languages and the translation of high-level languages into machine code. In this document,we will explore the key concepts and principles of compiler design, as well as its significance in the realm of computer science.First and foremost, it is essential to understand the purpose of a compiler. A compiler is a software tool that translates the source code of a program written in a high-level language into an equivalent machine code. Thisprocess involves several stages, including lexical analysis, syntax analysis, semantic analysis, code generation, and code optimization. Each stage plays a vital role inensuring the correctness and efficiency of the compiled code.The lexical analysis stage involves scanning the source code to identify and tokenize the individual components, such as keywords, identifiers, operators, and constants. This stage is crucial for breaking down the source codeinto its basic elements, which are then used in the subsequent stages of the compilation process.Following the lexical analysis, the syntax analysis stage checks the syntactic structure of the source code to ensure that it conforms to the grammar of the programming language. This stage utilizes parsing techniques, such as LL(1) and LR(1) parsing, to construct the parse tree of the source code. The parse tree represents the hierarchical structure of the program and serves as the basis for the subsequent semantic analysis.Semantic analysis is the stage where the meaning of the source code is analyzed in the context of the programming language. This involves type checking, scope resolution, and other semantic checks to ensure the correctness of the program. Any semantic errors are reported at this stage,and the compiler may also perform certain optimizations based on the semantic information gathered.Once the semantic analysis is complete, the compiler proceeds to the code generation stage, where the intermediate representation of the source code istranslated into the target machine code. This stage involves mapping the high-level language constructs to the corresponding machine instructions, as well as managing the memory layout and addressing modes.Finally, the code optimization stage aims to improve the efficiency of the generated code by applying various optimization techniques, such as constant folding, loop optimization, and register allocation. These optimizations help enhance the performance of the compiled code and reduce the overall execution time.In conclusion, the principles of compiler design are essential for the development of efficient and reliable software systems. By understanding the various stages of compilation and the associated principles, programmers cangain insights into the inner workings of programming languages and the translation process. As technology continues to advance, the principles of compiler design will remain a cornerstone of computer science, driving innovation and progress in the field of software development.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Public interface Moveable
{ void move(double x, double y); }
public interface Powered extends Moveable
{ double milesPerGallon(); }
10
Although you cannot put instance fields or static methods in an interface, you can supply constants in them.
if (salary < other.salary) return -1; if (salary > other.salary) return 1; return 0;
}
…
}
When implementing the interface, you must declare the method as public. Otherwise, the compiler assumes that the method has package visibility—the 6 default for a class.
When making a method call, the compiler needs to be able to check that the method actually exists: sort--compareTo
The existence of the method is assured because Implementing the interface.
13
门和警报:门都有open( )和close( )两个动作;有些门具有报警 alarm( )的功能,那么该如何实现?
14
Object Cloning
15
Object Cloning
copying
Cloning
16
When you make a copy of a variable, the original and the copy are references to the same object.
public interface Comparable<T> { int compareTo(T other); } All methods of an interface are automatically public. For that reason, it is not necessary to supply the keyword public when declaring a method in an interface. All methods of an interface are automatically public. For that reason, it is not necessary to supply the keyword public when declaring a method in an 4 interface.
Some interfaces define just constants and no methods.
11
Interfaces and Abstract Classes
why the designers of the Java programming language bothered with introducing the concept of interfaces. Why can’t Comparable simply be an abstract class:
classname implements interfacename
class Employee implements Comparable { public int compareTo(Object otherObject)
{ Employee other = (Employee) otherObject;
Comparable--- compareTo
8
Properties of Interfaces
Interfaces are not classes. In particular, you can never use the new operator to instantiate an interface:
Supplying instance fields and method implementations is the job of the classes that implement the interface.
You can think of an interface as being similar to an abstract class with no instance fields.
Some interfaces have multiple methods, interfaces can also define constants. What is more important. Interfaces never have instance fields, and the methods are never implemented in the interface.
abstract class Comparable //why not? {
public abstract int compareTo (object other);
} Class Employee extends Comparable
{…
public int compareTo(Object other) { . . . } …}
12
The designers of Java chose not to support multiple inheritance
Class Employee extends Person, Comparable //ERROR.
A class can only extend a single class ,but each class can implement as many interfaces:
5
To make a class implement an interface, you carry out two steps: 1. You declare that your class intends to implement the given interface.
2. You supply definitions for all methods in the interface.
x = new Comparable(…);//ERROR
You can still declare interface variables. An interface variable must refer to an object of a class that implements the interface:
In the Java programming language, an interface is not a class but a set of requirements for the classes that want to conform to the interface.
“If your class conforms to a particular interfaceห้องสมุดไป่ตู้ then I’ll perform the service.”
As of Java SE 5.0, the Comparable interface has been enhanced to be a generic type.
class Employee implements Comparable<Employee>
{
public int compareTo(Employee other) { if (salary < other.salary) return -1; if (salary > other.salary) return 1; return 0; } … }
Object have a method, and the method must take
an parameter and return an integer.
3
As of Java SE 5.0, the Comparable interface has been enhanced to be a generic type.
This allows for multiple chains of interfaces that go from a greater degree of generality to a greater degree of specialization.
Just as you can build hierarchies of classes, you can extend interfaces.
Class Employee extends Person implements Comparable
class Employee implements Cloneable, Comparable
Instead, interfaces afford most of the benefits of multiple inheritance while avoiding the complexities and inefficiencies.
