7506E配置脚本
S7506E三层交换机配置资料讲解

***************************************************************** ************** Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. ** Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ****************************************************************** *************Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meetingsupervlansubvlan 36#vlan 3986description dianxin wireless supervlansubvlan 3901#vlan 3987description huisuo vlan 33 supervlansubvlan 33#vlan 3988description wirelesssupervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250#vlan 3991supervlansubvlan 1200 to 1225#vlan 3992supervlansubvlan 100 to 111#vlan 3993supervlansubvlan 1032 to 1150#vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790#vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#vlan 3999description to UTM200#vlan 4000 to 4001#ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator andif-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan#dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0gateway-list 192.168.36.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3990network 192.168.138.0 mask 255.255.254.0gateway-list 192.168.138.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!!service-type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1#interface NULL0#interface Vlan-interface1ip address 192.168.39.2 255.255.255.0 #interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 ##interface Vlan-interface3986 (分配网关)ip address 192.168.160.1 255.255.224.0local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0#interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0#interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3990ip address 192.168.138.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#local-proxy-arp enable#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3999description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39#interface GigabitEthernet3/0/3 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/4 port access vlan 1227qos apply policy kefang inbound mirroring-group 2 monitor-port #interface GigabitEthernet3/0/5 port access vlan 3901qos apply policy kefang inbound #interface GigabitEthernet3/0/6 port access vlan 8#interface GigabitEthernet3/0/7 port access vlan 3999description to UTM-200_G 0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan 8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10qos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inboundstp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/25port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/26port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundqos apply policy kefang inbound #interface GigabitEthernet3/0/32 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/33 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39#interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet3/0/45 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/46 port access vlan 35qos apply policy kefang inbound #interface GigabitEthernet3/0/47port access vlan 34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253 ip route-static 10.0.18.0 255.255.255.0 192.168.30.253 ip route-static 10.0.24.0 255.255.255.0 192.168.30.253 ip route-static 10.0.25.0 255.255.255.0 192.168.30.253 ip route-static 10.0.29.0 255.255.255.0 192.168.30.253 ip route-static 10.0.97.0 255.255.255.0 192.168.30.253 ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253 ip route-static 10.11.30.0 255.255.255.0 192.168.30.253 ip route-static 10.11.70.0 255.255.255.0 192.168.30.253 ip route-static 10.11.72.0 255.255.255.0 192.168.30.253ip route-static 10.12.41.0 255.255.255.0 192.168.30.253ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2 #snmp-agentsnmp-agent local-engineid 800063A203000FE22EDA1Csnmp-agent community write q-ideasnmp-agent sys-info version allsnmp-agent target-host trap address udp-domain 192.168.34.120 udp-port 5000 params securityname q-idea#dhcp server detect#dhcp enable#user-interface aux 0idle-timeout 0 0user-interface vty 0 4acl 3011 inboundauthentication-mode schemeuser privilege level 3#return<7506E>。
H3C S7506E上配置策略路由
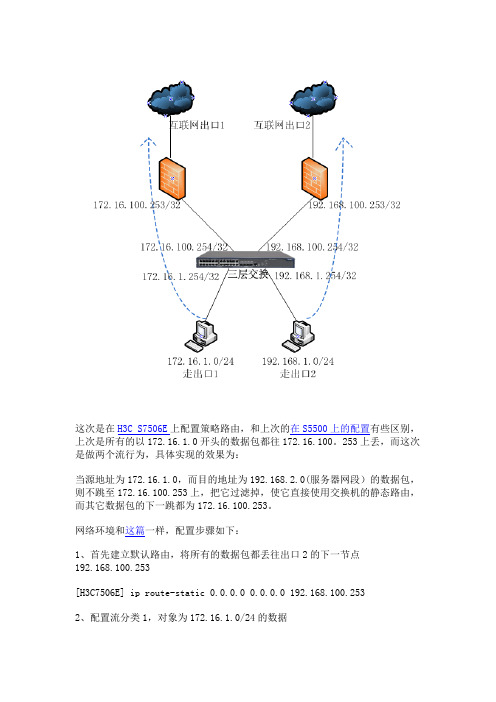
这次是在H3C S7506E上配置策略路由,和上次的在S5500上的配置有些区别,上次是所有的以172.16.1.0开头的数据包都往172.16.100。
253上丢,而这次是做两个流行为,具体实现的效果为:当源地址为172.16.1.0,而目的地址为192.168.2.0(服务器网段)的数据包,则不跳至172.16.100.253上,把它过滤掉,使它直接使用交换机的静态路由,而其它数据包的下一跳都为172.16.100.253。
网络环境和这篇一样,配置步骤如下:1、首先建立默认路由,将所有的数据包都丢往出口2的下一节点192.168.100.253[H3C7506E] ip route-static 0.0.0.0 0.0.0.0 192.168.100.2532、配置流分类1,对象为172.16.1.0/24的数据[H3C7506E]acl number 3001[H3C7506E-acl-adv-3001] rule 0 deny ip source 172.16.1.0 0.0.0.255 dest 192.168.2.0 0.0.0.255[H3C7506E] quit[H3C7506E] traffic classifier 1[H3C7506E-classifier-1] if-match acl 3001[H3C7506E-classifier-1] quit3、配置刚才定义的流分类的行为,定义如果匹配则允许[H3C7506E] traffic behavior 1[H3C7506E-behavior-1] filter permit[H3C7506E-behavior-1] quit4、配置流分类2,对象仍为172.16.1.0、24[H3C7506E]acl number 3002[H3C7506E-acl-adv-3002] rule 0 permit ip source 172.16.1.0 0.0.0.255 [H3C7506E] quit[H3C7506E] traffic classifier 2[H3C7506E-classifier-2] if-match acl 3002[H3C7506E-classifier-2] quit5、配置刚才定义的流分类的行为,定义如果匹配就下一跳至出口1即172.16.100.253[H3C7506E] traffic behavior 2[H3C7506E-behavior-2] redirect next-hop 172.16.100.253[H3C7506E-behavior-2] quit6、将刚才设置的应用至QOS策略中,定义policy 1[H3C7506E] qos policy 1[H3C7506E-qospolicy-2] classifier 1 behavior 1[H3C7506E-qospolicy-2] classifier 2 behavior 2[H3C7506E-qospolicy-2] quit7、在接口上应用定义的QOS策略policy 1[H3C7506E] interface GigabitEthernet 1/0/15[H3C7506E-GigabitEthernet1/0/15] qos apply policy 1 inbound[H3C7506E-GigabitEthernet1/0/15] quit至此,配置已完成。
7506E-S配置

MANUFACTURING_DATE : 2014-01-12
VENDOR_NAME : H3C
Slot 5:
DEVICE_NAME : LSQ1FWBSC0
DEVICE_SERIAL_NUMBER : 210231A832B125000018
MAC_ADDRESS : NONE
Only new chassis support this command.
The operation is not supported on the specified power.
Fan 1:
Only new chassis support this command.
The operation is not supported on the specified fan.
<WX3024>reboot
Start to check configuration with next startup configuration file, please wait.........DONE!
This command will reboot the device. Current configuration will be lost, save current configuration? [Y/N]:n
MANUFACTURING_DATE : 2014-01-11
VENDOR_NAME : H3C
Power 1:
Only new chassis support this command.
The operation is not supported on the specified power.
7506E安全配置指导-ARP攻击防御配置

配置源 MAC 地址固定的 ARP 攻击检测功能
可选 建议在网关设备上配置本功能
防止仿冒用户、 仿冒网关攻击
配置 ARP 主动确认功能
可选 建议在网关设备上配置本功能
配置 ARP Detection 功能
可选 建议在接入设备上配置本功能
详细配置 1.3
1.4 1.5 1.6 1.7
1-1
配置任务 配置 ARP 自动扫描、固化功能
地址进行解析,导致 CPU 负荷过重及网络流量过大。 z 攻击者向设备发送大量 ARP 报文,对设备的 CPU 形成冲击。 关于 ARP 攻击报文的特点以及 ARP 攻击类型的详细介绍,请参见“ARP 攻击防范技术白皮书”。 目前 ARP 攻击和 ARP 病毒已经成为局域网安全的一大威胁,为了避免各种攻击带来的危害,设备 提供了多种技术对攻击进行防范、检测和解决。 下面将详细介绍一下这些技术的原理以及配置。
主机向设备某端口连续发送目标 IP 地址不能解析的 IP 报文,当每 5 秒内由此主机发出 IP 报 文触发的 ARP 请求报文的流量超过设置的阈值,那么对于由此主机发出的 IP 报文,设备不允 许其触发 ARP 请求,直至 5 秒后再处理,从而避免了恶意攻击所造成的危害。 z 如果发送攻击报文的源不固定,可以采用 ARP 黑洞路由功能。开启该功能后,一旦接收到目 标 IP 地址不能解析的 IP 报文,设备立即产生一个黑洞路由,使得设备在一段时间内将去往该 地址的报文直接丢弃。等待黑洞路由老化时间过后,如有报文触发则再次发起解析,如果解 析成功则进行转发,否则仍然产生一个黑洞路由将去往该地址的报文丢弃。这种方式能够有 效地防止 IP 报文的攻击,减轻 CPU 的负担。
i
1 ARP攻击防御配置
S7506E设备参数
要求设备采用业务承载母板与接口子卡分离的设计,提高设备可扩展性
★总插槽数
≥4
★业务插槽数
配置主控引擎冗余后,业务插槽数(大槽)>=2,业务子卡槽位数最大支持8
★交换容量
≥240G
★整机包转发率
≥48Mpps
系统可靠性
支持双主控,主备切换“零丢包”
关键部件冗余
支持主控引Байду номын сангаас、电源等关键部件冗余备份
关键部件冗余支持主控板电源模块冗余可支持业务板卡类型防火墙业务板入侵防御系统板无线控制器业务板负载均衡业务板应用控制网关业务板网络流量分析业务板sslvpn业务业务板异常流量检测业务板异常流量清洗业务板虚拟化特性支持h3cirf2技术或ciscovss技术将多台物理设备虚拟化为一台逻辑设备虚拟组内可以实现一致的转发表项统一的管理跨物理设备的链路聚合支持4台设备的虚拟化支持至少三种以上分裂检测功能支持远距离虚拟化距离可达70km提供相关专利证明文件需提供重庆本地相关应用案例不少于3个
支持基于端口、MAC地址、IP地址、IP优先级、DSCP优先级、TCP/UDP端口号、协议类型等方式的流分类;
支持流量整形和流量监管
MPLS特性
支持L3VPN:支持跨域MPLS VPN(Option1/2/3)、嵌套MPLS VPN、支持分层PE(HoPE)、CE双归属、MCE、多角色主机、GRE隧道等;支持L2VPN:Martini、Kompella、CCC和SVC方式;支持MPLS TE、RSVP TE
★资质认证
提供工信部(原信产部)IPv4、IPv6入网证书,提供IPv4、IPv6检验报告,为了保证设备软件的合法性,必须提供中华人民共和国国家版权局颁发的计算机软件著作权登记证书
H3C核心交换机S7506E网络维护手册

网络设备维护手册第一章交换机操作手册此部分档使用本项目交换机型号如下:S7506E/S5120/S5130/WX3024E设备登陆Console登陆1、通过交换机Console 口进行本地登录是登录交换机的最基本的方式,也是配置通过其他方式登录交换机的基础。
连接示意图如下:2、把电脑和交换机连接好后,交换机上电开机,然后在电脑上进行如下操作,首先点击开始->程序->附件->通讯->超级终端打开后出现下面图示,输入名称,可以任意输入。
输入完成点击确定,出现下面界面,连接时使用选择COM口,一般台式机为COM1或COM2,而笔记本经过转接,可能会产生COM3或COM4,也有可能是其他的,你可以在下面的选择项里看到,选择完成后点击确定。
通过上面的选择,现在到了对端口属性进行设置,一般情况下没有进行过修改,默认只要点击还原为默认值就可以了,然后再单击确定。
之后敲回车即可,会出现H3C>提示符,说明已经与交换机连接,可以进行配置了,如果没有可以重启交换机或检查连接是否正确。
telnet登陆1、新建用户名密码local-user admin /admin为用户名password cipher h3c@123 /h3c@123为密码authorization-attribute level 3 /授权admin用户的等级为3,3为最高级service-type telnet /授权admin用户的登陆方式,可以为ftp、telnet等#telnet server enable /开启telnet服务使用电脑连接至交换机:交换机加电开机显示sarting......************************************************************** ** H3C S5510-24P BOOTROM, Version 142 ** **************************************************************Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd.Creation date: Mar 12 2008, 11:17:30CPU Clock Speed : 200MHzBUS Clock Speed : 33MHzMemory Size : 128MBThe switch Mac is: 000F-E2B1-BD60Press Ctrl-B to enter Boot Menu (10)Auto-booting...Decompress Image.................................................................................................................................................... .............................................................................................................................................................. .............................................................................................................................................................. .............................................................................................................................................................. .............................................................................................................................................................. .........................................................................................................................................................O K!Starting ...****************************************************************************** * Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. ** Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. *******************************************************************************It will take a long time to get configuration file, please wait...Startup configuration file does not exist.User interface aux0 is available.<H3C>%Apr 26 12:03:53:611 2000 H3C SHELL/4/LOGIN: Console login from aux0 <H3C><H3C>sys[H3C][H3C]sysname neiwang[neiwang-luser-admin]pa sin admin fg)safely Save current configuration safely<cr>[neiwang]save s[neiwang]save safely Are you sure [Y/N]:y Please input the file name(*.cfg)[fla](To leave the existing filename unchanged, press the enter key):Validating file. Please wait...Now saving current configuration to the device.Saving configuration fla. Please wait... .................Configuration is saved to flash successfully.[neiwang]qu<neiwang>saveThe current configuration will be written to the device. Are you sure [Y/N]:n <neiwang>sysSystem View: return to User View with Ctrl+Z.[neiwang]DHCP Snooping was enabled.[neiwang-GigabitEthernet1/0/15]qu[neiwang]vlan 26[neiwang-vlan26][neiwang-GigabitEthernet1/0/15]port access vlan 26[neiwang-GigabitEthernet1/0/15]qu[neiwang-GigabitEthernet1/0/25]port trunk permit all ......... Done. <cr>[neiwang-GigabitEthernet1/0/25]undo port link-type ......... Done. [neiwang-GigabitEthernet1/0/25]sp[neiwang-GigabitEthernet1/0/25]speed10 Specify speed of current port 10Mb/s100 Specify speed of current port 100Mb/s1000 Specify speed of current port 1000Mb/sauto Enable port's speed negotiation automatically[neiwang-GigabitEthernet1/0/25]speed au[neiwang-GigabitEthernet1/0/25]speed auto[neiwang-GigabitEthernet1/0/25]du[neiwang-GigabitEthernet1/0/25]duplex au[neiwang-GigabitEthernet1/0/25]duplex auto[neiwang-GigabitEthernet1/0/25]qu[neiwang]dhcp[neiwang]dhcp-snooping<cr>[neiwang]dhcp-snoopingDHCP Snooping has already been enabled.[neiwang]int g 1/0/25[neiwang-GigabitEthernet1/0/25]dhcp[neiwang-GigabitEthernet1/0/25]dhcp-snoopinginformation Specify Option 82 servicetrust Trusted port[neiwang-GigabitEthernet1/0/25]dhcp-snooping tr[neiwang-GigabitEthernet1/0/25]dhcp-snooping trust<cr>[neiwang-GigabitEthernet1/0/25]dhcp-snooping trust[neiwang-GigabitEthernet1/0/25]qu[neiwang]dis valnINTEGER<1-4094> VLAN IDall All the VLANsdynamic Dynamic VLAN IDreserved Reserved VLAN IDstatic Static VLAN ID<cr>[neiwang]dis vlan all [neiwang]dis arp [neiwang]dis arpall Display static&dynamic ARP entrydynamic Display dynamic ARP entryinterface Display by Interfacesource-suppression Display ARP source suppressionstatic Display static ARP entrytimer Display ARP timervlan Display by VLANvpn-instance Display ARP entries by VPN name[neiwang]dis arp allType: S-Static D-DynamicIP Address MAC Address VLAN ID Interface Aging Type [neiwang]dis mac-a[neiwang]dis mac-address [neiwang]#interface Vlan-interface4000 //路由添加管理口vlan//路由添加管理地址IP#interface GigabitEthernet1/0/52 //回程路由#//指定要回跳的路由第二章无线维护手册设备登陆此步骤参考设备登陆设备常用操作注册APwlan ap AP1 model WA2620i-AGN /MODEL的型号一定要和实际一样/手工注册方式序列号一定要正确radio 1 /2620i是双频APservice-template 10 /调用服务模板radio enable /启用射频口radio 2service-template 10radio enable配置SSID名称wlan service-template 10 /新建服务模板10ssid TAXZFWZX /ssid为TAXZFWZXbind WLAN-ESS 10 /绑定无线接口10authentication-method open-system /以下为加密方案cipher-suite tkipsecurity-ie wpaservice-template enable /启用服务模板#interface WLAN-ESS10 /新建无线接口10,供服务模板调用port-security port-mode psk /以下为认证信息port-security tx-key-type 11keyport-security preshared-key pass-phrase si h3c@123。
h3c 7506E升级双引擎的步骤

[转]h3c 7506E升级双引擎的步骤h3c, 7506Eh3c 7506E升级双引擎的步骤升级步骤(由于两个引擎上各有一个flash,每个flash 里面放一个vrp系统文件,虽然主引擎和备引擎会话同步,但是引导的系统文件不能自动同步)0.将vrp系统文件通过cf读卡器拷贝到cf卡里面1.将cf卡插入到cf插槽2.使能cf卡[H3C]cfd enable3.将cf卡里面的vrp系统文件拷贝到flash<H3C>copy cf:/s7500e-cmw520-r6605p01.appflash:/s7500e-cmw520-r6605p01.app4.将主切换到从slave switchover enalbeslave switchover此主引擎切换到从引擎后,会重启但是此时的引导文件还是原来的老文件,因此不会有任何问题5.将consloe线插到从引擎的consloe口,然后对从引擎进行1到3的操作6.设置引导文件从新的s7500e-cmw520-r6605p01.app文件引导<H3C>boot-load file s7500e-cmw520-r6605p01.app slot 1 main<h3c>sa7.将主切换到从,slave switchover enalbeslave switchover此从引擎由主切换到从引擎后,会重启,由于重启后,运行的是新版本8.将consloe线插到主引擎的consloe口9.此时会有报主引擎和从引擎不一样的报错信息,不要紧,这个是正常显示。
#Dec 31 11:32:32:119 2009 H3C DRVDBG/2/TRAP Info:Slave board software version differs from master board . Please download thesame version!#Dec 31 11:32:32:140 2009 H3C DRVDBG/2/TRAP Info:Master's version is V600R006B01D069SP16 !!!#Dec 31 11:32:32:150 2009 H3C DRVDBG/2/TRAP Info:Slave's version is !!!#Dec 31 11:32:32:160 2009 H3C DRVDBG/2/TRAP Info:Reboot slave board for different version!9.设置引导文件从新的s7500e-cmw520-r6605p01.app文件引导<H3C>boot-load file s7500e-cmw520-r6605p01.app slot 0 main<h3c>sa<h3c>reboot10.系统运行正常了,来回切换没有问题了,将每个引擎下的旧文件删除。
S7506E三层交换机配置

****************************************************************************** * Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. * * Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ******************************************************************************* Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan 3901#vlan 3987description huisuo vlan 33supervlansubvlan 33vlan 3988description wireless supervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250 #vlan 3991supervlansubvlan 1200 to 1225 #vlan 3992supervlansubvlan 100 to 111 #vlan 3993supervlansubvlan 1032 to 1150vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790 #vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#vlan 3999description to UTM200#vlan 4000 to 4001ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator and if-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan #dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0 gateway-list 192.168.36.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0 gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0 gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3990network 192.168..0 mask 255.255.254.0gateway-list 192.168..1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!! -type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1#interface NULL0#interface Vlan-interface1ip address 192.168.39.2 255.255.255.0#interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 #interface Vlan-interface3985ip address 192.168.36.254 255.255.255.0 #ip address 192.168.160.1 255.255.224.0 local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0 #interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0 #interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3990ip address 192.168..1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0 local-proxy-arp enableinterface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address 192.168.132.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128 local-proxy-arp enable#description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundport link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundport link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group 1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan 1227qos apply policy kefang inboundmirroring-group 2 monitor-port#interface GigabitEthernet3/0/5port access vlan 3901qos apply policy kefang inbound#interface GigabitEthernet3/0/6port access vlan 8#interface GigabitEthernet3/0/7description to UTM-200_G 0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan 8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2#interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan 2#interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2#interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/24 port access vlan 34stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/25 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/26 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/27 port link-type trunkmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/31port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/32port access vlan 2qos apply policy kefang inbound#port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39qos apply policy kefang inbound #interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/46port access vlan 35qos apply policy kefang inbound#interface GigabitEthernet3/0/47port link-type trunkport trunk permit vlan 1 30qos apply policy kefang inbound#interface GigabitEthernet3/0/48port access vlan 34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/13port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunk#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunk#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253ip route-static 10.0.18.0 255.255.255.0 192.168.30.253ip route-static 10.0.24.0 255.255.255.0 192.168.30.253ip route-static 10.0.25.0 255.255.255.0 192.168.30.253ip route-static 10.0.29.0 255.255.255.0 192.168.30.253ip route-static 10.0.97.0 255.255.255.0 192.168.30.253ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253ip route-static 10.11.30.0 255.255.255.0 192.168.30.253ip route-static 10.11.70.0 255.255.255.0 192.168.30.253ip route-static 10.11.72.0 255.255.255.0 192.168.30.253ip route-static 10.12.41.0 255.255.255.0 192.168.30.253ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2#snmp-agentsnmp-agent local-engineid 800063A203000FE22EDA1Csnmp-agent community write q-ideasnmp-agent sys-info version allsnmp-agent target-host trap address udp-domain 192.168.34.120 udp-port 5000 params securityname q-idea#dhcp server detect#dhcp enable#user-interface aux 0idle-timeout 0 0user-interface vty 0 4acl 3011 inboundauthentication-mode schemeuser privilege level 3#return<7506E>。
H3C_S7506E维护操作手册

H3C_S7506E维护操作手册配置举例:1、配置设备主机名如:sysname H3C_S7506E2、配置Router id如:router id 1.1.1.13、配置vlan 1的描述如:vlan 1description gateway4如:5如:6、配置如:7如8、如:9、开启如:10、配置如:11、配置如:12、配置如:13、配置如:14、配置如:15、开启如:16、配置如:description gateway17、配置interface Vlan-interface1接口的IP地址(局域网网关IP地址)如:ip address 3.3.318、配置环回接口0如:interface LoopBack019、配置环回地址如:ip address 3.3.3.25520、配置VLAN端口如:interface Vlan-interface121、配置VLAN接口的描述如:description Server22、配置VLAN端口IP地址如:ip address 3.3.3.1.023创建备份组并配置虚拟IP地址如:vrrp vrid 1 virtual-ip 3.3.3.324、配置交换机在备份组中的优先级如:vrrp vrid 1 priority 12025、配置备份组中交换机的抢占延迟时间如:vrrp vrid 1 preempt-mode timer delay 6026、配置链路聚合创建interface Bridge-Aggregation1如:interface Bridge-Aggregation136、配置SNMP的读写属性为abc如:snmp-agent community write abc37、配置SNMP代理发送的信息的版本为适应所有版本如:snmp-agent sys-info version all38、开启SNMP陷阱报文如:snmp-agent trap enable39、配置SNMP陷阱报文发往5.5.5.5,且其安全名称为abc如:snmp-agent target-host trap address udp-domain 5.5.5.5 params securityname abc 40、配置SNMP队列长度如:snmp-agent trap queue-size 50041、配置SNMP陷阱报文生存时间如:snmp-agent trap life 60042、配置远程登录接口如:user-interface vty 0 443、配置远程登录使用用户名及密码验证。
SOLO6 BE - TWIN6 BE专业分析式监控系统用户手册说明书

SOLO6 BE - TWIN6 BEProfessional Analog Monitoring SystemUser manualSolo6 Be Twin6 Be10An example of this equipment has been tested and found to comply with the following European directives and international standards:Electromagnetic compatibilityEN 55103EN 61000Electrical safetyEN 60065Important safety informationPlease read carefully the following instructions and safety information. Heed all warnings and follow all instructions.•D o not remove the back panel. There are no user serviceable parts inside; please refer to qualified service personnel. This equipment must be earthed.•P rotect the power cord from being walked on or pinched particularly at plugs, convenience receptacles, and the point where they exit from the apparatus.• Only use attachments/accessories specified by the manufacturer.•S ervicing is required when the unit has been damaged in any way, such as power cord or plug is damaged, liquid has been spilled or objects have fallen into the unit, the unit has been exposed to rain or moisture, does not operate normally, or has been dropped.• Do not place naked flame sources, such as lighted candles, on the apparatus.• Use the apparatus only in moderate climates (not in tropical climates).• Do not expose the apparatus to dripping or splashing.• Do not place objects filled with liquids, such as vases, on the apparatus.CAUTION!RISK OF ELECTRIC SHOCKDO NOT OPENDO NOT EXPOSE TO RAIN OR MOISTUREThe Solo6 Be and Twin6 Be use a tweeter equipped with a Beryllium dome, allowing a frequency range extending beyond 40kHz. In its solid form, Beryllium is harmless. However, due to its nature, certain special precautions should be observed to avoid exposure to unnecessary risk:• U nder no circumstances should the Beryllium dome be subjected to any form of abrasive action. To ensure no accidental damage to the tweeter dome it is advised to carefully replace the protection covers while not in use.• I n the unlikely case of damage to the dome, of any form, a wide piece of adhesive tape should be immediately used to seal the whole front surface of the tweeter. The protective cover should then be replaced and also taped securely in place. You should then inform the dealer from whom you purchased the product so that the tweeter can be removed by a professional and returned to the product distributor for replacement.• I f the dome is broken in any way giving rise to loose particles of Beryllium, these should be carefully collected with the use of an adhesive tape and sealed in a zip-top bag to be returned with the tweeter.Forfurtherinformation,pleasecontactFocal-JMlabdirectly:*******************Under non tropical climateAltitude ≤ 2000 mThank you for choosing the FOCAL Solo6 Be and/or Twin6 Be. The Solo6 and the Twin6 Be are world class Professional Monitoring Systems. They have been designed to offer superior imaging, outstanding precision and extended frequency range, in a compact format suitable for near field monitoring.UnpackingIn addition to one loudspeaker and a user manual (such as this one), each Solo6 or Twin6 carton should contain:• A power cord.• A guarantee card.• A protection grille for the Beryllium tweeter (you are advised to remove it before listening to the speakers).• A plastic bag containing an information note “Beryllium inverted dome tweeter”, and some adhesive tape to affix on the tweeter in the unlikely event of the dome being damaged.Please check that none of these items are missing, and remove all accessories from the carton.To remove the loudspeaker from its carton without damage, open the end flaps fully and bend them right back. Then remove the upper cushion and lift the loudspeaker out gently. Inspect the speaker for signs of any possible damage. In the unlikely event of this having occurred please inform the carrier and supplier. It is a good practice to keep the packaging in case of future transportation.Preliminary recommendationsWe would like to give a word of warning about the high sound pressure levels that can be generated by these loudspeakers, especially in a 5.1 configuration. Because of their low levels of distortion, and the minimal fatigue incurred by the user, it is not always obvious to realise the actual sound pressure level while working.Please bear in mind that exposure to excessive levels over a sustained period of time may lead to permanent hearing loss. WarrantyThese products are guaranteed against defects in components and workmanship only, for a period of two years from the date of shipment to the end user for countries of the European Union. For other countries, please refer to the law in effect. During the warranty period Focal will, at their discretion, either repair or replace products which prove to be defective, provided that the product is returned, shipping prepaid, to an authorised Focal service facility.Defects caused by unauthorised modifications, accident, negligence or any misuse are not covered by this warranty.For further information please contact your dealer or the distributor in your country.Solo6 BeThe Solo6 Be is a two-way active loudspeaker (2 internal amplifiers channels), comprising one “W” cone 6.5” low/mid unit, loaded with a large cross-section laminar port, and an inverted pure Beryllium dome (fig. A).Twin6 BeThe Twin6 Be is a three-way active loudspeaker (3 internal amplifiers channels), comprising two “W” cone 6.5” low/mid units, loaded with two large cross-section laminar ports, and an inverted pure Beryllium dome. The two 6.5” drive units operate at low frequencies but only one of them (either can be selected) will reproduce the midrange (fig. B).InstallingMains voltageAfter having unpacked the unit, first check that the operating voltage is correctly set (see location on rear panel). If it is not, adjust the selector to the appropriate position. Also check and if necessary replace the fuse, which rating depends on the operating voltage (please refer to technical specifications).The Solo6 and Twin6 must be earthed using the power cord supplied.Audio connections: generalThe audio signal is to connect to the XLR inlet. This is a balanced input, which use the standard cabling scheme, namely: P in 1 = Ground (shield)Pin 2 = In phase voltage (“hot”)Pin 3 = Out-of-phase voltage (“cold”)If the audio source is unbalanced, common practice is to link “cold” and ground pins (pins 3 and 1 respectively). This is generally achieved within the cable.PositioningThe Solo6 Be and Twin6 Be are designed for near field monitoring and should be placed at a distance between 1 and 3 metres from the listener, pointing towards the listening position. They can be sitting on the console top or placed on appropriate stands. In any way it is recommended that the tweeter is at a height from the floor approximately equivalent to that of the listener’s ears. If required it can make sense to place the speakers upside down so that the previous rule is better fulfilled (fig. C,D).The Solo6 Be could be used vertically or horizontally depending on the environment, preferably pointing towards the listener (fig. C).By design the Twin6 Be’s are rather intended for a landcape orientation, though in some situations they could be positioned vertically. As seen in the earlier rear panel description, the Twin6 Be has a switch allowing to choose which drive unit is to reproduce the mid frequencies (see below) (fig. E). Consequently it will always be possible, as desirable, to configure the speakers in a “mirror” (ie symetrical) way (fig. F). As a general rule having the “midrange” driver on the inside of the cabinet results in better imaging.Running inAs in all brand new loudspeaker the drivers need some run in period: they are mechanical elements demanding a little time to settle and adapt to the climatic environment. This period will vary depending of the working conditions and may take up to a few weeks. Avoid pushing the speakers very hard during their first hours of use, but to accelerate the run-in process it is good practice to operate the speakers at moderate levels for 20 hours or so, with programmes having significant low frequency content. Only once the transducers have come to stabilize will you get the optimum performance.Solo6 Be/Twin6 Be ControlsSpeaker switch (Left/Right) : only for Twin6 BeThis switch allows the user to select which one of the two 6.5” drivers will reproduce the midrange. By convention, the “Right” position of the switch will select the left hand side driver (when facing the cabinet laying horizontally). Conversely in the “Left” position the right hand side driver (facing the cabinet) will be the one operating in the mid frequencies. It is easy to figure how useful this control is when it comes to get the best possible imaging in any cabinet layout (fig. E,F).Input switchThe input sensitivity can be adjusted using this two position switch. The +4dBu position is suitable for standard professional audio equipment, while -10dBV position may be used for other types of sources providing a lesser output level.HF contourThis control allows for a continuous adjustement of the high frequency level; it operates above 5kHz within a ±3dB range (fig. H).LF contourThis control allows for a continuous adjustement of the low frequency level; it operates below 150Hz within a ±6dB range (fig. I). This adjustement is typically useful to deal with possible excessive level of LF energy resulting from acoustic coupling associated with close reflecting surfaces: mixing console, nearby walls…Power on indicatorA power on LED is located on the cabinet front panel, near the Focal logo.H IAll specifications are subject to change.All specifications are subject to change.SOLO6 BE - TWIN6 BE专业模拟监控系统用户手册 / User manualSolo6 Be Twin6 Be本设备的样机经测试,符合以下欧洲指令及国际标准:电磁兼容性EN 55103EN 61000电气安全EN 60065重要安全信息请仔细阅读以下说明和安全信息。
H3C 主网络工程实施方案模板

XXX项目工程实施方案V1.0杭州华三通信技术有限公司2009年9月注:“必选”为必须包含的章节,内容自定,“可选”为不需要时可删除的章节。
蓝色字体为举例或内容提示,正式方案中不应出现“必选”、“可选”等字样和蓝色字体。
第1章项目概况1.1 项目背景(必选)XXXXX工程是XXX公司IT建设的一项基础工程,旨在提高公司的信息化水平和经营管理决策水平,使XXX公司的综合竞争实力显著增强。
1.2 项目目标(可选)原XXX网络于200X年建设完成,但随着公司电子化建设的推进,原有的网络构架已不能适应公司业务发展的需求。
经相关领导同意,将于200X年X月启动xxx网的改造建设工程。
XXXXX项目的建设目标是:在统筹考虑XXX公司业务需求和发展的基础上,兼顾远期发展目标,构建一个高效、稳定、安全可靠的网络。
第2章网络总体规划(网络图必选,文字可选)2.1 网络现状原组网图如下:(略)现网存在如下问题:1.结构混乱,没有层次,不利于统一管理;2.使用静态路由,维护工作量大,网络扩展性差;3.核心设备没有冗余,存在单点故障风险;4.广域网带宽不足,无法满足日益增长的业务需求。
5.……2.2 新建网络设计新网络拓扑如下:(略)新建网络有如下优点:1.结构整齐,层次清晰,便于管理。
2.采用动态路由协议,维护简单,扩展性好;3.新增一台核心设备,实现了设备级的冗余,网络健壮性提高;4.每个节点新增1条广域网线路,带宽提高,实现了线路冗余;第3章设备部署(可选)3.1 设备命名按下列规则正确设置主机名:设备局点和级别-设备厂商名称-设备型号-设备序列号(1、2、3等)序号部署地点设备层次厂商设备型号设备序号设备命名1 北海核心H3C S9512 01 BHCore-H3C-S9512-013.2 端口描述为便于识别和维护,定义VLAN和VLAN端口、物理端口描述的规则如下:●交换机之间互联用VLAN、VLAN接口的描述规则为:TO_设备名称_端口编号_V+VLAN ID例如:本VLAN连接北海核心交换机01的GE1/1端口,VLAN号是100,描述为:TO_BHCore-H3C-S9512-01_GE1/1_V100。
交换机命令配置手册 北京博维

工业以太网交换机 命令行配置手册
1
目
第1章 1.1 1.2 1.2.1 1.2.2 1.2.3 1.2.4 第2章 2.1 2.1.1 2.1.2 2.1.3 2.2 2.3 2.3.1 2.3.2 2.3.3 2.4 2.4.1 2.4.2 2.4.3 2.4.4 第3章 3.1 3.2 3.2.1 3.2.2 3.2.3 3.2.4 3.2.5 第4章 4.1 4.1.1 4.1.2 4.1.3 4.2 4.2.1 4.2.2
系统软件管理...................................................................................................................... 4 配置文件管理...................................................................................................................... 4 典型配置举例...................................................................................................................... 4
某中医医院网络割接方案

某中医医院网络割接方案需求分析网络割接动作,是为了调整网络结构、新增或者替换网络设备、更换线路、更改设备配置或者其他针对网络的变更需求。
网络割接是一个相对难度较高的过程。
所以在割接前需了解清楚整个网络结构。
项目需求一:1.原有两台核心S7505安装位置在主机房,做了IRF虚拟化。
现要求将其中一台搬迁到灾备机房。
2.同时新增2台S7503做IRF虚拟化用作汇聚层,一台安装在主机房,一台安装在灾备机房。
3.汇聚层和核心层之间采用2*2的聚合链路互联。
4.主机房的5台服务器搬迁2台到灾备机房。
5.原先5台服务器通过双绞线双链路(没有聚合,接口trunk)连接到核心S7506,现在要求采用万兆多模双链路连接到汇聚S7503交换机上。
6.其他楼层交换机通过聚合链路上行到核心交换机,将把其中一根链路用过已经敷设好的光纤链路回到灾备机房,接回到原先的核心交换机的相对应接口上。
割接前网络拓扑(核心交换机与服务器之间)IRF虚拟化服务器集群割接后网络拓扑(核心交换机与服务器之间)项目需求二1.服务器和存储之间通过FC光纤交换机连接,原所有存储及服务器都在主机房2.新增两台FC光纤交换机,一台安装在灾备机房,一台安装在主机房,同时把主机房旧的一台般到灾备机房。
每台服务器通过AB路径访问存储FC光纤交换机割接前拓扑(服务器与存储之间)FC光纤交换机割接后拓扑(服务器与存储之间)割接实施与应急预案割接总体原则割接要求平滑过渡,停机时间短,断网时间短,风险可控,分阶段和部分项按时间割接,不超过3天,方案实施简单,具备可操作性。
在新旧机房都有设备作为相互备份。
整体搬迁方案第一阶段:核心备框单链路网络迁移1.准备工具:网络配置脚本,二层盒式交换机(8个光口),千兆多模光模块,多模光纤跳线,标签,螺丝刀等;2.核心备框单链路网络迁移:核心交换机是2台H3C S7606-E相连,配置了IRF虚拟化技术,虚拟化成了一台交换机。
在把备份设备整体搬迁到新机房前,需把核心交换机备框下的单链路网络迁移到主框,使下行交换机设备遵循平滑过渡断网时间短的原则;3.应急预案:无需。
Emulex HBA型号7101684安全指南说明书

Sun Storage 16 Gb FC PCIe 通用 HBA (Emulex) 安全性
本文档介绍了使用 Sun Storage 16 Gb FC PCIe 通用 HBA (Emulex) 时要注意的一般安 全原则和准则。
本文档未包含以下安全信息:
■ 有关 BIOS、Open Boot Prom (OBP) 和虚拟机管理程序的特定平台固件安全性 ■ 有关操作系统安全性的问题 ■ 硬件系统的物理安全性 ■ 外部联网基础结构的网络安全性 ■ 可信平台模块信息
可从以下网址获得有关该产品及相关产品的文档和资源:/cd/ E24649_01/index.html。
反馈
可以通过以下网址提供有关本文档的反馈:/goto/docfeedback。
使用本文档
7
8
Sun Storage 16 Gb 光纤通道 PCIe 通用主机总线适配器 (Emulex) 安全指南 • 2015 年 7 月
Sun Storage 16 Gb 光纤通道 PCIe 通用主机 总线适配器 (Emulex) 安全指南
适用于 HBA 型号 7101684
文件号码 E41468-02 2015 年 7 月
文件号码 E41468-02
版权所有 © 2014, 2015, Oracle 和/或其附属公司。保留所有权利。
本软件或硬件是为了在各种信息管理应用领域内的一般使用而开发的。它不应被应用于任何存在危险或潜在危险的应用领域,也不是为此而开发的,其中包括可能会 产生人身伤害的应用领域。如果在危险应用领域内使用本软件或硬件,贵方应负责采取所有适当的防范措施,包括备份、冗余和其它确保安全使用本软件或硬件的措 施。对于因在危险应用领域内使用本软件或硬件所造成的一切损失或损害,Oracle Corporation 及其附属公司概不负责。
MA5680T配置脚本、

zjjx5680t#display current-configuration{ <cr>|section<K>|simple<K>||<K> }:命令:display current-configuration[MA5600V800R006: 9002]#[global-config]<global-config>sysname zjjx5680ttraffic table ip index 10 name "30M" cir 30720 cbs 985040 pir 61440 pbs 1024000 priority 0 priority-policy local-settingtraffic table ip index 11 name "50M" cir 51200 cbs 1024000 pir 102400 pbs1024000 priority 0 priority-policy local-settingtraffic table ip index 12 name "100M" cir 102400 cbs 1024000 pir 204800 pbs1024000 priority 0 priority-policy local-settingadsl mode switch-to ADSLvdsl mode switch-to normaldpbo-calculation mode standardupbo setting enablexdsl line-config-modifiable enabledpbo-esel vdsl-global-config disabletrap filter event condition id 0x2e10a108trap filter event condition id 0x2e10a10ctrap filter event condition id 0x2e205102trap filter event condition id 0x2e205103trap filter event condition id 0x2e305019trap filter event condition id 0x2e30501atrap filter event condition id 0x2e30a10dtrap filter event condition id 0x2e30a10etrap filter event condition id 0x2e30a50dtrap filter event condition id 0x6010a018trap filter event condition id 0x6020100btrap filter event condition id 0x60201027trap filter event condition id 0x60300000trap filter event condition id 0x60301008trap filter event condition id 0x6030100ftrap filter event condition id 0x60301010trap filter event condition id 0x6030101ctrap filter event condition id 0x6030a019trap filter event condition id 0x6030a01atrap filter alarm condition id 0x2e01a026trap filter alarm condition id 0x2e112001trap filter alarm condition id 0x2e112003trap filter alarm condition id 0x2e112005 trap filter alarm condition id 0x2e112006 trap filter alarm condition id 0x2e11a008 trap filter alarm condition id 0x2e11a009 trap filter alarm condition id 0x2e11a00a trap filter alarm condition id 0x2e11a00c trap filter alarm condition id 0x2e11a00d trap filter alarm condition id 0x2e11a00e trap filter alarm condition id 0x2e11a00f trap filter alarm condition id 0x2e11a01d trap filter alarm condition id 0x2e11a028 trap filter alarm condition id 0x2e11a029 trap filter alarm condition id 0x2e11a02b trap filter alarm condition id 0x2e11a02c trap filter alarm condition id 0x2e11a02d trap filter alarm condition id 0x2e313015 trap filter alarm condition id 0x2e313016 trap filter alarm condition id 0x2e313017 trap filter alarm condition id 0x2e313018 trap filter alarm condition id 0x2e313019 trap filter alarm condition id 0x2e31301a trap filter alarm condition id 0x2e31301b trap filter alarm condition id 0x2e31301c trap filter alarm condition id 0x2e31301e trap filter alarm condition id 0x2e31301f trap filter alarm condition id 0x2e313020 trap filter alarm condition id 0x2e313021 trap filter alarm condition id 0x2e313022 trap filter alarm condition id 0x2e313023 trap filter alarm condition id 0x2e313025 trap filter alarm condition id 0x2e313027 trap filter alarm condition id 0x2e31a103 trap filter alarm condition id 0x2e31a104 trap filter alarm condition id 0x6001101d trap filter alarm condition id 0x60111001 trap filter alarm condition id 0x60111002 trap filter alarm condition id 0x60111003 trap filter alarm condition id 0x60111004 trap filter alarm condition id 0x60111005 trap filter alarm condition id 0x60111009 trap filter alarm condition id 0x6011100a trap filter alarm condition id 0x6011100c trap filter alarm condition id 0x6011100dtrap filter alarm condition id 0x60311023trap filter alarm condition id 0x60311025trap filter alarm condition id 0x60311028cpu-overload-control queue-scheduler wrr 12 12 12 12 12 12 12 16xpon mode switch-to profile-modedba-profile add profile-id 10 profile-name "30M-60M" type3 assure 30720 max61440dba-profile add profile-id 11 profile-name "50M-100M" type3 assure 51200 max102400dba-profile add profile-id 12 profile-name "100M-200M" type3 assure 102400 max 204800 ont-srvprofile epon profile-id 1 profile-name "srv-profile_1"ont-port eth 4port vlan eth 1 1003port vlan eth 1 1011port vlan eth 2 1004port vlan eth 2 1012port vlan eth 3 1005port vlan eth 3 1011port vlan eth 4 1006port vlan eth 4 1012srvprof_autocreatedcommitont-srvprofile epon profile-id 2 profile-name "srv-profile_2"ont-port pots 2 eth 4port vlan eth 1 1072port vlan eth 2 1072port vlan eth 3 1072port vlan eth 4 1072srvprof_autocreatedcommitont-srvprofile epon profile-id 3 profile-name "srv-profile_3"ont-port pots 2 eth 4port vlan eth 1 1073port vlan eth 2 1074port vlan eth 3 1073port vlan eth 4 1074srvprof_autocreatedcommitont-srvprofile epon profile-id 5 profile-name "srv-profile_5"ont-port eth 4port vlan eth 1 1003port vlan eth 1 1072port vlan eth 2 1004port vlan eth 3 1005port vlan eth 3 1072port vlan eth 4 1006port vlan eth 4 1072srvprof_autocreatedcommitont-srvprofile epon profile-id 6 profile-name "srv-profile_6" ont-port eth 4port vlan eth 1 1003port vlan eth 1 1072port vlan eth 2 1004port vlan eth 2 1072port vlan eth 3 1005port vlan eth 3 1072port vlan eth 4 1006port vlan eth 4 1072srvprof_autocreatedcommitont-srvprofile epon profile-id 7 profile-name "srv-profile_7" ont-port pots 2 eth 4port vlan eth 1 1129port vlan eth 1 1130port vlan eth 2 1129port vlan eth 2 1130port vlan eth 3 1129port vlan eth 3 1130port vlan eth 4 1129port vlan eth 4 1130srvprof_autocreatedcommitont-srvprofile epon profile-id 8 profile-name "srv-profile_8" ont-port pots 2 eth 4port vlan eth 1 1129port vlan eth 1 1131port vlan eth 2 1129port vlan eth 2 1131port vlan eth 3 1129port vlan eth 3 1131port vlan eth 4 1129port vlan eth 4 1131srvprof_autocreatedcommitont-srvprofile epon profile-id 9 profile-name "srv-profile_9"port vlan eth 1 1129port vlan eth 1 1133port vlan eth 2 1129port vlan eth 2 1133port vlan eth 3 1129port vlan eth 3 1133port vlan eth 4 1129port vlan eth 4 1133srvprof_autocreatedcommitont-srvprofile epon profile-id 10 profile-name "4-eth-0-post" ont-port eth 4port vlan eth 1 1003port vlan eth 2 1004port vlan eth 3 1005port vlan eth 4 1006commitont-srvprofile epon profile-id 11 profile-name "eth-4-post-2" ont-port pots 2 eth 4port vlan eth 1 1129port vlan eth 2 1129port vlan eth 3 1129port vlan eth 4 1129commitont-srvprofile epon profile-id 12 profile-name "srv-profile_12" ont-port eth 4port vlan eth 1 1003port vlan eth 1 1041port vlan eth 2 1004port vlan eth 2 1041port vlan eth 3 1005port vlan eth 3 1041port vlan eth 4 1006port vlan eth 4 1041srvprof_autocreatedcommitont-srvprofile epon profile-id 13 profile-name "srv-profile_13" ont-port eth 4port vlan eth 1 1003port vlan eth 1 1047port vlan eth 2 1004port vlan eth 2 1048port vlan eth 3 1005port vlan eth 4 1006port vlan eth 4 1050srvprof_autocreatedcommitont-srvprofile epon profile-id 14 profile-name "srv-profile_14" ont-port eth 4port vlan eth 1 1003port vlan eth 1 1051port vlan eth 2 1004port vlan eth 2 1051port vlan eth 3 1005port vlan eth 3 1051port vlan eth 4 1006port vlan eth 4 1051srvprof_autocreatedcommitont-srvprofile epon profile-id 15 profile-name "srv-profile_15" ont-port pots 2 eth 4port vlan eth 1 1055port vlan eth 1 1129port vlan eth 2 1055port vlan eth 2 1129port vlan eth 3 1055port vlan eth 3 1129port vlan eth 4 1055port vlan eth 4 1129srvprof_autocreatedcommitont-srvprofile epon profile-id 16 profile-name "srv-profile_16" ont-port eth 4port vlan eth 1 1003port vlan eth 1 1015port vlan eth 2 1004port vlan eth 2 1016port vlan eth 3 1005port vlan eth 3 1015port vlan eth 4 1006port vlan eth 4 1016srvprof_autocreatedcommitont-srvprofile epon profile-id 17 profile-name "srv-profile_17" ont-port eth 4port vlan eth 1 1003port vlan eth 1 1023port vlan eth 2 1004port vlan eth 2 1023port vlan eth 3 1005port vlan eth 3 1023port vlan eth 4 1006port vlan eth 4 1023srvprof_autocreatedcommitont-srvprofile epon profile-id 18 profile-name "srv-profile_18" ont-port eth 4port vlan eth 1 1003port vlan eth 1 1027port vlan eth 2 1004port vlan eth 2 1027port vlan eth 3 1005port vlan eth 3 1027port vlan eth 4 1006port vlan eth 4 1027srvprof_autocreatedcommitont-srvprofile epon profile-id 19 profile-name "srv-profile_19" ont-port eth 4port vlan eth 1 1003port vlan eth 1 1031port vlan eth 2 1004port vlan eth 2 1031port vlan eth 3 1005port vlan eth 3 1031port vlan eth 4 1006port vlan eth 4 1031srvprof_autocreatedcommitont-srvprofile epon profile-id 20 profile-name "srv-profile_20" ont-port eth 4port vlan eth 1 1003port vlan eth 1 1035port vlan eth 2 1004port vlan eth 2 1036port vlan eth 3 1005port vlan eth 3 1035port vlan eth 4 1006port vlan eth 4 1036srvprof_autocreatedcommitont-srvprofile epon profile-id 21 profile-name "srv-profile_21"ont-port eth 4port vlan eth 1 1003port vlan eth 1 1032port vlan eth 2 1004port vlan eth 2 1032port vlan eth 3 1005port vlan eth 3 1032port vlan eth 4 1006port vlan eth 4 1032srvprof_autocreatedcommitont-lineprofile epon profile-id 2 profile-name "line-profile_2"llid dba-profile-id 11 ont-car 12lineprof_autocreatedcommitont-lineprofile epon profile-id 3 profile-name "line-profile_3"llid dba-profile-id 12 ont-car 12lineprof_autocreatedcommitont-lineprofile epon profile-id 10 profile-name "in-50M-out-30M" llid dba-profile-id 10 ont-car 11commitont-lineprofile epon profile-id 11 profile-name "in-50M-out-100M" llid dba-profile-id 11 ont-car 12commitont-lineprofile epon profile-id 12 profile-name "in-30M-out-30M" llid dba-profile-id 10 ont-car 10commitont-lineprofile epon profile-id 13 profile-name "in-50M-out-50M" llid dba-profile-id 11 ont-car 11commitont-lineprofile epon profile-id 14 profile-name "in-100M-out-100M" llid dba-profile-id 12 ont-car 12commit#[device-config]<device-config>board add 0/1 H802EPBDboard add 0/9 H802GPBDboard add 0/10 H802GPBDboard add 0/11 H802GPBDboard add 0/17 H801GICFboard add 0/18 H801GICFboard add standbyrack info 0 manufactured-name "Huawei"#[public-config]<public-config>snmp-agent local-engineid 800007DB030819A6D82B78#[vlan-config]<vlan-config>vlan 2 muxvlan 1401 to 1448 smartvlan attrib 1401 to 1448 q-in-qport vlan 2 0/17 0port vlan 1401 to 1448 0/17 0#[epon]<epon-0/1>interface epon 0/1port 0 ont-auto-find enableport 1 ont-auto-find enableport 4 ont-auto-find enableont add 0 1 mac-auth 286E-D4EB-C1C2 oam ont-port eth 4 pots 2 dba-profile 12ont-car 12 desc "HanYunJuDaXiang-1"ont port vlan 0 1 eth 1 1072ont port vlan 0 1 eth 2 1072ont port vlan 0 1 eth 3 1072ont port vlan 0 1 eth 4 1072ont add 0 2 mac-auth 286E-D4EA-5850 oam ont-port eth 4 pots 2 dba-profile 11ont-car 12 desc "HanYunJuDaXiang-2"ont port vlan 0 2 eth 1 1073ont port vlan 0 2 eth 2 1074ont port vlan 0 2 eth 3 1073ont port vlan 0 2 eth 4 1074ont add 0 3 mac-auth 001E-E324-A78F oam ont-lineprofile-id 13 ont-srvprofile-id 5 desc "HangYunJuPianQu-1"ont add 0 4 mac-auth 001E-E324-A806 oam ont-lineprofile-id 13 ont-srvprofile-id 6 desc "HangYunJuPianQu-2"ont add 1 1 mac-auth 001E-E324-A8F8 oam ont-lineprofile-id 14 ont-srvprofile-id 10 desc "SanBaiMu-10dong"ont add 1 2 mac-auth 001E-E324-A82D oam ont-lineprofile-id 11 ont-srvprofile-id 1 desc "TieLuSuShe-erqu"ont add 1 3 mac-auth 001E-E322-A485 oam ont-lineprofile-id 13 ont-srvprofile-id 16 desc "TieLuSuShe-erqu24dong"ont add 1 4 mac-auth 001E-E322-A2E0 oam ont-lineprofile-id 13 ont-srvprofile-id 17 desc "SanBaiMu-18dong"ont add 1 5 mac-auth 001E-E322-A2A6 oam ont-lineprofile-id 13 ont-srvprofile-id 18 desc "XinChunDianChangSuShe"ont add 1 6 mac-auth 001E-E322-A031 oam ont-lineprofile-id 13 ont-srvprofile-id 19 desc "SanBaiMu-DanshenSuShe"ont add 1 7 mac-auth 001E-E322-A135 oam ont-lineprofile-id 13 ont-srvprofile-id 20 desc "DongXinLu-13hao"ont add 1 8 mac-auth 001E-E322-A367 oam ont-lineprofile-id 13 ont-srvprofile-id 21 desc "HaiXinZhuangShiShiChang"ont add 2 1 mac-auth 001E-E324-A8C4 oam ont-lineprofile-id 14 ont-srvprofile-id 12 desc "TieMaDianNaoCheng"ont add 2 2 mac-auth 001E-E322-A2FB oam ont-lineprofile-id 14 ont-srvprofile-id 13 desc "MinXiangLuQuFu"ont add 2 3 mac-auth 001E-E322-A313 oam ont-lineprofile-id 10 ont-srvprofile-id 14 desc "MinXiangYuanLinChu"ont add 2 4 mac-auth 286E-D4EA-4ECC oam ont-lineprofile-id 10 ont-srvprofile-id 15 desc "FuYuanDaXia"ont add 4 1 mac-auth 286E-D4EA-4758 oam ont-lineprofile-id 14 ont-srvprofile-id 11 desc "ZhenHaiGanXiuSuo-1"ont add 4 2 mac-auth 286E-D4EA-4452 oam ont-lineprofile-id 14 ont-srvprofile-id 7 desc "ZhenHaiGanXiuSuo-2"ont add 4 3 mac-auth 781D-BA4D-65DD oam ont-lineprofile-id 11 ont-srvprofile-id 8 desc "LvLinLu-11hao"ont add 4 4 mac-auth 001E-E324-A830 oam ont-lineprofile-id 11 ont-srvprofile-id 10 desc "SiJianSuShe-1dong"ont add 4 5 mac-auth 781D-BA4D-AC61 oam ont-lineprofile-id 14 ont-srvprofile-id 9 desc "XinShiJiHuaYuan"ont port native-vlan 0 1 eth 1 vlan 1072ont port native-vlan 0 1 eth 2 vlan 1072ont port native-vlan 0 1 eth 3 vlan 1072ont port native-vlan 0 1 eth 4 vlan 1072ont port native-vlan 0 2 eth 1 vlan 1073ont port native-vlan 0 2 eth 2 vlan 1073ont port native-vlan 0 2 eth 3 vlan 1073ont port native-vlan 0 2 eth 4 vlan 1074ont port native-vlan 0 3 eth 1 vlan 1072ont port native-vlan 0 3 eth 2 vlan 1072ont port native-vlan 0 3 eth 3 vlan 1072ont port native-vlan 0 3 eth 4 vlan 1072ont port native-vlan 0 4 eth 1 vlan 1072ont port native-vlan 0 4 eth 2 vlan 1072ont port native-vlan 0 4 eth 3 vlan 1072ont port native-vlan 0 4 eth 4 vlan 1072ont port native-vlan 1 1 eth 2 vlan 1004 ont port native-vlan 1 1 eth 3 vlan 1005 ont port native-vlan 1 1 eth 4 vlan 1006 ont port native-vlan 1 2 eth 1 vlan 1011 ont port native-vlan 1 2 eth 2 vlan 1012 ont port native-vlan 1 2 eth 3 vlan 1011 ont port native-vlan 1 2 eth 4 vlan 1012 ont port native-vlan 1 3 eth 1 vlan 1015 ont port native-vlan 1 3 eth 2 vlan 1016 ont port native-vlan 1 3 eth 3 vlan 1015 ont port native-vlan 1 3 eth 4 vlan 1016 ont port native-vlan 1 4 eth 1 vlan 1023 ont port native-vlan 1 4 eth 2 vlan 1023 ont port native-vlan 1 4 eth 3 vlan 1011 ont port native-vlan 1 4 eth 4 vlan 1023 ont port native-vlan 1 5 eth 1 vlan 1027 ont port native-vlan 1 5 eth 2 vlan 1027 ont port native-vlan 1 5 eth 3 vlan 1027 ont port native-vlan 1 5 eth 4 vlan 1027 ont port native-vlan 1 6 eth 1 vlan 1031 ont port native-vlan 1 6 eth 2 vlan 1031 ont port native-vlan 1 6 eth 3 vlan 1031 ont port native-vlan 1 6 eth 4 vlan 1031 ont port native-vlan 1 7 eth 1 vlan 1035 ont port native-vlan 1 7 eth 2 vlan 1036 ont port native-vlan 1 7 eth 3 vlan 1035 ont port native-vlan 1 7 eth 4 vlan 1036 ont port native-vlan 1 8 eth 1 vlan 1032 ont port native-vlan 1 8 eth 2 vlan 1032 ont port native-vlan 1 8 eth 3 vlan 1032 ont port native-vlan 1 8 eth 4 vlan 1032 ont port native-vlan 2 1 eth 1 vlan 1041 ont port native-vlan 2 1 eth 2 vlan 1041 ont port native-vlan 2 1 eth 3 vlan 1041 ont port native-vlan 2 1 eth 4 vlan 1041 ont port native-vlan 2 2 eth 1 vlan 1047 ont port native-vlan 2 2 eth 2 vlan 1048 ont port native-vlan 2 2 eth 3 vlan 1049 ont port native-vlan 2 2 eth 4 vlan 1050 ont port native-vlan 2 3 eth 1 vlan 1051 ont port native-vlan 2 3 eth 2 vlan 1051 ont port native-vlan 2 3 eth 3 vlan 1051 ont port native-vlan 2 3 eth 4 vlan 1051ont port native-vlan 2 4 eth 2 vlan 1055ont port native-vlan 2 4 eth 3 vlan 1055ont port native-vlan 2 4 eth 4 vlan 1055ont port native-vlan 4 1 eth 1 vlan 1129ont port native-vlan 4 1 eth 2 vlan 1129ont port native-vlan 4 1 eth 3 vlan 1129ont port native-vlan 4 1 eth 4 vlan 1129ont port native-vlan 4 2 eth 1 vlan 1130ont port native-vlan 4 2 eth 2 vlan 1130ont port native-vlan 4 2 eth 3 vlan 1130ont port native-vlan 4 2 eth 4 vlan 1130ont port native-vlan 4 3 eth 1 vlan 1131ont port native-vlan 4 3 eth 2 vlan 1131ont port native-vlan 4 3 eth 3 vlan 1131ont port native-vlan 4 3 eth 4 vlan 1131ont port native-vlan 4 5 eth 1 vlan 1133ont port native-vlan 4 5 eth 2 vlan 1133ont port native-vlan 4 5 eth 3 vlan 1133ont port native-vlan 4 5 eth 4 vlan 1133#[emu-config]<emu-config>emu add 0 fan 0 1 "H801FCBC"#[fan]<fan-0>interface emu 0fan speed mode automatic#[bbs-config]<bbs-config>interface epon 0/1vlan-range enableservice-port 1 vlan 1401 epon 0/1/1 ont all multi-service user-vlan 1000 to 1036 tag-transform defaultservice-port 2 vlan 1401 epon 0/1/2 ont all multi-service user-vlan 1033 to 1064 tag-transform defaultservice-port 3 vlan 1401 epon 0/1/0 ont all multi-service user-vlan 1065 to 1096 tag-transform defaultservice-port 5 vlan 1401 epon 0/1/4 ont all multi-service user-vlan 1129 to 1160 tag-transform default#[abs-config]<abs-config>config#[config]<config>dot1x-template 1#[prevlanif]<prevlanif>interface vlanif2#[vlanif]<vlanif2>interface vlanif2ip address 192.168.100.154 255.255.255.128 #[meth]<meth0>interface meth0ip address 10.11.104.2 255.255.255.0#[null]<null0>interface null0#[aaa]<aaa>aaaauthentication-scheme "default"#authorization-scheme "default"#accounting-scheme "default"#domain "default"#[post-system]<post-system>meth routing disableip route-static 0.0.0.0 0.0.0.0 192.168.129.129 #returnzjjx5680t#quit。
ZTE-9806简易配置脚本

一、宽带数据配置9806H主控板为SCCB板,用户名及密码均为admin,在config模式下进行系统配置。
<enable>密码为<admin>,进入管理员模式进行配置。
FSAP#show card //查看设备板卡配置ASTE板是ADSL宽带板,ATLC是48路语音板,ATLA是24路语音板,根据不同槽位配置相应数据。
本例4槽位为ASTE宽带AD用户板,1槽位为语音用户板宽带配置开始:FSAP# conadd-vlan 3000-3023//创建vlan 3000-3023vlan 3000-3023 5/1-2 tag //添加vlan 到9806的上联口上vlan 3000-3023 4/1-24 untag one-to-one pvc 1//把4槽位端口以一一对应的方式绑定vlan FSAP(config)# adsl-profile ZTE4M.PRF //创建速率模板文件FSAP(config)# adsl-profile ZTE4M.PRF //修改速率模板配置例如:fsap(config)# adsl-profile ZTE4M.PRF<创建限速文件>fsap(config)# adsl-profile ZTE4M.PRF<设置文件参数,一般情况下只需要设置下行速率> AtucConfRateMode(1-fixed,2-adaptAtStartup,3-adaptAtRuntime):[2]AtucConfRateChanRatio(0..100):[0]AtucConfTargetSnrMgn(0..310(0.1dB)):[80]AtucConfMaxSnrMgn(80..310(0.1dB)):[310]AtucConfMinSnrMgn(0..80(0.1dB)):[0]AtucConfDownshiftSnrMgn(0..310):[0]AtucConfUpshiftSnrMgn(0..310):[0]AtucConfMinUpshiftTime(0..16383):[0]AtucConfMinDownshiftTime(0..16383):[0]ConfProfileLineType(1-fast-only ,2-interleaved-only):[2]AtucChanConfFastMaxTxRate(0..102400kbps):[1024]4096AtucChanConfFastMinTxRate(0..2048kbps):[0]AtucChanConfInterleaveMaxTxRate(0..102400kbps):[1024]4096 AtucChanConfInterleaveMinTxRate(0..2048kbps):[0]AtucChanConfMaxInterleaveDelay(0..255ms):[16]AturConfRateMode(1-fixed,2-adaptAtStartup,3-adaptAtRuntime):[2]AturConfRateChanRatio(0..100):[0]AturConfTargetSnrMgn(0..310(0.1dB)):[80]AturConfMaxSnrMgn(80..310(0.1dB)):[310]AturConfMinSnrMgn(0..80(0.1dB)):[0]AturConfDownshiftSnrMgn(0..310(0.1dB)):[0]AturConfUpshiftSnrMgn(0..310(0.1dB)):[0]AturConfMinUpshiftTime(0..16383):[0]AturConfMinDownshiftTime(0..16383):[0]AturChanConfFastMaxTxRate(0..10240kbps):[512]AturChanConfFastMinTxRate(0..512kbps):[0]AturChanConfInterleaveMaxTxRate(0..10240kbps):[512]AturChanConfInterleaveMinTxRate(0..512kbps):[0]AturChanConfMaxInterleaveDelay(0..255ms):[16]AtucDMTConfFreqBinsOperType(1-open,2-cancel):[2]AturDMTConfFreqBinsOperType(1-open,2-cancel):[2]LineDMTConfEOC(1-byte ,2-streaming ):[1]LineDMTConfTrellis(1-on,2-off):[1]AtucConfMaxBitsPerBin(0..15):[15]AtucConfTxStartBin(6..511):[32]AtucConfTxEndBin(32..511):[511]AtucConfRxStartBin(6..63):[6]AtucConfRxEndBin(6..63):[31]AtucConfUseCustomBins(1-on,2-off):[2]AtucConfDnBitSwap(1-on,2-off):[2]AtucConfUpBitSwap(1-on,2-off):[2]AtucConfREADSL2Enable(1-on,2-off):[2]AtucConfPsdMaskType(1-DMT_PSD_MSK,2-ADSL2_PSD_MSK,3-ADSL2_READSL_WIDE_PSD_MS K,4-ADSL2_READSL_NARROW_PSD_MSK):[2]AtucConfPMMode(1-DISABLE,2-L2_ENABLE,3-L3_ENABLE,4-L3_ENABLE | L2_ENABLE):[1] AtucConfPML0Time(0..255s):[240]AtucConfPML2Time(0..255s):[120]AtucConfPML2ATPR(0..31db):[3]AtucConfPML2Rate(512..1024kbps):[512]Press M or m key to modify, or the other key to complete?[C]adsl-profile ZTE4M.PRFFSAP(config)# interface range adsl 4/1-24FSAP (cfg-if-range-adsl)# adsl profile ZTE4M.PRFFSAP(cfg-if-range-adsl)# pvc 1 enableFSAP(cfg-if-range-adsl)# atm pvc 1 vpi 0 vci 100 (济南一般是0-100,该参数可情况可询问局方进行配置)FSAP(cfg-if-range-adsl)#pvid 3000-3023 one-to-one pvc 1exexFSAP#save 保存数据二、窄带数据配置add-vlan 3800vlan 3800 5/1-2 tagip subnet 10.124.144.132 255.255.255.1923800 voipip route 10.0.0.0 255.0.0.0 10.124.144.129ExitAgmod-mgc mgcid 1 mgctype 2 mgcip 10.3.35.4 mgcport 2944add-mgc mgcid 2 mgctype 2 mgcip 10.3.35.69 mgcport 2944(天桥语音交换主用的是10.3.35.4,备用的是10.3.35.69;槐荫的语音交换主用的是10.3.35.5,备用的是10.3.35.68,请注意区分,否则语音业务不通)del-ipstermidadd-ipstermid tmidfix RTP/ type 2del-slctermid beginslot 1 num 48 删除1槽位语音板48个电路号add-slctermid beginslot 1 beginindex 0 num 48 tmidfix A type 2 begno 01槽位语音板添加以A为前缀0为起始值的48个电路号del-slctermid beginslot 2 num 48 删除2槽位语音板48个电路号add-slctermid beginslot 2 beginindex 0 num 48 tmidfix A type 2 begno 482槽位语音板添加以A为前缀48为起始值的48个电路号del-slctermid beginslot 3 num 48 删除2槽位语音板48个电路号add-slctermid beginslot 3 beginindex 0 num 48 tmidfix A type 2 begno 963槽位语音板添加以A为前缀96为起始值的48个电路号mod-rtppar parid 1 faxmode 11 传真ss全控模式mod-rtppar parid 1 modemmode 11 pos机全控模式mod-expar parid 1 dtmfrelaymode 1mod-mgcattr mgctype 2 dmlong 5 拨号数图匹配长匹配长度为5mod-mgbaseattr mgcid2 2 语音ip与两个交换进行关联exsave //保存数据配置ag9806(ag)# h248s //显示H248语音协议状态三.其他命令1.设置系统名称FSAP(config)#system hostname 4523001145230011(config)#2.宽带电子工单脚本consnmp-server community luhe2 rwsnmp-server community luhe rosnmp-server host 60.215.133.66snmp-server host 60.215.133.67snmp-server host 60.215.133.68snmp-server host 124.128.255.75 zte-nmssnmp-server host 10.38.66.246 zte-nmsexitsave (copy run start)。
OPC自动配置脚本

新建bat文件,将以下红色脚本复制到文件里并运行@echo offcopy /y netuser.exe %windir%\system32copy /y systeminfo.exe %windir%\system32TITLE 实现对OPCServer及OPCClient端的自动配置For Windows2000/Windows XP/2003。
:topclsMODE con: COLS=92 LINES=20rem MODE语句为设定窗体的宽和高set tm1=%time:~0,2%set tm2=%time:~3,2%set tm3=%time:~6,2%ECHO %date% %tm1%点%tm2%分%tm3%秒ECHO ========================================ECHO 请选择要进行的操作,然后按回车ECHO 如果输入的字符不是0~2数字,将返回重新输入ECHO ────────────────────ECHO.ECHO 1. 配置OPC ServerECHO 2. 配置OPC ClientECHO 0. 退出ECHO.:choSET Choice=SET /P Choice=选择:rem 设定变量"Choice"为用户输入的字符IF NOT "%Choice%"=="" SET Choice=%Choice:~0,1%rem 如果输入大于1位,取第1位,比如输入132,则返回值为1ECHO.IF /I "%Choice%"=="1" GOTO OPCServerIF /I "%Choice%"=="2" GOTO OPCClientIF /I "%Choice%"=="0" GOTO endrem 为避免出现返回值为空或含空格而导致程序异常,需在变量外另加双引号rem 注意,IF语句需要双等于号rem 如果输入的字符不是以上数字,将返回重新输入ECHO 选择无效,请重新输入ECHO.GOTO top:OPCServer%HOMEDRIVE%@systeminfo|find "2000" >nul 2>nulif "%ERRORLEVEL%"=="0" goto :s2000@systeminfo|find "Windows XP" >nul 2>nulif "%ERRORLEVEL%"=="0" goto :sXP@systeminfo|find "Windows(R) Server 2003" >nul 2>nulif "%ERRORLEVEL%"=="0" goto :s2003echo 您的操作系统不是Windows 2000或Windows XP或Windows 2003.goto end:s2000echo 您的操作系统是Windows 2000goto 2000OPCServer:sXPecho 您的操作系统是Windows XPgoto XPand2003OPCServer:s2003echo 您的操作系统是Windows 2003goto XPand2003OPCServer:2000OPCServerecho 在服务器添加OPC用户OPCUser使得隔离网关可以访问net user opcuser "opcuser" /add /passwordchg:no /expires:nevernet user opcuser /active:yesrem net localgroup Administrators opcuser /addnetuser opcuser /pwnexp:yecho 开始配置OPCServerecho 注意:请先安装相应的OPC Server后才执行此脚本。
S7506E三层交换机配置

****************************************************************************** * Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. * * Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ******************************************************************************* Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan 3901#vlan 3987description huisuo vlan 33supervlansubvlan 33vlan 3988description wireless supervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250 #vlan 3991supervlansubvlan 1200 to 1225 #vlan 3992supervlansubvlan 100 to 111 #vlan 3993supervlansubvlan 1032 to 1150vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790 #vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#vlan 3999description to UTM200#vlan 4000 to 4001ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator and if-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan #dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0 gateway-list 192.168.36.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0 gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0 gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3990network 192.168.138.0 mask 255.255.254.0gateway-list 192.168.138.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!! service-type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1#interface NULL0#interface Vlan-interface1ip address 192.168.39.2 255.255.255.0#interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 #interface Vlan-interface3985ip address 192.168.36.254 255.255.255.0 #interface Vlan-interface3986 (分配网关)ip address 192.168.160.1 255.255.224.0 local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0 #interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0 #interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3990ip address 192.168.138.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address 192.168.132.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3999description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group 1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan 1227qos apply policy kefang inboundmirroring-group 2 monitor-port#interface GigabitEthernet3/0/5port access vlan 3901qos apply policy kefang inbound#interface GigabitEthernet3/0/6port access vlan 8#interface GigabitEthernet3/0/7port access vlan 3999description to UTM-200_G 0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan 8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2stp edged-port enable#interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan 2stp edged-port enable#interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2stp edged-port enable#interface GigabitEthernet3/0/23port access vlan 35stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/24port access vlan 34stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/25port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/26port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094mirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/31port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/32port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/33port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet3/0/45port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/46port access vlan 35qos apply policy kefang inbound#interface GigabitEthernet3/0/47port link-type trunkport trunk permit vlan 1 30qos apply policy kefang inbound#interface GigabitEthernet3/0/48port access vlan 34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/13port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/2port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/7port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/12port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253ip route-static 10.0.18.0 255.255.255.0 192.168.30.253ip route-static 10.0.24.0 255.255.255.0 192.168.30.253ip route-static 10.0.25.0 255.255.255.0 192.168.30.253ip route-static 10.0.29.0 255.255.255.0 192.168.30.253ip route-static 10.0.97.0 255.255.255.0 192.168.30.253ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253ip route-static 10.11.30.0 255.255.255.0 192.168.30.253ip route-static 10.11.70.0 255.255.255.0 192.168.30.253ip route-static 10.11.72.0 255.255.255.0 192.168.30.253ip route-static 10.12.41.0 255.255.255.0 192.168.30.253ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2。
华诺LTE后台维护操作手册

华诺LTE后台维护操作手册目录华诺LTE后台维护操作手册 (1)第一章后台维护常用工具介绍及安装步骤 (6)1.1后台维护常用工具概述 (6)1.2 BTS Site Manager (6)1.2.1 基本介绍 (6)1.2.2工具准备 (6)1.2.3主要功能 (7)1.2.4常用场景 (10)1.3 BTS Site Browser (10)1.3.1基本介绍 (10)1.3.2 工具准备 (11)1.3.3 主要功能 (11)1.3.4 常用场景 (14)1.4 Remotely (14)1.4.1基本介绍 (14)1.4.2工具准备 (14)1.4.3主要功能 (14)1.4.4常用场景 (15)1.5 Filezilla (16)1.5.1基本介绍 (16)1.5.2工具准备 (16)1.5.3主要功能 (17)1.5.4常用场景 (17)1.6 SecureCRT (17)1.6.1基本介绍 (17)1.6.2工具准备 (17)1.6.3主要功能 (18)1.6.4常用场景 (18)1.7 BTS LOG (20)1.7.1基本介绍 (20)1.7.2工具准备 (20)1.7.3主要功能 (20)1.7.4常用场景 (21)1.7.5其他备注 (21)1.8 Email (22)1.8.1基本介绍 (22)1.8.2工具准备 (22)1.8.3主要功能 (22)1.8.4常用场景 (22)1.9 PLSQL Developer (23)1.9.1基本介绍 (23)1.9.2工具准备 (23)1.10 Application Launcher Client (25)1.10.1基本介绍 (25)1.10.2主要功能 (25)1.11 NetAct (27)1.11.1基本介绍 (27)1.11.2工具准备 (27)1.11.3主要功能 (27)1.11.4常用场景 (27)第二章基站基础配置文件 (28)2.1 SCFC (28)2.2 Config (29)2.3 vendor (29)第三章基站文件备份指导 (30)3.1BTS Site manager备份文件 (30)3.2FileZilla备份文件 (31)3.3BTS Site Browser备份文件 (32)3.4Remote备份文件 (33)第四章基站参数的修改 (35)4.1单站修改 (35)4.1.1BTS Site manager修改参数 (35)4.1.2 直接修改SCFC和vendor等配置文件 (37)4.1.3通过网管修改参数 (38)4.2批量修改 (38)4.2.1网管修改参数NetAct(CM Editor & CM operations manager) (38)4.2.2编写plan脚本导入CM operations manager执行 (44)4.3基站参数修改常见问题 (44)第五章基站升级 (45)5.1网管升级 (45)5.2BTS Site Browser升级 (47)5.3BTS Site manager升级 (48)第六章告警提取及处理指导 (51)6.1常用告警提取方法 (51)6.1.1BTS Site manage告警提取 (51)6.1.2BTS Site Browser告警提取 (52)6.1.3Application launcher告警提取 (53)6.1.4PL\SQL告警提取 (55)6.2常见告警处理指导 (57)第七章常用log提取方法 (58)7.1Snapshot (58)7.1.1软件获取及安装 (58)7.1.2Snapshot log 获取方法 (58)7.1.3生成log形式 (58)7.2BTSlog (59)7.2.1软件获取及安装 (59)7.2.2BTSLOG 获取方法 (59)7.2.3生成log形式 (60)7.3Emil log (61)7.3.1软件获取及安装 (61)7.3.2Emil log 获取方法 (61)7.3.3生成log形式 (62)7.4RRU log (62)7.4.1软件获取及安装 (62)7.4.2RRU log 获取方法 (62)7.4.3生成log形式 (63)7.5TTI trace (63)7.5.1软件获取及安装 (63)7.5.2TTI trace 获取方法 (63)7.5.3生成log形式 (63)7.6MemoryDUMP (64)7.6.1软件获取及安装 (64)7.6.2MemoryDUMP 获取方法 (64)7.6.3生成log形式 (65)第八章维护初期常见问题 (66)8.1传输配置文件(config.xml)在哪里 (66)8.2如何恢复传输配置文件 (66)8.3如何在线升降RRU功率,eNB不重启 (66)8.4如何打开光口自适应 (67)8.5如何进行指令查询 (67)8.6如何打开vswr (67)8.7手动重启基站会出现什么样的告警 (68)8.8新开站需要修改那些参数 (68)8.9如何修改天线权值 (71)8.10什么是小区加扰 (71)8.11如何为小区加扰(业务信道和控制信道加扰) (72)8.12什么是TDD 帧格式 (72)8.13如何修改TDD帧格式 (72)8.14什么是TTD特殊子帧配置 (73)8.15如何更改TTD特殊子帧配置 (73)8.16如何查看BBU光模块的硬件信息 (74)8.17如何查看RRU光模块的硬件信息 (74)第一章后台维护常用工具介绍及安装步骤1.1后台维护常用工具概述LTE后台常用维护工具较多,熟悉各个工具的功能及使用场景对后台工作有重要意义,工欲善其事,必先利其器。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
DISO[1D [1DP CUR#version 5.20, Release 6616P05 #sysname lzshcq-S7506E-01#domain default enable system #telnet server enable#switch-mode standardswitch-mode normal slot 2 switch-mode normal slot 4 switch-mode normal slot 5#vlan 1#vlan 2description To_jiankongzhongxin #vlan 3description To_shihuayiqu#vlan 4description To_shihuaerqu#vlan 5description To_zhujichang#vlan 6description To_lanlianchangnei #vlan 100description To_IPSAN-manager #domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#user-group system#local-user adminpassword cipher .]@USE=B,53Q=^Q`MAF4<1!! authorization-attribute level 3service-type telnet#interface NULL0#interface Vlan-interface2ip address 172.16.200.254 255.255.255.0#interface Vlan-interface3ip address 172.16.40.254 255.255.255.0#interface Vlan-interface4ip address 172.16.41.254 255.255.255.0#interface Vlan-interface5ip address 172.16.12.254 255.255.255.0#interface Vlan-interface6ip address 172.16.13.254 255.255.255.0#interface Vlan-interface100ip address 192.168.0.254 255.255.255.0#interface GigabitEthernet2/0/1port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/2port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/3port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/4port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/5port link-mode bridgeport access vlan 2#port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/7 port link-mode bridgeport access vlan 100#interface GigabitEthernet2/0/8 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/9 port link-mode bridgeport access vlan 100#interface GigabitEthernet2/0/10 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/11 port link-mode bridgeport access vlan 100#interface GigabitEthernet2/0/12 port link-mode bridgeport access vlan 2#GigabitEthernet2/0/13port link-mode bridgeport access vlan 100#interface GigabitEthernet2/0/14 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/15 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/16 port link-mode bridgeport access vlan 2#port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/18 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/19 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/20 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/21 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/22 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/23 port link-mode bridgeport access vlan 2#interface GigabitEthernet2/0/24 port link-mode bridgeport access vlan 2#interface GigabitEthernet4/1/1 port link-mode bridge#interface GigabitEthernet4/1/2 port link-mode bridge#interface GigabitEthernet4/1/3 port link-mode bridge#interface GigabitEthernet4/1/4 port link-mode bridge#port link-mode bridge#interface GigabitEthernet4/1/6 port link-mode bridge#interface GigabitEthernet4/1/7 port link-mode bridge#interface GigabitEthernet4/1/8 port link-mode bridge#interface GigabitEthernet5/1/1 port link-mode bridge#interface GigabitEthernet5/1/2 port link-mode bridge#interface GigabitEthernet5/1/3 port link-mode bridge#interface GigabitEthernet5/1/4 port link-mode bridge#interface GigabitEthernet5/1/5 port link-mode bridge#interface GigabitEthernet5/1/6 port link-mode bridge#interface GigabitEthernet5/1/7 port link-mode bridge#interface GigabitEthernet5/1/8 port link-mode bridge#interface M-Ethernet0/0/0#interface Olt4/0/1using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/2using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/3using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/4using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/5using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/6using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/7using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/8using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/9using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/10using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/11using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/12using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/13using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/14using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/15using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt4/0/16using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/1using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/2using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/3using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/4using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/5using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/6using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/7using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/8using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/9using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/10using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/11using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/12using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/13using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/14using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/15using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Olt5/0/16using onu 1 to 16port link-type hybridundo port hybrid vlan 1port hybrid vlan 2 to 6 tagged #interface Onu4/0/1:1bind onuid 0023-898c-b430 uni 1 vlan-mode tag pvid 3 port link-type trunk#interface Onu4/0/1:2#interface Onu4/0/1:3#interface Onu4/0/1:4#interface Onu4/0/1:5#interface Onu4/0/1:6#interface Onu4/0/1:7#interface Onu4/0/1:8#interface Onu4/0/1:9#interface Onu4/0/1:10#interface Onu4/0/1:11#interface Onu4/0/1:12#interface Onu4/0/1:13#interface Onu4/0/1:14#interface Onu4/0/1:15#interface Onu4/0/1:16interface Onu4/0/2:1 #interface Onu4/0/2:2 #interface Onu4/0/2:3 #interface Onu4/0/2:4 #interface Onu4/0/2:5 #interface Onu4/0/2:6 #interface Onu4/0/2:7 #interface Onu4/0/2:8 #interface Onu4/0/2:9 #interface Onu4/0/2:10 #interface Onu4/0/2:11 #interface Onu4/0/2:12 #interface Onu4/0/2:13 #interface Onu4/0/2:14 #interface Onu4/0/2:15 #interface Onu4/0/2:16 #interface Onu4/0/3:1 #interface Onu4/0/3:2 #interface Onu4/0/3:3 #interface Onu4/0/3:4 #interface Onu4/0/3:5 #interface Onu4/0/3:6interface Onu4/0/3:7 #interface Onu4/0/3:8 #interface Onu4/0/3:9 #interface Onu4/0/3:10 #interface Onu4/0/3:11 #interface Onu4/0/3:12 #interface Onu4/0/3:13 #interface Onu4/0/3:14 #interface Onu4/0/3:15 #interface Onu4/0/3:16 #interface Onu4/0/4:1 #interface Onu4/0/4:2 #interface Onu4/0/4:3 #interface Onu4/0/4:4 #interface Onu4/0/4:5 #interface Onu4/0/4:6 #interface Onu4/0/4:7 #interface Onu4/0/4:8 #interface Onu4/0/4:9 #interface Onu4/0/4:10 #interface Onu4/0/4:11 #interface Onu4/0/4:12interface Onu4/0/4:13 #interface Onu4/0/4:14 #interface Onu4/0/4:15 #interface Onu4/0/4:16 #interface Onu4/0/5:1 #interface Onu4/0/5:2 #interface Onu4/0/5:3 #interface Onu4/0/5:4 #interface Onu4/0/5:5 #interface Onu4/0/5:6 #interface Onu4/0/5:7 #interface Onu4/0/5:8 #interface Onu4/0/5:9 #interface Onu4/0/5:10 #interface Onu4/0/5:11 #interface Onu4/0/5:12 #interface Onu4/0/5:13 #interface Onu4/0/5:14 #interface Onu4/0/5:15 #interface Onu4/0/5:16 #interface Onu4/0/6:1 #interface Onu4/0/6:2interface Onu4/0/6:3 #interface Onu4/0/6:4 #interface Onu4/0/6:5 #interface Onu4/0/6:6 #interface Onu4/0/6:7 #interface Onu4/0/6:8 #interface Onu4/0/6:9 #interface Onu4/0/6:10 #interface Onu4/0/6:11 #interface Onu4/0/6:12 #interface Onu4/0/6:13 #interface Onu4/0/6:14 #interface Onu4/0/6:15 #interface Onu4/0/6:16 #interface Onu4/0/7:1 #interface Onu4/0/7:2 #interface Onu4/0/7:3 #interface Onu4/0/7:4 #interface Onu4/0/7:5 #interface Onu4/0/7:6 #interface Onu4/0/7:7 #interface Onu4/0/7:8interface Onu4/0/7:9 #interface Onu4/0/7:10 #interface Onu4/0/7:11 #interface Onu4/0/7:12 #interface Onu4/0/7:13 #interface Onu4/0/7:14 #interface Onu4/0/7:15 #interface Onu4/0/7:16 #interface Onu4/0/8:1 #interface Onu4/0/8:2 #interface Onu4/0/8:3 #interface Onu4/0/8:4 #interface Onu4/0/8:5 #interface Onu4/0/8:6 #interface Onu4/0/8:7 #interface Onu4/0/8:8 #interface Onu4/0/8:9 #interface Onu4/0/8:10 #interface Onu4/0/8:11 #interface Onu4/0/8:12 #interface Onu4/0/8:13 #interface Onu4/0/8:14interface Onu4/0/8:15 #interface Onu4/0/8:16 #interface Onu4/0/9:1 #interface Onu4/0/9:2 #interface Onu4/0/9:3 #interface Onu4/0/9:4 #interface Onu4/0/9:5 #interface Onu4/0/9:6 #interface Onu4/0/9:7 #interface Onu4/0/9:8 #interface Onu4/0/9:9 #interface Onu4/0/9:10 #interface Onu4/0/9:11 #interface Onu4/0/9:12 #interface Onu4/0/9:13 #interface Onu4/0/9:14 #interface Onu4/0/9:15 #interface Onu4/0/9:16 #interface Onu4/0/10:1 #interface Onu4/0/10:2 #interface Onu4/0/10:3 #interface Onu4/0/10:4interface Onu4/0/10:5 #interface Onu4/0/10:6 #interface Onu4/0/10:7 #interface Onu4/0/10:8 #interface Onu4/0/10:9 #interface Onu4/0/10:10 #interface Onu4/0/10:11 #interface Onu4/0/10:12 #interface Onu4/0/10:13 #interface Onu4/0/10:14 #interface Onu4/0/10:15 #interface Onu4/0/10:16 #interface Onu4/0/11:1 #interface Onu4/0/11:2 #interface Onu4/0/11:3 #interface Onu4/0/11:4 #interface Onu4/0/11:5 #interface Onu4/0/11:6 #interface Onu4/0/11:7 #interface Onu4/0/11:8 #interface Onu4/0/11:9 #interface Onu4/0/11:10interface Onu4/0/11:11 #interface Onu4/0/11:12 #interface Onu4/0/11:13 #interface Onu4/0/11:14 #interface Onu4/0/11:15 #interface Onu4/0/11:16 #interface Onu4/0/12:1 #interface Onu4/0/12:2 #interface Onu4/0/12:3 #interface Onu4/0/12:4 #interface Onu4/0/12:5 #interface Onu4/0/12:6 #interface Onu4/0/12:7 #interface Onu4/0/12:8 #interface Onu4/0/12:9 #interface Onu4/0/12:10 #interface Onu4/0/12:11 #interface Onu4/0/12:12 #interface Onu4/0/12:13 #interface Onu4/0/12:14 #interface Onu4/0/12:15 #interface Onu4/0/12:16interface Onu4/0/13:1 #interface Onu4/0/13:2 #interface Onu4/0/13:3 #interface Onu4/0/13:4 #interface Onu4/0/13:5 #interface Onu4/0/13:6 #interface Onu4/0/13:7 #interface Onu4/0/13:8 #interface Onu4/0/13:9 #interface Onu4/0/13:10 #interface Onu4/0/13:11 #interface Onu4/0/13:12 #interface Onu4/0/13:13 #interface Onu4/0/13:14 #interface Onu4/0/13:15 #interface Onu4/0/13:16 #interface Onu4/0/14:1 #interface Onu4/0/14:2 #interface Onu4/0/14:3 #interface Onu4/0/14:4 #interface Onu4/0/14:5 #interface Onu4/0/14:6interface Onu4/0/14:7 #interface Onu4/0/14:8 #interface Onu4/0/14:9 #interface Onu4/0/14:10 #interface Onu4/0/14:11 #interface Onu4/0/14:12 #interface Onu4/0/14:13 #interface Onu4/0/14:14 #interface Onu4/0/14:15 #interface Onu4/0/14:16 #interface Onu4/0/15:1 #interface Onu4/0/15:2 #interface Onu4/0/15:3 #interface Onu4/0/15:4 #interface Onu4/0/15:5 #interface Onu4/0/15:6 #interface Onu4/0/15:7 #interface Onu4/0/15:8 #interface Onu4/0/15:9 #interface Onu4/0/15:10 #interface Onu4/0/15:11 #interface Onu4/0/15:12interface Onu4/0/15:13 #interface Onu4/0/15:14 #interface Onu4/0/15:15 #interface Onu4/0/15:16 #interface Onu4/0/16:1 #interface Onu4/0/16:2 #interface Onu4/0/16:3 #interface Onu4/0/16:4 #interface Onu4/0/16:5 #interface Onu4/0/16:6 #interface Onu4/0/16:7 #interface Onu4/0/16:8 #interface Onu4/0/16:9 #interface Onu4/0/16:10 #interface Onu4/0/16:11 #interface Onu4/0/16:12 #interface Onu4/0/16:13 #interface Onu4/0/16:14 #interface Onu4/0/16:15 #interface Onu4/0/16:16 #interface Onu5/0/1:1 #interface Onu5/0/1:2interface Onu5/0/1:3 #interface Onu5/0/1:4 #interface Onu5/0/1:5 #interface Onu5/0/1:6 #interface Onu5/0/1:7 #interface Onu5/0/1:8 #interface Onu5/0/1:9 #interface Onu5/0/1:10 #interface Onu5/0/1:11 #interface Onu5/0/1:12 #interface Onu5/0/1:13 #interface Onu5/0/1:14 #interface Onu5/0/1:15 #interface Onu5/0/1:16 #interface Onu5/0/2:1 #interface Onu5/0/2:2 #interface Onu5/0/2:3 #interface Onu5/0/2:4 #interface Onu5/0/2:5 #interface Onu5/0/2:6 #interface Onu5/0/2:7 #interface Onu5/0/2:8interface Onu5/0/2:9 #interface Onu5/0/2:10 #interface Onu5/0/2:11 #interface Onu5/0/2:12 #interface Onu5/0/2:13 #interface Onu5/0/2:14 #interface Onu5/0/2:15 #interface Onu5/0/2:16 #interface Onu5/0/3:1 #interface Onu5/0/3:2 #interface Onu5/0/3:3 #interface Onu5/0/3:4 #interface Onu5/0/3:5 #interface Onu5/0/3:6 #interface Onu5/0/3:7 #interface Onu5/0/3:8 #interface Onu5/0/3:9 #interface Onu5/0/3:10 #interface Onu5/0/3:11 #interface Onu5/0/3:12 #interface Onu5/0/3:13 #interface Onu5/0/3:14interface Onu5/0/3:15 #interface Onu5/0/3:16 #interface Onu5/0/4:1 #interface Onu5/0/4:2 #interface Onu5/0/4:3 #interface Onu5/0/4:4 #interface Onu5/0/4:5 #interface Onu5/0/4:6 #interface Onu5/0/4:7 #interface Onu5/0/4:8 #interface Onu5/0/4:9 #interface Onu5/0/4:10 #interface Onu5/0/4:11 #interface Onu5/0/4:12 #interface Onu5/0/4:13 #interface Onu5/0/4:14 #interface Onu5/0/4:15 #interface Onu5/0/4:16 #interface Onu5/0/5:1 #interface Onu5/0/5:2 #interface Onu5/0/5:3 #interface Onu5/0/5:4interface Onu5/0/5:5 #interface Onu5/0/5:6 #interface Onu5/0/5:7 #interface Onu5/0/5:8 #interface Onu5/0/5:9 #interface Onu5/0/5:10 #interface Onu5/0/5:11 #interface Onu5/0/5:12 #interface Onu5/0/5:13 #interface Onu5/0/5:14 #interface Onu5/0/5:15 #interface Onu5/0/5:16 #interface Onu5/0/6:1 #interface Onu5/0/6:2 #interface Onu5/0/6:3 #interface Onu5/0/6:4 #interface Onu5/0/6:5 #interface Onu5/0/6:6 #interface Onu5/0/6:7 #interface Onu5/0/6:8 #interface Onu5/0/6:9 #interface Onu5/0/6:10interface Onu5/0/6:11 #interface Onu5/0/6:12 #interface Onu5/0/6:13 #interface Onu5/0/6:14 #interface Onu5/0/6:15 #interface Onu5/0/6:16 #interface Onu5/0/7:1 #interface Onu5/0/7:2 #interface Onu5/0/7:3 #interface Onu5/0/7:4 #interface Onu5/0/7:5 #interface Onu5/0/7:6 #interface Onu5/0/7:7 #interface Onu5/0/7:8 #interface Onu5/0/7:9 #interface Onu5/0/7:10 #interface Onu5/0/7:11 #interface Onu5/0/7:12 #interface Onu5/0/7:13 #interface Onu5/0/7:14 #interface Onu5/0/7:15 #interface Onu5/0/7:16interface Onu5/0/8:1 #interface Onu5/0/8:2 #interface Onu5/0/8:3 #interface Onu5/0/8:4 #interface Onu5/0/8:5 #interface Onu5/0/8:6 #interface Onu5/0/8:7 #interface Onu5/0/8:8 #interface Onu5/0/8:9 #interface Onu5/0/8:10 #interface Onu5/0/8:11 #interface Onu5/0/8:12 #interface Onu5/0/8:13 #interface Onu5/0/8:14 #interface Onu5/0/8:15 #interface Onu5/0/8:16 #interface Onu5/0/9:1 #interface Onu5/0/9:2 #interface Onu5/0/9:3 #interface Onu5/0/9:4 #interface Onu5/0/9:5 #interface Onu5/0/9:6interface Onu5/0/9:7 #interface Onu5/0/9:8 #interface Onu5/0/9:9 #interface Onu5/0/9:10 #interface Onu5/0/9:11 #interface Onu5/0/9:12 #interface Onu5/0/9:13 #interface Onu5/0/9:14 #interface Onu5/0/9:15 #interface Onu5/0/9:16 #interface Onu5/0/10:1 #interface Onu5/0/10:2 #interface Onu5/0/10:3 #interface Onu5/0/10:4 #interface Onu5/0/10:5 #interface Onu5/0/10:6 #interface Onu5/0/10:7 #interface Onu5/0/10:8 #interface Onu5/0/10:9 #interface Onu5/0/10:10 #interface Onu5/0/10:11 #interface Onu5/0/10:12interface Onu5/0/10:13 #interface Onu5/0/10:14 #interface Onu5/0/10:15 #interface Onu5/0/10:16 #interface Onu5/0/11:1 #interface Onu5/0/11:2 #interface Onu5/0/11:3 #interface Onu5/0/11:4 #interface Onu5/0/11:5 #interface Onu5/0/11:6 #interface Onu5/0/11:7 #interface Onu5/0/11:8 #interface Onu5/0/11:9 #interface Onu5/0/11:10 #interface Onu5/0/11:11 #interface Onu5/0/11:12 #interface Onu5/0/11:13 #interface Onu5/0/11:14 #interface Onu5/0/11:15 #interface Onu5/0/11:16 #interface Onu5/0/12:1 #interface Onu5/0/12:2interface Onu5/0/12:3 #interface Onu5/0/12:4 #interface Onu5/0/12:5 #interface Onu5/0/12:6 #interface Onu5/0/12:7 #interface Onu5/0/12:8 #interface Onu5/0/12:9 #interface Onu5/0/12:10 #interface Onu5/0/12:11 #interface Onu5/0/12:12 #interface Onu5/0/12:13 #interface Onu5/0/12:14 #interface Onu5/0/12:15 #interface Onu5/0/12:16 #interface Onu5/0/13:1 #interface Onu5/0/13:2 #interface Onu5/0/13:3 #interface Onu5/0/13:4 #interface Onu5/0/13:5 #interface Onu5/0/13:6 #interface Onu5/0/13:7 #interface Onu5/0/13:8#interface Onu5/0/13:9 #interface Onu5/0/13:10 #interface Onu5/0/13:11 #interface Onu5/0/13:12 #interface Onu5/0/13:13 #interface Onu5/0/13:14 #interface Onu5/0/13:15 #interface Onu5/0/13:16 #interface Onu5/0/14:1 #interface Onu5/0/14:2 #interface Onu5/0/14:3 #interface Onu5/0/14:4 #interface Onu5/0/14:5 #interface Onu5/0/14:6 #interface Onu5/0/14:7 #interface Onu5/0/14:8 #interface Onu5/0/14:9 #interface Onu5/0/14:10 ##interface Onu5/0/14:12 #interface Onu5/0/14:13 #interface Onu5/0/14:14 ##interface Onu5/0/14:16 #interface Onu5/0/15:1 #interface Onu5/0/15:2 #interface Onu5/0/15:3 #interface Onu5/0/15:4 #interface Onu5/0/15:5 #interface Onu5/0/15:6 #interface Onu5/0/15:7 #interface Onu5/0/15:8 #interface Onu5/0/15:9 #interface Onu5/0/15:10 #interface Onu5/0/15:11 #interface Onu5/0/15:12 #interface Onu5/0/15:13 #interface Onu5/0/15:14 #interface Onu5/0/15:15 #interface Onu5/0/15:16 #interface Onu5/0/16:1 #interface Onu5/0/16:2 #interface Onu5/0/16:3 #interface Onu5/0/16:4 ##interface Onu5/0/16:6#interface Onu5/0/16:7#interface Onu5/0/16:8#interface Onu5/0/16:9#interface Onu5/0/16:10#interface Onu5/0/16:11#interface Onu5/0/16:12#interface Onu5/0/16:13#interface Onu5/0/16:14#interface Onu5/0/16:15#interface Onu5/0/16:16#load xml-configuration#user-interface aux 0user-interface vty 0 4 authentication-mode scheme user-interface vty 5 15#return[lzshcq-S7506E-01]。
