Chapter 2 E-commerce business models电子商务模式参考PPT
电子商务 中英对照E-commerce Chapter2

20世纪80年代末独立 的学术和研究网络合 并成了互联网
1979年杜克大学和 北卡罗来纳大学的 一群学生和程序员 创建了用户新闻网
20世纪90年代起 互联网成为全球 性的共享资源
1991年美国科学基金 会进一步放宽对互联 网商业活动的限制, 并对互联网实施私有 化
1996年发展到 30多万台计算 机
20世纪60年代初,美 国防部担心核武器攻 击计算机设施,意欲 创建全球性网络
1969年美国防部将加州 大学洛杉矶分校与圣巴 巴拉分校、斯坦福大学 国际研究所、犹他大学 的四台计算机连接起来
1972年 电子邮件诞 生
互 联 网 的 起 源 与 发 展
1989年美科学基金会 允许两家商业性的电 子邮件服务商与互联 网建立有限的连接
world wide web
Computer network 计算机网络 Technology allowing people to connect computers to each other Internet 因特网 A large system of interconnected computer (internet) spanning the globe(地球) World Wide Web 万维网
p58
2. Packet-switched networks
- Works well for(适用于) telephone calls
Circuit switching 线路交换
- Does not work as well for:
Sending data across large WAN, interconnected network Circuit-switched network problem 线路交换网络的问题 • Connected circuit failure - Causes interrupted connection, data loss 中断连接,数据丢失
电子商务英语教学课件Unit 2 Enterprise and E-commerce
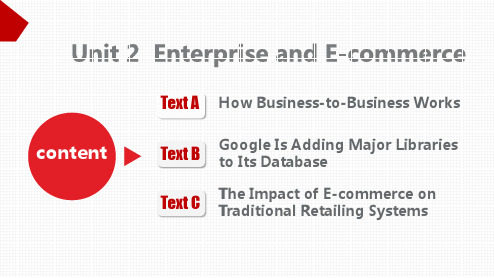
Google Is Adding Major Libraries to Its Database
Analysis of sentences
划线部分为定语从句,修饰前面的 publishers,whose为关系词, are of interest 有趣的 enough to 足以…… in large quantifies 大量地
与基于互联网的电子商务相比,电子数据交换(EDI)标 准化程度更低,成本也更高,通常使用XML(可扩展标记 语言)来允许买方和卖方在线沟通。
本句中, 划线部分是一个 非限定性定语从句, 修饰 “Internet based eBusiness”, 对其进行进 一步补充说明。
How Business-to-Business Works
Google Is Adding Major Libraries to Its Database
Analysis of sentences
The Amazon and Google programs work by restricting the access of users to only a few pages of a copyrighted book during each search, offering enough to help them decide whether the book meets their requirements enough to justify ordering the print version.
How Business-to-Business Works
Some notes
economy of scale 因经营规模扩大而得到的经济节约 fixed pricing固定价格 work on 从事于, 致力于 back-end system 后端系统 B2B 企业对企业电子商务 EDI (Electronic Data Interchange) 电子数据交换 XML (eXtensible Markup Language) 可扩展标识语言
10种电商模式解析

10种电商模式解析电商模式(E-commerce business models)是指在互联网上进行商业交易的方式和模式。
随着互联网技术的不断发展,电商模式也在不断演变和创新。
本文将分析并解析10种常见的电商模式。
一、B2C电商模式(Business-to-Consumer)B2C电商模式是指企业通过互联网将产品直接销售给消费者的模式。
企业在网上开设电商平台,提供商品信息、交易、支付、配送等服务,消费者通过电商平台选择和购买商品。
这种模式的代表企业包括京东、天猫等。
二、C2C电商模式(Consumer-to-Consumer)C2C电商模式是指消费者之间通过互联网进行购买和销售商品的模式。
平台提供商品信息展示、交流和支付等功能,消费者可以在平台上发布自己的商品信息,并与其他消费者达成交易。
淘宝、闲鱼等是典型的C2C电商平台。
三、B2B电商模式(Business-to-Business)B2B电商模式是指企业间通过互联网进行交易和合作的模式。
企业可以在线上寻找供应商、采购商品、交换信息、签订合同等。
阿里巴巴是最著名的B2B电商平台之一。
四、O2O电商模式(Online-to-Offline)O2O电商模式是指将线上的商业活动与线下的实体店铺相结合的模式。
即通过互联网将顾客引流到实体店铺消费,或者在线上下订单,到实体店铺取货。
美团、饿了么等属于O2O电商模式的代表。
五、群购电商模式(Group-buying)群购电商模式是指通过团购网站向消费者提供优惠的商品或服务,消费者可以组团购买以获取更低的价格。
例如美团、糯米等。
六、跨境电商模式(Cross-border)跨境电商模式是指通过互联网进行国际贸易销售的模式。
企业通过电商平台将国内商品出口到海外市场,或者将国外商品引进至国内市场。
淘宝全球购、亚马逊等都是跨境电商平台。
七、社交电商模式(Social e-commerce)社交电商模式是指在社交媒体平台上进行商品推广、销售和交易的模式。
00888电子商务英语课文Unit2

00888电子商务英语课文Unit2Unit 2 Planning an E-businessText A Elements of a Good Business Plan一个好的商业计划要素Business plans will vary from company reflecting their different needs. For example,an established business looking at adding an online componentwill be able to focus on integration between the physical store and the online store. A pure player –a business operating solely on the internet-will use its business plans to demonstrate its market analysis and seek funding. Regardless of use, good business plans generally consist of an executive summary, a market analysis, a description of the company and its management, a marketing and sales strategy, and a description of products and services offered. If necessary, business plans can include funding requests and necessary financial information.商业计划将不同的公司反映他们不同的需求。
E-Commerce options(unit 2)

Self-Hosting
Companies that host their own Web sites usually do so because they anticipate a high-volume of transactions, have the technical and financial resources to invest in special hardware and customized software, and have sufficient staff to maintain the entire system.
Virtual Stores
You operate the store’s Web page, but the products are actually purchased from another online store. The role of your store is to attract customers who are interested in the products you are advertising.
Table B-1 Goals and Solutions
goals Generate extra income without spending much time resources Very limited money No products to sell Limited time E-commerce solution Issue information Link such Web sites that offer affiliate programs Sell items in online auction Use a service that hosts your store for free and that processes credit card transaction
《电子商务概论》课程教学大纲
《电子商务概论》课程教学大纲一、课程简介电子商务作为一门新兴的学科,主要内容侧重于向学生介绍在互联网时代,电子商务给传统商业模式带来的影响,以及为开展电子商务所采用的技术和方法,目的在于使学生通过本课程的学习,能够使学生掌握电子商务的基本框架和基本内容,对电子商务的基本概念和框架、电子商务模式、电子商务战略、计算机网络基础设施、信息处理技术、电子商务支付技术、电子商务的安全技术、网络营销、物流管理与电子商务系统开发、电子商务环境建设等电子商务的基本理论有更进一步的理解。
二、教学目标本课程是电子商务专业的专业必修课,也是非电子商务专业的创新创业拓展专业课。
通过本课程的学习,要求学生掌握电子商务的基本理论和方法,理解电子商务技术原理及各种商务模式的应用。
掌握相关的电子商务网络技术、支付技术、物流技术及安全技术的基本能力。
三、主要教学模式和教学手段该课程采用理论教学和实践教学相结合的方法,在多媒体教室内进行理论教学,主要以知识传授为主;在专业实验室内进行实验模拟操作,以操作练习为主,将理论与实践结合,进而使学生具备一定的电子商务职业能力。
四、教学内容Chapter 1 E-commerce Overview(电子商务概述)(一)目的与要求1.掌握电子商务的基本概念;2.了解电子商务的基本框架模式;3. 理解电子商务的功能和作用;4.理解电子商务发展在经济建设中的作用。
(二)教学内容Case: (引例:)1.1 The Basic Concepts ofE-commerce(电子商务的基本概念)1.1.1 The Definition of E-commerce(电子商务的定义)1.1.2 The Contents of E-commerce(电子商务的内容)1.1.3 Functions & Features of E-commerce(电子商务的功能及特性)1.2 Emergence andDevelopment(电子商务的产生与发展)1.2.1 Developing History of E-commerce(电子商务的发展历程)1.2.2 Trend of E-commerce Development(电子商务的发展趋势)1.3 The Structure andSystem of EC(电子商务的结构与系统)1.3.1 The Basic Framework of E-commerce(电子商务的基本框架)1.3.2 Application Framework of E-commerce(电子商务的应用框架)1.3.3 The System Composition of EC(电子商务的系统组成)Chapter 2 E-commerce Models(电子商务模式)(一)目的与要求1.理解电子商务模式的形成;2.掌握电子商务的交易模式以及 B2B、B2C、C2C 等经典电子商务模式及相应的盈利模式;3.熟悉几种新型的电子商务模式,能结合具体案例对电子商务模式进行分类。
电子商务英语教程5-Business Models of E-commerce

Text B Understanding B2C E-commerce
New words
property n. 财产 intimacy n. 亲密, 亲密的状况 forum n. 提供公开讨论机会的宣传媒介, 如报纸或广播电视的专题讨论节目等 streamlined a. 有效组织或简单化的 linkage n. 联系或关系 prospective a. 预期的 innovative a. 革新的, 创新的 intellectual a. 智力的 proposition n. 提议, 建议 strengthen v. 加强
过渡页
Transition Page
01
第3 页 第3 页
Text A Business-to-Consumer E-commerce
New words
confidently ad. 信赖地, 安心地 improvement n. 改进, 进步 physically ad. 实体上的 promotion n. 促进, 促销 rapidly ad. 快速地 software n. 软件 suitable a. 适合的, 相配的 virtual a. 虚拟的
随着消费者越来越习惯于在线购买产品,其他产品类别 将会越来越nsumer E-commerce
Analysis of sentences
第9 页
Some experts believe that, in the long term, this type of businesses should be more successful than pure e-commerce businesses.
第4 页
Text A Business-to-Consumer E-commerce
电子商务英语unit2
24, 2014
5
Text Analysis
A Brief Introduction to Electronic Commerce
Electronic Commerce and Electronic Business [1] Many people think the term “electronic commerce” (EC) means shopping on the Internet. However, electronic commerce also includes many other activities, such as businesses trading with other businesses and internal processes that companies use to support their buying, selling, hiring, planning and other activities.(译文)
What are the differences between EC models and traditional business models? Which one do you prefer, traditional models or EC models? Why?
April 24, 2014
April 24, 2014
7
Text Analysis
Classification of EC A common classification of EC is by the types of entities participating in the business processes. (译文) The following types of EC [2] are commonly distinguished.
Lesson 2 E-commerce Business Models

3
1. E-commerce Business Models
1. E-commerce Business Models
Eight Key Elements of a Business Model
2. Major Business-to-Consumer (B2C) Business Models 3. Major Business-to-Business (B2B) Business
5
Key Elements of A Business Model
Components
Value proposition Revenue Model Market opportunity Competitive environment
Key Questions
Why should the customer buy from you? How will you earn money? What marketspace do you intend to serve, and what is its size? Who else occupies your intended marketspace?
6
Key Elements of A Business Model
Components
Competitive advantage Market strategy
Key Questions
What special advantages does your firm bring to the marketspace? How do you plan to promote your products or services to attract your target audience? What types of organizational structures within the firm are necessary to carry out the business plan? What kinds of experiences and background are important for the company’s leaders to have?
Introduction to E-Commerce Chapter 2

E-commerce BusinessINSIGHT ON TECHNOLOGYSEARCH, ADS, AND APPS: THE FUTURE FORGOOGLE (AND MICROSOFT)When the Web was first invented,no one envisaged that by 2008online search would grow to a morethan $10 billion dollar business. In fact, early pundits thought that online search would be a commodity business, at best a small niche player in e-commerce. But in 2008, with paid search spending comprising more than 40% of the U.S. online advertising market, and paid search ad spending growing at around 20% a year over the past several years, the search engine market is booming, along with the larger Internet advertising marketplace now estimated at about $26 billion. About 85% of Internet users in the United States use a search engine at least once during a month. The top ten search engines in May 2008 conducted an estimated 7.8 billion searches, an average of about 250 million a day. No one knows the ultimate demand for search on the Web, but as the cost (both in terms of money and time) of searching declines, and the power of search engines increases, it is now apparent that search will be a major Web-based industry driven in large part by advances in technology. What is less apparent is who exactly will dominate this marketspace and what role technology (as opposed to marketing muscle or economics) will play in the ultimate outcome. Where’s the money in search? A related question is how many search engines will remain when the competition is over.Today, five Web sites account for over 95% of all Web searches: Google (59.3%), Yahoo (16.9%), MSN/Windows Live Search (13.3%), AOL (4.1%), and (2.1%). The real powerhouses of search are Google and Yahoo, which provide over 75% of all searches. Microsoft unveiled its own proprietary search technology in February 2005, and has made some progress at the expense of Yahoo and .AOL does not have an independent search capability but instead purchases all of its search results and online ads from Google.Of these firms, Google stands out as the only “pure” search engine for which search is the major line of business, whereas the other firms are either content portals (Yahoo and AOL) or, in the case of Microsoft, the provider of 95% of the world’s desktop computer operat-ing systems. In 2004, Google became a public company, greatly expanding its capital foundation to support further growth. Google’s securities filings with the Securities and Exchange Commission show just how profitable the search business has become. In 2007, Google reported revenue of $16.6 billion, 99% of which it derived from various forms of search-based advertising. Google’s net income (profit) was $4.2 billion. While Google started out as a search company with unique technology as the basis of its business model, search and search engine advertising growth have started to slow somewhat (from 100% annual increases, to 20% in 2007, and an estimated 15% in 2011). In response, Google is turning into a three-play company: search, advertising, and apps (applications).Leadership in the search engine industry has changed hands several times. In the first round of the search engine wars, the original keyword search engines such as Alta Vista were replaced by Google, which claimed to possess superior technology, and Yahoo, which offered content, not just search. In the second round, an upstart firm named exploded onto the scene and created the marketplace for paid placement on search engines. Rather than be at the mercy of obscure search engine ranking rules, pay-for-placement allowed firms to pay for(continued)a top ranking, and then pay only when they received a click. grew to become and in a few years equaled the size of Google. Overture was purchased by Yahoo in 2003.Google achieved its early and powerful lead in the search business through superior software technology, a highly efficient computer hardware architecture, and excellent Web site design. Google was started in 1998 by two enterprising Stanford grad students, Sergey Brin and Larry Page, who were studying data mining and the process of analyzing data for patterns. That research later became the basis of their business, Google, which can search millions of Web pages in less than a second. Early search engines like Alta Vista (which once had 90% of the search market) merely counted how many times a search term appeared on a given Web page to determine where to rank a particular page. If you searched on “iPhone,” Alta Vista would show you pages ranked in terms of the number of times the Web site’s home page, and other pages, contained the word “iPhone.” Google’s search, on the other hand, uses the popularity of Web pages as themost important crite-ria for ranking pages,as well as the page con-tent. The more other Webpages link to a particularpage, the higher it jumpsin Google’s rankingstructure called Page-Rank. This is called “linkanalysis” and is runindependently of the querybeing made. Once all theWeb’s indexed pages areranked, Google alsofactors in other informa-tion, such as the textcontent of a page, its link structure, proximity of search words to one another on the page, fonts, heading, and text of nearby pages. The company uses a number of software algorithms to carry out each search, drawing on the power of an undisclosed number of servers (rumored to be anywhere from 100,000 to 450,000) located in server “farms” through-out the world. Some people believe Google has the largest computing system in the world.It is unclear if Google can maintain its technological edge in search given the investments being made by both Yahoo and Microsoft, as well as the proliferation of several other smaller but popular search engines such as AOL (4% of searches) and (2% of searches). The original PageRank patent is owned by Stanford University, where it was created, and expires in 2017. Larry Page and Sergey Brin have an exclusive license until 2011, after which time their license is not exclusive. The validity of that patent has not been tested and there are ways to design around it. The concept of analyzing a social network, and ranking the “influence of participants” in terms of who receives and sends the mostNOT AVAILABLE FORELECTRONIC VIEWING(continued)communications (links) is hardly original to Google, but instead was a basic insight of sociologists in the 1950s who studied commu-nities as social networks. In the competition among search engines, it is clear that search alone is not the key ingredient, just the foun-dation for the winning hand. It’s a necessary but not sufficient condition for success.Google’s strategy has been to extend its advantages in search into two areas and try to “out-invent” the competition. These new areas are advertising and applications: in the words of CEO Eric Schmidt, Google is all about “search, ads, and apps.” It has extended search to include images, books, scholars, content, finance, and news. It has extended its advertising services through its AdWords and AdSense programs. AdWords is an auction program that allows advertisers to bid for placement on Google pages. AdSense allows Google to place ads on publisher Web sites (basically any Web site is a “publisher”Web site) based on the content of that site’s Web pages. Other services include Google Geo (maps, Earth, and local content), and Google Checkout (an online wallet).Google is also starting to push into Microsoft’s territory in the applications market. Google’s applications include Gmail, Docs and Spreadsheets, Calendar, Groups, Orkut (a social networking environment), and Blogger. In case you’ve missed the last two decades, most of these are “Office”applications where Microsoft currently has a near monopoly. Where to put Google’s $1.65 billion purchase of YouTube? Wall Street analysts have had a tough time with this question too. YouTube is all three: it’s an online application for storing and sharing videos; it’s a search system for videos; and it’s an advertiser’s dream come true: according to comScore, nearly 80 million users watched more than 3 billion user posted videos in Jan-uary 2008.While Google’s software applications may be popular, they have not yet turned into big money makers, and Microsoft still “owns” 95% of the world’s PC office envi-ronment. Almost all (99%) of Google’s rev-enue still comes from search and advertising (including AdWords and AdSense). And while Microsoft has invested billions developing its own search engine, so far it has gained only at the expense of AOL and , and seems stuck at about 13%-14% of the market (an improvement over previous years when it was below 10%). Google has increased its share of search a bit to 53% from 51%.In a “life imitates art” moment, both companies purchased advertising networks to help target banner ads within a month of one another. Google bought DoubleClick for $3.1 billion in April 2007, and Microsoft protested the purchase to the Department of Justice as “anti-competitive.” A month later, Microsoft bought aQuantive for $6 billion, the largest purchase in Microsoft history. Earlier in 2006, it bought in-game advertising pioneer Massive Inc. There’s just no shame among monopolists and oligopolists!The future portends an expensive battle among the world’s largest Internet technology titans for control of search, advertising, and applications on your PC. Stay tuned.SOURCES:"Nielsen Online Announces May U.S.Search Share Rankings," Nielsen Online,June 19,2008;eMarketer,Inc.,"US Online Advertis-ing:Resilient in a Rough Economy," by David Hallerman,March 2008;Google Inc.Form 10-K for the year ended December 31,2007 filed with the Secu-rities and Exchange Commission,February 15,2008;"YouTube Looks for the Money Clip," by Yi-Wyn Yen,Fortune,March 25,2008;“Google Keeps Tweaking Its Search Engine,”by Saul Hansell,New York Times,June 3,2007;“Out of Chaos,Order.Or So Google Says,”by Miguel Helft,New York Times,May 11,2007;“Is Google Too Powerful,”by Rob Hof,BusinessWeek,April 9,2007;“Google Looks To Boost Ads with YouTube,”by Kevin Delaney,New York Times,October 10,2006.INSIGHT ON BUSINESSONVIA EVOLVESFew e-commerce start-ups reflectthe nimble behavior of entrepre-neurial firms better than Onvia.Founded in 1996 by Vancouver entre-preneur Glenn Ballman, Onvia started out as a market hub or exchange aimed at helping the 15 million small businesses in America shop for the best deals on products and services. Starting out at home, Ballman created a Web site where small businesses could buy and sell products, access small business information, and purchase business software. Originally called , in 1998 Ballman moved to Seattle in part to attract venture capital funding, and renamed the company (in Latin, “on the road”). After several rounds of venture capital investment that accumulated to more than $71 million in 1999, Onvia went public in March 2000, at the offering price of $21, raising an addition $240 million.By 2000, Onvia had over a million small business users, andthousands of suppli-ers, and also hadbuilt strategic rela-tionships with Visaand AOL to build co-branded Web sitesfor the small busi-ness market. But thecompany remainedu n p r o f i t a b l ebecause, like somany other exch-anges, it could notattract enough sup-pliers willing tocompete against oneanother in an openmarketplace. This reduced the goods and services available in the marketplace and reduced trading volume. Because Onvia made money only when goods were exchanged, Onvia revenues never achieved a profitable level. By December 2000, Onvia had laid off over 200 employees, and its stock sank to $1, the delisting price for stocks on NASDAQ.Not one to give up easily, founder Ballman initiated a recovery plan. He sold off Onvia’s online purchasing of software, hardware, and business products to a competitor, F irstsource Corporation, retaining only the Onvia procure-ment network that matches buyers and sellers. Then the company completely switched markets from the small business service market to the gov-ernment procurement and service market. In this new marketspace, Onvia planned to provide procurement services to local, state, and federal government agencies and feed sales leads to small businesses wanting to serve that market.(continued) NOT AVAILABLE FORELECTRONIC VIEWINGSOURCES :“About Onvia,”,July 7,2008; Inc.Form 10-Q for the quarter ended June 30,2008,filed with the Securities and Exchange Commission on August 13,2008;“Onvia's Quarterly Revenue Grows 10% Over Q1 2007,”Onvia,Inc.,April 29,2008; Inc.Form 10-K for the fiscal year ended December 31,2007,filed with the Securities and Exchange Commission on March 31,2008.In March 2001, Onvia purchased DemandStar Inc., a leading provider of buyer-side business-to-government platforms that had over 270government agency subscribers. In June 2001,Onvia purchased ProjectGuides, the nation’s largest online bid gathering and distribution service. This acquisition permitted the company to greatly increase the flow of bids from agencies into the marketplace. It also began compiling a proprietary database, called Onvia Dominion,that now contains 5 million procurement records,275,000 vendor profiles, and coverage of more than 78,000 government purchasing offices nationwide. In 2005, the company introduced Onvia Business Builder, a business intelligence tool that allows companies to mine the Onvia Dominion database for information relevant to their business, and in 2006, added Onvia Navigator, an enhanced search tool for the database. In February 2008, Onvia launched yetanother new product, Onvia Planning and Con-struction, which expands its solutions for thecommercial and residential development market.Onvia makes money by charging clients a sub-scription fee for access to its products and serv-ices, by licensing its content to third parties who then resell the data, and by selling cus-tom market information reports.The changes in its business model have enabled Onvia to regain stability, although it is not yet profitable. During the period from 2002to 2007, revenue almost tripled, from $7 million to over $20 million, and in 2007, Onvia recorded its first annual net profit.. As of June 2008,Onvia had approximately 8,100 clients with an annual contract value of approximately $18.2million. According to Mike Pickett, Onvia’s Chairman and Chief Executive Office, Onvia is very pleased with its progress. In 2008. Onvia jumped from 120th to 26th in the Seattle Times 2008 rankings of Northwest businesses. It appears that Onvia has finally discovered a viable business model. Onvia’s stock currently sells in the $4–$6 range.product and service, such as marketing-related, financial, or computing services Forexample, Exostar is an online trading exchange for the aerospace and defense industry,founded by BAE Systems, Boeing, Lockheed Martin, Raytheon, and Rolls-Royce in2000. Exostar connects with over 300 procurement systems in 20 different countriesand has registered more than 40,000 trading partners worldwide.Y ou’re walking past the local PizzaHut and your cell phone rings. Who’scalling? No, it’s not your significantother or a parent or friend. It’s Pizza Hut. They just wanted to let you know that pizzas are on sale—two for one, until 6 P.M. today. Want to find out someone’s address when you know the home phone number and then get a map to that location? Go to Google and enter that person’s phone number. The top listing will provide you the name and address of the owner of that phone number. Click a button and you will get a map to the house or business. Google calls it PhoneBook, but it never asked you to join. Y ou could opt out if you search hard enough. Or let’s say you want to set up a wireless network in your house using Wi-Fi (short for an 802.11b radio network). Y our neighbor will possibly be able to pick up your signals (and network traffic) if they are within 300 feet of your base station and “join” your network.These scenarios are not far-fetched, but instead represent capabilities of existing technology. Some of these capabilities have benign or even humanitarian intentions. For instance, since Octo-ber 2001, all cell phone providers are required to implement “E911” (Emergency 911), in which your cell phone’s embedded GPS chips (global posi-tioning system chips) can be tracked by emergency responders or law enforcement even if the phone is not turned on, and to automatically track the loca-tion of phones that are turned on. In true emergen-cies, these capabilities are helpful. If you are in an emergency and use your cell phone to call for help, authorities can find your location nearly instantly.But while the primary goal of these wireless tracking capabilities is enhanced public safety, companies are already developing business models centered on applications that will allow them to exploit the technology. Called “location-based services,” companies such as MapQuest work with local businesses to provide directions to restaurants, theaters, and other attractions over cell phones. And with around 255 million cell phone users in the United States today, there are significant business opportunities for telephone carriers, mapping services, and local businesses. In 2006, mobile advertising revenues totaled over $300 million and are expected to grow to over $2 billion by 2011.Proposals for the creation of a “wireless 411”cell phone directory creates cause for even greater concern. F or instance, in October 2006, Trans-Union, one of the major credit bureau companies, acquired Qsent, which is developing a new wireless 411 service. According to TransUnion, Qsent’s tech-nology is ready to go whenever cell phone providers decide to enable it. The service would requires sub-scribers to opt-in in order for their number to be included in the directory. However, such protection does not apply to a new cell phone directory being compiled by Intelius, which is also in the business of selling background checks online for a fee. Intelius’s directory, available for $15 per search, is based on data from marketing companies and public records.The specter of more unsolicited, unwanted phone calls coupled with “Big Brother”-like location tracking has privacy advocates raising the alarm. “Developing wireless technology shows many indications of repeating two privacy disasters of the wired Internet—spam and nonconsensual tracking,” said one privacy expert.The wireless industry, mindful of the privacy issues raised in the online e-commerce context, has issued calls for stringent self-regulation in an attempt to avoid government-imposed regulation.F or instance, the Mobile Marketing Association (MMA) has a Code of Conduct for wireless marketing campaigns, developed by an MMA board-appointed Privacy Advisory CommitteeINSIGHT ON SOCIETYIS PRIVACY POSSIBLE IN A WIRELESSWORLD?(continued)whose members included Cingular Wireless, Procter & Gamble, and VeriSign, among others. The MMA has also established a wireless anti-spam commit-tee. TRUSTe, a not-for-profit organization that operates an Internet privacy seal program, has Wireless Privacy Principles and Implementation Guidelines, drafted by a Wireless Advisory Commit-tee that included TRUSTe, AT&T Wireless, Microsoft, HP, the MMA, the Wireless Location Industry Association, and various consumer advocacy groups such as the Center for Democracy and Technology. The guidelines cover such topics as notice, third-party sharing of personally identifiable information, and the use of location-based informa-tion. Under the guidelines, wireless service providers are encouraged to provide a full privacy statement to the consumer prior to or during the collection of personally identifiable information, or upon first use of a service. They should only disclose that informa-tion to a third party for uses unrelated to the provision of services if the consumer has provided “opt-in” consent prior to such use. F inally, the guidelines state that wireless service providers should only use location information for services other than those related to placing or receiving voice calls if consumers opt-in. According to Verizon Wireless spokesperson Jeffrey Nelson, “We are more concerned with maintaining the relationship with our customers than with someone who wants to use their location information.”And what about government regulation? The 2003 CAN-SPAM Act requires the Federal Com-munications Commission to issue rules to protect wireless subscribers from unwanted mobile service commercial messages, and provides that consumers can list their cell phone numbers in the National Do Not Call Registry. In August 2004, in accordance with the CAN-SPAM Act, the FCC proposed regu-lations, most of which went into effect in October 2004. The F CC prohibits sending wireless commercial e-mail messages unless the individual addressee has given the sender express prior authorization. The F CC also created a publicly available FCC wireless domain names list with the domain names used for mobile service messaging so that senders of commercial mail could more easily determine which addresses are directed at mobile services.To date, wireless location-based services remain largely unregulated. The Wireless Com-munications and Public Safety Act (often called the “911 Act”) added the term “location” to the definition of customer proprietary network information (CPNI) held by telecommunication carriers, to make it eligible for certain privacy protections offered by the Communications Act of 1934. The 911 Act also required that the F CC establish rules regarding how telecommunications carriers treat CPNI. The F CC did so in July 2002, adopting an approach that requires an individual’s affirmative consent (opt-in) for some circumstances and assuming consent is granted unless an individual indicates otherwise (opt-out) in others. The Wireless Location Industry Association has also developed draft wireless policy standards for its members that combines an opt-in and out-out approach. Congress continues to debate how to protect wireless subscribers further, but thus far none have passed since CAN-SPAM in 2003. Will consumers be so enthralled with the idea of services tailored to their specific location that they won’t mind being tracked? Privacy watchdogs don’t think so and predict that any company whose business model is predicated on that assumption is underestimating the increasing sensitivity of the American public to privacy concerns.SOURCES:“Cellphone Directory Grabs Your Number,”by Tricia Duryee,Seattle Times,August 13,2007;“US Mobile Advertising and Search Markets,“Frost & Sullivan,July 24,2007;“World Telecommunication Indicators Database,”International Telecommunication Union,June 2007;“Wireless Location Tracking Draws Privacy Questions,“ Anne Broache,C/Net ,May 17,2006;“Wireless Privacy and Spam:Issues for Congress,”by Marcia S.Smith,CRS Report for Congress,December 22,2004;“FCC Seeks Comment on Rules to Eliminate Spam from Mobile Phones,”Federal Communications Commission Press Release, ,March 11,2004;“TRUSTe Announces First Wireless Privacy Standards to Protect Mobile Users,”TRUSTe Press Release,,;“Mobile Marketing Association Releases Code of Conduct for Wireless Campaigns,“ Mobile Marketing Association Press Release,,December 2,2003.Every industry can be characterized by a set of value-adding activities performed by a variety of actors.Internet technology enables firms to create an enhanced value web in cooperation with their strategic alliance and partner firms,customers,and direct and indirect suppliers.C A S E S T UD Y。
e_commerce chapter2

Business plan
Describes a firm’s business model
E-commerce business model
Uses/leverages unique qualities of Internet and
Web
Copyright © 2015 Pearson Education, Inc.
Slide 2-13
8. Management Team
“What kind of backgrounds should the
company’s leaders have?” A strong management team:
Can make the business model work
Slide 2-12
7. Organizational Development
“What types of organizational
structures within the firm are necessary to carry out the business plan?”
Describes how firm will organize work
Slide 2-14பைடு நூலகம்
Raising Capital
Seed capital Traditional sources
Incubators
Commercial banks
Angel investors Venture capital firms Strategic partners
E-commerce Business Models and Concepts
《电子商务英语》-Unit_2
wide adj. 宽的 4注解:speed v& n.
v. 加快,(使某事物)加速 n. 速度,快速
Text A The Internet allows direct access to information, products, and services, which cuts out middlemen and causes economic deflation. 通过互联网可以直接获得信息、产品以及服务,避免了 中间环节,节省了开支。 4注解:cut out 去除,删除 deflation n. 通货紧缩
Text A Because the business centers around the Internet, be sure to discuss the management team's level of Internet expertise and where they gained it.
the competition 竞争者; 对手
Text A The company must also get the word out about its web site by adopting submission to database ...... 公司还必须把网址提交到搜索引擎的数据库中并且在公 司发送的所有电子邮件的末尾添加URL,从而广泛宣传 其网址。 4注解:get the word out 宣传,广而告之 adopt v. 采取,采纳 submit v. 提交,递交 submit a resignation 提交辞呈 v. 屈服,服从
(1)外形,轮廓。
He saw the outline of a house against sky. (2)提纲,大纲,概要。 an outline of European History
Chapter-2-E-commerce-business-models电子商务模式PPT课件

.
Slide 2-7
Question 3: how viable(切实可行) is each business model? Explain your answer.
Answer:
1) put yourself into it; make a decision, choosing your favorable business model;
▪ defined by the revenue potential in each of the market niches where you hope to compete
▪ Marketspace
▪ the area of actual or potential commercial value in which a company intends to operate
▪ Questions?
▪ Why will customers choose to do business with your firm instead of another company? (KOZMO)
▪ What will your firm provide that other firms do not and cannot?
▪ E-commerce revenue models include:
▪ advertising ▪ subscription ▪ transaction fee ▪ sales ▪ Affiliate ▪ What else?
.
Slide 2-14
Eight Key Ingredients of a Business Model: (2) Revenue Model
电子商务 E-commerce_model_and_architecture

Community model – discussion site or information sharing site that based on user loyalty. Revenue is generated by sale of ancillary products and services, e.g. Red Hat.
Advertising model – provide contents and services mixed with advertising messages.
Portal, e.g. YNYTimes Digital Query-based placement, e.g. Google Contextual advertising, e.g. Gator
Merchant model – wholesales or retailers of goods and services.
Virtual storefront, e.g. Amazon Catalog merchant, e.g. Land’s End Click and mortar, e.g. Barnes & Noble Bit vendor, e.g.
Business
Consumer
Category of EC models
Brokerage model – market-maker that bring together buyers and sellers and facilitate transactions.
Marketplace exchange, e.g. ChemConnect Reverse auction site , e.g. Auction site, e.g. e-Bay Transaction broker, e.g. PayPal Virtual marketplace, e.g.
电子商务(英文版)课后作业及答案

电子商务(英文版)课后作业及答案Chapter1 Introduction to Electronic Commerce1、One definition :Electronic CommerceThe The electronic electronic electronic commerce commerce commerce is is is used used used in in in its its its broadest broadest broadest sense sense sense and and and includes includes includes all all business activities that use Internet technologies. 2、Three important thinking points :Business Models, Revenue Models, Business ProcessBusiness Business model model model is is is a a a set set set of of of processes processes processes that that that combine combine combine to to to achieve achieve achieve a a a company’s company’s primary goal which is typical to yield a profit. Revenue Models is a specific collection of business processes used to identify customers, market to those customers, and generate sales to those customers. The idea is helpful for classifying revenue-generating activities for communication and analysis purposes. Business processes include purchasing raw materials or goods for resale, converting materials and labor into finished goods, managing transportation and logistics, hiring and training employees, managing the finances of the business, and many other activities.3、Three theoretical points: Value chains, Strategic alliance and SWOTValue chains is a way of organizing the activities that each strategic business unit undertakes to unit undertakes to design, produce, design, produce, promote, market, deliver, and support the products or service it sells. Strategic alliance is the relationship that companies coordinate their strategies, resources, and skill sets by forming long-term, stable relation with other companies and individuals based on shared purpose. SWOT analysis is including strengths, weaknesses, opportunities and threats. It’s It’s one one one popular popular popular technique technique for for analyzing analyzing analyzing and and and evaluating evaluating evaluating business business business opportunities. opportunities. The analyst first looks into the business unit to identify its strengths and weaknesses. Then the analyst reviews the environment in which the business unit operates and identifies opportunities presented by that environment and the threats posed by environment. Chapter2 Technology I nfrastructure: Infrastructure: T heThe Internet and the World Wide Web 1、P92 Review Questions 5P57 P57 Intranet Intranet Intranet and and and Internet Internet Internet compared, compared, compared, it it it can can can be be be said said said that that that the the the Internet Internet Internet is is is a a worldwide network and intranet is the implementation of Internet technology in the in-house, it can with little cost and time will enterprise internal information from from a a a large large large number number number of of of resources, resources, resources, reasonable reasonable reasonable transfer transfer transfer to to to everyone. everyone. everyone. Intranet Intranet Intranet for for enterprise provides a can make full use of the communication lines, economic and effective effective to to to establish establish establish intranet intranet intranet scheme scheme scheme and and and Intranet Intranet Intranet applications, applications, applications, enterprises enterprises enterprises can can effectively carry on financial management, supply chain management, inventory management, customer relationship management and so on. Chapter3 Selling o non the Web: Revenue Models and Building a Web Presence P174 Review Questions 3P158 Channel Channel conflict conflict conflict refers to refers to the activities that a member of a channel channel is is engaged in or is not conducive to the organization to achieve its own goals, and then all kinds of contradictions and disputes. Distribution channel channel design is design is the channel members in different angles, different interests and different methods and so so on, on, on, under under under the the the influence influence influence of of of many many many factors; factors; factors; therefore, therefore, therefore, the the the channel channel channel conflict conflict conflict is is inevitable. To To resolve resolve resolve conflicts conflicts conflicts through through through persuasion persuasion persuasion is is is to to to use use use leadership. leadership. leadership. In In In essence, essence, persuasion persuasion is is is the opportunity to the opportunity to c ommunicate with the channel communicate with the channel members of the conflict, which emphasizes the influence of the behavior rather than the information sharing, but also in order to reduce the conflict caused by the division of labor. The goal of the negotiation is to stop the conflict between members. Compromise may avoid conflict, but it can't solve the root cause of the conflict. exist, it will eventually lead to conflict. In As long as the pressure continues to fact, negotiation is a method of channel members to bargain. In the course of the negotiations, each member will give up some things to avoid the conflict, but the use of negotiation or persuasion to see members of the communication skills. In fact, when the conflict is resolved by the above method, each member needs to form an independent strategy to ensure that the problem can be solved. Chapter4 Marketing on the Web1、Two Market Strategies (Web Market Segmentation)4Cs of MarketingAimed at consumer demand. We must first understand (NEED CONSUMER'S) A imed at consumer demand. We must first understand study and analyze the needs and desires of consumers, rather than to consider what companies can produce products. (COST) The cost that the consumer is willing to pay. First of all, we should understand consumers to meet the needs and desires are willing to pay much money, rather than to make the price of the product, that is, to the consumers to how much money. (CONVENIENCE) Consumer convenience. Products should be taken into account how to facilitate the use of consumers. (COMMUNICATION) Communication with consumers. To the consumer as the center of the implementation of marketing communication is very important, through interaction, communication and other means, the enterprise internal and external marketing integration, the customers and the interests of both sides of the enterprise together.4Ps of MarketingPRODUCT: pay attention to the development of the functional requirements of the product has a unique selling point, the functional requirements of the product in the first place. PRICE: according to the different market positioning, the development of different pricing strategies, product pricing is based on the company's brand strategy, focusing on the gold content of the brand. (PLACE)Distribution: enterprises do not directly to consumers, but to pay attention to the cultivation of the dealer and the establishment of sales network, business and consumer contact is through the distributors to carry out. PROMOTION: enterprises focus on changing the sales behavior to stimulate the consumer, in order to promote the growth of consumer spending in the short term, to attract other brands of consumers or lead to advance consumption to promote sales growth. Market SegmentationNetwork market segmentation refers to enterprises on the basis of investigation and study, according to the network consumer desire to buy, purchase motivation and habits of different, the network marketing is divided into different types of groups, each consumer group constitutes the enterprise of a market segment. Funnel modelThe five tier of the funnel corresponds to each link of the enterprise's search marketing, which reflects the number and loss of customers from the display, click, access, and consultation until the order process is generated. From the maximum amount of the show to the minimum order quantity, this layer of the process of narrowing that there are customers for a variety of reasons to leave, to lose interest in the business or to give up. 2、Several Market TechniquesWeb AdvertisementsWeb Advertisement typesW eb advertising (including Banner, Button, huge vertical edges, etc.) Text link advertising Email advertising Button advertising Sponsorship Advertising combined with content Interstitial ads Home page advertisement Keyword advertising E-mail MarketingIt is a kind of network marketing means to transfer value information to target users through email, under the premise of user's prior permission. Email marketing has three basic elements: user license, e-mail delivery of information, information on the value of the user. Three factors, the lack of a, can not be called effective Email marketing. Email marketing is a direct way to communicate with customers by e-mail. At the same time, it is also widely used in the field of network marketing. E-mail marketing is one of the oldest online marketing practices, it can be said that email marketing than the vast majority of Web site promotion and Internet marketing practices are to be old. Technology-enabled customer relationshipClickstreamClick stream analysisClick stream the concept of pay more attention to the users browse the web site of the entire process, the web log records the user clicks as is figure of "point", and click stream is more like the "point" string together to form the "line." Can also be the point that is the site of the Page, and the line is to visit the site of the Session. So click on the flow of data is collected by the site log, which can contain more information than the web site log, so as to make the results based on click stream data more abundant and efficient. Searching engine positioning and domain names promotionpaid search engine placementIt is through the search engine optimization, search engine rankings and research key words popularity and relevance in the search engine results page to obtain a higher ranking of marketing tools. Search engine optimization of website ranking is very important, because search engine in by crawler or spider) program to collect web data, according to the complex algorithm (each search engine ranking algorithm and method is not the same) to determine the page for a search term correlation and decide the ranking of. When the customer in the search engine to find related products or services, it is through the professional search engine optimization page usually can get a higher ranking. 3、Online brandingAffiliate marketing 关联营销Affiliate marketing is a built in mutually beneficial mutual benefit based on marketing, in cross marketing (cross marketing is refers to the time, money, ideas, activities or presentation space resources integration, for any business to provide a channel for the low cost and to contact more potential customers a marketing method) based on, will be what things, products and brand marketing for relevance, to achieve deep multi guide. At the same time, the related marketing is also a new, low-cost, enterprise in the website to improve the income of marketing methods. Affiliate marketing is sometimes called tying marketing, the current association of sales in many stores have started to use the. Viral Marketing Strategies 病毒营销Viral marketing is refers to the through similar pathology and computer virus transmission modes, namely self-replicating viral propagation process, using existing social networks to enhance brand awareness or to other marketing purposes. Viral marketing is started by the information source, relying on user spontaneous word-of-mouth publicity; achieve a fast roll snowball communication effect. It describes a information transfer strategy, economics known for viral marketing, because this strategy like a virus, transmit information to thousands, hundreds of audience by rapid replication. 。
电子商务专业英语课后答案.doc

Chapter 1 Introduction to E-CommerceANSWER1.Answer the following questionsL business-to-consumer, business-to-business, business processes, consumer-to-consumer, and business-to-government2.A business model is a set of processes that combine to achieve a company's goal, which is to yield a profit.NO.3.A revenue model is a specific collection of business processes used to identify customers, market to those customers, and generate sales to those customers.4.books and CDs, etc.5.Transaction costs are the total of all costs that a buyer and seller incur as they gather infonnation and negotiate a purchase-and-sale transaction.6.As more people or organizations participate in a network, the value of the network to each participant increases. This increase in value is called a network effect.7.The key issues that any company faces when it conducts international commerce include trust and culture, language, infrastructure, international law and currency.8.Localization means a translation that considers multiple elements of the local environment, such as business and cultural practices, in addition to local dialect variations in the language・II.Fill in the blanks in each of the following1.Internet2.dot-com pure dot-com3.internationalmodity5.electronic traditional6.vertical integration.rmation coordination8.value chainChapter 3 E-Business ModelsI.a) True b) False. This is the concept of a true auction. c) False・ A reserve price is the lowest price a seller will accept in an auction・ d) True e) False. The name-your price model allows customers to get Chapter 1 Introduction to E-Commerce 115a lower price by clearing the price with a number of vendors・ This does not involve an auction. f) False. Brick-and-mortar business are offline businesses・ This term is often associated with companies who have both and online and offline presence・ g) False. Web-based training is currentlyused by organizations around the world, h) True i) True j) TrueII.a) Brick-and-mortar b) Demand sensitive pricing model c) shopping cart d) auction e) vertical, horizontal f) community g) reverse auctions h) B2B exchanges i) online trading j) comparison shopping III.Categorize each of the following items as it best relates to the storefront model, the auction model or the dynamic pricing models:a)Auction model b) Auction model c) Storefront modeld) Storefront model e) Dynamic pricing・ f) Dynamic pricingChapter 4 B2B E-CommerceI.Write an Abstract of this paper in about 100 words.Abstract- Just as the industrial revolution mechanized the manufacturing functions of firms, the infonnationrevolution is automating their merchant functions. Four types of potential productivity gains are expected frombusiness-to-business (B2B) electronic commerce: cost efficiencies from automation of transactions, potentialadvantages of new market intermediaries, consolidation of demand and supply through organized exchanges, andchanges in the extent of vertical integration of firms. The article examines the characteristics of B2B onlineintermediaries, including categories of goods traded, market mechanisms employed, and ownership arrangements,and considers the market structure of B2B e-commerce.II.Answer the following questions1.The popular phrase B2B e-commerce refers to the substitution of computer data processing and Internet communications for labor sendees in the production of economic transactions.2.Expectations about productivity gains from B2B e-commerce can be usefully divided into four areas: possible efficiencies from automation of transactions, potential economic advantages of new market intermediaries, consolidation of demand and supply through organized exchanges, and chcinges in the extent of vertical integration of companies.3.Intermediaries can reduce transaction costs relative to direct exchange, by reducing the costs of search, certifying product quality, mitigating communication costs, and providing guarantees for buyer or seller commitments・4.E-commerce intermediaries can be classified into four main categories: brokers, auctioneers, dealers, and exchanges. 116电子商务专业英语(第二版)III.State whether the following are True or False?l.T 2.T 3.F 4.T 5.TChapter 5 Electronic Payment SystemsANSWERI.Answer the following questions1.List five parties may be involved in the e-payment method・They are:a)Customer/payer/buyer. The party making the e-payment in exchange for goods or servicesb)Merchant/payee/seller. The party receiving the e-payment in exchange for goods and servicesc)Issue匚The banks or nonbanking institutions that issue the e-payment instrumentused to make the purchased)Regulator. Usually a government agency whose regulations control the e・paymentprocesse)Automated Clearing House (ACH). An electronic network that transfers moneybetween bank accounts2.List Characteristics of Successful E-payment Methods Interoperability and portability; security; anonymity; divisibility; easy of use; transaction fees; critical mass・3.What are virtual credit cards?This is an e-payment system in which a credit card issuer issues a special number that can be used in place of regukir credit card numbers to make online purchases・ This allows users to use a credit card online without having to disclose the actual credit card number.4.Describe the difference between the contact card and contactless card・A contact card is inserted in a smart card reade匚These cards have a small gold plate about one -half inch in diameter on the front; when the card is inserted in the reader, the plate makes electronic contact and data are passed to and from the chip.In addition to the chip, a contactless card has an embedded antenna・ In this case, data (and applications) are passed to and from the card through the card's antenna to another antenna attached to a cardreader unit or other device.5.List Advantages of E-billingChapter 1 Introduction to E-Commerce 117From the perspective of the billing firm, the most obvious benefit is the reduction in expenses related to billing and processing payments・ E-billing also enables better customer service. Another advantage relates to advertising.From the customer's perspective, E-billing reduces the customer^ expenses by eliminating the cost of checks, postage, and envelopes. E-billing simplifies and centralizes payment processing and provides better record keeping.II. Fill in the blanks in each of the following1.Credit cards, Charge cards, Debit cards2.e-wallet3.smart card, microprocessor, memory, nonprogrammable4.Stored-value5.e-check6.electronic bill presentment and payment (EBPP)Chapter 6 E-Commerce Security ANSWERI.Answer the following questions1.Describe the difference between a nontechnical and a technical cyber attack.Nontechnical attacks are those in which a perpetrator uses chicanery or other forms of persuasion to trick people into revealing sensitive information or performing actions that can be usedto compromise the security of a network.. These attacks are also called social engineering attacks. In contrast to nontechnical attacks, software and systems knowledge are used to perpetmte technical attacks ・ In conducting a technical attack, an expert hacker often uses a methodical approach ・2.How are DDoS attacks peipetrated?Once an attacker has access to a large number of computers, they load the specialized DDoS software onto these computers. The software lays in wait, listening for a command to begin the attack. When the cominand is given, the distributed network of computers begins sending out requests to the target computer. The requests can be legitimate queries for information or can beveryspecialized computer commands designed to overwhelm specific computer resources.3.What are the major forms of malicious code?Viruses, Worms, Macro viruses and macro worms, and Trojan Horses.4.What are some common mistakes that EC sites make in managing their security?Undervalued information. Few organizations have a clear understanding of the value of specific information assets.Narrowly defined security boundaries. Most organizations focus on securing their internal networks and fail to understand the security practices of their supply chain partners.Reactive security management. Many organizations are reactive rather than proactive focusing on security after an incident or problem occurs.Dated security management processes. Organizations rarely update or change their security practice to meet changing needs. Similarly, they rarely update the knowledge and skills of their staff about best practices in information security.Lack of communication about security responsibilities. Security often is viewed as an IT problem, not an organizational one.Chapter 1 Introduction to E-Commerce 1195.Describe the difference between physiological biometrics and behavioral biometrics・ Physiological biometrics are based on measurements derived directly from different partsof the body (e.g., sea ns of fingerprints, the iris, hand geometry, and facial characteristics)・ In contrast, behavioral biometrics are derived from various actions and indirectly from various body parts (e.g., voice scans or keystroke monitoring ).6.Describe the basic components of encryption・All encryption has four basic parts: the plaintext, ciphertext, encryption algorithm, and the key.7.What are the basic differences between symmetric and asymmetric encryption?In a symmetric (private) key system the same key is used to encrypt and decrypt the plaintext. The sender and receiver of the text must share the same key without revealing it to anyone else——thus making it a so-called private system.Public (Asymmetric) key encryption uses a pair of matched keys—a public key that is publicly available to anyone and a private key that is known only to its owner.8.What is a personal firewall?Personal firewalls are designed to protect desktop systems by monitoring all the traffic that passes through the computer\ network interface card.Chapter 7 PricingI.True or FalseI.F 2.T3. F4.T5. FII.Fill the blanks1.Target-return pricing2.internd content is easy to package; of the low friction between buyers and sellers; the cost of adding new customers is low3.frenzy pricingIII.Answer the following questions1 ・ Identify the six results of the interactivity force of the Internet on pricing・(1)It is easier to reach wider audiences.(2)It is easier and cheaper to implement dynamic pricing strategies・(3)It is easier and cheaper to change prices・⑷ It is cheaper for consumers to investigate prices. 120 电子商务专业英语(第二版)(5)It is easier to understand and measure consumers? reactions to price promotions・(6)It is easier to receive customer feedback on price, understand customer willingness to pay for a product, and implement price scrimin at ion strategies.2.In what ways has the individualization force of the Internet affected pricing?(1)By informing companies of their pricing and product desires, consumers make it easier for firms toconvey prices of products in which they have an interest・(2)Customers can register their preferences with firms, making it easier for those finns to offer targeted, individualized pricing promotions・(3)Customers can more easily participate in dynamic pricing processes. Sites that practice dynamic pricing can notify customers via e-mail when their bids are no longer the highest.3.What is a loss leader? What types are most likely to be used?A loss leader is an item offered at very low prices (below its total cost) in order to attract greater store traffic. Typically, such items are well-known brands, staples for price-sensitive consumers, and/or seasonal/holiday/special demand items.4.Describe the two primary ways that the Internet has enhanced the attractiveness of dynamic pricing. First are decreased menu costs. Menu costs are the costs associated with changing the price of a good. For goods advertised on the Web, it is easy and virtually costless to change product prices, making it very attractive for firms to change their prices based on demand and supply conditions. Second is interactivity. The Internet makes it easy for sellers and buyers around the world to interactand negotiate prices. The fact that buyers and sellers can easily interact from their homes or workplaces via the Internet makes it easy to conduct dynamic pricing structures.Chapter 8 Internet MarketingI.Answer the following questions1.What is Internet marketing?Internet marketing is the process of building and maintaining customer relationships through online activities tofacilitate the exchange of ideas, products, and services that satisfy the goals of both parties.2.What are the seven stages of Internet marketing?The seven stages are (1) setting corporate and business-unit strategy, (2) framing the market opportunity, (3)formulating the marketing strategy, (4) designing the customer interface, (5) designing the marketing program, (6)crafting the customer interface, and (7) evaluating the results of the marketing program.3.What are the four stages of the customer relationship?The four stages are: (1) awareness (the degree to which the customer has some basic information, knowledge, Chapter 1 Introduction to E-Commerce 121or attitudes about a firm or its offerings, but has not initiated any communications with the firm);(2)exploration(customer and firm begin to initiate communications and actions that enable an evaluation of whether or not to pursuea deeper connection); (3) commitment (customer and firm feel a sense of obligation or responsibility for each other);and (4) dissolution (isolation of the most valuable customer group and subsequent focus on this particular group).4.What are the six classes of variables in the Internet marketing mix?The six variables are product, pricing, communication, community, distribution, and branding・5.What is the Marketspace Matrix?The Marketspace Matrix is a framework illustrating the levers that the Internet marketer may choose to use ateach stage of the customer relationship. These levers are the six classes of variables including product, pricing,communication, community, distribution and branding, and the stages of customer relationships are awaieness,exploration, commitment and dissolution.6.How do interactivity and individuality come into play in the design of the marketing program? Interactivity is the extent to which two-way communication flow occurs between the firm and customers; individuality refers to a consumer's personal experience with the firm. Both impact the design of all of the levers ofthe Internet marketing mix一price, market communications, and products and services・7.What are the critical success factors for the Internet marketing professional?The critical success factors are (I) customer advocacy and insight (marketing professionals need to strategicallycollect information from many disparate sources, create insightful customer mosaics, and effectively translate theminto marketing strategies and tactics); (2) integration (marketing professionals need to have an integrated or holisticview of the customer and the enterprise in order to create a uniquely advantaged strategic plan); (3) balanced thinking(marketing professionals need to be highly analytical and very creative in order to understand the strategic andtactical implications of the Internet); and (4) willingness to accept risk and ambiguity (marketing professionals needto retool themselves and their companies to enter into a whole new era of customer-centric marketing). 122电子商务专业英语(第二版)Chapter 9 Legal Issues of E■CommerceI.True or False1.T2.F3.T4.F5.T6. F7.T&FII. Answer the following questions1.List some of the ways that the Internet can be used to collect information about individuals.(1)By reading an inciividuaPs newsgroup postings(2)By looking up an individual5s name and identity in an Internet directory(3)By reading an individuaPs e-mail(4)By conducting surveillance on employees(5)By wiretapping wireline and wireless communication lines and listening to employees(6)By asking an individual to complete a Web site registration(7)By recording an individuaPs actions as they navigate the Web with a browser, usually using cookies2.List four types of intellectual property.There are four main types of intellectual property in EC: copyrights, trademarks, domain names, and patents.3.List the legal rights covered by a copyright.A copyright is an exclusive grant from the government that confers on its owner an essentially exclusive right to: (1) reproduce a work, in whole or in part, and (2) distribute, perform, or display ♦Itto the public in any form or manner, including the Internet. In general, the owner has an exclusive right to export the copyrighted work to another country.4.List the legal rights of a trademark owner.The owner of a registered trademai-k has exclusive rights to: (1) Use the trademark on goods and services for which the trademark is registered. (2) Take legal action to prevent anyone else fromusing the trademark without consent on goods and services (identical or similar) for which the trademark is registered.Chapter 10 LogisticsI.l.B 2.A 3. A 4.B 5.C 6.A 7.AII.Translations:1.物流是与时间有关的资源配置或是总供应链的战略管理。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
emerging areas of e-commerce. ▪ Understand key business concepts and
strategies applicable to e-commerce.
Slide 2-10
E-Commerce Business Models
Business model
a set of planned activities designed to result in a profit in a marketplace
Slide 2-7
Question 3: how viable(切实可行) is each business model? Explain your answer.
Answer: 1) put yourself into it; make a decision, choosing your
favorable business model; 2) what kind of style of the bookstore it will be if you
Business plan
a document that describes a firm’s business model
E-commerce business model
a business model that aims to use and leverage the unique qualities of the Internet and the World Wide Web. —— still profit!
How to discuss and answer?
1) what business model? Amazon: B2C; E-tailor and virtual merchant, and market-creator B&N: E-tailor; bricks and clicks; 2) core competencies: elaborate… 3) the role of Internet: importance is different;
Slide 2-2
Slide 2-3
Slide 2-4
Sample Case Analysis
Question 1: analyze both Amazon and B&N using the value chain and competitive forces models.
How to discuss and answer: 1) find out the concept of
Slide 2-11
Eight Key Ingredients of a Business Model
Slide 2-12
Eight Key Ingredients of a Business Model: (1) Value Proposition
▪ Defines how a company’s product or service fulfills the needs of customers.
▪ Questions?
▪ Why will customers choose to do business with your firm instead of another company? (KOZMO)
unfavorable one, discuss about its possibilities to make a living.
Slide 2-9
Learning Objectives
▪ Identify the key com
Answer: 1) investigate online to find out the current situation of these
two companies; 2) analyze why the situation happen? 3) make a reserved prediction or forecast. As for the
CHAPTER 2
E-Commerce Business Models and Concepts
Created by, David Zolzer, Northwestern State University—Louisiana Slide 2-1
Opening Case Study: who’s who?
were the owner? how would you improve the shopping experience?
Slide 2-8
Question 4: which company will dominate the book retailing industry? Explain it.
Slide 2-6
Question 2: compare and evaluate the business models used by Amazon and B&N. What are their core competencies? What role does the Internet play in each of these business models?
‘value chain’; 2) find out the ‘competitive
forces’ 3) give answers;
Slide 2-5
What to consider? 这两家企业的“五种竞争力”分别是什么?
1)供应商的讨价还价能力 2)购买者的讨价还价能力 3)潜在竞争者进入的能力 4)替代品的替代能力 5)行业内竞争者现在的竞争能力
