Role-Based Access Controls
第4讲 访问控制

RUID 25 EUID 18
RUID 25 EUID 25
UNIX Access Control Lists
modern UNIX systems support ACLs can specify any number of additional users / groups and associated rwx permissions ACLs are optional extensions to std perms group perms also set max ACL perms when access is required
enables privileged programs to access files / resources not generally accessible
应用于目录,表示只有目录中任何文件的所有者才可以重命名、移动或 删除该文件
sticky bit
superuser
is exempt from usual access control restrictions
Access Control Elements
subject - entity that can access objects
a
process representing user/application often have 3 classes: owner, group, world
(Any program that is owned by, and SetUID to, the ―superuser‖ potentially grants unrestricted access to the system to any user executing that program)
Role-Based Access Control

Figure 11-1(a). Taxonomy of RBAC Models Figure 11-1(b). Taxomony of ARBAC Models (11) NetWare 4 as an Example ofRole-Based Access ControlJeremy Epstein, Cordant, Inc., and Ravi Sandhu, George Mason Universityjepstein@, 11400 Commerce Park Drive, Reston VA 22091sandhu@, Department of Information and Software Systems Engineering,Fairfax, VA 220301.0IntroductionIn [SAND96a], the second author describes a taxonomy of role-basedaccess control (RBAC) models, divided into four classes shown inFigure 11-1(a), Taxonomy of RBAC Models . A complementary set ofmodels is used for administrative role-based access control (ARBAC), asshown in Figure 11-1(b), Taxonomy of ARBAC Models . In this positionpaper, we describe how the RBAC and ARBAC models can be partiallyimplemented using unmodified NetWare 4 servers.2.0NetWare Access Control PoliciesNetWare includes two major types of objects with separate but interrelatedsecurity policies. NetWare Directory Services (NDS) objects representabstractions such as users, roles, groups, and computers, while file systemobjects provide a traditional hierarchical file system. Both file and NDSobjects are supported by sophisticated access control mechanisms thatallow assignment of rights to users, groups, and other entities. In addition,they allow rights assignments to be inherited in a hierarchical fashion.Most importantly, they allow assignment of access rights in a granularfashion: rights to a file or directory can be controlled independently fromThe tree structure does not include anything akin to a “hard” link in a UNIX file system. However, objects of 1class Asias can be used to provide a symbolic link-like capability.Figure 11-2. Sample NDS Structurethe ability to change file or directory access rights. That is, a user can,through a role, be granted the ability to read, write, create, or delete fileswithout having any ability to share those files with others.2.1NDS Object Access Control PolicyNDS is an X.500-like system for managing data that represents anorganization's assets. Every object in NDS has a class, which is defined inthe schema . The schema contains approximately 20 built-in classes (e.g.,User, Organization), and can be extended by authorized users. Dependingon the class of an object, it will have one or more attributes , also known asproperties . Attributes are used to store information about some aspect ofan object. For example, an object of class User has attributes to representthe person's name, home directory, login script, etc. Some attributes aresecurity relevant (e.g., those relating to passwords) while others are not(e.g., the user's telephone number).NDS objects are organized in a tree, much as many file systems organizefiles and directories into a tree . NDS objects are either container objects,1which correspond to directories in a file system, or leaf objects, whichcorrespond to files in a file system. Whether an object is a container orleaf object is determined by its class, as defined in the NDS schema.Figure 11-2, Sample NDS Structure , shows an NDS structure that mightrepresent an organization. Objects are named by their complete path to theroot, starting at the leaf. For example, Sally.Finance.Acme is the completename of the left-most node in the tree.Users log in to NetWare servers by providing the name of their NDS Userobject. When presented with the proper password (and meeting otherrestrictions, such as an unexpired account), the user is logged in, and his or2her security equivalence list, which is used in calculating access rights, iscomputed as follows:All users are security equivalent to the pseudo-object named [Public].Users are security equivalent to all container objects in the path fromtheir User object to the root of the tree, designated [Root], includingboth themselves and [Root].Users are security equivalent to those objects to which they areexplicitly made security equivalent by the administrator.All rights in NDS are passed through security equivalence. Groupmembership is just one example of security equivalence, but does not playany special role (contrary to what is stated in [SCHA94]).Note that users cannot choose a subset of security equivalences to be usedfor a session: they gain all security equivalences. Thus, a given user maybe represented by several NDS User objects to reflect different uses of thesystem (e.g., as an administrator or as an ordinary user). The user wouldselect which NDS User object to use, depending on the task to beaccomplished.While NDS can be configured in many different ways, typicalconfigurations allow administrative users (but not ordinary users) to createand delete NDS objects in one or more containers. Administrative userscan usually modify the attributes of NDS objects that they are responsiblefor. Non-administrative users may be able to modify some of the attributesof their User objects, such as the Login Script or Telephone Numberattributes.2.1.1NDS Object Access Control AlgorithmEvery NDS object has an Access Control List (ACL), which is stored as anattribute of the NDS object. An ACL is a list of triples, where theelements of the triple are as follows:The subject name, which is either the name of an NDS object (e.g., aspecific User, Group, or Organization), or a pseudo-ID such as [Root],[Public], or [Inherited Rights Filter] (abbreviated IRF).Protected attribute, which for NDS object rights calculation is thereserved symbol [Entry Rights].Access rights, which is zero or more of Supervisor, Create, Delete,Rename, and Browse. The Supervisor right implies all other rights.An object O1's rights to object O2 is computed as follows:For each object O' to which O1 is security equivalent, compute therights for O' to O2 by searching from the root of the tree toward O2.2“Security equivalence” is a misnomer. Security equivalences are neither transitive nor reflexive.R, which is initially empty, represents the object rights O' has to O2.For each node N along the path, perform the following steps:-If N's ACL includes an entry with the subject name [InheritedRights Filter] and a protected attribute of [Entry Rights], thenremove all access rights from R except those listed in the IRF.-If N's ACL contains an entry with the subject name of O' and aprotected attribute of [Entry Rights], then set R to the accessrights for the entry.Union the value of R calculated in the first step for each O' together,yielding the rights of O1 to O2.This algorithm allows setting an ACL at one location in the NDS tree andallowing the rights to flow down using inheritance. For example, inFigure 11-1, if Edward.Acme has the Supervisor right to the Acme object,then he will have the Supervisor right (and therefore all rights) to allobjects in the NDS tree (unless they are blocked with an IRF). IfSally.Finance.Acme is made security equivalent to Edward.Acme, then shewill also have the Supervisor right to all objects. An alternate method is toassign Admin.Acme the Supervisor right to Acme, and makeEdward.Acme security equivalent to Admin.Acme. In this case,Sally.Finance.Acme would not gain the Superviso r right to Acme unlessshe is security equivalent to Admin.Acme (i.e., she does not obtain therights transitively through Edward.Acme).Note that groups are simply a particular case of security equivalence in thisscheme: assigning rights to an NDS Group object and making NDS Userobjects security equivalent to the Group object is no different thanassigning rights to any other class of NDS object and establishing securityequivalence of NDS user object to object of that other class.2.1.2NDS Attribute Access Control AlgorithmThe ACL for an NDS object is also used for NDS attributes, with thefollowing changes:The protected attribute can be either the name of a specific attribute(e.g., Home Directory) or the pseudo-attribute [All Properties Rights].The access rights are zero or more of Supervisor, Compare, Add or3Delete Self, Read, and Write. Note that the Supervisor attribute rightis different from the Supervisor object right.An object O1's rights to attribute A of object O2 is computed as follows:1.For each object O' to which O1 is security equivalent, compute therights for O' to all attributes of O2 by searching from the root of thetree toward O2. R, which is initially empty, represents the attributerights O' has to O2. For each node N along the path, perform thefollowing steps:3Add or Delete Self is one right, not two (i.e., the word “or” does not indicate there are two rights).a.If N's ACL includes an entry with the subject name [InheritedRights Filter] and a protected attribute of [All Properties Rights],then remove all access rights from R except those listed in theIRF.b.If N's ACL contains an entry with the subject name of O' and aprotected attribute of [All Properties Rights], then set R to theaccess rights for the entry.2.For node O2 only, perform the following steps:a.If O2's ACL includes an entry with the subject name [InheritedRights Filter] and a protected attribute of A, then remove allaccess rights from R except those listed in the IRF.b.If O2's ACL contains an entry with the subject name of O' and aprotected attribute of A, then set R to the access rights for theentry.3.Union the value of R calculated in steps 1 and 2 for each O' together,yielding the rights of O1 to attribute A of O2.4.For each object O' to which O1 is security equivalent, determinewhether O' has the Supervisor object right to O2 by searching from the root of the tree toward O2. S, which is initially false, representswhether O' has the Supervisor object right to O2. For each node Nalong the path, perform the following steps:a.If N's ACL includes an entry with the subject name [InheritedRights Filter], a protected attribute of [Entry Rights], and the IRFdoes not include the Supervisor right, then clear S.b.If N's ACL contains an entry with the subject name of O', aprotected attribute of [Entry Rights], and the access rights includethe Supervisor right, then set S.5.If the value of S for any of the values of O' computed in step 4 is set,then O1 has all rights to attribute A of O2, regardless of the results of step 3.There are certain attributes, which are flagged in special ways, that are not modified by the ACL. For example, attributes may be marked as Read-Only, which precludes modification to the attribute, even if the user has adequate rights. Other attributes are marked as Public-Read, which is equivalent to the ACL entry <[Public], A, Read> (where A is the name of the attribute). Attributes are marked as Read-Only or Public-Read as part of the attribute definition, and not as part of the ACL for the object.An important aspect of the above policy is that rights to individual attributes are not inherited, but rights to all attributes (as represented by the symbol [All Properties Rights]) are inherited. Thus, a user could be given the Read and Write rights to [All Properties] at the root of the NDS tree, which would provide access to all lower objects (unless modified by IRFs or subsequent trustee assignments), but giving the Read and Write rights to the Telephone Number attribute at the root would only affect access to the attribute of that particular object.There is no “protected attribute” field in a trustee list entry, whereas there is in an NDS ACL entry.4The Access Control right allows changing the trustee list, except to add an entry with the Supervisor right. Note 5that there is no Executive right, because users execute programs on workstations over which the server has no control. Similarly, there is no “setuid” concept as in UNIX for protected subsystems. The IRF for a file cannot block inheritance of the Supervisor right.6 2.2File System Object Access Control PolicyFiles in a NetWare file system are organized in a hierarchical tree, much asany traditional file system. Files are organized into volumes , whichtypically represent disk drives. File system rights rely on many of thesame concepts as NDS rights: security equivalence, inheritance, andinherited rights filters. The file system access control policy is similar, butnot identical, to the NDS object and NDS attribute policy. Every filesystem object (file or directory) may have a trustee list, which is equivalentto an ACL. Elements of a trustee list are pairs , where the first element is4the subject name and the second element is the access rights (zero or moreof Supervisor, Read, Write, Create, Erase, Modify, File Scan, or AccessControl ). Any NDS object with at least one right to a file system object is5called a trustee of the object, indicating that it has (partial) responsibilityfor the data contained in the file or directory. An object O1's rights to afile or directory F is computed as follows:For each object O' to which O1 is security equivalent, compute the rights for O' to F by searching from the root of the volume toward F.R, which is initially empty, represents the object rights O' has to F.For each node N along the path, perform the following steps:-If N's trustee list includes an entry with the subject name[Inherited Rights Filter], then remove all access rights from Rexcept those listed in the IRF .6-If N's ACL contains an entry with the subject name of O', thenset R to the access rights for the entry, unless R already containsthe Supervisor right, in which case R is unchanged. Union the value of R calculated in the first step for each O' together,yielding the rights of O1 to F.Just as inheritance is used to assign rights in a relatively small number oflocations in NDS, so too can it be used in the file system. For example,assigning the single trustee entry <[Public], {Read, File Scan}> to the\PUBLIC directory will allow all users access to all files in that directory(and all subdirectories) without assigning any rights to individual files inthe directory.Note that because of inheritance, rights are typically not assigned at theroot of a volume, because that would provide rights to the whole volume(unless blocked by an IRF).3.0Using NetWare for RBACNetWare 4 can be used to enforce portions of the RBAC0, RBAC1, ARBAC0, and ARBAC1 policies described in [SAND96a]. The objects to be protected for RBAC0 and RBAC1 are files and directories, while the objects to be protected for ARBAC0 and ARBAC1 are NDS objects. We do not believe that NetWare can be used for implementation of role constraints (RBAC2 and ARBAC2) and, therefore, it cannot be used for the consolidated model (RBAC3 and ARBAC3), which presumes the presence of role constraints.3.1RBAC0: Base ModelRBAC0 provides basic RBAC features. The objects we wish to protect using RBAC0 are files and directories in the file system. The users of RBAC0 are equivalent to users in NetWare, and the permissions are the NetWare file rights (Supervisor, Read, Write, Create, Erase, Modify, File Scan, and Access Control). Roles can be implemented using any NDS object, although the Organizational Role object is most suitable for the purpose because of its name.3.1.1What Can be DoneRBAC0 calls for a many-to-many relationship between roles and users and between roles and permissions. In NetWare, users may be security equivalent to an arbitrary number of other objects, and objects may have an arbitrary number of users that are security equivalent to them. This allows us to establish a many-to-many relationship between users and roles. Similarly, the same permission (right) can be assigned to any number of roles and vice versa.The essence of RBAC0 in NetWare is the ability to assign access rights independently from access control rights. That is, a role could have the ability to create, delete, read, and write files in a directory without the ability to grant others access to that directory. This would be done by not assigning the Access Control right to the role. In turn, user’s rights are limited by the roles to which they are security equivalent.3.1.2What Cannot be DoneAs noted above, NetWare has no concept of sessions operating in different roles as called for in RBAC0. Users obtain those rights associated with all objects to which they are security equivalent. Thus, there is no capability for dynamic activation and deactivation of roles during a session; a user must log out from one NetWare User account and log in as a different one to change their role. This is a weakness of NetWare, as it forces users to either have their maximum rights available at all times or to maintain multiple accounts, each of which is used for a different purpose (e.g., user or administrator).A client operating system could maintain a mapping of user identities to roles and transparently log the user in and out as necessary. For example, the user might present a name and a role, and the client would map that to an NDS User object. Similarly, given sufficient client operating system support, users could have multiple windows each of which is logged in to aNetWare server as a different user ID, thus presenting the facade of havingmultiple concurrent sessions. We are unaware of any implementation ofthis mechanism. In addition, maintaining multiple synchronized identitieswould be administratively cumbersome.3.1.3Possible ExtensionsNetWare has no concept of a granularity below files. For example, itmight be desirable to have RBAC to records in a database. This can beaccomplished by extending the NetWare server using NetWare Loadable7Modules (NLMs), which extend the server operating system. Additionalmessages could be defined between clients and servers to provide access todatabase records. Such messages could rely on the authentication servicesprovided by NetWare and could "piggy-back" by using the existing accesscontrols to enforce RBAC on a row or column basis.3.2RBAC1: Role HierarchiesThe purpose of role hierarchies is to allow structuring of rights as they aretypically done in an organization to reflect authority and responsibility.NetWare's rights inheritance coupled with NDS hierarchy works well forsuch a concept. Container objects, which are used for grouping NDSobjects, can be trustees of a file just as any other NDS object. Becauseusers are security equivalent to all containers they are transitivelycontained in, assigning rights to a container assigns those rights to all users(and other NDS objects) in that container.However, NDS containers are inverted with respect to the usualorganizational model that individuals near the top (i.e., root) have moreauthority and responsibility and authority than individuals closer to thebottom (i.e., the leaves).A second difficulty with mapping NetWare access controls to RBAC1 isthe notion of transitivity. [SAND96a] suggests that access controls shouldbe transitive, so a Vice President would obtain not only those rightsassigned to the Department Head role, but also transitively the rightsassociated to the Engineer role. However, security equivalence is nottransitive, so this concept must be implemented administratively (e.g.,either by assigning the Vice President role all of the rights of DepartmentHead and Engineer roles, or by making each instance of a user who is aVice President security equivalent to all three roles). [SAND96a] alsodescribes the notion of inheriting rights from multiple roles. This is doneeasily in NetWare by making a User object security equivalent to anarbitrary number of other NDS objects.NetWare does not meet the proposed requirement of role hierarchies beingpartial orders. Partial orders are reflexive, transitive, and anti-symmetric.NetWare's security equivalence mechanism provides reflexivity and anti-symmetry, but not transitivity.7Commercial database systems (e.g., ORACLE) that run on NetWare use this technology.As with RBAC0, RBAC1 includes the concept of sessions that can be usedfor a role. RBAC1 extends the concept further by requiring that users beable to assume any subset of the roles to which they are authorized, giventhe hierarchical nature of roles. This is impossible in NetWare, short ofcreating a separate user account for each unique combination of roles thata user might wish to exercise.3.3ARBAC0: Administrative Base ModelThe notion of ARBAC0 is identical to that of RBAC0, except that it isconcerned with administrative controls rather than access to files anddirectories. Just as NetWare's file access control policy can be used toprovide roles with access to files and directories, so can the NDS accesscontrol policy be used to provide roles with access to NDS objects andtheir attributes. For example, by providing a role with the Supervisorobject right to a container, individuals security equivalent to that role canadminister objects within the container, subject to access blocked by IRFs.The role-based administrative access can be divided at an arbitrarily fine-grained level. For example, a Telephone-Manager role could be definedthat has the Read and Write rights to the Telephone Number attribute of allNDS objects. However, to do this, the role would have to be listed on theACL for every object in the NDS tree, because attribute-specific rights arenot inherited.3.4ARBAC1: Administrative Role HierarchiesThe relationship of ARBAC1 to RBAC1 is the same as ARBAC0 toRBAC0. Just as hierarchies of users can be established to provide accessto file system objects, so too can hierarchies be used for access to NDSobjects. As with RBAC1, though, the lack of transitivity in the securityequivalence mechanism limits the ability to meet the criteria established in[SAND96a].4.0ExamplesIn this section we provide several examples of how the NetWaremechanisms can be used to implement an RBAC policy.4.1File System ExamplesConsider the NDS structure as shown previously in Figure 11-2 and thefile system structure as shown in Figure 11-3, Sample File SystemStructure.Figure 11-3. Sample File System StructureTable 11-1, Sample File System Trustee Assignments, shows sampletrustee assignments for this configuration. Recall that all users areautomatically security equivalent to each container in which their userobject is located and that users obtain the union of rights available to eachobject to which they are security equivalent. Thus, with no additionalassignments, users Alice and Bob will have File Scan, Create, Read, andWrite rights to all files and directories in \MKTG\EUROPE (by virtue ofbeing security equivalent to Europe.Marketing.Acme, which is a trustee ofthe directory). Similarly, users Cheryl and David will have the File Scan,Create, Read, and Write rights to all files and directories in \MKTG\ASIA(by virtue of being security equivalent to Asia.Marketing.Acme, which is atrustee of the directory). Alice, Bob, Cheryl, and David will all have theFile Scan, Create, Read, and Write rights to all files in\MKTG\COMMON (by virtue of being security equivalent toMarketing.Acme). Note that none of these assignments allow the users topropagate permissions, because no one has the Access Control orSupervisor right. Without any explicit security equivalences, no one hasrights to \MKTG\FORECAST.Table 11-1. Sample File System Trustee AssignmentsNow assume that Bob.Europe.Marketing.Acme is made security equivalent to Mgr.Europe.Marketing.Acme, and similarly .Marketing is made security equivalent to .Marketing.Acme. By this assignment, each will obtain the Access Control right to the respective\MKTG\EUROPE or \MKTG\ASIA directory, and the File Scan, Read, and Write rights to the \MKTG\FORECAST directory. If Bob goes on vacation, Cheryl can be made security equivalent toMgr.Europe.Marketing.Acme and will instantly obtain the rights usually exercised by Bob. Note that it is not sufficient for Cheryl to be made security equivalent to Bob, because Bob is not directly a trustee, and security equivalence is not transitive.By making Edward.Acme security equivalent to Mktg-Mgr.Marketing.Acme, he will obtain the Supervisor right to the marketing portion of the file system. Note that no one has access to the root of the file system tree: because of inheritance, access to the root is rarely granted.In an analogous fashion, we could assign rights to the \FINANCE portion of the file system. There is, of course, no reason why objects in Finance.Acme could not have rights to files in \MKTG, or vice versa.Thus, by using security equivalence and inheritance, a small number of access control assignments are sufficient for controlling a large file system tree. Using Organizational Role and Organizational Unit objects as trustees simplifies the management of the file system, which is a key goal of RBAC.4.2NDS ExamplesAgain consider the NDS structure as shown previously in Figure 11-2. Table 11-2, Sample NDS Trustee Assignments, shows sample ACL assignments for this configuration. With these trustee assignments, all users in Finance.Acme will have the Browse right to the Finance container, while all users in Marketing.Acme will have the Browse right to the Marketing container. The Finance organization has an administrator who has the Supervisor right to that portion of the NDS tree, while the Marketing organization has a less powerful administrator with Create and Delete rights, but not the Supervisor right. In addition, the organization as a whole has an administrator who has the Supervisor right to the entire tree.Table 11-2. Sample NDS Trustee AssignmentsBy making Edward.Acme security equivalent to Admin.Acme, he will obtain the Supervisor right to the whole tree. If Sally.Finance.Acme is made security equivalent to Manager.Finance.Acme, then she will have theSupervisor right to the Finance part of the NDS tree. Using an InheritedRights Filter, Admin.Acme could be blocked from having any rights inFinance.Acme, thus allowing only Sally to administer those portions of thetree.Because of security equivalence, any user can take over administration ofthe tree simply by being made security equivalent to Admin.Acme (orManager.Finance.Acme, for that portion of the tree). As in the file systemexamples, because security equivalence is not transitive, it is not sufficientto make a user security equivalent to Sally, because her rights are notassigned directly, but rather come from security equivalence.Thus, using assignment of rights to Organizational Unit and OrganizationalRole objects, we can configure access rights in the NDS tree with a bareminimum of configuration settings.5.0ConclusionsRBAC can be partially implemented using existing commercial products.The inability to provide some of the features suggested by the [SAND96a]family of models suggests that perhaps a finer-grained distinction offeatures would be desirable, rather than an all-inclusive definition ofmeeting a given set of RBAC criteria. By analogy, this is similar todefining a security target using the ITSEC [ITSEC91] or the proposedCommon Criteria [COMM96] and comparing a product to the target,rather than using a one-size-fits-all approach to security as in the OrangeBook [DOD85].NetWare provides many useful features for implementing RBAC. It wouldbe significantly more useful if it provided the ability for users to selectsessions by selecting at login time what objects they want to be securityequivalent to (as a subset of their authorized set), and transitivity insecurity equivalence.6.0References[COMM96] Common Criteria Editorial Board, Common[SCHA94] M. Schaefer, G. Grossman, and J. Epstein, Criteria for Information Technology Security Evaluation,“Using a Semiformal Model 2C a C2 Better,”Version 1.0, January 1996. Available from: Proceedings of the 17th National Computer Security /nistpubs/cc/read_l.Conference, Baltimore, MD, 11-14 October 1994,153-164.[DOD85] U.S. Department of Defense, Trusted ComputerSystems Evaluation Criteria, DOD 5200.28-STD,Washington, DC, December 1985.[ITSEC91] Information Technology Security EvaluationCriteria (ITSEC), Provisional Harmonised Criteria,Version 1.2, Luxembourg: Office for OfficialPublications of the European Communities, June 1991.[SAND96a] Ravi S. Sandhu, Edward J. Coyne, Hal L.Feinstein, and Charles E. Youman, “Role-Based AccessControl,” IEEE Computer, 29:2, February 1996, 38-47.。
A Knowledge-Based Approach to Internet Authorizations Using PKI

A Know l e d ge-Base d Approach t o I nt e rne t Aut h oriz at ion Using PKI Al ong L inT rust ed E-Se rv ic e s L aborat oryH P L aborat orie s Brist olH P L-2000-133Oc t ob e r 13t h , 2000*E-m ail: al in@h pl b.h pl.h pol ic y-driv e nm anage m e n t, se c urit ym anage m e n t,aut h oriz at ion I n t h is pape r, a k n ow l e d ge-base d approac h t o In t e rn e taut h oriz at ions is proposed by using Publ ic-Key I nf rast ruc t ure(PKI)based digit al c e rt if ic at e s, t rustm ode l s, Rol e-Base d Ac c e ss Cont rol(RBAC), andint e l l ige n t bac k t rac k ing. Se c urit y pol ic ie s are e xpre sse d as t h erul e s in a k now l e d ge b ase. An inf e re n c e e n gine is ut il ise d t oe v al uat e pol ic ie s, dynam ic al l y assign rol e s t o In t e rn e t use rs, and re d o rol e s assignm e n t aut om at ic al l y.*I nt e rnal Accession Dat e O n l y Approv ed f or Ext e rnal Publ icat ion © Copyrigh t H e w l e t t-Pack ard Com pany 2000A Knowledge-Based Approach to Internet Authorizations Using PKIAlong LinTrusted E-Services LaboratoryHewlett-Packard LaboratoriesFilton Road, Stoke GiffordBristol BS34 8QZ, U.K.Email: alin@AbstractIn this paper, a knowledge-based approach to Internet authorizations is proposedby using Public-Key Infrastructure (PKI) based digital certificates, trust models,Role-Based Access Control (RBAC), and intelligent backtracking. Securitypolicies are expressed as the rules in a knowledge base. An inference engine isutilised to evaluate policies, dynamically assign roles to Internet users, and redoroles assignment automatically.Keywords: Policy-Driven Management, Security Management, Authorization1 IntroductionWith more electronic services being deployed for access over the Internet, security is becoming an increasingly critical issue. Existing access control mechanisms do not provide a flexible management solution to Internet authorizations. Discretionary Access Control (DAC) prevents unauthorized users from performing operations on resources by administering the relevant Access Control List (ACL), which is not scalable for Internet environments. Mandatory Access Control (MAC) eases the security management by attaching security labels to subjects and objects, and enforces a specific security policy that allows only one-directional information flow between those subjects and objects. However, it does not provide any support for general Internet authorizations. Although several RBAC systems have been developed, they still have the following drawbacks: manual user-role assignment, business logic coupled privileges, and the assumption that users are known to resource providers in advance. Attribute and authorization certificates contain accessing rights within them and seem to be a promising solution [5].Attribute Certificates (ACs) bind attributes to users Distinguished Names (DNs). They can be used with identity certificates to achieve the mapping: attributes ?DN ?public key. The motivation for introducing ACs in PKI technology was that X.509 public key certificates were used for identity purpose by establishing a secure certified relationship between issued public keys and their owners. Although attribute information can beincluded in X.509 v3 certificates as extensions to satisfy application-specific needs, this is not worthy from the perspectives of interoperability, jurisdiction, and revocation. First, private attributes extensions make it hard for disparate systems to interoperate with each other. Second, it is difficult for an organization to issue a certificate containing both the identity information and attributes that may be accessing rights. Finally, attributes are more volatile than identity information, and therefore need revoking more frequently. However, having authorizations in an AC has drawbacks too. First, an attribute certificate authority must issue ACs to potential Internet users before they can access the controlled resources, which is inconvenient to users and sometimes can be disastrous to security managers from certificates management perspective. Second, for those ACs that have a long period of validity, revoking them can be much of a burden to the issuing CA when the accessing rights in them have to be updated due to the business policy changes.In this paper, it is assumed that ACs contain only users comparatively stable attributes without any accessing rights. A user may have several ACs issued by different trusted CAs that have intimate knowledge of the user. E.g., an accredited university or institute issues its graduates normal ACs containing such attributes as degrees, qualifications, majors, graduation dates, and the like. A bank issues each of its account owners an AC that contains account number, account type, branch name, opening date, and so on. A trusted driving license agency may issue a qualified driver an AC that includes driving license number, car categories, validity dates, address, and the like. A user’s ACs will then be used by various resource providers to make authorization decisions based on their business-specific security policies.In the following, a knowledge-based RBAC is discussed first. Second, an automated user-role assignment based on their digital certificates and intelligent backtracking is described. Third, a knowledge-based approach to Internet authorizations is proposed by using PKI, trust models, RBAC, automated user-role assignment, and intelligent backtracking.2 Knowledge-Based RBACIn RBAC [1, 2, 3], permissions are only associated with roles and users get permissions by being members of appropriate business roles. This greatly simplifies a system’s security management. Security officers create business roles and assign those roles to users based on their qualifications and responsibilities in organizations. Users can be easily reassigned from one role to another. Roles may be granted new permissions as new services are deployed, and permissions can be revoked from roles as needed. However, traditional RBAC systems assume that a user’s role is known when it requests particular resources, which requires the user to register with the resource providers in advance. This is neither convenient to Internet users nor cost-effective from systemmanagement perspective. In Internet situations, it may be helpful to allow authorized users to access resources without asking them to register with resource providers in advance. An automated user-role assignment solution has been suggested [4], but it did not discuss how digital certificates are exchanged between users and resource providers. In Knowledge-Based RBAC (KBRBAC), application-specific user-role assignment policy, trust models, and business logic on roles privileges are provided as a knowledge base. Any changes to it will dynamically drive the changes in an organization’s security policies on its business processes, thus significantly alleviating the security management in a system. An independent knowledge base also gives security managers a lot of flexibility. When the knowledge base for configuring an RBAC system is empty, roles must be assigned to users manually and there is no extra business logic on roles privileges; otherwise, if the user-role assignment policies are enforceable and described in the knowledge base, those roles may be assigned to users automatically at run-time. For other roles that must be manually assigned to users, their role-assignment policy attributes are ‘null’. To be more flexible, each role privilege is associated with a predicate used as the business logic on it. A predicate is defined by a set of rules. A privilege consists of a set of operations and objects to be performed on by role members. The role definition and an example are given in appendixes A, B, respectively.Even though the knowledge base can be built by the security manager of an RBAC system with the help of an authoring tool on the resource controller’s side, it still requires some information about the potential Internet users. What kind of information about a resource requestor should or can be sent to resource providers? How can the trust relationship be established between the unknown Internet users and service providers? These issues will be discussed in the following sections.3 Automated Role-Assignment Using PKI and Intelligent Backtracking An approach has been proposed to dynamically map a user to predefined business roles based on the user’s digital certificates issued by trusted Certificate Authorities (CAs) and role-assigning policies pre-set by resource providers [4]. Because the user does not know anything about a resource provider’s authorization policy, various digital certificates may be required to present to the resource provider for accessing a particular resource [5]. An intelligent backtracking mechanism is therefore necessary for supporting the non-deterministic automated user-role assignment, which means there will be a lot of traffic between a resource requestor and a resource provider at run-time. Furthermore, in order to validate Internet users digital certificates, the trust relationships between resource providers and CAs have to be defined in the trust models of a knowledge base.Although a user may be assigned several business roles based on its digital certificates and pre-set role-assigning policies, only some of them will authorize it to access the requested resource. For those roles that have privileges matching the user’s current accessrequest, the policy evaluator will be called to evaluate the policies enforced on those privileges. If the policy evaluates true, the user’s current request is authorized and the relevant actions can then be performed on the resource; otherwise, alternative roles will be tried. For each assigned role, if either it does not have a matching privilege for the user’s current request or the matching privilege’s associated authorization policy evaluates false, the inference engine will redo the previous role assignment automatically. If all roles have been tried, the user’s request will be denied. Because the inference engine can support backtracking and policy evaluation, it can be combined into one on the resource provider side.To avoid assigning a user to the roles that do not have the required privilege, an efficient indexing mechanism is needed to support the retrieval of the candidate assignable roles. Only those roles having the required privilege will be tried assigning to the user for current request. However, whether a role will be assigned to a user still depends on the user’s presented digital certificates, the service provider’s role-assignment policy and trust models, which are expressed as rules in a knowledge base. The service provider may not trust some Certificate Authority (CA), and asks the user to present other digital certificates issued by particular CAs. When a user accesses a resource, the resource provider will first get a set of candidate roles whose privileges match the user’s current request to improve the role-assignment efficiency. Then, it will try to assign those roles to the user based on the presented digital certificates and the knowledge base.separation of duties when role-assigning policies are set, an automated mechanism for guaranteeing this is very helpful so that two conflicting roles will not be assigned to auser at run-time. This can be achieved by not satisfying the policies on two conflicting roles assignment simultaneously or storing users assigned roles information in a database persistently. A user’s candidate assignable roles must not be in conflict with the roles that have already been assigned to the user (see Fig. 1). If such conflicts occur, the security manager will be informed of them and take necessary measures as required.Our automated role-assignment solution based on PKI and intelligent backtracking has a unique advantage over the traditional RBAC and others [4] in that it enables users to specify various domain-specific security policies in a knowledge base. It allows Internet users to access resources more conveniently and security policies can be managed flexibly. Furthermore, because much of the user-role assignment management has been automated, the security manager’s work will be reduced to a minimum by using a configurable knowledge base.4 A Knowledge-Based Approach to Internet Authorizations Using PKI Now that we have discussed how to authorize a user’s request based on its digital certificates, a knowledge base, and intelligent backtracking, we need to consider what information needs to be exchanged between the user and the resource provider without disclosing the server side security policies to the user. It is not reasonable to ask the user to submit all its digital certificates, most of which may be irrelevant to its current request, and the user may not be willing to do that. Therefore, during the authorization decision-making, users digital certificates may be requested. For simplicity, we assume that the user has already been authenticated and we will only focus on the authorizations below. There are three steps in requesting a user’s digital certificates. First, the Server Security Agent (SSA) needs to decide what digital certificates are required for the current user’s request. Based on the request and the security policies in the knowledge base, the SSA can automatically find the potential set of digital certificates using a logical reasoning. Second, the SSA checks if some of those digital certificates have already been cached in a directory and are still valid, and then sends a request for unavailable digital certificates to the user. Finally, the user sends the requested digital certificates back to the SSA, which will then cache them in its directory for future use using Lightweight Directory Access Protocol (LDAP).However, sending digital certificates is only part of the Internet authorization (illustrated in Fig. 2). If any of the following conditions holds, the SSA will have to redo its previous role assignment and find another set of digital certificates to try other alternative roles for the user’s current request, and re-evaluate the associated authorization policy.•Some digital certificates presented have already been revoked by their CAs using Certificate Revocation Lists (CRLs) or the Online Certificate Status Protocol (OCSP).• Some digital certificates are neither valid nor trusted by the SSA according to the trust models described in the knowledge base.• The presented digital certificates cannot assign the user a role that authorizes the current request based on the resource provider’s role-assigning policy expressed in the knowledge base.• The authorization policy on the assigned role’s matching privilege evaluates false using the system models in the current context.The client’s digital certificates can be sent to the SSA by using a trusted applet digitally signed by the resource provider or a plug-in for the client’s Web browser. The communication between the user and the resource provider is based on Secure Socket Layer (SSL). The client can optionally configure the certificate-sending policy on what digital certificates can be sent automatically without being informed in advance. If there is no policy configured for sending a particular certificate, a user will be informed of thecertificate request by default, and will decide whether to send it to the SSA for the user’s current request. If there is a certificate-sending policy and it evaluates false, the requested digital certificate will not be sent to the SSA; otherwise, it will be sent to the SSA automatically without the user’s intervention. In Business-to-Business situations, client side authorization for sending digital certificates to the server side also needs a knowledge base that describes the client’s certificate-sending policy and trust models (as shown in Fig. 3).Regarding the client’s trust in an applet, there are two primary types of models. One is hierarchical and the other is based on the web of trust. The former assumes that the user’s chain of digital certificates is rooted by a CA trusted by its receivers. The latter allows any of the digital certificates in a chain can be cross-certified by more than one CAs. Because trust policies are always business related and application-specific, they must be configurable by means of an independent knowledge base so that the SSA, a Web browser or a trusted applet can use it to make trust decisions.As pointed out in [6,7,8], a logic-based knowledge representation is expressive enough and has several advantages over other approaches. PROLOG (PROgramming in LOGic) is based on Horn-clauses, which is a subset of first order logic, and has a solid theoretical foundation. What is more, both policy evaluation and policy conflict detection can be easily done within the logic framework as well. Therefore, it is adopted as the policy representation language in this paper.5 ConclusionsIn this paper, a knowledge-based approach to Internet authorizations is proposed by using PKI-based digital certificates, trust models, policy-based roles privileges, automated user-role assignment, and intelligent backtracking. Security policies are expressed as the rules in an independent knowledge base. An inference engine is utilized to evaluate various policies, dynamically assign roles to Internet users, and redo roles assignment automatically. The innovative approach makes the administration of Internet users accesses to resources less of a burden to security managers. The proposed architecture for Internet authorizations is capable of dealing with both unknown Internet users and automatic user-role administration. It overcomes some of the drawbacks of existing RBAC systems, which are neither flexible for access control management nor convenient to Internet users.A policy-authoring tool is strongly recommended to be used to alleviate the administration task of security managers. The tool should be capable of mapping a user’s access request to a role’s privilege and even refining a high-level security policy into executable rules, so that security managers can focus on the specification of authorization policies, trust models, and role-assigning policies in the knowledge base.References[1] Ferraiolo D F, Barkley J F, Kuhn D R, A Role-Based Access Control Model and Reference Implementation Within a Corporate Intranet, ACM Transactions on Information and System Security, Vol. 2, No. 1, (1999) 34-64.[2] Ferraiolo D F, Cugini J A, Kuhn D R, Role-Based Access Control (RBAC): Features and Motivations, In Proc. of 11th Annual Computer Security Applications Conf., (1995) 241-248, /rbac/newpaper/rbac.html.[3] Giuri L and Iglio P, A formal model for role based access control with constraints, In Proc. of the Computer Security Foundations Workshop, (1996) 136-145.[4] Herzberg A, Mass Y, Mihaeli J, Naor D, and Ravid Y, Access Control Meets Public Key Infrastructure, Or: Assigning Roles to Strangers, /TrustEstablishment/paper.htm.[5] Johnston W, Mudumbai S, and Thompson M, Authorization and Attribute Certificates for Widely Distributed Access Control, In Proc. of the IEEE 7th International Workshops on Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE-98), (1998) 340-345.[6] Li N, Feigenbaum J and Grosof B, A Logic-based Knowledge Representation for Authorization with Delegation, In Proc. of the 12th IEEE Computer Security Foundations Workshop, (1999) 162-174.[7] Massacci F, Reasoning about Security: a Logic and a Decision Method for Role-Based Access Control, In Proc. of the International Joint Conference on Qualitative and Quantitative Practical Reasoning (ECSQARU/FAPR-97), Lecture Notes in Artificial Intelligence, Vol. 1244 (1997) 421-435.[8] Seamons K E, Winsborough W and Winslett M, Internet Credential Acceptance Policies, In Proc. of the Workshop on Logic Programming for Internet Applications, July 1997, /~winsboro/papers/CAP.html.Appendix A – the role syntax<Role> ::= ‘Name:’<Role Name>‘.’‘Role-Assigning Policy:’{<Predicate> | ‘null’}‘.’‘Authorizations:’<Privileges>‘.’<Role Name> ::= <Symbolic Atom><Privileges> ::= <Privilege>*<Privilege> ::= <Policy> ‘,’{<Method>}+‘.’Where, <Policy> is a predicate and is described by a set of PROLOG clauses defined as below, and <Method> is defined as an external function in models. A special predicate is symbolic atom ‘true’.<Clause> :: = <Fact> | <Rule><Fact> ::= <Predicate>‘.’<Rule> ::= <Predicate> ‘:-’<Conditions>‘.’<Conditions> ::= ‘(’<Conditions> ‘)’| <Expression> | ‘!’<Expression>| <Expression> ‘,’ <Conditions><Expression> ::= <Argument><RelOp><Argument> | <Predicate><RelOp> ::= ‘==’| ‘<’| ‘>’| ‘<=’| ‘>=’| ‘!=’<Symbolic Atom> ::= [‘a’-‘z’]{[‘a’-‘z’] | [‘A’-‘Z’] | [‘0’-‘9’] | ‘_’}*<Argument> ::= <Symbolic Atom> | <String> | <Number> | <Logical Variable>| <Functor><Parameters><Functor> ::= <Symbolic Atom> | ‘.’| <Arithmetic Operators><Parameters> ::= ‘(‘<Argument>{‘,’<Argument>}*‘)’<Logical Variable> ::= ‘_’| [‘A’-‘Z’]{[‘a’-‘z’] | [‘A’-‘Z’] | [‘0’-‘9’] | ‘_’}*<Predicate> ::= <Symbolic Atom>[<Parameters>]<Policy> ::= <Predicate>Appendix B – A Bank ExampleWe use a simple example to demonstrate the ideas contained in the paper. It is assumed that a full-time student has already been issued an identity certificate by an accredited university, and has got a digital driving license issued by the Driving License Agency (DLA) after having passed both the theory and practical tests. The student wants to getthe service of car rental or hotel reservation on the Internet, which requires the student to open an account in a recognized bank first to get digital credit certificates.The bank provides a set of E-services, including new account creation, normal bank account transactions, and interest enquiries. In the following, various kinds of policies are modeled by PROLOG rules and the methods of privileges are left undefined. Some predicates are simply defined and even omitted here.Name: bank_account_owners.Role-Assigning Policy: bank_account_attribute_certs( Account_ids, Certificates ). Authorizations:transfer_accounts_policy( Request, Account_ids, [From, To, Amount] ),transfer_money( From, To, Amount ).account_access_policy( Request, Account_id, Account_ids ),get_balance( Account_id, Balance ). // get the balance of the bank account.account_access_policy( Request, Account_id, Account_ids ),deposit_money( Account_id, Amount ).withdraw_policy( Account_id, Amount),withdraw_money( Account_id, Amount )..Name: bank_account_creators.Role-Assigning Policy: certificates_for_bank_account_creation( Request, Identity ). Authorizations:true, issue_account_attribute_certificate( Identity, Request )..Name: default.Role-Assigning Policy: true.Authorizations:get_interest_rate_policy( Request, Type ),report_interest_rate( Type ). // return the interest rate to the user..// If the request is to create a new bank account and the user has valid and acceptable // identity certificates, collect them into Accepted_certificates; Otherwise, return false.certificates_for_bank_account_creation( Request, Identity_cert ) :-creating_bank_account( Request ),request_certificates( Certificates ), // Its definition is omittedvalid_and_accepted_certificates( Certificates, Accepted_Certificates ),has_acceptable_identity_certificate( Accepted_certificates, Identity_cert ).// Test if there is a valid and acceptable identity certificate in the given set of certificates withdraw_policy( Account_id, Amount ) :-get_balance(Account_id, Balance),get_credit_limit( Account_id, Credit_limit),Amount <= Balance + Credit_limit.transfer_accounts_policy( Request, Account_ids, [From, To, Amount] ) :-get_transfer_parameters( Request, From, To, Amount ),member( From, Accounts_ids ),member( To, Accounts_ids ),withdraw_policy( From, Amount ).// Request attribute certificates issued by the bank to the user, and collect bank account // numbers into Account_numbers. If the user doesn’t have valid and acceptable attribute // certificate issued by the bank, it returns false.bank_account_attribute_certs( Account_numbers, Certificates ) :-request_certificates( Certificates ), // Its definition is omittedvalid_and_accepted_certificates( Certificates, Accepted_Certificates ),get_account_numbers( Accepted_Certificates, Accounts_numbers ),Accounts_numbers \= [].// Get the bank account numbers of valid and accepted bank account attribute certificates get_account_numbers( [Certificate|Rest], [No|Account_Nos] ) :-get_account_identifier( Certificate, No ),get_account_numbers( Rest, Account_Nos ).get_account_numbers( [_|Rest], Account_Nos ) :-get_account_numbers( Rest, Account_Nos ).get_account_numbers( [], [] ).// Get the bank account number of a valid and accepted bank account attribute certificate get_account_identifier( Certificate, Id ) :-valid_certificate( Certificate ),this_bank_service_accepted_certificate( Certificate ),bank_account_no( Certificate, Id ).account_access_policy( Request, Account_id, Account_ids ) :-get_account_id_from_request( Request, Account_id ),// get the account number from the user’s requestmember( Account_id, Account_ids ).valid_and_accepted_certificates( [Valid|Rest], [Valid|Certificates] ) :- valid_and_accepted_certifiacte(Valid ),// test if the certificate is valid and accepted by the bank service provider valid_and_accepted_certificates ( Rest, Certificates ).valid_and_accepted_certificates ( [_|Rest], Certificates ) :-valid_and_accepted_certificates ( Rest, Certificates ).valid_and_accepted_certificates( [], [] ).。
概念:用户角色权限的管理(Role-BasedAccessControl)

概念:⽤户⾓⾊权限的管理(Role-BasedAccessControl)RBAC ⽤户管理规范概念:每个user有多个accounts,每个account 有⼀个account binding,有多个roles和多个tasks举个例⼦:某个⽤户现在manager,这是admin添加了另⼀个⾓⾊supervisor的⾓⾊给他,数据结构是这样的(HdLogin)user{accounts : [{type : "administrator" //可以抽象或具体: administrator, managerpassword : "1234",roles :[{type: "manager",roleTaskss : ",manager,supervisor,"},{type: "supervisor",roleTaskss : ",supervisor,"}],accountBindings : [{type : "email",primaryKey : "xxx@xxx"}]}]}*primaryKey是email format,电话号码,webchat。
*灰⾊是之前的需求,保留⽽已⾃动登⼊,在employer page 登⼊后,会有cookies,去到candidate page时,会⾃动登⼊。
过程是发现有cookies同时type 是customer。
如果在candidate 登出时,employer 也会⾃动登出。
因为在登出后,在refresh⼜会⾃动登⼊,死循环很奇怪!半⾃动登⼊,在employer page 登⼊后,会有cookies,去到candidate page时,点击登⼊,在这⾥看当下页⾯的业务逻辑,如果是只有⼀个⾓⾊可以登⼊的话,就直接帮他登⼊如果是2个⾓⾊,就会有⼀个选项让他选择哪个⾓⾊,如果是选择的⾓⾊在HdLogin有记⼊的话,会⾃动登⼊(cookies是属于当下界⾯)如果是选者的⾓⾊是不在HdLogin的话,会需要⾃⼰登⼊⼿动登⼊,意思是每⼀个页⾯的业务逻辑都是只有⽀持⾃⼰页⾯的cookies。
外文翻译--Web环境下基于角色的访问控制

附录A:英文原文Role-Based Access Control for the WebJohn F. Barkley, D. Richard Kuhn, Lynne S. Rosenthal, Mark W. Skall, and AnthonyV. Cincotta,National Institute of Standards and Technology Gaithersburg, Maryland 20899ABSTRACTEstablishing and maintaining a presence on the World Wide Web (Web), once a sideline for U.S. industry, has become a key strategic aspect of marketing and sales. Many companies have demonstrated that a well designed Web site can have a positive effect on their profitability. Enabling customers to answer their own questions by clicking their way through Web pages, instead of dealing with operators and voice response systems, increases the efficiency of the customer interface.One of the most challenging problems in managing large networked systems is the complexity of security administration. This is particularly true for organizations that are attempting to manage security in distributed multimedia environments such as those using World Wide Web services. Today, security administration is costly and prone to error because administrators usually specify access control lists for each user on the system individually.Role-based access control (RBAC) is a technology that is attracting increasing attention, particularly for commercial applications, because of its potential for reducing the complexity and cost of security administration in large networked applications. The concept and design of RBAC is perfectly suited for use on both intranets and internets. It provides a secure and effective way to manage access to an organization’s Web information. This paper describes a research effort to develop RBAC on the Web. The security and software components that provide RBAC fornetworked servers using Web protocols have been implemented and are described in this paper. The RBAC components can be linked with commercially available web servers, and require no modification of the server software.IntroductionEstablishing and maintaining a presence on the World Wide Web (Web), once a sideline for U.S. industry, has become a key strategic aspect of marketing and sales. Many companies have demonstrated that a well-designed Web site can have a positive effect on their profitability. Enabling customers to answer their own questions by clicking their way through Web pages, instead of dealing with operators and voice response systems, increases the efficiency of the customer interface. Companies are seizing the Web as a swift way to streamline - even transform their organizations.More recently companies have begun using web technology to service the public as well as private and internal clients. Web sites are set up to segregate some information from the general public, providing it to only selected or "private" clients. Typically, public internet is cordoned off from the general public by having user accounts and passwords. Additionally, Web sites are now running inside the company often created for and by employees. These internal private nets or "intranets" use the infrastructure and standards of the Internet and the World Wide Web but are cordoned off from the public Internet through firewalls.The Web can be used as an inexpensive yet powerful alternative to other forms of communications. A plethora of corporate information (e.g., procedures, training materials, directories, forms) can be converted to electronic form and made available via the Web. With a single source for these materials the cost of maintenance is significantly reduced, while greatly simplifying the task of ensuring currency. Thus an objective of enterprise computing, creation of a company wide system irrespective of the underlying information technology infrastructure can be fulfilled.Although the internet and intranets can offer great benefits to a company or government agency, security threats remain. To date net enthusiasts tend to focus on how to link people and businesses, not on using the network as a way to run and manage businesses securely. Althoughexisting Web servers can effectively provide all or nothing access to a particular Web site and a number of popular Web servers can even provide fairly fine grained access control, they provide very primitive tools to administer these controls from the perspective of a single enterprise.This paper describes the benefits of RBAC and an implementation of RBAC on the Web (RBAC/Web), and in particular as RBAC applies to an intranet computing environment. This will provide Web administrators with a capability for the first time to centrally administer and regulate user access to information in a manner that is consistent with the current set of laws, regulations, and practices that face their business today. Although this paper focuses on intranets, the benefits, concepts and implementation of RBAC/Web are also applicable to a company’s internet environment where restrictive access to information is desired. RBAC DescriptionRole-based access control (RBAC) [1], [2], [3], [4], [5] is an alternative to traditional discretionary (DAC) and mandatory access control (MAC) policies that is attracting increasing attention [6], particularly for commercial applications. The principal motivation behind RBAC is the desire to specify and enforce enterprise-specific security policies in a way that maps naturally to an organization's structure. Traditionally, managing security has required mapping an organization's security policy to a relatively low-level set of controls, typically access control lists.With RBAC, security is managed at a level that corresponds closely to the organization's structure. Each user is assigned one or more roles, where roles are based on the user's job responsibilities and competencies in the organization. Each role is assigned one or more privileges (e.g., information access, deletion, creation), see Figure 1. It is a user's membership into roles that determine the privileges the user is permitted to perform. Security administration with RBAC consists of determining the operations that must be executed by persons in particular jobs, and assigning employees to the proper roles.The RBAC framework provides for mutually exclusive roles as well as roles having overlapping responsibilities and privileges. For example, some general operations may be allowed by all employees, while otheroperations may be specific to a role. Role hierarchies are a natural way of organizing roles within an organization and defining the relationship and attributes of the roles. Complexities introduced by mutually exclusive roles or role hierarchies as well as regulating who can perform what actions, when, from where, in what order, and in some cases under what relational circumstances, is all handled by the RBAC software. Separation of DutyRBAC mechanisms can be used by a system administrator in enforcing a policy of separation of duties. Separation of duties is considered valuable in deterring fraud since fraud can occur if an opportunity exists for collaboration between various job related capabilities. Separation of duty requires that for particular sets of transactions, no single individual be allowed to execute all transactions within the set. The most commonly used examples are the separate transactions needed to initiate a payment and to authorize a payment. No single individual should be capable of executing both transactions. The system administrator can control access at a level of abstraction that is natural to the way that enterprises typically conduct business. This is achieved by statically and dynamically regulating users' actions through the establishment and definition of roles, role hierarchies, relationships, and constraints.We define static separation of duty to mean that roles which have been specified as mutually exclusive cannot both be included in a user's set of authorized roles. With dynamic separation of duty, users may be authorized for two roles that are mutually exclusive, but cannot have both roles active at the same time. In other words, static separation of duty enforces the mutual exclusion rule at the time an administrator sets up role authorizations, while dynamic separation of duty enforces the rule at the time a user selects roles for a session.Role Administration and VisualizationThe roles are established, manipulated and viewed using the RBAC/Web Admin tool. The Admin tool allows system administrators to create and define roles, role hierarchies, relationships and constraints. Once theRBAC framework is established for the organization, the principal administrative actions are the granting and revoking of users into and out of roles as job assignments dictate. These maintenance tasks are easily performed using the Admin tool.Additionally, the Admin tool is being enhanced to utilize the Virtual Reality Modeling Language (VRML, pronounced 'vermal'). VRML is an interactive, inter-networked, 3D graphics language for the Web. It is used to represent graphics, test, sound, and links to other content as either a static or dynamic picture on the Web. The inclusion of VRML into RBAC lets system administrators use an interactive computer model to check and validate the role structure, relationship, and privileges. Being able to view and interact with complex models, allows the administrator to identify conflicts, eradicate flaws and improve the implementation early in the RBAC setup.The VRML component will enable authorized users to navigate the RBAC database, finding and linking roles, and displaying attributes and graphics associated with those roles. By presenting a 3D model of established roles, the user can easily see which roles are mutually exclusive as well as the hierarchical structure of related roles and conflicts between roles (see Figure 2). VRML's navigational controls allows the user to interactively 'walk-through' and manipulate the view perspective of the 3D model, known as a scene graph. For example, the scene graph can be rotated to show the 'backside' of the graph where role relationships may have been obscured when viewed as a 'flat', 2D graph. To improve readability, clarity and flexibility, the role hierarchy is organized into layers, where each layer contains another level of detail. By 'clicking' on a role, the role opens to reveal the next layer of related roles or information about the role, e.g., the privileges associated with that role or a user membership list.RBAC ExampleConsider the branch office of a bank. In this environment, there are roles such as branch manager, teller, and account representative, as illustrated in Figure 2.The graph structure shows role hierarchy. The role financial_advisor inherits the role account_rep. An individual authorized for the rolefinancial_advisor is permitted to perform all of the operations permitted to an individual authorized for the role account_rep. Thus, an individual in the role of financial_advisor is able to create and remove accounts. Because account representatives, branch managers, internal auditors, and tellers are all employees of the bank, their corresponding roles inherit the employee role.In Figure 2, the role account_rep is highlighted, appearing as a dark sphere, in order to show the other role relationships for account_rep. The roles teller and account_holder are shown as yellow rectangular solids to indicate that these roles have a "Dynamic Separation of Duties" (DSD) relationship with the role account_rep. This relationship is a conflict in interest relationship indicating that an individual acting in the role of account_rep cannot also be acting in either of the roles of account_holder or teller. The policy of the bank is that an account representative, an employee of the bank, can have an account in the bank but such an individual may not simultaneously process their personal account while processing accounts of others. Likewise, because a teller has an open cash drawer that must balance when closed, an individual acting in the role of account_rep and sitting at a desk away from a teller's window is not permitted to simultaneously act in the role of teller even if authorized for that role.The role internal_auditor is shown in a red hexahedron to indicate that this role has a "Static Separation of Duties" (SSD) relationship with the role account_rep. The SSD relationship is also a conflict of interest relationship like the DSD relationship but much stronger. If two roles have a DSD relationship, then they may both be authorized for an individual but that individual may not act in both roles simultaneously. If two roles have a SSD relationship, then they may not even be authorized for the same individual. In this example, the policy of the bank is that there is a fundamental conflict of interest between the roles of internal_auditor and account_rep. Thus, these two roles may never be authorized for the same individual.The new version of the Admin tool using VRML will allow us to represent conflicts of interest and other relationships in a more natural way and view the scene from an infinite number of viewpoints. VRML allows complex3D objects to be created for this purpose. The user can 'enter' a selected role and explore several levels of detail (i.e., information) associated with that role. In addition, the sound capabilities of VRML can be utilized to give audio warnings when roles are used which cause conflicts of interest or other problems, or when improper procedures are used. RBAC for World Wide Web ApplicationsRole Based Access Control (RBAC) for the World Wide Web (RBAC/Web) is an implementation of RBAC for use by World Wide Web (Web) servers. Because RBAC/Web places no requirements on a browser, any browser that can be used with a particular Web server can be used with that server enhanced with RBAC/Web. RBAC/Web is implemented for both UNIX (e.g., for Netscape, NCSA, CERN, or Apache servers) and Windows NT (e.g., for Internet Information Server, WebSite, or Purveyor) environments.Components of RBAC/Web are shown in Table 1. RBAC/Web for UNIX uses all of the components in Table 1. Because built-in NT security mechanisms are closely compatible with RBAC, the NT version uses only the Database, Session Manager, and Admin Tool components. RBAC/Web for NT requires no modification of Web server internals or access to source code. With RBAC/Web for UNIX, there are two ways to use RBAC/Web with a UNIX Web server.The simplest way is by means of the RBAC/Web CGI. The RBAC/Web CGI can be used with any existing UNIX server without modifying its source code. RBAC URLs are passed through the Web server and processed by the RBAC/Web CGI. RBAC/Web configuration files map URLs to file names, while providing access control based on the user's roles. Installation of the RBAC/Web CGI is similar to the installation of the Web server.附录B:中文翻译Web环境下基于角色的访问控制John F. Barkley, D. Richard Kuhn, Lynne S. Rosenthal, Mark W. Skall, 和Anthony V. Cincotta,国家研究院所定规则及盖瑟斯堡技术,马里兰20899摘要建立和维持一个万维网(Web),它作为美国工业的一种附属形式,已经成为了买卖和销售战略中的重点。
利用RBAC模型实现一个通用的权限管理系统

利⽤RBAC模型实现⼀个通⽤的权限管理系统本⽂主要描述⼀个通⽤的权限系统实现思路与过程。
也是对此次制作权限管理模块的总结。
制作此系统的初衷是为了让这个权限系统得以“通⽤”。
就是⽣产⼀个web系统通过调⽤这个权限系统(⽣成的dll⽂件),就可以实现权限管理。
这个权限系统会管理已⽣产系统的所有⽤户,菜单,操作项,⾓⾊分配,权限分配,⽇志等内容。
实现此功能从正常访问和⾮法访问两个⽅⾯⼊⼿。
正常访问即⽤户登录系统后只能看到或操作⾃⼰拥有的菜单;⾮法访问即通过拼写url等途径访问系统的某个功能;所以程序除了实现⽤户登录后获取⽤户拥有的菜单权限,更要挡住⽤户的⾮法请求。
两者缺⼀不可。
⼀.概念 实现这个功能主要利⽤RBAC权限设计模型,英⽂(Role-Based Access Control)译为基于⾓⾊的权限管理⼜叫基于⾓⾊的访问控制。
⼆.数据库设计1.系统表:因为要达到"通⽤",所以这个表会记录各个系统。
其他⽤户、菜单、操作、权限表每条记录都会对应系统代码。
字段说明:Code —> 系统标识代码SysName —> 系统名称2.菜单表:记录菜单。
每个功能当成⼀个菜单,菜单有url属性,⽤户通过点击菜单来访问对应功能;字段说明:ID —> 主键,⾃增标识MenuName —> 菜单名称 PageUrl —> 菜单对应url PId —> 菜单⽗级Id Lv —> 菜单等级,分⼀级菜单和⼆级菜单ControllerAction —> 菜单唯⼀标识,⽤来做权限控制SystemCode —> 系统标识代码3.操作表:此表主要是为了判断⽤户是否有来操作某个具体功能,如常⽤的【删除】功能等操作都放在这个表⾥;字段说明:ID —> 主键,⾃增标识OprateName —> 操作名称 OperateCode —> 操作标识代码SystemCode —> 系统标识代码4.⽤户表:记录所有系统的使⽤⽤户。
针对基于多父角色RBAC模型的研究与应用
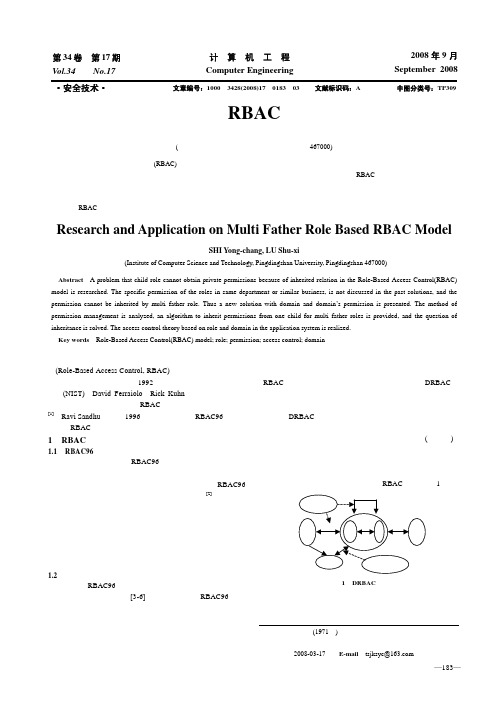
2008年9月September 2008—183—计 算 机 工 程Computer Engineering 第34 第17期Vol 卷.34 No.17 ·安全技术·文章编号:1000—3428(2008)17—0183—03文献标识码:A中图分类号:TP309针对基于多父角色RBAC 模型的研究与应用史永昌,鲁书喜(平顶山学院计算机科学与技术学院,平顶山 467000)摘 要:针对基于角色的访问控制(RBAC)模型中由于继承关系产生的子角色不能拥有私有权限问题进行了研究。
当前的解决方案在表示同一机构或相同业务性质的角色共有特定权限方面存在不足,也不能满足多父角色权限继承的要求。
对RBAC 模型进行了扩展,给出一种基于域和域权限的解决方案,并结合实际项目具体分析系统实现权限管理的方法,提出多父角色权限继承的算法,解决了多父角色权限继承问题,在系统的安全管理中实现了基于角色和域的访问控制。
关键词:RBAC 模型;角色;权限;访问控制;域Research and Application on Multi Father Role Based RBAC ModelSHI Yong-chang, LU Shu-xi(Institute of Computer Science and Technology, Pingdingshan University, Pingdingshan 467000)【Abstract 】A problem that child role cannot obtain private permissions because of inherited relation in the Role-Based Access Control(RBAC)model is researched. The specific permission of the roles in same department or similar business, is not discussed in the past solutions, and the permission cannot be inherited by multi father role. Thus a new solution with domain and domain’s permission is presented. The method of permission management is analyzed, an algorithm to inherit permissions from one child for multi father roles is provided, and the question of inheritance is solved. The access control theory based on role and domain in the application system is realized. 【Key words 】Role-Based Access Control(RBAC) model; role; permission; access control; domain访问控制是安全技术的重要部分,而基于角色的访问控制(Role-Based Access Control, RBAC)作为目前主流的访问控制模型,成为研究的热点。
Role-basedAccess...

Users
Roles
Permissions
Within an organization, roles are relatively stable, while users and permissions are numerous and may change rapidly.
Chapters 1 and 2 display the fundamentals of access control. They are very easy to read and are illustrated through different examples.
Chapters 3, 4 and 5 explain the RBAC security model. Core features of RBAC, inheritance relationship and separation of duties are explained in details. The first of these chapters explains the core features: users, roles, permissions, role activation, user and permission assignments. Chapter 5 is on role hierarchies including inheritance and hierarchy structures. It also discusses separation of duty (SoD) and constraints in RBAC systems: types of SoD, SoD concepts in role hierarchies, SoD issues in privilege and role assignments, and temporal constraints. There are no complex mathematical functions to understand; instead, the examples that illustrate the fundamental concepts are well explained.
Fortinet FortiNAC 角色基于的动态网络访问控制概述说明书

Visibility: Comprehensive Endpoint IdentificationWith the rapid proliferation of personal mobile devices, IoT products, and Shadow IT (technologies added to the network without involving IT/cybersecurity staff), protecting countless endpoint types that are not owned, managed, or updated by corporate IT has become a significant challenge for security leaders. FortiNAC addresses this challenge in a couple of different ways:Device-to-User ProfilingFortiNAC uses multiple information and behavior sources to accurately identify everything on the network. It provides detailed profiling of wired, wireless, and even headless devices. This comprehensive agentless scanning process automatically discovers endpoints, classifying them by type and determining if the device is corporate-issued or employee-owned. FortiNAC supports enhanced profiling capabilities to ensure the trust of Windows Remote Management (WinRM) and Windows Management Instrumentation (WMI) devices. FortiNAC also offers passive scanning capabilities for identifying sensitive devices without disruption—such as industrial control systems (ICS) and their supervisory control and data acquisition (SCADA) subset systems within operational technology (OT) networks.FortiNAC also identifies individual users of devices to apply the appropriate role-based network access policies to protect critical data and sensitive assets, while ensuring compliance with all applicable industry regulations and standards. Additionally, FortiNAC gives security management teams centralized administration and reporting from a single console.Continuous Risk AssessmentFortiNAC validates an endpoint’s configuration as it attempts to join the network. If the configurationis found to be noncompliant, the connection is either prevented or the device is isolated orgranted limited-access VLAN. Users are then warned that their device must be remediated.Access is granted only after corrective measures have been taken. Even then, FortiNACperforms ongoing deep information scanning to provide continuous evaluation post-connection.4 Enforcement: Granular Access ControlsIn addition to the breadth of devices connecting to corporate networks, security architectsmust also manage an expanding variety of users, groups, and applications—which results in a dramatically higher level of network complexity.As part of the Fortinet Security Fabric architecture, FortiNAC’s tight integration with the FortiGate next-generation firewall (NGFW) enables dynamic access controls that ensure that users and devices only have access to the resources they need. Specific features include:Segmentation Based on Business IntentA flat and open internal network makes it easy for hackers, malicious users, or automated malware to roam freely across the organization in search of sensitive data and IP to exfiltrate. Supporting intent-based network segmentation, FortiGate NGFWs dynamically retrieve device details (e.g., user group, tagged information) from FortiNAC as devices connect or disconnect. FortiGate then uses this information to apply policies in order to segment network access for that specific device. Network access policies defined in FortiNAC determine the type of segmentation based on the specific business needs. FortiNAC can implement segmentation policies and change configurations on switches and wireless products from more than 70 vendors. Dynamic role-based network access controls logically create network segments that group applications, link data together, and limit access to specific groups that enhance internal network security.Simplified Guest AccessFortiNAC streamlines the secure registration process of guest users, while keeping them safely away from any parts of the network containing sensitive data. When appropriate, users can self-register their own devices (laptops, tablets, or smartphones), shifting the workload away from IT staff. If preferred, the simplified task of onboarding guests can also be delegated to designated network administrators.Automated ResponsivenessAutomation is the “holy grail” of an integrated security architecture. Instituting policy-based automated security actions helps the connected security solutions share real-time intelligence to contain potential threats before they can spread. This also helps security leaders reduce their strain on overburdened/under-resourced support teams. Without human involvement to bog down the response time, attacks and breaches can be handled with speed, efficiency, and efficacy. FortiNAC delivers real-time, automated threat responses that can immediately quarantine any suspicious endpoints or users (including IoT)—to reduce containment time from days to seconds. FortiNAC automation capabilities include:as well as centralized policy management.1Louis Columbus , “Improving Endpoint Security Needs To Be A Top Goal In 2020,” Forbes, October 27, 2019.2“2019 Cost of a Data Breach Report ,” Ponemon Institute and IBM Security, July 2019.3“Mobile Security Index 2019,” Verizon, March 2019.4“The Cost of Cybercrime: Ninth Annual Cost of Cybercrime Study ,” Accenture and Ponemon Institute, March 6, 2019.administrative dashboard. FortiNAC also features comprehensive history tracking and built-in analytics to accelerate forensic investigation and remediation efforts. It helps streamline analyst reviews by leveraging contextual awareness surrounding an alert to help quickly locate problem devices, diagnose problems, and prioritize security events. This, in turn, helps to accelerate time to resolution while reducing the burden on staff.Policy SimulationFortiNAC enables “what-if” scenarios when defining network access policies. By test-driving policies, administrators can evaluate the impact of making changes before implementing them. This feature helps organizations avoid implementing a policy that is too restrictive or too open and adversely impacts users and their devices.Scalable Access Control for Every Connected EndpointEndpoint devices will remain a prime target for cyber criminals as long as they offer an easy, exploitable pathway to valuable data and intellectual property. FortiNAC helps security architects protect their connected endpoints from threats. Beyond its robust validation and continuous monitoring capabilities, FortiNAC uses dynamic role-based network access control to create network segments that keep compromised devices from causing extended problems across the organization. Automated containment responses across the Fortinet Security Fabric go even further to protect enterprises from the onslaught of sophisticated, endpoint-targeted attacks.Beyond these core capabilities, FortiNAC can be deployed as a hardware appliance, a virtual appliance, or a cloud service—offering security architects a flexible, third-generation NAC solution that can adapt to the unique needs of any environment. Designed with scalability in mind, FortiNAC also helps lower total cost of ownership by not requiring a server in every deployment location. It also leverages existing directory, networking, and security infrastructures to protect existing investments and minimize disruption.5Instantaneous Containment and ComplianceFortiNAC offers a broad and customizable set of automation policies that can instantlytrigger containment settings across other Security Fabric elements (e.g., FortiGate,FortiSwitch, FortiAP) when a targeted behavior is observed. Potential threats are containedby isolating suspect users and vulnerable devices, or by enforcing a range of responsiveactions. As a compensating control for IoT devices with weak security, FortiNAC monitorsfor unusual behavior and automatically quarantines suspicious endpoints. For example,if an IoT device starts pinging a DNS server, it will be tracked, an alert will be generated,and the port can be immediately locked down while awaiting analyst review.Control features are accessed via a highly customizable, easy-to-use, web-based。
CISSP认证考试(访问控制)模拟试卷1(题后含答案及解析)

CISSP认证考试(访问控制)模拟试卷1(题后含答案及解析)题型有:1.1.Which of the following does not correctly describe a directory service?A.It manages objects within a directory by using namespaces.B.It enforces security policy by carrying out access control and identity management functions.C.It assigns namespaces to each object in databases that are based on the X.509 standard and are accessed by LDAP.D.It allows an administrator to configure and manage how identification takes place within the network.正确答案:C解析:C正确。
大多数企业都有包含公司网络资源和用户信息的某种类型的目录。
基于X.500标准(不是X.509)和一种协议类型,即轻量目录访问协议(Lightweight Directory Access Protocol,LDAP),大多数目录都遵循分层的数据库结构,允许主体和应用程序与这个目录进行交互。
应用程序可以通过向目录提出一个LDAP请求来获得某一特定用户的信息;用户也可以使用相似请求获得某个特定资源的信息。
目录服务基于X.500标准,给数据库中的每个客体分配一个LDAP可访问的可分辨名称(distinguished names)。
每一个可分辨名称都代表着某个特定客体的属性的集合,并作为一个条目存储在目录中。
A不正确。
因为层次数据库中的客体都是通过日录服务进行管理的。
访问控制模型简介

——访问控制矩阵
按列看是访问控制表内容
按行看是访问能力表内容
——MAC的安全级别
强制访问策略将每个用户及文件赋于一个访问级 别,如,最高秘密级,秘密级,机密级及无级别 级。其级别为依次降低,系统根据主体和客体的 敏感标记来决定访问模式。访问模式包括: 下读:用户级别大于文件级别的读操作; 上写:用户级别小于文件级别的写操作; 下写:用户级别等于文件级别的写操作; 上读:用户级别小于文件级别的读操作;
Discretionary Access Control(DAC)自主访问控 制模型 自主访问控制模型是根据自主访问控制策略建立的一 种模型,允许合法用户以用户或用户组的身份访问策 略规定的客体,同时阻止非授权用户访问客体,某些 用户还可以自主地把自己所拥有的客体的访问权限授 予其他用户
——DAC模型特点
——RBAC特点
RBAC模型是20世纪90年代研究出来的一种新 模型,从本质上讲,这种模型是对前面描述 的访问矩阵模型的扩展。这种模型的基本概 念是把许可权(Permission)与角色(Role) 联系在一起,用户通过充当合适角色的成员 而获得该角色的许可权
五、LBAC模型
现有的基于层次的访问控制模型(LBAC)就是基 于工作流视角的。它通常被用于由多个工作流管 理系统实现的组织间(inter-organizational) 工作流。原因是LBAC采用了一个独立的访问层 (Access Layer,AC),它封装了该组织的访问 控制系统。由访问层将组织内的工作流转化为组 织间的工作流,而采用同样的方式对组织内和组 织间的工作流的访问控制问题进行处理。概括说 来,所谓工作流视角的LBAC,就是指把整个访问 控制过程看作是层次化的工作流的实现
访问控制和系统审计

Access and Information Flow Controls
所有的客体都只有一个主体; 对于每个试图访问客体的操作,都必须检验权限; 有且仅有主体和主体指定的用户可以更改权限; 管理员可以取得客体的所有权,但不能再归还; 系统必须保证自身不能被管理员以外的用户改变; 系统必须有能力对所有的操作进行记录,并且只有
管理员和由管理员指定的用户可以访问该记录。 SCO UNIX 和 Windows NT 属于 C2 级
2:no easy way to keep track of who has access to a file.
3:a file requires access to other files.
Embed the passwords Specify all file passwords up front Supply the password for each additional file
C1级:(Discretionary Security Protection)自主安全保护。这一级的系 统必须对所有的用户进行分组;对于每 个用户必须注册后才能使用;系统必须 记录每个用户的注册活动;系统对可能 破坏自身的操作发出警告。
计算机安全等级划分
C2级:(Controled Access Protection)可控 访问保护。在C1级基础上,增加了以下要求:
基于重复角色和任务优先级的访问控制模型

大连理工大学
硕士学位论文
基于重复角色和任务优先级的访问控制模型
姓名:***
申请学位级别:硕士
专业:软件工程
指导教师:***
20061217
大连理工大学硕士学位论文
图3.4实际价值率
F谵.3.4HitVahmRatio
HVF算法与EDF算法相比,在任务数量较少的情况下EDF算法优于HvF算法,但是当任务数量达到15以后,HVF算法表现出更好的性能,其原因在于HVF算法更加偏重于考虑任务的价值,因此在任务数量越大的情形下实现了更高的价值累积。
3.4.2截止期保证率
截止期保证率(deadlineguaranteeratio,简称DGR)是指任务被满足截止期的情况,它体现了一个调度算法的健壮性。
图3.5给出了RF算法、HVF算法、EDF算法与PTB算法在不同任务数量下的DGR变化趋势,其中x轴是标称任务数量,Y轴表示不同调度算法的截止期保证率DGR。
图3.5截止期保证率
Fig.3.5Deadlineguaranteeratio
从图中我们不难发现,EDF在任务数量较少的情形下,其DGR是最高的,其中主要原因在于它更侧重于任务的开始时间,但是随着任务数量的增加,它的性能急剧下降,健壮性比较差。
HvF算法的DGR始终是最小的,其主要原因在于它更侧重于任务的价值,。
网络信息安全的物理安全措施

入侵检测
利用入侵检测技术,实时
2
监测网络流量和系统日志
,发现异常行为和攻击企
图。
门禁控制
3 建立门禁系统,对重要区
域进行出入控制,限制未 授权人员的访问。
安全漏洞与风险评估
漏洞扫描
定期进行漏洞扫描,发现网络信 息系统存在的安全漏洞和弱点。
持续监控
对修补后的系统进行持续监控, 确保漏洞修补的有效性。
定期审查和更新安全政策
根据组织发展和安全威胁的变化,定期对安全政策进行审查和更新。
安全意识教育与培训
开展安全意识教育活动
通过讲座、培训课程等形式,提高员工对物理安全的认识和重视程度。
定期进行安全培训
针对不同岗位和职责的员工,提供针对性的安全培训,提高员工的安全操作技能 。
安全事件应急响应
建立安全事件应急预案
审计日志
记录用户对信息系统的访问和操作,以便后续审查和分析。
监控系统
实时监测网络和系统的运行状态,及时发现异常行为和潜在 的安全威胁。
Part
02
物理环境安全
场地安全
场地选址
选择具备良好自然条件和安全防 护的场地,远离潜在的安全隐患 区域,如危险品仓库、机场等。
物理访问控制
实施严格的物理访问控制,包括 门禁系统、监控摄像头和保安人 员等,确保只有授权人员能够进 入关键区域。
安全设备监控
对安全设备进行实时监控,及时发现和处理安全 事件,确保网络信息系统的稳定运行。
3
安全设备更新与升级
定期对安全设备进行更新和升级,以应对新的安 全威胁和漏洞,提高安全设备的防护能力。
Part
04
物理安全管理与培训
安全政策与制度
IBM Cloud Object Storage System 版本 3.14.6 角色权限管理说明

(Container Mode only) This role must be assigned to all accounts that interact with the Service API.
User accounts either can be created to be local to the system or linked to a directory server account on Active Directory (AD), Lightweight Directory Access Protocol (LDAP) or Keystone.
Table 1. Roles available to Manager Web Interface
Role
Privileges
Super User
Perform any action within the Manager Web Interface except read from or write to a Vault.
Every time a User attempts to access a URL in the Manager Web Interface, it checks: v What Privilege can view the page? v What Roles have this Privilege? v Does the current User have one (or more) of those roles?
Security Officer
Manage accounts and security within the Manager Web Interface.
Operator
RBAC:基于角色的访问控制(Role-BasedAccessControl)

RBAC:基于⾓⾊的访问控制(Role-BasedAccessControl)本⽂只讨论两种基于⾓⾊的访问控制的不同点,不涉及权限设计的数据库设计。
基于⾓⾊的访问控制(Role-Based Access Control)可分为隐式⾓⾊访问控制和显式⾓⾊访问控制。
隐式⾓⾊访问控制:没有明确定义⼀个⾓⾊到底包含了哪些可执⾏的⾏为。
显式⾓⾊访问控制:也称为“基于资源的访问控制”,因为这种权限设计的粒度细化到了资源层⾯,资源有很多种,⽐如数据库表的增删查改、url、菜单、按钮等等。
来看⼀个隐式⾓⾊访问控制的例⼦:if (user.hasRole("Project Manager")) {//页⾯显⽰某个按钮} else {//页⾯不显⽰某个按钮}如果需求改变了,另外⼀个⾓⾊要显⽰该按钮,那么就必须改变上⾯的代码为:if (user.hasRole("Project Manager") || user.hasRole("Department Manager") ) {//页⾯显⽰某个按钮} else {//页⾯不显⽰某个按钮}那以后如果还有其他⾓⾊呢,可以想象,这种权限设计⽅式有多糟糕。
再来看⼀个显⽰⾓⾊访问控制(基于资源的访问控制)的例⼦:if (user.isPermitted("projectReport:view:12345")) {//页⾯显⽰某个按钮} else {//页⾯不显⽰某个按钮}如果现在的需求改了,那么只要在该⾓⾊对应的权限集合⾥⾯再加上"projectReport:view:12345"这⼀资源访问权限即可,⽐隐式⾓⾊访问权限需要去修改源代码要⽅便得多。
rbac实现原理

rbac实现原理Role-Based Access Control (RBAC) is a widely used access control model that provides a flexible and scalable approach to managing permissions within an organization. It is based on the concept of roles, which represent a collection of permissions that define a user's authority in the system. RBAC ensures that users only have access to the resources and actions that they are authorized to perform based on their assigned roles. In this article, we will explore the principles and implementation of RBAC.RBAC consists of three primary components: users, roles, and permissions. Users represent individuals or entities that interact with the system. Roles define a set of permissions that are associated with specific responsibilities or job functions. Permissions represent discrete actions or operations that can be performed on system resources.The core principle of RBAC is that access to resources is granted based on the user's role, not their individual identity. This decoupling of role and user simplifies the management of access control, particularly in large organizations with complex permission requirements.RBAC implementation usually involves several steps:1. Role Identification: The first step is to identify the roles that exist within the system. This can be done by analyzing the responsibilities and job functions of users in the organization. Roles should be defined in a way that closely aligns with the organization's structure and business processes.2. Role Assignment: Once roles are identified, they need to be assigned to users. This assignment can be based on various factors such as the user's job function, department, or project involvement. Roles can be assigned to individual users or to groups of users.3. Permission Assignment: Permissions need to be associated with roles to define what actions the users with those roles are allowed to perform. Permissions should be granular and specific, allowing for fine-grained control over access to resources.4. Role Hierarchy: Roles can be organized in a hierarchical structure to simplify role assignment and permission management. This allows certain roles to inherit permissions from higher-level roles. For example, a manager role may have additional permissions compared to a regular employee role.5. Role-Based Access Control Policies: RBAC policies are defined to specify the rules and conditions that govern access control. These policies determine which users can assume which roles, which roles can perform which actions, and under what conditions access is granted or denied.6. Enforcement Mechanisms: RBAC is enforced through various mechanisms such as access control lists, authorization modules, or security middleware. These mechanisms verify the user's role and check if they have the necessary permissions to perform the requested action. Role-based access control can be implemented at different levels, including the operating system, database, or application layer.RBAC offers several benefits for organizations:1. Access Control Simplification: RBAC simplifies the management and administration of access control by organizing permissions into roles. This reduces the administrative overhead of managing individual user permissions.2. Scalability: RBAC is highly scalable, allowing organizations to easily add or remove users, roles, and permissions as the organization evolves and grows.3. Security: RBAC enhances security by ensuring that users only have access to the resources and actions that are necessary for their job function. This reduces the risk of unauthorized access and data breaches.4. Compliance: RBAC helps organizations meet regulatory and compliance requirements by providing a systematic approach to managing access control. RBAC provides auditable records of user roles and permissions, enabling organizations to demonstrate compliance to auditors.In conclusion, RBAC is a powerful access control model that provides a flexible and scalable approach to managing permissions within an organization. By organizing permissions into roles and associating them with users, RBAC simplifies access control administration and enhances security. RBAC's principles and implementation steps help organizations achieve effective access control and compliance with regulatory requirements.。
基于实例团队和任务的RBAC模型

基于实例团队和任务的RBAC模型许俊峰;许珊珊;刘鑫【摘要】该文针对现有的基于角色的访问控制模型的缺陷和工作流管理系统的特征,提出了一种新的访问控制和授权管理模型,称之为基于实例团队和任务的RBAC 模型.模型的主要思想是将权限分配给任务,再将任务分配给角色,任务实例启动执行时指派实例团队,角色通过任务与权限相关联,用户通过角色和实例团队获取权限.该模型解决了传统的基于角色访问控制中仅仅通过角色来分派权限的缺陷,保证了权限授予对应角色的用户集合中的某一确定用户,提高了系统的安全性和灵活性.【期刊名称】《杭州电子科技大学学报》【年(卷),期】2010(030)006【总页数】4页(P56-59)【关键词】角色;任务;访问控制;实例团队;工作流【作者】许俊峰;许珊珊;刘鑫【作者单位】杭州电子科技大学理图形图像研究所,浙江,杭州,310018;杭州电子科技大学理图形图像研究所,浙江,杭州,310018;杭州电子科技大学理图形图像研究所,浙江,杭州,310018【正文语种】中文【中图分类】TN4010 引言近年来,信息管理系统随着计算机应用技术的快速发展变的越来越复杂,系统的安全问题越来越重要,而访问控制是整个系统安全的重要组成部分。
人们提出了各种各样的满足系统安全管理需求的访问控制模型。
传统的访问控制模型主要包括自主访问控制模型(Discretionary Access Control,DAC)和强制访问控制模型(Mandatory Access Control,MAC)等。
由Sandhu R提出的RBAC96(Role-Based Access Control,RBAC)模型[1]和ARBAC97模型[2]引进了“角色”的概念。
在RBAC模型中,先将访问权限先分配给角色,然后再将用户分配给适当的角色,从而获得相应角色的权限。
但RBAC模型属于静态的分配权限,它没有将任务从角色中分离出来[3],而且没有考虑到工作流[4]。
TRBAC:基于信任的访问控制模型

TRBAC:基于信任的访问控制模型刘武;段海新;张洪;任萍;吴建平【摘要】访问控制是根据网络用户的身份或属性,对该用户执行某些操作或访问某些网络资源进行控制的过程.对现有访问控制模型进行分析,并针对其不足对RBAC 模型进行了扩展,提出了基于信任的访问控制模型TRBAC(trust based access control model).该模型可以提供更加安全、灵活以及细粒度的动态访问授权机制,从而提高授权机制的安全性与可靠性.%Access control is a process which controls users to execute some operations or access some network resources according to the users' identity or attribution. The discretionary access control and mandatory access control are two main access control modes which are broadly used in secure operating systems. Discretionary access control is based on user identity and/or groups and mandatory access control is usually based on sensitivity labels. Neither of these two modes can completely satisfy the requirements of all access control. Discretionary access control is too loose to restrict the propagation of privileges while mandatory access control is too rigid to use flexibly. This paper analyzes current access control models, and extends the RBAC (role based access control) model aiming at its deficiency, and based on which we propose a trust based access control model (TRBAC). The TRBAC model can provide more security, flexible and fine-grained dynamic access control mechanism, and therefore improve both the security and the reliability of authorization mechanism.【期刊名称】《计算机研究与发展》【年(卷),期】2011(048)008【总页数】7页(P1414-1420)【关键词】信任;可信计算;访问控制;网络安全;网络管理【作者】刘武;段海新;张洪;任萍;吴建平【作者单位】清华大学信息网络工程研究中心北京 100084;清华大学信息网络工程研究中心北京 100084;清华大学信息网络工程研究中心北京 100084;重庆师范大学经济与管理学院重庆400047;清华大学信息网络工程研究中心北京 100084【正文语种】中文【中图分类】TP393.07访问控制[1]是根据网络用户的身份或属性对该用户执行某些操作或访问某些网络资源进行控制的过程.访问控制有3个目的:1)防止非法用户侵入系统,访问受保护的网络资源或服务;2)为合法用户授予适当权限,允许其访问受保护的网络资源或服务;3)防止合法用户访问未被授权的网络资源或服务[2-3].本文分析了现有访问控制模型,针对其不足,对RBAC模型进行了扩展,提出了基于信任的访问控制模型TRBAC(trust based access control model),并通过实验对该模型进行验证.1 访问控制模型研究综述目前的主流访问控制模型[4-6]包括:自主访问控制(DAC)、强制访问控制(MAC)以及基于角色的访问控制(RBAC),以下分别进行分析.1.1 自主访问控制自主访问控制(discretionary access control,DAC)[7]是在确认主体身份的基础上,根据其身份标识与权限的对应关系进行授权.DAC的基本思想是客体所有者自主决定其他主体对该客体的访问权限,而获得访问权限的主体还可以将自己的权限进一步授予其他的主体.通过这种方式,DAC的授权就形成了一个链式结构,例如主体A,B,C,D之间存在一个授权关系:A→B→C→D,这表示主体A将对某个客体o的权限授予主体B,主体B又将该权限授予主体C,最后C将权限又传递给主体D,这样,主体A,B,C,D都拥有了对客体o的相同访问权限.在这个链式结构中,每个主体都只能对自己的后继节点进行权限管理,而无法对更下一层的节点进行管理.DAC的优点是主体对授权过程具有极大的灵活性,但缺点是权限的授予过程存在链式结构,它能控制主体能否直接获得对客体的访问权限,但不能控制主体间接获得对客体的访问权限,因此安全性能相对较低.另外在权限管理方面,系统需要维护不同主体对不同客体的不同访问权限之间的关系,权限管理复杂性较高.1.2 强制访问控制强制访问控制(mandatory access control,MAC)[8]是依据主体以及客体的安全属性来决定是否进行访问授权.MAC的基本思想是:每个主体、客体都有一个代表其安全属性的标签.其中,主体的安全属性反映了主体能够获得的权限等级,客体的安全属性表示客体的敏感程度.MAC通过比较主体与客体的安全属性来决定用户是否能够获得访问权限.MAC的优点是在权限授予过程中,不仅需要检查主体是否对客体具有操作权限,还需要检查主、客体的安全属性是否符合要求,这使得授权过程更加安全.因此,MAC适合对安全性要求较高的应用系统.MAC的缺点是权限管理系统必须为每个主体或客体分配安全属性,并需要仔细定义主、客体安全属性之间的对应关系,从而防止出现合法主体不能对授权客体进行操作,以及非法主体能够对未授权客体进行操作的现象.因此,MAC的权限管理难度较大.1.3 基于角色的访问控制基于角色的访问控制(role-based access control,RBAC)[1]通过在用户集合与权限集合之间建立角色集合,将权限的授予过程分为2步进行.首先,权限管理根据应用系统的组织结构设置不同的角色,并建立了角色与权限之间的映射关系:“角色→权限子集”,在这个关系中,角色成为权限子集的所有者.其次,权限管理根据主体身份的不同为其分配对应的角色,这建立了主体与角色之间的映射关系:“主体→角色”.在这个关系中,主体是角色的使用者.通过上述2个步骤,RBAC就建立起了主体与权限的映射关系:“主体→角色→权限子集”.RBAC的优点是避免了DAC与MAC中用户与权限之间的直接映射关系,而建立了一个分层的间接映射关系.这个方法有效地降低了权限管理的复杂度,具有较高的灵活性.当然,RBAC模型也存在许多不足之处:首先,RBAC模型在将角色分配给用户时,只验证用户的身份真实性,而没有考虑用户的行为可信性.其次,RBAC模型采用预先分配方式为角色进行访问授权,而在用户实际使用权限的过程中并不进行监管与控制,当发现用户进行恶意操作时,系统很可能已经受到侵害. 随着对信任模型研究的深入,一些学者提出了将信任集成到传统的访问控制模型中[9-10].例如,Chakraborty等人在RBAC模型的基础上,提出了TrustBAC [11]模型.该模型在用户获得角色之前,首先计算该用户的信任值,然后根据信任值决定用户能够获得该角色,即用户的信任值决定其能否获得对应的权限.TrustBAC模型克服了RBAC模型动态性、监管性不足等缺点,能够动态地进行角色分配.但它也存在一定的不足之处,例如只要用户的信任值达到一定程度,都能获得对应角色的全部权限,而不考虑各个权限对用户信任值的不同需求,这给恶意用户提供了绕过访问控制的机会:他们可以通过先积累信任值,获得较高等级的角色权限后再对系统进行破坏.2 基于信任的访问控制模型TRBAC在上一节中,对现有访问控制模型进行了介绍,发现它们存在着种种不足.针对这些不足,本文对RBAC模型进行了扩展,提出一种基于信任的访问控制模型TRBAC.该模型从权限对用户的具体要求出发,综合计算用户的多种信任特征,实现细粒度、灵活的授权机制,从而更为安全合理地为用户分配所需权限.2.1 模型结构图1所示为本文提出的TRBAC模型结构:Fig.1 Structure of TRBAC model.图1 TRBAC模型结构定义1.TRBAC模型可以形式化地定义如下:1)用户.USER={user1,user2,…,usern},系统中用户的集合.用户指一个可以独立访问系统服务的主体,可以是自然人,也可以是具有自主行为的网络程序等.2)服务.SERVICE={service1,service2,…,servicen},系统为用户提供的服务集合.3)操作.OPERATION={read,write,execute,…},用户对服务可以执行的操作集合.4)条件.CONDITION,用户对服务可以执行操作时的条件.在本模型中,条件是指用户为了获得对应权限,其信任值应该达到的信任阈值.5)权限.PERMISSION={p1,p2,…,pn},权限集合.权限是对系统提供的服务进行访问的许可.在本模型中,将权限定义为pi=(op,s,condition),其中服务s是访问控制系统的真正客体,操作op是作用在该服务上的一种访问方式,condition∈CONDITION是用户被允许执行该操作时信任值应该达到的阈值条件. 6)角色.ROLE={role1,role2,…,rolen},系统设置的角色集合.角色是指一个系统中的工作或位置,代表对系统中某些部分进行操作的资格或权利.角色role可以看作是将权限分配给用户的映射函数,即P=role(user),其中P⊆PERMISSION.7)信任值.TRUSTVALUE,根据信任计算算法得到的用户信任值,其值域为[0,1].8)上下文.CONTEXT,计算信任值时所需要的上下文环境.9)会话.SESSION,会话集合.会话对应于一个用户和一组激活的角色,表示用户获得角色的过程.一个用户可以进行多次会话,在每次会话中获得不同的角色,这样用户也将具有不同的访问权限.10)URA⊆USER×ROLE:用户角色分配,是用户集合USER到角色集合ROLE的多对多的映射关系,表示一个用户可以获得多个角色,一个角色也可以被分配给多个用户.(user;role)∈URA:表示用户user拥有角色role,即表示用户user可以使用角色role所具有的权限.11)UTA⊆USER×TRUSTVALUE:用户信任值分配,表示用户集合USER到信任值集合TRUSTVALUE的多对多映射关系,即一个用户可以拥有不同的信任值,从而表示用户不同的信任特征.12)RPA⊆ROLE×PERMISSION:角色权限分配,是权限集合PERMISSION到角色集合ROLE的多对多映射关系.PRA(p,role)表示权限p被赋予给角色role,即拥有角色role的用户能够使用权限p.13)PA⊆TRUSTVALUE×PERMISSION,权限激活,是指根据用户信任值以及权限的条件判断该用户能否使用该权限的过程.2.2 信任值计算不同的上下文可能要求考虑该用户不同的信任特征,采用的信任计算算法也可能有不同,各有侧重.如图2所示,本文先对上下文进行如下定义:定义2.CONTEXT=(TF,TA),其中:1)TF={tf1,tf2,…,tfn}表示上下文对用户所要求的信任特征子集,子集中的元素定义为:tfi=(featurei,wi),featurei表示用户的某种信任特征名称,wi表示在计算用户信任值时,该信任特征所占的比重,wi的值越大,表示该信任特征越重要.2)TA={ta1,ta2,…,tan}表示计算信任值时使用的算法名称,例如average,weight等.average表示计算各信任特征的平均值,weight表示根据权重计算这些信任特征的加权平均值.因此,在某个上下文c中,用户user的对应信任值为:Fig.2 The context and trust feature graph.图2 上下文与信任特征关系图2.3 授权过程在TRBAC模型中,用户获得权限的过程分为2部分:首先,用户进行身份认证(autentication).通过身份认证后,TRBAC模型建立会话,并根据用户的身份标识为其分配角色(role assignment).在这个过程中,用户获得了使用角色所拥有的权限的资格,但此时还不能使用这些权限.将此时用户所拥有的权限集称为基本权限集(basic permission set,BPS).定义3.基本权限集是指在一个系统中,用户(user)根据其身份标识得到的角色(role)所具有的权限集合,即BPSuser=role(user).接下来,用户在访问服务之前,TRBAC模型根据上下文对用户进行信任计算(trust value computing),并根据所请求权限的条件判断用户是否能够使用该权限.当用户的信任值达到使用权限的条件后,用户获得授权并访问服务(access services).在用户访问服务之后,TRBAC模型对用户的行为进行评价(behavior assessment).当用户再次访问服务时,重新进行上述过程.在这个过程中,用户的行为结果会对下一次访问授权产生影响,从而保证用户使用权限的安全性.整个过程如图3所示:Fig.3 The experimental environment of TRBAC model.图3 TRBAC模型实验环境3 实验与评价3.1 实验场景本实验以一台文件服务器(FTP)的访问控制过程来举例说明TRBAC模型的应用,如图4所示:Fig.4 The context and trust feature relationship graph.图4 上下文与信任特征关系图在实验中,建立了2个角色:role1与role2.其中:1)角色role1具有权限集合P1,该权限集合中的权限包括:op11=(d,s1,0.2),op12=(d,s2,0.4),op13=(d,s3,0.6),op14=(u,s4,0).角色role2具有权限集合P2,该权限集合中的权限包括:op21=(d,s1,0.2),op22=(d,s2,0.4),op23=(u,s4,0).在权限的设置中,d表示下载操作,u表示上传操作.从权限的设置可以看到,只有当用户的信任值超过权限的阈值后,服务器才允许该用户获得对应的下载速率.同时,为了鼓励用户向服务器上传文件,将用户执行上传权限(op14与op23)的阈值设置为0,即允许任何用户上传文件,从而积累信任值.2)本文还设置了计算用户信任值时所需考虑的上下文(c1与c2).在本实验中,由于用户的信任值来源于其上传操作,因此设置c1=c2=((1,tfupload),“weight”),表示只考虑用户上传操作的信任特征值tfupload,且使用加权平均的算法来计算用户的综合信任值:3)s1,s2,s3,s4的下载速率(download speed)均为100KBps.根据用户执行上传操作的情况计算其上传信任特征值.在实验中,本文将用户上传操作所得到的评分值设为rupload∈[0,1],则其上传信任特征值为:其中,α∈[0,1]为历史因子,表示用户历史信任值在当前信任值中所占的比重.在本实验中,α=0.4.3.2 实验结果在实验中,本文模拟了2个用户user1与user2,分别对应角色role1与role2,他们通过向文件服务器上传文件获得信任值,并根据该信任值来激活不同的权限,以获得相应的下载速率.图5显示了用户user1的信任值与下载速率.实验结果表明:用户user1的信任值越高,能获得的下载速率越高,这也表明能获得的权限也就越大.而当其信任值降低时,相应的下载速率也被降低,尤其是当信任值低于角色role1的所有权限的条件时,用户也就无法获得任何的权限(下载速率为0).Fig.5 Trust value and download speed graph of user user1.图5 用户user1的信任值与下载速率信任值越高,用户能获得的下载速率越高,这也表明用户能获得的权限也就越大.而当其信任值降低时,相应的下载速率也被降低,尤其是当信任值低于角色role1的所有权限的条件时,用户也就无法获得任何的权限(下载速率为0).图6显示了用户user2的信任值与下载速率.从图6中可以得出以下结论:Fig.6 Trust calue and download speed graph of user user2.图6 用户user2的信任值与下载速率1)与图5类似,用户user2的信任值越高,能获得的下载速率越高,这表明用户能获得的权限也就越大.而当其信任值降低时,相应的下载速率也被降低.尤其是当信任值低于角色role2的所有权限的条件时,用户也就无法获得任何的权限(下载速率为0).2)在角色role2的权限集{p21,p22,p23}中,所有权限的最大下载速率只有200KBps,因此,即使用户user2的信任值可以到达权限p13的信任阈值(0.6),他也无法获得该权限.这就避免了用户通过积累信任值来获得更大权限的可能.为了对比TRBAC模型的安全性,本文在同样的实验场景中模拟实现了TrustBAC模型[11].在本实验中,角色role1与role2所具有的权限集合保持不变.同时,设置用户获得角色role1的信任阈值为0.6,而获得角色role2的信任阈值为0.4. 图7与图8分别显示了2个角色的用户的信任值与下载速率.从实验结果中可以看出:1)用户的信任值越高,从TrustBAC获得的角色等级越高:当信任值超过0.6时,用户可以获得角色role1;低于0.6而高于0.4时,可以获得角色role2;低于0.4则无法获得任何角色.2)用户获得角色后,可以使用该角色中的所有权限.实验结果显示,用户总是使用角色权限集合中下载速率最大的权限(获得角色role1时下载速率为500KBps,获得角色role2时下载速率为200KBps).Fig.7 Trust value and download speed graph of user role1.图7 用户role1的信任值与下载速率通过以上2个实验可以看出:首先,TRBAC模型克服了TrustBAC模型安全性不足的缺点,用户无法利用自己的信任值从系统中无限制地获取任意等级的角色,也就无法获得更高的访问权限.Fig.8 Trust value and download speed graph of user role2.图8 用户role2的信任值与下载速率其次,在TRBAC模型中,用户在使用权限前进行信任评估,根据信任值决定其获得相应的权限;而在TrustBAC模型中,用户只要获得了角色,便可以使用所有的权限.因此与TrustBAC模型相比,TRBAC模型能够在更细的粒度上实现对访问权限的控制.最后,TRBAC模型在用户使用角色的权限集合的过程中,对其行为可信性进行实时评估,用户当前的行为将影响其随后的访问权限;而TrustBAC模型只是在用户下一次获取角色前才重新评估,用户当前的行为并不对本次会话中的其他访问产生影响.因此TRBAC模型具有更好的动态性,能够及时制止用户的异常行为.4 结论本文分析了现有访问控制模型的不足,并在RBAC模型的基础上,提出了基于信任的访问控制模型TRBAC.与传统RBAC模型以及TrustBAC模型相比,TRBAC模型的优点表现在:1)增强了授权的动态性.TRBAC模型克服了RBAC静态分配权限的缺点,根据用户的信任值动态地决定授权,使模型能够随时发现用户的异常行为并及时作出反应. 2)增强了授权的安全性.TRBAC模型引入了基本权限集的概念,并根据用户的当前信任值决定是否授权,而不是根据用户的角色一次性地授予所有权限.TRBAC模型克服了TrustBAC模型安全性不足的缺点,使得用户无法利用自己的信任值提升所能获得的角色等级,用户获得的最大权限被限定在基本权限集的范围内.3)细化信任计算的粒度.在计算信任值时考虑不同上下文对用户不同信任特征的要求,使得信任值所反映的用户行为更加准确,对权限分配的控制也就更加精确.参考文献[1]Sejong O,Seog P.Task-role-based access control model[J].Information System,2003,28(6):533-536[2]Liu Wu,Duan Haixin,Zhang Hong,et al.Study on trust basedP2Pnetwork security management[J].Journal on Communications,2008,29(11):12-17(in Chinese)(刘武,段海新,张洪,等.基于信任的P2P网络安全管理体系结构研究[J].通信学报,2008,29(11):12-17)[3]Lin Chuang,Feng Fujun,Li Junshan.Access control in new network environment[J].Journal of Software,2007,18(4):955-966(in Chinese)(林闯,封富君,李俊山.新型网络环境下的访问控制技术[J].软件学报,2007,18(4):955-966)[4]Sandhu R,Coyne E J,Feinstein H L,et al.Role-based access control models[J].IEEE Computer,1996,29(2):38-47[5]Sandhu R,Bhamidipati V,Munawer Q.The ARBAC97 model for role-based administration of roles[J].ACM Trans on Information and System Security(TISSEC),1999,2(1):105-135[6]Sandhu R,Munawer Q.The ARBAC99model for administration of roles[C]//Proc of the 15th Annual Computer Security Applications Conf.Piscataway,NJ:IEEE,1999:229-238[7]Wei L K,Jarzabek S.A generic discretionary access control system for reuse frameworks[C]//Proc of the 22nd Int Computer Software and Applications Conf.Piscataway,NJ:IEEE,1998:356-361[8]Fan Yanfang,Han Zhen,Liu Jiqiang,et al.A mandatory access control model with enhanced flexibility multimedia informationnetworking and security[C]//Proc of the Int Conf on Digital Object Identifier 2009.Piscataway,NJ:IEEE,2009:120-124[9]Li N,Mitchell J C,Winsborough W H.Design of a rolebased trust-management framework[C]//Proc of the IEEE Symp on Security and Privacy.Washington,DC:IEEE Computer Society,2002:114-130 [10]Blaze M,Feigenbaum J,Lacy J.Decentralized trust management[C]//Proc of the 17th Symp on Security and Privacy.Los Alamitos:IEEE Computer Society,1996:164-173[11]Chakraborty S,Ray I.TrustBAC-integrating trust relationships into the RBAC model for access control in open systems[C]//Proc of the ACM Symp on Access Control Models and Technologies.New York.ACM,2006:49-58。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Role-Based Access ControlsReprinted from15th National Computer Security Conference (1992)Baltimore, Oct 13-16, 1992. pp. 554 - 563David F. Ferraiolo and D. Richard KuhnNational Institute of Standards and TechnologyTechnology AdministrationU.S. Department of CommerceGaithersburg, Md. 20899 USAABSTRACTWhile Mandatory Access Controls (MAC) are appropriate for multilevel secure military applications, Discretionary Access Controls (DAC) are often perceived as meeting the security processing needs of industry and civilian government. This paper argues that reliance on DAC as the principal method of access control is unfounded and inappropriate for many commercial and civilian government organizations. The paper describes a type of non-discretionary access control - role-based access control (RBAC) - that is more central to the secure processing needs of non-military systems than DAC. Keywords: access control, computer security, discretionary access control, integrity, mandatory access control, role, TCSEC1IntroductionThe U.S. government has been involved in developing security technology for computer and communications systems for some time. Although advances have been great, it is generally perceived that the current state of security technology has, to some extent failed to address the needs of all. [1], [2] This is especially true of organizations outside the Department of Defense (DoD). [3]The current set of security criteria, criteria interpretations, and guidelines has grown out of research and development efforts on the part of the DoD over a period of twenty plus years. Today the best known U.S. computer security standard is the Trusted Computer System Evaluation Criteria (TCSEC [4] ). It contains security features and assurances, exclusively derived, engineered and rationalized based on DoD security policy, created to meet one major security objective - preventing the unauthorized observation of classified information. The result is a collection of security products that do not fully address security issues as they pertain to unclassified sensitive processing environments. Although existing security mechanisms have been partially successful in promoting security solutions outside of the DoD [2] , in many instances these controls are less then perfect, and are used in lieu of a more appropriate set of controls.The TCSEC specifies two types of access controls: Discretionary Access Controls (DAC) and Mandatory Access Controls (MAC). Since the TCSEC's appearance in December of 1983, DAC requirements have been perceived as being technically correct for commercial and civilian government security needs, as well as for single-level military systems. MAC is used for multi-level secure military systems, but its use in other applications is rare. The premise of this paper is that there exists a control, referred to as Role-Based Access Control (RBAC), that can be more appropriate and central to the secure processing needs within industry and civilian government than that of DAC, although the need for DAC will continue to exist.2Aspects of Security PoliciesRecently, considerable attention has been paid to researching and addressing the security needs of commercial and civilian government organizations. It is apparent that significant and broad sweeping security requirements exist outside the Department of Defense. [2] , [5] , [6] Civilian government and corporations also rely heavily on information processing systems to meet their individual operational, financial, and information technology requirements. The integrity, availability, and confidentiality of key software systems, databases, and data networks are major concerns throughout all sectors. The corruption, unauthorized disclosure, or theft of corporate resources could disrupt an organization's operations and have immediate, serious financial, legal, human safety, personal privacy and public confidence impact.Like DoD agencies, civilian government and commercial firms are very much concerned with protecting the confidentiality of information. This includes the protection of personnel data, marketing plans, product announcements, formulas, manufacturing and development techniques. But many of these organizations have even greater concern for integrity. [1]Within industry and civilian government, integrity deals with broader issues of security than confidentiality. Integrity is particularly relevant to such applications as funds transfer, clinical medicine, environmental research, air traffic control, and avionics. The importance of integrity concerns in defense systems has also been studied in recent years.[7] , [8]A wide gamut of security policies and needs exist within civilian government and private organizations. An organizational meaning of security cannot be presupposed. Each organization has unique security requirements, many of which are difficult to meet using traditional MAC and DAC controls.As defined in the TCSEC and commonly implemented, DAC is an access control mechanism that permits system users to allow or disallow other users access to objects under their control:A means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certainaccess permission is capable of passing that permission (perhaps indirectly) on to any other subject (unless restrained by mandatory access control). [4]DAC, as the name implies, permits the granting and revoking of access privileges to be left to the discretion of the individual users. A DAC mechanism allows users to grant or revoke access to any of the objects under their control without the intercession of a system administrator.In many organizations, the end users do not ``own'' the information for which they are allowed access. For these organizations, the corporation or agency is the actual ``owner'' of system objects as well as the programs that process it. Control is often based on employee functions rather than data ownership.Access control decisions are often determined by the roles individual users take on as part of an organization. This includes the specification of duties, responsibilities, and qualifications. For example, the roles an individual associated with a hospital can assume include doctor, nurse, clinician, and pharmacist. Roles in a bank include teller, loan officer, and accountant. Roles can also apply to military systems; for example, target analyst, situation analyst, and traffic analyst are common roles in tactical systems. A role based access control (RBAC) policy bases access control decisions on the functions a user is allowed to perform within an organization. The users cannot pass access permissions on to other users at their discretion. This is a fundamental difference between RBAC and DAC.Security objectives often support a higher level organizational policy, such as maintaining and enforcing the ethics associated with a judge's chambers, or the laws and respect for privacy associated with the diagnosis of ailments, treatment of disease, and the administering of medicine with a hospital. To support such policies, a capability to centrally control and maintain access rights is required. The security administrator is responsible for enforcing policy and represents the organization.The determination of membership and the allocation of transactions to a role is not so much in accordance with discretionary decisions on the part of a system administrator, but rather in compliance with organization-specific protection guidelines. These policies are derived from existing laws, ethics, regulations, or generally accepted practices. These policies are non-discretionary in the sense that they are unavoidably imposed on all users. For example, a doctor can be provided with the transaction to prescribe medicine, but does not possess the authority to pass that transaction on to a nurse.RBAC is in fact a form of mandatory access control, but it is not based on multilevel security requirements. As defined in the TCSEC, MAC isA means of restricting access to objects based on the sensitivity (as represented by a label) of the information contained in the objects and the formal authorization (i.e. clearance) of subjects to access information of such sensitivity. [4]Role based access control, in many applications (e.g. [9] , [10] , [11] is concerned more with access to functions and information than strictly with access to information.The act of granting membership and specifying transactions for a role is loosely analogous to the process of clearing users (granting membership) and the labeling (associate operational sensitivities) of objects within the DoD. The military policy is with respect to one type of capability: who can read what information. For these systems the unauthorized flow of information from a high level to a low level is the principal concern. As such, constraints on both reads and writes are in support of that rule. Within a role-based system, the principal concern is protecting the integrity of information: ``who can perform what acts on what information.''A role can be thought of as a set of transactions that a user or set of users can perform within the context of an organization. Transactions are allocated to roles by a system administrator. Such transactions include the ability for a doctor to enter a diagnosis, prescribe medication, and add a entry to (not simply modify) a record of treatments performed on a patient. The role of a pharmacist includes the transactions to dispense but not prescribe prescription drugs. Membership in a role is also granted and revoked by a system administrator.Roles are group oriented. For each role, a set of transactions allocated the role is maintained. A transaction can be thought of as a transformation procedure [1] (a program or portion of a program) plus a set of associated data items. In addition, each role has an associated set of individual members. As a result, RBACs provide a means of naming and describing many-to-many relationships between individuals and rights. Figure 1 depicts the relationships between individual users, roles/groups, transformation procedures, and system objects.The term transaction is used in this paper as a convenience to refer to a binding of transformation procedure and data storage access. This is not unlike conventional usage of the term in commercial systems. For example, a savings deposit transaction is a procedure that updates a savings database and transaction file. A transaction may also be quite general, e.g. ``read savings file''. Note however, that ``read'' is not a transaction in the sense used here, because the read is not bound to a particular data item, as ``read savings file'' is.The importance of control over transactions, as opposed to simple read and write access, can be seen by considering typical banking transactions. Tellers may execute a savings deposit transaction, requiring read and write access to specific fields within a savings file and a transaction log file. An accounting supervisor may be able to execute correction transactions, requiring exactly the same read and write access to the same files as the teller. The difference is the process executed and the values written to the transaction log file.Figure 1: Role relationshipsThe applicability of RBAC to commercial systems is apparent from its widespread use. Baldwin [9] describes a database system using roles to control access. Nash and Poland [10] discuss the application of role based access control to cryptographic authentication devices commonly used in the banking industry. Working with industry groups, the National Institute of Standards and Technology has developed a proposed standard,``Security Requirements for Cryptographic Modules,'' (Federal Information Processing Standard 140-1) [11] that will require support for access control and administration through roles. To date, these role based systems have been developed by a variety of organizations, with no commonly agreed upon definition or recognition in formal standards. Role based access controls described in this paper address security primarily for application-level systems, as opposed to general purpose operating systems.3Formal Description of RBACTo clarify the notions presented in the previous section, we give a simple formal description, in terms of sets and relations, of role based access control. No particular implementation mechanism is implied.For each subject, the active role is the one that the subject is currently using: AR(s: subject) = {the active role for subject s}.Each subject may be authorized to perform one or more roles:RA(s: subject) = {authorized roles for subject s}.Each role may be authorized to perform one or more transactions:TA(r: role) = {transactions authorized for role r}.Subjects may execute transactions. The predicate exec(s,t) is true if subject s can execute transaction t at the current time, otherwise it is false:exec(s: subject, t: tran) = true iff subject s can execute transaction t.Three basic rules are required:1.Role assignment: A subject can execute a transaction only if the subject hasselected or been assigned a role:execARtran∀ssubjects⇒tt s),(()(,:,:Ο/).≠The identification and authentication process (e.g. login) is not considered atransaction. All other user activities on the system are conducted throughtransactions. Thus all active users are required to have some active role.2.Role authorization: A subject's active role must be authorized for the subject:ARsubjects∀RAs⊆)).(:s)(,(With (1) above, this rule ensures that users can take on only roles for which theyare authorized.3.Transaction authorization: A subject can execute a transaction only if thetransaction is authorized for the subject's active role:TAt sttrant⇒s∈subject∀execAR())).),(((,,:s:With (1) and (2), this rule ensures that users can execute only transactions for which they are authorized. Note that, because the conditional is ``only if'', this rule allows the possibility that additional restrictions may be placed on transaction execution. That is, the rule does not guarantee a transaction to be executable just because it is in TA(AR(s)), the set of transactions potentially executable by the subject's active role. For example, a trainee for a supervisory role may be assigned the role of ``Supervisor'', but have restrictions applied to his or her user role that limit accessible transactions to a subset of those normally allowed for the Supervisor role.In the preceding discussion, a transaction has been defined as a transformation procedure, plus a set of data items accessed by the transformation procedure. Access control in the rules above does not require any checks on the user's right to access a data object, or on the transformation procedure's right to access a data item, since the data accesses are built into the transaction. Security issues are addressed by binding operations and data into a transaction at design time, such as when privacy issues are addressed in an insurance query transaction.It is also possible to redefine the meaning of ``transaction'' in the above rules to refer only to the transformation procedure, without including a binding to objects. This would require a fourth rule to enforce control over the modes in which users can access objects through transaction programs. For example, a fourth rule such as4. )).t sexecaccessARsobjectos⇒∀subjectttranto((),,,),((,,:,::xcould be defined using a transaction (redefined to transformation procedure) to object access function access(r, i, o, x) which indicates if it is permissible for a subject in role r to access object o in mode x using transaction t, where x is taken from some set of modes such as read, write, append. Note that the Clark-Wilson access control triple could be implemented by letting the modes x be the access modes required by transaction t, and having a one-to-one relationship between subjects and roles. RBAC, as presented in this paper, thus includes Clark and Wilson access control as a special case.Use of this fourth rule might be appropriate, for example, in a hospital setting. A doctor could be provided with read/write access to a prescription file, while the hospital pharmacist might have only read access. (Recall that use of the first three rules alone requires binding the transaction program t and data objects that t can access, and only controls access to the transactions.) This alternative approach using the fourth rule might be helpful in enforcing confidentiality requirements.Another use of RBAC is to support integrity. Integrity has been defined in a variety of ways, but one aspect [8] of integrity is a requirement that data and processes be modified only in authorized ways by authorized users. This seems to be a reasonable security objective for many real systems, and RBAC should be applicable to such systems.In general, the problem of determining whether data have been modified only in authorized ways can be as complex as the transaction that did the modification. For this reason, the practical approach is for transactions to be certified and trusted. If transactions must be trusted then access control can be incorporated directly into each transaction. Requiring the system to control access of transaction programs to objects through the access function used in rule (4) might then be a useful form of redundancy, but it could involve significant overhead for a limited benefit in enforcing integrity requirements. Therefore, inclusion of a transaction to object access control function in RBAC would be useful in some, but not all applications.4Centrally Administering Security Using RBACRBAC is flexible in that it can take on organizational characteristics in terms of policy and structure. One of RBAC's greatest virtues is the administrative capabilities it supports.Once the transactions of a Role are established within a system, these transactions tend to remain relatively constant or change slowly over time. The administrative task consists of granting and revoking membership to the set of specified named roles within the system. When a new person enters the organization, the administrator simply grants membership to an existing role. When a person's function changes within the organization, the user membership to his existing roles can be easily deleted and new ones granted. Finally, when a person leaves the organization, all memberships to all Roles are deleted. For an organization that experiences a large turnover of personnel, a role-based security policy is the only logical choice.In addition, roles can be composed of roles. For example, a Healer within a hospital can be composed of the roles Healer, Intern, and Doctor. Figure 2 depicts an example of such a relationship.Figure 2: Multi-Role relationshipsBy granting membership to the Role Doctor, it implies access to all transactions defined by Intern and Healer, as well as those of a Doctor. On the other hand, by granting membership to the Intern role, this implies transactions of the Intern and Healer not the Doctor. However, by granting membership to the Healer role, this only allows access to those resources allowed under the role Healer.5Principle of Least PrivilegeThe principle of least privilege has been described as important for meeting integrity objectives. [8] The principle of least privilege requires that a user be given no more privilege than necessary to perform a job. Ensuring least privilege requires identifying what the user's job is, determining the minimum set of privileges required to perform that job, and restricting the user to a domain with those privileges and nothing more. By denying to subjects transactions that are not necessary for the performance of their duties, those denied privileges cannot be used to circumvent the organizational security policy. Although the concept of least privilege currently exists within the context of the TCSEC, requirements restrict those privileges of the system administrator. Through the use of RBAC, enforced minimum privileges for general system users can be easily achieved.6Separation of DutiesRBAC mechanisms can be used by a system administrator in enforcing a policy of separation of duties. Separation of duties is considered valuable in deterring fraud since fraud can occur if an opportunity exists for collaboration between various job related capabilities. Separation of duty requires that for particular sets of transactions, no single individual be allowed to execute all transactions within the set. The most commonly used examples are the separate transactions needed to initiate a payment and to authorize a payment. No single individual should be capable of executing both transactions. Separation of duty is an important consideration in real systems. [1] , [12] , [13] , [14] The sets in question will vary depending on the application. In real situations, only certain transactions need to be restricted under separation of duty requirements. For example, we would expect a transaction for ``authorize payment'' to be restricted, but a transaction ``submit suggestion to administrator'' would not be.Separation of duty can be either static or dynamic. Compliance with static separation requirements can be determined simply by the assignment of individuals to roles and allocation of transactions to roles. The more difficult case is dynamic separation of duty where compliance with requirements can only be determined during system operation. The objective behind dynamic separation of duty is to allow more flexibility in operations. Consider the case of initiating and authorizing payments. A static policy could require that no individual who can serve as payment initiator could also serve as payment authorizer. This could be implemented by ensuring that no one who can perform the initiator role could also perform the authorizer role. Such a policy may be too rigid for commercial use, making the cost of security greater than the loss that might be expected without the security. More flexibility could be allowed by a dynamic policy that allows the same individual to take on both initiator and authorizer roles, with the exception that no one could authorize payments that he or she had initiated. The static policy could be implemented by checking only roles of users; for the dynamic case, the system must use both role and user ID in checking access to transactions.Separation of duty is necessarily determined by conditions external to the computer system. The Clark-Wilson [1] scheme includes the requirement that the system maintainthe separation of duty requirement expressed in the access control triples. Enforcement is on a per-user basis, using the user ID from the access control triple. As discussed above, user functions can be conveniently separated by role, since many users in an organization typically perform the same function and have the same access rights on TPs and data. Allocating access rights according to role is also helpful in defining separation of duty in a way that can be enforced by the system.7Summary and ConclusionsIn many organizations in industry and civilian government, the end users do not ``own'' the information for which they are allowed access. For these organizations, the corporation or agency is the actual ``owner'' of system objects, and discretionary access control may not be appropriate. Role-Based Access Control (RBAC) is a nondiscretionary access control mechanism which allows and promotes the central administration of an organizational specific security policy.Access control decisions are often based on the roles individual users take on as part of an organization. A role specifies a set of transactions that a user or set of users can perform within the context of an organization. RBAC provide a means of naming and describing relationships between individuals and rights, providing a method of meeting the secure processing needs of many commercial and civilian government organizations. Various forms of role based access control have been described and some are used in commercial systems today, but there is no commonly accepted definition or formal standards encompassing RBAC. As such, evaluation and testing programs for these systems have not been established as they have for systems conforming to the Trusted Computer Security Evaluation Criteria. This paper proposed a definition of The requirements and access control rules for RBAC proposed in this paper could be used as the basis for a common definition of access controls based on user roles. References1 D.D. Clark and D.R. Wilson. A Comparison of Commercial and Military Computer Security Policies. In IEEE Symposium on Computer Security and Privacy, April 1987.2 Computers at Risk. National Research Council, National Academy Press, 1991.3 Minimum Security Functionality Requirements for Multi-User Operating Systems (draft). Computer Systems Laboratory, NIST, January 27 1992.4 Trusted Computer Security Evaluation Criteria, DOD 5200.28-STD. Department of Defense, 1985.5 Z.G. Ruthberg and W.T. Polk, Editors. Report of the Invitational Workshop on Data Integrity. SP 500-168. Natl. Inst. of Stds. and Technology, 1989.6 S.W. Katzke and Z.G. Ruthberg, Editors. Report of the Invitational Workshop on Integrity Policy in Computer Information Systems. SP 500-160. Natl. Inst. of Stds. and Technology, 1987.7 J.E. Roskos, S.R. Welke, J.M. Boone, and T. Mayfield. Integrity in Tactical and Embedded Systems. Institute for Defense Analyses, HQ 89-034883/1, October 1989.8 Integrity in Automated Information Systems. National Computer Security, Center, September 1991.9 R.W. Baldwin. Naming and Grouping Privileges to Simplify Security Management in Large Databases. In IEEE Symposium on Computer Security and Privacy, 1990.10 K.R. Poland M.J. Nash. Some Conundrums Concerning Separation of Duty. In IEEE Symposium on Computer Security and Privacy, 1990.11 Security Requirements for Cryptographic Modules. Federal Information Processing Standard 140-1, National Institute of Standards and Technology, 1992.12 W.R. Shockley. Implementing the Clark/Wilson Integrity Policy Using Current Technology. In Proceedings of 11th National Computer Security Conference, October 1988.13 A R. Sandhu. Transaction Control Expressions for Separation of Duties. In Fourth Aerospace Computer Security Applications Conference, December 1988.14 S. Wiseman P. Terry. A 'New' Security Policy Model. In IEEE Symposium on Computer Security and Privacy, May 1989.。
