1 Constructing Reliable Web Applications using Atomic Actions
concrete 单词

ConcreteIntroductionConcrete is a versatile building material that has been used for centuries. It is composed of cement, water, and aggregates such as sand and gravel. The mixture is poured into molds or forms and left to harden, resulting in a solid and durable structure. Concrete is widely used in construction due to its strength, durability, and affordability. In this article, we will explore the various applications, advantages, and disadvantages of using concrete.Applications of ConcreteConcrete has a wide range of applications in the construction industry. Some of its common uses include:1.Buildings: Concrete is commonly used in the construction ofbuildings, both residential and commercial. It provides structural stability and can withstand various weather conditions.2.Roads and Bridges: Concrete is widely used for constructing roadsand bridges. The durability of concrete makes it an ideal choicefor withstanding heavy traffic and harsh weather conditions.3.Dams and Reservoirs: Concrete is used to build dams andreservoirs due to its ability to withstand the pressure of largevolumes of water. It is also resistant to corrosion, making itsuitable for water-related structures.4.Foundations: Concrete is often used to create strong and stablefoundations for buildings. Its strength and ability to resistcompressive forces make it an ideal choice for this application. 5.Sidewalks and Driveways: Concrete is commonly used for sidewalksand driveways due to its durability and low maintenancerequirements.Advantages of ConcreteThere are several advantages to using concrete in construction:1. Strength and DurabilityConcrete is known for its strength and durability. It can withstand heavy loads and is resistant to fire, water, and weathering. This makes it a reliable choice for long-lasting structures.2. VersatilityConcrete can be molded into various shapes and sizes, allowing for flexible and creative designs. It can also be colored, stained, or stamped to achieve the desired aesthetic appeal.3. Low MaintenanceOnce concrete has hardened, it requires minimal maintenance. It does not rot or warp like wood and does not require periodic painting or sealing.4. Environmentally FriendlyConcrete is an eco-friendly material as it can be produced from locally available resources. It also has a long lifespan, reducing the need for frequent replacements and minimizing waste.Disadvantages of ConcreteWhile concrete has many advantages, there are also some disadvantages to consider:1. Initial CostThe initial cost of using concrete can be higher compared to other building materials. The cost of materials, labor, and equipment required for concrete construction can add up, especially for large-scale projects.2. WeightConcrete is a heavy material, which can pose challenges during transportation and construction. Special equipment may be required to handle and transport large quantities of concrete.3. CrackingAlthough concrete is strong and durable, it is prone to cracking over time. Changes in temperature, moisture, and settlement can cause cracks to form, requiring repair and maintenance.4. Environmental ImpactThe production of cement, a key component of concrete, releases a significant amount of carbon dioxide, contributing to greenhouse gas emissions. Steps are being taken to reduce the carbon footprint of concrete production through the use of alternative materials and technology.ConclusionConcrete is a widely used building material due to its strength, durability, and versatility. It has numerous applications in construction, ranging from buildings and roads to dams and foundations. While there are advantages to using concrete, such as its strength and low maintenance requirements, there are also disadvantages to consider, including the initial cost and environmental impact. As technology advances, efforts are being made to further improve the sustainability and performance of concrete in construction.。
编译原理 英文

编译原理英文Compilation Principle。
Compilation principle is a fundamental course in computer science and software engineering. It is the basis for understanding how programming languages are designed, implemented, and executed. In this document, we will explore the key concepts and principles of compilation, as well as its significance in the field of computer science.1. Introduction to Compilation Principle。
Compilation principle is the process of translating a high-level programming language into a low-level machine language that can be executed by a computer. This process involves several stages, including lexical analysis, syntax analysis, semantic analysis, code generation, and code optimization. Each stage plays a crucial role in ensuring that the final executable code is efficient and error-free.2. Key Concepts of Compilation Principle。
女性消费者网络购物的动因及障碍因素分析

题目:女性消费者网络购物的动因及障碍因素分析院系名称:专业班级:学生姓名:学号:指导教师:教师职称:摘要网络购物的崛起及其强劲的发展势头使我们无法忽略它对整个社会经济发展的作用,而在网络购物迅速发展的背后消费者行为的变化更是我们关注的一个重要问题,有人将21世纪称为“她世纪”,以女性消费者作为目标顾客群或营销对象已成为商家的共识。
随着电子商务的进一步发展,如此众多高消费力的女性网民已经形成了一个潜力极大的网络消费市场。
本论文对有关消费者网络购物的研究文献进行了综述。
分析了网络市场的特点,从网络消费者的特点和购物影响因素出发,阐述了目前网络市场的消费者状况和影响他们进行网上购物的普遍因素,既而引出了女性消费者独特的消费心理和消费行为。
论文在研究中构建了模型,通过问卷的调查和个别访谈得出了一些女性消费者网络购物的动因和障碍因素,并从产品策略、价格策略、渠道策略、促销策略四方面提出积极的对策。
通过研究,得出以下结论:影响女性网络购物的动因有:价格便宜,产品及相关信息丰富,购物方便,不想落伍,从众心理;影响女性网络购物的障碍有:安全得不到保障,商家信用得不到保障,产品信息不可靠,缺少购物感受。
关键词:女性消费网络购物动因障碍Title The Motive and Obstacles Factors Analysis of FemaleConsumers Internet ShoppingAbstractThe rise of Internet shopping and its strong momentum of development so that we can not ignore its role in the socio-economic development, and in the shopping network behind the rapid development of the changes in consumer behavior is of concern to us an important issue, some people will be the 21st century Referred to as "her Century", female consumers as the target customers or marketing businesses have become targets of the consensus. With the further development of e-commerce, high consumption of so many female Internet users has become a great potential of the Internet consumer market. This paper reviewers about the study of consumer shopping network literature. Analysis of the characteristics of the network market, from the characteristics of network consumers and shopping factors, reviewing the state of the current consumer Internet market, then leading to the female consumers unique consumer Psychology and consumer behavior. Constructing model in papers, through questionnaires the survey and individual interviews with a number of female consumers about the motive and obstacles factors of internet shopping, and from four respects that product strategy, pricing strategy, channel strategy, marketing strategy proposing positive countermeasures. This helps online retailers to market segments, then developing targeted marketing strategies and adopting corresponding marketing tool, and has a practical significance also to promote the development of China's online retail industry .Through the research, draw the following conclusions: impact on women's shopping network Cause: cheaper price, product and related information-rich, shopping convenience and do not want to fall behind, sheep mentality; impact on women's shopping network obstacles: lack of protection safety , The lack of protection business credit, product information is not reliable, the lack of shopping experience.Keywords Women's Consumption Internet Shopping Causes Obstacles目次1 引言 (1)1.1选题背景 (1)1.2研究的目的与意义 (1)1.3文献综述 (2)1.4研究的内容与方法 (4)2 研究的理论基础 (4)2.1网络环境下的消费者行为分析 (4)2.2女性消费者购物行为分析 (7)3 分析模型的建立 (8)3.1理性行动理论和计划行为理论的基本内容 (8)3.2女性网络消费行为模型的构建 (10)4 女性消费者网络购物的动因研究 (11)4.1网上消费者的需求和动机 (11)4.2女性消费者网络购物的动因 (13)5 女性消费者网络购物的障碍因素研究 (15)5.1女性消费者网络购物的障碍及相应营销建议 (15)5.2针对女性消费者的网络营销策略 (17)结论 (21)致谢 (22)参考文献 (23)附录 (25)1 引言1.1 选题背景随着互联网的普及,网络逐渐成为一种新的购物渠道。
The_14th_Five-Year_Plan_Starts_A_New_Journey_to_A_

The 14th Five-Y ear Plan Starts A New Jour-ney to A Modernized Socialist Country2021 is a year of special im-portance in China’s modern-ization process, since it is the first year of the 14th Five-Year Plan and the start of a new journey to build a modern socialist country.In a period of f ive years, the Five-Year Plan specifies future direc-tion for economic and social develop-ment in China, and is an important way for China to carry out develop-ment strategies and build consensus on development. In March 2021, the 14th Five-Year Plan for National Economic and Social Development and the Long-Range Objectives Through the Year 2035 (draft) was adopted on National People’s Con-gress and Chinese People’s Political Consultative Conference (NPC and CPPCC).According to the 14th Five-Year Plan, to promote high-quality development during the 14th Five-Year Plan period, China has to carry out a new development concept for a new pattern in a new stage, insist on deepening supply-side structural reform, establish an effective system to encourage domestic demand and build a strong domestic market, un-swervingly promote reform and open-ing-up, strengthen the leading role of domestic grand circulation and the role of international circulation in im-proving the efficiency and level of do-mestic circulation, to secure healthy and mutual stimulating domestic and international dual circulation.The new Five-Year Plan highlights high-quality developmentThe 14th Five-Year Plan had 20major indicators of five categories to assess economic and social develop-ment results, and compared with last Five-Year Plan some indicators were new, some were newly described and some were deleted.As in previous Five-Year Plans, indicators of economic development category came first. H owever, the plan had no specific expected average annual GDP growth rate for next five years, but proposed to keep the econ-omy within a reasonable range and put forward specific goals according to each year’s situation.Expected indicators are antic-ipated goals by the central govern-ment, which will be achieved mainly through independent behavior of market players. In addition to GDP growth rate, there were two otherexpected indicators for “economic de-By Audrey Guo10velopment”: annual labor productivity growth (higher than GDP), and the urbanization rate of permanent urban residents (as high as 65% by 2025), reflecting the potential of future de-velopment.In terms of innovation-driven development, the indicators will be upgraded comprehensively in 2025: the value added from core industries in the digital economy will be in-creased to 10% of GDP, the annual average growth of total R&D spend-ing will be more than 7%, accounting for a higher percentage of GDP thanduring the 13th Five-Year Plan pe-riod, and the number of high-value invention patents per 10,000 people will come to 12.The drive of digital economy for economic and social development is becoming increasingly important, so it needs forward-looking minds to develop relevant indicators, reflecting that China is aiming at leading the industrial development, promoting high-quality economic development and building a new development pat-tern during the 14th Five-Year Plan period.The indicators related to inven-tion patents had a new modifier of “high value”, meaning more attention will be paid to the quality rather than the quantity of innovation. Compared with last Five-Year Plan, “contribution of scientific and technological advanc-es to economic growth” and “Internet access” were no longer listed as major indicators, reflecting the indicators were kept pace with the times.Of the 20 main indicators, 7 were directly related to the well-be-ing of people, making the plan truly considerate to people’s livelihood, including three new, namely surveyed urban unemployment rate (lower than 5.5%), number of practicing physi-cians (physician assistants) per 1,000 people (3.2), and nursery capacity for children under 3 years per 1,000 peo-ple (4.5).Compared with the 13th Five-Year Plan, two indicators of rural population lifted out of poverty and rebuilt housing in rundown urban ar-eas were moved out, since China has won the battle against poverty.The “resources and environ-ment” category in the 13th Five-Year Plan was replaced by “ecologicalconservation”, and all such indicatorsare obligatory targets. Although thenumber was cut to 5 from 10, eachof these indicators has great effects.Obligatory targets are commitmentsto the people, and indicators thatfurther strengthen the government’sresponsibility on the basis of antici-pation. 13.5% and 18% of reductionin energy consumption and carbondioxide emissions per unit of GDPrespectively, and 24.1% of forest cov-erage rate. These indicators will fullydemonstrate the “green” economicdevelopment in China.New stage and new goals ofdevelopment require the indicatorsystem to keep pace with the times.20 main indicators not only carry onthose of previous Five-Year Plans, butalso embody the innovations requiredby the new era, as they are more inline with the situation of economicand social development in China atpresent and in next five years.Ministries and commissionsare releasing developmentplans one after anotherState-owned Assets Supervisionand Administration Commission(SASAC): The digital economy, plat-form economy and sharing economywill be vigorously developed duringthe 14th Five-Year Plan periodOn April 16, 2021 at the pressconference, secretary general andnews spokesman of the SASAC,Peng Huagang said, during the 14thFive-Year Plan period, SASAC willguide enterprises to further grasp theopportunities in a new round of tech-nological revolution and industrialtransformation, focus on key sectorsof emerging industries with goodfoundation, features and advantages,and actively take part in the con-struction of new infrastructure, new-type urbanization and key projects oftransportation and water conservancy,etc., vigorously develop digital econ-omy, platform economy and sharingeconomy. While accelerate the cul-tivation of new drives for economicdevelopment.Ministry of Ecological Envi-ronment: China exceeded 2020 car-bon emission reduction goalOn June 4, 2021, according to theMinistry of Ecological Environment,the carbon emission intensity in 2020in China dropped by 18.8% comparedto 2015, exceeding the obligatorytarget of the 13th Five-Year Plan,while the share of non-fossil energyin China’s energy consumption cameto 15.9%, both exceeding the goalsfor 2020 set by China. In September2020, China made a solemn commit-ment to the world that China wouldstrive to achieve carbon emissionpeaking by 2030 and carbon neutralityby 2060. Therefore, in the outline of14th Five-Year Plan and Vision 2035,it was an important topic to developa green mind in production and lives,and to peak carbon emissions and sta-bilize and then decline.Ministry of Industry and Infor-mation Technology: Accelerate thedigital transformation of the manu-facturing industryThe 14th Five-Year Plan for theDevelopment of info-communica-tions Industry (the Plan) was officiallyissued in November 2021, which putforward the overall goal for the 14thFive-Year Plan period, namely, by2025 the overall scale of informationand communication industry willbe further expanded, the quality ofdevelopment will be signif icantlyimproved, the construction of a newdigital infrastructure is basicallycompleted which is high-speed andubiquitous, integrated and intercon-nected, intelligent and green, safe and Obligatory targetsare commitmentsto the people, andindicators thatfurther strengthenthe government’sresponsibility on thebasis of anticipation.11reliable, the innovation capacity will be greatly enhanced, new business models will flourish, and the ability to empower digital transformation and upgrading of the economy and society has been comprehensively strengthened. By the end of 2025, the information and communication in-dustry will reach a new level of green development, with a 15% reduction in comprehensive energy consumption per unit of total telecom services, and the PUE value of newly-built large and super-large data centers below 1.3.General Administration of Customs: Enhance the cooperation of the Belt and RoadOn July 27, 2021, the General Administration of Customs issued the 14th Five-Year Plan for Customs, specif y ing the development and implementation plans for the Belt and Road cooperation, construction of free trade zones, public health at ports, intellectual property protection, bio-safety at national gateway and anti-smuggling, etc. According to the plan, in the next five years, members of international customs cooperation mechanism along the Belt and Road will increase from 53 in 2020 to more than 90 in 2025, and the number of countries (regions) interconnected with China through overseas “sole window” will increase from 1 at pres-ent to 15, the number of countries (regions) who signed AEO (Autho-rized Economic Operator) mutual recognition arrangements with Chi-na will top 60 from 42. In next five years, 35 international sanitary ports will be constructed in China, to en-hance the ability of Chinese portsto respond quickly and effectively topublic health emergencies.Intellectual Property Office:Ensure the milestone goal of con-structing a strong intellectual prop-erty rights powerhouse as scheduledIn late October 2021, the StateCouncil issued National Plan forProtection and Application of Intel-lectual Property Rights During the14th Five-Year Plan Period, specify-ing “four new goals” for the IP-relat-ed work, which include scaling newheights in IP protection, achievingnew results in IP application, reachinga new stage in IP services, and mak-ing new breakthroughs in interna-tional IP cooperation. Meanwhile, itproposed to 8 anticipatory indicators,including in 2025 lifting the numberof high-value invention patents per10,000 people to 12, the number ofoverseas invention patents grantedto 90,000, the registered amount ofintellectual property pledge financingto RMB 320 billion, the total annualimport and export value of intellectu-al property royalties to RMB 350 bil-lion, the value added from patent-in-tensive industries to 13% of GDP, thevalue added from copyright industriesto 7.5% of GDP, the social satis-faction rate of intellectual propertyprotection to 82, and the convictionrate of first instance civil intellectualproperty cases to 85%, in order to en-sure the milestone goal of construct-ing a strong IPR powerhouse will becompleted as scheduled.Ministry of Commerce: Boostand deepen innovations in scienceand technology, institution, indus-try and business modelsRecently, the Ministry of Com-merce issued the Plan for High-qual-ity Development of Foreign Tradeduring the 14th Five-year Plan Peri-od, which highlighted the deepeninginnovations in science and technol-ogy, institution, industry and busi-ness models, outlined 10 major tasksincluding green trade, trade digita-lization, integration of domestic andforeign trade and other new trendsin international trade, to provideguidance for the innovative develop-ment of foreign trade. In 2021, newindustrial forms brought new growth:more than 2,000 overseas warehouseswere built, and in the first ten monthsfrom January to October of 2021,cross-border e-commerce import andexport grew by 19.5%. According tothe plan, during the 14th Five-YearPlan period, China will further expandthe opening-up of domestic market,encourage the import of high-qualityconsumer goods, increase the importof advanced technology, importantequipment, key components, energyresources products and agriculturalproducts in short in domestic mar-ket, optimize the list of cross-bordere-commerce retail imports, furtherpromote local processing of importsin border trade, and stimulate importsfrom neighboring countries, in order tovigorously develop trade of high-qual-ity, high-tech, high value-added greenand low-carbon products. 12。
刘奕群计算机科学与技术系,副教授

教育背景工学学士(计算机科学与技术), 清华大学, 中国, 2003;工学博士(计算机科学与技术), 清华大学, 中国, 2007.社会工作清华大学计算机系2003级本科生辅导员(2003.8-2004.12);清华大学计算机系首届国防定向班计36班辅导员(2003.8-2005.8)计算机系分团委书记,学生工作组副组长(2004.12-2006.8)清华大学校党委学生部辅导员,清华大学学生TMS协会会长(2005.9-2006.2)清华大学计算机科学与技术系: 学生工作组长(2006.9-2011.10)、党委副书记(2011.11-); 中国人工智能学会知识工程与分布智能专委会委员、副秘书长中国中文信息学会青年工作委员会委员、社会媒体处理专委会委员奖励与荣誉清华大学优秀共产党员(2003);清华大学综合优秀一等奖学金(东芝奖学金)(2004);清华大学综合优秀一等奖学金(一二•九奖学金) (2005);清华大学“一二•九”辅导员奖(2005);清华大学综合优秀一等奖学金(北电奖学金) (2006);清华大学优秀博士论文(2007);清华大学“林枫”优秀辅导员奖(2008);清华大学计算机系优秀共产党员、先进工作者(2009);“钱伟长中文信息处理科学技术奖”青年创新奖一等奖(2010);清华大学计算机系先进工作者(2010).清华大学优秀党建与思想政治工作者(2011).清华大学教学成果一等奖(2012).清华大学优秀教材一等奖(2012).清华大学青年教师教学比赛一等奖(2012).华为奖教金(2012).研究领域网络信息检索, 网络用户行为分析, 自然语言处理讲授课程搜索引擎技术基础(课号40240762, 本科);搜索引擎产品设计与实践(课号80240482, 研究生).研究概况我的主要研究兴趣集中在网络搜索引擎技术,尤其是基于用户行为分析方法改进搜索引擎性能这一研究领域。
面对海量繁杂的网络数据与千差万别的用户行为,传统的信息检索、机器学习、自然语言处理技术在搜索引擎系统中的应用面临着极大的挑战。
动态信任关系建模和管理技术研究

49.Gerck E Toward Real-World Models of Trust 1998
20.Chen R.W.Yeager Poblano:A Distributed Trust Model for Peer-to-Peer Networks.Sun Microsystems 2000
21.Winsborough W H.N Li Towards Practical Automated Trust Negotiation 2002
11.A.Abdul-Rahman.S.Halles A distributed trust model 1997
12.A.Abdul-Rahman.S.Hailes Using recommendations for managing trust in distributed systems 1997
34.F.Cornelli.E.Damiani.S.C.Vimercati.S.Paraboschi,P.Samarati A reputation-based approach for choosing reliable resources in peer-to-peer networks 2002
●由于PeerTrust和SecDWTrust都采用了社群信任查询的方法,因此在可信节点占大多数的情况下可以避免虚假的推荐,在~定程度上减轻了联合作弊的危害。而DwTrust 仪依赖直接经验进行判断,在缺乏赢接交互历史的情况下,无法识别联合欺骗行为。
未能加载文件或程序集“XXX”或它的某一个依赖项。试图加载格式不正确的程序。

未能加载⽂件或程序集“XXX”或它的某⼀个依赖项。
试图
加载格式不正确的程序。
“/xxxxx”应⽤程序中的服务器错误。
--------------------------------------------------------------------------------
未能加载⽂件或程序集“xxx”或它的某⼀个依赖项。
试图加载格式不正确的程序。
说明: 执⾏当前 Web 请求期间,出现未处理的异常。
请检查堆栈跟踪信息,以了解有关该错误以及代码中导致错误的出处的详细信息。
异常详细信息: System.BadImageFormatException: 未能加载⽂件或程序集“xxx”或它的某⼀个依赖项。
试图加载格式不正确的程序。
源错误:
执⾏当前 Web 请求期间⽣成了未处理的异常。
可以使⽤下⾯的异常堆栈跟踪信息确定有关异常原因和发⽣位置的信息。
将应⽤程序⽣成为Any CPU就可以了
反之,如果系统是64位的Win7,就应该将新项⽬的⽣成⽬标平台改为x86
64位的Win7 解决⽅案的⽣成⽬标平台设置为x86
32位操作系统解决⽅案的⽣成⽬标平台设置为AnyCPU
我遇到过这个问题有两次,不过环境不同。
第⼀次:Windows 2008 Server R2 64位;
第⼆次:Windows 7 64位;
原因分析:操作系统是64位的,但发布的程序引⽤了⼀些32位的ddl,所以出现了兼容性的问题。
解决⽅案:IIS——应⽤程序池——⾼级设置——启⽤32位应⽤程序:true。
2022年初级网络管理员考试题库(完整版)

2022年初级网络管理员考试题库(完整版)单选题1.在HTML语言中,()可用来为图像定义一串预备的可替换的文本。
A、AltB、ReplaceC、TextD、Title答案:A解析:在HTML语言中,可以通过<img>标签中的Alt属性为不能看到HTML文档中图像的浏览者提供文字说明。
2.在TCP/IP协议体系结构中,不可靠的传输层协议为()。
A、UDPB、TCPC、ICMPD、SMTP答案:A解析:在TCP/IP协议栈中传输层有TCP协议和UDP协议2种,UDP协议是不可靠的协议。
3.下面关于HTTPS的描述中,错误的是()。
A、HTTPS是安全的超文本传输协议B、HTTPS是HTTP和SSL/TLS的组合C、HTTPS和SHTTP是同一个协议的不同简称D、HTTPS服务器端使用的缺省TCP端口是443答案:C解析:超文本传输安全协议(HypertextTransferProtocolSecure,HTTPS)是超文本传输协议和SSL/TLS的组合,用以提供加密通讯及对网络服务器身份的鉴定。
HTTPS连接经常被用于万维网上的交易支付和企业信息系统中敏感信息的传输, HTTPS服务器端使用默认的TCP443端口。
HTTPS不应与在RFC2660中定义的安全超文本传输协议(S-HTTP)相混。
而SHTP则是HTTP协议的的扩展,目的是保证商业贸易的传输安全,只工作在应用层,仅限于web应用,因此并未获得广泛使用。
4.BGPrunsoverareliabletransport().Thiseliminatestheneedtoimplemente xplicitupdatefragmentation,retransmission,acknowledgement,and(请作答此空).Anyauthenticationschemeusedbythetransportprotocolmaybeusedinad ditiontoBGP'sown()mechanisms.TheerrornotificationmechanismusedinBGP ()thatthetransportprotocolsupportsa‚graceful‛close,i.e.,thatallou tstandingdatawillbedelivered()theconnectionisclosed.A、synchronizationB、conflictC、transportD、sequencing答案:D解析:bgp通过可靠的传输协议运行。
2022-2023学年天津市和平区高三(下)第一次质检英语试卷

2022-2023学年天津市和平区高三(下)第一次质检英语试卷从A、B、C、D四个选项中,选出可以填入空白处的最佳选项。
1.(1分)---I'm not looking forward to this.It's going to be a really hard exam.---Oh,________ I'm sure we'll all get good marks.()A.I can't agree more.B.You'd better get started.C.You must be kidding me.D.I won't worry about it too much.2.(1分)---Hi,there.Can I help you with anything today?---Oh,yes.________,I'd like to buy a present for my niece's birthday.()A.Exactly B.Somehow C.Actually D.Definitely3.(1分)Having the courage to be disliked does not mean that you can use your weaknesses as an ________ for not improving yourself.()A.capacity B.excuse C.passion D.demand4.(1分)The way we use a language is so________that one could say there are as many varieties as speakers of English.()A.individual B.commonC.exceptional D.reliable5.(1分)Through comparison,he found that the location of the 117 known Maya cities ________to the positions of the stars.()A.correspond B.appeal C.subscribe D.belong6.(1分)You________so slowly.I just needed a few seconds to get used to your voice.()A.shouldn't speak B.couldn't have spokenC.don't have to D.needn't have spoken7.(1分)The power of Charlie Chaplin's works is not only in his acting,but also in the stories and characters he________.()A.had created B.has createdC.created D.creates8.(1分)Jackson turned out at the Grammy Awards,________music artists are given an award for their artistic or technical achievement.()A.when B.where C.which D.whose9.(1分)The North and South Poles represents the final frontiers of exploration on Earth,and ________ they have become an strong attraction for both researchers and tourists.()A.in other words B.as a consequenceC.by the way D.on the contrary10.(1分)Many people believe cloning is________nature but I think it is a way of helping nature.()A.beneath B.far from C.ahead of D.against11.(1分)I was 12 and ,________all my old friends,I felt shy and lonely at the new school.()A.lost B.having been lostC.having lost D.losing12.(1分)The procedure appealed to the staff a lot________it was introduced to them in January.()A.since B.until C.when D.though13.(1分)-I'm not going to the party tonight.I'll stay at home and read.-Come on,________()A.You get a frog in your throat.B.You're pulling your weight.C.We'd better throw in the towel.D.Don't be such a wet blanket.14.(1分)________ all this put under debate is whether they need to move their cattle to another field for nutrition purpose.()A.How B.Why C.What D.That15.(1分)---I will leave you two alone.I am sure you two must have a lot to________.---Yes.It is two years since we last got together.()A.catch up B.take in C.bring out D.give away阅读下面短文,掌握其大意,然后从16-35 各题所给的A、B、C、D 四个选项中,选出最佳选项。
复杂进化关系类群 英文

复杂进化关系类群英文The Intricate Evolutionary Relationships of Complex TaxaThe study of evolutionary relationships among organisms has long been a subject of fascination for scientists and naturalists alike. One particularly intriguing aspect of this field is the examination of complex taxa, which often exhibit intricate and multifaceted evolutionary histories. These taxa, characterized by their diverse morphological features, ecological adaptations, and genetic compositions, present a unique challenge in unraveling the intricate web of their evolutionary connections.At the heart of this endeavor lies the concept of phylogenetics, the study of the evolutionary relationships among organisms based on their shared characteristics. Phylogenetic analyses, employing a variety of techniques such as morphological comparisons, molecular sequencing, and computational algorithms, have been instrumental in shedding light on the complex evolutionary histories of many taxa. By carefully examining the similarities and differences between organisms, scientists can construct hypothetical evolutionary trees, or phylogenies, that illustrate the branching patterns and divergence points that have shaped the diversity of life on our planet.One such example of a complex taxon is the order Carnivora, which includes a diverse array of mammals such as cats, dogs, bears, and seals. These animals exhibit a wide range of morphological and behavioral adaptations, reflecting their varied ecological niches and evolutionary trajectories. Phylogenetic studies of the Carnivora have revealed intricate relationships, with some species sharing more recent common ancestors than others, and the emergence of distinct clades or lineages that have diversified over time.Another compelling example can be found in the class Reptilia, which encompasses a broad range of organisms, from the iconic dinosaurs to the modern-day crocodiles, snakes, and lizards. The evolutionary history of reptiles has been a subject of intense scrutiny, with ongoing debates and revisions to their phylogenetic relationships. The emergence of new fossil evidence and the application of advanced molecular techniques have helped to refine our understanding of the complex evolutionary connections within this diverse group of animals.The study of complex taxa is not limited to the animal kingdom; the plant world also presents numerous examples of intricately related organisms. The angiosperm, or flowering plant, clade is a prime illustration, with its vast diversity of species exhibiting a wide range of morphological, ecological, and genetic characteristics. Unravelingthe evolutionary relationships among angiosperms has been a major focus of botanical research, with phylogenetic analyses providing insights into the origins and diversification of this dominant group of land plants.One of the key challenges in studying the evolutionary relationships of complex taxa lies in the inherent complexity of their histories. Many organisms have undergone multiple episodes of speciation, extinction, and adaptation, resulting in a tangled web of evolutionary connections that can be difficult to disentangle. Additionally, the acquisition of new traits, the loss of ancestral features, and the phenomenon of convergent evolution can further complicate the interpretation of phylogenetic data.To address these challenges, scientists have developed increasingly sophisticated tools and techniques for phylogenetic analysis. Advances in DNA sequencing, computational algorithms, and statistical modeling have allowed researchers to delve deeper into the genetic underpinnings of evolutionary relationships, providing a more robust and nuanced understanding of the complex taxa under study.Furthermore, the integration of multiple lines of evidence, such as morphological, ecological, and developmental data, has become crucial in constructing comprehensive and reliable phylogenetichypotheses. By considering a diverse array of characteristics, scientists can better account for the multifaceted nature of evolutionary processes and arrive at more accurate representations of the intricate connections within complex taxa.The study of complex taxa and their evolutionary relationships holds immense value for our understanding of the natural world. It not only sheds light on the historical patterns and mechanisms that have shaped the diversity of life but also has practical applications in fields such as conservation biology, disease ecology, and biotechnology. By unraveling the complex evolutionary histories of organisms, we can gain insights into their adaptations, vulnerabilities, and potential for future diversification, ultimately informing our efforts to protect and manage the natural world.In conclusion, the study of complex taxa and their evolutionary relationships is a fascinating and multifaceted field of inquiry. Through the application of advanced phylogenetic techniques and the integration of diverse lines of evidence, scientists are continuously expanding our understanding of the intricate web of life on our planet. As we delve deeper into the complexities of evolutionary histories, we unlock new insights that have the potential to transform our perspectives and guide our stewardship of the natural world.。
工程常数英语

工程常数英语Title: Engineering Constants: The Language of Technology IntroductionIn the realm of engineering, constants are the bedrock upon which designs, calculations, and innovations stand. They are indispensable elements that enable engineers to communicate their ideas, plans, and solutions with precision and clarity. These constants, often referred to as engineering constants, serve as a universal language that transcends cultural and geographical boundaries, providing a common ground for engineers worldwide.The Importance of Engineering ConstantsEngineering constants play a crucial role in various fields of engineering, from mechanical and civil toelectrical and chemical. They provide a set of standard values that can be relied upon for calculations, simulations,and design processes. These constants include physical constants like gravity, thermal conductivity, and elastic modulus, as well as material properties such as density, tensile strength, and specific heat.Understanding these constants is essential for engineers to ensure that their designs are safe, efficient, and reliable. For instance, when designing a bridge, an engineer must consider the material's tensile strength to ensure it can withstand the expected loads. Similarly, when designing an electronic circuit, the constant for resistivity is critical to prevent overheating and potential failure.Physical ConstantsPhysical constants are fundamental properties of the universe that remain unchanged regardless of the location or conditions. Examples include the speed of light, Planck's constant, and Avogadro's number. In engineering, some of the most commonly used physical constants are:1. Gravitational constant (g): This constant is essential for calculating forces due to gravity. On Earth, g is approximately 9.81 m/s².2. Speed of light (c): Equal to approximately 299,792km/s, this constant is crucial in the field of electrical engineering and the design of optical systems.3. Boltzmann constant (k): Used in thermodynamics, it relates the temperature of a system to the average kinetic energy of its particles.4. Stefan-Boltzmann constant (σ): This constant is used in calculations involving thermal radiation and is vital in thermal engineering design.5. Coefficient of friction (μ): Represents the ratio of the force of friction between two surfaces to the force pressing them together. It is essential in mechanical engineering for understanding how objects interact with each other.Material PropertiesMaterial properties are intrinsic characteristics of a substance that determine its behavior under different conditions. These properties can be categorized into mechanical, thermal, electrical, and chemical properties. Some key examples include:1. Density (ρ): The mass per unit volume of a material, crucial for structural design and weight considerations.2. Young's modulus (E): Measures a material's stiffness or elasticity, which is important for analyzing stress and strain in structures.3. Poisson's ratio (ν): A measure of the Poisson effect, which describes the expansion or contraction of a material perpendicular to the direction of loading.4. Thermal conductivity (k): Indicates a material'sability to conduct heat, essential for designing heat exchangers and thermal management systems.5. Electrical resistivity (ρ): Determines how much a material opposes the flow of electric current, critical forthe design of electrical circuits and systems.6. Corrosion resistance: The ability of a material to withstand corrosion, significant for applications in harsh environments or where longevity is a priority.Standardization and UnitsStandardization plays a vital role in engineering by ensuring consistency and compatibility across designs and products. One significant aspect of standardization is theuse of consistent units. The International System of Units (SI) is the modern form of the metric system and is widely adopted in engineering due to its simplicity and universality.The SI system is based on seven base units: the meter (m) for length, kilogram (kg) for mass, second (s) for time, ampere (A) for electric current, Kelvin (K) for temperature, candela (cd) for luminous intensity, and mole (mol) for amount of substance. Derived units are also used, such as the newton (N) for force, pascal (Pa) for pressure, and joule (J) for energy.ConclusionEngineering constants serve as the cornerstone of engineering practice, enabling engineers to design, analyze, and create with confidence. By understanding and applying these constants, engineers can push the boundaries of what is possible, constructing structures, machines, and systems that are not only functional but also aesthetically pleasing, environmentally friendly, and economically viable. As technology continues to advance, the importance of theseconstants will only grow, making them an evergreen subject of study and application for engineers across generations.。
人教版高中英语必修一必修四必修五选修七词性转换表
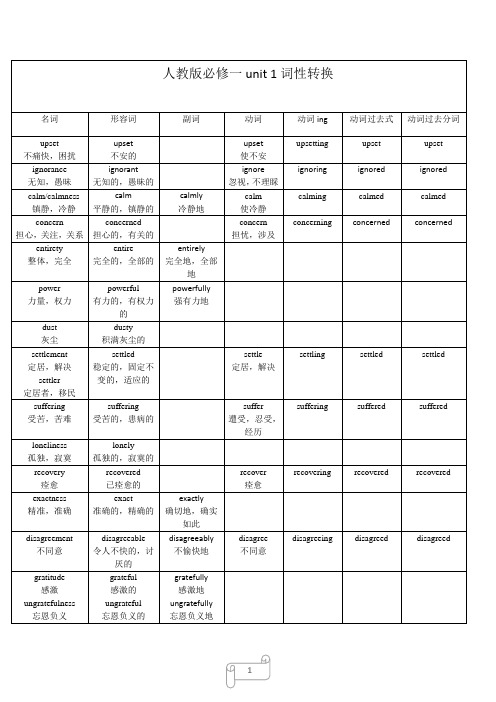
foreseeing
foresaw
foreseen
investigation调查
investigator
调查者
investigate
调查
investigating
investigated
investigated
blame
责备
blame
责备
blaming
blamed
blamed
pollution
污染
有营养的
discovery
发现
discover
发现
discovering
discovered
discovered
focus
焦点
focus
使集中
focusing
focused
focused
reduction
减少
reduced
减少的
reduce
减少
reducing
reduced
reduced
underlined
representation
代表
representative
有代表性的
represent
代表,象征
representing
represented
represented
association
社团,联系,联想
associated
有关联的
associational
协会的
associate
(使)联系
associating
organized
organized
determination
决心
determined
已决定的,坚决的
一个applicationContext加载错误导致的阻塞问题及解决方法

⼀个applicationContext加载错误导致的阻塞问题及解决⽅法问题为对接⼀个sso的验证模块,正确的对接姿势为,接⼊⼀个 filter, 然后接⼊⼀个 SsoListener 。
然⽽在接⼊之后,却导致了应⽤⽆法正常启动,或者说看起来很奇怪,来看下都遇到什么样的问题,以及是如何处理的?还是 web.xml, 原本是这样的: (很简洁!)<?xml version="1.0" encoding="UTF-8" ?><web-app xmlns="/xml/ns/javaee" xmlns:xsi="/2001/XMLSchema-instance"xsi:schemaLocation="/xml/ns/javaee /xml/ns/javaee/web-app_3_0.xsd"version="3.0"><display-name>xx-test</display-name><filter><filter-name>encodingFilter</filter-name><filter-class>org.springframework.web.filter.CharacterEncodingFilter</filter-class><init-param><param-name>encoding</param-name><param-value>UTF-8</param-value></init-param><init-param><param-name>forceEncoding</param-name><param-value>true</param-value></init-param></filter><filter-mapping><filter-name>encodingFilter</filter-name><url-pattern>/*</url-pattern></filter-mapping><servlet><servlet-name>spring</servlet-name><servlet-class>org.springframework.web.servlet.DispatcherServlet</servlet-class><init-param><param-name>contextConfigLocation</param-name><param-value>classpath:spring/spring-servlet.xml</param-value></init-param><load-on-startup>1</load-on-startup></servlet><servlet-mapping><servlet-name>spring</servlet-name><url-pattern>/</url-pattern></servlet-mapping></web-app>⽽需要添加的 filter 如下:<filter><filter-name>SessionFilter</filter-name><filter-class>com.xxx.session.RedisSessionFilter</filter-class></filter><filter-mapping><filter-name>SessionFilter</filter-name><url-pattern>/*</url-pattern></filter-mapping><listener><listener-class>com.xx.session.SSOHttpSessionListener</listener-class></listener><filter><filter-name>SSOFilter</filter-name><filter-class>com.xxx.auth.SSOFilter</filter-class></filter><filter-mapping><filter-name>SSOFilter</filter-name><url-pattern>/*</url-pattern></filter-mapping><context-param><param-name>configFileLocation</param-name><param-value>abc</param-value></context-param> 另外再加⼏个必要的配置⽂件扫描!对接完成!不费事! 然后,我坑哧坑哧把代码copy过来,准备 commit 搞定收⼯! 结果,不出所料,server 起不来了。
如何使用Angular进行Web应用开发

如何使用Angular进行Web应用开发Angular是一种开源的JavaScript框架,用于构建动态的Web应用程序。
它由Google开发和维护,为开发人员提供了一种简洁、高效的方式来构建现代化的Web应用。
本文将讲述如何使用Angular进行Web应用开发,并按照以下章节进行分类。
第一章:介绍Angular框架首先,我们需要了解Angular框架的基本概念和工作原理。
Angular采用了组件化的开发模式,通过组件的组合和嵌套来构建Web应用。
它还提供了一套强大的指令和服务,用于处理DOM操作、数据绑定、依赖注入等常见任务。
理解这些概念对于正确使用Angular非常重要。
第二章:设置Angular开发环境在开始使用Angular之前,我们需要设置好开发环境。
首先,我们需要安装Node.js和npm包管理器。
然后,我们可以使用npm 安装Angular CLI(命令行界面),它提供了一些常用的命令,帮助我们创建和管理Angular项目。
另外,我们还需要一个集成开发环境(IDE)来编写和调试Angular代码。
第三章:创建Angular项目使用Angular CLI可以很容易地创建一个新的Angular项目。
我们只需要在命令行中运行"ng new"命令,指定项目名称即可。
Angular CLI将自动创建项目的基本结构,并安装所需的依赖项。
我们还可以使用"ng generate"命令来生成组件、服务、路由等其他文件,加快项目搭建的速度。
第四章:组件的开发与使用在Angular中,组件是构建Web应用的基本单位。
我们可以使用"ng generate component"命令创建一个新的组件,并在组件类中定义其行为和属性。
然后,我们可以在模板中使用这些组件,并通过数据绑定和事件绑定与组件进行交互。
组件的开发与使用是Angular应用开发的核心部分,需要熟练掌握。
abap message_text_build英文语言

In the SAP environment, ABAP (Advanced Business Application Programming) is a fundamental tool that enables developers to build robust business applications. One of its critical components is the messaging system, which facilitates communication between the system and users through precise and meaningful messages. The construction of high-quality and standard-compliant message texts in ABAP plays a pivotal role in ensuring seamless user experience, efficient debugging, and maintaining consistency across applications. This essay delves into the nuances of crafting such message texts from various perspectives.**Message Text Construction Fundamentals**ABAP's MESSAGE statement serves as the cornerstone for conveying information or errors to users. A message text typically consists of a message number, a message class, and a message text itself. The message text should be clear, concise, and informative, avoiding technical jargon where possible. It must clearly convey the issue at hand without overwhelming the user with unnecessary details.For instance, rather than just stating 'Error in Processing', a more informative message could read, "Invalid data entered in field XYZ. Please ensure the value meets the predefined criteria." This way, the user immediately understands the specific issue and how to resolve it, enhancing the application’s usability.**Adherence to Standards**SAP has strict guidelines for message texts to maintain uniformity and clarity across all modules. These include adhering to language conventions, using complete sentences, and refraining from ambiguous phrases. Messages should be written in active voice and structured to follow a problem-action-solution format whenever applicable.Moreover, SAP recommends using unique message classes for different types of messages – like error, warning, info, etc. Each message class correspondsensures that the application reacts appropriately based on the message type.**Internationalization and Localization**High-quality message texts also consider global audiences by being internationalized and localized. In ABAP, this means that message texts should be created in a way that allows easy translation into other languages without changing the program logic. Developers achieve this by storing message texts in custom message classes or using standard SAP ones, which can be translated via transaction SE91.**Dynamic Message Texts**To achieve maximum context relevance, dynamic message texts can be constructed in ABAP. This involves embedding variables or field values directly into the message text, allowing for greater specificity. For example, `MESSAGE e001(zmymessageclass) WITH variable1 variable2.` Here, the placeholders variable1 and variable2 will be replaced with actual values during runtime, providing users with precise and actionable information.**Debugging and Error Handling**Well-crafted message texts play an integral part in debugging and error handling. Detailed messages enable developers to quickly identify and rectify issues. They can encapsulate crucial data such as object names, line numbers, or specific conditions that led to the error. This level of detail in messages not only expedites the troubleshooting process but also contributes to better maintenance and future-proofing of the codebase.**Conclusion**Crafting high-quality and standard-compliant message texts in ABAP is a multifaceted endeavor. It demands adherence to SAP's prescribed guidelines, consideration of internationalization/localization aspects, and leveraging dynamic constructs for contextual precision. Furthermore, it's about writing messages that serve both end-users and developers effectively – providing clear instructions and facilitating swift issue resolution. By diligentlyquality, maintainability, and user-friendliness of their ABAP applications.This 1000-word overview barely scratches the surface of the meticulous work involved in constructing effective message texts in ABAP. However, it underscores the importance of treating message creation as a vital aspect of software development that requires equal attention to detail and planning as any other coding task.The pursuit of excellence in message texts underpins the broader commitment to delivering robust, reliable, and user-centric SAP solutions, thereby reflecting the core principles of ABAP programming in action.。
写一篇申请加入野外生存夏令营的英语作文

写一篇申请加入野外生存夏令营的英语作文Wilderness Survival Summer Camp Application EssayThe call of the wild has always beckoned to me, whispering promises of freedom, adventure, and a chance to test my mettle against the untamed forces of nature. As I ponder the opportunity to join your esteemed wilderness survival summer camp, I am filled with a sense of profound excitement and an unwavering determination to prove myself worthy of this challenge.From a young age, I have been captivated by the stories of explorers, survivalists, and adventurers who have ventured into the heart of the wilderness, armed with nothing but their wits, their skills, and an unbreakable spirit. Their tales of endurance, problem-solving, and the ability to thrive in the face of adversity have ignited a fire within me, a desire to push the boundaries of my own capabilities and to discover the limits of my resilience.I believe that participating in your wilderness survival summer camp would be the perfect opportunity for me to translate my passion forthe outdoors into tangible skills and real-world experience. The prospect of learning from seasoned instructors, mastering the art of fire-making, navigating through dense forests, and constructing reliable shelters fills me with a sense of eager anticipation. I am confident that I possess the physical stamina, mental fortitude, and adaptability required to excel in such an immersive and demanding environment.Moreover, I am drawn to the holistic approach of your program, which not only focuses on the technical aspects of wilderness survival but also emphasizes the importance of environmental stewardship, teamwork, and personal growth. I believe that these elements are crucial in cultivating a well-rounded individual who is not only capable of thriving in the wild but also possesses a deep respect and appreciation for the natural world.Throughout my life, I have sought out opportunities to challenge myself and push the boundaries of my comfort zone. Whether it was embarking on a solo hiking expedition, volunteering for a conservation project in a remote location, or tackling a physically demanding outdoor sport, I have always been driven by a desire to expand my horizons and to discover the depths of my own potential.This unwavering spirit of adventure and self-discovery is what I believe sets me apart as a candidate for your wilderness survivalsummer camp. I am not simply seeking a recreational experience; I am seeking a transformative journey that will forever shape the way I perceive the world and my place within it.During my time in the camp, I am confident that I will not only acquire the practical skills necessary for survival in the wilderness but also develop a deeper understanding of myself, my strengths, and my limitations. The challenges that I will face, both physical and mental, will undoubtedly push me to my limits, but I am eager to embrace this opportunity for personal growth and self-discovery.Beyond the immediate benefits of the camp, I believe that the lessons I learn and the experiences I gain will have a lasting impact on my future endeavors. The ability to think critically, adapt to changing circumstances, and work collaboratively in high-stress environments are all invaluable skills that will serve me well in my academic pursuits, my future career, and my overall personal development.Furthermore, I am eager to share the knowledge and insights I gain from the camp with my community. I envision myself becoming an ambassador for the importance of outdoor education and environmental stewardship, inspiring others to explore the natural world and to develop a deeper appreciation for its fragility and resilience.In conclusion, I am confident that my passion for the outdoors, my unwavering determination, and my commitment to personal growth make me an ideal candidate for your wilderness survival summer camp. I am excited by the prospect of immersing myself in the raw beauty of nature, pushing the boundaries of my own capabilities, and emerging from the experience as a more resilient, adaptable, and environmentally conscious individual. I humbly request the opportunity to be a part of your esteemed program, and I am eager to embark on this transformative journey that will undoubtedly leave an indelible mark on my life.。
盐份过滤器工艺技术流程

盐份过滤器工艺技术流程1.首先,取一定比例的原水并进行初步过滤。
First, take a certain proportion of raw water and conduct preliminary filtration.2.然后,将原水送入反渗透设备进行高压处理。
Then, the raw water is sent to the reverse osmosis equipment for high-pressure treatment.3.反渗透设备通过半透膜过滤,将盐份分离出去。
The reverse osmosis equipment separates the salt through semi-permeable membrane filtration.4.分离出的盐份会和废水一起排出系统。
The separated saltwill be discharged from the system along with the waste water.5.经过反渗透处理后的水质变得清澈透明。
The water quality becomes clear and transparent after reverse osmosis treatment.6.接下来,对水质进行终端处理和消毒。
Next, the water quality is treated and disinfected at the terminal.7.终端处理和消毒可以杀灭细菌和病毒,确保水质卫生安全。
Terminal treatment and disinfection can kill bacteria and viruses to ensure water quality and safety.8.经过处理后的水质达到国家卫生标准。
The treated water quality meets the national health standards.9.最后,将处理后的水质进行储存和输送。
北京市第五十七中学2024-2025学年高三上学期8月考试英语试题

北京市第五十七中学2024-2025学年高三上学期8月考试英语试题一、完形填空I entered this world with Poland syndrome, a disease that prevented the formation of my right arm and muscles. My parents believed playing with Lego could enhance my 1 and gifted me my first kit when I was five. Initially I 2 to piece the components together but finally I crafted my first Lego work — a car. By the age of nine, I had fashioned my first prosthetic arm (义肢) using Lego — a simple box that perfectly accommodated my right arm.This early creation sparked my drive for further 3 . Years later, I developed another prosthetic arm called the MK-1, which had fingers, a motor, a pressure sensor, and a grabber capable of 4 things. Before constructing it, I was against traditional prosthetics as they were too 5 . My parents had looked into getting one years earlier, only to be discouraged by the prohibitive price. So, I concluded that I might not need one because I was managing well without.As the years passed, my creations evolved from MK-1 to the more advanced and comfortable MK-V. One day, a couple with their eight-year-old son, who lost both arms in an accident, reached out to me after learning about my story. Short of money, they couldn’t afford well-functioning prosthetics. “Daniel,” the father 6 asked, “we were wondering if you could help build a set of prosthetics for our son.”It would be a challenging task, but I responded with a “yes”. Without any delay, I 7 the task. The subsequent days witnessed how I carefully selected the Lego piece and intricately integrated practical components to enhance its dexterity (灵巧). Days turned into weeks, and the boy-customized prosthetics finally took shape. It’s time for them to fulfill their intended purpose.I rushed to the boy’s home and 8 the prosthetics onto him. They worked! The room erupted with cheers! The boy expressed his gratitude and sprinted to his parents to 9 them in the biggest hug. Never had I imagined that my creations, born out of mere 10 , would someday make such a difference.1.A.stability B.mobility C.flexibility D.reliability2.A.learned B.attempted C.managed D.struggled 3.A.effort B.investment C.application D.exploration 4.A.picking up B.setting up C.pulling up D.rolling up 5.A.unstable B.expensive C.inconvenient D.clumsy 6.A.gratefully B.desperately C.hurriedly D.earnestly 7.A.embarked on B.set off C.figured out D.carried on 8.A.secured B.placed C.guaranteed D.stuck 9.A.encounter B.engrave C.engage D.envelop 10.A.awe B.dedication C.fun D.boredom二、语法填空阅读下列短文,根据短文内容填空。
spring学习(十二)--spring中WebApplicationInitializer解析

spring学习(⼗⼆)--spring中WebApplicationInitializer解析 上⽂中讲解了如何通过WebApplicationInitializer取代Web.xml进⾏spring容器的启动,WebApplicationInitializer是⼀个接⼝,通过实现WebApplicationInitializer,在其中可以添加servlet,listener等。
在Web容器启动的时候,spring-web会通过SPI机制,加载这个接⼝的实现类,从⽽起到web.xml相同的作⽤。
下⾯就看⼀下这个接⼝的详细内容:public interface WebApplicationInitializer {void onStartup(ServletContext servletContext) throws ServletException;}WebApplicationInitializer只有⼀个⽅法,⽐较简单,看不出什么头绪。
在WebApplicationInitializer同级别有个SpringServletContainerInitializer类,我们来看下这个类的代码:package org.springframework.web;@HandlesTypes(WebApplicationInitializer.class)public class SpringServletContainerInitializer implements ServletContainerInitializer {@Overridepublic void onStartup(Set<Class<?>> webAppInitializerClasses, ServletContext servletContext)throws ServletException {List<WebApplicationInitializer> initializers = new LinkedList<WebApplicationInitializer>();if (webAppInitializerClasses != null) {for (Class<?> waiClass : webAppInitializerClasses) {// Be defensive: Some servlet containers provide us with invalid classes,// no matter what @HandlesTypes says...if (!waiClass.isInterface() && !Modifier.isAbstract(waiClass.getModifiers()) &&WebApplicationInitializer.class.isAssignableFrom(waiClass)) {try {initializers.add((WebApplicationInitializer) waiClass.newInstance());}catch (Throwable ex) {throw new ServletException("Failed to instantiate WebApplicationInitializer class", ex);}}}}if (initializers.isEmpty()) {servletContext.log("No Spring WebApplicationInitializer types detected on classpath");return;}AnnotationAwareOrderComparator.sort(initializers);servletContext.log("Spring WebApplicationInitializers detected on classpath: " + initializers);for (WebApplicationInitializer initializer : initializers) { //这⾥指定了调⽤的类的⽅法,onStartup()initializer.onStartup(servletContext);}}}SpringServletContainerInitializer这个类⾥也有个onStartup⽅法,看⼀下它的逻辑。
HttpApplication理解

HttpApplication理解HttpApplication对象是经由HttpApplicationFactory.GetApplicationInstance(并最终调⽤HttpRuntime.CreateNonPublicInstance)创建的HttpApplicationFactory它的主要任务是使⽤ URL 信息来查找 URL 虚拟⽬录和汇集的 HttpApplication 对象之间的匹配关系。
这个⼯⼚类的⾏为概括为有以下⼏点1、⼯⼚类维护, HttpApplication 对象池并使⽤它们来处理应⽤程序的请求。
池的寿命与应⽤程序的寿命相同。
2、应⽤程序的第⼀个请求到达时,⼯⼚类提取有关应⽤程序类型的信息(global.asax 类)、设置⽤于监视更改的⽂件、创建应⽤程序状态并触发 Application_OnStart 事件。
⼯⼚类从池中获取⼀个 HttpApplication 实例,并将要处理的请求放⼊实例中。
如果没有可⽤的对象,则创建⼀个新的 HttpApplication 对象。
要创建 HttpApplication 对象,需要先完成 global.asax 应⽤程序⽂件的编译。
3、HttpApplication 开始处理请求,并且只能在完成这个请求后才能处理新的请求。
如果收到来⾃同⼀资源的新请求,则由池中的其他对象来处理。
4、应⽤程序对象允许所有注册的 HTTP 模块对请求进⾏预处理,并找出最适合处理请求的处理程序类型。
这通过查找请求的 URL 的扩展和配置⽂件中的信息来完成。
HttpApplicationFactory.GetApplicationInstance创建HttpApplication实例中有三个关键⽅法:HttpApplicationFactory._theApplicationFactory.EnsureInited() 该⽅法检查HttpApplicationFactory是否被初始化,如果没有,就通过HttpApplicationFactory.Init()进⾏初始化。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Constructing Reliable Web Applicationsusing Atomic ActionsM. C. Little, S. K. Shrivastava, S. J. Caughey, and D. B. InghamAbstractThe Web frequently suffers from failures which affect the performance andconsistency of applications run over it. An important fault-tolerance technique is theuse of atomic actions (atomic transactions) for controlling operations on services.Atomic actions guarantee the consistency of applications despite concurrent accessesand failures. Techniques for implementing transactions on distributed objects arewell-known: in order to become “transaction aware”, an object requires facilities forconcurrency control, persistence, and the ability to participate in a commit protocol.While it is possible to make server-side applications transactional, browsers typicallydo not possess such facilities, a situation which is likely to persist for the foreseeablefuture. Therefore, the browser will not normally be able to take part in transactionalapplications. The paper presents a design and implementation of a scheme that doespermit non-transactional browsers to participate in transactional applications, therebyproviding much needed end-to-end transactional guarantees.Keywords: World Wide Web, atomic actions, transactional integrity, consistency, fault-tolerance, distributed systems1. IntroductionThe Web is rapidly being populated by service providers who wish to sell their products to a large potential customer base. However, there are still important security and fault-tolerance considerations which must be addressed. One of these is the fact that the Web frequently suffers from failures which can affect both the performance and consistency of applications run over it. For example, if a user purchases a cookie granting access to a newspaper site, it is important that the cookie is delivered and stored if the user’s account is debited; a failure could prevent either from occurring, and leave the system in an indeterminate state. For resources such as documents, failures may simply be annoying to users; for commercial services, they can result in loss of revenue and credibility. Therefore, making Web applications fault-tolerant is important. Atomic actions (atomic transactions) are a well-known technique for guaranteeing application consistency in the presence of failures [DBL77][OMG95]. An atomic action guarantees that, despite failures, either all of the work conducted within its scope will be performed or it will all be undone. This is an extremely useful fault-tolerance technique, especially when multiple, possibly remote, transactional resources are involved. For this reason Web applications already exist which offer transactional guarantees to users. However, because significant resources are required to provide transactional properties, these guarantees only extend to resources used at Web servers, or between servers (see figure 1); browsers are not included, despite being a significant source of unreliability in the Web. Providing end-to-end transactional integrity between the browser and the application is important, however: in the previous example, the cookie must be delivered once the user’s account has been debited. As we shall show later, using cgi-scripts cannot provide this level of transactional integrity since replies sent after the transactions have completed may be lost, and replies sent during the transaction may need to be revoked if the transaction cannot complete successfully [OSF96].domainKey:Transactional objectApplication thread managing transaction(action manager)Figure 1: Current transactional Web applications.Despite the advent of technologies such as Java, browsers are typically resource scarce; requiring a browser to incorporate support for transactions for all applications would be inefficient, and impose an overhead on all users. In this paper we shall present a lightweight solution for providing these end-to-end transactional guarantees which does not require the browser to be transactional. We shall also present an implementation of this model, the W3OTrans toolkit, which has been implemented on the W3Objects object-oriented framework [DBI95].2. Atomic actionsAtomic actions are used in application programs to control the manipulation of persistent (long-lived) objects. Atomic actions have the following ACID properties [OMG95]:• Atomic: if interrupted by failure, all effects are undone (rolled back).• Consistent: the effects of a transaction preserve invariant properties.• Isolated: a transaction’s intermediate states are not visible to other transactions. Transactions appear to execute serially, even if they are performed concurrently.• Durable: the effects of a completed transaction are persistent; they are never lost (except in a catastrophic failure).A transaction can be terminated in two ways: committed or aborted (rolled back). When a transaction is committed, all changes made within it are made durable (forced on to stable storage, e.g., disk). When a transaction is aborted, all of the changes are undone. Atomic actions can also be nested; the effects of a nested action are provisional upon the commit/abort of the outermost (top-level) atomic action.2.1 Commit protocolA two-phase commit protocol is required to guarantee that all of the action participants either commit or abort any changes made. Figure 2 illustrates the main aspects of the commit protocol: during phase 1, the action coordinator, C, attempts to communicate with all of the action participants, A and B, to determine whether they will commit or abort. An abort reply from any participant acts as a veto, causing the entire action to abort. Based upon these (lack of) responses, the coordinator arrives at the decision of whether to commit or abort the action. If the action will commit, the coordinator records this decision on stable storage, and the protocol enters phase 2, where the coordinator forces the participants to carry out the decision. The coordinator also informs the participants if the action aborts.When each participant receives the coordinator’s phase 1 message, they record sufficient information on stable storage to either commit or abort changes made during the action. After returning the phase 1 response, each participant which returned a commit response must remain blocked until it has received the coordinator’s phase 2 message. Until they receive this message, these resources are unavailable for use by other actions. Ifthe coordinator fails before delivery of this message, these resources remain blocked. However, if crashed machines eventually recover, crash recovery mechanisms can be employed to unblock the protocol and terminate the action.Phase 1Phase 2Figure 2: Two-phase commit protocol.2.2 Transactional proxiesThe action coordinator maintains a transaction context where resources taking part in the action are required to be registered. Such a resource must obey the transaction commit protocol guaranteeing ACID properties; typically this means that the resource will provide specific operations which the action can invoke during the commit/abort protocol. However, it may not be possible to make all resources transactional in this way, e.g., legacy code which cannot be modified. To use these resources within an action it is often possible to provide transactional proxies: the proxy is registered with, and manipulated by, the action as though it were a transactional resource, and the proxy performs implementation specific work to make the resource it represents transactional. This requires that the proxy participate within the commit/abort protocol. Because the work of the proxy is performed as part of the action, it is guaranteed to be completed or undone despite failures of the action coordinator or action participants.How proxies are created and registered with an action will depend upon specifics of the transactional system, (some systems may not support proxies). For example, a system based on reflective techniques may use an appropriate meta-object protocol [RJS95]. Another technique would be through the use of open commit protocols, which give programmers the ability to control what an action participant does during each phase of the protocol; such a protocol can also be used to register resources which are not transactional but which can be driven by the commit/abort protocol [OMG95].2.3 Transactional gateways and browser proxiesOne straightforward way to provide end-to-end transactional integrity for a Web application and its users would be to empower the browser and incorporate into it transactional objects which are part of the application. These objects would then be able to participate directly in the application’s transactions. For instance, the newspaper example could place a transactional object within the browser which has operations for adding and removing the cookie. However, this then requires the browser to support transactional objects and (distributed) atomic actions. Although this may be acceptable for some applications, we are interested in the case where it would be considered either undesirable or impractical, e.g., because of security considerations. For such cases, a practical means of obtaining transactional guarantees between the application and browser will be through the use of transactional gateways and transactional browser proxies. A transactional gateway provides browsers with access to the transactional application by exporting application specific operations which can be invoked from the browser, e.g., an operation to purchase the newspaper. Importantly, an application may be accessed via many gateways: each gateway is configured to be used by browsers with specific functionality. For example, a gateway for transactional aware browsers may download transactional application objects to it; however, if the browser is not transactional, the gateway may be responsible for creating a transactional browser proxy, which is then responsible for cooperating with the browser to make it transactional, as described below. The gateway can also be made responsible for enforcing security, such as authenticating the user before allowing operations to be performed.A transactional browser proxy consists of code which resides within the browser and code which resides in the gateway. The proxy is used to allow a non-transactional browser to participate within an atomic action. The gateway receives a request from a browser, starts an atomic action and registers a browser proxy with it. The gateway then performs the operation, gives the result to the proxy, and depending upon the outcome of the operation, either commits or aborts the action. During the commit/abort protocol the proxy delivers the response to the browser, which must acknowledge receipt. For example, in the case of the newspaper example described earlier, the proxy can transmit the cookie to the browser during phase 2 of the protocol, when the action has guaranteed that all other changes have been committed, and the application can be sure that it will be delivered despite failures. If the action aborts, the proxy can transmit an error message, giving the reason for the failure.The server-side of the proxy performs most of the transactional work, whereas the browser code is relatively simple, needing only to be able to make any “changes” permanent in the case of a commit, or to undo them if the action aborts. This will typically be application specific, e.g., for a cookie, the browser-side proxy will need to write it to disk, whereas if the user is purchasing a specific edition of an electronic newspaper the proxy may receive the newspaper during phase 1, and either display it during phase 2 or discard it, depending upon whether the action commits or aborts. Therefore, transactional gateways and browser proxies provide a lightweight means for applications to gain end-to-end transactional integrity.A browser proxy can also support application specific processing; we give two examples below:• if the browser is invoked during phase 1 of the commit protocol and does not respond (e.g., to a simple“are-you-alive?” message), the proxy can cause the action to abort. If the action aborts, all of the other work performed within the action will be automatically undone. This enables the application to detect browser failures as late as possible, while still being able to undo any other work performed within the action, such as aborting a debit of the user’s account. If this did not occur, resources may remain unavailable until crash recovery mechanisms complete the transaction.• Rather than the simple “are-you-alive?” protocol, a more complex protocol could be used. For example, ifthe browser is executing on a mobile machine which is about to shut down due to low battery power, it could return the address of another agent during phase 1, to which the action coordinator should redirect the phase 2 outcome.Figure 3 shows two transactional gateways, A and B, for the same transactional newspaper application: users purchase cookies, and their payments are debited from a bank account which is held elsewhere, possibly by a different organisation. A purchase operation is required to atomically debit an account and deliver the purchased cookie to the user. Therefore, the transaction spans multiple domains and transactional objects.Transaction aware browsers use gateway B, whereas A is used by non-transactional browsers. As illustrated,prior to invoking the operation on the newspaper object, A creates a browser proxy which is registered with theatomic action.Non-Key:Gateway ProxyNewspaper objectAction manager Atomic operationsFigure 3: Transactional gateways.During the second phase of the commit protocol, the proxy transmits the cookie to the browser, which must acknowledge after storing it on disk; if a failure of either the browser or server occurs, the cookie will be retransmitted by the crash recovery mechanisms. Apart from starting and ending transactions, the application does not have to perform additional work in order to guarantee that the user’s request will be performed despitefailures. (In the case of the transactional browser, the cookie is simply the state of one of the transactional objects within the browser which were downloaded by B.)Another advantage of transactional gateways and browser proxies is that they can be used to support the construction of modular applications. The same transactional application can be accessed from the Web and from other (distributed) environments, only the gateway need change. For example, in figure 4 the same application has been made available to Web users and ORB clients [OMG91]. Each gateway is responsible for the protocol aspects of interfacing the application with the specific distributed environment.Non-Figure 4: Inter-working.Having presented a model for providing lightweight end-to-end transactional guarantees for Web applications, we shall now describe a system which implements it.3. W3OTransWe have developed the W3OTrans toolkit which provides programmers with the ability to implement Web applications using atomic actions and objects. Although we shall concentrate on the support for building transactional gateways and browser proxies, W3OTrans also supports the following types of transactional application:(i) the application executes entirely at the Web server, as the result of the browsing user selecting a specificURL.(ii) t he application executes entirely within the browser.(iii) t he application executes within the browser and the Web server; the server may contain the more security-sensitive resources, for example. In this case, the browser is simply another address space for the application.Using W3OTrans, programmers can build transactional applications which span multiple Web servers, multiple browsers, or execute locally within a single browser. In addition, transactions can span browser invocations, and can be arbitrarily nested. In order to do this, W3OTrans is implemented in C++ and Java, enabling server-side applications to take full advantage of more efficient compilation techniques. However, since all of the W3OTrans facilities are available in both languages, applications can be written entirely in Java.3.1 Impact of the Java security modelThe use of Java to implement the browser-side version of W3OTrans raises some important security issues. Java security is imposed by a SecurityManager object, which defines what an applet can, and cannot do [SUN95][ORA96]. Although it is believed that users will eventually be able to provide their own SecurityManager, currently the Java interpreter provides the only implementation. As described in [ORA96], generally an applet cannot remotely communicate with a node other than the one from which it was loaded. In addition, an applet cannot write to the disk of the machine on which it is being run. If an applet is loaded directly from the user’s disk then many of these restrictions are relaxed.However, the problem for Java programmers is that each implementer of a Java interpreter can provide a different security model and SecurityManager object, which may impose different constraints. Therefore, to enable applications written with W3OTrans to execute in any Java-aware Web browser, our two major premises were not to modify the language or the interpreter. Services such as persistence and concurrency control are accessed through interfaces which do not specify an implementation, allowing objects to determine the required implementation at run-time. For example, an object written using W3OTrans can choose implementations for persistence based upon the security restrictions of the Java interpreter, the user’s requirements, and the application, without modifications to the application. For example, where the SecurityManager prevents applets from accessing the local disk for persistence, a remote persistence service can be used.3.2 W3OTrans classesW3OTrans is built on the W3Objects system [DBI95][DBI96]. W3Objects is a framework for the construction of Web applications using object-oriented techniques. W3Objects are responsible for their own persistence, concurrency control, fault-tolerance, etc., which are provided through appropriate classes and libraries. In addition, every W3Object has the ability to guarantee referential integrity: the object can be prevented from being deleted as long as a single reference to it exists. W3Objects are available to standard Web browsers using the HTTP protocol, and can also possess interfaces which enable them to be invoked using other protocols.In keeping with the W3Objects methodology, objects obtain ACID properties through inheritance. W3OTrans presents programmers with an AtomicObject base class and the AtomicAction class. The AtomicObject class is responsible for supporting the properties of serialisability, failure atomicity and permanence of effect. Concurrency control can be applied on a per object basis, and uses a multiple reader/single writer policy. Each derived class must provide methods to convert an object’s state to/from a format which can be saved to stable storage. Therefore, the programmer has explicit control over which objects, and which parts of an object, are transactional.The AtomicAction class is used to create atomic actions. An action is automatically nested if it is created within the scope of another action. Whenever an AtomicObject is used within an action it is automatically registered with that action, i.e., it becomes part of the transactional context and will be manipulated by the action to guarantee ACID properties. If the object is in another address space (e.g., on a different machine), then the action will automatically span these address spaces. This occurs transparently to the application programmer: there is no special syntax required to ensure that transactional contexts cross address spaces.3.3 W3OTrans gateways and proxiesWhen building applications which require end-to-end transactional integrity for the browser but which do not require, or cannot allow, the browser to contain transactional objects, the programmer can create application specific transactional gateways and browser proxies. After developing the transactional application using the W3OTrans classes, the programmer uses a high-level definition language to specify the required gateway interface, i.e., the operations which the application supports and wants to export to the Web. Using this interface definition, W3OTrans tools automatically generate the server-side transactional gateway and Java code which allows it to be invoked from a browser applet, along with C++ and Java implementations of the browser proxy. The gateway is represented in the applet as a Java class with one method for each operation; each method is responsible for communicating with the actual server-side gateway. Currently the proxy protocol is based upon a simple “are-you-alive?” message as described in section 2.3. The programmer then modifies the server-side gateway code to begin and end atomic actions, and register browser proxies. There is no necessity to consider possible failure scenarios and attempt to perform compensating work: the transactions will automatically guarantee consistency and integrity. At this stage, the programmer has a complete server-side transactional application, and can now concentrate on the browser applet, which will allow users to interact with the application through the gateway.4. Bank ATM exampleHaving given an overview of the W3OTrans system, we shall now describe a bank account application which we have used it to build. The application presents Web users with the ability to insert, withdraw and inspect their accounts, which are accessed via a PIN. To preserve consistency in the presence of failures and concurrent users, the operations are performed as separate atomic actions. In order that the bank can serviceconcurrent write operations, each account is a separate transactional object. As shown in Figure 5, a Java applet displays a graphical representation of a bank ATM machine. When the user selects an operation, the applet displays a unique transaction identifier for this operation and then invokes the appropriate method onthe bank gateway.Figure 5: Bank applet.Although the inspect operation is atomic, it only reads the state of the account and therefore there is no requirement for end-to-end transactional integrity: if a failure occurs, the user can simply re-issue the request.However, both withdrawing and inserting money require stronger transactional guarantees: each operation must atomically modify the account and cause the applet to animate either the withdrawing or inserting of money. This is accomplished by the bank returning a token during the commit protocol which indicates whether the operation committed or aborted; the applet uses this to either animate, or print an error message.A failure to perform the operation may be the rest of insufficient funds, for example, or that the bank application crashed before debiting the account. As shown in figure 6, during phase 1 of the commit protocol the proxy determines whether the browser is still available. If the browser responds and the attempt to debit the user’s account can be made permanent, the protocol proceeds to phase 2 and commits the action, making permanent any changes. During this phase the browser proxy transmits the token to the applet, whichdispenses the money and acknowledges receipt of the token.Bank Application Bank appletBank ApplicationBank applet Figure 6: Bank Withdraw operation.If the Web server crashes during the action, the user can re-issue the request when the machine recovers by typing in the transaction identifier. The crash recovery mechanism at the Web server will determine the transaction outcome and complete the action. If the browser crashes before the end of phase 1 it will cause the action to abort. If it crashes after the coordinator has decided to commit, crash recovery will be responsible for resolving the action when the browser recovers. Therefore, when withdrawing money, if the user’s bank account is debited the application can guarantee that, regardless of failures, the money will be dispensed. Theprogrammer can develop the application without having to consider the possible failure scenarios and how to provide recovery mechanisms for them.5. Comparisons with other systemsIn this section we shall briefly consider other systems intended to integrate atomic actions and the Web.5.1 Transactions through cgi-scriptsFigure 7 shows how it is possible to use cgi-scripts to allow users to make use of applications which manipulate atomic resources [TRA96]: the user selects a URL which references a cgi-script on a Web server (message 1),which then performs the action and returns a response to the browser (message 2) after the action has completed. (Returning the message during the action is incorrect since the action may not be able to commit the changes.)In a failure free environment, this mechanism works well, with atomic actions guaranteeing the consistency of the server application. However, in the presence of failures it is possible for message 2 to be lost between the server and the browser. If the transaction commits, the reply will be sent after the transaction has ended;therefore, other work performed within the transaction will have been made permanent. For some applications this may not be a problem, e.g., where the result is simply confirmation that the operation has been performed.If the result is a cookie, however, the loss of the cookie will leave the user without his purchase and money,and may require the service provider to perform complex procedures to verify the cookie was lost, invalidate itand issue another.Figure 7: transactions through cgi-scripts5.2 Transactions in JavaThere are several groups working on incorporating transactions into Java [MA96][AG96]. These schemes are based on providing atomic actions with orthogonal-persistence : objects are written without requiring knowledge that they may be persistent or atomic: the Java runtime environment is modified to provide this functionality. The applet simply starts and ends transactions, and every object which is manipulated within a transaction will automatically be made atomic. We consider these approaches unsuitable for Web applications as they suffer from the following limitations:(i) They require changes to the Java interpreter and language. Applications written using these systems will only execute on specialised interpreters.(ii) Both schemes assume that the entire application will be written in Java, and will not be distributed, i.e., it will either execute at the browser or at the Web server.6. Conclusions and future workIn this paper we have presented an model for integrating atomic actions and the Web. Using transactional gateways and browser proxies we have shown how it is possible for non-transactional browsers to participate within a transaction. Applications can therefore obtain end-to-end transactional integrity, guaranteeing consistency in the presence of failures and concurrent access. The model is lightweight, and does not require the browser to incorporate support for transactions. We have presented the W3OTrans system which implements this model, and described an example which we have built using it.Currently W3OTrans provides support for the automatic construction of simple browser proxies and gateways.We intend to extend this support to arbitrary, application specific implementations. W3OTrans transactions are。
