Comparison of 3D algorithms for non-rigid motion and correspondence estimation
Modelling and Assimilation of Atmospheric Chemistry - ecmwf建模与大气化学ECMWF同化

Why Atmospheric Chemistry at NWP centres ?
- or in a NWP Training Course?
Environmental concern Air pollution Ozone hole Climate change
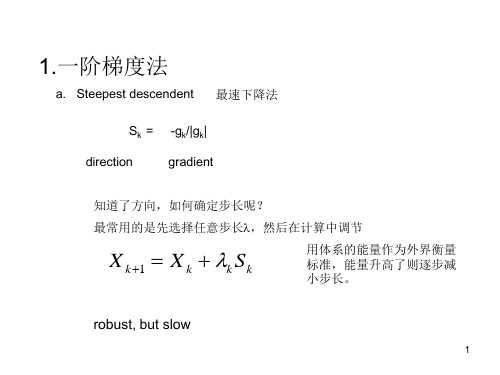
ppt 1:1012
Atmospheric Chemistry
Transport
Chemical Reactions
Photolysis
catalytical Cycles
Emissions
Atmospheric Reservoir
Training Data assimilation and Satellite Data – Johannes Flemming Dr. Martin Schultz - Max-Planck-Institut für Meteorologie, Hamburg
Rodwell and Jung Published in Quart. J. Roy. Meteorol. Soc., 134, 1479.1497 (2019)
Training Data assimilation and Satellite Data – Johannes Flemming
An other motivation …
Transport
wet & dry Deposition
Modelling atmospheric composition
Mass balance equation for chemical species ( up to 150 in state-of-the-art
信息可视化设计外文文献翻译中英文

信息可视化设计外文文献翻译中英文AbstractInformation visualization has become increasingly popular in recent years due to the growth of data analytics and the need for effective data presentation. This paper aims to introduce the concept of information visualization design and its importance as a tool for analyzing complex data sets. It also provides a comparative analysis of information visualization design strategies used in both Chinese and English literature, highlighting some key differences and similarities between the two.IntroductionInformation visualization design involves the graphical representation of data and information to facilitate understanding, analysis, and decision-making. As the amount of data being generated continues to grow exponentially, the need for effective information visualization design becomes critical. It enables users to explore, analyze, and interpret data in a more intuitive and interactive manner.Importance of Information Visualization DesignInformation visualization design plays a crucial role in transforming complex data into visually appealing and meaningful representations. It helps users identify patterns, trends, and relationships within data sets that might not be immediately apparent in raw data. Moreover, it allows users tocustomize and interact with the visual representations, enabling them to gain deeper insights and make more informed decisions.Comparison of Information Visualization Design Strategies Chinese LiteratureIn Chinese literature, there has been an emphasis on the use of color, shape, and layout to convey information effectively. Chinese researchers have explored various visualization techniques, including word clouds, treemaps, and interactive charts. They have also emphasized the importance of user-centered design, focusing on user needs, preferences, and cognitive processes.English LiteratureIn English literature, there has been a focus on the use of data-driven design principles and algorithms. English researchers have developed sophisticated visualization techniques such as scatter plots, heatmaps, and network graphs. They have also stressed the importance of data preprocessing and transformation to ensure accurate and reliable visualizations.Similarities and DifferencesAlthough there are some distinct approaches in Chinese and English literature, there are also some common principles and techniques that both share. Both Chinese and English researchers recognize the importance of clear and concise visualizations, effective use of color, and interactivity. Theyalso emphasize the importance of design evaluation and user testing to ensure the usability and effectiveness of visualizations.However, there are some differences in terms of research goals and focus. Chinese literature tends to emphasize the use of storytelling and narrative in information visualization design, aiming to engage users emotionally and create meaningful experiences. English literature, on the other hand, focuses more on the technical aspects of visualization design, such as algorithm development and optimization.ConclusionInformation visualization design is a crucial tool in analyzing and understanding complex data sets. Both Chinese and English literature provide valuable insights and techniques for effective information visualization design. By combining the strengths of both approaches, researchers and practitioners can create more impactful and user-friendly visualizations. As data continues to grow in volume and complexity, the field of information visualization design will continue to evolve, enabling us to derive greater insights and make better-informed decisions.。
Segmentation - University of M

Robustness
– Outliers: Improve the model either by giving the noise “heavier tails” or allowing an explicit outlier model
– M-estimators
Assuming that somewhere in the collection of process close to our model is the real process, and it just happens to be the one that makes the estimator produce the worst possible estimates
– Proximity, similarity, common fate, common region, parallelism, closure, symmetry, continuity, familiar configuration
Segmentation by clustering
Partitioning vs. grouping Applications
ri (x i , );
i
(u;
)
u2 2
u
2
Segmentation by fitting a model(3)
RANSAC (RAMdom SAmple Consensus)
– Searching for a random sample that leads to a fit on which many of the data points agree
Allocate each data point to cluster whose center is nearest
A Comparison of Algorithms for the

A Comparison of Algorithms for the Optimization of Fermentation ProcessesRui MendesIsabel RochaEug´e nio C.FerreiraMiguel RochaAbstract —The optimization of biotechnological processes isa complex problem that has been intensively studied in the past few years due to the economic impact of the products obtained from fermentations.In fed-batch processes,the goal is to find the optimal feeding trajectory that maximizes the final productivity.Several methods,including Evolutionary Algorithms (EAs)have been applied to this task in a number of different fermentation processes.This paper performs an experimental comparison between Particle Swarm Optimization,Differential Evolution and a real-valued EA in three distinct case studies,taken from previous work by the authors and literature,all considering the optimization of fed-batch fermentation processes.I.I NTRODUCTIONA number of valuable products such as recombinant pro-teins,antibiotics and amino-acids are produced using fer-mentation techniques.Additionally,biotechnology has been replacing traditional manufacturing processes in many areas like the production of bulk chemicals,due to its relatively low requirements regarding energy and environmental costs.Consequently,there is an enormous economic incentive to develop engineering techniques that can increase the pro-ductivity of such processes.However,these are typically very complex,involving different transport phenomena,microbial components and biochemical reactions.Furthermore,the nonlinear behavior and time-varying properties,together with the lack of reliable sensors capable of providing direct and on-line measurements of the biological state variables limits the application of traditional control and optimization techniques to bioreactors.Under this context,there is the need to consider quantita-tive mathematical models,capable of describing the process dynamics and the interrelation among relevant variables.Additionally,robust global optimization techniques must deal with the model’s complexity,the environment constraints and the inherent noise of the experimental process [3].In fed-batch fermentations,process optimization usually encompasses finding a given nutrient feeding trajectory that maximizes productivity.Several optimization methods have been applied in this task.It has been shown that,for simple bioreactor systems,the problem can be solved analytically [24].Rui Mendes and Miguel Rocha are with Department of Infor-matics and the Centro de Ciˆe ncias e Tecnologias da Computac ¸˜a o,Universidade do Minho,Braga,Portugal (email:azuki@di.uminho.pt,mrocha@di.uminho.pt).Isabel Rocha and Eug´e nio Ferreira with the Centro de Engenharia Biol´o gica da Universidade do Minho (email:irocha@deb.uminho.pt,ecferreira@deb.uminho.pt).Numerical methods make a distinct approach to this dy-namic optimization problem.Gradient algorithms are used to adjust the control trajectories in order to iteratively improve the objective function [4].In contrast,dynamic programming methods discretize both time and control variables to a predefined number of values.A systematic backward search method in combination with the simulation of the system model equations is used to find the optimal path through the defined grid.However,in order to achieve a global optimum the computational burden is very high [23].An alternative approach comes from the use of algorithms from the Evolutionary Computation (EC)field,which have been used in the past to optimize nonlinear problems with a large number of variables.These techniques have been applied with success to the optimization of feeding or temperature trajectories [14][1],and,when compared with traditional methods,usually perform better [20][6].In this work,the performance of different algorithms belonging to three main groups -Evolutionary Algorithms (EA),Particle Swarm (PSO)and Differential Evolution (DE)-was compared,when applied to the task of optimizing the feeding trajectory of fed-batch fermentation processes.Three test cases taken from literature and previous work by the authors were used.The algorithms were allowed to run for a given number of function evaluations that was deemed to be enough to achieve acceptable results.The comparison among the algorithms was based on their final result and on the convergence speed.The paper is organized as follows:firstly,the fed-batch fermentation case studies are presented;next,PSO,DE and a real-valued EA are described;the results of the application of the different algorithms to the case studies are presented;finally,the paper presents a discussion of the results,conclu-sions and further work.II.C ASESTUDIES :FED -BATCH FERMENTATIONPROCESSESIn fed-batch fermentations there is an addition of certain nutrients along the process,in order to prevent the accumu-lation of toxic products,allowing the achievement of higher product concentrations.During this process the system states change considerably,from a low initial to a very high biomass and product concen-trations.This dynamic behavior motivates the development of optimization methods to find the optimal input feeding trajectories in order to improve the process.The typical input in this process is the substrate inflow rate time profile.0-7803-9487-9/06/$20.00/©2006 IEEE2006 IEEE Congress on Evolutionary ComputationSheraton Vancouver Wall Centre Hotel, Vancouver, BC, Canada July 16-21, 20062018For the proper optimization of the process,a white box mathematical model is typically developed,based on dif-ferential equations that represent the mass balances of the relevant state variables.A.Case study IIn previous work by the authors,a fed-batch recombinant Escherichia coli fermentation process was optimized by EAs [17][18].This was considered as thefirst case study in this work and will be briefly described next.During the aerobic growth of the bacterium,with glucose as the only added substrate,the microorganism can follow three main different metabolic pathways:•Oxidative growth on glucose:k1S+k5Oµ1−→X+k8C(1)•Fermentative growth on glucose:k2S+k6Oµ2−→X+k9C+k3A(2)•Oxidative growth on acetic acid:k4A+k7Oµ3−→X+k10C(3) where S,O,X,C,A represent glucose,dissolved oxygen, biomass,dissolved carbon dioxide and acetate components, respectively.In the sequel,the same symbols are used to represent the state variables’concentrations(in g/kg);µ1to µ3are time variant specific growth rates that nonlinearly depend on the state variables,and k i are constant yield coefficients.The associated dynamical model can be described by the following equations:dXdt =(−k1µ1−k2µ2)X+F in,S S indt =(k3µ2−k4µ3)X−DA(6)dOdt =(k8µ1+k9µ2+k10µ3)X−CT R−DC(8)dWT f(10) The relevant state variables are initialized with the follow-ing values:X(0)=5,S(0)=0,A(0)=0,W(0)=3. Due to limitations in the feeding pump capacity,the value of F in,S(t)must be in the range[0.0;0.4].Furthermore, the following constraint is defined over the value of W: W(t)≤5.Thefinal time(T f)is set to25hours.B.Case study IIThis system is a fed-batch bioreactor for the production of ethanol by Saccharomyces cerevisiae,firstly studied by Chen and Huang[5].The aim is tofind the substrate feed rate profile that maximizes the yield of ethanol.The model equations are the following:dx1x4(11)dx2x4(12)dx3x4(13)dx41+x30.22+x2(15)g2=171.5x2dx10.12+A −ux1dt =x3x4e−5x4x5(19)dx3x5)x3(20) dx4x5(21)dx5(x4+0.4)(x4+62.5)(23) The aim of the optimization is tofind the feeding profile (u)that maximizes the following PI:P I=x1(T f)x5(T f)(24) Thefinal time is set to T f=15(hours)and the initial values for relevant state variables are the following:x1(0)= 0,x2(0)=0,x3(0)=1,x4(0)=5and x5(0)=1.The feed rate is constrained to the range u(t)∈[0.0;3.0].III.T HE A LGORITHMSThe optimization task is tofind the feeding trajectory, represented as an array of real-valued variables,that yields the best performance index.Each variable will encode the amount of substrate to be introduced into the bioreactor, in a given time unit,and the solution will be given by the temporal sequence of such values.In this case,the size of the genome would be determined based on thefinal time of the process(T f)and the discretization step(d)considered in the numerical simulation of the model,given by the expression: T fdI+1(25) where I stands for the number of points within each interpo-lation interval.The value of d used in the experiments was d=0.005,for case studies I,II and III.The evaluation process,for each individual in the pop-ulation,is achieved by running a numerical simulation of the defined model,given as input the feeding values in the genome.The numerical simulation is performed using ODEToJava,a package of ordinary differential equation solvers,using a linearly implicit implicit/explicit(IMEX) Runge-Kutta scheme used for stiff problems[2].Thefitness value is then calculated from thefinal values of the state variables according to the PI defined for each case.A.Particle Swarm OptimizationA particle swarm optimizer uses a population of particles that evolve over time byflying through space.The particles imitate their most successful neighbors by modifying their velocity component to follow the direction of the most successful position of their neighbors.Each particle is defined by:P(i)t= x t,v t,p t,e tx t∈R d is the current position in the search space;p t∈R d is the position visited by the particle in the past that had the best function evaluation;v t∈R d is a vector that represents the direction in which the particle is moving,it is called the‘velocity’;e t is the evaluation of p t under the function being optimized,i.e.e t=f(p t).Particles are connected to others in the population via a predefined topology.This can be represented by the adja-cency matrix of a directed graph M=(m ij),where m ij= 1if there is an edge from particle i to particle j and m ij=0 otherwise.At each iteration,a new population is produced by allow-ing each particle to move stochastically toward its previous best position and at the same time toward the best of the previous best positions of all other particles to which it is connected.The following is an outline of a generic PSO.1)Set the iteration counter,t=0.2)Initialize each x(i)and v(i)randomly.Set p(i)=x(i)0.3)Evaluate each particle and set e(i)=f(p(i)0).4)Let t=t+1and generate a new population,whereeach particle i is moved to a new position in the search space according to:(i)v(i)t=velocityvelocityupdate(v(i)t−1)=X j∈N(i)r·(c1+c2)4(i.e.,smallperturbations will be preferred over larger ones).where[min i;max i]is the range of values allowed for gene i.In both cases,an innovation is introduced:the mutation operators are applied to a variable number of genes(a value that is randomly set between1and10in each application). 20213p<0.001 20.001≤p<0.01 10.01≤p<0.05 N p≥0.05CanPso2.5154±0.71232.5563±0.70912.5641±0.7168 DE9.3693±0.05709.4738±0.00529.4770±0.0028 DEBest2.7077±0.19212.7419±0.21152.7936±0.2176 DETourn9.1044±0.19839.2913±0.12409.3596±0.1114 EA7.9371±0.13558.5161±0.08838.8121±0.0673 Fips9.1804±0.16429.4280±0.05519.4528±0.0538CanPso7.1461±1.11527.1461±1.11527.1461±1.1152 DE9.4351±0.00009.4351±0.00009.4351±0.0000 DEBest7.6932±0.83217.6937±0.83217.6937±0.8321 DETourn9.4099±0.05519.4099±0.05519.4099±0.0551 EA8.7647±0.14419.0137±0.14219.1324±0.1320 Fips9.4351±0.00009.4351±0.00009.4351±0.0000CanPso DE DEBest DETourn EA DEN-N-N3-3-1DETourn3-3-13-3-23-3-13-3-1FipsAlgorithm PI40k NFEs PI100k NFEs PI200k NFEsCanPso19385.2±284.319386.4±284.319406.8±272.5 DE20379.4±11.620397.2±13.920406.9±14.5 DEBest19418.1±290.019421.0±290.419430.5±293.5 DETourn20362.7±52.420380.4±42.720394.3±32.8 EA20151.8±69.720335.1±54.120394.7±23.1 Fips19818.0±160.719818.9±161.119818.9±161.1TABLE IVR ESULTS FOR CASE II FOR I=100(109VARIABLES),I=200(55 VARIABLES)AND I=540(21VARIABLES)RESPECTIVELY.Table V shows the comparison of the algorithms.As can be seen,CanPso continues to be the worst contender but DEBest is not a very bad choice when the number of variables is small.EA is still beaten by DE and DETourn in most cases. Figure2presents the convergence curve of the algorithms. DE and DETourn converge fast(around40,000NFEs);Fips gets stuck in a plateau that is higher than the one of DEBest and CanPso;EA converges slowly but is steadily improving. It seems that,given enough time,EAfinds similar solutions to either DE and DETourn.20233-3-1DEBest 3-3-1N-N-N 3-3-N EAN-N-N3-3-NN-N-N3-3-N3-3-NTABLE VP AIRWISE T -TEST WITH THEH OLM P -VALUE ADJUSTMENT FOR THEALGORITHMS OF CASEII.T HE P -VALUE CODES CORRESPOND TOI =100,I =200AND I =540RESPECTIVELY .1650017000 17500 18000 18500 19000 19500 20000 20500 050000100000 150000200000P INFEsCanPsoFips DE DEBest DETournEAFig.2.Convergence of the algorithms for case II for I =200.E.Results for case IIITable VI presents the results of the algorithms on case III.This case seems to be quite simple and most algorithms find similar results.DE ,Fips and EA are the best algorithms in this problem because of their reliability:they have narrow confidence intervals.DETourn seems to be a little less reliable,but its confidence intervals are still small enough.Table VII shows the comparison of the algorithms for this problem.In this case,most algorithms are not statistically different.This is the case when we turn to the reliability of the algorithms to draw conclusions.As we stated before,most algorithms find similar solutions,which indicates that this case is probably not a good benchmark to compare algorithms.Figure 3presents the convergence curve of the algorithms for I =100.In this case DE ,DETourn and Fips converge very fast;EA has a slower convergence rate;CanPso and DEBest get stuck in local optima.V.C ONCLUSIONSANDF URTHER W ORKThis paper compares canonical particle swarm (CanPso ),fully informed particle swarm (Fips ),a real-valued EA (EA )and three schemes of differential evolution (DE ,DEBest and DETourn )in three test cases of optimizing the feeding trajectory in fed-batch fermentation.Each of these problems was tackled with different numbers of points (i.e.,different values for I )to interpolate the feeding trajectory.This is a trade off:the more variables we have,the more precise the curve is but the harder it is to optimize.CanPso 27.069±1.75127.370±1.83627.579±1.681DE 32.641±0.02932.674±0.00232.680±0.001DEBest 30.774±1.00430.775±1.00430.775±1.004DETourn 32.624±0.05732.629±0.05632.631±0.056EA 32.526±0.02532.633±0.01332.670±0.008Fips 32.625±0.10032.629±0.09932.630±0.099CanPso 31.914±0.66231.914±0.66231.914±0.662DE 32.444±0.00032.444±0.00032.444±0.000DEBest 31.913±0.70031.914±0.70031.914±0.700DETourn 32.441±0.00532.441±0.00532.441±0.005EA 32.413±0.01232.439±0.00332.443±0.001Fips 32.444±0.00032.444±0.00032.444±0.000CanPsoDE DEBest DETourn EADE 1-N-N 1-N-N DETourn 2-N-NN-3-N1-N-N N-3-NFips1214 16 18 20 22 24 26 28 30 32 34 050000100000 150000200000P INFEsCanPsoFips DE DEBest DETournEAFig.3.Convergence of the algorithms for case III when I =100.to choose DE instead.Previous work by the authors [19]developed a new representation in EAs in order to allow the optimization of a time trajectory with automatic interpolation.It would be interesting to develop a similar approach within DE or Fips .Another area of future research is the consideration of on-line adaptation,where the model of the process is updated during the fermentation process.In this case,the good computational performance of DE is a benefit,if there is the need to re-optimize the feeding given a new model and values for the state variables are measured on-line.A CKNOWLEDGMENTSThis work was supported in part by the Portuguese Foundation for Science and Technology under project POSC/EIA/59899/2004.The authors wish to thank Project SeARCH (Services and Advanced Research Computing with HTC/HPC clusters),funded by FCT under contract CONC-REEQ/443/2001,for the computational resources made avail-able.R EFERENCES[1]P.Angelov and R.Guthke.A Genetic-Algorithm-based Approach toOptimization of Bioprocesses Described by Fuzzy Rules.Bioprocess Engin.,16:299–303,1997.[2]Spiteri Ascher,Ruuth.Implicit-explicit runge-kutta methods for time-dependent partial differential equations.Applied Numerical Mathe-matics ,25:151–167,1997.[3]J.R.Banga,C.Moles,and A.Alonso.Global Optimization of Bio-processes using Stochastic and Hybrid Methods.In C.A.Floudas and P.M.Pardalos,editors,Frontiers in Global Optimization -Nonconvex Optimization and its Applications ,volume 74,pages 45–70.Kluwer Academic Publishers,2003.[4]A.E.Bryson and Y .C.Ho.Applied Optimal Control -Optimization,Estimation and Control .Hemisphere Publication Company,New York,1975.[5]C.T.Chen and C.Hwang.Optimal Control Computation forDifferential-algebraic Process Systems with General Constraints.Chemical Engineering Communications ,97:9–26,1990.[6]J.P.Chiou and F.S.Wang.Hybrid Method of Evolutionary Algorithmsfor Static and Dynamic Optimization Problems with Application to a Fed-batch Fermentation puters &Chemical Engineering ,23:1277–1291,1999.[7]Maurice Clerc and James Kennedy.The particle swarm -explosion,stability,and convergence in a multidimensional complex space.IEEE Transactions on Evolutionary Computation ,6(1):58–73,2002.[8]J.Stuart Hunter George E.P.Box,William G.Hunter.Statistics forexperimenters:An introduction to design and data analysis .NY:John Wiley,1978.[9]Cyril Harold Goulden.Methods of Statistical Analysis,2nd ed .JohnWiley &Sons Ltd.,1956.[10]S Holm.A simple sequentially rejective multiple test procedure.Scandinavian Journal of Statistics ,6:65–70,1979.[11]J.Kennedy and R.Mendes.Topological structure and particle swarmperformance.In David B.Fogel,Xin Yao,Garry Greenwood,Hitoshi Iba,Paul Marrow,and Mark Shackleton,editors,Proceedings of the Fourth Congress on Evolutionary Computation (CEC-2002),Honolulu,Hawaii,May 2002.IEEE Computer Society.[12]Rui Mendes,James Kennedy,and Jos´e Neves.The fully informed par-ticle swarm:Simple,maybe better.IEEE Transactions on EvolutionaryComputation ,8(3):204–210,2004.[13]Z.Michalewicz.Genetic Algorithms +Data Structures =EvolutionPrograms .Springer-Verlag,USA,third edition,1996.[14]H.Moriyama and K.Shimizu.On-line Optimization of CultureTemperature for Ethanol Fermentation Using a Genetic Algorithm.Journal Chemical Technology Biotechnology ,66:217–222,1996.[15]S.Park and W.F.Ramirez.Optimal Production of Secreted Protein inFed-batch Reactors.AIChE J ,34(9):1550–1558,1988.[16]I.Rocha.Model-based strategies for computer-aided operation ofrecombinant E.coli fermentation .PhD thesis,Universidade do Minho,2003.[17]I.Rocha and E.C.Ferreira.On-line Simultaneous Monitoring ofGlucose and Acetate with FIA During High Cell Density Fermentation of Recombinant E.coli.Analytica Chimica Acta ,462(2):293–304,2002.[18]M.Rocha,J.Neves,I.Rocha,and E.Ferreira.Evolutionary algo-rithms for optimal control in fed-batch fermentation processes.In G.Raidl et al.,editor,Proceedings of the Workshop on Evolutionary Bioinformatics -EvoWorkshops 2004,LNCS 3005,pages pp.84–93.Springer,2004.[19]Miguel Rocha,Isabel Rocha,and Eug´e nio Ferreira.A new represen-tation in evolutionary algorithms for the optimization of bioprocesses.In Proceedings of the IEEE Congress on Evolutionary Computation ,pages 484–490.IEEE Press,2005.[20]J.A.Roubos,G.van Straten,and A.J.van Boxtel.An EvolutionaryStrategy for Fed-batch Bioreactor Optimization:Concepts and Perfor-mance.Journal of Biotechnology ,67:173–187,1999.[21]Rainer Storn.On the usage of differential evolution for functionoptimization.In 1996Biennial Conference of the North American Fuzzy Information Processing Society (NAFIPS 1996),pages 519–523.IEEE,1996.[22]Rainer Storn and Kenneth Price.Minimizing the real functions ofthe icec’96contest by differential evolution.In IEEE International Conference on Evolutionary Computation ,pages 842–844.IEEE,May 1996.[23]A.Tholudur and W.F.Ramirez.Optimization of Fed-batch BioreactorsUsing Neural Network Parameters.Biotechnology Progress ,12:302–309,1996.[24]V .van Breusegem and G.Bastin.Optimal Control of Biomass Growthin a Mixed Culture.Biotechnology and Bioengineering ,35:349–355,1990.2025。
正确对待算法的作文题目

正确对待算法的作文题目英文回答:When it comes to dealing with algorithms, it is important to approach them with a balanced perspective. On one hand, algorithms have greatly improved our lives by providing efficient solutions to complex problems. For example, search engines like Google use algorithms toquickly deliver relevant search results, saving us time and effort. Algorithms also play a crucial role in various industries, such as finance, healthcare, and transportation, where they help optimize processes and make informed decisions.However, it is equally important to acknowledge the potential drawbacks and ethical concerns associated with algorithms. One major concern is the issue of bias. Algorithms are created by humans and can inadvertentlyreflect the biases and prejudices of their creators. For instance, facial recognition algorithms have been found tohave higher error rates for people with darker skin tones, leading to potential discrimination. Another concern is the lack of transparency and accountability in algorithmic decision-making. When algorithms are used to make important decisions, such as in hiring or loan approvals, it iscrucial to ensure that they are fair, unbiased, and explainable.To address these concerns, it is necessary to have regulations and guidelines in place to govern the development and use of algorithms. Governments and organizations should promote transparency andaccountability by requiring algorithmic systems to be auditable and explainable. Additionally, there should be diversity and inclusivity in the teams developingalgorithms to minimize biases. Regular audits and evaluations of algorithms should be conducted to identify and rectify any biases or errors.Moreover, it is essential to educate the public about algorithms and their impact. Many people are unaware of how algorithms work and the potential consequences of their use.By promoting digital literacy and providing accessible resources, individuals can make informed decisions and actively engage in discussions about algorithmic fairness and ethics.In conclusion, algorithms have become an integral partof our lives, bringing numerous benefits and conveniences. However, we must approach them with caution and address the potential biases and ethical concerns they may pose. By implementing regulations, promoting transparency, and educating the public, we can ensure that algorithms are developed and used in a responsible and fair manner.中文回答:谈到处理算法时,我们需要以平衡的态度来对待它们。
The development and comparison of robust methods for estimating the fundamental matrix

1. Introduction
In most computer vision algorithms it is assumed that a least squares framework is su cient to deal with data corrupted by noise. However, in many applications, visual data are not only noisy, but also contain outliers, data that are in gross disagreement with a postulated model. Outliers, which are inevitably included in an initial t, can so distort a tting process that the tted parameters become arbitrary. This is particularly severe when the veridical data are themselves degenerate or near-degenerate with respect to the model, for then outliers can appear to break the degeneracy. In such circumstances, the deployment of robust estimation methods is essential. Robust methods continue to recover meaningful descriptions of a
statistical population even when the data contain outlying elements belonging to a di erent population. They are also able to perform when other assumptions underlying the estimation, say the noise model, are not wholly satis ed. Amongst the earliest to draw the value of such methods to the attention of computer vision researchers were Fischler and Bolles (1981). Figure 1 shows a table of x; y data from their paper which contains a gross outlier (Point 7). Fit 1 is the result of applying least squares, Fit 2 is the result of applying least squares after one robust method has removed the outlier, and the solid line is the result of applying their fully robust RANSAC algorithm to the data. The data set can also be used to demonstrate the failings of na ve heuristics to remove outliers. For example, discarding
几种常见的优化方法ppt课件
required for integration is usually trivial in comparison to
the time required for the force calculations.
Example of integrator for MD simulation
• One of the most popular and widely used integrators is
the Verlet leapfrog method: positions and velocities of
7
Continuous time molecular dynamics
1. By calculating the derivative of a macromolecular force
field, we can find the forces on each atom
as a function of its position.
11
Choosing the correct time step…
1. The choice of time step is crucial: too short and
phase space is sampled inefficiently, too long and the
energy will fluctuate wildly and the simulation may
– Rigid body dynamics
– Multiple time step algorithms
UNISINOS – Universidade do Vale do Rio dos Sinos

A Comparative Study of Algorithms for3D MorphingT ATIANA F IGUEIREDO E VERS,M ARCELO W ALTERUNISINOS–Universidade do Vale do Rio dos SinosPIPCA-Mestrado em Computac¸˜a o Aplicadatatiana,marcelow@exatas.unisinos.brAbstract.We present a comparative study between two3D morphing algorithms for polyhedral objects.A 3D morphing algorithm establishes a smooth transition between the source object and the target object.The two algorithms compared are the one presented by Hong et al.[1]and the one presented by Kent et al.[2].The main conclusion is that,in general,the latter algorithm delivers morphy sequences that look more natural.1IntroductionMorphing techniques allow the transformation of a sourceobject into a target object.One of the main goals of morph-ing is to convince the eye that the source object is smoothlytransformed into the target object.In this study we imple-mented and compared two algorithms([1]and[2]).We selected these2algorithms since they are among thefirst solutions presented for the3D morphing problem andstill today they are at the core of many morphing solutions.2AlgorithmsBoth algorithms divide the problem into two steps.Thefirststep deals with the correspondence between the points,orhow to establish a mapping between each point of the tar-get and source objects.Once this correspondence is estab-lished,the second step deals with the problem of interpola-tion.The algorithms differ on how to establish the mapping.Hong uses the criterion of the minimal dynamic distanceswhereas Kent combines the topologies of the source andtarget objects,creating a new object.For the interpolationstep both solutions use a linear interpolation between eachpair of correspondent vertices on a user-given number offrames.(a)Hong’smorphing(b)Kent’s morphingFigure1:Visual ComparisonMorphing KentIt does not seemvery real dependingon the complexityof objectsIntermediate Soft andforms continuousPolyhedralobjectsConectivity MantainTable1:Comparison between algorithms[1]and[2]3ConclusionsA summary of ourfindings is presented on Table1and a vi-sual comparison between the2algorithms in shown in Fig-ure1.The technique presented by Kent et al.preserves thetopology of intermediate objects,keeping the conectivitybetween the faces.This generates transformations with lit-tle distortions in the intermediate frames,that is,a soft andcontinuous morphing.The technique presented by Hong etal.,on the other hand,ignores the topological informationof the models,resulting in intermediate models where thefaces seem“tofly separately”during the transformation.Therefore,in general,the solution proposed by Kent hasbetter visual results.References[1]HONG,Tong Minh;MAGNENAT-THALMANN,N.;THALMANN,D.A General Algorithm for Interpola-tion in a Facet-Based Representation.In:Graphics In-terface’88...Canada.1988.p.229-235.[2]KENT,James R.;PARENT,Richard E.;CARLSON,Wayne E..Shape Transformation for Polyhedral Ob-jects.In:SIGGRAPH’92...,Estados Unidos.ACMPress.V ol.26,n.2,1992,p.47-54.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1 Introduction
Experimental comparison of algorithms for non-rigid motion and correspondence estimation is highly important. A vast amount of relevant work published in the last decade builds on heterogeneous ideas, yet no single algorithm is known to provide a robust solution under a variety of conditions. In this paper we attempt to cross-investigate a number of algorithms some well-established ones as well as some promising recent approaches with the aim of identifying the ideas that may lead to major improvements of current methods of non-rigid motion analysis. Why is it desirable to further improve current motion analysis techniques? The answer is: some developing applications impose much greater requirements for motion analysis than what current methods are capable of. While speci c applicationdependent techniques, e.g., left-ventricular surface motion tracking 10 or cerebral cortical surface correspondence estimation 13 , have proved to be very successful, in general very little is known about how to robustly recover unrestricted non-rigid motion from observations. The potential bene ts of such knowledge are manifold. It may further help the analysis of 3D biomedical images by quantifying what is currently perceived only visually as a motion eld between corresponding points. It may facilitate the segmentation of multiple motion by ltering out
flaskov,chandrag@ http: vims
Abstract
We address the problem of non-rigid motion and correspondence estimation in 3D images in the absense of prior domain information. A generic framework is utilized in which a solution is approached by hypothesizing correspondence and evaluting the motion models constructed under each hypothesis. We present and evaluate experimentally ve algorithms that can be used in this approach. Our experiments were carried out on synthetic and real data with ground truth correspondence information.
Funding for this work was provided u9984842 and CISE CDA-9703088.
motions with distinct characteristics. Another interesting potential application is decreasing the bandwidth in transmission of dynamic image sequences: if compact representation of the motion between successive images could be found, only this component would need to be transmitted instead of full images. The goal of a robust non-rigid motion estimation algorithm can be seen as the following: in the absence of any prior information other than 3D images before and after motion, recover some meaningful compact representation of the observed motion. Let us point out the three essential requirements of this scenario: 1. Correspondence between points, or other features, in images is assumed unknown. As part of its job, the algorithm must recover the correspondence, but it is not the only objective of the algorithm. 2. No prior shape information, nor any information about the physical properties, is available. 3. The algorithm must not be limited to speci c points in objects with some favorable properties. The problem of unknown correspondence lies at the heart of non-rigid motion estimation. In some cases, it may be decoupled from the motion estimation, in that the results of an algorithm providing only correspondence can be later used by a motion estimation algorithm that assumes known correspondence. For this reason we also consider the correspondence only" algorithms in the current investigation. The second requirement prompts us to leave out the physically-based methods as well as the methods utilizing global shape topology. The rationale here is that using a model from an inappropriate domain may lead to erroneous model estimation, which would severely hamper motion analysis. Finally, the requirement for applicability to arbitrary points rules out the techniques that are looking for feature points", such as points with high curvature, etc. Comprehensive coverage of non-rigid motion estimation techniques can be found in two literature reviews published in the mid-90's 1, 9 . Experimental cross-evaluation of such techniques, to our knowledge, is the rst of a kind. Due to space constraints and heterogeneity of existing algorithms we are only able to cover a small subset thereof. Nonetheless we hope that the ndings of this work provide a useful insight in development of more advanced techniques.
2 Generic Framework for Non-rigid Motion and Correspondence Estimation
