tigase开发指南
eclipse 3.4 三大框架(struts+hibernate+spring)搭建

eclipse 3.4 三大框架(struts+hibernate+spring)搭建
看到有很多文章都是eclipse+myeclipse搭建三大框架,其实,我们完全可以自己动手来搭建,搭建一个自己的myeclipse。
struts框架,到/下载struts tools 解压放到eclipse目录下的features 和plugins目录下即可,也可以通过后面安装hibernate时提供的网址下载。
这个比较简单,没什么难度,eclipse插件的安装,大多数都是解压后放到eclipse目录下的features和plugins也可以自己建目录,再接连接来使用插件(可以参考
网上的一些别的教程,有很多是关于eclipse插件安装的)。
spring框架,spring框架的安装前面的步骤与汉化的步骤相同,打开eclipse-帮助-Software Updates....
在打开的对话框中选择上面的第二项(Available Software)
点击Add Site按钮,弹出URL对话框,在对话框里输入:/updatesite/点击确定(OK)选择一下sping IDE等侍安装成功吧,sping框架如果下载了包,覆盖进去,是不能成功的,而且在安装时要先安装它,再安装hibernate,如果先安装了hibernate,sping 是安装不成功的,安装过程就会报错
hibernate框架,hibernate框架的安装同上,在URL项填:/jbosstools/updates/stable/,选择jboss tools,hibernate tools即可,这个网站里也有struts,也可以在这里安装,完成后eclipse会重启。
《PLC综合开发利器——CoDeSys基础编程及应用指南》_LGJ_V4(1)

PLC综合开发利器——CoDeSys基础编程及应用指南目录第0章前言 (7)第1章概述 (8)1.1IEC61131-3标准 (8)1.1.1IEC 61131简介 (8)1.1.2PLCopen组织概况 (9)1.1.3IEC 61131-3编程语言 (9)1.1.4IEC 61131-3标准语言的特点 (10)1.2软PLC-C O D E S YS (11)1.2.1软PLC控制方案 (12)1.2.2软PLC的发展方向 (13)1.3C O D E S YS概述 (14)1.3.1CoDeSys自动化解决方案 (14)1.3.2CoDeSys实时核 (16)1.4软件的安装 (17)1.4.1安装所需的软硬件要求 (18)1.4.2安装 (18)1.4.3启动编程软件 (18)1.4.4帮助 (18)1.4.5CoDeSys开发系统 (19)1.5获取资料、插件和技术论坛 (22)第2章CODESYS结构 (23)2.1软件模型 (23)2.1.1软件模型概述 (23)2.1.2软件模型的特点 (24)2.2设备 (24)2.2.1设备 (24)2.2.2设备编辑器 (27)2.3应用 (28)2.3.1任务 (28)2.3.2库文件 (38)2.3.3全局变量和局部变量 (48)2.3.4访问路径 (50)2.4程序组织单元 (51)2.4.1程序组织单元结构 (51)2.4.2函数 (53)2.4.3功能块 (56)2.4.4程序 (60)2.4.5创建的原则 (62)2.5应用对象 (62)2.5.1采样跟踪 (62)2.5.2持续变量 (68)2.5.3数据单元类型 (69)2.5.4全局网络变量 (70)2.5.5配方管理器 (71)第3章公共元素及变量 (73)3.1公用元素 (73)3.1.1字符集 (73)3.1.2分界符 (73)3.1.3关键字 (75)3.1.6空格和注释 (78)3.2变量的表示和声明 (82)3.2.1变量 (82)3.2.2标识符 (82)3.2.3变量声明 (82)3.3数据类型 (84)3.3.1标准数据类型 (84)3.3.2标准的扩展数据类型 (89)3.3.3自定义数据类型 (96)3.4变量的类型和初始化 (107)3.4.1变量的类型 (107)3.4.2变量的初始化 (109)3.5变量声明及字段指令 (110)3.5.1变量匈牙利命名法 (110)3.5.2字段Pragma指令 (111)第4章编程语言 (113)4.1指令表(IL) (114)4.1.1指令表编程语言简介 (114)4.1.2连接元素 (115)4.1.3操作指令 (118)4.1.4函数及功能块 (123)4.1.5应用举例 (124)4.2梯形图(LD)/功能块(FBD) (126)4.2.1梯形图/功能块图编程语言简介 (126)4.2.2连接元素 (128)4.2.3应用举例 (137)4.3结构化文本(ST) (141)4.3.1结构化文本编程语言简介 (141)4.3.2指令语句 (143)4.3.3应用举例 (153)4.4顺序流程图(SFC) (157)4.4.1顺序流程图编程语言简介 (158)4.4.2SFC的结构 (160)4.4.3应用举例 (172)4.5连续功能图(CFC) (173)4.5.1连续功能图编程语言结构 (173)4.5.2连接元素 (175)4.5.3CFC的组态 (182)4.5.4应用举例 (183)第5章指令系统 (184)5.1位逻辑指令 (184)5.1.1基本逻辑指令 (184)5.1.2置位优先与复位优先触发器指令 (189)5.1.3边沿检测指令 (192)5.2定时器指令 (194)5.2.1定时器 (194)5.3计数器指令 (198)5.3.1计数器简介 (198)5.3.2计数器指令 (198)5.4数据处理指令 (202)5.4.1选择操作指令 (202)5.5运算指令 (214)5.5.1赋值指令 (214)5.5.2算术运算指令 (214)5.5.3数学运算指令 (217)5.5.4地址运算指令 (221)5.6数据转换指令 (223)5.6.1数据类型转换指令 (223)第6章基础编程 (231)6.1基本编程操作 (231)6.1.1启动CoDeSys (231)6.1.2PLC程序文件的建立 (233)6.2通讯参数设置 (236)6.2.1启动Gateway Server 和PLC (236)6.3程序下载/读取 (239)6.3.1编译 (239)6.3.2登入下载 (239)6.3.3在线监控 (243)6.4程序调试 (246)6.4.1复位功能 (246)6.4.2调试工具 (248)6.5仿真 (251)6.5.1离线仿真 (251)6.6PLC脚本功能 (253)6.7程序隐含检查功能 (254)第7章程序结构 (258)7.1系统程序和用户程序 (258)7.2用户程序结构 (258)7.2.1常用的编程方法 (258)7.3锁存电路 (262)7.3.1创建锁存电路 (262)7.3.2锁存电路的实际应用 (265)第8章可视化界面建立及应用 (267)8.1C O D E S YS可视化界面 (268)8.2基本操作 (269)8.2.1创建可视化界面 (269)8.2.2添加工具 (269)8.2.3对齐工具 (270)8.2.4删除工具 (270)8.3工具 (270)8.3.1基本工具 (270)8.3.2通用控制工具 (275)8.3.3测量控制 (286)8.3.4灯/开关/位图 (292)8.3.5特殊控制 (294)8.3.6报警管理 (301)8.4视图的建立及编辑 (307)8.4.1应用举例 (307)第9章模拟量闭环控制的实现 (319)9.1模拟量闭环控制 (319)9.1.2闭环控制的主要性能指标 (320)9.2C O D E S YS的闭环控制功能 (321)9.2.1CoDeSys控制方法 (321)9.2.2使用CoDeSys实现闭环控制 (321)9.2.3模拟量输入数据整定 (323)9.2.4模拟量输出数据整定 (325)9.2.5输入数据滤波 (326)9.3数字PID控制器 (333)9.3.1PID控制原理 (333)9.3.2标准PID控制器 (335)9.3.3固定采样频率的PID控制器 (337)9.3.4PD控制器 (338)9.4数字PID控制的改进算法 (340)9.4.1积分分离控制器 (340)9.4.2带死区的PID控制器 (341)9.5闭环控制实例 (342)9.5.1PID参数整定 (342)9.5.2简易压紧机的控制实例 (343)第10章控制系统工程实例 (352)10.1.1电动机点动运行 (352)10.1.2控制电动机正、反转运行 (355)10.1.3电动机Y-△启动控制 (361)10.1.4恒压变频供水控制系统 (366)10.1.5气动分度盘正、反转控制 (371)10.1.6液位自动控制 (377)10.1.7火警报警系统 (383)10.1.8抢答器控制系统 (385)10.1.9交通灯信号控制程序 (388)10.1.10停车场管理 (393)第11章通信网络基础 (395)11.1通信技术基础 (395)11.1.1通信系统的结构 (395)11.1.2通讯传输模式 (396)11.1.3数据传送方式 (396)11.1.4数据传送介质 (400)11.2串行通信基础及协议标准 (405)11.2.1基本概述 (405)11.2.2串口通讯接口标准 (407)11.3现场总线系统 (409)11.3.1现场总线技术 (409)11.3.2现场总线的特点 (410)11.3.3IEC 61158标准 (413)11.3.4FCS与DCS的基本要点及区别 (416)11.3.5现场总线的发展历程及发展现状 (417)11.4工业以太网 (419)11.4.1TCP/IP (419)11.4.2TCP/IP的工作方式 (420)11.4.3IEEE 802通信标准 (422)11.4.4工业控制网络的拓扑结构 (424)第12章常用工业现场总线及介绍 (430)12.1CAN通讯 (430)12.1.2CANopen物理层 (439)12.1.3PDO通讯示例 (441)12.1.4SDO通信示例 (447)12.2M ODBUS网络基础 (452)12.2.1数据链路层 (453)12.2.2协议描述 (455)12.2.3Modbus串行的两种传输模式 (458)12.2.4Modbus功能码 (462)12.2.5Modbus 物理层 (465)12.2.6Modbus 串口的通讯组态 (470)12.3E THER CAT网络基础 (475)12.3.1EtherCAT物理层 (475)12.3.2EtherCAT硬件组成 (480)12.3.3EtherCAT运行原理 (480)12.3.4EtherCAT通讯模式 (489)12.3.5EtherCAT状态机 (493)12.3.6EtherCAT伺服驱动器控制应用协议 (495)12.3.7EtherCAT主从站通讯配置示例 (502)12.4PROFINET网络基础 (509)12.4.1PROFINET物理层 (509)12.4.2PROFINET (513)12.4.3PROFINET协议架构 (516)12.4.4同步实时通信 (520)12.4.5PROFINET主从站通讯配置 (523)12.5E THER N ET/IP网络基础 (532)12.5.1EtherNet/IP物理层 (532)12.5.2EtherNet/IP运行原理 (537)12.5.3EtherNet/IP网络性能性能指标 (543)12.5.4EtherNet/IP通讯配置 (544)第13章附录 (550)13.1附录A ST指令快查 (550)13.2附录B标准库FUN及FB快查 (551)13.3附录C常用快捷键 (553)13.3.1快捷输入 (554)13.4附录D参考文献 (556)第0章前言CoDeSys是德国3S公司的PLC编程软件,本书主要以介绍该软件的PLC编程功能。
tigase开发指南

tigase组件插件配置tigase启动时会初始化并启动相关组件和插件,启动的组件或开通监听端口号或访问数据库或者创建线程池,默认有些组件和插件非必须,我们也用不到,为了避免资源浪费,需要在配置中注释这些组件。
组件如下表格所示,红字的组件说明:配置文件配置启动组件:修改插件如下表格所示,红字的插件说明:配置文件配置启动组件:修改Tigase数据库表Tigase用户信息、权限信息、离线消息信息、在线离线状态信息都存储在数据库中,但有些数据我们不需要让tigagse存储、更新,比如在线离线状态信息,如果每个用户登录、登出都让tigase更新表的字段,并发高了,显然数据库承受不了。
为了避免资源浪费也需要避免这些操作。
登录状态上线更新上线状态更新是在验证用户名和密码时更新,验证功能是需要我们自定义的,仅需修改tigase验证模块的一小块代码即可。
下图贴出tigase源码修改方式。
登录状态下线更新下线状态更新是在用户退出、连接断开等时更新,修改代码也比较简单。
tigase 权限验证云果登陆流程时需要验证权限,权限验证需要分匿名用户和企业客服两种,匿名用户默认验证都可以通过,企业客服需要验证是否在用户中心登陆成功。
企业客服登陆1.登陆用户中心,登陆成功后,用户中心会保存cookieid至缓存中2.带着用户名、cookieid同tigase服务端建立连接3.从缓存中获取验证信息4.如果认证通过和tigase连接上tigase的验证是需要我们自定义开发的,只需要在tigase权限验证模块修改即可。
tigase 在线坐席获取匿名用户登陆需要根据客户名分配一个在线坐席会话。
tigase roster插件是用于返回好友列表,可以修改用来分配坐席列表。
插件的调用是在SessionManager中调用:客户端获取好友列表:tigase消息转发流程用户在发消息给客服时,如果客服不在线,需要分配给机器人客服,机器人客服是以tigase客户端方式使用的,并且为了负载均衡会有多个机器人客服,所以还需要分配。
Tigase XMPP(Jabber)Server部署步骤
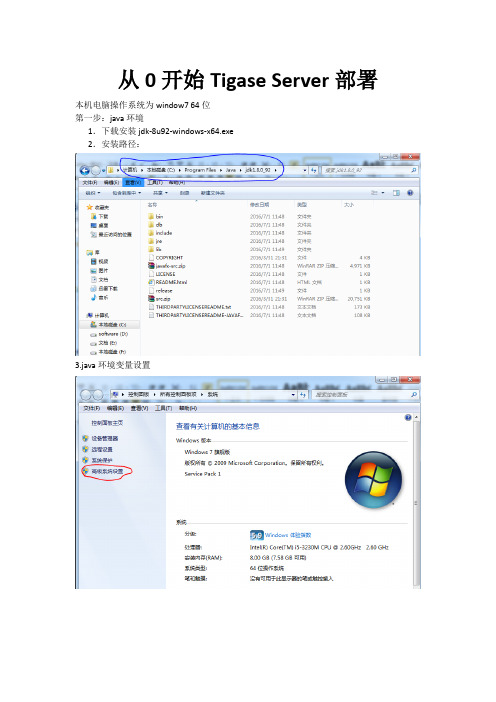
从0开始Tigase Server部署本机电脑操作系统为window7 64位第一步:java环境1.下载安装jdk-8u92-windows-x64.exe2.安装路径:3.java环境变量设置4.测试java环境是否安装好,运行cmd第二步:安装Tigase1.下载tigase-server-7.0.4-b3844.jar----https:///projects/tigase-server/files2.3.双击tigase-server-7.0.4-b3844.jar运行4.5.环境变量路径6.安装客户端:潘迪安Pandion再注册一个test-02,添加联系人test-01Win7安装并配置Tigase 5.2服务器标签:tigasexmppxmpp server2014-06-16 10:15 4704人阅读评论(7) 收藏举报分类:消息中间件(41)作者同类文章X版权声明:本文为博主chszs的原创文章,未经博主允许不得转载。
Win7安装并配置Tigase服务器作者:chszs,转载需注明。
博客主页:/chszs1、下载tigase-server-5.2.0-b3447.exe2、执行可执行文件,解压出tigase-server-5.2.0-b3447.jar,放到D盘根目录3、以管理员权限打开CMD环境,并执行以下命令:D:\>java -jar tigase-server-5.2.0-b3447.jar弹出GUI界面,开始图形化安装过程。
- 接着选择Java安装环境,C:\jdk7- 选择“安装Tigase服务器”和“配置Tigase服务器”- 接着是Tigase的介绍- 接着是同意GNU许可证- 再接着是选择安装路径,d:\Tigase- 接着是选择要安装的包或模块,有:必选的:Base、Windows Files、可选的:Docs、Extras、Groovy scripting、Derby数据库及驱动、MySQL数据库驱动、PostgreSQL数据库驱动、SQL Server数据库驱动、OSGi依赖、HTTP API组件、源码我选择了Docs、Extras、Groovy scripting、MySQL数据库驱动、HTTP API组件、源码- 开始安装顺利执行完。
Eclipse下Hibernate入门

最近boss让做项目,借机学习了一下Hibernate,小有收获。
hiberante是对数据库持久层访问的一种机制,hibernate的应用可以使程序员将重点放到业务逻辑的实现上。
hibernate的原理是将数据库结构封装,使程序员可以像使用普通对象一样调用数据库的相关接口,从实现数据库的相关操作。
由于Exadel基于eclipse集成了Hibernate,并且方便易用所以我选用Exadel+Mysql还需要hibernate3.jar mysql-connector /downloads/在Mysql中新建test数据库(Mysql其实有个空的test数据库),然后新建下面的Tablecreate table user (id int(10) not null auto_increment primary key,name varchar(20) not null,password varchar(20) not null,email varchar(50),address varchar(100))type=innodb;新建Java Project,将Mysql_Driver,Hibernate两个user library添加到该工程的java build path中。
新建与数据表对应的POJO类:User和Contact/*****/package er;/*** @author lzy**/public class User{private Integer id;private String name;private String password;private Contact contact;/*** @return Returns the id.*/public Integer getId() {return id;}/*** @param id The id to set.*/public void setId(Integer id) { this.id = id;}/*** @return Returns the name.*/public String getName() {return name;}/*** @param name The name to set.*/public void setName(String name) { = name;}/*** @return Returns the password.*/public String getPassword() {return password;}/*** @param password The password to set.*/public void setPassword(String password) { this.password = password;}/*** @return Returns the contact.*/public Contact getContact() {return contact;}/*** @param contact The contact to set.*/public void setContact(Contact contact) { this.contact = contact;}}/****/package er;/*** @author lzy**/public class Contact {private String email;private String address;/*** @return Returns the address.*/public String getAddress() {return address;}/*** @param address The address to set.*/public void setAddress(String address) { this.address = address;}/*** @return Returns the email.*/public String getEmail() {return email;}/*** @param email The email to set.*/public void setEmail(String email) {this.email = email;}}添加Hibernate支持,这时系统会要求输入一些信息,按提示即可完成后系统自动生成hibernate.cfg.xml,User.hbm.xml映射文件必须稍作修改。
tigase开发的指南

tigase开发指南tigase组件插件配置tigase启动时会初始化并启动相关组件和插件,启动的组件或开通监听端口号或访问数据库或者创建线程池,默认有些组件和插件非必须,我们也用不到,为了避免资源浪费,需要在配置中注释这些组件。
组件如下表格所示,红字的组件说明:配置文件配置启动组件:修改init.properties插件如下表格所示,红字的插件说明:配置文件配置启动组件:修改init.properties/protocol/commands,jabber:iq:private,urn:xmpp:ping,amp,disco, domain-filter,zlib,message-carbons,vcard-xep-0292,urn:xmpp:timeTigase数据库表Tigase用户信息、权限信息、离线消息信息、在线离线状态信息都存储在数据库中,但有些数据我们不需要让tigagse存储、更新,比如在线离线状态信息,如果每个用户登录、登出都让tigase更新表的字段,并发高了,显然数据库承受不了。
为了避免资源浪费也需要避免这些操作。
登录状态上线更新上线状态更新是在验证用户名和密码时更新,验证功能是需要我们自定义的,仅需修改tigase验证模块的一小块代码即可。
下图贴出tigase源码修改方式。
登录状态下线更新下线状态更新是在用户退出、连接断开等时更新,修改代码也比较简单。
tigase 权限验证云果登陆流程时需要验证权限,权限验证需要分匿名用户和企业客服两种,匿名用户默认验证都可以通过,企业客服需要验证是否在用户中心登陆成功。
企业客服登陆1.登陆用户中心,登陆成功后,用户中心会保存cookieid至缓存中2.带着用户名、cookieid同tigase服务端建立连接3.从缓存中获取验证信息4.如果认证通过和tigase连接上tigase的验证是需要我们自定义开发的,只需要在tigase权限验证模块修改即可。
XMPP服务器tigase源码部署

XMPP服务器tigase源码部署1.下载安装支持首先确保已安装JDK1.6和Maven 2.x/3.x。
2.获取Tigase server源码svn co tigase-server3.使用Maven编译(文件将会被编译到根目录下的target文件夹下)mvn assembly:assembly4.对编译好的jar进行解压cd target/tar -zxvf tigase-server-5.1.0-SNAPSHOT-prodenv.tar.gz5.配置环境变量cd tigase-server-5.1.0-SNAPSHOT/vi /etc/profileJAVA_HOME=/usr/java/jdk1.6.0_29export JAVA_HOME PATHTIGASE_HOME="/home/workspace/tigase_server_dev/targe t/tigase-server-5.1.0-SNAPSHOT/"export TIGASE_HOME并修改tigase.conf文件中的jdkpath为JAVA_HOME="${JAVA_HOME}"6.赋予执行权限chmod u+x bin/*7.配置init.properties //mysql 为数据库config-type=--gen-config-def--admins=****************--virt-hosts =--debug=server--monitoring=jmx:9050,http:9080,snmp:9060--user-db=mysql--user-db-uri=jdbc:mysql://127.0.0.1:3306/tigasedb?user=root&password =smm10188.修改/tigase_server/src/main/assembly/prodenv.xml配置文件,使assembly能够编译打包好所有的jar和必要的配置文件。
stage 开发手册

stage 开发手册标题:Stage 开发手册一、引言Stage 是一个用于数据处理和分析的开源框架,它提供了一种简单易用的方式来构建复杂的数据管道。
本开发手册将帮助你了解如何使用 Stage 进行开发。
二、安装与配置1. 下载并安装 Java Development Kit (JDK) 8 或更高版本。
2. 下载 Stage 的最新发行版,并解压缩到指定目录。
3. 配置系统环境变量,将 Stage 的 bin 目录添加到 PATH 中。
三、快速开始1. 创建一个新的 Stage 项目。
你可以使用命令行工具或者集成开发环境(IDE)如 IntelliJ IDEA 或 Eclipse。
2. 在项目中创建一个新的 Stage 管道。
管道是 Stage 的基本单位,用于描述数据从输入源流向输出目的地的过程。
3. 在管道中添加阶段。
阶段是执行特定任务的基本单元,例如读取文件、过滤数据、转换数据等。
4. 运行你的 Stage 管道。
你可以使用命令行工具或者 IDE 来运行你的管道。
四、进阶指南1. 数据源与接收器:Stage 支持多种数据源和接收器,包括文件、数据库、消息队列等。
2. 转换阶段:Stage 提供了大量的转换阶段,可以帮助你完成各种数据处理任务。
3. 自定义阶段:如果你需要执行一些 Stage 不支持的任务,你可以编写自己的自定义阶段。
4. 并行处理:Stage 支持并行处理,可以提高数据处理的效率。
五、最佳实践1. 使用注释:在你的代码中添加注释,可以帮助你和其他开发者理解你的代码。
2. 测试你的代码:在发布你的代码之前,确保它通过了所有的测试。
3. 保持代码简洁:避免过度复杂的代码结构,尽量保持你的代码简洁易懂。
六、社区与支持Stage 拥有一个活跃的社区,你可以在这里找到大量的资源和帮助。
如果你遇到问题,可以在 Stack Overflow 或者 Stage 用户论坛上提问。
七、结语希望这份开发手册能帮助你更好地理解和使用 Stage。
最新tigase开发指南教学文案

tigase开发指南tigase组件插件配置tigase启动时会初始化并启动相关组件和插件,启动的组件或开通监听端口号或访问数据库或者创建线程池,默认有些组件和插件非必须,我们也用不到,为了避免资源浪费,需要在配置中注释这些组件。
组件如下表格所示,红字的组件说明:配置文件配置启动组件:修改init.properties插件如下表格所示,红字的插件说明:配置文件配置启动组件:修改init.properties/protocol/commands,jabber:iq:private,urn:xmpp:ping,amp,disco,domain-filter,zlib,message-carbons,vcard-xep-0292,urn:xmpp:timeTigase数据库表Tigase用户信息、权限信息、离线消息信息、在线离线状态信息都存储在数据库中,但有些数据我们不需要让tigagse存储、更新,比如在线离线状态信息,如果每个用户登录、登出都让tigase更新表的字段,并发高了,显然数据库承受不了。
为了避免资源浪费也需要避免这些操作。
登录状态上线更新上线状态更新是在验证用户名和密码时更新,验证功能是需要我们自定义的,仅需修改tigase验证模块的一小块代码即可。
下图贴出tigase源码修改方式。
登录状态下线更新下线状态更新是在用户退出、连接断开等时更新,修改代码也比较简单。
tigase 权限验证云果登陆流程时需要验证权限,权限验证需要分匿名用户和企业客服两种,匿名用户默认验证都可以通过,企业客服需要验证是否在用户中心登陆成功。
企业客服登陆1.登陆用户中心,登陆成功后,用户中心会保存cookieid至缓存中2.带着用户名、cookieid同tigase服务端建立连接3.从缓存中获取验证信息4.如果认证通过和tigase连接上tigase的验证是需要我们自定义开发的,只需要在tigase权限验证模块修改即可。
eclipse搭建SSH框架详解

SSH框架是最常用的框架之一,在搭建SSH框架的时候总有人遇到这样,那样的问题。
下面我介绍一下SSH框架搭建的全过程。
第一步:准备工作。
下载好eclipse,Struts2,Spring,Hibernate。
1.eclipse:eclipse下载的时候建议下载JavaEE版的eclipse。
当然你也可以下载eclipse-SDK。
(下载eclipse-SDK需要下载Web,Tomcat等plugins)2.Struts2:/download1)引入Struts的jar包。
下载struts-*-all.zip 解压后,struts/lib目录下是struts 所有的相关jar包。
其中有5个是必须的:Commons-logging-1.0.4.jar,Freemarker-2.3.13.jar,Ognl-2.6.11.jar,Struts2-core-2.1.6.jar,Xwork-2.1.2.jar 其余jar包并不是struts必须的。
还有3个包也要注意导入。
不导入运行Tomcat时候可能会出现异常。
commons-io-1.3.2.jar,commons-fileupload-1.2.1.jar,javassist-3.7.ga.jar 注意:javassist-3.7.ga.jar包是在struts2-blank-2.2.1.war示例工程中的web-inf/lib下的。
3.Spring:/download/community还可以在eclipse下安装下载。
具体步骤是这样的:1)打开eclipse-help-Software Updates.2) 在打开的对话框中选择上面的第二项(Available Software)。
3)点击Add Site按钮,弹出URL对话框。
4)在对话框里输入:/updatesite/点击OK。
5)选择sping IDE点击安装(Install)。
4.Hibernate:/projects/hibernate/files/hibernate3/5.Jdk的src.zip包导入。
StorageTek SL4000 模块化库系统安全指南说明书

S torageTek SL4000Modular Library System Security GuideE84232-01August2017StorageTek SL4000Modular Library System Security GuideE84232-01Copyright©2017,Oracle and/or its affiliates.All rights reserved.This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws.Except as expressly permitted in your license agreement or allowed by law,you may not use,copy,reproduce,translate,broadcast,modify,license, transmit,distribute,exhibit,perform,publish,or display any part,in any form,or by any means.Reverse engineering,disassembly,or decompilation of this software,unless required by law for interoperability,is prohibited.The information contained herein is subject to change without notice and is not warranted to be error-free.If you find any errors,please report them to us in writing.If this is software or related documentation that is delivered to the ernment or anyone licensing it on behalf of the ernment,then the following notice is applicable:ERNMENT END USERS:Oracle programs,including any operating system,integrated software, any programs installed on the hardware,and/or documentation,delivered to ernment end users are"commercial computer software"pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations.As such,use,duplication,disclosure,modification,and adaptation of the programs,including any operating system,integrated software,any programs installed on the hardware,and/or documentation,shall be subject to license terms and license restrictions applicable to the programs.No other rights are granted to the ernment.This software or hardware is developed for general use in a variety of information management applications.It is not developed or intended for use in any inherently dangerous applications,including applications that may create a risk of personal injury.If you use this software or hardware in dangerous applications,then you shall be responsible to take all appropriate fail-safe,backup,redundancy,and other measures to ensure its safe use.Oracle Corporation and its affiliates disclaim any liability for any damages caused by use of this software or hardware in dangerous applications.Oracle and Java are registered trademarks of Oracle and/or its affiliates.Other names may be trademarks of their respective owners.Intel and Intel Xeon are trademarks or registered trademarks of Intel Corporation.All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International,Inc.AMD, Opteron,the AMD logo,and the AMD Opteron logo are trademarks or registered trademarks of Advanced Micro Devices.UNIX is a registered trademark of The Open Group.This software or hardware and documentation may provide access to or information about content, products,and services from third parties.Oracle Corporation and its affiliates are not responsible for and expressly disclaim all warranties of any kind with respect to third-party content,products,and services unless otherwise set forth in an applicable agreement between you and Oracle.Oracle Corporation and its affiliates will not be responsible for any loss,costs,or damages incurred due to your access to or use of third-party content,products,or services,except as set forth in an applicable agreement between you and Oracle.ContentsPreface (v)Documentation Accessibility (v)Related Documentation (v)1OverviewNetwork Access........................................................................................................................................1-1 General Security Principles....................................................................................................................1-1 Keep Software Up To Date...............................................................................................................1-1 Restrict Network Access...................................................................................................................1-1 Keep Up To Date on Latest Security Information.........................................................................1-1 2Security FeaturesLibrary Interface Credential Requirements........................................................................................2-1 Users and Roles.........................................................................................................................................2-1 Certificates for HTTPS Interfaces.........................................................................................................2-2 Library Network Interfaces....................................................................................................................2-2 Default Port Numbers.......................................................................................................................2-3 Browser and Web Services Interfaces......................................................................................2-3Service Access..............................................................................................................................2-3SNMP............................................................................................................................................2-4E-mail............................................................................................................................................2-4DNS...............................................................................................................................................2-4NTP...............................................................................................................................................2-4Oracle Key Manager(OKM)......................................................................................................2-43InstallationHanding-Off the Library to the Customer..........................................................................................3-1 Creating the Administrator User.....................................................................................................3-1 Configuring the HTTPS Certificate.................................................................................................3-1 Redeployment...........................................................................................................................................3-1 A Secure Deployment ChecklistiiiivPreface This guide provides security principles and guidelines for Oracle’s StorageTek SL4000modular tape library(SL4000).Documentation AccessibilityFor information about Oracle's commitment to accessibility,visit the OracleAccessibility Program website at/pls/topic/lookup?ctx=acc&id=docacc.Access to Oracle SupportOracle customers that have purchased support have access to electronic supportthrough My Oracle Support.For information,visit/pls/topic/lookup?ctx=acc&id=info or visit/pls/topic/lookup?ctx=acc&id=trs if you are hearingimpaired.Related DocumentationGo to the Tape Storage section of the Oracle Help Center(/en/storage/#tape)for additional SL4000documentation:■SL4000Library Guide■SL4000SCSI Reference Guide■SL4000Safety and Compliance Guide■SL4000Licensing Information User Manualvvi1Overview 1-1OverviewT his chapter describes the general security principles for the SL4000tape library.For an overview of the product,see the SL4000Library Guide .Network AccessOracle designs and documents all tape library products for use within a controlled server environment with no general network or user work access isrequired between the library and various other servers and workstations,including:■Workstations used to access the library through the GUI or SCI interfaces ■Servers running applications that use the SCI interface,such as an ACSLS server or a custom application that uses SCI■SMTP servers for sending e-mail notifications■SNMP servers■SDP2server for "phone-home"(ASR)functionality■Oracle Key Manager (OKM)clusters for delivering encryption keys to tape drives User access to the library requires credentials (id and password)to be created on the library and to be used when connecting to the library.General Security PrinciplesThe following principles are fundamental to using any product securely.Keep Software Up To DateKeep all software versions and patches up to date.This document assumes a software level of version 1.0.Restrict Network AccessKeep the library behind a data center firewall to restricted access to a known network route,which can be monitored and restricted if necessary.As an alternative,you can substitute a firewall router for multiple,independent firewalls.You should identify the hosts allowed to attach to the library and block all other hosts where possible.Keep Up To Date on Latest Security InformationOracle continually improves its software and documentation.Check this document every release for revisions.General Security Principles1-2StorageT ek SL4000Modular Library System Security Guide2Security Features 2-1Security FeaturesT his chapter describes security features of the SL4000tape library.Library Interface Credential RequirementsThe library provides a browser-based GUI interface and a web services API(StorageTek Library Control Interface -SCI)for configuring,managing,and operating the library.Connecting with either interface requires valid credentials (user ID and password).When using the GUI,whether remotely with a browser or locally at the operator panel,you must provide a valid user ID and password to log in.When using SCI,you must embed the user ID and password into the SOAP header of each SCI method call.The library uses the WS-Security SOAP extension as defined by OASIS WS-SecurityPolicy 1.2(July 2007).Because the credentials in the header are in plain text,SCI must use an HTTPS connection.The exact details of how to include the SOAP headers depends on the language used to invoke the web services API.Users and RolesThere are two categories of users –customer (with four roles:Viewer,Operator,User,and Administrator)and service (with three roles:Service,Advanced Service,and Escalation).A user’s role determines their access to GUI functions and SCI methods:■See the “User Roles”section of the SL4000Library Guide for role descriptions and authorized GUI functions.Creating Customer UsersThe administrator can use the GUI to create customer users by defining the user ID,password,and role (see the “Add,Modify,or Delete a User”section in the SL4000Library Guide ).Passwords must be at least eight characters long and include a mix of letters (uppercase or lowercase)and numbers.Creating Service UsersService users are either automatically generated by the library following the detection of a fault or manually created by the administrator.Service users have a specified role,but a randomly generated user ID and encrypted password (known as a key file).Oracle Services can decrypt the key file to provide the credentials to a field engineer.Service users expire 72hours after creation and cannot be extended.When the library detects a fault,it automatically creates a user with the "Service"role and generates an encrypted support bundle (which contains the service key file).YouCertificates for HTTPS Interfaces2-2StorageT ek SL4000Modular Library System Security Guide must manually transmit the support bundles to Oracle Service,unless you have configured the library to perform Automated Service Requests (ASR).If the fault requires more than 72hours to resolve or requires a higher-level service role,the administrator may need to create an additional service user ID through the GUI (see the “Add a Service User”in the SL4000Library Guide ).Certificates for HTTPS InterfacesTo ensure the security of connections over HTTPS,a certificate is required on the library.The library supports three certificate types:■Default certificate (weak encryption,not recommended for use beyond installation)■Self-signed certificate (strong encryption,but requires a security exception in the browser)■Third-party signed certificate (strong encryption,guaranteed security,automatically accepted by most browsers)During initial installation,the library uses the default certificate.You should replace it by generating a new self-signed certificate (see "Generate a Self-Signed Certificate"in the SL4000Library Guide ).Using a self-signed certificate is secure,but will causebrowsers to generate a warning when connecting to the library.To avoid this warning,you must configure a security exception in the browser or install a third-party signed certificate.After generating a self-signed certificate,you may install a third-party signedcertificate which offers the strongest encryption and security,and eliminates the need for a browser security exception.Creating a properly signed certificate is a two step process.First,download the certificate signing request (CSR)from the library and submit the CSR to a third-party certifying authority (CA).Then,once the CA creates the signed certificate,upload it to the library along with a copy of the CA's certificate (see "Install a Third-Party-Signed Certificate"in the SL4000Library Guide ).Provided the certificate is signed by a well known CA,the browser will connect over HTTPS without warnings.Library Network InterfacesThe library has four sets of external network interfaces located in the Base Module’s card cage on the Library Controller and Root Switch Cards.For a diagram of the physical locations of the ports,see "Base Module Card Cage"in the SL4000Library Guide .■Customer ports —Used to connect the library into the customer's ed for library management functions (configuration,code upgrades,monitoring,andso on).Used by applications that use the web services interface (SCI).■Service port —May be used to connect to a "phone home server"(specifically Automated Service Requests (ASR)using SDP2).If connected to SDP2,the port will be connected continuously.Service engineers can also use this port while servicing the library.■OKM port —Used to connect the library to an Oracle Key Management (OKM)cluster.However,you may connect to an OKM cluster using the Service orCustomer interface.■Inter-library ports —These ports are disabled and not used in a SL4000library.Library Network InterfacesSecurity Features 2-3Default Port NumbersBy default,the library uses the port numbers listed in the table below.If using afirewall,configure it to allow traffic to use these ports.Enable the ports listed below on each of the network interfaces that are in use (except the OKM ports —you only need to enable the OKM ports on the network interface used to connect to the OKM cluster.See Oracle Key Manager (OKM)).Browser and Web Services InterfacesThe GUI can use both HTTP and HTTPS.The SCI interface uses only HTTPS to secure for the credentials passed in each request.By default,these two protocols are on their standard port number of 80for HTTP and 443for HTTPS.You can modify these ports in the GUI (see "Configure the Library with the Configuration Wizard"in the SL4000Library Guide ).Service AccessUnder normal library operations only customer-created users may log in to the library However,the administrator can enable service access when necessary (see Creating Service Users ).Creating a service user with an Escalation role enables access to the library that is not normally allowed.Specifically,an Escalation user can log in to Linux on the library using SSH on port 22and can access the WebLogic console function using port 7104for HTTP or 7105for HTTPS.Service users expire 72hours aftercreation.The library disables port 22if there are no enabled service users.The library always enables ports 7104and 7105,but unless an Escalation user exists,there are no valid users that can log in to the WebLogic console.22TCP SSH SSH access to Linux running on library.Only enabled for 72hours after an "Escalation"role service user is created.To library25TCPSMTPConnection to external SMTP (Simple Mail Transfer Protocol)server.Required if you have configured any e-mail destinations.From library 53TCP &UDP DNS DNS (domain name server)lookup.From library 80TCP HTTP Default port for browser access.To library 161UDP SNMP Inbound GET requests through SNMP .To library 162UDP SNMP Outbound SNMP TRAPs.From library 123TCP NTP Connection from library to an external NTP server.From library 443TCP HTTPS Default port for browser and web services interfaces.To library 7104TCP HTTP Alternate port for browser access.To library 7102TCP HTTPS Alternate port for browser and web services interfaces.To library 7104TCP HTTP Browser GUI based access to WebLogic console running on the library.Only accessible by an "Escalation"user.To library 7105TCPHTTPS Browser GUI based access to WebLogic console running on the library.Only accessible by an "Escalation"user.To library Externally DefinedTCP HTTP &HTTPSServers that are configured to receive outbound SCI calls will listen for SCI calls on ports of their choice.Open these port number in any firewalls and provided the port numbers configuring the destination on the library.From libraryExternally DefinedTCP OKM If the library is configured to retrieve tape drive encryption keys from a OKM cluster,open the ports used for OKM (see the OKM documentation).From libraryLibrary Network InterfacesSNMPThe library supports SNMP v3protocol.The library uses ports161(inbound)and162(outbound)for SNMP GET commands and SNMP traps respectively.E-mailThe library can send e-mail messages when certain events occur(see"ConfiguringNotifications"in the SL4000Library Guide).If you configure e-mail destinations,youmust also configure an SMTP server and open port25.DNSDNS configuration is optional.You only need to configure DNS if destinations(SNMP,E-mail,Outbound SCI)use host names.You can add up to three DNS servers(see"Configure the Library with the Configuration Wizard"in the SL4000Library Guide).DNS uses port53.NTPThe library can use an external NTP server to control the library clock.If using anexternal NTP server,you must open port123.Oracle Key Manager(OKM)You can connect an OKM cluster to the library's customer port,service port,or OKMport.The location of the OKM appliance within your network determines which portyou should use.You select the port during network configuration of the library(see"Configure the Library with the Configuration Wizard"in the SL4000Library Guide).Unlike older tape libraries,the SL4000only requires a single connection to OKM,rather than individual connections to each encrypted tape drive.You must open theports used by OKM on the selected connection.See the OKM documentation fordetails on which port numbers to use.2-4StorageT ek SL4000Modular Library System Security Guide3Installation An Oracle installation engineer will install and test the SL4000library using apre-defined user ID("installer")which initially uses with a well-known password.Thefirst step the installer performs is to change this password.Handing-Off the Library to the CustomerAfter testing the SL4000,the installation engineer begins the hand-off process totransfer the library to the customer.The hand-off involves creating an Administratoruser and finalizing the HTTPS certificate.The installation engineer initiates thehand-off,but the library administrator must complete the process.Creating the Administrator UserIn the first step of the hand-off,the administrator enters a user ID and password tocreate the Administrator account.After completing the hand-off,the library willremove the Installer user and the newly created Administrator user will be the ONLYaccount that can log in to the library.Configuring the HTTPS CertificateIn the second step of the hand-off,the administrator configures the certificate forHTTPS.There are two options:1.Continue to use the default certificate(not recommended)2.Generate a new self-signed certificate.If you do not generate a self-signed certificate,you can still access the library usingHTTPS,but it will use the weakest form of encryption.If you generate a self-signed certificate,the library begins using it immediately.Forbest security,you should replace the self-signed certificate with a third-party signedcertificate(see"Install a Third-Party Signed Certificate"in the SL4000Library Guide).RedeploymentIf you need to decommission the library,an Administrator or Service user can reset thelibrary to factory defaults through the GUI.However,you CANNOT undo this action.Redeploying the library will require Oracle Services to re-perform the installation andcustomer hand-off.Installation3-1Redeployment3-2StorageT ek SL4000Modular Library System Security GuideASecure Deployment Checklist A-1Secure Deployment ChecklistThe following security checklist includes guidelines that help secure the library:❏Enforce password management ❏Enforce access controls ❏Restrict network access –Implement a firewall–The firewall must no be compromised –Monitor system access❏Check network IP addresses❏Contact Oracle Security Products if you encounter any vulnerability in Oracle tape librariesA-2StorageT ek SL4000Modular Library System Security Guide。
tigase自定义插件的开发与配备

tigase自定义插件的开发与配备tigase自定义插件的开发与配置tigase插件开发官方地址:/content/plugin-development下面是自己的翻译加理解,英文一般,如果有误请大家指出。
-----------------------------------------------------------------------------------------------------**************************************************简介*****************************************每个PACKETS都会经过SM(session manager)的四个处理步骤:1,Pre-processing为了不影响Session Manager的性能需要限制该方法处理时间为极小值,用于判断当前package是否应该被阻塞,如果返回为true,则表示阻塞。
(应该只要有一个pre-processor阻塞就算阻塞)2,Processing如果一个Package没有被任何的pre-processors阻塞,则继续执行该方法。
所有对当前XML段感兴趣的processor都会将该段加入到独立的线程里运行,这些现成使用内部固定的队列。
当所有感兴趣的processor都执行完后就可以得到通知进入下一步。
3,post-processor对于在第2步中没有被任何processor处理的package将会通过所有的post-processors,并被最后一个post-processor转发到一个目的地,大多数情况是以<message/>的形式被转发。
4,filter对于以上三步任何形式的结果result输出,都会被所有的filters 拦截过滤,这些结果可能最终被拦截也可能被放行。
由于session manager和processors都是消费者,所以在所有的processors中应该至少有一个processor新建一个package并发送给某个目标。
80GA整合StrutsSpringHibernate框架实例教程

目录一、实验素材 (2)二、准备工作 (3)1. MyEclipse 8.0 GA Download and Install (3)2. J2SDK Download and Install (3)3. TOMCAT6 Download and Install (4)4. Struts2 Download (4)5. SQL Server2005 JDBC Driver Download and Install (4)三、搭建框架 (6)1. Create Web Project (6)2. Add Struts 2.1.8.1 Capabilities (8)3. Add Spring 2.5 Capabilities (10)4. Create Database Connection (13)5. Add Hibernate 3.2 Capabilities (15)6. Delete Conflictive Jars (22)7. Create struts.xml (22)8. Overwrite web.xml (23)9. Use Hibernate Reverse (24)10. Create UserInfoServiceImpl.java (26)11. Create UserInfoService.java (27)12. Create UserInfoAction.java (29)13. New Jsp Pages (31)14. Overwrite applicationContext.xml (32)15. Create log4j.properties (34)四、发布网站 (35)1. S2SH Project Structure (35)2. Tomcat Deployment (36)3. Start Server (37)五、版本控制(Visual Source Safe) (38)1. Vss Plugin Download and Install (38)2. Create Database (38)3. Add Project to VSS Server (39)4. New MyEclipse Web Project (40)5. Apply VSS Server to MyEclipse (42)一、实验素材1. 开发环境:MyEclipse 8.0 GA(Eclipse3.5.1,JRE1.6.0.10和MyEclipse Enterprise WorkBench8.0)2. 运行环境:JDK 6 Update 20(JRE1.6.0.13)3. 开发框架:Struts 2.1.8.1,Spring 2.5,Hibernate 3.24. 应用服务器:tomcat 6.0.265. 数据库服务器:SQL Server 2005二、准备工作1. MyEclipse 8.0 GA Downl oad and Install官方网址:/最新版本:MyEclipse 8.0 GA该安装包集成了Eclipse3.5.1,JRE1.6.0.10和MyEclipse Enterprise WorkBench8.0的自动安装包(仅Windows平台)。
Apache Tapestry教程:架构、设置、快速入门指南等说明书

sAbout the T utorialApache Tapestry is an open source, component based web framework written in Java. Tapestry was developed by “Howard Lewis Ship” and later open sourced and included into the Apache Foundation. It became a top-level Apache Project in 2006. Tapestry can work under any application server and easily integrate with all back ends like Spring, Hibernate, etc.This tutorial will explore the Architecture, Setup, Quick Start Guide, Tapestry Components and finally walk through with Simple Applications.AudienceThis is a tutorial for Java programmers and other people who are aspiring to make a career in Java Web Framework using Tapestry. This tutorial will give you enough understanding on creating Tapestry Web Applications.PrerequisitesBefore proceeding with this tutorial, you need to have a sound knowledge of core Java, particularly on Annotations, Basic Understanding of Web Application, Basic Client Side Programming (HTML, CSS & JavaScript) and Basic Working Knowledge of Eclipse IDE. Disclaimer & CopyrightCopyright 2016 by Tutorials Point (I) Pvt. Ltd.All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher.We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. If you discover any errors on our website or inthistutorial,******************************************.T able of ContentsAbout the Tutorial (i)Audience (i)Prerequisites (i)Disclaimer & Copyright (i)Table of Contents .................................................................................................................................... i i1.TAPESTRY ─ OVERVIEW (1)2.TAPESTRY ─ ARCHITECT URE (2)3.TAPESTRY – INSTALLATION (6)4.TAPESTRY – QUICK START (8)Run Application (10)Using Eclipse (12)5.PROJECT LAYOUT (22)6.TAPESTRY – CONVENTION OVER CONFIGURATION (26)7.TAPESTRY – ANNOTATION (27)8.TAPESTRY – PAGES AND COMPONENTS (29)9.TAPESTRY – TEMPLATES (31)Tapestry Namespace (31)Expansions (32)Elements (33)Assets (37)CSS (38)Client Side JavaScript (40)Linking JavaScript Files (40)JavaScript Stack (42)10.TAPESTRY – COMPONENTS (43)Rendering (43)Parameters (49)Component Events / Page Navigation (54)Events (55)11.TAPESTRY – BUILT-IN COMPONENTS (59)If Component (59)Unless and Delegate Component (60)Loop Component (63)PageLink Component (64)EventLink Component (65)ActionLink Component (67)Alert Component (68)12.TAPESTRY – FORMS & VALIDATIONS COMPONENTS (70)Checkbox Component (70)TextField Component (71)PasswordField Component (73)TextArea Component (74)Select Component (75)RadioGroup Component (77)Submit Component (78)Form Validation (80)13.TAPESTRY – AJAX COMPONENT (83)Zone Component (83)14.TAPESTRY – HIBERNATE (86)15.TAPESTRY – STORAGE (94)Persistence Page Data (94)Session Storage (95)16.TAPESTRY – ADVANCED FEATURES (97)Apache Tapestry5Apache Tapestry is an open source web framework written in Java. It is a component based web framework . Tapestry components are Java Classes. They are neither inherited from a framework specific base class nor implementation of an interface and they are just plain POJOs (Plain old Java Objects).The important feature of the Java used by tapestry is Annotation . Tapestry web pages are constructed by using one or more components, each having a XML based template and component class decorated with a lot of Tapestry's Annotations. Tapestry can create anything ranging from a tiny, single-page web application to a massive one consisting of hundreds of pages.Benefits of TapestrySome of the benefits provided by tapestry are:∙Highly scalable web applications. ∙Adaptive API. ∙Fast and mature framework. ∙Persistent state storage management. ∙ Build-in Inversion of Control.Features of TapestryTapestry has the following features:∙Live class reloading ∙Clear and detailed exception reporting ∙Static structure, dynamic behaviors. ∙Extensive use of Plain Old Java Objects (POJOs) ∙ Code less, deliver more.Why Tapestry?Already Java has a lot of web frameworks like JSP, Struts, etc., Then, why do we need another framework? Most of the today's Java Web Frameworks are complex and have a steep learning curve. They are old fashioned and requires compile, test and deploy cycle for every update.1.Apache Tapestry On the other hand, Tapestry provides a modern approach to web application programming by providing live class reloading. While other frameworks are introducing lots of interfaces, abstract & base classes, Tapestry just introduces a small set of annotations and still provides the ability to write large application with rich AJAX support.6Apache Tapestry7Tapestry tries to use the available features of Java as much as possible. For example, all Tapestry pages are simply POJOs. It does not enforce any custom interfaces or base class to write the application. Instead, it uses Annotation (a light weight option to extend the functionality of a Java class) to provide features. It is based on battle-tested Java Servlet API and is implemented as a Servlet Filter . It provides a new dimension to the web application and the programming is quite Simple, Flexible, Understandable and Robust. WorkflowLet us discuss the sequence of action taking place when a tapestry page is requested.2.8Step 1: The Java Servlet receives the page request. This Java Servlet is the configured in such a way that the incoming request will be forwarded to tapestry. The configuration is done in the web.xml as specified in the following program. Filter and Filter Mapping tag redirects all the request to Tapestry Filter.Step 2: The Tapestry Filter calls the HttpServletRequestHandler Service by its Service() method.Step 3: HttpServletRequestHandler stores the request and response in RequestGlobals. It also wraps the request and response as a Request and Response object and sends it to the RequestHandler.Step 4: The RequestHandler is an abstraction on top of HttpServletRequest of Servlet API. Some of the salient feature of the tapestry is done in RequestHandler section. The feature of tapestry can be extended by writing a filter in RequestHandler. RequestHandler provides several build-in filters, which include:CheckForUpdates Filter – Responsible for live class reloading. This filter checks the java classes for changes and update the application as necessary.9Apache Tapestry ∙Localization Filter – Identify the location of the user and provide localization support for the application.∙StaticFiles Filter –Identify the static request and aborts the process. Once the process is aborted, Java Servlet takes control and process the request.∙Error Filter –Catches the uncaught exception and presents the exception report page.The RequestHandler also modifies and stores the request and response in the RequestQlobalsand invokes the MasterDispatcher service.Step 5: The MasterDispatcher is responsible for rendering the page by calling several dispatchers is a specific order. The four-main dispatchers called by MasterDispatcher is as follows:∙RootPath Dispatcher – It recognizes the root path “/” of the request and render the same as Start page.∙Asset Dispatcher – It recognized the asset (Java assets) request by checking the url pattern /assets/ and sends the requested assets as byte streams.∙PageRender Dispatcher – Bulk of the tapestry operations are done in PageRender Dispatcher and the next dispatcher Component Dispatcher. This dispatcher recognizes the particular page of that request and its activation context (extra information). It then renders that particular page and sends it to the client. For example, if the request url is /product/12123434, the dispatcher will check if any class with name product/12123434 is available. If found, it calls product/12123434 class, generate the response and send it to the client. If not, it checks for product class. If found, it calls product class with extra information 121234434, generates the response and sends it to the client. This extra information is called Activation Context.If no class is found, it simply forwards the request to Component Dispatcher.∙Component Dispatcher – Component Dispatcher matches the URL of the page with the pattern –/<class_name>/<component_id>:<event_type>/<activation_context>.For example, /product/grid:sort/asc represents the product class, grid component, sortevent type and asc activation context. Here, event_type is optional and if none is provided, the default event type action will be triggered.Usually, the response of the component dispatcher is to send a redirect to the client.Mostly, the redirect will match PageRender Dispatcher in the next request and proper response will be send to the client.10Apache Tapestry11In this chapter, we will discuss how to install Tapestry on our machine.PrerequisiteTapestry's only dependency is Core Java . Tapestry is developed independently without using any third party library / framework. Even the IoC library used by tapestry is developed from the scratch. Web application written in tapestry can be built and deployed from console itself. We can use Maven , Eclipse and Jetty to improve the development experience. Maven provides quick start application templates and options to host application in Jetty, Java's de-facto development server. Eclipse provides extensive project management features and integrates well with maven.An ideal tapestry application development needs the following:∙ Java 1.6 or later ∙ Apache Maven ∙ Eclipse IDE ∙Jetty ServerVerify Maven InstallationHopefully, you have installed Maven on your machine. To verify the Maven installation, type the command given below: You could see the response as shown below:If Maven is not installed, then download and install the latest version of maven by visiting the Maven website.3.Apache TapestryDownload TapestryThe latest version of tapestry is 5.4 and can be downloaded from the Tapestry website. It is enough to download the binary package. If we use the Maven Quick Start Template, then it is not necessary to download Tapestry separately. Maven automatically downloads the necessary Tapestry Jars and configures the application. We will discuss how to create a basic Tapestry Application using Maven in the next chapter.12Apache Tapestry13After Tapestry installation, let us create a new initial project using Maven as shown below: You could see the response as shown below: After Maven building all the operations, choose archetype to create Tapestry 5 QuickStart project as follows: Choose archetype:∙ → org.apache.tapestry:quickstart (Tapestry 5 Quickstart Project)∙ → org.apache.tapestry:tapestry-archetype (Tapestry 4.1.6 Archetype)Choose a number or apply filter (format: [groupId:]artifactId, case sensitive contains): : 14.Now you will get a response like what is shown below:Extract the QuickStart version number as follows:Here, the QuickStart project takes the version for the option 5, “5.4.1”. Now, Tapestry archetype asks the following information one by one as follows:∙ 5.1 groupId: Define value for property 'groupId': : com.example∙ 5.2 artifactId: Define value for property 'artifactId': : Myapp∙ 5.3 version: Define value for property 'version': 1.0-SNAPSHOT: :∙ 5.4 package name:Define value for property 'package': com.example: : com.example.MyappNow your screen asks confirmation from you:Confirm properties configuration:∙groupId: com.example∙artifactId: Myapp∙version: 1.0-SNAPSHOT∙package: com.example.MyappVerify all the properties and confirm the changes using the option shown below:You would see the screen like the one shown below.Here, you have successfully built the Tapestry Quick Start project. Move to the location of the newly created Myapp directory with the following command and start coding.Run ApplicationTo run the skeleton project, use the following command.15You get a screen like this,As of now, we have created a basic Quick Start project in Tapestry. To view the running application in the web browser, just type the following URL in the address bar and press enter: http://localhost:8080/myappHere, myapp is the name of the application and the default port of the application in development mode is 8080.16Using EclipseIn the previous chapter, we discussed about how to create a Tapestry Quick Start application in CLI. This chapter explains about creating a skeleton application in Eclipse IDE.Let us use a Maven archetype to create skeleton application. To configure a new application, you can follow the steps given below.Step 1: Open Eclipse IDEOpen your Eclipse and choose File → New →Project… →option as shown in the following screenshot.Now, choose Maven → Maven project option.Note: If Maven is not configured then configure and create a project.After selecting the Maven project, click Next and again click the Next button.1718After that, you will get a screen where you should choose the configure option. Once it is configured, you will get the following screen.Step 2: Catalog ConfigurationAfter the first step is done, you should click on Add Remote Catalog. Then add the following changes as shown in the following screenshot.19Now, Apache Tapestry Catalog is added. Then, choose filter option org.apache.tapestry quickstart 5.4.1 as shown below.20Then click Next and the following screen will appear.21Step 3: Configure GroupId, ArtifactId, version and packageAdd the following changes to the Tapestry Catalog configuration.Then click Finish button, now we have created the first skeleton application. The first time you use Maven, project creation may take a while as Maven downloads many JAR dependencies for Maven, Jetty and Tapestry. After Maven finishes, you'll see a new directory, MyFirstApplication in your Package Explorer view.22End of ebook previewIf you liked what you saw…Buy it from our store @ https://23。
使用 tigger 编程的步骤

使用 tigger 编程的步骤
Tigger编程是一种基于Tiger语言的编程方法,Tiger语言是一种静态类型的编程语言,用于教学和研究。
使用Tigger编程的步骤可以分为以下几个方面:
1. 学习Tiger语言,首先,你需要学习Tiger语言的语法、语义和基本特性。
Tiger语言是一种类似Pascal和C语言的静态类型语言,因此熟悉这些语言的人可能会更容易学习Tiger语言。
2. 理解Tigger编程范例,了解Tigger编程的范例和示例,可以帮助你更好地理解如何使用Tiger语言进行编程。
这些范例可以包括简单的算法实现、数据结构定义等。
3. 编写Tigger程序,根据你的需求和目标,开始编写Tigger 程序。
这可能涉及到设计算法、定义数据结构、实现函数等。
4. 调试和测试,在编写Tigger程序的过程中,你需要进行调试和测试,以确保程序的正确性和稳定性。
这可能涉及到使用调试工具、编写测试用例等。
5. 优化和改进,一旦你的Tigger程序能够正常运行,你可能需要对程序进行优化和改进,以提高性能和可维护性。
总的来说,使用Tigger编程的步骤包括学习Tiger语言、理解Tigger编程范例、编写Tigger程序、调试和测试、以及优化和改进。
通过这些步骤,你可以更好地掌握Tiger语言和Tigger编程方法,从而实现你的编程目标。
今天开始学习SSH框架:StrutsSpringHibernate练习(完整)

今天开始学习SSH框架:StrutsSpringHibernate练习(完整)Struts+Spring+Hibernate练习(完整)工具:Eclipse3.1、MyEclipse4.03、Tomcat5.5.9、Properties Editor 插件、MySql4.1.13新建工程:名称为 login创建Struts框架创建 index.jsp,增加一链接指向 login.jsp按下Ctrl + N,创建login.jsp、LoginAction,使用MyEclipse 的向导就可以了,记得选对正确的版本在ActionForm配置页中选择类型为动态Form,并继承于DynaValidatorForm,新增两个属性:username、password,在创建jsp文件打上钩,将路径改为/login.jsp,然后下一步,改LoginAction的Input source改为/login.jsp,点击完成按下Ctrl + N 创建一个forwards,记得选对正确的版本name 输入 indexGo路径选择 /index.jsp配置validator先添加Struts插件,使用向导Plugin class : org.apache.struts.validator.ValidatorPlugInProperty : pathnamesValue : /WEB-INF/validator-rules.xml,/WEB-INF/validation.xml这里需要两个xml文件现在创建“validation.xml”文件在这里说明一点,我使用MyEclipse创建的Struts框架中缺少了validator-rules.xml文件,需要动拷贝到WEB-INF目录中此文件可以到下载文件内容如下:<form-validation><formset><form name="loginForm"><field property="username" depends="required"><arg0 key="ername" /></field><field property="password" depends="required"><arg0 key="prompt.password" /></field></form></formset></form-validation>编辑资源文件“ApplicationResources.properties”增加以下内容ername=User Nameprompt.password=User Passworderrors.required={0} is required.再创建中文件资源文件“ApplicationResources_zh_CN.properties”增加以下内容ername=用户名称prompt.password=登录密码errors.required={0} 必需填写!修改struts-config.xml文件在以下位置增加绿色字体部份<action-mappings ><actionattribute="loginForm"input="/login.jsp"name="loginForm"path="/login"scope="request"validate="true"type="com.test.struts.action.LoginAction" /></action-mappings>这里说明提交的数据必需经过验证,而验证则是通过validator框架进行的。
Eclipse开发环境配置-indigo

开发环境配置1、java环境安装本系统使用java7开发,版本如下:配置安装后需要配置环境变量,如下所示:配置classpath,如下:并在path中添加java7安装目录中的bin目录路径,如下所示:检验是否安装成功,cmd进入命令行模式,输入java,出现如下画面表示安装java完成:2、web容器安装本系统开发环境使用tomcat6及以上版本,“开发工具”目录提供了apache—tomcat-7.0。
53.zip。
解压安装包到自己的电脑上,建议不要解压到中文目录下,老师的tomcat7放在了E盘根目录E:\apache-tomcat-7.0。
53.配置网上有些安装教程提到需要配置CATALINA_HOME环境变量,此变量指向了tomcat 的目录,主要是为了方便tomcat运行使用,如果配置了,你的电脑上有多个tomcat目录时只能成功运行那个和CATALINA_HOME一致的tomcat,如果不配置,在你启动tomcat时它会自己确定tomcat目录,这里我们就不配置了。
运行运行tomcat目录中的bin/startup。
bat,启动tomcat,如果启动不起来就到logs查看错误日志,启动后有浏览器输入http://localhost:8080/,进入如下画面表示tomcat安装成功。
3、eclipse环境eclipse安装本系统开发使用eclipse—indigo进行开发,在“开发工具”目录中有eclipse—3。
7-indigo 32位.zip安装包。
解压安装包到固定位置,建议不要解压到中文目录,运行:eclipse。
exe,初次运行会让你确定自己的工作区,工作区是你创建project工程的地方,选择一个容易操作到的目录作为你的工作区,建议工作区目录不要设在中文目录中.Eclipse插件安装:将“开发工具”目录的“eclipse-plugins"目录拷贝到自己的电脑上,“eclipse—plugins”目录中包括了三个插件,另将此目录的txt文件拷贝到eclipse目录中dropins目录下,并对每个txt文件中的路径修改正确,指定插件文件夹位置。
techsure devops platform使用流程

TechSure DevOps平台是一种工具链和体系方法,旨在优化开发工作和运行维护工作。
它基于人(People)、流程(Process)和平台(Platform)这三大支柱构建,即DevOps = 人+ 流程+ 平台。
以下是使用TechSure DevOps平台的基本流程:
1. 持续集成和持续交付:开发人员频繁地将代码集成到共享的代码库中,以便进行自动构建和运行测试。
持续交付则通过自动化构建、测试和部署流程,确保软件在任何时候都可以进行交付,从而提高交付速度。
2. 自动化测试:在代码合并到主干之前,自动运行测试套件以确保代码质量。
3. 自动化部署:一旦代码通过测试,就可以自动部署到生产环境。
4. 自动化监控:在生产过程中,监控系统的性能和健康状况,确保应用程序的稳定性。
5. 自动化回滚:如果新版本的应用程序出现问题,可以自动回滚到之前的版本。
GoogleC++单元测试框架(Gtest)系列教程之一——入门

Google C++单元测试框架
Google C++单元测试框架(简称Gtest),可在多个平台上使用(包括Linux, Mac OS X, Windows, Cygwin和Symbian),它提供了丰富的 断言、致命和非致命失败判断,能进行值参数化测试、类型参数化测试、“死亡测试”。Gtest是一个开源的项目,其源码可以从这里下载,目 前的代码发行版是1.6.0。
970 child_pid = clone(&ExecDeathTestChildMain, stack_top, SIGCHLD, &args);
改成:
970 child_pid = fork();
使用make编译过后并不需要执行make install命令安装Gtest相关的,对自己的测试代码进行编译时,从当前目录引用头文件和库文件即可。 执行用例 源码文件的samples目录下为我们提供了多个用例,从sample1到sample9,Gtest作者由浅入深为我们讲解了Gtest的用法,怎么执行这些用 例呢? 首先进入源码目录下的make目录,其中包含了一个Makefile文件,执行make命令,make命令执行过后可以看到该目录下增加了几个文件, 其中sample1_unittest就是sample1的可执行文件了。执行./sample1_unittest即可看到测试的运行结果:
为编译生成其他用例的可执行文件,我们可以参照make目录下的Makefile文件,或者执行以下步骤: 将gtest-main.a动态库文件拷贝到samples目录下,执行以下命令:
$ g++ -I ../include/ -c sample2_
JG-RP-216RoHS部品应急准备和响应控制程序

污染应急准备和响应报告书》。 5.4 突发污染事故处理完后,事故发生所在部门负责人,应召集相关人员研究防止事故再次
发生的对策。 5.5 检查和教育
5.5.1 各应急重点场所工作认真,在工作开始前和完成后,均应进行 A.日常污染源/污染物检查 B.各部门定期组织有关人员进行集中污染源检查。
5.5.2 教育 A.对应急重点场所工作人员,应进行岗位教育。 B.出现突发污染事故时,应急处理措施教育培训。 C.由行政部组织相关人员每年一次进行应急突发污染事件响应培训练习,并以文字 或照片记录本公司的练习,行政部负责。
1.0 目的:
RoHS 管理体系文件
RoHS 部品应急准备和响应 控制程序
编 号 NO.: JG-RP-216 版 本 Rev.: A0 生效日期 Date: 2006-7-12 页 码 Page: 3 of 6
为了确定应急情况并采取应急措施,在发生紧急情况后作出响应,减少绿色部品对 ROHS
符合性造成的影响,特制定本程序文件。
编 号 NO.: JG-RP-216 版 本 Rev.: A0 生效日期 Date: 2006-7-12 页 码 Page: 5 of 6
6.0 引用文件:无 7.0 相关记录:
7.1《突发污染应急准备和响应报告书》 8.0 附件:
《突发污染应急准备和响应流程图》
JG-RP-41601
****本文件及其内容为本公司之财产,未经授权不得复制*****夜间Fra bibliotek发现人
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
tigase开发指南
tigase组件插件配置
tigase启动时会初始化并启动相关组件和插件,启动的组件或开通监听端口号或访问数据库或者创建线程池,默认有些组件和插件非必须,我们也用不到,为了避免资源浪费,需要在配置中注释这些组件。
组件如下表格所示,红字的组件说明:
配置文件配置启动组件:
修改init.properties
插件如下表格所示,红字的插件说明:
配置文件配置启动组件:修改init.properties
Tigase数据库表
Tigase用户信息、权限信息、离线消息信息、在线离线状态信息都存储在数据库中,但有些数据我们不需要让tigagse存储、更新,比如在线离线状态信息,如果每个用户登录、登出都让tigase更新表的字段,并发高了,显然数据库承受不了。
为了避免资源浪费也需要避免这些操作。
登录状态上线更新
上线状态更新是在验证用户名和密码时更新,验证功能是需要我们自定义的,仅需修改tigase验证模块的一小块代码即可。
下图贴出tigase源码修改方式。
登录状态下线更新
下线状态更新是在用户退出、连接断开等时更新,修改代码也比较简单。
tigase 权限验证
云果登陆流程时需要验证权限,权限验证需要分匿名用户和企业客服两种,匿名用户默认验证都可以通过,企业客服需要验证是否在用户中心登陆成功。
企业客服登陆
1.登陆用户中心,登陆成功后,用户中心会保存cookieid至缓存中
2.带着用户名、cookieid同tigase服务端建立连接
3.从缓存中获取验证信息
4.如果认证通过和tigase连接上
tigase的验证是需要我们自定义开发的,只需要在tigase权限验证模块修改即可。
tigase 在线坐席获取
匿名用户登陆需要根据客户名分配一个在线坐席会话。
tigase roster插件是用于返回好友列表,可以修改用来分配坐席列表。
插件的调用是在SessionManager中调用:
客户端获取好友列表:
tigase消息转发流程
用户在发消息给客服时,如果客服不在线,需要分配给机器人客服,机器人客服是以tigase客户端方式使用的,并且为了负载均衡会有多个机器人客服,所以还需要分配。
分配这块功能需要修改tigase sessionmanage组件处理消息模块的一段代码。
Tigase所有的消息都会经sessionmanager 进行处理。
Packet类中没有setStanzaTo方法需要修改加入
tigase离线消息存储
tigase在用户不在线时,会把消息存储在数据库中,默认是关系型数据库,这块我们是需要存储到hbase等nosql数据库中的,这块功能需要修改下源码tigase已经写好的离线消息插件。
此外tigase默认的离线消息存储是有条数限制的,需要修改配置文件
tigase用户连接断开通知客服
client与server连接断开,SessionManager会接收到断开消息,会话断开是通过SessionCloseProc插件实现。
断开通知客服需要在连接断开时,发一条消息给客服JID通知。
Packet类中没有setStanzaTo方法需要修改加入
tigase组件插件开发
tigase组件插件开发,官方开发文档有详细介绍,可直接阅读《tigase-DevelopmentGuide.pd》,已上传上传到svn。
云果以后需要自定义一些组件、插件实现自定义功能。
tigase配置文件
云果基于tigase源码开发功能时,需要增加一些自定义的配置,关于配置文件模块,tigase是作为一个组件开发的,所以我们仅需要简单修改一下配置文件模块。
tigase ssl
SSL(Secure Sockets Layer 安全套接层),及其继任者传输层安全(Transport Layer Security,TLS)是为网络通信提供安全及数据完整性的一种安全协议。
TLS与SSL在传输层对网络连接进行加密。
Tigase 支持ssl通信功能,底层使用NIO+JSSE实现。
1.启用ssl
修改init.properties,增加配置
注:5280端口号用于正常通信,5281端口号用于ssl通信
2.js连接tigase ssl
由原来的访问地址http://ip:5280 改为https://ip:5281即可正常访问。
注:由于https请求浏览器需要可信证书才允许访问,否则会拒绝访问,需要把访问的https地址设置为可信才能访问或者加入可信证书。
导入pem文件至浏览器下面3会介绍。
3.ssl证书
tigase发布的包解压后,在certs/目录中包含了密钥和证书,其中后缀名位.pem是ssl钥匙包含了公钥和私钥匙,tigase启动时会为每个domain生成一个domain.pem文件,如果不配置domain使用default.pem文件。
pem文件也可以使用openssl生成,上线系统建议自己生成。
pem文件可以导入至浏览器证书中,这样浏览器才不会禁止你的https请求。
证书如下所示:
注:上线系统外网使用ssl一般采用第三方的收费的商用证书,客户端导入证书非常shan麻烦,浏览器内部会有一些CA ROOT证书,一般包含了常用的商用证书。
tigase 负载均衡
Tigase从5.2.0版开始,引入了负载均衡功能,可以把终端访问用户重定向到最适合的集群节点上。
此负载均衡功能依赖于see-other-host的XMPP流错误消息(stream error message)。
此机制背后的基本原则是如果用户当前正尝试连接的节点与返回消息的节点不是集群中的同一个节点,那么用户将被重定向。
此原则需要获得用户的JID实现重定向。
一、可用的实现
此Tigase的实现跟其他实现一样,是可扩展的,支持不同的、可插拨的重定向策略,实现了SeeOtherHostIfc接口。
当前有三种可用的策略:
1)SeeOtherHost策略
此策略是最基本的实现,它会返回init.properties配置文件中的单个主机名或当前的主机名。
2)SeeOtherHostHashed策略
这是Tigase默认使用的策略,它对用户的JID值的进行哈希计算,根据哈希值来把终端连接重定向到SeeOtherHostIfc的集群环境中的节点。
所有有效的节点是根据默认的集群组成和所有连接到集群并工作的节点共同决定,也可以把所有的节点配置到init.properties中。
3)SeeOtherHostDB策略
此策略是SeeOtherHost策略的扩展实现,它根据Tigase数据库的user_id和node_id配对的形式来决定终端用户应该被重定向到哪一个节点。
二、配置选项
下面是实际的负载均衡重定向最基本的相关配置:
–cm-see-other-host=
它可能的值包括:
tigase.server.xmppclient.SeeOtherHost
tigase.server.xmppclient.SeeOtherHostHashed
tigase.server.xmppclient.SeeOtherHostDB
none - disables redirection
说明:前三行为三种重定向策略,最后一种是不使用重定向策略。
其余的所有选项都是以连接管理器per-connection-manager为基础进行配置的,因此这些选项都需要加上相应的连接管理器ID作为前缀,比如c2s、bosh、ws的配置,下面以c2s配置为例:
c2s/cm-see-other-host/default-host=host1;host2;host3
用分号来间隔重定向的主机节点名
c2s/cm-see-other-host/active=OPEN;LOGIN
用分号来间隔终端用户可以被重定向的阶段
当前可使用的值包括:
OPEN 它表示打开XMPP stream期间可以进行重定向
LOGIN 它表示在授权认证用户会话期间可以进行重定向
Tigase默认的重定向阶段是OPEN阶段。
SeeOtherHostDB策略附加的选项包括:
c2s/cm-see-other-host/db-url
JDBC连接的URI,用于查询重定向信息;如果没有配置,那么会使用–user-db-uri的值。
c2s/cm-see-other-host/get-host-query
SQL查询语句,它应该能返回重定向的主机名。
c2s/cm-see-other-host/get-all-data-query
SQL辅助器查询语句,它能够返回来自数据库所有的重定向数据。
c2s/cm-see-other-host/get-all-query-timeout
设置执行查询的超时时间。
注:tigase默认的负载均衡实现比较简单,负载的方式是客服端向任意服务端请求,服务端内部通过一些负载方式,分配一台服务端,然后把分配这台服务器连接信息返回给客户端,客户端在连接
分配的这台服务端,使得客户端多了个一个步骤。
建议使用LVS负载均衡器实现负载功能。
