Modelling routing in wireless ad hoc networks with dynamic Bayesian games
InHand ER605 5G 边缘路由器 用户手册说明书

IInHand ER6055G 边缘路由器用户手册资料版本:V1.0—2023.09首先非常感谢您选择本公司产品!在使用前,请您仔细阅读本用户手册。
非本公司书面许可,任何单位和个人不得擅自摘抄、复制本书内容的部分或全部,并不得以任何形式传播。
由于不断更新,本公司不能承诺本资料与实际产品一致,同时也不承担由于实际技术参数与本资料不符所导致的任何争议,任何改动恕不提前通知。
本公司保留最终更改权和解释权。
版权所有©2023北京映翰通网络技术股份有限公司及其许可者版权所有,保留一切权利。
本手册图形界面约定1简介 (1)2硬件部分 (2)指示灯说明 (2)通过Reset按钮恢复出厂 (3)3默认配置 (4)4路由器快速联网 (5)环境准备 (5)设备联网 (6)有线接入网络 (6)蜂窝接入网络 (8)Wi-Fi(STA)接入网络 (10)5仪表盘 (11)设备信息 (11)接口状态 (11)流量统计 (12)Wi-Fi连接数 (12)客户端流量Top5 (13)6状态 (14)链路监控 (14)蜂窝信号 (14)客户端 (15)VPN (15)事件 (15)上行链路表 (18)上行链路设置 (18)8本地网络 (20)9Wi-Fi (21)10VPN (22)IPSec VPN (22)L2TP VPN (24)客户端 (24)服务器 (25)VXLAN VPN (25)11安全 (27)防火墙 (27)入站规则/出站规则 (27)端口转发 (28)MAC地址过滤 (29)策略路由 (29)12服务 (31)接口管理 (31)DHCP Server (31)DNS Server (32)固定地址列表 (32)静态路由 (32)Dynamic DNS (33)adm管理 (35)云管理 (35)远程访问控制 (36)时钟 (37)设备选项 (37)配置管理 (38)设备告警 (38)工具 (39)Ping (39)Traceroute (40)抓包 (40)日志服务器 (41)其他设置 (41)Web登陆管理 (41)设备自动重启 (42)SIP ALG (42)Edge Router605是北京映翰通面向商业联网领域推出的新一代5G边缘路由器产品,该产品为各行业提供高速安全的网络接入。
计算机科学ESI期刊汇总

期刊全称期刊简称Acm Computing Surveys ACM COMPUT SURV Acm Journal On Emerging Technologies in Computing Systems ACM J EMERG TECH COM Acm Sigcomm Computer Communication Review ACM SIGCOMM COMP COMAcm Sigplan Notices ACM SIGPLAN NOTICES Acm Transactions On Algorithms ACM T ALGORITHMS Acm Transactions On Applied Perception ACM T APPL PERCEPT Acm Transactions On Architecture and Code Optimization ACM T ARCHIT CODE OPAcm Transactions On Autonomous and Adaptive Systems ACM T AUTON ADAP SYS Acm Transactions On Computational Logic ACM T COMPUT LOGAcm Transactions On Computer Systems ACM T COMPUT SYST Acm Transactions On Computer-Human Interaction ACM T COMPUT-HUM INT Acm Transactions On Database Systems ACM T DATABASE SYST Acm Transactions On Design Automation of Electronic Systems ACM T DES AUTOMAT EL Acm Transactions On Embedded Computing Systems ACM T EMBED COMPUT S Acm Transactions On Graphics ACM T GRAPHIC Acm Transactions On Information and System Security ACM T INFORM SYST SE Acm Transactions On Information Systems ACM T INFORM SYST Acm Transactions On Intelligent Systems and Technology ACM T INTEL SYST TEC Acm Transactions On Internet Technology ACM T INTERNET TECHN Acm Transactions On Knowledge Discovery From Data ACM T KNOWL DISCOV D Acm Transactions On Mathematical Software ACM T MATH SOFTWARE Acm Transactions On Modeling and Computer Simulation ACM T MODEL COMPUT S Acm Transactions On Multimedia Computing Communications and Applications ACM T MULTIM COMPUT Acm Transactions On Programming Languages and Systems ACM T PROGR LANG SYS Acm Transactions On Reconfigurable Technology and Systems ACM T RECONFIG TECHN Acm Transactions On Sensor Networks ACM T SENSOR NETWORK Acm Transactions On Software Engineering and Methodology ACM T SOFTW ENG METH Acm Transactions On Storage ACM T STORAGEAcm Transactions On the Web ACM T WEBActa Informatica ACTA INFORMAd Hoc & Sensor Wireless Networks AD HOC SENS WIREL NEAd Hoc Networks AD HOC NETWAdvances in Computers ADV COMPUTAdvances in Engineering Software ADV ENG SOFTW Aeu-International Journal of Electronics and Communications AEU-INT J ELECTRON C Annals of Telecommunications-Annales Des Telecommunications ANN TELECOMMUNApplied Clinical Informatics APPL CLIN INFORMApplied Ontology APPL ONTOLApplied Soft Computing APPL SOFT COMPUTArtificial Intelligence ARTIF INTELLArtificial Intelligence Review ARTIF INTELL REVArtificial Life ARTIF LIFEAutomated Software Engineering AUTOMAT SOFTW ENG Autonomous Agents and Multi-Agent Systems AUTON AGENT MULTI-AG Bell Labs Technical Journal BELL LABS TECH JBioinformatics BIOINFORMATICSBmc Bioinformatics BMC BIOINFORMATICSBriefings in Bioinformatics BRIEF BIOINFORM Business & Information Systems Engineering BUS INFORM SYST ENG+China Communications CHINA COMMUN Cluster Computing-the Journal of Networks Software Tools and Applications CLUSTER COMPUT Cmc-Computers Materials & Continua CMC-COMPUT MATER CONCmes-Computer Modeling in Engineering & Sciences CMES-COMP MODEL ENGCognitive Computation COGN COMPUTCognitive Systems Research COGN SYST RESCommunications of the Acm COMMUN ACMComputational Biology and Chemistry COMPUT BIOL CHEMComputational Geosciences COMPUTAT GEOSCIComputational Linguistics COMPUT LINGUISTComputer COMPUTERComputer Aided Geometric Design COMPUT AIDED GEOM D Computer Animation and Virtual Worlds COMPUT ANIMAT VIRT W Computer Applications in Engineering Education COMPUT APPL ENG EDUCComputer Communications COMPUT COMMUNComputer Graphics Forum COMPUT GRAPH FORUMComputer Journal COMPUT JComputer Languages Systems & Structures COMPUT LANG SYST STR Computer Methods and Programs in Biomedicine COMPUT METH PROG BIO Computer Methods in Applied Mechanics and Engineering COMPUT METHOD APPL M Computer Methods in Biomechanics and Biomedical Engineering COMPUT METHOD BIOMECComputer Music Journal COMPUT MUSIC JComputer Networks COMPUT NETW Computer Science and Information Systems COMPUT SCI INF SYSTComputer Speech and Language COMPUT SPEECH LANGComputer Standards & Interfaces COMPUT STAND INTER Computer Supported Cooperative Work-the Journal of Collaborative Computing COMPUT SUPP COOP W J Computer Systems Science and Engineering COMPUT SYST SCI ENGComputer Vision and Image Understanding COMPUT VIS IMAGE UNDComputer-Aided Design COMPUT AIDED DESIGN Computers & Chemical Engineering COMPUT CHEM ENGComputers & Education COMPUT EDUCComputers & Electrical Engineering COMPUT ELECTR ENGComputers & Fluids COMPUT FLUIDSComputers & Geosciences COMPUT GEOSCI-UKComputers & Graphics-Uk COMPUT GRAPH-UKComputers & Industrial Engineering COMPUT IND ENGComputers & Operations Research COMPUT OPER RESComputers & Security COMPUT SECURComputers & Structures COMPUT STRUCTComputers and Concrete COMPUT CONCRETE Computers and Electronics in Agriculture COMPUT ELECTRON AGRComputers and Geotechnics COMPUT GEOTECHComputers in Biology and Medicine COMPUT BIOL MEDComputers in Industry COMPUT INDComputing COMPUTINGComputing and Informatics COMPUT INFORMComputing in Science & Engineering COMPUT SCI ENG Concurrency and Computation-Practice & Experience CONCURR COMP-PRACT EConnection Science CONNECT SCIConstraints CONSTRAINTS Cryptography and Communications-Discrete-Structures Boolean Functions and Sequences CRYPTOGR COMMUNCryptologia CRYPTOLOGIACurrent Bioinformatics CURR BIOINFORMData & Knowledge Engineering DATA KNOWL ENG Data Mining and Knowledge Discovery DATA MIN KNOWL DISCDecision Support Systems DECIS SUPPORT SYST Design Automation For Embedded Systems DES AUTOM EMBED SYST Designs Codes and Cryptography DESIGN CODE CRYPTOGRDigital Investigation DIGIT INVESTDisplays DISPLAYSDistributed and Parallel Databases DISTRIB PARALLEL DATDistributed Computing DISTRIB COMPUTEmpirical Software Engineering EMPIR SOFTW ENGEngineering With Computers ENG COMPUT-GERMANYEnterprise Information Systems ENTERP INF SYST-UK Environmental Modelling & Software ENVIRON MODELL SOFTWEtri Journal ETRI J Eurasip Journal On Wireless Communications and Networking EURASIP J WIREL COMM European Journal of Information Systems EUR J INFORM SYSTEvolutionary Bioinformatics EVOL BIOINFORMEvolutionary Computation EVOL COMPUTExpert Systems EXPERT SYSTFormal Aspects of Computing FORM ASP COMPUTFormal Methods in System Design FORM METHOD SYST DES Foundations and Trends in Information Retrieval FOUND TRENDS INF RETFrontiers in Neurorobotics FRONT NEUROROBOTICSFrontiers of Computer Science FRONT COMPUT SCI-CHI Frontiers of Information Technology & Electronic Engineering FRONT INFORM TECH ELFundamenta Informaticae FUND INFORMture Generation Computer Systems-the International Journal of Grid Computing and EscienFUTURE GENER COMP SY Genetic Programming and Evolvable Machines GENET PROGRAM EVOL MGraphical Models GRAPH MODELSHuman-Computer Interaction HUM-COMPUT INTERACT Ibm Journal of Research and Development IBM J RES DEVIcga Journal ICGA JIeee Annals of the History of Computing IEEE ANN HIST COMPUTIeee Communications Letters IEEE COMMUN LETTIeee Communications Magazine IEEE COMMUN MAG Ieee Communications Surveys and Tutorials IEEE COMMUN SURV TUTIeee Computational Intelligence Magazine IEEE COMPUT INTELL M Ieee Computer Architecture Letters IEEE COMPUT ARCHIT L Ieee Computer Graphics and Applications IEEE COMPUT GRAPHIeee Design & Test IEEE DES TESTIeee Internet Computing IEEE INTERNET COMPUT Ieee Journal of Biomedical and Health Informatics IEEE J BIOMED HEALTHIeee Journal On Selected Areas in Communications IEEE J SEL AREA COMMIeee Micro IEEE MICROIeee Multimedia IEEE MULTIMEDIAIeee Network IEEE NETWORKIeee Pervasive Computing IEEE PERVAS COMPUTIeee Security & Privacy IEEE SECUR PRIVIeee Software IEEE SOFTWAREIeee Systems Journal IEEE SYST JIeee Transactions On Affective Computing IEEE T AFFECT COMPUT Ieee Transactions On Autonomous Mental Development IEEE T AUTON MENT DE Ieee Transactions On Broadcasting IEEE T BROADCASTIeee Transactions On Communications IEEE T COMMUN Ieee Transactions On Computational Intelligence and Ai in Games IEEE T COMP INTEL AIIeee Transactions On Computers IEEE T COMPUTIeee Transactions On Cybernetics IEEE T CYBERNETICS Ieee Transactions On Dependable and Secure Computing IEEE T DEPEND SECURE Ieee Transactions On Evolutionary Computation IEEE T EVOLUT COMPUT Ieee Transactions On Haptics IEEE T HAPTICS Ieee Transactions On Information Forensics and Security IEEE T INF FOREN SEC Ieee Transactions On Information Theory IEEE T INFORM THEORYIeee Transactions On Learning Technologies IEEE T LEARN TECHNOLIeee Transactions On Mobile Computing IEEE T MOBILE COMPUT Ieee Transactions On Multimedia IEEE T MULTIMEDIA Ieee Transactions On Neural Networks and Learning Systems IEEE T NEUR NET LEAR Ieee Transactions On Parallel and Distributed Systems IEEE T PARALL DISTR Ieee Transactions On Services Computing IEEE T SERV COMPUTIeee Transactions On Software Engineering IEEE T SOFTWARE ENG Ieee Transactions On Visualization and Computer Graphics IEEE T VIS COMPUT GR Ieee Transactions On Wireless Communications IEEE T WIREL COMMUN Ieee Wireless Communications IEEE WIREL COMMUN Ieee-Acm Transactions On Computational Biology and Bioinformatics IEEE ACM T COMPUT BI Ieee-Acm Transactions On Networking IEEE ACM T NETWORKIeice Transactions On Communications IEICE T COMMUN Ieice Transactions On Information and Systems IEICE T INF SYSTIet Biometrics IET BIOMETRICSIet Computer Vision IET COMPUT VIS Iet Computers and Digital Techniques IET COMPUT DIGIT TEC Iet Information Security IET INFORM SECUR Iet Radar Sonar and Navigation IET RADAR SONAR NAVIet Software IET SOFTWInformatica INFORMATICA-LITHUAN Information and Computation INFORM COMPUT Information and Software Technology INFORM SOFTWARE TECH Information Fusion INFORM FUSION Information Processing Letters INFORM PROCESS LETT Information Retrieval INFORM RETRIEVALInformation Sciences INFORM SCIENCESInformation Systems INFORM SYSTInformation Systems Frontiers INFORM SYST FRONTInformation Systems Management INFORM SYST MANAGEInformation Technology and Control INF TECHNOL CONTROL Information Visualization INFORM VISUAL Informs Journal On Computing INFORMS J COMPUT Integrated Computer-Aided Engineering INTEGR COMPUT-AID E Integration-the Vlsi Journal INTEGRATIONIntelligent Data Analysis INTELL DATA ANALInteracting With Computers INTERACT COMPUT International Arab Journal of Information Technology INT ARAB J INF TECHN International Journal For Numerical Methods in Biomedical Engineering INT J NUMER METH BIO International Journal of Ad Hoc and Ubiquitous Computing INT J AD HOC UBIQ CO International Journal of Approximate Reasoning INT J APPROX REASONInternational Journal of Bio-Inspired Computation INT J BIO-INSPIR COM International Journal of Computational Intelligence Systems INT J COMPUT INT SYS International Journal of Computer Networks and Communications INT J COMPUT NETW CO International Journal of Computers Communications & Control INT J COMPUT COMMUN International Journal of Cooperative Information Systems INT J COOP INF SYSTInternational Journal of Data Mining and Bioinformatics INT J DATA MIN BIOINInternational Journal of Data Warehousing and Mining INT J DATA WAREHOUSInternational Journal of Distributed Sensor Networks INT J DISTRIB SENS NInternational Journal of Foundations of Computer Science INT J FOUND COMPUT S International Journal of General Systems INT J GEN SYST International Journal of High Performance Computing Applications INT J HIGH PERFORM C International Journal of Information Security INT J INF SECUR International Journal of Information Technology & Decision Making INT J INF TECH DECIS International Journal of Machine Learning and Cybernetics INT J MACH LEARN CYB International Journal of Network Management INT J NETW MANAG International Journal of Neural Systems INT J NEURAL SYST International Journal of Parallel Programming INT J PARALLEL PROG International Journal of Pattern Recognition and Artificial Intelligence INT J PATTERN RECOGN International Journal of Satellite Communications and Networking INT J SATELL COMM N International Journal of Sensor Networks INT J SENS NETW International Journal of Software Engineering and Knowledge Engineering INT J SOFTW ENG KNOW International Journal of Uncertainty Fuzziness and Knowledge-Based Systems INT J UNCERTAIN FUZZ International Journal of Unconventional Computing INT J UNCONV COMPUT International Journal of Wavelets Multiresolution and Information Processing INT J WAVELETS MULTI International Journal of Web and Grid Services INT J WEB GRID SERVInternational Journal of Web Services Research INT J WEB SERV RESInternational Journal On Artificial Intelligence Tools INT J ARTIF INTELL T International Journal On Document Analysis and Recognition INT J DOC ANAL RECOG International Journal On Semantic Web and Information Systems INT J SEMANT WEB INFInternet Research INTERNET RESIt Professional IT PROF Journal of Ambient Intelligence and Humanized Computing J AMB INTEL HUM COMP Journal of Ambient Intelligence and Smart Environments J AMB INTEL SMART EN Journal of Applied Logic J APPL LOGIC Journal of Artificial Intelligence Research J ARTIF INTELL RES Journal of Automated Reasoning J AUTOM REASONING Journal of Bioinformatics and Computational Biology J BIOINF COMPUT BIOL Journal of Biomedical Informatics J BIOMED INFORMJournal of Cellular Automata J CELL AUTOMJournal of Cheminformatics J CHEMINFORMATICS Journal of Communications and Networks J COMMUN NETW-S KOR Journal of Communications Technology and Electronics J COMMUN TECHNOL EL+Journal of Computational Analysis and Applications J COMPUT ANAL APPL Journal of Computational Science J COMPUT SCI-NETH Journal of Computer and System Sciences J COMPUT SYST SCI Journal of Computer and Systems Sciences International J COMPUT SYS SC INT+ Journal of Computer Information Systems J COMPUT INFORM SYSTJournal of Computer Science and Technology J COMPUT SCI TECH-CHJournal of Computers J COMPUTJournal of Cryptology J CRYPTOLJournal of Database Management J DATABASE MANAGE Journal of Experimental & Theoretical Artificial Intelligence J EXP THEOR ARTIF IN Journal of Functional Programming J FUNCT PROGRAMJournal of Grid Computing J GRID COMPUTJournal of Heuristics J HEURISTICS Journal of Information Science and Engineering J INF SCI ENGJournal of Information Technology J INF TECHNOLJournal of Intelligent & Fuzzy Systems J INTELL FUZZY SYSTJournal of Intelligent Information Systems J INTELL INF SYST Journal of Internet Technology J INTERNET TECHNOLJournal of Logic and Computation J LOGIC COMPUT Journal of Logical and Algebraic Methods in Programming J LOG ALGEBR METHODS Journal of Machine Learning Research J MACH LEARN RES Journal of Management Information Systems J MANAGE INFORM SYSTJournal of Mathematical Imaging and Vision J MATH IMAGING VISJournal of Molecular Graphics & Modelling J MOL GRAPH MODEL Journal of Multiple-Valued Logic and Soft Computing J MULT-VALUED LOG S Journal of Network and Computer Applications J NETW COMPUT APPLJournal of Network and Systems Management J NETW SYST MANAG Journal of New Music Research J NEW MUSIC RES Journal of Next Generation Information Technology J NEXT GENER INF TEC Journal of Optical Communications and Networking J OPT COMMUN NETW Journal of Organizational and End User Computing J ORGAN END USER COM Journal of Organizational Computing and Electronic Commerce J ORG COMP ELECT COM Journal of Parallel and Distributed Computing J PARALLEL DISTR COM Journal of Real-Time Image Processing J REAL-TIME IMAGE PR Journal of Research and Practice in Information Technology J RES PRACT INF TECH Journal of Software-Evolution and Process J SOFTW-EVOL PROC Journal of Statistical Software J STAT SOFTW Journal of Strategic Information Systems J STRATEGIC INF SYST Journal of Supercomputing J SUPERCOMPUT Journal of Systems and Software J SYST SOFTWAREJournal of Systems Architecture J SYST ARCHITECTJournal of the Acm J ACM Journal of the Association For Information Systems J ASSOC INF SYST Journal of the Institute of Telecommunications Professionals J I TELECOMMUN PROF Journal of Universal Computer Science J UNIVERS COMPUT SCI Journal of Visual Communication and Image Representation J VIS COMMUN IMAGE R Journal of Visual Languages and Computing J VISUAL LANG COMPUT Journal of Visualization J VISUAL-JAPANJournal of Web Engineering J WEB ENGJournal of Web Semantics J WEB SEMANT Journal of Zhejiang University-Science C-Computers & Electronics J ZHEJIANG U-SCI C Journal On Multimodal User Interfaces J MULTIMODAL USER INKnowledge and Information Systems KNOWL INF SYSTKnowledge Engineering Review KNOWL ENG REVKnowledge-Based Systems KNOWL-BASED SYST Ksii Transactions On Internet and Information Systems KSII T INTERNET INF Language Resources and Evaluation LANG RESOUR EVALLogical Methods in Computer Science LOG METH COMPUT SCIMalaysian Journal of Computer Science MALAYS J COMPUT SCI Mathematical and Computer Modelling of Dynamical Systems MATH COMP MODEL DYN Mathematical Modelling of Natural Phenomena MATH MODEL NAT PHENO Mathematical Programming MATH PROGRAM Mathematical Structures in Computer Science MATH STRUCT COMP SCI Medical Image Analysis MED IMAGE ANALMemetic Computing MEMET COMPUT Microprocessors and Microsystems MICROPROCESS MICROSY Minds and Machines MIND MACHMobile Information Systems MOB INF SYSTMobile Networks & Applications MOBILE NETW APPLMultidimensional Systems and Signal Processing MULTIDIM SYST SIGN PMultimedia Systems MULTIMEDIA SYST Multimedia Tools and Applications MULTIMED TOOLS APPLNatural Computing NAT COMPUTNetworks NETWORKSNeural Computation NEURAL COMPUTNeural Network World NEURAL NETW WORLDNeural Networks NEURAL NETWORKSNeural Processing Letters NEURAL PROCESS LETTNeurocomputing NEUROCOMPUTINGNew Generation Computing NEW GENERAT COMPUT New Review of Hypermedia and Multimedia NEW REV HYPERMEDIA M Online Information Review ONLINE INFORM REV Optical Switching and Networking OPT SWITCH NETWOptimization Methods & Software OPTIM METHOD SOFTWParallel Computing PARALLEL COMPUT Peer-To-Peer Networking and Applications PEER PEER NETW APPLPerformance Evaluation PERFORM EVALUATION Personal and Ubiquitous Computing PERS UBIQUIT COMPUTPervasive and Mobile Computing PERVASIVE MOB COMPUTPhotonic Network Communications PHOTONIC NETW COMMUN Presence-Teleoperators and Virtual Environments PRESENCE-TELEOP VIRT Problems of Information Transmission PROBL INFORM TRANSM+Programming and Computer Software PROGRAM COMPUT SOFT+ Rairo-Theoretical Informatics and Applications RAIRO-THEOR INF APPLReal-Time Systems REAL-TIME SYSTRequirements Engineering REQUIR ENGResearch Synthesis Methods RES SYNTH METHODS Romanian Journal of Information Science and Technology ROM J INF SCI TECH Science China-Information Sciences SCI CHINA INFORM SCIScience of Computer Programming SCI COMPUT PROGRAMScientific Programming SCI PROGRAMMING-NETH Security and Communication Networks SECUR COMMUN NETW Siam Journal On Computing SIAM J COMPUTSiam Journal On Imaging Sciences SIAM J IMAGING SCISigmod Record SIGMOD REC Simulation Modelling Practice and Theory SIMUL MODEL PRACT TH Simulation-Transactions of the Society For Modeling and Simulation International SIMUL-T SOC MOD SIMSoft Computing SOFT COMPUTSoftware and Systems Modeling SOFTW SYST MODELSoftware Quality Journal SOFTWARE QUAL J Software Testing Verification & Reliability SOFTW TEST VERIF REL Software-Practice & Experience SOFTWARE PRACT EXPERSpeech Communication SPEECH COMMUNStatistics and Computing STAT COMPUTSwarm Intelligence SWARM INTELL-USTelecommunication Systems TELECOMMUN SYST Theoretical Biology and Medical Modelling THEOR BIOL MED MODEL Theoretical Computer Science THEOR COMPUT SCI Theory and Practice of Logic Programming THEOR PRACT LOG PROG Theory of Computing Systems THEOR COMPUT SYST Transactions On Emerging Telecommunications Technologies T EMERG TELECOMMUN T Universal Access in the Information Society UNIVERSAL ACCESS INFUser Modeling and User-Adapted Interaction USER MODEL USER-ADAPVirtual Reality VIRTUAL REAL-LONDONVisual Computer VISUAL COMPUTVldb Journal VLDB JWiley Interdisciplinary Reviews-Data Mining and Knowledge Discovery WIRES DATA MIN KNOWL Wireless Communications & Mobile Computing WIREL COMMUN MOB COM Wireless Networks WIREL NETW Wireless Personal Communications WIRELESS PERS COMMUN World Wide Web-Internet and Web Information Systems WORLD WIDE WEBISSN EISSN ESI学科名称0360-03001557-7341COMPUTER SCIENCE 1550-48321550-4840COMPUTER SCIENCE 0146-48331943-5819COMPUTER SCIENCE 0362-13401558-1160COMPUTER SCIENCE 1549-63251549-6333COMPUTER SCIENCE 1544-35581544-3965COMPUTER SCIENCE 1544-35661544-3973COMPUTER SCIENCE 1556-46651556-4703COMPUTER SCIENCE 1529-37851557-945X COMPUTER SCIENCE 0734-********-7333COMPUTER SCIENCE 1073-05161557-7325COMPUTER SCIENCE 0362-59151557-4644COMPUTER SCIENCE 1084-43091557-7309COMPUTER SCIENCE 1539-90871558-3465COMPUTER SCIENCE 0730-********-7368COMPUTER SCIENCE 1094-92241557-7406COMPUTER SCIENCE 1046-81881558-2868COMPUTER SCIENCE 2157-69042157-6912COMPUTER SCIENCE 1533-53991557-6051COMPUTER SCIENCE 1556-46811556-472X COMPUTER SCIENCE 0098-35001557-7295COMPUTER SCIENCE 1049-33011558-1195COMPUTER SCIENCE 1551-68571551-6865COMPUTER SCIENCE 0164-09251558-4593COMPUTER SCIENCE 1936-74061936-7414COMPUTER SCIENCE 1550-48591550-4867COMPUTER SCIENCE 1049-331X1557-7392COMPUTER SCIENCE 1553-30771553-3093COMPUTER SCIENCE 1559-11311559-114X COMPUTER SCIENCE 0001-59031432-0525COMPUTER SCIENCE 1551-98991552-0633COMPUTER SCIENCE 1570-87051570-8713COMPUTER SCIENCE 0065-2458null COMPUTER SCIENCE 0965-99781873-5339COMPUTER SCIENCE 1434-84111618-0399COMPUTER SCIENCE 0003-43471958-9395COMPUTER SCIENCE 1869-03271869-0327COMPUTER SCIENCE 1570-58381875-8533COMPUTER SCIENCE 1568-49461872-9681COMPUTER SCIENCE 0004-37021872-7921COMPUTER SCIENCE 0269-28211573-7462COMPUTER SCIENCE 1064-54621530-9185COMPUTER SCIENCE 0928-89101573-7535COMPUTER SCIENCE 1387-25321573-7454COMPUTER SCIENCE 1089-70891538-7305COMPUTER SCIENCE 1367-48031460-2059COMPUTER SCIENCE 1471-21051471-2105COMPUTER SCIENCE 1467-54631477-4054COMPUTER SCIENCE 1867-02021867-0202COMPUTER SCIENCE 1673-5447null COMPUTER SCIENCE 1386-78571573-7543COMPUTER SCIENCE 1546-22181546-2226COMPUTER SCIENCE1526-14921526-1506COMPUTER SCIENCE 1866-99561866-9964COMPUTER SCIENCE 1389-0417null COMPUTER SCIENCE 0001-07821557-7317COMPUTER SCIENCE 1476-92711476-928X COMPUTER SCIENCE 1420-05971573-1499COMPUTER SCIENCE 0891-********-9312COMPUTER SCIENCE 0018-91621558-0814COMPUTER SCIENCE 0167-83961879-2332COMPUTER SCIENCE 1546-42611546-427X COMPUTER SCIENCE 1061-37731099-0542COMPUTER SCIENCE 0140-36641873-703X COMPUTER SCIENCE 0167-70551467-8659COMPUTER SCIENCE 0010-46201460-2067COMPUTER SCIENCE 1477-84241873-6866COMPUTER SCIENCE 0169-26071872-7565COMPUTER SCIENCE 0045-78251879-2138COMPUTER SCIENCE 1025-58421476-8259COMPUTER SCIENCE 0148-92671531-5169COMPUTER SCIENCE 1389-12861872-7069COMPUTER SCIENCE 1820-02141820-0214COMPUTER SCIENCE 0885-23081095-8363COMPUTER SCIENCE 0920-54891872-7018COMPUTER SCIENCE 0925-97241573-7551COMPUTER SCIENCE 0267-6192null COMPUTER SCIENCE 1077-31421090-235X COMPUTER SCIENCE 0010-44851879-2685COMPUTER SCIENCE 0098-13541873-4375COMPUTER SCIENCE 0360-13151873-782X COMPUTER SCIENCE 0045-79061879-0755COMPUTER SCIENCE 0045-79301879-0747COMPUTER SCIENCE 0098-30041873-7803COMPUTER SCIENCE 0097-84931873-7684COMPUTER SCIENCE 0360-83521879-0550COMPUTER SCIENCE 0305-05481873-765X COMPUTER SCIENCE 0167-40481872-6208COMPUTER SCIENCE 0045-79491879-2243COMPUTER SCIENCE 1598-81981598-818X COMPUTER SCIENCE 0168-16991872-7107COMPUTER SCIENCE 0266-352X1873-7633COMPUTER SCIENCE 0010-48251879-0534COMPUTER SCIENCE 0166-36151872-6194COMPUTER SCIENCE 0010-485X1436-5057COMPUTER SCIENCE 1335-9150null COMPUTER SCIENCE 1521-96151558-366X COMPUTER SCIENCE 1532-06261532-0634COMPUTER SCIENCE 0954-********-0494COMPUTER SCIENCE 1383-71331572-9354COMPUTER SCIENCE 1936-24471936-2455COMPUTER SCIENCE 0161-11941558-1586COMPUTER SCIENCE 1574-89362212-392X COMPUTER SCIENCE 0169-023X1872-6933COMPUTER SCIENCE 1384-58101573-756X COMPUTER SCIENCE0167-92361873-5797COMPUTER SCIENCE 0929-55851572-8080COMPUTER SCIENCE 0925-10221573-7586COMPUTER SCIENCE 1742-28761873-202X COMPUTER SCIENCE 0141-93821872-7387COMPUTER SCIENCE 0926-87821573-7578COMPUTER SCIENCE 0178-27701432-0452COMPUTER SCIENCE 1382-32561573-7616COMPUTER SCIENCE 0177-06671435-5663COMPUTER SCIENCE 1751-75751751-7583COMPUTER SCIENCE 1364-81521873-6726COMPUTER SCIENCE 1225-64632233-7326COMPUTER SCIENCE 1687-14991687-1499COMPUTER SCIENCE 0960-085X1476-9344COMPUTER SCIENCE 1176-93431176-9343COMPUTER SCIENCE 1063-65601530-9304COMPUTER SCIENCE 0266-47201468-0394COMPUTER SCIENCE 0934-********-299X COMPUTER SCIENCE 0925-98561572-8102COMPUTER SCIENCE 1554-06691554-0677COMPUTER SCIENCE 1662-52181662-5218COMPUTER SCIENCE 2095-22282095-2236COMPUTER SCIENCE 2095-91842095-9230COMPUTER SCIENCE 0169-29681875-8681COMPUTER SCIENCE 0167-739X1872-7115COMPUTER SCIENCE 1389-25761573-7632COMPUTER SCIENCE 1524-07031524-0711COMPUTER SCIENCE 0737-********-7051COMPUTER SCIENCE 0018-86462151-8556COMPUTER SCIENCE 1389-6911null COMPUTER SCIENCE 1058-61801934-1547COMPUTER SCIENCE 1089-77981558-2558COMPUTER SCIENCE 0163-68041558-1896COMPUTER SCIENCE 1553-877X1553-877X COMPUTER SCIENCE 1556-603X1556-6048COMPUTER SCIENCE 1556-60561556-6064COMPUTER SCIENCE 0272-17161558-1756COMPUTER SCIENCE 2168-2356null COMPUTER SCIENCE 1089-78011941-0131COMPUTER SCIENCE 2168-21942168-2194COMPUTER SCIENCE 0733-********-0008COMPUTER SCIENCE 0272-17321937-4143COMPUTER SCIENCE 1070-986X1941-0166COMPUTER SCIENCE 0890-********-156X COMPUTER SCIENCE 1536-12681558-2590COMPUTER SCIENCE 1540-79931558-4046COMPUTER SCIENCE 0740-74591937-4194COMPUTER SCIENCE 1932-81841937-9234COMPUTER SCIENCE 1949-30451949-3045COMPUTER SCIENCE 1943-06041943-0612COMPUTER SCIENCE 0018-93161557-9611COMPUTER SCIENCE 0090-67781558-0857COMPUTER SCIENCE 1943-068X1943-0698COMPUTER SCIENCE0018-93401557-9956COMPUTER SCIENCE 2168-22672168-2275COMPUTER SCIENCE 1545-59711941-0018COMPUTER SCIENCE 1089-778X1941-0026COMPUTER SCIENCE 1939-14122329-4051COMPUTER SCIENCE 1556-60131556-6021COMPUTER SCIENCE 0018-94481557-9654COMPUTER SCIENCE 1939-13821939-1382COMPUTER SCIENCE 1536-12331558-0660COMPUTER SCIENCE 1520-92101941-0077COMPUTER SCIENCE 2162-237X2162-2388COMPUTER SCIENCE 1045-92191558-2183COMPUTER SCIENCE 1939-13741939-1374COMPUTER SCIENCE 0098-55891939-3520COMPUTER SCIENCE 1077-26261941-0506COMPUTER SCIENCE 1536-12761558-2248COMPUTER SCIENCE 1536-12841558-0687COMPUTER SCIENCE 1545-59631557-9964COMPUTER SCIENCE 1063-66921558-2566COMPUTER SCIENCE 1745-13451745-1345COMPUTER SCIENCE 1745-13611745-1361COMPUTER SCIENCE 2047-49382047-4946COMPUTER SCIENCE 1751-96321751-9640COMPUTER SCIENCE 1751-86011751-861X COMPUTER SCIENCE 1751-87091751-8717COMPUTER SCIENCE 1751-87841751-8792COMPUTER SCIENCE 1751-88061751-8814COMPUTER SCIENCE 0868-49521822-8844COMPUTER SCIENCE 0890-********-2651COMPUTER SCIENCE 0950-58491873-6025COMPUTER SCIENCE 1566-25351872-6305COMPUTER SCIENCE 0020-01901872-6119COMPUTER SCIENCE 1386-45641573-7659COMPUTER SCIENCE 0020-02551872-6291COMPUTER SCIENCE 0306-43791873-6076COMPUTER SCIENCE 1387-33261572-9419COMPUTER SCIENCE 1058-05301934-8703COMPUTER SCIENCE 1392-124X null COMPUTER SCIENCE 1473-87161473-8724COMPUTER SCIENCE 1091-98561526-5528COMPUTER SCIENCE 1069-25091875-8835COMPUTER SCIENCE 0167-92601872-7522COMPUTER SCIENCE 1088-467X1571-4128COMPUTER SCIENCE 0953-********-7951COMPUTER SCIENCE 1683-3198null COMPUTER SCIENCE 2040-79392040-7947COMPUTER SCIENCE 1743-82251743-8233COMPUTER SCIENCE 0888-613X1873-4731COMPUTER SCIENCE 1758-03661758-0374COMPUTER SCIENCE 1875-68911875-6883COMPUTER SCIENCE 0975-********-9322COMPUTER SCIENCE 1841-98361841-9844COMPUTER SCIENCE 0218-84301793-6365COMPUTER SCIENCE。
802.11n中用来提高吞吐量的机制

802.11n是一种无线局域网(WLAN)技术标准,旨在提高无线网络的速度和稳定性。
在802.11n标准中,有几种机制被用来提高吞吐量,从而改善无线网络的性能。
本文将介绍802.11n中用来提高吞吐量的机制,并对其原理和实际应用进行详细阐述。
一、MIMO技术MIMO是Multiple-Input Multiple-Output的缩写,即多输入多输出技术。
802.11n标准采用了MIMO技术,通过同时使用多个天线进行数据传输和接收,从而提高了无线网络的吞吐量。
MIMO技术能够在不增加频谱带宽的情况下,通过空间复用的方式提高数据传输速率,增强了信号的抗干扰性和覆盖范围。
利用MIMO技术,802.11n标准支持了1x1、2x2、3x3甚至4x4等不同数量的天线配置,能够实现更多数据的并行传输,提高了网络的整体性能。
MIMO技术还能够通过空间复用和波束成形等手段来提高信号的覆盖范围和可靠性,从而进一步提高了网络的吞吐量和稳定性。
二、帧聚合技术802.11n标准引入了帧聚合技术,通过将多个数据帧合并成一个更大的帧进行传输,从而提高了数据传输的效率和吞吐量。
在传统的802.11a/g标准中,每个数据帧都需要经过一定的信道竞争和保护间隔,从而导致了较为低效的信道利用率和较低的吞吐量。
而在802.11n标准中,通过帧聚合技术,可以将多个数据帧合并成一个更大的帧进行传输,减少了信道竞争的次数,提高了信道的利用效率,进而提高了网络的吞吐量。
帧聚合技术的引入显著改善了无线网络的性能,使得802.11n能够更好地满足多媒体数据传输等高吞吐量的应用需求。
三、频谱聚合技术802.11n标准还引入了频谱聚合技术,通过同时使用多个频段来传输数据,从而提高了无线网络的吞吐量。
在传统的802.11a/g标准中,无线网络只能使用2.4GHz或5GHz的某一个频段进行数据传输,因此受到了频谱资源的限制,无法充分利用现有的频谱资源来提高网络的吞吐量。
HP Color LaserJet Enterprise MFP M776用户指南说明书
Legal informationCopyright and License© Copyright 2019 HP Development Company, L.P.Reproduction, adaptation, or translation without prior written permission is prohibited, except as allowedunder the copyright laws.The information contained herein is subject to change without notice.The only warranties for HP products and services are set forth in the express warranty statementsaccompanying such products and services. Nothing herein should be construed as constituting anadditional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.Edition 1, 10/2019Trademark CreditsAdobe®, Adobe Photoshop®, Acrobat®, and PostScript® are trademarks of Adobe Systems Incorporated.Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries.macOS is a trademark of Apple Inc., registered in the U.S. and other countries.AirPrint is a trademark of Apple Inc., registered in the U.S. and other countries.Google™ is a trademark of Google Inc.Microsoft®, Windows®, Windows® XP, and Windows Vista® are U.S. registered trademarks of MicrosoftCorporation.UNIX® is a registered trademark of The Open Group.iiiT able of contents1 Printer overview (1)Warning icons (1)Potential shock hazard (2)Printer views (2)Printer front view (2)Printer back view (4)Interface ports (4)Control-panel view (5)How to use the touchscreen control panel (7)Printer specifications (8)T echnical specifications (8)Supported operating systems (11)Mobile printing solutions (12)Printer dimensions (13)Power consumption, electrical specifications, and acoustic emissions (15)Operating-environment range (15)Printer hardware setup and software installation (16)2 Paper trays (17)Introduction (17)Load paper to Tray 1 (multipurpose tray) (17)Load Tray 1 (multipurpose tray) (18)Tray 1 paper orientation (19)Use alternative letterhead mode (24)Enable Alternative Letterhead Mode by using the printer control-panel menus (24)Load paper to Tray 2 (24)Load Tray 2 (24)Tray 2 paper orientation (26)Use alternative letterhead mode (29)Enable Alternative Letterhead Mode by using the printer control-panel menus (29)Load paper to the 550-sheet paper tray (30)Load paper to the 550-sheet paper tray (30)550-sheet paper tray paper orientation (32)Use alternative letterhead mode (35)Enable Alternative Letterhead Mode by using the printer control-panel menus (35)ivLoad paper to the 2 x 550-sheet paper trays (36)Load paper to the 2 x 550-sheet paper trays (36)2 x 550-sheet paper tray paper orientation (38)Use alternative letterhead mode (41)Enable Alternative Letterhead Mode by using the printer control-panel menus (41)Load paper to the 2,700-sheet high-capacity input paper trays (41)Load paper to the 2,700-sheet high-capacity input paper trays (41)2,700-sheet HCI paper tray paper orientation (43)Use alternative letterhead mode (45)Enable Alternative Letterhead Mode by using the printer control-panel menus (45)Load and print envelopes (46)Print envelopes (46)Envelope orientation (46)Load and print labels (47)Manually feed labels (47)Label orientation (48)3 Supplies, accessories, and parts (49)Order supplies, accessories, and parts (49)Ordering (49)Supplies and accessories (50)Maintenance/long-life consumables (51)Customer self-repair parts (51)Dynamic security (52)Configure the HP toner-cartridge-protection supply settings (53)Introduction (53)Enable or disable the Cartridge Policy feature (53)Use the printer control panel to enable the Cartridge Policy feature (54)Use the printer control panel to disable the Cartridge Policy feature (54)Use the HP Embedded Web Server (EWS) to enable the Cartridge Policy feature (54)Use the HP Embedded Web Server (EWS) to disable the Cartridge Policy feature (55)Troubleshoot Cartridge Policy control panel error messages (55)Enable or disable the Cartridge Protection feature (55)Use the printer control panel to enable the Cartridge Protection feature (56)Use the printer control panel to disable the Cartridge Protection feature (56)Use the HP Embedded Web Server (EWS) to enable the Cartridge Protection feature (56)Use the HP Embedded Web Server (EWS) to disable the Cartridge Protection feature (57)Troubleshoot Cartridge Protection control panel error messages (57)Replace the toner cartridges (58)T oner-cartridge information (58)Remove and replace the cartridges (59)Replace the imaging drums (62)Imaging drum information (62)Remove and replace the imaging drums (63)Replace the toner-collection unit (66)T oner-collection unit information (66)vRemove and replace the toner-collection unit (67)Replace the staple cartridge (M776zs model only) (70)Staple cartridge information (70)Remove and replace the staple cartridge (71)4 Print (73)Print tasks (Windows) (73)How to print (Windows) (73)Automatically print on both sides (Windows) (74)Manually print on both sides (Windows) (74)Print multiple pages per sheet (Windows) (75)Select the paper type (Windows) (75)Additional print tasks (76)Print tasks (macOS) (77)How to print (macOS) (77)Automatically print on both sides (macOS) (77)Manually print on both sides (macOS) (77)Print multiple pages per sheet (macOS) (78)Select the paper type (macOS) (78)Additional print tasks (79)Store print jobs on the printer to print later or print privately (79)Introduction (79)Create a stored job (Windows) (79)Create a stored job (macOS) (80)Print a stored job (81)Delete a stored job (81)Delete a job that is stored on the printer (81)Change the job storage limit (82)Information sent to printer for Job Accounting purposes (82)Mobile printing (82)Introduction (82)Wi-Fi, Wi-Fi Direct Print, NFC, and BLE printing (82)Enable wireless printing (83)Change the Wi-Fi Direct name (83)HP ePrint via email (83)AirPrint (84)Android embedded printing (85)Print from a USB flash drive (85)Enable the USB port for printing (85)Method one: Enable the USB port from the printer control panel (85)Method two: Enable the USB port from the HP Embedded Web Server (network-connectedprinters only) (85)Print USB documents (86)Print using high-speed USB 2.0 port (wired) (86)Method one: Enable the high-speed USB 2.0 port from the printer control panel menus (86)Method two: Enable the high-speed USB 2.0 port from the HP Embedded Web Server (network-connected printers only) (87)vi5 Copy (88)Make a copy (88)Copy on both sides (duplex) (90)Additional copy tasks (92)6 Scan (93)Set up Scan to Email (93)Introduction (93)Before you begin (93)Step one: Access the HP Embedded Web Server (EWS) (94)Step two: Configure the Network Identification settings (95)Step three: Configure the Send to Email feature (96)Method one: Basic configuration using the Email Setup Wizard (96)Method two: Advanced configuration using the Email Setup (100)Step four: Configure the Quick Sets (optional) (104)Step five: Set up Send to Email to use Office 365 Outlook (optional) (105)Introduction (105)Configure the outgoing email server (SMTP) to send an email from an Office 365 Outlookaccount (105)Set up Scan to Network Folder (108)Introduction (108)Before you begin (108)Step one: Access the HP Embedded Web Server (EWS) (108)Step two: Set up Scan to Network Folder (109)Method one: Use the Scan to Network Folder Wizard (109)Method two: Use Scan to Network Folder Setup (110)Step one: Begin the configuration (110)Step two: Configure the Scan to Network Folder settings (111)Step three: Complete the configuration (118)Set up Scan to SharePoint (118)Introduction (118)Before you begin (118)Step one: Access the HP Embedded Web Server (EWS) (118)Step two: Enable Scan to SharePoint and create a Scan to SharePoint Quick Set (119)Scan a file directly to a SharePoint site (121)Quick Set scan settings and options for Scan to SharePoint (122)Set up Scan to USB Drive (123)Introduction (124)Step one: Access the HP Embedded Web Server (EWS) (124)Step two: Enable Scan to USB Drive (124)Step three: Configure the Quick Sets (optional) (125)Default scan settings for Scan to USB Drive setup (126)Default file settings for Save to USB setup (126)Scan to email (127)Introduction (127)Scan to email (127)Scan to job storage (129)viiIntroduction (129)Scan to job storage on the printer (130)Print from job storage on the printer (132)Scan to network folder (132)Introduction (132)Scan to network folder (132)Scan to SharePoint (134)Introduction (134)Scan to SharePoint (134)Scan to USB drive (136)Introduction (136)Scan to USB drive (136)Use HP JetAdvantage business solutions (138)Additional scan tasks (138)7 Fax (140)Set up fax (140)Introduction (140)Set up fax by using the printer control panel (140)Change fax configurations (141)Fax dialing settings (141)General fax send settings (142)Fax receive settings (143)Send a fax (144)Additional fax tasks (146)8 Manage the printer (147)Advanced configuration with the HP Embedded Web Server (EWS) (147)Introduction (147)How to access the HP Embedded Web Server (EWS) (148)HP Embedded Web Server features (149)Information tab (149)General tab (149)Copy/Print tab (150)Scan/Digital Send tab (151)Fax tab (152)Supplies tab (153)Troubleshooting tab (153)Security tab (153)HP Web Services tab (154)Networking tab (154)Other Links list (156)Configure IP network settings (157)Printer sharing disclaimer (157)View or change network settings (157)Rename the printer on a network (157)viiiManually configure IPv4 TCP/IP parameters from the control panel (158)Manually configure IPv6 TCP/IP parameters from the control panel (158)Link speed and duplex settings (159)Printer security features (160)Introduction (160)Security statements (160)Assign an administrator password (160)Use the HP Embedded Web Server (EWS) to set the password (160)Provide user access credentials at the printer control panel (161)IP Security (161)Encryption support: HP High Performance Secure Hard Disks (161)Lock the formatter (161)Energy-conservation settings (161)Set the sleep timer and configure the printer to use 1 watt or less of power (161)Set the sleep schedule (162)Set the idle settings (162)HP Web Jetadmin (163)Software and firmware updates (163)9 Solve problems (164)Customer support (164)Control panel help system (165)Reset factory settings (165)Introduction (165)Method one: Reset factory settings from the printer control panel (165)Method two: Reset factory settings from the HP Embedded Web Server (network-connectedprinters only) (166)A “Cartridge is low” or “Cartridge is very low” message displays on the printer control panel (166)Change the “Very Low” settings (166)Change the “Very Low” settings at the control panel (166)For printers with fax capability (167)Order supplies (167)Printer does not pick up paper or misfeeds (167)Introduction (167)The printer does not pick up paper (167)The printer picks up multiple sheets of paper (171)The document feeder jams, skews, or picks up multiple sheets of paper (174)Clear paper jams (174)Introduction (174)Paper jam locations (174)Auto-navigation for clearing paper jams (175)Experiencing frequent or recurring paper jams? (175)Clear paper jams in the document feeder - 31.13.yz (176)Clear paper jams in Tray 1 (13.A1) (177)Clear paper jams in Tray 2 (13.A2) (182)Clear paper jams in the fuser (13.B9, 13.B2, 13.FF) (188)ixClear paper jams in the duplex area (13.D3) (194)Clear paper jams in the 550-sheet trays (13.A3, 13.A4) (199)Clear paper jams in the 2 x 550 paper trays (13.A4, 13.A5) (206)Clear paper jams in the 2,700-sheet high-capacity input paper trays (13.A3, 13.A4, 13.A5, 13.A7) (213)Resolving color print quality problems (220)Introduction (220)Troubleshoot print quality (221)Update the printer firmware (221)Print from a different software program (221)Check the paper-type setting for the print job (221)Check the paper type setting on the printer (221)Check the paper type setting (Windows) (221)Check the paper type setting (macOS) (222)Check toner-cartridge status (222)Step one: Print the Supplies Status Page (222)Step two: Check supplies status (222)Print a cleaning page (222)Visually inspect the toner cartridge or cartridges (223)Check paper and the printing environment (223)Step one: Use paper that meets HP specifications (223)Step two: Check the environment (223)Step three: Set the individual tray alignment (224)Try a different print driver (224)Troubleshoot color quality (225)Calibrate the printer to align the colors (225)Troubleshoot image defects (225)Improve copy image quality (233)Check the scanner glass for dirt and smudges (233)Calibrate the scanner (234)Check the paper settings (235)Check the paper selection options (235)Check the image-adjustment settings (235)Optimize copy quality for text or pictures (236)Edge-to-edge copying (236)Improve scan image quality (236)Check the scanner glass for dirt and smudges (237)Check the resolution settings (238)Check the color settings (238)Check the image-adjustment settings (239)Optimize scan quality for text or pictures (239)Check the output-quality settings (240)Improve fax image quality (240)Check the scanner glass for dirt and smudges (240)Check the send-fax resolution settings (242)Check the image-adjustment settings (242)Optimize fax quality for text or pictures (242)Check the error-correction setting (243)xSend to a different fax machine (243)Check the sender's fax machine (243)Solve wired network problems (244)Introduction (244)Poor physical connection (244)The computer is unable to communicate with the printer (244)The printer is using incorrect link and duplex settings for the network (245)New software programs might be causing compatibility problems (245)The computer or workstation might be set up incorrectly (245)The printer is disabled, or other network settings are incorrect (245)Solve wireless network problems (245)Introduction (245)Wireless connectivity checklist (245)The printer does not print after the wireless configuration completes (246)The printer does not print, and the computer has a third-party firewall installed (246)The wireless connection does not work after moving the wireless router or printer (247)Cannot connect more computers to the wireless printer (247)The wireless printer loses communication when connected to a VPN (247)The network does not appear in the wireless networks list (247)The wireless network is not functioning (247)Reduce interference on a wireless network (248)Solve fax problems (248)Checklist for solving fax problems (248)What type of phone line are you using? (249)Are you using a surge-protection device? (249)Are you using a phone company voice-messaging service or an answering machine? (249)Does your phone line have a call-waiting feature? (249)Check fax accessory status (249)General fax problems (250)The fax failed to send (250)No fax address book button displays (250)Not able to locate the Fax settings in HP Web Jetadmin (250)The header is appended to the top of the page when the overlay option is enabled (251)A mix of names and numbers is in the recipients box (251)A one-page fax prints as two pages (251)A document stops in the document feeder in the middle of faxing (251)The volume for sounds coming from the fax accessory is too high or too low (251)Index (252)xiPrinter overview1Review the location of features on the printer, the physical and technical specifications of the printer,and where to locate setup information.For video assistance, see /videos/LaserJet.The following information is correct at the time of publication. For current information, see /support/colorljM776MFP.For more information:HP's all-inclusive help for the printer includes the following information:●Install and configure●Learn and use●Solve problems●Download software and firmware updates●Join support forums●Find warranty and regulatory informationWarning iconsUse caution if you see a warning icon on your HP printer, as indicated in the icon definitions.●Caution: Electric shock●Caution: Hot surface●Caution: Keep body parts away from moving partsPrinter overview1●Caution: Sharp edge in close proximity●WarningPotential shock hazardReview this important safety information.●Read and understand these safety statements to avoid an electrical shock hazard.●Always follow basic safety precautions when using this product to reduce risk of injury from fire orelectric shock.●Read and understand all instructions in the user guide.●Observe all warnings and instructions marked on the product.●Use only a grounded electrical outlet when connecting the product to a power source. If you do notknow whether the outlet is grounded, check with a qualified electrician.●Do not touch the contacts on any of the sockets on the product. Replace damaged cordsimmediately.●Unplug this product from wall outlets before cleaning.●Do not install or use this product near water or when you are wet.●Install the product securely on a stable surface.●Install the product in a protected location where no one can step on or trip over the power cord.Printer viewsIdentify certain parts of the printer and the control panel.Printer front viewLocate features on the front of the printer.2Chapter 1 Printer overviewPrinter front view3Printer back viewLocate features on the back of the printer.Interface portsLocate the interface ports on the printer formatter. 4Chapter 1 Printer overviewControl-panel viewThe control panel provides access to the printer features and indicates the current status of the printer.NOTE:Tilt the control panel for easier viewing.The Home screen provides access to the printer features and indicates the current status of the printer.screens.NOTE:The features that appear on the Home screen can vary, depending on the printerconfiguration.Control-panel view5Figure 1-1Control-panel view?i 12:42 PM6Chapter 1 Printer overviewHow to use the touchscreen control panelPerform the following actions to use the printer touchscreen control panel.T ouchT ouch an item on the screen to select that item or open that menu. Also, when scrolling T ouch the Settings icon to open the Settings app.How to use the touchscreen control panel 7SwipeT ouch the screen and then move your finger horizontally to scroll the screen sideways.Swipe until the Settings app displays.Printer specificationsDetermine the specifications for your printer model.IMPORTANT:The following specifications are correct at the time of publication, but they are subject to change. For current information, see /support/colorljM776MFP .T echnical specificationsReview the printer technical specifications.Product numbers for each model ●M776dn - #T3U55A ●Flow M776z - #3WT91A ●Flow M776zs - #T3U56APaper handling specificationsPaper handling features Tray 1 (100-sheet capacity)Included Included Included Tray 2 (550-sheet capacity)IncludedIncludedIncluded8Chapter 1 Printer overview550-sheet paper trayOptional Included Not included NOTE:The M776dn models accept one optional550-sheet tray.Optional Included Included2 x 550-sheet paper tray and standNOTE:The M776dn models accept one optional550-sheet tray that may be installed on top of thestand.Optional Not included Not included2,700-sheet high-capacity input (HCI) paper trayand standNOTE:The M776dn models accept one optional550-sheet tray that may be installed on top of theoptional printer stand.Printer standOptional Not included Not included NOTE:The M776dn models accept one optional550-sheet tray that may be installed on top of theoptional printer stand.Inner finisher accessory Not included Not included Included Automatic duplex printing Included IncludedIncludedIncluded Included Included10/100/1000 Ethernet LAN connection with IPv4and IPv6Hi-Speed USB 2.0Included Included IncludedIncluded Included IncludedEasy-access USB port for printing from a USBflash drive or upgrading the firmwareIncluded Included Included Hardware Integration Pocket for connectingaccessory and third-party devicesHP Internal USB Ports Optional Optional OptionalOptional Optional OptionalHP Jetdirect 2900nw Print Server accessory forWi-Fi connectivity and an additional Ethernet portOptional IncludedIncludedHP Jetdirect 3100w accessory for Wi-Fi, BLE, NFC,and proximity badge readingPrints 45 pages per minute (ppm) on Letter-sizepaper and 46 ppm on A4-size paperEasy-access USB printing for printing from a USBIncluded Included Includedflash driveT echnical specifications9Included Included Included Store jobs in the printer memory to print later orprint privatelyScans 100 pages per minute (ppm) on A4 andIncluded Included Included letter-size paper one-sidedIncluded Included Included 200-page document feeder with dual-headscanning for single-pass duplex copying andscanningNot included Included Included HP EveryPage T echnologies including ultrasonicmulti-feed detectionNot included Included Included Embedded optical character recognition (OCR)provides the ability to convert printed pages intotext that can be edited or searched using acomputerIncluded Included Included SMART Label feature provides paper-edgedetection for automatic page croppingIncluded Included Included Automatic page orientation for pages that haveat least 100 characters of textIncluded Automatic tone adjustment sets contrast,Included Includedbrightness, and background removal for eachpageIncluded Included Includedfolders on a networkIncludedSend documents to SharePoint®Included IncludedIncluded Included Included NOTE:Memory reported on the configurationpage will change from 2.5 GB to 3 GB with theoptional 1 GB SODIMM installed.Mass storage: 500 GB hard disk drive Included Included IncludedSecurity: HP Trusted Platform Module (TPM)Included Included IncludedT ouchscreen control panel Included Included IncludedRetractable keyboard Not included Included Included 10Chapter 1 Printer overviewFax Optional Included IncludedSupported operating systemsUse the following information to ensure printer compatibility with your computer operating system.Linux: For information and print drivers for Linux, go to /go/linuxprinting.UNIX: For information and print drivers for UNIX®, go to /go/unixmodelscripts.The following information applies to the printer-specific Windows HP PCL 6 print drivers, HP print driversfor macOS, and to the software installer.Windows: Download HP Easy Start from /LaserJet to install the HP print driver. Or, go tothe printer-support website for this printer: /support/colorljM776MFP to download the printdriver or the software installer to install the HP print driver.macOS: Mac computers are supported with this printer. Download HP Easy Start either from /LaserJet or from the Printer Support page, and then use HP Easy Start to install the HP print driver.1.Go to /LaserJet.2.Follow the steps provided to download the printer software.Windows 7, 32-bit and 64-bit The “HP PCL 6” printer-specific print driver is installed for this operating system aspart of the software installation.Windows 8.1, 32-bit and 64-bit The “HP PCL-6” V4 printer-specific print driver is installed for this operating systemas part of the software installation.Windows 10, 32-bit and 64-bit The “HP PCL-6” V4 printer-specific print driver is installed for this operating systemas part of the software installation.Windows Server 2008 R2, SP 1, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2012, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2012 R2, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2016, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2019, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Supported operating systems11macOS 10.13 High Sierra, macOS 10.14 MojaveDownload HP Easy Start from /LaserJet , and then use it to install the print driver.NOTE:Supported operating systems can change.NOTE:For a current list of supported operating systems and HP’s all-inclusive help for the printer, go to /support/colorljM776MFP .NOTE:For details on client and server operating systems and for HP UPD driver support for this printer, go to /go/upd . Under Additional information , click Specifications .●Internet connection●Dedicated USB 1.1 or 2.0 connection or a network connection● 2 GB of available hard-disk space ●1 GB RAM (32-bit) or2 GB RAM (64-bit)●Internet connection●Dedicated USB 1.1 or 2.0 connection or a network connection●1.5 GB of available hard-disk spaceNOTE:The Windows software installer installs the HP Smart Device Agent Base service. The file size is less than 100 kb. Its only function is to check for printers connected via USB hourly. No data is collected. If a USB printer is found, it then tries to locate a JetAdvantage Management Connector (JAMc) instance on the network. If a JAMc is found, the HP Smart Device Agent Base is securelyupgraded to a full Smart Device Agent from JAMc, which will then allow printed pages to be accounted for in a Managed Print Services (MPS) account. The driver-only web packs downloaded from for the printer and installed through the Add Printer wizard do not install this service.T o uninstall the service, open the Control Panel , select Programs or Programs and Features , and then select Add/Remove Programs or Uninstall a Programto remove the service. The file name isHPSmartDeviceAgentBase.Mobile printing solutionsHP offers multiple mobile printing solutions to enable easy printing to an HP printer from a laptop, tablet, smartphone, or other mobile device.T o see the full list and to determine the best choice, go to /go/MobilePrinting .NOTE:Update the printer firmware to ensure all mobile printing capabilities are supported.●Wi-Fi Direct (wireless models only, with HP Jetdirect 3100w BLE/NFC/Wireless accessory installed)●HP ePrint via email (Requires HP Web Services to be enabled and the printer to be registered with HP Connected)●HP Smart app ●Google Cloud Print12Chapter 1 Printer overview。
赫斯曼VLAN和ROUTING配置
1、VLAN配置
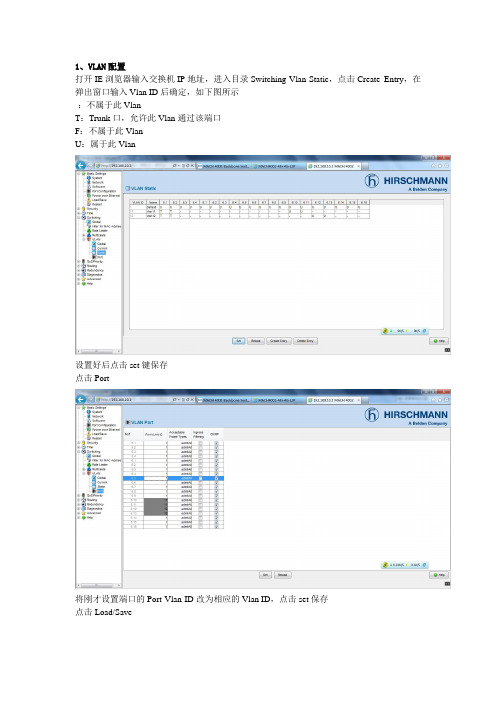
打开IE浏览器输入交换机IP地址,进入目录Switching-Vlan-Static,点击Create Entry,在弹出窗口输入Vlan ID后确定,如下图所示
-:不属于此Vlan
T:Trunk口,允许此Vlan通过该端口
F:不属于此Vlan
U:属于此Vlan
设置好后点击set键保存
点击Port
将刚才设置端口的Port-Vlan-ID改为相应的Vlan ID,点击set保存
点击Load/Save
点击Save to Device配置完成
2、路由配置
如果需要两个VLAN之间通讯,需要配置VLAN的路由功能。
只能配置核心交换机的路由功能。
将电脑接入核心交换机的管理端口,通过WEB界面方式访问交换机并配置路由接口地址,输入交换机的管理地址(172.16.8.251),用户名:admin,
密码:private
选择Routing—Global,将Routing选项打钩,启用路由功能。
为VLAN1创建路由接口172.16.1.254
选择Routing—Interfaces—Configueation
点击右下角的配置向导Wizard,弹出配置向导画面,如图:
点击Next
配置路由地址
配置VLAN1的路由地址为172.16.1.254,同样,配置VLAN2的路由地址为172.16.2.254。
配置好路由后需要保存配置,点击“Save configuration”,如图:
注:配置路由功能时,电脑需安装JAVA程序。
罗翔网络WiFly GSX 802.11 b g无线局域网模块数据手册说明书

WiFly GSX 802.11 b/g Wireless LAN ModuleFeatures•Qualified 2.4GHz IEEE 802.11b/g transceiver •High throughput, 1Mbps sustained data ratewith TCP/IP and WPA2•Ultra-low power - 4uA sleep, 40mA Rx,210mA Tx (max)•Small, compact surface mount module•On board ceramic chip antenna and U.FL connector for external antenna•8 Mbit flash memory and 128 KB RAM•UART hardware interface•10 general purpose digital I/O•8 analog sensor interfaces•Real-time clock for wakeup and time stamping •Accepts 3.3V regulated or 2-3V battery•Supports Adhoc connections•On board ECOS -OS, TCP/IP stacks•Wi-Fi Alliance certified for WPA2-PSK•FCC / CE/ ICS certified and RoHS compliant.•Industrial (RN-131G) and commercial(RN-131C ) grade temperature options Applications•Remote equipment monitoring•Telemetry••Home Automation•Medical device monitoringDescriptionThe WiFly GSX module is a stand alone, embedded wireless 802.11 networking module. Because of its small form factor and extremely low power consumption, the RN-131G is perfect for mobile wireless applications such as asset monitoring, GPS tracking and battery sensors. The WiFly GSX module incorporates a 2.4GHz radio, processor, TCP/IP stack, real-time clock, crypto accelerator, power management and analog sensor interfaces. This complete solution is preloaded with software to simplify integration and minimizes development of your application. In the simplest configuration the hardware only requires four connections (PWR, TX, RX, GND) to create a wireless data connection. Additionally, the sensor interface provides temperature, audio, motion, acceleration and other analog data without requiring additional hardware. The WiFly GSX module is programmed and controlled with a simple ASCII command language. Once the WiFly GSX is setup it can scan to find an access point, associate, authenticate and connect over any WifI network.Block DiagramOverview•Host Data Rate u p to 1 Mbps for UART•Intelligent, built-in power management with programmable wakeup•Can be powered from regulated 3.3-3.7V source or 2.0-3.0V batteries•Real time clock for time stamping, auto-sleep and auto-wakeup•Configuration over UART using simple ASCII commands•Telnet configuration over WiFi•Over the air firmware upgrade (FTP)•Memory 128 KB RAM,2MB ROM, 2 KB battery-backed memory, 8 Mbit Flash.•Secure WiFi authentication WEP-128, WPA-PSK (TKIP), WPA2-PSK (AES)•Built in networking applications DHCP, UDP, DNS, ARP, ICMP, TCP, sockets•802.11 power save and roaming functionsEnvironmental ConditionsParameter RN-131G RN-131C Temperature Range (Operating) -30 o C ~ +85 o C 0 o C ~ +70 o CTemperature Range (Storage) -40o C ~ +85 o C -40o C ~ +85 o C Relative Humidity (Operating) ≤90% ≤90%Relative Humidity (Storage) ≤90% ≤90% Electrical CharacteristicsSupply Voltage Min Typ. Max. Unit Supply Voltage VDD 3.0 3.3 3.7 VDC Supply Voltage (VBATT option) 2.0 3.0 3.3 VDCPin 21 switched 3.3V output 150 ma Digital IinputInput logic HIGH VIH 2.3V VDC Input logic LOW VIL 1.0V VDC Digital Output drivePIO 4,5,6,7,8 24 ma PIO 9,10,11,12,13 8 ma Power consumptionSleep 4 uA Standby (doze) - 15 - mA Connected (idle, RX) 40 mA Connected (TX) 140 212 mAAnalog Sensor InputsParameter Value Sense 0,1,2,3 wakeup detect threshold 500mVAD sense 0-7 measurement range 0-400mVPrecision 14 bits = 12uVAccuracy 5% un-calibrated, .01% calibrated Minimum conversion time 35uS (5kHz over wifi )Sensor Power (pin 33) output resistance 3.3V 10 ohms, max current = 50mA Radio CharacteristicsParameter Specifications Frequency 2402 ~ 2480MHzModulation 802.11b compatibility : DSSS(CCK-11, CCK-5.5, DQPSK-2, DBPSK-1) 802.11g : OFDM (default)Channel intervals 5MHzChannels 1 - 14Transmission rate (over the air) 1 – 11Mbps for 802.11b / 6 – 54Mbps for 802.11g Receive sensitivity -85dBm typ.Output level (Class1) +18dBmMaximum RF input to U.FLconnector10 dBmTop view(pads not visible from top)Pin Name Description Default1 SENSOR-6 Sensor interface, analog input to module, 1.2V No connect2 SENSOR-4 Sensor interface, Analog input to module, 1.2V No connect3 SENSOR-5 Sensor interface, Analog input to module, 1.2V No connect4 SENSOR-7 Analog input to module, 1.2V No connect5 RESET Module reset, Active Low, reference to VDD-BATT, 160 usec pulse Pull up6 EPC-ANT-A EPC port, RFID antenna A No connect7 EPC-ANT-B EPC port, RFID antenna B No connect8 SUPERCAP Balance center pin voltage on stacked super capacitors, Analog 3.3V No connect9 FORCE_AWAKE Force the module to wakeup, input to module, 31us min. pulse10 GPIO-13 UART RTS flow control, 8mA drive, 3.3V tolerant11 GPIO-12 UART CTS flow control, 8mA drive, 3.3V tolerant12 UART-RX RX to the module, 8mA drive, 3.3V tolerant13 UART-TX TX from the module, 8mA drive, 3.3V tolerant14 SPI-MOSI SPI master data out (Contact Roving Networks for details) No connect15 SPI-CLK SPI clock, (Contact Roving Networks for details) No connect16 SPI-MISO SPI master data in (Contact Roving Networks for details) No connect17 3.3V-REG-OUT boost regulator control output, connect to 3.3V-REG-IN to enable No connect18 3.3V-REG-IN boost regulator control input, connect to 3.3V-REG-OUT to enable GND to disable19 GND Ground20 VDD-BATT Battery input, 2.0-3.3V with boost regulator in use, 3.0-3.7V otherwise21 VDD-IN 3.3 to 3.7 voltage, do not connect when boost regulator is in use22 DMA-TX Debug port *(apply 100K pulldown if ultra low sleep power reqd) HIGH Z23 DMA-RX Debug port No connect24 GPIO-9 Restore factory resets, 8mA drive, 3.3V tolerant INPUT25 GPIO-8 GPIO, 24mA drive, 3.3V tolerant GP output26 GPIO-7 GPIO, 24mA drive, 3.3V tolerant GP output27 GPIO-6 Connection STATUS, 24mA drive, 3.3V tolerant LED output28 GPIO-5 Data transfer STATUS, 24mA drive, 3.3V tolerant LED output29 GPIO-4 Association STATUS, 24mA drive, 3.3V tolerant LED output30 SENSOR-1 Sensor interface, analog input to module, 1.2V31 SENSOR-2 Sensor interface, analog input to module, 1.2V32 SENSOR-3 Sensor interface, analog input to module, 1.2V33 SENSE-PWR Voltage output from module to power external sensors, 3.3V34 SENSOR-0 Wakeup from external condition35 NO CONNECT No connect 36-44 GND Must be connected for proper antenna performanceantenna37 mm2 mm2 mm 2 mm1 mm2 mm 20 mmBottom vie w2 mm28.5 mmpin 23pin 14pin 1pin 36Design Concerns1. Minimizing radio interference. When integrating the WiFlymodule with on board chip antenna make sure the area around the chip antenna end the module protrudes at least 6mm from the mother board PCB and any metal enclosure. Ifthis is not possible use the on board U.FL connector to route to an external Antenna.The 8.5 mm area under the antenna end of the moduleshould be keep clear of metallic components, connectors, vias, traces and other materials that can interfere with the radio signal. 2. Proper grounding. For the module antenna to function pins36- to 44 must be connected to GND. We suggest you place module such that 0.5mm of theses pads is exposed. This provides access for soldiering pins 36 through 44 from below and provides ample clearance of the antenna from the PCB.3. Solder Reflow. Reflow temperature must not exceed 220C.To reflow solder the RN-131G and RN-131C module onto a PCB Roving recommends a RoHS compliant solder paste equivalent to the NIHON ALMIT paste or OMNIX OM-310 solder paste from Alpha metals. NOTE: Use no clean Flux, Do NOT water wash!Note also, that the temperature profile is based on the IC level and other components level only (without the shield can). So if we go on module perspective, above 245C profile should be acceptable.In fact the module temperature profile specifications tells, that you should be able to go beyond 240C (from 220C[60secs] to 250C[10secs]). The module temperature profile diagram is shown below.Bottom vie w Mother Board For RN-1318.5 mm For proper antennaPerformance p in s 36 through 44 mu st begrounded Top view4. U.FL connector. Use Hirose U.FL connector U.FL-R-SMT to for connecting external antennas. See RovingNetworks U.FL to SMA cable. Part number: RN-UFL-SMA65. Connection Status. GPIO-4, GPIO-5, GPIO-6 are available to drive a status LEDs. GPIO-6 indicates TCP/IPconnection status. This signal is ON high for an active connection, toggles fast to indicate no IP address and toggles slow indicates IP address OK but not connection. GPIO-4 indicates association status. High means not associated with a network, Off indicates associated and Internet access is OK. GPIO-5 toggles when data is transferred.6. Keep out areas. When designing your PCBavoid exposed trace and via beneath the module.7. Powering the module. The WiFly module canbe powered from either 3.0VDC batteries or 3.3VDC regulated power.3.0VDC battery power• Apply power to pin 20 (VDD-BATT) • Short pin 17 (3.3V-REG-OUT) to pin 18(3.3V-REG-IN) (battery boost mode) • 150mA of current at 3.3V available forexternal devices on pin 21 when in battery boost mode.3.3 VDC power• Apply power to pin 20(VDD-BATT) and pin 21 (VDD-IN)• Connect pin 18 (3.3V-REG-IN) to ground and leave pin 17 (3.3V-REG-OUT) unconnected.8. Achieving lowest power in sleep modeTo achieve the lowest power consumption (4uA) in sleep mode connect a weak pull down (100K resistor to GND) on the following pin.Pin 22 - DMA-TXIf GPIO-8 through GPIO-4 are being used to drive an output, connect a 100k pull down resistor. Any GPIOs not used (No connect) can be left floating.Pin 25 - GPIO-8 Pin 26 - GPIO-7 Pin 27 - GPIO-6 Pin 28 - GPIO-5 Pin 29 - GPIO-4Other GPIO lines: No pulldown needed, internal pulldown ( 80K ) already on chip.The power consumption in sleep mode without these signals connected to a pull down is 655uA9. Sensor Interfaces. Inputs must not exceed 1.2V. Sensitivity saturates at 400 mV.10. Adhoc mode and Restoring Factory Settings. Adhoc mode is controlled through GPIO-9. It is a good idea toconnect pin 24, GPIO-9 to a switch or jumper connected to a pull up. When GPIO-9 is driven high at power upBottom view: The re are twopad s o n th e module. Avoid ny exposed tracesin these area swill be RESTORED. This is useful for cases where the module is mis-configured and is no long responding.Compliance InformationFCC ID U3O-G2M5477 Part 15.247IC(canada) RSS-210CEEU ID # 0681REGU9M20901-1000-CRADIOEN 300328 V1.7.1 (10/2006)EMCEN 301489-1 V1.8.1 (04/2008), EN 301489-17 V1.3.2 (04/2008)SAFETYEN 60950-1:2001+A11:2004RoHs CompliantOrdering InformationPart Number DescriptionRN-131G Industrial Temperature (-30 to + 85 C ) With chip antenna and U.FL connectorRN-131C Commercial Temperature (0 to + 70 C ) With chip antenna and U.FL connector RN-131G-EVAL Development Kit for the RN-131G (Includes the RN-131G module)RN-134SuRFboard carrier PCB for RN-131, RS-232, LEDs, power regulator. Sensor connections RN-SMA4-RP 4” external antenna with reverse polarity SMA connector. Used with RN-UFL-SMA6RN-UFL-SMA6 6 inch cable with U.FL connector on one end and SMA on the otherFor other configurations, contact Roving Networks directly.Visit for current pricing and a list of distributors carrying our products.Copyright © 2009 Roving Networks. All rights reserved.Roving Networks reserves the right to make corrections, modifications, and other changes to its products, documentation and services at any time. Customers should obtain the latest relevant information before placing orders and should verify that such information is current and complete.Roving Networks assumes no liability for applications assistance or customer product design. Customers are responsible for their products and applications using Roving Networks components. To minimize the risks associated with customer products and applications, customers should provide adequate design and operating safeguards.RN-131G & RN-131C809 University Avenue • Los Gatos, CA 95032 • Tel (408) 395-6539 • ***********************~ page 11 ~ failure of the Roving Networks product would reasonably be expected to cause severe personal injury or death, unless officers of the parties have executed an agreement specifically governing such use.All other trademarks are property of their respective owners.。
Software-DefinedNetworking

Software⁃Defined Networking▶Zhili SunProfessor Zhili Sun is chair of communication networking at the Centre for Communication Systems Research,University of Sur⁃rey,UK.He received his BSc in mathematics from Nanjing Uni⁃versity,China,in 1982.He received his PhD in computer science from Lancaster University,UK,in 1991.From 1989to 1993,he worked as a postdoctoral research fellow at Queen Mary Universi⁃ty,London.He has worked in the capacity of principle investiga⁃tor and technical co ⁃coordinator on many projects within EU framework programs,within the EPSRC,and within industry.He has published more than 125papers in international journals andconference proceedings and has also authored book chapters.He was the sole author of Satellite Networking:Principles and Protocols,1st and 2nd editions,published by Wiley in 2005and 2014respectively.He was a contributing editor of IP Networking Over Next ⁃Generation Satellite Systems,published by Springer in 2008.He was also contributing editor of the textbook Satellite Communications Systems:Systems,Techniques and Technology,5th ed.,published by Wiley in 2009.His research interests include wire⁃less and sensor networks,satellite communications,mobile operating systems,Internet protocols and architecture,clod computing,SDN,multicast,and security.SSoftware⁃Defined Networking Zhili Sun,Jiandong Li,and Kun YangJune 2014Vol.12No.2ZTE COMMUNICATIONS 01oftware ⁃defined networking (SDN)is a promising technology for next ⁃generation networking and has attracted much attention from academics,network equipment manufacturer,network operators,andservice providers.It has found applications in mobile,data center,and enterprise networks.The SDN architecture has a centralized,programmable control plane that is separate from the data plane.SDN also provides the ability to control and manage virtualized resources and networks without requiring new hardware technologies.This is a major shift in networking technologies.The ITU ⁃T has been engaged in SDN standardization,and the European Telecommunications Standard Institute (ETSI)has been working on network function virtualization (NFV),which complements SDN.The Open Network Foundation (ONF)is a non⁃profit organization dedicated to promoting the adoption of open SDN.Recently,much work has been done on SDN to meet future network requirements.Network virtualization creates multiple virtual infrastruc⁃tures within a deployed infrastructure.These virtualized infra⁃structures can be created over a single physical infrastructure.Each virtual network can be isolated from each other and pro⁃grammed to meet user requirements in terms of resource func⁃tionality and capacity.This ensures that appropriate network resources are provided to the user.The SDN framework includes programmable control plane,data⁃forwarding plane abstraction,and methods to map the vir⁃tualized infrastructures onto the underlying physical network infrastructure.Key issues to be addressed are network resource isolation,network abstraction,topology awareness,quick reconfigurabili⁃ty,performance,programmability,management,mobility,secu⁃rity,and wireless network access.We received strong response to this call for papers on SDN from network operators,equipment manufacturers,universi⁃ties,and research institutes.Following a peer⁃review process,we selected nine papers for inclusion in this special issue.The first paper,“Network Function Virtualization Technolo⁃gy:Progess and Standardization ”discusses the main challeng⁃es in SDN faced by network carriers.This paper also discusses current standardization activities and research on NFV related to SDN.The second paper,“Service Parameter Exposure and Dy⁃namic Service Negotiation in SDN Environments,”discusses the ability of SDN to facilitate dynamic provisioning of network services.The paper focuses on two main aspects of the SDN framework:network abstraction and dynamic parameter expo⁃sure and negotiation.The third paper,“SDN⁃Based Broadband Network for Cloud Services,”discusses how SDN/NFV will be vital for construct⁃ing cloud⁃oriented broadband infrastructure,especially within data center networks and for interconnecting between data cen⁃▶Jiandong LiProfessor Jiandong Li received his BS,MS and PhD degrees from Xidian University,China,in 1982,1985and 1991.From 1990to 1994,he was an associate professor at Xidian University and be⁃came a full professor in 1994.In 1995,he undertook the role of PhD supervisor at Xidian University.From 2007to 2012,he was executive vice dean of the Graduate School of Xidian University.From 1997to 2006,he was dean of School of Telecommunica⁃tions Engineering,Xidian University.From 2001to 2003,he was a visiting professor at Cornell University.Professor Li has previ⁃ously been awarded the National Science Fund Award for Distin⁃guished Young Scholars.He is a senior member of the IEEE,a senior member of the China Institute of Electronics (CIE),and a fellow of the China Institute of Communica⁃tions (CIC).From 1993to 1994and then from 1999to 2000,he was a member of the Personal Communications Networks Specialist Group for China “863”Communication High Technology Program.He is also a member of the Broadband Wireless Mobile Com⁃munication Specialist Group,Ministry of Information Industry,China,and director of the Broadband Wireless IP Standard Work Group,Ministry of Information Industry,Chi⁃na.His main research interests include broadband wireless mobile communications,cognitive and software⁃defined radio,and wireless ad⁃hoc networks.▶Kun YangProfessor Kun Yang received his PhD degree from University Col⁃lege London.He received his MSc and BSc degrees from Jilin University,China.He is currently a chair professor in the School of Computer Science and Electronic Engineering,University of Essex,and leads the Network Convergence Laboratory there.Be⁃fore joining the University of Essex in 2003,he worked for sever⁃al years at University College London on EU research projects.His main research interests include heterogeneous wireless net⁃works,fixed⁃mobile convergence,future Internet technology and network virtualization,and cloud computing and networking.Hemanages research projects funded by sources such as UK EPSRC,EU FP7,and indus⁃try.He has published more than 150journal papers.He serves on the editorial boards of both IEEE and non⁃IEEE journals.He is a senior member of the IEEE and a fellow of IET.June 2014Vol.12No.2ZTE COMMUNICATIONS02Software⁃Defined NetworkingZhili Sun,Jiandong Li,and Kun Yangter networks.The authors propose SDN/NFV in broadband ac⁃cess to realize a virtualized residential gateway.The fourth paper,“D ⁃ZENIC:A Scalable Distributed SDN Controller Architecture,”describes a solution to minimizing the cost of network state distribution.This solution is a net⁃work control platform called D⁃ZNEIC that supports distribut⁃ed deployment and linear scale ⁃out by trading off complexity for scalabilityThe fifth paper,“Software⁃Defined Cellular Mobile Network Solutions,”describes current research on and solutions for soft⁃ware⁃defined cellular networks.It also discusses related speci⁃fications and possible research directions.The sixth paper,“SDN ⁃Based Data Offloading for 5G Mo⁃evolved with SDN abstraction in the mobile backhaul and en⁃hanced components that facilitate the move towards 5G.The seventh paper,“Integrating IPsec Within OpenFlow Ar⁃chitecture for Secure Group Communication,”discusses Inter⁃net Protocol security (IPsec)in the context of OpenFlow archi⁃tecture and SDN.The eighth paper,“Virtualized Wireless SDNs:Modelling Delay Through the Use of Stochastic Network Calculus,”de⁃scribes a delay model for a software ⁃defined wireless virtual network with some theoretical investigation into wireless SDN.The final paper,“Load Balancing Fat⁃Tree on Long⁃Lived Flows:Avoiding Congestions in Data Center Network,”de⁃scribes a dynamic load⁃balancing algorithm for fat tree in the。
5G网络高倒流问题优化研究

I G I T C W技术 研究Technology Study44DIGITCW2023.10从当前的网络发展形势来看,5G/LTE (长期演进)双网共存并存仍然是通信的主流趋势。
从用户角度出发,由于5G 网络的带宽大、网速快,使用感知更好。
倘若网络优化不完善、参数设置不合理等因素,导致大量5G 终端用户仍然驻留在4G 网络上,造成4G 网络负荷高、5G 网络空闲的高倒流现象,无法将5G 网络资源有效转换成为收入。
结合实际案例分析,我们摸索出了一套通过配置无线侧网络参数来解决5G 网络高倒流问题的策略和方法,提升5G 用户驻留比,提高5G 网络投资效益。
1 5G网络高倒流原因分析5G 网络高倒流小区定义:在4G 网络和5G 网络共同覆盖的区域,当该区域内的5G 用户产生的4G 流量占比大于30%,即定义为高倒流小区。
由于目前5G 网络处于建设期,网络覆盖范围相对于4G 网络存在一定的差距,其中一部分由于参数设置不合理,导致5G 网络的业务会回落至4G 网络,造成5G 流量倒流,5G 基站和4G 基站的负荷不均衡[1]。
1.1 5G网络覆盖分析运营商在5G 网络工程建设当中,为充分利用现有4G 杆塔资源进行建设,同时为降低投资,4G 网络与5G 网络基本都是共址建设。
前期在4G 网络建设过程中,为保证网络覆盖能力,天线多是占用最优势的点位,而5G 网络建设时只能依据现有天面剩余资源进行建设。
因此5G 天线安装时往往无法使用最佳天面位置,5G 网络覆盖能力与4G 网络相比存在较大差距,造成5G 网络深度覆盖能力弱于4G 网络。
1.2 无线参数分析4G/5G 的无线参数对5G 小区高倒流也存在影响,4G/5G 的互操作参数的配置策略会收缩5G 网络真实的覆盖范围。
包括空闲态的5G 用户驻留策略(4G/5G 网络间的小区重选流程)和连接态的驻留策略(4G/5G网络间的异系统切换与覆盖重定向流程)[2]。
主动队列管理下大时滞网络路径拥塞控制算法

文章编号:1006 - 9348 (2021)03 - 0268 - 04主动队列管理下大时滞网络路径拥塞控制算法刘国芳,张炜(四川大学锦江学院,四川眉山620860)摘要:与传统的无线网络相比,大时滞网络对路径拥塞环境下的无线通道交换具有较高的要求。
为此提出主动队列管理下 大时滞网络路径拥塞控制算法。
首先利用主动队列管理算法对相邻路由节点网络路径的拥塞情况展开预测,进而分析网络 路由节点的队列状态;然后以优化后续节点队列、传输距离以及传输方向为目的,从路径概率选择、分组丢弃函数、WSN蚁 群路由选取三个角度优化网络路径,从而实现路径拥塞控制。
实验结果表明,上述算法能够有效缩短网络的传输时滞,且能 耗和丢包率较低,具有较高的应用价值。
关键词:主动队列管理;无线通道;交换网络;路由;拥塞控制中图分类号:TP399 文献标识码:BPath Congestion Control Algorithm for Large TimeDelay Networks under Active Queue Management 第38卷第3期__________________________计算机仿真____________________________2021年3月LIU Guo -fan g,Z H A N G W ei(Jinjiang College,Sichuan University,Meishan Sichuan620860,China)ABSTRACT:In the large time - delay network,there is a high demand for wireless channel switching in path congestion environment.In this regard,this paper puts forward a path congestion control algorithm with active queue management for large delay networks.Firstly,based on the active queue management algorithm,the congestion of the network path of the adjacent routing nodes was predicted,and the queue status of the network routing nodes was analyzed.Secondly,the optimization of subsequent node queue,transmission distance and transmission direction were taken as indicators to optimize the network path from path probability selection,packet drop function and WSN ant colony routing selection.Eventually,path congestion control was completed.The simulation results show that the algorithm has short transmission delay,low energy consumption and packet loss rate,and high practicability.KEYW ORDS:Active queue management;Wireless channel;Switching network;Routing;Congestion controli引言无线通道交换网络是设定在监测区域中的一些小型路 由节点,通过无线通信的方式衍生出的具有多跳性、自组织 性的网络系统[|]。
北大考博辅导:北京大学管理科学与工程考博难度解析及经验分享

北大考博辅导:北京大学管理科学与工程考博难度解析及经验分享根据教育部学位与研究生教育发展中心最新公布的第四轮学科评估结果可知,全国共有133所开设管理科学与工程专业的大学参与了2017-2018管理科学与工程专业大学排名,其中排名第一的是清华大学,排名第二的是同济大学,排名第三的是国防科技大学。
作为北京大学实施国家“211工程”和“985工程”的重点学科,光华管理学院的管理科学与工程一级学科在历次全国学科评估中均名列第一。
下面是启道考博整理的关于北京大学管理科学与工程考博相关内容。
一、专业介绍管理科学与工程专业培养具备必要的数学、经济学、计算机应用基础,具有扎实的管理学科的基本理论和基本知识,具备用先进的管理思想、方法、组织和技术以及数学和计算机模型对运营管理、组织管理和技术管理中的问题进行分析、决策和组织实施的高级专门人才。
北京大学光华管理学院的管理科学与工程专业在博士招生方面,不区分研究方向120100 管理科学与工程研究方向:00.不区分研究方向此专业实行申请考核制。
二、考试内容北京大学管理科学与工程专业博士研究生招生为资格审查加综合考核形式,由笔试+专业面试构成。
其中,综合考核内容为:学院组织所报考专业专家小组对申请人进行综合评议。
同时根据招生计划,按照一定的比例择优确定复试名单。
初审结果和复试名单将于2019年3月邮件通知。
1、复试时间及方式:一般安排在3月下旬。
复试采取笔试加面试的方式进行差额甄选,对学生的学科背景、专业训练和素质、分析和操作技能、外语水平、思维能力、创新能力等各方面进行综合考察。
2、笔试:即基础能力测试,按报考专业分别测试。
(1)对于报考应用经济学专业的学生,第一部分是高级微观经济学;第二部分是高级宏观经济学和计量经济学;两部分分值各占50%。
(2)对于报考除应用经济学外其他专业的学生,考察内容为各专业(方向)4/6试题,考生按报考专业/方向答题。
笔试成绩作为考生是否能进入面试的依据,但不计入复试总成绩。
Procedia Computer Science

Unlocking the promise of mobile value-added services byapplying new collaborative business models Original ResearchArticleTechnological Forecasting and Social Change , Volume 77, Issue 4, May 2010, Pages 678-693Peng-Ting Chen, Joe Z. Cheng Show preview | Related articles | Related reference work articlesPurchase $ 41.95 602 Software performance simulation strategies for high-level embedded system design Original ResearchArticlePerformance Evaluation , Volume 67, Issue 8, August2010, Pages 717-739Zhonglei Wang, Andreas Herkersdorf Close preview | Related articles |Related reference work articlesAbstract | Figures/Tables | ReferencesAbstractAs most embedded applications are realized in software, softwareperformance estimation is a very important issue in embedded system design.In the last decades, instruction set simulators (ISSs) have become anessential part of an embedded software design process. However, ISSs areeither slow or very difficult to develop. With the advent of multiprocessorsystems and their ever-increasing complexity, the software simulation strategybased on ISSs is no longer efficient enough for exploring the large designspace of multiprocessor systems in early design phases. Motivated by thelimitations of ISSs, a lot of recent research activities focused on softwaresimulation strategies based on native execution. In this article, we firstintroduce some existing software performance simulation strategies as well asour own approach for source level simulation, called SciSim , and provide adiscussion about their benefits and limitations. The main contribution of thisarticle is to introduce a new software performance simulation approach, callediSciSim (intermediate Source code instrumentation based Simulation), whichachieves high estimation accuracy, high simulation speed and lowPurchase $ 41.95implementation complexity. All these advantages make iSciSim well-suited for system level design. To show the benefits of the proposed approach, we present a quantitative comparison between iSciSim and the other discussed techniques, using a set of benchmarks.Article Outline1. Introduction2. Software performance simulation strategies2.1. Instruction set simulators2.2. Binary (Assembly) level simulation2.3. Source level simulation2.4. IR level simulation3. The SciSim approach for source level simulation3.1. Source code instrumentation3.2. Simulation3.3. Advantages and limitations of SciSim4. The iSciSim approach for performance simulation of compiler-optimized embedded software4.1. Intermediate source code generation4.2. Intermediate source code instrumentation4.2.1. Machine code extraction and mapping list construction4.2.2. Basic block list construction4.2.3. Static timing analysis4.2.4. Back-annotation of timing information4.3. Simulation4.3.1. Dynamic timing analysis4.3.2. Hardware and software co-simulation in SystemC5. Experimental results5.1. Source code vs. ISC5.2. Benchmarking SW simulation strategies 5.3. Dynamic cache simulation5.4. Simulation in SystemC6. Discussions and conclusions AcknowledgementsReferencesVitae603Computer anxiety and ICT integration in English classesamong Iranian EFL teachers Original Research ArticleProcedia Computer Science, Volume 3, 2011, Pages 203-209Mehrak Rahimi, Samaneh YadollahiClose preview | PDF (190 K) | Related articles | Related reference work articlesAbstract | ReferencesAbstractThe purpose of this study was to determine Iranian EFL teachers’ level of computeranxiety and its relationship with ICT integration into English classes and teachers’ personalcharacteristics. Data were collected from 254 Iranian EFL teachers by Computer AnxietyRating Scale, ICT integration rating scale, and a personal information questionnaire. Theresults indicated a positive relationship between computer anxiety and age; however,computer anxiety, gender, and experience of teaching were not found to be related. Aninverse correlation was found between computer anxiety and ICT integration. While ICTintegration correlated negatively with age and years of teaching experience, it was notfound to be related to gender.604An environmental decision support system for spatialassessment and selective remediation OriginalResearch ArticleEnvironmental Modelling & Software, Volume 26, Issue 6,June 2011, Pages 751-760Purchase$ 19.95Robert N. Stewart, S. Thomas Purucker Close preview | Related articles | Related reference work articles Abstract | Figures/Tables | ReferencesAbstractSpatial Analysis and Decision Assistance (SADA) is a Windows freewareprogram that incorporates spatial assessment tools for effective environmentalremediation. The software integrates modules for GIS, visualization,geospatial analysis, statistical analysis, human health and ecological riskassessment, cost/benefit analysis, sampling design, and decision support.SADA began as a simple tool for integrating risk assessment with spatialmodeling tools. It has since evolved into a freeware product primarily targetedfor spatial site investigation and soil remediation design, though itsapplications have extended into many diverse environmental disciplines thatemphasize the spatial distribution of data. Because of the variety of algorithmsincorporated, the user interface is engineered in a consistent and scalablemanner to expose additional functionality without a burdensome increase incomplexity. The scalable environment permits it to be used for both applicationand research goals, especially investigating spatial aspects important forestimating environmental exposures and designing efficient remedial designs.The result is a mature infrastructure with considerable environmental decisionsupport capabilities. We provide an overview of SADA’s central functions anddiscuss how the problem of integrating diverse models in a tractable mannerwas addressed.Article OutlineNomenclature1. Introduction2. Methods2.1. Sample design2.2. Data management and exploratory data analysis2.3. Spatial autocorrelation2.4. Spatial models3. Results 3.1. Scalable interfacing and decision support3.2. Risk assessment3.2.1. Human health risk3.2.2. Ecological risk3.3. Selective remedial design4. Discussion and ConclusionAcknowledgementsReferencesResearch highlights ► SADA is mature software for data visualization, processing, analysis, and modeling. ► User interface balances functional scalability and decision support. ► Widely used due to free availability and shallow learning curve . ► Integration of spatial estimation and risk tools allows for rich decision support. 605 CoDBT: A multi-source dynamic binary translator using hardware –software collaborativetechniques Original Research ArticleJournal of Systems Architecture , Volume 56, Issue 10,October 2010, Pages 500-508Haibing Guan, Bo Liu, Zhengwei Qi, Yindong Yang,Hongbo Yang, Alei LiangShow preview | Related articles | Related reference work articles Purchase $ 31.50606 An analysis of third-party logistics performance and service provision Original Research ArticleTransportation Research Part E: Logistics andTransportation Review , Volume 47, Issue 4, July 2011, Pages 547-570Chiung-Lin Liu, Andrew C. Lyons Purchase$ 41.95Show preview | Related articles | Related reference work articles 607 Intelligent QoS management for multimedia services support in wireless mobile ad hoc networks OriginalResearch ArticleComputer Networks , Volume 54, Issue 10, 1 July 2010, Pages 1692-1706Lyes Khoukhi, Soumaya Cherkaoui Show preview | Related articles | Related reference work articlesPurchase $ 31.50 608 Limit to improvement: Myth or reality?: Empirical analysis of historical improvement on threetechnologies influential in the evolution ofcivilization Original Research ArticleTechnological Forecasting and Social Change ,Volume 77,Issue 5, June 2010, Pages 712-729 Yu Sang Chang, Seung Jin Baek Show preview| Supplementary content| Related articles | Relatedreference work articlesPurchase $ 41.95 609An enhanced concept map approach to improving children’s storytelling ability Original Research ArticleComputers & Education , Volume 56, Issue 3, April 2011, Pages 873-884Chen-Chung Liu, Holly S.L. Chen, Ju-Ling Shih, Guo-Ting Huang, Baw-Jhiune Liu Show preview | Related articles | Related reference work articlesPurchase $ 24.95610Human –computer interaction: A stable discipline, a nascent science, and the growth of the longtail Original Research ArticleInteracting with Computers , Volume 22, Issue 1, January 2010,Pages 13-27Alan Dix Show preview | Related articles | Related reference work articlesPurchase$ 31.50 611Post-agility: What follows a decade of agility? Original Research ArticleInformation and Software Technology , Volume 53, Issue 5,May 2011, Pages 543-555Richard Baskerville, Jan Pries-Heje, Sabine MadsenShow preview | Related articles | Related reference work articlesPurchase $ 19.95612Confidentiality checking an object-oriented class hierarchy Original Research ArticleNetwork Security , Volume 2010, Issue 3, March 2010, Pages 16-20S. Chandra, R.A KhanShow preview | Related articles | Related reference work articlesPurchase $ 41.95 613 European national news Computer Law & Security Review , Volume 26, Issue 5, September 2010, Pages 558-563 Mark Turner Show preview | Related articles | Related reference work articlesPurchase $ 41.95 614 System engineering approach in the EU Test Blanket Systems Design Integration Original Research ArticleFusion Engineering and Design , In Press, CorrectedProof , Available online 23 February 2011D. Panayotov, P. Sardain, L.V. Boccaccini, J.-F. Salavy, F.Cismondi, L. Jourd’Heuil Show preview | Related articles | Related reference work articlesPurchase $ 27.95 615A knowledge engineering approach to developing mindtools for context-aware ubiquitouslearning Original Research ArticleComputers & Education, Volume 54, Issue 1, January 2010, Pages 289-297Hui-Chun Chu, Gwo-Jen Hwang, Chin-Chung Tsai Show preview | Related articles |Related reference work articles Purchase $ 24.95616“Hi Father”, “Hi Mother”: A multimodal analysis of a significant, identity changing phone call mediated onTV Original Research Article Journal of Pragmatics, Volume 42, Issue 2, February 2010,Pages 426-442Pirkko Raudaskoski Show preview | Related articles | Related reference work articlesPurchase $ 19.95 617Iterative Bayesian fuzzy clustering toward flexible icon-based assistive software for the disabled OriginalResearch ArticleInformation Sciences , Volume 180, Issue 3, 1 February 2010, Pages 325-340Purchase$ 37.95Sang Wan Lee, Yong Soo Kim, Kwang-Hyun Park,Zeungnam BienShow preview | Related articles | Related reference work articles 618 A framework of composable access control features: Preserving separation of access control concerns from models to code Original Research ArticleComputers & Security , Volume 29, Issue 3, May 2010, Pages 350-379Jaime A. Pavlich-Mariscal, Steven A. Demurjian, LaurentD. MichelShow preview | Related articles | Related reference work articlesPurchase $ 31.50 619 Needs, affect, and interactive products – Facets ofuser experience Original Research ArticleInteracting with Computers , Volume 22, Issue 5, September 2010, Pages 353-362Marc Hassenzahl, Sarah Diefenbach, Anja Göritz Show preview | Related articles | Related reference work articlesPurchase $ 31.50 620 An IT perspective on integrated environmental modelling: The SIAT case Original Research ArticleEcological Modelling , Volume 221, Issue 18, 10 September 2010,Pages 2167-2176P.J.F.M. Verweij, M.J.R. Knapen, W.P. de Winter, J.J.F. Wien, J.A. te Roller, S. Sieber, J.M.L. JansenShow preview | Related articles | Related reference work articlesPurchase $ 31.50。
毛驴AWK-1137C系列工业无线客户端说明书

AWK-1137C SeriesIndustrial802.11a/b/g/n wireless clientFeatures and Benefits•IEEE802.11a/b/g/n compliant client•Comprehensive interfaces with one serial port and two Ethernet LAN ports•Millisecond-level Client-based Turbo Roaming1•2x2MIMO future-proof technology•Integrated robust antenna and power isolation•Anti-vibration design•Compact size for your industrial applications•Easy setup and deployment with AeroMagCertificationsIntroductionThe AWK-1137C is an ideal client solution for industrial wireless mobile applications.It enables WLAN connections for both Ethernet and serial devices,and is compliant with industrial standards and approvals covering operating temperature,power input voltage,surge,ESD,and vibration. The AWK-1137C can operate on either the2.4or5GHz bands,and is backwards-compatible with existing802.11a/b/g deployments to future-proof your wireless investments.Industrial Ruggedness•Integrated antenna and power isolation designed to provide500V insulation protection against external electrical interference•-40to75°C wide operating temperature models(-T)available for smooth wireless communication in harsh environmentsMobility-Oriented Design•Client-based Turbo Roaming1for<150ms roaming recovery time between APs•MIMO technology to ensure transmitting and receiving capability while on the move•Anti-vibration performance(with reference to IEC60068-2-6)Easy Integration•Semi-automatically configurable to reduce deployment cost•AeroMag support for error-free setup of your industrial applications’basic WLAN settings•Various communication interfaces for connecting to different types of devices•One-to-many NAT to simplify your machine setupSpecificationsWLAN InterfaceWLAN Standards802.11a/b/g/n802.11i Wireless SecurityModulation Type DSSSMIMO-OFDMOFDMFrequency Band for US(20MHz operating channels) 2.412to2.462GHz(11channels)5.180to5.240GHz(4channels)5.260to5.320GHz(4channels)21.The Turbo Roaming recovery time indicated herein is an average of test results documented,in optimized conditions,across APs configured with interference-free20-MHz RF channels,WPA2-PSK security,and default Turbo Roaming parameters.The clients are configured with3-channel roaming at100Kbps traffic load.Other conditions may also impact roaming performance.For more information about Turbo Roaming parameter settings,refer to the product manual.5.500to5.700GHz(11channels)35.745to5.825GHz(5channels)Frequency Band for EU(20MHz operating channels) 2.412to2.472GHz(13channels)5.180to5.240GHz(4channels)5.260to5.320GHz(4channels)35.500to5.700GHz(11channels)3Frequency Band for JP(20MHz operating channels) 2.412to2.484GHz(14channels)5.180to5.240GHz(4channels)5.260to5.320GHz(4channels)35.500to5.700GHz(11channels)3Wireless Security WEP encryption(64-bit and128-bit)WPA/WPA2-Enterprise(IEEE802.1X/RADIUS,TKIP,AES)WPA/WPA2-PersonalTransmission Rate802.11b:1to11Mbps802.11a/g:6to54Mbps802.11n:6.5to300MbpsTransmitter Power for802.11a23±1.5dBm@6to24Mbps21±1.5dBm@36Mbps20±1.5dBm@48Mbps18±1.5dBm@54MbpsTransmitter Power for802.11b26±1.5dBm@1Mbps26±1.5dBm@2Mbps26±1.5dBm@5.5Mbps25±1.5dBm@11MbpsTransmitter Power for802.11g23±1.5dBm@6to24Mbps22±1.5dBm@36Mbps20±1.5dBm@48Mbps19±1.5dBm@54MbpsTransmitter Power for802.11n(2.4GHz)23±1.5dBm@MCS0/820MHz17±1.5dBm@MCS7/1520MHz23±1.5dBm@MCS0/840MHz17±1.5dBm@MCS7/1540MHzTransmitter Power for802.11n(5GHz)23±1.5dBm@MCS0/820MHz18±1.5dBm@MCS7/1520MHz23±1.5dBm@MCS0/840MHz18±1.5dBm@MCS7/1540MHzTransmitter Power2.4GHz26dBm18dBm18dBm5GHz(UNII-1)23dBm23dBm23dBm5GHz(UNII-2)23dBm23dBm23dBm5GHz(UNII-2e)23dBm23dBm23dBm5GHz(UNII-3)23dBm––Note:Based on regional regulations,the maximum transmission power allowed onthe UNII bands is restricted in the firmware,as indicated above.Receiver Sensitivity for802.11a-90dBm@6Mbps-88dBm@9Mbps-87dBm@12Mbps-85dBm@18Mbps-81dBm@24Mbps-78dBm@36Mbps-74dBm@48Mbps-73dBm@54MbpsReceiver Sensitivity for802.11b-89dBm@1Mbps-89dBm@2Mbps-89dBm@5.5Mbps-88dBm@11MbpsReceiver Sensitivity for802.11g-88dBm@6Mbps-88dBm@9Mbps-88dBm@12Mbps-87dBm@18Mbps-84dBm@24Mbps-81dBm@36Mbps-77dBm@48Mbps-75dBm@54MbpsReceiver Sensitivity for802.11n(2.4GHz)-70dBm@MCS720MHz-70dBm@MCS1520MHz-64dBm@MCS740MHz-65dBm@MCS1540MHzReceiver Sensitivity for802.11n(5GHz)-69dBm@MCS720MHz-70dBm@MCS1520MHz-64dBm@MCS740MHz-66dBm@MCS1540MHzWLAN Operation Mode Client,Client-Router,Slave,SnifferAntenna External,2/2dBi,Omni-directional,2RP-SMA maleAntenna Connectors2RP-SMA femaleEthernet Interface10/100BaseT(X)Ports(RJ45connector)2Standards IEEE802.1Q for VLAN TaggingIEEE802.3for10BaseTIEEE802.3u for100BaseT(X)Ethernet Software FeaturesManagement DHCP Server/Client,HTTP,IPv4,LLDP,SMTP,SNMPv1/v2c/v3,Syslog,TCP/IP,Telnet,UDP,Proxy ARP,Wireless Search Utility,VLAN,MXview,MXconfigSecurity HTTPS/SSL,RADIUS,SSHTime Management NTP Client,SNTP ClientFirewallFilter ICMP,MAC address,IP protocol,Port-basedSerial InterfaceConnector DB9maleSerial Standards RS-232,RS-422/485,RS-232/422/485Operation Modes Disabled,Real COM,RFC2217,TCP Client,TCP Server,UDPData Bits5,6,7,8Stop Bits1,1.5,2Parity None,Even,Odd,Space,MarkFlow Control None,RTS/CTS,XON/XOFFBaudrate75bps to921.6kbpsSerial Data Log256KBSerial SignalsRS-232TxD,RxD,RTS,CTS,DCD,GND,DTR,DSRRS-422Tx+,Tx-,Rx+,Rx-,GNDRS-485-2w Data+,Data-,GNDRS-485-4w Tx+,Tx-,Rx+,Rx-,GNDLED InterfaceLED Indicators SYS,LAN1,LAN2,WLAN,SerialInput/Output InterfaceButtons Reset buttonPhysical CharacteristicsHousing MetalIP Rating IP30Dimensions77.1x115.5x26mm(3.035x4.55x1.024in)Weight470g(1.03lb)Installation DIN-rail mounting,Wall mounting(with optional kit)Power ParametersInput Voltage9to30VDCPower Connector1removable3-contact terminal block(s)Power Consumption11.7W(max.)Reverse Polarity Protection SupportedEnvironmental LimitsOperating Temperature Standard Models:0to60°C(32to140°F)Wide Temp.Models:-40to75°C(-40to167°F)Storage Temperature(package included)-40to85°C(-40to185°F)Ambient Relative Humidity5to95%(non-condensing)Standards and CertificationsEMC EN61000-6-2/-6-4,EN55032/24EMI CISPR22,FCC Part15B Class AEMS IEC61000-4-2ESD:Contact:8kV;Air:15kVIEC61000-4-3RS:80MHz to1GHz:10V/mIEC61000-4-4EFT:Power:2kV;Signal:1kVIEC61000-4-5Surge:Power:2kV;Signal:1kVIEC61000-4-6CS:10VIEC61000-4-8PFMFRadio ANATEL,EN300328,EN301489-1/17,EN301893,FCC ID SLE-1137C,MIC,NCC,SRRC,WPC,KC,RCMSafety EN60950-1,UL60950-1Vibration IEC60068-2-6MTBFTime1,125,942hrsStandards Telcordia SR332WarrantyWarranty Period5yearsDetails See /warranty Package ContentsDevice1x AWK-1137C Series wireless client Antenna2x2.4/5GHz antennaInstallation Kit1x DIN-rail kitDocumentation1x quick installation guide1x warranty card DimensionsOrdering InformationAWK-1137C-EU EU802.11a/b/g/n0to60°C AWK-1137C-EU-T EU802.11a/b/g/n-40to75°C AWK-1137C-JP JP802.11a/b/g/n0to60°C AWK-1137C-JP-T JP802.11a/b/g/n-40to75°C AWK-1137C-US US802.11a/b/g/n0to60°C AWK-1137C-US-T US802.11a/b/g/n-40to75°C Accessories(sold separately)AntennasANT-WDB-ANF-0407 2.4/5GHz,omni-directional antenna,4/7dBi,N-type(male)ANT-WDB-ANF-0609 2.4/5GHz,omni-directional antenna,6/9dBi,N-type(female)ANT-WDB-ANM-0306 2.4/5GHz,omni-directional antenna,3/6dBi,N-type(male)ANT-WDB-ANM-0407 2.4/5GHz,dual-band omni-directional antenna,4/7dBi,N-type(male)ANT-WDB-ANM-0502 2.4/5GHz,omni-directional antenna,5/2dBi,N-type(male)ANT-WDB-ANM-0609 2.4/5GHz,omni-directional antenna,6/9dBi,N-type(male)ANT-WDB-ARM-02 2.4/5GHz,omni-directional rubber duck antenna,2dBi,RP-SMA(male)ANT-WDB-ARM-0202 2.4/5GHz,panel antenna,2/2dBi,RP-SMA(male)ANT-WDB-PNF-1518 2.4/5GHz,panel antenna,15/18dBi,N-type(female)MAT-WDB-CA-RM-2-0205 2.4/5GHz,ceiling antenna,2/5dBi,MIMO2x2,RP-SMA-type(male)MAT-WDB-DA-RM-2-0203-1m 2.4/5GHz,desktop antenna,2/3dBi,MIMO2x2,RP-SMA-type(male),1m cableMAT-WDB-PA-NF-2-0708 2.4/5GHz,panel antenna,7/8dBi,MIMO2x2,N-type(female)ANT-WSB5-ANF-125GHz,omni-directional antenna,12dBi,N-type(female)ANT-WSB5-PNF-185GHz,directional panel antenna,18dBi,N-type(female)ANT-WSB-ANF-09 2.4GHz,omni-directional antenna,9dBi,N-type(female)ANT-WSB-PNF-12 2.4GHz,directional panel antenna,12dBi,N-type(female)ANT-WSB-PNF-18 2.4GHz,directional panel antenna,18dBi,N-type(female)ANT-WSB-AHRM-05-1.5m 2.4GHz,omni-directional/dipole antenna,5dBi,RP-SMA(male),1.5m cableWireless AdaptorsA-ADP-RJ458P-DB9F-ABC01DB9female to RJ45connector for the ABC-01Wireless Antenna CableA-CRF-RFRM-R4-150RF magnetic stand,RP-SMA(male)to RP-SMA(female),RG-174/U cable,1.5mA-CRF-RFRM-S2-60SS402cable,RP-SMA(male)to RP-SMA(female)A-CRF-RMNM-L1-300N-type(male)to RP SMA(male),LMR-195Lite cable,3mA-CRF-RMNM-L1-600N-type(male)to RP SMA(male),LMR-195Lite cable,6mA-CRF-RMNM-L1-900N-type(male)to RP SMA(male),LMR-195Lite cable,9mCRF-N0117SA-3M N-type(male)to RP SMA(male),CFD200cable,3mSurge ArrestorA-SA-NFNF-01Surge arrestor,N-type(female)to N-type(female)Wireless Terminating ResistorA-TRM-50-RM Termination resistor,50ohms,N-type maleWall-Mounting KitsWK-35-01Wall-mounting kit,2plates,6screws,35x44x2.5mm©Moxa Inc.All rights reserved.Updated Apr30,2019.This document and any portion thereof may not be reproduced or used in any manner whatsoever without the express written permission of Moxa Inc.Product specifications subject to change without notice.Visit our website for the most up-to-date product information.。
思科linksys-wrt310n无线n千兆路由器说明书

RouterModel: WRT310NIncredible coverage and performance for your Connected HomeThe Wireless-N Gigabit Router is really three devices in one box. First, there’s the Wireless Access Point, which lets you connect to the network without wires. There’s also a built-in 4-port full-duplex 10/100 Switch to connect your wired-Ethernet devices together. Finally, the Router function ties it all together and lets your whole network share a high-speed cable or DSL Internet connection.The Access Point built into the Router uses the very latest wireless networking technology, Wireless-N (draft 802.11n). By overlaying the signals of multiple radios, Wireless-N’s “Multiple In, Multiple Out” (MIMO) technology multiplies the effective data rate. Unlike ordinary wireless networking technologies that are confused by signal reflections, MIMO actually uses these reflections to increase the range and reduce “dead spots” in the wireless coverage area. The robust signal travels farther, maintaining wireless connections much farther than standard Wireless-G.With Wireless-N, the farther away you are, the more speed advantage you get. It works great with standard Wireless-G and -B equipment, but when both ends of the wireless link are Wireless-N, the router can increase the throughput even more by using twice as much radio band, yielding speeds far faster than standard Wireless-G. But unlike other speed-enhanced technologies, Wireless-N can dynamically enable this double-speed mode for Wireless-N devices, while still connecting to other wireless devices at their respective fastest speeds. In congested areas, the “good neighbor” mode ensures that the Router checks for other wireless devices in the area before gobbling up the radio band.To help protect your data and privacy, the Router can encode all wireless transmissions with industrial-strength 256-bit encryption. It can serve as your network’s DHCP Server, has a powerful SPI firewall to protect your PCs against intruders and most known Internet attacks, and supports VPN pass-through. Configuration is a snap with the web browser-based configuration utility.The incredible speed of Wireless-N makes it ideal for media-centric applications like streaming video, gaming, and Voice over IP telephony, and gives you plenty of headroom to run multiple media-intense data streams through the network at the same time, with no degradation in performance. With the Linksys Wireless-N Gigabit Router at the center of your home or office network, you can share a high-speed Internet connection, files, printers, and multi-player games, and run media-intensive applications at faster than 10/100 wired network speeds, without the hassle of stringing wires!DATASHEETInternet-sharing Router and 4-port Gigabit Switch, with a built-in speed and range enhanced Wireless Access PointMIMO technology uses multiple radios per band to create robust signals for maximum range and speed, with reduced dead spots Much faster than Wireless-G, but also works great with Wireless-G and -B devicesWireless signals are protected by industrial-strength encryption, and your network is protected from Internet attacks by a powerful SPIfirewallA Division of Cisco Systems, Inc. 121 TheoryIrvine, CA 92617 USA E-mail: *****************Web:Linksys products are available in more than 50 countries, supported by 12 Linksys Regional Offices throughout the world. For a complete list of local Linksys Sales and Technical Support contacts, visit our worldwide website at The maximum performance for wireless is derived from IEEE Standard 802.11 specifications. Actual performance can vary, including lower wireless network capacity, data throughput rate, range and coverage. Performance depends on many factors, conditions and variables, including distance from the access point, volume of network traffic, building materials and construction, operating system used, mix of wireless products used, interference and other adverse conditions.Check the product package and contents for specific features supported. Specifications are subject to change without notice.Linksys is a registered trademark or trademark of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries.Copyright © 2007 Cisco Systems, Inc. All rights reserved. Other brands and product names are trademarks or registered trademarks of their respective holders.7120510NC-JLModel: WRT310NSpecifications Model WRT310NStandards Draft 802.11n v2.0, 802.11g, 802.11b, 802.3, 802.3u Ports Power, Internet, Ethernet Buttons Reset, Wi-Fi Protected SetupLEDsEthernet (1-4), Wi-Fi Protected Setup, Wireless, Internet, Power Cabling Type CAT 5e # of Antennas 3Detachable (Y/N) No RF Pwr (EIRP) in dBm 17UPnP able/cert AbleSecurity Features Up to 256-Bit Wireless Encryption, SPI Firewall Security Key Bits 64, 128, 256Environmental Dimensions 7.95" x 1.34" x 6.30" (202 x 34 x 160 mm)Weight 11.99 oz (0.34 kg)Power12V, 1ACertification FCC, CE, IC-03Operating Temp. 32 to 104°F (0 to 40°C)Storage Temp.-4 to 158°F (-20 to 70°C)Operating Humidity 10 to 85% Noncondensing Storage Humidity5 to 90% NoncondensingPackage ContentsWireless-N Gigabit RouterSetup CD-ROM with Norton Internet Security User Guide on CD-ROM Quick InstallEthernet Network Cable Power AdapterMinimum RequirementsInternet Explorer 6.0 or Firefox 1.0CD-ROM DriveWindows XP or VistaWired or Wireless* Network Adapter*For optimum wireless performance, we recommend Linksys Wireless-N adapters (WPC300N, WMP300N, or WUSB300N).••••••••••FeaturesComplies with IEEE draft 802.11n standardsBlazing fast wireless speeds for high bandwidth applications such as video streaming or file sharing ••。
3GPP TS 36.331 V13.2.0 (2016-06)

3GPP TS 36.331 V13.2.0 (2016-06)Technical Specification3rd Generation Partnership Project;Technical Specification Group Radio Access Network;Evolved Universal Terrestrial Radio Access (E-UTRA);Radio Resource Control (RRC);Protocol specification(Release 13)The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented.This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organizational Partners' Publications Offices.KeywordsUMTS, radio3GPPPostal address3GPP support office address650 Route des Lucioles - Sophia AntipolisValbonne - FRANCETel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16InternetCopyright NotificationNo part may be reproduced except as authorized by written permission.The copyright and the foregoing restriction extend to reproduction in all media.© 2016, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC).All rights reserved.UMTS™ is a Trade Mark of ETSI registered for the benefit of its members3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational PartnersLTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM AssociationBluetooth® is a Trade Mark of the Bluetooth SIG registered for the benefit of its membersContentsForeword (18)1Scope (19)2References (19)3Definitions, symbols and abbreviations (22)3.1Definitions (22)3.2Abbreviations (24)4General (27)4.1Introduction (27)4.2Architecture (28)4.2.1UE states and state transitions including inter RAT (28)4.2.2Signalling radio bearers (29)4.3Services (30)4.3.1Services provided to upper layers (30)4.3.2Services expected from lower layers (30)4.4Functions (30)5Procedures (32)5.1General (32)5.1.1Introduction (32)5.1.2General requirements (32)5.2System information (33)5.2.1Introduction (33)5.2.1.1General (33)5.2.1.2Scheduling (34)5.2.1.2a Scheduling for NB-IoT (34)5.2.1.3System information validity and notification of changes (35)5.2.1.4Indication of ETWS notification (36)5.2.1.5Indication of CMAS notification (37)5.2.1.6Notification of EAB parameters change (37)5.2.1.7Access Barring parameters change in NB-IoT (37)5.2.2System information acquisition (38)5.2.2.1General (38)5.2.2.2Initiation (38)5.2.2.3System information required by the UE (38)5.2.2.4System information acquisition by the UE (39)5.2.2.5Essential system information missing (42)5.2.2.6Actions upon reception of the MasterInformationBlock message (42)5.2.2.7Actions upon reception of the SystemInformationBlockType1 message (42)5.2.2.8Actions upon reception of SystemInformation messages (44)5.2.2.9Actions upon reception of SystemInformationBlockType2 (44)5.2.2.10Actions upon reception of SystemInformationBlockType3 (45)5.2.2.11Actions upon reception of SystemInformationBlockType4 (45)5.2.2.12Actions upon reception of SystemInformationBlockType5 (45)5.2.2.13Actions upon reception of SystemInformationBlockType6 (45)5.2.2.14Actions upon reception of SystemInformationBlockType7 (45)5.2.2.15Actions upon reception of SystemInformationBlockType8 (45)5.2.2.16Actions upon reception of SystemInformationBlockType9 (46)5.2.2.17Actions upon reception of SystemInformationBlockType10 (46)5.2.2.18Actions upon reception of SystemInformationBlockType11 (46)5.2.2.19Actions upon reception of SystemInformationBlockType12 (47)5.2.2.20Actions upon reception of SystemInformationBlockType13 (48)5.2.2.21Actions upon reception of SystemInformationBlockType14 (48)5.2.2.22Actions upon reception of SystemInformationBlockType15 (48)5.2.2.23Actions upon reception of SystemInformationBlockType16 (48)5.2.2.24Actions upon reception of SystemInformationBlockType17 (48)5.2.2.25Actions upon reception of SystemInformationBlockType18 (48)5.2.2.26Actions upon reception of SystemInformationBlockType19 (49)5.2.3Acquisition of an SI message (49)5.2.3a Acquisition of an SI message by BL UE or UE in CE or a NB-IoT UE (50)5.3Connection control (50)5.3.1Introduction (50)5.3.1.1RRC connection control (50)5.3.1.2Security (52)5.3.1.2a RN security (53)5.3.1.3Connected mode mobility (53)5.3.1.4Connection control in NB-IoT (54)5.3.2Paging (55)5.3.2.1General (55)5.3.2.2Initiation (55)5.3.2.3Reception of the Paging message by the UE (55)5.3.3RRC connection establishment (56)5.3.3.1General (56)5.3.3.1a Conditions for establishing RRC Connection for sidelink communication/ discovery (58)5.3.3.2Initiation (59)5.3.3.3Actions related to transmission of RRCConnectionRequest message (63)5.3.3.3a Actions related to transmission of RRCConnectionResumeRequest message (64)5.3.3.4Reception of the RRCConnectionSetup by the UE (64)5.3.3.4a Reception of the RRCConnectionResume by the UE (66)5.3.3.5Cell re-selection while T300, T302, T303, T305, T306, or T308 is running (68)5.3.3.6T300 expiry (68)5.3.3.7T302, T303, T305, T306, or T308 expiry or stop (69)5.3.3.8Reception of the RRCConnectionReject by the UE (70)5.3.3.9Abortion of RRC connection establishment (71)5.3.3.10Handling of SSAC related parameters (71)5.3.3.11Access barring check (72)5.3.3.12EAB check (73)5.3.3.13Access barring check for ACDC (73)5.3.3.14Access Barring check for NB-IoT (74)5.3.4Initial security activation (75)5.3.4.1General (75)5.3.4.2Initiation (76)5.3.4.3Reception of the SecurityModeCommand by the UE (76)5.3.5RRC connection reconfiguration (77)5.3.5.1General (77)5.3.5.2Initiation (77)5.3.5.3Reception of an RRCConnectionReconfiguration not including the mobilityControlInfo by theUE (77)5.3.5.4Reception of an RRCConnectionReconfiguration including the mobilityControlInfo by the UE(handover) (79)5.3.5.5Reconfiguration failure (83)5.3.5.6T304 expiry (handover failure) (83)5.3.5.7Void (84)5.3.5.7a T307 expiry (SCG change failure) (84)5.3.5.8Radio Configuration involving full configuration option (84)5.3.6Counter check (86)5.3.6.1General (86)5.3.6.2Initiation (86)5.3.6.3Reception of the CounterCheck message by the UE (86)5.3.7RRC connection re-establishment (87)5.3.7.1General (87)5.3.7.2Initiation (87)5.3.7.3Actions following cell selection while T311 is running (88)5.3.7.4Actions related to transmission of RRCConnectionReestablishmentRequest message (89)5.3.7.5Reception of the RRCConnectionReestablishment by the UE (89)5.3.7.6T311 expiry (91)5.3.7.7T301 expiry or selected cell no longer suitable (91)5.3.7.8Reception of RRCConnectionReestablishmentReject by the UE (91)5.3.8RRC connection release (92)5.3.8.1General (92)5.3.8.2Initiation (92)5.3.8.3Reception of the RRCConnectionRelease by the UE (92)5.3.8.4T320 expiry (93)5.3.9RRC connection release requested by upper layers (93)5.3.9.1General (93)5.3.9.2Initiation (93)5.3.10Radio resource configuration (93)5.3.10.0General (93)5.3.10.1SRB addition/ modification (94)5.3.10.2DRB release (95)5.3.10.3DRB addition/ modification (95)5.3.10.3a1DC specific DRB addition or reconfiguration (96)5.3.10.3a2LWA specific DRB addition or reconfiguration (98)5.3.10.3a3LWIP specific DRB addition or reconfiguration (98)5.3.10.3a SCell release (99)5.3.10.3b SCell addition/ modification (99)5.3.10.3c PSCell addition or modification (99)5.3.10.4MAC main reconfiguration (99)5.3.10.5Semi-persistent scheduling reconfiguration (100)5.3.10.6Physical channel reconfiguration (100)5.3.10.7Radio Link Failure Timers and Constants reconfiguration (101)5.3.10.8Time domain measurement resource restriction for serving cell (101)5.3.10.9Other configuration (102)5.3.10.10SCG reconfiguration (103)5.3.10.11SCG dedicated resource configuration (104)5.3.10.12Reconfiguration SCG or split DRB by drb-ToAddModList (105)5.3.10.13Neighbour cell information reconfiguration (105)5.3.10.14Void (105)5.3.10.15Sidelink dedicated configuration (105)5.3.10.16T370 expiry (106)5.3.11Radio link failure related actions (107)5.3.11.1Detection of physical layer problems in RRC_CONNECTED (107)5.3.11.2Recovery of physical layer problems (107)5.3.11.3Detection of radio link failure (107)5.3.12UE actions upon leaving RRC_CONNECTED (109)5.3.13UE actions upon PUCCH/ SRS release request (110)5.3.14Proximity indication (110)5.3.14.1General (110)5.3.14.2Initiation (111)5.3.14.3Actions related to transmission of ProximityIndication message (111)5.3.15Void (111)5.4Inter-RAT mobility (111)5.4.1Introduction (111)5.4.2Handover to E-UTRA (112)5.4.2.1General (112)5.4.2.2Initiation (112)5.4.2.3Reception of the RRCConnectionReconfiguration by the UE (112)5.4.2.4Reconfiguration failure (114)5.4.2.5T304 expiry (handover to E-UTRA failure) (114)5.4.3Mobility from E-UTRA (114)5.4.3.1General (114)5.4.3.2Initiation (115)5.4.3.3Reception of the MobilityFromEUTRACommand by the UE (115)5.4.3.4Successful completion of the mobility from E-UTRA (116)5.4.3.5Mobility from E-UTRA failure (117)5.4.4Handover from E-UTRA preparation request (CDMA2000) (117)5.4.4.1General (117)5.4.4.2Initiation (118)5.4.4.3Reception of the HandoverFromEUTRAPreparationRequest by the UE (118)5.4.5UL handover preparation transfer (CDMA2000) (118)5.4.5.1General (118)5.4.5.2Initiation (118)5.4.5.3Actions related to transmission of the ULHandoverPreparationTransfer message (119)5.4.5.4Failure to deliver the ULHandoverPreparationTransfer message (119)5.4.6Inter-RAT cell change order to E-UTRAN (119)5.4.6.1General (119)5.4.6.2Initiation (119)5.4.6.3UE fails to complete an inter-RAT cell change order (119)5.5Measurements (120)5.5.1Introduction (120)5.5.2Measurement configuration (121)5.5.2.1General (121)5.5.2.2Measurement identity removal (122)5.5.2.2a Measurement identity autonomous removal (122)5.5.2.3Measurement identity addition/ modification (123)5.5.2.4Measurement object removal (124)5.5.2.5Measurement object addition/ modification (124)5.5.2.6Reporting configuration removal (126)5.5.2.7Reporting configuration addition/ modification (127)5.5.2.8Quantity configuration (127)5.5.2.9Measurement gap configuration (127)5.5.2.10Discovery signals measurement timing configuration (128)5.5.2.11RSSI measurement timing configuration (128)5.5.3Performing measurements (128)5.5.3.1General (128)5.5.3.2Layer 3 filtering (131)5.5.4Measurement report triggering (131)5.5.4.1General (131)5.5.4.2Event A1 (Serving becomes better than threshold) (135)5.5.4.3Event A2 (Serving becomes worse than threshold) (136)5.5.4.4Event A3 (Neighbour becomes offset better than PCell/ PSCell) (136)5.5.4.5Event A4 (Neighbour becomes better than threshold) (137)5.5.4.6Event A5 (PCell/ PSCell becomes worse than threshold1 and neighbour becomes better thanthreshold2) (138)5.5.4.6a Event A6 (Neighbour becomes offset better than SCell) (139)5.5.4.7Event B1 (Inter RAT neighbour becomes better than threshold) (139)5.5.4.8Event B2 (PCell becomes worse than threshold1 and inter RAT neighbour becomes better thanthreshold2) (140)5.5.4.9Event C1 (CSI-RS resource becomes better than threshold) (141)5.5.4.10Event C2 (CSI-RS resource becomes offset better than reference CSI-RS resource) (141)5.5.4.11Event W1 (WLAN becomes better than a threshold) (142)5.5.4.12Event W2 (All WLAN inside WLAN mobility set becomes worse than threshold1 and a WLANoutside WLAN mobility set becomes better than threshold2) (142)5.5.4.13Event W3 (All WLAN inside WLAN mobility set becomes worse than a threshold) (143)5.5.5Measurement reporting (144)5.5.6Measurement related actions (148)5.5.6.1Actions upon handover and re-establishment (148)5.5.6.2Speed dependant scaling of measurement related parameters (149)5.5.7Inter-frequency RSTD measurement indication (149)5.5.7.1General (149)5.5.7.2Initiation (150)5.5.7.3Actions related to transmission of InterFreqRSTDMeasurementIndication message (150)5.6Other (150)5.6.0General (150)5.6.1DL information transfer (151)5.6.1.1General (151)5.6.1.2Initiation (151)5.6.1.3Reception of the DLInformationTransfer by the UE (151)5.6.2UL information transfer (151)5.6.2.1General (151)5.6.2.2Initiation (151)5.6.2.3Actions related to transmission of ULInformationTransfer message (152)5.6.2.4Failure to deliver ULInformationTransfer message (152)5.6.3UE capability transfer (152)5.6.3.1General (152)5.6.3.2Initiation (153)5.6.3.3Reception of the UECapabilityEnquiry by the UE (153)5.6.4CSFB to 1x Parameter transfer (157)5.6.4.1General (157)5.6.4.2Initiation (157)5.6.4.3Actions related to transmission of CSFBParametersRequestCDMA2000 message (157)5.6.4.4Reception of the CSFBParametersResponseCDMA2000 message (157)5.6.5UE Information (158)5.6.5.1General (158)5.6.5.2Initiation (158)5.6.5.3Reception of the UEInformationRequest message (158)5.6.6 Logged Measurement Configuration (159)5.6.6.1General (159)5.6.6.2Initiation (160)5.6.6.3Reception of the LoggedMeasurementConfiguration by the UE (160)5.6.6.4T330 expiry (160)5.6.7 Release of Logged Measurement Configuration (160)5.6.7.1General (160)5.6.7.2Initiation (160)5.6.8 Measurements logging (161)5.6.8.1General (161)5.6.8.2Initiation (161)5.6.9In-device coexistence indication (163)5.6.9.1General (163)5.6.9.2Initiation (164)5.6.9.3Actions related to transmission of InDeviceCoexIndication message (164)5.6.10UE Assistance Information (165)5.6.10.1General (165)5.6.10.2Initiation (166)5.6.10.3Actions related to transmission of UEAssistanceInformation message (166)5.6.11 Mobility history information (166)5.6.11.1General (166)5.6.11.2Initiation (166)5.6.12RAN-assisted WLAN interworking (167)5.6.12.1General (167)5.6.12.2Dedicated WLAN offload configuration (167)5.6.12.3WLAN offload RAN evaluation (167)5.6.12.4T350 expiry or stop (167)5.6.12.5Cell selection/ re-selection while T350 is running (168)5.6.13SCG failure information (168)5.6.13.1General (168)5.6.13.2Initiation (168)5.6.13.3Actions related to transmission of SCGFailureInformation message (168)5.6.14LTE-WLAN Aggregation (169)5.6.14.1Introduction (169)5.6.14.2Reception of LWA configuration (169)5.6.14.3Release of LWA configuration (170)5.6.15WLAN connection management (170)5.6.15.1Introduction (170)5.6.15.2WLAN connection status reporting (170)5.6.15.2.1General (170)5.6.15.2.2Initiation (171)5.6.15.2.3Actions related to transmission of WLANConnectionStatusReport message (171)5.6.15.3T351 Expiry (WLAN connection attempt timeout) (171)5.6.15.4WLAN status monitoring (171)5.6.16RAN controlled LTE-WLAN interworking (172)5.6.16.1General (172)5.6.16.2WLAN traffic steering command (172)5.6.17LTE-WLAN aggregation with IPsec tunnel (173)5.6.17.1General (173)5.7Generic error handling (174)5.7.1General (174)5.7.2ASN.1 violation or encoding error (174)5.7.3Field set to a not comprehended value (174)5.7.4Mandatory field missing (174)5.7.5Not comprehended field (176)5.8MBMS (176)5.8.1Introduction (176)5.8.1.1General (176)5.8.1.2Scheduling (176)5.8.1.3MCCH information validity and notification of changes (176)5.8.2MCCH information acquisition (178)5.8.2.1General (178)5.8.2.2Initiation (178)5.8.2.3MCCH information acquisition by the UE (178)5.8.2.4Actions upon reception of the MBSFNAreaConfiguration message (178)5.8.2.5Actions upon reception of the MBMSCountingRequest message (179)5.8.3MBMS PTM radio bearer configuration (179)5.8.3.1General (179)5.8.3.2Initiation (179)5.8.3.3MRB establishment (179)5.8.3.4MRB release (179)5.8.4MBMS Counting Procedure (179)5.8.4.1General (179)5.8.4.2Initiation (180)5.8.4.3Reception of the MBMSCountingRequest message by the UE (180)5.8.5MBMS interest indication (181)5.8.5.1General (181)5.8.5.2Initiation (181)5.8.5.3Determine MBMS frequencies of interest (182)5.8.5.4Actions related to transmission of MBMSInterestIndication message (183)5.8a SC-PTM (183)5.8a.1Introduction (183)5.8a.1.1General (183)5.8a.1.2SC-MCCH scheduling (183)5.8a.1.3SC-MCCH information validity and notification of changes (183)5.8a.1.4Procedures (184)5.8a.2SC-MCCH information acquisition (184)5.8a.2.1General (184)5.8a.2.2Initiation (184)5.8a.2.3SC-MCCH information acquisition by the UE (184)5.8a.2.4Actions upon reception of the SCPTMConfiguration message (185)5.8a.3SC-PTM radio bearer configuration (185)5.8a.3.1General (185)5.8a.3.2Initiation (185)5.8a.3.3SC-MRB establishment (185)5.8a.3.4SC-MRB release (185)5.9RN procedures (186)5.9.1RN reconfiguration (186)5.9.1.1General (186)5.9.1.2Initiation (186)5.9.1.3Reception of the RNReconfiguration by the RN (186)5.10Sidelink (186)5.10.1Introduction (186)5.10.1a Conditions for sidelink communication operation (187)5.10.2Sidelink UE information (188)5.10.2.1General (188)5.10.2.2Initiation (189)5.10.2.3Actions related to transmission of SidelinkUEInformation message (193)5.10.3Sidelink communication monitoring (195)5.10.6Sidelink discovery announcement (198)5.10.6a Sidelink discovery announcement pool selection (201)5.10.6b Sidelink discovery announcement reference carrier selection (201)5.10.7Sidelink synchronisation information transmission (202)5.10.7.1General (202)5.10.7.2Initiation (203)5.10.7.3Transmission of SLSS (204)5.10.7.4Transmission of MasterInformationBlock-SL message (205)5.10.7.5Void (206)5.10.8Sidelink synchronisation reference (206)5.10.8.1General (206)5.10.8.2Selection and reselection of synchronisation reference UE (SyncRef UE) (206)5.10.9Sidelink common control information (207)5.10.9.1General (207)5.10.9.2Actions related to reception of MasterInformationBlock-SL message (207)5.10.10Sidelink relay UE operation (207)5.10.10.1General (207)5.10.10.2AS-conditions for relay related sidelink communication transmission by sidelink relay UE (207)5.10.10.3AS-conditions for relay PS related sidelink discovery transmission by sidelink relay UE (208)5.10.10.4Sidelink relay UE threshold conditions (208)5.10.11Sidelink remote UE operation (208)5.10.11.1General (208)5.10.11.2AS-conditions for relay related sidelink communication transmission by sidelink remote UE (208)5.10.11.3AS-conditions for relay PS related sidelink discovery transmission by sidelink remote UE (209)5.10.11.4Selection and reselection of sidelink relay UE (209)5.10.11.5Sidelink remote UE threshold conditions (210)6Protocol data units, formats and parameters (tabular & ASN.1) (210)6.1General (210)6.2RRC messages (212)6.2.1General message structure (212)–EUTRA-RRC-Definitions (212)–BCCH-BCH-Message (212)–BCCH-DL-SCH-Message (212)–BCCH-DL-SCH-Message-BR (213)–MCCH-Message (213)–PCCH-Message (213)–DL-CCCH-Message (214)–DL-DCCH-Message (214)–UL-CCCH-Message (214)–UL-DCCH-Message (215)–SC-MCCH-Message (215)6.2.2Message definitions (216)–CounterCheck (216)–CounterCheckResponse (217)–CSFBParametersRequestCDMA2000 (217)–CSFBParametersResponseCDMA2000 (218)–DLInformationTransfer (218)–HandoverFromEUTRAPreparationRequest (CDMA2000) (219)–InDeviceCoexIndication (220)–InterFreqRSTDMeasurementIndication (222)–LoggedMeasurementConfiguration (223)–MasterInformationBlock (225)–MBMSCountingRequest (226)–MBMSCountingResponse (226)–MBMSInterestIndication (227)–MBSFNAreaConfiguration (228)–MeasurementReport (228)–MobilityFromEUTRACommand (229)–Paging (232)–ProximityIndication (233)–RNReconfiguration (234)–RNReconfigurationComplete (234)–RRCConnectionReconfiguration (235)–RRCConnectionReconfigurationComplete (240)–RRCConnectionReestablishment (241)–RRCConnectionReestablishmentComplete (241)–RRCConnectionReestablishmentReject (242)–RRCConnectionReestablishmentRequest (243)–RRCConnectionReject (243)–RRCConnectionRelease (244)–RRCConnectionResume (248)–RRCConnectionResumeComplete (249)–RRCConnectionResumeRequest (250)–RRCConnectionRequest (250)–RRCConnectionSetup (251)–RRCConnectionSetupComplete (252)–SCGFailureInformation (253)–SCPTMConfiguration (254)–SecurityModeCommand (255)–SecurityModeComplete (255)–SecurityModeFailure (256)–SidelinkUEInformation (256)–SystemInformation (258)–SystemInformationBlockType1 (259)–UEAssistanceInformation (264)–UECapabilityEnquiry (265)–UECapabilityInformation (266)–UEInformationRequest (267)–UEInformationResponse (267)–ULHandoverPreparationTransfer (CDMA2000) (273)–ULInformationTransfer (274)–WLANConnectionStatusReport (274)6.3RRC information elements (275)6.3.1System information blocks (275)–SystemInformationBlockType2 (275)–SystemInformationBlockType3 (279)–SystemInformationBlockType4 (282)–SystemInformationBlockType5 (283)–SystemInformationBlockType6 (287)–SystemInformationBlockType7 (289)–SystemInformationBlockType8 (290)–SystemInformationBlockType9 (295)–SystemInformationBlockType10 (295)–SystemInformationBlockType11 (296)–SystemInformationBlockType12 (297)–SystemInformationBlockType13 (297)–SystemInformationBlockType14 (298)–SystemInformationBlockType15 (298)–SystemInformationBlockType16 (299)–SystemInformationBlockType17 (300)–SystemInformationBlockType18 (301)–SystemInformationBlockType19 (301)–SystemInformationBlockType20 (304)6.3.2Radio resource control information elements (304)–AntennaInfo (304)–AntennaInfoUL (306)–CQI-ReportConfig (307)–CQI-ReportPeriodicProcExtId (314)–CrossCarrierSchedulingConfig (314)–CSI-IM-Config (315)–CSI-IM-ConfigId (315)–CSI-RS-Config (317)–CSI-RS-ConfigEMIMO (318)–CSI-RS-ConfigNZP (319)–CSI-RS-ConfigNZPId (320)–CSI-RS-ConfigZP (321)–CSI-RS-ConfigZPId (321)–DMRS-Config (321)–DRB-Identity (322)–EPDCCH-Config (322)–EIMTA-MainConfig (324)–LogicalChannelConfig (325)–LWA-Configuration (326)–LWIP-Configuration (326)–RCLWI-Configuration (327)–MAC-MainConfig (327)–P-C-AndCBSR (332)–PDCCH-ConfigSCell (333)–PDCP-Config (334)–PDSCH-Config (337)–PDSCH-RE-MappingQCL-ConfigId (339)–PHICH-Config (339)–PhysicalConfigDedicated (339)–P-Max (344)–PRACH-Config (344)–PresenceAntennaPort1 (346)–PUCCH-Config (347)–PUSCH-Config (351)–RACH-ConfigCommon (355)–RACH-ConfigDedicated (357)–RadioResourceConfigCommon (358)–RadioResourceConfigDedicated (362)–RLC-Config (367)–RLF-TimersAndConstants (369)–RN-SubframeConfig (370)–SchedulingRequestConfig (371)–SoundingRS-UL-Config (372)–SPS-Config (375)–TDD-Config (376)–TimeAlignmentTimer (377)–TPC-PDCCH-Config (377)–TunnelConfigLWIP (378)–UplinkPowerControl (379)–WLAN-Id-List (382)–WLAN-MobilityConfig (382)6.3.3Security control information elements (382)–NextHopChainingCount (382)–SecurityAlgorithmConfig (383)–ShortMAC-I (383)6.3.4Mobility control information elements (383)–AdditionalSpectrumEmission (383)–ARFCN-ValueCDMA2000 (383)–ARFCN-ValueEUTRA (384)–ARFCN-ValueGERAN (384)–ARFCN-ValueUTRA (384)–BandclassCDMA2000 (384)–BandIndicatorGERAN (385)–CarrierFreqCDMA2000 (385)–CarrierFreqGERAN (385)–CellIndexList (387)–CellReselectionPriority (387)–CellSelectionInfoCE (387)–CellReselectionSubPriority (388)–CSFB-RegistrationParam1XRTT (388)–CellGlobalIdEUTRA (389)–CellGlobalIdUTRA (389)–CellGlobalIdGERAN (390)–CellGlobalIdCDMA2000 (390)–CellSelectionInfoNFreq (391)–CSG-Identity (391)–FreqBandIndicator (391)–MobilityControlInfo (391)–MobilityParametersCDMA2000 (1xRTT) (393)–MobilityStateParameters (394)–MultiBandInfoList (394)–NS-PmaxList (394)–PhysCellId (395)–PhysCellIdRange (395)–PhysCellIdRangeUTRA-FDDList (395)–PhysCellIdCDMA2000 (396)–PhysCellIdGERAN (396)–PhysCellIdUTRA-FDD (396)–PhysCellIdUTRA-TDD (396)–PLMN-Identity (397)–PLMN-IdentityList3 (397)–PreRegistrationInfoHRPD (397)–Q-QualMin (398)–Q-RxLevMin (398)–Q-OffsetRange (398)–Q-OffsetRangeInterRAT (399)–ReselectionThreshold (399)–ReselectionThresholdQ (399)–SCellIndex (399)–ServCellIndex (400)–SpeedStateScaleFactors (400)–SystemInfoListGERAN (400)–SystemTimeInfoCDMA2000 (401)–TrackingAreaCode (401)–T-Reselection (402)–T-ReselectionEUTRA-CE (402)6.3.5Measurement information elements (402)–AllowedMeasBandwidth (402)–CSI-RSRP-Range (402)–Hysteresis (402)–LocationInfo (403)–MBSFN-RSRQ-Range (403)–MeasConfig (404)–MeasDS-Config (405)–MeasGapConfig (406)–MeasId (407)–MeasIdToAddModList (407)–MeasObjectCDMA2000 (408)–MeasObjectEUTRA (408)–MeasObjectGERAN (412)–MeasObjectId (412)–MeasObjectToAddModList (412)–MeasObjectUTRA (413)–ReportConfigEUTRA (422)–ReportConfigId (425)–ReportConfigInterRAT (425)–ReportConfigToAddModList (428)–ReportInterval (429)–RSRP-Range (429)–RSRQ-Range (430)–RSRQ-Type (430)–RS-SINR-Range (430)–RSSI-Range-r13 (431)–TimeToTrigger (431)–UL-DelayConfig (431)–WLAN-CarrierInfo (431)–WLAN-RSSI-Range (432)–WLAN-Status (432)6.3.6Other information elements (433)–AbsoluteTimeInfo (433)–AreaConfiguration (433)–C-RNTI (433)–DedicatedInfoCDMA2000 (434)–DedicatedInfoNAS (434)–FilterCoefficient (434)–LoggingDuration (434)–LoggingInterval (435)–MeasSubframePattern (435)–MMEC (435)–NeighCellConfig (435)–OtherConfig (436)–RAND-CDMA2000 (1xRTT) (437)–RAT-Type (437)–ResumeIdentity (437)–RRC-TransactionIdentifier (438)–S-TMSI (438)–TraceReference (438)–UE-CapabilityRAT-ContainerList (438)–UE-EUTRA-Capability (439)–UE-RadioPagingInfo (469)–UE-TimersAndConstants (469)–VisitedCellInfoList (470)–WLAN-OffloadConfig (470)6.3.7MBMS information elements (472)–MBMS-NotificationConfig (472)–MBMS-ServiceList (473)–MBSFN-AreaId (473)–MBSFN-AreaInfoList (473)–MBSFN-SubframeConfig (474)–PMCH-InfoList (475)6.3.7a SC-PTM information elements (476)–SC-MTCH-InfoList (476)–SCPTM-NeighbourCellList (478)6.3.8Sidelink information elements (478)–SL-CommConfig (478)–SL-CommResourcePool (479)–SL-CP-Len (480)–SL-DiscConfig (481)–SL-DiscResourcePool (483)–SL-DiscTxPowerInfo (485)–SL-GapConfig (485)。
胡林教师简历 - 长沙理工大学欢迎您!

胡林硕士研究生导师简介基本信息姓名:胡林性别:男出生年月:1978.8最终学历:研究生职称:讲师学位:博士所在院系:汽机学院汽车工程系E-Mail:hulin888@教学情况一、讲授的主要课程[1] 《汽车构造》,本科生专业课,48学时;[2] 《汽车电控单元与接口技术》,本科生专业课,32学时。
二、承担的实践性教学[1] 汽车服务工程、车辆工程专业的生产实习指导[2] 汽车服务工程、车辆工程专业毕业论文设计指导三、主持的教学研究课题[1] 汽车类专业创新实践能力培养教学研究.长沙理工大学教改项目科研情况一、研究方向汽车电子;汽车安全;车辆动力学二、承担的主要课题主持湖南省教育厅项目《动态路径规划理论研究》,项目编号:13C1015,经费:1万,2013-2015 主持教育部留学回国人员科研启动基金《基于路口交通信号延时的动态路径规划研究》,项目编号:教外司留【2012】1707,经费:3万,2013-2015主持湖南省科技计划《随机时变路网中车辆路径规划的关键技术研究》,项目编号:2012FJ3004,经费:2万,2012-2013主持人社部留学人员科技活动择优资助《基于混合遗传算法的城市间动态路径规划研究》,项目编号:国人社【2011】721,经费:3万,2012-2014主持北京卡达克科技中心横向课题《中国交通事故深入研究前期数据库开发》,经费:50万,2013-2014主持瑞喆实业(上海)有限公司横向课题《冷却循环水系统节能技术开发》,经费:30万,2012-2013主持上海市优秀青年教师科研专项基金《分层级联信息融合车辆定位及动态路径规划研究》,经费:3万,2009主持湖南省研究生科研创新项目《车辆定位及动态路径规划理论和方法研究》,经费:1万,2008参与德国BMBF项目《Ad-hoc Wireless Systems for Vehicular Communications》,经费:30万欧元,2009-2011参与国家自然科学基金委项目《多车协作驾驶纵向控制动力学建模与仿真研究》,项目编号:11272067,经费:86万,2013-2016参与国家“863”科技计划项目《汽车空气动力学关键技术研究与应用》,项目编号:2007AA04Z122,经费:73万,2007-2009参与湖南省重点科技计划项目《汽车高速气动特性优化设计平台构建与应用》,项目编号:06FJ2001,经费:35万,2006-2008参与湖南亮才汽车安全技术有限公司横向课题《汽车主动安全智能避撞系统研制开发》,经费:30万,2007-2008参与湘潭电机股份有限公司横向课题《220吨电动轮自卸车技术开发》,经费:30万,2007 参与湘潭电机股份有限公司横向课题《SF33900型电动轮自卸车整车性能分析与优化》,经费:39万,2008三、主要研究论文共发表论文30多篇,其中SCI检索3篇,EI检索15篇[1]Lin Hu, Jing Huang, Fangyi Li. Simulation and Optimization of Vehicle Ride Comfort on Random Road, Advances in Mechanical and Electronic Engineering:Lecture Notes in Electrical Engineering.176, pp 495-501,2012 (EI:20124115546088) [2]Hu, L , Gu, Z.-Q,Huang, J, et al. Research and realization of optimum route planning in vehicle navigation systems based on a hybrid genetic algorithm.Proceedings of the Institution of Mechanical Engineers, Part D: Journal of Automobile Engineering. 222,pp757-763,2008 (SCI:000257469500010;EI: 20082711350997)[3]Hu, Lin; Gu, Zheng-Qi; Huang, Jing; Xiang, Yu; Wu, Tong-Feng.Simulation of 30.00R51 Radialtire's stiffness characteristics.Journal of System Simulation,20,pp2210-2214,2008(EI:20082011257294)[4]胡林,谷正气,杨易,黄晶.基于权值D-S 证据理论的车辆导航地图匹配.中国公路学报,21(2): 116-120,2008 (EI: 20082011256611)[5]胡林,谷正气,黄晶,杨易.基于传感器融合的车辆全球定位.汽车工程,30(8):491-495,2008 (CSCD核心)[6]Huang, Jing; Zhong, Zhihua; Hu, Lin; Liu, Dihui.Protecting performance analysis and structural optimization of a sandwiched tube-type airbag.Journal of Mechanical Engineering,45(6):107-112, 2009 (EI: 20092912195761)[7]Huang J, Zhong Z, Hu L, et al. Modelling and simulation of a sandwiched tube-type airbag and its optimization using design of experiments. Proceedings of the Institution of Mechanical Engineers, Part D: Journal of Automobile Engineering,221(9):1089-1095, 2007(SCI: 000249896000006; EI: 20080211008073)[8]Yang Y, Gu ZQ, Hu L. Research on the information fusion method of the Global Positioning System-dead reckoning vehicle integrated navigation system. Proceedings of the Institution of Mechanical Engineers, Part D: Journal of Automobile Engineering,221(5):543-553, 2007 (SCI: 000247852500003;EI: 20072710686284)四、知识产权及成果胡林,一种车辆事故自动报警系统,专利号:201220116548.9胡林,一种汽车内紧急报警装置,专利号:201220095638.4 胡林,一种基于远程控制的汽车防盗装置,专利号:201120570147.6 胡林,跑车,专利号:201130507834.9 胡林,矿用车,专利号:201130507835.3 谷正气、胡林等,座椅综合性能体验评价试验装置,专利号:200610031909.9 谷正气、胡林等,风洞彩色烟流试验装置,专利号:200610031985.X 颜运昌、胡林等,TFSJ-II电网防窃电实时监测系统,省部级科技成果。
INTERNATIONAL JOURNAL OF WIRELESS AND MOBILE COMPUTING (IJWMC) 1 A Biologically Inspired Qo

A Biologically Inspired QoS Routing Algorithm forMobile Ad Hoc NetworksZhenyu Liu,Marta Z.Kwiatkowska,and Costas ConstantinouAbstract—This paper presents an Emergent Ad hoc Routing Algorithm with QoS provision(EARA-QoS).This ad hoc QoS routing algorithm is based on a swarm intelligence inspired routing infrastructure.In this algorithm,the principle of swarm intelligence is used to evolutionally maintain routing information. The biological concept of stigmergy is applied to reduce the amount of control traffic.This algorithm adopts the cross-layer optimisation concept to use parameters from different layers to determine routing.A lightweight QoS scheme is proposed to provide service-classified traffic control based on the data packet characteristics.The simulation results show that this novel routing algorithm performs well in a variety of network conditions.Index Terms—MANET,routing,QoS,swarm intelligence.I.I NTRODUCTIONM OBILE ad hoc networks(MANETs)are wireless mo-bile networks formed munication in such a decentralised network typically involves temporary multi-hop relays,with the nodes using each other as the relay routers without anyfixed infrastructure.This kind of network is veryflexible and suitable for applications such as temporary information sharing in conferences,military actions and disaster rescues.However,multi-hop routing,random movement of mobile nodes and other features unique to MANETs lead to enormous overheads for route discovery and maintenance.Furthermore, compared with the traditional networks,MANETs suffer from the resource constraints in energy,computational capacities and bandwidth.To address the routing challenge in MANETs,many ap-proaches have been proposed in the literature.Based on the routing mechanism for the traditional networks,the proactive approaches attempt to maintain routing information for each node in the network at all times[1]–[3],whereas the reactive approaches onlyfind new routes when required[4]–[6].Other approaches make use of geographical location information for routing[7],[8].Those previous works only provide a basic “best effort”routing functionality that is sufficient for con-ventional applications such asfile transfer or email download. To support real-time applications such as V oIP and video stream in MANETs,which have a higher requirement for delay,jitter and packet losses,provision of Quality-of-Service (QoS)is necessary in addition to basic routing functionality. Z.Liu and M.Z.Kwiatkowska is with School of Computer Science,The University of Birmingham,Birmingham,England B152TT.C.Constantinou is with the Department of Electronic Electrical and Computer Engineering,The University of Birmingham,Birmingham,England B152TT.Given the nature of MANETs,it is difficult to support real-time applications with appropriate QoS.In some cases it may be even impossible to guarantee strict QoS requirements.But at the same time,QoS is of great importance in MANETs since it can improve performance and allow critical information to flow even under difficult conditions.At present,the most fundamental challenges of QoS support in MANETs concern how to obtain the available bandwidth and maintain accurate values of link state information during the dynamic evolution of such a network[9].Based on common techniques for QoS provision in the Internet,some researchers proposed the integration of QoS provision into the routing protocols[10],[11].However,since these works implicitly assumed the same link concept as the one in wired networks,they still do not fully address the QoS problem for MANETs.In this paper,we propose a new version of the self-organised Emergent Ad hoc Routing Algorithm with QoS provisioning(EARA-QoS).This QoS routing algorithm uses information from not only the network layer but also the MAC layer to compute routes and selects different paths to a destination depending on the packet characteristics.The underlying routing infrastructure,EARA originally proposed in[12],is a probabilistic multi-path algorithm inspired by the foraging behaviour of biological ants.The biological concept of stigmergy in an ant colony is used for the interaction of local nodes to reduce the amount of control traffic.Local wireless medium information from the MAC layer is used as the artificial pheromone(a chemical used in ant communications) to reinforce optimal/sub-optimal paths without the knowledge of the global topology.One of the optimisations of EARA-QoS over EARA is the use of metrics from different layers to make routing decisions. This algorithm design concept is termed as the cross-layer design approach.Research[13]has shown the importance of cross-layer optimisations in MANETs,as the optimisation at a particular single layer might produce non-intuitive side-effects that will degrade the overall system performance.Moreover, the multiple-criteria routing decisions allow for the better usage of network characteristics in selecting best routes among multiple available routes to avoid forwarding additional data traffic through the congested areas,since the wireless medium over those hotspots is already very busy.The parameters for measuring wireless medium around a node depend largely on the MAC layer.In this paper,we focus on the IEEE802.11 DCF mode[14],since it is the most widely used in both cellular wireless networks and in MANETs.This cross-layer technique of using MAC layer information can be appliedeasily to other MAC protocols.In addition to the basic routing functionality,EARA-QoS supports an integrated lightweight QoS provision scheme.In this scheme,traffic flows are classified into different service classes.The classification is based on their relative delay bounds.Therefore,the delay sensitive traffic is given a higher priority than other insensitive traffic flows.The core technique of the QoS provision scheme is a token bucket queuing scheme,which is used to provide the high priority to the real-time traffic,and also to protect the lower-priority traffic from star-vation.Experimental results from simulation of mobile ad hoc networks show that this QoS routing algorithm performs well over a variety of environmental conditions,such as network size,nodal mobility and traffic loads.II.B ACKGROUNDIn this section,we give a brief introduction to background knowledge on ant colony heuristics,and the QoS provision techniques in MANETs.A.Foraging Strategies in AntsOne famous example of biological swarm social behaviour is the ant colony foraging [15](see Figure 1).Many ant species have a trail-laying,trail-following behaviour when foraging:individual ants deposit a chemical substance called pheromone as they move from a food source to their nest,and foragers follow such pheromone trails.Subsequently,more ants are attracted by these pheromone trails and in turn reinforce them even more.As a result of this auto-catalytic effect,the optimal solution emerges rapidly.In this food searching process a phenomenon called stigmergy plays a key role in developing and manipulating local information.It describes the indirect communication of individuals through modifying theenvironment.Fig.1.All Ants Attempt to Take the Shortest PathFrom the self-organisation theory point of view,the be-haviour of the social ant can be modelled based on four elements:positive feedback,negative feedback,randomness and multiple interactions [16].This model of social ants using self-organisation theories provides powerful tools to transfer knowledge about the social insects to the design of intelligent decentralised problem-solving systems.B.Quality-of-Service in MANETsQuality-of-Service (QoS)provision techniques are used to provide some guarantee on network performance,such as average delay,jitter,etc.In wired networks,QoS provision can generally be achieved with the over-provisioning of re-sources and with network traffic engineering [17].With the over-provisioning approach,resources are upgraded (e.g.fibre optic data link,advanced routers and network cards)to make networks more resistant to resource demanding applications.The advantage of this approach is that it is easy to be implemented.The main disadvantage of this approach is that all the applications still have the same priority,and the network may become unpredictable during times of bursting and peak traffic.In contrast,the idea of the traffic engineering approach is to classify applications into service classes and handle each class with a different priority.This approach overcomes the defect of the former since everyone is following a certain rule within the network.The traffic engineering approach has two complemen-tary means to achieve QoS provisioning,Integrated Services (IntServ)and Differentiated Services (DiffServ).IntServ [18]provides guaranteed bandwidth for flows,while DiffServ [19]provides hard guarantees for service classes.Both of the approaches rely on the possibility to make bandwidth reservations.The former was used in ATM (Asynchronous Transfer Mode)[20]and is today the method of achieving QoS in RSVP-IntServ [21].On the other hand,in the DiffServ approach,no reservation is done within the network.Instead,QoS is achieved by mechanisms such as Admission Control ,Policy Manager ,Traffic Classes and Queuing Schedulers .These mechanisms are used to mark a packet to receive a particular forwarding or dropping treatment at each node.Based on QoS provision techniques in wired networks,many QoS approaches are proposed to provide QoS services for MANETs.Flexible QoS Model for MANETs (FQMM)[22],is the first QoS approach for MANETs,which combines knowledge on IntServ/DiffServ in wired networks with con-sideration of MANETs.As an essential component to achieve the QoS provisioning,QoS routing algorithms tightly integrate QoS provisioning into routing protocols.The QoS version of AODV (QoS-AODV)[23],the Core-Extraction Distributed Ad Hoc Routing (CEDAR)protocol [10],the Multimedia Support for Mobile Wireless Networks (MMWN)protocol [11],and the ticket-based protocols [24]are examples of QoS routing algorithms proposed for MANETs.On the other hand,QoS signaling techniques are inde-pendent of the underlying routing protocols.The In-band Signalling for QoS in Ad-Hoc Mobile Networks (INSIGNIA)algorithm [25]is the typical signaling protocol designed exclusively for MANETS.The idea of CEDAR,MMWN,and ticket-based protocols is to disseminate link-state information across the network in order to enable other nodes to find routes that meet certain QoS criteria,like the minimum bandwidth.On the other hand,INSIGNIA piggybacks resource reservations onto data packets,which can be modified by intermediate nodes to inform the communication endpoint nodes in case of lack ofresources.All those approaches are based on the idea that the wireless links between mobile nodes have certain QoS related properties,in particular a known amount of available bandwidth,and that nodes are able to give guarantees for traffic traversing these links.III.C RITIQUE OF E XISTING Q O S A PPROACHES INMANET SNowadays,most of the QoS provisioning techniques are derived from the QoS approaches of the wired networks. However,QoS support approaches proposed in wired networks are based on the assumption that the link characteristics such as bandwidth,delay,loss rate and error rate must be available and manageable.However,given the challenges of MANETs, e.g.dynamic topology and time-varying link capacity,this assumption does not apply any longer.Thus,applying the concepts of wired traffic engineering QoS approaches directly to MANETs is extremely difficult.Generally,the situation in MANETs is completely different from those in wired networks.In wireless networks,the available bandwidth undergoes fast time-scale variations due to channel fading and errors from physical obstacles.These effects are not present in wired networks.In MANETs,the wireless channel is a shared-access medium,and the available bandwidth even varies with the number of hosts contending for the channel.Below we analyse why the IntServ/DiffServ models are not appropriate for MANETs respectively. IntServ based approaches are not applicable for MANETs mainly due to two factors,huge resource consumption and computation power limitation.Firstly,to support IntServ,a huge amount of link state information has to be built and main-tained for each mobile node.The amount of state information increases proportionally with the number offlows,which is also a problem with the current IntServ QoS scheme.Secondly, current wireless networks employ two major MAC techniques, the single-channel approach and the multiple channel ap-proach.With single-channel approach(e.g.IEEE802.11[14]), all nodes share the same channel and therefore potentially interfere with each other.With a multiple-channel approach (e.g.Bluetooth[26]or CDMA[27]),nodes can communicate on several channels simultaneously.Both of the two MAC techniques have a similar bandwidth reservation mechanism. This common mechanism requires a transmission schedule to define time slots,in which nodes take their turns periodically. For each slot,its duration and a set of possible simultaneous transmissions must be defined.However,in wireless networks, the problem offinding an optimal schedule is proved to be NP-complete[28],which is a fundamental limitation of QoS provisioning in wireless networks.On the other hand,the DiffServ approach is a lightweight QoS model for interior routers since individual stateflows are aggregated into sets of service classes whose packets are treated differently at the routing nodes.This makes routing a lot easier in the network.Thus this approach could be a potential solution for MANETs.Even though it is not practical to provide a hard separation of different service classes in MANETs,relative prioritisation is possible in such a way that traffic of a certain class is given a higher or lower priority than traffic of other service classes.One solution would be to divide the traffic into a predefined set of service classes that are defined by their relative delay bounds,such as delay sensitive(realtime)and insensitive(bulk)traffic.Realtime traffic should be given higher priority than bulk traffic.No absolute bandwidth guarantees are provided.Some work based on service differentiation rather than resource reservations in MANETs already exists[29].IV.D ESCRIPTION OF EARA-Q O SEARA-QoS is an on-demand multipath routing algorithm for MANETs,inspired by the ant foraging intelligence.This algorithm incorporates positive feedback,negative feedback and randomness into the routing computation.Positive feed-back originates from destination nodes to reinforce the existing pheromone on good paths.Ant-like packets,analogous to the ant foragers,are used to locallyfind new paths.Artificial pheromone is laid on the communication links between nodes and data packets are biased towards strong pheromone,but the next hop is chosen probabilistically.To prevent old routing solutions from remaining in the current network status,expo-nential pheromone decay is adopted as the negative feedback. Each node using this algorithm maintains a probabilistic routing table.In this routing table,each route entry for the destination is associated with a list of neighbour nodes.A probability value in the list expresses the goodness of node as the next hop to the destination.For each neighbour, the shortest hop distance to the destination and the largest sequence number seen so far are also recorded.In addition to the routing table,each node also possesses a pheromone table.This table tracks the amount of pheromone on each neighbour link.The table may be viewed as a ma-trix with rows corresponding to neighbourhood and columns to destinations.There are three threshold values controlling the bounds on pheromone in the table.They are the upper pheromone that prevents extreme differences in pheromone, the lower pheromone,below which data traffic cannot be forwarded,and the initial pheromone that is assigned when a new route is found.In addition to the routing data structures present above,the following control packets are used in EARA-QoS to perform routing computation:Route Request Packet(RQ)containing destination ad-dress,source address and broadcast ID.Route Reply Packet(RP)containing source address,des-tination address,sequence number,hop account and life-time.Reinforcement Signal(RS)containing destination ad-dress,pheromone value and sequence number.Local Foraging Ant(LFA)containing source address (the node that sent LFA),the least hop distance from the source to the destination,stack of intermediate node address and hop count.Hello Packet(HELLO)containing source(the node that sent Hello)address and hop count(set to0).A.Parameters of Lower Layers1)The Average MAC Layer Utilisation:Thefirst metric is the average MAC layer utilisation for a node.This metric measures the usage of the wireless medium around that node. As the instantaneous MAC layer utilisation at a node is either (busy)or(idle),we average this value over a period of time window as follows:(1) where is the time when the medium is busy in the window.This average MAC utilisation indicates the degree to which the wireless medium around that node is busy or idle.We consider the instantaneous MAC layer utilisation level at a node to be1when the wireless medium around that node either detects physical carrier to be present or is deferring due to virtual carrier sensing,inter-frame spacing,or backoff.In addition,we also consider the medium is busy at any time when the node has at least one packet in the transmission queue.2)The Transmission Queue Heuristic:The second metric isa heuristic value that is calculated with the network interface transmission queue length in the current node.Apart from the media status,the transmission queue length is also a key factor that can affect the packet latency or packet drop due to the size limit on the queue length.We define the heuristic value with the following rules.If the outgoing network interface employs a single queue scheme,the heuristic value is defined as:(2) where is the length(in bytes waiting to be sent)of the interface queue in node,and is the maximum packet bytes allowed in the queue.If the network interface employs the multiple virtual queue scheme for each outgoing link,the heuristic value is defined as:(3)where is the length(in bytes waiting to be sent)of the virtual queue of the link in node and denotes the neighbourhood of node as a next-hop to some destination.3)The Average MAC Layer Delay:The last metric is the MAC layer delay for the link.The MAC layer delay is defined as the interval from when the RTS frame is sent at node to when the data frame is received successfully at node.The average MAC delay is obtained by averaging these values over a time window as follows:(4)where is the time interval in the window,and is a coefficient.This average MAC delay indicates the degree of interference.In regions where there is a lot of interference from other nodes,MAC delay is high due to the contentionof the channel.B.Data PropagationWhen multiple virtual queue scheme is employed,the rout-ing probability value is computed by the composition ofthe pheromone values,the local heuristic values and the linkdelays as follows:(5) where,and()are tunable parametersthat control the relative weight of pheromone trail,MAC delay and heuristic value,and is the neighbourhood as a next-hop to some destination.Incorporating the heuristic value and link delay in the rout-ing computation makes this algorithm possess the congestionawareness property.Based on the probabilistic routing table, data traffic will be distributed according to the probabilitiesfor each neighbour in the routing table.The routing algorithmexhibits load balancing behaviour.Nodes with a large number of packets in the buffer are avoided.The EARA-QoS algorithm consists of several components.They are the route discovery procedure,the positive and neg-ative reinforcement,and the local connectivity management.C.Route DiscoveryWe use a similar route discovery procedure as describedin[12].On initialisation,a neighbourhood for each node is built using the single-hop HELLO messages.Whenever atraffic source needs a route to a destination,it broadcastsroute request packets(RQ)across the network.Rather than simplyflooding the RQ packets,we adopt the probabilisticbroadcast scheme explored in[30]combined with the MAClayer utilisation.When a nodefirst receives a packet,with probability it broadcasts the packet to its neighbours,andwith probability it discards the packet.The probabilityvalue is calculated as(6) where()is the coefficient.This broadcast scheme helps to discover new routes avoiding congestion areas,but atthe cost of missing potential routes to the destination. During the course offlooding RQ packets to the destination ,the intermediate node receiving a RQ packetfirst sets up reverse paths to the source by recording the source addressand the previous hop node in the message cache.If a validroute to the destination is available,that is,there is at least one link associated with the pheromone trail greater than the lower pheromone bound,the intermediate node generates a route reply(RP).The RP is routed back to the source via the reverse paths.Otherwise,the RQ is rebroadcast.Other than just establishing a single forward path,whenthe destination node receives RQs it will send a RP to allthe neighbours from which it sees a RQ.In order to maintain multiple loop-free paths at each intermediate node,node(b) Path Reinforcement(c) Local Repair(a) Initial Pheromone Setup Fig.2.Illustrating Working Mechanism of EARA-QoSmust record all new forward paths that possess the latest sequence number but hold a lower hop-count in its routing table,and also send a RP to all the neighbours from which it saw a RQ.During the course of the RP tracking back to the source,an initial pheromone value is assigned to the corresponding neighbour node,which indicates a valid route to the destination.This process is illustrated in Figure2(a).D.Route ReinforcementAfter the destination node receives the data traffic sent by the source node,it begins to reinforce some good neighbour(s)in order to“pull”more data traffic through the good path(s)by sending reinforcement signal packets(RS) whenever it detects new good paths.When node receives a RS,it knows it has an outgoing link toward the destination ,which is currently deemed a good path.Subsequently, node updates the corresponding pheromone table entry with the value and forwards a RS packet to(at least one) selected neighbour locally based on its message cache,e.g.the neighbour(s)that saw the least hops of the incoming packets. The amount of the pheromone used to positively rein-force the previous hop neighbour is computed as follows.If the RS packet is sent by the destination to node,then is calculated using the upper bound pheromone value ,(7) If the RS packet is sent by an intermediate node towards node,the is calculated using the current largest pheromone value max()in node with the next hop to the destination in the pheromone table,max(8) where,and are parameters that control the relative weight of the relative source hop distance,the rel-ative packet number and the local queue heuristic. Incorporating the congestion-measuring metric into the reinforcement can lead data traffic to avoid the congestion areas.The relative source hop distance is calculated as follows:(9) where is the shortest hop distance from the source to the current node through node,and is the shortest hop distance from to.This parameter is used to ensure that paths with shorter hop distance from the source node to the current node are reinforced with more pheromone.The relative packet number is calculated as follows:(10) where is the number of incoming packets from neighbour to the destination,and is the total number of incomingpackets towards the destination.This parameter is used to indicate that the data forwarding capacity of a link also affects the reinforcement.The more data arrives,the stronger reinforcement is generated for the corresponding link.On receiving the RS from a neighbour,node needs to positively increase the pheromone of the link towards node.If the sequence number in the RS is greater than the one recorded in the pheromone table,node updates its corresponding pheromone with the value of carried on the RS:(11) If the sequence number is equal to the current one,then:ifotherwise(12)If the sequence number in RS is less than the current one in the pheromone table,then this RS is just discarded.Node also has to decide to reinforce(at least)one of its neighbours by sending the RS message based on its own message cache.This process will continue until reaching the source node.As a result of this reinforcement,good quality routes emerge,which is illustrated in Figure2(b).The same procedure can apply to any intermediate node to perform local link error repair as long as it has pheromone value that is greater than the lower bound.For instance,if an intermediate node detects a link failure from one of its upstream links, it can apply the reinforcement rules to discover an alternative path as shown in Figure2(c).There is also an implicit negative reinforcement for the pheromone values.Within every time interval,if there is no data towards a neighbour node,its corresponding pheromone value decays by a factor as follows:(13)E.Local Foraging AntsIn a dynamic network like MANET,the changes of the net-work topology create chances for new good paths to emerge.In order to make use of this phenomenon,this algorithm launcheslocal foraging ants(LFA)with a time interval to locallysearch for new routes whenever all the pheromone trails of a node towards some destination drop below the threshold.The LFA will take a random walk from its original node. During the course of its walk,if the LFA detects congestionaround a node(the average channel utilisation is greaterthan a predefined threshold value),then the LFA dies to avoid increasingly use the wireless medium.Otherwise,theLFA pushes the address of the nodes that it has travelledinto its memory stack.To avoid forming of loops,LFA will not choose to travel to the node that is already in.Before reaching the maximum hop,if LFA canfind a node with pheromone trails greater than and the hop distanceto destination not greater than the one from its original nest,itreturns to its’nest’following its memory stack and updates the corresponding paths with.Otherwise,it simply dies.F.Local Connectivity ManagementNodes maintain their local connectivity in two ways.When-ever a node receives a packet from a neighbour,it updates its local connectivity information to ensure that it includes thisneighbour.In the event that a node has not sent any packets toits neighbours within a time interval,it has to broadcast a HELLO packet to its neighbours.Failure to receive packetsfrom the neighbourhood in indicates changes in the local connectivity.If HELLO packets are not received from the nexthop along an active path,the node that uses that next hop issent notification of link failure.In case of a route failure occurring at node,cannot for-ward a data packet to the next hop for the intended destination .Node sends a RS message that sets ROUTE RERR tag to inform upstream nodes of the link failure.This RS signalassigns to the corresponding links the lower bound.Here, RS plays the role of an explicit negative feedback signal to negatively reinforce the upstream nodes along the failure path. This negative feedback avoids causing buffer overflow due to caching on-flight packets from upstream nodes. Moreover,the use of HELLO packets can also help to ensure that only nodes with bidirectional connectivity are deemed as neighbours.For this purpose,the HELLO packet sent by a node has an option to list the nodes from which it has heard HELLO packets,and nodes that receive the HELLO check to ensure that it uses only routes to neighbours that have sent HELLO packets.G.The QoS Provision SchemeThis section describes a lightweight approach to DiffServ. The basic idea is to classifyflows into a predefined set of service classes by their relative delay bounds.Admission control only works at the source node.There is no session orflow state information maintained at intermediate nodes. Once a realtime session is admitted,its packets are marked as RT(realtime service)and otherwise they are considered as best-effort bulk packets.As depicted in Figure3,each of these traffic classes is buffered in a logically separate queue.A simple novel queuing strategy,based on the token bucket scheme,provides high priority to realtime traffic,and also protects the lower-priority traffic from starvation.No absolute bandwidth guarantees are provided in this scheme.We explain this queuing strategy and its novelty below.The queues are scheduled according to a token bucket scheme.In this scheme,prioritisation is achieved with token balancing.Each traffic class has a balance of tokens,and the class with higher balance has a higher priority when dequeuing the next packet for transmission.For each transmission of a packet of class,an amount of tokens is subtracted from the class’token balance and an equal fraction thereof is added to every other class’balance such that the sum of all tokens is always the same.The weight value reflects the delay sensitivity assigned to the different classes.A higher weight value corresponds to a lower delay sensitivity.The size of the token balance together with the value determines the maximal length of a burst of traffic from one class.In this scheme,as long as the amount of delay-sensitive traffic does not grow too large,it is forwarded as quickly as possible,and if it does grow too large,starvation of other traffic classes is prevented.Setting the upper bound of a class’token balance depending on its delay-sensitivity enables further tuning of the describedmethod.Fig.3.Overview of Service Differentiation SchemeIn this packet scheduling scheme,routing protocol pack-ets are given unconditional priority before other packets. Moreover,realtime applications normally have stringent delay bounds for their traffic.This means that packets arriving too late are useless.From the application’s point of view,there is no difference between late and lost packets.This implies that it is actually useless to forward realtime packets that stay in a router for more than a threshold amount of time,because they will be discarded at the destination anyway.Dropping those packets instead has the advantage of reducing the load in the network.To our knowledge,this service classification based queuing scheme is the simplest implemented QoS provisioning technique designed exclusively for MANETs so far.V.C HARACTERISTICS OF THE A LGORITHMThis proposed protocol,implementing the cross-layer design concept,exhibits some properties that show itsfitness as a solution for mobile ad hoc networks:Loop-freeness:during the route discovery phase,the nodes record the unique sequence number of RP packets.。
Tenda AC6 双频智能 WiFi 路由器 说明书

AC1200 Smart Dual-Band WiFi RouterAC6• Dual-band concurrent transfer rate of up to 1167 Mbps• Support wireless signal repeater and WISP•• Support VPN server • Management with Tenda App •• Built-in separated signal amplifiersFeatures1. Superior gaming and UHD streaming experienceFour external high-gain antennas • Extreme WiFi transfer rate of up to 1167 Mbps• Broadcom ARM Cortex-A7 900 MHz processor with DDR2 memory foroutstanding performance2. Ultimate coverage without deadzones• High-power amplifiers for whole-home coverage• Beamforming+ technology to boost the transmission range for 802.11ac WiFidevices• Four external high-gain antennas to achieve whole-home HD coverage3. Smart management via Tenda App• Smart WiFi schedule to automatically• Advanced QoS for uninterrupted HD video streaming• Power saving and LED control for energy-conservative household• Smart Tenda App for management anytime anywhereAC6 is a dual-band wireless router dedicated to home users for smart homenetworking. It boasts a concurrent dual-band wireless data transfer rate of upto 1167 Mbps. Its built-in signal amplifiers, Beamforming technology, and fourexternal antennas o er you lag-free gaming and uninterrupted videostreaming experience. AC6 also provides the Smart WiFi Schedule function,which automatically turns on/o WiFi to reduce power consumption andbring smart internet connectivity to your family.6-8 Floor, Tower E3, No.1001, Zhongshanyuan Road,Nanshan District, Shenzhen, China. 518052E-mail:*****************.cnTel:+86-755-2765 7098Fax:+86-755-2765 7178Website:Specifications are subject to change without notice.Copyright ©2017 SHENZHEN TENDA TECHNOLOGY CO.,LTD. All rights reserved. Tenda is the trademark of SHENZHEN TENDA TECHNOLOGY CO.,LTD. All other brand names mentioned herein are the trademark or registered trademarks of their respective holders.。
wanem参数

wanem参数【原创实用版】目录1.Wanem 参数概述2.Wanem 参数的组成3.Wanem 参数的作用4.Wanem 参数的应用实例5.Wanem 参数的未来发展趋势正文一、Wanem 参数概述Wanem 参数,全称 Wireless Network Emulation Model parameters,是一种用于模拟无线网络环境的参数设置。
通过 Wanem 参数,可以实现对无线网络的精确建模,从而帮助研究人员和工程师更好地理解和优化无线网络的性能。
二、Wanem 参数的组成Wanem 参数主要包括以下几个方面:1.无线电传播模型:用于描述无线信号在空间中的传播特性,包括信号的衰减、反射、散射等现象。
常见的无线电传播模型有两径瑞利模型、LogDistancePropagationLossModel 等。
2.物理层模型:用于描述无线网络的物理层特性,包括信号调制、解调、信道编码、解码等。
常见的物理层模型有 OFDM、DPSK 等。
3.链路层模型:用于描述无线网络的链路层特性,包括数据帧的格式、传输速率、误码率等。
常见的链路层模型有 802.11b、802.11g、802.11n 等。
4.网络层模型:用于描述无线网络的网络层特性,包括路由选择、拥塞控制、流量控制等。
常见的网络层模型有 TCP/IP、UDP 等。
三、Wanem 参数的作用Wanem 参数在无线网络建模中起着关键作用,主要表现在以下几个方面:1.提高无线网络建模的精确度:通过设置合适的 Wanem 参数,可以实现对无线网络的精确建模,从而更好地反映实际无线网络的性能。
2.降低无线网络建模的复杂度:Wanem 参数将复杂的无线网络建模问题简化为一系列参数的设置,从而降低了建模的复杂度。
3.便于无线网络性能分析和优化:通过调整 Wanem 参数,可以方便地分析无线网络的性能,并为网络优化提供有力支持。
四、Wanem 参数的应用实例Wanem 参数广泛应用于以下领域:1.无线网络性能测试:通过设置不同的 Wanem 参数,可以模拟不同环境下的无线网络性能,从而对网络设备和协议进行性能测试。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Modelling Routing in Wireless Ad Hoc Networks with Dynamic Bayesian GamesPetteri NurmiHelsinki Institute for Information Technology(HIIT)/Basic Research UnitDepartment of Computer Science,P.O.Box68FI-00014University of Helsinki,FinlandEmail:petteri.nurmi@cs.helsinki.fiAbstract—Mobile agents acting in wireless ad hoc networks are energy constrained,which leads to potential selfishness as nodes are not necessarily willing to forward packets for other nodes.Situations like this are traditionally analyzed using game theory and recently also the ad hoc networking community has witnessed game-theoretic approaches to especially routing. However,from a theoretical point-of-view the contemporary game-theoretic approaches have mainly ignored two important aspects:non-simultaneous decision making and incorporating history information into the decision making process.In this article we propose a new model thatfills these gaps and allows to analyze routing theoretically.I.I NTRODUCTIONIn wireless ad hoc networks[1]a collection of nodes, i.e.mobile hosts,forms a self-organizing network without any support from pre-established infrastructure.The lack of infrastructure support forces the nodes to implement all net-working tasks by themselves and for routing this means that packets must be routed using other nodes as intermediate relays.Simple routing schemes,such as the dynamic source routing protocol[2],are sufficient only if all nodes are willing to participate in the forwarding.However,nodes are energy constrained by their battery level and want to maximize their lifetime,which leads to potential selfishness as the nodes may refuse to forward packets for other nodes.Simulations have shown that network throughput rate often degrades signif-icantly when simple routing schemes are used and even a small portion of the nodes acts selfishly[3].For this reason methods for stimulating cooperation among the nodes are required.A method for cooperation stimulation should have afirm theoretical background.However,most of the existing approaches are mainly verified by experimental evaluation, which makes theoretical analysis of the systems difficult.A routing decision is essentially a conflict situation that can be modelled using tools from game theory.The contemporary approaches have analyzed routing in a stage-wise manner using so-called static games[4],in which routing is modelled by looking at a single set of packets and where all relays on the routing path act as if all nodes decide simultaneously whether to forward the packets or not.Clearly this kind of approach is unrealistic especially in multi-hop routing and in dense ad hoc networks as there is delay between the 1Research supported by the Academy of Finland grant202203.sending of a packet by the source node and the packet processing in an intermediate node.Within the delay time,the energy level of an intermediate node usually decreases,which causes important model parameters to change and makes the assumption of simultaneous decision making no longer valid. Anotherflaw in the existing approaches is that they mainly ignore the temporal aspect(past actions)in game play or give no proper justification for the model that is used.To overcome these deficiencies,we propose a new model that uses dynamic Bayesian games[4,Chap.8].Dynamic Bayesian games allow formulating a generic model,in which no restrictions are put on the delay between sending a set of packets and forwarding them.Additionally,the new model allows analyzing optimality in terms of past actions and makes it possible to take into account various sources of uncertainty.The organization of this paper is as follows:in Section II we discuss related work on cooperation stimulation mechanisms and on game-theoretic routing models of ad hoc networks.In Section III we introduce the new model and in Section IV implementation issues related to our model are discussed.In Section V we conclude the paper and discuss future work.In the Appendix we present game-theoretic material that is used in the optimality proof of Section III.II.R ELATED W ORKThe initial approaches for cooperation stimulation in ad hoc networks use either a reputation mechanism[5]or some kind of a virtual currency system.The approaches based on reputation attempt to identify selfish nodes and to isolate non-cooperative nodes from the network.Among thefirst reputation approaches is the watchdog-mechanism in which the forwarding rate of neighbouring nodes is monitored[6]. If a neighbour does not forward messages,it is considered non-cooperative and information about the non-cooperative reputation is propagated in the network.The information about non-cooperative nodes is used by a pathrater that rates paths between the source and the destination node.Together the watchdog and the pathrater methods make it possible to avoid paths with misbehaving nodes.From a theoretical perspective, the main problem with this approach is that misbehaviour is actually rewarded as no packets are routed through non-cooperative nodes,but the packets of the non-cooperative nodes are still forwarded.However,the general mechanismof monitoring traffic from neighbouring nodes has been used in many other approaches and it is also used in the approach proposed in this article.To overcome the problems with the watchdog approach, more elaborate reputation mechanisms such as Core[7]and Confidant[8]have been proposed.These methods extend the watchdog approach so that each node calculates a reputation value based on the information it has obtained about the forwarding rate of another node.The lower the reputation value of a node,the less likely it is that a packet is forwarded for that node.The proposed approaches differ in,e.g.what information is used,how the information is used,how hard misbehaviour is punished and how re-integration of temporally misbehaving nodes back in the network is performed.The main problem with these approaches is that they lack a formal model,which makes theoretical analysis difficult.In addition, the decision making mechanism is not asflexible as in our model.The approaches using a virtual currency system model the forwarding problem as an economic market,where sending and forwarding cost money.The approach proposed by But-tyán and Hubaux uses a currency called NUGLET[9].Each node is assumed to have a separate secure hardware module that has a NUGLET counter.The counter increases when a node forwards a packet for another node,and decreases when a node sends a packet of its own.The NUGLET counter must always be positive,so the approach forces the nodes to forward at least the same amount of traffic as they send themselves.A similar kind of solution was presented by Anderegg and Eidenbenz[10],who derive a truthful Vickrey-Clarke-Groves mechanism(VCG)[11]–[13]for routing.In their approach, thefirst phase of routing is to ask the nodes for their costs to forward packets.Based on this information the minimum energy path is calculated.Due to energy constraints,the nodes are attracted to cheating,but the authors prove that using premium payments,i.e.,additional pay to the nodes on the minimum energy path,it is in the best interest of a node to report the actual energy cost in thefirst phase.Another related approach was proposed by Srinivasan,Nuggehalli,Chiasserini and Rao[14].Their approach uses a generous TIT-FOR-TAT policy that guarantees(under certain conditions)cooperation in a game that is played repeatedly.Essentially the TIT-FOR-TAT policy[4,p.173]means that if a node does not cooperate, the other nodes will not forward packets for that node in the next time frame(packet session).The generous version uses slightly milder punishments.All the virtual currency approaches use computational mechanism design[15]methods for cooperation stimulation. Although the authors of the articles do not usually formulate a proper game-theoretic model,the approaches can be seen as static repeated games[4,Chap.5].This formulation does not properly take into account the uncertainty inherent in the network,which is due to node mobility,energy constraints etc. In addition,the assumption of simultaneous decision making is hard to justify especially in dense ad hoc networks.In a recent approach[16]the authors argue that TIT-FOR-TAT strategies make threats that are not credible and that TIT-FOR-TAT strategies lead to unrealistic models.The solution the authors propose is to use milder punishments, which are"partially cooperative".This means that nodes act optimally according to their beliefs about the behaviour of other nodes,but that their actions do not necessarily lead to globally optimal behaviour,in which all resources are optimally allocated.A properly formulated game-theoretic model was intro-duced by Urpi,Bonuccelli and Giordano[17],who use static Bayesian games[18]–[20]to model forwarding behaviour.In Bayesian games each node has a"secret type",which in this case is the energy class(remaining energy)of a node.The secret type affects decision making,but is only known to the node itself.However,nodes have beliefs about the types of neighbouring nodes and they base their decision making on their beliefs.Although this model properly formulates the game the nodes are playing,it still is very unrealistic as the static framework does not allow non-simultaneous decision making.In addition,the strategies in this framework are not dependent on past behaviour.However,this approach is closest to our approach as we also use energy classes and define beliefs over the energy classes of neighbouring nodes.As a conclusion we argue that the problems with existing approaches are twofold.First of all,the models consider only stage-games,in which a single packet is sent.Secondly, the approaches assume that the stage-games are static by nature.In our approach we consider dynamic stage-games with incomplete information that are repeatedfinitely many times and in which the model parameters are updated after each stage-game ends.This way we can model the various sources of uncertainty and take into account the past actions.III.D EFINITION OF THE G AMEIn this section we present a new framework that allows non-simultaneous decision making and takes past actions into account.We attempt to keep the discussion as general as possible and for this reason we do notfix all the components of the model,but instead give the conditions that must be satisfied.We start by defining some notation.Let be an arbitrary ad hoc network and afinite set of nodes(agents)belonging to;thus we defineand.An arbitrary node of the setis indexed by the variable.We assume that nodes have topology information only about the nodes within the range of their transmitter(local topology),but not about the nodes outside this region.The nodes that are within the range of the transmitter constitute the neighbourhood of a node.The variable is used to denote the neighbourhood of node.For simplicity we assume that the neighbourhood topologies are symmetric,i.e.,.The nodes are energy constrained as they have a limited amount of energy available.In addition,the nodes are energy-aware as they know their current energy level and try to minimize unnecessary energy consumption.A node is said to be rational if it maximizes throughput of its own messagesand minimizes unnecessary energy consumption.Moreover, we assume that the level of remaining energy can be measuredat reasonable accuracy and,without loss of generality,we assume that the energy level can be represented with afinite set of possible values.Thefiniteness is achieved using a global discretization method so that all nodes have the same set of possible values.We call the discretized energy level the energy class of a node and use the variable to denote the energy class of node at an arbitrary time.In the rest of the paper, the energy class of a node is also called the type of a player (node).Sending and forwarding decisions in a network are analyzed at discrete periods of time.We approach the situation from the point of view of an individual node and define for each a time period,,so that a new period starts when the node generates some packets and decides whether to send them to the network or to discard them.The number of packets generated by node at time period is denoted by,and the number of the generated packets that are actually sent to the network is denoted by.Thus,at each time period the relation holds.We define the action history of a sending node at time period to be a vector that contains the number of packets sent at time periods :(1) For simplicity,we restrict the setting by assuming that each message sent by an arbitrary node is broadcasted to all nodes in the neighbourhood.However,every node decides individually whether to forward the packets or not. From the point of view of the sending node,the decision and the corresponding forwarding action by a node take place at time period and we can define to be the number of packets that node forwards for node at time period.The sender’s decision of how many packets to send depends on its beliefs about the energy classes of the neighbouring nodes;if it believes that all neighbouring nodes have used all of their energy or that they are non-cooperative,it is not rational to send anything as sending consumes energy.The energy classes of the neighbouring nodes are not a priori known,but instead we assume that node has a probability distribution defined over the possible values of the energy class of a node.The probabilities of the energy classes at time period depend on the joint history profile of the actions made by node and node.The history profile is(4) where is the energy class of a sending node at time period and is the energy class of a node that is forwarding packets for at time step and is an arbitrary probability distribution.By defining a conditional probability density in the way shown in Equation4,we construct a belief system for the node.The beliefs reflect the level of knowledge a node has in the beginning of a time period.In addition,the beliefs play an important role when we want to define optimality of our model in the Bayesian sense.We return to this issue later in this section.Similarly as the decisions made by the sender depend on the sender’s beliefs about the energy classes of the neighbouring nodes,the decisions of the forwarding nodes depend on the beliefs the nodes have about the energy class of the sender.To assure consistency of the belief system with respect to actions, the model is constructed in such a way that the probabilities depend on the number of packets sent by node.The definition of the probability distribution of a forwarding node is given in Equation5.to denote the joint belief system of nodes and:DEFINITION1:A sending game is a5-tuple(I,,),where is the set of players,defines the action space of the game,is the belief system of the game.The set consists of two nodes and,whereand the set consists of action pairs for which the relation holds.The utility functionwhere is the utility function of the sender and is the utility function of the forwarder for the messages arriving from sender node. The type space is equivalent to the set of possible energy class values for a node and the belief system,where is a suitable probability distribution,is some sending node,is forwarding node and is either the node or the node.The variable denotes the action of and the variable(8) Whereas the sender obtains new information each time the game advances to the next period,the forwarder obtains new information within the individual periods.We require that also the forwarder’s beliefs are kept in a consistent state meaning that the probabilities are updated using the Bayes’rule every time the forwarder observes an action made by the sender. Again the posterior probabilities of period form the prior probabilities of stage and the actual calculations are carried out in a similar fashion as in Equation8.We assume that the support of an individual node’s action space equals the complete action space.Thus,for all nodes ,we have,where the support is defined in Equation9.(9) The assumption that the support equals the complete action space means that all the actions performed by the players have positive probabilities.This is realistic because we look at the entire time span a node is connected to a network.Thus it is reasonable to assume that a node can fail or that a node can change its behaviour policy in the course of time.This assumption significantly simplifies the analysis of the model as it makes the perfect Bayesian equilibrium a strong enough equilibrium concept.Otherwise stronger equilibrium concepts, such as the sequential equilibrium[21],that allow unexpected actions must be used.Moreover,if we assign positive priorprobabilities over the elements of the action space,the proba-bility of a totally unexpected action approaches zero in infinity, but the game is repeated only afinite number of times.Thus the probability remains instead a small positive value.In addition,we assume that the types of a player are sta-tistically independent and thus uncorrelated.The assumptions we have made are general assumptions that are usually made in game-theoretic systems that use dynamic Bayesian systems. In addition,from the definition of the belief system and the update rule,it follows that our model satisfies the Bayesian conditions given in the Appendix.To analyze optimality of our model,we would like to apply subgame perfection[22]and especially its extension to perfect Bayesian equilibrium to our model.A game is said to be subgame perfect,if the restriction of strategies to a single stage(time period)constitutes a Nash-equilibrium.Thus if we"forget"the previous play and look only at the current situation,the actions the players perform must form an optimal agreement between the players.Perfect Bayesian equilibrium (PBE)extends subgame perfection to games with incomplete information.In PBE,each stage game played at a single period must constitute a Bayes-Nash equilibrium.In other words, when the actions are restricted to a single time period they must be optimal given the beliefs the players have at the beginning of that time period.In a Bayes-Nash equilibrium optimal strategies can be defined as behaviour strategies that maximize the expected utility of a player.According to this definition,the sender’s optimal strategy is the number of packets it should send to the network in order to maximize its utility.However,before we can define the optimal actions in a broadcast model,we need to define optimality in a unicast model.In a unicast communication model the sender and the forwarder communicate directly with each other.In this model the optimal strategy of the sender is given by Definition 2.For notational simplicity,the time indices have been omitted from all variables in the remainder of this Section. DEFINITION2:The optimal behaviour policy of the sender at time period isThe probabilities were defined in Equation4and the term is a behaviour strategy of player in the game where node acts as the sender.The behaviour strategy tells the probability that node performs the action given the action of the sender.Finally,the term is the utility function of node which was defined in Equation7.In the broadcast model it is rational to send packets if some neighbouring node is willing to forward them.The optimal sender strategy in the broadcast model is defined as the maximum of the optimal strategies of individual"unicast" games.This modification is given in Definition3.DEFINITION3:The optimal behaviour policy of the sender at time period in a broadcast model.In Definition3we have made the assumption that packets are numbered and that the decision making process of forwarding nodes considers the individual packets in numbering order. The optimal strategy of the forwarder can be defined in a similar manner.The forwarder makes a decision only after the sender has already made some action.The action performed by the sender is observable so the forwarder has more information available than the sender.Again,the optimal behaviour strategy of the forwarder is the strategy that maximizes the expected utility given the current beliefs. The form of the utility should be such that it measures expected gain in future throughput.The formal definition of the optimal strategy is given in Definition4where the term was defined in Equation5.DEFINITION4:Optimal behaviour policy of the for-warder at time period.Here is the behaviour strategy of the sender which tells the probability that node sends packets(at time period )given her energy class.Together with the belief systemIV.R OUTING M ODEL AND I MPLEMENTATION I SSUES The theoretical model presented in the previous section has two main contributions.First of all it allows theoretical analysis of various routing protocols.Secondly,it makes it possible to implement new"intelligent"routing protocols that can be theoretically justified.In this section we discuss implementation issues related to our model by introducing apseudo-protocol that implements all relevant aspects of our model.The pseudo-protocol consists of two phases.In thefirst phase a node joins an ad hoc network by discovering its neighbours and by assigning prior probabilities over the energy class values of the neighbours.As in the previous section, we assume that each packet is broadcasted to all neighbours and thus,to discover its neighbours,a nodefirst sends a JOIN message to the network.The nodes that respond form the neighbourhood.Additionally,the node constructs a prior probability distribution over the energy class values of the neighbours.The general form of the initialization phase is presented in Algorithm1.Send JOIN messagewhile receives messages dosender of messageConstructend while Algorithm2Initialization of priors formust perform the same operations.Thus each time a node receives a JOIN-message,it must construct a new probability distribution for the new node.The second phase of the pseudo-protocol is a working phase. After a node has joined the network it is ready to work as an ordinary peer.This means that the node listens to incoming traffic and when it notices messages that require an action it decides what action to perform(if any).In addition,at certain periods of time the node generates traffic(packets of its own) that must be sent to the network.The decisions made in the forwarding process depend on the type of the message.If the message is a JOIN-message, the node must respond by sending the corresponding response message(see discussion above).If the message is a forward request,the node must update its belief system and decide whether to forward the message or not.The decision is based on Definition4and the general form of the forwarding process is presented in Algorithm3.The last type of message that needs to be discussed is that the message is a forwarded message that node has generated.This means that the stage game at period ends and that the node must update its beliefs about the energy class of the neighbour that forwarded the message.Even withInput:messages m from node at period: Calculate posterior:broadcasting,the update operations are carried out in a pair-wise manner to assure correctness of beliefs.This means that at this point only the probability of node is updated.To allow"late"updates,meaning that the node has gone on to state for some and that it receives a forwarding decision of the stage from another node,we need to have a well-defined packet numbering.The main practical difference of our model with regards to other routing protocols is the extensive use of probability distributions.However,probability calculations are easily time (and energy)consuming so it is of utmost importance to im-plement the probability distributions as efficiently as possible. Another important factor that has a large effect on efficiency is the number of packets a node can send within a single frame and the number of possible energy classes.In practice,if the number of possible values is sufficiently small,the calculations can be often implemented efficiently enough by enumerating all alternatives.V.C ONCLUSIONS AND F UTURE W ORKIn this article we presented a new theoretical model that can be used to analyze routing behaviour in wireless ad hoc networks.We did notfix the form of the utility functions or the form of the probability functions as it is hard to give a theoretical justification to why a particular kind of functions or distributions should be used.The model presented in this article can be extended to take into account related sources of uncertainty,such as node mobility.It is only required that a probability distribution is defined over the new source of uncertainty and that the probabilities are updated using the Bayes’rule whenever possible.As long as the beliefs are consistent with the information obtained and the actions are optimal given the beliefs,the model is theoretically consistent. However,the theoretical bounds of optimality of the probabil-ity system are less attractive when thefiniteness of the games is taken into account and in practice the prior probabilities need to be carefully assigned,especially as the number of sources of uncertainty increases.In the future,our goals are both theoretical and practical. The main practical goal is to test different utility functions and probability distributions and to compare them in networks with different network parameters such as the number of selfish nodes or rate of node mobility.In addition,our goal is to compare the new model to existing approaches.The theoret-ical goals are to extend the model into a multi-hop model and to analyze behaviour strategies and belief systems more thoroughly.In addition,our goal is to extend the theoretical model so that node mobility is taken into account.The main contribution of this article is the definition of a formal routing model,in which decision making is non-simultaneous and the game play is modelled as a series of games where the nodes remember the previous actions of the game and where the model parameters are continuously updated.A CKNOWLEDGMENTSThe author thanks Floris Geerts for helpful discussions at various stages of the work.Additionally,the author thanks Patrik Floréen,Niina Haiminen,Jussi Kollin and Greger Lindén for comments on earlier drafts.R EFERENCES[1] C.E.Perkins,Ed.,Ad Hoc Networking.New York:Addison-Wesley,2001.[2] D.B.Johnson,D.A.Maltz,and J.Broch,“DSR:The dynamic sourcerouting protocol for multi-hop wireless ad hoc networks,”in Ad Hoc Networking,C.E.Perkins,Ed.New York:Addison-Wesley,2001, ch.5,pp.139–172.[3]P.Michiardi and R.Molva,“Simulation-based analysis of securityexposures in mobile ad hoc networks,”in European Wireless Conference, 2002.[4] D.Fudenberg and J.Tirole,Game Theory.Cambridge,Massachusetts:MIT Press,1991.[5]P.Resnick,R.Zeckhauser,E.Friedman,and K.Kuwabara,“Reputationsystems:Facilitating trust in internet interactions,”Communications of the ACM,vol.43,no.12,pp.45–48,Dec.2000.[6]S.Marti,T.J.Giuli,i,and M.Baker,“Mitigating routingmisbehavior in mobile ad hoc networks,”in Proceedings of the6th Annual International Conference on Mobile Computing and Networking, Aug.2000,pp.255–265.[7]P.Michiardi and R.Molva,“Core:a collaborative reputation mech-anism to enforce node cooperation in mobile ad hoc networks,”in Proceedings of the IFIP TC6/TC11Sixth Joint Working Conference on Communications and Multimedia Security:Advanced Communications and Multimedia Security.Kluwer,2002,pp.107–121.[8]S.Buchegger and J.-Y.L.Boudec,“Performance analysis of the CON-FIDANT protocol:Cooperation of nodes–fairness in dynamic ad hoc networks,”in Proceedings of the3rd ACM International Symposium on Mobile Ad Hoc Networking and Computing,2002,pp.226–236. [9]L.Buttyán and J.-P.Hubaux,“Stimulating cooperation in self-organizingmobile ad hoc networks,”Mobile Networks and Applications,vol.8, no.5,pp.579–592,Oct.2003.[10]L.Anderegg and S.Eidenbenz,“Ad hoc-VCG:a truthful and cost-efficient routing protocol for mobile ad hoc networks with selfish agents,”in Proceedings of the9th Annual International Conference on Mobile Computing and Networking(MobiCom).ACM Press,2003,pp.245–259.[11]W.Vickrey,“Counterspeculation,auctions,and competitive sealed ten-ders,”The Journal of Finance,vol.16,no.1,pp.8–37,Mar.1961.[12] E.H.Clarke,“Multipart pricing of public goods,”Public Choice,vol.8,pp.19–33,1971.[13]T.Groves,“Incentives in teams,”Econometrica,vol.41,no.4,pp.617–631,July1973.[14]V.Srinivasan,P.Nuggehalli,C.F.Chiasserini,and R.R.Rao,“Co-operation in wireless ad hoc networks,”in Proceedings of the22nd INFOCOM,vol.2.IEEE,Mar.2003,pp.808–817.[15]N.Nisan and A.Ronen,“Algorithmic mechanism design,”Games andEconomic Behaviour,vol.35,pp.166–196,2001.[16] E.Altman,A.A.Kherani,P.Michiardi,and R.Molva,“Non-cooperativeforwarding in ad hoc networks,”INRIA,Sophia Antipolis,France,Tech.Rep.RR-5116,Feb.2004.[17] A.Urpi,M.Bonuccelli,and S.Giordano,“Modelling cooperationin mobile ad hoc networks:a formal description of selfishness,”in Proceedings of Modelling and Optimization in Mobile,Ad Hoc and Wireless Networks(WiOpt),Mar.2003.[18]J.C.Harsanyi,“Games with incomplete information played by Bayesianplayers,part I.The basic model,”Management Science,vol.14,no.3, pp.159–182,Nov.1967.[19]——,“Games with incomplete information played by Bayesian players,part II.Bayesian equilibrium points,”Management Science,vol.14, no.5,pp.320–334,Jan.1968.[20]——,“Games with incomplete information played by Bayesian players,part III.The basic probability distribution of the game,”Management Science,vol.14,no.7,pp.486–502,Mar.1968.[21] D.M.Kreps and R.Wilson,“Sequential equilibria,”Econometrica,vol.50,no.4,pp.863–894,July1982.。
