SonicWALL防火墙说明
SonicWALL 防火墙 HA 配置
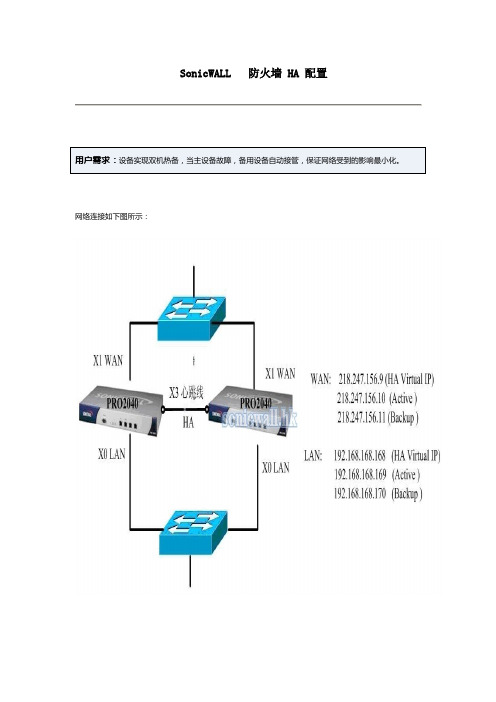
SonicWALL 防火墙 HA 配置网络连接如下图所示:SonicWALL HA是Active/Passive方式的HA,配置界面相当简单,所有配置只需要在主设备上配置,备用设备会自动同步主设备的配置。
配置主设备时,不要打开备用设备电源,待主设备配置完毕之后,连接好物理线路,打开备用设备电源,备用设备自动与主设备同步全部的配置信息。
注意:备用设备要和主设备采用同样的操作系统版本号。
如果备用设备启用UTM的功能,那么备用设备要提前注册,拿到全部的UTM的授权。
主设备的UTM License不会同步到备用设备。
1.进入主设备的管理界面https://192.168.168.168, 默认的LAN口IP地址,用户名是 admin, 密码password2.进入Network->Interfaces界面,配置X1口(WAN),X0口(LAN)的IP地址。
这里X1口是WAN口,IP 地址218.247.156.9, 这个地址将成为HA发生切换之后WAN口的虚拟地址,从WAN外部通过218.247.156.9能访问到当前工作的设备,即如果主设备宕机,那么通过这个地址访问到的是备用设备。
X0 口IP地址用默认的 192.168.168.168. 这个地址将成为HA发生切换之后LAN口的虚拟地址,从LAN 内部通过192.168.168.168能访问到当前工作的设备,即如果主设备宕机,那么通过这个地址访问到的是备用设备。
3.进入Hardware Failover->Setting 界面,选中Enable Hardware Failover激活HA配置,点右上角的Apply按钮使HA生效。
如果希望主设备恢复后立刻切换回到主设备工作,那么选中Enable Preempt Mode,点右上角的Apply按钮使之生效.4.进入Hardware Failover->Monitoring界面,点X0口的配置按钮,5.在Interface X0 Monitoring Settings界面的Primary IP Address, Backup IP Address分别填写主/备设备的管理IP地址。
SonicWALL配置手册--
SonicWALL防火墙标准版配置SonicWall标准版网络向导配置 (1)SonicWall标准版规则向导配置 (7)SonicWall标准版一般规则向导配置 (7)SonicWall标准版服务器规则向导配置 (12)SonicWall标准版一般规则直接配置 (15)SonicWall标准版服务器1对1 NA T配置 (18)SonicWall标准版透明模式配置 (19)SonicWall标准版网络向导配置首次接触SonicWALL防火墙设备,我们将电源接上,并开启电源开关,将X0口和你的电脑相连(注:请用交叉线),SonicWALL防火墙默认的IP地址为192.168.168.168,我们也可以通过setuptool.exe这个小工具探知SonicW ALL防火墙的IP地址。
如图所示:当网线和电源等都连接好之后,我们设置一下本机的IP地址,以便和SonicWALL防火墙处于同一个网段。
如图所示:设置好IP地址后,我们在IE浏览器的地址栏输入SonicWALL防火墙的IP地址,点next,提示我们是否修改管理员密码,暂时不修改,点next,提示我们修改防火墙的时区,我们选择中国的时区。
点next,提示我们设置W AN口的地址获取类型,这时候,我们需要和ISP相联系,并选择相关的类型,这里以静态地址为例:我们点next,输入相关的信息,IP地址、掩码、网关、DNS服务器等,如果不知道此处该如何设置,请和你的ISP联系。
点next,提示我们设置LAN口的IP和掩码,我们根据自己的规划和网络的实际情况设置,此处我没有修改。
点next,防火墙询问我们在LAN口是否开启DHCP server的功能,并是否是默认的网段,我们可根据实际情况做调整,决定开始或关闭,以及网段地址等,如下图:点next,防火墙将把前面做的设置做一个摘要,以便我们再一次确认是否设置正确,如果有和实际不符的地方,可以点back返回进行修改。
sonicwall防火墙中文教程

2019/12/2
39
PRO4060 Shared Secret
2019/12/2
40
PRO4060 Log PAYLOAD_MALFORMED 表示共享密钥不匹配,网络故障导致VPN隧道 断开,如果隧道两端VPN设备采用的DPD不是 一个标准,重新协商时也可能出现此错误
2019/12/2
41
TCP 超时时间的设置,TCP Setting和防火墙规则设置
2019/12/2
11
SonicOS 标准版 防火墙LAN口和WAN口透明
2019/12/2
12
2019/12/2
13
2019/12/2
14
2019/12/2
15
注:透明模式并不意味着所有的业务端 口都“透明”,必须设置必要的防火 墙规则以允许WAN到LAN或WAN到DMZ服 务器的访问。
2019/12/2
46
防火墙不能升级签名的诊断步骤
1. 确认LAN PC能通过防火墙WAN口访问互联网
2. 确认防火墙System->Diagnostics里的DNS解析能解析
3. 防火墙通过HTTPS直接访问 ,不能经过代理 服务器.
ARP代理透明
设备工作在3层,设备的两个端口处于同一个网段,但两个端 口占用同一个IP地址,需要管理员指定哪些网络范围的IP 地址在设备的某一个端口,使设备能正确转发数据包到正 确的端口。
SonicWALL的UTM设备透明方式是ARP代理透明,需要在WAN口 和LAN口(或DMZ口)占用一个IP地址。
2019/和ARP代理透明
2.SonicOS 标准版透明 3.SonicOS 增强版透明
2019/12/2
SonicWALL NSA UTM防火墙规则说明

防火墙的基本功能就是实现对于内外网之间的访问控制,和路由器及交换机产品类似,防火墙也使用一种策略的规则来实现管理,这也是一种ACL(Access Control List)。
防火墙规则是由5个部分组成,源地址、源端口、目的地址、目的端口、执行动作来决定。
SonicWALLNSA系列产品都是采用基于对象的控制方式,通过定义不同的对象,然后把它们组合到一条策略中,来实现访问规则的配置。
防火墙规则能够控制到单向访问,配置防火墙策略,首先需要判定访问方向,如果方向不对,就会出现配置好的策略不起作用,或根本无法达到应有的目的等情况。
访问方向的是按照发起方来进行判定的,如从内网访问外网的WEB网站,就属于从内网访问外网方向(LAN->WAN)。
不同方向的访问规则不会相互干扰。
常见的防火墙策略的方向分为从外网(WAN)到内网(LAN),从内网到外网,从内网到DMZ,从DMZ到内网,从DMZ到外网,从外网到DMZ等几种。
最常用的就是从内网(LAN)到外网(WAN)的策略配置,因为要控制内网的用户到外网的访问。
在配置几条策略在一个访问方向的时候,需要注意到是策略的排列,防火墙产品对于策略的匹配是有规则的,上面的规则优先于下面的规则,(上面是指在规则界面中排在上方的规则),当防火墙进行策略匹配时,一旦查询到一条匹配规则,防火墙将停止向下查询。
如果同时需要做几个规则,需要考虑这几条规则的逻辑关系。
SonicWALL NSA产品在出厂默认情况下,规则是从安全级别高的区域,如内网(LAN)到所有安全级别低的区域-------如外网(WAN)和DMZ--------是允许访问的,而从安全级别低的区域到安全级别高的区域,是禁止访问的。
SonicWALL UTM防火墙是基于对象管理的,防火墙规则是在各个安全区域之间定义的。
只要把一个物理端口划分到一个安全区域,在防火墙的Firewall->Access Rules界面就可以定制各个区域之间的安全规则。
SonicWALL PRO3060防火墙配置

SonicWALL PRO3060防火墙配置SonicWall网络向导配置 (1)SonicWall规则配置 (7)SonicWall一般规则配置 (7)SonicWall服务器规则向导配置 (10)SonicWall透明模式配置 (13)SonicWall对象配置 (16)SonicWall网络向导配置首次接触SonicW ALL防火墙设备,我们将电源接上,并开启电源开关,将X0口和你的电脑相连(注:请用交叉线),SonicWALL防火墙默认的IP地址为192.168.168.168当网线和电源等都连接好之后,我们设置一下本机的IP地址,以便和SonicWALL防火墙处于同一个网段。
如图所示:设置好IP地址后,我们在IE浏览器的地址栏输入SonicWALL防火墙的IP地址,防火墙将弹出网络配置向导界面点next,提示我们是否修改管理员密码,根据需要我们将密码设置为实际密码,点next,提示我们修改防火墙的时区,我们选择中国的时区。
点next,提示我们设置W AN口的地址获取类型,这时候,我们需要和ISP相联系,并选择相关的类型,这里以静态地址为例:点next,输入相关的信息,IP地址、掩码、网关、DNS服务器等,如果不知道此处该如何设置,请和你的ISP联系。
点next,提示我们设置LAN口的IP和掩码,我们根据自己的规划和网络的实际情况设置,此处我没有修改。
点next,设置DHCP server的相关配置,如果不开启,把勾取消即可。
点next,点apply,设置生效。
点close,回到登陆界面输入帐号密码后,点login当把配置做好以后,我们将防火墙的X1口接到ISP进来的网线上,将X0口接到内网交换机上。
SonicWall规则配置SonicWall一般规则配置这时,我们已经可以访问外网了。
此时的策略是默认允许内网的所有机器可以任意的访问外网,为了符合公司的安全策略,我们如果要相关的安全策略,限制一些访问的协议。
SonicWALL配置手册--

SonicWALL防火墙标准版配置SonicWall标准版网络向导配置 (1)SonicWall标准版规则向导配置 (11)SonicWall标准版一般规则向导配置 (11)SonicWall标准版服务器规则向导配置 (21)SonicWall标准版一般规则直接配置 (25)SonicWall标准版服务器1对1 NAT配置 (29)SonicWall标准版透明模式配置 (31)SonicWall标准版网络向导配置首次接触SonicWALL防火墙设备,我们将电源接上,并开启电源开关,将X0口和你的电脑相连(注:请用交叉线),SonicWALL防火墙默认的IP地址为192.168.168.168,我们也可以通过setuptool.exe这个小工具探知SonicWALL防火墙的IP地址。
如图所示:页脚内容1当网线和电源等都连接好之后,我们设置一下本机的IP地址,以便和SonicWALL防火墙处于同一个网段。
如图所示:设置好IP地址后,我们在IE浏览器的地址栏输入SonicWALL防火墙的IP地址,页脚内容2点next,提示我们是否修改管理员密码,页脚内容3暂时不修改,点next,提示我们修改防火墙的时区,我们选择中国的时区。
页脚内容4点next,提示我们设置WAN口的地址获取类型,这时候,我们需要和ISP相联系,并选择相关的类型,这里以静态地址为例:页脚内容5我们点next,输入相关的信息,IP地址、掩码、网关、DNS服务器等,如果不知道此处该如何设置,请和你的ISP联系。
页脚内容6点next,提示我们设置LAN口的IP和掩码,我们根据自己的规划和网络的实际情况设置,此处我没有修改。
页脚内容7点next,防火墙询问我们在LAN口是否开启DHCP server的功能,并是否是默认的网段,我们可根据实际情况做调整,决定开始或关闭,以及网段地址等,如下图:页脚内容8点next,防火墙将把前面做的设置做一个摘要,以便我们再一次确认是否设置正确,如果有和实际不符的地方,可以点back返回进行修改。
sonicwall防火墙设置方法有哪些

sonicwall防火墙设置方法有哪些sonicwall防火墙想要设置下!用什么方法好呢?下面由店铺给你做出详细的sonicwall防火墙设置方法介绍!希望对你有帮助!sonicwall防火墙设置方法一:假设你要把服务器192.168.3.5的80端口映射出去,其中192.168.3.5做好了花生壳(或者你外网是个固定IP)首先到network→Services里,点击添加新建一个端口。
名称:TCP80,类型TCP,端口范围80-80.然后在SonicWALL右上角你可以看到一个三角形的按钮,叫Wizards ,点击那个按钮。
在弹出的页面中选择Public Server Wizard ,点击next,Server Type选择other,Services 就选择你刚才建立的TCP80,点击下一步Server Name就是你在防火墙上看到服务器的名字(以后可以在防火墙规则以及NAT规则里看到这个),随便起个自己认识的就行,Server Private IP Address就是你服务器的内网IP(192.168.3.5) 点击下一步之后,会出现Server Public IP Address,这个如果你是ADSL拨号的就不用管(如果是固定IP的话就填你的外网IP,不过这里一般防火墙会帮你自动填入)直接点击下一步,之后就会出来确认信息,点击apply应用设置即可。
等向导弹出结束按钮,按close退出即可。
至此,完成服务器192.168.3.5的80端口发布。
备注:默认情况下80口是被运营商封堵的,如果需要使用80端口直接打开,就必须去运营商处进行备案。
你也可以发布成其他端口,然后采用IP+端口号(例如202.96.133.22:8888)这样的进行访问。
sonicwall防火墙设置方法二:配置连接有三个基本步骤:配置SonicWALL防火墙,创建配置账户,安装和配置SonicWALL Global Client。
Dell SonicWALL NSA系列下一代防火墙用户手册说明书

Organizations of all sizes depend on their networks to access internal and external mission-critical applications. As advances in networking continueto provide tremendous benefits, organizations are increasingly challenged by sophisticated and financially-motivated attacks designed to disrupt communication, degrade performance and compromise data. Malicious attacks penetrate outdated stateful packet inspection firewalls with advanced application layer exploits. Point products add layers of security, but are costly, difficult to manage, limited in controlling network misuse and ineffective against the latest multipronged attacks.By utilizing a unique multi-core design and patented Reassembly-Free Deep Packet Inspection® (RFDPI) technology*, the Dell™ SonicWALL™ Network Security Appliance (NSA) Series of Next-Generation Firewalls offers complete protection without compromising network performance. The low latency NSA Series overcomes the limitations of existing security solutions by scanning the entirety of each packet for current internal and external threats in real-time. The NSA Series offers intrusion prevention, malware protection, and application intelligence, control and visualization, while delivering breakthrough performance. With advanced routing, stateful high-availability and high-speed IPSec and SSL VPN technology, the NSA Series adds security, reliability, functionality and productivity to branch offices, central sites and distributed mid-enterprise networks, while minimizing cost and complexity.Comprised of the Dell SonicWALL NSA 220, NSA 220 Wireless-N, NSA 250M, NSA 250M Wireless-N, NSA 2400, NSA 3500 and NSA 4500, the NSA Series offers a scalable range of solutions designed to meet the network security needs of any organization.Network SecurityAppliance SeriesNext-Generation Firewall• Next-Generation Firewall• Scalable multi-core hardware andReassembly-Free Deep PacketInspection• Application intelligence, controland visualization• Stateful high availability and loadbalancing• High performance and loweredtco• Network productivity• Advanced routing services andnetworking• Standards-based Voice over IP(VoIP)• Dell Sonicwall clean Wireless• onboard Quality of Service (QoS)• Integrated modules support• Border Gateway Protocol (BGP)support• More concurrent SSL VPN sessionsFeatures and benefitsNext-Generation Firewall features integrate intrusion prevention, gateway anti-virus, anti-spyware and URL filtering with application intelligence and control, and SSL decryption to block threats from entering the network and provide granular application control without compromising performance.Scalable multi-core hardware and Reassembly-Free Deep Packet Inspection scans and eliminates threats of unlimited file sizes, with near-zero latency across thousands of connections at wire speed.Application intelligence, control and visualization provides granular control and real-time visualization of applications to guarantee bandwidth prioritization and ensure maximum network security and productivity. Stateful high availability and load balancing features maximize total network bandwidth and maintain seamless network uptime, delivering uninterrupted access to mission-critical resources, and ensuring that VPN tunnels and other network traffic will not be interrupted in the event of a failover. High performance and lowered tcoare achieved by using the processingpower of multiple cores in unison todramatically increase throughput andprovide simultaneous inspectioncapabilities, while lowering powerconsumption.Network productivity increases becauseIT can identify and throttle or blockunauthorized, unproductive andnon-work related applications and websites, such as Facebook® or YouTube®,and can optimize WAN traffic whenintegrated with Dell SonicWALL WANAcceleration Appliance (WXA) solutions.Advanced routing services andnetworking features incorporate 802.1qVLANs, multi-WAN failover, zone andobject-based management, loadbalancing, advanced NAT modes, andmore, providing granular configurationflexibility and comprehensive protectionat the administrator’s discretion.Standards-based Voice over IP (VoIP)capabilities provide the highest levels ofsecurity for every element of the VoIPinfrastructure, from communicationsequipment to VoIP-ready devices suchas SIP Proxies, H.323 Gatekeepers andCall Servers.Dell SonicWALL clean Wirelessoptionally integrated into dual-bandwireless models or via Dell SonicWALLSonicPoint wireless access pointsprovides powerful and secure 802.11a/b/g/n 3x3 MIMO wireless, and enablesscanning for rogue wireless accesspoints in compliance with PCI DSS.onboard Quality of Service (QoS)features use industry standard 802.1pand Differentiated Services Code Points(DSCP) Class of Service (CoS)designators to provide powerful andflexible bandwidth management that isvital for VoIP, multimedia content andbusiness-critical applications.Integrated modules support on NSA250M and NSA 250M Wireless-Nappliances reduce acquisition andmaintenance costs through equipmentconsolidation, and add deploymentflexibility.Border Gateway Protocol (BGP)support enables alternate networkaccess paths (ISPs) if one path fails.More concurrent SSL VPN sessions addscalability, while extending End PointControl to Microsoft® Windows® devicesensures anti-malware and firewalls areup-to-date.Best-in-class threat protection Dell SonicWALL deep packetinspection protects against network risks such as viruses, worms, Trojans, spyware, phishing attacks, emerging threats and Internet misuse. Application intelligence and control adds highly controls to prevent data leakage and manage bandwidth at the application level.The Dell SonicWALL Reassembly-Free Deep Packet Inspection (RFDPI) technology utilizes Dell SonicWALL’s multi-corearchitecture to scan packets in real-time without stalling traffic in memory.This functionality allows threats to be identified and eliminated over unlimited file sizes and unrestricted concurrent connections, without interruption.The Dell SonicWALL NSA Series provides dynamic network protection through continuous, automated security updates, protecting against emerging and evolving threats, without requiring any administrator intervention.Dynamic security architectureand managementMobile users32Application intelligence and control Dell SonicWALL Application Intelligence and Control provides granular control, data leakage prevention, and real-time visualization of applications to guarantee bandwidth prioritization and ensure maximum network security and productivity. An integrated feature of Dell SonicWALL Next-Generation Firewalls, it uses Dell SonicWALL RFDPItechnology to identify and control applications in use with easy-to-use pre-defined application categories (such as social media or gaming)—regardless of port or protocol. Dell SonicWALL Application Traffic Analytics provides real-time and indepth historical analysis of data transmitted through the firewall including application activities by user.1Dell SonicWALL clean VPNDell SonicWALL Clean VPN™ secures the integrity of VPN access for remote devices including those running iOS or Android by establishing trust for remote users and these endpoint devices and applying anti-malware security services, intrusion prevention and application intelligence and control to eliminate the transport of malicious threats• The SonicWALL NSA 2400 is ideal for branch office and small- to medium-sized corporate environments concerned about throughput capacity and performance • The SonicWALL NSA 220, NSA 220 Wireless-N, NSA 250M and NSA 250M Wireless-N are ideal for branch office sites in distributed enterprise, small- to medium-sizedbusinesses and retail environmentscentralized policy managementThe Network Security Appliance Series can be managed using the SonicWALL Global Management System, which provides flexible, powerful and intuitive tools to manage configurations, viewreal-time monitoring metrics andintegrate policy and compliancereporting and application traffic analytics,all from a central location.Server Anti-Virusand Anti-SpywareServers anti-threatprotectionVPNVPNClientRemoteAccessUpgradeServiceWeb siteand contentusage control Enforced ClientAnti-Virusand Anti-SpywareClient PCs anti-threat protectionFlexible, customizable deployment options –NSA Series at-a-glanceEvery SonicWALL Network Security Appliance solution delivers Next-Generation Firewall protection, utilizing a breakthrough multi-core hardware design and Reassembly-Free Deep Packet Inspection for internal and external network protection without compromising network performance. Each NSA Series product combineshigh-speed intrusion prevention, file and content inspection, and powerful application intelligence and controlwith an extensive array of advanced networking and flexible configuration features. The NSA Series offers an accessible, affordable platform that is easy to deploy and manage in a wide variety of corporate, branch office and distributed network environments.• The SonicWALL NSA 4500 is ideal for large distributed and corporate central-site environments requiring high throughput capacity and performance • The SonicWALL NSA 3500 is idealfor distributed, branch office and corporate environments needing significant throughput capacity and performanceSecurity services andupgradesGateway Anti-Virus,Anti-Spyware, IntrusionPrevention and ApplicationIntelligence and controlService delivers intelligent,real-time network security protectionagainst sophisticated application layerand content-based attacks includingviruses, spyware, worms, Trojans andsoftware vulnerabilities such as bufferoverflows. Application intelligence andcontrol delivers a suite of configurabletools designed to prevent data leakagewhile providing granular application-level controls along with tools enablingvisualization of network traffic.Enforced client Anti-Virusand Anti-spyware (McAfee)working in conjunction withDell SonicWALL firewalls,guarantees that allendpoints have the latest versions ofanti-virus and anti-spyware softwareinstalled and active.content Filtering Serviceenforces protection andproductivity policies byemploying an innovativerating architecture, utilizingadynamic database to block up to 56categories of objectionable webcontent.Analyzer is a flexible, easyto use web-basedapplication traffic analyticsand reporting tool thatprovides powerful real-time andhistorical insight into the health,performance and security of the network.Virtual Assist is a remotesupport tool that enablesa technician to assumecontrol of a PC or laptopfor the purpose of providingremote technical assistance. Withpermission, the technician can gaininstant access to a computer using aweb browser, making it easy to diagnoseand fix a problem remotely without theneed for a pre-installed “fat” client.Dynamic Support Servicesare available 8x5 or 24x7depending on customerneeds. Features includeworld-class technicalsupport, crucial firmware updates andupgrades, access to extensive electronictools and timely hardware replacementto help organizations get the greatestreturn on their Dell SonicWALLinvestment.Global VPN clientUpgrades utilize a softwareclient that is installed onWindows-based computersand increase workforce productivity byproviding secure access to email, files,intranets, and applications for remoteusers.provide clientlessLinux-based systems. With integratedSSL VPN technology, Dell SonicWALLfirewall appliances enable seamless andsecure remote access to email, files,intranets, and applications from a varietyof client platforms via NetExtender, alightweight client that is pushed onto theuser’s machine.SonicWALL Mobile connect™,a single unified client app forApple® iOS and Google®Android™, provides smartphone andtablet users superior network-levelaccess to corporate and academicresources over encrypted SSL VPNconnections.comprehensive Anti-SpamService (CASS) offerssmall- to medium-sizedbusinesses comprehensiveprotection from spam andviruses, with instant deployment overexisting Dell SonicWALL firewalls. CASSspeeds deployment, eases administrationand reduces overhead by consolidatingsolutions, providing one-click anti-spamservices, with advanced configuration injust ten minutes.Deep Packet Inspection for of SSL-Encrypted traffic (DPI-SSL) transparentlydecrypts and scans both inbound andoutbound HTTPS traffic for threats usingDell SonicWALL RFDPI. The traffic is thenre-encrypted and sent to its originaldestination if no threats or vulnerabilitiesare discovered.Denial of Service attack prevention 22 classes of DoS, DDoS and scanning attacksKey exchange K ey Exchange IKE, IKEv2, Manual Key, PKI (X.509), L2TP over IPSec Route-based VPN Yes (OSPF, RIP)Certificate support Verisign, Thawte, Cybertrust, RSA Keon, Entrust, and Microsoft CA for Dell SonicWALL-to-Dell SonicWALL VPN, SCEP Dead peer detection Yes DHCP over VPN Yes IPSec NAT TraversalYes Redundant VPN gatewayYesGlobal VPN client platforms supported Microsoft Windows 2000, Windows XP, Microsoft Vista 32/64-bit, Windows 7 32/64-bitSSL VPN platforms supportedMicrosoft Windows 2000 / XP / Vista 32/64-bit / Windows 7, Mac 10.4+, Linux FC 3+ / Ubuntu 7+ / OpenSUSEMobile Connect platforms supported iOS 4.2 and higher, Android 4.0 and higherSecurity servicesDeep Packet Inspection Service Gateway Anti-Virus, Anti-Spyware, Intrusion Prevention and Application Intelligence and Control Content Filtering Service (CFS) HTTP URL,HTTPS IP, keyword and content scanning ActiveX, Java Applet, and cookie blocking bandwidth management on filtering categories, allow/forbid lists Gateway-enforced Client Anti-Virus and Anti-Spyware McAfee Comprehensive Anti-Spam Service Supported Application Intelligence Application bandwidth management and control, prioritize or block application and Control by signatures, control file transfers, scan for key words or phrasesDPI SSL Provides the ability to decrypt HTTPS traffic transparently, scan this traffic for threats using Dell SonicWALL’s Deep Packet Inspection technology (GAV/AS/IPS/ Application Intelligence/CFS), then re-encrypt the traffic and send it to its destination if no threats or vulnerabilities are found. This feature works for both clients and workingIP Address assignment Static, (DHCP, PPPoE, L2TP and PPTP client), Internal DHCP server, DHCP relay NAT modes1:1, 1:many, many:1, many:many, flexible NAT (overlapping IPs), PAT, transparent modeVLAN interfaces (802.1q) 25352550200Routing OSPF, RIPv1/v2, static routes, policy-based routing, MulticastQoS Bandwidth priority, maximum bandwidth, guaranteed bandwidth, DSCP marking, 802.1pIPv6Yes AuthenticationXAUTH/RADIUS, Active Directory, SSO, LDAP, Novell, internal user database, Terminal Services, Citrix Internal database/single sign-on users 100/100 Users150/150 Users250/250 Users300/500 Users1,000/1,000 UsersVoIPFull H.323v1-5, SIP, gatekeeper support, outbound bandwidth management, VoIP over WLAN, deep inspection security, full interoperability with most VoIP gateway and communications devicesSystemZone security Yes SchedulesOne time, recurring Object-based/group-based management Yes DDNSYesManagement and monitoring Web GUI (HTTP, HTTPS), Command Line (SSH, Console), SNMP v3: Global management with Dell SonicWALL GMSLogging and reporting Analyzer, Local Log, Syslog, Solera Networks, NetFlow v5/v9, IPFIX with extensions, real-time visualizationHigh availabilityOptional Active/Passive with State SyncLoad balancing Yes, (Outgoing with percent-based, round robin and spill-over); (Incoming with round robin,random distribution, sticky IP, block remap and symmetrical remap)StandardsTCP/IP, UDP, ICMP, HTTP, HTTPS, IPSec, ISAKMP/IKE, SNMP, DHCP, PPPoE, L2TP, PPTP, RADIUS, IEEE 802.3Wireless standards802.11 a/b/g/n, WPA2, WPA, TKIP, 802.1x, EAP-PEAP, EAP-TTLS WAN acceleration supportYesFlash memory32 MB compact Flash 512 MB compact Flash3G wireless/modem * With 3G/4G USB adapter or modem — With 3G/4G USB adapter or modemPower supply 36W external Single 180W ATX power supplyFansNo fan/1 internal fan 2 internal fans 2 fansPower input10-240V, 50-60Hz Max power consumption 11W/15W 12W/16W 42W 64W 66W Total heat dissipation 37BTU/50BTU 41BTU/55BTU 144BTU 219BTU 225BTUCertificationsVPNC, ICSA Firewall 4.1 EAL4+, FIPS 140-2 Level 2, VPNC, ICSA Firewall 4.1, IPv6 Phase 1, IPv6 Phase 2Certifications pending EAL4+, FIPS 140-2 Level 2, IPv6 Phase 1, IPv6 Phase 2 —Form factor 1U rack-mountable/ 1U rack-mountable/ 1U rack-mountable/ and dimensions 7.125 x 1.5 x 10.5 in/ 17 x 10.25 x 1.75 in/ 17 x 13.25 x 1.75 in/18.10 x 3.81 x 26.67 cm 43.18 x 26 x 4.44 cm 43.18 x 33.65 x 4.44 cmWeight 1.95 lbs/0.88 kg/ 3.05 lbs/1.38 kg/ 8.05 lbs/ 3.65 kg 11.30 lbs/ 5.14 kg2.15 lbs/0.97 kg3.15 lbs/1.43 kg WEEE weight V 3.05 lbs/1.38 kg/4.4 lbs/2.0kg/ 8.05 lbs/ 3.65 kg 11.30 lbs/5.14 kg3.45 lbs/1.56 kg4.65 lbs/2.11 kgMajor regulatoryF CC Class A, CES Class A, CE, C-Tick, VCCI, Compliance MIC, UL, cUL, TUV/GS, CB, NOM, RoHS, WEEE Environment 40-105° F, 0-40° C 40-105° F, 5-40° CMTBF 28 years/15 years 23 years/14 years 14.3 years 14.1 years 14.1 yearsHumidity5-95% non-condensing 10-90% non-condensingcertificationsSpecificationsTesting methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services. Full DPI Performance/Gateway AV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs. Actual maximum connection counts are lower when Next-Generation Firewall services are enabled. VPN throughput measured using UDP traffic at 1280 byte packet size adhering to RFC 2544. Supported on the NSA 3500 and higher. Not available on NSA 2400. *USB 3G card and modem are not included. See http://www.Dell /us/products/cardsupport.html for supported USB devices. The Comprehensive Anti-Spam Service supports an unrestricted number of users but is recommended for 250 users or less. With Dell SonicWALL WXA Series Appliance.Network Security Appliance 3500 01-SSC-7016NSA 3500 TotalSecure* (1-year) 01-SC-7033Network Security Appliance 450001-SSC-7012NSA 4500 TotalSecure* (1-year) 01-SC-7032Network Security Appliance 2400 01-SSC-7020NSA 2400 TotalSecure* (1-year) 01-SC-7035Network Security Appliance 250M 01-SSC-9755Network Security Appliance 250M Wireless-N 01-SSC-9757 (US/Canada)Network Security Appliance 250M TotalSecure* 01-SSC-9747Network Security Appliance 250M Wireless-N TotalSecure*01-SSC-9748 (US/Canada)Network Security Appliance 220 01-SSC-9750Network Security Appliance 220 Wireless-N 01-SSC-9752 (US/Canada)Network Security Appliance 220 TotalSecure* 01-SSC-9744Network Security Appliance 220 Wireless-N TotalSecure*01-SSC-9745 (US/Canada)For more information on Dell SonicWALL network security solutions, please visit .*Includes one-year of Gateway Anti-Virus, Anti-Spyware, Intrusion Prevention, andApplication Intelligence and Control Service, Content Filtering Service and Dynamic Support 24x7.Security Monitoring Services from Dell SecureWorks are available for thisappliance Series. For more information, visit /secureworks。
SonicWall防火墙透明模式配置(三层交换机)
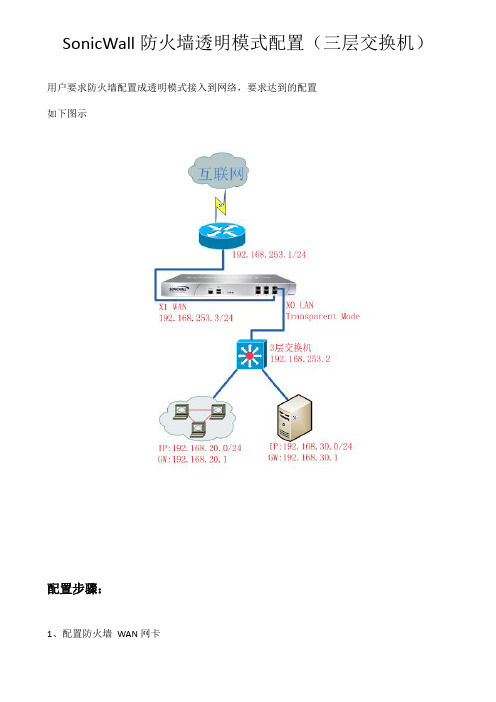
SonicWall防火墙透明模式配置(三层交换机)用户要求防火墙配置成透明模式接入到网络,要求达到的配置
如下图示
配置步骤:
1、配置防火墙WAN网卡
2、建立透明模式下的地址对象
(注意:透明范围不能够包含了防火墙本身的地址(192.168.254.21)以及防火墙的网关地址(192.168.254.1) ,同时也不能够包含防火墙WAN口外面的地址,即如果防火墙WAN外面还有其他的地址如192.168.254.200 则Transparent Range 不能够包含该地址, 否则可能会引发安全问题!!)
3、建立内网地址对象(注意:本范例中仅示例了2 个内网网段,可根据实际情况增加)
4、建立地址对象组
5、配置内网3 层交换机的地址对象
6、配置完成后的界面显示如下:
7、配置内网地址访问外网的回程路由(必须配置!!)
8、配置防火墙LAN网卡配置透明模式
9、关闭防火墙DHCP服务器
配置完成!。
sonicwall防火墙如何设置

sonicwall防火墙如何设置安装了sonicwall防火墙,但不会设置,该怎么办呢?下面由店铺给你做出详细的sonicwall防火墙设置方法介绍!希望对你有帮助!sonicwall防火墙设置方法一:进入管理页面,有一个配置向导,按照那个一步步来,可以初步连接上去,在此基础上你可以再进行其他的管理配置sonicwall防火墙设置方法二:最简单的方法自然是使用向导,登录防火墙之后,右上角有个Wizards,点那个,然后进去之后选择Public Server Wizard,一步一步来就可以了,服务器类型看你要建立哪种服务器,根据需要选择后面那一页是填服务器名字,你服务器内网IP,还有备注。
最后那外网IP防火墙会根据当前WAN口IP自动填写,一般来说没必要改。
最后完成就行了,防火墙会自动创建相关规则,很方便。
如果不使用向导,就得做以下步骤:首先要设置访问规则,在防火墙filewall里的WAN→LAN,设置源IP为any,目的地址是你内网那个IP,然后服务选择相应的端口(例如是网页服务器就选择HTTP什么的,也可以自定义)。
端口any即可。
之后需要在network里做NAT策略,源地址any,不转换;目的地址是你的防火墙外网地址,转换为你的那个内网地址,端口和上面防火墙上设置的一样。
之后如果你想在内网使用外网IP来访问服务器,就需要再做NAT 策略,把内网的地址转换为公网IP,否则你无法在内网使用域名或者外网IP访问服务器(当然内网IP是可以的)。
相关阅读:sonicwall防火墙介绍优点:SonicWALL®网络安全设备(NSA)系列下一代防火墙采用了独特的多核设计以及具有专利的免重组深度包检测®(RFDPI)技术*,让您无需牺牲网络性能即可获得全方位的安全保护。
NSA系列克服了现有安全解决方案的各种局限性它能实时地对每一个数据包执行整体扫描,以检测当前出现的内部及外部威胁。
NSA系列提供了入侵防御、恶意软件保护以及应用智能、控制和可视化功能,同时提供了突破性性能。
SonicWall NSv 虚拟防火墙安全指南说明书

The design, implementation and deployment of modern network architectures, such as virtualization and cloud, continue to be a game-changing strategy for many organizations. Virtualizing the data center, migratingto the cloud, or a combination of both, have demonstrated significant operational and economic advantages. However, vulnerabilities within virtual environments are well-documented. New vulnerabilities are discovered regularly that yield serious security implications and challenges. To ensure application services are delivered safely, efficiently and in a scalable manner, while combating threats harmful to all parts of the virtual framework including virtual machines (VM), application workloads and data must be among the top priorities. SonicWall Network Security virtual (NS v) firewalls help security teams reduce these types of security risks and vulnerabilities, which can cause serious disruptionto your business-critical services and operations. With full-featured security tools and services including reassembly-free deep packet inspection (RFDPI), security controls and networking services equivalent to what a SonicWall physical firewall provides, NS v effectively shield all critical components of your private or public cloud environments.NS v is easily deployed and provisioned in a multi-tenant virtual environment, typically between virtual networks (VNs). This allows it to capture communications and data exchanges between virtual machines for automated breach prevention, while establishing stringent access control measures for data confidentiality and VMs safety and integrity. Security threats (suchas cross-virtual-machine or side-channel attacks and common network-based intrusions and applicationand protocol vulnerabilities) are neutralized successfully through SonicWall’s comprehensive suite of security inspection services1. All VM traffic is subjected to multiple threat analysis engines, including intrusion prevention, gateway anti-virus andanti-spyware, cloud anti-virus, botnet filtering, application control and Capture Advanced Threat Protection multi-engine sandboxing.SonicWall Network Securityvirtual (NS v) seriesNext-gen security for public, private or hybrid cloud environmentsBenefits:Public and private cloud security• Attain Next-Gen firewall capabilitiescoupled with agility, scalabilityand security of the cloud withoutperformance impact• Gain complete visibility and controlof your virtual infrastructurefor automated real-time threatprevention• Ensure appropriate placement ofsecurity policies• Deliver safe application enablementrules by application, user and deviceregardless of VM location• Leverage multi-tenancy and micro-segmentation, with proper securityzoning and isolations• Platform support across privatecloud platform (ESXi, Hyper-V3) andpublic cloud platforms (AWS3, Azure)• Flexible licensing modelsVirtual machine protection• Defend against zero-dayvulnerabilities with CaptureAdvanced Threat Protection (ATP)• Prevent unauthorized takeover ofvirtual systems• Stop unauthorized access toprotected data assets• Block malicious and intrusiveactions, such as spreading malware,executing operating systemcommands, file system browsing andC&C communication• Prevent service disruption of anypart or entire virtual ecosystemSegmentation SecurityFor optimal effectiveness against Advanced Persistent Threats (APTs), network security segmentation must apply an integrated set of dynamic, enforceable barriers to advanced threats. With segment-based security capabilities, NS v can group similar interfaces and apply the same policies to them, instead of having to write the same policy for each interface. By applying security policies to the inside of the VN, segmentation can be configured to organize network resources into different segments, and allow or restrict traffic between those segments. This way, access to critical internal resources can be strictly controlled.NS v can automatically enforce segmentation restrictions based upon dynamic criteria, such as user identity credentials, geo-IP location and the security stature of mobile endpoints. For extended security, NS v it also capableof integrating multi-gigabit network switching into its security segment policy and enforcement. It directs segment policy to traffic at switching points throughout the network, and globally manage segment security enforcement from a single pane of glass.Since segments are only as effectiveas the security that can be enforced between them, NS v applies intrusion prevention service (IPS) to scan incoming and outgoing traffic on the VLAN segment to enhance security for internal network traffic. For each segment,it enforces a full range of security services on multiple interfaces based on enforceable policy.Flexible Deployment Use CasesWith infrastructure support for high availability (HA) implementation,NS v fulfills scalability and availability requirements of Software Defined Data Centers (SDDC). It ensures system resiliency, service reliability, and regulatory conformance. Optimized for broad range of public, private and hybrid deployment use cases, NS v can adapt to service-level changes and ensure VMs and their application workloads and data assets are available, as well as secure.It can do it all at multi-Gbps speed and low latency. Organizations gain all the securityadvantages of a physical firewall, withthe operational and economic benefitsof virtualization. This includes systemscalability, operation agility, provisioningspeed, simple management andcost reduction.The NS v Series is available in multiplevirtual flavors carefully packaged forbroad range of virtualized and clouddeployment use cases. Delivering multi-gigabit threat prevention and encryptedtraffic inspection performance, theNS v Series can adapt to capacity-levelincreases and ensure VNs safety andapplication workloads and data assets areavailable as well as secure.Governs CentrallyNS v deployments are centrally managedusing both on premise with SonicWallGMS2, and with SonicWall CaptureSecurity Center2, an open, scalablecloud security management, monitoring,reporting and analytics softwarethat is delivered as a cost-effectiveas-a-service offering.Capture Security Center gives theultimate in visibility, agility and capacityto govern the entire SonicWall virtual andphysical firewall ecosystem with greaterclarity, precision, and speed – all from asingle-pane-of-glass.FeaturesSonicOS PlatformThe SonicOS architecture is at the coreof every SonicWall physical and virtualfirewall including the NSv and NS a Series,SuperMassive™ Series and TZ Series.Refer to the SonicWall SonicOS Platformdatasheet for complete list of featuresand capabilities.Automated breach prevention1This includes complete advanced threatprotection, including high-performanceintrusion and malware prevention, andcloud-based sandboxing.Around-the-clock security1New threat updates are automaticallypushed to firewalls in the field withactive security services, and takeeffect immediately without rebootsor interruptions.Zero-day protection1NS v protects against zero-day attackswith constant updates against the latestexploit methods and techniques thatcover thousands of individual exploits.Threat APINS v receives and leverages any andall proprietary, original equipmentmanufacturer and third-party intelligencefeeds to combat advanced threats,such as zero-day, malicious insider,compromised credentials, ransomwareand advanced persistent threats.Zone protectionNS v strengthens internal security bysegmenting the network into multiplesecurity zones, with intrusion preventionservice keeping threats from propagatingacross the zone boundaries. Creating andapplying access rules and NAT policiesto traffic passing through the variousinterfaces, it can allow or deny internalor external network access based onvarious criteria.Application intelligence and control1With application-specific policies, NS vprovides granular control over networktraffic on the level of users, emailaddresses, schedules, and IP-subnets. Itcontrols custom applications by creatingsignatures based on specific parametersor patterns unique to an application inits network communications. Internal orexternal network access are allowed ordenied based on various criteria.Data leakage preventionNS v provides the ability to scan streams of data for keywords. This restrict the transfer of certain file names, file types, email attachments, attachment types, email with certain subjects, and email or attachments with certain keywords or byte patterns.Application layer bandwidth management Using packet monitor, NS v can select among various bandwidth management settings to reduce network bandwidth usage by an application. This helps gain further control over the network.Secure communicationNS v ensures that data exchange between groups of virtual machines is done securely, including isolation,confidentiality, integrity, and information flow control within these networks via use of segmentation.Access controlNS v validates that only VMs that satisfy a given set of conditions are able to access data that belongs to another through the use of er authenticationNS v creates policies to control or restrict VM and workload access by unauthorized users.Data confidentialityNS v blocks information theft and illegitimate access to protected data and services.Virtual network resilience and availability NS v prevents disruption or degradation of application services and communications. System safety and integrityNS v stops unauthorized takeover of VM systems and services.Traffic validation, inspection and monitoring mechanismsNS v detects irregularities and malicious behaviors and stop attacks targeting VM workloads.¹ Requires SonicWall Advanced Gateway Security Services (AGSS) subscription.² SonicWall Global Management System and Capture Security Center require separate licensing or subscription.3 Pending Hyper-V and AWS Marketplace availabilityGOVERNS CENTRALLY• Establish an easy path to comprehensive security management, analytic reporting and compliance to unify your network security defense program • Automate and correlate workflows to form a fully coordinated security governance, compliance and risk management strategyCOMPLIANCE• Helps make regulatory bodies and auditors happy with automatic PCI, HIPAA and SOX security reports • Customize any combination of security auditable data to help you move towards specific compliance regulationsRISK MANAGEMENT• Move fast and drive collaboration, communication and knowledge across the shared security framework • Make informed security policy decisions based on time-critical and consolidated threat information for higher level of security efficiencyGMS provides a holistic approach to security governance, compliance and risk managementNS v Series system specificationsNS v Series system specifications con'tCurrently supporting SonicOS 6.5.0. SonicOS 6.5.2 support available end of calendar year.Memory with Jumbo frame disabled.Memory with Jumbo frame enabled. Additional memory is required for Jumbo frame enabled.High availability available on VMware ESXi platform and Microsoft Hyper-V.Published performance numbers are up to the specification and the actual performance may vary depending on underlying hardware, network conditions; firewall configuration and activated services. Performance and capacities may also vary based on underlying virtualization infrastructure, and we recommend additional testing within your environment to ensure your performance and capacity requirements are met. Performance metrics were observed using Intel Xeon W Processor (W-2195 2.3GHz, 4.3GHz Turbo, 24.75M Cache) running SonicOSv 6.5.0.2 with VMware vSphere 6.5.Testing done with multiple flows through multiple port pairs.VPN throughput measured using UDP traffic at 1418 byte packet size adhering to RFC 2544. All specifications and features are subject to change.Features1High availability is currently not supported on AWS and AzureBreach prevention subscription servicesFirewall• Stateful packet inspection• Reassembly-Free Deep Packet Inspection • DDoS attack protection (UDP/ICMP/SYNflood)• IPv4/IPv6• Biometric authentication forremote access• DNS proxy• REST APIsTLS/SSL/SSH decryption and inspection1• Deep packet inspection for TLS/SSL/SSH • Inclusion/exclusion of objects, groups orhostnames• TLS/SSL control• Granular DPI SSL controls per zoneor ruleCapture advanced threat protection1• Real-Time Deep Memory Inspection • Cloud-based multi-engine analysis• Virtualized sandboxing• Hypervisor level analysis• Full system emulation• Broad file type examination• Automated and manual submission• Real-time threat intelligence updates • Block until verdict• Capture ClientIntrusion prevention1• Signature-based scanning• Automatic signature updates• Bi-directional inspection• Granular IPS rule capability• GeoIP enforcement• Botnet filtering with dynamic list• Regular expression matching Anti-malware1• Stream-based malware scanning• Gateway anti-virus• Gateway anti-spyware• Bi-directional inspection• No file size limitation• Cloud malware databaseApplication identification1• Application control• Application bandwidth management• Custom application signature creation• Data leakage prevention• Application reporting overNetFlow/IPFIX• Comprehensive application signaturedatabaseTraffic visualization and analytics• User activity• Application/bandwidth/threat usage• Cloud-based analyticsWeb content filtering1• URL filtering• Proxy avoidance• Keyword blocking• HTTP header insertion• Bandwidth manage CFS rating categories• Unified policy model with app control• Content Filtering ClientVPN• Auto-provision VPN• IPSec VPN for site-to-site connectivity• SSL VPN and IPSec client remote access• Redundant VPN gateway• Mobile Connect for iOS, Mac OSX, Windows, Chrome, Android andKindle Fire• Route-based VPN (OSPF, RIP, BGP)Networking• PortShield• Jumbo frames• Enhanced logging• VLAN trunking2• RSTP (Rapid Spanning Tree Protocol)• Layer-2 QoS• Port security• Dynamic routing (RIP/OSPF/BGP)• Policy-based routing (ToS/metric andECMP)• NAT• DNS/DNS proxy• DHCP server• Bandwidth management• A/P high availability with state sync3• Inbound/outbound load balancing• Wire mode4• Asymmetric routing• Common Access Card (CAC) supportVoIP• Granular QoS control• Bandwidth management• SIP transformations per access rule• SIP proxy supportManagement and monitoring• Capture Security Center, GMS, Web UI,CLI, REST APIs, SNMPv2/v3• Logging• Netflow/IPFix exporting• Cloud-based configuration backupStorage• Logs• Reports• Firmware backups1Requires added subscription2VLAN interface not supported on AWS/Azure 3High availability not supported on AWS/Azure 4Wire mode not supported on AWS/Azure© 2018 SonicWall Inc. ALL RIGHTS RESERVED. SonicWall is atrademark or registered trademark of SonicWall Inc. and/or its affiliates SonicWall, Inc.1033 McCarthy Boulevard | Milpitas, CA 95035 NS vSeries ordering informationAbout UsSonicWall has been fighting the cybercriminal industry for over 27 years, defending small, medium-sized businesses and enterprises worldwide. Our combination of products andpartners has enabled an automated real-time breach detection and prevention solution tuned to the specific needs of the more than 500,000 organizations in over 215 countries and territories, so you can do more business with less fear. For more information, visit or follow us on Twitter, LinkedIn, Facebook and Instagram.*Please consult with your local SonicWall reseller for a complete list of SKUsSonicWall NS v Firewall PromotionThe following NS a /NS sp series firewalls are eligible to receive a one-year license to the corresponding NS vVirtual Appliance TotalSecure Subscription* at no additional cost.Prevention and Application Firewall Service, Content Filtering Premium Service, Capture Security Center and 24x7 Support.。
SonicWall TZ系列统一威胁管理(UTM)防火墙说明书

The SonicWall TZ series of Unified Threat Management (UTM) firewalls is ideally suited for any organization that requires enterprise-grade network protection. SonicWall TZ series firewalls provide broad protection with advanced security services consisting of on-box and cloud-based anti-malware,anti-spyware, application control, intrusion prevention system (IPS), and URL filtering. To counter the trend of encrypted attacks, the TZ series has the processing power to inspect encrypted SSL/TLS connections against the latest threats. Combined with Dell X-Series switches, selected TZ series firewalls can directly manage the security of these additional ports.Backed by the SonicWall Global Response Intelligent Defense (GRID) network, the SonicWall TZ series delivers continuous updates to maintain a strong network defense against cybercriminals. The SonicWall TZ series is able to scan every byte of every packet on all ports and protocols with almost zero latency and no file size limitations.The SonicWall TZ series features Gigabit Ethernet ports, optional integrated 802.11ac wireless*, IPSec and SSL VPN, failover through integrated 3G/4G support, load balancing and network segmentation. The SonicWall TZ series UTM firewalls also provide fast, secure mobile access over Apple iOS, Google Android, Amazon Kindle, Windows, Mac OS X and Linux platforms.The SonicWall Global Management System (GMS) enables centralized deployment and management of SonicWall TZ series firewalls from a single system.Managed security for distributed environments Schools, retail shops, remote sites, branch offices and distributed enterprises need a solution that integrates with their corporate firewall. SonicWall TZ series firewalls share the same code base—andsame protection—as our flagship SuperMassive next-generation firewalls. This simplifies remote site management, as every administrator sees the same user interface (UI). GMS enables network administrators to configure, monitor and manage remote SonicWall firewalls through a single pane of glass. By adding high-speed, secure wireless, the SonicWall TZ series extends the protection perimeter to include customers and guests frequenting the retail site or remote office.SonicWall TZ seriesExceptional security and stellar performance at a disruptively low TCOBenefits:• Enterprise grade networkprotection• Deep packet inspection of all trafficwithout restrictions on file size orprotocol• Secure 802.11ac wirelessconnectivity using integratedwireless controller or viaexternal SonicPoint wireless accesspoints• SSL VPN mobile access for AppleiOS, Google Android, AmazonKindle, Windows, Mac OS andLinux devices• Over 100 additional ports canbe securely managed by theTZ console when deployed incombination with Dell X-SeriesswitchesFor emerging enterprises, retail and branch offices looking for security performance at a value price, the SonicWall TZ600 next-generation firewall secures networks with enterprise-class features and uncompromising performance.USB port (3G/4G WAN Failover)Link and activityIndicator LEDsPower LEDTest LEDPort X1 WANPortpower8x1GbE switch (configurable)Console port Expansion module Slot (future)SonicWall TZ500 seriesFor growing branch offices and SMBs, the SonicWall TZ500 series delivers highly effective, no-compromise protection withnetwork productivity and optional integrated 802.11ac dual-band wireless.(3G/4G WAN Failover)X1 WAN Port poweractivity Indicator LEDs(configurable)portFor small business, retail and branch office locations, the SonicWall TZ400 series delivers enterprise-grade protection. Flexible wireless deployment is available with either external SonicPoint Access points or 802.11ac wireless integrated into the unit.SonicWall TZ300 seriesThe SonicWall TZ300 series offers an all-in-one solution that protects networks from attack. Unlike consumer grade products, the SonicWall TZ300 series firewall combines effective intrusion prevention, anti-malware and content/URL filtering with optional802.11ac integrated wireless and broadest secure mobile platforms support for laptops, smartphones and tablets.(3G/4G WAN Failover)X0 LANPort X1WAN PortpoweractivityIndicator LEDs3x1GbE switch(configurable)portUSB port (3G/4G WANFailover)X1 WAN Port powerLink and activity IndicatorLEDsPower LED Test LED(configurable)portFor wired and wireless small and home office environments, the SonicWall SOHO series delivers the same business-class protectionlarge organizations require at a more affordable price point.USB port (3G/4G WAN Failover)X0 LAN Port X1 WAN PortpowerLink andactivityIndicator LEDsPower LED Test LED(configurable)portExtensible architecture for extreme scalabilityand performanceThe Reassembly-Free Deep Packet Inspection (RFDPI) engineis designed from the ground up with an emphasis on providingsecurity scanning at a high performance level, to match boththe inherently parallel and ever-growing nature of networktraffic. When combined with multi-core processor systems, thisparallel-centric software architecture scales up perfectly toaddress the demands of deep packet inspection at high trafficloads. The SonicWall TZ Series platform relies on processorsthat, unlike x86, are optimized for packet, crypto and networkprocessing while retaining flexibility and programmability inthe field — a weak point for ASICs systems. This flexibility isessential when new code and behavior updates are necessaryto protect against new attacks that require updated and moresophisticated detection techniques.branch officeX-series switchGlobal management and reportingFor larger, distributed enterprise deployments, the optional SonicWall Global Management System (GMS) provides administrators a unified, secure and extensible platform to manage SonicWall security appliances and Dell X-Series switches. It enables enterprises to easily consolidate the management of security appliances, reduce administrative and troubleshooting complexities and governs all operational aspects of the security infrastructure including centralized policy management and enforcement, real-time event monitoring, analytics and reporting, and more. GMS also meets the firewall change management requirements of enterprises through a workflow automation feature. GMS provides a better way to manage network security by business processes and service levels that dramatically simplify the lifecycle management of your overall security environments rather than on a device-by-device basis.Reassembly-Free Deep Packet Inspection (RFDPI) engineThe RFDPI engine provides superior threat protection and application control without compromising performance. This patented engine inspects the traffic stream to detect threats at Layers 3-7. The RFDPI engine takes network streams through extensive and repeated normalization and decryption in order to neutralize advanced evasion techniques that seekto confuse detection engines and sneak malicious codeinto the network. Once a packet undergoes the necessary preprocessing, including SSL decryption, it is analyzed against a single proprietary memory representation of three signature databases: intrusion attacks, malware and applications. The connection state is then advanced to represent the position of the stream relative to these databases until it encountersa state of attack, or another “match” event, at which point a pre-set action is taken. As malware is identified, the SonicWall firewall terminates the connection before any compromise can be achieved and properly logs the event. However, the engine can also be configured for inspection only or, in the case of application detection, to provide Layer 7 bandwidth management services for the remainder of the applicationstream as soon as the application is identified.Security and protectionThe dedicated, in-house SonicWall Threat Research Team workson researching and developing countermeasures to deploy to the firewalls in the field for up-to-date protection. The team leverages more than one million sensors across the globe for malware samples, and for telemetry feedback on the latest threat information, which in turn is fed intothe intrusion prevention, anti-malware and application detection capabilities. SonicWall firewall customers with current subscriptions are provided continuously updated threat protection aroundthe clock, with new updates taking effect immediately without rebootsor interruptions. The signatures onthe appliances protect against wide classes of attacks, covering up to tensof thousands of individual threats witha single signature. In addition to the countermeasures on the appliance, all SonicWall firewalls also have accessto the SonicWall CloudAV service, which extends the onboard signature intelligence with more than 17 million signatures, and growing. This CloudAV database is accessed via a proprietary light-weight protocol by the firewall to augment the inspection done on the appliance. With Geo-IP and botnet filtering capabilities, SonicWall next-generation firewalls are able to block traffic from dangerous domains or entire geographies in order to reduce the riskprofile of the network. Application intelligenceand controlApplication intelligence informs administrators of application traffic traversing the network, so they can schedule application controls based on business priority, throttle unproductive applications and block potentially dangerous applications. Real-time visualization identifies traffic anomalies as they happen, enabling immediate countermeasures against potential inbound or outbound attacks or performance bottlenecks. SonicWall application traffic analytics providegranular insight into applicationtraffic, bandwidth utilization andsecurity threats, as well as powerfultroubleshooting and forensicscapabilities. Additionally, secure singlesign-on (SSO) capabilities enhance theuser experience, increase productivityand reduce support calls. Managementof application intelligence and controlis simplified by using an intuitive web-based interface.Flexible and secure wirelessAvailable as an optional feature, high-speed 802.11ac wireless* combineswith SonicWall next-generationfirewall technology to create a wirelessnetwork security solution that deliverscomprehensive protection for wired andwireless networks.This enterprise-level wirelessperformance enables WiFi-ready devicesto connect from greater distancesand use bandwidth-intensive mobileapps, such as video and voice, inhigher density environments withoutexperiencing signal degradation.* 802.11ac currently not available on SOHO models; SOHO models support 802.11a/b/g/nFeaturesSonicOS feature summaryFirewall• Stateful packet inspection• Reassembly-Free Deep PacketInspection• DDoS attack protection(UDP/ICMP/SYN flood)• IPv4/IPv6 support• Biometric authentication for remote access• DNS proxy• Threat APISSL/SSH decryption and inspection1• Deep packet inspection for TLS/SSL/SSH • Inclusion/exclusion of objects, groups or hostnames• SSL controlCapture Advanced Threat Protection1• Cloud-based multi-engine analysis• Virtualized sandboxing• Hypervisor level analysis• Full system emulation• Broad file type examination• Automated & manual submission• Real-time threat intelligence updates • Auto-Block capabilityIntrusion prevention1• Signature-based scanning• Automatic signature updates• Bidirectional inspection engine• Granular IPS rule capability• GeoIP/Botnet filtering2• Regular expression matchingAnti-malware1• Stream-based malware scanning• Gateway anti-virus• Gateway anti-spyware• Bi-directional inspection• No file size limitation• Cloud malware database Application identification1• Application control• Application visualization2• Application component blocking• Application bandwidth management• Custom application signature creation• Data leakage prevention• Application reporting over NetFlow/IPFIX• User activity tracking (SSO)• Comprehensive application signaturedatabaseWeb content filtering1• URL filtering• Anti-proxy technology• Keyword blocking• Bandwidth manage CFS ratingcategories• Unified policy model with app control• Content Filtering ClientVPN• Auto-provision VPN• IPSec VPN for site-to-site connectivity• SSL VPN and IPSec client remote access• Redundant VPN gateway• Mobile Connect for iOS, Mac OS X,Windows, Chrome, Android and KindleFire• Route-based VPN (OSPF, RIP)Networking• PortShield• Enhanced logging• Layer-2 QoS• Port security• Dynamic routing• SonicPoint wireless controller• Policy-based routing• Asymmetric routing• DHCP server• NAT• Bandwidth management• High availability - Active/Standby withstate sync3• Inbound/outbound load balancing• L2 bridge mode, NAT mode• 3G/4G WAN failover• Common Access Card (CAC) supportVoIP• Granular QoS control• Bandwidth management• DPI for VoIP traffic• H.323 gatekeeper and SIP proxy supportManagement and monitoring• Web GUI• Command line interface (CLI)• SNMPv2/v3• Centralized management and reportingwith SonicWall GMS• Logging• Netflow/IPFix exporting• Single Sign-On (SSO)• Terminal service/Citrix support• Application and bandwidth visualization• IPv4 and IPv6 management• Dell X-Series switch managementIPv6• IPv6 filtering• 6rd (rapid deployment)• DHCP prefix delegation• BGPWireless• Dual-band (2.4 GHz and 5.0 GHz)• 802.11 a/b/g/n/ac wireless standards2• Wireless intrusion detection andprevention• Wireless guest services• Lightweight hotspot messaging• Virtual access point segmentation• Captive portal• Cloud ACLRequires added subscriptionNot available on SOHO seriesState sync high availability only on SonicWall TZ500 and SonicWall TZ600 modelsSonicWall TZ series system specifications*Future use.Testing Methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services. Full DPI/GatewayAV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs.VPN throughput measured using UDP traffic at 1280 byte packet size adhering to RFC 2544. All specifications, features and availability are subject to change. BGP is available only on SonicWall TZ400, TZ500 and TZ600.All TZ integrated wireless models can support either 2.4GHz or 5GHz band. For dual-band support, please use SonicWall's wireless access points products (SonicPoints)SonicWall TZ Series ordering information© 2017 SonicWall Inc. ALL RIGHTS RESERVED. SonicWall is atrademark or registered trademark of SonicWall Inc. and/or its affiliates SonicWall, Inc.5455 Great America Parkway | Santa Clara, CA 95054 About UsSonicWall has been fighting the cyber-criminal industry for over 25 years, defending small, medium size businesses and enterprises worldwide. Our combination of products and partners has enabled a real-time cyber defense solution tuned to the specific needs ofthe more than 500,000 global businesses in over 150 countries, so you can do more business with less fear.。
如何配置SonicWALL防火墙
如何配置SonicWALL防火墙SonicWALL防火墙在中小型企业市场中非常的常见。
从那些小型的非营利公司,到中型公司的企业生意,都在依赖于SonicWALL的设备来保护他们的网络通信安全。
SonicWall使用专用的SonicOS操作系统驱动它的防火墙设备。
绝大多数SonicWALL设备现在都使用由SonicOS增强的操作系统。
这两个操作系统之间的主要区别在于,增强版启用了系统的固件(Firmware)来提供ISP失败恢复服务,区域管理以及广域网负载平衡。
安装向导SonicWALL随它的防火墙设备提供了多种向导。
根据型号不同,可用的菜单也各有差异(举例来说,像“WEP/WAP加密功能设置”菜单就只有那些具备无线功能的型号才有)安装向导是个节约时间的工具,可以简化新路由器的部署。
或当网络被重新设计后,一台SonicWALL设备可被复位成刚出厂的默认设置,这时可以使用安装向导对设备重新设置。
要使用安装向导,登录进入SonicWALL防火墙后,再点击“安装向导(Wizard)”按钮。
该向导按钮(图A)可以在主要的“系统|状态”(System | Status)页中找到。
图A:SonicWALL系统状态页提供了关于防火墙设置的大量信息下面是使用一台SonicWALL PRO 1260的整个过程。
点击了“向导”按钮后,SonicWALL配置向导提供4个选择(图B)图B图B注:SonicWALL配置向导提供4个选择。
管理员可以选择安装向导(用于配置SonicWALL设备来加密网络连接),或者端口防护接口向导(PortShield Interface Wizard,用于分割网络),或者公用服务器向导(用于提供内部服务器给公众使用),或者VPN向导(用于配置一个VPN网络)。
考虑好你是否打算选择安装向导,端口防护接口向导,公用服务器向导或是VPN向导。
就本例而言,我们将选择安装向导,并点击下一步。
安装向导出现。
sonicwall防火墙设置主要方法有哪些

sonicwall防火墙设置主要方法有哪些sonicwall防火墙设置要怎么样设置才能发挥最大的功效呢?下面由店铺给你做出详细的sonicwall防火墙设置主要方法介绍!希望对你有帮助!sonicwall防火墙设置主要方法一:SonicWALL防火墙的默认管理IP为192.168.168.168,需要把网线接到X0口(默认的LAN口)帐号admin,密码password。
如果实在进不去可以reset,使用回形针或者其他的什么东西去戳一下那个小孔(一般在电源旁边,有的型号是在正面)按住大约10秒左右,之后可以看到test灯闪烁,然后就可以通过默认的帐号和密码进去管理了。
不过需要注意的是reset之后一切配置都没有了,如果不是万不得已,最好还是别这样做。
sonicwall防火墙设置主要方法二:sonicwaLL IP:192,168.168.168user:adminpassword:password要是该过忘记了,就重置吧用针按着reset孔20秒左右开始重置,reset是,test灯会闪烁红色。
ip一般都是192,168.168.168如果不是用抓包软件测试一下就行,获取个arp request的数据包,就知道了sonicwaLL的原始ip sonicwall防火墙设置主要方法三:选择network→interface之后你可以看到各个接口,点击外网(WAN)口后面的编辑然后你可以看到一个manageent 后面有些HTTP HTTPS PING SSH等的,这里你只需要将HTTP和HTTPS勾选上即可。
这样,在你外网畅通的情况下别人就可以远程通HTTP或者HTTPS来管理这台设备。
例如你在WAN端口上看到的地址是51.123.21.8,那么当你打开管理后,别人就能通过来管理你的防火墙。
SonicWall SuperMassive Series 产品说明说明书

The SonicWall SuperMassive Series is SonicWall’s next-generation firewall (NGFW) platform designed for large networks to deliver scalability, reliability and deep security at multi-gigabit speeds with near zero latency.Built to meet the needs of enterprise, government, education, retail, healthcare and service provider, the SuperMassive Series is ideal for securing distributed enterprise networks, data centers and service providers.The combination of SonicWall’s SonicOS operating system, patented* Reassembly-Free Deep Packet Inspection® (RFDPI) technology and massively multi-core, highly scalable hardware architecture, the SuperMassive 9000 Series deliver industry-leading application control, intrusion prevention, malware protection and TLS/SSL decryption and inspection at multi-gigabit speeds. The SuperMassive Series is thoughtfully designed with power, space and cooling (PSC) in mind, providing the leading Gbps/watt NGFW in the industry for high performance packet and data processing, application control and threat prevention.The SonicWall RFDPI engine scans every byte of every packet across all ports, delivering full content inspection of the entire stream while providing high performance and low latency. This technology is superior to proxy designs that reassemble content using sockets bolted to anti-malware programs, which are plagued with inefficiencies and the overhead of socket memory thrashing, which leads to high latency, low performance and file size limitations. The RFDPI engine delivers full content inspection to eliminate various forms of malware before they enter the network and provides protection against evolving threats — without file size, performance or latency limitations.The RFDPI engine also performs full decryption and inspection of TLS/SSL and SSH encrypted traffic as well asnon-proxyable applications, enabling complete protection regardless of transport or protocol. It looks deep inside every packets (the header and data part) searching for protocol non-compliance, threats, zero-days, intrusions, and even defined criteria to detect and prevent attacks hidden inside encrypted traffic, cease the spread of infections, and thwart command and control (C&C) communications and data exfiltration. Inclusion and exclusion rules allow total control to customize which traffic is subject to decryption and inspection based on specific organizational compliance and/or legal requirements. Application traffic analytics enablethe identification of productive and unproductive application traffic in real time, and traffic can then be controlled through powerful application-level policies. Application control can be exercised on both a per-user and per-group basis, along with schedules and exception lists. All application, intrusion prevention and malware signatures are constantly updated by the SonicWall Capture Labs threats research team. Additionally, SonicOS, an advanced purpose-built operating system, provides integrated tools that allowfor custom application identification and control.SonicWall SuperMassive SeriesUncompromising, high-performance, next-generation firewall protection foryour enterprise network.Benefits:• Get complete breach preventionincluding high performanceintrusion prevention, lowlatency malware protection andcloud-based sandboxing• Gain full granular applicationidentification, controland visualization• Find and block hidden threats withdecryption and inspection of TLS/SSL and SSH encrypted traffic,without performance problems• Scale security performance for10/40 Gbps data centers• Adapt to service-level increasesand ensure network servicesand resources are availableand protected*U.S. Patents 7,310,815; 7,600,257; 7,738,380; 7,835,361SuperMassive 9000 SeriesSeries lineupThe SonicWall SuperMassive 9000 Series features 4 x 10-GbE SFP+, up to 12 x 1-GbE SFP , 8 x 1-GbE copper and 1 GbEmanagement interfaces, with an expansion port for an additional 2 x 10- GbE SFP+ interfaces (future release). The 9000 Series features hot-swappable fan modules and power supplies.SuperMassive 9000 Seriesdisplay port interface4 x 10-GbE SFP+ ports 8 x 1-GbE SFP ports 8 x 1-GbEportsDual USB ports LCD Dual hot-Expansion bay Two hot-swappable,Dual hot-Expansion bayTwo hot-swappable,SD card for future usedisplayport interface SFP+ ports12 x 1-GbE 2 x 80Gb 8 x 1-GbE ports LCDcontrolsReassembly-Free Deep Packet Inspection engineRFDPI is a single-pass, low latency inspection system that performs stream-based, bi-directional traffic analysis at high speed without proxying or buffering to effectively uncover intrusion attempts, malware and identify application traffic regardless of port and protocol. This proprietary engine relies on streaming traffic payload inspection in order to detect threats at Layers3-7. The RFDPI engine takes network streams through extensive and repeated normalization and decryption in orderto neutralize advanced obfuscation andevasion techniques that seek to confusedetection engines and sneak maliciouscode into the network.Once a packet undergoes the necessarypre-processing, including TLS/SSLdecryption, it is analyzed against a singleproprietary memory representationof multiple signature databases:intrusion attacks, malware, botnet andapplications. The connection stateis then advanced to represent theposition of the stream relative to thesedatabases until it encounters a state ofattack, or other “match” event, at whichpoint a preset action is taken. In mostcases, the connection is terminatedand proper logging and notificationevents are created. However, the enginecan also be configured for inspectiononly or, in the case of applicationdetection, to provide Layer 7 bandwidthmanagement services for the remainderof the application stream as soon as theapplication is identified.PacketPacket assembly-based processSonicWall stream-based architecture Competitive proxy-based architectureWhen proxybecomes full orcontent too large,files bypassscanning.Reassembly-free Deep Packet Inspection (RFDPI)Reassembly-free packetscanning eliminates proxyand content size limitations.Inspection timeLess MoreInspection timeLess MoreInspection capacityMin MaxExtensible architecture for extremescalability and performanceThe RFDPI engine is purposely designedwith a keen focus on providing securityscanning at a high level of performance,to match both the inherently paralleland ever growing nature of networktraffic. When combined with multi-coreprocessor systems, this parallelism-centric software architecture scales upperfectly to address the demands ofdeep packet inspection (DPI) at hightraffic loads. The SuperMassive platformrelies on processors that, unlike x86,are optimized for packet, crypto andnetwork processing while retainingflexibility and programmability in thefield — a weak point for ASICs systems.This flexibility is essential when new codeand behavior updates are necessaryto protect against new attacks thatrequire updated and more sophisticateddetection techniques. Another aspectof the platform design is the uniqueability to establish new connectionson any core in the system, providingultimate scalability and the ability todeal with traffic spikes. This approachdelivers extremely high new sessionestablishment rates (new conn/sec) whiledeep packet inspection is enabled — akey metric that is often a bottleneck fordata center deployments.Advanced threat protection SonicWall Capture Advanced Threat Protection Service1 is a cloud-based multi-engine sandbox that extends firewall threat protection to detect and prevent zero-day threats. Suspicious files are sent to the cloud for analysis with the option to hold them at the gateway until a verdict is determined. Themulti-engine sandbox platform, which includes virtualized sandboxing, full system emulation and hypervisor level analysis technology, executes suspicious code and analyzes behavior. When afile is identified as malicious, a hash is immediately created within Capture and later a signature is sent to firewalls to prevent follow-on attacks.The service analyzes a broad rangeof operating systems and file types, including executable programs, DLL, PDFs, MS Office documents, archives, JAR and APK.Capture provides an at-a-glance threat analysis dashboard and reports, which detail the analysis results for files sent to the service, including source, destination and a summary plus details of malwareaction once detonated.Capture LabsThe dedicated, in-house SonicWall Capture Labs threats researchteam researches and develops countermeasures to deploy to customer firewalls for up-to-date protection. The team gathers data on potential threat data from several sources including our award-winning network sandboxing service, Capture Advanced Threat Protection, as well as more than 1 million SonicWall sensors located around the globe that monitor traffic for emerging threats. It is analyzed via machine learning using SonicWall's Deep Learning Algorithms to extract the DNA from the code to see if it is related to any known forms of malicious code. SonicWall NGFW customers with the latest security capabilities are provided continuously updated threat protection around the clock. New updates take effect immediately without rebootsor interruptions. The signatures onthe appliances protect against wideclasses of attacks, covering up to tensof thousands of individual threats with asingle signature.In addition to the countermeasures onthe appliance, SuperMassive firewallsalso have access to the SonicWallCloudAV1, which extends the onboardsignature intelligence with tens ofmillions of signatures, and growingby millions annually. This CloudAVdatabase is accessed by the firewall viaa proprietary, lightweight protocol toaugment the inspection done on theappliance. With Capture AdvancedThreat Protection1, a cloud-based multi-engine sandbox, organizations canexamine suspicious files and code in anisolated environment to stop advancedthreats such as zero-day attacks.Protection CollectionClassificationCountermeasureL A B S1 Requires added subscriptionApplication intelligence and control Application intelligence informs administrators of application traffic traversing their network so they can schedule application controls based on business priority, throttle unproductive applications and block potentially dangerous applications. Real-time visualization identifies traffic anomalies as they happen, enabling immediate countermeasures against potential inbound or outbound attacks or performance bottlenecks.SonicWall Application Traffic Analytics1 provide granular insight into application traffic, bandwidth utilization and security threats, as well as powerful troubleshooting and forensicscapabilities. Additionally, secure single sign-on (SSO) capabilities ease the user experience, increase productivity and reduce support calls. Management of application intelligence and controlis simplified by the intuitive web-based interface.Global management and reportingFor highly regulated organizations wanting to achieve a fully coordinated security governance, complianceand risk management strategy,the optional SonicWall Global Management System1 (GMS®) provides administrators a unified, secure and extensible platform to manage SonicWall firewalls, wireless access points and switches through a correlated and auditable workstream process. GMS enables enterprises to easily consolidate the managementof security appliances, reduce administrative and troubleshooting complexities, and govern all operational aspects of the security infrastructure, including centralized policy management and enforcement; real-time event monitoring; user activities; application identifications; flow analytics and forensics; compliance and audit reporting; and more. GMS also meets the firewall change management requirementsof enterprises through a workflowautomation feature. With GMS workflowautomation, all enterprises will gainagility and confidence in deploying theright firewall policies, at the right timeand in conformance to complianceregulations. GMS provides a coherentway to manage network security bybusiness processes and service levels,dramatically simplifying lifecyclemanagement of your overall securityenvironments as compared to managingon a device-by-device basis.• Centralizedmanagement• Error-free policymanagement• Strong access control• Comprehensiveaudit trails• PCI, HIPAA, SOXreport templates• Lower operating costsPort Expansion ScalabilitySonicWall GMS Secure Compliance EnforcementBenefits1 Requires added subscription1 Requires added subscriptionFirewall• Stateful packet inspection• Reassembly-Free DeepPacket Inspection• DDoS attack protection(UDP/ICMP/SYN flood)• IPv4/IPv6 support• Biometric authentication forremote access• DNS proxy• Threat APISSL/SSH decryption and inspection2• Deep packet inspection for TLS/SSL/SSH • Inclusion/exclusion of objects, groupsor hostnames• SSL ControlCapture advanced threat protection2• Cloud-based multi-engine analysis• Virtualized sandboxing• Hypervisor level analysis• Full system emulation• Broad file type examination• Automated and manual submission • Real-time threat intelligence updates • Auto-block capabilityIntrusion prevention2• Signature-based scanning• Automatic signature updates• Bi-directional inspection engine• Granular IPS rule set• GeoIP enforcement• Botnet filtering with dynamic list• Regular expression matchingAnti-malware2• Stream-based malware scanning• Gateway anti-virus• Gateway anti-spyware• Bi-directional inspection• No file size limitation• Cloud malware database Application identification2• Application control• Application traffic visualization• Application component blocking• Application bandwidth management• Custom application signature creation• Data leakage prevention• Application reporting overNetFlow/IPFIX• User activity tracking (SSO)• Comprehensive applicationsignature databaseWeb content filtering2• URL filtering• Anti-proxy technology• Keyword blocking• Bandwidth management forCFS categories• Unified policy model with app control• Content Filtering ClientVPN• Auto-provision VPN• IPSec VPN for site-to-site connectivity• SSL VPN and IPSEC client remote access• Redundant VPN gateway• Mobile Connect for iOS, Mac OSX, Windows, Chrome, Android andKindle Fire• Route-based VPN (OSPF, RIP, BGP)Networking• Dynamic LAG using LACP• PortShield• Jumbo frames• Path MTU discovery• Enhanced logging• VLAN trunking• Port mirroring• Layer-2 QoS• Port security• Dynamic routing (RIP/OSPF/BGP)• SonicWall wireless controller1• Policy-based routing(ToS/metric and ECMP)• NAT• DHCP server• Bandwidth management• Link aggregation (static and dynamic)• Port redundancy• A/P high availability with state sync• A/A clustering• Inbound/outbound load balancing• L2 bridge, wire/virtual wire mode, tapmode, NAT mode• 3G/4G WAN failover (not onSuperMassive 9800)• Asymmetric routing• Common Access Card (CAC) supportWireless• MU-MIMO• Wireless planning tool• Band steering• Beamforming• AirTime fairness• MiFi extender• Guest cyclic quotaVoIP• Granular QoS control• Bandwidth management• DPI for VoIP traffic• H.323 gatekeeper and SIP proxy supportManagement and monitoring• Web GUI• Command-line interface (CLI)• SNMPv2/v3• Centralized management and reportingwith SonicWall Global ManagementSystem (GMS)2• Logging• Netflow/IPFix exporting• Cloud-based configuration backup• BlueCoat security analytics platform• Application and bandwidth visualizer• IPv4 and IPv6 Management• LCD management screen• Dell X-Series switch management11 Not supported on SonicOS 6.2.7.72 Requires added subscriptionSuperMassive 9000 Series system specificationsTesting Methodologies: Maximum performance based on RFC 2544 (for firewall). Actual performance may vary depending on network conditions and activated services. Full DPI/Gateway AV/Anti-Spyware/IPS throughput measured using industry standard Spirent WebAvalanche HTTP performance test and Ixia test tools. Testing done with multiple flows through multiple port pairs. VPN throughput measured using UDP traffic at 1280 byte packet. Applies to SuperMassive 9200, 9400 and 9600. SuperMassive 9800 UC APL certification is pending. Supported on SonicOS 6.1 and 6.2. For every 125,000 DPI connections reduced, the number of available DPI SSL connections increases by 750. *Future use. All specifications, features and availability are subject to change.SuperMassive 9000 Series ordering information*Please consult with a SonicWall SE for a complete list of supported SFP and SFP+ modules.© 2017 SonicWall Inc. ALL RIGHTS RESERVED. SonicWall is atrademark or registered trademark of SonicWall Inc. and/or its affiliates in the U.S.A. and/or other countries. All other trademarksand registered trademarks are property of their respective owners.SonicWall, Inc.5455 Great America Parkway | Santa Clara, CA 95054 Refer to our website for additional information. About UsSonicWall has been fighting the cyber-criminal industry for over 25 years, defending small, medium size businesses and enterprises worldwide. Our combination of products and partners has enabled a real-time cyber defense solution tuned to the specific needs of the more than 500,000 global businesses in over 150 countries, so you can do more business with less fear.Datasheet-SuperMassive-US-VG-MKTG476。
SonicWALL防火墙说明

防火墙部分:1、SonicWALL GAV/IPS/Application Firewall: 此License包含:a.网关杀毒(Gateway Anti-virus),b.反间谍软件(Anti-spyware),c.入侵防护(IPS),d.Application Firewall(应用管控,上网行为管理的增强功能),e.智能应用流量实时监控(App Flow Monitor).这一个license就包含了这所有的功能,不能单独拆开购买。
这个license分1年,2年,3年。
• a.网关杀毒:网关杀毒功能是用于对所有经过防火墙流量进行病毒过滤。
能够对公司上网的用户和服务器进行病毒防护。
病毒库是可以自动更新的。
• b.反间谍软件:反间谍功能是对所有经过防火墙流量进行间谍软件的过滤。
能够对公司上网的用户和服务器进行间谍软件的过滤。
间谍软件签名库也是可以自动更新的。
• c.入侵防护:入侵防护功能能够对对外公布的服务器进行有效的保护,比如说防止DoS,DDoS,flooding等攻击,也能够防护诸如SQL注入,数据库攻击,cc攻击等。
攻击签名库也是是自动更新的。
• d.Application Firewall:此功能用于聊天工具的管控,下载工具的管控,炒股软件的管控,在线视频的管控等。
并且还能对包进行深度包检测,对任意包内容进行识别和匹配。
应用签名库是自动更新的。
• e.智能应用实时监控(Application Flow Monitor):用于接口带宽,应用流量的实时监控和分析。
比如说能够看到HTTP流量,P2P流量,视频流量分别占了多少百分比,分别是哪些IP 用的最多,分别用了多少流量等.2. SonicWALL Content Filtering Service Premium Business Edition(CFS):•此License用于网站内容过滤。
购买此license后就能按照网站类别对网页浏览进行控制。
关于SonicWALL防火墙的连接数说明
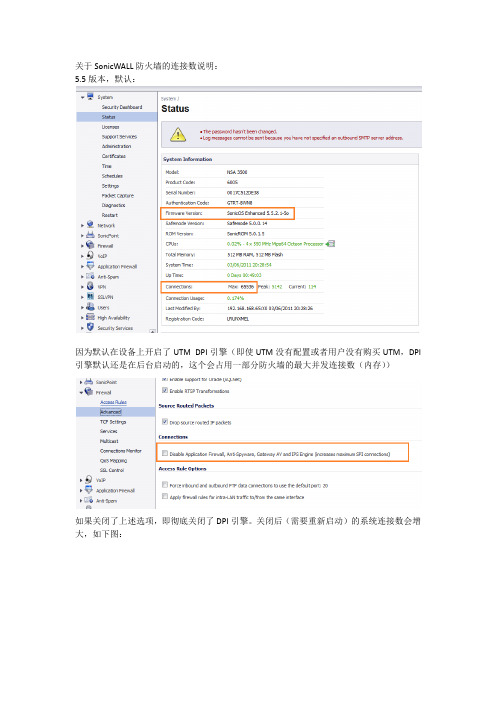
关于SonicWALL防火墙的连接数说明:
5.5版本,默认:
因为默认在设备上开启了UTM DPI引擎(即使UTM没有配置或者用户没有购买UTM,DPI 引擎默认还是在后台启动的,这个会占用一部分防火墙的最大并发连接数(内存))
如果关闭了上述选项,即彻底关闭了DPI引擎。
关闭后(需要重新启动)的系统连接数会增大,如下图:
5.6以后的版本,增加了配置选项
下面是关闭DPI后的总体连接数:
对应的选项:UTM services (Application Firewall, Anti‐Spyware, Gateway AV, and IPS Engine)
disabled for highest number of SPI connections
下图是开启UTM DPI引擎后的连接数:(系统默认配置)
对应的选项:
Recommended for normal deployments with UTM services enabled
下面是增加系统UTM连接数的配置:
对应的选项:
Optimized for deployments requiring more UTM connections but less performance critical
截图如下:
另外,在防火墙的配置界面,还有开启UTM后增加设备吞吐性能的配置页面(配置后部需要重启)。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
防火墙部分:
1、SonicWALL GAV/IPS/Application Firewall: 此License包含:
a.网关杀毒(Gateway Anti-virus),
b.反间谍软件(Anti-spyware),
c.入侵防护(IPS),
d.Application Firewall(应用管控,上网行为管理的增强功能),
e.智能应用流量实时监控(App Flow Monitor).
这一个license就包含了这所有的功能,不能单独拆开购买。
这个license分1年,2年,3年。
• a.网关杀毒:网关杀毒功能是用于对所有经过防火墙流量进行病毒过滤。
能够对公司上网的用户和服务器进行病毒防护。
病毒库是可以自动更新的。
• b.反间谍软件:反间谍功能是对所有经过防火墙流量进行间谍软件的过滤。
能够对公司上网的用户和服务器进行间谍软件的过滤。
间谍软件签名库也是可以自动更新的。
• c.入侵防护:入侵防护功能能够对对外公布的服务器进行有效的保护,比如说防止DoS,DDoS,flooding等攻击,也能够防护诸如SQL注入,数据库攻击,cc攻击等。
攻击
签名库也是是自动更新的。
• d.Application Firewall:此功能用于聊天工具的管控,下载工具的管控,炒股软件的管控,在线视频的管控等。
并且还能对包进行深度包检测,对任意包内容进行识别和匹配。
应用
签名库是自动更新的。
• e.智能应用实时监控(Application Flow Monitor):用于接口带宽,应用流量的实时监控和分析。
比如说能够看到HTTP流量,P2P流量,视频流量分别占了多少百分比,分别是
哪些IP 用的最多,分别用了多少流量等.
2. SonicWALL Content Filtering Service Premium Business Edition(CFS):•此License用于网站内容过滤。
购买此license后就能按照网站类别对网页浏览进行控制。
比如说,可以不允许员工访问色情,暴力,购物等网站。
如果不购买此license,只能手动
添加网站黑名单列表,工作量很大。
这个license分1年,2年,3年。
3.SonicWALL Gold/EClass Support 24x7:
•24*7的售后支持服务。
包含了24*7的电话支持服务,远程协助的服务,邮件支持服务。
另外还包含了产品新软件升级的服务和硬件维保服务。
SonicWALL售后支持服务分1
年,2年,3年。
4.SonicWALL Comprehensive Gateway Security Suite:
•SonicWALL Comprehensive Gateway Security Suite包含以上1+2+3。
5.SonicWALLTotalSecure 1 Yr:
•SonicWALL Total Secure包含一个硬件设备加上1年的SonicWALL Comprehensive Gateway Security Suite.
SSLVPN部分:
1.SonicWALLAventail E-Class SRA EX9000 Base Appliance with Administrator Test
License:
•SSLVPN Aventail EX9000硬件一台
2.SonicWALL E-Class SRA 20,000 User
•20000并发用户数授权
3.SonicWALL E-Class Support 24x7 for SRA EX9000 10,000 USER
•EX9000 10000并发用户数授权的24*7的售后支持服务。
包含了24*7的电话支持服务,远程协助的服务,邮件支持服务。
另外还包含了产品新软件升级的服务和硬件维保服务。
SonicWALL售后支持服务分1年,2年,3年。
