CODE SIZE LIMIT IN RESTRICTED VERSION EXCEEDED
HP HP-UX 说明书

阅读同义词

acute—intense 急性的-剧烈的astound—surprise 令人极为惊讶的-令人惊讶attachment (to) —preference (for) 喜爱-喜爱attendant—accompanying 伴随的-伴随的attire—clothing 衣服-衣服attribute—characteristic 特征bizarre—odd-奇异的-奇怪的boost—raise 促进-提高bound—limit 限制-限制break (with)—departure (from)与…相分离-与…相分离calculate—determine 计划-决定carry—support 支撑-支撑celestial—astronomical 天上的-天文的consort—associate 合伙人,伴侣-合伙人,伙伴consult—counsel 商量-商量counteract—negate 抵消-取消,否定counterpart—version 副本-版本cumbersome—burdensome 麻烦的-麻烦的deft—skilled 灵巧的-熟练的detectable—measurable 可察觉的,可测出的-可测量的detectable—sizable 可察觉的,可测出的-巨大的devastate—ruin 损坏-毁灭dramatic—striking 引人注目的-引人注目的embed—encase 植入-包裹embrace—recipient 接受者-接受者enable —help 使能够-帮助enact—perform 制定法律,扮演角色-扮演角色end—goal 目的-目的entomb—trap 埋葬-使陷于…之中eradicate—eliminate 根除-清除exalted—superior 高贵的-出众的execute—create(按计划和设计)做成,制成-创造exert—apply 施加-施行exorbitant—expensive 昂贵的—昂贵的feed—put 填入-放入fine—minute 细小的-微小的fixture—commonplace object 固定设备-常规物体frame—pose 给…设框-使摆好姿势gap—opening 裂缝-裂缝hemisphere—side 半球-一侧herald—announce 预示,宣布-预示,宣布homogeneous—uniform 同源的-一致的inevitable—ineluctable 不可避免的-不可避免的ingot—a block of metal 金属锭-一块金属inhibit—hinder 阻止-妨碍initially—at first 最初-第一instantaneous—immediate 立竿见影的-立即的interchangeable—equivalent 可替换的-等值的inviting—attractive 吸引人的-吸引人的jolt—shock 使震惊-使震惊lament—complain about 令人对…感到遗憾-抱怨magnitude—extent 量值,大小-范围maneuver—trick 策略,花招-诡计marked—pronounced 明显的-明显的meticulous—careful 谨小慎微的,过分注意细节的-小心的milestone—significant development 里程碑-重大的发展minuscule—tiny 微小的-微小的minute—tiny 微小的-微小的'` monopolize—dominate 垄断-支配mundane—ordinary 世俗的-平常的myriad of—many 无数的-许多的novel—innovative 新颖的-创新的noxious—harmful 有害的-有害的peculiar—distinctive 独特的-独特的prominent—prestigious 卓越的-著名的property—characteristic 特性-特点proponent—supporter 支持者-支持者protrude—project 突出-突出puncture—pierce 刺破-刺破rare—infrequent 希罕的-不经常的reliance—dependence 依靠-依靠revise—change 修改-改变roll back—reduce 把…压到标准水平-降低,减少rotate—alternate 旋转-交替rupture—burst 爆裂-爆裂sanitation—health 卫生-卫生scale—climb 攀登-攀登secure—acquire 弄到,获得-获得secure—safe 安全的-安全的smother—eliminate 窒息-清楚snap—break 断裂-断裂sole—only 唯一的-唯一的solemn—serious 严肃的-严肃的sort out—separate 区分-分离spark—bring (about)/usher (in)引起,开始-引起/开始spawn—create 引起,大量生产-创造spot—identify 发现-确定,鉴别staggering—overwhelming 令人惊愕的-压倒性的staple—basic element 主要部分-基本组成部分strategy—scam/trick 诡计-诡计/诡计strength—basis 力量的源泉-基础stringent—strict 严格的-严格的subsidize—finance 资助-资助substantiate—verify 证实-证实sumptuous—luxurious 奢侈的-奢侈的supplement—extension 补充-扩展,延伸supposed—seeming 假定的-表面上的supremacy—dominance 至高无上-优势supreme—most outstanding 至高无上的-最出类拔萃的surge—accelerate 汹涌进行-加速发展tangle—twist/jumble 纠缠-缠绕、使混乱uniform—integrate 统一-整合unravel—discover 弄清-发现usher in—begin 开始-开始yield—provide 产生-提供阅读近意词ded=extra( 答案还有continuing)anchor=hold in a placeabstract = concrete (文中找反意)Advance = improvementaccomplished = achievedAdmit (permit to enter) =let inAdjusted = modificated (adjusted adj.调整过的)Annually = yearlyavenue (大路,手段方法) = meansa matter of speculation--supposition(speculation 的同义词) adjusted--modificatedadvance--improvementaccumulate-- collect/press down,(它在原文的句子是the diamonds accumulate in somewhere)appeal--attractionattachment to --preference forarray=range n.排列, 编队, 军队, 衣服, 大批vt.部署, 穿着, 排列attendant-- accompanyingascribed to--assumed to be true ofafford--provide/purchase/originate/requireavailable--obtainableapparent--obviousbeckon= invitebeckoning (引诱人的, 令人心动的)=invitingBreed = reproduce (breed v.(使)繁殖, 教养, 抚养n.品种, 种类)beckoning=invitingbreed--reproducebrilliant--brightboost --raiseboom--expansionbeneficial--advantageousconstant = stablecounter of = in the opposition ofcontinual = constantconsistently= regularlycounter of = in the opposite ofCritical = significantCritical = significantcritical --importantcritical --essentialchisel==carvecounter of--in the opposite ofconstantly -----regularly(i guess)classic--typicalclose--careful (其他选项为final/instant/restricted) n. 结束couple--associatecommemorate--celebratecorrespondence 一致harmoniesconfine--limitcamouflage--hideconstituent--componentcounterpart --versionconsequently--therefore / thusconvert--transform"demise"--decline,demand=needdetrimental = harmfuldurable=lastingDetermining (测定) = calculatingDetractor = critic (detractor n.诽谤者, 恶意批评者)diffusion (笔试:diffuse = travel)distinguish = notice from the differenceDistribute = spreaddevoted to--dependent on/concentrated on/related to发明和entrepreneurial risks were devoted to the..... which has no certain profit.distribute = spreaddisturb-upsetdebate--arguedetrimental--harmfuldaring -- bolddiffuse--traveldispute--argumentdangle--hung hangdiversity--variedevoke=stimulateengage=involveexceeded = surpassedemploy=useexceedingly -- extremelyendangered ( 将要绝种的) = abundant(反义词,句中选)Enrich = enhance 选项里有enhance/conceal/enlargeentail = involve entail: vt.使必需, 使蒙受, 使承担, 遗传给Erratic (不稳定的,古怪的) = irregularEven= alreadyEvenly = equally (evenly adv.均匀地, 平坦地)exhibit (n. v. 展示,陈列)= feature (展出、公开= emphasize,display, publicize, ) (句中选)Expanse (笔试:expand = increase)express = communicateExtraneous ( 无关紧要的,外来的,inessential, from outside)expressed--communicatedsome concerns about forest are expressed till early 1900. expressed- municated, B.increased. exhibit--feature(句中选)endangered<-->abundant(反义词,句中选)entail----involveenrich(enhance,enlarge,conceal,根据上下文有可能选conceal,我选enhance),establishment--formationenclosure--surroundingera--periodenormous--凶暴的,巨大的enhance --improve or enlargeelaborate adj.精心制作的, 详细阐述的, 精细vt.精心制作, 详细阐述v.详细描述embedded--encasedessentially adv.本质上, 本来even--already 恰好,正当expendable -- unprofitableexpose to--subject toexert--causeexpanse--areaexpanse == (笔试:expand = increase)这一题expanse 是考“n.区域”的意思for instance=for examplefast (go without food) (not sure !!!, donot affect you adversely)forage==feedflourishing--thrivingfragment--break upGap (笔试:gap 缺口,裂口= opening)Generate 产生, 发生Given = particularhence =thereforeharsh =drastichazard=dangerhaul (拖拉, 拖运)= pullHeightening (提高,升高) = increasingHub 中心=centerHydroelectric (adj.水力发电的)highlight/layer---innerhider-interfereheightening--increasinghost--great number世纪末19 世纪初美国制造业的革新.其中有一题tailors, butchers and a (host) of trades began to ...hub--center,hollow n.洞, 窟窿, 山谷adj.空的, 虚伪的, 空腹的, 凹的adv.<口> 彻底vi.形成空洞vt.挖空, 弄凹hamper--make difficultyheed--noticehold -- proposehold--keep upheighten--increase"indigenous"----native (in the context),incorporable = includedimmediately = closest( 说类人猿是人类最近的进化祖先)In and of themselves (not sure) = aloneIncorporable= Included (Incorporable adj.可结合的, 可包含的) indementionInitiate =begin;Instant = moment (adj. N. 片刻,瞬间)Invariably = alwaysinitiate =begin;in spite of that : HOWEVERimmediately: closest( 说类人猿是人类最近的进化祖先) Indemention Ingemination indemnificationIn quantity--in a large amount ofinauspicious--unfavorableintimidating 威吓, 胁迫incidental--minor pointincoherently 无条理的incorporate--includeillusion n.幻想immense adj.极广大的, 无边的, <口>非常好的ingenuity n.机灵, 独创性, 精巧, 灵活性ingenuity-- resourcefulnessingenious adj.机灵的, 有独创性的, 精制的, 具有创造才能inhibit --hindered inhibitinvade -- move intoinvaluable--highly usefuljeopardy=threatenJudge (判断,评价) = estimatejolting --shockingkey--significantlandscape=sceneryluxuriant=thriving( 答案还有moist)launch = startlack--withoutlinked--connectedmastery 的形容词形式-expert,maintain-continuemoreover=in addition( 答案还有thus)matter 文中issuemask = disguise MASKED 伪装的,隐藏的,潜伏的"milestone"---significant events ( in the context)Milestone = significant events (select in whole paragraph, spend much time for this one)Moreover-additionallymean --- signify (还有一选项intend)monopolize form --dominatemotif--patternmonitored--observedmagnitude--extendminutely adv.详细地, 精密地minutely--finelyminute --tinyminuscule--tinymodification--alteration(另有clarification),milestone--significant developmentmonotonous--boringNote = recordnature--characternotwithstanding --despitenote--recordoutbreak = sudden increase(improved, upsetted, 另两个我忘了)obscure=conceal 答案有干扰选项diminishoccasion-eventoutlet 出口,出路occasion-eventobscured- concealobtain --acquire"prosperous"--wreathy,premise = assumptionparcel out= distributeprocurement= obtainpractical/predictable/great-----p*midable(practical, not very sure)? came from a article: the American army in 1776, ----conquer prohibited = extremelypare away --- removePattern (n. 式样, 格调, 图案vt. 根据图形模仿,仿造= match, imitate)Pinnacle = high pointIBT-SAT 小马过河—专业备考社区小马过河——专业备考社区Pledge (保证, 誓言) = Promisepractically (几乎,差不多) = nearlyPredicament 困境Premise 前提v. 假设=assumePrevious = PastPrimitive (原始的,早期的,朴实无华的) = earlyPrincipal = dominantPrinciple = ruleprocure ( 获得,取得acquire, obtain/ 实现,完成= bring about, effect, procure a solution)primitive: earlypurchase==grip vt.买, 购买n.买, 购买principle (two times) 1 noun form i guess means-- ruleprincipal--mainproximity--closenessprocurement--obtainProcure===obtainpore--holeprior ----- pastpredicament: difficult situationpredicament--serious situationperspective, n.透视画法, 透视图, 远景, 前途, 观点, 看法, 观点, 观察protruding--projectingPunctual----没有直接对应选项(carefully(my key 表示时间精确not sure)potential--possiblepresumable--probablyprimary--dominantpreviously--beforepronounced--strongpose==presenteserve == saveRadical (基础的,根本的) = fundamental (radical = drastic) Rather than = instead ofRemedy (治疗)= cure,rigorous schedule = demanding(rigorous 严格的,严厉的demanding 要求高的,苛求的如:a demanding job )Rival = competitor"ramification"--consequence;ramification--consequenceredundancyremarkable--incrediblerevolutionous--quick discardingrevolutional --quick discarding/(我选了change,回来查字典发现我错了)revolution--dramatical changerigorous--demanding.refreshing--unusualrelevant adj.有关的, 相应的ritual n.典礼, (宗教)仪式, 礼节adj.典礼的, (宗教)仪式的rupture--burstradical--extremeremote--far awayshortage 照反义词spontaneous = unplannedsacred = holysubject to = vulnerable tosusceptible to = prone tosuccession----seriessparse,文中着反义词richscrap=fragmentset in motion = start (使开始运转,如set the plan in motion) Severe = harshshare = proportion (proportion 比例, 均衡, 面积, 部分vt.使成比例, 使均衡, 分摊)silhouette = outline (silhouette n.侧面影象, 轮廓)Simultaneous (同时发生的)= at the same timeSolicit = request (solicit v.恳求,请求)Specified (详细说明) = stateda matter of speculation (思索,推测,投机)= supposition (speculation 的同义词)stunning = dramatically(不?定) 都在句中? (stunning: very surprising, very impressive ,另人印象深刻的; dramatically: 有戏剧表现力的,引人注目的)sturdy = strongsubsequent (后来的,随后的) = latersupplant = replaceSusceptible to (容易….的): prone tostem from --- grow out ofset in motion 的同义词,选项有start 等Webster 地解释比较好:to give impulse tospecified : statedsilhouette =outlinesolicit==requestsevere--harshsacred--holystaple--importantsimultaneoussoaked--absorbedsplit--dividedscorching--exceeding hotsite--locationsingularly--particularlystint 紧缩节省slightest 最轻微的sparingly 节俭地spur--stimulusstaggering 惊人的,巨大的stunned--hinderedstunt v.阻碍...发育, 妨碍...生长, 作惊人表演, 使绝招n.发育迟缓, 矮小的人(或物), 惊人表演, 绝技sumptuous--luxuriousshield--protectshrink < > spread(反义)significant-- meaningful (obvious is not right)spawn--createspot--identifysnap--breakshied away from--avoid"tangible"---physicaltracts (of land) = areaTangible = materialteasers (爱戏弄人的人/ 难题a puzzling problem)Transfer = movetricky (狡猾的,棘手的,difficult)tendency==inclinationteemed with--were full ofUnderlying = inner (underlying adj.在下面的, 隐含的,implicit 如underlying meaning)underpinning (基础, 支柱, 支撑a support or foundation) Unqualified (不合格的,无限制的,绝对的) = complete utilitarian = functional (文中选) (utilitarian adj.功利的, 实利的, 功利主义的n.功利论者)unqualified =complete;utilitarian =functionaluniversally--without exceptionunrestricted--unlimitedundergone--experiencedvigorous = strongvexing = difficult (not sure) (vex: 使恼怒,使痛苦, puzzle, annoy) vast--immensevast--greatvehicle--meansvariability==tendency to changewithstand==persist >avoid/persist(原文是:...brick withstood the weathering for a long time...) withstand=resistwear--usewhatever --in any case/ at any rate/at all eventwary--cautiousway station--stopyield--providegame-->animals teemed with-->were full ofpronounced-->strong fragment-->break upestablishment-->formation consequently-->thereforeheighten-->increase previously-->before era-->perioddriven-->pushed poses-->presentsvariability-->tendency to changesubstantially-->significantly monitored-->observedcapable of using-->able to use shift-->changeforsook-->leftsignature-->identifying characteristicsstandardized-->uniformorientation-->arrangement terrain-->ground delineate-->outline prescribing-->assigning promotes-->contributes toindicators-->signs obviously-->clearly components-->elements common-->shared broad-->general overlapping-->haring characteristics compelled-->forced stumbled upon-->accidentaladapted-->modifiedtedious-->tiresome facilitating-->easing freezing-->haltingcontexts-->settings accommodate-->allow for pounding-->hitting conspicuous-->noticeable assess-->evaluatetoxin-->poison diverge-->move apart depicted-->presentedprecision-->accuracy obvious-->clear feed-->satisfysources-->supplies means-->methods flourishing-->thriving univerisally-->without exception anxious-->eagerat bay-->under control soaked up-->absorded split-->divided scorching-->exceedingly hot attributed-->creditedsuccessive-->subsequent stimulates-->causes scarcity-->shortage encourageed-->promoted vast-->great affords-->providesremote-->far away available-->obtainable vehicle-->meansin essence-->basically constitutes-->consists ofgradually-->little by little diminished-->reduceddiversity-->variety expanses-->areas prior-->pastacceleration-->speeding up essential-->fundamentaloutgroeth-->result incentive-->motive impede-->obstruct severe-->large convert-->transform magnitude-->extent beneficial-->advantageous envisioned-->conceived ofscan-->examine orbiting-->revoling power-->strengthcases-->situations exhibit-->show unusual-->uncommonthus-->consequently constant-->continued sequence-->succession attain-->reach on the other hand-->however solitary-->lone rotates-->turns allocates-->designates spoken for-->claimed status-->position in its own right-->independentconceiving-->imagining support-->sustain alternative-->option sequence-->order periodic-->regular elsewhere-->in other places hampering-->restricting accelerated-->speeded upsubjected to-->placed under adjacent-->nearby accountfor-->explainsroughly-->approximately puzzle-->question convert-->transform spend-->use practical-->realistic critical-->importanttracing-->following vital-->important components-->parts occasionally-->sometimes aquatic-->marineapparently-->seeminglyconveys-->communicatates reacting-->responding repel-->ward off waves-->groups rocked-->moved capital-->moneyprevailing-->dominantladen-->filled split-->divided anticipated-->expectedliabilities-->limitations compelling-->powerful nature-->quality reinforced-->strengthened discovers-->learnsresult-->consequencedislodge-->remove tasks-->responsibilities forage for-->hunt for dissemination-->spread advocating-->recommendinglittle more than-->simply mere-->insignificant flavor-->essence dispersal-->distribution segment-->part complex-->elaborate proposed-->hypothesized variation-->changesubsequently-->afterwardinquiring-->curious alternative-->different reproduce-->copy adorn-->decorate suggests-->indicates refined-->perfected pinnacle-->high point recurred-->reappearedrather-->instead at least-->at the minimum accompany-->join。
电脑错误代码

Windows NT 错误代码=========================================================== 作者: youhello()发表于: 2007.09.29 16:07分类: 程序开发出处: /post/4630/401658---------------------------------------------------------------Microsoft Windows NT Workstation8 LZERROR_UNKNOWNALG 不识别压缩算法。
-7 LZERROR_BADVALUE 输入参数超出可接受范围。
-6 LZERROR_GLOBLOCK 全局句柄错误。
-5 LZERROR_GLOBALLOC LZFile 结构的内存不足。
-4 LZERROR_WRITE 输出文件的空间不足。
-3 LZERROR_READ 压缩文件格式被破坏。
-2 LZERROR_BADOUTHANDLE 输出句柄无效。
-1 LZERROR_BADINHANDLE 输入句柄无效。
0L NO_ERROR 没有错误。
0L ERROR_SUCCESS 操作成功执行完毕。
1L ERROR_INVALID_FUNCTION 函数不正确。
2L ERROR_FILE_NOT_FOUND 系统无法找到指定的文件。
3L ERROR_PATH_NOT_FOUND 系统无法找到指定的路径。
4L ERROR_TOO_MANY_OPEN_FILES 系统无法打开文件。
5L ERROR_ACCESS_DENIED 访问被拒绝。
6L ERROR_INVALID_HANDLE 内部文件标识符不正确。
7L ERROR_ARENA_TRASHED 存储控制块被破坏。
8L ERROR_NOT_ENOUGH_MEMORY 处理该命令没有足够的存储可用。
9L ERROR_INVALID_BLOCK 存储控制块地址无效。
CODE_SIZE_LIMIT_IN_RESTRICTED_VERSION_EXCEEDED

CODE SIZE LIMIT IN RESTRICTED VERSION EXCEEDE D
本人在使用KEIL4编译软件时,由于程序代码过长,造成了如标题所示的错误,编译无法通过,开始我以为是自己的代码过长,造成软件无法编译通过的。
后来在网上一查,才发现是自己的keil软件没有经过破解,所以code size 一直受到限制。
因为使用STC ISP4.83烧录的时候需要hex文件,所以既然keil没有被破解,自然这工具就无法使用了。
因而我便从网上找了keil v8.02的破解工具,将该软件破解。
下面将破解图片献上。
第一步:找到这个破解软件,打开是这样一个界面
第二步:打开keil4,然后在file里找到如图所示的license management,如图
打开后复制CID至注册机界面,如图:
项会点亮,此时你变可以按下add lic了。
如下图所示
然后之后keil便会提示你注册成功。
它也会提示你使用期限,我的为2020年9月到期。
Klocwork培训手册K9.1

4.2 命令行分析 ........................................................................................................................... 11 4.3 KMC 分析步骤.......................................................................................................................12 4.4 TORNADO 程序分析 .................................................................................................................14
贝斯普萨(侦查文书)说明书

Besponsa™ (inotuzumab ozogamicin)(Intravenous)Document Number: IC-0317 Last Review Date: 10/24/2022Date of Origin: 09/19/2017Dates Reviewed: 09/2017, 11/2018, 11/2019, 11/2020, 11/2021, 07/2022, 11/2022Customized Date: 07/20/2022Effective Date: 01/01/2023I.Length of AuthorizationCoverage will be provided for 6 months (for up to a maximum of 6 cycles) and may not berenewed.II.Dosing LimitsA.Quantity Limit (max daily dose) [NDC Unit]:•Besponsa 0.9 mg powder for injection single-dose vial: 7 vials per 21 daysB.Max Units (per dose and over time) [HCPCS Unit]:Cycle 1•27 billable units (2.7 mg) on Day 1, 18 billable units (1.8 mg) on Days 8 and 15 of a 21 to 28-day cycleSubsequent Cycles (maximum of 5 cycles)•27 billable units (2.7 mg) on Day 1, 18 billable units (1.8 mg) on Days 8 and 15 of a 28-day cycle for up to 2 cycles•18 billable units (1.8 mg) on Day 1, Day 8, and Day 15 of a 28-day cycle for up to 3 cycles III.Initial Approval Criteria 1Coverage is provided in the following conditions:•Baseline electrocardiogram (ECG) is within normal limits; AND•Patient has not previously received treatment with inotuzumab ozogamicin; ANDUniversal Criteria 1-3•Patient has CD22-positive disease; ANDAdult B-Cell Precursor Acute Lymphoblastic Leukemia (ALL) † Ф 1-3•Patient is at least 18 years of age; ANDo Patient has relapsed or refractory disease; AND▪Used as single agent therapy; OR▪Used in combination with mini-hyper CVD (cyclophosphamide, dexamethasone, vincristine, methotrexate, cytarabine); AND➢Patient is Philadelphia chromosome (Ph)-negative; OR➢Patient is Philadelphia chromosome (Ph)-positive and refractory to prior tyrosine kinase inhibitor therapy (e.g., imatinib, dasatinib, ponatinib,nilotinib, bosutinib, etc.); OR▪Used in combination with tyrosine kinase inhibitor (TKI) therapy (e.g., bosutinib, dasatinib, imatinib, nilotinib, or ponatinib); AND➢Patient is Philadelphia chromosome (Ph)-positive; ORo Used as induction therapy in patients ≥65 years of age or with substantial comorbidities; AND▪Used in combination with mini-hyper CVD; AND▪Patient is Philadelphia chromosome (Ph)-negativePediatric B-Cell Precursor Acute Lymphoblastic Leukemia (ALL) ‡ 3,4•Patient is at least 2 years of age; AND•Patient has relapsed or refractory disease; AND•Used as single agent therapy; ANDo Patient is Philadelphia chromosome (Ph)-negative; ORo Patient is Philadelphia chromosome (Ph)-positive; AND▪Patient is intolerant or refractory to prior tyrosine kinase inhibitor (TKI) therapy(e.g., imatinib, dasatinib, etc.)† FDA Approved Indication(s); ‡ Compendium Recommended Indication(s);Ф Orphan DrugIV.Renewal Criteria 1Coverage cannot be renewed.V.Dosage/Administration 1VI.Billing Code/Availability InformationHCPCS Code:•J9229 − Injection, inotuzumab ozogamicin, 0.1 mg: 1 billable unit = 0.1 mgNDC:•Besponsa 0.9 mg lyophilized powder in single-dose vial: 00008-0100-xxVII.References1.Besponsa [package insert]. Philadelphia, PA; Pfizer Inc., March 2018. Accessed September2022.2.Kantarjian HM, DeAngelo DJ, Stelljes M, et al. Inotuzumab Ozogamicin versus StandardTherapy for Acute Lymphoblastic Leukemia. N Engl J Med. 2016 Aug 25;375(8):740-53.3.Referenced with permission from the NCCN Drugs & Biologics Compendium (NCCNCompendium®) inotuzumab ozogamicin. National Comprehensive Cancer Network,2022. The NCCN Compendium® is a derivative work of the NCCN Guidelines®.NATIONAL COMPREHENSIVE CANCER NETWORK®, NCCN®, and NCCNGUIDELINES® are trademarks owned by the National Comprehensive Cancer Network, Inc. To view the most recent and complete version of the Compendium, go online to. Accessed September 2022.4.Bhojwani D, Sposto R, Shah NN, et al. Inotuzumab ozogamicin in pediatric patients withrelapsed/refractory acute lymphoblastic leukemia [published correction appears inLeukemia. 2019 Mar 7;:]. Leukemia. 2019;33(4):884–892. doi:10.1038/s41375-018-0265-z. Appendix 1 – Covered Diagnosis CodesAppendix 2 – Centers for Medicare and Medicaid Services (CMS)Medicare coverage for outpatient (Part B) drugs is outlined in the Medicare Benefit Policy Manual (Pub. 100-2), Chapter 15, §50 Drugs and Biologicals. In addition, National Coverage Determination (NCD), Local Coverage Articles (LCAs), and Local Coverage Determinations (LCDs) may exist and compliance with these policies is required where applicable. They can be found at: https:///medicare-coverage-database/search.aspx. Additional indications may be covered at the discretion of the health plan.Medicare Part B Covered Diagnosis Codes (applicable to existing NCD/LCA/LCD): N/A。
Tasking VX C166 Lite一年版本限制说明

Restrictions of the TASKING VX-toolset Lite for C166MR119-800 (v2.5) August 25, 2010Restrictions of the TASKING VX-toolset Lite for C166Copyright © 2010 Altium Limited.All rights reserved.Y ou are permitted to print this document provided that (1) the use of such is for personal use only and will not be copied or posted on any network computer or broadcast in any media, and (2) no modifications of the document is made. Unauthorized duplication, in whole or part, of this document by any means, mechanical or electronic, including translation into another language, except for brief excerpts in published reviews, is prohibited without the express written permission of Altium Limited. Unauthorized duplication of this work may also be prohibited by local statute.Violators may be subject to both criminal and civil penalties, including fines and/or imprisonment. Altium, TASKING, and their respective logos are trademarks or registered trademarks of Altium Limited or its subsidiaries. All other registered or unregistered trademarks referenced herein are the property of their respective owners and no trademark rights to the same are claimed.Table of Contents1. Restrictions of the Lite Edition (1)1.1. User Guides (1)1.2. General Restrictions (1)1.3. Eclipse and Debugger (1)1.4. C Compiler (2)1.5. Linker (4)1.6. Options Overview (4)1.7. Pragmas (5)1.8. Considerations for Upgrading (6)iiiRestrictions of the TASKING VX-toolset Lite for C166 ivChapter 1. Restrictions of the Lite Edition This Lite Edition of the T ASKING VX-toolset for C166 has a reduced set of features compared to the full product.The following sections give an overview of the restrictions.1.1. User GuidesThe Getting Started and User Guide in the Lite Edition are the same as in the full version of the toolset. The not supported features and restrictions are described in this document.1.2. General RestrictionsC++ SupportThe Lite Edition does not support C++.The C++ compiler is not included in this product.Device SupportThe Lite Edition only supports XC2000 and XE16x devices.The full toolset also supports other C166 based devices.LibrariesOnly the C libraries and run-time libraries required to support the limited option set of the Lite Edition are included.The source files of the libraries are not included. Libraries for trapped floating-point are not included.LicensingThe Lite Edition is available as a node-locked license only.The full version is available as a node-locked license and a floating/network license in three different Editions: Standard, Professional and Premium.1.3. Eclipse and DebuggerTool optionsThe tool options (Project » Properties » C/C++ Build » Settings » Tool Settings) that are not supported in the Lite Edition are disabled (grayed out).Build toolsIt is not possible to use other build tools than Eclipse in combination with the Altium make (amk).The Lite Editions of the C compiler and linker will only run when you use the T ASKING Eclipse integrated development environment.1Restrictions of the TASKING VX-toolset Lite for C166Board supportThe Lite Edition only supports the "Infineon EasyKit XC2000/XE166" or custom hardware using theJT AG/OCDS via a miniWiggler.The full version of the product also supports debugging over RS-232, using a ROM/RAM monitor, and also supports additional evaluation boards. A miniWiggler can be requested or purchased from Infineon. Altium does not deliver this with the Lite Edition.Script debuggerThe script debugger, which can be used to run automated debugger scripts, is not included in the Lite Edition.1.4. C CompilerPredefined macroThe compiler in the Lite Edition has the predefined macro __LITE__.This macro is only defined in the Lite Edition, not in the full version.Y ou can use it to create conditional C code. For example:#ifdef __LITE__/* this part is only for the Lite Edition */...#endifMemory modelsThe Lite Edition only supports the near data memory model.The compiler option -Mn or--memory-model=near is accepted. Using the options for the far, shuge and huge memory model will result in an error.Also the option--near-functions, to make all functions by default near, is not supported in the Lite Edition. MIL linkingThe Lite Edition of the compiler has no support for MIL linking (--mil-link), which means that no global optimizations can be performed. Using MIL linking in the full version of the toolset often leads to significant optimization improvements. Automatic near The automatic near optimization (--automatic-near) is only useful for the far, shuge and huge memory model, and must be used in combination with MIL linking. Therefore this optimization is not supported in the Lite Edition.Data allocation thresholdsThe automatic data allocation thresholds are not supported in the Lite Edition.This applies to the near threshold (--near-threshold) and the bit addressable struct threshold (--bita-struct-threshold). Optimization settingsThe Lite Edition has a reduced set of optimizations. It is not possible to change the optimization level (-O/--optimize) or to change the trade-off between size and speed (-t/--tradeoff). Using the -O or--optimize options will result in an error.2Restrictions of the Lite Edition The -t and --tradeoff options only accept 4 as argument, meaning fully optimizing for size.The #pragma optimize and #pragma tradeoff are also not supported.The effective optimization is between optimization level 0 and level 1.The enabled optimizations are:•register coalescer (-Oa)•interprocedural register optimizations (-Ob)•common subexpression elimination (-Oc)•generic assembly code optimizations (-Og)All other optimizations are disabled.Section renamingThe Lite Edition does not support section renaming (-R/--rename-sections, #pragma section), only the default section names as generated by the compiler can be used.Treat double as floatThe -F/--no-double option is not available in the Lite Edition of the compiler.The single precision libraries are not included in the Lite product.Trapped floating-pointT rapped floating-point is not supported by the Lite Edition.The run-time floating-point libraries with trap support are not included.The option in Eclipse is not available.MISRA-CThe C compiler in the Lite Edition has no support for checking the MISRA-C rules.The option --misrac and the #pragma nomisrac are not supported.CERT CThe Lite Edition of the compiler has no support for checking against the CERT C Secure Coding Standard. The option --cert is not supported.ProfilingDynamic (instrumented) and static profiling are not supported in the Lite Edition of the toolset.The C compiler option -p/--profile and the #pragma profiling are not supported.Run-time error checkingThe compiler in the Lite Edition has no support for run-time error checking.The option -r/--runtime and the #pragma runtime are not supported.3Restrictions of the TASKING VX-toolset Lite for C166Global type checkingThe Lite Edition of has no support for checking mismatches between the types of globals and externs. The option --global-type-checking of the compiler is not supported.1.5. LinkerUnreferenced section removalThe unreferenced section removal optimization of the linker is not available in the Lite Edition.The option -Oc/--optimize=+delete-unreferenced-sections cannot be used.The linker does allow using explicit disabling of this optimization (-OC/--optimize=-delete-unreferenced-sections).Duplicate code and data removalThe duplicate code removal (-Ox/--optimize=+delete-duplicate-code) and duplicate data removal (-Oy/--optimize=+delete-duplicate-data) optimizations of the linker are not supported in the Lite Edition. The mentioned options cannot be used.The linker does allow using explicit disabling of these optimizations (-Ox/--optimize=+delete-duplicate-code) and (-OY/--optimize=-delete-duplicate-data).Global type checkingThe Lite Edition has no support for checking mismatches between the types of globals and externs.The option --global-type-checking of the linker is not supported.1.6. Options OverviewThe following sections give an overview of the options that are restricted or not-supported in the Lite edition. Note that it is not possible to run the tools outside Eclipse in the Lite edition.C compilerThe following options are not available in the Lite Edition of the compiler, an error is issued when used:--automatic-near--bita-struct-threshold--cert--global-type-checking--lsl-file--lsl-define--lsl-include--lsl-strategy--mil--mil-split--miscrac--misrac-advisory-warnings4Restrictions of the Lite Edition--misrac-required-warnings--misrac-version--near-functions--near-threshold--no-double / -F--optimize / -O--profile / -p--rename-sections / -R--runtime / -rThe following options are available but are only accepted with a fixed argument, an error is issued when other arguments are used:--tradeoff / -tOnly -t4 or --tradeoff=4 is accepted.--model / -MOnly -Mn or --model=near is accepted.LinkerNot-supported options:--global-type-checkingThe following option has restrictions to the allowed flags:--optimize / -OThe following flags are not supported, and error is issued when used:c+delete-unreferenced-sections+delete-duplicate-codex+delete-duplicate-datayOther flags of this option are supported.1.7. PragmasThe following pragmas are not supported, an error is issued when used:#pragma optimize#pragma endoptimize#pragma nomisrac#pragma profile#pragma endprofile5Restrictions of the TASKING VX-toolset Lite for C166#pragma profiling#pragma runtime#pragma section#pragma endsection#pragma compactmaxmatch#pragma maxcalldepth#pragma inline_max_incr#pragma inline_max_sizeThe following pragma has restrictionsThe only value that is accepted is 4.#pragma tradeoffOther values will result in an error1.8. Considerations for UpgradingFrom this document it is clear that the Lite Edition lacks many features that are available in the full version. Nevertheless it is absolutely possible to develop complete applications using the Lite Edition.This section gives some considerations for upgrading to the full version of the TASKING VX-toolset for C166. OptimizationsThe full version offers significant better optimizations. On code benchmarks the following improvements were measured.Code size (optimization for size)23%Average improvement when using the full version:Peak improvement when using the full version:50%Cycles (optimization for speed, measured with simulator)39%Average speed improvement when using the full version:76%Peak improvement when using full version:Large applicationsApplications with more than 4 pages of data (each 16kB) cannot be built with the Lite Edition, unless you explicitly use the __far, __shuge or __huge qualifiers on your C objects. Using the full toolset you can select the appropriate memory model and let the compiler automatically determine which objects can be best allocated in near data (automatic near feature).6Restrictions of the Lite Edition Build systemAs soon as you want to use your own build system or want to use the tools from the command line it is required to use the full toolset.LocatingFor locating specific sections in certain address ranges it is often required to use your own section naming. The specific sections can then be picked up easily in the linker script file.With the full version of the compiler you have full control over the generated section names.DebuggingThe Lite Edition lacks features that will help preventing and finding bugs:•Global type checking, helps finding problems caused by global/extern type mismatches.•The CERT C Secure Coding Standard is defined to prevent using C language constructions that are known to often result in bugs.The full compiler can analyze your code for these constructions.•The MISRA-C standard applies restrictions to the C standard to improve safety and reliability.The full compiler can check whether the MISRA-C rules are followed in your code.•The full version of the C compiler can add checks to your code to find run-time problems.This includes bounds checking, reporting of not handled case in a switch and memory allocation consistency checks.•When working with floating-point, the trapped floating-point libraries can help to find floating-point exceptions, such as division by zero and floating-point overflow/underflow, during development.These libraries are not included in the Lite Edition.•With the profiling feature in the full version you can find critical parts of your code and make improvements as needed.•The script debugger which is included in the full version can be used to create and run automated test scripts for testing your application.Silicon bug supportWorkarounds and assembler checks for new discovered CPU functional problems may only become available with the next regular version update of the Lite Edition, whereas for the full version intermediate patches may be released.This is an important consideration when developing a safety critical application. Program installationsWhen you upgrade from the Lite Edition to the full version, you can install the toolsets and use them next to each other on the system as they are installed in separate folders.Third party tool supportAltium has an active program in place to support third party tool vendors that offer various RTOS, middle-ware, debugger, modeling, etc., solutions that are compatible with T ASKING products. It is important7Restrictions of the TASKING VX-toolset Lite for C166to understand that for the VX-toolset for C166 these products have been qualified with the full version and that therefore compatibility with the Lite Edition may not be guaranteed. In case of doubt, please contact the appropriate tool vendor for more information.Legacy version supportAltium does not have/keep previous (legacy) versions of the Lite Edition available and will not make license keys available for older versions than the current. Projects that require availability and support of an old toolset release should be developed with the full version.8。
EG2001X针测机的保养和维护
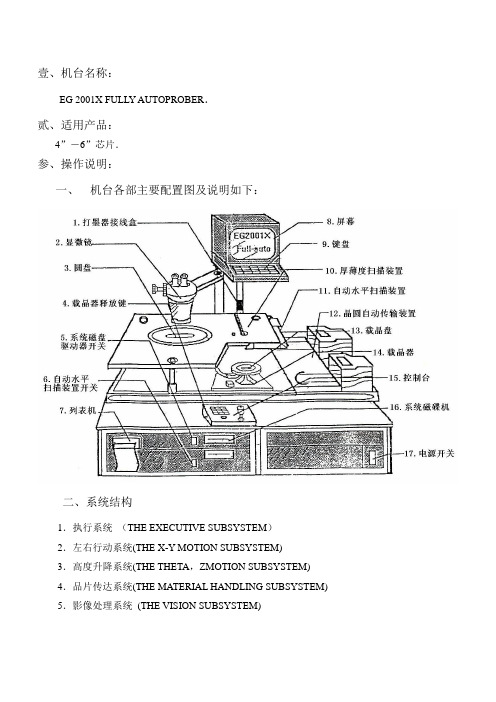
壹、机台名称:EG 2001X FULLY AUTOPROBER.贰、适用产品:4”-6”芯片.参、操作说明:一、机台各部主要配置图及说明如下:二、系统结构1.执行系统(THE EXECUTIVE SUBSYSTEM)2.左右行动系统(THE X-Y MOTION SUBSYSTEM)3.高度升降系统(THE THETA,ZMOTION SUBSYSTEM)4.品片传达系统(THE MATERIAL HANDLING SUBSYSTEM) 5.影像处理系统(THE VISION SUBSYSTEM)EG2001X针测机的保养和维护程序一.EG2001X全自动针测机l. 设备兴材料:工具组维修用润滑油(非腐蚀性)清洁用的布,细砂纸,酒精2. 作业程序:保养项目保养方法晶圆承载台用布清洁承载台,用酒精洗净INK渍移动平台用翘棒翘起CHUCK,用细砂纸磨去铁溴,再用布清洁平台和CHUCK底部并打蜡自动传输机构用吸尘器和布清洁干净INKERS 用酒精清洁INKER,并检查接线是否断裂,鱼线动作是否正常VISION MODULE 用气枪及吸尘器清洁干挣POWER MODULE 用气枪及吸尘器清洁干净散热风扇用气枪及吸尘器清洁干净电路板清洁用气枪及吸尘器清洁干净,并用酒精清洁电路板金手指二.EG2001X半自动针测机1. 设备兴材料:工具组维修用润滑油(非腐蚀性)清洁用的布和细砂纸,酒精2. 作业程序:全自动保养项目中去除自动传输机构,影映控制箱和PROIFILE的调整,其它同全自动。
三.机台的水平校正1. 设备与材料:精密水平仪2. 作业程序:先用水平仪在CHUCK平台上取三个方向,分别调整CHUCK底座的三颗螺丝至水平仪数值偏差在10MIL之内:同样用水平仪测锁圆盘的三个点调整平台的三个螺丝至偏差在10MIL之内。
四.PROFILE的校正:1. 移动CHUCK至PROFILE头的下方(WAFER OFF)2. 按PROG+0键(将PROFILE头降下)3. 按PROG+Z键(将PROFILE头与CHUCK接触,高度约255MIL)4. 将CHUCK高度调至247MIL(PROFILE动作时与CHUCK间距为8MIL)时,PROFILE BOX的LO,HI灯会减,如不灭则调旋钮至亮的一方旋转5. 调节好后,UP时HI灯亮,DOWN时LO灯亮PROBER各BOARD说明:A1:SYSTEM MEMORY PCB1. 包含主系统程序2. 存储程序参数/演算数值输入3. 内部时间控制A2:MOTION CONTROLLOGIC PCB主要控制X-Y MOTOR LOGIC 产生MOTOR DRIVE PULSE1. 控制MOTOR速度2. 控制TRA VEL距离3. 控制轴向移动4. 控制管理移动方向A3:SYSTEM CPU PCB1. RUN主系统程序2. 控制所有PCB3. 传达资料4. 管理所有的I/O PORTS (A4、A7)5. 控制AUTO ALIGNMENT(和VISION MODULE配合)6. 执行温度补偿A4:TESTER INTERFACE PCB含有3个I/O PORTS:1. TESTER:TEST START,TEST COMPLETE,REJECT LINES2. RS2323. IEEE-488A5:THETA,Z FUNCTION PCBl. 作THETA、Z INKER DRIVER PCB到SYSTEM CPU的界面;INKING信号:边缘SENSOR输入:THETA,Z DRIVER信号:ZENCODER。
航海通告及海图改正及如何填写航海日志

Chart[Last correction] - 1254[548/98] - 1260 - [343/99]
Light List Vol.F/99,3401
Chinese Notice 5/761/99 (HH.563/67/03) 18
5.根据英版《航海通告》改正海图
8)试述使用《航海通告》改正海图的基本原则和注意 事项,并根据下面给定的英版《航海通告》(1999 年)的内容改正海图,进行海图小改正的登记
5
3.识图
3)试述英版海图标题栏的主要内容和图廓注记
的主要内容及其作用,并根据Chart 5011填写
出下列海图图示:(1) 高程基准面至建筑物顶端
的高度(20m)
(2) 1978年据报
(3)
鱼礁
(4) 深度基准面以上的高度 (4.9m)
(5) 底质为中沙底
(6) 非危险沉船 (7)经
扫海的最浅水深25m的沉船 (8) 露出平均大
(6) 深度基准面上1.8m 的干出礁 (7)经扫海的最
浅水深25m的沉船 (8) 深度不明的危险暗礁 (9)
检疫锚地 (10) 编号为Z-44的平台(Platform) (11)
在3cm频带内应答具有莫尔斯信号(K)的雷达应答
标 (12) 标身为杆状的东方位标志
8
4.根据中版《航海通告》改正海图
Chart[Last correction] - 1254[548/98]
E(shore)
Chinese Notice 6/792/99 (HH.310/545/02)
19
5.根据英版《航海通告》改正海图
9) 试述使用《航海通告》改正海图的基本原则和注 意事项,并根据下面给定的英版《航海通告》 (1999年)的内容改正海图,进行海图小改正的登 记
银行卡跨行交易应答码终端显示规定

Code Response Description Action
含义
19
交易超时,请查询转入账户
A2
Time out, please inquiry the
destination account
--
转入行超时
20
无此转入账户
A3
No destination account
--
转入行无此账户
附表二:POS 终端显示内容
Decline 不允许持卡人进行的
not permitted to
交易
cardholder
58
Transaction
Decline 不允许终端进行的交
not permitted to
易
terminal
59
Suspected fraud
Decline 有作弊嫌疑
62
Restricted card
Decline 受限制的卡
日期切换正在处理
91
Issuer or switch is Decline 发卡行或银联不能操
inoperative
作
92
Financial institution Decline 金融机构或中间网络
or
intermediate
设施找不到或无法达
network
facility
到
cannot be found for
tries exceeded
限
11
余额不足,请查询
51
Not sufficient funds Decline 无足够的存款
Balance Insufficient, please
inquire
贝尔南特通信互联服务有限公司本地订购指南(LOH)版本13.0d的更新,适用于TCIF9发布13.0

BellSouth Interconnection Services675 West Peachtree StreetAtlanta, Georgia 30375Carrier NotificationSN91083924Date: January 5, 2004To: Competitive Local Exchange Carriers (CLEC)Subject: CLECs – (Documentation/Guides) - Update to the BellSouth Local Ordering Handbook (LOH) Version 13.0d for Telecommunications Industry Forum 9 (TCIF 9) Release 13.0This is to advise that BellSouth has identified the following documentation defects in the LOH Version 13.0d for TCIF 9 Release 13.0.CCPDescription Of The ChangeNumber1608 Added “RCO introduction” information for UNE P Centrex R/C/O tables1610 Updated LOH to add a valid note to the "SC" field to the entry note section for the “LCSL” field.Please refer to the attachments for specific details of the changes listed above.These changes will be reflected in the next update of the TCIF9 Release 13.0/LOH Version 13.0e scheduled to be posted February 9, 2004.A summary of all changes within this document will be listed in the Summary of Changes Section. This update can be found on the BellSouth Interconnection Services’ Web site in the Customer Guides Section at:Please contact your BellSouth Local Support Manager with any questions.Sincerely,ORIGINAL SIGNED BY JERRY HENDRIXJerry Hendrix – Assistant Vice PresidentBellSouth Interconnection ServicesAttachmentsCCP 1608 Attachment Listed Below13.0UNE P CentrexOverview For UNE P CentrexThis overview contains important information applicable to the following REQTYP M UNE P Centrex Product:•UNE PCentrex®•UNE P Centrex, is a Measured rate service.Telephone Number Assignment: Telephone numbers for these products are assigned to the Centrex, Common Block by CTX name, therefore telephone numbers may not be obtained from ATLAS. Telephone numbers inadvertently assigned from ATLAS by the CLEC may result in a clarification on or before the due date. Telephone numbers are not guaranteed until installed and working. To obtain telephone number assigned to common block - contact your Local Support Manager (LSM) .CAUTIONUNE P Centrex, may not be shared between service providers, therefore Partial Migration of service is allowed only when the following criteria is met:When a CLEC submits a request for initial and subsequent Partial Migration ACT= P, Q on Centrex, services, the ports being migrated must change, the CLEC may not share a UNE P Centrex, account with another service provider. The CLEC may choose to partial migrate to one of the following options:•The CLEC may request a new UNE P Centrex .•The CLEC may request to partial migrate the ports to an existing UNE P Centrex system provided the ports will migrate to a UNE P Centrex system that is already billed to the CLEC.•The CLEC may request to partial migrate the service and change to a different type of service (e.g., the ports may change to 1FB).CAUTIONCLECs must provide all USOCs and FIDs associated with provisioning theUNE PCentrex ports on Subsequent Service order activity i.e. CTX, CAT, SFG,DPG,CFNB, CFND etc.).When all ports at the service address (SA) main location of a UNE P Centrex, BellSouth® Centrex®, ESSX®, and/or MultiServ®/MultiServ PLUS® account are beingdisconnected or moved this will result in a complete move of the system (T) order. In the event all the lines at the main location are to be disconnected, the CLEC must advise BellSouth® of the new main telephone number, and the new main location service address (SA). The new main telephone number must be working at the new main address. This information may be indicated in the remarks section of the LSR.Generally CLECs do not need additional technical direction or assistance when ordering UNE P Centrex services, however if additional technical direction and assistance is required the CLEC should contact their Local Support Manager (LSM).If UNE P Centrex has the Customer Control feature, a Customer Control Initialization form must be completed and sent to the LCSC along with the Switch As Is / Switch As Specified / or Switch With PIC Change / Freeze order request.On complex services UNE P Centrex with Customer Control features,•when the end user and/or CLEC uses this feature to make a line or feature changea referral will be sent to the LCSC.•When the LCSC determines that a service order is needed to change customer service records (i.e., telephone number swaps) the referral will be treated as anLSR to make changes and a service order will be generated.•The CLEC is responsible for initiating a service order to correct any information pertaining to the Company's Published Directory Listings that changes as a result of a Customer Control TN swap.•The CLEC will receive a FOC, and a unique PON will be assigned indicating the change was generated due to Customer Control referral.DescriptionThe unbundled loop/port combination UNE-P Centrex as developed consists of all necessary UNE elements when ordered will provide CLECs an end-to-end voice grade service for their end-users. The basic UNE elements associated with a single UNE-P Centrex are as follows:•UNE Loop- a 2 Wire Voice Grade non-design loop from the CLECs end user customer NID to the BellSouth local serving central office. In some instanceswhere the CLEC's end user customer location is served from a different wirecenter than the Centrex Common block Serving Wire Center a 2 Wire VoiceGrade Design Loop will be utilized.•2-Wire Voice Grade port (Centrex): There is one associated BellSouth Centrex Switch port for each 2 Wire Voice Grade Loop. Each 2-Wire Voice grade port(Centrex) provides access to the Centrex features. Features available to eachstation vary depending on the type of switch in the serving central office. Theavailability of features and/or restrictions must be identified at the time ofordering Features inherent to the switch and switch software not currently being used or not purchased by Bellsouth may still be available to the CLEC through the Bona Fide Request (BFR) process.• A common Block Program: Within the BellSouth Switch the 2-wire voice grade ports (Centrex) are programmed into a common block of numbers which willpartition the switch to serve a specific customer and as such share certain inherent Centrex functionalities, capabilities, and features. The Common Block program is also known as the "Common Bock" or the "Centrex Customer Group". TheUnbundled Centrex Common Block defines system level parameters giving the Centrex virtually unlimited growth. Common equipment parameters offer theminimum capabilities of the system.•Network Access Registers: A NAR is associated with access outside of the Centrex system. Each NAR provides a single talking path to the public switched network or a private network. A NAR can be inbound, outbound or combination.All unbundled ports are subject to Unbundled Switching and to LocalInterconnection Usage charges. These charges will apply to each port/loopcombination of UNE-P Centrex. Consequently, other than to limit access to the Public Switched Network, NARs are on to a necessary network element of UNE-P Centrex. During the conversion process all NARs will be retained as is from the converted BellSouth service. NARs will be zero rated on the CLEC Account.Subsequent, rearrangements, additions, or removal of NARs will incur theappropriate subsequent activity charges (the USOC URECA should be used) per request. New installations can be provisioned with or without NARs at the request of the CLEC.•UARCX combination NARs (2 Way Measured)•UAR1X Incoming NARs (1 Way Incoming Measured)•UAROX Outgoing NARs (1 Way Outward Measured)•Unbundled Switching and Local Interconnection Usage Charges (URECS). these charges will apply to each port/loop combination of Une-P Centrex. •Telephone Numbers: Typically, there is a block of telephone numbers that form the common block or core of UNE-P Centrex. Additionally, one telephonenumber will be utilized for each port/loop combination in UNE-P Centrex. There will be no recurring charges to the CLEC for reserving telephone numbers for UNE-P Centex.•The UNE-P Centrex will be restricted by the capabilities of the serving Bellsouth Switch.•In states where the service must already exist on the BellSouth network before conversion, BellSouth will use the same facilities that currentllly serve the enduser wherever possible.•Feature functionality that is defined as "features that are a function of the Switch"will be available to the port at the state ordered rate or by contract negotiation.Feature functionality that is outside of the function of the switch definition havebeen developed and priced outside the scope of " features that are a function ofthe Switch".•The Centrex common block can be provisioned with the proper port to accept/terminate selected ancillary services within the Centrex. These serviceswould be accessed via a dialing code as part of the Centex functionality. Examples of these services are as follows:•Tie Lines•Foreign Exchange Service (FX)•WATS/800 service•Voice and Analog Data Private lines•DS1/High Cap Services•Centrex Control•Music and Announcement On Hold•Station Message Detail Interface (SMDI)UNE P Centrex service is furnished to subscribers requesting one (1) or more station lines served by the same Central Office Equipment.A subscribers system may be comprised of the following components:•Common Equipment (Required),•Station Ports (At least 1 is required),•Network Access Registers (NARs) (optional)•Additional (Optional) Features.A subscribers Port may be comprised of the following:•Station Port (Required),•Standard Features billing USOC (Required),•Selected Standard Features,•Selected Additional (Optional) Features•Selectable Additional (Optional) System FeatureOrdering InformationThe following chart details which forms are required, conditional, or optional for ordering this product. All forms should be populated as usual except where denoted otherwise in the Critical/Valid Entry Tables per Form section.Forms/ScreensUNE-P Centrex®SI LSR Hunting EU DL DSCR RS DRS PS NP LS LSNPR O[1] R C[2]C[3]R = Required C = Conditional O = optional[1] Hunting is optional only when ACT is C, T, V, P or Q, otherwise Hunting isprohibited.[2] DL notes: REQTYP M UNE P Centrex required when ACT = N or T.[3] DSCR is Required when a listing is a caption, degree of indent, or irregularplacementBellSouth®Centrex® Subsequent Ordering FormBellSouth®Centrex®/UNE PCentrex OfficialFormElectronicBusiness Set P-PhoneForm****CustomerControlInitializationFrom*****C [4] C[5]C[6]C[7]R = Required C = Conditional O = optionalNote [4]: BellSouth® Centrex®/UNE P Centrex Subsequent Ordering form is required when the ACT is C. When certain features are involved (i.e.Trunk side terminations, ACD, Electronic Business Sets etc.) withACT=C the official Ordering form should be used.BellSouth® Centrex®/UNE P Centrex Official Form is required when theACT is N ,V or T .The BellSouth® Centrex®/UNE P Centrex Subsequent Ordering form islocated on:/forms/html/lec_form.htmlNote [5]: The BellSouth® Centrex®/UNE P Centrex Official Form is located on /forms/html/centrexunep.htmlNote [6]: Electronic business Set P-Phone form is used when the request is for an Electronic Business P-Phone Line when certain features are involved inthe conversion (i.e. Trunk side terminations, Electronic Business Sets etc).Electronic business Set P-Phone form is used when the ACT is C or V,andthe request is for an Electronic Business P-Phone Line. Please refer to theBellSouth® P-Phone chapter to obtain the Electronic Business Set KeySheets and Additional Module form.Note [7]: Customer Control Initialization Form is required when the customer has Centrex Control, and the ACT=V.Completing the LSR and EU FormsThe Required, Conditional and Optional (R/C/O) fields on the LSR and EU forms will be given for every valid REQTYP/ACT combination for this product.The following chart shows all of the valid account level activities for UNE P Centrex Service.<< MichelleThere are no notes for the ***** indicatorsshown for ACTs Y, P, and Q in the table below. >>Valid Account Level ActivitiesUNE-P Centrex®N* C D T** R V S B W L Y*** P**** Q****X X X XNote: " X " denotes valid account level activities.Request for Conversion ACT = V must be submitted to the AccountTeam/CSRG/CLEC Care.* Request for new system ACT = N must be submitted to the CRSG.*** Denial of service is done on ACT = D which will result in a completedisconnect of the system or denial of service at end user level may beaccomplished simply by disconnecting the individual line.Account level activities (ACT) apply to the entire account. The ACTs are defined below:N = New installation and/or accountC = Change an existing account (e.g., Rearrangement, Partial disconnect oraddition)D = DisconnectionT = Outside move of end user location or Inside MoveR = Record activity is for ordering administrative changesV = Full Conversion of service as specified to new Local Service Provider (LSP) S = Seasonal partial suspend or restore partial accountB = Restore full account or restore denied accountW = Full Conversion of service as isL = Seasonal suspension full accountP = Conversion of service as specified: Partial Migration - InitialQ = Conversion of service as specified: Partial Migration - Subsequent Completing the BellSouth® Centrex® / UNE P Subsequent Ordering formThe BellSouth® Centrex®/UNE P Centrex Subsequent Ordering form may or may not be required depending on the account level activity. Each account level activity has valid line level activities (LNAs). These LNAs determine how, or if, the BellSouth® Centrex®/UNe P Centrex Official Ordering form should be populated.Line level activities (LNA) apply to the specified line only. The valid LNAs are listed below:N = New Installation (e.g., new line or additional line)C = Change or Modification to an Existing LineD = DisconnectionG = Conversion or Migration to new LSP as specified (specify ALL FEATURESrequested for conversion service).X = Telephone Number ChangeV = Conversion or Migration to new LSP as specified (specify only thosechanges from existing service).W = Conversion or Migration as isP = PIC ChangeL = Seasonal SuspendB = RestoreThe following chart gives the valid LNAs for each account level activity (ACT) and the associated UNE P Centrex form usage.If ACT is: Then LNA is: The BellSouth® Centrex®/UNE P CentrexSubsequent Ordering Form Is:N N Prohibited (See Note 1)C N, C, D, X or P RequiredD Prohibited Not RequiredV N, D, X, V, W or P Prohibited (See Note 1)Note 1: The BellSouth® Centrex/UNE P Centrex Official form should be used. It is located on:/forms/html/centrexunep.htmlCompleting the DL and DSCR Forms/ScreensIf directory listings are required, please refer to REQTYP J for more information on completing the DL and DSCR forms/screens.REQTYP / ACT Combinations for REQTYP M: UNE P Centrex ServiceThe following charts show the Required, Conditional and Optional (R/C/O) fields on the LSR and EU forms for the valid REQTYP/ACT combinations.All unmentioned fields are either invalid, not applicable, prohibited or not supported. When fields are populated which are not supported by BellSouth, these not supported fields will be ignored. Populating any other fields may result in a fatal reject or a clarification of the service request.Please note the following codes:•Mandatory entries are indicated by quotation marks ("xxx").•Optional fields marked with an asterisk (*) force at least one of the conditional fields to become required when populated.•Fields used only for manual orders are followed by (m).•Fields used only for electronic orders are followed by (e).See the Data Element Dictionary Section for additional information on each of the fields listed below.CLEC Forms On-Line [UNE P Centrex Service Form/Instructions]Refer to the ICS WebPortal page (), select 'Tools, Forms & Reports' on toolbar, select 'Forms and Templates', then select "CLEC Forms Online" or just go to CLEC Forms On-Line web page located at:/forms/html/lec_form.htmlCentrex Ordering Document (Subsequent Service Ordering Activity)This form may not be used to submit a request for a new UNE P Centrex system. The official BellSouth® Centrex ®/UNE P Centrex -ordering document must be submitted for new systems.The official ordering document may be obtained from the following; go to CLEC Forms On-Line web page located at:/forms/html/lec_form.htmlThe LSR and EU forms must accompany this formCCP 1610 Attachment Listed BelowRelease 13.0 (TCIF9)SCService Center (LSR Page)DefinitionIdentifies the BellSouth® Service Center.Definition Notes:NoneValid EntriesLCSC = BellSouth® Local Carrier Service CenterorLCSL = BellSouth® LNP to Resale/UNE P MigrationsNote 1: An entry of “LCSL” is the only valid entry when the REQTYP “E”, “M”, “N”, “P” and the ACT is “V” or “P” and the request is for an LNP to Resale/UNE P MigrationNote 2: An entry of “LCSC” is prohibited when the REQTYP is “E”, “M”, “N”, “P” and the ACT is “V” or “P” and the request is for an LNP to Resale/UNE P MigrationData Characteristics4 alpha charactersExamples LCSC or LCSLConditional Usage NotesNoneBusiness Rules* * * * * * * * * * End of definition for field SC * * * * * * * * * * Version 13.0D, TCIF9 / LSOG4。
keil破解——解决下载问题

用keil调试程序时编译通过当按下build target时会显示:Build target 'Target 1'linking...BL51 BANKED LINKER/LOCATER V6.00 - SN: Eval VersionCOPYRIGHT KEIL ELEKTRONIK GmbH 1987 - 2005"asdfdsadfdsa.obj"TO "asdfasdf"********************************************************************* ********** RESTRICTED VERSION WITH 0800H BYTE CODE SIZE LIMIT; USED: 0CDEH BYTE (160%) ********************************************************************** *********Program Size: data=8.0 xdata=0 code=3328LINK/LOCATE RUN COMPLETE. 0 WARNING(S), 0 ERROR(S)*** FATAL ERROR L250: CODE SIZE LIMIT IN RESTRICTED VERSION EXCEEDED MODULE: asdfdsadfdsa.obj (-----)LIMIT: 0800H BYTESTarget not created看到这样的错误,一头雾水,网上有人讲用的是试用版的,只能编译2K,下个破解版的。
一下就是破解版的整个安装过程,挺烦的。
安装指南:1.点击c51v802.exe直接安装直到结束,安装路径最好选用默认的c:\keil与原来的老板本放到相同的目录下会自动添加一个新的目录c:\keil\uv32.第一次运行请先进入file->License Management弹出窗口下输入注册码,注册码由Keil_lic_v2.exe生成,选择V2选项,生成后复制LIC0内容到keil弹出窗口的New License ID Code中然后点击AddLIC,注意看看注册后的使用期限,如果太短可以用注册机重新生成,一般都可以找到30年左右.若添加license ID 一直提示“ ERROR R208: RENEW LICENSE ID CODE (LIC)”。
水利专业名词(中英文对照)

水利专业名词(中英)A安全储备safety reserve安全系数safety factor安全性safety岸边溢洪道river-bank spillway岸边绕渗by-pass seepage around bank slope 岸墙abutment wall岸塔式进水口bank-tower intakeB坝的上游面坡度upstream slpoe of dam坝的下游面downstream face of dam坝顶dam crest坝顶长度crest length坝顶超高freeboard of dam crest坝高dam height坝顶高程crest elevation坝顶宽度crest width坝段monolith坝基处理foundation treatment坝基排水drain in dam foundation 坝基渗漏leakage of dam foundation 坝肩dam abutment坝壳dam shell坝坡dam slope坝坡排水drain on slope坝体混凝土分区grade zone of concrete in dam 坝体排水系统drainage system in dam坝型选择selection of dam type坝址选择selection of dam site坝趾dam toe坝踵dam heel坝轴线dam axis本构模型constitutive model鼻坎bucket比尺scale比降gradient闭门力closing force边墩side pier边界层boundary layer边墙side wall边缘应力boundary stress变形观测deformation observation变中心角变半径拱坝variable angle and radius arch dam 标准贯入试验击数number of standard penetration test 冰压力ice pressure薄壁堰sharp-crested weir薄拱坝thin-arch dam不均匀沉降裂缝differential settlement crack不平整度irregularityC材料力学法method of strength of materials材料性能分项系数partial factor for property of material 侧槽溢洪道side channel spillway侧轮side roller侧收缩系数coefficient of side contraction测缝计joint meter插入式连接insert type connection差动式鼻坎differential bucket掺气aeration掺气槽aeration slot掺气减蚀cavitation control by aeration厂房顶溢流spill over power house沉降settlement沉井基础sunk shaft foundation沉沙池sediment basin沉沙建筑物sedimentary structure沉沙条渠sedimentary channel沉陷缝settlement joint沉陷观测settlement observation衬砌的边值问题boundary value problem of lining 衬砌计算lining calculation衬砌自重dead-weight of lining承载能力bearing capacity承载能力极限状态limit state of bearing capacity持住力holding force齿墙cut-off wall冲击波shock wave冲沙闸flush sluice冲刷坑scour hole重现期return period抽排措施pump drainage measure抽水蓄能电站厂房pump-storage power house 出口段outlet section初步设计阶段preliminary design stage初参数解法preliminary parameter solution 初生空化数incipient cavitation number初应力法initial stress method船闸navigation lock垂直升船机vertical ship lift纯拱法independent arch method刺墙key-wall粗粒土coarse-grained soil错缝staggered jointD大坝安全评价assessment of dam safety 大坝安全监控monitor of dam safety大坝老化dam aging大头坝massive-head dam单层衬砌monolayer lining单级船闸lift lock单线船闸single line lock挡潮闸tide sluice导流洞diversion tunnel导墙guide wall倒虹吸管inverted siphon倒悬度overhang等半径拱坝constant radius arch dam等中心角变半径拱坝constant angle and variable radius arch dam 底流消能energy dissipation by hydraulic jump底缘bottom edge地基变形foundation deformation地基变形模量deformation modulus of foundation地基处理foundation treatment地下厂房underground power house地下厂房变压器洞transformer tunnel of underground power house 地下厂房出线洞bus-bar tunnel of underground power house地下厂房交通洞access tunnel of underground power house地下厂房通风洞ventilation tunnel of underground power house 地下厂房尾水洞tailwater tunnel of underground power house地下轮廓线under outline of structure地下水groundwater地形条件topographical condition地形图比例尺scale of topographical map地应力ground stress地震earthquake地震烈度earthquake intensity地质条件geological condition垫层cushion垫座plinth吊耳lift eye调度dispatch跌坎drop-step跌流消能drop energy dissipation跌水drop迭代法iteration method叠梁stoplog丁坝spur dike定向爆破堆石坝directed blasting rockfill dam 动强度dynamic strength动水压力hydrodynamic pressure洞内孔板消能energy dissipation by orifice plate in tunnel 洞内漩流消能energy dissipation with swirling flow in tunnel 洞身段tunnel body section洞室群cavern group洞轴线tunnel axis陡坡steep slope渡槽短管型进水口intake with pressure short pipe断层fault堆石坝rockfill dam对数螺旋线拱坝log spiral arch dam多级船闸multi-stage lock多线船闸multi-line lock多心圆拱坝multi-centered arch dam多用途隧洞multi-use tunnelE二道坝secondary damF发电洞power tunnel筏道logway反弧段bucket反滤层filter防冲槽erosion control trench防洪flood preventi,flood control防洪限制水位restricted stage for flood prevention 防浪墙parapet防渗墙anti-seepage wall防渗体anti-seepage body放空底孔unwatering bottom outlet非常溢洪道emergency spillway非线性有限元non-linear finite element method非溢流重力坝nonoverflow gravity dam分岔fork分洪闸flood diversion sluice分项系数partial factor分项系数极限状态设计法limit state design method of partial factor 封拱arch closure封拱温度closure temperature浮筒式升船机ship lift with floats浮箱闸门floating camel gate浮运水闸floating sluice辅助消能工appurtenant energy dissipationG刚体极限平衡法rigid limit equilibrium method刚性支护rigid support钢筋混凝土衬砌reinforced concrete lining钢筋计reinforcement meter钢闸门steel gate高边坡high side slope高流速泄水隧洞discharge tunnel with high velocity 工程管理project management工程规划project plan工程量quantity of work工程设计engineering design工程施工engineering construction工作桥service bridge工作闸门main gate拱坝坝肩岩体稳定stability of rock mass near abutment of arch dam 拱坝布置layout of arch dam拱坝上滑稳定分析up-sliding stability analysis of arch dam拱坝体形shape of arch dam拱端arch abutment拱冠arch crown拱冠梁法crown cantilever method拱冠梁剖面profile of crown cantilever拱内圈intrados拱外圈extrados固结consolidation固结灌浆consolidation grouting管涌piping灌溉irrigation规范code,specification过坝建筑物structures for passing dam 过滤层transition layer过渡区transition zone过木机log conveyer过木建筑物log pass structures过鱼建筑物fish-pass structuresH海漫flexible涵洞culvert河道冲刷river bed scour荷载load荷载组合load combination横缝transverse joint横拉闸门horizontal rolling /sliding gate 洪水标准flood standard虹吸溢洪道siphon spillway厚高比thickness to hight ratio弧形闸门radial gate护岸工程bank-protection works护坡slope protection护坦apron戽琉消能bucke-type energy dissipation 滑坡land slip滑楔法sliding wedge method滑雪道式溢洪道skijump spillway环境评价environment assessment换土垫层cushion of replaced soil回填灌浆backfill grouting混凝土concrete混凝土衬砌concrete lining混凝土防渗墙concrete cutoff wall混凝土面板concrete face slab混凝土面板堆石坝concrete-faced rockfill dam 混凝土重力坝concrete gravity damJ基本荷载组合basic load combination基本剖面basic profile基面排水base level drainage激光准直发method of laser alignment极限平衡法limit equilibrium method极限状态limit state坚固系数soundness coefficient剪切模量shear modulus剪切应力shear stress检查inspection检修闸门bulkhead简单条分法simple slices method建筑材料construction material简化毕肖普法simplified Bishop’s method渐变段transition键槽key/key-way浆砌石重力坝cement-stone masonry gravity dam 交叉建筑物crossing structure交通桥access bridge校核洪水位water level of check floo校核流量check flood discharge接触冲刷contact washing接触流土soil flow on contact surface节制闸controlling sluice结构可靠度reliability of structure结构力学法structural mechanics method 结构系数structural coefficient截流环cutoff collar截水槽cutoff trench进口段inlet进口曲线inlet curve进水喇叭口inlet bellmouth进水闸inlet sluice浸润面saturated area浸润线saturated line经济评价economic assessment井式溢洪道shaft spillway静水压力hydrostatic pressure均质土坝homogeneous earth damK开敞式溢洪道open channel spillway开裂机理crack mechanism勘测exploration survey坎上水深water depth on sill抗冲刷性scour resistance抗冻性frost resistance抗滑稳定安全系数safety coefficient of stability against sliding 抗剪断公式shear-break strength formula抗剪强度shear strength抗裂性crack resistance抗磨abrasion-resistance抗侵蚀性erosion-resistance抗震分析analysis of earthquake resistance颗粒级配曲线grain size distribution curve可靠度指标reliability index可行性研究设计阶段design stage of feasibility study 空腹重力坝hollow gravity dam空腹拱坝hollow arch dam空化cavitation空化数cavitation number空蚀cavitation damage空隙水压力pore water pressure控制堰control weir枯水期low water period库区reservoir area宽顶堰broad crested weir 宽缝重力坝slotted gravity dam 宽高比width to height ratio 扩散段expanding section 扩散角divergent angleL拦沙坎sediment control sill 拦污栅trash rack廊道gallery浪压力wave pressure棱体排水prism drainage理论分析theory analysis力法方程canonical equation of force method 连续式鼻坎plain bucket联合消能combined energy dissipation梁式渡槽beam-type flume量水建筑物water-measure structure裂缝crack临界水力坡降critical hydraulic gradient临时缝temporary joint临时性水工建筑物temporary hydraulic structure流量discharge流速flow velocity流态flow pattern流土soil flow流网flow net流向flow direction露顶式闸门emersed gateM马蹄形断面horseshoe section脉动压力fluctuating pressure锚杆支护anchor support门叶gate flap迷宫堰labyrinth weir面流消能energy dissipation of surface regime 模型试验model test摩擦公式friction factor formula摩擦系数coefficient of friction目标函数objective functionN内部应力internal stress内摩擦角internal friction angle内水压力internal water pressure挠度观测deflection observation泥沙压力silt pressure粘性土cohesive soil碾压混凝土重力坝roller compacted concrete gravity dam 凝聚力cohesion扭曲式鼻坎distorted type bucketP排沙底孔flush bottom outlet排沙漏斗flush funnel排沙隧洞flush tunnel排水drainage排水孔drain hole排水设施drainage facilities抛物线拱坝parabolic arch dam喷混凝土支护shotcrete support喷锚支护spray concrete and deadman strut漂木道log chute平板坝flat slab buttress dam平衡重式升船机vertical ship lift with counter weight平面闸门plain gate平压管equalizing pipe坡率slope ratio破碎带crush zone铺盖blanketQ启闭机hoist启门力lifting force砌石拱坝stone masonry arch dam 潜坝submerged dam潜孔式闸门submerged gate倾斜仪clinometer曲线形沉沙池curved sedimentary basin渠首canal head渠道canal渠系建筑物canal system structure取水建筑物water intake structureR人工材料心墙坝earth-rock dam with manufactured central core 人字闸门mitre gate任意料区miscellaneous aggregate zone溶洞solution cavern柔度系数flexibility coefficient褥垫式排水horizontal blanket drainage软弱夹层weak intercalationS三角网法triangulation method 三角形单元triangular element三心圆拱坝three center arch dam 三轴试验triaxial test扇形闸门sector gate上游upstream设计洪水位design flood level设计基准期design reference period 设计阶段design stage设计阶段划分dividing of design stage 设计流量design discharge设计状况系数design state coefficient 设计准则design criteria伸缩缝contraction joint渗流比降seepage gradient渗流变形seepage deformation渗流分析seepage analysis渗流量seepage discharge渗流体积力mass force of seepage渗流系数permeability coefficient 生态环境ecological environment 生态平衡ecological balance失效概率probability of failure施工导流construction diversion施工缝construction joint施工管理construction management施工条件construction condition施工图阶段construction drawing stage 施工进度construction progress实体重力坝solid gravity dam实用剖面practical profile实用堰practical weir事故闸门emergency gate视准线法collimation method收缩段constringent section枢纽布置layout of hydraulic complex 输水建筑物water conveyance structure 竖式排水vertical drainage数值分析numerical analysis双层衬砌double-layer lining双曲拱坝double curvature arch dam 水电站地下厂房underground power house水电站建筑物hydroelectric station structure 水垫塘cushion basin水工建筑物hydraulic structure水工隧洞hydraulic tunnel水环境water environment水库吹程fetch水库浸没reservoir submersion水库渗漏reservoir leakage水库坍岸reservoir bank caving水库淹没reservoir inundation水力资源water power resource水力劈裂hydraulic fracture水利工程hydraulic engineering,water project 水利工程设计design of hydroproject水利工程枢纽分等rank of hydraulic complex水利枢纽hydraulic complex水面线water level line水能hydraulic energy水平位移horizontal displacement水体污染water pollution水土流失water and soil loss水位急降instantaneous reservoir drawdown 水压力hydraulic pressu水闸sluice水质water quality水资源water resources顺坝longitudinal dike四边形单元quadrangular element塑性破坏failure by plastic flow塑性变形plastic deformation塑性区plastic range锁坝closure dike锁定器dog deviceTT型墩T-type pier塌落拱法roof collapse arch method塔式进水口tower intake台阶式溢流坝面step-type overflow face弹塑性理论elastoplastic theory弹性基础梁beam on elastic foundation 弹性抗力elastic resistance弹性中心elastic centre弹性理论theory of elasticity特殊荷载组合special load combination 体形优化设计shape optimizing design 挑距jet trajectory distance挑流消能ski-jump energy dissipation 挑射角exit angle of jet调压室surge tank贴坡排水surface drainage on dam slope通航建筑物navigation structure通气孔air hole土工复合材料geosynthetic土工膜geomembrane土工织物geotexile土石坝earth-rock dam土压力earth pressure土质材料斜墙坝earth-rock dam with inclined soil core 土质心墙坝earth-rock dam with central soil core 驼峰堰hump weir椭圆曲线elliptical curveWWES型剖面堰WES curve profile weir外水压力external water pressure弯矩平衡moment equilibrium围岩surrounding rock围岩强度strength of surrounding rock 围岩稳定分析围岩压力surrounding rock pressu帷幕灌浆curtain grouting维修maintenance尾水渠tailwater canal温度缝temperature joint温度计thermometer温度应变temperature strain温度应力temperature stress温降temperature drop温升temperature rise污水处理sewage treatment无坝取水undamed intake无粘性土cohesionless soil无压泄水孔free-flow outletX下游downstream现场检查field inspection橡胶坝rubber dam消力池stilling basin消能防冲设计design of energy dissipation and erosion control消能工energy dissipator校核洪水位water level of check flood 校核流量check flood discharge斜缝inclined joint斜墙inclined core泄洪洞flood discharge tunnel泄洪雾化flood discharge atomization 泄水重力坝overflow gravity dam胸墙breast wall悬臂梁cantiever beam汛期flood perioY压力计pressure meter压缩曲线compressive curve淹没系数coefficient of submergence 扬压力uplift养护cure液化liquifaction溢洪道spillway溢流面overflow face溢流前缘length of overflow crest溢流堰顶overflow crest溢流重力坝overflow gravity dam翼墙wing wall翼墙式连接wing wall type connection 引航道approach channel引水渠diversion canal引张线法tense wire method应力分析stress analysis应力集中stress concentration应力应变观测stress-strain observation应力重分布stress redistribution永久缝permanent joint优化设计optimizing design有坝取水barrage intake有效库容effective storage预压加固soil improvement by preloading 预应力衬砌prestressed lining原型prototype约束条件constraint condition允许水力坡降allowable hydraulic gradient Z增量法increment method闸底板floor of slui闸墩pier闸孔sluice opening闸孔跨距span of sluice opening闸门槽gate slot闸室chamber of sluice闸首lock head闸址sluice site正槽溢洪道chute spillw正常使用极限状态limit state of normal operation 正应力normal stress正常溢洪道main spillw支墩坝buttress dam止水watertight seal止水装置sealing device趾板toe slab趾墩toe pier滞回圈hysteresis loop主应力principal stress纵缝longitudinal joint阻尼比damped ratio作用action作用水头working pressure head最优含水率optimum moisture content。
热点02 网络环境与未成年人保护(原卷版)---备战2021年高考英语考前时事热点话题阅读+题型专练

备战2021年高考英语考前时事热点话题阅读热点02 网络环境与未成年人保护一、阅读理解1Facebook and other social media companies should make children aware that their online activity is monitored by their parent or carer, under a code to improve child Internet safety in the UK.Turning off the “like” function, and limiting data collection and geolocation tools on popular platforms such as Instagram and Facebook, are among a 16-point list of recommendations for age-appropriate design released by the Information Commisioner’s Office (ICO).It said some techniques, which platforms employ to encourage users to use them, including Facebook “likes”, should not be used to try to keep under-18s online for longer. Other recommendations under the ICO’s code of practice for Internet companies, which platforms would be responsible for carrying out, include: *Limiting how children’s personal data is collected, used and shared by social media companies.*Making “high privacy” the default (默认) setting for children using social media platforms unless there is a convincing reason not to.*Requiring social media companies to show that all staff involved in the design and development of services likely to be used by children obey the code of practice.*Introducing age checks on platforms or treating all users as if they were children.Companies that do not stick to the code could face fines of up to 4% of their global turnover, around $1.6 bn for Facebook. The consultation ended at the end of May, and the final version of the code of practice, regarded as a new international standard is expected to come into effect by 2020.Elizabeth Denham, the information commissioner, said, “This is the connected generation. The Internet and all its wonders have been a part of their everyday lives. We shouldn’t have to prevent our c hildren from being able to use it, but we must demand that they should be protected when they do. This code does that.”The ICO sought views from parents and children while developing the code of practice, as well as those of designers, app developers and academics.The NSPCC children’s charity said social networks had “continually failed to put child safety first in their design”, resulting in “bad consequences”. “That’s why it is vital this code requires children to be given the highestprivacy settings b y default and forces companies to act in the best interests of children,” the NSPCC’s associate head of child safety online Andy Burrows said.Lady Beeban Kidron, the chair of the 5Rights Foundation and who led the debate about the creation of the recommen dations, said, “For too long we have failed to recognize children’s rights and needs online. I firmly believe in the power of technology to transform lives, be a force for good and rise to the challenge of promoting the rights and safety of our children. But in order to fulfill that role, it must consider the best interests of children, not simply its own commercial interests.”1. Why did the ICO create the code?A. To protect social media companies.B. To ensure children’s safety on the Internet.C. To prevent under-18s from staying online.D. To reduce the functions of popular platforms.2. What will happen to social media companies if they don’t follow the code?A. They’ll be fined.B. They’ll receive warnings.C. They’ll be required to apologize.D. They’ll have to stop their platforms.3. What can we learn from Denham’s words?A. She has a low opinion of popular platforms.B. She considers the code to be quite necessary.C. She fails to recognize children’s needs online.D. She expects children to avoid using the Internet.4. What does the underlined word “fulfill” mean in the last paragraph?A. Praise.B. Define.C. Meet.D. Find.2TikTok has pushed a new safety update in November to its app that allows parents to take more control of their teenager's accounts, as social media companies come under increasing pressure to make their platforms safer for children.The company said Tuesday that its “Family Pairing” feature now enables parents to tum off comments on theirchildren's videos entirely or to limit them to friends only. Parents whose accounts are linked to their kids will also be able to set their accounts to private, turn off the search function for content, users or sounds, and limit who can see which videos their children have liked.Launched (发布) in March, the Family Pairing tool lets parents see how long their children are spending on TikTok each day and limit the content they can see.TikTok allows children to register and create an account if they're over the age of 13. All they need to do is provide their date of birth. However, because TikTok doesn't require registers to prove their identities, some children under 13 have registered by lying about their age,according to U. K. regulator Ofcom (英国通讯管理局).Alexandra Evans, head of child safety public policy for TikTok in Europe, told CNBC that Family Pairing has “put itself in parents' shoes” since it was launched.“If we're thinking about it as a toolbox, we wanted to offer more tools,” she said on a video call ahead of the announcement.5. What pushed TikTok to launch the new update?A. The pressure from social media.B. The concern about kids' online safety.C. The force from government.D. The increasing need of users.6. What is the second paragraph mainly about?A. The safety tips from TikTok.B. New apps explored by TikTok.C. New functions of Family Pairing.D. The limits on Family Pairing.7. What is Ofcom mainly concerned about?A. The difficulty in opening an account.B. The low age limit for users.C. TikTok's failure to check identities.D. The demand for users' birth dates.8. What's Evans attitude toward the new Family Pairing?A. Uninterested.B. Objective.C. Disappointed.D. Supportive.9. What might be the best title of the passage?A. TikTok's Safety Update.B. New Guidelines for Safety.C. Family Pairing under Debate.D. Controlling Your Kids Online.3Bicycles, roller skates and skateboards are dangerous. I still have scars (伤疤) on my knees from mychildhood run-ins with various wheeled devices. Admittedly, I was a foolish kid, but I’m glad I didn’t spend my childhood trapped indoors to protect me from any injury.“That which does not kill us makes us stronger.” But parents can’t handle it when teenagers put this theory into practice. And now technology has become the new field for the age-old battle between adults and their freedom-seeking kids.Locked indoors, unable to get on their bicycles and hang out with their friends, teens have turned to social media and their mobile phones to gossip and socialize with their friends. What they do online often mirrors what they might otherwise do if their mobility weren’t so heavily restricted (限制) in the age of helicopter parenting. Social media and smartphones have become so popular in recent years because teens need a place to call their own. They want the freedom to explore their identity and the world around them. Instead of climbing out of windows, they jump online.As teens have moved online, parents have projected their fears onto the Internet, imagining all the potential dangers that youth might face.Rather than helping teens develop strategies (策略) to deal with public life and the potential risks of interacting with others, fearful parents have focused on tracking, monitoring and blocking. These approaches don’t help teens develop the skills they need to manage complex social situations. “Protecting” kids may feel like the right thing to do, but it denies teens the chances of learning as they come of age in a technology-soaked world.The key to helping youth in the modern digital li fe isn’t more restrictions. It’s freedom — plus communication. Urban theorist Jane Jacobs used to argue that the safest neighborhoods were those where communities collectively took interest in and paid attention to what happened on the streets. Safety didn’t come from surveil lance (监视) cameras or keeping everyone indoors but from a collective willingness to watch out for one another and be present as people struggled. The same is true online.What makes the digital street safe is when teens and adults collectively agree to open their eyes and pay attention, communicate and work together to deal with difficult situations. Teens need the freedom to wander the digital street, but they also need to know that caring adults are behind them and supporting them wherever they go. The fi rst step is to turn off the tracking software. Then ask your kids what they’re doing when they’re online — and why it’s so important to them.10. When he was a child, the writer ______.A. became disabledB. spent much time outdoorC. always stayed at homeD. was ignored by his parents11. Teens go online mainly because ______.A. online games mirror real lifeB. they want to fight against their parentsC. online experiences make them strongD. they need a space of their own12. By menti oning “helicopter parenting” (Paragraph 3), the writer means parents ______.A. remove any hidden dangers their kids may faceB. use helicopters to track their kidsC. prevent their kids from going to schoolD. protect their kids too much13. According to the passage, helicopter parents may make kids ______.A. lose the chances of learningB. handle complex social situations wellC. adapt to the digital world quicklyD. develop strategies to deal with public life14. The main idea of the passage is that ______.A. kids should be given freedom to deal with online risksB. safe neighborhoods come from joint efforts of allC. the digital street is a threat to kids’ safetyD. kids should be warned against potential dangers in society4Many parents set rules for their children’s on line activity, such as limiting (限制) the amount of time they can spend online. But some children in the US and UK are saying that they’d like to make rules for parents, too. Their main complaint? That their parents share too many photos of them online.In a 2016 study, it was found that parents in the US share an average of 116 photos of their kids after they are born. Most were taken before the child turned 8 years old. Many of the photos showed kids in embarrassingsituations, like having food all over their faces, Quartz reported.Parents do like to share their child’s progress as he or she grows up. But their kids don’t like it as much. In a survey of UK children between the ages of 12 and 16, 70 percent said they felt their parents d idn’t respect their online privacy (隐私), according to Digital Parenting magazine.In addition, many kids said that other students at school sometimes picks on (捉弄) them after their parents post photos online, CBS News noted. In one case, a girl was bullied (欺负) by boys at school after they found her moms’ blogs, which had many family photos.“Each time a photo or video is uploaded, it creates a digital footprint of a child, which can follow them into adult life, “a spokeswoman for a leading children’s charity in the UK said. “It’s always important to ask children for their permission (允许) before posting photos or videos of them.”What is sharenting?There’s a new word English to describe it when parents post pictures of their online—“sharenting”, or a combin ation of the world “share” and “parenting”.15. According to the first paragraph, what do kids in the US and UK complain about?A. Their parents setting rules for their online activity.B. Their parents limiting the amount of time they spend online.C. Their parents posting too many photos of them online.D. Their parents setting high expectations for their schoolwork.16. About 70 percent of UK teenagers think their parents _____.A. care too much about their progress in schoolB. forget to set good examples for themC. don’t care enough about their online safetyD. don’t respect their online privacy17. What do we know from the story?A. Parents should ask kids for permission before sharing their photos.B. UK kids don’t mind that their photos are shared b y their parents.C. Sharing photos online helps kids live a better adult life.D. Kids don’t get bullied at school when their photos are shared online.18. You might see this article from the column in the newspaper.A. Nature TodayB. All about SpaceC. Philosophy for LifeD. Society and Culture5A few years ago, my sister-in-law started to feel concerned about her teenage daughter. What was she doing after school? Where was she spending her time? My niece was an excellent student, and took part in all kinds of after-cla ss activities. Even so, her mom decided to put a tracking app on the kid’s phone. At first, this made my sister-in-law “feel better”. Then the good situation suddenly ended. She recalled, “I found out that she was someplace that she sai d she wasn’t. I went out in the middle of the night and found her walking without shoes in the middle of the street with some friends.” Things went quickly downhill for the mother and the daughter after that.With 73% of teens having their own smartphones now, according to a 2015 Pew study, more and more of their parents are facing the question: To spy or not?Ana Homayoun, founder of Green Ivy Educational Consulting, has advised many parents and their kids about this. “I’ve found teens are more receptive t o tracking apps when it is included as part of a family use agreement to improve safety than when it is placed as a secret tool to watch them,” she said.Mark Bell, a father of a teenage girl, said, “We don’t have tracking apps, but we have set some ground rules that my daugh ter must follow in exchange for us providing a smartphone,” he said. For example, his daughter must “friend” him on social media accounts so that he can review posts, and must share all passwords.When you’re trying to build trust, you need to create an environment that encourages it. So, to win their trust, you always need to be straight with your children. “Parents must let children know how and when they’ll be watching them,” said Doctor Pauleh Weigle. If they’re not open about it, he warns, it can “grea tly damage the parent and child relationship”.19. Why did the author’s sister-in-law use the app?A. She was interested in new apps.B. She was worried about her daughter.C. She wanted to know about after-class activities.D. She wanted to teach her daughter about the app.20. What can we learn about today’s children from Homayoun?A. They doubt family use agreements.B. They are worried about online safety.C. They welcome the use of tracking apps.D. They dislike being spied on secretly with tracking apps.21. According to Paragraph 5, Bell’s daughter.A. kept him out of her online groupsB. developed some bad online habitsC. allowed him to know her online behaviorD. wanted to put a tracking app on her phone22. What should be done before using a tracking app according to Weigle?A. Tell the kid about it.B. Check the kid’s phone.C. Teach the kid how to use it.D. Advise the kid to use his phone less.6A 17-year-old Bangladeshi boy has won this year's International Children's Peace Prize for his work to fight cyberbullying(网络欺凌)in his country.The prize winner, Sadat Rahman, promised to keep fighting online bullying until it no longer exists. “The fight against cyberbullying is like a war, and in this war I am a soldier,"Sadat Rahman said during a ceremony on November 13 in The Hague, the Netherlands.He added,"If everybody keeps supporting me, then together we will win this battle against cyberbullying."Rahman developed a mobile phone application that provides education about online bullying and a way to report cases of it. He said he began his work on the project after hearing the story of a 15-year-old girl who took her own life as a result of cyberbullying."I will not stop until we receive no more cases through the app,"Rahman said at the ceremony.The award comes with a fund of over $118,000, which is offered by the KidsRights Foundation. The group chooses projects to support causes that are closely linked to the winner's work. Past well-known winners of the prize include Pakistani human rights activist Malala Yousafzai.Swedish climate activist Greta Thunberg won the prize too. And students who organized the March for Our Lives event in 2018 after a deadly mass shooting at their school in the American state of Florida also won.Yousafzai won the International Children's Peace Prize in 2013. A year later, she won the Nobel Peace Prizefor campaigning for girls to have a universal right to education. She praised Rahman's work during the ceremony. She spoke through video conferencing. "All children have the right to be protected from violence no matter if it is physical or mental, ofline or online," she said. "Cyberbullying goes against that right."23. What inspired Rahman to fight cyberbullying?A. The support of the public.B. The fund from a foundation.C. A case reported through an online project.D. A child's death caused by online bullying.24. Rahman was highly thought of by Malala Yousafzai forA. his determination to fight for children's safetyB. his effort to follow the steps of the past winnersC. his contribution to protecting children from online bullyingD. his devotion to developing an application for bullying education25. Which of the following is the best title for the text?A. Online Violence Against Children Needs More AttentionB. Different Means to Campaigning Against Online ViolenceC. Bangladeshi Boy Wins International Children's Peace PrizeD. Famous Winners Achieve International Fame for Their Fighting7Sometimes, when looking at the things that have been lying around for a long time in our lives, we probably realize that those items may be useful to others. With the development of the internet, online communities have figured out a way to generate profit from the sharing of those underused assets. Using websites and social media platforms that facilitate the buying and selling of second-hand goods, it is now easier than ever for peer-to-peer sharing activities to take place. And this is what we call sharing economy.One of the things consumers appreciate when using or working in the sharing economy is the flexibility. It offers services to people when and where they want them. For those who don’t care for traditional office work, sharing economies do not require professional working environments, so there is no need to put yourself in an atmosphere that unfits for your personality. It allows people to choose flexible atmosphere to work remotely instead of in one physical office space.A sharing economy helps consumers to earn money by renting out underused goods or resources. For example, you can rent out a home using Airbnb, expensive tools from one’s garage, cars, or even sharing the groceries before going on a holiday. All of these provide a way for items to be resold and repurposed instead of just thrown away. Therefore, it helps to reduce waste and make or save money for the provider and users.But the sharing economy is not without criticisms. The sharing economy is developing faster than existing regulations or ongoing supervision. One downside is that in many cases there is a lack of regulation to check the products and services exchanged during these deals. Unlike formal companies, unregulated individuals do not follow certain regulations and this can lead to poorer and inconsistent quality of goods and services and a higher risk of fraud. For example, hotels are inspected to assure quality, whereas some apartments for short-term rental online are not. The digitally-driven peer-to-peer nature of the sharing economy services sometimes doesn’t match well with certain regulations, which on the other hand, helps keep the provided services more affordable.Another problem is related to safety concerns. Most sharing economy platforms are based on trust, as well as ratings by guests and hosts. But sometimes it happens that one uses a car, or rents an apartment and it is totally different than one imagines. After all, we have heard some unpleasant tales of guests and hosts.The sharing economy definitely has its lovers and haters. Many are not ready to switch to that model, where others are already using more than four platforms in their daily lives.26. What makes peer-to-peer sharing activities easier?A. The convenience of the network.B. The development of community.C. People’s keeping underused things.D. People’s demand of second-hand goods.27. The example in paragraph 4 is used to show .A. sharing economy services are more affordableB. short-term rental apartments are cheaper than hotelsC. the current rules can’t regulate the quality of online busine ssD. apartments rental online can’t ensure the safety of the guests28. What is the author’s attitude towards sharing economy?A. Supportive.B. Neutral.C. Disapproving.D. Doubtful.29. Which of the following shows the development of ideas in the passage?I: Introduction P: Point Sp: Sub-point (次要点) C: ConclusionA. B.C. D.8The internet has led to a huge increase in credit-card(信用卡)____Your card information could even be for sale in an illegal Website(非法网站). Websites offering cheap goods and services should be regarded with care Online shoppers who enter their credit-card information may never receive the goods they thought they bought.The thieves then go shopping with your card number—or sell the information over the Internet. Computer hackers(黑客)have broken down security(安全) system, raising questions about the safety of card holder information.Several months ago, 25,000 customers of a CD universe, an online music retailer(批发商), were not lucky. Their names, addresses and credit-card numbers were posted on a Website after the retailer refused to pay US $ 157,828 to get back the information.Credit-card firms are now fighting against online fraud. Master-card is working on plans for Web only credit-card, with a lower credit limit. The card could be used only for shopping online. However , there are a few simple steps you can take to keep from being cheated.Ask about your credit-card firm’s online rule s: under British law, cardholders are responsible for the first US $ 78 of any fraudulent spending. And shop only at secure sites: send your credit-card information only if the Website offers advanced secure system.If the security is in place, a letter will appear in the bottom right-hand corner of your screen. The Website address may also start http://--the extra “s” stands for secure. If in doubt, give your credit-card information over the telephone.Keep your password safe: most online sites require a user name and password before placing an order. Treat your password with care.30. The underli ned word “fraud” in the first paragraph probably means ______.A. cheatingB. saleC. paymentD. use31. According to this passage most people worry about shopping on the Internet because ______.A. a great number of stolen credit-cards are sold on the Internet every dayB. fraud on the Internet happens very oftenC. many Websites break down every dayD. there are too many illegal Websites on the Internet32. Thieves usually get the information of the credit-card ______.A. because many customers lost their cardsB. by paying money for people working in the information companiesC. because of the carelessness of the customersD. by stealing the information from Websites33. If the passwords of your credit-cards are not probably kept, _____.A. the bank and the shop will suffer great lossesB. you will not be able to get back your informationC. you might suffer great lossesD. the bank will answer for your loss34. Wh at’s the best title of the passage?A. How to Beat Online Credit-card ThievesB. How to Shop on the InternetC. Never Use Credit-card Without an Advanced ComputerD. Why Thieves Steal Credit-card Information9Dansh Boyd, who holds positions at Microsoft Research, New York University, and Harvard's Berkman Center for Internet and Society, has a pointed message for parents: Most everything we think we know about the way our kids are using the Internet is wrong. Boyd's new book, it's Complicated: The Social Lives of Networked Teens, makes the case that the Internet isn't nearly as scary or damaging to young people as many moms and dads believe.As the mother of a 16-yaer-old, I found most of it fascinating. Here are two of my biggest takeaways: Technology is not turning our teens into social misfits.Although the image persists that young people would rather test than talk, and prefer connecting of Facebook than hanging out in person, Boyd says this isn't true. "Most of the teens that I met ... were desperate for the opportunity to leave their homes to gather with friends," she writes.The trouble is that in many communities, young people have less freedom than they once did because they are so over scheduled and because parents are worried about their safety. "The era of being able to run around after school as long as you are home before dark is long over." Boyd notes.To make up for this lost freedom, teens have turned to their computers. "The success of social media must be understood partly in relation to this shrinking social landscape." Boyd explains. Facebook, Twitter. Instagram, Snapchat, and other sites "are not only new public spaces: they are in many cases the only 'public' spaces in which teens can easily communicate with large groups of their peers."Adolescents aren't as Internet savvy as we like to think.Although teens have been called "digital natives" for having grown up practically glued to their computers and smart-phones, they still remain simple in many ways about what they find online. After all, they're just kids."Many of today's teens are indeed deeply engaged with social media ... but this does not mean that they have the knowledge or skills to make the most of their online experiences," Boyd writes. "The so-called 'digital natives,' far from being useful, is often a distraction to understanding the challenges that youth face in the networked world."One area in which young people need help is in learning to distinguish between valid and misleading sources of information. "Teens may make their own media or share content online," Boyd observes, "but this does not mean that they inherently have the knowledge or perspective to critically examine what they consume."Yet many teachers, librarians, and, yes, parents do. "Even those who are afraid of technology," Boyd says, "can offer valuable critical perspective."As a mom or dad, the most important thing for your kid to plug into is your hard-earned wisdom.35. Danah Boyd's new book mainly talks about ________.A. the correct and wise use of the Internet for young peopleB. teens' real social lives online and advice for parentsC. measures parents can take to deal with the damaging InternetD. fascinating takeaways for a mother of a 16-year-old。
curl返回常见错误码.

curl返回常见错误码CURLE_UNSUPPORTED_PROTOCOL(1)你的URL传递给libcurl的使用协议,这libcurl的不支持。
支持可能是你没有使用一个编译时的选项,它可以是一个拼写错的协议字符串,或者只是一个协议的libcurl没有代码。
CURLE_FAILED_INIT(2)非常早期的初始化代码失败。
这可能是内部错误或问题,资源问题,一些基本的东西可能无法完成初始化时间。
CURLE_URL_MALFORMAT(3)该网址的格式不正确。
CURLE_NOT_BUILT_IN(4)libcurl的内置在一个编译时决定所要求的功能,协议或购股权没有被发现。
这意味着,一个功能或选项是不启用或明确禁用的libcurl建时,为了得到它的功能,你必须得到一个重建的libcurl的。
CURLE_COULDNT_RESOLVE_PROXY(5)无法解析代理服务器。
代理主机无法得到解决。
CURLE_COULDNT_RESOLVE_HOST(6)无法解析主机。
给定的远程主机没有得到解决。
CURLE_COULDNT_CONNECT(7)connect()的主机或代理失败。
CURLE_FTP_WEIRD_SERVER_REPLY(8)连接到一个FTP服务器后,libcurl的预期得到一定的回复返回。
这个错误代码表示,它有一个奇怪的或坏的答复。
指定的远程服务器可能不是一个确定的FTP服务器。
CURLE_REMOTE_ACCESS_DENIED(9)我们被拒绝访问的资源的URL。
对于FTP,发生这种情况而力图改变的远程目录。
CURLE_FTP_ACCEPT_FAILED(10)在等待服务器的连接时,一个主动FTP会话使用,被送到控制连接或类似的错误代码。
CURLE_FTP_WEIRD_PASS_REPLY(11)发送到服务器的FTP密码后,libcurl的预计正确的答复。
此错误代码指示返回了意外的代码。
Linux内存错误诊断

Linux内存错误诊断先了解⼀些概念DRAM(Dynamic Random Access Memory),即动态,最为常见的。
ECC是“Error Checking and Correcting”的简写,中⽂名称是“错误检查和纠正”。
ECC内存,即应⽤了能够实现错误检查和纠正技术(ECC)的内存条。
EDAC,即Error Detection And Correction(错误检测与纠正)。
内存有两种错误类型分别是CE和UE,CE 是 Correctable Error 的简称, UE是Uncorrectable Error的简称,CE即可恢复的错误,暂不影响系统的正常运⾏。
可以在找时机停机换掉。
UE为不可恢复的内存错误,通常会导致宕机。
系统messages⽇志[root@my-host mg4a]# grep kernel /var/log/messagesJan 14 19:01:11 my-host kernel: mce: [Hardware Error]: Machine check events loggedJan 14 19:01:12 my-host kernel: EDAC MC0: 1 CE memory read error on CPU_SrcID#0_Ha#1_Chan#1_DIMM#0 (channel:5 slot:0 page:0x554c02 offset:0x3c0 grain:32 syndrome:0x0 - area:DRAM err_code:0001:0091 socke [root@my-host mg4a]# grep "[0-9]" /sys/devices/system/edac/mc/mc*/csrow*/ch*_ce_count/sys/devices/system/edac/mc/mc0/csrow0/ch1_ce_count:0/sys/devices/system/edac/mc/mc0/csrow0/ch5_ce_count:1/sys/devices/system/edac/mc/mc1/csrow0/ch1_ce_count:0/sys/devices/system/edac/mc/mc1/csrow0/ch5_ce_count:0/sys/devices/system/edac/mc/mc2/csrow0/ch1_ce_count:0/sys/devices/system/edac/mc/mc2/csrow0/ch5_ce_count:0/sys/devices/system/edac/mc/mc3/csrow0/ch1_ce_count:0/sys/devices/system/edac/mc/mc3/csrow0/ch5_ce_count:0[root@my-host mg4a]# dmidecode -t 1# dmidecode 3.0Getting SMBIOS data from sysfs.SMBIOS 2.7 present.Handle 0x0044, DMI type 1, 27 bytesSystem InformationManufacturer: LENOVOProduct Name: Lenovo System x3750 M4 -[8753IH5]-Version: 03Serial Number: 06FF367UUID: C4EF8080-7926-11E5-8B14-6C0B849B418EWake-up Type: OtherSKU Number: XxXxXxXFamily: System X这是另外⼀台设备messges⽇志Jun 27 13:53:25 irora30 kernel: [Hardware Error]: MC4 Error (node 2): DRAM ECC error detected on the NB.Jun 27 13:53:25 irora30 kernel: EDAC amd64 MC2: CE ERROR_ADDRESS= 0x8de3b1960Jun 27 13:53:25 irora30 kernel: EDAC MC2: CE page 0x8de3b1, offset 0x960, grain 0, syndrome 0xab40, row 5, channel 0, label "": amd64_edacJun 27 13:53:25 irora30 kernel: [Hardware Error]: Error Status: Corrected error, no action required.Jun 27 13:53:25 irora30 kernel: [Hardware Error]: CPU:1 (15:2:0) MC4_STATUS[-|CE|MiscV|-|AddrV|-|-|CECC]: 0x8c204000ab080a13Jun 27 13:53:25 irora30 kernel: [Hardware Error]: MC4_ADDR: 0x00000008de3b1960Jun 27 13:53:25 irora30 kernel: [Hardware Error]: cache level: L3/GEN, mem/io: MEM, mem-tx: RD, part-proc: RES (no timeout)Jun 27 14:19:27 irora30 auditd[5571]: Audit daemon rotating log filesJun 27 19:09:23 irora30 auditd[5571]: Audit daemon rotating log filesJun 27 23:59:21 irora30 auditd[5571]: Audit daemon rotating log filesJun 28 02:15:55 irora30 kernel: [Hardware Error]: MC4 Error (node 2): DRAM ECC error detected on the NB.Jun 28 02:15:55 irora30 kernel: EDAC amd64 MC2: CE ERROR_ADDRESS= 0x8d9ea5960Jun 28 02:15:55 irora30 kernel: EDAC MC2: CE page 0x8d9ea5, offset 0x960, grain 0, syndrome 0xab40, row 5, channel 0, label "": amd64_edacJun 28 02:15:55 irora30 kernel: [Hardware Error]: Error Status: Corrected error, no action required.Jun 28 02:15:55 irora30 kernel: [Hardware Error]: CPU:1 (15:2:0) MC4_STATUS[-|CE|MiscV|-|AddrV|-|-|CECC]: 0x8c204000ab080813Jun 28 02:15:55 irora30 kernel: [Hardware Error]: MC4_ADDR: 0x00000008d9ea5960Jun 28 02:15:55 irora30 kernel: [Hardware Error]: cache level: L3/GEN, mem/io: MEM, mem-tx: RD, part-proc: SRC (no timeout)Jun 28 03:08:25 irora30 kernel: [Hardware Error]: MC4 Error (node 2): DRAM ECC error detected on the NB.Jun 28 03:08:25 irora30 kernel: EDAC amd64 MC2: CE ERROR_ADDRESS= 0x8ded39960Jun 28 03:08:25 irora30 kernel: EDAC MC2: CE page 0x8ded39, offset 0x960, grain 0, syndrome 0xab40, row 5, channel 0, label "": amd64_edacJun 28 03:08:25 irora30 kernel: [Hardware Error]: Error Status: Corrected error, no action required.Jun 28 03:08:25 irora30 kernel: [Hardware Error]: CPU:1 (15:2:0) MC4_STATUS[-|CE|MiscV|-|AddrV|-|-|CECC]: 0x8c204000ab080813Jun 28 03:08:25 irora30 kernel: [Hardware Error]: MC4_ADDR: 0x00000008ded39960Jun 28 03:08:25 irora30 kernel: [Hardware Error]: cache level: L3/GEN, mem/io: MEM, mem-tx: RD, part-proc: SRC (no timeout)Jun 28 03:45:13 irora30 rhsmd: In order for Subscription Manager to provide your system with updates, your system must be registered with the Customer Portal. Please enter your Red Hat login to ensure your system is up-t Jun 28 04:44:25 irora30 auditd[5571]: Audit daemon rotating log filesJun 28 09:34:22 irora30 auditd[5571]: Audit daemon rotating log filesJun 28 10:02:30 irora30 ansible-command: Invoked with warn=True executable=None _uses_shell=True _raw_params=df -hl /var|awk 'NR>1 && int($5) > 80' removes=None creates=None chdir=NoneJun 28 14:23:49 irora30 auditd[5571]: Audit daemon rotating log filesJun 28 19:09:25 irora30 auditd[5571]: Audit daemon rotating log files故障确认及定位故障内存槽位[root@irora30 ~]# grep "[0-9]" /sys/devices/system/edac/mc/mc*/csrow*/ch*_ce_count/sys/devices/system/edac/mc/mc0/csrow4/ch0_ce_count:0/sys/devices/system/edac/mc/mc0/csrow5/ch0_ce_count:0/sys/devices/system/edac/mc/mc1/csrow4/ch0_ce_count:0/sys/devices/system/edac/mc/mc1/csrow5/ch0_ce_count:0/sys/devices/system/edac/mc/mc2/csrow4/ch0_ce_count:0/sys/devices/system/edac/mc/mc2/csrow5/ch0_ce_count:294/sys/devices/system/edac/mc/mc3/csrow4/ch0_ce_count:0/sys/devices/system/edac/mc/mc3/csrow5/ch0_ce_count:0/sys/devices/system/edac/mc/mc4/csrow4/ch0_ce_count:0/sys/devices/system/edac/mc/mc4/csrow5/ch0_ce_count:0/sys/devices/system/edac/mc/mc5/csrow4/ch0_ce_count:0/sys/devices/system/edac/mc/mc5/csrow5/ch0_ce_count:0/sys/devices/system/edac/mc/mc6/csrow4/ch0_ce_count:0/sys/devices/system/edac/mc/mc6/csrow5/ch0_ce_count:0/sys/devices/system/edac/mc/mc7/csrow4/ch0_ce_count:0/sys/devices/system/edac/mc/mc7/csrow5/ch0_ce_count:0[root@irora30 ~]#count:不为0的⾏即代表存在内存错误。
ISO 12944是规定钢结构的涂层防腐系统的标准

ISO 12944是规定钢结构的涂层防腐系统的标准(Corrosion protection of steel structures by protective paint systems),为工程师、工程顾问、工程承包方以及涂层的供应商提供了全面的有关涂层防腐的指导。
ISO 12944 共分为8 个部分定义了涂装系统的“防腐年限(Durability)”定义了环境的“腐蚀等级(Corrosion Categories)”为选择涂装系统提供了指导表示为 3 个年限低低(Low) 2 至 5 年中(Medium)5 至15 年高(High) 大于15 年C4 H表示腐蚀环境为高盐度的工业地区和中等盐度的海岸地区,比如化工厂,游泳池,海船和船厂等在这种环境下,仅靠电镀或静电喷涂是难以达到15年以上的防腐寿命的,根据ISO12944第 5 部分–防护涂装系统可以进行涂层系统的设计厚度/ 预期防腐年限类别 DFT 范围(µm) (含富锌底漆)最小dft (µm) 预期防腐年限C2 80 低(2-5 年)80 –120 中(5-15 年)160 –200 80 高(>15 年)C3120 –160 低(2-5 年)160 –200 80 中(5-15 年)200 –240 160 高(>15 年)C4 160 –200 160 低(2-5 年)200 –240 200 中(5-15 年)240 –320 240 高(>15 年)C5IC5M 200 低(2-5 年)160 –240 160 中(5-15 年)280 –400 280 高(>15 年)一般涂层系统由底漆,中层漆和面漆三道涂层组成,在此腐蚀环境下,通常选用的油漆有:富锌底漆,环氧中层漆盒聚氨酯面漆。
1. ScopeThis International Standard specifies requirements for thickness corrosion resistance and mechanical and physical properties of non-electrolytically applied zinc flake coatings steel fasteners with metric threads.If applies to both coating with of without chromate.If fasteners with metric thread with pitch below 0.8mm ( 〈 MS )or fasteners with small internal drives or cavities are to be coated. special agreement between supplier and purchaser is required.Coatings according to this international Standard may also be applied to steel screws which from their own mating threads sush as wood screw, self tapping screws,self drilling screw,thread cutting screws and thread rolling screws as well as to non-threaded steel parts sush as washers and pins.They may be similarly applied to steel fasteners with other types of thread.Coatings according to this international Standard can be supplied with integral lubricant and/ or with an externally added lubricant.2. Normative referencesThe following normative documents contain provisions which,through reference in thistest,constitute provisions of this international Standard. At the time of publication,the editions indicated were valid. All normative documents are subject to revision. and parties to agreements based on this international Standard are encouraged to investigate the possibility of applying the most recent editions of the normative documents indicated below. For undated references, the latest edition of the normative document referred to applies. Members of ISO and IEC maintain registers of currently valid International Standard.ISO 898-1 :1989Mechanical properties of fastener . Bolts, screws and studsISO 1502 :1978ISO general purpose metric screw thread-GaugingISO 1463 :1982Metallic and oxide coatings-Measurement of coating thickness-Microscopical methodISO 6988 : 1085Metallic and other non-organic coatings-Sulfur dioxide test with general condensation of moisture ISO 8991 : 1986Designation system for fastenersISO 9227 : 1990Corrosion tests in artificial atmospheres-salt spray testISO/DIS 15330 : 1997Fasteners-Preloading test for the detection of hydrogen embitterment-Parallel bearing surface method3. DefinitionNon -electrolytically applied zinc flake coating( with or without integral lubricant)A coating which is produced byapplying on the surface of a fastener a zinc flake dispersion,possibly with addition of aluminum flakes .in a suitable medium which under influence of heat(curing)generates a bonding of the flakes and between flakes and the substrate thus forming a sufficiently electrically conduction inorganic surface coating to ensure cathode protection. The coating may or may not contain chromate.4. GeneralIt is a characteristic df this type of coating that no hydrogen which could be absorbed by the parts is generated during the coating process. Therefore, by using pretreatment cleaning methods which do not generate nascent hydrogen (for example blast cleaning),there is not risk of hydrogen embitterment form the surface preparation procedure.If cleaning methods are applied which could lead to hydrogen absorption (such as cleaning).then for fasteners which 8 hardness above 365 Hv in process control shall be conducted to ensure that the process with regard to hydrogen embroilment is under control. This can be done by a preload test according to ISO 15330However it should be noted that a non electrolytically applied zinc flake coating has a high permeability for hydrogen which during the curing process, allows effusion of hydrogen which may have been absorbed before the coating process.5.Dimensional requirements and testingThe applicability of coating to ISO metric threads is limited by the fundamental deviation of the threads concerned as given in table 1 and, hence, by the pitch and tolerance positions. The coating shall not cause the zero line(basic size)to be exceeded in the case of external threads, nor shall it fall below in the case of internal threads. this means that for an internal thread of tolerances position H, a measurable coating thickness can only be applied to the thread if the tolerance zone is not taken up to the zero line(basic size).After coating, ISO metric screw threads shall be gauged according to ISO 1502 with a GO-gauge of tolerance position h for external threads and H for internal threads. When gauging the coated thread a maximum torque of 0,001 d3. (N.m)is acceptable, where d is the nominal thread diameter in min.Other product dimensions apply only before coating.NOTE Care should be exercised where relatively thick coatings may affect dimensions with small tolerances such as internal drives or small nuts, in these cases agreements shall be made between the supplier and the purchaser.Table 1 - Theoretical upper limits of coating thickness for ISO metric threadsIf a minimum coating thickness( t min)is required in order to achieve a specified corrosion resistance (see clause 6)the range of the coating thickness has to be taken into consideration which is approximately the same as the minimum coating itself. Therefore the maximum coating thickness to be expected is twice as much as the required minimum coating thickness see table 2. The minimum fundamental deviation required for a specified minimum coating thickness which is 4 t max (or 8 t min )is also given in table 2.Table 2 -Coating thickness and required fundamental deviationIf for a given pitch the fundamental deviation as given in table 1 is not sufficient to allow for the required minimum coating thickness then.--either the tolerance position of the thread has to be changed ( e.g.f instead of g )--or the tolerance within the given tolerance field has to be restricted such that the thread has to be manufactured at the upper limit for the internal thread or at the lowerlimit external thread of the respective tolerance.Required minimum local coating thickness to achieve specified corrosion resistance are given in table 3.If the minimum local coating thickness is specified (see table 3) it may be measured by magnetic or X ray techniques. In the case of dispute the referee test shall be the microscopical method as described in ISO 1463. The surfaced to be used for thickness measurements are those given in figure1 Measuring areaFigure 1 --Measuring area for coating thickness measurement on threaded fasteners6 Testing of corrosion protectionThe neutral salt spray test according to ISO9227 is used to evaluate the quality of the coating. The test is applied to coated parts which are in the as delivered condition. Performance in the test cannot be related to corrosion protection behavior in particular service environments.NOTE In normal cases the coating shall be defined by specifying the test duration for neutral salt spray test according to table 3. see example 1 in clause 9.After the neutral salt spray test with a test duration according to table 3 there shall be no visible ferrous(red) corrosion attack on the base metal.Table 3 -- Test duration ( Neutral salt spray test )7. Mechanical and physical properties and testing7.1GeneralThe coating process shall not adversely influence the mechanical and physical properties of fasteners as specified in the relevant ISO Standards.Consideration shall be given by the manufacturer supported by testing if necessary. to determine whether the curing temperature and duration as specified by the coater are suitable foe the particular type of fastener to be coated.7.2 AppearanceThe colour of the coating is silver grey. The coated fastener shall be free from blisters, localized excess coating and uncoated areas which may have adverse effects on corrosion protection and fitness for use.Special techniques may be necessary to avoid excess coating or uncoated areas with parts such as washers. nuts and recess drive screw.7.3 Temperature resistanceAfter heating the coated fasteners for 3 hours at 150℃(part temperature) the corrosion resistance requirements as specified in clause 6 shall still be met.7.4 DuctilityAfter loading the coated fastener with the proof load specified in ISO 898-1 the corrosion resistance as specified in clause 6 shall still be met in areas other than where thread engagement has occurred. This requirement applies to bolts. screws and studs with metric thread only.7.5 Adhesion/ cohesionIf an adhesive tape with an a dhesive strength of (7 N ± 1 N) per 25 mm width is pressed by hand on the surface and is subsequently pulled off jerkily and perpendicularly to the surface. the coating shall not be peeled off the base metal. Small amounts of the coating material sticking on the tape are acceptable.7.6 Cathodic protectionThe cathodic protection capability of the coating can be tested by making the salt spray test according to be clause with a specimen which is scratched to the base metal, the scratch having a width of max.0.5 mm. After the salt spray rest of 72 h there shall be no red rust in the scratched area.7.7 Torque/tension relationship for coatings with integral lubricant or externally added lubricant The requirements for torque/tension shall be agreed between the manufacturer and purchaser.8. Applicability of tests8.1 GeneralAll requirements given in the clause 5, 6 and 7 apply as far as they are general characteristics of the coating or are separately specified by the customer. The tests included in clause 8.2 shall be carried out for each lot of fasteners. The tests included in clause 8.3 are not intended to be applied for each fastener lot, but are used for in process control.8.2 Tests mandatory for each lot--Gauging of threads ( 5 )--Appearance ( 7.2 )--Adhesion/cohesion ( 7.5 )8.3 Tests to be made for in process control--Neutral salt spray test (6)--Temperature resistance ( 7.3 )--Ductility ( 7.4 )--Cathodic protection ( 7.6 )8.4 Tests which are only to be made when specified by the customer-- Coating thickness ( 5 )--Torque/tension relationship for coating with integral lubricant ( 7.7 )9. DesignationThe designation of the coating shall be added to the product designation in accordance with the designation system specified in ISO 8991 using the symbol flZn for non-electrolytically applied zinc flake coating, a figure for the required duration of salt spray test in hours and, if necessary,the specification for a coating with chromate(yc) or without chromate (nc).EXAMPLE 1 Hexagon head bolt ISO 4014 - M12 X 80 - 10.9 with a non-electrolytically applied zinc flake coating(flZc), with a required duration of salt spray test of 480 h:Hexagon head bolt ISO 4014 - M12 X 80 - 10.9 - flZn - 480hif a coating with integral lubricant is required,the letter L shall be added to the designation after the symbol for the zinc flake coating:Hexagon head bolt ISO 4014 - M12 X 80 - 10.9 - flZnL - 480hif a coating with a subsequent lubrication(external lubricant) is required, the letter L shall be added at the of the designation:Hexagon head bolt ISO 4014 - M12 X 80 - 10.9 - flZn - 480h - LEXAMPLE 2 Hexagon head bolt ISO 4014 - M12 X 80 - 10.9 with a non-electrolytically applied zinc flake coating without chromate flZnnc, with a required duration of salt spray test of 480 h: Hexagon head bolt ISO 4014 - M12 X 80 - 10.9 - flZnnc - 480hEXAMPLE 3 Hexagon head bolt ISO 4014 - M12 X 80 - 10.9 with a non-electrolytically applied zinc flake coating with chromate flZnyc, with a required duration of salt spray test of 480 h: Hexagon head bolt ISO 4014 - M12 X 80 - 10.9 - flZnyc - 480h10. Ordering requirementsWhen ordering threaded parts to be coated according to this International Standard, the flowing information shall be supplied to the coater:a) THe reference to this International standard and the coating designation(see clause 9).b) The matrial of the part and its. condition, e.g. heat treatment, hardness ororder properties, which may be influenced by the coating process..c) Thread tolerances if different from the product standardd) Performance(torque/tension, coefficient of friction, sealing) and the testmethods for integrally lubricated or supplementary lubricated coating shallbe agreed between the manufacturer and purchaser.e) Tests to be carried out, if any(see clause 8)f) Sampling。
identification翻译

identification翻译基本解释●identification:识别,鉴定,身份证明●/aɪˌdentɪfɪˈkeɪʃən/●n. 识别,鉴定●n. 身份证明具体用法●●名词:oo识别,鉴定ooo同义词:recognition, verification, authentication, validation, confirmationooo反义词:misidentification, confusion, disorientation, misrecognition, misunderstandingooo例句:witness who saw the crime happening. (目击犯罪发生的证人确认了嫌疑犯的身份。
)●Accurate identification of the species is crucial for the successof the conservation project. (准确识别物种对于保护项目的成功至关重要。
)●The identification process involves several steps to ensure theaccuracy of the results. (识别过程涉及多个步骤以确保结果的准确性。
)●Identification of the problem is the first step towards findinga solution. (识别问题是找到解决方案的第一步。
)●The identification of the chemical compound was achievedthrough advanced laboratory techniques. (通过先进的实验室技术实现了化合物的鉴定。
)●The identification badge must be worn at all times while onthe premises. (在场所内必须始终佩戴识别徽章。
美国德克萨斯州驾驶考试中英对照 版

美国德克萨斯州驾驶考试模拟题及相关资料中英对照为了帮助我深爱的妻子 Cathy 顺利通过德克萨斯州的驾驶考试,我利用搜集到的考试模拟题、真题及其他资料,翻译并整理。
利用这份资料,妻子顺利通过考试,笔试路考一次通过,不负我一番苦心。
愿与大家分享,希望每对相爱夫妇均能幸福美满。
ZF 2011.10 理论部分:License & License Related 驾照相关内容Your drivers license may be suspended for causing one serious accident。
出现严重的事故,你的驾照会被暂停。
Your license may be suspended or revoked for letting someone use your license。
让别人使用你的驾照,你的驾照将被暂停或吊销。
If a policeman requests you to take a test to see if you are driving under the influence of alcohol or drugs, and you refuse, your license will be suspended for 6 months.当警察要求你参加酒精或药物测试,你拒绝,你的驾照将被暂停 6 个月。
When a parent signs the application of a minor for a drivers license, the parent and the teenager assume responsibility.当父母签字同意未成年人参加驾驶考试时,家长和未成年人均承担相应责任。
An instruction permi t is good for 1 year from the applicant’s next birthday.家长的同意一年有效,截止于申请人的下一个生日。
关于景区旅游游客限流政策通知英语小作文

关于景区旅游游客限流政策通知英语小作文全文共3篇示例,供读者参考篇1Notice on Tourist Flow Control Policy in Scenic AreasDear Visitors,In order to better protect the environment, ensure the safety of tourists, and improve the overall visitor experience, we have implemented a tourist flow control policy in our scenic area. The purpose of this policy is to manage the number of visitors in the area at any given time, in order to prevent overcrowding, reduce damage to the natural environment, and enhance the quality of the visitor experience.Effective immediately, the following measures will be put into place:1. Visitor Capacity Limits: We will be limiting the number of visitors allowed in the scenic area at any given time. Once the maximum capacity has been reached, entrance will be temporarily closed until the number of visitors inside the area has decreased.2. Timed Entry: Visitors will be required to reserve a specific entry time in advance. This will help us manage the flow of visitors throughout the day, and prevent overcrowding during peak hours.3. Restricted Access to Certain Areas: Some sections of the scenic area may have restricted access in order to protect fragile ecosystems or cultural heritage sites. Please respect all posted signs and stay on designated trails at all times.4. Group Size Limitations: In order to reduce the impact of large tour groups on the environment and other visitors, we will be limiting the size of groups allowed in the area.5. Increased Monitoring and Enforcement: Park staff will be stationed throughout the area to monitor visitor numbers, enforce park rules, and ensure that all visitors are following the policies in place.We appreciate your cooperation and understanding as we work to enhance the visitor experience and protect the natural beauty of our scenic area. By following these guidelines, you can help us create a more sustainable and enjoyable environment for everyone to enjoy.Thank you for your support,[Scenic Area Management Team]篇2Notice on Visitor Flow Restriction Policy of Scenic Spot TourismIn order to ensure the safety and comfort of tourists, and protect the ecological environment of the scenic spot, starting from August 1st, 2021, the management committee of the scenic spot has decided to implement a visitor flow restriction policy. The specific measures are as follows:1. Daily Visitor Limit: The scenic spot will limit the number of visitors per day to control the overall flow of tourists. Visitors must make reservations in advance through the official website or designated reservation platforms. Once the daily visitor limit is reached, no entry will be allowed.2. Time Slot Reservations: Visitors must choose a specific time slot for entry when making a reservation. Time slots are divided into morning, afternoon, and evening. Entry is only allowed during the chosen time slot, and visitors are not allowed to enter at other times.3. Group Size Limit: Each reservation is limited to a maximum group size of 10 people. Large tour groups are required to make separate reservations for each group member.4. Visitor Registration: Upon arrival at the scenic spot, visitors must present their reservation confirmation, valid ID, and health code for registration. Failure to provide these documents may result in refusal of entry.5. Compliance with Regulations: Visitors must comply with all relevant regulations and guidelines of the scenic spot, including but not limited to environmental protection rules, safety instructions, and code of conduct.6. Enforcement of Policy: The scenic spot will deploy staff to enforce the visitor flow restriction policy and ensure compliance with the rules. Visitors who violate the policy may be asked to leave the scenic spot.We trust that all visitors will cooperate with us in implementing these measures for a safe and pleasant travel experience. Thank you for your understanding and support.Management Committee of Scenic Spot TourismDate: July 15th, 2021篇3Tourist Flow Control Policy NoticeDear Visitors,In order to better protect the ecology and environment of our scenic area, and to provide a better travel experience for visitors, the scenic area's management committee has decided to implement a tourist flow control policy starting from next month.The main objectives of the tourist flow control policy are as follows:1. Reduce overcrowding: By limiting the number of visitors to the scenic area each day, we aim to reduce overcrowding and alleviate the pressure on the environment and facilities.2. Better protection of natural resources: Over-tourism can have a negative impact on the ecology and environment of the scenic area. By controlling the number of visitors, we can better protect the natural resources and preserve the beauty of the landscape.3. Improve visitor experience: By reducing overcrowding, visitors can enjoy a more peaceful and enjoyable experience, without having to compete for space or wait in long lines.The specific details of the tourist flow control policy are as follows:1. Advance reservations: Visitors will need to make advance reservations before visiting the scenic area. Only a limited number of tickets will be available each day.2. Time slots: Visitors will be assigned a specific time slot for their visit. Late arrivals will not be allowed entry.3. Time limit: Visitors will be allowed a maximum of four hours to explore the scenic area. This will help to ensure that all visitors have a chance to enjoy the attractions.4. Visitor quotas: A daily visitor quota will be set, and once this quota is reached, entry will be closed for the day. We recommend booking your tickets in advance to avoid disappointment.We appreciate your understanding and cooperation in implementing the tourist flow control policy. Together, we can preserve the beauty of our scenic area for future generations to enjoy.Thank you for your cooperation.Sincerely,Scenic Area Management Committee。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
CODE SIZE LIMIT IN RESTRICTED VERSION EXCEEDE D
2010-08-01 15:05:24| 分类:默认分类阅读3433 评论10 字号:大中小订阅
本人在使用c8051f020编译软件silicon laboratories IDE集成编程环境时,由于程序代码过长,造成了如标题所示的错误,编译无法通过,开始我以为是自己的代码过长,造成软件无法编译通过的。
后来在网上一查,才发现是自己的keil软件没有经过破解,所以code size 一直受到限制。
因为在使用IDE的时候,在该集成环境中,就是要添加keil软件提供的工具的,所以既然keil没有被破解,自然而然这工具就无法使用了。
因而我便从网上找了keil v8.02的破解工具,将该软件破解。
下面将破解图片献上。
第一步:找到这个破解软件
打开是这样一个界面
选择V2模式将LICO里的注册码复制下来
然后在keil软件下在file里找到如图所示的license management
打开后会有这样一个界面叫你输入new license id code 将之前复制的注册码黏贴到这个框框中,之后你便会发现add lic 这个选项会点亮,此时你变可以按下add lic了。
如下图所示
然后之后keil 便会提示你注册成功并告诉你使用期限,我看了下我自己的可以使用到2014年五月
至此,我发现一个很重要的信息,你不懂英文真的很可怕。
因为在找错误的时候,他提示的都是英文的,假如你不懂英文,那你找起错误来,肯定会很麻烦,所以大家在有空的时候,还是得多看些英语单词,已提高自己的英文水平。
这个英语嘛都是从一点一滴积累起来的。
