DELL RAC使用指南
戴尔易安信远程访问控制器6(iDRAC6)企业版刀片服务器版本3.2用户指南说明书

Integrated Dell Remote Access Controller 6 (iDRAC6) Enterprise for Blade Servers版本 3.2 用户指南注和小心________________________________________本出版物中的信息如有更改,恕不另行通知。
© 2011 Dell Inc. 版权所有,翻印必究。
未经 Dell Inc. 书面许可,严禁以任何形式复制这些材料。
本文中使用的商标:Dell™、DELL™ 徽标、OpenManage™、和 PowerEdge™ 是 Dell Inc. 的商标。
Microsoft ®、Windows ®、Windows Server ®、Internet Explorer ®、Windows Vista ®、MS-DOS ™、ActiveX ™ 和 Active Directory ® 是 Microsoft Corporation 在美国和/或其他国家/地区的商标或注册商标。
Red Hat ® 和 Red Hat Enterprise Linux ®是 Red Hat, Inc. 在美国和其他国家/地区的注册商标。
Novell ® 和 SUSE ® 是 Novell, Inc. 在美国和其他国家或地区的注册商标。
Intel ® 和 Pentium ® 是 Intel Corporation 在美国和其他国家/地区的注册商标。
UNIX ® 是 The Open Group 在美国和其它国家/地区的注册商标。
Thawte ® 是 Thawte Consulting (Pty) Ltd. 的注册商标。
VeriSign ® 是 VeriSign, Inc. 及其分支机构在美国和美国以外国家/地区的注册商标。
DELL iDRAC6(BMC IPMI) 介绍

DELL iDRAC6介绍关键字:dell iDRAC6 IPMI BMCiDRAC6 概览Integrated Dell Remote Access Controller 6 (iDRAC6) 版本1.7 用户指南此版本有何新功能iDRAC6 Express 管理功能iDRAC6 Enterprise 和vFlash 介质支持的平台支持的操作系统支持的Web 浏览器支持的远程访问连接iDRAC6 端口您可能需要的其它说明文件Integrated Dell Remote Access Controller6 (iDRAC6) 是一种系统管理硬件和软件解决方案,用于为Dell PowerEdge 系统提供远程管理功能、崩溃系统恢复和电源控制功能。
iDRAC6 在远程监测/控制系统中使用集成的片上系统微处理器。
iDRAC6 与受管PowerEdge 服务器共存于系统板上。
服务器操作系统负责执行应用程序;iDRAC6 负责监测和管理操作系统之外的服务器环境和状态。
可以配置iDRAC6 向您发送电子邮件或简单网络管理协议(SNMP) 陷阱警报来通知警告或错误。
为帮助诊断系统崩溃的可能原因,iDRAC6 可以在检测到系统崩溃时记录事件数据并捕获屏幕图像。
默认情况下,启用的iDRAC6 网络界面使用静态IP 地址192.168.0.120。
必须对其进行配置,才能访问iDRAC6。
当在网络上配置iDRAC6 后,可以通过iDRAC6 Web 界面、Telnet 或Secure Shell (SSH) 和支持的网络管理协议(如智能平台管理接口[IPMI])以分配的IP 地址对其进行访问。
此版本有何新功能提高了Web GUI 性能。
提高了vFlash性能。
带外硬件和固件资源清册支持。
控制台启动无需SSO。
工作注释。
改善系统现场可更换单元(FRU) 数据(FRU 产品信息区域中的产品名称、序列号、资产标签和版本)。
戴尔易安信iDRAC6集成式远程访问控制器3.00版说明书

###################################################################### INTEGRATED DELL(TM) REMOTE ACCESS CONTROLLER 6 (iDRAC6) VERSION 3.00 ######################################################################This document contains updated information about the Integrated DellRemote Access Controller 6.For more information about iDRAC6, including installation andconfiguration information, see the "Integrated Dell Remote AccessController 6 (iDRAC6) Enterprise for Blade Servers Version 3.00User Guide" and the "Dell OpenManage(TM) Server AdministratorUser's Guide." These documents are located on the Dell Supportwebsite at "/manuals." On the "Manuals" page, click"Software" > "Systems Management". Click on the appropriate productlink on the right-side to access the documents.######################################################################TABLE OF CONTENTS######################################################################This file contains the following sections:* Criticality* Minimum Requirements* Release Highlights* Important Notes and Known Issues###################################################################### CRITICALITY######################################################################2 - Recommended###################################################################### MINIMUM REQUIREMENTS######################################################################====================================================================== SUPPORTED SYSTEMS====================================================================== iDRAC6 is supported on the following Dell PowerEdge(TM) systemsin the Dell PowerEdge M1000e system enclosure:* Dell PowerEdge M610* Dell PowerEdge M710* Dell PowerEdge M910* Dell PowerEdge M610x* Dell PowerEdge M710HD====================================================================== SUPPORTED MANAGED SERVER OPERATING SYSTEMS====================================================================== The iDRAC6 is supported by the following operating systems:* Microsoft(R) Windows Server(R) 2003 familyThe Windows Server 2003 family includes:- Windows Server 2003 (Standard, Enterprise, and DataCenterEditions) with SP2 (x86, x86_64)- Windows Server 2003 Web Edition with SP2 (x86, x86_64) on M910 only- Windows Server 2003 R2 (Standard, Enterprise, and DataCenterEditions) with SP2 (x86, x86_64)* Microsoft Windows Server 2008 SP2 (Standard, Enterprise,and DataCenter Editions) (x86, x86_64)- Windows Server 2008 SP2 Web Edition (x86, x86_64) on M910 only* Microsoft Windows Server 2008 EBS SP1 (Standard and Premium Editions)* Microsoft Windows Server 2008 R2 (Standard, Enterprise,and DataCenter Editions) (x86_64)- Windows Server 2008 R2 Web Edition (x86_64) on M910 only* SUSE(R) Linux Enterprise Server (SLES) 10 SP3 (x86_64)* SUSE Linux Enterprise Server (SLES) 11 (x86_64)* Red Hat(R) Enterprise Linux (RHEL) 4.8 (x86, x86_64)* Red Hat(R) Enterprise Linux (RHEL) 5.5 (x86, x86_64)* Hyper-V(TM) and Hyper-V R2* VMware(R) ESX 4.0 Update 1* ESXi(TM) 4.0 Update1 Flash* XenServer(TM) 6.0 HDDNote:Use the Dell-customized ESXi 4.0 Update 1 Embedded edition. Thisimage is available at and . The remotedeployment and local installation of ESXi through Virtual Media isnot supported for standard ESXi Embedded version 4.0, as theinstallation may fail with the error message, "Installation failedas more than one USB device found."====================================================================== SUPPORTED WEB BROWSERS====================================================================== * Microsoft Internet Explorer(R) 7.0 for Windows Server 2003 SP2,Windows Server 2008 SP2, Windows XP SP3, and Windows Vista(R) SP2* Microsoft Internet Explorer 8.0 for Windows Server 2003 SP2,Windows Server 2008 SP2, Windows Server 2008 R2, Windows XP SP3,Windows 7, and Windows Vista(R) SP2.Internet Explorer 8 requires Java(TM) Runtime Environment (JRE)version 1.6.14 or later* Microsoft Internet Explorer 8.0 (64-bit) for Windows 7 (x86_64)and Windows Server 2008 R2 (x86_64)* Mozilla(R) Firefox(R) 3.0 on Windows XP SP3, Windows Server 2003 SP2,Windows Server 2008 SP2, Windows Server 2008 R2, Windows Vista SP2,Windows 7, RHEL 4.8, RHEL 5.4, SLES 10 SP3, and SLES 11* Mozilla(R) Firefox(R) 3.6 on Windows Server 2008 SP2,Windows Server 2008 R2, Windows Vista SP2, Windows 7, RHEL 4.8,RHEL 5.4, and SLES 11* Mozilla(R) Firefox(R) 3.6 (64-bit) on RHEL 5.4 (x86_64) andSLES 11 (x86_64)====================================================================== FIRMWARE VERSIONS====================================================================== Recommended firmware versions for CMC and BIOS:* CMC Firmware: 3.0 (required for M610x and M710HD)* Dell PowerEdge M610 BIOS: 2.1.8 or later* Dell PowerEdge M710 BIOS: 2.1.8 or later* Dell PowerEdge M910 BIOS: 1.1.6 or later* Dell PowerEdge M610x BIOS: 2.1.8 or later* Dell PowerEdge M710HD BIOS: 1.0.x or later###################################################################### RELEASE HIGHLIGHTS (FIRMWARE VERSION 3.00)######################################################################* Support for M610x and M710HD systems* Remote Enablement enhancements* vFlash enhancements* New Web GUI visual design* Virtual Console preview* Regular maintenance###################################################################### IMPORTANT NOTES AND KNOWN ISSUES FOR iDRAC6 3.00######################################################################This section provides important notes and additional information aboutknown issues for the iDRAC6 Firmware version 3.00:* If you are upgrading from iDRAC versions 2.1 or 2.2, you must firstinstall iDRAC version 2.30 or 2.31 before installing the 3.00 version.* When connecting to the iDRAC Web interface with a certificate thebrowser does not trust, the browser's certificate error warning maydisplay a second time after you acknowledge the first warning. Thisis the expected behavior to ensure security.* To use Virtual Console with Java plug-in, the supported JRE versionis 1.6.0_20 or higher.* When the JRE is configured to verify the certificate againsta Certificate Revocation List (CRL) and/or online certificatevalidation the certificate validation may sometimes fail. Thisis because the Certificate Authority (CA) that issued the certificateis not accessible due to connectivity problems or is notresponding in a timely manner. In such cases, wait and retry ata later time.* Remote Services: When using TFTP to download an ISO image to thevFlash, if the image exceeds the partition size, no error messagewill be generated. However, subsequent operations on the ISO willfail.* On certain hardware configurations, based on the firmware release,firmware downgrades are not allowed.* For Remote Enablement auto-discovery, ensure that the user ID onthe provisioning server does not contain any spaces, as iDRAC6 userIDs may not contain spaces. If a user ID containing spaces isconfigured on the provisioning server, the auto-discovery processmay be successful, but the resulting iDRAC6 account will not be usable.* If you run Dell Update Packages (DUPs) when vFlash is in-use, thevFlash is disconnected and reconnected. If a write operation isin-progress, this action can corrupt the vFlash contents. If thisoccurs, the vFlash SD card will have to be re-initialized.* Reboot the managed system running on VMware ESX 3.x operatingsystem after an iDRAC6 update is completed. This ensures thatthe VMware ESX operating system re-enumerates the virtualdevices and enables virtual floppy and virtual CD-ROMfeatures of the iDRAC6. After the reboot, virtual devicesincluding virtual floppy, work as expected.* Updating iDRAC6 using the DOS Utility when DOS is booted using PXE. The iDRAC6 can be updated using the DOS utility when DOS is booted using PXE. However, the new firmware image has to be on a local media on the system for this to work properly. Local media can be a RAMDISK, HD, or a USB key on the server. When the image is stored on non-local devices like a network drive, PXE server drive, and so on, the iDRAC6update on multiple systems must be sequenced that is, it should bedone one system after the other. After the first system completes theupdate, the second system starts the update. After the second systemcompletes the update, the third system starts the update and so on.* On systems running Windows operating systems, theExplorer window(s) for any media does not close automatically if you remove the media. You must close the window(s) after you removethe media.On systems running Linux operating systems, the filebrowser window(s) for any media closes automatically if you removethe media.* iDRAC6 Linux DUPs do not support VMware ESX 4.0 operatingsystems. If the Linux DUP for iDRAC6 is run on VMwareESX 4.0, the DUP will fail.You can update iDRAC6 using one of the following methods:- CMC GUI-based update- iDRAC6 GUI-based update- Remote RACADM-based update* If you receive the message "A webpage is not responding onthe following website" in Internet Explorer 8.0, see:"/ie/archive/2009/05/04/ie8-in-windows-7-rc-reliability-and-telemetry.aspx""/?kbid=970858"* In Internet Explorer 7.0, if several tabs are open and you launchthe iDRAC6 Virtual Console, all the tabs are hidden whilethe Virtual Console is open. If the tab warning is turned off andyou close the Virtual Console, all the tabs and the browsercloses without warning.To prevent this, go to "Internet Properties" > "Tabs" >"Settings" and select the "Warn me when closing multiple tabs"option.* If a Virtual Media drive is disconnected using the "OS eject"option, then the drive may not be available until the operatingsystem re-enumerates the USB devices. For the operating systemto auto-detect the Virtual Media drive, the iDRAC6 Virtual Mediadevice can be reattached. To do this:1. Go to "System" > "Virtual Console/Media" >"Configuration".2. Set the "Attach Virtual Media" option to "Detach" and click "Apply".3. Set the "Attach Virtual Media" option to "Attach" and click "Apply". * The "racresetcfg" command in RACADM restores all properties totheir default values except "cfgDNSRacName" in the"cfgLanNetworking" group.* The iDRAC6 Linux DUP cannot be run on 64-bit RHEL 4 Update 7due to known issues in that operating system. See the Red HatKB article at "/faq/docs/DOC-3402" touse the DUP on RHEL 4 Update 7.* Smart Card login fails after a logout from the same browser window.Open a new browser window to login.* When using a configuration file with RACADM to configureiDRAC6, changing objects that affect the networkconnection stops the rest of the configuration filefrom taking effect.* To execute iDRAC DUPs in XenServer(TM) 5.6, you must installthe procmail package. You can install the procmail RPM in CentOS5.4 i386, which can be downloaded from any public site that hostsCentOS packages. However, it is recommend not to install *any*RPMs manually on XenServer, instead it is recommended that youdownload and install the OpenManage Supplemental Pack from. It contains the procmail package and is thesupported method for installing third party packages and applicationsin XenServer.* Using the iDRAC web console to shutdown the XenServer operatingsystem by selecting "Graceful Shutdown" does not shut down theserver. As best practice, it is recommended that you use theshutdown menu option in the XenServer console or in the XenCentermanagement GUI.* TFTP firmware update from local RACADM will not work after aracresetcfg or if IPv6 addresses are used. Use the firmwareRACADM for TFTP firmware update.* When using the virtual console on RHEL with Firefox, if thenetwork connection to the iDRAC is lost a blank message boxmay pop up. If the network connection is shortly restoredthe message box may eventually display the “Virtual Consoleis restarted” message and will then close. Normally themessage will immediately display in the message box but onrare occasions it may not display. The display of the messageis controlled by the JRE and if the blank message box isseen this is not an iDRAC firmware issue.* When connecting to the iDRAC GUI using browsers supportinglocalized languages, some popups may have generic messages thatare not localized in the title such as: "The page athttps://10.35.155.207 says:". This is a browser limitationand cannot be changed in the iDRAC.* When using the Virtual Console that uses the Java plug-in with attached Virtual Media, occasionally when disconnecting the Virtual Media the console also closes unexpectedly. When this happens, restartthe Virtual Console to regain access.* When the system is configured for extended schema and a device objectis created in the Active Directory(TM) child domain, iDRAC launch usingSingle Sign-On (SSO) fails for the user created in the child domain andthe root domain. To successfully perform SSO when the user object isdefined in the child domain, associate the user object in the childdomain with “Authenticated user” group.* During the SLES 11 installation through the "Dell Systems ManagementTools and Documentation" DVD, if the DVD is connected through VirtualMedia, the image installation may not proceed after the systemconfiguration step. It shows a warning dialog message similar tothe following:"Empty destination in URL: hd:///install/?device=/dev/sdc1".To continue the installation, delete the question mark ‘?’, refreshthe URL and the installation will proceed. This issue is not seen whenusing the managed system's local CD/DVD or using the operating system DVDdirectly instead of the "Dell Systems Management Tools andDocumentation" DVD.* When using the WSMan DCIM_RAIDService GetAvailableDisks method to retrieve specific RAID devices, the XML file passed to the command will contain a“RaidLevel” value for selection. No error checking is done on the RaidLevelValue. Therefore, if an incorrect or invalid value is specified, incorrectresults may be returned (for example, “abcd” becomes “0”; “64.999” becomes“64”). The RaidLevel specified must be an appropriate integer RAIDlevel value (“1”, “2”, “4”, “64”, “128”, “2048”, “8192”, “16384”, perDCIM_VirtualDiskView.mof).* When all the 16 iDRAC-supported user accounts are configured, attempts tomodify user privileges through the iDRAC GUI fails with the error message“Cannot delete or disable the user. At least one user must be enabled”.Temporarily disabling any one user account restores the ability to modify(all) user account settings. After completing the required accountprivilege changes, the disabled account may be re-enabled.Alternatively, RACADM may be used to modify account settings,irrespective of the number of user accounts that are configured.* At times, the Virtual Console feature of iDRAC becomes unavailable.When this happens issue a “racadm racreset” command to reaccess theVirtual Console.* On few Windows operating systems, under certain conditions, the iDRACivmcli.exe will fail. This is due to run-time components of Visual C++(R)Libraries (VC++ 2008 redistributable package) required to run applicationsthat are not available. To resolve this, download and install MicrosoftVisual C++ 2008 Redistributable Package (x86) from the following location:/downloads/details.aspx?familyid=9B2DA534-3E03-4391- 8A4D-074B9F2BC1BF&displaylang=en* When launching both the iDRAC GUI and the Virtual Console from CMC forthe same managed server, a cmc_root GUI session may not be closed properlyeven when properly logging out of the CMC launched iDRAC GUI window. Ifthis happens, it must be closed manually or the session will remain openuntil it reaches the session timeout. This reduces the available Web sessionsfor logging into the iDRAC until it times out. This session can be closedthrough the “racadm closessn” command or by navigating to the iDRAC SessionsGUI page at "System / Remote Access / iDRAC6" > "Network/Security" > "Sessions". * When using the iDRAC Virtual Console to connect to a managed server with arecent Linux distribution operating system installed, you may experiencemouse synchronization problems. This may be due to the Predictable PointerAcceleration feature of the GNOME desktop. For proper mouse synchronizationin the iDRAC Virtual Console, this feature must be disabled. To disablePredictable Pointer Acceleration, in the mouse section of the/etc/X11/xorg.conf file, add: Option "AccelerationScheme" "lightweight".If synchronization problems continue to be experienced, make the followingadditional changes: In the <user_home>/.gconf/desktop/gnome/peripherals/mouse/%gconf.xml file, change the values for "motion_threshold" and"motion_acceleration" to "-1".* To use Virtual Media with recent Windows releases on the management station,you should log into the management station with an Administrator's account.If you do not, the CD/DVD redirection may not work properly and may causecontinuous USB bus resets. If this happens, set the “Attach Virtual Media”option to “Detach” to stop the USB bus resets and allow CD/DVD redirectionto work properly when you log in again with an Administrator's account.* When you create a vFlash partition from an image file using the GUI orRACADM, if you do not have an open browser for the iDRAC GUI, you will notbe able to connect to the GUI until the create operation is completed. Ifyou need to connect to the iDRAC GUI, you must first have the browserconnected to the iDRAC URL to have access. This is important when a largepartition is being created from an image file since it may take a longtime to complete.* If the browser is enabled to use a proxy server, you will not be able toconnect to the iDRAC GUI. The browser must be set to not use a proxyserver for the iDRAC IP address.* The mention of WS-MAN support for digest authentication in chapter 16 ofthe User Guide is incorrect. iDRAC6 does not support digest authentication.###################################################################### Information in this document is subject to change without notice.(C) 2010 Dell Inc. All rights reserved.Reproduction of these materials in any manner whatsoever withoutthe written permission of Dell Inc. is strictly forbidden.Trademarks used in this text: "Dell", "OpenManage", and "PowerEdge"are trademarks of Dell Inc.; "Microsoft", "Windows", "InternetExplorer", "Windows Server", "Windows Vista", "ActiveX","Hyper-V Server", "Hyper-V", "Visual C++", and "Active Directory"are either trademarks or registered trademarks of Microsoft Corporationin the United States and/or other countries; "Intel" isa registered trademark of Intel Corporation in the United Statesand other countries; "SUSE" is a registered trademark of Novell Corporation; "Red Hat" and "Red Hat Enterprise Linux" are registered trademarks of Red Hat, Inc. in the United States and other countries; "VMware", "ESX Server", and "ESXi Server” are registered trademarks or trademarks of VMware, Inc. in the United States and/or other jurisdictions; "XenServer" is a trademark of Citrix Systems, Inc. in the United States and/or other countries; "Java" is a trademarks of Sun Microsystems, Inc. in the United States and other countries; "Mozilla" and "Firefox" are either registered trademarks or trademarks of Mozilla Foundation.Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own.July 2010。
iDRAC配置手册

目录配置iDRACIntegrated Dell™ Remote Access Controller 固件版本 1.11用户指南开始之前用于配置iDRAC 的界面配置任务配置网络(使用CMC Web 界面)更新iDRAC 固件本部分介绍了如何建立iDRAC 访问以及如何配置管理环境以使用iDRAC。
开始之前配置iDRAC 前收集以下项目:•Dell Chassis Management Controller 用户指南•Dell PowerEdge Installation and Server Management CD•Dell Systems Management Consoles CD•Dell PowerEdge Service and Diagnostic Utilities CD•Dell PowerEdge Documentation CD用于配置iDRAC 的界面可以使用iDRAC 配置公用程序、iDRAC Web 界面、本地RACADM CLI 或SM-CLP CLI 配置iDRAC。
在受管服务器上安装操作系统和Dell PowerEdge 服务器管理软件后,本地RACADM CLI 才可用。
表 2-1说明这些界面。
表2-1. 配置界面配置任务本部分概括介绍Management Station、iDRAC 以及受管服务器的配置任务。
要执行的任务包括配置iDRAC 以供远程使用、配置要使用的iDRAC 功能、在受管服务器上安装操作系统,以及在Management Station 和受管服务器上安装管理软件。
可以用来执行每个任务的配置任务列在任务之下。
注:执行本指南中的配置程序前,必须在机箱中安装并配置CMC 和输入/输出模块,且PowerEdge 服务器必须实际安装在机箱中。
配置Management Station通过安装Dell OpenManage 软件、Web 浏览器以及其它软件公用程序来设置Management Station。
iDRAC 7使用概要

iDRAC7用户手册/support/edocs/software/smdrac3/idrac7/1.20.20/cs/ug/ug.pdf1. 开机按F2,选择“iDRAC Settings ”进入iDRAC设置界面:2. iDRAC 配置界面:3. 往下移动可以配置IPV4地址:4,电源设置:从冗余电源改成单电之后,需要把power supply options 设为:No Redundancy,否则机器会报电源冗余缺失iDRAC 7使用概要Saturday, September 14, 20132:03 PM5,iDRAC7中加入了风扇转速的控制:6,用户帐户的设置:7,如果服务器超过3次非正常关机,Lifecycle Controller|USC会被死锁,自检界面显示如下图:解方法:进入Lifecycle Controller 将lifecycle controller从recovery mode改回Enabled状态,保存重启即可.8,如果小液晶显示的不是Service Tag,通常会是idrac中LCD message设置改了,将Set LCD message设为Service Tag即可,9. 通过IE访问配置的iDRAC6 IP地址: (默认用户名为root 密码为calvin,默认IP:192.168.0.120)10. 登录后可以查看机器服务编号,BIO版,收集或者清除系统日志等11. 查看电源的工作状态及电源的配置:12. 配置告警筛选13,管理许可协议:14. 查看iDRAC信息:15. 查看iDRAC 网络配置:16. 启动重定向:17. 重定向界面:18. 启动虚拟介质, 就是把本地的光驱或ISO文件当成服务器上的光驱使用:19. 首先要确认Virtual Media的附件状态为自动附加(Auto Attach)或附加(Attach):20. 然后在启动虚拟介质打开后的菜单选择光驱或ISO文件:21. 在启动时选择Virtual CD即可远程安装系统:。
DELL__iDRAC6(BMC_IPMI)_介绍

DELL iDRAC6介绍关键字:dell iDRAC6 IPMI BMCiDRAC6 概览Integrated Dell Remote Access Controller 6 (iDRAC6) 版本1.7 用户指南此版本有何新功能iDRAC6 Express 管理功能iDRAC6 Enterprise 和vFlash 介质支持的平台支持的操作系统支持的Web 浏览器支持的远程访问连接iDRAC6 端口您可能需要的其它说明文件Integrated Dell Remote Access Controller6 (iDRAC6) 是一种系统管理硬件和软件解决方案,用于为Dell PowerEdge 系统提供远程管理功能、崩溃系统恢复和电源控制功能。
iDRAC6 在远程监测/控制系统中使用集成的片上系统微处理器。
iDRAC6 与受管PowerEdge 服务器共存于系统板上。
服务器操作系统负责执行应用程序;iDRAC6 负责监测和管理操作系统之外的服务器环境和状态。
可以配置iDRAC6 向您发送电子邮件或简单网络管理协议(SNMP) 陷阱警报来通知警告或错误。
为帮助诊断系统崩溃的可能原因,iDRAC6 可以在检测到系统崩溃时记录事件数据并捕获屏幕图像。
默认情况下,启用的iDRAC6 网络界面使用静态IP 地址192.168.0.120。
必须对其进行配置,才能访问iDRAC6。
当在网络上配置iDRAC6 后,可以通过iDRAC6 Web 界面、Telnet 或Secure Shell (SSH) 和支持的网络管理协议(如智能平台管理接口[IPMI])以分配的IP 地址对其进行访问。
此版本有何新功能提高了Web GUI 性能。
提高了vFlash性能。
带外硬件和固件资源清册支持。
控制台启动无需SSO。
工作注释。
改善系统现场可更换单元(FRU) 数据(FRU 产品信息区域中的产品名称、序列号、资产标签和版本)。
Dell Precision Rack 7910 快速入门指南说明书

1Install the system into a rack Plaats het systeem in een rekInstallez le système dans un rackSetzen Sie das System in ein Rack einInstallare il sistema in un rack2Connect the keyboard, mouse, and monitor(optional)Sluit het toetsenbord, de muis en de monitor aan (optioneel)Connectez le clavier, la souris et le moniteur (facultatif)Schließen Sie die Tastatur, die Maus und den Monitor (optional) anConnettere la tastiera, il mouse e il monitor (opzionale)to support3Connect the system to a power sourceSluit het systeem aan op een voedingsbronConnectez le système à une source d’alimentationSchließen Sie das System an eine Energiequelle anConnettere il sistema a una fonte di alimentazione4Loop and secure the power cable in theretention clipVoer de voedingskabel door de borgclipFormez une boucle et fixez le câble d’alimentation au clip de maintienSchleifen Sie das Stromkabel durch und befestigen Sie es in der HalteklammerArrotolare e assicurare il cavo di alimentazione alla clip di contenimento5Turn on the systemSchakel het systeem inMettez le système sous tensionSchalten Sie das System einAccendere il sistema© 2014 Dell Inc.© 2014 Microsoft Corporation.Printed in China.2014-081. Power button/Power light2. NMI button3. System identification button4. VGA connector5. LCD menu buttons6. Information tag7. LCD panel8. Hard-drives9. vFlash media card slot 10. USB 2.0 connector11. USB management port/iDRAC Direct 12. Optical-drive (optional)13. System identification button 14. System identification connector15. iDRAC8 Enterprise port (optional)16. PCIe expansion card slots half height 17. Serial connector 18. VGA connector 19. USB 3.0 connectors20. PCIe Expansion card slots full height 21. Network connectors 22. Power supply1. Aan-/uitknop/stroomlampje2. NMI-knop3. Systeemidentificatieknop4. VGA-aansluiting5. Lcd-menuknoppen6. Informatielabel7. Lcd-paneel8. Harde schijven9. Sleuf voor vFlash-geheugenkaart 10. USB 2.0-aansluiting 11. USB-poort/iDRAC Direct 12. Optisch station (optioneel)13. Systeemidentificatieknop 14. Systeemidentificatieaansluiting 15. iDRAC8 Enterprise-poort(optioneel)16. PCIe-uitbredingssleuven(halve hoogte)17. Seriële aansluiting 18. VGA-aansluiting 19. USB 3.0-aansluitingen 20. PCIe-uitbredingssleuven(volledige hoogte)21. Netwerkaansluitingen 22. Voeding1. Bouton d’alimentation/Voyantd’alimentation 2. Bouton NMI3. Bouton d’identification du système4. Port VGA5. Boutons de menu de l’écrand’affichage LCD 6. Étiquette d’informations 7. Écran d’affichage LCD 8. Disques durs9. Logement pour carte mémoire vFlash 10. Port USB 2.011. Port de gestion USB/iDRAC Direct 12. Lecteur optique (en option)13. Bouton d’identification du système14. Port d’identification du système 15. Port iDRAC8 Enterprise (en option)16. Logements pour carte d’extensionPCIe demi-hauteur 17. Port série 18. Port VGA 19. Ports USB 3.020. Logements pour carte d’extensionPCIe pleine hauteur 21. Ports réseau 22. Alimentation1. Betriebsschalter/Betriebsanzeige2. NMI-Taste3. Systemidentifikationstaste4. VGA-Anschluss5. LCD-Menütasten6. Informations-Tag7. LCD-Bildschirm8. Festplatten9. vFlash-Medienkartensteckplatz 10. USB 2.0-Anschluss11. USB-Verwaltungsport/iDRAC Direct 12. Optisches Laufwerk (optional)13. Systemidentifikationstaste 14. Systemidentifikationsanschluss 15. iDRAC8 Enterprise-Anschluss(optional)16. PCIe-Erweiterungskartensteckplätzehalber Baulänge 17. Serieller Anschluss 18. VGA-Anschluss 19. USB 3.0-Anschlüsse20. PCIe-Erweiterungskartensteckplätzevoller Baulänge 21. Netzwerkanschlüsse 22. Netzteil1. Accensione/Indicatore dialimentazione 2. Pulsante NMI3. Pulsante di identificazionedel sistema 4. Connettore VGA 5. Pulsanti del menu LCD 6. Etichetta informativa 7. Pannello LCD 8. Dischi rigidi9. Slot scheda multimediale vFlash 10. Connettore USB 2.011. Posta di gestione USB/iDRAC Direct 12. Unità ottica (opzionale)13. Pulsante di identificazione del sistema14. Connettore di identificazionedel sistema 15. Porta iDRAC8 Enterprise(opzionale)16. Slot scheda di espansione PCIea mezza altezza 17. Connettore seriale 18. Connettore VGA 19. Connettori USB 3.020. Slot scheda di espansione PCIea tutta altezza 21. Connettori di rete 22. AlimentatoreFeaturesKenmerken | Caractéristiques | Funktionen | FunzioniProduct support and manualsProductondersteuning en handleidingen Support produits et manuelsProduktsupport und HandbücherSupporto tecnico e manuali del prodotto /support/support/manualsContact DellNeem contact op met Dell | Contacter Dell Kontaktaufnahme mit Dell | Contattare Dell/contactdellRegulatory and safetyRegelgeving en veiligheid | Réglementations et sécuritéSicherheitshinweise und Zulassungsinformationen Normative e sicurezza/regulatory_complianceRegulatory modelWettelijk model | Modèle réglementaireMuster-Modellnummer | Modello di conformitàE31SRegulatory typeWettelijk type | Type réglementaireMuster-Typnummer | Tipo di conformitàE31S001Computer modelComputermodel | Modèle de l’ordinateur Computermodell | Modello del computerDell Precision Rack 7910。
iDRAC配置手册

目录配置iDRACIntegrated Dell™ Remote Access Controller 固件版本 1.11用户指南开始之前用于配置iDRAC 的界面配置任务配置网络(使用CMC Web 界面)更新iDRAC 固件本部分介绍了如何建立iDRAC 访问以及如何配置管理环境以使用iDRAC。
开始之前配置iDRAC 前收集以下项目:∙Dell Chassis Management Controller 用户指南∙Dell PowerEdge Installation and Server Management CD∙Dell Systems Management Consoles CD∙Dell PowerEdge Service and Diagnostic Utilities CD∙Dell PowerEdge Documentation CD用于配置iDRAC 的界面可以使用iDRAC 配置公用程序、iDRAC Web 界面、本地RACADM CLI 或SM-CLP CLI 配置iDRAC。
在受管服务器上安装操作系统和Dell PowerEdge 服务器管理软件后,本地RACADM CLI 才可用。
表 2-1说明这些界面。
表2-1. 配置界面配置任务本部分概括介绍Management Station、iDRAC 以及受管服务器的配置任务。
要执行的任务包括配置iDRAC 以供远程使用、配置要使用的iDRAC 功能、在受管服务器上安装操作系统,以及在Management Station 和受管服务器上安装管理软件。
可以用来执行每个任务的配置任务列在任务之下。
注:执行本指南中的配置程序前,必须在机箱中安装并配置CMC 和输入/输出模块,且PowerEdge 服务器必须实际安装在机箱中。
配置Management Station通过安装Dell OpenManage 软件、Web 浏览器以及其它软件公用程序来设置Management Station。
dell racadm windows 用法

dell racadm windows 用法在Windows操作系统中使用Dell RACADMDell Remote Access Controller (RAC)是一种管理工具,可用于在远程或本地管理Dell服务器。
RACADM是一种命令行工具,可在Windows操作系统中使用,以便轻松地执行对Dell服务器的管理操作。
以下是使用Dell RACADM的一些常见用法:1. 安装Dell RACADM:要在Windows操作系统中使用Dell RACADM,您需要首先下载和安装Dell OpenManage Server Administrator(OMSA)软件包。
此软件包包含了RACADM工具。
您可以在Dell官方网站上找到OMSA软件包,并按照安装向导进行安装。
2. 连接到服务器:一旦安装了Dell OMSA软件包,您可以打开命令提示符或PowerShell,并使用以下命令连接到要管理的Dell服务器:racadm -r <IP地址> -u <用户名> -p <密码>在此命令中,<IP地址>是Dell服务器的IP地址,<用户名>和<密码>是用于RAC登录的凭据。
3. 寻找系统信息:通过使用以下命令,您可以获取有关Dell服务器的一些基本信息:racadm getsysinfo这将显示服务器模型、固件版本、安装的操作系统等。
4. 修改服务器BIOS设置:您可以使用Dell RACADM修改服务器的BIOS设置。
例如,要启用或禁用Intel Hyper-Threading Technology,可以使用以下命令: racadm set BIOS.SysProfileSettings.ProcessorHyperThread enable这将启用Hyper-Threading技术。
5. 监控硬件健康状态:使用以下命令,您可以监控Dell服务器的硬件健康状况:racadm getsensorinfo这将提供有关服务器温度、电源状态、风扇速度等的信息。
Dell iDRAC 9 用户指南说明书

Integrated Dell Remote Access Controller 9 版本 3.30.30.30 用户指南2019 3注意、小心和警告:“注意”表示帮助您更好地使用该产品的重要信息。
:“小心”表示可能会损坏硬件或导致数据丢失,并告诉您如何避免此类问题。
:“警告”表示可能会导致财产损失、人身伤害甚至死亡。
© 2018 - 2019 Dell Inc. 或其子公司。
保留所有权利Dell、EMC 和其他商标均是 Dell Inc. 或其子公司的商标。
其他商标可能是其各自所有者的商标。
章 1: 概览 (15)iDRAC 配合 Lifecycle Controller 一起使用的优点 (15)主要功能 (15)此发行版中的新功能 (18)如何使用本指南 (18)支持的 Web 浏览器 (18)支持的操作系统和虚拟机监控程序 (18)iDRAC 许可证 (19)许可证类型 (19)获取许可证的方法 (19)从 Dell Digital Locker 获取许可证密钥 (20)许可证操作 (20)在 iDRAC9 中的已许可功能 (21)访问 iDRAC 的界面和协议 (25)iDRAC 端口信息 (27)您可能需要的其他说明文件 (28)联系 Dell (29)从 Dell 支持站点访问说明文件 (29)章 2: 登录 iDRAC (30)使用 OpenID Connect 登录 iDRAC (31)以本地用户、Active Directory 用户或 LDAP 用户身份登录 iDRAC (31)使用智能卡作为本地用户登录 iDRAC (32)使用智能卡作为 Active Directory 用户登录 iDRAC (32)使用单一登录登录 iDRAC (32)使用 iDRAC Web 界面登录 iDRAC SSO (32)使用 CMC Web 界面登录 iDRAC SSO (33)使用远程 RACADM 访问 iDRAC (33)验证 CA 证书以在 Linux 上使用远程 RACADM (33)使用本地 RACADM 访问 iDRAC (34)使用固件 RACADM 访问 iDRAC (34)查看系统运行状况 (34)使用公共密钥验证登录 iDRAC (34)多个 iDRAC 会话 (35)使用 SMCLP 访问 iDRAC (35)安全默认密码 (35)在本地重设默认的 iDRAC 密码 (35)远程重设默认 iDRAC 密码 (36)更改默认登录密码 (37)使用 Web 界面更改默认登录密码 (37)使用 RACADM 更改系统将显示默认登录密码 (37)使用 iDRAC 设置公用程序更改默认登录密码 (37)启用或禁用默认密码警告消息 (38)IP 阻止 (38)目录3使用 Web 界面启用或禁用 OS 到 iDRAC 直通 (38)使用 RACADM 启用或禁用警报 (39)章 3: 设置受管系统 (40)设置 iDRAC IP 地址 (40)使用 iDRAC 设置公用程序设置 iDRAC IP (41)使用 CMC Web 界面设置 iDRAC IP (43)启用配置服务器 (44)使用自动配置功能配置服务器和服务器组件 (44)使用散列密码提供更高的安全性 (49)修改本地管理员帐户设置 (50)设置受管系统位置 (51)使用 Web 界面设置受管系统位置 (51)使用 RACADM 设置受管系统位置 (51)使用 iDRAC 设置公用程序设置受管系统位置 (51)优化系统性能和功耗 (51)使用 iDRAC Web 界面修改散热设置 (51)使用 RACADM 修改散热设置 (53)使用 iDRAC 设置公用程序修改散热设置 (56)使用 iDRAC Web 界面修改 PCIe 气流设置 (56)设置管理站 (57)远程访问 iDRAC (57)配置支持的 Web 浏览器 (57)配置 Internet Explorer (57)配置 Mozilla Firefox (58)配置 Web 浏览器以使用虚拟控制台 (59)查看 Web 界面的本地化版本 (62)更新设备固件 (62)使用 iDRAC Web 界面更新固件 (64)计划自动固件更新 (65)使用 RACADM 更新设备固件 (67)使用 CMC Web 界面更新固件 (67)使用 DUP 更新固件 (67)使用远程 RACADM 更新固件 (67)使用 Lifecycle Controller 远程服务更新固件 (68)从 iDRAC 更新 CMC 固件 (68)查看和管理分阶段更新 (69)使用 iDRAC Web 界面查看和管理分阶段更新 (69)使用 RACADM 查看和管理分阶段更新 (69)回滚设备固件 (69)使用 iDRAC Web 界面回滚固件 (70)使用 CMC Web 界面回滚固件 (70)使用 RACADM 回滚固件 (70)使用 Lifecycle Controller 回滚固件 (70)使用 Lifecycle Controller 远程服务回滚固件 (70)恢复 iDRAC (71)备份服务器配置文件 (71)使用 iDRAC Web 界面备份服务器配置文件 (71)使用 RACADM 备份服务器配置文件 (72)计划自动备份服务器配置文件 (72)4目录使用 iDRAC Web 界面导入服务器配置文件 (73)使用 RACADM 导入服务器配置文件 (74)还原操作顺序 (74)使用其他系统管理工具监测 iDRAC (74)支持服务器配置配置文件—导入和导出 (74)使用 iDRAC Web 界面导入服务器配置配置文件 (75)使用 iDRAC Web 界面导出服务器配置配置文件 (75)BIOS 设置或 F2 中的安全引导配置 (75)BIOS 恢复 (76)章 4: 配置 iDRAC (77)查看 iDRAC 信息 (78)使用 Web 界面查看 iDRAC 信息 (78)使用 RACADM 查看 iDRAC 信息 (79)修改网络设置 (79)使用 Web 界面修改网络设置 (79)使用本地 RACADM 修改网络设置 (79)配置 IP 筛选 (79)密码组选择 (81)使用 iDRAC Web 界面配置密码组选择 (81)使用 RACADM 配置密码组选择 (81)FIPS 模式 (81)启用 FIPS 模式 (82)禁用 FIPS 模式 (82)配置服务 (82)使用 Web 界面配置服务 (83)使用 RACADM 配置服务 (83)启用或禁用 HTTPS 重定向 (83)配置 TLS (83)使用 Web 界面配置 TLS (84)使用 RACADM 配置 TLS (84)使用 VNC 客户端管理远程服务器 (84)使用 iDRAC Web 界面配置 VNC 服务器 (85)使用 RACADM 配置 VNC 服务器 (85)设置带 SSL 加密的 VNC 查看器 (85)设置不带 SSL 加密的 VNC 查看器 (85)配置前面板显示屏 (85)配置 LCD 设置 (85)配置系统 ID LED 设置 (86)配置时区和 NTP (87)使用 iDRAC Web 界面配置时区和 NTP (87)使用 RACADM 配置时区和 NTP (87)设置第一引导设备 (87)使用 Web 界面设置第一引导设备 (88)使用 RACADM 设置第一引导设备 (88)使用虚拟控制台设置第一引导设备 (88)启用上次崩溃屏幕 (88)启用或禁用 OS 到 iDRAC 直通 (89)支持 OS 到 iDRAC 直通功能的卡 (89)目录5使用 Web 界面启用或禁用 OS 到 iDRAC 直通 (90)使用 RACADM 启用或禁用 OS 到 iDRAC 直通 (91)使用 iDRAC 设置公用程序启用或禁用 OS 到 iDRAC 直通 (91)获取证书 (91)SSL 服务器证书 (92)生成新的证书签名请求 (92)上载服务器证书 (93)查看服务器证书 (94)上载自定义签名证书 (94)下载自定义 SSL 证书签名证书 (94)删除自定义 SSL 证书签名证书 (95)使用 RACADM 配置多个 iDRAC (95)禁用访问以修改主机系统上的 iDRAC 配置设置 (96)章 5: 查看 iDRAC 和受管系统信息 (97)查看受管系统运行状况和属性 (97)配置资产跟踪 (97)查看系统资源清册 (97)查看传感器信息 (98)监测 CPU、内存和输入输出模块的性能指标 (99)使用 Web 界面监测 CPU、内存和输入输出模块的性能指标 (100)使用 RACADM 监测 CPU、内存和输入输出模块的性能指标 (100)检查系统的新鲜空气符合性 (100)查看历史温度数据 (101)使用 iDRAC Web 界面查看历史温度数据 (101)使用 RACADM 查看历史温度数据 (101)配置入口温度的警告阈值 (101)查看主机操作系统上可用的网络接口 (102)使用 Web 界面查看主机操作系统上可用的网络接口 (102)使用 RACADM 查看主机操作系统上可用的网络接口 (102)查看 FlexAddress 夹层卡光纤连接 (102)查看或终止 iDRAC 会话 (103)使用 Web 界面终止 iDRAC 会话 (103)章 6: 设置 iDRAC 通信 (104)使用 DB9 电缆通过串行连接与 iDRAC 进行通信 (105)针对串行连接配置 BIOS (105)启用 RAC 串行连接 (105)启用 IPMI 串行连接基本和终端模式 (106)使用 DB9 电缆时在 RAC 串行和串行控制台之间切换 (108)从串行控制台切换到 RAC 串行 (108)从 RAC 串行切换到串行控制台 (108)使用 IPMI SOL 与 iDRAC 进行通信 (108)针对串行连接配置 BIOS (108)配置 iDRAC 以使用 SOL (109)启用支持的协议 (110)使用 LAN 上 IPMI 与 iDRAC 通信 (113)使用 Web 界面配置 LAN 上 IPMI (113)6目录使用 iDRAC 设置公用程序配置 LAN 上 IPMI (113)使用 RACADM 配置 LAN 上 IPMI (113)启用或禁用远程 RACADM (114)使用 Web 界面启用或禁用远程 RACADM (114)使用 RACADM 启用或禁用远程 RACADM (114)禁用本地 RACADM (114)启用受管系统上的 IPMI (114)为 RHEL 6 引导期间的串行控制台配置 Linux (115)允许在引导后登录到虚拟控制台 (115)在 RHEL 7 中配置串行终端 (117)从串行控制台控制 GRUB (117)支持的 SSH 加密方案 (118)对 SSH 使用公共密钥验证 (119)章 7: 配置用户帐户和权限 (122)iDRAC 用户角色和权限 (122)建议使用的用户名和密码字符 (123)配置本地用户 (123)使用 iDRAC Web 界面配置本地用户 (124)使用 RACADM 配置本地用户 (124)配置 Active Directory 用户 (125)对 iDRAC 使用 Active Directory 验证的前提条件 (125)支持的 Active Directory 验证机制 (127)标准架构 Active Directory 概览 (127)配置标准架构 Active Directory (128)扩展架构 Active Directory 概览 (130)配置扩展架构 Active Directory (132)测试 Active Directory 设置 (139)配置通用 LDAP 用户 (139)使用 iDRAC 基于 Web 的界面配置通用 LDAP 目录服务 (140)使用 RACADM 配置通用 LDAP 目录服务 (140)测试 LDAP 目录服务设置 (140)章 8: 系统锁定模式 (142)章 9: 配置 iDRAC 以进行单一登录或智能卡登录 (144)Active Directory 单一登录或智能卡登录的前提条件 (144)将 iDRAC 注册为 Active Directory 根域中的计算机 (144)创建 Active Directory 对象并提供权限 (145)为 Active Directory 用户配置 iDRAC SSO 登录 (145)在 Active Directory 中创建用户以进行 SSO 登录 (145)生成 Kerberos Keytab 文件 (146)使用 Web 界面为 Active Directory 用户配置 iDRAC SSO 登录 (146)使用 RACADM 为 Active Directory 用户配置 iDRAC SSO 登录 (146)管理站设置 (146)启用或禁用智能卡登录 (147)使用 Web 界面启用或禁用智能卡登录 (147)使用 RACADM 启用或禁用智能卡登录 (147)使用 iDRAC 设置公用程序启用或禁用智能卡登录 (147)目录7为 Active Directory 用户配置 iDRAC 智能卡登录 (148)为本地用户配置 iDRAC 智能卡登录 (148)使用智能卡登录 (149)章 10: 配置 iDRAC 以发送警报 (150)启用或禁用警报 (150)使用 Web 界面启用或禁用警报 (150)使用 RACADM 启用或禁用警报 (151)使用 iDRAC 设置公用程序启用或禁用警报 (151)筛选警报 (151)使用 iDRAC Web 界面筛选警报 (151)使用 RACADM 筛选警报 (152)设置事件警报 (152)使用 Web 界面设置事件警报 (152)使用 RACADM 设置事件警报 (152)设置警报复现事件 (152)使用 RACADM 设置警报复现事件 (152)使用 iDRAC Web 界面设置警报复现事件 (152)设置事件操作 (153)使用 Web 界面设置事件操作 (153)使用 RACADM 设置事件操作 (153)配置电子邮件警报、SNMP 陷阱或 IPMI 陷阱设置 (153)配置 IP 警报目标 (153)配置电子邮件警报设置 (155)配置 WS 事件 (157)配置 Redfish 事件 (157)监测机箱事件 (157)使用 iDRAC Web 界面监测机箱事件 (157)使用 RACADM 监测机箱事件 (157)警报消息 ID (158)章 11: iDRAC 9 Group Manager (161)Group Manager (161)摘要视图 (162)管理登录 (162)添加新用户 (162)更改用户密码 (163)删除用户 (163)配置警报 (163)导出 (163)查找到的服务器视图 (164)作业视图 (164)作业导出 (165)Group Information(组信息)面板 (165)组设置 (165)在所选服务器上的操作 (166)章 12: 管理日志 (168)8目录使用 Web 界面查看系统事件日志 (168)使用 RACADM 查看系统事件日志 (168)使用 iDRAC 设置公用程序查看系统事件日志 (168)查看 Lifecycle 日志 (169)使用 Web 界面查看 Lifecycle 日志 (169)使用 RACADM 查看 Lifecycle 日志 (170)导出 Lifecycle Controller 日志 (170)使用 Web 界面导出 Lifecycle Controller 日志 (170)使用 RACADM 导出 Lifecycle Controller 日志 (170)添加工作注释 (170)配置远程系统日志记录 (171)使用 Web 界面配置远程系统日志记录 (171)使用 RACADM 配置远程系统日志记录 (171)章 13: 监测和管理电源 (172)监测功率 (172)使用 Web 界面监测 CPU、内存和输入输出模块的性能指标 (172)使用 RACADM 监测 CPU、内存和输入输出模块的性能指标 (172)设置功耗的警告阈值 (173)使用 Web 界面设置功耗警告阈值 (173)执行电源控制操作 (173)使用 Web 界面执行电源控制操作 (173)使用 RACADM 执行电源控制操作 (173)功率限额 (174)刀片服务器中的功率上限 (174)查看和配置功率上限策略 (174)配置电源设备选项 (175)使用 Web 界面配置电源设备选项 (175)使用 RACADM 配置电源设备选项 (175)使用 iDRAC 设置公用程序配置电源设备选项 (175)启用或禁用电源按钮 (176)多向量冷却 (176)章 14: 对网络设备执行资源清册、监测和配置操作 (177)资源清册和监测网络设备 (177)使用 Web 界面监测网络设备 (177)使用 RACADM 监测网络设备 (177)连接视图 (177)资源清册和监测 FC HBA 设备 (179)使用 Web 界面监测 FC HBA 设备 (179)使用 RACADM 监测 FC HBA 设备 (179)动态配置虚拟地址、启动器和存储目标设置 (179)支持 I/O 标识优化功能的卡 (180)支持 I/O 标识优化功能的 NIC 固件版本 (181)iDRAC 设置为远程分配地址模式或控制台模式时的虚拟地址/远程分配地址和持久性策略行为 (181)FlexAddress 和 IO 标识的系统行为 (182)启用或禁用 I/O 标识优化功能 (183)配置持久性策略设置 (183)目录9章 15: 管理存储设备 (187)理解 RAID 概念 (188)什么是 RAID (188)为了可用性和性能组织数据存储 (189)选择 RAID 级别 (189)比较 RAID 级别的性能 (195)支持的控制器 (196)支持的机柜 (196)支持的存储设备功能的摘要 (196)资源清册和监测存储设备 (200)使用 Web 界面监测存储设备 (200)使用 RACADM 监测存储设备 (201)使用 iDRAC 设置公用程序监测背板 (201)查看存储设备拓扑 (201)管理物理磁盘 (201)分配或取消分配物理磁盘作为全局热备用 (202)将物理磁盘转换为 RAID 或非 RAID 模式 (202)擦除物理磁盘 (203)擦除 SED 设备数据 (204)重建物理磁盘 (205)管理虚拟磁盘 (205)创建虚拟磁盘 (205)编辑虚拟磁盘高速缓存策略 (207)删除虚拟磁盘 (207)检查虚拟磁盘一致性 (208)初始化虚拟磁盘 (208)加密虚拟磁盘 (208)分配或取消分配专用热备用 (209)使用 Web 界面管理虚拟磁盘 (211)使用 RACADM 管理虚拟磁盘 (211)RAID 配置功能 (212)管理控制器 (213)配置控制器属性 (213)导入或自动导入外部配置 (215)清除外部配置 (216)重设控制器配置 (217)切换控制器模式 (217)12Gbps SAS HBA 适配器操作 (219)监测驱动器上的预测性故障分析 (219)非 RAID 模式或 HBA 模式下的控制器操作 (219)在多个存储控制器上运行 RAID 配置作业 (220)管理保留的高速缓存 (220)管理 PCIe SSD (220)对 PCIe SSD 进行资源清册和监测 (221)准备移除 PCIe SSD (221)擦除 PCIe SSD 设备数据 (222)管理机柜或背板 (223)配置背板模式 (224)查看通用插槽 (226)10目录设置 SGPIO 模式 (226)设置机柜资产标签 (227)设置机柜资产名称 (227)选择要应用设置的操作模式 (227)使用 Web 界面选择操作模式 (227)使用 RACADM 选择操作模式 (228)查看和应用挂起操作 (228)使用 Web 界面查看、应用或删除挂起操作 (228)使用 RACADM 查看和应用挂起操作 (229)存储设备 - 应用操作方案 (229)闪烁或取消闪烁组件 LED (230)使用 Web 界面闪烁或取消闪烁组件 LED (230)使用 RACADM 闪烁或取消闪烁组件 LED (230)章 16: BIOS 设置 (232)章 17: 配置并使用虚拟控制台 (234)支持的屏幕分辨率和刷新率 (235)配置虚拟控制台 (235)使用 Web 界面配置虚拟控制台 (235)使用 RACADM 配置虚拟控制台 (235)预览虚拟控制台 (235)启动虚拟控制台 (236)使用 Web 界面启动虚拟控制台 (236)使用 URL 启动虚拟控制台 (236)使用 Java 或 ActiveX 插件禁用虚拟控制台或虚拟介质启动过程中的警告消息 (236)使用虚拟控制台查看器 (237)基于 HTML5 的虚拟控制台 (237)同步鼠标指针 (239)通过 Java 或 ActiveX 插件的虚拟控制台传递所有键击 (240)章 18: 使用 iDRAC 服务模块 (243)安装 iDRAC 服务模块 (243)从 iDRAC Express 和 Basic 安装 iDRAC Service Module (243)从 iDRAC Enterprise 安装 iDRAC Service Module (244)iDRAC Service Module 支持的操作系统 (244)iDRAC Service Module 监测功能 (244)从 iDRAC Web 界面使用 iDRAC Service Module (250)从 RACADM 中使用 iDRAC Service Module (250)将 iDRAC 服务模块用于 Windows Nano OS (250)章 19: 使用 USB 端口进行服务器管理 (251)通过直接 USB 连接访问 iDRAC 界面 (251)使用 USB 设备上的服务器配置文件配置 iDRAC (251)配置 USB 管理端口设置 (252)从 USB 设备导入服务器配置文件 (253)章 20: 使用 Quick Sync 2 (256)配置 iDRAC Quick Sync 2 (256)目录11使用 Web 界面配置 iDRAC Quick Sync 2 设置 (257)使用 RACADM 配置 iDRAC 快速同步 2 设置 (257)使用 iDRAC 设置公用程序配置 iDRAC Quick Sync 2 设置 (257)使用移动设备查看 iDRAC 信息 (257)章 21: 管理虚拟介质 (258)支持的驱动器和设备 (258)配置虚拟介质 (259)使用 iDRAC Web 界面配置虚拟介质 (259)使用 RACADM 配置虚拟介质 (259)使用 iDRAC 设置公用程序配置虚拟介质 (259)连接的介质状态和系统响应 (259)访问虚拟介质 (260)使用虚拟控制台启动虚拟介质 (260)不使用虚拟控制台启动虚拟介质 (260)添加虚拟介质映像 (261)查看虚拟设备详细信息 (261)访问驱动程序 (261)重设 USB (262)映射虚拟驱动器 (262)取消映射虚拟驱动器 (263)通过 BIOS 设置引导顺序 (263)启用一次性虚拟介质引导 (263)章 22: 安装和使用 VMCLI 公用程序 (265)安装 VMCLI (265)运行 VMCLI 公用程序 (265)VMCLI 语法 (265)访问虚拟介质的 VMCLI 命令 (266)VMCLI 操作系统 Shell 选项 (266)章 23: 管理 vFlash SD 卡 (267)配置 vFlash SD 卡 (267)查看 vFlash SD 卡属性 (267)启用或禁用 vFlash 功能 (268)初始化 vFlash SD 卡 (269)使用 RACADM 获取上次状态 (269)管理 vFlash 分区 (269)创建空白分区 (270)使用映像文件创建分区 (271)格式化分区 (271)查看可用分区 (272)修改分区 (272)连接或断开分区 (273)删除现有分区 (274)下载分区内容 (275)引导至分区 (275)章 24: 使用 SMCLP (276)12目录使用 SMCLP 的系统管理功能 (276)运行 SMCLP 命令 (276)iDRAC SMCLP 语法 (277)导航 MAP 地址空间 (280)使用 show 动词 (280)使用 -display 选项 (280)使用 -level 选项 (280)使用 -output 选项 (280)用法示例 (280)服务器电源管理 (281)SEL 管理 (281)映射目标导航 (282)章 25: 部署操作系统 (283)使用远程文件共享部署操作系统 (283)管理远程文件共享 (283)使用 Web 界面配置远程文件共享 (284)使用 RACADM 配置远程文件共享 (285)使用虚拟介质部署操作系统 (285)从多个磁盘安装操作系统 (285)在 SD 卡上部署嵌入式操作系统 (286)在 BIOS 中启用 SD 模块和冗余 (286)章 26: 使用 iDRAC 排除受管系统故障 (287)使用诊断控制台 (287)重设 iDRAC 并将 iDRAC 重设为默认值 (287)计划远程自动诊断 (288)使用 RACADM 计划远程自动诊断 (288)查看开机自检代码 (288)查看引导和崩溃捕获视频 (289)配置视频捕获设置 (289)查看日志 (289)查看上次系统崩溃屏幕 (289)查看系统状态 (290)查看系统前面板 LCD 状态 (290)查看系统前面板 LED 状态 (290)硬件故障指示灯 (290)查看系统运行状况 (291)在服务器状态屏幕上检查错误消息 (291)重新启动 iDRAC (291)使用 iDRAC Web 界面重设 iDRAC (291)使用 RACADM 重设 iDRAC (291)擦除系统和用户数据 (292)将 iDRAC 重设为出厂默认设置 (292)使用 iDRAC Web 界面将 iDRAC 重设为出厂默认设置 (292)使用 iDRAC 设置公共程序将 iDRAC 重设为出厂默认设置 (293)章 27: iDRAC 中的 SupportAssist 集成 (294)SupportAssist 注册 (294)目录13安装服务模块 (295)服务器操作系统代理信息 (295)SupportAssist (295)服务请求门户 (295)集合日志 (295)生成 SupportAssist 收集 (295)使用 iDRAC Web 界面手动生成 SupportAssist 收集 (296)设置 (296)收集设置 (297)联系信息 (297)章 28: 常见问题 (298)系统事件日志 (298)网络安全性 (299)Active Directory (299)单一登录 (300)智能卡登录 (301)虚拟控制台 (301)虚拟介质 (304)vFlash SD 卡 (306)SNMP 验证 (306)存储设备 (306)iDRAC 服务模块 (306)RACADM (308)永久设置默认密码至 calvin (308)其他 (309)章 29: 使用案例场景 (313)排除受管系统不可访问的故障 (313)获取系统信息和访问系统运行状况 (313)设置警报和配置电子邮件警报 (314)查看并导出系统事件日志和生命周期日志 (314)用于更新 iDRAC 固件的界面 (314)执行正常关机 (314)创建新的管理员用户帐户 (314)启动服务器远程控制台和挂载 USB 驱动器 (315)使用连接的虚拟介质和远程文件共享安装裸机操作系统 (315)管理机架密度 (315)安装新的电子许可证 (315)在一次主机系统重新引导中为多个网卡应用 I/O 标识配置设置 (315)14目录1概览Integrated Dell Remote Access Controller (iDRAC) 设计用于提高系统管理员的工作效率和 Dell EMC 服务器的整体可用性。
Dell服务器iDRAC(IPMI)如何连接管理服务器
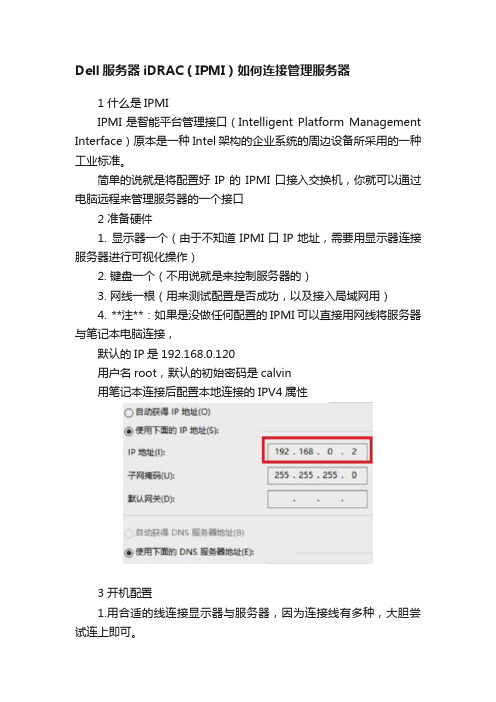
Dell服务器iDRAC(IPMI)如何连接管理服务器1 什么是IPMIIPMI是智能平台管理接口(Intelligent Platform Management Interface)原本是一种Intel架构的企业系统的周边设备所采用的一种工业标准。
简单的说就是将配置好IP的IPMI口接入交换机,你就可以通过电脑远程来管理服务器的一个接口2 准备硬件1. 显示器一个(由于不知道IPMI口IP地址,需要用显示器连接服务器进行可视化操作)2. 键盘一个(不用说就是来控制服务器的)3. 网线一根(用来测试配置是否成功,以及接入局域网用)4. **注**:如果是没做任何配置的IPMI可以直接用网线将服务器与笔记本电脑连接,默认的IP是192.168.0.120用户名root,默认的初始密码是calvin用笔记本连接后配置本地连接的IPV4属性3 开机配置1.用合适的线连接显示器与服务器,因为连接线有多种,大胆尝试连上即可。
2.插上鼠标,服务器开机3.当服务器出现Press <Ctrl-E> for Remote Access Setup within 5 sec...时同时按下Ctrl键和E键**注:** 因服务不同按键略有差异,主要看到Remote Access Setup within 5 sec.按下这些关键字所对应的按键按下就可进入iDRAC配置界面(1)我进入的是iDRAC6的配置界面,如下图:(2)配置界面:**将iDRAC6 LAN 和IPMI Over LAN这两项状态都设为On**3)按下LAN Parameters进行IP的配置(4)根据交换机可分配的IP网段进行配置,正常情况下IP、网关、DNS缺一不可(5)按下LAN UserConfiguration进行web登录时用户名和密码的设置最后按Esc退出保存!# 4 验证1.此时将服务器的IPMI口和笔记本网线口连接即可验证(部分服务器会标出,未标出的可以看与其他网线口略有不同的就是IPMI口了)用笔记本连接后可以直接打开浏览器输入你设置的IP地址进行访问,如不能访问,请检查你的以太网连接的IPV4是不是自动获取IP2.将服务器的IPMI接入到交换机,交换机做一些简单的配置即可实现远程连接了。
Dell EMC PowerEdge Rack Servers快速参考指南说明书

Dell EMC PowerEdge rack servers help you build a modern infrastructure that minimizes IT challenges and drives business success. Choose from a complete portfolio of 1, 2, and 4-socket rack servers to deliver high core density for your traditional applications, virtualization, and cloud-native workloads. Enhanced memory speeds, faster NVMe storage options,1 and BIOS tuning allows you to match performance to your workload for ultimate efficiency.15th generation of PowerEdge ServersR750Powerful compute forcommon businessR940R940xaR740R740xd2“Dell EMC PowerEdge servers are the foundation of the work we do here. They provide the automation, the security, the flexibility, and the reliability to make sure that we can continue to focus on what we do best as a company.”- Ryan Gariepy Co-founder and Chief Technology Officer, OTTO Motors“We can deploy our PowerEdge servers in minutes because iDRAC is always on and integrates with Dell EMC OpenManage...”- Aldo Armiento, Chief Technology Officer, Immobiliare.it“We’ll save 35 percent on a five-year TCO with the Dell EMC VDI solution. The PowerEdge rack servers were ready to go out of the box for hosting our storage requirements. We saved 30 percent compared to a standalone SAN.”- Bruce Salisbury IT Director, Capital Area Human Services1 Not all features are available on all platforms.2Drives use hybrid carrier to fit in 3.5” drive bay. (For the R740xd2 - a hybrid configuration is available with up to 10 2.5” SSDs)14th generation of PowerEdge Serversexperts to lead deployments from basic hardware installations through planning, configuration and complex integrations.Manage: The ProSupport Enterprise Suite ensures 24x7 access to senior ProSupport engineers along with automated proactive and predictive service enabled by SupportAssist. Our personalized service and preventative measures help you get ahead of problems before they happen.Contacta Dell EMC ExpertView more resourcesLearn more aboutDell EMC server solutionsOctober 2021 Rev. A02。
idrac使用手册

idrac使用手册摘要:idrac 使用手册一、idrac 简介二、idrac 安装与配置1.安装前的准备工作2.安装过程及注意事项3.配置idrac三、idrac 基本功能1.远程控制2.硬件监控3.系统管理四、idrac 高级功能1.虚拟媒体2.虚拟KVM3.自动化运维五、idrac 的安全与优化1.安全设置2.性能优化六、常见问题与解决方案1.无法连接到idrac2.虚拟媒体无法使用3.系统管理功能异常七、总结与展望正文:【idrac 简介】idrac(Integrated Dell Remote Access Controller)是戴尔(Dell)服务器提供的一款远程管理工具,通过idrac,用户可以实现对服务器的远程控制、硬件监控、系统管理等操作,大大提高了服务器管理的便捷性和效率。
【idrac 安装与配置】【安装前的准备工作】在安装idrac 之前,请确保服务器已安装操作系统,并确保操作系统已配置好网络参数。
同时,需要获取服务器的idrac 许可证密钥,以便完成安装。
【安装过程及注意事项】1.访问戴尔官网,下载适用于服务器型号的idrac 软件。
2.将下载的软件上传至服务器,并通过命令行或图形界面运行安装程序。
3.按照安装向导的提示,完成idrac 的安装。
4.安装过程中,请确保服务器与客户端之间的网络连接畅通。
【配置idrac】1.打开服务器管理界面,进入idrac 的配置页面。
2.设置管理员密码,以保护idrac 的安全。
3.配置idrac 的网络设置,使其与服务器操作系统网络配置保持一致。
4.设置虚拟媒体,以便通过idrac 访问服务器的光驱、软驱等设备。
【idrac 基本功能】【远程控制】通过idrac,用户可以随时随地通过网络远程控制服务器,查看服务器状态,执行命令行操作等。
【硬件监控】idrac 提供实时的硬件监控功能,包括CPU、内存、硬盘、风扇等硬件设备的运行状态,帮助用户及时发现并解决问题。
Dell OpenManage 底板管理控制器公用程序 4.5 用户指南说明书

Dell OpenManage 底板管理控制器公用程序 4.5 用户指南配置 Managed System: Dell OpenManage 底板管理控制器公用程序 4.5 用户指南这些选项包括COM1、COM3、"BMC Serial"(BMC 串行)、BMC NIC、"Off"(关闭)和RAC(如果系统上已安装了 RAC 选件)。
如果使用 BMC,则串行端口 1 会使用COM1地址,而通信可以通过串行端口,也可以通过集成的共享 NIC。
RAC 控制只使用COM1地址。
当控制台重定向被设置为使用串行端口 1 时,不会有"Off"(关闭)和COM3选项。
111如果打算通过串行电缆连接访问 BMC,请选择"BMC Serial"(BMC 串行)。
111如果正在使用 SOL Proxy 并且准备通过共享 LAN 访问 BMC,请选择BMC NIC。
111按 <Enter> 返回"System Setup"(系统设置)屏幕。
111使用上下箭头键导航至"Console Redirection"(控制台重定向)字段,然后按 <Enter>。
111使用上下箭头键导航至"Console Redirection"(控制台重定向)选项,然后使用空格键将控制台重定向功能设置为"Serial Port 1"(串行端口 1)。
还可以根据情况启用"Redirection after Boot"(引导后重定向)。
111使用上下箭头键导航至"Failsafe Baud Rate"(故障安全波特率)选项,然后使用空格键设置控制台故障安全波特率(如果适用)。
1111使用上下箭头键导航至"Remote Terminal Type"(远程终端类型)选项,然后使用空格键选择VT 100/VT 200或ANSI(如果适用)。
戴尔易安信远程访问控制器(iDRAC)用户指南说明书

###################################################################### Integrated DELL(TM) REMOTE ACCESS CONTROLLER (iDRAC)######################################################################This document contains updated information about the Integrated DellRemote Access Controller (iDRAC).For more information about iDRAC, including installation andconfiguration information, see the "Integrated Dell Remote AccessController User's Guide" and the "Dell OpenManage(TM) ServerAdministrator User's Guide." These documents are located on yourProduct Documentation CD and on the Dell Support site at"."######################################################################TABLE OF CONTENTS######################################################################This file contains the following sections:* Criticality* Minimum Requirements* Release Highlights* Known Issues for iDRAC version 1.0* Known Issues for Documentation###################################################################### CRITICALITY######################################################################1 - Urgent###################################################################### MINIMUM REQUIREMENTS######################################################################The following subsections list operating systems that are compatiblewith the iDRAC.====================================================================== SUPPORTED SYSTEMS====================================================================== iDRAC is supported on the following Dell PowerEdge(TM) systems in theDell PowerEdge M1000-e system enclosure:* Dell PowerEdge M600 and M605====================================================================== SUPPORTED MANAGED SERVER OPERATING SYSTEMS====================================================================== The iDRAC is supported by the following operating systems:* Microsoft(R) Windows Server(R) 2003 familyThe Windows Server 2003 family includes- Windows Server 2003 R2 (Enterprise and Standard Editions) with SP2(32-bit).- Windows Server 2003 (Web Edition) with SP2 (32-bit).- Windows Server 2003 R2 Standard and Enterprise Edition with SP2(32-bit x86_64).- Windows Server 2003 Standard and Enterprise Editions x64 Editionswith SP2.- Windows Storage Server 2003 R2 Express and Workgroup x64 Editions(x86_64).* Windows Vista(R) Gold Business and Enterprise Editions.* Microsoft Windows Server 2008 Web, Standard, and Enterprise Editions(32-bit x86)* Microsoft Windows Server 2008 Web, Standard, Enterprise andDatacenter (x64) EditionsNOTE: When installing Windows Server 2003 with SP1, be aware ofchanges to DCOM security settings. For more information, seearticle 903220 from the Microsoft Support website at"/kb/903220."* Red Hat(R) Enterprise Linux WS, ES, and AS (version 3)(x86 and x86_64).* Red Hat(R) Enterprise Linux WS, ES, and AS (version 4)(x86 and x86_64).* Red Hat(R) Enterprise Linux 5 (x86 and x86_64).* SUSE(R) Linux Enterprise Server 9 with Update 3 (x86_64).* SUSE Linux Enterprise Server 10 (x86_64) Gold.====================================================================== SUPPORTED WEB BROWSERS====================================================================== * Microsoft Internet Explorer 6.0 (32-bit) with SP2 for Windows XP andWindows 2003 R2 SP2 only.* Microsoft Internet Explorer 7.0 for Windows Vista, Windows XP, andWindows 2003 R2 SP2 only.* Mozilla Firefox 1.5 (32-bit) on SUSE Linux (version 10) only.* Mozilla Firefox 2.0 (32-bit).=============================================FIRMWARE VERSIONS=============================================* iDRAC Firmware Version: 1.11###################################################################### RELEASE HIGHLIGHTS (FIRMWARE VERSION 1.11)###################################################################### iDRAC version 1.11 has key fixes for Active Directory, Services(SSH, SOL), and in addition, it supports the FlexAddress feature.###################################################################### RELEASE HIGHLIGHTS (FIRMWARE VERSION 1.03)###################################################################### Enhanced TOE key detection.###################################################################### RELEASE HIGHLIGHTS (FIRMWARE VERSION 1.02)###################################################################### A few fixes in the version display, SM-CLP, last crash screen page etcareas are included in this release.###################################################################### RELEASE HIGHLIGHTS (FIRMWARE VERSION 1.0)###################################################################### * Initial release of iDRAC firmware.iDRAC Management Features for the initial release include:* Dynamic Domain Name System (DDNS) registration* Remote system management and monitoring using a Web interface, thelocal RACADM command line interface via console redirection, and theSM-CLP command line over a telnet/SSH connection.* Support for Microsoft Active Directory authentication --Centralizes iDRAC user IDs and passwords in Active Directory usingthe standard schema or an extended schema.* Console Redirection — Provides remote system keyboard,video, and mouse functions.* Virtual Media -- Enables a managed server to access a localmedia drive on the management station or ISO CD/DVD images on anetwork share.* Monitoring -- Provides access to system information and status ofcomponents.* Access to system logs -- Provides access to the system event log,the iDRAC log, and the last crash screen of the crashed orunresponsive system that is independent of the operating system.* Dell OpenManage(TM) integration -- Enables you to launch the iDRACWeb interface from Dell OpenManage Server Administrator or ITAssistant.* iDRAC alert -- Alerts you to potential managed node issues throughan email message or SNMP trap.* Remote power management -- Provides remote power managementfunctions, such as shutdown and reset, from a management console.* Intelligent Platform Management Interface (IPMI) support.* Secure Sockets Layer (SSL) encryption -- Provides secure remotesystem management through the Web interface.* Password-level security management -- Prevents unauthorized accessto a remote system.* Role-based authority -- Provides assignable permissions fordifferent systems management tasks.##################################################################### KNOWN ISSUES FOR iDRAC##################################################################### This section provides additional information about known issues withthe iDRAC Firmware version 1.0.* Configuring iDRAC to use Static IP using 'syscfg' utilityGiven below is the method to use the syscfg utility to set the iDRACto use a static IP address. It has to be done in 2 steps.Step 1: "syscfg lcp --ipaddrsrc=static"Wait at least 5 seconds. After this time, the change to static IPwill be in effect and the next syscfg command will succeed.Step 2: "syscfg lcp --gateway=(gateway IP) --ipaddress=(valid IP address)--subnetmask=255.255.255.0"* Manual OS Installation REQUIREMENT when using 'virtual floppy' Using vMedia to do a Windows / Other installation, there is one thing REQUIRED to enable completing the installation.When there is a need to install drivers using a floppy disk - ENSUREthe 'Virtual Floppy' device is the FIRST device in the 'BootSequence'. Use BIOS Setup screens to ensure this.This way, the drivers in the floppy can be used to install the storageetc drivers and complete the Windows / Other installation.* Configuring the 'Host Name String' using the iDRAC ConfigurationUtilityWith OMSA installed -OMSA takes precedence. OMSA sets the 'Host Name String' every time it starts up. Given above, even if 'Host Name String' is set using theiDRAC Configuration Utility', it will be overwritten by OMSA when it starts up.With OMSA NOT installed -The iDRAC Configuration Utility can be used to configure the 'HostName String'.* Accessing remote floppy disks and CD-ROMs from (VMWare) VMs Accessing remote floppy disks and CD-ROMs from (VMWare) VMs is NOT supported.Only devices directly connected to an ESX server or a floppy or CD-ROM ISO image present in the ESX Service Console can be made accessible to the VM. Avoid this issue by creating an image of the floppy or CD-ROM and copying it to the Service Console.* Updating iDRAC using DOS update utility, from a PXE network setup The iDRAC can be updated using the DOS utility when DOS is booted using PXE. However, the new FW image has to be on a local media on the server for this to work properly. Local media can be a RAMDISK, HD or USB key on the server. Alternatively, the update of iDRACs onmultiple servers has to be sequenced, i.e. done one server after theother, with the 1st completing update and the 2nd starting update andso on to 3rd after 2nd is done, 4th after 3rd is done etc.* Usage of virtual CD-ROM in SLES 9Use the auto-attach checkbox in the vMedia area of the Web GUI of theiDRAC when using CD-ROM devices in SLES 9.Another way to do the same when using SM-CLP is to set the/system1/sp1/oemdell_vmservice1 enabledstate to VMEDIA_AUTO_ATTACH.* Setting of iDRAC time, after an iDRAC FW updateWith OMSA installed -When iDRAC firmware is updated, with OMSA installed, iDRAC's time isset by OMSA every 4 hours. This means about 4 hours after iDRAC isupdated,it will receive the correct time from OMSA. From that point,the iDRAC will use that time for time stamping events in SEL, etc.With OMSA _not_ installed -When iDRAC firmware is updated, with OMSA not installed, iDRAC's time is setby BIOS. For that to happen, the server has to be power cycled. Oncethe power cycle is completed, i.e., the server is back up, the iDRAC willreceive the correct time from BIOS, and that time will be used fortime stamping events in SEL, etc.* RACADM restore default configuration behaviorThe racresetcfg command in RACADM restores all properties except cfgDNSRacName in the cfgLanNetworking group to their default values.* Configuring iDRAC using RACADM configThe actual time the user needs to wait after executing the racresetcfg commandwithin racadm may vary depending on the network speed.* iDRAC Media Redirection using floppy disks on Vista management stationwith IE7 and ActiveXThe iDRAC's IP address needs to be added to the 'Trusted Sites' list,before launching the Console Redirection session on a managementstation running Vista with IE7.1 Click Tools-> Internet Options-> Security-> Trusted sites.2 Click Sites and enter the IP address or DNS name of the iDRAC.3 Click Add.* Configuring specific DNS parameters using 'racadm config -f <filename>'DHCP has to be enabled on the iDRAC for the following two DNSparameters to be configurable, using 'racadm config -f <filename>' -1) cfgDNSServersFromDHCP, 2) cfgDNSDomainNameFromDHCP.* Behavior of the iDRAC Virtual Media functionality, when the media is removed On Windows -Once the media is removed, the Explorer window(s) for this media donot close by themselves.User action IS required. Please close the Explorer window(s), once themedia is removed.On Linux -Once the media is removed, the file browser window(s) for this mediado close by themselves.User action is NOT required.* Saving the image of the 'Last Crash Screen' from the iDRAC GUIFirst, go to the 'Last Crash Screen' page on the iDRAC GUI. Then:Internet Explorer -To save the image of the 'Last Crash Screen', right-click on theimage and click 'Save Picture As'. Then, browse to a location and savethe image.Firefox -To save the image of the 'Last Crash Screen', right-click on theimage and click 'Save Image As'. Then, browse to a location and savethe image.* Using the iVMCLI tool from within a system running Windows VistaTo use iVMCLI from within a system running Windows Vista -The user has to start up the 'cmd' with 'Run as Administrator'.(iVMCLI requires the user has 'administrator' privileges when it is used.)Aside -User can log in as a non-admin user, but when using iVMCLI, the userhas to start 'cmd' with 'Run as Administrator' thereby giving themadmin privileges to enable using iVMCLI.###################################################################### KNOWN ISSUES FOR DOCUMENTATION###################################################################### This section provides additional information about known issues withthe iDRAC Firmware version 1.0 User's Guide.* None###################################################################### Information in this document is subject to change without notice.(C) 2008 Dell Inc. All rights reserved.Reproduction in any manner whatsoever without the written permissionof Dell Inc. is strictly forbidden.Trademarks used in this text: "Dell", "Dell OpenManage", and"PowerEdge" are trademarks of Dell Inc.; "Microsoft", "Windows","Windows Server", "Windows Vista", and "Active Directory" are trademarksor registered trademarks of Microsoft Corporation; "Intel" is atrademark of Intel Corporation; "SUSE" is a registered trademark ofNovell, Inc.; "Red Hat" is a registered trademark of Red Hat, Inc.Other trademarks and trade names may be used in this document to referto either the entities claiming the marks and names or their products.Dell Inc. disclaims any proprietary interest in trademarks and tradenames other than its own.June 2008。
idrac使用手册

idrac使用手册
IDRAC(Integrated Dell Remote Access Controller)是戴尔服务器的远程管理工具。
它允许用户通过网络远程管理和监控戴尔服务器,包括服务器开关、电源控制、远程控制台访问和硬件监控等功能。
以下是IDRAC使用手册的基本内容和功能:
1. 登录IDRAC:打开web浏览器,输入IDRAC的IP地址或
域名,然后输入您的用户名和密码进行登录。
2. 远程控制台:IDRAC提供了虚拟控制台功能,允许您远程
访问服务器的控制台,就像坐在服务器旁边一样。
您可以通过虚拟控制台来查看和操作服务器的操作系统。
3. 电源控制和开关:IDRAC允许您对服务器的电源进行控制,包括开机、重启、关闭等操作。
4. 硬件监控:IDRAC可以监控服务器的各种硬件,包括CPU、内存、硬盘、电源等。
您可以查看实时数据和日志,以便及时发现和解决硬件故障。
5. 警报和通知:IDRAC可以配置警报和通知,以便在服务器
出现故障或异常时及时通知管理员。
您可以通过电子邮件、短信或SNMP等方式接收通知。
6. 远程虚拟媒体:通过IDRAC,您可以将远程计算机上的光
盘镜像或USB设备映射到服务器上,从而远程安装操作系统或进行其他磁盘操作。
7. 远程BIOS访问:IDRAC还允许您通过远程方式访问服务器的BIOS设置,以便进行BIOS配置和调整。
这些只是IDRAC使用手册的一部分内容,您可以根据具体情况和需求进行更详细的了解和配置。
请注意,不同型号的戴尔服务器和IDRAC版本可能会略有不同,建议您根据具体型号和版本查阅相关的使用手册和文档。
戴尔易安信 PowerEdge R730xd 服务器 RACADM 命令行参考指南说明书

RACADM Command Line Reference Guide Addendum for Carrier Grade ChassisManagement ControllerNotes and CautionsNOTE: A NOTE indicates important information that helps you make better use of your computer.CAUTION: A CAUTION indicates potential damage to hardware or loss of data if instructions are not followed.____________________Information in this publication is subject to change without notice.©2012Dell Inc.All rights reserved.Reproduction of these materials in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden. Trademarks used in this text: Dell™, the DELL logo, FlexAddress™, OpenManage™, PowerEdge™, and PowerConnect™ are trademarks of Dell Inc. Microsoft®, Active Directory®, Internet Explorer®, Windows®, Windows Server®, and Windows Vista®are either trademark s or registered trademarks of Microsoft Corporation in the United States and other countries. Red Hat® and Red Hat Enterprise Linux® are registered trademarks of Red Hat, Inc. in the United States and other countries. Novell® is a registered trademark and SUSE ™ is a trademark of Novell Inc. in the United States and other countries. Intel® is a registered trademark of Intel Corporation. UNIX® is a registered trademark of The Open Group in the United States and other countries. Avocent® is a trademark of Avocent Corporation. OSCAR® is a registered trademark of Avocent Corporation or its affiliates.Copyright 1998-2006 The OpenLDAP Foundation. All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted only as authorized by the OpenLDAP Public License. A copy of this license is available in the file LICENSE in the top-level directory of the distribution or, alternatively, at /license.html. OpenLDAP is a registered trademark of the OpenLDAP Foundation. Individual files and/or contributed packages may be copyrighted by other parties and subject to additional restrictions. This work is derived from the University of Michigan LDAP v3.3 distribution. This work also contains materials derived from public sources. Information about OpenLDAP can be obtained at /. Portions Copyright 1998-2004 Kurt D. Zeilenga. Portions Copyright 1998-2004 Net Boolean Incorporated. Portions Copyright 2001-2004 IBM Corporation. All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted only as authorized by the OpenLDAP Public License. Portions Copyright 1999-2003 Howard Y.H. Chu. Portions Copyright 1999-2003 Symas Corporation. Portions Copyright 1998-2003 Hallvard B. Furuseth. All rights reserved. Redistribution and use in source and binary forms, with or without modification, are permitted provided that this notice is preserved. The names of the copyright holders may not be used to endorse or promote products derived from this software without their specific prior written permission. This software is provided "as is'' without express or implied warranty. Portions Copyright (c) 1992-1996 Regents of the University of Michigan. All rights reserved. Redistribution and use in source and binary forms are permitted provided that this notice is preserved and that due credit is given to the University of Michigan at Ann Arbor. The name of the University may not be used to endorse or promote products derived from this software without specific prior written permission. This software is provided "as is'' without express or implied warranty.Other trademarks and trade names may be used in this publication to refer to either the entities claiming the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own.2012 - 11RACADM Command Line Reference Guide Addendum for Carrier Grade CMC 3OverviewThis addendum provides the changes to the RACADM Command Line Interface for Carrier Grade CMC. The controller firmware Carrier Grade CMC for NEBS enabled chassis requires changes to the command line interface due to the use of DC input power. This document only provides the updated RACADM commands for DC input power operation. For all other commands, see the RACADM Command Line Reference Guide for iDRAC7 1.00.00 and CMC 4.1 available at /manuals .The following racadm commands are updated for Carrier Grade CMC:•getpbinfo •getsensorinfogetpbinfoExample[Power Budget Status]System Input Power = 775 WPeak System Power = 775 WPeak System Power Timestamp = 09:21:22 07/13/2012Minimum System Power = 733 WMinimum System Power Timestamp = 09:18:28 07/13/2012Overall Power Health = OKRedundancy = YesSystem Input Power Cap = 16685 WRedundancy Policy = Grid Redundancy Dynamic PSU Engagement Enabled = NoSystem Input Max Power Capacity = 8916 WInput Redundancy Reserve = 8916 WInput Power Allocated to Servers = 910 WInput Power Allocated to Chassis Infrastructure = 216 WTotal Input Power Available for Allocation = 7057 WStandby Input Power Capacity = 0 WServer Based Power Management Mode = No Description Displays power budget status information.To use this subcommand, you must have CMC Login User privilege.Synopsis racadm getpbinfoMax Power Conservation Mode = NoServer Performance Over Power Redundancy = No[Chassis Power Supply Status Table]<Name> <Model> <Power State> <Input Current> <Input Volts> <Output Rated Power>PS1 OHPTJR Online 0.9 A -56.0 2700 W PS2 OHPTJR Online 0.8 A -56.0 2700 W PS3 OHPTJR Online 3.3 A -55.9 2700 W PS4 OHPTJR Online 3.9 A -55.9 2700 W PS5 OHPTJR Online 3.4 A -56.0 2700 W PS6 OHPTJR Online 1.8 A -56.0 2700 W[Server Module Power Allocation Table]<Slot#> <Server Name> <Power State> <Allocation> <Priority> <Blade Type>1 SLOT-01 N/A N/A 1 N/A2 SLOT-02 N/A N/A 9 N/A3 SLOT-03 ON 245 W 1 PowerEdgeM6004 SLOT-04 ON 196 W 1 PowerEdgeM6055 SLOT-05 ON 169 W 1 PowerEdgeM6006 SLOT-06 N/A N/A 1 N/A7 SLOT-07 N/A N/A 1 N/A8 SLOT-08 N/A N/A 1 N/A9 SLOT-09 N/A N/A 1 N/A10 SLOT-10 ON 158 W 1 PowerEdgeM60511 SLOT-11 N/A N/A 1 N/A12 SLOT-12 N/A N/A 1 N/A13 SLOT-13 ON 142 W 1 PowerEdgeM60514 SLOT-14 N/A N/A 1 N/A15 SLOT-15 N/A N/A 1 N/A16 SLOT-16 N/A N/A 1 N/A[Server Module Power Allocation Table]<Slot#><Server Name><PowerState><Allocation><Priority><Blade Type>1 SLOT-01 N/A N/A 5 N/A2 SLOT-02 OFF 0W 5 PowerEdgeM8053 SLOT-03 ON 164 W5 N/A4 SLOT-04 ON 155W 55 SLOT-05 ON 180W 56 SLOT-06 ON 180 W 5 PowerEdgeM6007 SLOT-07 ON 170W 58 SLOT-08 N/A N/A 5 N/A9 SLOT-09 N/A N/A 5 N/A10 SLOT-10 Extension(2) N/A 5 N/A11 SLOT-11 N/A N/A 5 N/A12 SLOT-12 ON 125W 5 PowerEdgeM60013 SLOT-13 N/A N/A 5 N/A14 SLOT-14 ON 342 W 5 N/A4RACADM Command Line Reference Guide Addendum for Carrier Grade CMCRACADM Command Line Reference Guide Addendum for Carrier Grade CMC 515 SLOT-15 ON 140W 516 SLOT-16 ON 125 W 5 N/AgetsensorinfoExamples<racadm getsensorinfo <senType> <Num> <sensorName> <status> <reading> <units> <lc> <uc>FanSpeed 1 Fan-1 OK 4908 rpm 2522 14500FanSpeed 2 Fan-2 OK 4882 rpm 2522 14500FanSpeed 3 Fan-3 OK 4932 rpm 2522 14500FanSpeed 4 Fan-4 OK 4930 rpm 2522 14500FanSpeed 5 Fan-5 OK 4988 rpm 2522 14500FanSpeed 6 Fan-6 OK 4993 rpm 2522 14500FanSpeed 7 Fan-7 OK 4923 rpm 2522 14500FanSpeed 8 Fan-8 OK 4901 rpm 2522 14500FanSpeed 9 Fan-9 OK 4876 rpm 2522 14500<senType> <Num> <sensorName> <status> <reading> <units> <lc> <uc>Temp 1 Ambient_Temp OK 21 celcius N/A 40<senType><Num><sensorName><status><AC-OK status>PWR1PS-1Online OK PWR2PS-2Online OK PWR3PS-3Online OK PWR4PS-4Online OK PWR5PS-5Online OK PWR6PS-6 Online OK <senType><Num><sensorName><status>Cable1IO-Cable OK Cable 2FPC-Cable OK Description Displays status for system sensors.To use this subcommand, you must have CMC Login User privilege.Synopsisracadm getsensorinfo6RACADM Command Line Reference Guide Addendum for Carrier Grade CMC。
Dell PowerEdge服务器(14代例R740 T640)通过IDRAC9配置RAID的方法
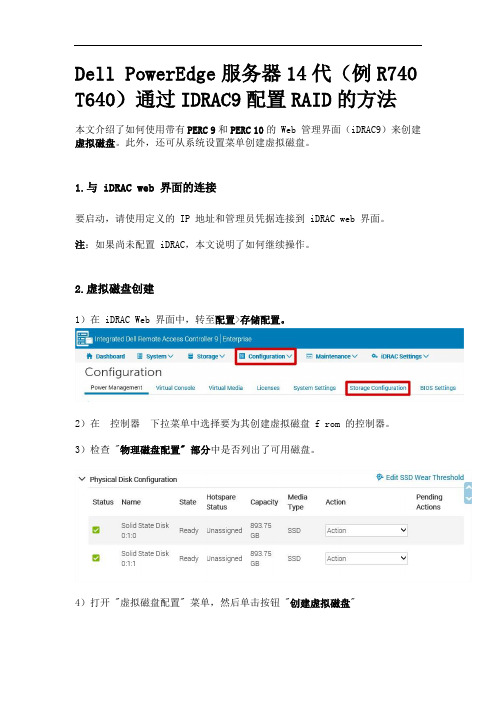
Dell PowerEdge服务器14代(例R740 T640)通过IDRAC9配置RAID的方法本文介绍了如何使用带有PERC 9和PERC 10的 Web 管理界面(iDRAC9)来创建虚拟磁盘。
此外,还可从系统设置菜单创建虚拟磁盘。
1.与 iDRAC web 界面的连接要启动,请使用定义的 IP 地址和管理员凭据连接到 iDRAC web 界面。
注:如果尚未配置 iDRAC,本文说明了如何继续操作。
2.虚拟磁盘创建1)在 iDRAC Web 界面中,转至配置>存储配置。
2)在控制器下拉菜单中选择要为其创建虚拟磁盘 f rom 的控制器。
3)检查 "物理磁盘配置" 部分中是否列出了可用磁盘。
4)打开 "虚拟磁盘配置" 菜单,然后单击按钮 "创建虚拟磁盘"5)将显示 "creator" 向导以配置虚拟磁盘属性。
在容量字段中,输入虚拟磁盘的大小。
在选择磁盘的情况下,将显示最大大小,然后更新。
准备就绪时,单击 "添加到挂起操作"。
注:您可以在磁盘名称中使用字母数字字符、空格、连字符和下划线。
在创建虚拟磁盘时,您输入的任何其他特殊字符都将被删除。
6)消息 "RAC0685:已为此创建虚拟磁盘创建挂起操作" 操作将显示,以确认任务创建。
SEO7)要执行此创建任务,请导航至页面底部并选择立即应用。
如果需要,可以计划任务。
8) raid 配置任务开始。
可以在菜单维护>作业队列中监视状态。
9)任务完成后,虚拟磁盘将在菜单存储>虚拟磁盘中列出。
虚拟磁盘现在可以使用,并且需要由您的操作系统格式化。
对于采用 iDRAC6/7/8 的较旧的旧系统,此选项不可用,您必须在 Raid BIOS 中创建或使用 Dell Open Manage Server Administrator。
戴尔服务器iDRAC6远程管理卡使用手册

戴尔服务器iDRAC6远程管理卡使用手册iDRAC6 Express 管理功能iDRAC6 Express 提供以下管理功能:•动态域名系统 (DDNS) 注册•使用 Web 界面和 SM-CLP 命令行通过 Serial、Telnet 或 SSH 连接进行远程系统管理和监控•支持 Microsoft® Active Directory® 验证—使用扩展模式或标准模式将 iDRAC6 用户 ID 和密码集中在 Active Directory 中•监控—提供对系统信息和组件状态的访问•访问系统日志—能够访问系统事件日志、iDRAC6 日志和崩溃或无响应系统的上次崩溃屏幕,而不受操作系统状态的影响•Dell OpenManage™ 软件集成—使您能够从 Dell OpenManage Server Administrator 或 Dell OpenManage IT Assistant 启动 iDRAC6 Web 界面•iDRAC6 警报—通过电子邮件信息或 SNMP 陷阱提示潜在受管节点问题•远程电源管理—从管理控制台提供远程电源管理功能,比如关机和重设•智能平台管理接口 (IPMI) 支持•安全套接字层 (SSL) 加密—通过 Web 界面提供安全的远程系统管理•密码级别安全性管理—防止未授权访问远程系统•基于角色的权限—为不同的系统管理任务提供可分配的权限•IPv6 支持—增加 IPv6 支持,例如:允许使用 IPv6 地址访问 iDRAC6 Web 界面、指定 iDRAC NIC 的 IPv6 地址、指定目标号码以配置 IPv6 SNMP 警报目标。
•WS-MAN 支持—使用 Web Services for Management (WS-MAN) 协议提供网络可访问管理。
•SM-CLP 支持—增加服务器管理命令行协议 (SM-CLP) 支持,这提供了系统管理 CLI 实施的标准。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
cfgNicEnable=1
cfgNicIpAddress=10.40.95.2
cfgNicNetmask=255.255.255.0
按Esc键退出系统设置程序以便完成系统设置程序配置.
一些型号的Dell PowerEdge系统(800,1425SC,1800,1850,1855,2800,2850,6800,
6850)上RAC的功能是由BMC来实现的.Dell PowerEdge系统底板管理控制器(BMC)
通过与主机板上的不同传感器通信来监视系统是否有严重事件,并在某些参数超
DELL RAC使用指南
2006.04.11
Dell Remote Access Card III(DRAC III)、DRAC III/XT、DRAC 4、
Dell Embedded Remote Access Controller(ERA)和嵌入式远程访问选件
(ERA/O),以上控制器将被统称为"RAC".RAC用于为Dell PowerEdge系统提
出其预置阈值时发出警报和日志事件.BMC支持工业标准的Intelligent Platform
Management Interface(IPMI)规范,可以实现远程配置、监测和恢复系统.
RAC通过与系统的ESM通信,可报告有关电压、温度和风扇速率的警告或错误.
此外,RAC可以记录系统崩溃的可能原因,并保存最新的崩溃屏幕(仅限于运行
cfgNicGateway=10.40.95.254
cfgNicUseDhcp=0
修改设置使RAC固件串口生效,串口为COM2或RAC,这样就可以通过超级终端连上
COM2口或者RAC口
C:\WINNT\system32>racadm -r10.40.95.2 -uroot -pcalvin config -g
cfgNicEnable=1
cfgNicIpAddress=192.168.0.120
cfgNicNetmask=255.255.255.0
cfgNicGateway=192.168.0.1
cfgNicUseDhcp=0
查看RAC网口当前的网络配置
C:\WINNT\system32>racadm -r192.168.0.120 -uroot -pcalvin getconfig -g cfgCurrentLanNetworking
Microsoft Windows操作系统的系统).
如果系统停机,RAC可以发出警报,并可以远程启动已关闭的系统.
可以通过集成网络适配器(从机器背面看在右下脚)将电子邮件信息或SNMP Trap发
送至Management Station,发出有关管理型系统中潜在问题的警报.
RAC网口(从机器背面看在右下脚网口)的默认IP地址是192.168.20.1/24,网关是
C:\WINNT\system32>racadm -r192.168.0.120 -uroot -pcalvin config -g cfgLanNetworking
-o cfgNicIpAddress 10.40.95.2
Object value successfully modified
RAC固件(3.35)已经改正了这个问题):
C:\WINNT\system32>racadm -r10.40.95.2 -uroot -pcalvin config -g cfgSerial
-o cfgSerialTelnetEnable 1
Object value successfully modified
cfgSerialConsoleColor=1
cfgSerialConsoleAnsi=1
硬重置RAC固件,使刚才修改的Serial配置生效
C:\WINNT\system32>racadm -r10.40.95.2 -uroot -pcalvin racreset hard
Warning: Hard reset will destroy the PCI configuration space in the RAC.
使RAC固件中root用户的Email报告生效,并发往pupil@
C:\WINNT\system32>racadm -r10.40.95.2 -uroot -pcalvin config -g cfgUserAdmin -i 1 -o cfgUserAdminEmailEnable 1
Object value successfully modified
C:\WINNT\system32>racadm -r10.40.95.2 -uroot -pcalvin config -g cfgUserAdmin -i 1 -o cfgUserAdminEmailAddress pupil@
# cfgNicCurrentIpAddress=192.168.0.120
# cfgNicCurrentNetmask=255.255.255.0
# cfgNicCurremtGateway=192.168.0.1
# cfgNicCurrentDhcpWasUsed=0
修改RAC网口的网络配置
cfgSerialConsoleQuitKey=<CR>~.
cfgSerialConsoleIdleTimeout=0x12c
cfgSerialConsoleShellType=0x2
cfgSerialConsoleNoAuth=0
cfgSerialConsoleCommand=
cfgSerialTelnetEnable=1
控制台重定向;否则,按Esc键退出"System Setup"(系统设置)程序,并完成您系
统的BIOS串行/远程登录文本控制台配置.
向下滚动选择"Integrated Devices"(集成设备).
在子菜单中,向下滚动至"Serial Port 1"(串行端口 1)并设置为"Off"(关).
C:\WINNT\system32>racadm -r192.168.0.120 -uroot -pcalvin config -g cfgLanNetworking
-o cfgNicGateway 10.40.95.254
Object value successfully modified
可以使用racadm命令行公用程序(RAC的命令行状态和配置公用程序,可以编写脚本)
来配置RAC并更新RAC固件.
查看RAC网口的网络配置
C:\WINNT\system32>racadm -r192.168.0.120 -uroot -pcalvin getconfig -g cfgLanNetworking
供远程管理功能.
本例是Dell PowerEdge 2650,具体RAC就是ERA,为方便以后用RAC来替代ERA
安装或嵌入了RAC的系统将被称为管理型系统.
远程访问RAC的系统将被称为Management Station.
术语系统控制台是指系统的键盘、鼠标和显示器.
可以使用控制台重定向将带有RSC系统的显示器、键盘和鼠标重定向至
Management Station.方法如下:
打开或重新启动系统,出现F2相关信息时立即按F2键,
向下滚动并选择"Console Redirection"(控制台重定向),
将"Console Redirection"(控制台重定向)屏幕设置为以下设置:
"Console Redirection"(控制台重定向)RAC或COM2(视BIOS而定,其中一个选项可用)
Object value successfully modified
C:\WINNT\system32>racadm -r10.40.95.2 -uroot -pcalvin config -g cfgUserAdmin -i 1 -o cfgUserAdminEmailCustomMsg Dell2650
"Remote Terminal Type"(远程终端类型)为ANSI或VT100/VT 220,视特定需要而定
"Redirection After Boot"(引导之后重定向)为"Disabled"(已禁用)
如果管理型系统是PowerEdge 1750,请执行以下附加步骤来启用串行/远程登录
为RAC固件Email报告设置远程SMTP服务器
C:\WINNT\system32>racadm -r10.40.95.2 -uroot -pcalvin config -g cfgRemoteHosts -
o cfgRhostsSmtpServerIpAddr 10.40.95.27
Object value successfully modified
cfgSerial -o cfgSerialConsoleEnable 1
Object value successfully modified
修改设置使RAC固件网口远程Telnet服务生效,这样就可以telnet到RAC的网口地址了,
这个telnet服务程序特别不安全,任何随意的用户(包括root)和密码都可以登录(新的
