ccna_final_exam_ccna第一学期期末考试20-0-0()
CCNA第一学期各章习题及答案

诶了我累了目录第二章网络通信P2-8第三章应用层功能及协议P9-14第四章OSI传输层P15-20第五章OSI网络层P21-27第六章网络编址-IPv4 P28-34第七章数据链路层P35-40第八章OSI物理层P41-45第九章以太网P46-51第十章网络规划和布线P52-61第十一章配置和测试网络P62-70第一学期末考试P71-91文档末尾返回目录第二章网络通信001 TCP/IP 网络接入层有何作用?路径确定和数据包交换数据表示、编码和控制可靠性、流量控制和错误检测详细规定构成物理链路的组件及其接入方法将数据段划分为数据包002下列哪些陈述正确指出了中间设备在网络中的作用?(选择三项)确定数据传输路径发起数据通信重新定时和重新传输数据信号发送数据流管理数据流数据流最后的终止点003下列哪三项陈述是对局域网 (LAN) 最准确的描述?(选择三项)LAN 通常位于一个地域内。
此类网络由由一个组织管理。
LAN 中的不同网段之间一般通过租用连接的方式连接。
此类网络的安全和访问控制由服务提供商控制。
LAN 为同一个组织内的用户提供网络服务和应用程序访问。
此类网络的每个终端通常都连接到电信服务提供商 (TSP)。
004 什么是 PDU?传输期间的帧损坏在目的设备上重组的数据因通信丢失而重新传输的数据包特定层的封装005 OSI 模型哪两层的功能与 TCP/IP 模型的网络接入层相同?(选择两项)网络层传输层物理层数据链路层会话层006请参见图示。
所示网络属于哪一类型?WANMANLANWLAN007 以下哪种特征正确代表了网络中的终端设备?管理数据流发送数据流重新定时和重新传输数据信号确定数据传输路径008 第 4 层端口指定的主要作用是什么?标识本地介质中的设备标识源设备和目的设备之间的跳数向中间设备标识通过该网络的最佳路径标识正在通信的源终端设备和目的终端设备标识终端设备内正在通信的进程或服务009 请参见图示。
CCNA第四学期官方章节考试题之第四学期《Final_Examination》(附答案)

公司与AA2SSH存在不正确的访问控制列表条目。
访问列表中的必须在会防止以明文传输登录信息如果身份验证失败,则会断开PPP 会话连接会发起双向握手容易遭受回送攻击4命令show frame-relay map的输出如下:Serial 0 (up): ip 192.168.151.4 dlci 122, dynamic, broadcast, status defined, active 下列哪三种说法正确描述了所示内容的意义?(选择三项。
)192.168.151.4代表远程路由器的IP 地址192.168.151.4代表本地串行接口的IP 地址DLCI 122代表远程串行接口DLCI 122代表用于连接远程地址的本地编号broadcast表示动态路由协议(例如RIP v1)可通过此PVC 发送数据包active表明ARP 进程正在工作5路由器的SDM 主页会显示哪三点信息?(选择三项。
)ARP 缓存闪存的总容量和可用容量路由表已配置的LAN 接口的数量是否配置了DHCP 服务器该LAN 中路由器的数量6从非军事区分界点本地环路网云确保在确认确保路由器上有通向下列哪三种说法正确描述了CSU/DSU调制解调器用于端接本地数字环路。
CSU/DSU调制解调器用于端接本地模拟环路。
路由器通常被视为路由器通常被视为10在链路质量测试完毕后,路由器在协商第LCPNCP它会被丢弃。
它会被放到队列中,直到主机它会被转换,源端口号保持为它会被分配其端口范围内的第一个可用端口号。
交换虚电路的相关信息将DLCI 映射到网络地址提供流量控制提供错误通知提供拥塞通知发送keepalive 数据包以检验PVC 的工作情况14请参见图示。
下列说法中哪三项正确?(选择三项。
)启用了NAT 过载。
启用了动态NAT。
地址转换会失败。
接口配置不正确。
地址为192.168.1.255 的主机将被转换。
进入0/0/2 接口的流量先被转换,然后才流出串行接口0/0/0。
2016CCNA1各章及期末考试答案

ITN 第7 章考试1什么是套接字?正确响应您的响应源和目的IP 地址以及源和目的以太网地址的组合源IP 地址与端口号的组合或目的IP 地址与端口号的组合源和目的序列号和确认号的组合源和目的序列号和端口号的组合套接字是源IP 地址与源端口号的组合,或者目的IP 地址与目的端口号的组合。
此试题参考以下领域的内容:Introduction to Networks•7.1.2 TCP 和UDP 简介2主机设备需要通过网络发送大型视频文件,同时为其他用户提供数据通信。
下列哪种功能可以让不同通信流同时发生,而不会让一个数据流使用所有可用带宽?正确响应您的响应窗口大小多路复用端口号确认多路复用对交替发送多个通信流很有用。
窗口大小用于降低数据通信速率。
端口号用于将数据流传送到正确的应用程序。
确认用于通知发送设备数据包流已收到或未收到。
此试题参考以下领域的内容:Introduction to Networks•7.1.1 数据传输3主机设备通过HTTP 协议向Web 服务器发送数据包。
传输层使用下列哪项来将数据流传送到服务器上的正确应用程序?正确响应您的响应序列号确认源端口号目的端口号目的端口号用于将数据流传输到正确的应用程序,而源端口号由源设备随机生成并进行跟踪。
序列号用于指示如何重组和重新排序收到的数据段。
确认用于通知发送设备数据包流已收到或未收到。
此试题参考以下领域的内容:Introduction to Networks•7.1.1 数据传输4UDP 传输协议有什么有利功能?正确响应您的响应确认已接收的数据减少传输延迟使用序列号跟踪数据段能够重新传输丢失的数据由于其报头小于TCP 报头,UDP 协议可以减少传输延迟。
此试题参考以下领域的内容:Introduction to Networks•7.1.1 数据传输5下列哪种场景描述了传输层提供的功能?正确响应您的响应学生使用教室里的VoIP 电话给家里打电话。
CCNA网络第一期期末测试答案
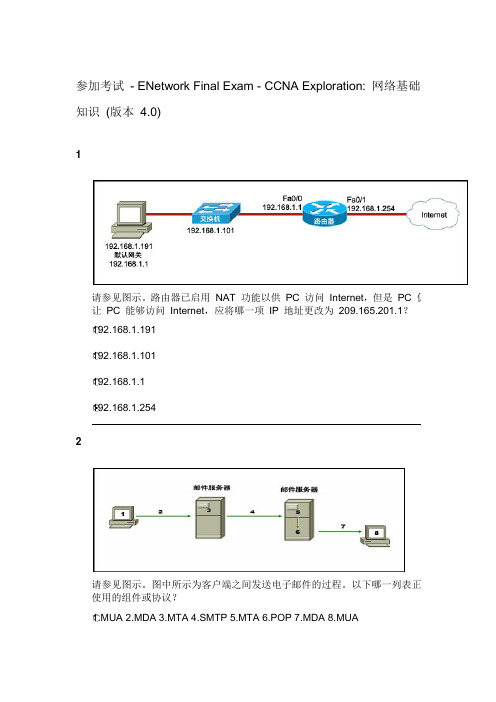
参加考试- ENetwork Final Exam - CCNA Exploration: 网络基础知识(版本4.0)1请参见图示。
路由器已启用NAT 功能以供PC 访问Internet,但是PC 仍然让PC 能够访问Internet,应将哪一项IP 地址更改为209.165.201.1?192.168.1.191192.168.1.101192.168.1.1192.168.1.2542请参见图示。
图中所示为客户端之间发送电子邮件的过程。
以下哪一列表正确使用的组件或协议?1.MUA2.MDA3.MTA4.SMTP5.MTA6.POP7.MDA8.MUA1.MUA2.POP3.MDA4.SMTP5.MTA6.MDA7.SMTP8.MUA1.MUA2.POP3.SMTP4.MDA5.MTA6.SMTP7.POP8.MUA1.MUA2.SMTP3.MTA4.SMTP5.MTA6.MDA7.POP8.MUA3数据链路层有哪两项功能?(选择两项)分割和记录数据。
在源主机和目的主机上运行的程序之间进行数据交换。
控制数据如何传递到介质中。
生成信号以表示每个帧中的比特。
使用帧头和帧尾封装每个数据包,以便在本地介质中进行传输。
4请参见图示。
PC 已连接到网络。
下列哪一项操作将验证PC 能够与其默认网关通信?使用ping 127.0.0.1命令。
使用ipconfig命令。
使用ipconfig/all命令。
使用ping 10.0.0.254命令。
5一位技术人员必须通过要求提供口令来确保交换机特权执行模式的安全。
哪种类型的口令能满录的需要并可视为最安全的口令?控制台电缆使能使能加密口令VTY6请参见图示。
下列关于图中所示IP 配置的陈述,哪三项是正确的?(选择三项)分配给该计算机的地址代表私有地址。
该计算机无法在本地网络外通信。
此计算机的网络可支持126 台主机。
该计算机地址的前缀是/27。
分配给该计算机的IP 地址可在Internet 上路由。
网络管理员考核试题

ccna 第一学期期末考试试题与答案1网络管理员想要限制访问路由器的特权执行模式。
管理员应该使用哪一种口令?使能aux控制台VTY2请参见图示。
主机已与交换机 2 断开连接并连接到交换机1。
为了让该主机在网络中正常工作,应该为其分配怎样的IP 地址、子网掩码和默认网关?IP 地址:10.10.9.37,子网掩码:255,255,255,240,默认网关:10.10.9.35IP 地址:10.10.9.37,子网掩码:255.255.255.224,默认网关:10.10.9.35IP 地址:10.10.9.29,子网掩码:255,255,255,248,默认网关:10.10.9.35IP 地址:10.10.9.32,子网掩码:255.255.255.224,默认网关:10.10.9.35IP 地址:10.10.9.37,子网掩码:255.255.255.224,默认网关:196.1.105.6IP 地址:10.10.9.63,子网掩码:255.255.255.224,默认网关:10.10.9.353下列哪两种介质可用于连接相距500 米的两台设备?(选择两项)10 BASE-T1000 BASE-TX10 BASE-21000 BASE LX1000 BASE-SX4请参见图示。
为了使此网络中的主机接入Internet,路由器RT_A 需要提供哪种功能?地址转换DHCP 服务ftpWeb 服务器5请参见图示。
技术人员正在处理网络问题,需要验证路由器的LAN 接口。
要确认路由器接口工作正常,应该从此主机ping 哪个地址?127.0.0.1192.168.64.196192.168.254.1192.168.254.9192.168.254.2546请参见图示。
主机 A 正在向主机 B 传输数据。
数据离开Router1 的Fa0/1 接口时将使用哪一种地址组合?目的IP:192.168.72.2,源MAC:0007.C2B4.3421目的IP:192.168.10.4,源MAC:0030.8596.DE81目的IP:192.168.10.4,源MAC:0007.C2B4.3421目的IP:192.168.72.2,源MAC:0030.8596.DE817请参见图示。
CCNA第一学期Finalexam考试英文版答案

CCNA第一学期Finalexam考试英文版答案(R&S.)C 1A medium-sized business is researching available options for connecting to the Internet.Thecompany is looking for a high speed option with dedicated, symmetric access.Whichconnection type should the company choose?DSLdialupsatelliteleased linecable modem2What is the purpose of having a converged network?to provide high speed connectivity to all end devicesto make sure that all types of data packets will be treated equallyto achieve fault tolerance and high availability of data network infrastructure devicesto reduce the cost of deploying and maintaining thecommunication infrastructure3What characteristic of a network enables it to quickly grow to support new users andapplications without impacting the performance of the service being delivered to existing users?reliabilityscalabilityquality of serviceaccessibility4Which connection provides a secure CLI session with encryption to a Cisco switch?a console connectionan AUX connectiona Telnet connectionan SSH connection5A network technician is attempting to configure an interface by entering the followingcommand:SanJose(config)#ip address192.168.2.1255.255.255.0.The command isrejected by the device.What is the reason for this? The command is being entered from the wrong mode of operation.The command syntax is wrong.The subnet mask information is incorrect.The interface is shutdown and must be enabled before the switch will accept the IP address.6After several configuration changes are made to a router, the copy running-configurationstartup-configuration command is issued.Where will the changes be stored?flashROMNVRAMRAMthe configuration registera TFTP server7Refer to the exhibit.From global configuration mode,an administrator is attempting to create a message-of-the-day banner by using thecommand banner motd V Authorized access only!Violators will be prosecuted!V When users log in using Telnet,the banner does not appear correctly.What is the problem? The banner message is too long.The delimiting character appears in the banner message.The symbol“!”signals the end of a banner message.Message-of-the-day banners will only appear when a user logs in through the console port.8What are three characteristics of an SVI?(Choose three.) It is designed as a security protocol to protect switch ports.It is not associated with any physical interface on a switch.It is a special interface that allows connectivity by different types of media.It is required to allow connectivity by any device at any location.It provides a means to remotely manage a switch.It is associated with VLAN1by default.9A technician configures a switch with these commands: SwitchA(config)#interface vlan1SwitchA(config-if)#ip address192.168.1.1255.255.255.0 SwitchA(config-if)#no shutdownWhat is the technician configuring?Telnet accessSVIpassword encryptionphysical switchport access10In computer communication,what is the purpose of message encoding?to convert information to the appropriate form for transmissionto interpret informationto break large messages into smaller framesto negotiate correct timing for successful communication11What protocol is responsible for controlling the size of segments and the rate at whichsegments are exchanged between a web client and a web server?TCPIPHTTPEthernet12What are two benefits of using a layered network model? (Choose two.)It assists in protocol design.It speeds up packet delivery.It prevents designers from creating their own model.It prevents technology in one layer from affecting other layers.It ensures a device at one layer can function at the next higher layer.13What is the process of dividing a data stream into smaller pieces before transmission?segmentationencapsulationencodingflow control14When IPv4addressing is manually configured on a web server,which property of the IPv4configuration identifies the network and host portion for an IPv4address?DNS server addresssubnet maskdefault gatewayDHCP server address15A network administrator is troubleshootingconnectivity issues on a ing a tester,the administrator notices that the signals generated by the server NIC are distorted and not usable.In which layer of the OSI model is the error categorized?presentation layernetwork layerphysical layerdata link layer16A network engineer is measuring the transfer of bits across the company backbone for amission critical database application.The engineer notices that the network throughputappears lower than the bandwidth expected.Which three factors could influence thedifferences in throughput?(Choose three.)the amount of traffic that is currently crossing the networkthe sophistication of the encapsulation method applied to the datathe type of traffic that is crossing the networkthe latency that is created by the number of network devices that the data is crossingthe bandwidth of the WAN connection to the Internetthe reliability of the gigabit Ethernet infrastructure of the backbone17Which type of UTP cable is used to connect a PC to a switch port?consolerollovercrossoverstraight-through18What is a characteristic of the LLC sublayer?It provides the logical addressing required that identifies the device.It provides delimitation of data according to the physical signaling requirements of the medium.It places information in the frame allowing multiple Layer 3protocols to use the same network interface and media.It defines software processes that provide services to the physical layer.19What are the three primary functions provided by Layer 2data encapsulation?(Choosethree.)error correction through a collision detection methodsession control using port numbersdata link layer addressingplacement and removal of frames from the mediadetection of errors through CRC calculationsdelimiting groups of bits into framesconversion of bits into data signals20What will a host on an Ethernet network do if it receives a frame with a destination MACaddress that does not match its own MAC address?It will discard the frame.It will forward the frame to the next host.It will remove the frame from the media.It will strip off the data-link frame to check the destination IP address.21What are two actions performed by a Cisco switch? (Choose two.)building a routing table that is based on the first IP address in the frame headerusing the source MAC addresses of frames to build and maintain a MAC address tableforwarding frames with unknown destination IP addresses to the default gatewayutilizing the MAC address table to forward frames via the destination MAC addressexamining the destination MAC address to add new entries to the MAC address table22What are two examples of the cut-through switching method?(Choose two.)store-and-forward switchingfast-forward switchingCRC switchingfragment-free switchingQOS switching23Refer to the exhibit.If host A sends an IP packet to host B,what will the destination address be in the frame when it leaves host A?DD:DD:DD:DD:DD:DD172.168.10.99CC:CC:CC:CC:CC:CC172.168.10.65BB:BB:BB:BB:BB:BBAA:AA:AA:AA:AA:AA24What are two services provided by the OSI network layer?(Choose two.)performing error detectionrouting packets toward the destinationencapsulating PDUs from the transport layerplacement of frames on the mediacollision detection25What information is added during encapsulation at OSI Layer3?source and destination MACsource and destination application protocolsource and destination port numbersource and destination IP address26What are two functions of NVRAM?(Choose two.)to store the routing tableto retain contents when power is removedto store the startup configuration fileto contain the running configuration fileto store the ARP table27Refer to the exhibit.The network administrator for a small advertising company has chosen to use the192.168.5.96/27 network for internal LAN addressing.As shown in the exhibit,a static IP address is assigned to the company web server.However,the web server cannot access the Internet.The administrator verifies that local workstations with IP addresses that are assigned by a DHCP server can access the Internet,and the web server is able to ping local workstations.Which component is incorrectly configured?subnet maskDNS addresshost IP addressdefault gateway address28Why does a Layer3device perform the ANDing process on a destination IP address andsubnet mask?to identify the broadcast address of the destination networkto identify the host address of the destination hostto identify faulty framesto identify the network address of the destination network29What are the three ranges of IP addresses that are reserved for internal private use?(Choosethree.)10.0.0.0/864.100.0.0/14127.16.0.0/12172.16.0.0/12192.31.7.0/24192.168.0.0/1630Which three addresses are valid public addresses? (Choose three.)198.133.219.17192.168.1.24510.15.250.5128.107.12.117192.15.301.24064.104.78.22731What type of IPv6address is FE80::1?loopbacklink-localmulticastglobal unicast32Refer to the exhibit.On the basis of the output,which two statements about network connectivity are correct? (Choose two.)There is connectivity between this device and the device at192.168.100.1.The connectivity between these two hosts allows for videoconferencing calls.There are4hops between this device and the device at 192.168.100.1.The average transmission time between the two hosts is2 milliseconds.This host does not have a default gateway configured.33Which subnet would include the address192.168.1.96as a usable host address?192.168.1.64/26192.168.1.32/27192.168.1.32/28192.168.1.64/2934How many hosts are addressable on a network that has a mask of255.255.255.248?268141625435Which statement is true about variable-length subnet masking?Each subnet is the same size.The size of each subnet may be different,depending on requirements.Subnets may only be subnetted one additional time.Bits are returned,rather than borrowed,to create additional subnets.36Refer to the exhibit.Consider the IP address of 192.168.10.0/24that has been assigned to a high school building.The largest network in this building has100 devices.If192.168.10.0is the network number for the largest network,what would be the network number for thenext largest network,which has40devices?192.168.10.0192.168.10.128192.168.10.192192.168.10.224192.168.10.24037In what two situations would UDP be the preferred transport protocol over TCP?(Choosetwo.)when applications need to guarantee that a packet arrives intact,in sequence,and unduplicatedwhen a faster delivery mechanism is neededwhen delivery overhead is not an issuewhen applications do not need to guarantee delivery of the datawhen destination port numbers are dynamic38What important information is added to the TCP/IPtransport layer header to ensurecommunication and connectivity with a remote network device?timing and synchronizationdestination and source port numbersdestination and source physical addressesdestination and source logical network addresses39What is the TCP mechanism used in congestion avoidance? three-way handshakesocket pairtwo-way handshakesliding window40Which three statements characterize UDP?(Choose three.)UDP provides basic connectionless transport layer functions.UDP provides connection-oriented,fast transport of data at Layer 3.UDP relies on application layer protocols for error detection.UDP is a low overhead protocol that does not provide sequencing or flow control mechanisms.UDP relies on IP for error detection and recovery.UDP provides sophisticated flow control mechanisms.41Which two tasks are functions of the presentation layer? (Choose two.)compressionaddressingencryptionsession controlauthentication42Which two protocols operate at the highest layer of the TCP/IP protocol stack?(Choose two.)DNSEthernetIPPOPTCPUDP43Which two roles can a computer assume in a peer-to-peer network where a file is beingshared between two computers?(Choose two.)clientmasterserverslavetransient44What is the function of the HTTP GET message?to request an HTML page from a web serverto send error information from a web server to a web clientto upload content to a web server from a web clientto retrieve client email from an email server using TCP port11045A wireless host needs to request an IP address.What protocol would be used to process therequest?FTPHTTPDHCPICMPSNMP46When planning for network growth,where in the network should packet captures take place toassess network traffic?on as many different network segments as possibleonly at the edge of the networkbetween hosts and the default gatewayonly on the busiest network segment47When applied to a router,which command would help mitigate brute-force password attacksagainst the router?exec-timeout30service password-encryptionbanner motd$Max failed logins=5$login block-for60attempts5within6048Refer to the exhibit.An administrator is testing connectivity to a remote device with the IP address10.1.1.1.What does the output of this command indicate?Connectivity to the remote device was successful.A router along the path did not have a route to the destination.A ping packet is being blocked by a security device along the path.The connection timed out while waiting for a reply fromthe remote device.。
ccna1章节与期末答案

第一章:正确答案:2.4.5•解析:由于不需要使用网络设备和专用服务器,对等网络易于创建,复杂性更低,且成本更少。
而且对等网络也没有集中管理。
这种网络安全性更低,不可扩展,而且那些同时充当客户端和服务器的设备可能性能更差正确答案:1解析:正确答案: 3.5解析:选择网络介质的条件包括:所选介质可以成功传送信号的距离、要安装所选介质的环境、必须传输的数据量和速度以及介质和安装的成本。
正确答案:3和4解析:终端设备上的应用程序可以生成数据,更改数据内容并且负责启动封装过程。
正确答案:1和4解析:终端设备会发出通过网络传输的数据。
中间设备会在链路发生故障时通过备用路径传输数据,并且会过滤数据传输以增强安全性。
网络介质提供网络消息的传输通道。
正确答案:4解析:外联网是公司外部的人或企业合作伙伴访问数据的网络区域。
内部网只描述通常仅供内部人员访问的网络区域。
当设备连接到有线网络时,有线LAN 会受BYOD(自带设备)影响。
使用大学无线LAN 的设备多为平板电脑和智能手机。
大学生主要使用无线WAN 来访问他们的手机运营商网络。
.正确答案:2解析:由于通过Internet 可以联系在线供应商,所以家庭用户通过Internet 进行网上购物。
内联网基本上是仅供内部使用的局域网。
外联网是外部合作伙伴访问组织内部特定资源的网络。
家庭用户并不一定使用LAN 来访问Internet。
例如,PC 可以通过调制解调器直接连接到ISP。
正确答案:1解析:内部网这个术语用于表示一个组织的私有局域网和广域网连接。
内部网的设计旨在仅允许该组织的成员、员工或其他获得授权的人员进行访问。
正确答案:2和4解析:电缆和DSL 均能实现高带宽、始终联网,并提供到主机计算机或LAN 的以太网连接。
10正确答案:2和3解析:移动电话连接需要使用移动电话网络。
卫星连接通常用于家庭或企业外部不便使用物理布线的位置。
11正确答案:2解析:当对网络资源的请求超出了可用容量时,网络就会变得拥堵。
CCNA第1学期测试题

Which of the following is considered a limitation of RIP v1?RIP v1 does not send subnet mask information in its updates.RIP v1 is not widely supported by networking hardware vendors.RIP v1 consumes excessive bandwidth by multicasting routing updates using a Class D address.RIP v1 requires enhanced router processors and extra RAM to function effectively.RIP v1 does not support load balancing across equal-cost paths.RIP v1 authentication is complicated and time-consuming to configure.Which of the following statements are true regarding RIP v1 and v2? (Choose three.)Both RIP versions use hop count.Both RIP versions can provide authentication of update sources.Both RIP versions use 16 hops as a metric for infinite distance.RIP v1 uses split horizon to prevent routing loops while RIP v2 does not.RIP v1 uses hold-down times to prevent routing loops while RIP v2 does not.RIP v1 broadcasts routing table updates, while RIP v2 multicasts its updates.A new network is to be configured on a router. Which of the following tasks must be completed to configure this interface and implement dynamic IP routing for the new network? (Choose three.)Select the routing protocol to be configured.Assign an IP address and subnet mask to the interface.Update the ip host configuration information with the device name and new interface IP address.Configure the routing protocol with the new network IP address.Configure the routing protocol with the new interface IP address and subnet mask.Configure the routing protocol in use on all other enterprise routers with the new network information.Router1 and Router2 shown in the topology have been configured with the no ip subnet-zero command. Which of the following valid VLSM network numbers could be used for the serial link between Router1 and Router2? (Choose two.)192.168.1.0/30192.168.1.4/30192.168.1.8/30192.168.1.96/30192.168.1.138/30192.168.1.190/30Which command would a network administrator use to determine if the routers in an enterprise havelearned about a newly added network?router# show ip addressrouter# show ip routerouter# show ip networksrouter# show ip interface briefrouter# debug ip protocolrouter# debug rip updateHow does a router know of paths to destination networks? (Choose two.)inspection of the destination IP address in data packetsARP requests from connected routersmanual configuration of routesupdates from other routersDHCP information broadcastsupdates from the SMTP management information baseRefer to the network shown. How will Router1 summarize and advertise the four networks attached to its Ethernet ports?172.16.16.0/20172.16.19.0/20172.16.16.0/20 and 172.16.19.0/20172.16.16.0/22172.16.18.0/24172.16.0.0/24In the network shown in the graphic, three bits were borrowed from the host portion of a Class C address. How many valid host addresses will be unused on the three point-to-point links combined if VLSM is not used?34123684180A Class C address has been assigned for use in the network shown in the graphic. Using VLSM, which bit mask should be used to provide for the number of host addresses required on Router A, while wasting the fewest addresses?/31/30/29/28/27/26How often does RIP v1 send routing table updates, by default?every 30 secondsevery 45 secondsevery 60 secondsevery 90 secondsWhat is the default network mask for a Class B address?255.0.0.0255.255.0.0255.255.255.0255.255.255.255Which subnet mask is represented by the /21 notation?255.255.224.0255.255.248.0255.255.252.0255.255.240.0Which of the following are contained in the routing updates of classless routing protocols? (Choose two.)32-bit addressnext hop router interfacesubnet maskunicast host addressLayer 2 addressWhat is the purpose of the network command used in the configuration of the RIP routing protocol?It specifies RIP v2 as the routing protocol.It enables the use of VLSM.It specifies the fastest path to the destination route.It specifies which interfaces will exchange RIP routing updates.It activates RIP for all routes that exist within the enterprise network.Which of the following problems does VLSM help to alleviate?the shortage of IP addressesthe difficulty of assigning static IP addresses to hosts in large enterprisesthe complexity of implementing advanced routing protocols such as OSPF and EIGRPthe shortage of network administrators qualified in the use of RIP v1 and IGRPWhat does VLSM allow a network administrator to do?utilize one subnet mask throughout an autonomous systemutilize multiple subnet masks in the same IP address spaceutilize IGRP as the routing protocol in an entire autonomous systemutilize multiple routing protocols within an autonomous systemA Class C network address has been subnetted into eight subnetworks. Using VLSM, the last subnet willbe divided into eight smaller subnetworks. What bit mask must be used to create eight smallersubnetworks, each having two usable host addresses?/26/27/28/29/30/31An additional subnet is required for a new Ethernet link between Router1 and Router2 as shown in the diagram. Which of the following subnet addresses can be configured in this network to provide a maximum of 14 useable addresses for this link while wasting the fewest addresses?192.1.1.16/26192.1.1.96/28192.1.1.160/28192.1.1.196/27192.1.1.224/28192.1.1.240/28The network shown in the diagram is having problems routing traffic. It is suspected that the problem is with the addressing scheme. What is the problem with the addressing used in the topology?The address assigned to the Ethernet0 interface of Router1 is a broadcast address for that subnetwork.The subnetwork configured on the serial link between Router1 and Router2 overlaps with the subnetwork assigned to Ethernet0 of Router3.The subnetwork assigned to the Serial0 interface of Router1 is on a different subnetwork from the address for Serial0 of Router2.The subnetwork assigned to Ethernet0 of Router2 overlaps with the subnetwork assigned to Ethernet0 of Router3.The routers in the diagram use the subnet assignments shown. What is the most efficient route summary that can be configured on Router3 to advertise the internal networks to the cloud?192.1.1.0/26 and 192.1.1.64/27192.1.1.128/25192.1.1.0/23 and 192.1.1.64/23192.1.1.0/24192.1.1.0/25192.1.1.0/24 and 192.1.1.64/24。
思科第一学期期末考试最新考题CCNA

1Refer to the exhibit. Which Layer 2 protocol could be used inside nework A and network C?IPTCPUDPEthernet2Refer to the exhibit. Which set of devices contains only intermediary devices?A, B, D, GA, B, E, FC, D, G, IG, H, I, J3Refer to the exhibit. The headers added at each layer are shown. Which layer adds the destination and source pro to ensure that data is delivered to the correct application?physical layerdata link layernetwork layertransport layer4T he Layer 4 header contains which type of information to aid in the delivery of data?service port numberhost logical addressdevice physical addressvirtual connection identifier5Which fiber connector supports full-duplex Ethernet?6W hich device should be used for routing a packet to a remote network?access switchDHCP serverhubrouter7Refer to the exhibit. Host A sends a frame to host C with a destination MAC address CC. The MAC address for h in the MAC table of switch SW1. How will SW1 handle the frame?Switch SW1 will drop the frame.Switch SW1 will forward the frame to host C.Switch SW1 will flood the frame out all ports.Switch SW1 will flood the frame out all ports except port Fa0/1.8Refer to the exhibit. A network technician has made several changes to R1 since the configuration has last bee modified configuration did not produce the desired changes. The technician wants to store a backup copy of the saved c on a TFTP server before reloading. Which action will cause the unmodified data to be saved on the TFTP serve9Which three statements are true about network layer addressing? (Choose three.)It uniquely identifies each host.It assists in forwarding packets across internetworks.It uses a logical 32-bit IPv4 address.It is not a configurable address.It is a physical address.It identifies the host from the first part of the address.10W hat is the result of using the clock rate 56000 command at the serial interface of the router?The interface is configured as a DCE device.The interface timers are cleared.The FastEthernet interface is made to emulate a serial interface by assigning it a timing signal.The IP address for the serial interface is configured.11Examine the graphic with current configurations. Host A in the Clerical office failed and was replaced. Altho 127.0.0.1 was successful, the replacement computer cannot access the company network. With proxy ARP disabled interface of the New York router, what is the likely cause of the problem?network card failurenetwork cables unpluggedIP address incorrectly enteredsubnet mask incorrectly entered12A s network administrator, what is the subnet mask that allows 510 hosts given the IP address 172.30.0.0?255.255.0.0255.255.248.0255.255.252.0255.255.254.0255.255.255.0255.255.255.12813Which OSI layer uses a connection-oriented protocol to ensure reliable delivery of data?application layerpresentation layersession layertransport layer14A network has grown too large for technicians to configure network addresses and hosts files for name resolutio application layer services should be added to the server to allow these needs to be satisfied dynamically? (DNSFTPDHCPHTTPSMTP15Refer to the exhibit. Host A wants to access the Internet. Which combination of a Layer 2 address and a Layer 3 enable this access from host A?Destination MAC: 0030.8596.DE83 Default gateway: 209.165.202.130Destination MAC: 0030.8596.DE82 Default gateway: 172.16.9.2Destination MAC: 0030.8517.44C4 Default gateway: 172.16.1.1Destination MAC: 0030.8517.44C4 Default gateway: 209.165.202.13016 A network administrator is asked to design a new addressing scheme for a corporate network. There are 60 usersoffice, 40 users in the branch office, 28 users in manufacturing, 12 in the sales office, and 4 users in the rese Which VLSM addressing scheme that uses the 192.168.88.0/24 network will fulfill the requirements while wastin addresses?192.168.88.0/26 main192.168.88.32/26 branch192.168.88.64/26 manufacturing 192.168.88.96/27 sales192.168.88.128/28 research192.168.88.0/26 main192.168.88.64/26 branch192.168.88.128/27 manufacturing192.168.88.160/28 sales192.168.88.176/29 research192.168.88.0/27 main192.168.88.32/27 branch192.168.88.64/28 manufacturing192.168.88.80/29 sales192.168.88.88/30 research192.168.88.0/27 main192.168.88.64/28 branch192.168.88.80/28 manufacturing192.168.88.96/29 sales192.168.88.104/30 research17W hich physical connector type is used for a serial V.35 connection to the CSU/DSU?18Refer to the exhibit. Which two facts can be determined about the topology? (Choose two.)Four collision domains are present.One logical network is represented.Two broadcast domains are present.Three networks are needed.Three logical address ranges are required.19W hat are three characteristics of CSMA/CD? (Choose three.)It monitors the media for presence of a data signal.After detecting a collision, hosts can resume transmission after a random timer has expired.A jam signal is used to ensure that all hosts are aware that a collision has occurred.Devices can be configured with a higher transmission priority.Data is transmitted only when the data signal is present.It uses a token system to avoid collisions.20Refer to the exhibit. The serial interface of the router was configured with the use of the commands that ar router cannot ping the router that is directly connected to interface serial 0/0/0. What should the network t to solve this problem?Configure the description at interface serial 0/0/0.Configure an IP address on interface serial 0/0/0.Remove the no shutdown command at interface serial 0/0/0Reboot the router.21W hich OSI layer uses the header information to reassemble the data segments into streams?application layernetwork layerpresentation layersession layertransport layer22Refer to the exhibit. The NAT functionality of the router is enabled to provide Internet access to the PC. How is still unable to access the Internet. Which IP address should be changed to 209.165.201.1 to enable the PC t Internet?192.168.1.191192.168.1.101192.168.1.1192.168.1.25423Refer to the exhibit. A technician uses the nslookup command on the PC and views the output that is displayed in What is the IP address of the primary domain name server used by the host?10.10.10.32192.168.1.5192.168.1.99192.168.2.10024Which memory contents will change as a result of using the Router# erase startup-config command on a routerRAMROMflashNVRAM25W hile configuring a router, a network technician wants to name the router. Which prompt should the technician see the hostname command?Router>Router#Router(config)#Router(config-line)#26Refer to the exhibit. The PC, the routing table of which is displayed, is configured correctly. To which netwo interface does the IP address 192.168.1.254 belong?PCswitchrouter interface fa0/0router interface fa0/127Refer to the exhibit. A network administrator is troubleshooting a link that is down between Router1 and Router the problem, which wire pairs need to be switched on one of the Ethernet cable ends?pair 1 and pair 2pair 1 and pair 3pair 2 and pair 3pair 2 and pair 428Refer to the exhibit. A PC is connected to a network. Which action will verify that the PC can communicate wit gateway?Use the ping 127.0.0.1 command.Use the ipconfig command.Use the ipconfig/all command.Use the ping 10.0.0.254 command.29Refer to the exhibit. Host B was powered off. What change will occur in the MAC table of the switch?The table will remain unaffected.The switch will remove the MAC address at Fa0/19.The switch will retain the MAC address until host B is powered on again.The switch will rebuild the MAC table by assigning the FFFF.FFFF.FFFF address to port Fa0/19.30What information is contained in the header of Layer 3 to help data delivery?port numberdevice physical addressdestination host logical addressvirtual connection identifier31 A network technician is tasked with setting up a network for six users, but the users should be able to use thto log on from any of the six computers. What type of network should be used?workgroupP2P applicationspeer-to-peer networkclient-server network32Refer to the exhibit. A web browser is running on host PC1 with an IP address 10.10.2.2/24. A dynamic port num is assigned to the browser. The browser sends a request for a web page to the web server with an IP address 192.1 Which statement is true?The session is established using TCP, and the socket number for the web server is 192.168.1.254: 80.The session is established using TCP, and the socket number for the web server is 192.168.1.254: 49152.The session is established using UDP, and the socket number for the web server is 192.168.1.254: 80.The session is established using UDP, and the socket number for the web server is 192.168.1.254: 49152.33Refer to the exhibit. An administrator on PC1 wants to view some HTML code from a web page housed on the web s client application will allow this request to be started?34Refer to the exhibit. What is required on host A for a network technician to create the initial configurationan FTP clienta Telnet clienta terminal emulation programa web browser35What are two characteristics of the data link layer? (Choose two.)It segments and reorders the data.It exchanges the frames between nodes.It defines the method by which network devices place data onto the media.It manages the transfer of data between the processes that run on each host.It retrieves signals from the media and restores them to their bit representations.36A network administrator wants to restrict access to the router privileged EXEC mode. Which password should the a use?enableauxconsoleVTY37Which three IPv4 addresses represent a broadcast for a subnet? (Choose three.)172.16.4.63 /26172.16.4.129 /26172.16.4.191 /26172.16.4.51 /27172.16.4.95 /27172.16.4.221 /2738Refer to the exhibit. Host X is unable to communicate with host Y. Which command can be run at host X to det intermediary device is responsible for this failure?telnet 192.168.1.1ping 192.168.1.1ftp 192.168.1.1tracert 192.168.1.139Refer to the exhibit. Which option shows the correct topology given the configuration of Router1?40I f an administrator wished to return a router to the default state, what additional step must be taken after command erase start-up config?Reload the device.Issue the command copy running-config start-up config.Perform a show running-config to verify that the file was removed.Enter the interface commands to allow the device to connect to the network.41By using the ipconfig command, a network administrator determines that a workstation has the address 192.168.bits set in the subnet mask. To what network does the workstation belong?192.168.3.8192.168.3.16192.168.3.24192.168.3.3242W hich statement is true about router hostnames?A hostname should be unique on each router.A router hostname cannot contain capital letters.A router hostname is configured in privileged executive mode.A router hostname must be created before any other configurations can be added to the device.43 A user types the enable command. What task can be performed at the privileged EXEC mode?Configure the device.Configure individual interfaces.Configure individual terminal lines.Issue show and debug commands.44Refer to the exhibit. Which logical topology describes the exhibited network?starringpoint-to-pointmulti-access45Refer to the exhibit. A user wants to access the Internet from the PC. A part of the running configuration o is shown. Which default gateway IP address should be configured at the PC to enable this access?10.1.192.110.1.192.210.1.192.54192.31.7.146Which statement is true about the ICMP protocol?It is an application layer protocol.It is designed to make IP a reliable protocol.It is often filtered out of networks for security purposes.If a host does not respond to an ICMP echo request, the host is not functioning.47Refer to the exhibit. At which OSI layer is serial interface 0/0/1 experiencing problems?Layer 1Layer 2Layer 3Layer 448Refer to the exhibit. The host was disconnected from switch 2 and connected to switch 1. Which combination of subnet mask, and default gateway should be assigned to this host to allow it to function in the network?IP address: 10.10.9.37 Subnet mask: 255.255.255.240 Default gateway: 10.10.9.35IP address: 10.10.9.37 Subnet mask: 255.255.255.224 Default gateway: 10.10.9.35IP address: 10.10.9.29 Subnet mask: 255.255.255.248 Default gateway: 10.10.9.35IP address: 10.10.9.32 Subnet mask: 255.255.255.224 Default gateway: 10.10.9.35IP address: 10.10.9.37 Subnet mask: 255.255.255.224 Default gateway: 196.1.105.6IP address: 10.10.9.63 Subnet mask: 255.255.255.224 Default gateway: 10.10.9.3549Refer to the exhibit. The diagram represents the process of sending email between clients. Select the list below t identifies the component or protocol used at each numbered stage of the diagram.1.MUA2.MDA3.MTA4.SMTP5.MTA6.POP7.MDA8.MUA1.MUA2.POP3.MDA4.SMTP5.MTA6.MDA7.SMTP8.MUA1.MUA2.POP3.SMTP4.MDA5.MTA6.SMTP7.POP8.MUA1.MDA2.SMTP3.MTA4.SMTP5.MTA6.MUA7.POP8.MDA1.MUA2.SMTP3.MTA4.SMTP5.MTA6.MDA7.POP8.MUA50What is the Cisco IOS?system software for Cisco devicesRead Only Memory in Cisco devicesnon-volatile storage for device configurationsan initial operating system that is used for boot functions。
CCNA第一学期各章习题和参考答案.doc

CCNA第一学期各章习题和参考答案第二章网络通信1、TCP/IP网络接入层有何作用?A路径确定和数据包交换B数据表示、编码和控制C可靠性、流量控制和错误检测E将数据段划分为数据包2、下列哪些陈述正确指出了中间设备在网络中的作用?(选择三项)B发起数据通信D发送数据流F数据流最后的终止点3、下列哪三项陈述是对局域网(LAN) 最准确的描述?(选择三项)C LAN 中的不同网段之间一般通过租用连接的方式连接。
D此类网络的安全和访问控制由服务提供商控制。
F此类网络的每个终端通常都连接到电信服务提供商(TSP)。
004 什么是PDU?A传输期间的帧损坏B在目的设备上重组的数据C因通信丢失而重新传输的数据包005 OSI 模型哪两层的功能与TCP/IP 模型的网络接入层相同?(选择两项)018哪个应用层协议通常用于支持客户端与服务器之间的文件传输?A HTMLB HTTP D Telnet019哪个应用层协议中规定了Microsoft 网络中用于文件共享的服务?A DHCPB DNS D SMTP E Telnet020服务器上的应用层通常如何处理多客户端服务请求?A终止与服务的所有连接B拒绝与单一守护程序的多个连接C暂停当前连接,建立新连接第四章OSI传输层001下列哪两项是用户数据报协议(UDP) 的功能?(选择两项)A流量控制 D 面向连接E 序列和确认002请参见图示。
此Wireshark 捕获输出的第7 行中执行的是哪一项TCP 操作?A会话创建B 数据段重传C 数据传输D 会话断开003数据段的TCP 报头中为什么包含端口号?A指示转发数据段时应使用的正确路由器接口B 标识接收或转发数据段时应使用的交换机端口C确定封装数据时应使用的第3 层协议让接收主机转发数据到适当的应用程序E让接收主机以正确的顺序组装数据包004OSI 模型哪一层负责规范信息从源设备到目的设备准确可靠地流动?A应用层 B 表示层 C 会话层传输层 E 网络层005请参见图示。
ccna1期末考试题

Refer to the exhibit. In a network, host A is sending data segments to host B. The flow control of the segments that are being exchanged is displayed. Which two statements are true about this communication? (Choose two.)The initial window size is determined via the two-way handshake.The window size for the TCP session that is represented is initially set to 3000 bytes.Acknowledgment number 3001 indicates that host A will send the next segment with sequence number 3001.Host B expects that the next received segment number will be 3000.No more acknowledgments will be exchanged.2Refer to the exhibit. A host is using NAT to connect to the Internet. Which three IP addresses enable this connection? (Choose three.)10.1.1.6310.1.1.3710.1.1.3910.1.1.3210.1.1.6010.1.1.23determines the correct destination application?timing and synchronization bitsdestination and source physical addressesdestination and source logical network addressesdestination and source process numbers4Which password restricts Telnet access to the router?enableenable secretconsoleVTY5Refer to the exhibit. To create the initial configuration, a network technician connected host A to the router using the connection that is shown. Which statement is true about this connection?It terminates at the Ethernet port of the router.It provides out-of-band console access.It terminates at the serial interface of the router.It requires a Telnet client on host A to access the router.6Which three addresses belong to the category of public IP addresses? (Choose three.)127.0.0.1196.1.105.6132.11.9.9910.0.0.1172.16.9.1046.1.1.977Refer to the exhibit. All devices in the network use default configurations. How many logical address ranges are required in this topology?234568Refer to the exhibit. A host is connected to hub 1. Which combination of IP address, subnet mask, and default gateway can allow this host to function in the network?IP address: 172.16.31.36 Subnet mask: 255.255.255.240 Default gateway: 172.16.31.35IP address: 172.16.31.63 Subnet mask: 255.255.255.224 Default gateway: 172.16.31.35IP address: 172.16.31.29 Subnet mask: 255.255.255.248 Default gateway: 172.16.31.35IP address: 172.16.31.32 Subnet mask: 255.255.255.224 Default gateway: 172.16.31.35IP address: 172.16.31.29 Subnet mask: 255.255.255.240 Default gateway: 172.16.30.1IP address: 172.16.31.37 Subnet mask: 255.255.255.224 Default gateway: 172.16.31.359Refer to the exhibit. Host B attempts to establish a TCP/IP session with host C. During this attempt, a frame was captured at the FastEthernet interface fa0/1 of the San Francisco router. The packet inside the captured frame has the source IP address 10.10.1.2, and the destination IP address is 10.31.1.20. What is the destination MAC address of the frame at the time of capture?0060.7320.D6320060.7320.D6310040.8517.44C30009.B2E4.EE030010.C2B4.342110What is the result of using the clock rate 56000 command at the serial interface of the router?The interface is configured as a DCE device.The interface timers are cleared.The FastEthernet interface is made to emulate a serial interface by assigning it a timing signal.The IP address for the serial interface is configured.11Refer to the exhibit. Host A wants to access the Internet. Which combination of a Layer 2 address and a Layer 3 address will enable this access from host A?Destination MAC: 0030.8596.DE83 Default gateway: 209.165.202.130Destination MAC: 0030.8517.44C4 Default gateway: 172.16.1.1Destination MAC: 0030.8517.44C4 Default gateway: 209.165.202.13012Refer to the exhibit. A technician uses the nslookup command on the PC and views the output that is displayed in the exhibit. What is the IP address of the primary domain name server configured at the host? (Choose two.)192.168.1.99192.168.2.10010.10.10.32192.168.1.5the IP address of the website resolver1.xyz.local13Refer to the exhibit. Host A is accessing multiple servers. Which combination of port number and address will uniquely identify a particular process running on a specific server?MAC address of the server and port number of the serviceIP address of the host and port number of the serviceMAC address of the host and port number of the serviceIP address of the server and port number of the serviceRouter>Router(config-if)#Router#Router(config)#15What are three characteristics of CSMA/CD? (Choose three.)It monitors the media for presence of a data signal.After detecting a collision, hosts can resume transmission after a random timer has expired.A jam signal is used to ensure that all hosts are aware that a collision has occurred.Devices can be configured with a higher transmission priority.Data is transmitted only when the data signal is present.It uses a token system to avoid collisions.Which three statements are true about network layer addressing? (Choose three.)It uniquely identifies each host.It assists in forwarding packets across internetworks.It uses a logical 32-bit IPv4 address.It is not a configurable address.It is a physical address.It identifies the host from the first part of the address.17Refer to the exhibit. The serial interface of the router was configured with the use of the commands that are shown. The router cannot ping the router that is directly connected to interface serial 0/0/0. What should the network technician do to solve this problem?Configure the description at interface serial 0/0/0.Configure an IP address on interface serial 0/0/0.Remove the no shutdown command at interface serial 0/0/0Reboot the router.18Refer to the exhibit. The PC, the routing table of which is displayed, is configured correctly. To which network device or interface does the IP address 192.168.1.254 belong?PCswitchrouter interface fa0/0router interface fa0/119Which three IPv4 addresses represent valid host addresses for a subnet? (Choose three.)10.1.12.79/2810.1.12.113/2810.1.12.32/2810.1.11.5/2710.1.11.97/2710.1.11.128/2720Refer to the exhibit. Which two facts can be determined about the topology? (Choose two.)Three networks are needed.Two logical address ranges are required.A single broadcast domain is present.Three collision domains are present.Four networks are needed.21Refer to the exhibit. Communication between hosts X and Y is restricted to the local network. What is the reason for this?The gateway addresses are broadcast addresses.Host Y is assigned a multicast address.Host X and host Y belong to different networks.Host X is assigned a network address.22Refer to the exhibit. Which logical topology describes the exhibited network?starringpoint-to-pointmulti-access23Refer to the exhibit. The network administrator wants to remotely access the CLI of the router from PC1 using modem 1. Which port of the router should be connected to modem 2 to enable this access?consoleEthernetauxiliaryserial24Which statement is true about the running configuration file in a Cisco IOS device?It affects the operation of the device immediately when modified.It is stored in NVRAM.It should be deleted using the erase running-config command.It is automatically saved when the router reboots.25Refer to the exhibit. What two facts can be determined from the session information that is displayed? (Choose two.)This exchange is part of the three-way handshake.The destination port indicates that a Telnet session has been initiated.The source port does not support communication with the destination port that is listed.The destination port indicates that an SMTP session has been initiated.The protocol is a connection-oriented protocol.26Because of a security violation, the router password must be changed. What information can be learned from these configuration entries? (Choose two.)Router(config)# line vty 0 4Router(config-line)# password arj15Router(config-line)# loginThis configuration allows users to connect by using a modem.Users must specify which line, 0 or 4, they wish to connect to when making a connection.This configuration allows users to connect to the router via the use of the telnet command.This configuration allows five users to make simultaneous connections to this router.The configured password is automatically encrypted on the router.27Which OSI layer uses a connection-oriented protocol to ensure reliable delivery of data?application layerpresentation layertransport layer28Refer to the exhibit. Which list refers only to end devices?D,E,F,GA,H,B,CA,D,E,FA,D,E,G29Refer to the exhibit. The diagram represents the process of sending e-mail between clients. Which list correctly identifies the component or protocol used at each numbered stage of the diagram?1.MUA2.MDA3.MTA4.SMTP5.MTA6.POP7.MDA8.MUA1.MUA2.POP3.MDA4.SMTP5.MTA6.MDA7.SMTP8.MUA1.MUA2.POP3.SMTP4.MDA5.MTA6.SMTP7.POP8.MUA1.MUA2.SMTP3.MTA4.SMTP5.MTA6.MDA7.POP8.MUA30192.168.1.191192.168.1.101192.168.1.1192.168.1.254Refer to the exhibit. Each media link is labeled. What type of cable should be used to connect the different devices?Connection 1 - rollover cable Connection 2 - straight-through cable Connection 3 - crossover cableConnection 1 - straight-through cable Connection 2 - crossover cable Connection 3 - rollover cableConnection 1 - crossover cable Connection 2 - rollover cable Connection 3 - straight-through cableConnection 1 - crossover cable Connection 2 - straight-through cable Connection 3 - rollover cableConnection 1 - straight-through cable Connection 2 - straight-through cable Connection 3 - straight-through cable 32What is the effect of using the Router# copy running-config startup-config command on a router?The contents of ROM will change.The contents of RAM will change.The contents of NVRAM will change.The contents of flash will change.33Which three statements are true about transport layer protocols? (Choose three.)TCP and UDP manage communication between multiple applications.TCP retransmits the packets for which the acknowledgment is not received.TCP acknowledges received data.UDP exchanges frames between the nodes of the network.TCP has no mechanism to acknowledge transmission errors.UDP uses windowing and sequencing to provide reliable transfer of data.34Which two types of media are useful for connecting two devices separated by a distance of 500 meters? (Choose two.)10 BASE-T1000 BASE-TX10 BASE-21000 BASE LX1000 BASE-SX35Which information is used by the router to determine the path between the source and destination hosts?the host portion of the IP addressthe network portion of the IP addresshost default gateway addressthe MAC address36The network administrator wants to install a private application on a server. Which range of port numbers is normally assigned to this application to make it accessible by clients?0 to 25549152 to 655351024 to 491510 to 102337Refer to the exhibit. PC1 is unable to access PC2. To troubleshoot this problem, the technician needs to confirm that the next hop interface is operational. Which default gateway address should the technician ping from PC1 to confirm this?10.0.0.254192.168.0.249192.168.0.25010.0.1.25438Refer to the exhibit. Cable 1 and Cable 2 are wired for specific physical layer requirements. Which three segments use Cable 2?(Choose three.)Segment 1Segment 2Segment 3Segment 4Segment 5Segment 639An organization has been assigned network ID 10.10.128.0 and subnet mask 255.255.224.0. Which IP address range can be used for this organization?10.10.128.0 to 10.10.160.25510.10.128.0 to 10.10.159.25510.10.128.0 to 10.10.192.25510.10.128.0 to 10.10.0.15910.10.128.0 to 10.10.159.040Refer to the exhibit. A PC is communicating with another PC on a remote network. The two networks are connected by three routers.Which action will help to identify the path between the hosts?Use the ipconfig command at the host.Use the ipconfig/all command at the destination.Use the tracert command at the host.Use the ping command at the destination.41Which OSI layer offers ordered data reconstruction services?application layernetwork layerpresentation layersession layertransport layer42A host is transmitting a video over the network. How does the transport layer allow this host to use multiple applications to transmit other data at the same time as the video transmission?It uses error control mechanisms.It uses a connectionless protocol only for multiple simultaneous transmissions.It uses multiple Layer 2 source addresses.It uses multiple port numbers.43What are two functions of the data link layer? (Choose two.)It segments and reorders the data.It exchanges data between programs that are running on the source and destination hosts.It controls how data is placed onto the media.It generates signals to represent the bits in each frame.It encapsulates each packet with a header and a trailer to transfer it across the local media.44Refer to the exhibit. Which three statements are true about the IP configuration that is displayed? (Choose three.)The assigned address is a private address.The PC cannot communicate with the DNS server.The network can have 126 hosts.The prefix of the computer address is /26.The IP address is routable on the Internet.The IP address is a multicast address.45Refer to the exhibit. A technician has connected the PC to the switch using a Category 6 UTP cable. Which two statements are true about this connection? (Choose two.)The cable that is used is an Ethernet crossover cable.The transmit pin of the cable is terminated to the receive pin.The maximum distance between the switch and the PC can be 100 m.The maximum supported bandwidth is 1000 Mb/s.The Category 6 cable simulates a point-to-point WAN link and is unusable for this type of connection.Refer to the exhibit. Host B was powered off. What change will occur in the MAC table of the switch?The table will remain unaffected.The switch will remove the MAC address at Fa0/19 immediately.The switch will retain the MAC address until host B is powered on again.The switch will rebuild the MAC table by assigning the FFFF.FFFF.FFFF address to port Fa0/19.47Which device should be used for routing a packet to a remote network?access switchDHCP serverhubrouter48An organization wants to create a subnet of the IP network 172.16.0.0. This subnet will accommodate 1000 hosts. Which subnet mask should be assigned to this network?255.255.0.0255.255.248.0255.255.252.0255.255.254.0255.255.255.0255.255.255.12849Refer to the exhibit. Host C is able to ping 127.0.0.1 successfully, but is unable to communicate with hosts A and B in the organization.What is the likely cause of the problem?Hosts A and B are not on the same subnet as host C.The IP addresses on the router serial interfaces are wrong.The subnet mask on host C is improperly configured.The FastEthernet interface fa0/0 of router 1 is wrongly configured.50Refer to the exhibit. Host X is unable to communicate with host Y. Which command can be run at host X to determine which intermediary device is responsible for this failure?telnet 192.168.1.1ping 192.168.1.1ftp 192.168.1.1tracert 192.168.1.1。
ccna考试题及答案

ccna考试题及答案1. 以下哪项是网络层的功能?A. 路由选择B. 错误检测C. 流量控制D. 封装数据包答案:A2. 在OSI模型中,哪一层负责在网络中传输数据?A. 应用层B. 传输层C. 会话层D. 网络层答案:D3. 以下哪个协议是用于在IP网络中发现网络设备的?A. ARPB. RARPC. ICMPD. OSPF答案:A4. 在TCP/IP模型中,哪一层与OSI模型的传输层相对应?A. 应用层B. 互联网层C. 网络接口层D. 传输层答案:D5. 以下哪个地址是一个有效的IPv4地址?A. 192.168.1.256B. 192.168.1.1C. 10.0.0.0D. 172.16.300.1答案:B6. 在配置路由器时,以下哪个命令用于进入全局配置模式?A. enableB. configure terminalC. privileged execD. user exec答案:B7. 以下哪个命令用于在Cisco设备上显示当前配置?A. show running-configB. show startup-configC. show configD. show current-config答案:A8. 在Cisco设备上,以下哪个命令用于保存当前的配置到启动配置文件?A. copy running-config startup-configB. copy startup-config running-configC. save running-configD. save startup-config答案:A9. 以下哪个命令用于在Cisco设备上查看所有接口的状态?A. show interfacesB. show ip interface briefC. show interface statusD. show running-config interface答案:B10. 在Cisco设备上,以下哪个命令用于关闭接口?A. shutdownB. no shutdownC. disableD. no enable答案:A11. 以下哪个命令用于在Cisco设备上启用接口?A. shutdownB. no shutdownC. disableD. no enable答案:B12. 在配置静态路由时,以下哪个命令用于指定下一跳地址?B. ip static-routeC. route ipD. static-route ip答案:A13. 以下哪个命令用于在Cisco设备上清除ARP表?A. clear arp-cacheB. clear arpC. clear arp tableD. clear ip arp答案:D14. 在配置动态路由协议时,以下哪个命令用于在接口上启用RIP?A. ip rip enableB. ip rip receiveD. network rip答案:C15. 以下哪个命令用于在Cisco设备上查看RIP路由表?A. show ip ripB. show ip route ripC. show ripD. show ip protocols答案:B16. 在配置EIGRP时,以下哪个命令用于指定自动汇总?A. metric weightsB. auto-summaryC. network auto-summaryD. no auto-summary答案:B17. 以下哪个命令用于在Cisco设备上查看EIGRP邻居?A. show ip eigrp neighborsB. show eigrp neighborsC. show ip eigrpD. show eigrp interfaces答案:A18. 在配置OSPF时,以下哪个命令用于指定路由器ID?A. router-idB. router ospfC. networkD. area答案:A19. 以下哪个命令用于在Cisco设备上查看OSPF路由表?A. show ip ospfB. show ip ospf databaseC. show ospfD. show ip route ospf答案:D20. 在配置VLAN时,以下哪个命令用于创建一个新的VLAN?A. vlan databaseB. configure terminalC. vlan [vlan-id]D. new-vlan答案:C21. 以下哪个命令用于将接口分配给VLAN?A. switchport mode accessB. switchport mode trunkC. switchport access vlan [vlan-id]D. switchport trunk vlan [vlan-id]答案:C22. 在配置交换机时,以下哪个命令用于将接口设置为Trunk 模式?A. switchport mode accessB. switchport mode trunkC. switchport access vlan [vlan-id]D. switchport trunk vlan [vlan-id]答案:B23. 以下哪个命令用于在Cisco设备上查看VLAN配置?A. show vlanB. show vlan briefC. show vlan detailD. show vlan all答案:B24. 在配置VTP时,以下哪个命令用于将交换机设置为VTP服务器模式?A. vtp mode serverB. vtp mode clientC. vtp mode transparentD. vtp mode off答案:A25. 以下哪个命令用于在Cisco设备上查看VTP状态?A. show vtp statusB. show vtp statisticsC. show vtp passwordD. show vtp configuration答案:A26. 在配置STP时,以下哪个命令用于设置根桥?A. spanning-tree root primaryB. spanning-tree root secondaryC. spanning-tree root primary [priority]D. spanning-tree root secondary [priority]答案:C27. 以下哪个命令用于在Cisco设备上查看STP状态?A. show spanning-treeB. show spanning-tree detailC. show spanning-tree summaryD. show spanning-tree interface答案:A28. 在配置VLAN Trunking Protocol (VTP) 时,以下哪个命令用于设置VTP域名?A. vtp domain [domain-name]B. vtp password [password]C. vtp mode [mode]D. vtp version [version]答案:A29. 以下哪个命令用于在Cisco设备上查看当前的VTP版本?A. show vtp statusB. show vtp statisticsC. show vtp passwordD. show vtp configuration答案:A30. 在配置端口安全时,以下哪个命令用于限制接口上可以学习到的最大MAC地址数量?A. switchport port-security maximum [mac-count]B. port-security maximum [mac-count]C. switchport port-security violation restrictD. port-security violation shutdown答案:A这些题目和答案仅供学习和参考之用,实际的CCNA考试内容和形式可能会有所不同。
思科第一学期期末考试考题CCNA

1Refer to the exhibit. Which Layer 2 protocol could be used inside nework A and network C?IPTCPUDPEthernet2Refer to the exhibit. Which set of devices contains only intermediary devices?A, B, D, GA, B, E, FC, D, G, IG, H, I, J3Refer to the exhibit. The headers added at each layer are shown. Which layer adds the destination and source process num ensure that data is delivered to the correct application?physical layerdata link layernetwork layertransport layer4The Layer 4 header contains which type of information to aid in the delivery of data?service port numberhost logical addressdevice physical addressvirtual connection identifier5Which fiber connector supports full-duplex Ethernet?6Which device should be used for routing a packet to a remote network?access switchDHCP serverhubrouter7Refer to the exhibit. Host A sends a frame to host C with a destination MAC address CC. The MAC address for host C is no table of switch SW1. How will SW1 handle the frame?Switch SW1 will drop the frame.Switch SW1 will forward the frame to host C.Switch SW1 will flood the frame out all ports.Switch SW1 will flood the frame out all ports except port Fa0/1.8Refer to the exhibit. A network technician has made several changes to R1 since the configuration has last been saved. Th configuration did not produce the desired changes. The technician wants to store a backup copy of the saved configurationserver before reloading. Which action will cause the unmodified data to be saved on the TFTP server?9Which three statements are true about network layer addressing? (Choose three.)It uniquely identifies each host.It assists in forwarding packets across internetworks.It uses a logical 32-bit IPv4 address.It is not a configurable address.It is a physical address.It identifies the host from the first part of the address.10What is the result of using the clock rate 56000 command at the serial interface of the router?The interface is configured as a DCE device.The interface timers are cleared.The FastEthernet interface is made to emulate a serial interface by assigning it a timing signal.The IP address for the serial interface is configured.11Examine the graphic with current configurations. Host A in the Clerical office failed and was replaced. Although a ping to 12 successful, the replacement computer cannot access the company network. With proxy ARP disabled on the Fa0/0 interfac York router, what is the likely cause of the problem?network card failurenetwork cables unpluggedIP address incorrectly enteredsubnet mask incorrectly entered12As network administrator, what is the subnet mask that allows 510 hosts given the IP address 172.30.0.0?255.255.0.0255.255.248.0255.255.252.0255.255.254.0255.255.255.0255.255.255.12813Which OSI layer uses a connection-oriented protocol to ensure reliable delivery of data?application layerpresentation layersession layertransport layer14 A network has grown too large for technicians to configure network addresses and hosts files for name resolution. Which twlayer services should be added to the server to allow these needs to be satisfied dynamically? (Choose two.)DNSFTPDHCPHTTPSMTP15Refer to the exhibit. Host A wants to access the Internet. Which combination of a Layer 2 address and a Layer 3 address w access from host A?Destination MAC: 0030.8596.DE83 Default gateway: 209.165.202.130Destination MAC: 0030.8596.DE82 Default gateway: 172.16.9.2Destination MAC: 0030.8517.44C4 Default gateway: 172.16.1.1Destination MAC: 0030.8517.44C4 Default gateway: 209.165.202.13016 A network administrator is asked to design a new addressing scheme for a corporate network. There are 60 users in the musers in the branch office, 28 users in manufacturing, 12 in the sales office, and 4 users in the research office. Which VLSM scheme that uses the 192.168.88.0/24 network will fulfill the requirements while wasting the fewest addresses?192.168.88.0/26 main192.168.88.64/26 manufacturing192.168.88.96/27 sales192.168.88.128/28 research192.168.88.0/26 main192.168.88.128/27 manufacturing192.168.88.160/28 sales192.168.88.176/29 research192.168.88.0/27 main192.168.88.64/28 manufacturing192.168.88.80/29 sales192.168.88.88/30 research192.168.88.0/27 main192.168.88.80/28 manufacturing192.168.88.96/29 sales192.168.88.104/30 research17Which physical connector type is used for a serial V.35 connection to the CSU/DSU?18Refer to the exhibit. Which two facts can be determined about the topology? (Choose two.)Four collision domains are present.One logical network is represented.Two broadcast domains are present.Three networks are needed.Three logical address ranges are required.19What are three characteristics of CSMA/CD? (Choose three.)It monitors the media for presence of a data signal.After detecting a collision, hosts can resume transmission after a random timer has expired.A jam signal is used to ensure that all hosts are aware that a collision has occurred.Devices can be configured with a higher transmission priority.Data is transmitted only when the data signal is present.It uses a token system to avoid collisions.20Refer to the exhibit. The serial interface of the router was configured with the use of the commands that are shown. The rou ping the router that is directly connected to interface serial 0/0/0. What should the network technician do to solve this probleConfigure the description at interface serial 0/0/0.Configure an IP address on interface serial 0/0/0.Remove the no shutdown command at interface serial 0/0/0Reboot the router.21Which OSI layer uses the header information to reassemble the data segments into streams?application layernetwork layerpresentation layersession layertransport layer22Refer to the exhibit. The NAT functionality of the router is enabled to provide Internet access to the PC. However, the PC is access the Internet. Which IP address should be changed to 209.165.201.1 to enable the PC to access the Internet?192.168.1.191192.168.1.101192.168.1.1192.168.1.25423Refer to the exhibit. A technician uses the nslookup command on the PC and views the output that is displayed in the exhib IP address of the primary domain name server used by the host?10.10.10.32192.168.1.5192.168.1.99192.168.2.10024Which memory contents will change as a result of using the Router# erase startup-config command on a router?RAMROMflashNVRAM25While configuring a router, a network technician wants to name the router. Which prompt should the technician see when e hostname command?Router>Router#Router(config)#Router(config-line)#26Refer to the exhibit. The PC, the routing table of which is displayed, is configured correctly. To which network device or inte IP address 192.168.1.254 belong?PCswitchrouter interface fa0/0router interface fa0/127Refer to the exhibit. A network administrator is troubleshooting a link that is down between Router1 and Router2. To correc which wire pairs need to be switched on one of the Ethernet cable ends?pair 1 and pair 2pair 1 and pair 3pair 2 and pair 3pair 2 and pair 428Refer to the exhibit. A PC is connected to a network. Which action will verify that the PC can communicate with its default gUse the ping 127.0.0.1 command.Use the ipconfig command.Use the ipconfig/all command.Use the ping 10.0.0.254 command.29Refer to the exhibit. Host B was powered off. What change will occur in the MAC table of the switch?The table will remain unaffected.The switch will remove the MAC address at Fa0/19.The switch will retain the MAC address until host B is powered on again.The switch will rebuild the MAC table by assigning the FFFF.FFFF.FFFF address to port Fa0/19.30What information is contained in the header of Layer 3 to help data delivery?port numberdevice physical addressdestination host logical addressvirtual connection identifier31 A network technician is tasked with setting up a network for six users, but the users should be able to use their accounts toany of the six computers. What type of network should be used?workgroupP2P applicationspeer-to-peer networkclient-server network32Refer to the exhibit. A web browser is running on host PC1 with an IP address 10.10.2.2/24. A dynamic port number of 4915 to the browser. The browser sends a request for a web page to the web server with an IP address 192.168.1.254/24. Which true?The session is established using TCP, and the socket number for the web server is 192.168.1.254: 80.The session is established using TCP, and the socket number for the web server is 192.168.1.254: 49152.The session is established using UDP, and the socket number for the web server is 192.168.1.254: 80.The session is established using UDP, and the socket number for the web server is 192.168.1.254: 49152.33Refer to the exhibit. An administrator on PC1 wants to view some HTML code from a web page housed on the web server. application will allow this request to be started?34Refer to the exhibit. What is required on host A for a network technician to create the initial configuration on Router1?an FTP clienta Telnet clienta terminal emulation programa web browser35What are two characteristics of the data link layer? (Choose two.)It segments and reorders the data.It exchanges the frames between nodes.It defines the method by which network devices place data onto the media.It manages the transfer of data between the processes that run on each host.It retrieves signals from the media and restores them to their bit representations.36 A network administrator wants to restrict access to the router privileged EXEC mode. Which password should the administrenableauxconsoleVTY37Which three IPv4 addresses represent a broadcast for a subnet? (Choose three.)172.16.4.63 /26172.16.4.129 /26172.16.4.191 /26172.16.4.51 /27172.16.4.95 /27172.16.4.221 /2738Refer to the exhibit. Host X is unable to communicate with host Y. Which command can be run at host X to determine whic device is responsible for this failure?telnet 192.168.1.1ping 192.168.1.1ftp 192.168.1.1tracert 192.168.1.139Refer to the exhibit. Which option shows the correct topology given the configuration of Router1?40If an administrator wished to return a router to the default state, what additional step must be taken after issuing the comma start-up config?Reload the device.Issue the command copy running-config start-up config.Perform a show running-config to verify that the file was removed.Enter the interface commands to allow the device to connect to the network.41By using the ipconfig command, a network administrator determines that a workstation has the address 192.168.3.38 with the subnet mask. To what network does the workstation belong?192.168.3.8192.168.3.16192.168.3.24192.168.3.3242Which statement is true about router hostnames?A hostname should be unique on each router.A router hostname cannot contain capital letters.A router hostname is configured in privileged executive mode.A router hostname must be created before any other configurations can be added to the device.43 A user types the enable command. What task can be performed at the privileged EXEC mode?Configure the device.Configure individual interfaces.Configure individual terminal lines.Issue show and debug commands.44Refer to the exhibit. Which logical topology describes the exhibited network?starringpoint-to-pointmulti-access45Refer to the exhibit. A user wants to access the Internet from the PC. A part of the running configuration of the router is sho default gateway IP address should be configured at the PC to enable this access?10.1.192.110.1.192.210.1.192.54192.31.7.146Which statement is true about the ICMP protocol?It is an application layer protocol.It is designed to make IP a reliable protocol.It is often filtered out of networks for security purposes.If a host does not respond to an ICMP echo request, the host is not functioning.47Refer to the exhibit. At which OSI layer is serial interface 0/0/1 experiencing problems?Layer 1Layer 2Layer 3Layer 448Refer to the exhibit. The host was disconnected from switch 2 and connected to switch 1. Which combination of IP address, and default gateway should be assigned to this host to allow it to function in the network?IP address: 10.10.9.37 Subnet mask: 255.255.255.240 Default gateway: 10.10.9.35IP address: 10.10.9.37 Subnet mask: 255.255.255.224 Default gateway: 10.10.9.35IP address: 10.10.9.29 Subnet mask: 255.255.255.248 Default gateway: 10.10.9.35IP address: 10.10.9.32 Subnet mask: 255.255.255.224 Default gateway: 10.10.9.35IP address: 10.10.9.37 Subnet mask: 255.255.255.224 Default gateway: 196.1.105.6IP address: 10.10.9.63 Subnet mask: 255.255.255.224 Default gateway: 10.10.9.3549Refer to the exhibit. The diagram represents the process of sending email between clients. Select the list below that correc the component or protocol used at each numbered stage of the diagram.1.MUA2.MDA3.MTA4.SMTP5.MTA6.POP7.MDA8.MUA1.MUA2.POP3.MDA4.SMTP5.MTA6.MDA7.SMTP8.MUA1.MUA2.POP3.SMTP4.MDA5.MTA6.SMTP7.POP8.MUA1.MDA2.SMTP3.MTA4.SMTP5.MTA6.MUA7.POP8.MDA1.MUA2.SMTP3.MTA4.SMTP5.MTA6.MDA7.POP8.MUA50What is the Cisco IOS?system software for Cisco devicesRead Only Memory in Cisco devicesnon-volatile storage for device configurationsan initial operating system that is used for boot functions。
ccna1章节与期末答案

第一章:正确答案:2.4.5解析:由于不需要使用网络设备和专用服务器,对等网络易于创建,复杂性更低,且成本更少。
而且对等网络也没有集中管理。
这种网络安全性更低,不可扩展,而且那些同时充当客户端和服务器的设备可能性能更差正确答案:1解析:正确答案: 3.5解析:选择网络介质的条件包括:所选介质可以成功传送信号的距离、要安装所选介质的环境、必须传输的数据量和速度以及介质和安装的成本。
正确答案:3和4解析:终端设备上的应用程序可以生成数据,更改数据内容并且负责启动封装过程。
正确答案:1和4解析:终端设备会发出通过网络传输的数据。
中间设备会在链路发生故障时通过备用路径传输数据,并且会过滤数据传输以增强安全性。
网络介质提供网络消息的传输通道。
正确答案:4解析:外联网是公司外部的人或企业合作伙伴访问数据的网络区域。
内部网只描述通常仅供内部人员访问的网络区域。
当设备连接到有线网络时,有线LAN 会受BYOD(自带设备)影响。
使用大学无线LAN 的设备多为平板电脑和智能手机。
大学生主要使用无线WAN 来访问他们的手机运营商网络。
.正确答案:2解析:由于通过Internet 可以联系在线供应商,所以家庭用户通过Internet 进行网上购物。
内联网基本上是仅供内部使用的局域网。
外联网是外部合作伙伴访问组织内部特定资源的网络。
家庭用户并不一定使用LAN 来访问Internet。
例如,PC 可以通过调制解调器直接连接到ISP。
正确答案:1解析:内部网这个术语用于表示一个组织的私有局域网和广域网连接。
内部网的设计旨在仅允许该组织的成员、员工或其他获得授权的人员进行访问。
正确答案:2和4解析:电缆和DSL 均能实现高带宽、始终联网,并提供到主机计算机或LAN 的以太网连接。
10正确答案:2和3解析:移动电话连接需要使用移动电话网络。
卫星连接通常用于家庭或企业外部不便使用物理布线的位置。
11正确答案:2解析:当对网络资源的请求超出了可用容量时,网络就会变得拥堵。
CCNA第二学期期末考试Final:Exam

路由器获知到的第一条路径仅使用路由器获知到的前两条路径路由器获知到的最后一条路径全部四条路径对于为防备路由环路而经过毒性反转实现的水平切割方法,哪两项表达正确?(选择两项。
)全部Cisco IOS都会默认启用此方法。
会将一个表示无量大胸怀的值分派给路由以将其毒化。
将毒化路由更新发回该更新的发送接口。
指示路由器将可能会影响路由的改正保持一段特定的时间。
限制数据包在被抛弃以前能够在网络中传输的跳数。
在两台路由器能够使用OSPF形成街坊毗邻关系以前一定达成哪两项任务?(选择两项。
)路由器一定选举出指定路由器。
路由器一定在网络种类方面达成一致。
路由器一定使用同样的dead时间间隔。
路由器一定互换链路状态恳求。
路由器一定互换数据库描绘数据包。
以下路由器组件和操作的配对中,哪两项是正确的?(选择两项。
)DRAM -加载bootstrapRAM -储存操作系统闪存- 启动时履行诊疗NVRAM -储存配置文件ROM -存贮备份配置文件POST -运转硬件模块诊疗以下对于无类路由协议的陈说,哪两项是正确的?(选择两项。
)无类路由协议可用于不连续子网。
无类路由协议可在路由更新中转发超网路由。
无类路由协议没法在路由表中实行有类路由。
无类路由协议仅使用跳数胸怀。
无类路由协议的路由更新中不包含子网掩码。
请拜见图示。
在图示的此中一台设施上运转了show cdp neighbors命令。
依据此信息,可推测出哪两项结论?(选择两项。
)在路由器上运转了该命令。
ABCD是一台非CISCO设施。
两台设施间存在第 3 层连通性。
ABCD支持路由功能。
ABCD连结到相邻设施的Fa0/0接口。
R3 。
图中显示了全部三台路由器的路由。
从该输出能够获得什么结论?请拜见图示。
网络连结有三台路由器:R1 、 R2 和R1和R3经过S0/0/0接口相连。
R1 S0/0/0接口的IP 地点为10.1.1.2 。
R2 S0/0/1接口的IP 地点为10.3.3.2 。
ccna_final_exam_ccna第一学期期末考试20-0-0

ENetwork Final Exam -CCNA Exploratio n:网络基础知识(版本4.0)1下列有关网络层编址的陈述中哪三项是正确的?(选择三项。
)网络层编址使用分层式结构。
使用长度为48位的地址。
以太网交换机可以使用它来作出转发决定。
它不支持广播。
其使用的编址方法可以识别地址的网络部分。
网络层编址可以区分每台主机。
请参见图示。
在PC上发出所示的命令。
IP地址代表什么? 主机的IP地址主机的默认网关主机的主页IP地址主机的首选域名服务器网站的IP地址。
哪三个地址属于公有IP地址?(选择三项。
)数据链路层有哪两项功能?(选择两项)分割和记录数据。
在源主机和目的主机上运行的程序之间进行数据交换。
控制数据如何传递到介质中。
CCNA19连接 直通电缆,连接 直通电缆,连接 交叉电缆 连接 直通电缆,连接 交叉电缆,连接 全反电缆 连接 交叉电缆,连接 全反电缆,连接 直通电缆 连接 交叉电缆,连接 直通电缆,连接 交叉电缆 连接直通电缆,连接全反电缆,连接交叉电缆IP : 172 16J.20 MAC: 0007J1F74.AC09请参见图示。
主机 A 要访问In ter net 。
哪项第2层地址和第3层地址的组合可以让主机 A 实现此访问? 目的MAC :,默认网关:目的MAC :,默认网关: 目的MAC :,默认网关:目的MAC :,默认网关: 下列哪三项是CSMA/CD 的特征?(选择三项。
)设备会侦听介质,并且仅当无法检测到介质上存在其它信号时才会传输数据。
介质上的所有设备均可侦听所有通信。
设备根据配置的优先级来进行通信。
发生冲突后,引起冲突的设备会优先尝试传输数据。
发生冲突时,所有设备会在一段时间内停止传输数据,该段时间的长度随机决定。
CSMA/CD 使用令牌系统来避免冲突。
下列哪三个IPv4地址代表子网的有效网络地址?(选择三项。
)FaO/1: 172.16.9.1 MAC : 0030.8517.44C3Fa0/0:172.16.9.2Fa0/0:172.16.1.1 MAC : 003C 859€,DE&2 MAC: 0030.851 儿44C4FaO/1: M9.165.202.130MAC: 0030.8596, DEB3Internet主机A请参见图示。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
CCNA1ENetworkFinal Exam- CCNAExploration: 网络基础知识(版本 4.0)1下列有关网络层编址的陈述中哪三项是正确的?(选择三项。
)网络层编址使用分层式结构。
使用长度为48 位的地址。
以太网交换机可以使用它来作出转发决定。
它不支持广播。
其使用的编址方法可以识别地址的网络部分。
网络层编址可以区分每台主机。
2请参见图示。
在PC 上发出所示的命令。
IP 地址代表什么?主机的IP 地址主机的默认网关主机的主页IP 地址主机的首选域名服务器网站的IP 地址。
3哪三个地址属于公有IP 地址?(选择三项。
)4数据链路层有哪两项功能?(选择两项)分割和记录数据。
在源主机和目的主机上运行的程序之间进行数据交换。
控制数据如何传递到介质中。
生成信号以表示每个帧中的比特。
使用帧头和帧尾封装每个数据包,以便在本地介质中进行传输。
5请参见图示。
主机A 要访问Internet。
哪项第2 层地址和第3 层地址的组合可以让主机A 实现此访问?目的MAC:,默认网关:目的MAC:,默认网关:目的MAC:,默认网关:目的MAC:,默认网关:6下列哪三项是CSMA/CD 的特征?(选择三项。
)设备会侦听介质,并且仅当无法检测到介质上存在其它信号时才会传输数据。
介质上的所有设备均可侦听所有通信。
设备根据配置的优先级来进行通信。
发生冲突后,引起冲突的设备会优先尝试传输数据。
发生冲突时,所有设备会在一段时间内停止传输数据,该段时间的长度随机决定。
CSMA/CD 使用令牌系统来避免冲突。
7下列哪三个IPv4 地址代表子网的有效网络地址?(选择三项。
)8请参见图示。
用记号来表示每条介质链路。
用来连接不同设备的正确电缆类型是什么?连接1 - 直通电缆,连接2 - 直通电缆,连接3 - 交叉电缆连接1 - 直通电缆,连接2 - 交叉电缆,连接3 - 全反电缆连接1 - 交叉电缆,连接2 - 全反电缆,连接3 - 直通电缆连接1 - 交叉电缆,连接2 - 直通电缆,连接3 - 交叉电缆连接1 - 直通电缆,连接2 - 全反电缆,连接3 - 交叉电缆9请参见图示。
主机C 能够成功地ping 通,但无法与组织中的主机A 和B 通信。
此问题的原因可能是什么?主机A 和B 与主机 C 不在同一个子网中。
路由器串行接口上的IP 地址有误。
主机C 配置的子网掩码不正确。
路由器1 的FastEthernet 接口配置有误。
10请参见图示。
根据显示的IP 配置回答,主机A 和主机B 无法在本地网络外通信的原因是什么?对主机A 分配了网络地址。
对主机B 分配了组播地址。
主机A 和主机B 属于不同的网络。
对网关地址分配了广播地址。
11请参见图示。
假设所有设备均使用默认配置。
支持显示的拓扑需要多少个子网?1345712请参见图示。
主机A 发送了一个以为目的MAC 地址的帧。
交换机将如何处理该帧?它会丢弃该帧。
它会将该帧送回到主机A。
它会将该帧发送到除主机A 之外的所有主机。
它会将该帧转发到默认网关。
13哪个OSI 层提供面向连接的可靠数据通信服务?应用层表示层会话层传输层网络层14当客户端应用程序发出到服务器的连接时,下列哪一个范围的端口号会动态地分配到客户端应用程序?0 到2550 到10231024 到49151大于6553515请参见图示。
路由器的路由表如图所示。
该路由器收到以为目的地址的数据包。
它将如何处理该数据包?它会丢弃数据包。
它会通过FastEthernet 0/1 转发该数据包。
它会将数据包转发到下一跳地址。
它会将数据包转发到。
16请参见图示。
对图示拓扑可以得出哪两项结论?(选择两项)需要三个网络。
需要两个逻辑地址范围。
存在一个广播域。
存在三个冲突域。
需要四个网络。
17作为网络管理员,假设IP 地址为,能够支持510 台主机的子网掩码是什么?18下列有关在Cisco IOS 设备上运行配置文件的陈述,哪一项是正确的?修改配置文件会立即对设备的操作造成影响。
配置文件存储在NVRAM 中。
可使用erase running-config命令删除配置文件。
路由器重新启动时会自动保存配置文件。
19请参见图示。
PC 已连接到网络。
下列哪一项操作将验证PC 能够与其默认网关通信?使用命令。
使用ipconfig命令。
使用ipconfig/all命令。
使用命令。
20您所在的网际网络发生了路由问题。
要鉴别此错误,应该检查以下哪种设备?接入点主机集线器路由器交换机21请参见图示。
路由器已启用NAT 功能以供PC 访问Internet,但是PC 仍然无法访问Internet。
为了让PC 能够访问Internet,应将哪一项IP 地址更改为?22请参见图示。
路由器的串行接口已使用图中所示的命令进行配置。
路由器无法ping 通直接连接到serial 0/0/0 接口的路由器。
网路技术人员应该如何解决此问题?配置Serial 0/0/0 接口的描述。
配置serial 0/0/0 接口的IP 地址。
在serial 0/0/0 接口上删除no shutdown命令重新启动路由器。
23请参见图示。
主机X 无法与主机Y 通信。
在主机X 上运行哪一项命令可识别导致此故障的中间设备?tracert24网络技术人员想要使用ip命令在路由器接口上配置IP 地址。
输入此命令后,技术人员会看到下列哪一项提示?Router>Router(config-if)#Router#Router(config)#25请参见图示。
下列关于图中所示IP 配置的陈述,哪三项是正确的?(选择三项)分配给该计算机的地址代表私有地址。
该计算机无法在本地网络外通信。
此计算机的网络可支持126 台主机。
该计算机地址的前缀是/27。
分配给该计算机的IP 地址可在Internet 上路由。
分配给该计算机的IP 地址是广播地址。
26下列有关网络层编址的陈述中哪三项是正确的?(选择三项。
)唯一标识每台主机。
有助于通过网际网络转发数据包。
使用32 位逻辑IPv4 地址。
是不可配置的地址。
是物理地址。
通过地址的第一部分来标识主机。
27当OSI 模型下层执行无连接协议时,通常使用什么来确认数据已收到并请求重传丢失的数据?IPUDP以太网无连接确认面向连接的上层协议或服务28请参见图示。
从显示的会话信息中可以得出以下哪两个结论?(选择两项)所用的协议是一种面向连接的协议。
此交换是三次握手的一部分。
SYN 标志代表开始建立会话。
目的端口表示已经发起了FTP 会话。
源端口不支持与列出的目的端口通信。
29请参见图示。
主机A 要连接到位于不同网络中的主机B。
为了实现此连接,可以为主机A 分配哪三项IP 地址?(选择三项。
)30请参见图示。
某用户要从PC 访问Internet。
路由器的部分运行配置如图所示。
要实现此访问,应该为PC 配置下列哪一个默认网关IP 地址?31请参见图示。
网络中的主机A 和B 正在传输层交换数据段。
下列关于此交换的陈述,哪两项是正确的?(选择两项)主机A 正在使用FTP 向主机B 传输文件。
主机A 将发送起始字节编号为11 的下一数据段。
目的主机的数据段表示已成功收到11 字节。
主机A 正在发起到主机B 的Telnet 会话。
主机B 可以发送开始字节编号为2 的下一数据段。
32在路由器的串行接口处使用clock rate 56000命令会产生什么结果?接口被配置为DCE 设备。
接口的计时器信息被清除。
通过为FastEthernet 接口分配计时信号,使其模拟串行接口。
串行接口的IP 地址得以配置。
33请参见图示。
主机A 要访问电子邮件。
要传达此请求,将使用哪一个目的套接字数字?34下列哪一个OSI 层负责管理数据段?应用层表示层会话层传输层35由于发生安全规规事件,必须更改路由器口令。
从以下配置项可获知什么信息?(选择两项。
)Router(config)#line vty 0 3Router(config-line)# password c13c0Router(config-line)#login这些配置项对远程访问指定了三条Telnet 线路。
这些配置项对远程访问指定了四条Telnet 线路。
这些配置项将控制台口令和Telnet 口令设置为"c13c0"。
因为Telnet 配置不完整,所以Telnet 访问将遭到拒绝。
允许使用"c13c0" 作为口令访问Telnet。
36一位技术人员必须通过要求提供口令来确保交换机特权执行模式的安全。
哪种类型的口令能满足此类登录的需要并可视为最安全的口令?控制台电缆使能使能加密口令VTY37请参见图示。
技术人员正在处理网络问题,需要验证路由器的LAN 接口。
要确认路由器接口工作正常,应该从此主机ping 哪个地址?38哪种口令在创建时自动加密?vtyaux控制台电缆使能加密口令使能口令39请参见图示。
网络管理员使用Telnet 从PC1 远程访问RouterB 的CLI。
下列有关此连接的陈述中哪一项正确?数据经过自动加密。
Telnet 服务器进程正在PC1 上运行。
连接通过路由器上的VTY 会话而进行。
在此会话期间,RouterB 收到要求检索数据的GET 请求。
40请参见图示。
图中所示的主机连接到集线器1。
为了让该主机在网络中正常工作,应该为其分配怎样的IP 地址、子网掩码和默认网关?IP 地址,子网掩码:,默认网关:IP 地址,子网掩码:,默认网关:IP 地址,子网掩码:,默认网关:IP 地址,子网掩码:,默认网关:IP 地址,子网掩码:,默认网关:IP 地址,子网掩码:,默认网关:41请参见图示。
主机A 尝试与主机B 建立TCP/IP 会话。
尝试期间,捕获了源MAC 地址为而目的MAC 地址为的帧。
捕获的帧中封装了源IP 地址为而目的IP 地址为的数据包。
此数据包是在网络中哪一点捕获的?离开主机A离开ATL离开Dallas离开NYC42请参见图示。
哪种逻辑拓扑是对图示网络最准确的描述?星型环型点对点总线网状43请参见图示。
在配置网络时,技术人员采用如图所示的方式对5e 类电缆两端进行接线。
下列关于此设置的陈述,哪两项是正确的?(选择两项)该电缆适用于将交换机连接到路由器的以太网端口。
该电缆适用于连接不同类型的设备。
电缆无法使用,必须重新接线。
该电缆的端接方式为将发送引脚连接到接收引脚。
该电缆模拟了点对点WAN 链路。
44下列哪三项陈述说明了传输层协议的特征?(选择三项)应用层协议使用TCP 端口号和UDP 端口号。
TCP 使用端口号提供可靠的IP 数据包传输。
UDP 使用窗口和确认获得可靠的数据传输。
TCP 使用窗口和定序提供可靠的数据传输。
TCP 是面向连接的协议。
