东软防火墙配置
02.neteye firewall 5200_初始设置

课程目标
• 了解初始设置的连接方式 • 了解初始设置的配置过程
初始设置的连接方式
• 设备初始设置的准备工作,连接方式,用一 台PC连接防火墙的CONSOLE口,如下图 :
配置过程
• 打开PC “开始菜单”>“附件” >“通讯” >“ 超级终端”,任意输入名称点击确定,如 图:
配置过程
• 选择相应的连接端口,通常默认为COM1口 ,然后确定,如图:
配置过程
• 进行所选网卡的设置,直接回车代表选择 括号中默认值:
• Please input IP address (192.168.1.100): 10.1.1.1
• Please input subnet mask (255.255.255.0):
• Please enter default router to use with selected interface (192.168.1.1):
回顾
• NetEye FW5200如何进行初始设置。 • NetEye FW5200初始设置的连接方式。 • NetEye FW5200初始设置的配置过程。
初始设置
演讲人: 唐作夫 tangzf@ 网络安全产品营销中心 东软集团股份有限公司
Copyright 2008 By Neusoft Group. All rights reserved
初始设置
• NetEye FW5200防火墙提供了方便快捷的 初始化设置功能,设备开箱后必须进行初 始设置,设置后才可以对防火墙进行进一 步配置。另外,当防火墙执行恢复出厂设 置操作后也必须进行该操作。
配置过程
• 配置完成进行登录: • You now have access to WebUI and can
东软防火墙配置
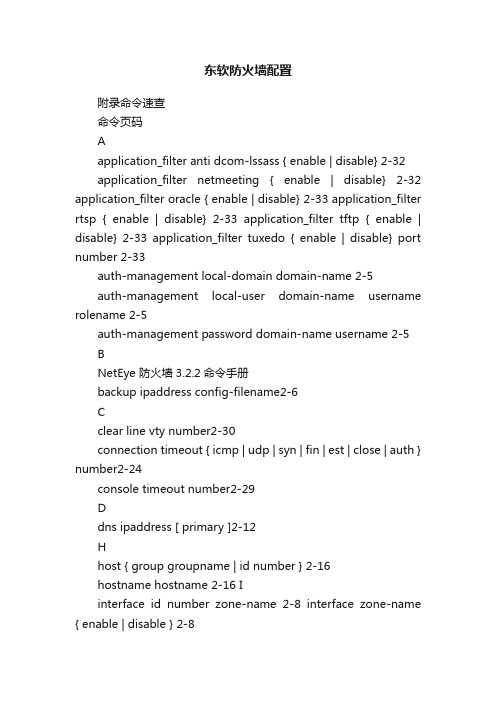
东软防火墙配置附录命令速查命令页码Aapplication_filter anti dcom-lssass { enable | disable} 2-32application_filter netmeeting { enable | disable} 2-32 application_filter oracle { enable | disable} 2-33 application_filter rtsp { enable | disable} 2-33 application_filter tftp { enable | disable} 2-33 application_filter tuxedo { enable | disable} port number 2-33auth-management local-domain domain-name 2-5auth-management local-user domain-name username rolename 2-5auth-management password domain-name username 2-5 BNetEye 防火墙3.2.2命令手册backup ipaddress config-filename2-6Cclear line vty number2-30connection timeout { icmp | udp | syn | fin | est | close | auth } number2-24console timeout number2-29Ddns ipaddress [ primary ]2-12Hhost { group groupname | id number } 2-16hostname hostname 2-16 Iinterface id number zone-name 2-8 interface zone-name { enable | disable } 2-8interface zone-name ipaddress netmask 2-8L附录命令速查license { generate | upload | download } ipaddress filename 2-2Mmode { route | switch } [ anti-attack ] 2-9Nno auth-management domain-name 2-5no auth-management local-user domain-name username 2-5no dns ipaddress 2-12 no host { id | group } 2-16no interface zone-name ipaddress netmask 2-8no proxy address ipaddress 2-12no proxy route ipaddress netmask [ gateway ] 2-11no proxy vlanpass number 2-12no radius-server1-1no route dst-ipaddress netmask zone-name [ ipaddress [ metric number] ] |[metric number [ ipaddress ] ] ] 2-10NetEye 防火墙3.2.2命令手册no route dst-ipaddress netmask ipaddress [ zone-name [ metric number ] ] |[ metric number [ zone-name ] ] 2-10no route dst-ipaddress netmask metric number [ zone-name [ ipaddress ] ] |2-11[ ipaddress [ zone-name ] ]no rule nat number 2-14 no rule nip number 2-20 no rule ip-mac number 2-21no rule local-access number 2-23no rule multicast number 2-22no rule packet-filter number 2-20no system time ntp 2-3no user username 1-2 Ppassword2-5password [ username ] 1-2 ping { ipaddress | hostname | domain } 2-3附录命令速查proxy address ipaddress netmask mac zone-list [ vlan number type 802.1q ] 2-11proxy route dst-ipaddress netmask gateway 2-11proxy vlanpass number 2-12 Rradius-server host ipaddress [ port number ]1-1radius-server port number 1-1 radius-server secret 1-1reboot 2-3reset 2-3restore ipaddress config-filename 2-6route dst-ipaddress netmask ipaddress[ zone-name [ metric number ] ]|[ metric number [ zone-name ] ] 2-10route dst-ipaddress netmask zone-name [ ipaddress [ metric numbe r ] ] |2-10[ metric number [ ipaddress ] ]rule ip-mac move srcnumber dstnumber 2-21rule ip-mac otherip { permit | deny } 2-21NetEye 防火墙3.2.2命令手册rule ip-mac sequence number { enable | disable } 2-21rule ip-mac zone { ipaddress-list | any} macaddress{enable| disable }[ sequence number ] 2-21rule local-access { ip-range | any } [ mac ] zone ipaddress service { ping |authentication | management | auth-pwd } { permit | deny } { enable | disable }2-23[ sequence number ]rule local-access { ip-range | any }[ mac ] zone ipaddress service { tcp | udp }{ port-range | any } { permit | deny } { enable | disable }[ sequence2-23number ]rule local-access move srcnumber dstnumber 2-23rule local-access sequence number advanced worktime { { on week timelist }2-23| off }rule local-access sequence number { enable | disable } 2-23 rule multicast move srcnumber dstnumber 2-22 rule multicast sequence number advanced audit { on | off } 2-22 rule multicast sequence number advanced worktime { { on week timelist } |2-22off }rule multicast sequence number { enable | disable } 2-22rule multicast source client { iplist | any } { permit | deny }{enable | disable }2-22[ sequence number ]附录命令速查rule nat move srcnumber dstnumber 2-14rule nat non-single src-zone { sip-list | any } dst-zone { dip | dip-range }2-14{service { { { tcp | udp } sip { { sport dip dport } | { { sport-range | any } dip } }[ domain ] } | { icmp sip dip } } enable | disable } [ sequence number ]rule nat sequence number { enable | disable } 2-14rule nat single src-zone sip dst-zone dip { enable | disable } [ sequence2-14number ]rule nip move srcnumber dstnumber 2-21 rule nip sequence number advanced worktime { { on week timelist } | off } 2-20 rule nip sequence number { enable | disable } 2-21rule nip src-zone { smac-list | any } dst-zone { dmac-list | any } protocol name{ protocolnumber | any} { permit | deny } {enable | disable }[ sequence2-20number ]rule packet-filter move srcnumber dstnumber 2-20rule packet-filter sequence number advanced audit { on | off } 2-19rule packet-filter sequence number advanced authentication { { on2-19auth-domain } | off }rule packet-filter sequence number advanced syncheck { on | off } 2-19rule packet-filter sequence number advanced worktime { { on week timelist } |2-19off }rule packet-filter sequence number { enable | disable } 2-20 NetEye 防火墙3.2.2命令手册rule packet-filter src-zone { sip-list | any } dst-zone { dip-list | any } protocolname icmp { echoreply | echo | info_request | info_reply | timestamptimestampreply | address | addressreply | dest_unreach | source_quench |2-18 redirect | time_exceeded | parameterprob | all } { permit | deny } { enable |disable } [ sequence number ]rule packet-filter src-zone { sip-list | any } dst-zone { dip-list | any } protocolname other { protocolnumber | any }{ permit | deny } { enable | disable }2-19 [ sequence number ]rule packet-filter src-zone { sip-list | any } dst-zone { dip-list | any } protocolname tcp { srcport | any } { dstport | any } { permit | deny } { enable |disable } [ sequence number ] 2-18rule packet-filter src-zone { sip-list | any } dst-zone { dip-list | any } protocolname udp { srcport | any } { dstport | any } { permit | deny } { enable |2-18 disable } [ sequence number ]Sservice audit { enable | disable } { local | network ipaddress | syslog3-1 ipaddress port }service ids { enable | disable } 2-28 service telnet { enable vty number [ timeout time ] | disable } 2-29 show connection status2-24附录命令速查show connection timeout { icmp | udp | syn | fin | est | close | auth | all } 2-24show dns 2-13show host 2-16show interface [ zone-name ] 2-8 show line 2-30show mode 2-9show proxy address 2-12show proxy route 2-11show proxy vlanpass 2-12show radius-server 1-2show route 2-11show rule ip-mac [ number ] 2-22show rule local-access [ number ] 2-24show rule multicast [ number ] 2-23show rule nat [ number ] 2-14NetEye 防火墙3.2.2命令手册show rule nip [ number ] 2-21 show rule packet-filter [ number ] 2-20show service audit 3-1show service ids 2-28show service telnet 2-30show system info 2-2show system time 2-3show user [ username ] 1-2shutdown 2-3sync { info-down | info-up } ipaddress filename 2-16system time ntp { ipaddress | domain-name | update | { week <1-7>2-2hh:mm:ss } }system time date time 2-2 system update ipaddress filename 2-3Tterminal language 2-30附录命令速查Uuser username{ local | radius } { security [ audit ] | audit [ security ] }1-1。
东软防火墙 NetEye FW 安装

5
2012-10-8
Neusoft Group Ltd.
管理主机的配置要求
• 硬件要求 – Pentium 450、256M内存、硬盘4GB以上的自由空间、 10M/100M以太网卡(ISA/PCI) • 软件要求 – Windows 2000、Windows XP – 安装Internet Explorer 4.0或以上版本 – TCP/IP协议 – IP地址为192.168.1.0网段
6
2012-10-8
Neusoft Group Ltd.
管理软件ቤተ መጻሕፍቲ ባይዱ安装
• • •
将机箱中 NetEye 防火墙管理系统安装光盘放入管理主机的光驱中,自动弹出“选择 安装程序”窗口; 此光盘显示:管理工具和认证客户端,其中管理工具安装在管理主机上; 想浏览整个光盘的内容,点击右下角的光盘图标;
7
2012-10-8
12
2012-10-8
Neusoft Group Ltd.
管理软件的安装
13
2012-10-8
Neusoft Group Ltd.
管理软件的安装
14
2012-10-8
Neusoft Group Ltd.
浏览开始菜单
• 四个应用程序
15
NetEye Firewall的架构
•
网卡
• • •
防火墙
管理主机
• •
防火墙是接入到网络中实现访问控 制等功能的网络设备; 防火墙上的所有软件在出厂时已经 安装完毕; 防火墙没有配置鼠标、键盘、显示 器等设备; 管理主机用于管理防火墙,配置防 火墙的安全策略等; 管理主机和防火墙之间的通信是经 过加密的; 管理主机需要用户单独准备;
NetEye东软防火墙配置手册

东软防火墙配置手册版本历史目录第一章文档说明 (4)1.1 编写目的 (4)1.2 项目背景 (4)第二章配置命令 (5)2.1 通过WEB登录 (5)2.2 虚拟系统 (6)2.2.1 查看虚拟系统信息 (6)2.2.2 创建一个虚拟系统 (6)2.2.3 删除一个虚拟系统 (7)2.2.4 添加描述 (8)2.2.5 启用/ 禁用虚拟系统 (8)2.2.6 切换虚拟系统 (9)2.3 制定安全策略 (10)2.3.1 IP包过滤 (10)2.3.2 安全策略流程 (12)2.4 地址转换NA T (14)2.5 高可用性HA (15)第一章文档说明1.1 编写目的编写该手册的主要目的是针对贵州二次安防项目工程技术人员提供东软防火墙基本的操作规范,同时,也可以作为贵州二次安防项目东软防火墙维护人员的参考阅读手册。
1.2 项目背景本项目是贵州电网公司根据《电力二次系统安全防护规定》(电监会5号令)、《电力系统安全防护总体方案》(国家电力监管委员会[2006]34号文及配套文件)和《南方电网电力二次系统安全防护技术实施规范》等电力二次系统安全防护相关规程规范的要求完成贵州电网公司省/地两级调度中心及220kV及以上电压等级变电站的生产控制大区业务系统接入电力调度数据网系统工程。
通过本项目的实施建立健全贵州电网电力二次系统安全防护体系。
项目的重点是通过有效的技术手段和管理措施保护电力实时监控系统及调度数据网络的安全,在统一的安全策略下保护重要系统免受黑客、病毒、恶意代码等的侵害,特别是能够抵御来自外部有组织的团体、拥有丰富资源的威胁源发起的恶意攻击,能够减轻严重自然灾害造成的损害,并能在系统遭到损害后,迅速恢复绝大部分功能,防止电力二次系统的安全事件引发或导致电力一次系统事故或大面积停电事故,保障贵州电网安全稳定运行。
第二章配置命令2.1 通过WEB登录1. 在可通过网络连接到NetEye 的计算机上打开Web 浏览器。
东软防火墙400

东软防火墙400
东软防火墙400是一种高效的网络安全解决方案,它被广泛应用于各类企业和机构的网络环境中。
该防火墙具有强大的防御功能,能够有效地保护网络免受各种网络攻击的威胁。
东软防火墙400采用了先进的技术和算法,可以实时监测网络流量,并通过智能分析和过滤,阻止恶意流量进入网络系统。
它能够识别和阻止各类网络攻击,包括DDoS攻击、SQL注入、跨站脚本攻击等,从而保护网络系统的安全性。
该防火墙还具有灵活的配置和管理功能,管理员可以根据实际需求,自定义规则和策略,对网络流量进行精确控制。
此外,东软防火墙400还支持多种安全认证方式,包括身份认证、IP地址认证等,确保只有经过授权的用户才能访问网络系统。
东软防火墙400还具有强大的日志记录和审计功能,它可以记录网络流量、安全事件等重要信息,并提供详细的审计报告,帮助管理员及时发现和解决网络安全问题。
总之,东软防火墙400是一种功能强大、性能稳定的网络安全解决方案,它能够帮助企业和机构保护网络安全,提高网络系统的可靠性和稳定性。
在当前日益复杂的网络安全威胁下,东软防火墙400是保障
网络安全的不可或缺的工具。
Quick Start_FW5120

IT SOLUTIONS & SERVICESNeusoft NetEye FirewallQuick Start Guide for FW5120Neusoft NetEye——Reliable Network SecurityCOPYRIGHTThe copyright of this software and related documentation isowned by Shenyang Neusoft Systems Integration Co., Ltd.Any infringement on the copyright will be prosecuted underapplicable law. Neither part or whole of the product, or themanual document may be reproduced or transferred in anyform or by any means (electronic or mechanical, includingphotocopying or recording), for any purpose, without thewritten permission of the copyright owner.Copyright © 2001-2009 Shenyang Neusoft SystemsIntegration Co., Ltd. All rights reserved.In no event shall Shenyang Neusoft Systems IntegrationCo., Ltd. be liable for any damage arising from the use ofthis product or the manual document.DisclaimerDue to an upgrade or other causes, information in thisguide is subject to change without notice. ShenyangNeusoft Systems Integration Co., Ltd. assumes noresponsibility for any damage or loss arising from omissionsor inaccuracies in this guide.Before operating on this appliance, make sure to read thisguide and related documentation carefully.Shenyang Neusoft Systems Integration Co., Ltd. assumesno responsibility for any damage arising from your ownimproper use.Introduction to This Documentation"Neusoft NetEye Firewall Quick Start Guide for FW5120"describes the functions, hardware features, installation,configuration, and maintenance of the FW5120 appliances.Make sure to read this guide carefully before and during theinstallation of the NetEye firewall (hereinafter called "thefirewall") so as to avoid any potential bodily injury ordamage to the appliance.This guide is organized as follows:Chapter 1, "NetEye Firewall Features" describes thefeatures of the NetEye firewall.NetEye Firewall Quick Start Guide for FW5120 1Chapter 2, "Firewall Hardware Architecture" describesthe hardware architecture of the firewall.Chapter 3, "Installing and Connecting the Firewall"describes how to install and connect the firewall. Itincludes installation requirements for the environment,setup considerations, and installation method, as wellas how to connect power and interfaces.Chapter 4, "Starting and Configuring the Firewall"describes how to start and configure the firewall,including how to perform the startup, how to log in,and what precautions should be taken at first use ofthe firewall.Chapter 5, "Limitations" describes the limitations ofthe firewall.Appendix A, "Common Problems" lists commonproblems and potential causes.2 NetEye Firewall Quick Start Guide for FW5120Neusoft NetEye——Reliable Network SecurityNetEye Firewall Quick Start Guide for FW5120 3Target AudienceThis guide is intended for experienced administrators who are responsible for installing and configuring Neusoft NetEye firewalls. It assumes a working knowledge ofnetworking and a conceptual understanding of LANs and WANs.Related DocumentationIn addition to this guide, documentation shipped with your appliance also includes the following:Neusoft NetEye Firewall Software User GuideNeusoft NetEye Firewall Software CLI Reference Guide Neusoft NetEye SCM Console User GuideNoticeseither a bodily injury might occur because of aphysical hazard or that damage to a structure,such as a room or equipment closet, mightdamage, equipment malfunction, loss of performance, loss of data, or interruptionof service.NoteNotes provide recommendations or informationof special interest.Environmental ProtectionThis appliance should be stored, used, and disposed of inaccordance with all applicable national laws andregulations.4 NetEye Firewall Quick Start Guide for FW5120Neusoft NetEye——Reliable Network SecurityContentsChapter 1 NetEye Firewall Features (7)1.1 Functional Features (7)1.2 Physical Features (10)Chapter 2 Firewall Hardware Architecture (13)2.1 Firewall Appliances (13)2.2 Front Panel (13)2.3 Back Panel (15)2.4 Side Panel (16)Chapter 3 Installing and Connecting the Firewall (19)3.1 Before You Begin (19)3.2 Installing the Firewall (20)3.3 Connecting the Firewall (22)Chapter 4 Starting and Configuring the Firewall (27)4.1 Performing the Initial Configuration (28)4.2 Performing Other Configurations (34)Chapter 5 Limitations (37)Appendix A Common Problems (39)NetEye Firewall Quick Start Guide for FW5120 56 NetEye Firewall Quick Start Guide for FW5120Neusoft NetEye——Reliable Network SecurityChapter 1 NetEye Firewall Features1.1 Functional Features1.Supports multiple firewall management modes,including WebUI, SSH, Telnet, and Console.2.Supports remote authentication. The firewall can beconfigured as the RADIUS client and use theauthentication service provided by the RADIUS server.It can remotely authenticate admin users, WebAuthusers, and VPN users and can support the accountingof WebAuth users and VPN users.3.Supports virtual systems (Vsys). A physical firewall canbe logically divided into several virtual firewalls, eachwith its own administrators, auditors, and securitypolicies.4.Supports switching and routing functions within onesystem and ensures security control over the datatransmitted within a network. That is, the system iscomposed of a router and multiple switches connectedto this router.5.Supports Virtual Local Area Network (VLAN). A physicalnetwork can be logically divided into several differentbroadcast domains. The NetEye firewall supports802.1Q trunking.6.Supports policy-based routing. You can specify whichpackets use a specified static routing table by settingconditions such as the incoming interface, source IPaddress, protocol, destination port, and so on.7.Supports session load balancing. You can set theweight for a specific next-hop router depending on itsperformance and other factors. In this way, thesessions are reasonably distributed.8.Supports IP packet filtering. You can implement controlover IP packets by setting parameters, such as theincoming interface, outgoing interface, source IPaddress, destination IP address, protocol, time, and soon.9.Supports non-IP packet filtering. You can implementcontrol over non-IP packets by setting parameters,NetEye Firewall Quick Start Guide for FW5120 7NetEye Firewall Featuressuch as the incoming interface, outgoing interface,source MAC address, destination MAC address,protocol, time, and so on.10.Supports the trusted address policy. You can specifythat the packets from some IP or MAC addresses canreach the firewall only through a specified zone or thatsome zones deny packets from specified IP or MACaddresses.11.Supports IP-MAC binding to avoid IP addressembezzlement and IP address spoofing.12.Supports Dynamic Host Configuration Protocol (DHCP).The firewall can dynamically assign TCP/IP settings,such as the IP address, subnet mask, gateway, andDNS servers for the DHCP client.13.Supports DNS server address setting. You can set amaximum of three DNS servers, including the primaryDNS server, the secondary DNS server, and the tertiaryDNS server.14.Supports domain name translation in DNS rules. Thefirewall translates the external IP addresscorresponding to the domain name into an internal IPaddress.15.Supports multicast access control. You can setparameters, such as the source IP address, multicastgroup address, incoming zone, outgoing zone, and soon, to specify whether a multicast packet can beforwarded by the firewall. In this way, you canimplement security control over network multicasttraffic.16.Supports IGMP snooping to enhance forwardingefficiency. The firewall can snoop on the IGMPmembership report messages, maintain the mappingbetween the multicast group addresses and theoutgoing VLAN interfaces, and forward the multicastpackets within a VLAN by using the mapping table.17.Supports Distance Vector Multicast Routing Protocol(DVMRP). The firewall can snoop on the IGMP andDVMRP report messages, maintain the routing table inthe Vsys, forward multicast packets, and maintain themulticast tree.8 NetEye Firewall Quick Start Guide for FW5120Neusoft NetEye——Reliable Network Security18.Supports policy-based Network Address Translation(NAT). Only when the packet meets the matchingconditions of a policy can the firewall perform NAT. Thematching conditions mainly include a specific IPaddress or an IP address range and a specified port.19.Supports NAT-based load balancing. The destination IPaddress of an incoming packet can be translated intothe different IP addresses of the intranet serversaccording to the amount of traffic on the servers.20.Supports detection of intra-zone or inter-zone data anddefense against attacks such as reconnaissance, denialof service, and suspicious packets.21.Supports Virtual Firewall Redundancy Protocol (VFRP).Some configurations and the dynamic runtimeinformation of the two firewalls can be synchronized. Ifthe primary device fails, the backup device will takeover the work from the primary device and continue towork as the primary one.22.Supports IP Security (IPSec) protocol. This protocolincludes two security protocols and a key managementprotocol: Authentication Header (AH), EncapsulatingSecurity Payload (ESP), and Internet Key Exchange(IKE).23.Supports two types of IPSec VPN access, site-to-siteIPSec VPN and remote-access IPSec VPN.24.Supports two types of authentication methods,preshared key authentication and digital certificateauthentication.25.Supports two types of VPN traffic control, policy-basedVPN and route-based VPN. The firewall also supportsL2TP over IPSec and NAT traversal.26.Supports installation of two different versions of thefirewall. You can switch from one version to anotherand install or delete a firewall system.27.Supports seamless upgrade. The upgraded firewallversion can inherit the license and configurations fromthe current version. The firewall is available for useimmediately after upgrade.28.Supports firewall upgrade and rollback. You can restorethe firewall to a previous state.NetEye Firewall Quick Start Guide for FW5120 9NetEye Firewall Features29.Supports monitoring of interfaces, HA status, routes,DNS, DHCP, ARP tables, CAM tables, session tables,system utilization, system health, multicast, systemlogs, VPN tunnels, and so on.30.Supports Simple Network Management Protocol(SNMP). The firewall can be configured as the manageddevice to be accessed and queried by the SNMPmanagement station for status information. Thefirewall supports SNMPv1, SNMPv2, and SNMPv3.31.Supports storage of system logs in local storage media.You can also send system logs to a remote server bydata carriers, such as syslog, e-mail, and SNMP trap foraudit.32.Supports Security Centralized Management (SCM).SCM Server, integrated with a Neusoft NetEye Seriesfirewall, provides centralized audit, monitoring, andreporting functions over the managed Neusoft NetEyeSeries firewalls by using SCM Console.1.2 Physical FeaturesThe FW5120 specifications are shown in Table1.Table 1 FW5120 SpecificationsName DescriptionFixedInterfaces4 Gigabit Ethernet interfacesExpansion Module NNCF-8-100T: 100 Mbps NIC Expansion Module (8 copper interfaces)TerminalManagementInterface1 RJ-45 portInput Power AC:90~264V 47~63Hz 1.5A(115V)1A(230V)Neusoft NetEye——Reliable Network SecurityWorkingTemperature0℃~ 40℃WorkingHumidity5% ~ 95%StorageTemperature-20℃~ 70℃StorageHumidity5% ~ 95%Overall Size (width X depth X height)440mm×300mm×44.5mmTable 1 FW5120 Specifications (continued) Name DescriptionNetEye Firewall FeaturesNeusoft NetEye——Reliable Network SecurityChapter 2 Firewall Hardware Architecture2.1 Firewall AppliancesFigure1 shows a sample illustration of an FW5120appliance. The dimensions (width X depth X height) are 440mm X 300 mm X 44.5 mm.Figure 1 FW5120 ApplianceThis document provides only a representative illustration.See the product for actual features.2.2 Front PanelFigure2 shows the front panel of an FW5120 appliance.Figure 2 FW5120 Front ViewThe front panel accommodates LED indicators, shown inTable2, which displays all the indications for system status.Firewall Hardware ArchitectureTable 2 FW5120 LED IndicationLED Indicator Status IndicationSystem Status Power LED On Indicates the powersupply is normal.Off Indicates no power orthe power supply isabnormal.HDD LED On Indicates the firewallis reading or writingdata on storagemedia.Off Indicates the firewallis not reading orwriting data onstorage media.Neusoft NetEye——Reliable Network Security2.3 Back PanelFigure 3 shows the back panel of an FW5120 appliance.Ethernet Interface Status ConnectionStatusBlinking Red Indicates this interface is working at 1000 Mbps and isstably connected withthe peer appliance.Blinking Green Indicates thisinterface is workingat 100 Mbps and isstably connected withthe peer appliance.Off Indicates noconnection with thepeer appliance, orthis interface isworking at 10 Mbps.Data On Indicates no data flowover this interface.BlinkingIndicates thisinterface is receivingor transmitting data.Table 2 FW5120 LED Indication (continued )LED IndicatorStatus IndicationFirewall Hardware ArchitectureFigure 3 FW5120 Back ViewThe back panel accommodates a 220 V AC power receptacleand power switch.2.4 Side PanelFigure4 shows the side panel of an FW5120 appliance.Figure 4 FW5120 Side ViewThe FW5120 ventilation holes are designed to dissipateheat to ensure that the appliance maintains an appropriatetemperature.Neusoft NetEye——Reliable Network Securityunblocked while the appliance is running.Enough space must be reserved aroundthe appliance to ensure good ventilation.Otherwise, internal components mightoverheat and cause the system not towork normally.Firewall Hardware ArchitectureNeusoft NetEye——Reliable Network SecurityChapter 3 Installing and Connecting the Firewall3.1 Before You Begin3.1.1 Check the Appliance and AccessoriesBefore you begin the installation, check the appliance andaccessories against the list provided to ensure the kit iscomplete.3.1.2 Precautions for Installation1.Power SafetyDisconnect Power Supply: Before installing thefirewall, disconnect the power supply by togglingthe power switch to the Off position on the backpanel of the firewall.Disconnect Power on the Cabinet: Before installingthe firewall into the cabinet, completely disconnectthe power on the cabinet. This should be consideredstandard procedure for the cabinet’s power supply.2.GroundingTo guard against potential electrical discharge damage,make sure the cabinet contains a third cord that isproperly grounded.receptacle of the cabinet, appropriategrounding measures must be taken forprotection of the cabinet. When thefirewall is plugged into an externalreceptacle, only the firewall is grounded.In this case, different appropriategrounding measures must also be takenfor protection of the entire cabinet,including the appliance and all accessorieshoused in the cabinet.Installing and Connecting the Firewall3.Overload ProtectionTo ensure safety, the electric power system in thebuilding should be available with appropriate protectionagainst a short circuit (current overload).4.Working EnvironmentTo ensure the normal running of the firewall andguarantee a long lifetime, note the following: keep theenvironment clean; keep the temperature and humiditywithin normal range; keep the firewall away from anyconductors and corrosives. In addition, the firewallshould be in a location with as little vibration aspossible. Do not place heavy items on the firewallappliance so that the metal shell will not be crushed,incurring damage to the firewall.3.2 Installing the FirewallFirst, secure the retaining braces on the two sides of thefirewall, as shown in Figure5, and then install thefirewall into the rack, as shown in Figure6.Neusoft NetEye——Reliable Network SecurityFigure 5 Installing the Firewall(A)Figure 6 Installing the Firewall (B)logo, which must remain intact until anengineer undertakes maintenance service.Otherwise, you will have to bear theresponsibility for any trouble incurred dueto the unauthorized opening of thechassis.After installing the firewall, ensure there isenough room around the firewall forventilation and heat dissipation to preventoverheating. In addition, make sure thecabinet has a good ventilation and heatdissipation system.Turn off and unplug the firewall before youInstalling and Connecting the Firewallclean the it. Do not clean with a wet clothor use cleansing solution.In order to reduce the risk of electricshock, do not open the chassis while thefirewall is still running. Do not open it evenwhen the power is off because residualstatic will probably damage the firewall,incurring a failure.3.3 Connecting the Firewall3.3.1 Connecting to the Ethernet InterfaceFW5120 firewalls use the RJ-45 Ethernet port.You can use a CAT 5 (CAT 5E or CAT 6) UTP or STP cablewith RJ-45 connectors at both ends, one connected to theEthernet interface of the firewall, and the other connectedto the Ethernet interface of another appliance within theLAN.The networking connection is shown in Figure7.Figure 7 Connecting to Ethernet Interface3.3.2 Connecting to the Console PortFW5120 firewalls provide a console port, which can beconnected to the serial port of a terminal using anNeusoft NetEye——Reliable Network Securityappropriate cable. After the connection is established, youcan perform operations on the firewall through the console(This procedure is recommended to be done only under theguidance of an engineer or directly by an engineer).FW5120 firewalls use a cable with an RJ-45 connector atone end and a DB-9 connector at the other end. The RJ-45connector is connected to the console port of the firewall,and the DB-9 connector is connected to the serial port of aterminal (such as a PC).Figure8 shows a console cable illustration.Figure 8 Console Cable IllustrationFigure9shows how to connect to the console port.Figure 9 Connecting to Console PortWith Windows 2000, PC HyperTerminal parameters wouldbe configured as follows:9600 bps8 data bitsInstalling and Connecting the Firewall1 stop bitNo parityNo data flow controlFor a terminal-emulation program, you should use astandard VT100 terminal.check the interface label to avoidconnecting into a wrong interface.No hot plugging is allowed on the consoleport.Neusoft NetEye——Reliable Network Security3.3.3 Connecting the Power SupplyFW5120 firewalls are equipped with AC power. To connectthe AC power, perform the following operations:1.Connect the female end of the power cord into thereceptacle on the back panel of the firewall.2.Connect the male end of the power cord into the ACpower receptacle.3.Turn on the power switch to check whether the powerLED on the front panel is illuminated. An illuminatedLED indicates a correct power connection.Figure10shows how to connect an AC power supply.Figure 10 Connecting AC Power Supplyare recommended to use AC surgesuppressors and lightening-proofreceptacles for protection.Installing and Connecting the FirewallNeusoft NetEye——Reliable Network SecurityChapter 4 Starting and Configuring the Firewall The first time you turn on a NetEye firewall, you need toconnect the firewall through a serial console connection andthen perform the initial configuration from the CLI. Thisprocess enables administrators to remotely access andconfigure the firewall.NoteUse the configuration steps outlined below tocomplete the initial configuration. Consoleprompts and console messages are shown inmonospace font. CLI commands and valuesyou enter are shown in monospace boldfont. Configuration variables are shown in italicsand are enclosed with angle brackets <>, forexample, <192.168.1.100>.You must use a serial console connection (RJ-45null-modem cable). After you perform the initialconfiguration, the console connection is no longer required.You can use any standard VT100-compatible terminal withan RS-232 data terminal equipment (DTE) interface or aterminal-emulation program configured with the followingsettings for the console:9600 bps8 data bitsNo parity1 stop bitStarting and Configuring the Firewall4.1 Performing the Initial ConfigurationYou can perform the initial configuration and manage thefirewall either through WebUI or the CLI.1.Press the power switch to the “on” position to turn onthe firewall.2.The following message appears on the console screen:LILO 22.5.91 NetEye_FW2 bootmgrPress key '2' to enter BOOTMGR command modeboot:The message remains on the screen for about fiveseconds, during which you either type 1 and pressEnter or do nothing. After a series of boot informationmessages, the console prompt appears.3.Apply License. (If a license is already applied on thefirewall, go directly to step 5.)Select either of the following methods to applylicense:1. Hyperterminal which supports X/Z Modem, e.g.Windows Hyperterminal2. TFTP server3. SFTP server4. Character stringPress '1' for Hyperterminal or '2' for TFTP serveror '3' for SFTP server or ‘4’ for Character string.( 'q' for EXIT ): <1, 2, 3, 4 or q>You can apply the license through the WindowsHyperTerminal by entering 1, the TFTP server byentering 2, the SFTP server by entering 3, or thecharacter string by entering 4. You can also do this byentering commands in the command-line interfaceafter you exit by entering q.Microsoft Windows HyperTerminalOn the HyperTerminal menu bar, choose Transfer >Send.Neusoft NetEye——Reliable Network SecurityIn the Send File dialog box, browse and select thelicense file and click Send.% License upload succeed, system need reboot!Continue? (y/n) yThe system will reboot.TFTP ServerConfiguring the system for accessing licensefrom TFTP serverSelect a port from the list (eth0):( 1 ) eth0( 2 ) eth1( 3 ) eth2( 4 ) eth3( 5 ) eth4( 6 ) eth5Please input ethernet port (eth0): <port ID ornumber>Please input IP address (192.168.1.100):<IPaddress>Please input subnet mask (255.255.255.0):<subnet mask>Please input default router to use with selectedinterface (192.168.1.1): <default router>You have entered the following parameters:Interface for initial connection: <port ID>IP address:<IP address>Subnet mask: <subnet mask>Default route: <default route>Is this information correct(*y/n) yPlease input TFTP server IP (192.168.1.1):<server IP>Please input license name(): <license name>% License upload succeed, system need reboot!Continue? (y/n)yThe system will reboot.Starting and Configuring the FirewallSFTP ServerConfiguring the system for accessing licensefrom SFTP serverSelect a port from the list (eth0):( 1 ) eth0( 2 ) eth1( 3 ) eth2( 4 ) eth3( 5 ) eth4( 6 ) eth5Please input ethernet port (eth0): <port ID ornumber>Please input IP address (192.168.1.100):<IPaddress>Please input subnet mask (255.255.255.0):<subnet mask>Please input default router to use with selectedinterface (192.168.1.1): <default router>You have entered the following parameters:Interface for initial connection: <port ID>IP address:<IP address>Subnet mask: <subnet mask>Default route: <default route>Is this information correct(*y/n) yPlease input SFTP server IP (192.168.1.1):<server IP>Please input SFTP server username: <loginusername>Please input SFTP server password: <loginpassword>Please input license path and name: <licensename>% License upload succeed, system need reboot!Continue? (y/n)yThe system will reboot.30 NetEye Firewall Quick Start Guide for FW5120Neusoft NetEye——Reliable Network SecurityLicense StringConfiguring the system for accessing licensefrom character stringPlease input character string of license:<character string of license>% License upload succeed, system need reboot!Continue? (y/n)yThe system will reboot.On reboot, follow step 2.4.Change the host name.Please choose the host name for this systemHostname: <new hostname>5.Set the system time.Please set the system time (YYYY-MM-DDHH:MM:SS)system time (2000-01-01 00:00:01):<system time>6.Set the system language.Please set system language1) English2) ChinesePlease enter a choice [1-*2,q]:<1 or 2>7.Change the root administrator password. (This step isoptional, but you are recommended to change thepassword after initial login.)Changing default password of root?(*y/n):yOld password(6-128): neteyeNew password(6-128):<new password>Repeat password(6-128):<new password>NetEye Firewall Quick Start Guide for FW5120 31Starting and Configuring the Firewall8.Add an administrator.Creating an administrator?(*y/n):yUsername: <admin user>Please select a login type1)Web2)Telnet3)Ssh4)ScmPlease enter a choice [*1-4](1)(example:1,2,3)<set login type>Password(6-128):<admin password>Repeat Password(6-128):<admin password>32 NetEye Firewall Quick Start Guide for FW5120Neusoft NetEye——Reliable Network Security9.Choose a way to configure your system and anaccessible port.Configure an interface and use our WebUI via aremote browser(*y/n):yConfigure an interface by using CLI(SSH)(*y/n):yYou can manage the firewall through either WebUI orthe CLI.Select a port from the list (eth0):<port ID ornumber>( 1 ) eth0( 2 ) eth1( 3 ) eth2( 4 ) eth3( 5 ) eth4( 6 ) eth5Please input ethernet port (eth0):<port ID ornumber>Please input IP address (192.168.1.100): <IPaddress>Please input subnet mask (255.255.255.0):<subnet mask>Please enter default router to use withselected interface (192.168.1.1): <defaultrouter>You have entered the following parameters:Interface for initial connection: <port ID>IP address: <IP address>Subnet mask: <subnet mask>Default route: <default route>Is this information correct(*y/n) yYou now have access to WebUI, CLI and can continueto configure the system via this interface.Start SCM Server?(*y/n): <whether to enable SCMserver>Allow SCM Server manager?(*y/n): <whether toallow SCM server manager>NetEye Firewall Quick Start Guide for FW5120 33。
东软防火墙配置

阅读指南〖手册目标〗本手册是沈阳东软软件股份有限公司的产品NetEye防火墙CLI的使用指南,它详细地介绍了CLI的功能和操作。
通过阅读本手册,用户可以掌握NetEye防火墙CLI的使用方法。
〖阅读对象〗本手册专为购买NetEye防火墙的用户编写。
用户在使用防火墙之前请仔细阅读本手册,以免误操作,造成不必要的损失。
〖手册构成〗本手册主要由以下几个部分组成:1.2.3.4. 第1章用户管理介绍管理员(root)登录CLI后所能进行的操作,如添加、编辑或删除其他具有管理权限的用户,以及修改自身或其它用户口令。
第2章安全管理介绍具有安全管理权限的用户登录CLI后所能进行的一系列操作,主要是防火墙接口的配置以及各种规则的配置。
第3章审计管理介绍具有安全管理权限的用户登录CLI后所能进行的关于审计功能的开启和关闭的操作。
附录命令速查为用户提供了快速查找命令的工具。
〖手册约定〗CLI约定y斜体——命令行参数(命令中必须由实际值进行替代的部分)采用斜体表示。
y[ ]——表示用“[ ]”括起来的部分在命令配置时是可选的。
y{ x | y | ... }——表示从两个或多个选项中必须选取一个。
y[ x | y | ... ]——表示从两个或多个选项中选取一个或者不选。
范例:sync { info-down | info-up } ipaddress filenamesync info-down 10.1.2.110 neteyefwCLI模式NetEye防火墙CLI配置共提供三种模式,分别为:普通模式:管理员(root)和安全员可以进入该模式。
在该模式下可以进行的操作有:进入特权模式、退出和语言管理。
特权模式:管理员(root)和安全员可以进入该模式。
在该模式下,可以查看系统信息及配置信息,可以对系统进行高级别的操作,但不能更改配置信息。
不同权限的用户进入特权模式后,所能做的操作也不同。
管理员(root)进入特权模式后可以进行的操作有:进入全局配置模式、退出特权模式、退出命令控制台、测试连通性、显示和终端配置。
连接防火墙的配置方法

连接防火墙的配置方法
防火墙的连接配置主要分为三个步骤,分别为Telnet连接、Web管理和SSH管理。
以下是这三个步骤的详细说明:
1. Telnet连接:在防火墙的GigabitEthernet0/0/0接口下进行配置。
2. Web管理:首先,在防火墙上使用命令开启服务,然后在浏览器中输入相应的网址,进入到Web页面。
点击详细信息,转到此页面。
第一栏选择语言,输入用户名与密码,即可进入防火墙Web页面。
3. SSH管理:具体步骤可能因防火墙型号和设置不同而有所差异,一般步骤是在防火墙上使用命令开启服务。
以上是防火墙的三种连接方式,具体操作可能因设备型号和设置不同而有所差异,建议参考具体设备的操作手册或咨询专业技术人员。
NetEye FW 过滤规则配置

4-13
连接建立过程
内网接口 192.168.0.2
外网接口 Internet
服务器
客户端
3 2 ‘
ACK SYN ACK SYN
3 ‘ 2 1 ‘
ACK SYN ACK SYN
1
NetEye Firewall 使用指南
4-14
外到内的访问,拒绝
提示: • 允许只是部分的允许; • 拒绝是绝对的禁止;
NetEye Firewall 使用指南
4-6
经过防火墙的典型访问
192.168.0.0/24 ……
内部网络
Internet
•
举例: 192.168.0.2 能够通过防火墙访问 ;
NetEye Firewall 使用指南
4-32
新建包过滤规则-3.2
•
•
可以输入:单个IP地址、IP地 址范围、域名; “去除下列地址”是指在一个 地址范围中,被去除的地址不 匹配此规则;
NetEye Firewall 使用指南
4-33
新建包过滤规则-3.3
•
例如: 192.168.0.16 属于 192.168.0.15 - 192.168.0.20 这个范围,但管理员不希望这 个IP匹配这个规则,就 “去 除”这个IP地址的,去除的IP 地址前面用“!”标识;
• •
NetEye Firewall 使用指南
4-28
新建包过滤规则-2.1
• • • 拒绝”意味着匹配该规则的连 接不允许通过; “允许”意味着匹配该规则的 连接可以通过;“允许”包括 两个内容; 选中复选框“对TCP连接进行 认证” ,表示:防火墙对TCP 请求包进行认证后,才允许通 过,认证需要的用户名/密码信 息存放在指定的认证域中,关 于认证域请参见《NetEye Firewall安全控制台使用指南》 中的“认证管理”章节;
虚拟化应用防火墙东软NISG-VA产品介绍
东软NISG-VA虚拟化应用防火墙通过实时监测和智能分析技术,有效 识别和拦截恶意流量,确保政府关键业务系统的安全稳定运行。
客户收益
该政府机构通过部署东软NISG-VA虚拟化应用防火墙,显著提高了关 键业务系统的安全防护能力,保障了政府业务的正常运行。
客户案例三:大型企业应用
客户背景
某跨国大型企业需要保护其云数据中心免受网络威胁和攻 击。
CHAPTER
测试环境与工具
测试环境
在虚拟化环境中搭建测试平台,包括 服务器、存储、网络等基础设施。
测试工具
使用业界标准的性能测试工具,如 LoadRunner、Gatling等,进行压力 测试和性能指标采集。
测试结果与分析
吞吐量
在一定负载下,东软NISG-VA产品 能够达到较高的吞吐量,满足虚拟化 环境的需求。
06 总结与展望
CHAPTER
产品总结
东软NISG-VA虚拟化应用防火墙提供了全面的安全防 护功能,包括入侵检测与防御、病毒防护、内容过滤
等,保障虚拟化环境的安全。
输入 部标署方题式
支持集中部署和分布式部署,可以根据实际需求灵活 配置,有效满足各种规模虚拟化环境的防护需求。
功能特性
管理界面
东软NISG-VA虚拟化应用防火墙具备良好的性能和稳 定性,能够确保虚拟化环境的顺畅运行。
启用日志记录功能,监控防火墙 的运行状态和流量情况,以便及 时发现和处理安全事件。
5. 测试与验收
完成配置后,对东软nisg-va虚拟 化应用防火墙进行测试,确保各项 功能正常工作,符合安全需求。
常见问题与解决方案
1. 问题
无法登录管理界面。
01
2. 问题
东软防火墙

Eth 2---外网
Eth---3 用交叉线直连防火墙
Eth 4----xxx网
六、访问控制:允许Eth 1 访问 Eth 2 , 拒绝访问 Eth 3、4
允许Eth 2 访问 Eth 1 , 拒绝访问 Eth 3、4
二、 默认用户为:root 密码:neteye 进入用户管理界面,此页面下可以创建用户,并设置权限(安全控制、审计、管理)
三、 为方便调试已创建用户: xxxx 密码:xxxx 权限为:安全控制
四、 用xxxx 这个用户进入WEB界面后,先看到防火墙的所有信息
然后根据需求,设置防火墙的工作模式,是交换还是路由,
允许Eth 3 访问 Eth 4 , 拒绝访问 Eth 1、2
允许Eth 4访问 Eth 3 , 要选择“应用并保存”选项。
1、 交换模式下,Eth 口不需要配地址,也没有NAT的转换
2、 路由模式下,根据需求可以配置NAT、默认路由,它既充当路由器,又起到防火墙的作用。
五、 Eth 0口为管理接口,只有在配置防火墙时才使用
Eth 1-4可随意定义为 内网口、外网、DMZ区等
在我们这次配置中,Eth 口的定义:
东软Neteye 4032 防火墙维护手册
一、 Neteye 4032 的默认管理IP为192.168.1.100 ,我们用防火墙自带的一根交叉线和PC相连,PC的IP设置为和防火墙一个网段,在运行下ping 192.168.1.100,显示连通;在WEB浏览器下输入192.168.1.100,进入防火墙的WEB管理界面。
东软防火墙NetEye FW5000系列技术白皮书

NetEye Firewall 5000 Series东软防火墙NetEye FW5000系列技术白皮书目录应用背景 (3)东软NetEye FW5000系列的技术特点 (4)面向关键业务提供全面可用性保证 (4)优异的网络适应性 (5)充分适应特殊应用环境要求 (6)支持基于策略的透明VPN (7)强大的攻击防御能力 (7)东软NetEye FW5000系列防火墙主要功能 (8)基于状态检测技术的访问控制 (8)网络地址转换(NAT) (8)IP与MAC地址绑定 (9)支持VLAN Trunk (9)支持 Radius 、XAUTH、Web等认证协议 (10)支持NTP (10)SCM安全集中管理 (11)服务器负载均衡 (12)并发连接数限制 (12)对多播协议的支持 (12)可视化管理 (12)强大便利的向导功能 (13)支持SNMP (13)2应用背景网络和信息安全基础设施己经和电力、水力一样,成为国家稳定和发展的关键基础设施。
因此,保证关键行业的业务应用和信息资产安全显得日益紧迫和重要。
在这些应用环境中,业务服务器、核心骨干设备以及内网的安全性和可用性一旦遭到破坏,后果不堪设想,因此必须采用高性能的防火墙设备加以严密保护。
政府、金融、电信、电力等行业对网络安全的强劲需求推动了防火墙技术的不断发展。
本白皮书将说明东软NetEye FW5000系列防火墙如何帮助客户满足关键网络骨干节点的安全防护和性能保障要求。
关键行业骨干节点的边界安全防护有着共同的特点,最主要的就是对防火墙的性能、稳定性、网络适应性和应用适应性有着严苛的要求。
以性能的要求为例,一些大型商业银行数据中心的服务器数量高达上千台,仅备份网络的带宽就达 2.5G;大型政府网站的对外服务处理的查询量高达每秒20000次以上,而响应时间的要求是5秒以下。
因此,理想的防火墙设备应该能够提供最佳的安全性、性能、网络适应性和应用适应性,达到以下标准:l将高安全性放在首要地位,可抵御各种网络入侵和攻击,在瞬间做出安全和流量路由决策,即使在处理数Gbps的网络流量时也能做到这一点;l支持多样化的部署方式,具备面向复杂应用环境的功能特性,适应复杂且变化迅速的业务需求;l采用高性能的硬件架构,提供最佳的产品性价比,提高行业安全项目建设的投资回报率。
防火墙的基本配置与管理

防火墙的基本配置与管理
防火墙在计算机系统中扮演着重要的角色,它可以保护网络免受不受欢迎的访问和未经授权的信息泄露。
本文将介绍防火墙的基本配置和管理,以帮助保护您的计算机和网络安全。
防火墙基本配置
1. 确定防火墙的位置:防火墙可以在网络的边缘或内部部署。
根据网络的规模和需求,选择合适的位置来安装防火墙。
2. 设置规则和策略:根据安全要求,配置防火墙以允许或阻止特定的网络流量。
可以基于协议、端口、IP地址等来定制规则,确保只有经过验证的流量可以通过防火墙。
3. 更新和维护规则:定期审查和更新防火墙的规则和策略,确保它们与最新的威胁和安全需求保持一致。
防火墙的管理
1. 监控防火墙日志:定期检查防火墙的日志,以察觉任何潜在的安全问题或异常活动。
2. 更新防火墙软件:及时安装防火墙提供的补丁和更新,以弥补已知的漏洞并保持防火墙的功能和效能。
3. 配置安全策略:根据实际需求,调整和优化防火墙的安全策略。
这包括限制特定IP地址或端口的访问,允许或禁止特定协议等。
4. 定期测试和评估:定期进行防火墙的渗透测试和安全评估,以发现潜在的弱点并进行修复。
防火墙的配置和管理是确保计算机和网络安全的重要步骤。
遵循这些基本原则,并在需要时寻求专业人士的帮助和建议,可以最大限度地提供保护和安全性。
请注意,本文提供的信息仅供参考,具体的防火墙配置和管理取决于实际情况和特定需求。
在进行任何防火墙操作之前,请确认并遵守适用的法律和合规要求。
虚拟化应用防火墙东软NISGVA产品介绍

如何配置东软NISGVA虚拟化应用防火墙?
解答
可以参考产品文档中的配置指南进行配置,或者联系东软 技术支持团队获取帮助。
问题二
遇到网络攻击时,如何快速响应?
解答
可以启用东软NISGVA虚拟化应用防火墙的入侵防御功能 ,自动识别和防御网络攻击。同时,也可以联系东软技术 支持团队获取专业的应急响应服务。
产品采用高性能硬件架构和优化算法,确 保在处理大量网络流量时仍能保持出色的 性能表现。
灵活的部署方式
丰富的功能特性
支持多种部署方式,包括物理机、虚拟机 、容器等,满足不同场景下的安全需求。
提供访问控制、入侵防御、病毒防护、日 志审计等功能,满足用户多样化的安全需 求。
未来发展趋势预测
云网端一体化安全
与其他同类产品相比,东软NISGVA产品在吞吐量、延迟和并发连接数等方面均表 现出色。
此外,东软NISGVA产品还具有丰富的安全特性和灵活的管理功能,能够更好地满 足企业的安全需求。
综上所述,东软NISGVA产品在性能上具有较高的竞争力,是企业网络安全防护的 理想选择。
06 使用案例与客户反馈
CHAPTER
易于管理和维护
东软nisgva提供直观的管理界面 和丰富的管理功能,方便用户进 行配置、监控和维护。
全面的虚拟化安全防护
东软nisgva提供全面的虚拟化安全 防护功能,包括网络防火墙、应用 防火墙、入侵检测与防御等。
广泛的兼容性
东软nisgva兼容多种虚拟化平台 和操作系统,可轻松集成到现有 的虚拟化环境中。
随着云计算、物联网等技术的快 速发展,未来安全产品将更加注 重云、网、端一体化的安全防护。
AI驱动的安全防护
人工智能技术在安全领域的应用 将逐渐普及,通过AI驱动的安全 防护将更加智能、高效。
东软防火墙配置手册01

第1章用户管理该章节中的操作仅在root用户登录后可用。
语法:1.添加用户NetEye(config)# user username{ local | radius } { security [ audit ] | audit [ security ] } 2.配置RADIUS服务器NetEye(config)# radius-server host ipaddress]3.配置RADIUS服务器端口NetEye(config)#radius-server port number4.设置RADIUS服务器密码NetEye(config)# radius-server secret5.将RADIUS服务器设置为默认状态NetEye(config)# no radius-server6.查看RADIUS服务器1-1NetEye防火墙3.2.2命令手册NetEye# show radius-server7.删除用户NetEye(config)# no user username8.更改用户口令NetEye(config)# password [ username ]9.显示当前防火墙上的用户信息(包括用户名、权限、认证方式) NetEye#show user [ username ]1-2第1章用户管理表1-1 命令描述关键字和变量描述user 用户管理security 安全员权限audit 审计员权限radius-server 设置RADIUS服务器host RADIUS服务器主机port RADIUS服务器端口secret RADIUS服务器密码password 修改用户的口令show 查看信息username 用户名WORD{1-12}number 端口号<1-65535>ipaddress RADIUS服务器的ip地址1-3。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
附录命令速查命令页码Aapplication_filter anti dcom-lssass { enable | disable} 2-32application_filter netmeeting { enable | disable} 2-32 application_filter oracle { enable | disable} 2-33 application_filter rtsp { enable | disable} 2-33 application_filter tftp { enable | disable} 2-33 application_filter tuxedo { enable | disable} port number 2-33auth-management local-domain domain-name 2-5auth-management local-user domain-name username rolename 2-5auth-management password domain-name username 2-5BNetEye 防火墙3.2.2命令手册backup ipaddress config-filename2-6Cclear line vty number2-30connection timeout { icmp | udp | syn | fin | est | close | auth } number2-24console timeout number2-29Ddns ipaddress [ primary ]2-12Hhost { group groupname | id number } 2-16hostname hostname 2-16 Iinterface id number zone-name 2-8 interface zone-name { enable | disable } 2-8interface zone-name ipaddress netmask 2-8L附录命令速查license { generate | upload | download } ipaddress filename 2-2Mmode { route | switch } [ anti-attack ] 2-9Nno auth-management domain-name 2-5no auth-management local-user domain-name username 2-5no dns ipaddress 2-12 no host { id | group } 2-16no interface zone-name ipaddress netmask 2-8no proxy address ipaddress 2-12no proxy route ipaddress netmask [ gateway ] 2-11no proxy vlanpass number 2-12no radius-server1-1no route dst-ipaddress netmask zone-name [ ipaddress [ metric number] ] |[metric number [ ipaddress ] ] ] 2-10NetEye 防火墙3.2.2命令手册no route dst-ipaddress netmask ipaddress [ zone-name [ metric number ] ] |[ metric number [ zone-name ] ] 2-10no route dst-ipaddress netmask metric number [ zone-name [ ipaddress ] ] |2-11[ ipaddress [ zone-name ] ]no rule nat number 2-14 no rule nip number 2-20 no rule ip-mac number 2-21no rule local-access number 2-23no rule multicast number 2-22no rule packet-filter number 2-20no system time ntp 2-3no user username 1-2 Ppassword2-5password [ username ] 1-2 ping { ipaddress | hostname | domain } 2-3附录命令速查proxy address ipaddress netmask mac zone-list [ vlan number type 802.1q ] 2-11proxy route dst-ipaddress netmask gateway 2-11proxy vlanpass number 2-12 Rradius-server host ipaddress [ port number ]1-1radius-server port number 1-1 radius-server secret 1-1reboot 2-3reset 2-3restore ipaddress config-filename 2-6route dst-ipaddress netmask ipaddress[ zone-name [ metric number ] ]|[ metric number [ zone-name ] ] 2-10route dst-ipaddress netmask zone-name [ ipaddress [ metric numbe r ] ] |2-10[ metric number [ ipaddress ] ]rule ip-mac move srcnumber dstnumber 2-21rule ip-mac otherip { permit | deny } 2-21NetEye 防火墙3.2.2命令手册rule ip-mac sequence number { enable | disable } 2-21rule ip-mac zone { ipaddress-list | any} macaddress{enable | disable }[ sequence number ] 2-21rule local-access { ip-range | any } [ mac ] zone ipaddress service { ping |authentication | management | auth-pwd } { permit | deny } { enable | disable }2-23[ sequence number ]rule local-access { ip-range | any }[ mac ] zone ipaddress service { tcp | udp }{ port-range | any } { permit | deny } { enable | disable } [ sequence2-23number ]rule local-access move srcnumber dstnumber 2-23rule local-access sequence number advanced worktime { { on week timelist }2-23| off }rule local-access sequence number { enable | disable } 2-23rule multicast move srcnumber dstnumber 2-22 rule multicast sequence number advanced audit { on | off } 2-22rule multicast sequence number advanced worktime { { on week timelist } |2-22off }rule multicast sequence number { enable | disable } 2-22rule multicast source client { iplist | any } { permit | deny }{enable | disable }2-22[ sequence number ]附录命令速查rule nat move srcnumber dstnumber 2-14rule nat non-single src-zone { sip-list | any } dst-zone { dip | dip-range }2-14{service { { { tcp | udp } sip { { sport dip dport } | { { sport-range | any } dip } }[ domain ] } | { icmp sip dip } } enable | disable } [ sequence number ]rule nat sequence number { enable | disable } 2-14rule nat single src-zone sip dst-zone dip { enable | disable } [ sequence2-14number ]rule nip move srcnumber dstnumber 2-21 rule nip sequence number advanced worktime { { on week timelist } | off } 2-20rule nip sequence number { enable | disable } 2-21rule nip src-zone { smac-list | any } dst-zone { dmac-list | any } protocol name{ protocolnumber | any} { permit | deny } {enable | disable } [ sequence2-20number ]rule packet-filter move srcnumber dstnumber 2-20rule packet-filter sequence number advanced audit { on | off } 2-19rule packet-filter sequence number advanced authentication { { on2-19auth-domain } | off }rule packet-filter sequence number advanced syncheck { on | off } 2-19rule packet-filter sequence number advanced worktime { { on week timelist } |2-19off }rule packet-filter sequence number { enable | disable } 2-20NetEye 防火墙3.2.2命令手册rule packet-filter src-zone { sip-list | any } dst-zone { dip-list | any } protocolname icmp { echoreply | echo | info_request | info_reply | timestamptimestampreply | address | addressreply | dest_unreach | source_quench |2-18 redirect | time_exceeded | parameterprob | all } { permit | deny } { enable |disable } [ sequence number ]rule packet-filter src-zone { sip-list | any } dst-zone { dip-list | any } protocolname other { protocolnumber | any }{ permit | deny } { enable | disable }2-19 [ sequence number ]rule packet-filter src-zone { sip-list | any } dst-zone { dip-list | any } protocolname tcp { srcport | any } { dstport | any } { permit | deny } { enable |disable } [ sequence number ] 2-18rule packet-filter src-zone { sip-list | any } dst-zone { dip-list | any } protocolname udp { srcport | any } { dstport | any } { permit | deny } { enable |2-18 disable } [ sequence number ]Sservice audit { enable | disable } { local | network ipaddress | syslog3-1 ipaddress port }service ids { enable | disable } 2-28 service telnet { enable vty number [ timeout time ] | disable } 2-29 show connection status2-24附录命令速查show connection timeout { icmp | udp | syn | fin | est | close | auth | all } 2-24show dns 2-13show host 2-16show interface [ zone-name ] 2-8 show line 2-30show mode 2-9show proxy address 2-12show proxy route 2-11show proxy vlanpass 2-12show radius-server 1-2show route 2-11show rule ip-mac [ number ] 2-22show rule local-access [ number ] 2-24show rule multicast [ number ] 2-23show rule nat [ number ] 2-14NetEye 防火墙3.2.2命令手册show rule nip [ number ] 2-21 show rule packet-filter [ number ] 2-20show service audit 3-1show service ids 2-28show service telnet 2-30show system info 2-2show system time 2-3show user [ username ] 1-2shutdown 2-3sync { info-down | info-up } ipaddress filename 2-16system time ntp { ipaddress | domain-name | update | { week <1-7>2-2hh:mm:ss } }system time date time 2-2 system update ipaddress filename 2-3Tterminal language 2-30附录命令速查Uuser username{ local | radius } { security [ audit ] | audit [ security ] }1-1附录-11。
