华为USG防火墙配置实例脚本-PPPOE
华为usg2210防火墙配置实例

<USG2200>display current-configurationdetect h323d09:29:14 2016/03/17detect qq#sysname USG2200detect#sl2tp enabledetect netbiundo l2tp domain suffix-separator @undo tunnel authentic#iike dpd interval 10allow l2tp#ifirewall packet-filter default permit interzone local trust direction inbound unicastundo synchronization#firewall packet-filter default permit interzone local trust direction outboundlocal-user user2firewall packet-filter default permit interzone local untrust direction inboundlocal-user user3 password cipher %$%$`;WkNM${E;O=5--=%yfirewall packet-filter default permit interzone local untrust direction outboundal-user user3 service-type ppp local-user useauthentication-mode vpndb#nat server 1 protocol udp global 218.56.104.*** any inside 192.100.7.73 anyheme test.scmauthorization-mode vpndb#ip df-unreachables enableaccounting-scheme defaultdomain dot1xfirewall ipv6 statistic system enableauthentication-scheme test.sc#dns resolvefirewall defend syn-flood enablefirewall defend arp-flood enablefirewall defend sip-flood enablefirewall defend udp-flood fingerprint-hit destination-max-rate 5firewall defend udp-flood fingerprint-hit source-max-rate 3firewall defend sip-flood port range 1 65535#firewall statistic system enable#pki certificate access-control-policy default permit#dns proxy enable#license-server domain #web-manager enableweb-manager security enable port 8443#user-manage web-authentication security port 8888##radius-server template test.tpl##ldap-server template test.tplldap-server authentication base-dn dc=my-domain,dc=com ldap-server group-filter ouldap-server authentication-filter (objectclass=*) ldap-server user-filter cnldap-server server-type ad-ldap#acl number 2001rule 5 permit source 192.100.7.0 0.0.0.255 rule 10 permit source 10.10.10.0 0.0.0.255acl number 3000rule 5 permit udp source-port eq 1701 rule 10 permit udp destination-port eq 1701 #acl number 3001#ike proposal 1encryption-algorithm 3des-cbcdh group2 group1integrity-algorithm aes-xcbc-96 hmac-sha1-96 hmac-md5-96 #ike peer ike20111583362exchange-mode autoike negotiate compatiblepre-shared-key %$%$sEPH;hfv{*71&V3Zc:QS^C:1%$%$ ike-proposal 1remote-id-type none#ipsec proposal prop20111583362encapsulation-mode autoesp authentication-algorithm sha1esp encryption-algorithm 3des#ipsec policy-template tpl20111583362 1 security acl 3000security acl public-ip-transparentike-peer ike20111583362alias celue1scenario point-to-multipoint l2tp-user-access proposal prop20111583362local-address applied-interfacesa duration traffic-based 1843200sa duration time-based 3600#ipsec policy ipsec2011158331 10000 isakmp template tpl #interface Cellular0/1/0link-protocol ppp#interface Virtual-Template0ppp authentication-mode chap papalias L2TP_LNS_0remote address pool#interface GigabitEthernet0/0/0ip address 10.10.10.1 255.255.255.0#interface GigabitEthernet0/0/1ip address 218.56.104.*** 255.255.255.252 ipsec policy ipsec2011158331 auto-neg nat enabledetect ftp#interface NULL0alias NULL0#firewall zone localset priority 100#firewall zone trustset priority 85detect ftpdetect rtspenticationdetect mmsUsdetect mgcpUsernamedetect sipsername:detect pptpme:admindetect sqlnetword:*detect h323n failed!detect qqUsedetect msndetect netbiosICE:This is a padd interface GigabitEthernet0/0/0 #firewall zone untrustccess or use may leadset priority 5detect ftpdetect rtspWarndetect mmsefault authdetect mgcpthod and pasdetect sipsole.detect pptpdetect sqlnetdetect h323G2200>detect qqor the sakdetect msny, please mdetect dnsiginal passdetect ilsuser.detect netbiosadd interface GigabitEthernet0/0/1<USG2200>display cyrrent-c#ffirewall zone dmzset priority 50 ^detect ftpErrodetect rtspmeter founddetect mmsion.detect mgcpdetect sipdetect ftp09detect rtsp03/17detect mms#detect pptpp domain sufdetect sqlnetdetect h323#detect qqterval 10detect dns#detect ilsket-filterdetect netbiosnterzone local#ufirewall zone name us2set priority 66detect ftpfirdetect rtspfilter defaudetect mmsterzone locdetect mgcpction outboudetect sipdetect pptpdetect sqlnetdetect h323packet-filtedetect qqermit intedetect dnsuntrust dirdetect ilsnddetect netbios#firewall interzone local trustdetect dnsdetect ilsdetect netbiosfirew#lfirewall interzone local untrusterzone local dmz direction outbo detect ftpdetect sqlnetus1 directiondetect h323detect rtspdetect qqdetect msnfirewalldetect dnsr default pdetect ilsone local udetect netbiosbound#firewall interzone local dmz detect ftpall packet-detect mmslt permit idetect mgcpt untrust didetect pptpnddetect sipdetect sqlnetdetect h323firewaldetect rtsper default pdetect qqzonedetect msndetectdetect mmsfirewaldetect mgcper default pdetect pptpne trust dmzdetect siputbounddetect sqlnetdetect h323detect rtspfirewadetect qqilter defadetect dnsnterzone dmdetect ilsrection inbdetect netbios#detect mmsone dmz untdetect mgcpn outbounddetect pptpdetect sipdetect sqlnetdetect h323r 0 protocoldetect rtsp18.56.104.18detect qqe 192.100.detect dnsdetect ilsdetect netbios#firewall interzone trust untrustlobal 218.56.104.*** any inside detect ftp anydetect mmsdetect mgcpdetect pptp#detect siphables enabdetect sqlnet#detect h323v6 sessiondetect rfirewall defend http-flooddetect ftpdetect mmsfirewadetect mgcpt-scan enabldetect pptpdetect sipewall defendetect sqlnetledetect h323firewdetect rtspmp-flood enadetect qqdetect msndetect ilsdetect netbioswall defend syn#lfirewall interzone trust us1firewall defendetect ftpenabledetect mmsdetect mgcp defend sip-detect pptpdetect sipfirdetect sqlnetp-flood fingerdetect h323tination-maxdetect rtspdetect qqdetect dnsdetect ilsdefend udp-detect netbiost-hit source-ma#rfirewall interzone trust us2 detect ftpwall defenddetect mmsort range 1detect mgcpdetect pptpdetecdetect ilsdetect netbios##sfirewall interzone dmz untrustlicense-server domain lic.hudetect ftpdetect mms#detect mgcp enabledetect pptpweb-managerdetect sipable port 8user-managdetect rtspication secudetect qq888detect msndetect dns#detect ilsrver templadetect netbios#firewall interzone us1 untrustlate test.tpl detect ftpldap-servdetect mmsation base-detect mgcpin,dc=comdetect pptpdetect sipdetect sqlneter group-filtedetect h323detect rtsp-server authdetect qqfilter (obdetect dnsdetect ilsdetect netbiosldap-server u#rfirewall interzone us2 untrustldap-server server-typdetect ftpdetect m#5firewall interzone us1 dmz#acl ndetect ftpdetect mmsermit udp sdetect mgcp 1701detect pptpdetect sip 10 permitdetect rtsp#acldetect qq1detect dnse proposaldetect ilsencrypdetect netbiosdes-cbc#firewall interzone us2 dmzup2 group1 detect ftp-algorithmdetect mmshmac-sha1-9detect mgcpdetect pptpdetect sip#detect sqlnet111583362detect h323exchadetect rtspdetect qqe negotiatdetect dnsdetect ilspre-shadetect netbios;hfv{*71&V3Zc:Q#Cfirewall interzone us2 us1 detectdetect ilsdetect netbiosp encryption-al#r#hl2tp-group 1undo tunnel authenticationtemplate tpl20111583362 1 allow l2tp virtual-template 0security acl 3000#bgp 2#uripv4-family unicastnsparentundo synchronizationike-peer ike20111583#2aaalocal-user user2 password cipher %$%$c'D=2Et9!4PN)9O{Ix*S,d[R%$%$tipointl2tp-user-accesslocal-user user2 service-type ppplocal-addreslocal-user user2 level 0local-user user3 password cipher %$%$`;WkNM${E;O=5--=%y)-;\SJ%$%$sa duration time-based 3600#ipslocal-user user3 service-type pppkmp template tpllocal-user user3local-user user5 password cipher %$%$mkyG076$a8C'6T6lJN)FG"vm%$%$ remote address pool#interfalocal-user user5 service-type pppip address 10.local-user user5 level 0local-user user1 password cipher %$%$#P{Q0BpNp"yz9!2LK54Bag^U%$%$ip address 218.56.104.*** 255.255.255.252local-user user1 service-type pppy ipsec2011158331 auto-neglocal-user user1 level 0nat enablelocal-user huawei password cipher %$%$-a$}Vs@0k&S}SpNMuu/E6e\S%$%$ULL0 #firewall zone localset prilocal-user huawei password valid-days 999 trustset priority 85local-user huawei serv ftpdeauthentication-scheme test.scmdetect sipauthentication-mode vpndbdetect sqlnet#deauthorization-scheme defaultqqdetect msnauthorization-scheme test.scmdetect ilsdetectauthorization-mode vpndbinterface GigabitEthernet0/#accounting-scheme default#firewall zone dm#domain defaultet priority 50domain dot1xdetect ftpdomain test.domct rtspauthentication-scheme test.scm mgcpdetect sipdetect mmsdip route-static 192.100.7.0 255.255.255.0 10.10.10.2 pptp detect sqlnetdete#banner enabledetect qq#v-gateway test 218.56.104.*** private detect netbios#firewall zone#auser-interface con 0set priorituser-interface tty 2 3etect ftpmodem bothuser-interface vty 0 4detect mgcpauthentication-mode aaadetect pptpprotocol inbound alldetect h32#ip address-set sslvpn type objectetect dnsdetect ilsaddress 0 11.50.1.0 mask 24#firewall int#zsa l#aslbust#cwmp#detect h32policy 1detecaction permitdetect qqpolicy source 1.5.1.0 mask 24 detect dnsdetectpolicy destination 1.5.2.0 mask 24#firewall interzone localpolicy 0action permittect ftppolicy source 1.4.1.0 mask 24ect mgcpdetect pppolicy destination 1.3.1.0 mask 24detect sqlnetdetec#hnat-policy interzone trust untrust outboundtect qq detect msnnetwork-extension enablenetwork-extension point-to-point enablenetwork-extension netpool 10.5.5.50 10.5.5.150 255.255.255.0 network-extension mode manualnetwork-extension manual-route 10.5.5.0 255.255.255.0network-extension manual-route 124.0.0.0 255.0.0.0network-extension manual-route 119.0.0.0 255.0.0.0network-extension manual-route 183.0.0.0 255.0.0.0network-extension manual-route 111.0.0.0 255.0.0.0network-extension manual-route 1.0.0.0 255.0.0.0network-extension manual-route 11.0.0.0 255.0.0.0network-extension manual-route 12.0.0.0 255.0.0.0network-extension manual-route 13.0.0.0 255.0.0.0network-extension manual-route 14.0.0.0 255.0.0.0network-extension manual-route 15.0.0.0 255.0.0.0network-extension manual-route 16.0.0.0 255.0.0.0network-extension manual-route 17.0.0.0 255.0.0.0network-extension manual-route 18.0.0.0 255.0.0.0network-extension manual-route 19.0.0.0 255.0.0.0network-extension manual-route 20.0.0.0 255.0.0.0securitypolicy-default-action permit user-src-ippolicy-default-action permit user-dst-ippolicy-default-action permit user-urlpolicy-default-action permit vt-src-ippassword-setting password-intension low 8 high 31 digits 1 letters 2 mix password-setting safe-policy 1password-setting lifetime 0 alarm 0certification cert-anonymous cert-field user-filter subject cn group-filter subject cncertification cert-anonymous filter-policy permit-allcertification cert-challenge cert-field user-filter subject cncertification user-cert-filter key-usage any#****END****##return<USG2200><USG2200><USG2200><USG2200><USG2200>。
网络安全之华为USG防火墙配置实例

网络安全之华为USG防火墙配置实例USG5500系列产品是华为技术有限公司面向大中型企业和下一代数据中心推出的新一代电信级统一安全网关设备。
USG5500系列产品部署于网络出口处,有效阻止Internet 上的黑客入侵、DDoS攻击,阻止内网用户访问非法网站,限制带宽,为内部网络提供一个安全可靠的网络环境。
这里华迪教育以此为例,给同学们讲解防火墙配置实例。
华为USG防火墙配置内容:(1)内部网络通过防火墙访问外部网络(NAT)(2)外部网络能够访问内部服务器的映射网站主要配置命令如下:Step 1: 设置内、外网接口IPinterface GigabitEthernet0/0/1ip address 192.168.10.1 255.255.255.0interface GigabitEthernet0/0/8ip address 211.95.1.200 255.255.255.0Step 2: 指定内网信任区和外网非信任区firewall zone trustdetect ftp (启用FTP应用层转换)add interface GigabitEthernet0/0/1firewall zone untrustadd interface GigabitEthernet0/0/8step 3 : 开启内网FTP服务映射到外网,开通区域间的通信许可firewall interzone trust untrustdetect ftp (开启内网到外网的FTP服务映射)firewall packet-filter default permit allstep 4:定义NAT地址池、配置NAT Server发布内网站点服务nat address-group 1 211.95.1.200 211.95.1.200nat server zone untrust protocol tcp global 211.95.1.200 www inside 192.168.10.254 wwwnat server zone untrust protocol tcp global 211.95.1.200 ftp inside 192.168.10.254 ftpnat server zone trust protocol tcp global 211.95.1.200 www inside 192.168.10.254 wwwnat server zone trust protocol tcp global 211.95.1.200 ftp inside 192.168.10.254 ftpStep 5 :配置nat转换,使得内网可以访问外网nat-policy interzone trust untrust outboundpolicy 1action source-natpolicy source 192.168.10.0 0.0.0.255address-group 1Step 6: 配置源地址转换,强制要求内网用户须通过映射地址访问内部服务器nat-policy zone trustpolicy 1action source-natpolicy source 192.168.10.0 0.0.0.255policy destination 211.95.1.254 0 address-group 1。
华为防火墙配置使用手册(自己写)

华为防火墙配置使用手册防火墙默认的管理接口为g0/0/0,默认的ip地址为192.168.0.1/24,默认g0/0/0接口开启了dhcp server,默认用户名为admin,默认密码为Admin@123一、配置案例1.1 拓扑图GE 0/0/1:10.10.10.1/24GE 0/0/2:220.10.10.16/24GE 0/0/3:10.10.11.1/24WWW服务器:10.10.11.2/24(DMZ区域)FTP服务器:10.10.11.3/24(DMZ区域)1.2 Telnet配置配置VTY 的优先级为3,基于密码验证。
# 进入系统视图。
<USG5300> system-view# 进入用户界面视图[USG5300] user-interface vty 0 4# 设置用户界面能够访问的命令级别为level 3[USG5300-ui-vty0-4] user privilege level 3配置Password验证# 配置验证方式为Password验证[USG5300-ui-vty0-4] authentication-mode password# 配置验证密码为lantian[USG5300-ui-vty0-4]set authentication password simple lantian ###最新版本的命令是authentication-mode password cipher huawei@123配置空闲断开连接时间# 设置超时为30分钟[USG5300-ui-vty0-4] idle-timeout 30[USG5300] firewall packet-filter default permit interzone untrust local direction inbound //不加这个从公网不能telnet防火墙。
基于用户名和密码验证user-interface vty 0 4authentication-mode aaaaaalocal-user admin password cipher ]MQ;4\]B+4Z,YWX*NZ55OA!!local-user admin service-type telnetlocal-user admin level 3firewall packet-filter default permit interzone untrust local direction inbound如果不开放trust域到local域的缺省包过滤,那么从内网也不能telnet的防火墙,但是默认情况下已经开放了trust域到local域的缺省包过滤。
华为USG设备配置脚本及联通最新路由表

USG2000基础配置手册初始化设备:reset saved-configurationREBOOTNY1.# 进入系统视图。
<USG> system-view# 进入Ethernet 0/0/0视图。
[USG A] interface Ethernet 0/0/0# 配置Ethernet 0/0/0(公网)的IP地址。
[USG A-Ethernet0/0/0] ip address 61.163.165.108 255.255.255.128 #公网IP,运营商提供# 退回系统视图。
[USG A-Ethernet0/0/0] quit2.# 进入Ethernet 0/0/1视图。
[USG A] interface Ethernet 0/0/1# 配置内部局域网Ethernet 0/0/1的IP地址。
[USG A-Ethernet0/0/1] ip address 192.168.0.1 255.255.255.0[USG A-Ethernet0/0/1] dhcp select interface# 退回系统视图。
[USG A-Ethernet0/0/1] quit3.# 进入Trust区域视图。
[USG A] firewall zone trust# 配置Ethernet 0/0/1加入Trust区域。
#通常内网在trust区域[USG A-zone-trust] add interface Ethernet 0/0/1# 退回系统视图。
[USG A-zone-trust] quit# 进入Untrust区域视图。
[USG A] firewall zone untrust# 配置Ethernet 0/0/0加入Untrust区域。
#通常外网在untrust区域[USG A-zone-untrust] add interface Ethernet 0/0/0# 退回系统视图。
[USG A-zone-untrust] quit4.#配置需要上网的ACL[USG] acl 2000[USG-acl-basic-2000] rule permit[USG-acl-basic-2000] quit5.# 配置NAT地址池。
网络安全之华为USG防火墙配置实例

网络安全之华为USG防火墙配置实例USG5500系列产品是华为技术有限公司面向大中型企业和下一代数据中心推出的新一代电信级统一安全网关设备。
USG5500系列产品部署于网络出口处,有效阻止Internet 上的黑客入侵、DDoS攻击,阻止内网用户访问非法网站,限制带宽,为内部网络提供一个安全可靠的网络环境。
这里华迪教育以此为例,给同学们讲解防火墙配置实例。
华为USG防火墙配置内容:(1)内部网络通过防火墙访问外部网络(NAT)(2)外部网络能够访问内部服务器的映射网站主要配置命令如下:Step 1: 设置内、外网接口IPinterface GigabitEthernet0/0/1ip address 192.168.10.1 255.255.255.0interface GigabitEthernet0/0/8ip address 211.95.1.200 255.255.255.0Step 2: 指定内网信任区和外网非信任区firewall zone trustdetect ftp (启用FTP应用层转换)add interface GigabitEthernet0/0/1firewall zone untrustadd interface GigabitEthernet0/0/8step 3 : 开启内网FTP服务映射到外网,开通区域间的通信许可firewall interzone trust untrustdetect ftp (开启内网到外网的FTP服务映射)firewall packet-filter default permit allstep 4:定义NAT地址池、配置NAT Server发布内网站点服务nat address-group 1 211.95.1.200 211.95.1.200nat server zone untrust protocol tcp global 211.95.1.200 www inside 192.168.10.254 wwwnat server zone untrust protocol tcp global 211.95.1.200 ftp inside 192.168.10.254 ftpnat server zone trust protocol tcp global 211.95.1.200 www inside 192.168.10.254 wwwnat server zone trust protocol tcp global 211.95.1.200 ftp inside 192.168.10.254 ftpStep 5 :配置nat转换,使得内网可以访问外网nat-policy interzone trust untrust outboundpolicy 1action source-natpolicy source 192.168.10.0 0.0.0.255address-group 1Step 6: 配置源地址转换,强制要求内网用户须通过映射地址访问内部服务器nat-policy zone trustpolicy 1action source-natpolicy source 192.168.10.0 0.0.0.255policy destination 211.95.1.254 0 address-group 1。
华为防火墙-USG6000-全图化Web典型配置案例(V4.0)

文档版本V4.0发布日期2016-01-20登录Web 配置界面Example9:应用控制(限制P2P 流量、禁用QQ )Example8:基于用户的带宽管理Example7:SSL VPN 隧道接入(网络扩展)Example6:客户端L2TP over IPSec 接入(VPN Client/Windows/Mac OS/Android/iOS )Example5:点到多点IPSec 隧道(策略模板)Example4:点到点IPSec 隧道Example3:内外网用户同时通过公网IP 访问FTP 服务器Example2:通过PPPoE 接入互联网Example1:通过静态IP 接入互联网目录341118263651116131141组网图缺省配置管理接口 GE0/0/0IP 地址 192.168.0.1/24 用户名/密码admin/Admin@123登录Web 配置界面6~810及以上配置登录PC 自动获取IP 地址1在浏览器中输入https://接口IP 地址:port2输入用户名/密码3Firewall192.168.0.*GE0/0/0192.168.0.1/24网口局域网内所有PC都部署在10.3.0.0/24网段,均通过DHCP动态获得IP地址。
企业从运营商处获取的固定IP地址为1.1.1.1/24。
企业需利用防火墙接入互联网。
项目数据说明DNS服务器 1.2.2.2/24 向运营商获取。
网关地址 1.1.1.254/24 向运营商获取。
23配置外网接口 参数45配置内网接口参数6123配置内网接口GE1/0/2的DHCP 服务,使其为局域网内的PC 分配IP 地址412134配置允许内网IP地址访问外网241新建源NAT ,实现内网用户正常访问Internet531、检查接口GigabitEthernet 1/0/1(上行链路)的连通性。
1查看接口状态是否为Up。
2、在内网PC上执行命令ipconfig /all,PC正确分配到IP地址和DNS地址。
华为USG设备配置脚本及联通最新路由表

USG2000基础配置手册初始化设备:reset saved-configurationREBOOTNY1.# 进入系统视图。
<USG> system-view# 进入Ethernet 0/0/0视图。
[USG A] interface Ethernet 0/0/0# 配置Ethernet 0/0/0(公网)的IP地址。
[USG A-Ethernet0/0/0] ip address 61.163.165.108 255.255.255.128 #公网IP,运营商提供# 退回系统视图。
[USG A-Ethernet0/0/0] quit2.# 进入Ethernet 0/0/1视图。
[USG A] interface Ethernet 0/0/1# 配置内部局域网Ethernet 0/0/1的IP地址。
[USG A-Ethernet0/0/1] ip address 192.168.0.1 255.255.255.0[USG A-Ethernet0/0/1] dhcp select interface# 退回系统视图。
[USG A-Ethernet0/0/1] quit3.# 进入Trust区域视图。
[USG A] firewall zone trust# 配置Ethernet 0/0/1加入Trust区域。
#通常内网在trust区域[USG A-zone-trust] add interface Ethernet 0/0/1# 退回系统视图。
[USG A-zone-trust] quit# 进入Untrust区域视图。
[USG A] firewall zone untrust# 配置Ethernet 0/0/0加入Untrust区域。
#通常外网在untrust区域[USG A-zone-untrust] add interface Ethernet 0/0/0# 退回系统视图。
[USG A-zone-untrust] quit4.#配置需要上网的ACL[USG] acl 2000[USG-acl-basic-2000] rule permit[USG-acl-basic-2000] quit5.# 配置NAT地址池。
华为USG6000系列防火墙共享上网及组网基本配置

华为USG6000系列防火墙共享上网及组网基本配置公司各楼层通过交换机汇聚到楼宇核心交换机,楼宇核心汇聚到总核心,然后通过USG6000安全策略访问外网路由器实现共享上网功能。
楼宇核心:划分楼层VLAN 配置网关上一跳路由<Huawei>sys[huawei]sysname hexinjiaohuan[hexinjiaohuan]vlan batch 10 20 30 40[hexinjiaohuan]int vlan 10[hexinjiaohuan-Vlanif10]ip address 192.168.10.254 24 [hexinjiaohuan]int vlan 20[hexinjiaohuan-Vlanif20]ip address 192.168.20.254 24 [hexinjiaohuan]int vlan 30[hexinjiaohuan-Vlanif30]ip address 192.168.30.254 24 [hexinjiaohuan]int vlan 40[hexinjiaohuan-Vlanif40]ip address 192.168.60.1 30 [hexinjiaohuan]int g0/0/3[hexinjiaohuan-GigabitEthernet0/0/3]port link-type access [hexinjiaohuan-GigabitEthernet0/0/3]port default vlan 10 [hexinjiaohuan]int g0/0/1[hexinjiaohuan-GigabitEthernet0/0/1]port link-type access [hexinjiaohuan-GigabitEthernet0/0/1]port default vlan 20 [hexinjiaohuan]int g0/0/4[hexinjiaohuan-GigabitEthernet0/0/4]port link-type access [hexinjiaohuan-GigabitEthernet0/0/4]port default vlan 30 [hexinjiaohuan]int g0/0/2[hexinjiaohuan-GigabitEthernet0/0/2]port link-type access [hexinjiaohuan-GigabitEthernet0/0/2]port default vlan 40 [hexinjiaohuan]ip route-static 0.0.0.0 0.0.0.0 192.168.60.2<hexinjiaohuan>saveThe current configuration will be written to the device.Are you sure to continue?[Y/N]y总核心交换机:配置上下访问端口和上下访问路由<Huawei>sys[Huawei]sysname zonghexin[zonghexin]vlan batch 40 50[zonghexin]int vlan 40[zonghexin-Vlanif40]ip address 192.168.60.2 30 [zonghexin]int g0/0/2[zonghexin-GigabitEthernet0/0/2]port link-type access [zonghexin-GigabitEthernet0/0/2]port default vlan 40 [zonghexin]int vlan 50[zonghexin-Vlanif50]ip address 192.100.50.2 30 [zonghexin]int g0/0/1[zonghexin-GigabitEthernet0/0/1]port link-type access [zonghexin-GigabitEthernet0/0/1]port default vlan 50 [zonghexin]ip route-static 192.168.10.0 255.255.255.0 192.168.60.1 [zonghexin]ip route-static 192.168.20.0 255.255.255.0 192.168.60.1[zonghexin]ip route-static 192.168.30.0 255.255.255.0 192.168.60.1 [zonghexin]ip route-static 0.0.0.0 0.0.0.0 192.100.50.1<zonghexin>saveThe current configuration will be written to the device.Are you sure to continue?[Y/N]y防火墙USG6000:配置访问策略允许内网所有PC访问外网(路由器)地址Username:adminPassword: (默认密码Admin@123)The password needs to be changed. Change now? [Y/N]: yPlease enter old password: (默认密码Admin@123)Please enter new password: 新密码Please confirm new password: 新密码确认[USG6000V1]int g1/0/1 //配置内网端口[USG6000V1-GigabitEthernet1/0/1]ip address 192.100.50.1 255.255.255.252 [USG6000V1-GigabitEthernet1/0/1]service-manage http permit[USG6000V1-GigabitEthernet1/0/1]service-manage https permit[USG6000V1-GigabitEthernet1/0/1]service-manage ping permit[USG6000V1]int g1/0/0 //配置外网端口[USG6000V1-GigabitEthernet1/0/0]ip address 10.128.60.5 255.255.255.252 [USG6000V1]firewall zone trust //把端口加入到安全域[USG6000V1-zone-trust]add interface GigabitEthernet 1/0/1[USG6000V1]firewall zone untrust //把端口加入到非安全域[USG6000V1-zone-untrust]add interface GigabitEthernet1/0/0[USG6000V1]ip route-static 0.0.0.0 0.0.0.0 10.128.60.6[USG6000V1]ip route-static 192.168.10.0 255.255.255.0 192.100.50.2[USG6000V1]ip route-static 192.168.20.0 255.255.255.0 192.100.50.2[USG6000V1]ip route-static 192.168.30.0 255.255.255.0 192.100.50.2[USG6000V1]security-policy //访问策略[USG6000V1-policy-security]rule name "trust to untrust"[USG6000V1-policy-security-rule-trust to untrust][USG6000V1-policy-security-rule-trust to untrust]source-zone trust[USG6000V1-policy-security-rule-trust to untrust]destination-zone untrust [USG6000V1-policy-security-rule-trust to untrust] action permit[USG6000V1-policy-security-rule-trust to untrust] rule name local[USG6000V1-policy-security-rule-local]source-zone local[USG6000V1-policy-security-rule-local]destination-zone trust[USG6000V1-policy-security-rule-local]action permit<USG6000V1>save路由器:[Huawei]int g0/0/1[Huawei-GigabitEthernet0/0/1]ip address 10.128.60.6 255.255.255.252 [Huawei]ip route-static 0.0.0.0 0.0.0.0 10.128.60.5<Huawei>savepc>ping 10.128.60.6Ping 10.128.60.6: 32 data bytes, Press Ctrl_C to breakFrom 10.128.60.6: bytes=32 seq=1 ttl=252 time=765 ms From 10.128.60.6: bytes=32 seq=2 ttl=252 time=141 ms From 10.128.60.6: bytes=32 seq=3 ttl=252 time=78 msFrom 10.128.60.6: bytes=32 seq=4 ttl=252 time=78 msFrom 10.128.60.6: bytes=32 seq=5 ttl=252 time=78 msPC机测试通过基本功能实现。
华为防火墙USG3030的应用脚本

firewall defend ip-fragment enable
firewall defend ftp-bounce enable
firewall defend packet-header check enable
firewall defend large-icmp enable
nat server protocol tcp global 116.113.83.2 pptp inside 10.6.2.30 pptp
nat server protocol udp global 116.113.83.2 1701 inside 10.6.2.30 1701
nat server protocol udp global 116.113.83.2 1723 inside 10.6.2.30 1723
l<MFTG0-USG3030>dis cur
#
sysname MFTG0-USG3030
#
super password level 3 cipher `'"C4N8+=ROQ=^Q`MAF4<1!!
#
firewall dpi packet-number 2
#
firewall p2p-car include BT
firewall defend route-record enable
firewall defend tracert enable
firewall defend time-stamp enable
firewall defend ping-of-death enable
华为USG5500防火墙配置实验一
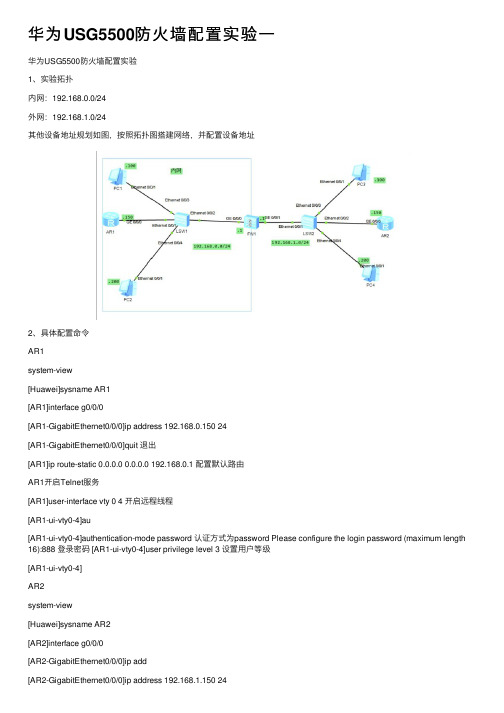
华为USG5500防⽕墙配置实验⼀华为USG5500防⽕墙配置实验1、实验拓扑内⽹:192.168.0.0/24外⽹:192.168.1.0/24其他设备地址规划如图,按照拓扑图搭建⽹络,并配置设备地址2、具体配置命令AR1system-view[Huawei]sysname AR1[AR1]interface g0/0/0[AR1-GigabitEthernet0/0/0]ip address 192.168.0.150 24[AR1-GigabitEthernet0/0/0]quit 退出[AR1]ip route-static 0.0.0.0 0.0.0.0 192.168.0.1 配置默认路由AR1开启Telnet服务[AR1]user-interface vty 0 4 开启远程线程[AR1-ui-vty0-4]au[AR1-ui-vty0-4]authentication-mode password 认证⽅式为password Please configure the login password (maximum length 16):888 登录密码 [AR1-ui-vty0-4]user privilege level 3 设置⽤户等级[AR1-ui-vty0-4]AR2system-view[Huawei]sysname AR2[AR2]interface g0/0/0[AR2-GigabitEthernet0/0/0]q[AR1]ip route-static 0.0.0.0 0.0.0.0 192.168.1.1AR2配置TelnetAR2]us[AR2]user-interface v[AR2]user-interface vty 0 4[AR2-ui-vty0-4]au[AR2-ui-vty0-4]authentication-mode p[AR2-ui-vty0-4]authentication-mode passwordPlease configure the login password (maximum length 16):666 或者[AR2-ui-vty0-4]set authentication password cipher 666 [AR2-ui-vty0-4]user privilege level 3[AR2-ui-vty0-4]q防⽕墙配置:The device is running!system-view[SRG]sysname FW1[FW1]interface g0/0/0[FW1-GigabitEthernet0/0/0]ip add 192.168.0.1 24Warning: Address already exists! 默认接⼝地址已经存在,不⽤管[FW1-GigabitEthernet0/0/0]q[FW1]interface g0/0/1[FW1-GigabitEthernet0/0/1]ip add 192.168.1.1 24[FW1-GigabitEthernet0/0/1]q[FW1]display zone 显⽰区域配置localpriority is 100#trustpriority is 85interface of the zone is (1):GigabitEthernet0/0/0#untrustpriority is 5interface of the zone is (0):dmzpriority is 50interface of the zone is (0):#[FW1][FW1]firewall zone name outside 创建⼀个名字为outside的区域[FW1-zone-outside]set priority 30 设置安全等级为30[FW1-zone-outside]q[FW1]firewall zone name inside[FW1-zone-inside]set priority 90[FW1-zone-inside]q[FW1]display zone[FW1]firewall zone outside 进⼊outside区域,把接⼝g0/0/1接⼊该区域[FW1-zone-outside]add interface GigabitEthernet 0/0/1 [FW1-zone-outside]display this 显⽰当前的配置#firewall zone name outsideset priority 30add interface GigabitEthernet0/0/1#return[FW1-zone-outside]q[FW1]display policy all 查看策略policy zone local#policy zone trust#policy zone untrust#policy zone dmz#policy zone outside#policy zone inside#policy interzone local trust outboundfirewall default packet-filter is permit#policy interzone local untrust inboundfirewall default packet-filter is deny#policy interzone local untrust outbound firewall default packet-filter is permit # policy interzone local dmz inboundfirewall default packet-filter is deny#policy interzone local dmz outboundfirewall default packet-filter is permit #policy interzone local outside inboundfirewall default packet-filter is deny#policy interzone local outside outbound firewall default packet-filter is permit # policy interzone local inside inboundfirewall default packet-filter is deny#policy interzone local inside outboundfirewall default packet-filter is permit #policy interzone trust untrust inboundfirewall default packet-filter is deny#policy interzone trust untrust outbound firewall default packet-filter is deny#policy interzone trust dmz inboundfirewall default packet-filter is deny#policy interzone trust dmz outboundfirewall default packet-filter is deny#policy interzone trust outside outbound firewall default packet-filter is deny #policy interzone inside trust inboundfirewall default packet-filter is deny#policy interzone inside trust outboundfirewall default packet-filter is deny#policy interzone dmz untrust inboundfirewall default packet-filter is deny#policy interzone dmz untrust outboundfirewall default packet-filter is deny#policy interzone outside untrust inboundfirewall default packet-filter is deny#policy interzone outside untrust outboundfirewall default packet-filter is deny#policy interzone inside untrust inboundfirewall default packet-filter is deny#policy interzone inside untrust outboundfirewall default packet-filter is deny#policy interzone dmz outside inboundfirewall default packet-filter is deny#policy interzone dmz outside outboundfirewall default packet-filter is deny#policy interzone inside dmz outboundfirewall default packet-filter is deny#policy interzone inside outside inboundfirewall default packet-filter is deny#policy interzone inside outside outboundfirewall default packet-filter is deny#[FW1]创建策略放⾏outbound流量[FW1]policy interzone trust outside outbound 定义outbound流量 [FW1-policy-interzone-trust-outside-outbound]poli [FW1-policy-interzone-trust-outside-outbound]policy 1[FW1-policy-interzone-trust-outside-outbound-1]poli[FW1-policy-interzone-trust-outside-outbound-1]policy so[FW1-policy-interzone-trust-outside-outbound-1]policy source192.168.0.150 001:27:13 2016/11/15[FW1-policy-interzone-trust-outside-outbound-1]poli[FW1-policy-interzone-trust-outside-outbound-1]policy de[FW1-policy-interzone-trust-outside-outbound-1]policy destination any 01:27:25 2016/11/15[FW1-policy-interzone-trust-outside-outbound-1]ac[FW1-policy-interzone-trust-outside-outbound-1]action p[FW1-policy-interzone-trust-outside-outbound-1]action permit01:27:34 2016/11/15[FW1-policy-interzone-trust-outside-outbound-1][FW1-policy-interzone-trust-outside-outbound-1]q01:27:37 2016/11/15[FW1-policy-interzone-trust-outside-outbound][FW1-policy-interzone-trust-outside-outbound]q01:27:38 2016/11/15[FW1][FW1]dis[FW1]display po[FW1]display poli[FW1]display policy i[FW1]display policy interzone t[FW1]display policy interzone trust o[FW1]display policy interzone trust outside outbound01:27:55 2016/11/15policy interzone trust outside outboundfirewall default packet-filter is denypolicy 1 (0 times matched)action permitpolicy service service-set ippolicy source 192.168.0.0 mask 255.255.255.0policy source 192.168.0.150 0policy destination any[FW1]firewall packet-filter default permit interzone trust outside Warning:Setting the default packet filtering to permit poses security risks. Youare advised to configure the security policy based on the actual data flows. Are you sure you want to continue?[Y/N]y[FW1]dis[FW1]display policy interzone trust outside outbound01:28:23 2016/11/15policy interzone trust outside outboundfirewall default packet-filter is permitpolicy 1 (0 times matched)action permitpolicy service service-set ippolicy source 192.168.0.0 mask 255.255.255.0policy source 192.168.0.150 0policy destination any恢复默认值deny[FW1]firewall packet-filter default deny interzone trust outside [FW1]display policy interzone trust outside outbound01:32:06 2016/11/15policy 1 (0 times matched)action permitpolicy service service-set ippolicy source 192.168.0.0 mask 255.255.255.0policy source 192.168.0.150 0policy destination any⽤内⽹的路由Telnet AR2后,可以登录在防⽕墙查看会话状态[FW1]display firewall session table verbose00:58:32 2016/11/15Current Total Sessions : 2telnet VPN:public --> publicZone: trust--> outside TTL: 00:00:10 Left: 00:00:00Interface: GigabitEthernet0/0/1 NextHop: 192.168.1.150 MAC: 00-e0-fc-7a-0b-5 a<--packets:18 bytes:867 -->packets:17 bytes:728192.168.0.150:49272-->192.168.1.150:23telnet VPN:public --> publicZone: trust--> outside TTL: 00:10:00 Left: 00:09:55Interface: GigabitEthernet0/0/1 NextHop: 192.168.1.150 MAC: 00-e0-fc-7a-0b-5 a<--packets:16 bytes:725 -->packets:17 bytes:726192.168.0.150:49957-->192.168.1.150:23[FW1]如何允许外⽹的⽤户Telnet到内⽹的路由器[FW1]policy interzone trust outside inbound[FW1-policy-interzone-trust-outside-inbound]policy 1[FW1-policy-interzone-trust-outside-inbound-1]policy source 192.168.1.150 0 [FW1-policy-interzone-trust-outside-inbound-1]policy destination 192.168.0.150 0 [FW1-policy-interzone-trust-outside-inbound-1]policy service service-set telnet [FW1-policy-interzone-trust-outside-inbound-1]action permit验证试验效果。
华为USG2200系列防火墙配置案例

华为USG2200系列防火墙配置案例以下是一份华为USG2200系列防火墙的配置案例:1.基本配置首先登录到防火墙的Web界面,在“系统”选项下进行基本的系统配置。
包括设定主机名、时区、DNS服务器和网关地址等。
2.网络配置在“网络”选项中进行网络配置。
设定防火墙的网络接口和IP地址。
可以设定多个网络接口,为不同的网络提供连接。
配置完成后,需要应用并重启防火墙。
3.防火墙策略在“安全策略”选项下进行防火墙策略的配置。
可以根据实际需求设置入站和出站规则,限制或允许特定的IP地址或端口访问。
可以设置默认的阻止或允许策略。
4.访问控制列表(ACL)在“ACL”选项中进行访问控制列表的配置。
可以创建不同的ACL规则,根据源和目的IP地址、端口和协议等进行过滤控制。
可以设置允许或阻止特定的流量通过。
5.网络地址转换(NAT)在“NAT”选项中进行网络地址转换的配置。
可以将内部私有IP地址映射到公网IP地址,实现内部网络与外部网络的通信。
配置时需要设置源和目的IP地址的转换规则。
6.入侵防御系统(IDS)在“IDS”选项中进行入侵防御系统的配置。
可以启用IDS功能,并设置规则、行为和告警等。
IDS可以监测和阻止可能的攻击行为,保护网络的安全。
7.虚拟专网(VPN)在“VPN”选项中进行虚拟专网的配置。
可以创建VPN隧道,实现不同地点的安全通信。
可以设置IPSec或SSL VPN,并配置相关的参数和安全策略。
8.日志和告警在“日志和告警”选项中进行日志和告警的配置。
可以设定日志记录的级别和方式,并设置告警的方式和内容。
日志和告警功能可以帮助管理员及时发现和处理安全事件。
以上只是一个简单的配置案例,实际情况可能会更加复杂。
华为USG2200系列防火墙拥有多种高级功能,如反病毒、应用控制、网页过滤等,可以根据具体需求进行配置。
总结起来,华为USG2200系列防火墙的配置步骤包括基本配置、网络配置、防火墙策略、ACL、NAT、IDS、VPN、日志和告警等。
华为USG的PPOE的经典配置

介绍关于华为防火墙USG.PPPoE的配置。
PPPoE典型应用:1.用户使用操作系统自带PPPoE客户端拨号,自己独享账号上网。
2.用户使用桌面网络设备(路由器/防火墙)等拨号。
3.使用NAT对内部网络地址进行转换。
并对内部网络用户启用DHCP,实现用户网络多台设备共享一个账号上网。
4.本文模拟应用2的网络模式,使用USG2110做拨号客户端,USG3000模拟运营商的宽带接入设备。
在USG3000上起Loopback口3.3.3.3模拟Internet应用,PC上启用DHCP。
二. PPPoE客户端(USG2110)配置1.配置内网用户网关地址和DHCP Serverinterface Ethernet0/0/1ip address 192.168.1.1 255.255.255.02.为内网用户配置DHCP Server,为内部用户分配IP地址dhcp enabledhcp server ip-pool 1network 192.168.1.0 mask 255.255.255.0gateway-list 192.168.1.1dns-list 11.1.1.1dhcp server forbidden-ip 192.168.1.13.设置PPPoE拨号参数dialer-rule 1 ip permit //配置拨号访问控制列表,匹配上才触发拨号interface Dialer1 //创建一个dialer口link-protocol ppp //拨号的用户名密码,由于不知道对端到底采用PAP还是CHAP,所以最好两个都配上ppp pap local-user huawei password simple huawei123ppp chap user huaweippp chap password simple huawei123ip address ppp-negotiate //配置地址由对端宽带接入设备分配dialer user huawei //配置触发拨号的用户dialer-group 1 //这个数字与dialer-rule编号一致dialer bundle 1 //配置此拨号串编号4.将dialer口绑定到出接口上,数字与dialer bundle一致interface Ethernet0/0/0pppoe-client dial-bundle-number5.将相关接口加入域firewall zone trustadd interface Ethernet0/0/1firewall zone untrustadd interface Dialer16.配置域间包过滤和NAT转换,采用easy ip方式,出口采用dialer口acl number 3001rule 5 permit ip source 192.168.1.0 0.0.0.255 logging firewall interzone trust untrustpacket-filter 3001 outboundnat outbound 3001 interface Dialer17.配置默认路由,由dialer口出去ip route-static 0.0.0.0 0.0.0.0 Dialer18.开启trust和untrust区域到local区域的默认包过滤firewall packet-filter default permit interzone local trustfirewall packet-filter default permit interzone local untrust三、PPPoE服务器端(USG3000)配置1.开启默认包过滤firewall packet-filter default permit all2.配置PPPoE Server参数interface Virtual-Template1 //创建一个VT接口ppp authentication-mode pap //采用的认证方式ip address 1.1.1.1 255.255.255.252 //配置VT口的IP地址remote address pool //为客户端分配的地址interface GigabitEthernet0/2pppoe-server bind Virtual-Template 1 //将VT口绑定到实接口上3.loopback口模拟Internet应用interface LoopBack0ip address 3.3.3.3 255.255.255.2554.将VT口加入域,实接口可不加firewall zone trustadd interface Virtual-Template15.配置本地的用户信息库,为客户端认证的账号和密码库local-user huawei password simple huawei123…6.配置地址池,客户端的地址从此池中分配ip pool 0 2.2.2.2 2.2.3.37.设置静态默认路由,由VT口出去ip route-static 0.0.0.0 0.0.0.0 Virtual-Template1四、验证效果1.PC上获得IP地址后,ping 3.3.3.3,查看效果C:\Documents and Settings\Administrator>ping 3.3.3.3Pinging 3.3.3.3 with 32 bytes of data:Reply from 3.3.3.3: bytes=32 time=2ms TTL=254Reply from 3.3.3.3: bytes=32 time=2ms TTL=254Reply from 3.3.3.3: bytes=32 time=2ms TTL=254Reply from 3.3.3.3: bytes=32 time=2ms TTL=254Ping statistics for 3.3.3.3:Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),Approximate round trip times in milli-seconds:Minimum = 2ms, Maximum = 2ms, Average = 2ms2.在client上查看会话表,可查看出会话、NAT转换信息[PPPoE-Client]display firewall session tableicmp:192.168.1.2:768[2.2.2.2:13093]-->3.3.3.3:7683.在PPPoE Client上查看PPPoE会话信息[PPPoE-Client]display pppoe-client session summaryPPPoE Client Session:ID Bundle Dialer Intf Client-MAC Server-MAC State3 1 1 Eth0/0/0 0018827712a7 0018828243d0 PPPUP4.在PPPoE Server上查看会话信息,同client上对应[PPPoE-Server]display pppoe-server session allSID Intf State OIntf RemMAC LocMAC3 Virtual-Template1:0 UP GE0/2 0018.8277.12a7 0018.8282.43d0。
华为USG5500防火墙配置实验一

华为USG5500防火墙配置实验1、实验拓扑内网:192.168.0.0/24外网:192.168.1.0/24其他设备地址规划如图,按照拓扑图搭建网络,并配置设备地址2、具体配置命令AR1<Huawei>system-view[Huawei]sysname AR1[AR1]interface g0/0/0[AR1-GigabitEthernet0/0/0]ip address 192.168.0.150 24[AR1-GigabitEthernet0/0/0]quit 退出[AR1]ip route-static 0.0.0.0 0.0.0.0 192.168.0.1 配置默认路由AR1开启Telnet服务[AR1]user-interface vty 0 4 开启远程线程[AR1-ui-vty0-4]au[AR1-ui-vty0-4]authentication-mode password 认证方式为password Please configure the login password (maximum length 16):888 登录密码 [AR1-ui-vty0-4]user privilege level 3 设置用户等级[AR1-ui-vty0-4]AR2<Huawei>system-view[Huawei]sysname AR2[AR2]interface g0/0/0[AR2-GigabitEthernet0/0/0]ip add[AR2-GigabitEthernet0/0/0]ip address 192.168.1.150 24[AR2-GigabitEthernet0/0/0]q[AR1]ip route-static 0.0.0.0 0.0.0.0 192.168.1.1AR2配置TelnetAR2]us[AR2]user-interface v[AR2]user-interface vty 0 4[AR2-ui-vty0-4]au[AR2-ui-vty0-4]authentication-mode p[AR2-ui-vty0-4]authentication-mode passwordPlease configure the login password (maximum length 16):666 或者[AR2-ui-vty0-4]set authentication password cipher 666[AR2-ui-vty0-4]user privilege level 3[AR2-ui-vty0-4]q防火墙配置:The device is running!<SRG>system-view[SRG]sysname FW1[FW1]interface g0/0/0[FW1-GigabitEthernet0/0/0]ip add 192.168.0.1 24Warning: Address already exists! 默认接口地址已经存在,不用管[FW1-GigabitEthernet0/0/0]q[FW1]interface g0/0/1[FW1-GigabitEthernet0/0/1]ip add 192.168.1.1 24[FW1-GigabitEthernet0/0/1]q[FW1]display zone 显示区域配置localpriority is 100#trustpriority is 85interface of the zone is (1):GigabitEthernet0/0/0#untrustpriority is 5interface of the zone is (0):#dmzpriority is 50interface of the zone is (0):#[FW1][FW1]firewall zone name outside 创建一个名字为outside的区域[FW1-zone-outside]set priority 30 设置安全等级为30[FW1-zone-outside]q[FW1]firewall zone name inside[FW1-zone-inside]set priority 90[FW1-zone-inside]q[FW1]display zone[FW1]firewall zone outside 进入outside区域,把接口g0/0/1接入该区域[FW1-zone-outside]add interface GigabitEthernet 0/0/1[FW1-zone-outside]display this 显示当前的配置#firewall zone name outsideset priority 30add interface GigabitEthernet0/0/1#return[FW1-zone-outside]q[FW1]display policy all 查看策略policy zone local#policy zone trust#policy zone untrust#policy zone dmz#policy zone outside#policy zone inside#policy interzone local trust inboundfirewall default packet-filter is permit#policy interzone local trust outboundfirewall default packet-filter is permit#policy interzone local untrust inboundfirewall default packet-filter is deny#policy interzone local untrust outbound firewall default packet-filter is permit #policy interzone local dmz inboundfirewall default packet-filter is deny#policy interzone local dmz outboundfirewall default packet-filter is permit #policy interzone local outside inboundfirewall default packet-filter is deny#policy interzone local outside outbound firewall default packet-filter is permit #policy interzone local inside inboundfirewall default packet-filter is deny#policy interzone local inside outboundfirewall default packet-filter is permit #policy interzone trust untrust inboundfirewall default packet-filter is deny#policy interzone trust untrust outbound firewall default packet-filter is deny#policy interzone trust dmz inboundfirewall default packet-filter is deny#policy interzone trust dmz outboundfirewall default packet-filter is deny#policy interzone trust outside inboundfirewall default packet-filter is deny#policy interzone trust outside outbound firewall default packet-filter is deny#policy interzone inside trust inboundfirewall default packet-filter is deny#policy interzone inside trust outboundfirewall default packet-filter is deny#policy interzone dmz untrust inboundfirewall default packet-filter is deny#policy interzone dmz untrust outboundfirewall default packet-filter is deny#policy interzone outside untrust inboundfirewall default packet-filter is deny#policy interzone outside untrust outboundfirewall default packet-filter is deny#policy interzone inside untrust inboundfirewall default packet-filter is deny#policy interzone inside untrust outboundfirewall default packet-filter is deny#policy interzone dmz outside inboundfirewall default packet-filter is deny#policy interzone dmz outside outboundfirewall default packet-filter is deny#policy interzone inside dmz inboundfirewall default packet-filter is deny#policy interzone inside dmz outboundfirewall default packet-filter is deny#policy interzone inside outside inboundfirewall default packet-filter is deny#policy interzone inside outside outboundfirewall default packet-filter is deny#[FW1]创建策略放行outbound流量[FW1]policy interzone trust outside outbound 定义outbound流量 [FW1-policy-interzone-trust-outside-outbound]poli[FW1-policy-interzone-trust-outside-outbound]policy 1[FW1-policy-interzone-trust-outside-outbound-1]poli[FW1-policy-interzone-trust-outside-outbound-1]policy so[FW1-policy-interzone-trust-outside-outbound-1]policy source192.168.0.150 001:27:13 2016/11/15[FW1-policy-interzone-trust-outside-outbound-1]poli[FW1-policy-interzone-trust-outside-outbound-1]policy de[FW1-policy-interzone-trust-outside-outbound-1]policy destination any 01:27:25 2016/11/15[FW1-policy-interzone-trust-outside-outbound-1]ac[FW1-policy-interzone-trust-outside-outbound-1]action p[FW1-policy-interzone-trust-outside-outbound-1]action permit01:27:34 2016/11/15[FW1-policy-interzone-trust-outside-outbound-1][FW1-policy-interzone-trust-outside-outbound-1]q01:27:37 2016/11/15[FW1-policy-interzone-trust-outside-outbound][FW1-policy-interzone-trust-outside-outbound]q01:27:38 2016/11/15[FW1][FW1][FW1]dis[FW1]display po[FW1]display poli[FW1]display policy i[FW1]display policy interzone t[FW1]display policy interzone trust o[FW1]display policy interzone trust outside outbound01:27:55 2016/11/15policy interzone trust outside outboundfirewall default packet-filter is denypolicy 1 (0 times matched)action permitpolicy service service-set ippolicy source 192.168.0.0 mask 255.255.255.0policy source 192.168.0.150 0policy destination any[FW1]firewall packet-filter default permit interzone trust outside Warning:Setting the default packet filtering to permit poses security risks. Youare advised to configure the security policy based on the actual data flows. Are you sure you want to continue?[Y/N]y[FW1]dis[FW1]display policy interzone trust outside outbound01:28:23 2016/11/15policy interzone trust outside outboundfirewall default packet-filter is permitpolicy 1 (0 times matched)action permitpolicy service service-set ippolicy source 192.168.0.0 mask 255.255.255.0policy source 192.168.0.150 0policy destination any恢复默认值deny[FW1]firewall packet-filter default deny interzone trust outside [FW1]display policy interzone trust outside outbound01:32:06 2016/11/15policy interzone trust outside outboundfirewall default packet-filter is denypolicy 1 (0 times matched)action permitpolicy service service-set ippolicy source 192.168.0.0 mask 255.255.255.0policy source 192.168.0.150 0policy destination any用内网的路由Telnet AR2后,可以登录在防火墙查看会话状态[FW1]display firewall session table verbose00:58:32 2016/11/15Current Total Sessions : 2telnet VPN:public --> publicZone: trust--> outside TTL: 00:00:10 Left: 00:00:00Interface: GigabitEthernet0/0/1 NextHop: 192.168.1.150 MAC: 00-e0-fc-7a-0b-5a<--packets:18 bytes:867 -->packets:17 bytes:728192.168.0.150:49272-->192.168.1.150:23telnet VPN:public --> publicZone: trust--> outside TTL: 00:10:00 Left: 00:09:55Interface: GigabitEthernet0/0/1 NextHop: 192.168.1.150 MAC: 00-e0-fc-7a-0b-5a<--packets:16 bytes:725 -->packets:17 bytes:726192.168.0.150:49957-->192.168.1.150:23[FW1]如何允许外网的用户Telnet到内网的路由器[FW1]policy interzone trust outside inbound[FW1-policy-interzone-trust-outside-inbound]policy 1[FW1-policy-interzone-trust-outside-inbound-1]policy source 192.168.1.150 0[FW1-policy-interzone-trust-outside-inbound-1]policy destination 192.168.0.150 0[FW1-policy-interzone-trust-outside-inbound-1]policy service service-set telnet[FW1-policy-interzone-trust-outside-inbound-1]action permit验证试验效果。
华赛防火墙PPPOE拨号配置实例
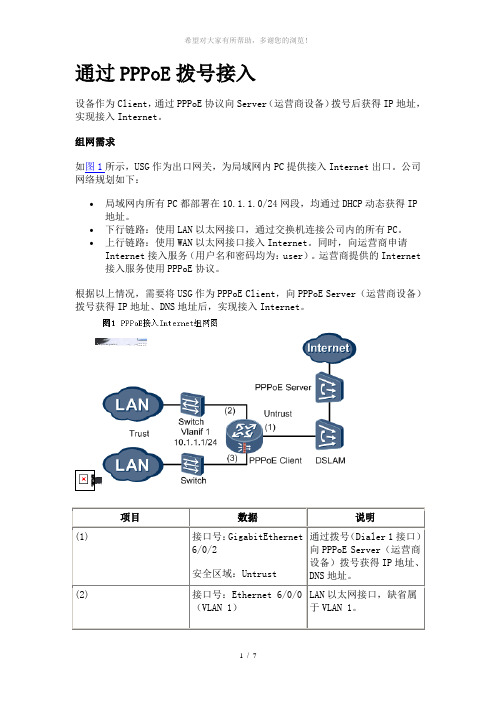
通过PPPoE拨号接入设备作为Client,通过PPPoE协议向Server(运营商设备)拨号后获得IP地址,实现接入Internet。
组网需求如图1所示,USG作为出口网关,为局域网内PC提供接入Internet出口。
公司网络规划如下:•局域网内所有PC都部署在10.1.1.0/24网段,均通过DHCP动态获得IP 地址。
•下行链路:使用LAN以太网接口,通过交换机连接公司内的所有PC。
•上行链路:使用WAN以太网接口接入Internet。
同时,向运营商申请Internet接入服务(用户名和密码均为:user)。
运营商提供的Internet接入服务使用PPPoE协议。
根据以上情况,需要将USG作为PPPoE Client,向PPPoE Server(运营商设备)拨号获得IP地址、DNS地址后,实现接入Internet。
项目数据说明(1) 接口号:GigabitEthernet6/0/2安全区域:Untrust通过拨号(Dialer 1接口)向PPPoE Server(运营商设备)拨号获得IP地址、DNS地址。
(2) 接口号:Ethernet 6/0/0(VLAN 1)LAN以太网接口,缺省属于VLAN 1。
配置思路1.配置下行链路。
在Vlanif 1上开启DHCP Server服务,为PC动态分配IP地址,指定PC 获得的网关和DNS服务器地址均为Vlanif 1接口。
PC上网通常需要解析域名,这就需要为其指定DNS服务器地址。
本例中采用USG作为DNS中继设备。
2.配置上行链路。
3.将接口加入到安全区域,并在域间配置NAT和包过滤。
将连接公司局域网的接口加入到高安全等级的区域(Trust),将连接Internet的上行接口加入到低安全等级的区域(Untrust)。
局域网内通常使用私网地址,访问Internet时,必须配置NAT。
本例中,因为上行接口通过拨号获得IP地址,每次拨号获得的IP地址可能不一样,所以采用Easy IP。
华为防火墙USG配置【范本模板】

内网:配置GigabitEthernet 0/0/1加入Trust区域[USG5300]firewall zone trust[USG5300-zone—untrust] add interface GigabitEthernet 0/0/1外网:配置GigabitEthernet 0/0/2加入Untrust区域[USG5300]firewall zone untrust[USG5300—zone—untrust] add interface GigabitEthernet 0/0/2DMZ:[USG5300]firewall zone dmz[USG5300—zone—untrust] add interface GigabitEthernet 0/0/3[USG5300-zone—untrust]quit1。
4.1 Trust和Untrust域间:允许内网用户访问公网policy 1:允许源地址为10.10.10。
0/24的网段的报文通过[USG5300]policy interzone trust untrust outbound[USG5300—policy—interzone-trust—untrust-outbound] policy 1[USG5300-policy-interzone-trust-untrust-outbound-1] policy source 10。
10。
10。
0 0。
0。
0.255[USG5300-policy-interzone-trust—untrust-outbound-1]action permit[USG5300—policy—interzone-trust-untrust—outbound-1] quit如果是允许所有的内网地址上公网可以用以下命令:[USG2100]firewall packet-filter default permit interzone trust untrust direction outbound //必须1.4。
华为防火墙-USG--PPPoE拨号配置
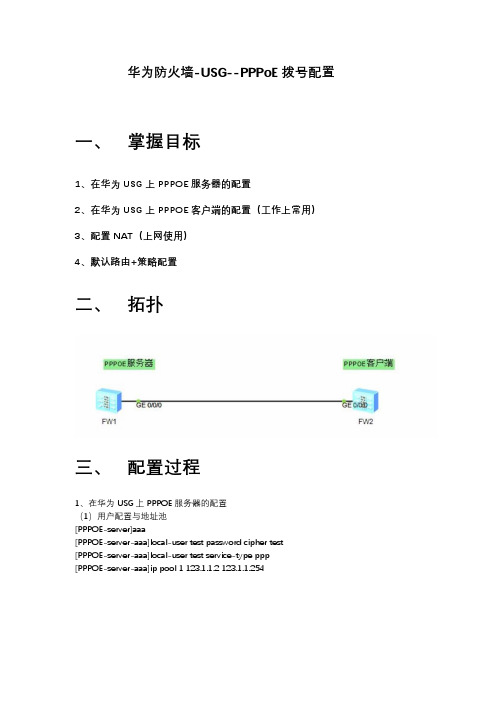
华为防火墙-USG--PPPoE拨号配置一、掌握目标1、在华为 USG 上 PPPOE 服务器的配置2、在华为 USG 上 PPPOE 客户端的配置(工作上常用)3、配置 NAT(上网使用)4、默认路由+策略配置二、拓扑三、配置过程1、在华为 USG 上 PPPOE 服务器的配置(1)用户配置与地址池[PPPOE-server]aaa[PPPOE-server-aaa]local-user test password cipher test[PPPOE-server-aaa]local-user test service-type ppp[PPPOE-server-aaa]ip pool 1 123.1.1.2 123.1.1.254(2)虚拟模板接口[PPPOE-server]interface g0/0/0[PPPOE-server-GigabitEthernet0/0/0]ip address 123.1.1.1 24[PPPOE-server]interface Virtual-Template 1[PPPOE-server-Virtual-Template1]ppp authentication-mode chap[PPPOE-server-Virtual-Template1]ip address unnumbered interface g0/0/0 [PPPOE-server-Virtual-Template1]remote address pool 1[PPPOE-server]interface g0/0/0[PPPOE-server-GigabitEthernet0/0/0]pppoe-server bind virtual-template 1说明:G0/0/0 接口已经加入对应的 Zone 了,否则需要加入后才能正常工作。
2、在华为 USG 上 PPPOE 客户端的配置(工作上常用)(1)拨号规则定义[PPPOE-Client]dialer-rule 1 ip permit(2)拨号接口配置[PPPOE-Client]interface Dialer 1[PPPOE-Client-Dialer1]dialer user test(用该帐号拨号)[PPPOE-Client-Dialer1]dialer-group 1 (对应规则1)[PPPOE-Client-Dialer1]dialer bundle 1(后续bundle调用在接口)[PPPOE-Client-Dialer1]ip address ppp-negotiate[PPPOE-Client-Dialer1]ppp chap user test[PPPOE-Client-Dialer1]ppp chap password cipher test(3)物理接口调用[PPPOE-Client]interface GigabitEthernet 0/0/0[PPPOE-Client-GigabitEthernet0/0/0]pppoe-client dial-bundle-number 1(4)注意事项有的版本需要把拨号接口加入到对应的 zone,有的版本则不需要,所以如果看到拨号一直没有成功,可以把拨号接口加入到 Zone。
华为防火墙USG配置

内网:配置GigabitEthernet 0/0/1 加入Trust 地区[USG5300] firewall zone trust[USG5300-zone-untrust] add interface GigabitEthernet 0/0/1外网:配置GigabitEthernet 0/0/2 加入Untrust 地区[USG5300] firewall zone untrust[USG5300-zone-untrust] add interface GigabitEthernet 0/0/2DMZ:[USG5300] firewall zone dmz[USG5300-zone-untrust] add interface GigabitEthernet 0/0/3[USG5300-zone-untrust] quitTrust 和Untrust 域间:同意内网用户接见公网policy 1:同意源地点为的网段的报文经过[USG5300] policy interzone trust untrust outbound[USG5300-policy-interzone -trust -untrust -outbound] policy 1[USG5300-policy-interzone -trust -untrust -outbound -1] policy source[USG5300-policy-interzone -trust -untrust -outbound -1] action permit[USG5300-policy-interzone -trust -untrust -outbound -1] quit假如是同意全部的内网地点上公网能够用以下命令:[USG2100]firewall packet -filter default permit interzone trust untrust direction outbound // 必须DMZ和Untrust 域间:从公网接见内部服务器policy 2:同意目的地点为,目的端口为21 的报文经过policy 3:同意目的地点为,目的端口为8080 的报文经过[USG5300] policy interzone untrust dmz inbound[USG5300-policy-interzone -dmz-untrust -inbound] policy 2[USG5300-policy-interzone -dmz-untrust -inbound -2] policy destination 0[USG5300-policy-interzone -dmz-untrust -inbound -2] policy service service -set ftp [USG5300-policy-interzone -dmz-untrust -inbound -2] action permit[USG5300-policy-interzone -dmz-untrust -inbound -2] quit[USG5300-policy-interzone -dmz-untrust -inbound] policy 3[USG5300-policy-interzone -dmz-untrust -inbound -3] policy destination 0[USG5300-policy-interzone -dmz-untrust -inbound -3] policy service service -set http [USG5300-policy-interzone -dmz-untrust -inbound -3] action permit[USG5300-policy-interzone -dmz-untrust -inbound -3] quit[USG5300-policy-interzone -dmz-untrust -inbound] quit配置内部服务器:<USG5300>system-view[USG5300] nat server protocol tcp global 8080 inside www[USG5300] nat server protocol tcp global ftp inside ftpNAT2、经过公网接口的方式创立Trust 地区和Untrust 地区之间的NAT 策略,确立进行NAT 变换的源地点范围网段,而且将其与外网接口GigabitEthernet 0/0/4 进行绑定。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
华为USG防火墙配置实例脚本-PPPOE
PPPOE分两部分:
PPPOE-Server(例如ADSL局端)和PPPoE Client(ADSL拨号上网。
客户端)PPPOE-Server:
G0/0接WAN、G0/1接局域网。
客户端通过PPPOE拨号拿IP上网。
公网IP 129.7.66.2/24、网关129.7.66.1,局域网拨到拿1.1.1.2/8-100的IP 典型应用:小区宽带、酒店等。
============================
firewall mode route
interface GigabitEthernet 0/0
ip address 129.7.66.2 24
ip route-static 0.0.0.0 0.0.0.0 129.7.66.1
firewall zone trust
add interface GigabitEthernet 0/1
firewall zone untrust
add interface GigabitEthernet 0/0
firewall packet-filter default permit all
#------------------------------------
interface Virtual-Template 1
ppp authentication-mode pap
ip address 1.1.1.1 255.0.0.0
remote address pool 1
firewall zone trust
add interface Virtual-Template 1
interface GigabitEthernet 0/1
pppoe-server bind Virtual-Template 1
#------------------------------------
aaa
local-user usg3000 password simple usg3000
ip pool 1 1.1.1.2 1.1.1.100
#-----------------------------------
acl 2001
rule 0 permit source 1.1.1.0 0.255.255.255
firewall interzone trust untrust
nat outbound 2001
=============================
PPPOE-Client
防火墙G0/0上接ADSL MODEM、局域网G0/1用IP192.168.1.1/24做网关。
防火墙自动拨号。
上网。
用户名1234密码123
========================================================================== firewall zone trust
add interface GigabitEthernet 0/1
firewall zone untrust
add interface GigabitEthernet 0/0
firewall packet-filter default permit all
interface GigabitEthernet 0/1
ip address 192.168.1.0 24
#-----------------------------------------
interface Dialer 1
link-protocol ppp
ppp pap local-user 123 password simple 123
ip address ppp-negotiate
dialer user usg3000
dialer bundle 1
firewall zone untrust
add interface Dialer 1
#-----------------------------------------
interface GigabitEthernet 0/0
pppoe-client dial-bundle-number 1
ip route-static 0.0.0.0 0.0.0.0 dialer1
#---------------------------------------
acl 2001
rule 0 permit source 192.168.1.0 0.0.0.255
firewall interzone trust untrust
nat outbound 2001。
