四川大学数据库系统_双语期末考题
数据库期末考试试题及答案

数据库期末考试试题及答案一、名词解释(每小题2分,共10分)1. 数据库(Database)2. 数据模型(Data Model)3. 表(Table)4. 字段(Field)5. 记录(Record)6. 主键(Primary Key)7. 外键(Foreign Key)8. 索引(Index)9. 视图(View)10. 存储过程(Stored Procedure)二、选择题(每小题2分,共20分)1. 下列哪个是关系型数据库管理系统?A. OracleB. MyBatisC. MongoDBD. Redis2. 在数据库中,哪个字段用于唯一标识一条记录?A. 字段名B. 数据类型C. 主键D. 索引3. 以下哪个不属于数据库的基本操作?A. 插入B. 删除C. 修改D. 格式化4. 下列哪个SQL语句用于创建表?A. SELECTB. INSERTC. CREATE TABLED. UPDATE5. 在SQL中,哪个关键字用于删除表?A. DROP TABLEB. DELETEC. ALTER TABLED. TRUNCATE TABLE6. 下列哪个SQL语句用于查询所有字段?A. SELECT FROM table_nameB. SELECT table_name FROMC. SELECT FROM table_nameD. SELECT table_name7. 以下哪个函数用于计算两个日期之间的差值?A. DATEDIFFB. TIMESTAMPDIFFC. DATE_ADDD. DATE_SUB8. 下列哪个SQL语句用于修改表的结构?A. MODIFY TABLEB. ALTER TABLEC. CHANGE TABLED. RENAME TABLE9. 下列哪个关键字用于创建外键约束?A. FOREIGN KEYB. CONSTRAINTC. PRIMARY KEYD. INDEX10. 以下哪个存储过程用于备份数据库?A. BACKUP DATABASEB. RESTORE DATABASEC. CREATE DATABASED. DROP DATABASE三、填空题(每小题2分,共20分)1. 在SQL中,用于插入数据的语句是______。
四川大学数据库2015年期末试卷和答案

(b)等值连接不把重复属性去掉,而自然连接要把重复属性去掉。
3、为什么将SQL 中的视图称为“虚表”?答:在SQL中创建一个视图时,系统只是将视图的定义存放在数据字典中,并不存储视图对应的数据,在用户使用视图时才去求对应的数据,因此,我们将视图称为“虚表”。
这样处理的目的是为了节约存储空间,因为视图对应的数据都可从相应的基本表中获得。
4、列出3条查询优化的启发式规则。
答:3 条启发式优化规则是:尽可能早地执行选择运算,尽可能早地执行投影运算,把笛卡尔积与附近的一连串选择和投影合并起来做。
5、试叙述“串行调度”与“可串行化调度”的区别。
答:事务的执行次序称为调度。
如果多个事务依次执行,则称为事务的串行调度。
如果利用分时的方法,同时处理多个事务,则称为事务的并发调度。
如果一个并发调度的结果与某一串行调度的执行结果等价,那么这个并发调度称为是可串行化的调度。
三、设计题(共8分)在学术论文完成过程中,一位学者可以撰写多篇论文,一篇论文也可由多位学者合著,每篇论文的作者都有一个排序。
一篇论文只能发表一次,学术刊物的某一辑(卷号、期号)发表多篇论文在。
设学者的属性有:身份证号、姓名、单位、通讯地址;论文的属性有:论文题目、主题、术语;学术刊物的属性有:ISBN号、名称、影响因子。
试完成以下两题:(1)根据这段话的意思,画出其E-R 图。
(4分)(2)将这个E-R 图转换为满足3NF的关系模式,并给出各关系模式中的主码。
(4分)(3)SELECT DISTINCT X.SnoFROM SC X, SC YWHERE X.Sno=Y.Sno AND o!=o;(4)SELECT DISTINCT SnoFROM SC XWHERE NOT EXISTS(SELECT *FROM CWHERE Teacher='张' AND NOT EXISTS(SELECT *FROM SC YWHERE Y.Sno=X.Sno AND o=o));五、查询优化(共10分)给定“学生-课程”数据库的关系模式如三大题4小题:S(Sno,Sname,Sgender,Sage)SC(Sno,Cno,Grade)C(Cno,Cname,Teacher)对查询“检索选修“信息系统”课程的学生姓名与年龄。
数据库期末考试试题及答案

数据库期末考试试题及答案一、单项选择题(每题2分,共20分)1. 数据库管理系统(DBMS)是()。
A. 一组软件B. 一个数据库C. 一组硬件D. 一个操作系统答案:A2. 在关系数据库中,关系是指()。
A. 行的集合B. 列的集合C. 行和列的有序对集合D. 行和列的无序对集合答案:C3. SQL是()。
A. 数据定义语言B. 数据控制语言C. 数据操纵语言D. 结构化查询语言答案:D4. 数据库系统的核心是()。
A. 数据模型B. 数据库管理系统C. 数据库D. 应用程序答案:C5. 数据库设计中,视图设计属于()。
A. 概念性设计B. 逻辑设计C. 物理设计D. 实体-关系模型设计答案:B6. 在关系数据库中,一个关系至少有一个候选键,一个候选键可以有()个属性。
A. 一个B. 多个C. 零个D. 任意个答案:B7. 数据库管理系统能提供数据的()。
A. 物理独立性B. 逻辑独立性C. 数据独立性D. 以上都是答案:D8. 数据库中,存储数据的基本单位是()。
A. 记录B. 字段C. 表D. 文件答案:C9. 数据库系统与文件系统相比,数据库系统能够提供()。
A. 数据共享B. 数据独立性C. 数据完整性D. 以上都是答案:D10. 在数据库中,数据的完整性约束不包括()。
A. 实体完整性B. 参照完整性C. 用户定义的完整性D. 数据冗余答案:D二、填空题(每题2分,共20分)1. 数据库系统由数据库、数据库管理系统和_________组成。
答案:数据库应用程序2. 数据库系统的核心是_________。
答案:数据库3. 数据库管理系统的主要功能包括数据定义、数据操纵、数据控制和_________。
答案:事务管理4. 在关系数据库中,关系模式的每一个分量称为_________。
答案:属性5. 数据库设计分为概念性设计、_________设计和物理设计三个阶段。
答案:逻辑6. 在数据库中,_________是指关系中的列。
四川大学数据库技术复习题三操作题

四川⼤学数据库技术复习题三操作题数据库技术试题三、操作题1. 设有关系数据库:职⼯关系EMPLOYEE (职⼯号,职⼯名,街道,城市)⼯作关系WORKS (职⼯号,公司号,⼯资)公司关系COMPANY (公司号,公司名,城市)假设职⼯可在多个公司兼职,请⽤关系代数表达式写出⾄少在公司号为‘C2’和‘C5’公司兼职的职⼯的职⼯号。
2. 设有关系数据库:职⼯关系EMPLOYEE (职⼯号,职⼯名,街道,城市)⼯作关系WORKS (职⼯号,公司号,⼯资)公司关系COMPANY (公司号,公司名,城市)试⽤SQL语句写出下列操作:将所有在“联华公司”⼯作的职⼯加薪5﹪。
3. 图书出版管理数据库中有两个基本表:图书 (书号,书名,作者编号,出版社,出版⽇期)作者 (作者编号,作者名,年龄,地址)试⽤SQL语句写出下列查询:检索年龄低于作者平均年龄的所有作者的作者名、书名和出版社。
4. 设有商店和顾客两个实体,“商店”有属性商店编号、商店名、地址、电话,“顾客”有属性顾客编号、姓名、地址、年龄、性别。
假设⼀个商店有多个顾客购物,⼀个顾客可以到多个商店购物,顾客每次去商店购物有⼀个消费⾦额和⽇期,⽽且规定每个顾客在每个商店⾥每天最多消费⼀次。
试画出ER图,并注明属性和联系类型。
5. 学校有多名学⽣,财务处每年要收⼀次学费。
为财务处收学费⼯作设计⼀个数据库,包括两个关系:学⽣ (学号,姓名,专业,⼊学⽇期)收费 (学年,学号,学费,书费,总⾦额)假设规定属性的类型:学费、书费、总⾦额为数值型数据;学号、姓名、学年、专业为字符型数据;⼊学⽇期为⽇期型数据。
列的宽度⾃定义。
试⽤SQL语句定义上述表的结构。
(定义中应包括主键⼦句和外键⼦句)6. ⽤SQL语⾔定义(1) 学⽣关系S,包括学号SNo、姓名SN、年龄SA、系别SD;(2) 课程关系C,包括课程号CNo、课程名CN、学分CC;(3) 学⽣选课关系SC,包括SNo、CNo和成绩G。
四川大学2021年数据库考试题1(含答案100分)

数据库一.单选题(共39题,58.5分)1在SQL语句中,表达式“工资BETWEEN 1200 AND 1250”的含义是•A、工资> 1200 AND 工资<1250•B、工资> 1200 OR 工资<1250•C、工资> =1200 AND 工资<=1250•D、工资> =1200 OR 工资<=1250正确答案: C答案解析:2要为当前表所有职工增加100元工资,正确的SQL命令是命令•A、CHANGE 职工SET 工资=工资+100•B、REPLACE 职工SET 工资=工资+100•C、EDIT 职工SET 工资=工资+100•D、UPDATE 职工SET 工资=工资+100正确答案: D答案解析:3如下SQL语句Select avg(工资),单位名 from 职工 where 单位号 in (select 单位号 from 单位where 单位名=”设计所”)查询结果为•A、2000.00•B、1833.33•C、2100.00•D、3000.00正确答案: B答案解析:4在浏览窗口中,不能将一条记录逻辑删除的操作是( )•A、将光标定位于该记录,按Ctrl+T键•B、将光标定位于该记录,按DELECT键•C、将光标定位于该记录,单击表菜单中的“切换删除标志”选项•D、单击该记录前的白色小方块,使其变黑。
正确答案: B答案解析:5删除表的SQL命令是•A、DROP TABLE•B、DELETE TABLE•C、ERASE TABLE•D、KILL TABLE正确答案: A答案解析:6有SQL语句:SELECT MIN(工资)FROM 职工的执行结果是•A、工资的最大值•B、工资的最小值•C、工资的平均值•D、工资的合计正确答案: B答案解析:7在SQL语句中用于限定条件的短语是•A、FOR•B、WHILE•C、WHERE•D、CONDITION正确答案: C答案解析:8Delete的作用是•A、将记录从表中彻底删除•B、只给要删除的记录做删除标志•C、不能删除记录•D、删除整个表中的记录正确答案: B答案解析:9在Foxpro6.0中,打开数据库使用的命令为( )•A、USE•B、SELECT•C、OPEN•D、CREATE正确答案: C答案解析:10要为当前表所有商品价格上调8%,正确的SQL命令是命令( )。
四川大学数据库系统原理期末考试试题

四川大学期末考试试题(闭卷)A课程名称:数据库系统原理一.选择题。
(每小题2分,共12分)1.以下不是事物性质的是()A.持久性 B.原子性 C.可串行性 D.一致性2.以下封解锁序列中,满足两段锁协议的是()A.Lock-X(U)…Lock-S(V)…Lock-S(W)…Unlock(U)…Unlock(W)…Unlock(V) B.Lock-X(U)…Unlock(U)…Lock-S(V)…Unlock(V)…Lock-S(W)…Unlock(W) C.Lock-X(U)…Lock-S(V)…Unlock(U)…Unlock(V)…Lock-S(W)…Unlock(W) D.Lock-X(U)…Unlock(U)…Lock-S(V)…Lock-S(V)…Unlock(W)…Unlock(W) 3.以下关于死锁的说法中正确的是()A.两段锁协议可避免死锁 B.DBMS一般采用超时法检查死锁C.死锁是由于持锁事务重启后造成的 D.系统中至少有两个并发事务才可能发生死锁4.当事务获得数据项Q的排他锁后,该事务()A.只能读Q B. 只能写Q C. 既能读Q,又能写QD.既不能读Q,也不能写Q5. 如果一个系统关系模式仅有两个属性,则该关系模式至少满足()A. INFB.2NFC.3NFD.BCNF6.在数据局设计中,画ER图是()的主要任务A.需求分析阶段 B.概念结构设计阶段C.逻辑结构设计阶段 D.物理结构设计阶段二.简答题。
(每小题6分,共12分)1.什么是数据库系统的三级模式结构?它是如何保证数据独立性的?2.1.以下1-2要求写出关系代数查询。
1.查询“t1003”号员工工作过的各部门部门编号和部门名;2.查询在“t1003”号员工工作过的所有部门都工作过的员工的编号及其姓名;以下3-6要求写出SQL查询:3.查询“t1003”号员工工作过的各部门部门编号和部门名;4.查询所有姓名为“王勇”的员工工作过的部门编号和部门名;5.查询在“t1003”号员工工作过的所有部门都工作过的员工的编号及其姓名;6.查询目前在职员工人数最多的部门编号。
四川大学数据库系统(双语)Database System教学大纲
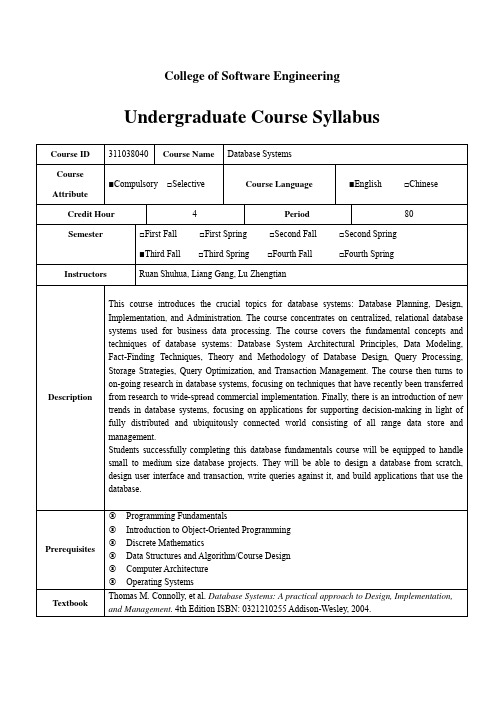
College of Software EngineeringUndergraduate Course SyllabusCourse ID 311038040Course Name Database SystemsCourseAttribute■Compulsory □Selective Course Language■English □Chinese Credit Hour 4 Period80Semester□First Fall □First Spring □Second Fall □Second Spring■Third Fall □Third Spring □Fourth Fall □Fourth Spring Instructors Ruan Shuhua, Liang Gang, Lu ZhengtianDescription This course introduces the crucial topics for database systems: Database Planning, Design, Implementation, and Administration. The course concentrates on centralized, relational database systems used for business data processing. The course covers the fundamental concepts and techniques of database systems: Database System Architectural Principles, Data Modeling, Fact-Finding Techniques, Theory and Methodology of Database Design, Query Processing, Storage Strategies, Query Optimization, and Transaction Management. The course then turns to on-going research in database systems, focusing on techniques that have recently been transferred from research to wide-spread commercial implementation. Finally, there is an introduction of new trends in database systems, focusing on applications for supporting decision-making in light of fully distributed and ubiquitously connected world consisting of all range data store and management.Students successfully completing this database fundamentals course will be equipped to handle small to medium size database projects. They will be able to design a database from scratch, design user interface and transaction, write queries against it, and build applications that use the database.Prerequisites 3Programming Fundamentals3Introduction to Object-Oriented Programming 3Discrete Mathematics3Data Structures and Algorithm/Course Design 3Computer Architecture3Operating SystemsTextbook Thomas M. Connolly, et al. Database Systems: A practical approach to Design, Implementation, and Management. 4th Edition ISBN: 0321210255 Addison-Wesley, 2004.Resource 1./~ruanshuhua/index_7.htm2./learning/sql/2008/thankyou/default.mspx3./developerworks/cn/db2/v94./database/index.html5.6.7.8./dist/jakarta/tomcat-59./downloads/packagesGrading 3Assignments and Class Participation: 10% 3Term Project: 20%3Midterm: 20%3Final Exam: 50%Topics 1Background (5 Periods )1.1Introduction to Databases (3 Periods )1.1.1History and Motivation for Information Systems1.1.2Characteristics and Limitations of File-Based Systems *1.1.3Motivation for Database Approach *1.1.4Some Common Database Applications1.1.5Meaning of the Term Database, Database Management Systems (DBMS), andDatabase Systems *1.1.6Typical Functions of a DBMS1.1.7Major Components of the DBMS Environment1.1.8History of the Development of DBMSs1.1.9Advantages and Disadvantages of DBMSs *1.1.10Phone Number Programing on any one Language and on any one DBMS (2Practice Periods) #11.2Database Environment (2 Periods )1.2.1Personnel Involved in the Database Environment *1.2.2The Concepts of Data Abstraction *1.2.3The Three-Level ANSI-SPARC Database Architecture *1.2.4Contents of External, Conceptual, and Internal Levels **1.2.5The Concepts External, Conceptual, and Internal Schemas **1.2.6Purpose of External/Conceptual and Conceptual/Internal Mappings **1.2.7Meaning of Logical and Physical Data Independence *1.2.8Database Languages DDL, DML and Distinction between Them *1.2.9 A Classification of Data Models *1.2.10Purpose/Importance of Conceptual Modeling **1.2.11Meaning of Client–Server Application Architecture and Advantages of This Typeof Architecture for a DBMS2The Relational Model and Languages (20 Periods )2.1The Relational Model (5 Periods )2.1.1Terminology of Relational Model **Topics2.1.2How Tables Are Used to Represent Data2.1.3Connection Between Mathematical Relations and Relations in the RelationalModel2.1.4Properties of Database Relations *2.1.5How to Identify Candidate, Primary, and Foreign Keys **2.1.6Meaning of Null *2.1.7Meaning of Entity Integrity and Referential Integrity **2.1.8Meaning of Enterprise Constraints *2.1.9Purpose and Advantages of Views *2.1.10Setting Integrity Constraints on any one DBMS (2 Practice Periods) #22.2Relational Algebra and Relational Calculus (5 Periods )2.2.1Meaning of the Term Relational Completeness *2.2.2How to Form Queries in Relational Algebra **2.2.3How to Form Queries in Tuple Relational Calculus **2.2.4How to Form Queries in Domain Relational Calculus **2.2.5Categories of Relational DML2.3SQL: Data Manipulation (5 Periods )2.3.1Purpose and Importance of SQL *2.3.2How to Retrieve Data From Database Using SELECT and **2.3.2.1Use Compound WHERE Conditions2.3.2.2Sort Query Results Using ORDER BY2.3.2.3Use Aggregate Functions (COUNT, SUM, AVG, MIN, MAX)2.3.2.4Group Data Using GROUP BY and HAVING2.3.2.5Use Subqueries2.3.2.6Join Tables Together2.3.2.7Perform Set Operations (UNION, INTERSECT, EXCEPT)2.3.3How to Update Database Using INSERT, UPDATE, and DELETE *2.3.4Using SQL Data Manipulation on any one DBMS (2 Practice Periods) #32.4SQL: Data Definition (5 Periods )2.4.1Data Types Supported by SQL Standard *2.4.2Purpose of Integrity Enhancement Feature of SQL **2.4.3How to Define Integrity Constraints Using SQL **2.4.3.1Required Data2.4.3.2Domain Constraints2.4.3.3Entity Integrity Constraints2.4.3.4Referential Integrity Constraints2.4.3.5Enterprise Constraints2.4.4How to Use the Integrity Enhancement Feature in the CREATE and ALTERTABLE Statements *2.4.5How to Create and Delete Views Using SQL *2.4.6How the DBMS Performs Operations on Views *2.4.7Under What Conditions Views Are Updatable **2.4.8Advantages and Disadvantages of Views2.4.9How the ISO Transaction Model Works *2.4.10How to Use the GRANT and REVOKE Statements as a Level of Security *2.4.11Using SQL Data Definition on any one DBMS (2 Practice Periods) #4Topics 3Database Analysis and Design Techniques (20 Periods )3.1Database Planning, Design, and Administration (2 Periods )3.1.1Main Components of an Information System3.1.2Main Stages of Database Application Lifecycle *3.1.3Main Phases of Database Design: Conceptual, Logical, and Physical Design **3.1.4How to Evaluate and Select a DBMS *3.1.5Distinction Between Data Administration and Database Administration *3.1.6Purpose and Tasks Associated with Data Administration and DatabaseAdministration3.2Fact-Finding Techniques (3 Periods )3.2.1Most Commonly Used Fact-Finding Techniques *3.2.2How to Use Each Fact-Finding Technique and the Advantages and Disadvantagesof Each3.2.3Significance of Applying Fact-Finding Techniques to Early Stages of DatabaseApplication Lifecycle *3.2.4How to Use Fact-Finding Techniques in the Database Application Lifecycle3.2.5Types of Facts Collected in Each Stage of Database Application Lifecycle *3.2.6Types of Documentation Produced in Each Stage of Database ApplicationLifecycle *3.2.7Introduction of DreamHome3.2.8Discussing and confirming the Database Project Requirements in the Group (2Practice Periods) #53.3Entity-Relationship Modeling (6 Periods )3.3.1How to Use Entity–Relationship (ER) Modeling in Database Design3.3.2Basic Concepts Associated with ER Model **3.3.3Structural Constraints in ER Model **3.3.4Diagrammatic Technique for Displaying ER Model Using Unified ModelingLanguage (UML) *3.3.5How to Identify and Resolve Problems with ER Models Called Connection Traps3.3.6How to Build an ER Model From a Requirements Specification **3.3.7Building an ER Model by Using Eclipse with UML (2 Practice Periods) #63.4Enhanced Entity-Relationship Modeling (4 Periods )3.4.1Limitations of Basic Concepts of the ER Model and Requirements to RepresentMore Complex Applications Using Additional Data Modeling Concepts3.4.2Most Useful Additional Data Modeling Concepts of Enhanced ER (EER) ModelCalled:3.4.2.1Specialization/Generalization **3.4.2.2Aggregation *3.4.2.3Composition *3.4.3 A Diagrammatic Technique for Displaying Specialization/Generalization,Aggregation, and Composition in an EER Diagram Using UML3.4.4Building an EER Model by Using Eclipse with UML (2 Practice Periods) #73.5Normalization (5 Periods )3.5.1Problems Associated with Redundant Data *3.5.2Identification of Various Types of Update Anomalies Such as Insertion, Deletion,and Modification Anomalies *Topics3.5.3How to Recognize Appropriateness or Quality of the Design of Relations *3.5.4Purpose of Normalization *3.5.5How to Use Functional Dependencies to Group Attributes into Relations being ina Known Normal Form **3.5.6How to Undertake Process of Normalization **3.5.7How to Identify Most Commonly Used Normal Forms, Namely 1NF, 2NF, 3NF,and Boyce–Codd Normal Form (BCNF) *3.5.8How to Identify Fourth (4NF) and Fifth (5NF) Normal Forms3.5.9An Actual Application Example for Normalization (2 Practice Periods) #84Methodology (15 Periods )4.1Conceptual Database Design (7 Periods )4.1.1Purpose of Conceptual Database Design4.1.2How to Decompose the Scope of the Design into Specific Users’ Views of theEnterprise *4.1.3How to Use ER Modeling to Build a Local Conceptual Data Model Based onInformation Given in a View of the Enterprise **4.1.4How to Validate Resultant Conceptual Model to Ensure it is a True and AccurateRepresentation of a View of the Enterprise *4.1.5How to Document Process of Conceptual Database Design *4.1.6End-Users Play an Integral Role Throughout Process of Conceptual DatabaseDesign4.1.7Building ER or EER Model for the Database Project (4 Practice Periods) #94.2Logical Database Design (5 Periods )4.2.1Purpose of Logical Database Design4.2.2How to Remove Features From a Local Conceptual Model that are notCompatible with the Relational Model *4.2.3How to Derive a Set of Relations From a Local Logical Data Model *4.2.4How to Validate These Relations Using the Technique of Normalization *4.2.5How to Validate a Logical Data Model to Ensure It Supports Required UserTransactions *4.2.6How to Merge Local Logical Data Models Based on Specific Views into a GlobalLogical Data Model of the Enterprise **4.2.7How to Ensure that the Resultant Global Model is a True and AccurateRepresentation of Enterprise *4.2.8Building Global Logical Model for the Database Project (2 Practice Periods) #104.3Physical Database Design (3 Periods )4.3.1Purpose of Physical Database Design4.3.2How to Map the Llogical Database Design to a Physical Database Design4.3.3How to Design Base Relations for Target DBMS *4.3.4How to Design Enterprise Constraints for Target DBMS *4.3.5How to Estimate the Size of the Database *4.3.6How to Select Appropriate File Organizations Based on Analysis of Transactions*4.3.7When to Use Secondary Indexes to Improve Performance *4.3.8How to Design Security Mechanisms to Satisfy User Requirements *4.3.9Building the Project Database on the Selected DBMS (2 Practice Periods) #11Topics 5Selected Database Issues (5 Periods )5.1Transaction Management (5 Periods )5.1.1Function and Importance of Transactions5.1.2Properties of Transactions **5.1.3Concurrency Control **5.1.3.1Meaning of Serializability5.1.3.2How Locking Can Ensure Serializability5.1.3.3Deadlock and How It Can Be Resolved5.1.3.4How Timestamping Can Ensure Serializability5.1.3.5Optimistic Concurrency Control5.1.3.6Granularity of Locking5.1.4Recovery Control *5.1.4.1Some Causes of Database Failure5.1.4.2Purpose of Transaction Log File5.1.4.3Purpose of Checkpointing5.1.4.4How to Recover Following Database Failure5.1.5Alternative Models for Long Duration Transactions5.1.6The Database Project Application Design, Such as Transaction Design, UserInterface Design (2 Practice Periods) #126Current Trends (5 Periods )6.1Distributed DBMSs - Concepts and Design (5 Periods )6.1.1What is a Distributed DBMS6.1.2Advantages and Disadvantages of Distributed Databases6.1.3Functions and Architecture for a DDBMS *6.1.4Distributed Database Design *6.1.5Levels of Transparency6.1.6Comparison Criteria for DDBMSs *6.1.7Building the Database System (2 Practice Periods) #137Emerging Trends (10 Periods )7.1Web Technology and DBMSs (5 Periods )7.1.1Basics of Internet, Web, HTTP, HTML, URLs7.1.2Multi-Tier Client-Server Architecture *7.1.3Advantages and Disadvantages of Web as a Database Platform *7.1.4Approaches for Integrating Databases into Web7.1.4.1Scripting Languages7.1.4.2Common Gateway Interface (CGI)7.1.4.3HTTP Cookies7.1.4.4Extending the Web Server7.1.4.5Java and JDBC, SQLJ, Servlets, and JSP7.1.4.6Microsoft Web Solution Platform: ASP and ADO7.1.5Building the Database System (2 Practice Periods) #147.2The Concepts of Data Warehousing and Data marts (5 Periods )7.2.1How Data Warehousing Evolved *7.2.2Main Concepts and Benefits Associated with Data Warehousing7.2.3How Online Transaction Processing (OLTP) Systems Differ From DataWarehousing *Topics7.2.4Problems Associated with Data Warehousing7.2.5Architecture and Main Components of a Data Warehousing *7.2.6Important Information Flows or Processes of a Data Warehouse **7.2.7Main Tools and Technologies Associated with Data Warehousing7.2.8Issues Associated with the Integration of a Data Warehousing and the Importanceof Managing Meta-Data *7.2.9Concept of a Data Mart and the Main Reasons for Implementing a Data Mart *7.2.10Advantages and Disadvantages of a Data Mart7.2.11Main Issues Associated with the Development and Management of Data Marts7.2.12Testing the Database System (2 Practice Periods) #15Notice:3* for emphases3** for emphases and difficulty3#x for the xth Practice Periods (Total 32 Practice Periods)Tools & Environment 3Microsoft Windows Server 200X3J2SDK 1.5 + Tomcat 5.0 + Eclipse 3.3 with UML 3Microsoft SQL SERVER 200XProjects A Web-Based Database SystemStudents will be able to plan, design, create, and maintain a Web-accessible database for a real estate company to keep track of their business, such as the parts, suppliers, and purchase orders, lease renewals, and so on. Included will be the tasks to write Web front-ends for users of the system, such as for the purchasing department to seek quotes, for the suppliers to place bids for work-orders, for the managers to monitor inventory, for client to maintenance personnel, for staff to manage property, and others.Phase 1 (5%)Goal: BackgroundProcedure: Students select a database project, capture necessary facts to build the required database application by using fact-finding techniques, analyse information about the part of organization to be supported by the database application, and use this information to identify users’ requirements for the new database system. Students must learn about the terminology, problems, opportunities, constraints, requirements, and priorities of the organization and the users of the new database system.Deliverables: The collection information and the report of requirements collection and analysis.Due on the fourth week in class. [Late submission policy – you lose 5% (of the maximum points) per day]Phase 2 (5%)Goal: Related Theories and TechniquesProjectsProcedure: Students discuss related theories in the new database system, select a development plaform and evaluate it, select an appropriate DBMS to support the new database application and evaluate it, and after singled out, are familiar with them as soon as possible.Deliverables: The collection information and the report of related theories and techniques.Due on the eighth week in class. [Late submission policy – you lose 5% (of the maximum points) per day]Phase 3 (5%)Goal: The Database System DesignProcedure: Students build data model by using the information in users’ requirements specification, refine conceptual data model, map it to a logical data model, select storage structures and access methods used to achieve efficient access to data on a specific DBMS.At the same time, students define the scope and boundaries of the new database system and the major user views, define the new system and database role (such as Manager or Supervisor), and give the design of user interface and application programs that use and process the database.Deliverables: The report of the database system design.Due on the twelfth week in class. [Late submission policy – you lose 5% (of the maximum points) per day]Phase 4 (5%)Goal: The Database System Implementation and EvaluationProcedure: Students implement the database system design in phase 3, build working model of a database application and evaluate if the database and application programs appear to be working according to requirements, such as to identify features of a system that work well, or are inadequate, to suggest improvements or even new features, to clarify the users’ requirements, to evaluate feasibility of a particular system design.Deliverables: The source code, the implementation state and result of the new database system, and the report of the database system implementation and evaluation.Due on the sixteenth week in class. [Late submission policy – you lose 5% (of the maximum points) per day]Version: 2008-07-15Author: Shuhua Ruan Date: 2008/ 07/ 15Auditor:Mei Hong Date: 2008/07/15Signature of leader:Date: 2008-7-30。
四川大学数据库技术复习题 一选择题

数据库技术试题一、选择题1. 单个用户使用的数据视图的描述称为A. 外模式B. 概念模式C. 内模式D. 存储模式2. 子模式DDL用来描述A. 数据库的总体逻辑结构B. 数据库的局部逻辑结构C. 数据库的物理存储结构D. 数据库的概念结构3. 在DBS中,DBMS和OS之间的关系是A. 相互调用B. DBMS调用OSC. OS调用DBMSD. 并发运行4. 当关系R和S自然联接时,能够把R和S原该舍弃的元组放到结果关系中的操作是A. 左外联接B. 右外联接C. 外部并D. 外联接5. 下列聚合函数中不忽略空值 (null) 的是A. SUM(列名)B. MAX(列名)C. COUNT( * )D. AVG(列名)6. 设关系模式R (A,B,C),F是R上成立的FD集,F = {B→C},则分解ρ = {AB,BC}相对于FA. 是无损联接,也是保持FD的分解B. 是无损联接,但不保持FD的分解C. 不是无损联接,但保持FD的分解D. 既不是无损联接,也不保持FD 的分解7. 在数据库设计中,将ER图转换成关系数据模型的过程属于A. 需求分析阶段B. 逻辑设计阶段C. 概念设计阶段D. 物理设计阶段8. SQL中,下列涉及空值的操作,不正确的是A. AGE IS NULLB. AGE IS NOT NULLC. AGE = NULLD. NOT (AGE IS NULL)9. 一个关系中的候选关键字。
A .至多一个B .可多个C .必须多个D .至少 3 个10. DBMS中实现事务持久性的子系统是A. 安全性管理子系统B. 完整性管理子系统C. 并发控制子系统D. 恢复管理子系统11. SQL的全局约束是指基于元组的检查子句和A. 非空值约束B. 域约束子句C. 断言D. 外键子句12. 分布式数据库系统中分片模式和分配模式均是A. 全局的B. 局部的C. 分布的D. 集中的13. 属性类型允许是基本数据类型、结构类型和集合类型的模型是A. 平面关系模型B. 嵌套关系模型C. 复合对象模型D. 分布式关系模型14. 用树型结构表示实体之间联系的数据模型称为A.关系模型B.运算模型C.网状模型D.层次模型15. 数据库系统的核心是A.数据库B.数据库管理系统C.数据模型D.软件工具16. 在SQL语言中,与X BETWEEN 10 AND 20等价的表达式是A.X>10 AND X<20B.X>=10 AND X<20C.X>10 AND X<=20D.X>=10 AND X<=2017. 某个E-R图中有5个实体型,2个1∶n联系和2个m∶n联系,则该E-R图转换的关系模式个数至少是A.5个B.7个C.8个D.9个18. 若关系模式R(V,F)中的每一个决定属性集都包含候选码,则R属于A.2NFB.3NFC.BCNFD.4NF19. 若事务T对数据R已加X锁,则其他事务对数据RA.可以加S锁不能加X锁B.不能加S锁可以加X锁C.可以加S锁也可以加X锁D.不能加任何锁20.在目前的并行数据库体系结构中,可扩充性最高的是A.SMB.SDC.SND.SK21.数据的正确性和相容性是指数据库的A.完整性B.安全性C.并发性D.一致性22.下列不属于事务的特性的是A.隔离性B.一致性C.完整性D.原子性23.系统在运行过程中,由于某种硬件故障,使存储在外存上的数据部分损失或全部损失,这种情况属于A.事务故障B.系统故障C.介质故障D.运行故障24.E-R图是数据库设计的常用工具之一,它适用于建立数据库的A.概念模型B.逻辑模型C.结构模型D.物理模型25.数据库逻辑结构设计的主要任务是A.建立E-R图B.把数据送入数据库C.建立数据流图和需求说明书D.将E-R图转换为某个DBMS所支持的数据模型26.下面不是SQL语言优点的是。
四川大学数据库系统期末试题2014-2015

四川大学期末考试试题(闭卷)(2014-2015学年第1学期)1. Multipl e Choices (20 marks, 2 marks for each)1)、The foll owing are functions of a DBMS except ( )A. c reating and processing formsB. creating d at abasesC. processing d at aD. a dministrating d at abases2)、In a one-to-many rel ationship, the entity that is on the one sid e of the rel ationship is call ed a ( )entity .A. p arentB. c hil dC. i nst anceD. s ubtype3)、When the values in one or more attributes being used as a foreign key must exist in another set of one or more attributes in another t abl e, we have created a ( ):A. transitive d epend ency .B. insertion anomaly.C. referential integrity constraint.D. normal form.4)) A tupl e is a ( ):A. column of a t abl e.B. two dimensional t abl e.C. row of a t abl e.D. key of a t abl e.5)、In which of the foll owing is a singl e-entity inst ance of one type rel ated to many entity inst ances of another type?()( )A. One-to-One Rel ationshipB. One-to-Many Rel ationshipC. Many-to-Many Rel ationshipD. Composite Rel ationship6)、Which of the foll owing is NOT a basic el ement of all versions of the E-R mod el?( )A. EntitiesB. AttributesC. Rel ationshipsD. Primary keys7)、The DROP T ABLE st atement:()A. d el etes the t abl e structure only.B. d el etes the t abl e structure al ong with the t abl e d at a.C. works whether or not referential integrity constraint s woul d be viol ated.D. is not an SQL st atement.8)、SQL views can be used to hid e:()A. columns and rows only.B. complicated SQL synt ax only.C. both of the above can be hid d en by an SQL view.D. None of the above is correct.9)、The first step in d at abase d evel opment is which of the foll owing?()A. Enterprise d at a mod elingB. Logical d at abase d esignC. Physical d at abase d esign and d efinitionD. Dat abase Impl ement ation10)、Which of the foll owing d at abase activities d etermines the entities, attributes, and rel ationships of d at a?()A. Conceptual d at a mod elingB. Logical d at abase d esignC. Physical d at abase d esign and d efinitionD. Dat abase impl ement ation2.Write SQL st atement s (30 marks, 6 marks for each)keys are underlined.branch (branch_name, branch_city, assets)customer (customer_name, customer_street, customer_city)loan (loan_number, branch_name, amount)borrower (customer_name, loan_numbe r)account (account_number, branch_name, balance)depositor (customer_name, account_number)From the database schema above, give an expression in SQL for each of queries 2, 3, 4 and 5.1)、Define the relation “account” in SQL.Tip: Describe primary keys, foreign keys and check constrains if necessary.2)、To find all loan number for loans made at the Perryridge branch with loan amounts greater than $1200.3)、Find all customers who have both a loan and an account4)、Find the names of all branches where the average account balance is more than $1,200.5)、Find all loan number which appear in the loan relation with null values for amount1)、What is the purpose of the index mechanism in database system? And give the definitions of primary index and secondary index.2)、Please list the five duties of a database administrator3)、Please give the definition of “trigger” in database system.4)、Explain the distinctions among the terms superkey, candidate key and primary key.4、Dat abase Design (30 marks)You are first required to create a conceptual data model of the data requirements for a company that specializes in IT training and then map the conceptual data model into a relational schema. The Company has 30 instructors and can handle up to 100 trainees per training session. The Company offers five advanced technology courses, each of which is taught by a teaching team of two or more instructors. Each instructor is assigned to a maximum of two teaching teams or may be assigned to do research. Each trainee undertakes one advanced technology course per training session.1) 、Identify the main entity types for the company.2)、Identify the main relationship types and specify the multiplicity for each relationship. State any assumptions you make about the data.3)、Using your answers for the previous two to draw a single ER model to represent the data requirements for the company.4)、Convert the E-R model into a relational schema using the mapping algorithm specified in this course. Specify key and referential integrity constraints, using directed arcs. Make sure you also identify alternate keys. Label each step of the mapping algorithm.。
数据库期末考试题及答案2024

数据库期末考试题及答案2024一、单项选择题(每题2分,共20分)1. 数据库管理系统(DBMS)的主要功能不包括以下哪项?A. 数据定义B. 数据操纵C. 数据存储D. 数据加密答案:D2. 在关系数据库中,以下哪个概念用于描述表之间的关系?A. 实体B. 属性C. 关系D. 键答案:C3. SQL语言中,用于查询数据的命令是?A. SELECTB. INSERTC. UPDATED. DELETE答案:A4. 以下哪个不是数据库设计阶段的任务?A. 需求分析B. 概念性设计C. 物理设计D. 数据备份答案:D5. 在数据库中,以下哪个术语指的是表中的一行?A. 元组B. 记录C. 字段D. 属性答案:B6. 数据库中的视图是什么?A. 存储在磁盘上的物理文件B. 虚拟表,基于一个或多个表的查询结果C. 表的物理存储位置D. 表的索引答案:B7. 以下哪个不是数据库完整性约束?A. 实体完整性B. 参照完整性C. 用户定义的完整性D. 索引完整性答案:D8. 在数据库中,主键的作用是什么?A. 唯一标识表中的每条记录B. 存储数据C. 排序数据D. 索引数据答案:A9. 数据库恢复的基础是?A. 事务日志B. 数据备份C. 索引D. 数据字典答案:A10. 以下哪个不是数据库并发控制的方法?A. 锁定B. 时间戳C. 乐观并发控制D. 批处理答案:D二、多项选择题(每题3分,共15分)1. 关系数据库管理系统中,以下哪些是基本的数据操纵语言(DML)?A. SELECTB. INSERTC. UPDATED. DELETEE. DROP答案:ABCD2. 数据库的三级模式包括以下哪些?A. 外模式B. 概念模式C. 内模式D. 实体模式E. 关系模式答案:ABC3. 在数据库设计中,以下哪些是规范化的目标?A. 减少数据冗余B. 消除更新异常C. 提高查询速度D. 增加数据存储E. 确保数据一致性答案:ABE4. 数据库索引的作用包括以下哪些?A. 提高查询速度B. 保证数据完整性C. 减少磁盘空间D. 优化数据排序E. 减少数据冗余答案:ADE5. 数据库并发控制的目的是什么?A. 防止数据丢失B. 避免数据不一致C. 提高系统性能D. 减少系统开销E. 确保事务的原子性答案:BE三、简答题(每题5分,共20分)1. 简述数据库事务的ACID属性。
四川大学数据库系统_双语期末考题

四川⼤学数据库系统_双语期末考题1.Multiple Choices (20 marks, 2 marks for each)1) In a database system, whose responsibility is it to provide data consistency?A. the database administrator'sB. the DBMS'sC. the user'sD. the application programmer's2) The term logical data independence refers to the ability to changeA. the conceptual schema without changing the external schemas, or the application programsB. the physical schema of the data without changing the external schemas, the conceptual schemas, or the application programsC. the application programs without changing the conceptual schemaD. the data without physically relocating the tables3) A database is needed for which of the following application scenarios?I. A video store that needs to keep track of data about members, about videos carried by the store, about videos rented by members, as well as data concerning borrow-date, return-date, and payment information.II. In the human resources department of a company, information about employees, their titles, their salaries and sick days, and about vacation days taken by each employee.III. A computer-simulated video game which needs to calculate and display, the physical (x, y) location of each actor in the game, the speed with which they are moving at the current instant, the direction in which they are moving, the action they are performing, the angle at which the game-player is viewing the scene.A. I and II onlyB. I onlyC. I and III onlyD. I, II, and III4) Which of the following are usually used to represents ENTITY TYPE in ER modeling.A. verbB. nounC. proposition.D. adjective5) What information is necessary when specifying the structure of a table in a relational schema?A. the name of the table, the names of the table's attributes, the data types of attributes, and the formats of attributesB. the name of the table and the names of the table's attributesC. the name of the table, the names of the table's attributes, the data types of the table's attributes, the formats of the table's attributes, and the maximum number of rows that the table can haveD. the name of the table and the amount of storage space to be allocated to the table6) Which of the following problems can be caused by data redundancy in a relational schema?I. Inefficient use of spaceII. Update anomalies and possible loss of dataIII. Inefficient use of processing timeA. I and II onlyB. II onlyC. I and III onlyD. I, II, and III7) Which of the following are properties of transactions in database systems?I. Atomicity and DurabilityII. Consistency and IsolationIII. Unique and IndependentA. I and II onlyB. I and III onlyC. II and III onlyD. I, II, and III8) Which of the following is true about transactions affecting the consistency of a database?A. A transaction always leaves the database in a consistent state.B. A transaction leaves the database in a consistent state if there is no system crash during the execution of the transaction.C. A transaction leaves the database in a consistent state if the user has not violated any integrity constraints.D. There are no guarantees that transactions will leave the database in a consistent state.9) In a two-phase locking protocol, what happens when a transaction requests a conflicting lock?A. The transaction is aborted immediately.B. The transaction immediately acquires the lock from the current lock-holder.C. The transaction proceeds without acquiring the lock.D. The transaction is blocked to acquire the lock.10) During recovery, which of the following transaction operations has both the before and after images?A. CommitB. InsertC. DeleteD. Update2. Write SQL statements (30 marks, 5 marks for each)Consider a database schema with the following relations:Student (SSN, name);Course (ID, instructorName, title, credits, classroom);Enroll (studentSSN, courseID, score);Write SQL statements in SQL2 to perform the following commands.1)Find SSNs and names of all students who are enrolled in a class taught by ‘Smith’;2)Find SSNs and names of all students who are NOT enrolled in a class taught by ‘Smith’;3)List alphabetically titles of all courses either are taught by teachers whose names begin with “Li”OR are taught in room number 4-456. Do NOT list duplicate titles;4)Find the name of the student who enrolled in the course titled “Database” and get the highest score;5)List all students’ name and their average score;6)Find SSNs and names of all students who are enrolled in at least all classes that the student ‘John’enrolled.3. Database Design (30 marks)Y ou are first required to create a conceptual data model of the data requirements for a company that specializes in IT training and then map the conceptual data model into a relational schema. The Company has 30 instructors and can handle up to 100 trainees per training session. The Company offers five advanced technology courses, each of which is taught by a teaching team of two or more instructors. Each instructor is assigned to a maximum of two teaching teams or may be assigned to do research. Each trainee undertakes one advanced technology course per training session.1) Identify the main entity types for the company.2) Identify the main relationship types and specify the multiplicity for each relationship. State any assumptions you make about the data.3) Using your answers for the previous two to draw a single ER model to represent the data requirements for the company.4) Convert the E-R model into a relational schema using the mapping algorithm specified in this course. Specify key and referential integrity constraints, using directed arcs. Make sure you also identify alternate keys. Label each step of the mapping algorithm.4. Normalization (20 marks)The following table lists dentist/patient appointment information. A patient is given an appointment at a specific date and time with a dentist located at a particular surgery. On each day of patient appointments, a dentist is allocated to a specific surgery for that day.Perform the following tasks:1) The table is susceptible to update anomalies. Provide examples of insertion, deletion, and update anomalies.2) Describe and illustrate the process of normalizing the table to BCNF. State any assumptions you make about the datashown in the table.。
SSD7试题2006-1

四川大学期末考试试题(闭卷)(2005-2006学年第2学期)课程号:课序号:课程名称:数据库系统原理(A卷)任课教师:阮树骅、张天庆适用专业年级:软件工程2004级学生人数: 400印题份数: 430 学号:姓名:1.Multiple Choices. (2poits×10)(1)The cardinality of a table i s the number of _____ in the table.A. keysB. foreign keysC. rowsD. coloums(2)Consi der the followi ng functional dependency.{A, B} -> {C}Regarding thi s dependency, whi ch of the followi ng statements i s (are) true?I. The val ues of C are uniquely determined by the values of A.II. The values of A are uni quely determined by the values of C.A. None.B. I only.C. I and II.D. II only.(3)The FD X -> Y i s a full dependency in a relation R, i f there is _____ attribute A that can be _____ X and thedependency still holds.A. at least one, added toB. at l east one, removed fromC. no, added to C. removed from(4)An excl usive l ock on a data i tem represents permi ssi on to perform whi ch of the operations, read and wri te, on thedata item?A. Both read and write.B. Wri te onl y.C. Read only.D. Nei ther read nor wri te.(5)In a two-phase locking protocol, what happens during the shri nki ng phase?A.The transaction cannot acqui re locks, but can release its l ocks.B.The transaction can acqui re locks, but cannot release its l ocks.C.The transaction can acqui re locks, and can release its l ocks.D.The transaction can acqui re locks, and can release its l ocks as l ong as the number of released locks i s greater(6)The term p hysical d ata indep endence refers to the ability to changeA.the conceptual schem a without changing the application program sB.the physical layout of the data without changing the external schem as, the conceptual schem as, or theapplication program sC.the application program s without changing the conceptual schem aD.the data without physically relocating the tables(7)What attributes does a subclass have?A.Just the attributes from the superclassB.All the attributes of its superclass, and possibly m oreC. A subset of the attributes of its superclassD.None of the attributes of its superclass(8)Hashing exhibi ts the best performance forA.equality searches involvi ng the key, provided the key i s used for hashi ngB.range queriesC.sequential scan of the enti re tableD.orderi ng query resul ts based on the key used for hashing(9)Whi ch of the followi ng can be used to measure hard disk dri ve performance?I.Seek timeII.Rotational latencyIII.Block transfer timeA.I onlyB. II onl yC. II and IIID. I, II, and III(10)In a two-phase locking protocol, what happens wh en a transaction requests a conflicting lock?A.The transaction imm ediately acquires the lock from the current lock-holder.B.The transaction proceeds without acquiring the lock.C.The transaction is blocked to acquire the lock.D.The transaction is aborted imm ediately.2.Write SQL statem ents.(5poits×6)You will be working wi th the followi ng schema:Empl oyee (SSN, name, salary, DNo)Department (DNo, DeptName, MgrSSN)Project (PNo, l ocation, ProjName)HourLog (SSN, PNo, hours)The Empl oyee relation provi des a list of employees wi th thei r SSN, name, salary, and department number (DNo). The SSN is unique for each employee. Each employee bel ongs to onl y one department. The Department relation contai ns a li st of the departments for the company. Its schema i ncludes a unique department number called DNo. It al so incl udes the name of the department (DeptName) and the social security number of the department's manager (MgrSSN). Each department has a onl y one manager. The Project relation incl udes a uni que project number (PNo), l ocation and the project name (ProjName). Anthe HourLog relati on li sts for each project the number of hours of work for each employee who i s assi gned to that project. The key of thi s relati on i s SSN and PNo. Write SQL statements in SQL2 to perform the following commands.(1)List all managers’ SSN, name and salary.(2)Find the name and the SSN of everyone who works more than 100 hours on one parti cul ar project.(3)Find the name and the SSN of everyone who works on at least two projects.(4)Find the name and the SSN of everyone who i s not working on any projects.(5)List alphabeti cally the names and SSNs of employees whose total work hours on all project are more than the averagehours.(6)Assume the relation Empl oyee and Department has been created usi ng the following statements:CREA TE TABLE Employee( SSN char (4) pri mary key,Name varchar (30),Salary fl oat,Dno char (2));CREA TE TABLE Department( DNo char(2) primary key,Deptname varchar(30),MgrSSN char(4))Write AL TER statements to speci fy the referential integrity constraints on above two relations.3.In this problem, w e shall design a database involving cities, the countries they ar e in, and "consulates." (领事馆) (15points×2)The r elevant information:●Each ci ty i s in a unique country. Data about ci ties incl ude the name of the city and its populati on. Names of ci ties areunique within countries, but two ci ties in different countries may have the same name (and possibly even the same population).●Information about a country incl udes its name and i ts head of state. You may assume no two countries have thesame name.●Information about a consulate incl udes its name, whi ch i s unique (e.g., "consulate of the Uni ted States in Toronto")and its street address (whi ch i s unique wi thin a city, but might not be unique among all consulates i n di fferent ci ties).●Cities and the country they are i n are related by a relationship In.●Consulates and the city in whi ch each i s located are related by a relationship Location.●Countries and consulates are related by a representation Represents. Each country represented by a consulate has aconsul, who i s represented only by a name. A subtle poi nt i s that occasi onally, a consulate will represent more thatone country. For example, country A may not have diplomati c relati ons wi th country B, so A will ask country C to represent A's i nterests in country B at their own consulates. In that case, the consul for country A i s actually a citizen of country C, and that person will likel y not be the same as the consul for country C at the same consulate.●While you might assume that a country would have at most one consulate in a given ci ty, whi ch i s not al ways thecase. For example, the US retains two consulates i n Jerusalem.Draw an ER schema for the database. Do not forget your reasonable assumptions.specified in this course. Specify keys and r efer ential integrity constraints, using dir ected arcs. Make sur e you also identify alternate keys. Label each step of the mapping algorithm. (15p oits)5.The following table stor es information about which member s borrow books in library. Note thata book can be lent to many m ember s at differ ent tim e. (20points)Member_Borrow_Book:Perform the following tasks.(1)List the prim ary key.(2)List all the FDs.(3)What norm al form is the relation in? Explain.(4)Apply norm alization to it increm entally, carrying the norm alization process through each of the higher norm alform s possible up to 3NF.。
数据结构2014(全英文) 四川大学期末考试试题

四川大学期末考试试题(闭卷)A (2013 ——2014 学年第 2 学期)
课程号:课序号:1 课程名称:数据结构(in English ) 任课教师:成绩:
适用专业年级:13电子商务学生人数:159印题份数:160学号:姓名:
2 题间不留空,一般应题卷分开教务处试题编号:
教务处试题编号:
四川大学期末考试试题(闭卷)B (2013 ——2014 学年第 2 学期)
课程号:402079030课序号:0,1 ,2 课程名称:数据结构任课教师:黄勇成绩:
适用专业年级:13电子商务学生人数:159印题份数:160学号:姓名:
注:1试题字迹务必清晰,书写工整。
本题 2 页,本页为第 1 页
2 题间不留空,一般应题卷分开教务处试题编号:
four railway carriages numbered {1,2,3,4 }, which
Programming Questions.(2*10=20)
Write a program that finds the height of a binary tree.
Write an algorithm to delete the i th element in the queue.
本题 2 页,本页为第 2 页
教务处试题编号:。
2022年四川大学计算机科学与技术专业《数据库原理》科目期末试卷A(有答案)

2022年四川大学计算机科学与技术专业《数据库原理》科目期末试卷A(有答案)一、填空题1、数据库系统是利用存储在外存上其他地方的______来重建被破坏的数据库。
方法主要有两种:______和______。
2、数据库管理系统的主要功能有______________、______________、数据库的运行管理以及数据库的建立和维护等4个方面。
3、主题在数据仓库中由一系列实现。
一个主题之下表的划分可按______、______数据所属时间段进行划分,主题在数据仓库中可用______方式进行存储,如果主题存储量大,为了提高处理效率可采用______方式进行存储。
4、在关系数据库的规范化理论中,在执行“分解”时,必须遵守规范化原则:保持原有的依赖关系和______。
5、数据库系统在运行过程中,可能会发生各种故障,其故障对数据库的影响总结起来有两类:______和______。
6、设某数据库中有作者表(作者号,城市)和出版商表(出版商号,城市),请补全如下查询语句,使该查询语句能查询作者和出版商所在的全部不重复的城市。
SELECT城市FROM作者表_____SELECT城市FROM出版商表;7、在RDBMS中,通过某种代价模型计算各种查询的执行代价。
在集中式数据库中,查询的执行开销主要包括______和______代价。
在多用户数据库中,还应考虑查询的内存代价开销。
8、在数据库系统封锁协议中,一级协议:“事务在修改数据A前必须先对其加X锁,直到事务结束才释放X锁”,该协议可以防止______;二级协议是在一级协议的基础上加上“事务T在读数据R之前必须先对其加S锁,读完后即可释放S锁”,该协议可以防止______;三级协议是在一级协议的基础上加上“事务T在读数据R之前必须先对其加S锁,直到事务结束后才释放S锁”,该协议可以防止______。
9、若事务T对数据对象A加了S锁,则其他事务只能对数据A再加______,不能加______,直到事务T释放A上的锁。
四川大学数据库2020年期末试卷和答案
(2020——2021学年第1学期)
课程号:304208040课序号:课程名称:数据库系统A原理任课教师:成绩:
适用专业年级:计算机应用2018级学生人数:印题份数:学号:姓名:
考生承诺
我已认真阅读并知晓《四川大学考场规则》和《四川大学本科学生考试违纪作弊处分规定(修订)》,郑重承诺:
1.项目(项目名,项目组长,指导老师,该老师指导的项目数)
假定:一个项目一位组长,一个项目只有一个指导老师。
2.职工(职工号,姓名,基本工资,工作部门)
假定:一个职工在一个部门工作。
3.R (A, B, C, D), F = {D→B , CD→A}
4.R(A,B,C), F = {C→A, AB→C}
请解答下列问题:
1.画出数据库的实体联系图(E-R图,5分);
2.将该E-R图转换为3NF的关系数据库模式(用下划线标出主码,5分);
3.基于上述的关系模式,用SQL写出如下查询:(5分)
求相关题目数量不足30的小节的节号和标题。(“相关题目”指使用了小节包含的知识点的题目)
参照第四大题的表结构,设有下面的SQL查询,请画出其关系代数表示的语法树,并用关系代数表达式的优化算法将其转化为优化的语法树。
5.找出所有其报酬高于所在项目平均报酬的员工的所在项目号、姓名和报酬;
6.查询参与了“张三”参与的所有项目,但没有参与“李四”参与的任何项目的员工的姓名。
某教材有若干知识点(点号,名称,视频链接),若干题目(题号,题干,难度,答案),若干小节(节号,标题,字数);每个题目使用一或多个知识点,一个知识点可被多个题目使用;一个知识点属于且只属于一个小节;一个小节包含一到多个知识点。今要建立该教材的数据库。(15分)
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1.Multiple Choices (20 marks, 2 marks for each)1) In a database system, whose responsibility is it to provide data consistency?A. the database administrator'sB. the DBMS'sC. the user'sD. the application programmer's2) The term logical data independence refers to the ability to changeA. the conceptual schema without changing the external schemas, or the application programsB. the physical schema of the data without changing the external schemas, the conceptual schemas, or the application programsC. the application programs without changing the conceptual schemaD. the data without physically relocating the tables3) A database is needed for which of the following application scenarios?I. A video store that needs to keep track of data about members, about videos carried by the store, about videos rented by members, as well as data concerning borrow-date, return-date, and payment information.II. In the human resources department of a company, information about employees, their titles, their salaries and sick days, and about vacation days taken by each employee.III. A computer-simulated video game which needs to calculate and display, the physical (x, y) location of each actor in the game, the speed with which they are moving at the current instant, the direction in which they are moving, the action they are performing, the angle at which the game-player is viewing the scene.A. I and II onlyB. I onlyC. I and III onlyD. I, II, and III4) Which of the following are usually used to represents ENTITY TYPE in ER modeling.A. verbB. nounC. proposition.D. adjective5) What information is necessary when specifying the structure of a table in a relational schema?A. the name of the table, the names of the table's attributes, the data types of attributes, and the formats of attributesB. the name of the table and the names of the table's attributesC. the name of the table, the names of the table's attributes, the data types of the table's attributes, the formats of the table's attributes, and the maximum number of rows that the table can haveD. the name of the table and the amount of storage space to be allocated to the table6) Which of the following problems can be caused by data redundancy in a relational schema?I. Inefficient use of spaceII. Update anomalies and possible loss of dataIII. Inefficient use of processing timeA. I and II onlyB. II onlyC. I and III onlyD. I, II, and III7) Which of the following are properties of transactions in database systems?I. Atomicity and DurabilityII. Consistency and IsolationIII. Unique and IndependentA. I and II onlyB. I and III onlyC. II and III onlyD. I, II, and III8) Which of the following is true about transactions affecting the consistency of a database?A. A transaction always leaves the database in a consistent state.B. A transaction leaves the database in a consistent state if there is no system crash during the execution of the transaction.C. A transaction leaves the database in a consistent state if the user has not violated any integrity constraints.D. There are no guarantees that transactions will leave the database in a consistent state.9) In a two-phase locking protocol, what happens when a transaction requests a conflicting lock?A. The transaction is aborted immediately.B. The transaction immediately acquires the lock from the current lock-holder.C. The transaction proceeds without acquiring the lock.D. The transaction is blocked to acquire the lock.10) During recovery, which of the following transaction operations has both the before and after images?A. CommitB. InsertC. DeleteD. Update2. Write SQL statements (30 marks, 5 marks for each)Consider a database schema with the following relations:Student (SSN, name);Course (ID, instructorName, title, credits, classroom);Enroll (studentSSN, courseID, score);Write SQL statements in SQL2 to perform the following commands.1)Find SSNs and names of all students who are enrolled in a class taught by ‘Smith’;2)Find SSNs and names of all students who are NOT enrolled in a class taught by ‘Smith’;3)List alphabetically titles of all courses either are taught by teachers whose names begin with “Li”OR are taught in room number 4-456. Do NOT list duplicate titles;4)Find the name of the student who enrolled in the course titled “Database” and get the highest score;5)List all students’ name and their average score;6)Find SSNs and names of all students who are enrolled in at least all classes that the student ‘John’enrolled.3. Database Design (30 marks)Y ou are first required to create a conceptual data model of the data requirements for a company that specializes in IT training and then map the conceptual data model into a relational schema. The Company has 30 instructors and can handle up to 100 trainees per training session. The Company offers five advanced technology courses, each of which is taught by a teaching team of two or more instructors. Each instructor is assigned to a maximum of two teaching teams or may be assigned to do research. Each trainee undertakes one advanced technology course per training session.1) Identify the main entity types for the company.2) Identify the main relationship types and specify the multiplicity for each relationship. State any assumptions you make about the data.3) Using your answers for the previous two to draw a single ER model to represent the data requirements for the company.4) Convert the E-R model into a relational schema using the mapping algorithm specified in this course. Specify key and referential integrity constraints, using directed arcs. Make sure you also identify alternate keys. Label each step of the mapping algorithm.4. Normalization (20 marks)The following table lists dentist/patient appointment information. A patient is given an appointment at a specific date and time with a dentist located at a particular surgery. On each day of patient appointments, a dentist is allocated to a specific surgery for that day.Perform the following tasks:1) The table is susceptible to update anomalies. Provide examples of insertion, deletion, and update anomalies.2) Describe and illustrate the process of normalizing the table to BCNF. State any assumptions you make about the data shown in the table.。
