数据库系统概念(database system concepts)英文第六版 课后练习题 答案 第8章
数据库系统概念原书第六版第八章

8.5.1 BCNF分解
Database System Concepts - 5th Edition, July 28, 2005.
7.2
©Silberschatz, Korth and Sudarshan
Database System Concepts - 5th Edition, July 28, 2005.
/*删NF· 算法通过为正则覆盖中的每个依赖显式地构造一个模式确保依赖的保持。 该算法通过保证至少有一个模式包含被分解模式的候选码,确保该分解是一个 无损分解。
Database System Concepts - 5th Edition, July 28, 2005.
7.9
©Silberschatz, Korth and Sudarshan
8.6.3
4NF 分解算法
Database System Concepts - 5th Edition, July 28, 2005.
7.10
©Silberschatz, Korth and Sudarshan
第八章 关系数据库设计
8.5 分解算法4
8.6 使用多值依赖的分解
8.7 更多的范式
8.8 数据库设计过程 8.9 时态数据建模
Database System Concepts - 5th Edition, July 28, 2005.
7.1
©Silberschatz, Korth and Sudarshan
7.3
©Silberschatz, Korth and Sudarshan
Database System Concepts - 5th Edition, July 28, 2005.
数据库系统概念(database system concepts)英文第六版 课后练习题 答案 第7章
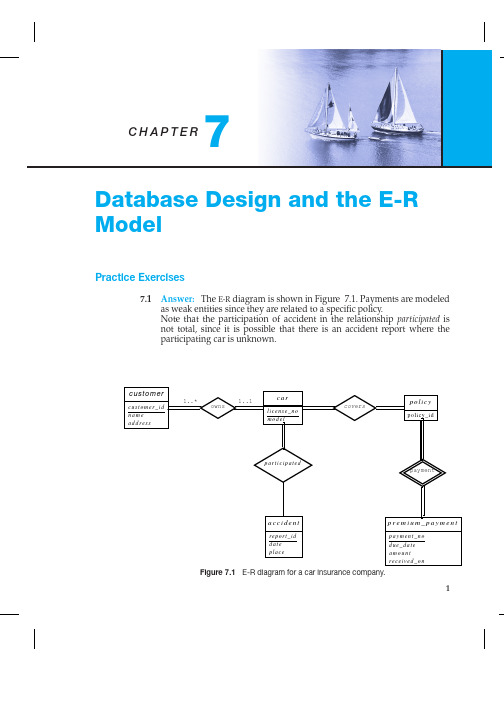
7.2 Answer: Note: the name of the relationship "course offering" needs to be changed to "section".
a. The E-R diagram is shown in Figure 7.2. Note that an alterantive is to model examinations as weak entities related to a section, rather than as a strong entity. The marks relationship would then be a binary relationship between student and exam, without directly involving section.
7.7 Answer: The primary key of a weak entity set can be inferred from its relationship with the strong entity set. If we add primary key attributes to the weak entity set, they will be present in both the entity set and the relationship set and they have to be the same. Hence there will be redundancy.
b. As indicated in the answer to the previous part, a path in the graph between a pair of entity sets indicates a (possibly indirect) relationship between the two entity sets. If there is a cycle in the graph then every pair of entity sets on the cycle are related to each other in at least two distinct ways. If the E-R diagram is acyclic then there is a unique path between every pair of entity sets and, thus, a unique relationship between every pair of entity sets.
数据库系统概念(database system concepts)英文第六版 PPT 第11章

11.8
©Silberschatz, Korth and Sudarshan
Sparse Index Files (Cont.)
Compared to dense indices:
Less space and less maintenance overhead for insertions and deletions. Generally slower than dense index for locating records.
Database System Concepts - 6th Edition
11.3
©Silberschatz, Korth and Sudarshan
Index Evaluation Metrics
Access types supported efficiently. E.g.,
records with a specified value in the attribute or records with an attribute value falling in a specified range of values.
actual records with that particular search-key value.
Secondary indices have to be dense
Database System Concepts - 6th Edition 11.10 ©Silberschatz, Korth and Sudarshan
value in the file.
E.g. index on ID attribute of instructor relation
数据库系统概念(database system concepts)英文第六版 课后练习题 答案 第11章

2Chapter11Indexing and Hashingb.c.11.4Answer:•With structure11.3.a:Insert9:10:InsertExercises3Delete23:Delete19:•With structure11.3.b:Insert9:Insert4Chapter 11Indexing and HashingDelete23:Delete 19:•With structure 11.3.c:Insert9:Insert10:Insert8:Delete 23:Delete 19:Exercises511.5Answer:If there are K search-key values and m −1siblings are involvedin the redistribution,the expected height of the tree is:log ⌊(m −1)n /m ⌋(K )11.6Answer:Extendable hash structure000 001010 011 100101 110 11111.7Answer:a.Delete 11:From the answer to Exercise 11.6,change the third bucketto:At this stage,it is possible to coalesce the second and third buckets.Then it is enough if the bucket address table has just four entriesinstead of eight.For the purpose of this answer,we do not do the coalescing.b.Delete 31:From the answer to 11.6,change the last bucket to:6Chapter11Indexing and Hashingc.Insert1:From the answer to11.6,change thefirst bucket to:d.Insert15:From the answer to11.6,change the last bucket to:11.8Answer:The pseudocode is shown in Figure11.1.11.9Answer:Let i denote the number of bits of the hash value used in thehash table.Let bsize denote the maximum capacity of each bucket.Thepseudocode is shown in Figure11.2.Note that we can only merge two buckets at a time.The common hashprefix of the resultant bucket will have length one less than the two bucketsmerged.Hence we look at the buddy bucket of bucket j differing from itonly at the last bit.If the common hash prefix of this bucket is not i j,thenthis implies that the buddy bucket has been further split and merge is notpossible.When merge is successful,further merging may be possible,which is handled by a recursive call to coalesce at the end of the function.11.10Answer:If the hash table is currently using i bits of the hash value,thenmaintain a count of buckets for which the length of common hash prefixis exactly i.Consider a bucket j with length of common hash prefix i j.If the bucketis being split,and i j is equal to i,then reset the count to1.If the bucketis being split and i j is one less that i,then increase the count by1.It thebucket if being coalesced,and i j is equal to i then decrease the count by1.If the count becomes0,then the bucket address table can be reduced insize at that point.However,note that if the bucket address table is not reduced at that point,then the count has no significance afterwards.If we want to postpone thereduction,we have to keep an array of counts,i.e.a count for each value ofExercises7 functionfindIterator(value V){/*Returns an iterator for the search on the value V*/Iterator iter();Set iter.v alue=V;Set C=root nodewhile(C is not a leaf node)beginLet i=samllest number such that V<=C.K iif there is no such number i then beginLet P m=last non-null pointer in the nodeSet C=C.P m;endelse Set C=C.P i;end/*C is a leaf node*/Let i be the least value such that K i=Vif there is such a value i then beginSet iter.index=i;Set iter.page=C;Set iter.acti v e=T RUE;endelse if(V is the greater than the largest value in the leaf)then beginif(C.P n.K1=V)then beginSet iter.page=C.P n;Set iter.index=1;Set iter.acti v e=T RUE;endelse Set iter.acti v e=F AL SE;endelse Set iter.acti v e=F AL SE;return(iter)}Class Iterator{variables:value V/*The value on which the index is searched*/boolean active/*Stores the current state of the iterator(TRUE or FALSE)*/int index/*Index of the next matching entry(if active is TRUE)*/PageID page/*Page Number of the next matching entry(if active is TRUE)*/ function next(){if(active)then beginSet ret Page=page;Set retI ndex=index;if(index+1=page.size)then beginpage=page.P nindex=0endelse index=index+1;if(page.K index=V)then acti v e=F AL SE;return(ret Page,retI ndex)endelse return null;}}Figure11.1Pseudocode forfindIterator and the Iterator class8Chapter11Indexing and Hashingdelete(value K l)beginj=first i high-order bits of h(K l);delete value K l from bucket j;coalesce(bucket j);endcoalesce(bucket j)begini j=bits used in bucket j;k=any bucket withfirst(i j−1)bits same as thatof bucket j while the bit i j is reversed;i k=bits used in bucket k;if(i j=i k)return;/*buckets cannot be merged*/if(entries in j+entries in k>bsize)return;/*buckets cannot be merged*/move entries of bucket k into bucket j;decrease the value of i j by1;make all the bucket-address-table entries,which pointed to bucket k,point to j;coalesce(bucket j);endFigure11.2Pseudocode for deletioncommon hash prefix.The array has to be updated in a similar fashion.Thebucket address table can be reduced if the i th entry of the array is0,wherei is the number of bits the table is using.Since bucket table reduction isan expensive operation,it is not always advisable to reduce the table.Itshould be reduced only when sufficient number of entries at the end ofcount array become0.11.11Answer:We reproduce the instructor relation below.Exercises9 ID dept salary10101Comp.Sci.Wu9000015151MusicEinstein9500032343HistoryGold8700045565Comp.Sci.Califieri6200076543FinanceCrick7200083821Comp.Sci.Kim80000a.Bitmap for salary,with S1,S2,S3and S4representing the given inter-vals in the same orderS1000000000000S3010*********b.The question is a bit trivial if there is no bitmap on the deptname attribute is:Comp.Sci010********* Music000101000000 History000000000100 Elec.Eng.010********* Finance010*********10Chapter11Indexing and HashingScan on these records with salary80000or more gives Wu and Singhas the instructors who satisfy the given query.11.12Answer:If the index entries are inserted in ascending order,the newentries get directed to the last leaf node.When this leaf node getsfilled,it is split into two.Of the two nodes generated by the split,the left nodeis left untouched and the insertions takes place on the right node.Thismakes the occupancy of the leaf nodes to about50percent,except the lastleaf.If keys that are inserted are sorted in descending order,the above situationwould still occur,but symmetrically,with the right node of a split nevergetting touched again,and occupancy would again be50percent for allnodes other than thefirst leaf.11.13Answer:a.The cost to locate the page number of the required leaf page foran insertion is negligible since the non-leaf nodes are in memory.On the leaf level it takes one random disk access to read and onerandom disk access to update it along with the cost to write onepage.Insertions which lead to splitting of leaf nodes require anadditional page write.Hence to build a B+-tree with n r entries ittakes a maximum of2∗n r random disk accesses and n r+2∗(n r/f)page writes.The second part of the cost comes from the fact that inthe worst case each leaf is halffilled,so the number of splits thatoccur is twice n r/f.The above formula ignores the cost of writing non-leaf nodes,sincewe assume they are in memory,but in reality they would also bewritten eventually.This cost is closely approximated by2∗(n r/f)/f,which is the number of internal nodes just above the leaf;we canadd further terms to account for higher levels of nodes,but these aremuch smaller than the number of leaves and can be ignored.b.Substituting the values in the above formula and neglecting the costfor page writes,it takes about10,000,000∗20milliseconds,or56hours,since each insertion costs20milliseconds.Exercises11c.function insert leaf(value K,pointer P)if(tree is empty)create an empty leaf node L,which is also the rootelse Find the last leaf node in the leaf nodes chain Lif(L has less than n−1key values)then insert(K,P)at thefirst available location in Lelse beginCreate leaf node L1Set L.P n=L1;Set K1=last value from page Linsert parent(1,L,K1,L1)insert(K,P)at thefirst location in L1endfunction insert parent(level l,pointer P,value K,pointer P1)if(level l is empty)then beginCreate an empty non-leaf node N,which is also the rootinsert(P,K,P1)at the starting of the node Nreturnelse beginFind the right most node N at level lif(N has less than n pointers)then insert(K,P1)at thefirst available location in Nelse beginCreate a new non-leaf page N1insert(P1)at the starting of the node Ninsert parent(l+1,pointer N,value K,pointer N1)endendThe insert leaf function is called for each of the value,pointerpairs in ascending order.Similar function can also be build for de-scending order.The search for the last leaf or non-leaf node at anylevel can be avoided by storing the current last page details in anarray.The last node in each level might be less than halffilled.To makethis index structure meet the requirements of a B+-tree,we can re-distribute the keys of the last two pages at each level.Since the lastbut one node is always full,redistribution makes sure that both ofthen are at least halffilled.11.14Answer:In a B+-tree index orfile organization,leaf nodes that areadjacent to each other in the tree may be located at different places ondisk.When afile organization is newly created on a set of records,it ispossible to allocate blocks that are mostly contiguous on disk to leafsnodes that are contiguous in the tree.As insertions and deletions occur12Chapter11Indexing and Hashingon the tree,sequentiality is increasingly lost,and sequential access has towait for disk seeks increasingly often.a.One way to solve this problem is to rebuild the index to restoresequentiality.b.i.In the worst case each n-block unit and each node of the B+-treeis halffilled.This gives the worst case occupancy as25percent.ii.No.While splitting the n-block unit thefirst n/2leaf pages areplaced in one n-block unit,and the remaining in the second n-block unit.That is,every n-block split maintains the order.Hence,the nodes in the n-block units are consecutive.iii.In the regular B+-tree construction,the leaf pages might not besequential and hence in the worst case,it takes one seek per leafing the block at a time method,for each n-node block,we will have at least n/2leaf nodes in it.Each n-node block canbe read using one seek.Hence the worst case seeks comes downby a factor of n/2.iv.Allowing redistribution among the nodes of the same block,doesnot require additional seeks,where as,in regular B+-tree werequire as many seeks as the number of leaf pages involvedin the redistribution.This makes redistribution for leaf blocksefficient with this scheme.Also the worst case occupancy comesback to nearly50percent.(Splitting of leaf nodes is preferredwhen the participating leaf nodes are nearly full.Hence nearly50percent instead of exact50percent)。
数据库系统概念(英文精编版.第六版)

Atomicity of updates
Failures
may lead to inconsistencies (1) account_A = account_A – 100 (2) account_B = account_B + 100
Example:
Concurrent access by multiple users
Exercises
Computer users interacts with data in the _______ level A. physical B. logical C. view D. all of the above Application users interact with data in the _______ level. A. physical B. logical C. view D. all of the above How the data are actually stored is called _______ A. Physical level B. Logical level C. View level D. Conceptual level
property is called ( )
A. Data inconsistency C. Data isolation B. Data redundancy D. Data integrity
1.3 View of Data
Hierarchy of Abstraction Levels
Three Abstraction Levels of Data
机械工业出版社
本课程学习内容
关系数据模型 关系数据库语言
数据库系统概念(database system concepts)英文第六版 第一章

Databa se Sy stem Concept s - 6th Edition
1 .3
©Silber schatz , Korth and S u dar
n Relational model (Chapter 2) n Example of tabular data in the relational model Columns
_____ Rows
Databa se Sy stem Concept s - 6th Edition
1 .10
©Silber schatz , Korth and S u dar
n Physical Data Independence – the ability to modify the physical schema without changing the logical schema l Applications depend on the logical schema l In general, the interfaces between the various levels and components should be well defined so that changes in some parts do not seriously influence others.
1 .5
©Silber schatz , Korth and S u dar
n Phys ical level : describes how a record (e.g., customer) is stored. n Logical level : describes data stored in database, and the relationships among the data. type instructor = record ID : string;
数据库系统概念(database system concepts)英文第六版 课后练习题 答案 第25章

C H A P T E R25Advanced Data Types and New ApplicationsPractice Exercises25.1What are the two types of time,and how are they different?Why doesit make sense to have both types of time associated with a tuple?Answer:A temporal database models the changing states of someaspects of the real world.The time intervals related to the data storedin a temporal database may be of two types-valid time and transactiontime.The valid time for a fact is the set of intervals during which the factis true in the real world.The transaction time for a data object is the set oftime intervals during which this object is part of the physical database.Only the transaction time is system dependent and is generated by thedatabase system.Suppose we consider our sample bank database to be bitemporal.Only the concept of valid time allows the system to answer queries suchas-“What was Smith’s balance two days ago?”.On the other hand,queries such as-“What did we record as Smith’s balance two daysago?”can be answered based on the transaction time.The differencebetween the two times is important.For example,suppose,three daysago the teller made a mistake in entering Smith’s balance and correctedthe error only yesterday.This error means that there is a differencebetween the results of the two queries(if both of them are executedtoday).25.2Suppose you have a relation containing the x,y coordinates and namesof restaurants.Suppose also that the only queries that will be askedare of the following form:The query specifies a point,and asks if thereis a restaurant exactly at that point.Which type of index would bepreferable,R-tree or B-tree?Why?Answer:The given query is not a range query,since it requires onlysearching for a point.This query can be efficiently answered by a B-treeindex on the pair of attributes(x,y).12Chapter25Advanced Data Types and New Applications25.3Suppose you have a spatial database that supports region queries(withcircular regions)but not nearest-neighbor queries.Describe an algo-rithm tofind the nearest neighbor by making use of multiple regionqueries.Answer:Suppose that we want to search for the nearest neighbor of apoint P in a database of points in the plane.The idea is to issue multipleregion queries centered at P.Each region query covers a larger area ofpoints than the previous query.The procedure stops when the result ofa region query is non-empty.The distance from P to each point withinthis region is calculated and the set of points at the smallest distance isreported.25.4Suppose you want to store line segments in an R-tree.If a line segment isnot parallel to the axes,the bounding box for it can be large,containinga large empty area.•Describe the effect on performance of having large bounding boxes on queries that ask for line segments intersecting a given region.•Briefly describe a technique to improve performance for such queries and give an example of its benefit.Hint:You can divide segmentsinto smaller pieces.Answer:Large bounding boxes tend to overlap even where the regionof overlap does not contain any information.The followingfigure:Rshows a region R within which we have to locate a segment.Notethat even though none of the four segments lies in R,due to the largebounding boxes,we have to check each of the four bounding boxes toconfirm this.A significant improvement is observed in the follwoingfigure:Practice Exercises3Rwhere each segment is split into multiple pieces,each with its own bounding box.In the second case,the box R is not part of the boxes indexed by the R-tree.In general,dividing a segment into smaller pieces causes the bounding boxes to be smaller and less wasteful of area. 25.5Give a recursive procedure to efficiently compute the spatial join of tworelations with R-tree indices.(Hint:Use bounding boxes to check if leaf entries under a pair of internal nodes may intersect.)Answer:Following is a recursive procedure for computing spatial join of two R-trees.SpJoin(node n1,node n2)beginif(the bounding boxes of n1and n2do not intersect)return;if(both n1and n2are leaves)output all pairs of entries(e1,e2)such thate1∈n1and e2∈n2,and e1and e2overlap;if(n1is not a leaf)NS1=set of children of n1;elseNS1={n1};if(n1is not a leaf)NS1=set of children of n1;elseNS1={n1};for each ns1in NS1and ns2in NS2;SpJoin(ns1,ns2);end25.6Describe how the ideas behind the RAID organization(Section10.3)canbe used in a broadcast-data environment,where there may occasionally be noise that prevents reception of part of the data being transmitted.4Chapter25Advanced Data Types and New ApplicationsAnswer:The concepts of RAID can be used to improve reliability ofthe broadcast of data over wireless systems.Each block of data that isto be broadcast is split into units of equal size.A checksum value iscalculated for each unit and appended to the unit.Now,parity data forthese units is calculated.A checksum for the parity data is appendedto it to form a parity unit.Both the data units and the parity unit arethen broadcast one after the other as a single transmission.On reception of the broadcast,the receiver uses the checksums to verify whether each unit is received without error.If one unit is foundto be in error,it can be reconstructed from the other units.The size of a unit must be chosen carefully.Small units not only requiremore checksums to be computed,but the chance that a burst of noisecorrupts more than one unit is also higher.The problem with usinglarge units is that the probability of noise affecting a unit increases;thus there is a tradeoff to be made.25.7Define a model of repeatedly broadcast data in which the broadcastmedium is modeled as a virtual disk.Describe how access time anddata-transfer rate for this virtual disk differ from the correspondingvalues for a typical hard disk.Answer:We can distinguish two models of broadcast data.In the caseof a pure broadcast medium,where the receiver cannot communicatewith the broadcaster,the broadcaster transmits data with periodic cy-cles of retransmission of the entire data,so that new receivers can catchup with all the broadcast information.Thus,the data is broadcast in acontinuous cycle.This period of the cycle can be considered akin to theworst case rotational latency in a disk drive.There is no concept of seektime here.The value for the cycle latency depends on the application,but is likely to be at least of the order of seconds,which is much higherthan the latency in a disk drive.In an alternative model,the receiver can send requests back to the broadcaster.In this model,we can also add an equivalent of disk accesslatency,between the receiver sending a request,and the broadcasterreceiving the request and responding to it.The latency is a function ofthe volume of requests and the bandwidth of the broadcast medium.Further,queries may get satisfied without even sending a request,sincethe broadcaster happened to send the data either in a cycle or basedon some other receivers request.Regardless,latency is likely to be atleast of the order of seconds,again much higher than the correspondingvalues for a hard disk.A typical hard disk can transfer data at the rate of1to5megabytes persecond.In contrast,the bandwidth of a broadcast channel is typicallyonly a few kilobytes per second.Total latency is likely to be of the orderof seconds to hundreds or even thousands of seconds,compared to afew milliseconds for a hard disk.25.8Consider a database of documents in which all documents are keptin a central database.Copies of some documents are kept on mobilePractice Exercises5 computers.Suppose that mobile computer A updates a copy of docu-ment1while it is disconnected,and,at the same time,mobile computer B updates a copy of document2while it is disconnected.Show how the version-vector scheme can ensure proper updating of the central database and mobile computers when a mobile computer reconnects. Answer:Let C be the computer onto which the central database is loaded.Each mobile computer(host)i stores,with its copy of each document d,a version-vector–that is a set of version numbers V d,i,j, with one entry for each other host j that stores a copy of the document d,which it could possibly update.Host A updates document1while it is disconnected from C.Thus, according to the version vector scheme,the version number V1,A,A is incremented by one.Now,suppose host A re-connects to C.This pair exchanges version-vectors andfinds that the version number V1,A,A is greater than V1,C,A by1,(assuming that the copy of document1stored host A was updated most recently only by host A).Following the version-vector scheme, the version of document1at C is updated and the change is reflected by an increment in the version number V1,C,A.Note that these are the only changes made by either host.Similarly,when host B connects to host C,they exchange version-vectors,and host Bfinds that V1,B,A is one less than V1,C,A.Thus,the version number V1,B,A is incremented by one,and the copy of docu-ment1at host B is updated.Thus,we see that the version-vector scheme ensures proper updating of the central database for the case just considered.This argument can be very easily generalized for the case where multiple off-line updates are made to copies of document1at host A as well as host B and host C.The argument for off-line updates to document2is similar.。
数据库系统概念(英文精编版.第六版)ch7 E-R Model

Example: instructor = (ID, name, street, city, salary ) course= (course_id, title, credits)
Domain – the set of permitted values for each attribute Attribute types:
Mapping Cardinality(映射基数)
Express the number of entities to which another entity can
be associated via a relationship set.
Most useful in describing binary relationship sets. For a binary relationship set R between entity sets A and
Entity-Relationship Model
The E-R model is a widely used data model for database
design.
It provides a convenient graphical representation to view
data, relationships and constraints.
Simple and composite attributes.
Single-valued and multi-valued attributes
Example: multivalued attribute: phone_numbers Can be computed from other attributes Example: age, given date_of_birth
数据库系统概念(database system concepts)英文第六版 课后练习题 答案 第26章

©Silberschatz, Korth and Sudarshan See for conditions on re-use
With the growth of networks, and the existence of multiple autonomous
database systems, workflows provide a convenient way of carrying out tasks that involve multiple systems.
Provide infrastructure for building and administering complex transaction
processing systems with a large number of clients and multiple servers.
Provide services such as:
Some commercial TP monitors: CICS from IBM, Pathway from Tandem,
Top End from NCR, and Encina from Transarc
Database System Concepts - 6th Edition
26.3
©Silberschatz, Korth and Sudarshan
TP Monitor Architectures
Database System Concepts - 6th Edition
26.4
©Silberschatz, Korth and Sudarshan
数据库系统概念(database system concepts)英文第六版 PPT 第15章

requesting and releasing locks. Locking protocols restrict the set of possible schedules.
Database System Concepts - 6th Edition
15.5
©Silberschatz, Korth and Sudarshan
The Two-Phase Locking Protocol (Cont.)
There can be conflict serializable schedules that cannot be obtained if
two-phase locking is used.
However, in the absence of extra information (e.g., ordering of access
to data), two-phase locking is needed for conflict serializability in the following sense: Given a transaction Ti that does not follow two-phase locking, we can find a transaction Tj that uses two-phase locking, and a schedule for Ti and Tj that is not conflict serializable.
©Silberschatz, Korth and Sudarshan
Lock-Based Protocols (Cont.)
Lock-compatibility matrix
数据库系统概念(database system concepts)英文第六版 PPT 第六章

Database System Concepts - 6th Edition
6.8
©Silberschatz, Korth and Sudarshan
Union Operation
Notation: r s Defined as:
r s = {t | t r or t s}
©Silberschatz, Korth and Sudarshan
Cartesian-Product Operation – Example
Relations r, s:
r x s:
Database System Concepts - 6th Edition
6.12
©Silberschatz, Korth and Sudarshan
Project Operation
Notation:
A , A , , A 1 2 k
(r )
where A1, A2 are attribute names and r is a relation name.
The result is defined as the relation of k columns obtained by erasing
For r s to be valid.
1. r, s must have the same arity (same number of attributes) 2. The attribute domains must be compatible (example: 2nd column of r deals with the same type of values as does the 2nd column of s)
数据库系统概念(databasesystemconcepts)英文第六版课后练习题答案第8章

C H A P T E R8Relational Database DesignExercises8.1Suppose that we decompose the schema R=(A,B,C,D,E)into(A,B,C)(A,D,E).Show that this decomposition is a lossless-join decomposition if thefollowing set F of functional dependencies holds:A→BCCD→EB→DE→AAnswer:A decomposition{R1,R2}is a lossless-join decomposition ifR1∩R2→R1or R1∩R2→R2.Let R1=(A,B,C),R2=(A,D,E),and R1∩R2= A.Since A is a candidate key(see PracticeExercise8.6),Therefore R1∩R2→R1.8.2List all functional dependencies satis?ed by the relation of Figure8.17.Answer:The nontrivial functional dependencies are:A→B andC→B,and a dependency they logically imply:AC→ B.There are19trivial functional dependencies of the form?→?,where???.Cdoes not functionally determine A because the?rst and third tuples havethe same C but different A values.The same tuples also show B does notfunctionally determine A.Likewise,A does not functionally determineC because the?rst two tuples have the same A value and different Cvalues.The same tuples also show B does not functionally determine C.8.3Explain how functional dependencies can be used to indicate the fol-lowing:910Chapter8Relational Database DesignA one-to-one relationship set exists between entity sets student andinstructor.A many-to-one relationship set exists between entity sets studentand instructor.Answer:Let Pk(r)denote the primary key attribute of relation r.The functional dependencies Pk(student)→Pk(instructor)andPk(instructor)→Pk(student)indicate a one-to-one relationshipbecause any two tuples with the same value for student must havethe same value for instructor,and any two tuples agreeing oninstructor must have the same value for student.The functional dependency Pk(student)→Pk(instructor)indicates amany-to-one relationship since any student value which is repeatedwill have the same instructor value,but many student values mayhave the same instructor value.8.4Use Armstrong’sa xioms to prove the soundness of the union rule.(Hint:Use the augmentation rule to show that,if?→?,then?→??.Apply theaugmentation rule again,using?→?,and then apply the transitivityrule.)Answer:To prove that:if?→?and?→?then?→??Following the hint,we derive:→?given→??augmentation rule→??union of identical sets→?given→??augmentation rule→??transitivity rule and set union commutativity8.5Use Armstrong’sa xioms to prove the soundness of the pseudotransitiv-ity rule.a xioms of the Pseudotransitivity Rule:Answer:Proof using Armstrong’sif?→?and??→?,then??→?.→?given→??augmentation rule and set union commutativity ?→?given→?transitivity rule8.6Compute the closure of the following set F of functional dependenciesfor relation schema R=(A,B,C,D,E).Exercises11A→BCCD→EB→DE→AList the candidate keys for R.Answer:Note:It is not reasonable to expect students to enumerate all of F+.Some shorthand representation of the result should be acceptable as long as the nontrivial members of F+are found.Starting with A→BC,we can conclude:A→B and A→ C.Since A→B and B→D,A→D(decomposition,transitive) Since A→C D and C D→E,A→E(union,decom-position,transi-tive)Since A→A,we have(re?exive)A→ABC DE from the above steps(union)Since E→A,E→ABC DE(transitive)Since C D→E,C D→ABC DE(transitive)Since B→D and BC→C D,BC→ABC DE (augmentative, transitive)Also,C→C,D→D,B D→D,etc.Therefore,any functional dependency with A,E,BC,or C D on the left hand side of the arrow is in F+,no matter which other attributes appear in the FD.Allow*to represent any set of attributes in R,then F+isB D→B,B D→D,C→C,D→D,B D→B D,B→D,B→B,B→B D,and all FDs of the form A?→?,BC?→?,C D?→?,E?→?where?is any subset of{A,B,C,D,E}.Thecandidate keys are A,BC,C D,and E.8.7Using the functional dependencies of Practice Exercise8.6,compute thecanonicalcover F c.Answer:The given set of FDs F is:-A→BCCD→EB→DE→AThe left side of each FD in F is unique.Also none of the attributes in the left side or right side of any of the FDs is extraneous.Therefore the canonical cover F c is equal to F.12Chapter8Relational Database Design8.8Consider the algorithm in Figure8.18to compute?+.Show that thisalgorithm is more ef?cient than the one presented in Figure8.8(Sec-tion8.4.2)and that it computes?+correctly.Answer:The algorithm is correct because:If A is added to result then there is a proof that?→ A.To see this,observe that?→?trivially so?is correctly part of result.IfA∈?is added to result there must be some FD?→?such thatA∈?and?is already a subset of result.(Otherwise f dcountwould be nonzero and the if condition would be false.)A full proofcan be given by induction on the depth of recursion for an executionof addin,but such a proof can be expected only from students witha good mathematical background.If A∈?+,then A is eventually added to result.We prove this byinduction on the length of the proof of?→A using Armstrong’saxioms.First observe that if procedure addin is called with someargument?,all the attributes in?will be added to result.Also if aparticular FD’sfdcount becomes0,all the attributes in its tail willde?nitely be added to result.The base case of the proof,A∈??A∈?+,is obviously true because the?rst call to addinhas the argument?.The inductive hypotheses is that if?→A canbe proved in n steps or less then A∈result.If there is a proof inn+1steps that?→A,then the last step was an application ofeither re?exivity,augmentation or transitivity on a fact?→?proved in n or fewer steps.If re?exivity or augmentation was usedin the(n+1)st step,A must have been in result by the end of the n thstep itself.Otherwise,by the inductive hypothesis??result.Therefore the dependency used in proving?→?,A∈?willhave f dcount set to0by the end of the n th step.Hence A will beadded to result.To see that this algorithm is more ef?cient than the one presented inthe chapter note that we scan each FD once in the main program.Theresulting array appears has size proportional to the size of the givenFDs.The recursive calls to addin result in processing linear in the sizeof appears.Hence the algorithm has time complexity which is linear inthe size of the given FDs.On the other hand,the algorithm given in thetext has quadratic time complexity,as it may perform the loop as manytimes as the number of FDs,in each loop scanning all of them once.8.9Given the database schema R(a,b,c),and a relation r on the schema R,write an SQL query to test whether the functional dependency b→cholds on relation r.Also write an SQL assertion that enforces the func-tional dependency.Assume that no null values are present.(Althoughpart of the SQL standard,such assertions are not supported by anydatabase implementation currently.)Answer:Exercises13a.The query is given below.Its result is non-empty if and only ifb→c does not hold on r.select bfrom rgroup by bhaving count(distinct c)>1b.create assertion b to c check(not exists(select bfrom rgroup by bhaving count(distinct c)>1))8.10Our discussion of lossless-join decomposition implicitly assumed thatattributes on the left-hand side of a functional dependency cannot take on null values.What could go wrong on decomposition,if this property is violated?Answer:The natural join operator is de?ned in terms of the cartesian product and the selection operator.The selection operator,gives unknown for any query on a null value.Thus,the natural join excludes all tuples with null values on the common attributes from the?nal result.Thus, the decomposition would be lossy(in a manner different from the usual case of lossy decomposition),if null values occur in the left-hand side of the functional dependency used to decompose the relation.(Null values in attributes that occur only in the right-hand side of the functionaldependency do not cause any problems.)8.11In the BCNF decomposition algorithm,suppose you use a functional de-pendency?→?to decompose a relation schema r(?,?,?)into r1(?,?) and r2(?,?).a.What primary and foreign-key constraint do you expect to holdon the decomposed relations?b.Give an example of an inconsistency that can arise due to anerroneous update,if the foreign-key constraint were not enforcedon the decomposed relations above.c.When a relation is decomposed into3NF using the algorithm inSection8.5.2,what primary and foreign key dependencies wouldyou expect will hold on the decomposed schema?14Chapter8Relational Database DesignAnswer:a.?should be a primary key for r1,and?should be the foreign keyfrom r2,referencing r1.b.If the foreign key constraint is not enforced,then a deletion of atuple from r1would not have a corresponding deletion from thereferencing tuples in r2.Instead of deleting a tuple from r,thiswould amount to simply setting the value of?to null in sometuples.c.For every schema r i(??)added to the schema because of a rule→?,?should be made the primary key.Also,a candidate key?for the original relation is located in some newly created relationr k,and is a primary key for that relation.Foreign key constraints are created as follows:for each relationr i created above,if the primary key attributes of r i also occur inany other relation r j,then a foreign key constraint is created fromthose attributes in r j,referencing(the primary key of)r i.8.12Let R1,R2,...,R n be a decomposition of schema U.Let u(U)be a rela-(u).Show thattion,and let r i=RIu?r11r21···1r nAnswer:Consider some tuple t in u.(u)implies that t[R i]∈r i,1≤i≤n.Thus,Note that r i=Rit[R1]1t[R2]1...1t[R n]∈r11r21...1r nBy the de?nition of natural join,t[R1]1t[R2]1...1t[R n]=(??(t[R1]×t[R2]×...×t[R n])) where the condition?is satis?ed if values of attributes with the samename in a tuple are equal and where?=U.The cartesian productof single tuples generates one tuple.The selection process is satis?edbecause all attributes with the same name must have the same valuesince they are projections from the same tuple.Finally,the projectionclause removes duplicate attribute names.By the de?nition of decomposition,U=R1∪R2∪...∪R n,which meansthat all attributes of t are in t[R1]1t[R2]1...1t[R n].That is,t is equalto the result of this join.Since t is any arbitrary tuple in u,u?r11r21...1r n8.13Show that the decomposition in Practice Exercise8.1is not a dependency-preserving decomposition.Answer:The dependency B→D is not preserved.F1,the restrictionof F to(A,B,C)is A→ABC,A→AB,A→AC,A→BC,Exercises15 A→B,A→C,A→A,B→B,C→C,AB→AC,AB→ABC,AB→BC,AB→AB,AB→A,AB→B,AB→C,AC(same as AB),BC(same as AB),ABC(same as AB).F2,the restriction of F to (C,D,E)is A→ADE,A→AD,A→AE,A→DE,A→A, A→D,A→E,D→D,E(same as A),AD,AE,DE,ADE(same as A).(F1∪F2)+is easily seen not to contain B→D since the only FD in F1∪F2with B as the left side is B→B,a trivial FD.We shall see in Practice Exercise8.15that B→D is indeed in F+.Thus B→D is not preserved.Note that C D→ABC DE is also not preserved.A simpler argument is as follows:F1contains no dependencies with D on the right side of the arrow.F2contains no dependencies withB on the left side of the arrow.Therefore for B→D to be preserved there mustbe an FD B→?in F+1and?→D in F+2(so B→D would followby transitivity).Since the intersection of the two schemes is A,?= A.Observe that B→A is not in F+1since B+=B D.8.14Show that it is possible to ensure that a dependency-preserving decom-position into3NF is a lossless-join decomposition by guaranteeing that at least one schema contains a candidate key for the schema being decom-posed.(Hint:Show that the join of all the projections onto the schemas of the decomposition cannot have more tuples than the original relation.)Answer:Let F be a set of functional dependencies that hold on a schema R.Let?={R1,R2,...,R n}be a dependency-preserving3NF decompo-sition of R.Let X be a candidate key for R.Consider a legal instance r of R.Let j=X(r)1R1(r)1R2(r) (1)R n(r).We want to prove that r=j.We claim that if t1and t2are two tuples in j such that t1[X]=t2[X],then t1=t2.To prove this claim,we use the following inductive argument–Let F′=F1∪F2∪...∪F n,where each F i is the restriction of F to the schema R i in?.Consider the use of the algorithm given in Figure8.8to compute the closure of X under F′.We use induction on the number of times that the f or loop in this algorithm is executed.Basis:In the?rst step of the algorithm,result is assigned to X,and hence given that t1[X]=t2[X],we know that t1[result]=t2[result] is true.Induction Step:Let t1[result]=t2[result]be true at the end of thek th execution of the f or loop.Suppose the functional dependency considered in the k+1thexecution of the f or loop is?→?,and that??result.??result implies that t1[?]=t2[?]is true.The facts that?→?holds forsome attribute set R i in?,and that t1[R i]and t2[R i]are in R i(r)imply that t1[?]=t2[?]is also true.Since?is now added to result by the algorithm,we know that t1[result]=t2[result]is true at the end of the k+1th execution of the f or loop.16Chapter8Relational Database DesignSince?is dependency-preserving and X is a key for R,all attributes in Rare in result when the algorithm terminates.Thus,t1[R]=t2[R]is true,that is,t1=t2–as claimed earlier.Our claim implies that the size of X(j)is equal to the size of j.Notealso that X(j)=X(r)=r(since X is a key for R).Thus we haveproved that the size of j equals that of ing the result of PracticeExercise8.12,we know that r?j.Hence we conclude that r=j.Note that since X is trivially in3NF,?∪{X}is a dependency-preservinglossless-join decomposition into3NF.8.15Give an example of a relation schema R′and set F′of functional depen-dencies such that there are at least three distinct lossless-join decompo-sitions of R′into BCNF.Answer:Given the relation R′=(A,B,C,D)the set of functionaldependencies F′=A→B,C→D,B→C allows three distinctBCNF decompositions.R1={(A,B),(C,D),(B,C)}is in BCNF as isR2={(A,B),(C,D),(A,C)}R2={(A,B),(C,D),(A,C)}R3={(B,C),(A,D),(A,B)}8.16Let a prime attribute be one that appears in at least one candidate key.Let?and?be sets of attributes such that?→?holds,but?→?does not hold.Let A be an attribute that is not in?,is not in?,and forwhich?→A holds.We say that A is transitively dependent on?.Wecan restate our de?nition of3NF as follows:A relation schema R is in3NF with respect to a set F of functional dependencies if there are nononprime attributes A in R for which A is transitively dependent on akey for R.Show that this new de?nition is equivalent to the original one.Answer:Suppose R is in3NF according to the textbook de?nition.Weshow that it is in3NF according to the de?nition in the exercise.Let A bea nonprime attribute in R that is transitively dependent on a key?forR.Then there exists??R such that?→A,?→?,A∈?,A∈,and?→?does not hold.But then?→A violates the textbookde?nition of3NF sinceA∈?implies?→A is nontrivialSince?→?does not hold,?is not a superkeyA is not any candidate key,since A is nonprimeExercises17Now we show that if R is in3NF according to the exercise de?nition,it is in3NF according to the textbook de?nition.Suppose R is not in3NF according the the textbook de?nition.Then there is an FD?→?that fails all three conditions.Thus?→?is nontrivial.?is not a superkey for R.Some A in?-?is not in any candidate key.This implies that A is nonprime and?→ A.Let?be a candidate key for R.Then?→?,?→?does not hold(since?is not a superkey), A∈?,and A∈?(since A is nonprime).Thus A is transitivelydependent on?,violating the exercise de?nition.8.17A functional dependency?→?is called a partial dependency if thereis a proper subset?of?such that?→?.We say that?is partially dependent on?.A relation schema R is in second normal form(2NF)if each attribute A in R meets one of the following criteria:It appears in a candidate key.It is not partially dependent on a candidate key.Show that every3NF schema is in2NF.(Hint:Show that every partial dependency is a transitive dependency.)Answer:Referring to the de?nitions in Practice Exercise8.16,a relation schema R is said to be in3NF if there is no non-prime attribute A in R for which A is transitively dependent on a key for R.We can also rewrite the de?nition of2NF given here as:“Arelation schema R is in2NF if no non-prime attribute A is partiallydependent on any candidate key for R.”To prove that every3NF schema is in2NF,it suf?ces to show that if a non-prime attribute A is partially dependent on a candidate key?,thenA is also transitively dependent on the key?.Let A be a non-prime attribute in R.Let?be a candidate key for R.Suppose A is partially dependent on?.From the de?nition of a partial dependency,we know that for someproper subset?of?,?→ A.Since???,?→?.Also,?→?does not hold,since?is acandidate key.Finally,since A is non-prime,it cannot be in either?or?.Thus we conclude that?→A is a transitive dependency.Hence we have proved that every3NF schema is also in2NF.8.18Give an example of a relation schema R and a set of dependencies suchthat R is in BCNF but is not in4NF.18Chapter8Relational Database DesignAnswer:R(A,B,C)A→→BExercises19result:=?;/*fdcount is an array whose ith element contains the number of attributes on the left side of the ith FD that arenot yet known to be in?+*/for i:=1to|F|dobeginlet?→?denote the ith FD;fdcount[i]:=|?|;end/*appears is an array with one entry for each attribute.The entry for attribute A is a list of integers.Each integeri on the list indicates that A appears on the left sideof the i th FD*/for each attribute A dobeginappears[A]:=NI L;for i:=1to|F|dobeginlet?→?denote the ith FD;if A∈?then add i to appears[A];endendaddin(?);return(result);procedure addin(?);for each attribute A in?dobeginif A∈result thenbeginresult:=result∪{A};for each element i of appears[A]dobeginfdcount[i]:=fdcount[i]-1;if fdcount[i]:=0thenbeginlet?→?denote the ith FD;addin(?);endendendendFigure8.18.An algorithm to compute?+.。
数据库系统概念(database system concepts)英文第六版 课后练习题 答案 第21章

C H A P T E R21Information RetrievalPractice Exercises21.1Compute the relevance(using appropriate definitions of term fre-quency and inverse document frequency)of each of the Practice Ex-ercises in this chapter to the query“SQL relation”.Answer:We do not consider the questions containing neither of thekeywords as their relevance to the keywords is zero.The number ofwords in a question include stop words.We use the equations givenin Section21.2to compute relevance;the log term in the equation isassumed to be to the base2.21.2Suppose you want tofind documents that contain at least k of a givenset of n keywords.Suppose also you have a keyword index that givesyou a(sorted)list of identifiers of documents that contain a specifiedkeyword.Give an efficient algorithm tofind the desired set of docu-ments.Answer:Let S be a set of n keywords.An algorithm tofind all docu-ments that contain at least k of these keywords is given below:12Chapter21Information RetrievalThis algorithm calculates a reference count for each document identi-fier.A reference count of i for a document identifier d means that atleast i of the keywords in S occur in the document identified by d.The algorithm maintains a list of records,each having twofields–adocument identifier,and the reference count for this identifier.This listis maintained sorted on the document identifierfield.initialize the list L to the empty list;for(each keyword c in S)dobeginD:=the list of documents identifiers corresponding to c;for(each document identifier d in D)doif(a record R with document identifier as d is on list L)thenR.re f erence count:=R.re f erence count+1;else beginmake a new record R;R.document id:=d;R.re f erence count:=1;add R to L;end;end;for(each record R in L)doif(R.re f erence count>=k)thenoutput R;Note that execution of the second for statement causes the list D to“merge”with the list L.Since the lists L and D are sorted,the timetaken for this merge is proportional to the sum of the lengths of the twolists.Thus the algorithm runs in time(at most)proportional to n timesthe sum total of the number of document identifiers corresponding toeach keyword in S.21.3Suggest how to implement the iterative technique for computing Page-Rank given that the T matrix(even in adjacency list representation)does notfit in memory.Answer:No answer21.4Suggest how a document containing a word(such as“leopard”)canbe indexed such that it is efficiently retrieved by queries using a moregeneral concept(such as“carnivore”or“mammal”).You can assumethat the concept hierarchy is not very deep,so each concept has onlya few generalizations(a concept can,however,have a large number ofspecializations).You can also assume that you are provided with a func-tion that returns the concept for each word in a document.Also suggesthow a query using a specialized concept can retrieve documents usinga more general concept.Answer:Add doc to index lists for more general concepts also.Practice Exercises3 21.5Suppose inverted lists are maintained in blocks,with each block not-ing the largest popularity rank and TF-IDF scores of documents in the remaining blocks in the list.Suggest how merging of inverted lists can stop early if the user wants only the top K answers.Answer:For all documents whose scores are not complete use upper bounds to compute best possible score.If K th largest completed score is greater than the largest upper bound among incomplete scores output the K top answers.No answer。
数据库系统概念(英文精编版第六版)ch5AdvancedSQL

5.1 Accessing SQL From a Programming
Language
5.2 Function and Procedures 5.3 Triggers
Chapter 5: Advanced SQL
教学目的:
了解数据库API 掌握用SQL编写函数和过程 掌握触发器的概念,用SQL编写触发器
5.1.1 JDBC Code Example
public static void JDBCexample(String dbid, String userid, String passwd) {
char deptname[80]; float salary; int lenOut1, lenOut2; HSTMT stmt; char * sqlquery = "select dept_name, sum (salary) from instructor group by dept_name"; SQLAllocStmt(conn, &stmt); /* send SQL commands to the database */ error = SQLExecDirect(stmt, sqlquery, SQL_NTS); if (error == SQL_SUCCESS) { /* bind C language variables to attributes of the query result */
JDBC (Java Database Connectivity) works with Java
5.1.2 ODBC Code Example
void ODBCexample() { RETCODE error; HENV env; HDBC conn;
数据库系统概念(英文精编版.第六版)
Attributes
Attribute Domain
The set of allowed values for each attribute is called the domain of the attribute
The special value null is a member of every domain
Instructor_schema = (ID, name, dept_name, salary)
r(R) is a relation on the relation schema R
We use lowercase names for relations.
Example: instructor (Instructor _schema)
2.5 Relational Query Languages
2.6 Relational Operations
Chapter 2: Relational Model
教学目的:
熟悉关系数据模型
教学重点:
简单属性、多值属性、复合属性
关系、关系模式、码等概念 关系模式图 关系代数的操作
?简单属性多值属性复合属性?关系关系模式码等概念?关系模式图?关系代数的操作?教学难点
Chapter 2: Relational Model
2.1 Structure of Relational Databases 2.2 Database Schema 2.3 Keys 2.4 Schema Diagrams
referenced relation
Exercise: 找出左图里面
存在的其他外码、参照关 系和被参照关系
数据库系统概念第六版课后习题部分答案2s
数据库系统概念第六版课后习题部分答案2sC H A P T E R2Introduction to the Relational ModelPractice Exercises2.1Consider the relational database of Figure??.What are the appropriateprimary keys?Answer:The answer is shown in Figure2.1,with primary keys under-lined.2.2Consider the foreign key constraint from the dept name attribute of in-structor to the department relation.Give examples of inserts and deletes tothese relations,which can cause a violation of the foreign key constraint.Answer:Inserting a tuple:(10111,Ostrom,Economics,110,000)into the instructor table,where the department table does not have thedepartment Economics,would violate the foreign key constraint.Deleting the tuple:(Biology,Watson,90000)from the department table,where at least one student or instructortuple has dept name as Biology,would violate the foreign key con-straint.employee(person name,street,city)works(person name company name,salary)company(company name,city)Figure2.1Relational database for Practice Exercise2.1.12Chapter2Introduction to the Relational Model2.3Consider the time slot relation.Given that a particular time slot can meetmore than once in a week,explain why day and start time are part of theprimary key of this relation,while end time is not.Answer:The attributes day and start time are part of the primary keysince a particular class will most likely meet on several different days,and may even meet more than once in a day.However,end time is notpart of the primary key since a particular class that starts at a particulartime on a particular day cannot end at more than one time.2.4In the instance of instructor shown in Figure??,no two instructors havethe same name.From this,can we conclude that name can be used as asuperkey(or primary key)of instructor?Answer:No.For this possible instance of the instructor table the namesare unique,but in general this may not be always the case(unless theuniversity has a rule that two instructors cannot have the same name,which is a rather unlikey scenario).2.5What is the result of?rst performing the cross product of student andadvisor,and then performing a selection operation on the result with thepredicate s id=ID?(Using the symbolic notation of relational algebra,this query can be written as?s id=I D(student×advisor).)Answer:The result attributes include all attribute values of studentfollowed by all attributes of advisor.The tuples in the result are asfollows.For each student who has an advisor,the result has a rowcontaining that students attributes,followed by an s id attribute identicalto the students ID attribute,followed by the i id attribute containing theID of the students advisor.Students who do not have an advisor will not appear in the result.Astudent who has more than one advisor will appear a correspondingnumber of times in the result.2.6Consider the following expressions,which use the result ofa relationalalgebra operation as the input to another operation.For each expression,explain in words what the expression does.a.?year≥2009(takes)1studentb.?year≥2009(takes1student)c. ID,name,course id(student1takes)Answer:a.For each student who takes at least one course in2009,displaythe students information along with the information about whatcourses the student took.The attributes in the result are:ID,name,dept name,tot cred,course id,section id,semester,year,gradeb.Same as(a);selection can be done before the join operation.c.Provide a list of consisting ofExercises3ID,name,course idof all students who took any course in the university.2.7Consider the relational database of Figure??.Give an expression in therelational algebra to express each of the following queries:a.Find the names of all employees who live in city“Miami”.b.Find the names of all employees whose salary is greater than$100,000.c.Find the names of all employees who live in“Miami”and whosesalary is greater than$100,000.Answer:a. name(?city=“Miami”(employee))b. name(?salary>100000(employee))c. name(?city=“Miami”∧salary>100000(employee))2.8Consider the bank database of Figure??.Give an expression in therelational algebra for each of the following queries.a.Find the names of all branches located in“Chicago”.b.Find the names of all borrowers who have a loan in branch“Down-town”.Answer:a. branch name(?branch city=“Chicago”(branch))b. customer name(?branch name=“Downtown”(borro w er1loan))。
数据库英文版第六版课后答案

数据库英文版第六版课后答案Chapter 1: IntroductionQuestions1.What is a database?A database is a collection of organized and structured data stored electronically in a computer system. It allows users to efficiently store, retrieve, and manipulate large amounts of data.2.What are the advantages of using a database system?–Data sharing and integration: A database system allows multiple users to access and share data simultaneously.–Data consistency and integrity: A database system enforces rules and constraints to maintain the accuracy and integrity of the data.–Data security: A database system provides access control mechanisms to ensure that data is accessed by authorized users only.–Data independence: A database system separates the data from the application programs that use it, allowing for easier applicationdevelopment and maintenance.Exercises1.Discuss the advantages and disadvantages of using a database system.Advantages:–Data sharing and integration–Data consistency and integrity–Data security–Data independenceDisadvantages:–Cost: Database systems can be expensive to set up and maintain.–Complexity: Database systems require a certain level of expertise to design, implement, and manage.–Performance overhead: Database systems may introduce some overhead in terms of storage and processing.Overall, the advantages of using a database system outweigh the disadvantages in most cases, especially for large-scale applications with multiple users and complex data requirements.Chapter 2: Relational Model and Relational Algebra Questions1.What is a relation? How is it represented in the relational model?A relation is a table-like structure that represents a set of related data. It is represented as a two-dimensional table with rows and columns, where each row corresponds to a record and each column corresponds to a attribute or field.2.What is the primary key of a relation?The primary key of a relation is a unique identifier for each record in the relation. It is used to ensure the uniqueness and integrity of the data.Exercises1.Consider the following relation:Employees (EmpID, Name, Age, Salary)–EmpID is the primary key of the Employees relation.–Name, Age, and Salary are attributes of the Employees relation.2.Write a relational algebra expression to retrieve the names of all employees whose age is greater than 30.π Name (σ Age > 30 (Employees))Chapter 3: SQLQuestions1.What is SQL?SQL (Structured Query Language) is a programming language designed for managing and manipulating relational databases. It provides a set of commands and statements that allow users to create, modify, and query databases.2.What are the main components of an SQL statement?An SQL statement consists of the following main components:–Keywords: SQL commands and instructions.–Clauses: Criteria and conditions that specify what data to retrieve or modify.–Expressions: Values, variables, or calculations used in SQL statements.–Operators: Symbols used to perform operations on data. Exercises1.Write an SQL statement to create a table called。
数据库系统概念(database system concepts)英文第六版 PPT 第五章

"select * from instructor where name = ‟" + name + "‟" Suppose the user, instead of entering a name, enters: X‟ or ‟Y‟ = ‟Y then the resulting statement becomes: "select * from instructor where name = ‟" + "X‟ or ‟Y‟ = ‟Y" + "‟" which is: select * from instructor where name = ‟X‟ or ‟Y‟ = ‟Y‟ User could have even used X‟; update instructor set salary = salary + 10000; - Prepared statement internally uses: "select * from instructor where name = ‟X\‟ or \‟Y\‟ = \‟Y‟ Always use prepared statements, with user inputs as parameters
How is this useful?
Database System Concepts - 6th Edition
5.10
©Silberschatz, Korth and Sudarshan
Metadata (Cont)
Database metadata DatabaseMetaData dbmd = conn.getMetaData();
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
C H A P T E R8Relational Database DesignExercises8.1Suppose that we decompose the schema R=(A,B,C,D,E)into(A,B,C)(A,D,E).Show that this decomposition is a lossless-join decomposition if thefollowing set F of functional dependencies holds:A→BCCD→EB→DE→AAnswer:A decomposition{R1,R2}is a lossless-join decomposition ifR1∩R2→R1or R1∩R2→R2.Let R1=(A,B,C),R2=(A,D,E),and R1∩R2=A.Since A is a candidate key(see PracticeExercise8.6),Therefore R1∩R2→R1.8.2List all functional dependencies satisfied by the relation of Figure8.17.Answer:The nontrivial functional dependencies are:A→B andC→B,and a dependency they logically imply:AC→B.There are19trivial functional dependencies of the form␣→,where⊆␣.Cdoes not functionally determine A because thefirst and third tuples havethe same C but different A values.The same tuples also show B does notfunctionally determine A.Likewise,A does not functionally determineC because thefirst two tuples have the same A value and different Cvalues.The same tuples also show B does not functionally determine C.8.3Explain how functional dependencies can be used to indicate the fol-lowing:910Chapter8Relational Database Design•A one-to-one relationship set exists between entity sets student andinstructor.•A many-to-one relationship set exists between entity sets studentand instructor.Answer:Let Pk(r)denote the primary key attribute of relation r.•The functional dependencies Pk(student)→Pk(instructor)andPk(instructor)→Pk(student)indicate a one-to-one relationshipbecause any two tuples with the same value for student must havethe same value for instructor,and any two tuples agreeing oninstructor must have the same value for student.•The functional dependency Pk(student)→Pk(instructor)indicates amany-to-one relationship since any student value which is repeatedwill have the same instructor value,but many student values mayhave the same instructor value.8.4Use Armstrong’s axioms to prove the soundness of the union rule.(Hint:Use the augmentation rule to show that,if␣→,then␣→␣.Apply theaugmentation rule again,using␣→␥,and then apply the transitivityrule.)Answer:To prove that:if␣→and␣→␥then␣→␥Following the hint,we derive:␣→given␣␣→␣augmentation rule␣→␣union of identical sets␣→␥given␣→␥augmentation rule␣→␥transitivity rule and set union commutativity8.5Use Armstrong’s axioms to prove the soundness of the pseudotransitiv-ity rule.Answer:Proof using Armstrong’s axioms of the Pseudotransitivity Rule:if␣→and␥→␦,then␣␥→␦.␣→given␣␥→␥augmentation rule and set union commutativity␥→␦given␣␥→␦transitivity rule8.6Compute the closure of the following set F of functional dependenciesfor relation schema R=(A,B,C,D,E).Exercises 11A →BCCD →EB →DE →AList the candidate keys for R .Answer:Note:It is not reasonable to expect students to enumerate all of F +.Some shorthand representation of the result should be acceptable as long as the nontrivial members of F +are found.Starting with A →BC ,we can conclude:A →B and A →C .Since A →B and B →D ,A →D (decomposition,transitive)Since A →C D and C D →E ,A →E (union,decom-position,transi-tive)Since A →A ,we have (reflexive)A →ABC DE from the above steps (union)Since E →A ,E →ABC DE (transitive)Since C D →E ,C D →ABC DE (transitive)Since B →D and BC →C D ,BC →ABC DE (augmentative,transitive)Also,C →C ,D →D ,B D →D ,etc.Therefore,any functional dependency with A ,E ,BC ,or C D on the left hand side of the arrow is in F +,no matter which other attributes appear in the FD.Allow *to represent any set of attributes in R ,then F +is B D →B ,B D →D ,C →C ,D →D ,B D →B D ,B →D ,B →B ,B →B D ,and all FDs of the form A ∗→␣,BC ∗→␣,C D ∗→␣,E ∗→␣where ␣is any subset of {A ,B ,C ,D ,E }.The candidate keys are A ,BC ,C D ,and E .8.7Using the functional dependencies of Practice Exercise 8.6,compute thecanonical cover F c .Answer:The given set of FDs F is:-A →BCCD →EB →DE →AThe left side of each FD in F is unique.Also none of the attributes in the left side or right side of any of the FDs is extraneous.Therefore the canonical cover F c is equal to F .12Chapter8Relational Database Design8.8Consider the algorithm in Figure8.18to compute␣+.Show that thisalgorithm is more efficient than the one presented in Figure8.8(Sec-tion8.4.2)and that it computes␣+correctly.Answer:The algorithm is correct because:•If A is added to result then there is a proof that␣→A.To see this,observe that␣→␣trivially so␣is correctly part of result.IfA∈␣is added to result there must be some FD→␥such thatA∈␥andis already a subset of result.(Otherwise f dcountwould be nonzero and the if condition would be false.)A full proofcan be given by induction on the depth of recursion for an executionof addin,but such a proof can be expected only from students witha good mathematical background.•If A∈␣+,then A is eventually added to result.We prove this byinduction on the length of the proof of␣→A using Armstrong’saxioms.First observe that if procedure addin is called with someargument,all the attributes inwill be added to result.Also if aparticular FD’s fdcount becomes0,all the attributes in its tail willdefinitely be added to result.The base case of the proof,A∈␣⇒A∈␣+,is obviously true because thefirst call to addinhas the argument␣.The inductive hypotheses is that if␣→A canbe proved in n steps or less then A∈result.If there is a proof inn+1steps that␣→A,then the last step was an application ofeither reflexivity,augmentation or transitivity on a fact␣→proved in n or fewer steps.If reflexivity or augmentation was usedin the(n+1)st step,A must have been in result by the end of the n thstep itself.Otherwise,by the inductive hypothesis⊆result.Therefore the dependency used in proving→␥,A∈␥willhave f dcount set to0by the end of the n th step.Hence A will beadded to result.To see that this algorithm is more efficient than the one presented inthe chapter note that we scan each FD once in the main program.Theresulting array a ppears has size proportional to the size of the givenFDs.The recursive calls to addin result in processing linear in the sizeof a ppears.Hence the algorithm has time complexity which is linear inthe size of the given FDs.On the other hand,the algorithm given in thetext has quadratic time complexity,as it may perform the loop as manytimes as the number of FDs,in each loop scanning all of them once.8.9Given the database schema R(a,b,c),and a relation r on the schema R,write an SQL query to test whether the functional dependency b→cholds on relation r.Also write an SQL assertion that enforces the func-tional dependency.Assume that no null values are present.(Althoughpart of the SQL standard,such assertions are not supported by anydatabase implementation currently.)Answer:Exercises13a.The query is given below.Its result is non-empty if and only ifb→c does not hold on r.select bfrom rgroup by bhaving count(distinct c)>1b.create assertion b to c check(not exists(select bfrom rgroup by bhaving count(distinct c)>1))8.10Our discussion of lossless-join decomposition implicitly assumed thatattributes on the left-hand side of a functional dependency cannot take on null values.What could go wrong on decomposition,if this property is violated?Answer:The natural join operator is defined in terms of the cartesian product and the selection operator.The selection operator,gives unknown for any query on a null value.Thus,the natural join excludes all tuples with null values on the common attributes from thefinal result.Thus, the decomposition would be lossy(in a manner different from the usual case of lossy decomposition),if null values occur in the left-hand side of the functional dependency used to decompose the relation.(Null values in attributes that occur only in the right-hand side of the functional dependency do not cause any problems.)8.11In the BCNF decomposition algorithm,suppose you use a functional de-pendency␣→to decompose a relation schema r(␣,,␥)into r1(␣,) and r2(␣,␥).a.What primary and foreign-key constraint do you expect to holdon the decomposed relations?b.Give an example of an inconsistency that can arise due to anerroneous update,if the foreign-key constraint were not enforcedon the decomposed relations above.c.When a relation is decomposed into3NF using the algorithm inSection8.5.2,what primary and foreign key dependencies wouldyou expect will hold on the decomposed schema?14Chapter8Relational Database DesignAnswer:a.␣should be a primary key for r1,and␣should be the foreign keyfrom r2,referencing r1.b.If the foreign key constraint is not enforced,then a deletion of atuple from r1would not have a corresponding deletion from thereferencing tuples in r2.Instead of deleting a tuple from r,thiswould amount to simply setting the value of␣to null in sometuples.c.For every schema r i(␣)added to the schema because of a rule␣→,␣should be made the primary key.Also,a candidate key␥for the original relation is located in some newly created relationr k,and is a primary key for that relation.Foreign key constraints are created as follows:for each relationr i created above,if the primary key attributes of r i also occur inany other relation r j,then a foreign key constraint is created fromthose attributes in r j,referencing(the primary key of)r i.8.12Let R1,R2,...,R n be a decomposition of schema U.Let u(U)be a rela-(u).Show thattion,and let r i= RIu⊆r11r21···1r nAnswer:Consider some tuple t in u.(u)implies that t[R i]∈r i,1≤i≤n.Thus,Note that r i= Rit[R1]1t[R2]1...1t[R n]∈r11r21...1r nBy the definition of natural join,t[R1]1t[R2]1...1t[R n]= ␣((t[R1]×t[R2]×...×t[R n]))where the conditionis satisfied if values of attributes with the samename in a tuple are equal and where␣=U.The cartesian productof single tuples generates one tuple.The selection process is satisfiedbecause all attributes with the same name must have the same valuesince they are projections from the same tuple.Finally,the projectionclause removes duplicate attribute names.By the definition of decomposition,U=R1∪R2∪...∪R n,which meansthat all attributes of t are in t[R1]1t[R2]1...1t[R n].That is,t is equalto the result of this join.Since t is any arbitrary tuple in u,u⊆r11r21...1r n8.13Show that the decomposition in Practice Exercise8.1is not a dependency-preserving decomposition.Answer:The dependency B→D is not preserved.F1,the restrictionof F to(A,B,C)is A→ABC,A→AB,A→AC,A→BC,Exercises 15A →B ,A →C ,A →A ,B →B ,C →C ,AB →AC ,AB →ABC ,AB →BC ,AB →AB ,AB →A ,AB →B ,AB →C ,AC (same as AB ),BC (same as AB ),ABC (same as AB ).F 2,the restriction of F to (C ,D ,E )is A →ADE ,A →AD ,A →AE ,A →DE ,A →A ,A →D ,A →E ,D →D ,E (same as A ),AD ,AE ,DE ,ADE (same as A ).(F 1∪F 2)+is easily seen not to contain B →D since the only FD in F 1∪F 2with B as the left side is B →B ,a trivial FD .We shall see in Practice Exercise 8.15that B →D is indeed in F +.Thus B →D is not preserved.Note that C D →ABC DE is also not preserved.A simpler argument is as follows:F 1contains no dependencies with D on the right side of the arrow.F 2contains no dependencies withB on the left side of the arrow.Therefore for B →D to be preserved theremustbe an FD B →␣in F +1and ␣→D in F +2(so B →D would follow by transitivity).Since the intersection of the two schemes is A ,␣=A .Observe that B →A is not in F +1since B +=B D .8.14Show that it is possible to ensure that a dependency-preserving decom-position into 3NF is a lossless-join decomposition by guaranteeing that at least one schema contains a candidate key for the schema being decom-posed.(Hint :Show that the join of all the projections onto the schemas of the decomposition cannot have more tuples than the original relation.)Answer:Let F be a set of functional dependencies that hold on a schema R .Let ={R 1,R 2,...,R n }be a dependency-preserving 3NF decompo-sition of R .Let X be a candidate key for R .Consider a legal instance r of R .Let j = X (r )1 R 1(r )1 R 2(r ) (1)R n (r ).We want to prove that r =j .We claim that if t 1and t 2are two tuples in j such that t 1[X ]=t2[X ],then t 1=t 2.To prove this claim,we use the following inductive argument –Let F ′=F 1∪F 2∪...∪F n ,where each F i is the restriction of F to the schema R i in .Consider the use of the algorithm given in Figure 8.8to compute the closure of X under F ′.We use induction on the number of times that the f or loop in this algorithm is executed.•Basis :In the first step of the algorithm,result is assigned to X ,and hence given that t 1[X ]=t 2[X ],we know that t 1[result ]=t 2[result ]is true.•Induction Step :Let t 1[result ]=t 2[result ]be true at the end of thek th execution of the f or loop.Suppose the functional dependency considered in the k +1th execution of the f or loop is →␥,and that ⊆result .⊆result implies that t 1[]=t 2[]is true.The facts that →␥holds for some attribute set Ri in ,and that t 1[R i ]and t 2[R i ]are inR i (r )imply that t 1[␥]=t 2[␥]is also true.Since ␥is now added to result by the algorithm,we know that t 1[result ]=t 2[result ]is true at theend of the k +1th execution of the f or loop.16Chapter8Relational Database DesignSinceis dependency-preserving and X is a key for R,all attributes in Rare in result when the algorithm terminates.Thus,t1[R]=t2[R]is true,that is,t1=t2–as claimed earlier.Our claim implies that the size of X(j)is equal to the size of j.Notealso that X(j)= X(r)=r(since X is a key for R).Thus we haveproved that the size of j equals that of ing the result of PracticeExercise8.12,we know that r⊆j.Hence we conclude that r=j.Note that since X is trivially in3NF,∪{X}is a dependency-preservinglossless-join decomposition into3NF.8.15Give an example of a relation schema R′and set F′of functional depen-dencies such that there are at least three distinct lossless-join decompo-sitions of R′into BCNF.Answer:Given the relation R′=(A,B,C,D)the set of functionaldependencies F′=A→B,C→D,B→C allows three distinctBCNF decompositions.R1={(A,B),(C,D),(B,C)}is in BCNF as isR2={(A,B),(C,D),(A,C)}R2={(A,B),(C,D),(A,C)}R3={(B,C),(A,D),(A,B)}8.16Let a prime attribute be one that appears in at least one candidate key.Let␣andbe sets of attributes such that␣→holds,but→␣does not hold.Let A be an attribute that is not in␣,is not in,and forwhich→A holds.We say that A is transitively dependent on␣.Wecan restate our definition of3NF as follows:A relation schema R is in3NF with respect to a set F of functional dependencies if there are nononprime attributes A in R for which A is transitively dependent on akey for R.Show that this new definition is equivalent to the original one.Answer:Suppose R is in3NF according to the textbook definition.Weshow that it is in3NF according to the definition in the exercise.Let A bea nonprime attribute in R that is transitively dependent on a key␣forR.Then there exists⊆R such that→A,␣→,A∈␣,A∈,and→␣does not hold.But then→A violates the textbookdefinition of3NF since•A∈implies→A is nontrivial•Since→␣does not hold,is not a superkey•A is not any candidate key,since A is nonprimeExercises17 Now we show that if R is in3NF according to the exercise definition,it is in3NF according to the textbook definition.Suppose R is not in3NF according the the textbook definition.Then there is an FD␣→that fails all three conditions.Thus•␣→is nontrivial.•␣is not a superkey for R.•Some A in−␣is not in any candidate key.This implies that A is nonprime and␣→A.Let␥be a candidate key for R.Then␥→␣,␣→␥does not hold(since␣is not a superkey), A∈␣,and A∈␥(since A is nonprime).Thus A is transitively dependent on␥,violating the exercise definition.8.17A functional dependency␣→is called a partial dependency if thereis a proper subset␥of␣such that␥→.We say thatis partially dependent on␣.A relation schema R is in second normal form(2NF)if each attribute A in R meets one of the following criteria:•It appears in a candidate key.•It is not partially dependent on a candidate key.Show that every3NF schema is in2NF.(Hint:Show that every partial dependency is a transitive dependency.)Answer:Referring to the definitions in Practice Exercise8.16,a relation schema R is said to be in3NF if there is no non-prime attribute A in R for which A is transitively dependent on a key for R.We can also rewrite the definition of2NF given here as:“A relation schema R is in2NF if no non-prime attribute A is partially dependent on any candidate key for R.”To prove that every3NF schema is in2NF,it suffices to show that if a non-prime attribute A is partially dependent on a candidate key␣,thenA is also transitively dependent on the key␣.Let A be a non-prime attribute in R.Let␣be a candidate key for R.Suppose A is partially dependent on␣.•From the definition of a partial dependency,we know that for someproper subsetof␣,→A.•Since⊂␣,␣→.Also,→␣does not hold,since␣is acandidate key.•Finally,since A is non-prime,it cannot be in eitheror␣.Thus we conclude that␣→A is a transitive dependency.Hence we have proved that every3NF schema is also in2NF.8.18Give an example of a relation schema R and a set of dependencies suchthat R is in BCNF but is not in4NF.18Chapter8Relational Database DesignAnswer:R(A,B,C)A→→BExercises19result:=∅;/*fdcount is an array whose i th element contains the number of attributes on the left side of the i th FD that arenot yet known to be in␣+*/for i:=1to|F|dobeginlet→␥denote the i th FD;fdcount[i]:=||;end/*appears is an array with one entry for each attribute.The entry for attribute A is a list of integers.Each integeri on the list indicates that A appears on the left sideof the i th FD*/for each attribute A dobeginappears[A]:=NI L;for i:=1to|F|dobeginlet→␥denote the i th FD;if A∈then add i to appears[A];endendaddin(␣);return(result);procedure addin(␣);for each attribute A in␣dobeginif A∈result thenbeginresult:=result∪{A};for each element i of appears[A]dobeginfdcount[i]:=fdcount[i]−1;if fdcount[i]:=0thenbeginlet→␥denote the i th FD;addin(␥);endendendendFigure8.18.An algorithm to compute␣+.。
