IDP配置手册及实例.new
Juniper IDP手册

Juniper Netscreen IDP配置手册2006.3目录一、前言 (3)二、理解IDP (3)1.三层架构 (3)2.部署模式 (3)三、IDP使用步骤(重要) (4)四、安装并设置IDP Management Server, IDP sensor ,UI (5)1.软件 (5)2.SENSOR线缆及接口 (5)3.安装Management Server (5)4.通过ACM设置Sensor(IDP出厂时已安装Sensor软件,非必要无需重新安装) . 65. 安装用户管理界面(UI) (7)五、通过UI配置Management Server并且下发策略到IDP Sensor (8)1.打开UI,出现如下界面: (8)2.增加objects(sensor,networks,host等等)。
(9)六、配置安全策略 (10)七、日志及报告 (14)八、运行企业安全事件探查器 (17)九、常用的IDP CLI命令 (21)一、前言该使用手册是一个简单的操作指南,主要列举了在IDP安装、使用过程中的一些主要的参数和步骤。
最重要的是,为确保客户方应用系统的稳定运行,建议IDP的工作模式由Sniffer Mode向In-line Mode过渡。
本使用指南主要针对3.0版本以及小版本的升级,如果有不详尽的地方,请参阅官方网站的IDP指南以及C&E。
二、理解IDP1.三层架构●IDP Sensor(即IDP设备):用于监控并且处理网络流量。
●IDP Management Server:运行于Linux或Solaris平台,用于存储所有的网络对象,日志,报表,安全策略、规则等。
●IDP User Interface (UI):运行在客户端PC的图形化管理系统,用于连接Management Server,处理存储在Management Server的日志、报表;定制并分发安全策略到Sensor。
IDD设置终端(MP型号仅限)说明书

5.3Setting TerminalsA user sets up the following terminals and SCSI terminating resistor before installing the IDD in the system as required.• Setting terminal:CN2 (MP model only)Figures 5.2 shows the setting terminal position. Figures 5.3 shows the allocation and defaultsettings.CAUTIONData loss1.The user must not change the setting of terminals not described in thissection. Do not change setting status set at factory shipment.2.Do not change the setting of terminals except following setting pins during the power is turned on.• Write protect: CN2 9-10 (MP model only)3.To short the setting terminal, use the short plug attached when the device is shipped from the factory.Figure 5.2IDD setting terminals position (MP model only)CN2Pin 1Figure 5.3Setting terminals (CN2 on MP model only)5.3.1SCSI ID setting (MP model only)Table 5.1 shows the SCSI ID setting. Refer to Figures 5.2 and 5.3 for terminal positioning and allocation.IMPORTANTWhen the SCSI ID is set using the external operator panel connector CN1, all pins listed in Table 5.1 should be open. If any of pins are shorted, unexpected SCSI ID is set.242220181614121086422321191715131197531Terminator power supply: Supply (LED signal)(IDD Reset signal)N.C.Force Single Ended: LVD mode Force Narrow: 16bit-SCSI Motor start mode Write protect: enabled SCSI ID #15Table 5.1SCSI ID setting (CN2 on MP model only)SCSI ID CN27-85-63-41-20Open Open Open Open1Open Open Open Short2Open Open Short Open3Open Open Short Short4Open Short Open Open5Open Short Open Short6Open Short Short Open7Open Short Short Short8Short Open Open Open9Short Open Open Short10Short Open Short Open11Short Open Short Short12Short Short Open Open13Short Short Open Short14Short Short Short Open15Short Short Short Short(default)IMPORTANT1.Set the SCSI ID so that there are no duplicates between SCSI devices onthe same SCSI bus.2.The priority of SCSI bus use in ARBITRATION phase is determined bySCSI ID as follows:7 > 6 > 5 > 4 > 3 > 2 > 1 > 0 > 15 > 14 > 13 > 12 > 11 > 10 > 9 > 85.3.2 Each mode setting (MP model only)(1)Setting terminator power supplyRefer to Table 5.2 for controlling the supply of power from the drive to the SCSI terminator power source (TERMPOW). For information on MP model, refer to Figures 5.2 and 5.3.Table 5.2Setting SCSI terminator power supply (MP model only)Supply on/off of SCSI terminator power from IDD CN2 23-24Supply off OpenSupply on Short(default)(2)Motor start modeSet how to control the starting of the IDD spindle motor according to Table 5.3. This setting only determines the operation mode when the power supply is turned on or the microcode is downloaded. In both modes, stopping or restarting the spindle motor can be controlled by specifying the START/STOP UNIT command.Table 5.3Motor start mode setting (MP model only)Start timing of the spindle motor CN2 11-12Starting of the motor is controlled with the START/STOP UNIT command.OpenThe motor is started immediately after the power supply is turned on or theShort(default) microcode is downloaded.Refer to Chapter 3 of the SCSI Logical Interface Specifications for details of the START/STOP UNIT command.(3)Write protectWhen the write protect function is enabled, writing to the disk medium is disabled.Table 5.4Write protect setting (MP model only)Write protect CN2 9-10Write operation is enabled.Open(default)Write operation is disable.Short(4)Setting of the SCSI interface operation modeBy establishing a short-circuit between the 15 and 16 CN2 setting terminals, the SCSI interface operation mode is forcibly set to the single-ended mode. When this setup terminal is open, the IDD automatically identifies the DIFFSNS signal level on the SCSI bus and the IDD SCSI interface operation mode is set to the operation mode.Table 5.5Setting of the SCSI interface operation mode (MP model only)Operation mode CN2 15-16 Follows the DIFFSNS signal level on the SCSI bus Open(default) Single-Ended mode Short(5)Setting the bus width of the SCSI interfaceBy establishing a short-circuit between the 13 and 14 CN2 setting terminals, the bus width for the SCSI interface is forcibly set to the 8-bit bus mode. This setup terminal must be set in order to guarantee the physical level of the SCSI interface’s upper bus (DB8-15, P1) inside the IDD only when the top-level bus (DB8-15, P1) for the IDD SCSI interface is not connected to the external part of the IDD.Table 5.6Setting the bus width of the SCSI interface (MP model only)Bus width CN2 13-1416 bit bus Open(default)8 bit bus Short5.3.3Mode settingsIn addition to the previously described settings using setting terminals, the IDD is provided with several mode settings. The mode settings are enabled by specifying the CHANGE DEFINITION command.Table 5.7 lists the mode settings and their settings at factory shipment.Refer to Section 3.1.4 of the SCSI Logical Interface Specifications for details of the command.Table 5.7Default mode settings (by CHANGE DEFINITION command)Mode setting Contents SCSI level SCSI-2SYNCHRONOUS DATA TRANSFER REQUEST message sending Sent from IDDUNIT ATTENTION report mode ReportedReselection retry count Not restrictedWIDE DATA TRANSFER REQUEST message sending Sent from IDDReselection time-out delay250 msSpindle motor start delay time0 sec (MP)12 sec × SCSI ID (MC)。
个人发展计划 idp 实例

个人发展计划 idp 实例个人发展计划(IDP)实例引言:每个人在自己的职业生涯中都需要不断发展和进步,而个人发展计划(IDP)就是为了帮助个人制定明确的目标,并规划实现这些目标所需的步骤和资源。
本文将以一个实例来展示一个个人发展计划的内容和步骤。
目标设定:作为一个会计师,我的主要目标是在职业生涯中不断提升自己的专业知识和技能,成为一名出色的财务专家。
为了实现这一目标,我将制定以下几个子目标:1. 提高财务分析能力:通过参加相关培训和课程,加强对财务报表的理解和分析能力,提高财务决策的准确性和效率。
2. 扩展税务知识:通过学习税法和税务规定,了解并掌握最新的税务政策和法规,提供更准确的税务咨询和规划服务。
3. 培养领导力:通过参与团队项目和管理培训,提升自己的领导能力和团队合作能力,成为一个优秀的团队领导者。
制定步骤:1. 自我评估:首先,我将对自己进行全面的自我评估,包括评估自己的专业知识和技能水平、职业发展目标和兴趣爱好等。
这将帮助我更好地了解自己的优势和不足,并确定需要提升的方面。
2. 设定目标:根据自我评估的结果,我将制定明确的目标,包括具体的职业发展目标和学习目标。
这些目标应该是可衡量和具体的,以便后续评估和调整。
3. 制定行动计划:为了实现这些目标,我将制定详细的行动计划。
例如,为了提高财务分析能力,我将报名参加相关的培训课程,阅读专业书籍和文章,并与行业内的专家进行交流和学习。
4. 寻找资源:为了顺利实施行动计划,我将寻找适当的资源支持。
这包括参加行业研讨会和培训班、加入相关的专业协会和组织,以及寻找导师或指导人帮助我在职业发展中取得更好的进步。
5. 实施和评估:在实施行动计划的过程中,我将定期对自己的进展进行评估,并根据评估结果进行调整和改进。
这将帮助我及时发现问题并采取相应的措施,确保目标的顺利实现。
6. 持续学习:除了制定和实施个人发展计划,我还将保持持续学习的习惯。
通过阅读专业书籍、参加学术讲座和行业研讨会,我将不断更新自己的知识和技能,保持与行业的同步。
迪普产品配置文档-基础篇(2012-11-05)

配置了关键字过滤功能,但无法过滤?
• 在配置行为审计的前提下,添加关键字过滤参数
35
35
UAG审计及流控
问题与排查
旁路模式,当设备异常重启或断电后,为何网络产生风暴?
• 中高端的GA、GE、TS设备,前三对儿接口默认自带断电保护,如镜像连接设备0、 1接口,设备正常运行下,0、1口为旁路且独立,当设备异常断电后,会启动断 掉保护机制,即0、1直通。建议使用不同接口对实现旁路,或SW上VLAN隔离
UAG 旁路部署模式
旁路部署方式 非在线部署
Internet 路由器
镜像 内部网络 交换机
对镜像流量进行用户行为审计
25
25
UAG审计及流控
调研信息
组网模式:在线模式、旁路模式、网关模式 PFP断电保护主机:是否使用,使用接口插卡类型(电、光) 开启安全策略:根据用户需求,如行为审计、流量分析、带宽限速等 UMC统一管理中心:是否安装
32
32
UAG审计及流控
配置步骤(7)
创建其他安全策略 修改管理员密码 修改管理地址,需同步修改日志输出“源IP” 添加管理默认路由
修改SNMP参数 修改日志保存时间(系统日志、业务日志、操作日志) 以上策略是否开启根据需求而定,配置方法参考用户手册
上下行链路接口类型(光、电)及速率、双工状态 部署链路数量 中、高端UAG,自带前三对儿电口断电保护功能
26
26
UAG审计及流控
配置步骤(1)
确认组网模式
•
•
透明桥接模式下几乎支持UAG所有功能,流控、审计、限速、web认证等
桥地址切忌与其他接口网段冲突,包括带外管理口
idp傻瓜安装手册

IDP中文安装手册目录3.1安装部署并配置IDP sensor (1)确定部署模式 (1)安装Sensor (1)3.2安装部署并配置Management Server (1)系统平台要求: (1)NSM光盘说明 (2)安装NSM前的操作 (3)第一步: (3)第二步: (3)第三步: (4)第四步: (4)第五步: (4)第六步: (4)正式安装管理软件 (5)第一步: (5)第二步: (6)第三步: (6)第四步: (7)第五步: (7)第六步: (8)第七步: (8)3.3安装部署并配置NSM windows客户端 (10)客户端的安装 (10)配置Management Server (12)1.打开UI(NetScreen-Security Manager),出现如下界面: (12)2.加栽NSM管理设备 (13)3.配置安全策略 (15)4.加载策略到设备上 (17)5.升级IDP引擎 (18)6.查看日志报表 (19)3.1安装部署并配置IDP sensor确定部署模式IDP Sensor部署为桥接和透明模式::用于监控并且防御经过的网络流量攻击。
IDP Management Server:用于存储所有的网络对象,日志,报表,安全策略、规则等。
IDP User Interface (UI):运行在客户端PC的图形化管理系统,用于连接Management Server,处理存储在Management Server的日志,报表;处理并分发安全策略到Sensor。
安装Sensor●用console线接笔记本至Sensor。
设置笔记本串口为:9600,8,N,1●看eth0配置,Ifconfig eth0●定义的配置,Ifconfig eth0 192.168.0.1 netmask 255.255.255.0●设置sensor管理接口ip地址,例如192.168.1.1/24,设置笔记本ip地址,例如:192.168.2.2/24●打开浏览器,输入:●用户名为:root,口令为:abc123●按照ACM(Appliance Configure Management)向导设置Sensor。
IDP系统安装维护操作手册

Netscreen IDP(入侵检测防御系统)系统安装维护操作手册北京天刚数码科技有限公司一、安装IDP Sensor的软件当IDP系统软件发生故障或者有新版本软件发布,可以通过Appliance CD进行IDP系统恢复,必须参照一下步骤:1.备份LICENSE由于LICENSE是随机带的,因此在恢复或升级系统之前必须先将LICENSE备份出来。
首先:通过FTP方式将两个文件(backuplic.sh & restorelic.sh)拷贝到IDP指定目录(/mnt/floppy)中;然后,执行命令:chmod 700 *.sh来添加这两个文件的执行权限;执行命令:./backuplic.sh,系统会将三个LICENSE文件(host-id & idp.cfg & idp.lic)拷贝到/mnt/floppy中;再使用FTP将这三个文件备份出来。
2.备份配置信息IDP会将所有配置信息(包括:定制的策略、LOG、系统信息、OBJECTS信息)放置在指定目录(/usr/idp/mgt-svr/var),因此使用一下命令:tar cvf filename /usr/idp/mgt-svr/var随后将这个文件备份出来以便后面恢复当初的配置3.恢复系统插入Appliance CD,连接显示器和键盘,重新启动IDP,当提示boot:时按回车,系统会自动恢复不需要任何操作,安装结束后按提示Ctrl+Alt+Del重起机器,系统会自动重起两次完成恢复工作。
4.恢复LICENSE恢复完系统后,缺省是没有LICENSE的,因此首先通过FTP方式将备份出来的三个LICENSE文件和restorelic.sh拷贝到制定目录(/mnt/floppy),输入命令:chmod 700 restorelic.sh添加文件执行属性输入命令:./restorelic.sh恢复LICENSE5.恢复系统配置将备份出来的系统配置文件(使用tar cvf filename /usr/idp/mgt-svr/var备份出来的文件)拷贝到临时目录,使用一下命令进行恢复:tar xvf filename6.确认系统恢复完成使用以下命令来确认系统恢复是否完成:scio lic list查看LICENSE是否安装成功;idp.sh status查看IDP所有进程是否启动成功进入/usr/idp/mgt-svr/bin目录,实行命令:./mgtSvr.sh status查看所有管理服务器的进程是否启动成功。
IDP导入license以及配置

SRX Getting Started - Quick Setup Guide for Configuring IDP ona SRX or J-Series deviceSUMMARY:This article describes the steps involved in configuring IDP on a SRX device.For other topics, go to the SRX Getting Started main page.SOLUTION:The basic configuration of IDP involves the following four tasks:I. Install IDP licenseThe IDP signature update is a subscription service requiring a license. In order to download and use the predefined attack signatures in a policy, the IDP license must be installed. If you are using only custom signatures, you do not need an IDP license.1. First, activate your subscription license by entering the authorization code and chassis serial number intothe Subscription Registration system. Refer to KB9731 for more information. If you still need help, please contact Customer Care for subscription and licensing issues.2. Then, install the license on the SRX in one of two ways -- automatically or manually:a. Automatically:Confirm the SRX device has connectivity to the Internet. Then run the following command:root> request system license updateORb. Manually:Licenses can also be loaded manually via JWeb, NSM, or using the CLI. The CLI command is as follows: root> request system license add terminal[Type ^D at a new line to end input,enter blank line between each license key]Paste the license key and press enterType Ctrl+DThe License key should be added successfully.3. Verify the license is installed using the command:root> show system licenseCheck for feature 'idp-sig'.NOTE: If running a Chassis Cluster, then the IDP license needs to be installed on both nodes.II. Download and install the Signature DatabaseAfter the IDP license is installed, the IDP Signature Database can be downloaded and installed byperforming the following steps:1. Confirm the device has the necessary configuration for connectivity to the Internet.2. Configure the signature database URL:root> editset security idp security-package urlhttps:///cgi-bin/index.cgiroot#commit3. Check the version of the signature database in the sigdb server. Look for 'Successfully retrieved' . In thisexample, the version in the server is 1577.root>request security idp security-package download check-serverSuccessfullyretrieved from(https:///cgi-bin/index.cgi).Version info:1577(Detector=10.2.160091104, Templates=2)4. Download the signature database:root> request security idp security-package download full-update5. Verify the progress of the download:root> request security idp security-package download statusroot> request security idp security-package download statusIn progress:downloading file ...platforms.xml.gzroot> request security idp security-package download statusDone;Successfullydownloaded from(https:///cgi-bin/index.cgi).Version info:1586(Tue Jan 19 12:28:29 2010, Detector=10.2.160091104) Important:When 'Successfully downloaded' is reported, proceed to the next step. If it is notsuccessfully downloaded, the install will fail.6. Install the signature DB by running the command:root> request security idp security-package installadmin> request security idp security-package install policy-templatesThis command loads the security package into the IDPD embedded DB. If there is an existing running policy it re-compiles the existing running policy and pushes the compiled policy to the data plane.Therefore, the install might take a while depending on the platform and the size of the policy. Lower end Branch platforms might take a longer time for install.7. Monitor the status of the install with the command:root> request security idp security-package install statusDone;Attack DB update : successful - [UpdateNumber=1581,ExportDate=Tue Jan 12 12:43:22 2010,Detector=10.2.160091104]Updating control-plane with new detector : successfulUpdating data-plane with new attack or detector : successfulThe 'UpdateNumber' field shows the version updated, the date when the signature db was released, and the detector version8. Verify the version of the sigdb installed:root>oAttack database version:1577(Tue Jan 5 13:27:18 2010)Detector version :10.2.160091104Policy template version :2Tips:Refer to KB16491 for instructions on how to schedule the signature database download for automatic updates.CLI Configuration1. Specify the URL for the security package:root# set security idp security-package urlhttps:///cgi-bin/index.cgiIMPORTANT:The URL stated above is correct. The URL, i.e. , specified in the some versions of the documentation is not correct. Please use the URL above.2. Specify the time and interval for the automatic download:root# set security idp security-package automatic interval <hours> start-time <the start of the first download>For example, to set the download to happen after three days, with the first automatic downloadingstarting on 14th July at 2:00 AM:root# set security idp security-package automatic interval 72 start-time 2013-07-14.02:00:003. Enable the automatic download:root# set security idp security-package automatic enableNOTES:If you have configured the device for automatic signature DB download, the new signature database is downloaded and installed.If there is a running IDP policy in the device, the policy is recompiled with the new signatures and pushed to the data plane.Similarly, if there is an existing running IDP policy and the previously installed detector's version is different from the newly downloaded one, then the newly downloaded detector is pushed to the data plane.∙Refer to TN83 for instructions on how to perform offline sigdb download.∙For additional information on the IDP Signature Database, refer to the Security Configuration Guide -- IDP Signature Database Chapter:/techpubs/en_US/junos10.4/information-products/topic-collections/security/softwar e-all/security/index.html?jd0e62605.htmlIII. Configure Recommended Policy as the IDP PolicyJuniper Networks provides predefined policy templates that can be used as a starting point for creating your own IDP policies. For getting started, it is recommended to use the predefined policy named'Recommended':1. Load the predefined templates, and select the Recommended template as the Active IDP policy. Referto KB16490for step by step instructions.CLI ConfigurationDownload the latest IDP policy templates (such as ‘Recommended’, ‘All with Logging') from the Juniper Website using the following command:root> request security idp security-package download policy-templates The policy-templates are downloaded to the directory: /var/db/idpd/sec-download/sub-downloadCheck the status of the download with the command:root> request security idp security-package download statusDone;Successfully downloadedfrom(https:///cgi-bin/index.cgi).clVersion info:2Install the template file:root> request security idp security-package install policy-templates It will be installed into: /var/db/scripts/commit/templates.xslCheck the status of the install with the command:root@SRX210-HM> request security idp security-package install status Done;policy-templates has been successfully updated into internal repository(=>/var/db/scripts/commit/templates.xsl)!Apply the template into the Junosconfig, and then commit!root> configureroot# set system scripts commit file templates.xslroot# commitcommit之后要把源文件删除delete system scripts commit file templates.xslOnce committed, the predefined templates can be used. Enter the following command to see the possible templates. You can set one of the predefined templates as the active policy, and also make changes to the policy.root# set security idp active-policy ?Possible completions:<active-policy> Set active policyDMZ_ServicesDNS_ServiceFile_ServerGetting_StartedIDP_DefaultRecommendedWeb_ServerFor example, to make Recommended template as the active IDP policy use the command:root# set security idp active-policy Recommendedroot# commit2. Verify that the Active IDP Policy is 'Recommended'. The Policy Name in the output below refers to theActive IDP Policy.root> show security idp statusSession Statistics:[ICMP: 0] [TCP: 0] [UDP: 0] [Other: 0]Policy Name : Recommended v0Running Detector Version : 10.2.1600911043. Perform the instructions below in the next section: 'IV. Enable a Security Policy for IDP inspection'.Tips:∙For additional information on configuring IDP policies, refer to the Security Configuration Guide -- IDP PoliciesChapter:/techpubs/en_US/junos10.4/information-products/topic-collections/securit y/software-all/security/index.html?jd0e54584.html∙Refer to KB15374 on how to verify if the IDP Policy was compiled and loaded successfully to the dataplane.IV. Enable a Security Policy for IDP inspectionOnce the IDP Policy is configured, IDP needs to be enabled on a security policy so that IDP inspection is performed. This is done by permitting application-services while configuring a security policy.For example, the following command forwards all traffic from-zone trust to-zone untrust to IDP tobe checked against the IDP rulebase:root# set security policies from-zone trust to-zone untrust policy idp-app-policy-1 match source-address any destination-address any application anyroot# set security policies from-zone trust to-zone untrust policy idp-app-policy-1 then permit application-services idpTips:∙For additional information on enabling IDP in a Security Policy, refer to the Security Configuration Guide -- Enabling IDP in a Security Policy:∙/techpubs/en_US/junos10.4/information-products/topic-collections/security/softwar e-all/security/index.html?topic-42452.html[edit]set applications application cust-app application-protocol ftp protocol tcp destination-port 78 inactivity-timeout 6000set security idpidp-policy ABC rulebase-ips rule ABC match application cust-appsetsecurity idpidp-policy ABC rulebase-ips rule ABC then action no-action set security idp active-policy ABC[edit]set applications application-set SrvAccessAppSet application junos-ssh set applications application-set SrvAccessAppSet application junos-telnet set applications application-set SrvAccessAppSet application cust-app set security idpidp-policy ABC rulebase-ips rule ABC match application SrvAccessAppSetset security idpidp-policy ABC rulebase-ips rule ABC then action no-action set security idp active-policy ABC[SRX] Update IDP in the secondary node of a SRX Chassis Cluster (High Availability)SUMMARY:Update IDP in the secondary node of a SRX High Availability cluster.PROBLEM OR GOAL:Symptom/Problem:∙Attack Database on secondary node is not in sync with primary node∙How do I sync the Attack DatabseWith Junos 11.4 and below, the IDP security package (attack signature database) is not updated on the secondary node (generally node1) when the IDP update command is run from the operational mode.This article will tell you how to update the IDP in the secondary node of a cluster. The secondary node ofa Chassis Cluster does not have a running Routing Subsystem, hence the Internet is not reachable fromthere.With Junos 12.1, a new feature was added to synchronize the IDP security package (attack signature database) in a Chassis Cluster automatically. (See the Release Notes: New Features - Junos 12.1 Branch SRX and New Features - Junos 12.1 High-end SRX.) With 12.1, the attack database version on each node of a Chassis Cluster should match. However, if they don't, perhaps if they were out of sync prior to an upgrade, this article provides instructions on how to sync them.CAUSE:SOLUTION:Important: The IDP license is necessary to be installed on the Secondary node as well for IDP to function. If the Attack database on the secondary node is N/A, the IDP license may not be installed.For help with the license, refer to the SRX Getting Started - Quick Setup Guide.Perform the instructions below to sync up the attack signature database on the secondary node: Junos 12.1 and aboveWith Junos 12.1, the attack database version on each node of a Chassis Cluster should match. However, if they are not in sync, re-download and re-install the attack signature database on the primary node, and it will be automatically synced to the secondary node. For instructions, refer to Section II Download and install the Signature Database of KB16489 - Quick Setup Guide for Configuring IDP on a SRX.Junos 11.4 and belowThe Secondary node is not able to connect to the Internet of non-running routing subsystem, but it always accepts data from the primary. We can use this ability of the HA secondary node to accept the IDP update files from the Primary node i.e. Node0 in this example, which is up-to-date in IDP:1. Go to the shell prompt:[primary node0]>start shell2. Login as the super user by typing "su":%supassword:<enter password>3. Copy the following from node0 to node1:%rcp-r -T /var/db/idpd/sec-download/* node1:/var/db/idpd/sec-download/ The rcp is a slow copy method, and the database is usually mostly 20MB+, so it will take time to finish.NOTE: If an older version of the Attack Database exists on the secondary node i.e. node1, you may get an error similar to this:cp: /var/db/idpd/sec-download/SignatureUpdate.xml and /var/db/idpd/sec-download/SignatureUpdate.xml are identical (not copied)If so, then remove the attack database from the secondary node1, and then run the RCP command again:%rm -rf node1:/var/db/idpd/sec-download/*%rcp -r -T /var/db/idpd/sec-download/* node1:/var/db/idpd/sec-download/ Note: The above commands are run from the shell mode, indicated by the "%" sign.If upgrade on primary is done using NSM, the attack database will be stored at location /var/db/idpd/nsm-download/. In this case use:%rcp -r -T /var/db/idpd/nsm-download/* node1:/var/db/idpd/sec-download/ 4.Once it completes, then go the CLI and type this command:[primary node0]>request security idp security-package install node 1If policy-templates are being used, then also run this command:>request security idp security-package install policy-templates node 1 5. Check the installation status using the command:[primary node0]>request security idp security-package install status6. After the completion of the installation, verify the IDP security package in node 1 using the command:[primary node0]>show security idp security-package-versionThis will give you the complete details about the package installed.For example:root> show security idp security-package-versionnode0:--------------------------------------------------------------------------Attack database version:2108(Thu Mar 29 12:47:45 2012)Detector version :12.6.160120213Policy template version :2108node1:--------------------------------------------------------------------------Attack database version:2108(Thu Mar 29 12:47:45 2012)Detector version :12.6.160120213Policy template version :2108[SRX/J] How to update IDP signature database automatically ona SRX or J-Series deviceSUMMARY:This article explains how to update an IDP signature database automatically on a SRX or J-Seriesdevice.For other IDP related articles, refer to KB16561.PROBLEM OR GOAL:Is there a way to set up the signature database download to happen at a specific time?SOLUTION:This section contains the following:JWebConfigurationThis example will configure the SRX to download the signature database once a week, with the first automatic download starting on the 10th of Jan at 2:00am.1. Select Configure>Security>IDP>Signature Update.2. Click the Download tab.3. Click the Security Package Automatic Download Settings link.4. In the URL field, leave it blank and the SRX will use the predefined default URL.5. In the Start Time field, enter 01-10.02:006. In the Interval field, enter 1687. Click the "Enable Schedule Update".8. Click OK.9. Click Apply and commit the changes.CLI Configuration1. Specify the URL for the security package:root# set security idp security-package urlhttps:///cgi-bin/index.cgiIMPORTANT:The URL stated above is correct. The URL, i.e. , specified in the some versions of the documentation is not correct. Please use the URL above.2. Specify the time and interval for the automatic download:root# set security idp security-package automatic interval <hours> start-time <the start of the first download>For example, to set the download to happen after three days, with the first automatic downloadingstarting on 14th July at 2:00 AM:root# set security idp security-package automatic interval 72 start-time 2013-07-14.02:00:003. Enable the automatic download:root# set security idp security-package automatic enableNOTES:∙If you have configured the device for automatic signature DB download, the new signature database is downloaded and installed.∙If there is a running IDP policy in the device, the policy is recompiled with the new signatures and pushed to the data plane.Similarly, if there is an existing running IDP policy and the previously installed detector's version is different from the newly downloaded one, then the newly downloaded detector is pushed to the data plane.Technical DocumentationFor more information on this refer to Updating the Signature Database Automatically.VerificationThe following command shows the configuration of the automatic download of the IDP security package:root@SRX210-HM> show configuration security idp security-packageautomatic {start-time "2013-7-14.02:00:00 +0000";interval 72;enable;}The following command shows the version of the attack-db installed:root@SRX210> show security idp security-package-versionAttack database version:1581(Tue Jan 12 12:43:22 2010)Detector version :10.2.160091104Policy template version :2The following command shows if the scheduled update started without any errors:root@SRX210> show log messages | match “Scheduled update”Jan 25 14:47:37 SRX210-HM idpd[982]: IDP_SCHEDULED_UPDATE_STARTED: Scheduled update has started(at Mon Jan 25 14:47:37 2010 )[SRX] IDP Attack Database download failureSUMMARY:The common reasons for IDP attack database download failures on a SRX device are listed.This article is referenced from the KB23422 - Resolution Guide - SRX - Verify/Troubleshoot IDP attack database on SRX.PROBLEM OR GOAL:When checking the status of the Attack database download with the request security idpsecurity-package download status command, the following error message is reported:user@srx> request security idp security-package download statusDone;fetching/uncompressing for....failedNote: If the Attack Database install failed, a common reason is that the AttackDatabase download also failed.CAUSE:This error message can be caused by multiple issues. The scenarios, which might cause the above error, can be broadly classified as follows:∙The SRX device does not have Internet connectivity.∙The DNS server is not configured on the SRX device.∙The SRX device does not have access to the SIG DB server.∙Storage space in the Compact Flash is full.SOLUTION:If the Attack database download fails, perform the following checks (these are the common failurereasons).Verify if the SRX device has Internet connectivity:1. Check if the ISP's next hop router/default gateway can be pinged from the SRX device.2. Check if an active route pointing to the ISP's next hop router is present in the SRX device's routing table:root> show route <IP address of the SRX'S default gateway>If an active route is absent, configure a static route to the ISP's router. For example:root# set routing-options static route 0/0 next-hop <ISP routers IP address>root# commit3. Check the state of the SRX device's egress interface to confirm that the link is physically up:root> show interfaces <interface name> terseVerify if the SRX device has the name-server configured:If the SRX does not have a name-server configured, then it can be configured as follows:root# set system name-server <Name Servers IP address>Verify if the SRX device's Signature Database server is configured:The URL for the Signature Database is configured as follows:root# set security idp security-package url https:///cgi-bin/index.cgiroot# commitVerify if the storage space in the Compact flash is not full:Check the storage space by using the following command:root> show system storageIf the space is full, perform a cleanup process and remove all the non-operational files from the Compact Flash. The set of non-operational files can be viewed by running the following command:root> request system storage clean up dry-runTo remove all such files, run the following command:root> request system storage clean up[SRX] How to install IDP update/database manually when internet is not at your reach [Transfer of IDP database from SRX to SRX]SUMMARY:How to install IDP update/database manually when Internet is not at your reach [Transfer of IDP database from SRX to SRX]PROBLEM OR GOAL:This article explains how to use a pre-installed IDP database in one SRX and have it installed in another one with help of a USB memory stick.SOLUTION:Perform the following steps:Mount the USB upon the /mnt mount-point in SRX1. Take an available SRX (Branch for a Branch and HighEnd for a HighEnd) in which IDP is pre-installed.Note: It must be running the same version of Junos.2. Plug in a USB stick into a USB slot. The USB should show itself on console as device da0: or da1 or da2etc. (Let us assume we get device id: da1 for the USB).3. Mount the USB using the shell command:%mount -t msdosfs /dev/da1s1 /mnt4. If the above command does work, make sure the USB was formatted in FAT / FAT32 / NTFS file systemusing a MS Windows desktop.Plug it again into the SRX and notice the device id, lets say we again get it as da1.Then try the step 3 command again. If it does not work, try the shell command below.%mount -t msdosfs /dev/da1 /mntThis will mount your USB to mount point /mntCopy the IDP database to the USB5. From the CLI, copy the downloaded IDP Database into the USB using the command:file copy /var/db/idpd/sec-download/* /mnt/6. Remove the USB from the SRX.Copy the IDP database into the other SRX in question:7. Mount the USB onto the new SRX, using the mounting steps 1 to 4 mentioned above.8. From the CLI , copy the database from the USB into the required directory using the command:file copy /mnt/* /var/db/idpd/sec-download/Install the Database:9. From the CLI, issue the following command to fetch the database fom the /var/db/idpd/sec-download/directory:request security idp security-package install10. Check the installation status using the command:request security idp security-package install status11. Check the installed status of the IDP package using the command:show security idpsecurity-package-versionandshow security idp statusThis will complete your offline IDP database update using another SRX.。
天融信IDP

图 2-1 多核并行处理架构示意图
2.2 精确的基于目标系统的流重组检测引擎
传统的基于单个数据包检测的入侵防御产品无法有效抵御 TCP 流分段重叠的攻击,任 何一个攻击行为通过简单的 TCP 流分段组合即可轻松穿透这种引擎,在受保护的目标服务 器主机上形成真正的攻击。TopIDP 产品采用了先进的基于目标系统的流重组检测引擎,首 先对到达的 TCP 数据包按照其目标服务器主机的操作系统类型进行流重组,然后对重组后 的完整数据进行攻击检测,从而从根源上彻底阻断了 TCP 流分段重叠攻击行为。
TopIDP 产品能够统计分析内网用户的上网行为,限制对恶意网站或者潜在不安全站点 的访问,通过与智能应用协议识别功能相结合,可以制定有效的管理策略,实现内网用户 的上网行为管理。TopIDP 产品具备内网主机监控功能,能够实时监测到每一个内网主机(以 ip 地址为标识)的各种应用流量、以及累积访问各类 URL 地址的数量,在网络中出现问题 时能够快速定位到问题源头(内网主机用户),可以有效威慑和遏制内网用户的各种违反 安全策略行为。
网络卫士入侵防御系统 TopIDP 产品说明
版权声明
本手册的所有内容,其版权属于北京天融信公司(以下简称天融信)所有, 未经天融信许可,任何人不得仿制、拷贝、转译或任意引用。本手册没有任何形 式的担保、立场倾向或其他暗示。
若因本手册或其所提到的任何信息引起的直接或间接的资料流失、利益损失, 天融信及其员工恕不承担任何责任。本手册所提到的产品规格及资讯仅供参考, 有关内容可能会随时更新,天融信恕不承担另行通知之义务。
图23cve兼容认证示意图24智能的应用协议识别能力topidp产品能够识别包括传统协议p2p下载股票交易即时通讯流媒体网络游戏网络视频等在内的10大类超过150种网络应用并能够详细统计每一种应用的流量天融信网络卫士入侵防御系统topidp系列产品说明天融信公司连接数和累积传输字节数使用户很容易判断网络中的各种带宽滥用行为继而采取包括阻断限制连接数限制流量等各种控制手段确保网络业务通畅
dlink基本配置命令

dlink基本配置命令dlink配置基本命令一、查看交换机的参数:show switch二、查看某个端口的流量:show packet ports 7三、查看某个端口的错误传输状态:show error ports 7四、禁止或启用端口:1、启用第七个端口config ports 7 state enable2、禁用第七个端口config ports 7 state disable五、配置端口模式:1、配置第7个端口的模式为自适应config ports 7 speed auto2、配置第7个端口的模式为10M半双工config ports 7 speed 10_half3、配置第7个端口的模式为100M半双工config ports 7 speed 100_half4、配置第7个端口的模式为10M全双工config ports 7 speed 10_full5、配置第7个端口的模式为100M全双工config ports 7 speed 100_fu六、配置带宽限制:1、配置第7个端口的收发速率均为1M,rx_rate为收,tx_rate为发config bandwidth_control 7 rx_rate 1 tx_rate 12、配置第7个端口的收发速率均无限制config bandwidth_control 7 rx_rate no_limit tx_rate no_limit七、创建交换机的用户名和密码1、创建一个角色为管理员,用户名为admin的用户create account admin(用户角色) admin(用户名)会提示输入密码2、修改用户名为admin的密码config account admin(用户名)会提示输入旧密码和新密码3、删除用户名为admin的用户delete account admin(用户名)八、配置SNMP服务1、创建访问此交换机snmp服务的密码create snmp community colorme(密码) view CommunityView read_only九、禁止或启用一些服务1、启用web服务enable web2、禁用web服务disable web3、启用telnet服务enable telnet4、禁用telnet服务disable telnet十、修改系统默认的Ip地址config ipif System ipaddress 192.168.1.242/24 vlan default state enable十一、配置Vlan命令:创建:create vlan [Vname] tag [VID]{1-101}删除:config vlan [Vname] delete [Ports]{1-26}给Vlan配置端口:config vlan [Vname] add untagged[Ports]{1-26}保存:Saveconfig vlan default delete 1-28config vlan default advertisement enablecreate vlan VLAN172 tag 172 advertisementconfig vlan VLAN172 add tagged 25-28config vlan VLAN172 add untagged 13-24create vlan VLAN192 tag 192 advertisementconfig vlan VLAN192 add tagged 25-28config vlan VLAN192 add untagged 1-12config ipif System ipaddress 172.31.213.252/24 vlan VLAN172 state enablecreate iproute default 172.31.213.254 1save all。
夏普IDP显示器产品培训

是
接口
有HDMI、有LAN、有S-Video
有DVI环出、RS232环出
音频控制
组合通道
独立通道
针对市三菱 夏普 优派
02
行业竞争品牌分析
01
松下等离子
尺寸:42-50-58-65-103 最大优势:灵活的接口设计。 主要劣势:等离子本身的缺陷(单独分析)
02
1200:1
亮度
450cd/㎡
400cd/㎡
500cd/㎡
500cd/㎡
500cd/㎡
450cd/㎡
视角
176°/176°
176°/176°
176°/176°
176°/176°
176°/176°
178°/178°
响应时间
6ms
6ms
16ms
8ms
6ms
8ms
背光灯
可以更换
不可以换
不可以换
不可以换
不可以换
二、PN系列产品介绍
灵活的图像格式 用内置屏幕图像功能可以动态性再现大量的信息。可以将来自PC 的数码信号以及AV信号以“画中画”(PIP)和“画外画”(PbyP)的形式播出放,也可以创建“2×2”,“3×3”,“4×4”和“5×5”的视频墙面。
端子
PN系列产品介绍
应用案例
歌华有线总前端项目
应用案例
谢谢!
添加副标题
汇报人姓名
技术特点
应用案例 最高人民法院会议系统
PN系列产品介绍
1080P全高清ASV黑色TFT显示器
PN系列产品介绍
为商业用途而设计 7×24小时全天候工作 它采用高可靠性的零部件以及高散热性的机体设计,因此性能十分可靠,适用于各种商业和工业用途。 纵向使用 根据操作的内容和信息,夏普提供可横 向使用和纵向使用的液晶显示器。
juniperIDP800配置手册及实例new

JUNIPER IDP配置手册1、IDP的初始化设置 (3)IDP sensor的初始化设置 (3)IDP模块的安装方法 (13)2、IDP的策略配置 (14)在NSM中寻找IDP设备和模块 (14)配置IDP的策略 (17)IDP配置实例 (22)IDP的入侵保护策略配置实例 (22)IDP防网络扫描配置实例 (23)IDP防SYN配置实例 (23)IDP特征库的升级 (24)查看IDP sensor的状态 (26)1、IDP的初始化设置IDP sensor的初始化设置加电以后,sensro开始启动,过了几分钟,设备就会启动完毕。
用网线连接电脑和sensor 的MGT接口,默认的IP地址是192.168.1.1,通过https://192.168.1.1/登录sensor的ACM管理界面。
默认的用户名和密码分别是root和abc123。
采用ACM方式配置,并修改IDP sensor 的工作模式等IDP sensor设置,登录进去以后会显示以下的界面,点击ACM可以开始配置IDP sensor;1.1.1、修改root和admin的密码,在使用NSM寻找sensor的时候需要使用。
(NSM服务器查找IDP sensor的时候会查询admin用户名,admin密码和root密码)1.1.2、修改设备的名字和域名,1.1.3、修改IDP的部署模式,可以根据实际情况选择相应的工作模式,如sniffor,bridge,transparent等,若选择transparent模式,可以选择bypass功能(限电口,IDP 800和IDP 8200有光纤BYPASS模块)。
PS:BYPASS功能是指在IDP掉电或出现问题后,IDP的两个接口是直通的状态,BYPASS切换一半需要5秒左右,设备不同时间会不一样1.1.4、配置IDP的HA模式,若IDP都有自带的HA专用接口。
1.1.5、配置网络接口,若修改工作模式,则需要重启IDP才可以生效。
Juniper IDP防御配置手册

SRX IDP防御配置手册2013Nicolash Qi目录IDP 学习心得 (1)一.IDP策略 (3)1.1 简介 (3)1.2 规则 (3)1.3 配置 (5)1.4 协议解码器 (6)1.5 内容解压缩 (7)1.6 自定义攻击 (7)二.IDP特征数据库 (10)2.1 简介 (10)2.2 管理特征数据库 (10)2.3 更新数据库 (10)2.4 预定义策略模板 (11)2.5 使用预定义模板 (12)三.应用层DDOS攻防 (13)3.1 简介 (13)3.2 应用层DDos参数(配置application-ddos参数) (14)3.3 应用层规则参数 (14)3.4 应用层DDos IP 操作 (15)3.5 应用层DDos规则操作 (15)3.6 配置实例(DNS) (15)四.IDP性能调整 (17)五.IDP日志 (17)一.IDP策略1.1 简介IDP策略定义了设备处理网络信息流的方式,对经过设备的流量实施各种攻击检查和防御技术。
IDP策略可以包含多个规则库,规则库可以包含多个规则,每一个规则定义了一组特定的攻击和防御的参数,网络流量匹配这些规则参数,则被认定为一个攻击。
可以定义多个IDP策略,但只有一个生效。
默认情况下IDP功能是启用的,不需要许可证,只是无法更新特征数据库和IDP策略模板,可以自己定义IDP的攻击。
注意:Branch 系列只支持 L3模式部署,Data center 支持L2/L3模式部署1.2 规则规则由如下几个部分组成:规则匹配条件规则对象规则操作规则通知1.规则匹配条件源/目区段——所有信息流从源区段传输到目标区段。
可选择任意区段充当源或目标。
源/目IP地址——指定网络信息流发起的源IP 地址。
可指定source-except 来指定除指定地址之外的所有源。
应用——指定目标IP 地址支持的应用层协议。
2.规则对象对象是可应用于规则的可重用逻辑实体。
D-LINK网络交换机的CLI的配置说明书

D-LINK网络交换机的CLI的配置说明书D-LINK网络交换机的CLI的配置说明书Show 命令可以查看交换机的各项的配置(交换机无法查看整体的当前和保存的配置信息)Create 命令可以创建交换的信息Config 命令可以对这些参数进行配置Delete命令可以删除所配制的参数Reboot 命令对交换机进行重新启动Save 命令保存交换机的配置信息的修改Reset 命令清空配置信息reset system 不仅清空运行时配置,还将把曾经保存过的配置全部清空,reset config仅清空运行时配置.Create account [admin|user]<username> 创建admin或user 级别的用户,回车输入两次密码创建输入为空密码Create account <username> 修改已创建的username用户,回车输入旧密码,在输入两次新密码Show account 可以看到你所创建的用户Show switch 可以查看交换机的信息Show iproute 查看路由表Show vlan 查看VLAN条目[enable|disable] telnet 23 此命令开启|删除telnet功能enable mac_notification 默认是关闭MAC地址通告的show ipif 查看交换机的配置接口信息config ipif System ipaddress 10.1.1.1/8修改System接口的IP地址注意接口名System的大小写备份/恢复配置download configuration 192.168.0.157 c:/xuekang/setting.txt 从192.168.0.157上下载配置文件upload configuration 192.168.0.157 c:/xuekang/setting.txt 到192.168.0.157上上穿配置文件端口镜像的设定config mirror port 1:5 [add|delete] sourece port 1:1-1:5 把1-5断口加到5端口上做镜像(默认关闭)链路聚合配置create link_aggregation group_id 1 创建一个聚合组1config link_aggregation group_id 1 master_port 5 ports 5-7,9创建MAC地址的绑定create arpentry 192.168.0.157 00-56-b5-45-B5-4H 为主机绑定IPdelete arpentry 192.168.0.157 删除IP的绑定show arpentry 查看某些主机的绑定CLI SWITCH LAYER3 VLAN 设定(以下Command 請注意大小寫)config vlan default delete 1-24 ->将default Vlan 移除,否則Port 在不带tag 的狀況下,将無法继续以下的Vlan 設定。
IDP-1 IDP-2 IDP INFINITY D Process Meter 操作手册说明书

IDP-1IDP-2IDPINFINITY®D Process Meter Operator’s Manual®NEWPORT Electronics,Inc./manualsCountersFrequency MetersPID ControllersClock/TimersPrintersProcess MetersOn/Off ControllersRecordersRelative HumidityTransmittersThermocouplesThermistorsWire Rate Meters Timers Totalizers Strain Gauge Meters Voltmeters Multimeters Soldering Iron Testers pH pens pH Controllers pH Electrodes RTDs Thermowells Flow SensorsFor Immediate AssistanceIn the U.S.A. and Canada: 1-800-NEWPORT ®In Mexico: (95) 800-NEWPORT SM Or call your local NEWPORT Office.Additional products from®NEWPORT Electronics,Inc.It is the policy of NEWPORT to comply with all worldwide safety and EMC/EMI regulations that apply.NEWPORT is constantly pursuing certification of its products to the European New Approach Directives.NEWPORT will add the CE mark to every appropriate device upon certification.The information contained in this document is believed to be correct but NEWPORT Electronics, Inc. accepts no liability for any errors it contains, and reserves the right to alter specifications without notice.WARNING: These products are not designed for use in, and should not be used for, patient connected applications.PATENT NOTICE:The “Meter Case Bezel Design” is a trademark of NEWPORT Electronics,Inc., registered in the U.S.. This product is covered by one or more of the following patents: U.S. Pat. No. Des. 336,895; 5,274,577 / CANADA 2052599; 2052600 / ITALY 1249456; 1250938 / FRANCE BREVET No. 91 12756 / SPAIN 2039150; 2048066 / UK PATENT No. GB2 249 837; GB2 248 954 / GERMANY DE 41 34398 C2. OTHER INTERNATIONAL PATENTS PENDING.Guide before installing orTable of ContentsSection Page SEC 1INTRODUCTION. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11.1Unpacking. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11.2 Safety Considerations. . . . . . . . . . . . . . . . . . . . . . . . . . . 2 SEC2ABOUT THE METER. . . . . . . . . . . . . . . . . . . . . . . . . . 32.1Front of the Meter. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 32.2Back of the Meter. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52.3Disassembly. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6 SEC 3GETTING STARTED. . . . . . . . . . . . . . . . . . . . . . . . . . 73.1Changing Configuration Jumpers. . . . . . . . . . . . . . . . . . . 73.2Mounting the Meter. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 83.3Connecting Sensor Input. . . . . . . . . . . . . . . . . . . . . . . . . 93.4Connecting Main Power. . . . . . . . . . . . . . . . . . . . . . . . . 12 SEC 4CONFIGURING THE METER. . . . . . . . . . . . . . . . . 134.1Selecting the Input Range. . . . . . . . . . . . . . . . . . . . . . . 134.2Selecting a Decimal Point Position. . . . . . . . . . . . . . . . . 144.3Scaling the Meter. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 144.3.1Internal Scaling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 154.3.2Live Scaling . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 164.4Changing the Meter’s Calibration. . . . . . . . . . . . . . . . . . 17 APPENDICESA Checking and Changing Main Board Power Jumpers. . . 19B Reference Tables. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21C Specifications. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23D CE Information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 25List of FiguresFigures Page2-1Front-Panel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .32-2 Connectors (ac-Powered and dc-Powered) . . . . . . . . . . . . . . .52-3dc-Power Connections . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .63-1S1 - S4 Jumpers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .83-2Meter - Exploded View . . . . . . . . . . . . . . . . . . . . . . . . . . . . .83-3Panel Cut-Out . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .93-43-Wire dc V oltage Input Connectionswith Internal Excitation . . . . . . . . . . . . . . . . . . . . . . . . . . . . .93-52-Wire dc V oltage Input Connectionswith External Excitation . . . . . . . . . . . . . . . . . . . . . . . . . . .103-64-20 mA Input Connections with External Excitation . . . . . .103-74-20 mA Transmitter Hook-Up with Internal Excitation . . . .113-8dc Current Input Connections with Current Source . . . . . . .113-9Main Power Connections ac . . . . . . . . . . . . . . . . . . . . . . . .123-10Main Power Connections dc . . . . . . . . . . . . . . . . . . . . . . . .12A-1115Vac Jumper Wiring (default) . . . . . . . . . . . . . . . . . . . . . .19A-2230 Vac Jumper Wiring . . . . . . . . . . . . . . . . . . . . . . . . . . . .20C-1Meter Dimensions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .24List of TablesTable Page2-1Connector Description. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53-1S1 - S4 DIP Switches. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 73-2ac Power Connections. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12 4-1Meter Calibration Table. . . . . . . . . . . . . . . . . . . . . . . . . . . . 18B-1Display Messages. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 211B-2Menu Configuration Displays. . . . . . . . . . . . . . . . . . . . . . . 2 B-3Run Mode Displays. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22B-4Factory Preset Values. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 22NOTESSECTION 1. INTRODUCTION1.1 UNPACKINGRemove the Packing List and verify that you have received all equipment. If there are any questions about the shipment, use the phone numbers listed on the back cover to contact the Customer Service Department nearest you.Upon receipt of shipment, inspect the container and equipment for any signs of damage. Note any evidence of rough handling in transit. Immediately report any damage to the shipping agent.The carrier will not honor any claims unless all shipping material issaved for their examination. After examining and removing contents,save packing material and carton in the event reshipment is necessary. Verify that you receive the following items in the shipping box:QTY DESCRIPTION1Programmable indicator/controller with all applicable connectors attached.1Owner’s Manual1Quick Start ManualIf you ordered any of the available options (except the “BL”blank Lensoption), they will be shipped in a separate container to avoid anydamage to your indicator/controler.SECTION 4. CONFIGURING THE METER4.1 SELECTING THE INPUT RANGE (INPT)Refer to Table B-2 for a summary list of menu configuration.To select your appropriate input range, follow these steps:1.Press the MENU button. The meter flashes “InP”.2.Press the ¢/TARE button. The meter flashes one of the following:*0 - 10 (for 0-10 volt)* 4 - 20 (for 4-20 mA)*20 - 4 (for 20-4 mA)*0 - 5 (for 0-5 volt)* 1 - 5 (for 1-5 volt)3.Press the ¢/TARE button to scroll through available choices.4.Press the MENU button to store your choice. The meter momentarilyshows “StOr”, followed by “dEc.P”(Decimal point).4.2 SELECTING A DECIMAL POINT POSITION (DEC.P)Refer to Table B-2 for a summary list of menu configuration.To select a decimal point display position, follow these steps:1.Press the MENU button until the meter shows “dEc.P”.2.Press the ¢/TARE button. The meter shows one of the following:*FFF.F*FFFF.*FFFF* F.FFF*FF.FF3.Press the ¢/TARE button to move the decimal point to the right oneposition.4.Press the MENU button to store your choice. The meter momentarilyshows “Stor”, followed by “ScAL” (Scaling).4.3 SCALING THE METERThere are two scaling methods. One method is internal scaling, “int”(scaling without known loads): you decide upon low and high reading values and manually enter them through the keyboard. The meter then operates with those new parameters. Another method is live scaling, “LivE”: you apply low and high input signals and change the meter reading accordingly. The meter calculates a new scale factor and then operates with those new parameters.4.3.1 Internal ScalingUse internal scaling if you do not have an actual input signal to the meter. With internal scaling the input values are assumed to be the low and high signal input based on the selection input (e.g. if you selected 4-20 mA input, the “rd1” input value will be 0400 for 4 mA and “rd2” will be 2000 for 20 mA). All you need to do is change what the meter should read at these two points. For internal scaling, follow these steps:Refer to Table B-2 for a summary list of menu configuration.1.Press the MENU button until the meter flashes “ScAL”.2.Press the ¢/TARE button until the meter shows “int”.3.Press the £/MAX button. The meter momentarily flashes “rd1”(read1), then shows the low input value based on the selected input range (e.g.if the input range is 0 - 10 V, the meter shows “0000”, or if input range is 4-20 mA, the meter shows “0400”).4.Enter the desired reading for this low input value using the £/MAX and¢/TARE buttons.5.Press the MENU button for the meter to accept the new value. The meterthen momentarily flashes “rd2”, then shows the high input value based on the selected input range (e.g. if the input range is 0 - 10 V, the meter shows “9999”or if the input range is 4-20 mA, the meter shows “2000” ).6.Enter the desired reading for this high input value using the £/MAX and¢/TARE buttons.7.Press the MENU button for the meter to accept the new value, savechanges and return to the run mode. The meter shows “Stor”andcalculates the new scale factor based on the new high and low values. 8.If the display is not zero with no load on your sensor, press the ¢/TAREbutton. Scaling is now complete.4.3.2 Live ScalingUse live scaling when a stable input source is available (e.g. 4-20 mA or voltage calibrator). Also use live scaling when the actual input from your sensor can be set to output values close to the low and high ends of your input. For live scaling, follow these steps:Refer to Table B-2 for a summary list of menu configuration.1.Press the MENU button until the meter flashes “ScAL”.2.Press the ¢/TARE button until the meter shows “LivE”.3.Press the £/MAX button. The meter momentarily flashes “rd1”.4.Apply the low input signal to the input. The meter then shows the livelow input source.5.Change the meter reading as required for the applied low input using the£/MAX and ¢/TARE buttons.6.Press the MENU button for the meter to accept the new value. Themeter then momentarily flashes “rd2”.7.Apply the high input signal to the input. The meter then shows the livehigh input source.8.Change the meter reading as required for the applied high input using the£/MAX and ¢/TARE buttons.9.Press the MENU button to save changes and return to the run mode.The meter shows “Stor”and calculates the new scale factor based on the new high and low values.APPENDIX BREFERENCE TABLESTable B-1. Display Messages* Represents any valueTable B-2. Menu Configuration Displays MENU¢/TARE£/MAXInP0-104-2020-40-51-5DEC.P FFF.FFFFF.FFFFF.FFFFF.FFScAL intLivE rd 1*XXXXrd 2*XXXX * Not displayed unless you press the £/MAX key.APPENDIX CSPECIFICATIONSAnalog Input Ranges: 4-20 mA, 0-5 Vdc, 1-5 Vdc, 0-10 VdcInput Impedance:V oltage: 1.0 MegCurrent: 100 ΩIsolation:Dielectric strength to 2500V transient per 3mmspacing base on EN61010 for 260Vrms or dcworking voltageAccuracy:0.05%R +/- LSBTempco:+/- 50 PPM/°CExcitation V oltage:24 Vdc @ 25mA10 Vdc @ 25mADisplay:LED 7-segment, 14.2 mm (0.56”)Range: +9999 to -1999Decimal Point: 4 positionsInput Power Information:V oltage ac:115/230 Vrms ±10%dc:9-32Vdc (Isolated up to 300 Vp)Power: 1.5 watt Excitation Unloaded2.5 Watts Maximum (with 20mA excitation load) Frequency:50/60 HzExternal Fuse Protection Recommended:ac 115V UL slow blow, 40mA, 250Vac 230V UL slow blow, 20mA, 250VEnvironment:Operating Temperature:0°to 60°C (32°to 140°F)Storage Temperature:-40°to 85°C (-40°to 185°F)Relative Humidity:95% at 40°C (non-condensing)MechanicalPanel Cutout: DIN 4896-100 / 1.77 x 3.66” (45 x 92 mm) Depth Behind Bezel: 3.94 in (100 mm)Weight:11 oz (312 g)Case Material:Polycarbonate, 94 V-O UL ratedExternal Features:Tare, Display Hold, Tare ResetCalibrationand the S4 jumper 7changing 17, 18installing/removing calibration jumper 6 Configuration jumperschanging 7, 8Configuration mode 3escaping from 4RESET button 4ßMAX button 4∂TARE button 4Connecting sensor input 9-11Connector label 5dc-power 62-wire voltage input connections 103-wire voltage input connection 9connectors 5, 6current input connections 11Decimal pointdisregarding in meter calibration 18factory default 20selecting 14Disassembly 6Front-panel buttonsMENU 4RESET4T-RST4ßMAX 4∂TARE 4Input rangeand internal scaling 15calibrating 17factory default 20selecting 13Installing the meter 9Internal scaling 15Live scaling 16Main board power jumpers 23, 24 MENU button 4Meter modesconfiguration mode 3run mode 3micro controller revision codeaccessing 7Mounting the meter 9RESET button 4Resetting peak and valley registers 4, 20 Run mode 3MENU button 4RESET button 4ßMAX button 4∂TARE button 4S1, S2 & S3 DIP switcheschanging 7Scalingerror message 19internal 14, 15live 14, 16Scaling without known loads 14, 15 Sensor excitationfactory default 20Sensor input 9-11connecting 9-11T-RST button 4V oltage calibratorand live scaling 16ßMAX button 4∂TARE button 4For immediate technical or application assistance please call:Newport Electronics, Inc.2229 South Yale Street • Santa Ana, CA • 92704 • U.S.A.TEL: (714) 540-4914 • FAX: (203) 968-7311TollFree:1-800-639-7678••e-mail:******************ISO 9001 CertifiedNewport Technologies, Inc.976 Bergar • Laval (Quebec) • H7L 5A1 • CanadaTEL: (514) 335-3183 • FAX: (514) 856-6886TollFree:1-800-639-7678•www.newport.ca•e-mail:***************Newport Electronics, Ltd.One Omega Drive • River Bend Technology CentreNorthbank, Irlam • Manchester M44 5BD • United KingdomTel: +44 161 777 6611 • FAX: +44 161 777 6622TollFree:0800488488••e-mail:******************.ukNewport Electronics B.V. - BeneluxTEL: +31 20 3472121 • FAX: +31 20 6434643TollFree:08000993344•www.newport.nl•e-mail:***************Newport Electronics spol s.r.o.Frystatska 184, 733 01 Karviná • Czech RepublicTEL: +420 59 6311899 • FAX: +420 59 6311114TollFree:0800-1-66342•www.newport.cz•e-mail:***************Newport Electronics GmbHDaimlerstrasse 26 • D-75392 Deckenpfronn • GermanyTEL: 49 7056 9398-0 • FAX: 49 7056 9398-29TollFree:0800/6397678•www.newport.de•e-mail:****************Newport Electronique S.A.R.L. - FranceTEL: +33 1 61 37 29 00 • FAX: +33 1 30 57 54 27TollFree:0800466342•www.newport.fr•e-mail:****************Mexico and Latin AmericaFAX: 001 (203) 359-7807TEL En Español: 001 (203) 359-7803M1866/030712160ML-01 Rev. KIDP-1IDP-2。
Juniper-IDP配置手册

Juniper Netscreen IDP配置手册目录一、理解IDP (3)1.三层架构 (3)2.部署模式 (3)二、安装并配置IDP Management Server, IDP sensor ,UI (3)1.确定部署模式 (3)2.安装Management Server (3)3.安装Sensor (4)三、连接IDP Sensor至网络 (5)四、安装用户管理界面(UI) (5)五、配置Management Server (5)1.打开UI,出现如下界面: (5)2.增加objects(sensor,networks,host等等)。
(6)六、配置安全策略 (7)1.Click Security policies->File->New Policy (7)2.Select Default Template,type Security Policy Nmae。
(9)七、运行企业安全事件探查器 (9)一、理解IDP1.三层架构●IDP Sensor::用于监控并且处理网络流量。
●IDP Management Server:用于存储所有的网络对象,日志,报表,安全策略、规则等。
●IDP User Interface (UI):运行在客户端PC的图形化管理系统,用于连接Management Server,处理存储在Management Server的日志,报表;处理并分发安全策略到Sensor。
2.部署模式●桥接和透明模式●ARP代理模式●路由模式●侦听模式二、安装并配置IDP Management Server, IDP sensor ,UI1. 确定部署模式2. 安装Management Server系统平台要求:RedHat Linux 7 或8Solaris 8 或9系统硬件要求:CPU: Quad Intel(R) Xeon(TM), 2.40GHzCache size: 512 KBMemTotal: 2GBHard Disk: 32.5 GB●以root用户身份登陆到Linux,必要时使用su 命令更改身份。
个人发展计划 idp 实例

个人发展计划 idp 实例个人发展计划(IDP)实例引言:个人发展计划(IDP)是指为了实现个人职业发展目标和提升自己能力而制定的一项计划。
通过制定个人发展计划,我们可以清晰地了解自己的优势和劣势,并设定明确的目标和行动计划,以不断提升自己的能力和实现个人发展。
一、自我评估在制定个人发展计划之前,首先要进行自我评估。
通过认真分析自己的优势、劣势、机会和威胁,了解自己的职业兴趣、价值观和目标,以及现阶段所面临的挑战和需要提升的能力。
二、设定职业发展目标根据自我评估的结果,制定明确的职业发展目标。
职业发展目标应该具备可衡量性和可实现性。
例如,短期目标可以是提升某个具体技能,长期目标可以是晋升到某个职位或拥有自己的企业。
三、制定行动计划根据职业发展目标,制定具体的行动计划。
行动计划应该包括具体的步骤、时间表和资源需求。
例如,如果目标是提升某个技能,行动计划可以包括学习相关知识、参加培训课程或寻找导师等。
四、学习与发展个人发展计划的核心是学习与发展。
在行动计划的基础上,制定学习计划,包括学习的内容、学习的方式和学习的时间安排。
学习可以通过多种途径,如自学、参加培训课程、参加研讨会等。
同时,要不断反思和总结学习的经验,以不断提升自己的能力。
五、寻找导师和学习伙伴在个人发展过程中,寻找导师和学习伙伴能够帮助我们更好地学习和成长。
导师可以提供指导和建议,帮助我们规划职业发展路径;学习伙伴可以与我们共同学习和分享经验,互相促进成长。
六、积极参与项目和活动通过参与项目和活动,可以锻炼自己的能力并展示自己的价值。
可以选择与自己职业发展相关的项目和活动,积累工作经验和展示自己的能力。
同时,积极参与团队合作,培养良好的沟通和协作能力。
七、定期评估和调整个人发展计划需要定期评估和调整。
通过定期评估,可以了解自己的进展情况,及时调整行动计划和学习计划。
评估可以通过与导师、学习伙伴或自我评估的方式进行。
结语:个人发展计划是每个人职业生涯中不可或缺的一部分。
IDP模板
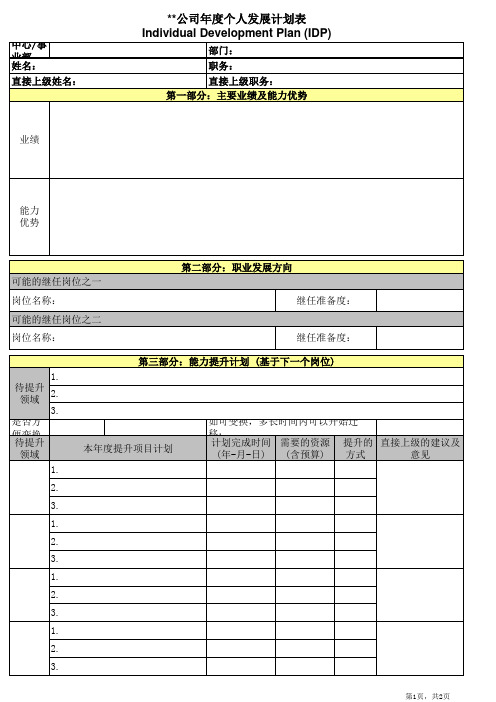
第2页,共2页
第二部分:职业发展方向 可能的继任岗位之一 岗位名称: 可能的继任岗位之二 岗位名称: 继任准备度: 第三部分:能力提升计划 (基于下一个岗位) 1. 待提升 2. 领域 3. 是否方便变换工作地点: 待提升 本年度提升项目计划 领域 1. 2. 3. 1. 2. 3. 1. 2. 3. 1. 2. 3.
本人签字: 直接上级的意见及建议:
日期:
年
月
日
直接上级签字:
日期:
年
月
日
第五部分:对年度执行情况的总结与评价 提升项 目 年度完成情况 尚存在的问题 下期拟改善/解决方向
本人的总结与评价:
本人签字: 直接上级的总结与评价:
日期:
年
月
日
直接上级签字:
日期:
年
月
日
说明:1.建议年度提升项目聚焦在3-5个 2.原则上,在职锻炼占总学习时间的70%,人际学习占20%,教育占10%
第1页,共2页
继任准备度:
如可变换,多长时间内可以开始迁移: 计划完成时间 需要的资源 提升的 直接上级的建议及 (年-月-日) (含预算) 方式 意见
**公司年度个人发展计划表 Individual Development Plan (IDP)
中心/事业部: 姓名: 直接上级姓名: 部门: 职务: 直接上级职务: 第四部分:本人和上级确认上述计划 本人的意见及建议:
待提升领域1223
**公司年度个人发展计划表 Individual Development Plan (IDP)
中心/事业部: 姓名: 直接上级姓名: 部门: 职务: 直接上级职务: 第一部分:主要业绩及能力优势
业绩
能力 优势
IDP流程操作细则

调查结果记录
调查展开
项 目 组 工 作 计 划 内 容
分 析 工 作 验 证 工 作 综 合 工 作
技术分析
需要的 功能分析
性能分析
形成分析报告
市场期望的 价格
市场分析
竞争环境
国家政策导向
验证
分析报告 是否正确
分析报告 有无遗漏
分析报告 有无过剩
汇总
技术综合 市场综合
初步技术规格 市场分析报告
概念方案
分析:有无遗漏 有无补充
站在系统角度上分析: 有无不周和漏洞
系统分析形成 〈项目市场分析报告〉 硬商品买卖在阿里巴巴 软商品交易在阿里巧巧
全面系统分析形成 〈项目技术分析报告〉
如何对分析报告进行验证和补充
流程
〈市场分析报告〉
〈技术分析报告〉 项目组组织市场部和 设计部成立联合调查组
再去向客户验证、 和标准、法规验证、 和其它厂家产品验证 走访用户 记录遗漏之处 记录修改之处 记录完善之处
研究所对《项目建议书》 的可行性进行初步的分析
研究所将《项目建议书》 送给网络厂领导研究决策
研究所将经过决策的 《项目建议书》取回
硬商品买卖在阿里巴巴 软商品交易在阿里巧巧
IPD流程操作指引--立项阶段(项目建议的决策结果)
不 同 意 立 项
《 项 目 建 议 书 》
被终止了, 气死了!
不同意立项!终止!
项目技术可行性结论
****项目
市场可行性分析报告
目录
1、项目技术可行性结论 2、项目市场业务规划和计 划书 3、项目市场分析报告 4、项目市场调查报告
综合:
〈项目市场业务规划和计划书》 《项目市场分析报告》 《项目市场调查报告》
IDP解决方案

XXX应用网站安全保护建议一、背景资料XXX应用网站承担…目前,网站没有设置基本的保护…二、面临的挑战及应对建议近两年来,来自每一个方面的资料显示出一个非常明显的结论,企业网络受到的内外威胁,尤其是导致网络和应用系统瘫痪的恶性事件,大部分来自于应用层的攻击,例如病毒、蠕虫和黑客攻击。
如何解决来自应用层威胁的问题,已经成了每一个需要实施网络安全系统的用户首先必须考虑解决的问题。
传统的网络防火墙主要解决:(1)网络二到四层的攻击和威胁问题;(2)安全区域的划分和隔离;(3)地址转换(NA T);等问题。
虽然有部分厂商的防火墙引入了应用层检测技术(目前最常用和成熟的技术是DI ———--—深层检测技术),但是受产品原型设计技术和硬件平台性能的限制,在相当长的一段时间内,防火墙产品还不能完全承担应用层的检测和保护重担,而且最终的产品功能还是要在应用层增加独立的防护系统.(以下的比较表格可以了解).面对目前最为头痛和急需应付的应用层威胁问题,应用网站应该在网络应用模式允许的情况下,在保证二到四层的防护基本具备的前提下,首先考虑实施应用层的保护系统,建议选用目前业内最为成熟的应用层保护系统—Juniper公司的IDP产品。
三、应用层保护系统的选择保护应用网站的关键是在网站的出入口实施相应的应用层网络安全控制系统,该系统在网络的出入口最大可能地实现:(1)拦截对网站构成严重威胁的恶意访问(包括未授权访问);(2)防止拒绝服务(DoS)攻击;(3)遏制和隔离病毒/蠕虫等恶意流量的攻击;(4)识别和拦截应用攻击;(5)防止非善意的网络侦察;(6)监控进出网站的访问和流量;(7)迅速定位来自内部的恶意流量源和未授权访问发起点。
1、应用层保护系统应该具备的技术和条件根据网站应用层保护系统(或俗称应用层防火墙)需要实现的目标,无论从功能上或技术上,应用层保护系统应该具备以下一些条件:(1)可以解读、分析网络层和应用层形态的网络流量数据包,使之具备检查应用层数据的基本能力,同时也可以分析网络层数据;(2)针对应用层数据报特征的多种检测技术——多重检测技术:●数据包状态签名技术和及时的更新提供●应用层协议异常检查技术●网络数据流量异常检查技术●后门检测技术●网络蜜罐引诱(反侦察)技术●网络哄骗检测技术●第二层攻击检测技术●同步泛洪检测技术●混合式攻击检测技术(3)可以不断更新和数量足够多的应用数据匹配特征库,并且提供客户化的匹配特征用户定制能力;(4)优化的策略设置功能,强大的事件跟踪和记录功能,为使用者提供完善的分析数据和报告.2、选择Juniper IDP无论从应用的要求、产品和功能的成熟程度,或者是技术先进性的角度考虑,选择Juniper 网络公司的IDP作为网站的保护系统是最为合适的选择.理由之一:Juniper 公司的IDP在业界内有多个“第一”,如下:1st –S ecurity device that detects and prevents attack by dropping malicious packets1st –M ulti—Method Detection (MMD)maximizes attack detection within a single product1st –S tateful Signature Detection (SSD)look for attacks in relevant traffic to reduce false alarms1st –C entralized, Rule-based Management for an Intrusion Detection Solution1st –S upport of All Instant Messaging Protocols to P rotect the Network from Potential-------------各类专业好文档,值得你下载,教育,管理,论文,制度,方案手册,应有尽有--------------Exploits理由之二:Juniper IDP 在所有同类产品的竞争对手中,是最为用户接受的产品,因此也就拥有最多的用户,如下第三方的统计报告结果:Juniper Networks – 1st in terms of units shipped (Source : Infonetics , 8/04) 在过去的一个季度,全球用户购买使用的每100台攻击防护系统中,有37台来自Juniper 公司的IDP.理由之三:IDP 在保护应用网站方面,具有传统防火墙不可比拟的优势,如下表:比较项IDP 防火墙 说明 工作模式 4种 3种 工作OSI 层次 2~7层 2~4层signature 是否开放式 是 否 开放模式的signature 允许客户查看、修改并触发响应方式signature 允许客户定制是 否 客户可以根据自己的需求来定制Signature 可集中管理 是 否 IDP Manager 可以管理10台以上IDP管理模式3层1层网络实时监控能力 强 一般IDP 可以解读100种应用层协议,并且有很强的日志记录功能,在做网络保护同时,是一个非常理想的网络实时监控和事件收集系统理由之四:Juniper IDP与防火墙相比较(即便是增加了DI功能的防火墙),有足够多的针对应用层的匹配比对特征数量,而且用户可以因应应用要求自定义特征,因此对于已知特征的攻击或是未知的攻击,IDP的防御效率远远超过防火墙.下表是IDP与对付应用层威胁能力最好的、带DI 功能的防火墙,在应付攻击特征种类和数量方面的比较.理由之五:Juniper IDP为用户提供强大的网络监控和记录功能,使用户能够及时了解网络状况,如访问流量、所使用的协议等等信息(详细见附件).附件:IDP产品简介Juniper网络公司入侵检测和防护(Juniper网络公司IDP)解决方案可提供在线攻击防护功能来防止蠕虫、病毒和特洛伊。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
JUNIPER IDP配置手册1、IDP的初始化设置 (3)IDP sensor的初始化设置 (3)IDP模块的安装方法 (13)2、IDP的策略配置 (14)在NSM中寻找IDP设备和模块 (14)配置IDP的策略 (17)IDP配置实例 (22)IDP的入侵保护策略配置实例 (22)IDP防网络扫描配置实例 (23)IDP防SYN配置实例 (23)IDP特征库的升级 (24)查看IDP sensor的状态 (26)1、IDP的初始化设置IDP sensor的初始化设置加电以后,sensro开始启动,过了几分钟,设备就会启动完毕。
用网线连接电脑和sensor 的MGT接口,默认的IP地址是192.168.1.1,通过https://192.168.1.1/登录sensor的ACM管理界面。
默认的用户名和密码分别是root和abc123。
采用ACM方式配置,并修改IDP sensor 的工作模式等IDP sensor设置,登录进去以后会显示以下的界面,点击ACM可以开始配置IDP sensor;1.1.1、修改root和admin的密码,在使用NSM寻找sensor的时候需要使用。
(NSM服务器查找IDP sensor的时候会查询admin用户名,admin密码和root密码)1.1.2、修改设备的名字和域名,1.1.3、修改IDP的部署模式,可以根据实际情况选择相应的工作模式,如sniffor,bridge,transparent等,若选择transparent模式,可以选择bypass功能(限电口,IDP 800和IDP 8200有光纤BYPASS模块)。
PS:BYPASS功能是指在IDP掉电或出现问题后,IDP的两个接口是直通的状态,BYPASS切换一般需要5秒左右,设备不同时间会不一样1.1.4、配置IDP的HA模式,若IDP都有自带的HA专用接口。
1.1.5、配置网络接口,若修改工作模式,则需要重启IDP才可以生效。
可能需要选择是否启动多个虚拟路由器,每两个接口属于一个虚拟路由器1.1.7、修改管理口的IP地址和管理口的网关,供NSM服务器和客户端远程连接使用,1.1.8、配置那些接口处于工作模式的状态下,以transparent为例,其他界面不同,但比较类似1.1.9、配置IDP MGT接口的静态路由和缺省网关(透明模式)输入缺省网关并选择对应的接口,若IDP为透明模式,则只需要做一个管理接口的网关即可;若为路由模式则需要在相应的接口做相应的网关1.1.10、DNS设置,设置IDP是否自动查询相关的域名,IDP特征库的升级是通过NSM服务器完成因此在配置NSM服务器时必须设置对应的DNS服务器,而IDP sensor则可以不设置;1.1.11、设置IDP的时间区域1.1.12、设置时间服务器NTP1.1.13、设置外置的Radius服务器,用户认证的时候使用1.1.14、SNMP设置,设置对应的SNMP服务器IP地址和端口号1.1.15、设置IDP的SSH访问,此功能必须开放,NSM服务器在查找IDP sensor的时候,首先是通过SSH获取IDP的SSH key;1.1.16、配置NSM服务器的IP地址和一次性密码,Device ID可以不填写,Primarynetscreen-Security Manager IP必须设置,通讯端口默认是7803,一次性密码(OTP)可以不设置。
NSM服务器查找IDP时使用了SSH KEY代替了OTP,因此可以不设置。
1.1.17、ACM配置,此处提示是否每次启动IDP管理的时候是否使用ACM模式以上配置完以后会出现汇总界面,并可以点击save & apply。
IDP会进行进程重启和修改自身的配置,需要几分钟的时间,如果修改了管理口的IP地址,还需要更改自身电脑的IP就可以重新连接IDP模块的安装方法Netscreen-ISG系列的防火墙的IDP模块安装,不需要进行上述的设置。
但该模块的设置都是通过NSM进行。
IP地址和路由都是依赖防火墙的路由和IP地址设置(注,IDP模块不支持sniffor模式)安装步骤:(以NS-ISG-2000为例)1.拆开防火墙NS-ISG-2000的机箱,在插槽的最后一个模块可以找到管理模块。
2. 管理模块上有两条内存,每条512M 。
将此内存拆下,然后将NS-ISG-1000-IKT 所带的内存,每条1GB 。
将内存装上,NS-ISG-2000的内存即为2G ,(增加了内存的ISG 系列防火墙并发会话数会增加一倍)3. 将NS-ISG-SEC 模块插入到机箱的其中一个插槽(不需要占用接口模块的槽位)4. 将NS-ISG-2000的版本升级到带IDP 功能的版本(如nsISG2000.5.4.0-IDP1.r9.0) 5. 将NS-ISG-SEC 的序列号和NS-ISG-2000-IKT 的认证码进行绑定生成license ,将此license导入防火墙中,重启防火墙。
此时防火墙会提示SCIO 和SCTOP 进行已经启动,设备的硬件安装已经完成。
2、IDP 的策略配置在NSM 中寻找IDP 设备和模块NSM 做为控制端,负责对IDP 进行配置和收集IDP 的日志等,有以下的几个功能(NSM 安装步骤另外写):1、 IDP 的策略是通过NSM 服务器上传到IDP sensor 中;2、 IDP 日志也是通过NSM 服务器进行保存安装了NSM 的postgresql 数据库中3、 IDP 的当前运行状态也会自动送到NSM 服务器上Slot 3 Mgt cardSlot 2-0Security Cards (扩展) ASIC CardI/O ModulesFan Card配置IDP sensor的第一步是去NSM的Device Manage r→Security Deivce中。
点击“+”添加设备模板。
并选择“Device”。
(NSM服务器安装过程见《NSM安装手册(DC版)》)在Device Name中输入设备模板的名字,在Color选择模板图标的颜色(名字和图标颜色只用于表示设备,没有实际意义)。
如果IDP已经配置好,则选择“device is reachable(i.e. static IP address)”。
并点击下一步输入IDP sensor的IP地址,admin用户名,密码和root的密码。
若设备是ISG+IDP。
则输入的admin用户名和密码均使用防火墙的用户名和密码。
在Connect To Device With 中选择使用什么协议和设备进行通讯,默认为SSHv2。
IDP和NSM通信的第二阶段则是通过DevSvr进程的7803端口通信点击下一步以后NSM服务器的DevSvr进程会按照实际情况去寻找设备。
找到设备以后,模板还没有设备的配置,只有设备的序列号等信息,因此需要在“Device→Configuration→Import Device Config”中导入现有设备的配置,则可以看到当前被导入设备的状态,序列号,软件版本等信息;或在新增的设备上双击鼠标左键,NSM 服务器会自动运行Import Device Config;配置IDP的策略IDP的策略配置是最为关键和要消耗较多的时间,IDP的策略包括以下几种1、IDP:入侵检测和保护的策略,主要针对来自应用层的攻击行为。
包括两种检查机制signature和anomaly2、Syn protector:syn泛滥保护策略,主要是针对通过IDP设备的SYN泛滥攻击3、Traffic anomaly:流量异常策略,主要是针对通过IDP的端口扫描4、Exempt:5、Backdoor:6、Honeypot :新建策略的时候是新建一整套的策略,具体的防护策略则在新建的策略里面添加在“Policy Manager→Security Policies”中点击右键,并选择New Policy输入名字和描述,并点击下一步选择Create new Policy for。
新建一套策略模板如果设备是防火墙ISG+IDP,则选择firewall/vpn Device。
如果设备是单独的IDP设备则选择Stand Alone IDP Devcies。
再次点击next以后选择安装到那台设备,可以暂时不选择,再点击next。
完成策略的模板设置。
若新建的是防火墙策略,则只出现防火墙部分,要增加IDP策略的时候则需要在‘+’那里选择add IDP Rulebase。
点击增加以后会出现一套IDP RULEBASE。
(其余honey pot,backdoor也是一样的设置)在source框中点击右键可以选择对应的地址,在attacks框中可以攻击特征库。
此时策略处于模板的形式,还没有安装到指定的设备上。
在“Install On”下面的“any”上点击右键,选择“Select Target”。
选择需要将此策略安装到指定的设备上。
策略新建完成以后需要进行保存。
保存好以后,选择“Device→Configuration→update Device Config”对该设备的配置进行升级。
IDP配置实例IDP的入侵保护策略配置实例本次配置的采用状态签名和协议异常的全部特征库,针对Metasploit发起的攻击进行检测,主要是针对IIS和SMB协议的攻击,配置图如下所示:本次因为两边的特征库不重叠,也就是策略1和策略2所引用的特征库都不一样,所以不需要选择Terminate Match。
如果是新手配置IDP,action可以配置recommand,可以对威胁等级较高的攻击进行drop connect或drop packet。
通过MetaSploit进行攻击发现有以下的条目经过检查发现被攻击的机器没有启动IIS,所以发送过去的80端口的请求,均被客户端发送RST数据包终结请求。
在客户端安装了IIS以后,再次进行攻击就由于有IIS的响应而产生了对应的LOG,如下所示:攻击已经被发现,但本次由于是测试IDP对攻击的检查力度,所以action都是accept IDP防网络扫描配置实例本次测试IDP的防扫描功能用的是NMAP工具,命令如下所示:nmap –sS X.X.X.XIDP的配置如下:Traffic anomalies选择detect,severity选择default,缺省是critical的等级在进行端口扫描以后出现以下的LOG日志信息IDP防SYN配置实例本次测试IDP的防SYN攻击功能采用的是HPING产生的SYN FLOOD攻击,命令如下所示hping x.x.x.x -p port -i u1000 -S而IDP的配置如下所示:MODE的模式采用了passive模式。
