rfc5037.Experience with the Label Distribution Protocol (LDP)
imap rfc标准

Internet Message Access Protocol (IMAP) is an email retrieval protocol. It stores email messages on a mail server and enables the recipient to view and manipulate them as though they were stored locally on their device. IMAP was developed in the late 1980s and has since become one of the most widely used email retrieval protocols.The IMAP standard is defined in RFC 3501, which was published in 2003. This document provides a detailed description of the protocol's functionality, including its data formats, commands, and responses. The standard specifies how IMAP clients and servers should communicate with each other to enable the retrieval and manipulation of email messages.One of the key features of IMAP is its support for multiple clients accessing the same mailbox simultaneously. This is achieved through the use of a "shared" storage model, where all clients see the same set of messages and folders stored on the server. This allows users to access their email from different devices without having to worry about synchronizing their messages manually.Another important aspect of IMAP is its support for message organization and management. Clients can create, delete, and rename folders, as well as move messages between folders. They can also search for specific messages based on various criteria, such as sender, subject, or date.IMAP also provides a range of features for managing individual messages. Clients can mark messages as read or unread, flag them for follow-up, and even move them to a specific folder. They can also reply to messages, forward them to others, and generate replies or forwards with attachments.Overall, the IMAP standard provides a powerful and flexible framework for managing email messages. Its support for shared storage, message organization, and advanced message management features make it a popular choice for both personal and business email users.。
.Net 调用SAP RFC接口来读取数据实战纪实
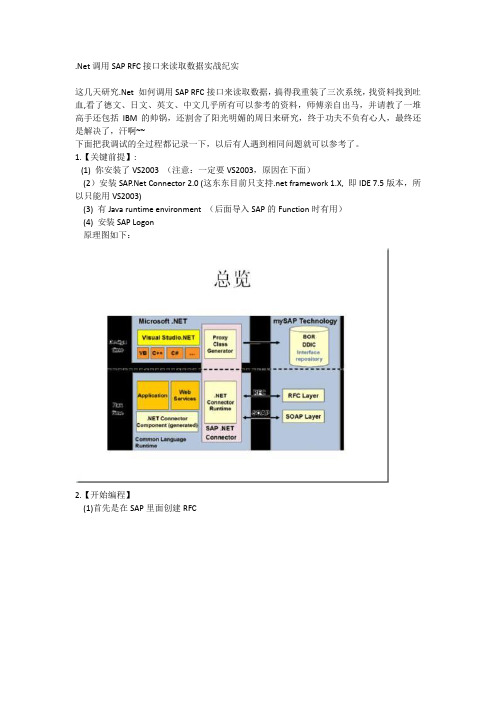
.Net 调用SAP RFC接口来读取数据实战纪实这几天研究.Net 如何调用SAP RFC接口来读取数据,搞得我重装了三次系统,找资料找到吐血,看了德文、日文、英文、中文几乎所有可以参考的资料,师傅亲自出马,并请教了一堆高手还包括IBM的帅锅,还割舍了阳光明媚的周日来研究,终于功夫不负有心人,最终还是解决了,汗啊~~下面把我调试的全过程都记录一下,以后有人遇到相同问题就可以参考了。
1.【关键前提】:(1) 你安装了VS2003 (注意:一定要VS2003,原因在下面)(2)安装 Connector 2.0 (这东东目前只支持.net framework 1.X, 即IDE 7.5版本,所以只能用VS2003)(3) 有Java runtime environment (后面导入SAP的Function时有用)(4) 安装SAP Logon原理图如下:2.【开始编程】(1)首先是在SAP里面创建RFC(2) VS里面编程先以Winform程序为例吧a.新建winform项目,因为装了 Connector,所以可以添加对SAP.Connector.dll和SAP.Connector .Rfc.dll的引用。
在项目中新建类,你会发现多了一个SAP Connector Proxy的类,新建一个,就是下面图中的SAPProxy1.sapwsdl文件啦。
b.在Form1.cs中添加控件(比较简陋,凑合看了)c.在SAP Test的Button事件里面加入以下代码private void button1_Click(object sender, System.EventArgs e){SAP.Connector.SAPLogonDestination myDest;SAP.Connector.SAPConnection myConn;SAPProxy1 myProx;BRFCKNA1Table xMara;System.Data.DataTable dMara;try{myDest = new SAP.Connector.SAPLogonDestination();myDest.DestinationName = "这里输入SAP服务器上的系统名称";myDest.Client = 这里输入SAP服务器的客户端号;ername = "这里输入SAP服务器访问的用户名";myDest.Password = "这里输入SAP服务器访问的密码";myConn = new SAP.Connector.SAPConnection(myDest);myConn.Open();xMara = new BRFCKNA1Table();//注意,这个BRFCKNA1Table可不是随便写的哈,看到下面就明白了myProx = new SAPProxy1();myProx.Connection = myConn;myProx.Rfc_Customer_Get("", this.textBox1.Text, ref xMara);// 注意,这个Rfc_Customer_Get就是你要call的RFC的function名称dMara = new System.Data.DataTable();dMara = xMara.ToADODataTable();dataGrid1.DataSource = dMara;dataGrid1.Refresh();myConn.Close();}catch(Exception ex){textBox1.Text = ex.ToString();}}d.从SAP服务器上导入RFC Function不要小看这一步哦【支线任务1】在C:\WINDOWS找到saplogon.ini,打开后把SysName和SrvPort下面的内容清空,不清空的话他会引导你去找SAP 服务器上的Messaging server,总是告诉你无法打开或者无法找到sapmsg.ini的文件,非常麻烦。
503校验规则未通过

503校验规则未通过在互联网时代,网站的可用性和稳定性对于用户和企业来说都是至关重要的。
然而,在网络运行过程中,难免会遇到一些错误和问题。
其中之一就是503校验规则未通过的问题。
当用户访问一个网站时,服务器会根据用户的请求来处理并返回相应的信息。
而当服务器遇到503校验规则未通过的情况时,它会向用户返回一个503错误码。
这意味着服务器目前无法处理用户的请求,通常是因为服务器暂时过载或维护中。
出现503错误码可能有多种原因。
首先,服务器可能由于访问量过大或处理复杂的请求而导致负载过高,无法及时响应用户的请求。
其次,服务器可能正在进行系统升级或维护,因此无法处理用户的请求。
还有一种可能是服务器出现故障或崩溃,导致无法正常工作。
为了解决503校验规则未通过的问题,网站管理员可以采取一些措施。
首先,他们可以增加服务器的处理能力,例如增加硬件资源或使用负载均衡技术。
这样可以提高服务器的并发处理能力,减少503错误的发生。
其次,他们可以合理规划网站的维护时间,避免在高峰期进行维护,从而减少对用户的影响。
此外,定期检查服务器的运行状态,及时发现并修复潜在的问题,也是降低503错误的有效措施。
对于用户而言,当遇到503校验规则未通过的错误时,应该首先确认自己的网络连接是否正常。
如果网络连接正常,可以尝试刷新页面或稍后再试。
如果问题仍然存在,可以尝试访问其他网站或联系网站管理员寻求帮助。
503校验规则未通过是一个常见的网络错误,可能由服务器负载过高、维护或故障等原因引起。
对于网站管理员来说,增加服务器处理能力、合理规划维护时间和及时修复问题是解决该问题的关键。
对于用户来说,确认网络连接、刷新页面或联系网站管理员是解决该问题的常见方法。
通过共同的努力,我们可以提高网站的可用性和稳定性,为用户提供更好的体验。
503校验规则未通过

503校验规则未通过摘要:1.503 校验规则的介绍2.503 校验规则未通过的原因3.解决503 校验规则未通过的方法4.总结正文:一、503 校验规则的介绍503 校验规则是指在网络访问过程中,服务器端根据访问者的请求,对请求进行校验,以判断请求是否合法。
其中,503 是服务器返回的一种状态码,表示服务器当前无法处理客户端的请求。
通常情况下,503 校验规则用于防范恶意访问、保护网站安全等方面。
二、503 校验规则未通过的原因当服务器返回503 状态码时,通常意味着客户端的请求被服务器拒绝。
导致503 校验规则未通过的原因有很多,以下是一些常见的原因:1.客户端请求过于频繁,超出了服务器的承受范围。
2.客户端请求的参数不合法,不符合服务器的校验规则。
3.服务器端的校验规则设置不合理,导致合法请求也被拒绝。
4.服务器端程序出现逻辑错误,无法正确处理客户端的请求。
5.网络环境问题,如网络延迟、带宽不足等,导致客户端请求无法及时到达服务器。
三、解决503 校验规则未通过的方法针对503 校验规则未通过的问题,可以从以下几个方面进行解决:1.优化客户端请求:降低请求频率,避免短时间内大量请求发送给服务器。
对于需要频繁请求的场景,可以考虑使用缓存、队列等技术来降低请求的实时性。
2.检查请求参数:确保发送给服务器的请求参数合法、正确。
对于需要携带参数的请求,可以对参数进行合法性校验,避免携带不合法的参数。
3.调整服务器端的校验规则:合理设置服务器端的校验规则,避免过度限制客户端的请求。
对于误报的情况,可以对服务器端的校验逻辑进行优化,提高校验的准确性。
4.修复服务器端程序逻辑错误:对于服务器端程序出现的逻辑错误,需要进行排查、修复。
可以通过日志分析、调试等方式,找出程序中存在的问题,并进行修复。
5.优化网络环境:提高网络带宽、降低网络延迟,以保证客户端请求能够及时到达服务器。
对于网络环境不稳定的情况,可以考虑使用负载均衡、CDN 等技术来提高服务的可用性。
SmartClass Ethernet测试仪 用户手册

第1章
开始..................................................................................................... 1
装箱清单.............................................................. 2
底部面板介绍.......................................................... 7
启动设备.............................................................. 7
关闭设备.............................................................. 7
不能将此产品作为市政污染废料进行处理,并且根据当地国家相关规则单独收集 处理。在欧盟地区,所有从 JDSU 公司 2005.8.13 日之后购买的设备可以在设 备使用寿命完毕时返回处理。JDSU 公司确保所有返回的废弃设备能够以环境友 好型方式进行重新使用、回收或处理,这些操作都要符合所有国家和国际废料处 理标准。
SmartClass Ethernet 测试仪用户手册
v
目录
第2章 第3章
vi
数据输入屏 ....................................................................................................10 结果屏............................................................................................................10 使用键盘 ............................................................ 11 选择菜单选项或配置设置............................................................................... 11 返回到上一级菜单.......................................................................................... 11 输入数字值 ....................................................................................................11 输入文本 ........................................................................................................11
合勤交换机使用手册

合勤科技交换机使用手册速查版本 1.0目录1. 硬件连接、常规设置与维护 (3)1.1 硬件安装 (3)1.2 硬件介绍 (3)1.3 常规设置 (5)2. 常规维护 (10)3. 高级设定 (12)3.1 VLAN设定 (12)3.2 STP(生成树协议)设置 (22)3.3 Access Control List (访问控制列表) (26)3.4 ES-3124_ACL功能完成IP与MAC的绑定 (30)3.5 ES-3124_Link Aggregation设置 (34)3.6 IGMP Snooping(组播侦听) (36)3.7 Static MAC Forwarding(静态MAC地址转发) (37)3.8 Filtering (过滤器) (37)3.9 Broadcast Storm Control (广播风暴控制) (37)3.10 Mirroring (端口镜像) (38)3.11 DHCP Relay (39)1. 硬件连接、常规设置与维护本章节介绍硬件连接方法,常规设置和基本维护方法,能够帮助您快速安全的将交换机接入网络。
1.1 硬件安装1.1.1 独立式安装:您可以将随机配备的绝缘脚垫安装到交换机底部,并将交换机置放到安全、干燥、清洁的环境中。
图-11.1.2 机架式安装(1)将随机配备的安装部件牢固的固定在交换机两侧。
如下图所示:图-2(2)利用安装部件将交换机牢固的安装在您的机架上。
如下图所示:注释: 合勤科技交换机系列,ES-2024A/ ES-3124/ ES-3148/ GS-2024/ ES-1528/ ES-1552/ GS-1524/ GS-1548都是标准的19英寸长度设计。
图-31.2 硬件介绍合勤交换机前面板的设计大体相似, 左侧是10/100/1000Mbps以太网接口,或者SFP光口。
右侧通常是上联端口,1000Mpbs的以太网接口或者SFP光口,或者是以太网和SFP双重属性端口。
rfc中常用的测试协议

rfc中常用的测试协议引言在计算机网络领域中,为了确保网络协议的正确性和稳定性,测试协议起到了至关重要的作用。
RFC(Request for Comments)是一系列文件,用于描述互联网相关协议、过程和技术。
在RFC中,也包含了一些常用的测试协议,用于验证和评估网络协议的功能和性能。
本文将介绍RFC中常用的测试协议,并深入探讨其原理和应用。
二级标题1:PING协议三级标题1.1:概述PING协议是一种常用的网络测试协议,用于测试主机之间的连通性。
它基于ICMP (Internet Control Message Protocol)协议,通过发送ICMP Echo Request报文并等待目标主机的ICMP Echo Reply报文来判断目标主机是否可达。
三级标题1.2:工作原理PING协议的工作原理如下: 1. 发送方主机生成一个ICMP Echo Request报文,并将目标主机的IP地址作为目的地。
2. 发送方主机将报文发送到网络中。
3.中间路由器收到报文后,将报文转发到下一跳路由器。
4. 目标主机收到ICMP Echo Request报文后,生成一个ICMP Echo Reply报文,并将其发送回发送方主机。
5. 发送方主机收到ICMP Echo Reply报文后,通过比较报文中的标识符和序列号等字段,判断目标主机是否可达。
三级标题1.3:应用场景PING协议在网络中的应用非常广泛,常用于以下场景: - 测试主机之间的连通性,判断网络是否正常工作。
- 测试网络延迟,通过计算ICMP Echo Request报文的往返时间来评估网络质量。
- 排查网络故障,通过检查ICMP Echo Reply报文中的错误码来定位故障原因。
二级标题2:Traceroute协议三级标题2.1:概述Traceroute协议用于跟踪数据包从源主机到目标主机经过的路径。
它通过发送一系列的UDP报文,并在每个报文中设置不同的TTL(Time to Live)值来实现。
(完整版)软件开发类投标项目全套解决方案模板(230页)

XXX航空移动化应用平台项目投标文件招标编号:正本招标方:XXX航空有限责任公司投标方:日期:目录1投标书 (13)2规格偏离表 (13)3资格证明文件 (13)3.1法人营业执照(三证合一) (13)3.2法定代表人授权书 (13)3.3 投标人的资信证明 (14)3.4 招标文件要求的其他资格证明文件 (15)3.4.1投标单位资质证书及项目人员资格证书 (15)3.4.1.1 CMMI等级登记证书 (15)3.4.1.2 ISO9001质量管理体系认证证书 (15)3.4.1.3 软件企业认证证书 (15)3.4.1.4 计算机软件著作权登记书-SDK (15)3.4.1.5计算机软件著作权登记书-MAS (16).4.1.6计算机软件著作权登记书-MMS (16)3.4.1.7计算机软件著作权登记书-EMM (16)3.4.1.8计算机软件著作权登记书-MDM (16)3.4.1.9 项目人员证书 (16)3.4.2投标单位近3年内获国家及地方政府荣誉证书 (19)3.4.2.1 2015年度中国移动互联网行业领军企业奖 (19)3.4.2.2 2014-2015年度云计算应用优秀实践单位奖 (19)3.4.2.3 2014年度中国最具影响力品牌奖 (19)3.4.2.4 2013年度最佳技术服务提供商 (19)3.4.2.5 2013年度中国移动应用平台最具影响力奖 (19)3.4.2.6 2014移动生产力十大优秀案例奖 (19)3.4.3投标单位综合情况审查表 (20)3.4.4拟派项目经理资格审查表 (20)3.4.5承担本项目主要技术人员和售后服务人员表 (20)3.4.6最近两年主要开发实施同类型企业相同或类似系统的开发案例 (21)3.4.6.1案例合同首尾页 (21)3.4.6.2 系统开发主界面截图 (23)4项目解决方案 (27)4.1项目解决方案内容 (27)4.1.1系统总体目标、设计架构、系统详细设计方案 (28)4.1.1.1设计原则 (28)1.统一设计原则 (28)2.稳定性原则 (28)3.统一设计原则 (28)4.稳定性原则 (28)5.先进性原则 (28)6.高可靠/高安全性原则 (28)7.开放性原则 (29)8.适用性原则 (29)9.可扩展性原则 (29)10.操作/维护的易用性原则 (29)11.高可靠/高安全性原则 (29)4.1.1.2架构设计 (30)4.1.1.2.1.系统架构设计 (30)4.1.1.2.2.业务系统架构设计 (32)4.1.1.2.3.业务处理架构 (33)4.1.1.2.4.网络拓扑图 (34)4.1.1.3技术路线 (36)4.1.1.3.1统一的移动构建平台 (36)4.1.1.3.2Hybrid移动开发引擎 (36)4.1.1.3.3面向服务的SOA接口集成 (36)4.1.1.3.4高并发处理机制 (37)4.1.1.3.5高效的内存数据库 (37)4.1.1.3.6兼容多种集成模式 (37)4.1.1.3.7开放式的框架设计 (37)4.1.1.3.8数据库选型 (37)4.1.1.4应用工具 (38)4.1.1.4.1.开发工具 (38)4.1.1.4.2.分析设计工具 (39)4.1.1.4.3.项目管理辅助工具 (39)4.1.1.4.4.测试工具 (40)4.1.1.4.5.统计工具 (41)4.1.1.4.6.开发语言 (43)4.1.1.4.7.辅助软件工具及其效果 (45)4.1.1.5移动平台建设方案 (46)4.1.1.5.1.移动业务整合平台(APPCAN MAS) (46)4.1.1.5.2.移动业务开发平台(APPCAN SDK) (54)1.音频对象API (56)2.电话对象API (56)3.照相机对象API (56)4.剪贴板对象API (56)5.日期控件API (56)6.联系人对象API (56)7.数据库对象API (56)8.设备信息对象API (56)9.下载对象API (56)10.邮件对象API (56)11.文件管理对象API (56)12.图片浏览对象API (57)13.Jabber对象API (57)14.位置服务对象API (57)15.日志log输出对象API (57)16.彩信对象API (57)17.支付宝API (57)18.二维码扫描对象API (57)19.传感器对象API (57)20.短信对象API (58)21.Socket对象API (58)22.上传对象API (58)23.视频对象API (58)24.widget对象API (58)25.平台对象API (58)26.多窗口机制API (58)27.跨域访问对象API (58)28.zip压缩解压缩API (58)29.百度广告推广接口 (58)30.百度地图接口 (58)31.百度统计接口 (59)32.数据统计分析自定义事件接口 (59)33.微博分享接口 (59)34.自定义编辑框接口 (59)35.游戏引擎接口 (59)(1)插件扩展 (59)AppCan IDE 启动画面 (63)AppCan IDE 代码编辑界面 (64)AppCan IDE模拟器与调试器 (64)AppCan IDE 本地打包界面 (65)AppCan UI框架控件 (66)AppCan Player示意图 (67)AppCan模拟器 (68)Mac Mini服务器 (69)AppCan SDK套装管理后台-项目列表 (70)AppCan SDK套装管理后台-项目管理 (70)AppCan SDK套装管理后台-引擎升级 (71)4.1.1.5.3.移动业务管理平台(APPCAN EMM) (72)4.1.1.6前端应用建设方案 (79)4.1.1.6.1.机票预订 (79)4.1.1.6.2.订单管理 (83)4.1.1.6.3.航班动态 (87)4.1.1.6.4.XXX商店 (91)4.1.1.6.5.会员注册\登录 (94)4.1.1.6.6.常用乘机人管理 (96)4.1.1.6.7.机票验真 (98)4.1.1.6.8.促销专区 (99)4.1.1.6.9.更多服务 (100)4.1.1.6.10.主页 (104)1、功能性:主页面集成APP中所有功能模块,用户可应用功能模块快速使用需求功能。
中文版RFC5009

RFC 5009:针对早期媒体授权的会话发起协议的隐私头部信息扩展网络工作组:R. Ejzak请求评议:Alcatel-Lucent分类:信息备注状态:该备注为互联网组织提供信息。
它没有定义任何一种互联网标准。
备注的分类是没有限制的。
简述:该文档描述了一种私有会话发起协议头字段信息,该头字段信息能被欧洲电信标准协会电信和互联网融合业务以及高级网络协议使用,并基于在第三代伙伴计划IP多媒体子系统中授权早期媒体。
这头字段对于在任何会话发起协议网络和需要在早期会话状态需要控制媒体流时很有用。
目录:1………………………………介绍2………………………………应用性说明3………………………………公约和简写4………………………………早期媒体授权背景4.1…………………………向后早期媒体4.2…………………………向前早期媒体5………………………………RFC 3959 和RFC 3960的适用性6………………………………操作概述7………………………………P-Early-Media头字段的局限性8…………………………………P-Early-Media头字段8.1………………………………用户代理客户端处理机制8.2………………………………用户代理服务端处理机制8.3………………………………网络代理处理机制9……………………………………正式语法10……………………………………安全性考虑11……………………………………IANA考虑11.1………………………………P-Early-Media SIP头字段的注册12……………………………………致谢13……………………………………参考文献13.1………………………………规范性参考13.2………………………………信息参考1.介绍这篇文档定义了P-Early-Media头字段的使用。
当相关网络的早期媒体规定被允许时,P-Early-Media头字段适用于在某个SIP网络中用SIP信息来授权直通转发向后和/或向前早期媒体。
RFC2865中文文档

RFC 2865 RADIUS 中文翻译收藏Network Working Group C. Rigney Request for Comments: 2865 S. Willens Obsoletes: 2138 LivingstonCategory: Standards Track A. RubensMeritW. SimpsonDaydreamerJune 2000远程认证拨号用户服务(RADIUS)备忘录状态本文档描述了一种Internet社区的Internet标准跟踪协议,它需要进一步进行讨论和建议以得到改进。
请参考最新版的“Internet正式协议标准” (STD1)来获得本协议的标准化程度和状态。
本备忘录可以不受限制地传播。
版权说明Copyright (C) The Internet Society (2000). All Rights Reserved.IESG说明:本协议已经被广泛实现和使用,经验表明当本协议在一个大范围的系统中使用会降低性能和丢失数据。
部分原因是协议中没有提供拥塞控制的机制。
读者可以发现阅读本文对跟踪IETF组织的AAA工作组的工作进程有很大的帮助,AAA工作组可能会开发一个能够更好的解决扩展性和拥塞控制问题的成功的协议。
摘要本文描述了一个传输认证、授权和配置信息的协议。
这些信息在想要认证链路的网络接入服务器(Network Access Server)和共享的认证服务器务器之间传递。
实现说明本备忘录记录了RADIUS协议,RADIUS协议的早期版本使用的UDP端口是16 45,由于和"datametrics"服务冲突,官方为RADIUS协议分配了一个新的端口号1812。
Rigney, et al. Standards Track [Page 1]RFC 2865 RADIUS June 2000目录1. 简介 (3)1.1 描述文档的约定 (4)1.2 术语 (5)2. 操作 (5)2.1 挑战/回应 (7)2.2 使用PAP和CHAP互操作 (8)2.3 代理 (8)2.4 为什么使用UDP (11)2.5 重发提醒 (12)2.6 被证明是有害的心跳 (13)3. 报文格式 (13)4. 报文类型 (17)4.1 接入请求报文 (17)4.2 接入成功回应报文 (18)4.3 接入拒绝回应报文 (20)4.4 接入挑战报文 (21)5. 属性 (22)5.1 User-Name (26)5.2 User-Password (27)5.3 CHAP-Password (28)5.4 NAS-IP-Address (29)5.5 NAS-Port (30)5.6 Service-Type (31)5.7 Framed-Protocol (33)5.8 Framed-IP-Address (34)5.9 Framed-IP-Netmask (34)5.10 Framed-Routing (35)5.11 Filter-Id (36)5.12 Framed-MTU (37)5.13 Framed-Compression (37)5.14 Login-IP-Host (38)5.15 Login-Service (39)5.16 Login-TCP-Port (40)5.17 (unassigned) (41)5.18 Reply-Message (41)5.19 Callback-Number (42)5.20 Callback-Id (42)5.21 (unassigned) (43)5.22 Framed-Route (43)5.23 Framed-IPX-Network (44)5.24 State (45)5.25 Class (46)5.26 Vendor-Specific (47)5.27 Session-Timeout (48)5.28 Idle-Timeout (49)5.29 Termination-Action (49)Rigney, et al. Standards Track [Page 2] RFC 2865 RADIUS June 20005.30 Called-Station-Id (50)5.31 Calling-Station-Id (51)5.32 NAS-Identifier (52)5.33 Proxy-State (53)5.34 Login-LAT-Service (54)5.35 Login-LAT-Node (55)5.36 Login-LAT-Group (56)5.37 Framed-AppleTalk-Link (57)5.38 Framed-AppleTalk-Network (58)5.39 Framed-AppleTalk-Zone (58)5.40 CHAP-Challenge (59)5.41 NAS-Port-Type (60)5.42 Port-Limit (61)5.43 Login-LAT-Port (62)5.44 Table of Attributes (63)6. IANA注意事项 (64)6.1 术语定义 (64)6.2 推荐的注册策略 (65)7. 举例 (66)7.1 用户Telnet到指定主机上 (66)7.2 用户使用CHAP认证方式认证 (67)7.3 用户使用挑战-回应卡 (68)8. 安全事项 (71)9. 更新记录 (71)10. 参考文献 (73)11. 致谢 (74)12. AAA工作组主席地址 (74)13. 作者地址 (75)14. 版权声明 (76)1. 简介本文档废弃了RFC 2138 [1]。
RFC5707 Media Server Markup Language 翻译

RFC5707 Media Server Markup Language 翻译8.4. <modifyconference>一个混音的所有特性或混合视频的呈现特性,在会议进行期间将能使用<modifyconference>标签来改变。
使用带有<audiomix>子标签的<modifyconference>标签来改变混音。
这也能用来为之前没有分配混音器的会议增加一个混音器。
使用带有<videolayout>子标签的<modifyconference>标签来改变视频呈现。
与混音器相似,这能用来为之前没有分配混合视频器的会议增加一个混合视频器。
包含混合器描述标签的<destroyconference/>标签,移除混合器。
8.6. <audiomix>所有混音属性用<audiomix>标签来定义。
属性:id:混音的一个任意的标识。
samplerate:整型值,指定混音器的抽样率。
可选参数,默认值为8000。
描述一个混音的例子如下:<audiomix id="mix1"><asn ri="10s"/><n-loudest n="3"/></audiomix>8.6.1. <n-loudest><n-loudest>标签来定义参加者基于他们语音能量的大小而被包含在混合会议中。
当没有<n-loudest>标签时,则混对所欲参加者的语音进行混合。
属性:n:被包含在混音中的参加者的数量,参加者音频的选定是基于最大音量的。
为必选参数。
8.6.2. <asn><asn>标签能够通知活跃发言者。
用带有事件名称为"msml.conf.asn"的<event>标签来通知活跃发言者。
解决在请求目标中找到无效字符。有效字符在RFC7230和RFC3986中定义的问题

解决在请求⽬标中找到⽆效字符。
有效字符在RFC7230和RFC3986中定义的问题前⾔今天因解决漏洞⽽更新了Tomcat,运⾏⽹站就报错类型异常报告消息在请求⽬标中找到⽆效字符。
有效字符在RFC 7230和RFC 3986中定义描述由于被认为是客户端对错误(例如:畸形的请求语法、⽆效的请求信息帧或者虚拟的请求路由),服务器⽆法或不会处理当前请求。
例外情况ng.IllegalArgumentException: 在请求⽬标中找到⽆效字符。
有效字符在RFC 7230和RFC 3986中定义如图所⽰:可能的原因是超链接带了特殊字符或中⽂第⼀部分因超链接参数带中⽂⽽报错通过脚本来将href超链接传递的参数转换为from表单提交1function linkClick(linkObject) {23var formObject = document.createElement('form');4 document.body.appendChild(formObject);5 formObject.setAttribute('method', 'post');6var url = linkObject.href;7var uri = '';8var i = url.indexOf('?');910if(i == -1) {11 formObject.action = url;12 } else {13 formObject.action = url.substring(0, i);14 }1516if( i >= 0 && url.length >= i + 1) {17 uri = url.substring(i + 1, url.length);18 }1920var sa = uri.split('&');2122for(var i = 0; i < sa.length; i++) {23var isa = sa[i].split('=');24var inputObject = document.createElement('input');25 inputObject.setAttribute('type', 'hidden');26 inputObject.setAttribute('name', isa[0]);27 inputObject.setAttribute('value', isa[1]);28 formObject.appendChild(inputObject);29 }3031 formObject.submit();3233return false;34 }超链接中加⼊onclick="return linkClick(this)1<a href='/Servlet?name=中⽂' onclick="return linkClick(this)">超链接</a>注:部分浏览器若传参出现urlencode编码,且不想出现这个编码时将27 inputObject.setAttribute('value', isa[1]);改为inputObject.setAttribute('value', decodeURIComponent(isa[1]));或java解码.URLDecoder.decode(mytext,"utf-8")第⼆部分超链接参数带特殊字符⽽报错参数中可能包含了 |{}[],% 等⼀些特殊字符修改Tomcat的server.xml⽂件向server.xml 中Connector添加relaxedPathChars="|{}[],%" relaxedQueryChars="|{}[],%"例如:(参数⾥有哪些特殊字符,就加哪些)<Connector port="80" protocol="HTTP/1.1"connectionTimeout="20000"redirectPort="8443"relaxedPathChars="|{}[],%" relaxedQueryChars="|{}[],%"/>结语:记得对传递参数进⾏过滤,防⽌他⼈插⼊脚本代码。
rfc4577

Network Working Group E. Rosen Request for Comments: 4577 P. Psenak Updates: 4364 P. Pillay-Esnault Category: Standards Track Cisco Systems, Inc. June 2006 OSPF as the Provider/Customer Edge Protocol forBGP/MPLS IP Virtual Private Networks (VPNs)Status of This MemoThis document specifies an Internet standards track protocol for the Internet community, and requests discussion and suggestions forimprovements. Please refer to the current edition of the "InternetOfficial Protocol Standards" (STD 1) for the standardization stateand status of this protocol. Distribution of this memo is unlimited. Copyright NoticeCopyright (C) The Internet Society (2006).AbstractMany Service Providers offer Virtual Private Network (VPN) servicesto their customers, using a technique in which customer edge routers (CE routers) are routing peers of provider edge routers (PE routers). The Border Gateway Protocol (BGP) is used to distribute thecustomer’s routes across the provider’s IP backbone network, andMultiprotocol Label Switching (MPLS) is used to tunnel customerpackets across the provider’s backbone. This is known as a "BGP/MPLS IP VPN". The base specification for BGP/MPLS IP VPNs presumes thatthe routing protocol on the interface between a PE router and a CErouter is BGP. This document extends that specification by allowing the routing protocol on the PE/CE interface to be the Open ShortestPath First (OSPF) protocol.This document updates RFC 4364.Rosen, et al. Standards Track [Page 1]Table of Contents1. Introduction (2)2. Specification of Requirements (3)3. Requirements (4)4. BGP/OSPF Interaction Procedures for PE Routers (6)4.1. Overview (6)4.1.1. VRFs and OSPF Instances (6)4.1.2. VRFs and Routes (6)4.1.3. Inter-Area, Intra-Area, and External Routes (7)4.1.4. PEs and OSPF Area 0 (8)4.1.5. Prevention of Loops (9)4.2. Details (9)4.2.1. Independent OSPF Instances in PEs (9)4.2.2. Router ID (10)4.2.3. OSPF Areas (10)4.2.4. OSPF Domain Identifiers (10)4.2.5. Loop Prevention (12)4.2.5.1. The DN Bit (12)4.2.5.2. Use of OSPF Route Tags (12)4.2.5.3. Other Possible Loops (13)4.2.6. Handling LSAs from the CE (14)4.2.7. Sham Links (16)4.2.7.1. Intra-Area Routes (16)4.2.7.2. Creating Sham Links (17)4.2.7.3. OSPF Protocol on Sham Links (18)4.2.7.4. Routing and Forwarding on Sham Links (19)4.2.8. VPN-IPv4 Routes Received via BGP (19)4.2.8.1. External Routes (20)4.2.8.2. Summary Routes (22)4.2.8.3. NSSA Routes (22)5. IANA Considerations (22)6. Security Considerations (23)7. Acknowledgements (23)8. Normative References (23)9. Informative References (24)1. Introduction[VPN] describes a method by which a Service Provider (SP) can use its IP backbone to provide a VPN (Virtual Private Network) service tocustomers. In that method, a customer’s edge devices (CE devices)are connected to the provider’s edge routers (PE routers). If the CE device is a router, then the PE router may become a routing peer ofthe CE router (in some routing protocol) and may, as a result, learn the routes that lead to the CE’s site and that need to be distributed to other PE routers that attach to the same VPN.Rosen, et al. Standards Track [Page 2]The PE routers that attach to a common VPN use BGP (Border GatewayProtocol) to distribute the VPN’s routes to each other. A CE router can then learn the routes to other sites in the VPN by peering withits attached PE router in a routing protocol. CE routers atdifferent sites do not, however, peer with each other.It can be expected that many VPNs will use OSPF (Open Shortest PathFirst) as their IGP (Interior Gateway Protocol), i.e., the routingprotocol used by a network for the distribution of internal routeswithin that network. This does not necessarily mean that the PErouters need to use OSPF to peer with the CE routers. Each site in a VPN can use OSPF as its intra-site routing protocol, while using, for example, BGP [BGP] or RIP (Routing Information Protocol) [RIP] todistribute routes to a PE router. However, it is certainlyconvenient, when OSPF is being used intra-site, to use it on thePE-CE link as well, and [VPN] explicitly allows this.Like anything else, the use of OSPF on the PE-CE link has advantages and disadvantages. The disadvantage to using OSPF on the PE-CE link is that it gets the SP’s PE router involved, however peripherally, in a VPN site’s IGP. The advantages though are:- The administrators of the CE router need not have any expertise in any routing protocol other than OSPF.- The CE routers do not need to have support for any routingprotocols other than OSPF.- If a customer is transitioning his network from a traditionalOSPF backbone to the VPN service described in [VPN], the use of OSPF on the PE-CE link eases the transitional issues.It seems likely that some SPs and their customers will resolve these trade-offs in favor of the use of OSPF on the PE-CE link. Thus, weneed to specify the procedures that must be implemented by a PErouter in order to make this possible. (No special procedures areneeded in the CE router though; CE routers just run whatever OSPFimplementations they may have.)2. Specification of RequirementsThe key words "MUST", "MUST NOT", "REQUIRED", "SHALL", "SHALL NOT","SHOULD", "SHOULD NOT", "RECOMMENDED", "MAY", and "OPTIONAL" in this document are to be interpreted as described in [RFC2119].Rosen, et al. Standards Track [Page 3]3. RequirementsConsider a set of VPN sites that are thought of as being in the same "OSPF domain". Two sites are considered to be in the same OSPFdomain if it is intended that routes from one site to the other beconsidered intra-network routes. A set of OSPF sites in the samedomain will almost certainly be a set of sites that togetherconstitute an "intranet", each of which runs OSPF as its intra-siterouting protocol.Per [VPN], the VPN routes are distributed among the PE routers byBGP. If the PE uses OSPF to distribute routes to the CE router, the standard procedures governing BGP/OSPF interactions [OSPFv2] wouldcause routes from one site to be delivered to another in type 5 LSAs (Link State Advertisements), as "AS-external" routes. This isundesirable; it would be much better to deliver such routes in type 3 LSAs (as inter-area routes), so that they can be distinguished fromany "real" AS-external routes that may be circulating in the VPN(that is, so that they can be distinguished by OSPF from routes that really do not come from within the VPN). Hence, it is necessary for the PE routers to implement a modified version of the BGP/OSPFinteraction procedures.In fact, we would like to have a very general set of procedures that allows a customer to replace a legacy private OSPF backbone easilywith the VPN service. We would like this procedure to meet thefollowing set of requirements:- The procedures should not make assumptions about the OSPFtopology. In particular, it should not be assumed thatcustomer sites are OSPF stub sites or NSSA (Not So Stubby Area) sites. Nor should it be assumed that a customer site contains only one OSPF area, or that it has no area 0 routers.- If VPN sites A and B are in the same OSPF domain, then routesfrom one should be presented to the other as OSPF intra-network routes. In general, this can be done by presenting such routes as inter-area routes in type 3 LSAs.Note that this allows two VPN sites to be connected via an"OSPF backdoor link". That is, one can have an OSPF linkbetween the two sites that is used only when the VPN backboneis unavailable. (This would not be possible with the ordinary BGP/OSPF interaction procedures. The ordinary procedures would present routes via the VPN backbone as AS-external routes, and these could never be preferred to intra-network routes.) This may be very useful during a period of transition from a legacy OSPF backbone to a VPN backbone.Rosen, et al. Standards Track [Page 4]- It should be possible to make use of an "OSPF backdoor link"between two sites, even if the two sites are in the same OSPFarea and neither of the routers attached to the inter-sitebackdoor link is an area 0 router. This can also be veryuseful during a transition period, and it eliminates any needto reconfigure the sites’ routers to be ABRs (Area BorderRouters).Assuming that it is desired to have the route via the VPNbackbone be preferred to the backdoor route, the VPN backboneitself must be presented to the CE routers at each site as alink between the two PE routers to which the CE routers arerespectively attached.- CE routers, connected to PE routers of the VPN service, maythemselves function as OSPF backbone (area 0) routers. An OSPF backbone may even consist of several "segments" that areinterconnected themselves only via the VPN service. In such a scenario, full intercommunication between sites connected todifferent segments of the OSPF backbone should still bepossible.- The transition from the legacy private OSPF backbone to the VPN service must be simple and straightforward. The transition is likely to be phased, such that customer sites are migrated one by one from the legacy private OSPF backbone to the VPNservice. During the transition, any given site might beconnected to the VPN service, to the legacy OSPF backbone, orto both. Complete connectivity among all such sites must bemaintained.Since the VPN service is to replace the legacy backbone, itmust be possible, by suitable adjustment of the OSPF metrics,to make OSPF prefer routes that traverse the SP’s VPN backbone to alternative routes that do not.- The OSPF metric assigned to a given route should be carriedtransparently over the VPN backbone.Routes from sites that are not in the same OSPF domain will appear as AS-external routes.We presuppose familiarity with the contents of [OSPFv2], includingthe OSPF LSA types, and will refer without further exegesis to type1, 2, 3, etc. LSAs. Familiarity with [VPN] is also presupposed. Rosen, et al. Standards Track [Page 5]4. BGP/OSPF Interaction Procedures for PE Routers4.1. Overview4.1.1. VRFs and OSPF InstancesA PE router that attaches to more than one OSPF domain MUST run anindependent instance of OSPF for each domain. If the PE is runningOSPF as its IGP (Interior Gateway Protocol), the instance of OSPFrunning as the IGP must be separate and independent from any otherinstance of OSPF that the PE is running. (Whether these instancesare realized as separate processes or merely as separate contexts of a common process is an implementation matter.) Each interface thatattaches to a VPN site belongs to no more than one OSPF instance.[VPN] defines the notion of a Per-Site Routing and Forwarding Table, or VRF. Each VRF is associated with a set of interfaces. If a VRFis associated with a particular interface, and that interface belongs to a particular OSPF instance, then that OSPF instance is said to be associated with the VRF. If two interfaces belong to the same OSPFinstance, then both interfaces must be associated with the same VRF. If an interface attaches a PE to a CE, and that interface isassociated with a VRF, we will speak of the CE as being associatedwith the VRF.4.1.2. VRFs and RoutesOSPF is used to distribute routes from a CE to a PE. The standardOSPF decision process is used to install the best OSPF-distributedroutes in the VRF.Per [VPN], BGP is used to distribute VPN-IPv4 routes among PErouters. An OSPF route installed in a VRF may be "exported" by being redistributed into BGP as a VPN-IPv4 route. It may then bedistributed by BGP to other PEs. At the other PEs, a VPN-IPv4 route may be "imported" by a VRF and may then be redistributed into one or more of the OSPF instances associated with that VRF.Import from and export to particular VRFs is controlled by the use of the Route Target Extended Communities attribute (or, more simply,Route Target or RT), as specified in [VPN].A VPN-IPv4 route is "eligible for import" into a particular VRF ifits Route Target is identical to one of the VRF’s import RouteTargets. The standard BGP decision process is used to select, fromamong the routes eligible for import, the set of VPN-IPv4 routes tobe "installed" in the VRF.Rosen, et al. Standards Track [Page 6]If a VRF contains both an OSPF-distributed route and a VPN-IPv4 route for the same IPv4 prefix, then the OSPF-distributed route ispreferred. In general, this means that forwarding is done according to the OSPF route. The one exception to this rule has to do with the "sham link". If the next hop interface for an installed (OSPF-distributed) route is the sham link, forwarding is done according to a corresponding BGP route. This is detailed in Section 4.2.7.4.To meet the requirements of Section 3, a PE that installs aparticular route into a particular VRF needs to know whether thatroute was originally an OSPF route and, if so, whether the OSPFinstance from which it was redistributed into BGP is in the samedomain as the OSPF instances into which the route may beredistributed. Therefore, a domain identifier is encoded as a BGPExtended Communities attribute [EXTCOMM] and distributed by BGP along with the VPN-IPv4 route. The route’s OSPF metric and OSPF route type are also carried as BGP attributes of the route.4.1.3. Inter-Area, Intra-Area, and External RoutesIf a PE installs a particular VPN-IPv4 route (learned via BGP) in aVRF, and if this is the preferred BGP route for the correspondingIPv4 prefix, the corresponding IPv4 route is then "eligible forredistribution" into each OSPF instance that is associated with theVRF. As a result, it may be advertised to each CE in an LSA.Whether a route that is eligible for redistribution into OSPF isactually redistributed into a particular OSPF instance may dependupon the configuration. For instance, the PE may be configured todistribute only the default route into a given OSPF instance. Inthis case, the routes that are eligible for redistribution would not actually be redistributed.In the following, we discuss the procedures for redistributing aBGP-distributed VPN-IPv4 route into OSPF; these are the procedures to be followed whenever such a route is eligible to be redistributedinto OSPF and the configuration does not prevent such redistribution. If the route is from an OSPF domain different from that of the OSPFinstance into which it is being redistributed, or if the route is not from an OSPF domain at all, then the route is considered an external route.If the route is from the same OSPF domain as the OSPF instance intowhich it is being redistributed, and if it was originally advertised to a PE as an OSPF external route or an OSPF NSSA route, it will betreated as an external route. Following the normal OSPF procedures, external routes may be advertised to the CE in type 5 LSAs, or in Rosen, et al. Standards Track [Page 7]type 7 LSAs, or not at all, depending on the type of area to whichthe PE/CE link belongs.If the route is from the same OSPF domain as the OSPF instance intowhich it is being redistributed, and if it was originally advertised to a PE as an inter-area or intra-area route, the route willgenerally be advertised to the CE as an inter-area route (in a type 3 LSA).As a special case, suppose that PE1 attaches to CE1, and that PE2attaches to CE2, where:- the OSPF instance containing the PE1-CE1 link and the OSPFinstance containing the PE2-CE2 link are in the same OSPFdomain, and- the PE1-CE1 and PE2-CE2 links are in the same OSPF area A (asdetermined by the configured OSPF area number),then, PE1 may flood to CE1 a type 1 LSA advertising a link to PE2,and PE2 may flood to CE2 a type 1 LSA advertising a link to PE1. The link advertised in these LSAs is known as a "sham link", and it isadvertised as a link in area A. This makes it look to routers within area A as if the path from CE1 to PE1 across the service provider’snetwork to PE2 to CE2 is an intra-area path. Sham links are anOPTIONAL feature of this specification and are used only when it isnecessary to have the service provider’s network treated as anintra-area link. See Section 4.2.7 for further details about thesham link.The precise details by which a PE determines the type of LSA used to advertise a particular route to a CE are specified in Section 4.2.8. Note that if the VRF is associated with multiple OSPF instances, the type of LSA used to advertise the route might be different indifferent instances.Note that if a VRF is associated with several OSPF instances, a given route may be redistributed into some or all of those OSPF instances, depending on the characteristics of each instance. If redistributed into two or more OSPF instances, it may be advertised within eachinstance using a different type of LSA, again depending on thecharacteristics of each instance.4.1.4. PEs and OSPF Area 0Within a given OSPF domain, a PE may attach to multiple CEs. EachPE/CE link is assigned (by configuration) to an OSPF area. Any link can be assigned to any area, including area 0.Rosen, et al. Standards Track [Page 8]If a PE attaches to a CE via a link that is in a non-zero area, then the PE serves as an ABR for that area.PEs can thus be considered OSPF "area 0 routers", i.e., they can beconsidered part of the "OSPF backbone". Thus, they are allowed todistribute inter-area routes to the CE via Type 3 LSAs.If the OSPF domain has any area 0 routers other than the PE routers, then at least one of those MUST be a CE router and MUST have an area 0 link to at least one PE router. This adjacency MAY be via an OSPF virtual link. (The ability to use an OSPF virtual link in this wayis an OPTIONAL feature.) This is necessary to ensure that inter-area routes and AS-external routes can be leaked between the PE routersand the non-PE OSPF backbone.Two sites that are not in the same OSPF area will see the VPNbackbone as being an integral part of the OSPF backbone. However, if there are area 0 routers that are NOT PE routers, then the VPNbackbone actually functions as a sort of higher-level backbone,providing a third level of hierarchy above area 0. This allows alegacy OSPF backbone to become disconnected during a transitionperiod, as long as the various segments all attach to the VPNbackbone.4.1.5. Prevention of LoopsIf a route sent from a PE router to a CE router could then bereceived by another PE router from one of its own CE routers, itwould be possible for routing loops to occur. To prevent this, a PE sets the DN bit [OSPF-DN] in any LSA that it sends to a CE, and a PE ignores any LSA received from a CE that already has the DN bit sent. Older implementations may use an OSPF Route Tag instead of the DNbit, in some cases. See Sections 4.2.5.1 and 4.2.5.2.4.2. Details4.2.1. Independent OSPF Instances in PEsThe PE MUST support one OSPF instance for each OSPF domain to whichit attaches. These OSPF instances function independently and do not leak routes to each other. Each instance of OSPF MUST be associated with a single VRF. If n CEs associated with that VRF are runningOSPF on their respective PE/CE links, then those n CEs are OSPFadjacencies of the PE in the corresponding instance of OSPF.Generally, though not necessarily, if the PE attaches to several CEs in the same OSPF domain, it will associate the interfaces to thosePEs with a single VRF.Rosen, et al. Standards Track [Page 9]4.2.2. Router IDIf a PE and a CE are communicating via OSPF, the PE will have an OSPF Router ID that is valid (i.e., unique) within the OSPF domain. More precisely, each OSPF instance has a Router ID. Different OSPFinstances may have different Router IDs.4.2.3. OSPF AreasA PE-CE link may be in any area, including area 0; this is a matterof the OSPF configuration.If a PE has a link that belongs to a non-zero area, the PE functions as an Area Border Router (ABR) for that area.PEs do not pass along the link state topology from one site toanother (except in the case where a sham link is used; see Section4.2.7).Per [OSPFv2, Section 3.1], "the OSPF backbone always contains allarea border routers". The PE routers are therefore considered area 0 routers. Section 3.1 of [OSPFv2] also requires that area 0 becontiguous. It follows that if the OSPF domain has any area 0routers other than the PE routers, at least one of those MUST be a CE router, and it MUST have an area 0 link (possibly a virtual link) to at least one PE router.4.2.4. OSPF Domain IdentifiersEach OSPF instance MUST be associated with one or more DomainIdentifiers. This MUST be configurable, and the default value (ifnone is configured) SHOULD be NULL.If an OSPF instance has multiple Domain Identifiers, one of these is considered its "primary" Domain Identifier; this MUST be determinable by configuration. If an OSPF instance has exactly one DomainIdentifier, this is of course its primary Domain Identifier. If anOSPF instance has more than one Domain Identifier, the NULL DomainIdentifier MUST NOT be one of them.If a route is installed in a VRF by a particular OSPF instance, theprimary Domain Identifier of that OSPF instance is considered theroute’s Domain Identifier.Consider a route, R, that is installed in a VRF by OSPF instance I1, then redistributed into BGP as a VPN-IPv4 route, and then installedby BGP in another VRF. If R needs to be redistributed into OSPFinstance I2, associated with the latter VRF, the way in which R is Rosen, et al. Standards Track [Page 10]advertised in I2 will depend upon whether R’s Domain Identifier isone of I2’s Domain Identifiers. If R’s Domain Identifier is not one of I2’s Domain Identifiers, then, if R is redistributed into I2, Rwill be advertised as an AS-external route, no matter what its OSPFroute type is. If, on the other hand, R’s Domain Identifier is oneof I2’s Domain Identifiers, how R is advertised will depend upon R’s OSPF route type.If two OSPF instances are in the same OSPF domain, then either:1. They both have the NULL Domain Identifier, OR2. Each OSPF instance has the primary Domain Identifier of theother as one of its own Domain Identifiers.If two OSPF instances are in different OSPF domains, then either:3. They both have the NULL Domain Identifier, OR4. Neither OSPF instance has the Primary Domain Identifier of the other as one of its own Domain Identifiers.(Note that if two OSPF instances each have the NULL DomainIdentifier, we cannot tell from the Domain Identifier whether theyare in the same OSPF Domain. If they are in different domains, andif routes from one are distributed into the other, the routes willappear as intra-network routes, which may not be what is intended.)A Domain Identifier is an eight-byte quantity that is a valid BGPExtended Communities attribute, as specified in Section 4.2.4. If a particular OSPF instance has a non-NULL Domain Identifier, whenroutes from that OSPF instance are distributed by BGP as VPN-IPv4routes, the routes MUST carry the Domain Identifier ExtendedCommunities attribute that corresponds to the OSPF instance’s Primary Domain Identifier. If the OSPF instance’s Domain Identifier is NULL, the Domain Identifier Extended Communities attribute MAY be omittedwhen routes from that OSPF instance are distributed by BGP;alternatively, a value of the Domain Identifier Extended Communities attribute that represents NULL (see Section 4.2.4) MAY be carriedwith the route.If the OSPF instances of an OSPF domain are given one or more non-NULL Domain Identifiers, this procedure allows us to determinewhether a particular OSPF-originated VPN-IPv4 route belongs to thesame domain as a given OSPF instance. We can then determine whether the route should be redistributed to that OSPF instance as an inter- area route or as an OSPF AS-external route. Details can be found in Sections 4.2.4 and 4.2.8.1.Rosen, et al. Standards Track [Page 11]4.2.5. Loop Prevention4.2.5.1. The DN BitWhen a type 3 LSA is sent from a PE router to a CE router, the DN bit [OSPF-DN] in the LSA Options field MUST be set. This is used toensure that if any CE router sends this type 3 LSA to a PE router,the PE router will not redistribute it further.When a PE router needs to distribute to a CE router a route thatcomes from a site outside the latter’s OSPF domain, the PE routerpresents itself as an ASBR (Autonomous System Border Router), anddistributes the route in a type 5 LSA. The DN bit [OSPF-DN] MUST be set in these LSAs to ensure that they will be ignored by any other PE routers that receive them.There are deployed implementations that do not set the DN bit, butinstead use OSPF route tagging to ensure that a type 5 LSA generated by a PE router will be ignored by any other PE router that mayreceive it. A special OSPF route tag, which we will call the VPNRoute Tag (see Section 4.2.5.2), is used for this purpose. To ensure backward compatibility, all implementations adhering to thisspecification MUST by default support the VPN Route Tag proceduresspecified in Sections 4.2.5.2, 4.2.8.1, and 4.2.8.2. When it is nolonger necessary to use the VPN Route Tag in a particular deployment, its use (both sending and receiving) may be disabled byconfiguration.4.2.5.2. Use of OSPF Route TagsIf a particular VRF in a PE is associated with an instance of OSPF,then by default it MUST be configured with a special OSPF route tagvalue, which we call the VPN Route Tag. By default, this route tagMUST be included in the Type 5 LSAs that the PE originates (as theresult of receiving a BGP-distributed VPN-IPv4 route, see Section4.2.8) and sends to any of the attached CEs.The configuration and inclusion of the VPN Route Tag is required for backward compatibility with deployed implementations that do not set the DN bit in type 5 LSAs. The inclusion of the VPN Route Tag may be disabled by configuration if it has been determined that it is nolonger needed for backward compatibility.The value of the VPN Route Tag is arbitrary but must be distinct from any OSPF Route Tag being used within the OSPF domain. Its value MUST therefore be configurable. If the Autonomous System number of theVPN backbone is two bytes long, the default value SHOULD be anautomatically computed tag based on that Autonomous System number: Rosen, et al. Standards Track [Page 12]Tag = <Automatic = 1, Complete = 1, PathLength = 01>0 0 0 0 0 0 0 0 0 0 1 1 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2 2 2 2 3 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ |1|1|0|1| ArbitraryTag | AutonomousSystem | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+1 1 0 1 0 0 0 0 0 0 0 0 0 0 0 0 _AS number of the VPN Backbone_If the Autonomous System number is four bytes long, then a Route Tag value MUST be configured, and it MUST be distinct from any Route Tag used within the VPN itself.If a PE router needs to use OSPF to distribute to a CE router a route that comes from a site outside the CE router’s OSPF domain, the PErouter SHOULD present itself to the CE router as an Autonomous System Border Router (ASBR) and SHOULD report such routes as AS-externalroutes. That is, these PE routers originate Type 5 LSAs reportingthe extra-domain routes as AS-external routes. Each such Type 5 LSA MUST contain an OSPF route tag whose value is that of the VPN RouteTag. This tag identifies the route as having come from a PE router. The VPN Route Tag MUST be used to ensure that a Type 5 LSA originated by a PE router is not redistributed through the OSPF area to another PE router.4.2.5.3. Other Possible LoopsThe procedures specified in this document ensure that if routinginformation derived from a BGP-distributed VPN-IPv4 route isdistributed into OSPF, it cannot be redistributed back into BGP as a VPN-IPv4 route, as long as the DN bit and/or VPN route tag ismaintained within the OSPF domain. This does not eliminate allpossible sources of loops. For example, if a BGP VPN-IPv4 route isdistributed into OSPF, then distributed into RIP (where all theinformation needed to prevent looping is lost), and then distributed back into OSPF, then it is possible that it could be distributed back into BGP as a VPN-IPv4 route, thereby causing a loop.Therefore, extreme care must be taken if there is any mutualredistribution of routes between the OSPF domain and any thirdrouting domain (i.e., not the VPN backbone). If the third routingdomain is a BGP domain (e.g., the public Internet), the ordinary BGP loop prevention measures will prevent the route from reentering theOSPF domain.Rosen, et al. Standards Track [Page 13]。
RFC2617 鉴权 中文

Network Working Group J. FranksRequest for Comments: 2617 Northwestern UniversityObsoletes: 2069 P. Hallam-BakerCategory: Standards Track Verisign, Inc.J. HostetlerAbiSource, Inc.S. LawrenceAgranat Systems, Inc.P. LeachMicrosoft CorporationA. LuotonenNetscape Communications CorporationL. StewartOpen Market, Inc.June 1999HTTP Authentication: Basic and Digest Access Authentication备忘(Status of this Memo)本文档跟踪记录Internet团体为完善协议而进行的讨论、建议。
详情请参见官方文件(STD1)。
本文可任意分发。
版权声明(Copyright Notice)Copyright (C) The Internet Society (1999). All Rights Reserved. 摘要(Abstract)“HTTP/1.0”中包括基本访问鉴别方案(Basic Access Authentication scheme)。
该方案不是安全的用户授权方法(除非与其它安全方法联合使用,如SSL[5]),因为其用户名和口令在网络上是以明文方式传送的。
本文档还提供了HTTP鉴别框架的规范,有关原始的基本鉴别方案和基于哈希加密的方案的内容,请参见分类访问鉴别(Digest Acccess Authentication)。
从RFC2069公布以来,其中涉及的一些可选元素因为出现问题而被移出;而还有一些新的元素因为兼容性的原因而被加入,这些新元素虽然是可选的,但还是强烈建议使用的,因而,RFC2069[6]最终可能会被本规范所替代。
rfc4301翻译--第五章到第八章

5. IP Traffic Processing5.1. Outbound IP Traffic Processing (protected-to-unprotected)Figure 2. Processing Model for Outbound TrafficIPsec MUST 按以下步骤来处理出方向的包:Step 1.当包从保护区接口进来,调用SPD选择功能来获得SPD-ID,用这个SPD-ID来选择合适的SPD。
(如果设备只需用一个SPD,那该步可以忽略)Step 2.用该包的头来匹配从第一步中得到的SPD的缓存。
注意这个缓存包含了SPD-O和SPD-S 中的记录。
Step 3.a.如果匹配上,用匹配上的缓存记录来确定该包是要被透传、丢弃或是被AH/ESP保护。
如果IPsec处理应用后,就会产生一个从SPD缓存记录到SAD缓存记录的链接(用于指定模式、加密算法、密钥、SPI、PMTU等),注意SA PMTU值,和分配状态检查标志位(出方向包的IP头中的DF位)来决定是要在IPsec处理前分片还是处理后分片,或者必须丢弃掉用ICMPPMTU消息发送。
b.如果没有找到匹配的缓存,则查找SPD-ID指定的SPD(SPD-S和SPD-O部分)。
如果SPD 记录说是要透传或是丢弃,那么就创建一个或多个新的出方向SPD缓存记录;如果SPD记录说是要保护,也就是说要创建一个SA,那么就要用密钥管理机制(如IKEv2)来生产一个SA,如果SA成功生成,就创建一条新的出方向(SPD-S)缓存记录以及出方向和入方向的SAD 记录;如果不能成功生成SA,就丢弃这个包。
Step 4.这个包被传送到出口转发功能,来选择包要出去的接口。
这个功能也许会使这个包被传回到IPsec边界,进行另外的IPsec处理,比如说支持嵌套SAs。
如果是这样,MUST在SPD-I 数据库中有一条记录,允许入方向透传这个包,否则这个包将被丢弃。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Network Working Group L. Andersson, Ed. Request for Comments: 5037 Acreo AB Category: Informational I. Minei, Ed. Juniper Networks B. Thomas, Ed. Cisco Systems, Inc. October 2007 Experience with the Label Distribution Protocol (LDP)Status of This MemoThis memo provides information for the Internet community. It doesnot specify an Internet standard of any kind. Distribution of thismemo is unlimited.AbstractThe purpose of this memo is to document how some of the requirements specified in RFC 1264 for advancing protocols developed by workinggroups within the IETF Routing Area to Draft Standard have beensatisfied by LDP (Label Distribution Protocol). Specifically, thisreport documents operational experience with LDP, requirement 5 ofsection 5.0 in RFC 1264.Table of Contents1. Introduction (2)2. Operational Experience (2)2.1. Environment and Duration (2)2.2. Applications and Motivation (3)2.3. Protocol Features (3)2.4. Security Concerns (4)2.5. Implementations and Inter-Operability (4)2.6. Operational Experience (4)3. Security Considerations (5)4. Acknowledgments (5)5. References (6)5.1. Normative References (6)5.2. Informative References (6)Andersson, et al. Informational [Page 1]1. IntroductionThe purpose of this memo is to document how some of the requirements specified in [RFC1264] for advancing protocols developed by workinggroups within the IETF Routing Area to Draft Standard have beensatisfied by LDP. Specifically, this report documents operationalexperience with LDP, requirement 5 of section 5.0 in RFC 1264.LDP was originally published as [RFC3036] in January 2001. It wasproduced by the MPLS Working Group of the IETF and was jointlyauthored by Loa Andersson, Paul Doolan, Nancy Feldman, AndreFredette, and Bob Thomas. It has since been obsoleted by [RFC5036].2. Operational ExperienceThis section discusses operational experience with the protocol. The information is based on a survey sent to the MPLS Working Group inOctober 2004. The questionnaire can be found in the MPLS WorkingGroup mail archives for October 2004.11 responses were received, all but 2 requesting confidentiality.The survey results are summarized to maintain confidentiality. Thenetworks surveyed span different geographic locations: US, Europe,and Asia. Both academic and commercial networks responded to thesurvey.2.1. Environment and DurationThe size of the deployments ranges from less than 20 Label Switching Routers (LSRs) to over 1000 LSRs. Eight out of the 11 deploymentsuse LDP in the edge and the core, two on the edge only, and one inthe core only.Sessions exist to peers discovered via both the basic and theextended discovery mechanisms. In half the cases, more than oneadjacency (and as many as four adjacencies) are maintained persession. The average number of LDP sessions on an LSR ranges fromunder 10 to just over 80. The responses are spread out as follows:under 10: 4 responses, 20-50: 4 responses, and over 80: 1 response.In the surveyed networks, the time LDP has been deployed ranges from under 1 year to over 4 years. The responses are spread out asfollows: under 1 year: 3 responses, 2 years: 2 responses, 3 years: 3 responses, and over 4 years: 3 responses.Andersson, et al. Informational [Page 2]2.2. Applications and MotivationNine of the 11 responses list Layer 3 Virtual Private Networks(L3VPNs) as the application driving the LDP deployment in thenetwork.The list of applications is as follows: L3VPNs: 9, pseudowires: 4current (and one planned deployment), L2VPNs: 4, forwarding based on labels: 2, and BGP-free core: 1.There are two major options for label distribution protocols, LDP and Resource Reservation Protocol-Traffic Engineering (RSVP-TE). One of the key differences between the two is that RSVP-TE has support fortraffic engineering, while LDP does not. The reasons cited forpicking LDP as the label distribution protocol are:o The deployment does not require traffic engineering - 6o Inter-operability concerns if a different protocol is used - 5 o Equipment vendor only supports LDP - 5o Ease of configuration - 4o Ease of management - 3o Scalability concerns with other protocols - 3o Required for a service offering of the service provider - 12.3. Protocol FeaturesAll deployments surveyed use the Downstream Unsolicited LabelDistribution mode. All but one deployment use Liberal Labelretention (one uses conservative).LSP setup is established with both independent and Ordered Control.Five of the deployments use both control modes in the same network.The number of LDP Forwarding Equivalence Classes (FECs) advertisedand LDP routes installed falls in one of two categories: 1) roughlythe same as the number of LSRs in the network and 2) roughly the same as the number of IGP routes in the network. Of the 8 responses that were received, 6 were in the first category and 2 in the second. Andersson, et al. Informational [Page 3]2.4. Security ConcernsA security concern was raised by one of the operators with respect to the lack of a mechanism for securing LDP Hellos.2.5. Implementations and Inter-OperabilityEight of the 11 responses state that more than one implementation(and as many as four different ones) are deployed in the samenetwork.The consensus is that although implementations differ, no inter-operability issues exist. The challenges listed by providers running multiple implementations are:o Different flexibility in picking for which FECs to advertiselabels.o Different flexibility in setting transport and LDP router-idaddresses.o Different default utilization of LDP labels for trafficresolution. Some vendors use LDP for both VPN and IPv4 traffic forwarding, while other vendors allow only VPN traffic toresolve via LDP. The challenge is to restrict the utilization of LDP labels to VPN traffic in a mixed-vendor environment.o Understanding the differences in the implementations.2.6. Operational ExperienceIn general, operators reported stable implementations and steadyimprovement in resiliency to failure and convergence times over theyears. Some operators reported that no issues were found with theprotocol since deploying.The operational issues reported fall in three categories:1. Configuration issues. Both the session and adjacency endpoints must be allowed by the firewall filters. Misconfiguration ofthe filters causes sessions to drop (if already established) or not to establish.2. Vendor bugs. These include traffic blackholing, unnecessarylabel withdrawals and changes, session resets, and problemsmigrating from older versions of the technology. Most reports stated that the problems reported occurred in early versions of the implementations.Andersson, et al. Informational [Page 4]3. Protocol issues.- The synchronization required between LDP and the IGP waslisted as the main protocol issue. Two issues werereported: 1) slow convergence, due to the fact that LDPconvergence time is tied to the IGP convergence time, and 2) traffic blackholing on a link-up event. When an interfacecomes up, the LDP session may come up slower than the IGPsession. This results in dropping MPLS traffic for a link- up event (not a failure but a restoration). This issue isdescribed in more detail in [LDP-SYNC].- Silent failures. Failure not being propagated to the headend of the LSP when setting up LSPs using independentcontrol.3. Security ConsiderationsThis document is a survey of experiences from deployment of LDPimplementations; it does not specify any protocol behavior. Thus,security issues introduced by the document are not discussed.4. AcknowledgmentsThe editors would like to thank the operators who participated in the survey for their valuable input: Shane Amante, Niclas Comstedt, Bruno Decraene, Mourad Kaddache, Kam Lee Yap, Lei Wang, and Otto Kreiter.Not all who participated are listed here, due to confidentialityrequests. Those listed have given their consent.Also, a big thank you to Scott Bradner, who acted as an independentthird party ensuring anonymity of the responses.The editors would like to thank Rajiv Papneja, Halit Ustundag, andLoa Andersson for their input to the survey questionnaire.Andersson, et al. Informational [Page 5]5. References5.1. Normative References[RFC1264] Hinden, R., "Internet Engineering Task Force InternetRouting Protocol Standardization Criteria", RFC 1264,October 1991.[RFC3036] Andersson, L., Doolan, P., Feldman, N., Fredette, A., and B. Thomas, "LDP Specification", RFC 3036, January 2001.[RFC3815] Cucchiara, J., Sjostrand, H., and J. Luciani, "Definitions of Managed Objects for the Multiprotocol Label Switching(MPLS), Label Distribution Protocol (LDP)", RFC 3815, June 2004.5.2. Informative References[RFC5036] Andersson, L., Minei, I., and B. Thomas, "LDPSpecification", RFC 5036, October 2007.[LDP-SYNC] Jork, M., Atlas, A., and L. Fang, "LDP IGPSynchronization", Work in Progress, July 2007.Editors’ AddressesLoa AnderssonAcreo ABIsafjordsgatan 22Kista, SwedenEMail: loa.andersson@acreo.seloa@pi.seIna MineiJuniper Networks1194 N.Mathilda AveSunnyvale, CA 94089EMail: ina@Bob ThomasCisco Systems, Inc.1414 Massachusetts AveBoxborough, MA 01719EMail: rhthomas@Andersson, et al. Informational [Page 6]Full Copyright StatementCopyright (C) The IETF Trust (2007).This document is subject to the rights, licenses and restrictionscontained in BCP 78, and except as set forth therein, the authorsretain all their rights.This document and the information contained herein are provided on an "AS IS" basis and THE CONTRIBUTOR, THE ORGANIZATION HE/SHE REPRESENTS OR IS SPONSORED BY (IF ANY), THE INTERNET SOCIETY, THE IETF TRUST AND THE INTERNET ENGINEERING TASK FORCE DISCLAIM ALL WARRANTIES, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTY THAT THE USE OF THE INFORMATION HEREIN WILL NOT INFRINGE ANY RIGHTS OR ANY IMPLIEDWARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Intellectual PropertyThe IETF takes no position regarding the validity or scope of anyIntellectual Property Rights or other rights that might be claimed to pertain to the implementation or use of the technology described inthis document or the extent to which any license under such rightsmight or might not be available; nor does it represent that it hasmade any independent effort to identify any such rights. Information on the procedures with respect to rights in RFC documents can befound in BCP 78 and BCP 79.Copies of IPR disclosures made to the IETF Secretariat and anyassurances of licenses to be made available, or the result of anattempt made to obtain a general license or permission for the use of such proprietary rights by implementers or users of thisspecification can be obtained from the IETF on-line IPR repository at /ipr.The IETF invites any interested party to bring to its attention anycopyrights, patents or patent applications, or other proprietaryrights that may cover technology that may be required to implementthis standard. Please address the information to the IETF atietf-ipr@.Andersson, et al. Informational [Page 7]。
