S T L a l g o r i t h m 算 法 r e m o n v e , r e m o v e _ i f ( 2 0 2 0 )
a b c d e f g h i j k l m n o p q r s t u v w x y z

a b c d e f g h i j k l m n o p q r s t u v w x y z注:(1)r、v两个字母用来拼写普通话和外来语,拼写广州话时不用。
(2)广州话拼音字母有三个附加符号:ê、é、ü,其中é是和汉语拼音字母不同的。
这几个字母是e、u字母的变体,叫不列入表内。
二、声母表b波p婆m摸f科d多t拖n挪l罗g哥k卡ng我h何gu姑ku箍z左c初s梳j知q雌x思y也w华注:(1)z、c、s和j、q、x两组声母,广州话的读音没有区别,只是在拼写韵母时有不同,z、c、s拼写a、o、é及a、o、e、é、ê、u等字母开头的韵母,例如:za渣,ca茶,xa沙。
j、q、x拼写i、ü及i、ü字母开头的韵母,例如:ji知,qi次,xi思。
(2)gu姑、ku箍是圆唇的舌跟音,作为声母使用,不能单独注音,单独注音时是音节,不是声母。
(3)y也,w华拼音时作为声母使用,拼写出来的音节相当于汉语拼音方案的复韵母,但由于广州话当中这些韵母前面不再拼声母,因此只作为音节使用三、韵母表a呀o柯u乌i衣ū于ê(靴) é诶m唔n五ai挨 ei矮 oi哀 ui会éi(非)ao拗 eo欧 ou奥iu妖êu(去)am(监) em庵im淹an晏 en(恩) on安 un碗in烟ūn冤 ên(春)ang(横) eng莺 ong(康) ung瓮ing英êng(香) éng(镜)ab鸭 eb(急) ib叶ad押 ed(不) od(渴) ud活 id热ūd月 êd(律)ag(客) eg(德) og恶 ug屋 ig益êg(约) ég(尺)注:(1)例字外加( )号的,只取其韵母。
(2)i行的韵母,前面没有声母的时候,写成yi衣,yiu妖,yim淹,yin烟,ying 英,yib叶,yid热,yig益。
国际贸易英文缩写常用语

国际贸易英文缩写常用语国际贸易英文缩写常用语CFR(cost and freight)成本加运费价 D/P(document against payment)付款交单 C.O (certificate of origin)一般原产地证 CTN/CTNS(carton/cartons)纸箱DL/DLS(dollar/dollars)美元PKG(package)一包,一捆,一扎,一件等 G.W.(gross weight)毛重C/D (customs declaration)报关单 W (with)具有FAC(facsimile)传真EXP(export)出口MIN (minimum)最小的,最低限度 M/V(merchant vessel)商船MT或M/T(metric ton)公吨INT(international)国际的INV (invoice)发票REF (reference)参考、查价STL.(style)式样、款式、类型RMB(renminbi)人民币PR或PRC(price) 价格S/C(sales contract)销售确认书 B/L (bill of lading)提单CIF (cost,insurance&freight)成本、保险加运费价T/T(telegraphic transfer)电汇 D/A (document against acceptance)承兑交单 G.S.P.(generalized system of preferences)普惠制PCE/PCS(piece/pieces)只、个、支等 DOZ/DZ(dozen)一打WT(weight)重量N.W.(net weight)净重EA(each)每个,各w/o(without)没有IMP(import)进口卧冰求鲤缩写 贸易频道助你今年发大财MAX (maximum)最大的、最大限度的 M 或MED (medium)中等,中级的S.S(steamship)船运DOC (document)文件、单据P/L (packing list)装箱单、明细表PCT (percent)百分比EMS (express mail special)特快传递T或LTX或TX(telex)电传S/M (shipping marks)装船标记PUR (purchase)购买、购货L/C (letter of credit)信用证交货delivery 轮船steamship(缩写S.S) 装运、装船shipment 租船charter (the chartered shep) 交货时间 time of delivery 定程租船voyage 定期租船time charter 贸易英语缩写 charter; 装运期限time of shipment 助你发展商机托运人(一般指出口商)shipper,consignor 世界贸易组织的缩写助你发展商机收货人consignee 贸易法规缩写班轮regular shipping liner 驳船lighter 舱位shipping space 油轮tanker 佛山二手()报关clearance of goods 陆运收据cargo receipt 国际贸易英文缩写要卖东西,当然选择佛山同城网提货to take delivery of goods 国际组织缩写空运提单airway bill 正本提单original B\\L选择港(任意港)optional port选港费optional charges 世界贸易组织的缩写选港费由买方负担 optional charges to be borne by the Buyers 或optional charges for Buyers\'account 国际的英文缩写佛山同城交易()一月份装船 shipment during January 或 January shipment 贸易英语缩写佛山二手() 一月底装船 shipment not later than Jan.31st.或shipment on or before Jan.31st. 国际的英文缩写一/二月份装船 shipment during Jan./Feb.或 Jan./Feb. shipment 贸易法规缩写 在......(时间)分两批装船 shipment during....in two lots 国际贸易英文缩写广州同城交易()在......(时间)平均分两批装船 shipment during....in two equal lots 贸易英语缩写分三个月装运 in three monthly shipments贸易法规缩写 进注,轻松让你寻找客户分三个月,每月平均装运 in three equal monthly shipments 国际贸易英文缩写要卖东西,当然选择佛山同城网立即装运 immediate shipments贸易英语缩写助你发展商机即期装运 prompt shipments 贸易英语缩写收到信用证后30天内装运 shipments within 30 days after receipt ofL/C 国际的英文缩写 允许分批装船 partial shipment not allowed partial shipment not permitted partial shipment notunacceptable国际的英文缩写本文来源佛山同城交易网AAA制自动许可制AAC 亚非会议A.A.R 保综合险(一切险) ABCコ,ド ABC商业密码 ac. 英亩a/c(或A/C) 银行往来存款 acpt 承兑;接受a/cs pay. 应付帐款 a/cs rec. 应收帐款 ACU 亚洲清算同盟 A/D 出票后ADB 亚洲开发银行 a.f. 预付运费AFA 自动外汇分配制度 AFDB 非洲开发银行 A.F.E.B. 核准的外汇银行 agcy 代理公司agt. 代理人AIQ制自动进口配额制 A.M. 互相保险A.N. 到货通知A/P 委托付款证A/P 委托购买证A/P 附加保险费A/P 付讫APO 亚洲生产率组织 APU 亚洲支付同盟 A/R 综合险,一切险 A/S 销货帐单A/S 见票后A/S 见票即付ASEAN 东南亚国家联盟 ASP 美国销售价格 ATAカルネ暂时许可簿册,临时过境证A.T.L. 实际全损A/V 从价A/W 实际重量A.W.B. 空运单国际组织缩写BB/Aレ,ト银行承兑利率 B/B 买入汇票B/C 托收汇票B/D 银行贴现B/D 银行汇票B/E 入港申报单B/E 汇票BETRO 英国出口贸易研究组织BIS 国际清算银行 B/G 保税货物B/L 提单B/N 钞票B/N 交货记录B.O. 分公司B.P. 应付票据B.R. 应收票据B/S 再进口免税证 B/St 即票BTN 布鲁塞尔税则分类 B.T.T. 银行电汇CC.A.D. 凭单付款C.B.D. 交货前付款 C.B.S. 装船前预付货款 C/C 商会C.C. 时价CCC 关税合作理事会 CCCN 关税合作理事会税则分类表C.F.S. 集装箱货运站 C.H. 货舱C.H. 票据交换所C.H. 海关Chq. 支票C.I. 领事签证发票 C/I 保险证书CIF関税込条件成本,保险费,运费加关税条件CIF条件成本,保险加运费条件CIF通関费用込条件成本,保险费,运费和一切进口费用条件世界贸易组织的缩写 CIF,C条件成本,保险费,运费加佣金条件CIFに関する国际统一规则 CIF买卖契约统一规则C.L.货物「コ」 (集装箱)整箱货CLP 装箱单C/N 发货通知单C/N 贷记通知书C/O 转交C/O 产地证明书C.O.D. 交货付款 C.O.F.C. 平板车装运集装箱COGSA 海洋货物运输法 cont. 合同c.o.s. 装船时付款 C/P 租船合同C.Q.D. 习惯快速装卸 C.T. 载货吨位C.t.l. 推定全损 C.W.O. 订货付款DD/A 承兑交单D/C 绕航条款D/C 贴现,折扣D/D 码头交货D/D 即期汇票,跟单汇票 D/F 空舱运费D/M 速遣费D/N 借记通知D/O 交货单,出货单 D/P 付款交单D.P.V. 完税价格 D.R. 码头收据d.t. 交货时间DW 载重量D/W 码头栈单D.W.T. 载重吨位 DWTC 载货吨EECAFE(UN) 亚洲及远东经济委员会 ECE 欧洲经济委员会国际组织缩写佛山同城交易()ECM 欧洲共同市场E/D 出口申报单EEC 欧洲经济共同体EFTA 欧洲自由贸易联盟E/L 出口许可证EMA 欧洲货币协定EPU 欧洲支付同盟ESCAP(UN) 亚洲及太平洋经济社会委员会 ETA 预计到达时间TTD 预计离港时间ETE 预计开航时间exch. 兑换,汇兑;交易所exd 已查,已检验作者: 夜半一点钟 2006-2-9 02:38 回复此发言--------------------------------------------------------------------------------2 国际贸易术语英文缩写FFA 外汇配额制度F.A 货物运送代理行f.a.a. 一切海损不赔F.A.K.「コ」同一费率F.A.Q. 良好平均质量,大路货 F.A.S. 启运地船边交大货价 F.B. 运费单F.B.E. 外国汇票FC,S约款「保」捕获拘留除外条款 FCL 整箱货FCL 整装集装箱f/d 自由港FEFC 远东水脚公会f.f.a 船边交货f.g.a 共同海损不赔F/L 运价表国际贸易英文缩写佛山二手()F.M. 不可抗力f.q. 实盘FOB 船上交货价FOR 火车上交货价FOT 卡车上交货价F.P.A. 单独海损不赔 frt.pd. 运费已付frt.ppd. 运费预付F.W.D. 淡水损失fy.pd. 付讫GG.A 共同海损g.b.q. 故障货物G.M.Q. 上好可销品质 G.N.P. 国民生产总值 Gr.R.T. 注册总吨grs.wt. 毛重GT 总吨位G.T.C. 撤销前有效G.T.M. 本月中有效G.T.W. 本周中有效HHKD 港币H.O. 总公司Hr 港口II.B.R.D. 联合国国际复兴开发银行I.C.C. 国际商会ICHCA 国际货物装卸协调联合会 I/D 进口申报单IFC 国际金融公司I/L 进口许可IMF 国际货币基金组织 IMF借款国际货币基金信贷 IMF引出権国际货币基金组织提款权INCOTERMS 国际贸易条件解释通则INTRADE 国际贸易发展协会 I.O.P. 不论损失率如何全部赔偿卧冰求鲤缩写IQ制进口配额制 I/R 汇入汇款ITC 国际贸易中心 ITC 国际贸易宪章 ITO 国际贸易组织 IUMI 国际海上保险联盟LL/A 卸货代理行 L/A 授权书LASH 载驳船L/C 信用证L/G 保证书L/H 质押证书L/I 赔偿保证书 Lkg 漏损LT 书信电报l.t.,L/T 长吨,英吨 LWL 载重线Mmarg. 保证金m/d 出票日后……个月(付款)MEA 制造厂商外销代理人M/F 舱单,载货单 MFN 最惠国M.I 海上保险min. 最低限度M.I.P. 海上保险单 mk 包装标志M/Lクロ,ズ溢短装条款M/O 汇款单M/R 大副收据M.T. 信汇M/T 公吨Nn/a 拒绝承兑,不接受 N/C 新租船契约N.C.V. 无商业价值 N/F (银行)无存款 N.G. 纯收益N.L. 纯损,净损失 N/M 无装运标志N.N. (票据)无签名 N/R 备装通知NRクロ,ズ免责条款 N/S 无存货N.S.F. 存款不足 NTB 非关税壁垒N.U. 船名不详NW,N.wt. 净重OOAEC 亚洲经济合作组织 O/B 开证银行O/C 货港未定租船合同 O/D 见票即付O.E.C.D. 经济合作与发展组织O.F. 海运运费O.G.L. 公开一般许可证 OR 船舶所有人承担风险 O/R 汇出汇款ovld. 过载PP/A 单独海损P.,L. 损益payt. 支付,付款 pd 付讫,通过P.D. 港务费p.l. 部分损失pm. 保费P/N 期票P.O.C. 停靠港P.O.D. 交货时付款 P.O.R. 避难港QQ 检疫Q/D 快递件,快速装卸 qlty. 品质quotn 报价,行市quty. 数量Rrd. 收讫R/D 与出票人接洽 R.D.C. 碰撞条款rept. 收据R.F.W.D. 雨淋淡水损害国际贸易英文缩写贸易频道助你今年发大财SS.C. 救助费S.D. 海损S.D. 装运单据s.d. 交货不足S/D 即期汇票SDR 特别提款权sgd 已签署SHEX 星期日和假日除外 SHINC 星期日和假日包括在内 sig. 签署SITC 标准国际贸易分类 S.L. 海难救助损失 S/N 装船通知单S.O. 卖方选择S/O 装货单SP 起运港spec. 说明书,规格 S.R. 本船收货单S.R. 货运收据,装货收据 S/S 轮船S.S.B.C. 沉没,触碓,火灾和碰撞S.T. 短吨stg. 英镑stor. 存仓费,栈租Ttfr. 转帐,过户 T.L. 全损T.L.O. 仅保全损 T.M.O. 电汇票T.P.N.D. 偷窃及提货不着险T/R 信托收据T/T 电汇T.T.B. 买入电汇 T.T.P. 应付电汇 T.T.R. 应收电汇WW.A. 承保单独海损,水渍险W/R 战争险w.r. 仓库收据W/W 仓单W/Wクロ,ズ仓至仓条款。
音标中文谐音表
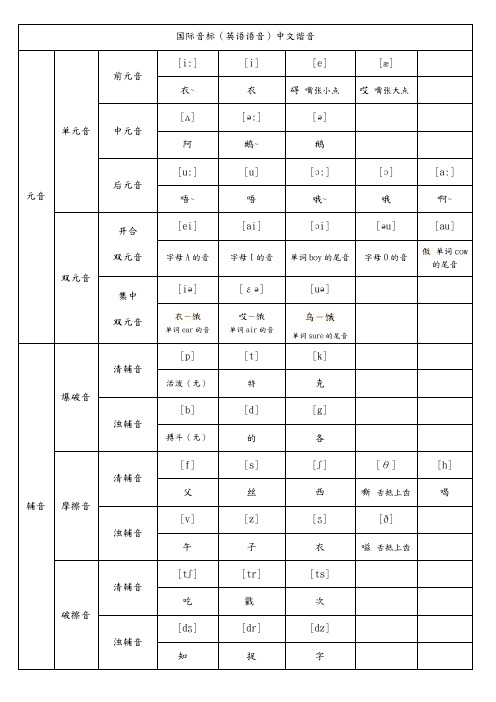
/i:/ bee/bi:/ feet/fi:t/ keep/ki:p/ key/ki:/ team/ti:m/ meet/mi:t/ /i/ it /it/ big/big/ city/siti/ give/giv/ sick/sik//e/ get/get/ best/best/ text/tekst/ help/help//æ/ fat/fæt/ have/hæv/ cat/kæt/ back/bæk/ hat/hæt//a:/ laugh/la:f/ glass/gla:s/ half/ha:f/ farm/fa:m/ park/pa:k// ɔ:/ horse/hɔ: s/ saw/sɔ:/ corn/kɔ:n/ course/kɔ:s/ salt/sɔ:t// ɔ / dog/dɔg/ pot/pɔt/ cost/kɔst/ what/wɔt/ honest/′ɔnist//u:/ food/fu:d/ moon/mu:n/ rule/ru:l/ loose/lu:s/ noon/nu:n//u/ book/buk/ put/put/ good/gud/ would/wud/ could/kud// ʌ / must/mʌst/ does/dʌz/ money/′mʌni/ ugly/′ʌgli/ come/kʌm//ə:/ nurse/nə:s/ bird/bə:d/ burn/bə:n/ turn/tə:n/ girl/gə:l//ə / better/betə/ never/nevə/ worker/wə:kə/ welcome/welkəm//ei/ may/mei/ name/neim/ game/geim/ eight/eit/ age/eidʒ//əu/ no/nəu/ home/həum/ hope/həup/ wrote/rəut/ note/nəut/ pose/pəuz//ai/ eye/ai/ time/taim/ buy/bai/ right/rait/ bike/baik/ kite/kait//au/ now/nau/ out/aut/ how/hau/ about/ ə′baut/ south/sauθ/ house/haus/ /ɔi/ boy/bɔi/ toy/tɔi/ noise/nɔiz/ voice/vɔis/ point/pɔint//iə/ ear/iə/ near/niə/ idea/ai′diə/ hear/hiə/ mere/miə/ spear/spiə/ /εə/ air/εə/ tear/tεə/ care/kεə/ dare/dεə/ fair/fεə/ there/ðεə//uə/ tour/tuə/ poor/puə/ sure/ʃuə/ moor/muə/(停泊) your/juə//p/ pea/pi:/ pie/pai/ top/tɔp/ cap/kæp/ people/pi:pl/ pride/praid//b/ bee/bi:/ by/bai/ buy/bai/ black/blæk/ bear/bεə//t/ let/let/ sat/sæt/ feet/fi:t/ team/ti:m/ tide/taid//d/ led/led/ sad/sæd/ feed/fi:d/ do/du:/ dear/diə//k/ lack/læk/ take/teik/ clock/klɔk/ class/kla:s/ weekend/′wi:kend//g/ big/big/ lag/læg/ glass/gla:s/ gum/gʌm/ good/gud/ guest/gest//f/ face/feis/ fast/fa:st/ leaf/li:f/ surf/sə:f/ favorite/′feivərit//v/ very/′veri/ five/faiv/ fever/′fi:və/ serve/sə:v/ never/′nevə//θ/ bath/ba:θ/(v洗澡) thick/θik/ mouth/mauθ/ breath/breθ/(n呼吸) /ð/ the/ ðə/ they/ðei/ that/ðæt/ mother/′mʌðə/ thus/ ðʌs/ then/ðen//s/ face/feis/ mouse/maus/ cakes/keiks/ caps/kæps/ likes/laiks//z/ close/kləuz/ keys/ki:z/ boys/bɔiz/ pens/penz/ halves/ha:vz//tʃ/ catch/kætʃ/ cheep/tʃi:p/ rich/ritʃ/ watch/wtʃ/ child/tʃaild//dʒ/ orange/′ɔridʒ/ large/la:dʒ/ juice/dʒu:s/ job/dʒɔb//tr/ tree/tri:/ try/trai/ true/tru:/ trouble/traubl/ track/træk//dr/ dry/drai/ dream/dri:m/ dress/dres/ drink/driŋk/ hundred/′hʌndrid//ʃ/ she/ʃi:/ sharp/ʃa:p/ fish/fiʃ/ shock/ʃɔk/ shoe/ʃu://ʒ/ pleasure/′pleʒə/ measure/′meʒə/ television/′teliviʒən//ts/ let′s/lets/ sports/spɔ:ts/ puts/puts/ writes/raits/ seats/si:ts//dz/ hands/hændz/ birds/bə:dz/ friends/freindz/ beds/bedz//h/ he/ hi:/ hard/ha:d/ him/him/ heard/hə:d/ half/ha:f//l/ like/laik/ late/leit/ learn/lə:n/ lead/li:d/ light/lait//m/ my/mai/ more/mɔ:/ seem/si:m/ meat/mi:t/ mind/maind/ men/men//n/ nice/nais/ wind/waind/ mind/maind/ rain/rein/ fine/fain//ŋ/ sing/siŋ/ wing/wiŋ/ ring/riŋ/ long/lɔŋ/ beautiful/bju:təfl//j/ you/ju:/ few/fju:/ yard/ja:d/ music/′mju:zik/ student/′stju:dnt//w/ work/wə:k/ way/wei/ well/wel/ what/wɔt/ twelve/twelv/ twin/twin/ /r/ red/red/ road/rəud/ write/rait/ wrong/rɔŋ/ problem/′prɔbləm/附:常见的字母与字母组合发音规则元音字母及元音字母组合拼读规则元音字母的发音元音字母a重读开音节 [ei] paper ; late ; make ; lake ; face重读闭音节[æ] bag ; fat ; cat ; lad der ; mass(*例外:any一些[e] ;many许多[e])非重读音节 [ə]或[i]即:[ə]—— ago ; along ; among ; above ; aloud[i]—— comrade ; village ; manager ; palace ; private ;necklace*连续相同的辅音(字母),一般只发一个音,而且归属后一个音节段。
高中物理公式有哪些

高中物理公式有哪些高中物理公式有哪些_知识点在高中的阶段里,有很多的同学是非常想知道,高中物理公式有哪些,怎么快速记忆物理公式呢,为了方便大家学习借鉴,下面小编精心准备了高中物理公式有哪些内容,欢迎使用学习!高中物理公式有哪些1)匀变速直线运动1.平均速度V平=s/t(定义式)2.有用推论Vt2-Vo2=2as3.中间时刻速度Vt/2=V平=(Vt+Vo)/24.末速度Vt=Vo+at5.中间位置速度Vs/2=[(Vo2+Vt2)/2]1/26.位移s=V平t=Vot+at2/2=Vt/2t7.加速度a=(Vt-Vo)/t {以Vo为正方向,a与Vo同向(加速)a 反向则a 0}8.实验用推论Δs=aT2 {Δs为连续相邻相等时间(T)内位移之差}注:(1)平均速度是矢量;(2)物体速度大,加速度不一定大;(3)a=(Vt-Vo)/t只是量度式,不是决定式;2)自由落体运动1.初速度Vo=02.末速度Vt=gt3.下落高度h=gt2/2(从Vo位置向下计算)4.推论Vt2=2gh(3)竖直上抛运动1.位移s=Vot-gt2/22.末速度Vt=Vo-gt (g=9.8m/s2≈10m/s2)3.有用推论Vt2-Vo2=-2gs4.上升最大高度Hm=Vo2/2g(抛出点算起)5.往返时间t=2Vo/g (从抛出落回原位置的时间)1)平抛运动1.水平方向速度:Vx=Vo2.竖直方向速度:Vy=gt3.水平方向位移:x=Vot4.竖直方向位移:y=gt2/25.运动时间t=(2y/g)1/2(通常又表示为(2h/g)1/2)6.合速度Vt=(Vx2+Vy2)1/2=[Vo2+(gt)2]1/2合速度方向与水平夹角β:tgβ=Vy/Vx=gt/V07.合位移:s=(x2+y2)1/2,位移方向与水平夹角α:tgα=y/x=gt/2Vo8.水平方向加速度:ax=0;竖直方向加速度:ay=g2)匀速圆周运动1.线速度V=s/t=2πr/T2.角速度ω=Φ/t=2π/T=2πf3.向心加速度a=V2/r=ω2r=(2π/T)2r4.向心力F心=mV2/r=mω2r=mr(2π/T)2=mωv=F合5.周期与频率:T=1/f6.角速度与线速度的关系:V=ωr7.角速度与转速的关系ω=2πn(此处频率与转速意义相同)3)万有引力1.开普勒第三定律:T2/R3=K(=4π2/GM){R:轨道半径,T:周期,K:常量(与行星质量无关,取决于中心天体的质量)} 2.万有引力定律:F=Gm1m2/r2 (G=6.67×10-11Nm2/kg2,方向在它们的连线上)3.天体上的重力和重力加速度:GMm/R2=mg;g=GM/R2 {R:天体半径(m),M:天体质量(kg)}4.卫星绕行速度、角速度、周期:V=(GM/r)1/2;ω=(GM/r3)1/2;T=2π(r3/GM)1/2{M:中心天体质量}5.第一(二、三)宇宙速度V1=(g地r地)1/2=(GM/r地)1/2=7.9km/s;V2=11.2km/s;V3=16.7km/s6.地球同步卫星GMm/(r地+h)2=m4π2(r地+h)/T2{h≈36000km,h:距地球表面的高度,r地:地球的半径}注:(1)天体运动所需的向心力由万有引力提供,F向=F万;(2)应用万有引力定律可估算天体的质量密度等;(3)地球同步卫星只能运行于赤道上空,运行周期和地球自转周期相同;(4)卫星轨道半径变小时,势能变小、动能变大、速度变大、周期变小(一同三反);(5)地球卫星的最大环绕速度和最小发射速度均为7.9km/s。
临床常用生化检验项目参考区间

I C S11.100C50中华人民共和国卫生行业标准W S/T404.6 2015临床常用生化检验项目参考区间第6部分:血清总钙㊁无机磷㊁镁㊁铁R e f e r e n c e i n t e r v a l s f o r c o m m o n c l i n i c a l b i o c h e m i s t r y t e s t sP a r t6:S e r u mc a l c i u m,p h o s p h o r u s,m a g n e s i u m,i r o n2015-04-21发布2015-10-01实施前言W S/T404‘临床常用生化检验项目参考区间“分为8个部分:第1部分:血清丙氨酸氨基转移酶㊁天门冬氨酸氨基转移酶㊁碱性磷酸酶和γ-谷氨酰基转移酶;第2部分:血清总蛋白㊁白蛋白;第3部分:血清钾㊁钠㊁氯;第4部分:血清总胆红素㊁直接胆红素;第5部分:血清尿素㊁肌酐;第6部分:血清总钙㊁无机磷㊁镁㊁铁;第7部分:血清乳酸脱氢酶㊁肌酸激酶;第8部分:血清淀粉酶㊂本部分为W S/T404的第6部分㊂本部分按照G B/T1.1 2009给出的规则起草㊂本部分主要起草单位:中国医科大学附属第一医院㊁中国人民解放军第四军医大学附属第一医院㊁复旦大学附属中山医院㊁北京大学第三医院㊁四川大学华西医院㊁广东省中医院㊁北京医院㊂本部分起草人:尚红㊁郝晓柯㊁潘柏申㊁张捷㊁王兰兰㊁黄宪章㊁陈文祥㊁张传宝㊁申子瑜㊁穆润清㊁赵敏㊂临床常用生化检验项目参考区间第6部分:血清总钙㊁无机磷㊁镁㊁铁1 范围W S /T404的本部分规定了中国成年人群血清总钙㊁无机磷㊁镁㊁铁的参考区间及其应用㊂本部分适用于医疗卫生机构实验室血清总钙㊁无机磷㊁镁㊁铁检验结果的报告和解释,相关体外诊断产品生产厂商也可参照使用㊂2 规范性引用文件下列文件对于本文件的应用是必不可少的㊂凡是注日期的引用文件,仅注日期的版本适用于本文件㊂凡是不注日期的引用文件,其最新版本(包括所有的修改单)适用于本文件㊂W S /T402 临床实验室检验项目参考区间的制定3 术语和定义W S /T402界定的术语和定义适用于本文件㊂4 参考区间建立4.1 中国成年人群(20~79岁)血清总钙㊁无机磷㊁镁㊁铁参考区间见表1㊂表1 中国成年人群血清总钙㊁无机磷㊁镁㊁铁参考区间项目单位分组参考区间血清总钙(C a )mm o l /L 男/女2.11~2.52血清无机磷(I P )mm o l /L 男/女0.85~1.51血清镁(M g)mm o l /L 男/女0.75~1.02血清铁(I r o n)μm o l /L 男10.6~36.7女7.8~32.24.2 中国成年人群血清总钙㊁无机磷㊁镁㊁铁参考区间建立过程的相关信息参见附录A ㊂5 参考区间应用5.1 一般原则5.1.1 临床实验室应首先考虑引用本文件的参考区间㊂注1:参考区间建立研究工作量和成本巨大,临床实验室引用参考区间比自己建立参考区间更为现实㊁可行㊂注2:本参考区间基于中国成年人群多中心研究结果,研究中的检验结果可溯源至国际公认参考方法或标准物质,参见附录W S/T404.6 20155.1.2使用本文件的参考区间前应进行必要的验证或评估㊂注1:外部参考区间在实验室的适用性主要取决于实验室与参考区间建立时检验结果的可比性和人群的适用性㊂注2:检验结果只有存在恒定的系统偏倚(检验结果正确度)才影响参考区间的适用性,过大的实验室内变异是实验室分析质量问题,不是参考区间适用性问题㊂注3:本文件的参考区间基于血清的检测结果建立,若临床实验室使用的标本类型为血浆,应进行适当的评估以决定是否采用本参考区间㊂5.2参考区间评估㊁验证和使用5.2.1按W S/T402的有关规定进行参考区间评估和验证㊂5.2.2如实验室确认与参考区间建立时的检验结果可比且人群适用,则可直接引用本文件的参考区间,若不确定或基于实验室管理体系的要求需对引用的参考区间进行验证,可按下列步骤进行:a)筛选合格参考个体不少于20名,筛选标准参见A.2.2;b)按本实验室操作程序采集㊁处理㊁分析样品;c)按适当方法检查并剔除离群值(若有,则另选参考个体补足);注:离群值检验采用D i x o n方法:首先将检测结果按照大小排序并计算极差R,然后分别计算最大和最小值与其相邻数值之差D;若D/Rȡ1/3,则将最大值或最小值视为离群值予以剔除;将余下数据重复前述步骤进行离群值检验,直至剔除所有离群值㊂d)如选择20个合格的参考个体,将20个检验结果与参考区间比较,若超出参考区间的数据不超过2个,则通过验证;若超过2个,则另选20名合格参考个体重新按照上述判断标准进行验证㊂如参考个体多于20个,超出参考区间的数据不超过10%则通过验证;若超过10%的数据超出参考区间,则另选至少20名合格参考个体,重新按照上述判断标准进行验证㊂验证结果若符合要求,可直接使用参考区间,否则应查找原因㊂5.3参考区间未通过验证时的处理程序5.3.1对未通过验证的情况,应首先评价分析质量尤其是正确度,若证实是检测系统导致的分析质量问题,应改进或更换分析系统㊂分析质量评价可采用(但不限于)下列方式:a)分析可互通有证标准物质或其他适宜参考物质;b)参加适宜正确度验证计划或标准化计划;c)与性能可靠的其他系统或方法进行比较㊂5.3.2若证明是人群原因(如民族㊁高海拔地区㊁特殊生活习惯等因素)未通过验证,则应按W S/T402的要求建立或引用适宜参考区间㊂W S/T404.6 2015附录A(资料性附录)参考区间建立过程的相关信息A.1参考区间建立的步骤本文件参考区间按W S/T402的要求采用多中心的研究方式建立,主要包括以下步骤:a)选择参考个体,组成参考样本组;b)采集处理血液样品,获得血清样品;c)检测血清样品,获得参考值;d)统计处理参考值,建立参考区间㊂A.2参考个体选择A.2.1参考样本组的选择设计总体参考人群为我国成年健康人群,参考样本组选自东北㊁华北㊁西北㊁华东㊁华南和西南6地区城乡居民,年龄范围为20~79岁,六地区最终入选的参考个体共计4397人,其中男性为1878人,女性为2519人㊂A.2.2参考个体的选择各中心分别在所在地区募集足够的可能参考个体,征得知情同意,进行参考个体的筛选,组成参考样本组㊂通过问卷调查㊁体格检查㊁实验室检查筛选参考个体,满足以下要求:a)问卷调查㊁体格检查:1)自觉健康;2)无下列疾病:急慢性感染(急性上呼吸道感染㊁肺炎㊁肺结核等)㊁消化系统疾病(肝硬化㊁肝炎㊁脂肪性肝病㊁胆石病㊁胆囊炎㊁慢性腹泻㊁炎症性肠病等)㊁肾脏疾病(慢性肾脏病㊁急性肾损伤等)㊁代谢和营养疾病(糖尿病㊁代谢综合征㊁血脂异常和脂蛋白异常血症㊁高尿酸血症与痛风等)㊁风湿性疾病(类风湿性关节炎㊁系统性红斑狼疮等)㊁甲状腺疾病(甲状腺功能亢进症㊁甲状腺功能减退症等)㊁血液系统疾病(贫血㊁白血病等)㊁动脉粥样硬化和血管疾病㊁心脏病㊁肌病㊁恶性肿瘤㊁烧伤和肌肉损伤㊁肥胖或消瘦[B M I(体重指数)ȡ28k g/m2或<18.5k g/m2]㊁高血压[收缩压ȡ140mmH g和(或)舒张压ȡ90mmH g];3)6个月内未进行手术,4个月内未献血㊁输血或大量失血,2周内未服用药物;4)无营养不良㊁素食㊁酗酒(长期饮酒或2周内大量饮酒)㊁嗜烟(吸烟量>20支/d);5)近期无剧烈运动或重体力劳动;6)女性未处于妊娠或哺乳期㊂b)通过实验室检查排除:1)丙氨酸氨基转移酶>80U/L;2)甘油三酯ȡ2.26mm o l/L;总胆固醇W S/T404.6 20154)空腹血糖ȡ7.0mm o l/L;5)血红蛋白:男性<120g/L;女性<110g/L;6) H B s A g阳性㊁抗-H C V阳性㊁抗-H I V阳性㊂A.3血液样品采集与处理血液样品采集与处理原则按W S/T225 2002有关要求进行,具体要求如下:a)参考个体准备:采血前3d保持正常生活习惯,不做剧烈运动和重体力劳动㊂采血前1d晚餐后至第二天上午采血前禁食,禁食时间8h~14h;b)采血:受检者取坐位,使用血清分离胶管,采用真空采血方式,自肘前静脉采血;c)血液样品处理:样品在采集后2h内及时分离血清,检查并剔除溶血㊁黄疸或乳糜样品,血清分离后2h内进行分析㊂A.4血清样品分析A.4.1分析系统使用目前我国临床实验室常用的多种分析系统㊂注:本参考区间建立所使用的分析系统及其检测结果的计量学溯源参见附录B㊂各分析系统检测结果的正确度验证见A.4.2㊂血清无机磷由于没有人血清基质的有证标准物质进行验证和评估,本文件的无机磷参考区间是基于多个分析系统检测数据的统计结果和综合临床意见设定㊂A.4.2分析系统性能评估分析系统应于参考个体血清样品分析前进行分析性能评估㊂按仪器和试剂说明书规定的操作程序运行分析系统㊂精密度评估:分析两个水平质控物,每日测定1批,重复测定4次,测定5d;正确度验证:分析美国国家标准与技术研究院(N I S T)的标准物质S R M956c和中国国家标准物质G B W09152对钙㊁镁㊁铁进行正确度验证㊂精密度和正确度满足W S/T403的有关要求㊂A.4.3血清样品分析及其质量控制分析性能符合要求后进行血清样品分析,每份血清样品分析一次㊂精密度控制采用两个水平质控物质,每独立分析批前后进行质控物质分析;每月分析有证标准物质S R M956c进行正确度控制㊂A.5参考值处理与参考区间建立A.5.1离群值检查按照D i x o n方法检查并剔除各组离群值㊂A.5.2分组判断按照n e s t e dA N O V A方法对性别㊁年龄㊁地区各组参考值进行组-组检验,判断需否分组,将不需分组的参考值合并,确定实际参考样本组㊂A.5.3参考限和参考区间建立采用中间95%区间做参考区间㊂用非参数方法分别计算各实际参考样本组参考值的2.5百分位数和百分位数作为参考下限和参考上限㊂根据临床意见对参考限进行适当取整形成参考区间㊂W S/T404.6 2015附录B(资料性附录)血清总钙㊁无机磷㊁镁㊁铁检测方法和检测结果的计量学溯源血清总钙㊁无机磷㊁镁㊁铁检测方法和检测结果的计量学溯源见表B.1㊂表B.1血清总钙㊁无机磷㊁镁㊁铁检测方法和检测结果的计量学溯源项目测定方法计量学溯源性I S TS R M956c血清总钙(C a)邻甲酚酞络合酮比色法/间接离子选择电极法换算N血清无机磷(I P)磷钼酸紫外法血清镁(M g)二甲苯胺蓝法/c a l m a g i t e比色法原子吸收光谱法血清铁(I r o n)亚铁嗪比色法N I S TS R M937W S/T404.6 2015参考文献[1] W S/T225 2002临床化学检验血液标本的收集与处理[2] W S/T403 2012临床生物化学检验常规项目分析质量指标[3]王吉耀.内科学.2版.北京:人民卫生出版社,2010[4] D o n a l dS.Y o u n g.分析前因素对临床检验结果影响.3版.李艳,等,译.北京:人民军医出版社,2009[5] C l i n i c a l a n dL a b o r a t o r y S t a n d a r d s I n s t i t u t e(C L S I).D e f i n i n g,e s t a b l i s h i n g,a n d v e r i f y i n g r e f-e r e n c e i n t e r v a l s i nt h ec l i n i c a l l a b o r a t o r y:A p p r o v e d G u i d e l i n e T h i r dE d i t i o n.C L S Id o c u m e n tC28-A3c.C L S I,W a y n e,P A,U S A,2010[6]I c h i h a r a.A na p p r a i s a l o f s t a t i s t i c a l p r o c e d u r e su s e d i nd e r i v a t i o no f r e f e r e n c e i n t e r v a l s.C l i nC h e m L a b M e d,2010,48:1537-1551。
26个字母记忆怎么联想记忆方法口诀

26个字母记忆怎么联想记忆方法口诀26个英文字母,是孩子学习英语的起点,它的重要性,家长可不能忽视。
联想记忆法可以帮助孩子快速记住26个英语字母而且不会忘记,记得牢。
那么你知道26个字母记忆怎么联想记忆吗?今天,为大家推荐26个字母记忆方法口诀。
26个字母记忆怎么联想记忆a----apple----苹果 b----bee ----蜜蜂c----cat ----猫 d----dog ----狗e----egg ----鸡蛋 f----fish ----鱼g----gate ----门 h----horse----马i ----ice ----冰块 j ----jeep ----吉普车k----key ----钥匙 l ----lock ----锁m----moon----月亮 n----nurse ----护士o----orange----橙子 p----pig ----猪q----queen----女王 r----rabbit----兔子s----snake----蛇 t----tiger----老虎u----UFO----不明飞行物 v----venus----维纳斯w----watch----手表 x----x-ray----x光、x射线y----young----年轻人 z----zoo ----动物园联想记忆:从苹果里飞出一只蜜蜂,蜜蜂扎了猫一下,猫跳起来咬了狗一口,狗一屁股坐到一堆鸡蛋上,从鸡蛋里面游出了一条鱼,鱼飞出去,把门撞倒了,门倒下来,压到了一匹马,马受惊后把脚底下的一块冰猛踢出去,冰块撞翻了一辆吉普车,车上装满了钥匙和锁,这些锁本来是用来锁住月亮的,在月亮上有一个护士在吃橙子,她把吃剩下的橙子喂给猪吃,结果猪就变成了一个女王,女王怀里抱着一只小白兔,小白兔变成了一条蛇,猛扑出去,把老虎咬了一口,老虎吓得立刻跳上了一个UFO,从UFO里掉出了一个维纳斯像,这个维纳斯像手上戴着一只非常漂亮的手表,从这只手表里射出一束x射线,这束射线打在一个年轻人身上,把他打到动物园里变成了动物。
26个拼音字母表 26个汉语拼音字母表

26个拼音字母表 26个汉语拼音字母表汉语拼音采用拉丁字母和一些附加符号表示汉语的发音。
对应汉语音系学(现代音韵学)的汉语音节结构划分,汉语拼音的形式构成也分为声母、韵母和声调三部分。
下面是精心为大家整理的26个拼音字母表,欢迎阅读。
更多26个拼音字母表相关内容请关注实用资料栏目!汉语拼音字母:Aa Bb Cc Dd Ee Ff Gg Hh Ii Jj Kk Ll Mm Nn Oo pp Qq Rr Ss Tt Uu Vv Ww Xx Yy Zz汉语拼音声母:b [玻] p [坡] m [摸] f [佛] d [得] t [特] n [讷] l [勒] g [哥] k [科] h [喝] j [基] q [欺] x [希] z [资] c[;雌] s [思] r [日] zh[知] ch [嗤] sh [诗] y [医] w [巫]汉语拼音韵母:单韵母 a[阿] o[喔] e[鹅] i[衣] u[乌] ü[迂]复韵母 ai[哀] ei[唉] ui[威] ao[奥] ou[欧] iu[由] ie[耶] üe[椰] er[儿]前鼻韵母 an[安] en[恩] in[因] un[温]后鼻韵母 ang[昂] eng[摁] ing[英] ong[雍]整体认读音节:zi ci si zhi chi shi ri yi wu yu yinying yun ye yue yuan声调符号:阴平:- 阳平:/ 上声:∨去声:﹨汉语拼音采用拉丁字母和一些附加符号表示汉语的发音。
对应汉语音系学(现代音韵学)的汉语音节结构划分,汉语拼音的形式构成也分为声母、韵母和声调三部分。
根据汉语拼音方案《字母表》的规定,汉语拼音使用26个现代基本拉丁字母,有大小写之分,字母顺序与英语字母表一致。
其中字母V/v,在方案中规定为“拼写外来语、少数民族语言和方言”之用。
由于汉语拼音的实际职能仅限于拼写汉语普通话,如今这条规定已然无人问津。
8 Quality of Experience in Virtual Environments

Being There: Concepts, effects and measurementof user presence in synthetic environmentsG. Riva, F. Davide, W.A IJsselsteijn (Eds.)Ios Press, 2003, Amsterdam, The Netherlands8Quality of Experience in VirtualEnvironmentsAndrea GAGGIOLI, Marta BASSI, Antonella DELLE FAVEAbstract. In this chapter, we present a new theoretical and methodologicalapproach to the study of presence and virtual experience. More specifically, ourwork aims at analyzing the quality of experience associated with virtualenvironments (VEs), in its emotional, cognitive and motivational components.Specific research instruments have been developed and widely used to study thequality of subjective experience, emphasizing the active role of individual inselecting environmental information. As concerns studies on virtual reality (VR),this holistic approach allows researchers to investigate the subjective perceptionof virtual events and settings, thus permitting comparisons across different tasksand environments. In addition, it provides information on personal factors suchas the motivational pattern, the degree of perceived immersion in theenvironment, the relevance of the activity to individual’s short and long-termgoals.In the first part of the chapter, we describe how virtual experience has beenstudied so far and provide the theoretical bases of the proposed approach. Thenwe present the research tools that we intend to use to analyze the quality ofvirtual experience: the Experience Sampling Method (ESM) and the FlowQuestionnaire (FQ). Finally, we explain how this approach can offer suggestionsfor research and practice in the development of virtual environments fosteringusers’ engagement and empowerment.Contents122 8.1 Introduction..............................................................................8.2 Presence: definitions, determinants and measurement (123)8.3 S ubjective experience and psychological selection:124 Theoreticalfoundations............................................................8.4 Quality of experience and presence in virtual reality (125)8.5 Methods and procedures (126)8.6 Quality of experience and VR: implications for research and129 practice.....................................................................................8.7 Conclusion (131)132 8.8 References................................................................................8.1 IntroductionIn recent years a growing number of researchers have begun to investigate the subjective experience persons report when interacting in virtual environments (VEs). However, “subjective experience” is an ambiguous construct that has been debated from the very beginning of psychological investigation. According to William James, “The world of our experience consists at all times of two parts, an objective and a subjective part (....). The objective part is the sum total of whatsoever at any given time we may be thinking of, the subjective part is the inner 'state' in which the thinking comes to pass” [1] (p. 402).Experience, in James's view, is the result of focusing attention on the content and sequence of conscious events: “(...) Millions of items in the outward order are present to my senses which never properly enter into my experience. Why? Because they have no interest for me. My experience is what I agree to attend to. Only those items which I notice shape my mind – without selective interest, experience is utter chaos” [2] (p. 499). More recently, other authors have also claimed the primacy of attention as a crucial process that regulates states of consciousness. According to Csikszentmihalyi, “ideas, feelings, wishes or sensations can appear in consciousness and therefore become ‘real’ to the person only when attention is turned to them” [3] (p. 337).So far, the largest body of psychological research on virtual experience has focused on the concept of presence, generally defined as a user’s subjective sensation of “being there” in a scene depicted by a medium [4]. Most of the authors point out that presence is an essential, defining aspect of virtual experience. The concept of presence is considered relevant for the design and the evaluation of VR applications and other interactive media.Some researchers have emphasized the usefulness of presence itself, and its relationship with task performance [5]. Others have pointed out the “ecological” value of presence: In their view, this construct is important because the greater the degree of presence, the greater the chance that participants’ behavior in a VE will be similar to their behavior in analogous circumstances in everyday reality [6]. Finally, the study of presence has an intrinsic heuristic value because it could shed light on conscious processes.We agree that presence is a key factor to understand VR experience, but we also believe that focusing exclusively on this concept could be limiting. Actually, researchers in the VR field are becoming increasingly aware that the virtual experience is a complex subjective phenomenon and its study should take into account all its constituting aspects. Banos and colleagues [7], for example, have emphasized that the concept of reality judgment has received less attention than presence and not much effort has been dedicated to test whether or not both constructs refer to the same domain. Other important aspects have generally been ignored by VR researchers. For example, emotions are an essential part of how people experience the world and their study could have important implications for better conceptual understanding of the virtual experience [8]. Similarly, the question of whether users’ experience of VEs is associated with enjoyment and interest has not yet been fully addressed, in spite of the fact that these variables could be relevant to predict the motivation of users to repeat such experience [9].In this chapter, presence is considered as a part of a process that involves persons interacting in both their usual environments and in virtual environments. Thus far, most research on presence has been conducted in VR laboratories in order to identify the single determinants of this construct. Thus, for instance, the work of several authors has focused on testing the psycho-physiological correlates of presence [10, 11]. This type of research is essential to the understanding of this phenomenon, but it does not allow to answer the question of what the virtual experience means to the people who are having it. To this purpose, we need to know how the experience is related to individuals’ thoughts, emotions, motivations and life-goals.We propose an alternative approach, involving the questions of what goes on in people’s minds when they interact with computer-generated, three-dimensional environments and how the content of their consciousness at such times is related to the rest of their goal-oriented behavior. This approach starts from the assumption that the individual, as an autonomous goal-directed system, manifests certain proprieties that are better understood in terms of total system functioning, rather than in terms of systems of lower-level complexity [12]. Conceptually, the purpose of such an approach is to be as “objective” about subjective experience phenomena as possible without compromising the essential personal meaning of the experience [13].In the first part of the chapter, we summarize how the construct of presence has been studied so far and provide the theoretical bases of the proposed approach. Then we present the research tools that we intend to use to analyze the quality of virtual experience: the Experience Sampling Method (ESM) and the Flow Questionnaire (FQ). Finally, we explain how this approach can offer suggestions for research and practice.8.2 Presence: definitions, determinants and measurementReview of the literature reveals different definitions and descriptions of presence. Slater and Usoh [14] described presence as “the (suspension of dis-) belief” of being located in a world other than the physical one (p. 134). Schloerb divided presence into “subjective presence” and “objective presence”. Objective presence is “the probability that the specific task is completed successfully” [15]. Subjective presence is the “probability that a person perceives that he or she is physically present in the given environment”. In contrast to such a definition, Mantovani and Riva [16] proposed an alternative, nondualistic conception of presence as a social construction. According to this definition, presence in an environment, real or simulated, means that individuals “can perceive themselves, objects and other people not only as situated in an external space but also as immersed in a sociocultural web connecting objects, people, and their interactions” (p. 540). Heeter [17] has argued for three different kinds of presence: “subjective personal presence”, “environmental presence” and “social presence”. Personal presence is the “extent to which and the reason why you feel like you are in a virtual world” (p. 262). Environmental presence is “the extent to which the environment itself appears to know that you are here and react to you” (p. 263). Social presence is “the extent to which other beings (living or synthetic) also exist in the world and appear to react to you” (p. 265). Lombard and Ditton [18] reviewed several conceptualisations of presence in the literature in the attempt to provide a unifying explication of the construct. According to this analysis, presence can be defined as the “a perceptual illusion of non-mediation” that occurs when a user incorrectly perceives a mediated scene as unmediated.Other authors have described presence as a “mental manifestation” [19] and an “existential phenomenon” [20]. Literature on presence also includes references to related terms such as “immersion”. Immersion has been defined by Witmer and Singer [21] as “a psychological state characterized by perceiving oneself to be enveloped by, included in, and interacting with an environment that provides a continuous stream of stimuli and experiences” (p. 227).Although the definitions of presence and related terminology vary across authors, there is a broad agreement on the major determinants of this construct (for thorough reviews see [4, 20, 22]).Lessiter and colleagues [23] divided variables that can determine a user’s presence into two general categories: a) media characteristics and b) user characteristics. Media characteristics category has been further partitioned into aspects of a) media form and b) media content [18, 24]. According to this differentiation, media form refers to proprietiesof a display medium, such as the extent of sensory information presented, the degree of control a participant has over positioning his/her sensors within the environment, and a user’s ability to modify aspects of the environment. Media content, on the other hand, refers to the objects, actors and events represented by the medium. User characteristics include relevant individual aspects such as users’ perceptual, cognitive, motor abilities, prior experience with mediated experiences, the length of their exposure to and/or interaction with the VE, and a willingness to suspend disbelief. Witmer and Singer [21] suggest that allocating sufficient attentional resources to the virtual environment is an important determinant of presence. According to this hypothesis, as users focus more attention on the VE stimuli, they should become more involved in the VE experience, thus attaining increased presence. Finally, social aspects of a virtual environment, such as the interaction between the user and other actors, be they virtual or real, can contribute to determining presence [17, 18].The different definitions of presence and of its determinants have generated different approaches to its measurement. They have been broadly classified in two groups: subjective reporting and objective corroborative measures [24, 25]. Subjective measures of presence are introspective evaluations of how “present” one feels in a virtual environment.Such methods include subjective evaluation scales [14, 21, 23], equivalence classes [26] and psychophysical methods, such as magnitude estimation, [27] cross-modality matching [28] and paired comparisons [15]. Objective corroborative measures of presence, on the other hand, involve monitoring the impact of a virtual environment on less consciously controlled reactions such as reflexive motor acts or physiological measures such as arousal, muscular tension and cardiovascular behavior [10, 11].8.3 Subjective experience and psychological selection: Theoretical foundationsWe propose to investigate the impact of VR on daily life and subjective experience from a theoretical perspective that stresses the active role of individuals in interacting with their natural and cultural environment. The process of adaptation to the natural environment provided humans with specific biological features, such as the upright position, the opposing thumb and the increase in brain mass that allowed survival and reproduction in any environmental niche. In addition, through the emergence of primary and higher-order consciousness [29, 30], the abilities to think of one’s self, and to plan, set and pursue goals greatly expanded the sphere of influence and the survival opportunities of our species.Thanks to the newly acquired biological features, humans began to build artifacts and behavioral rules, thus to create culture.While most researchers agree that humans are bio-cultural entities [31], theoretical approaches differ in their emphasis on the role and relevance of natural selection [32, 33], cultural pressures [34, 35], or the interaction between the two systems [36, 37] in shaping human behavior.Differently from genes that are exclusively stored in the human body, cultural information, or memes [38], use two different vehicles for their survival and reproduction [39, 40]: the individual's central nervous system, carrying intrasomatic culture acquired through experience and education; the material artifacts, storing extrasomatic cultural units. Therefore, memes have an advantage over genes, in that artifacts can outlive humans, becoming the repositories of peoples’ diachronic cultural memory [41, 42].According to bio-cultural theories [43], culture represents an autonomous inheritance system, continuously interacting with biology in the influence on human behavior. Memes’ survival and replication rely on a selection process based on cultural criteria and following its own teleonomy. As both inheritance systems use individuals as carriers of information units, competition or cooperation can arise between the two in shaping behavior: In wars,for example, genes’ tendency to survive and reproduce themselves can be overridden by the individual’s commitment to pursue his/her own memes' differential transmission and the suppression of the enemy culture [44].This deterministic approach to human behavior overlooks the role of individuals as active agents. Humans, as living systems, are open self-organizing psychophysical entities, that attain increasing levels of complexity through the exchange of information with the environment [45, 46, 47]. Beside inheriting a genotype, and building their culturetype by acquiring cultural information, individuals actively interact with the environment, selecting and differentially replicating throughout their lives a subset of biological and cultural information, in terms of activities, interests, values. A third selection paradigm comes into play: psychological selection [40]. By means of the differential investment of attention and psychic resources, the individual selects and organizes the information acquired from his/her context according to an emergent, autonomous criterion, that is the quality of experience. In particular, individuals preferentially engage in opportunities for action associated with a positive, complex and rewarding state of consciousness, called optimal experience or flow [48, 49].The basic feature of optimal experience is the perceived balance between high environmental opportunities for action (challenges) and adequate personal skills in facing them. Additional characteristics are deep concentration, clear rules in and unambiguous feedback from the task at hand, loss of self-consciousness, control on one’s actions and environment, positive affect and intrinsic motivation [50-52]. Optimal experience shows constant features at the cross-cultural level, and it can be associated with various daily activities, provided that individuals perceive them as complex opportunities for action in which to invest personal skills [53].Since optimal experience presents globally positive and rewarding features, people tend to replicate it through the preferential cultivation of associated activities [54]. This leads to the progressive improvement of related skills. As a consequence, in order to maintain the balance between high challenges and skills that characterizes optimal experience, the individual will search for increasingly complex opportunities for action. By virtue of this dynamic process of skills cultivation and challenge increase, optimal experience shapes psychological selection, and ultimately influences individual development through the building of a life theme, namely the set of goals and interests a person preferentially pursues and cultivates in his/her life [55].In this process, of course, cultural influences come into play. However, the subjective representation of environmental opportunities for action, the perceived quality of daily life and the creative interaction of the individual with the environment through self-determined motives and goals are the very key components of psychological selection [56, 57].8.4 Quality of experience and presence in virtual realityPresence stands out as one essential component of VR. In spite of the different theoretical and philosophical stances [58, 59], researchers seem to agree on three common features of the construct: (1) presence requires involvement into the virtual environment; hence the effectiveness of VEs is linked to the sense of presence reported by users; (2) presence is defined as a subjective experience; (3) presence is a multi-dimensional construct. Starting from this premise, efforts to operationalize presence have primarily focused on some perceptual and cognitive components, and on associated physiological responses, assessing them through self-reports and physiological tests.According to the above-described theoretical approach, we propose an analysis of the experience associated with VR that investigates at the same time the cognitive, motivational, and affective components. We will focus on the following questions: Canpresence be a component of a specific kind of experience, a peculiar configuration of affective, cognitive and motivational features? Is this association stable in different situations and with different samples of participants? Are there common features between the experience involving presence and optimal experience?Many studies have been carried out on the quality of experience associated with mass media, primarily television [60-63] and, more recently, with new technologies such as the internet [64]. Results show that television captures the attention of viewers independently of its content and long-term relevance for personal development. Watching TV, people feel more relaxed than usual, but less concentrated, active and satisfied. They perceive low challenges and high personal skills, a condition typical of relaxation and boredom. In situations of apathy and disengagement, TV viewing has been proved to exert a parachute effect in that it focuses individuals’ attention, preventing destructuration in consciousness and complete loss of involvement and motivation to act [65]. However, television’s added value does not primarily rest on the medium itself, but on its contents, and on the meaning individuals attach to them. The distinction between medium and content in relation to the associated quality of experience has also been drawn in recent studies on the web use.Among the various activities that can be performed in the web (navigation, information retrieval, playing games), only those that are functional to some personal goals or interests are associated with optimal experience [64, 66].Research thus far conducted highlights some crucial characteristics of VR that suggest its potential effectiveness in fostering optimal experiences : (a) Opportunities for action - In the virtual environment situations and tasks can be designed involving a wide range of human gestures and of perceptual and cognitive functions. The complexity of tasks can be gradually modified so that the individual can start to face the simplest situations and step towards more difficult ones (b) Skills – The tasks presented in the virtual environment can require specific skills, such as cognitive and practical ones, that can be refined and gradually increased during the sessions (c) Feedback – VR systems can offer a multimodal feedback to individuals’ actions and behavior (d) Control – Individuals can experience control of the situation while interacting in the virtual world, and using their abilities. In other words, VR offers challenges that can be gradually increased, simultaneously allowing the individual to gradually improve his/her skills: Therefore, it can be a potential source of optimal experience. In this dynamic process the feedback the person receives from VR, and the control perceived during the session also come into play.8.5 Methods and proceduresIn studying people’s daily life and associated quality of experience, researchers have adopted different methodological approaches, ranging from direct observation, time budget diaries to self-reports (for a review see [67]). For the investigation of VR, we will use two procedures: the Experience Sampling Method [68] and the Flow Questionnaire [48, 69].Experience Sampling Method (ESM) – The urge to study the subjective experience of persons interacting in natural environments, thus ensuring ecological validity [70], and the dissatisfaction with traditional methods based on retrospective recall of behavior and experience [71, 72] led to the development of ESM. This procedure is based on repeated on-line assessments of the external situation and personal states of consciousness, as real daily events and situations occur. It taps how people daily invest their attention and resources, what they do, what they think of, and how patterns in subjective experience relate to life conditions [73].Individuals taking part in ESM studies carry with them an electronic beeper. Different devices have been used, such as “doctor pagers” [74, 75], wrist terminals [76, 77], and electronic notebooks [66]. Beepers are programmed to send acoustic signals (beeps) atfixed or random times, according to the research goals [78]. Fixed schedules are advisable when the use of a time-related statistical analysis is planned, such as time-series analysis, and Markov processes. However, with fixed schedules participants easily recognize the periodicity, and this generates anticipatory behaviors, thoughts, and emotions. Random techniques usually reduce the likelihood of signal anticipation. In truly random schedules, however, long between-beep intervals may demotivate the participants. Another option is stratified random schedules, in which one or more beeps are randomly generated within each time block of the target sample period, thus maintaining individuals’ motivation and avoiding anticipation.ESM sessions usually last for one week, and participants receive five to eight signals a day during waking hours. According to ESM literature, this design is effective in portraying participants’ daily life and experience, and in maintaining individuals’ compliance [73, 79, 80]. Again, the time length and the number of beeps directly depend on the purposes of the study. In a research on parental roles, for example, primiparous couples were followed before and after delivery during eight ESM sessions, starting from the tenth week of pregnancy until the sixth month after childbirth [81].In addition to the beeper, participants are given a booklet of ESM forms (ESF). Whenever they receive an acoustic signal, they are expected to fill out a form. This procedure is rather quick since it takes about 2 minutes to complete a sheet. The ESF contains open-ended questions investigating situational variables such as place, activities carried out, social context, and subjective variables such as the content of thought, what was at stake in the activity, perceived goals, and physical conditions. The ESF also contains 0-12 Likert-type scales investigating the quality of experience in its various components: affect (e.g. happy, cheerful, sociable, friendly), motivation (e.g. wish doing the activity, free, involved) activation (e.g. alert, active, strong) and cognitive efficiency (e.g. concentration, unselfconsciousness, clear ideas). Two more Likert-type scales investigate participants’ perceived levels of challenges and skills in the activity carried out when beeped [74].Thanks to repeated sampling, after a standard ESM session (one week with 5 beeps per day), 35 sheets are collected for each participant, thus providing a rich databank on the quality of daily experience of each individual. ESFs completed after 20 minutes from signal receipt are discarded from analysis, thus avoiding distortions associated with retrospective recall [67]. Collected data are then stored for analysis. Answers to the open-ended questions are coded and grouped into broad content categories according to their function [82]. Scaled variables are transformed into z-scores.ESM data can be organized in two ways. In the beep-level analysis, the unit of data organization is the self-report. After standardization, each variable will have as many z-scores as are the ESFs. In the subject-level analysis, the unit of data organization is the individual. In this case, after the scores of each variable are standardized for each individual, aggregated values (mean z-scores) are calculated. Through this process, N is no longer the number of self-reports but the number of participants [80].The validity and reliability of the instrument have been widely investigated. As concerns ESM reliability, by means of split-half method and comparisons with other instruments (such as time budget), studies have shown ESM sampling accuracy in portraying individuals’ daily life [83], the stability of activity estimates and of psychological states [73], individual consistency over the week [84] and over two years [85]. As concerns ESM validity, studies have shown that ESM reports of psychological states covary in expected ways with the values of physical conditions [86], and situational factors, such as activity [62, 87], location [74] and social context [88]. In addition, researchers have found correlations between participants’ responses on ESM and their scores on other psychometric tools such as Maddi’s Alienation Test [89], Rosenberg Self-Esteem Scale [90], and Intrinsic Enjoyment and Boredom Coping Scales [91]. Finally,ESM differentiates between groups expected to be different, such as schizophrenic and non-schizophrenic patients [92], bulimic and regularly eating women [93], gifted and average mathematics students [94].Thanks to its robust methodological foundations and to its ecological validity, ESM has been used to investigate experience fluctuations in the natural environment in various research areas, such as developmental psychology [74, 75, 95, 96], psychopathology [79, 97], sport psychology [98, 99], and cross-cultural psychology [100].In order to assess the influence of perceived challenges and skills on the global quality of experience, the Experience Fluctuation Model was developed for the analysis of ESM data [101]. The model is built on the Cartesian plane, with challenges on the y-axis and skills on the x-axis (Figure 8.1), and it comprises eight 45° sectors, called channels . Each channel represents a defined range of ratios between challenges and skills. Given repeated ESM sampling, values of challenges and skills are standardized (M = 0, SD = 1). Thus, the center of the model - that is the origin of the axes - is zero and corresponds to the aggregated subjective mean.According to challenges/skills ratio, the standardized values of the other experiential variables change following a well-defined fluctuation pattern [51]. Specific experiential states, determined through the values of all the ESM variables, have been associated with the four main channels: In Channel 2, characterized by a balance between high challenges and high skills, optimal experience is reported. In channel 4, skills are higher and challenges lower than subjective mean: The associated experience is relaxation . Channel 6, characterized by low challenges and low skills, is associated with apathy . In channel 8, skills are lower and challenges higher than subjective mean: The associated experience has been labeled anxiety . The remaining channels represent intermediate experiential states, and are therefore referred to as transition channels [77].This model has proved to be a useful tool for studying the quality of experience associated with daily activities and contexts, for the analysis of how experience fluctuates within or between situations, and for detecting typical patterns of experience fluctuation characterizing individuals.Figure 8.1 The Experience Fluctuation Model (SM = Subjective mean).Channel 2Channel 3 Channel 1C H A L L E N G E SSKILLS。
人教版英语八年级上册Unit4 Grammar Focus 课件

重读闭音节、末尾只有一个
usbeifgul, careful,
辅音字母双写加 –er 或 –est biggpeorp-ublaigr,gseesitrous,
部分双音节和多音节词,形容 fluently/difficult
词+ly构成的副词,在原级前 加 more 或 most
more~,
most~
形容词、副词的最高级
注意
如果其前有形容词性物主代词或名词所有格等修饰语时, 则不 再用定冠词the。
如,Her youngest daughter is eleven years old. This is my newest coat.
形容词、副词的最高级
注意
of与in的区别
of与in都有“在…当中”的意思。 of:主语同of后面的名词是指比较的对象。 in:主语同in后面的名词是指比较的单位或场所。
heavy ____h_e_a_v_i_es_t relaxing____m_o_s_t_r_e_laxing
区分比较级和最高级的使用
1.看范围 两者间比较 ≥三者
2.看关键词 than
the .../ of+范围/ in +范围
3.特殊结构 The+比较级,the+比较级
比较级(-er) 最高级(-est)
The menu had only 10 dishes and the service was not good at all!
2. Blue Moon is _g_o_o_d___ (good), but Miller's is __th_e__b_e_s_t (good) in town. 3. The Big Screen is__m_o_r_e__ex_p_e_n_s_i_v_e_(expensive) than most cinemas, but 定C4.冠inM词eomthvea后ieC用Ci最tiyt高yis级h_ta_hs_et_hm_e_o__s_t_w__eo_x_r_p_s_e_tn_(sb_ia_vd_e)_(seexrvpiecnes,ibvue)t.wethacna表n示si两t 者th比e_较_,_用__比_较__级________ (commfoosrttcaobmlyf)othrtearbe.ly
汉语拼音字母表格模板(发音办法)

汉语拼音字母表声母表b p m f dt n l g kh j q x zhch sh r z cs y w韵母表a o e i u üai ei ui ao ou iuie üe eran en in un ünang eng ing ong字母表A aB bC cD dE eF fG gH hI iJ jK kL lN n M m O o P p Q q R r S s T t U u V v W w X xY y Z z注意:1)"知、蚩、诗、日、资、雌、思"等7个音节的韵母用i拼写作zhi,chi,shi,ri,zi,ci,si。
2)韵母er,用作韵尾时写成r。
例如,"儿童"拼作er-tong,"花儿"拼作huar3)韵母ㄝ单用的时候写成ê。
4)i行的韵母,前面没有声母的时候写成:yi(衣),ya(呀),ye(耶),yao(腰),you(优),yan(烟),yin(因),yang(央),ying(英),yong(雍)。
u行的韵母,前面没有声母的时候写成:wu(乌),wa(蛙),wo(窝),wai(歪),wei(威),wan(弯),wen(温),wang(汪),weng(翁)。
ü行的韵母,前面没有声母的时候写成:yu(迂),yue(约),yuan(冤),yun(晕)。
ü上的两点省略ü行的韵母跟声母j,q,x拼音的时候写成:ju(居),qu(区),xu(虚),ü上的两点也省略;但是跟声母n,l拼音的时候仍然写成:nü(女),lü(吕)。
5)ou,uei,uen前面加声母的时候写成:iu,ui,un。
例如niu(牛),gui(归),lun(论)。
6)在给汉字注音的时候,为了拼式简短,ng可以省作η四、声调符号声调符号标在音节的主要母音上,轻声不标。
英式和美式英语词汇
英国英语与美国英语的词汇差异(在线收听)1 公寓apartment flat洗洗手间间bathroom/restroom toilet罐头can tin糖果candysweets洋芋片chips crisps饼干cookie biscuit玉米corn maize对方付费电话collect call reverse charge call婴儿床crib cot尿布diaper nappy电梯elevator lift橡皮擦eraser rubber一楼first floor ground floor手电筒flashlight torch薯条french fries chips垃圾桶garbage can dustbin汽油gas, gasoline petrol果酱jelly jam汽车的引擎盖hood bonnet生气mad angry数学math maths餐巾、擦嘴巾napkin serviette丝袜panty-hose, pantihose tights薯片potatochips crisp手提包purse/pocketbook handbag足球soccer football来回票roundtrip return人行道sidewalk pavement炉子stove cooker毛衣sweater jersey, jumper卡车truck lorry汽车后面的行李箱trunk boot假期vacationholiday考古学archeology archaeology目录catalogcatalog ue文明civilization civilisation颜色color colour马路牙子curb kerb抵抗defense defence草稿draft draught最爱favorite favourite荣誉honor honour珠宝jewelry jewllery组织organization organisation练习practice practise轮胎tire tyre英国英语和美国英语在词汇上的差异美国英语是在英国对北美进行殖民开拓的过程中逐渐形成的一种区域性的英语变体 ,英国英语和美国英语在词汇上的差异主要有以下的方面:1.1.同一事物使用不同的单词来表示英国英语和美国英语所使用的词汇的意义大多数是一致的,但也有一些词汇在词义存在着较大的区别。
幼儿园26个拼音正确书写格式

幼儿园26个拼音正确书写格式英语字母大小写,初学书写要规范。
大写一律上两格,原则顶住第一线。
小写存有头上两格,b,d,h,k和l。
有尾下面占两格,g,q,y,p莫写错。
无头无尾中间格,十三字母诸法写下, a,c,e,m,n,o,r,s,u,v,w,x,z.中间。
i,t中上一个半,还有f,j三格点。
所有字母略右横,笔顺笔画须记请。
始学养成好习惯,大小宽窄要协调。
书写的规格(1)应按照字母的笔顺和字母在三格中应占的位置书写。
(2)每个字母都应当稍向右弯曲,约为5°,斜度必须一致。
(3)大写字母都应一样高,占上面两格,但不顶第一线。
(新写法要顶格)(4)小写字母a,c,e,m,n,o,r,s,u,v,w,x,z写下在中间的一格里,上下抵线,但都不出格。
(5)小写字母b,d,h,k,l的上端顶第一线,占上面两格。
(6)小写字母i和j的点、f和t的上端都在第一格中间,f和t的第二笔紧贴在第二线下。
(7)小写字母f g j p q y的下端抵第四线。
(8)小写字母a,d,h,i,k,l,m,n,t和u,它们的写诗就是一个上放的小圆钩,无法译成锐角。
(9)书写单词时,字母与字母之间的间隔要均匀、适当,不要凑得过紧,也不要离得太远。
(10)书写句子时,单词之间必须存有适度的距离,通常以腾出一个小写字母a的宽度为宜。
(11)标点符号要写在一定的位置上。
2)字母的笔顺字母要按一定的笔划顺序书写,其书写笔顺如下。
(请注意书写的格式和大小写的区别。
)通过上奏,我们可以窥见,有的字母就是一笔顺利完成,而有的是两笔或三笔顺利完成的。
现归纳如下:(1)一笔完成的字母:大写:c g j l o s v w z小写:a b c d e g h k l m n o q r s u v w y z(2)两笔顺利完成的字母:大写:b d k m p q r t u x y小写:f i j p t x(3)三笔完成的字母:大写:a e f h i n小写:无新法书写格式如下:。
汉语拼音字母表格模板(发音办法)

汉语拼音字母表声母表b p m f dt n l g kh j q x zh注意:1)"知、蚩、诗、日、资、雌、思"等7个音节的韵母用i拼写作zhi,chi,shi,ri,zi,ci,si。
2)韵母er,用作韵尾时写成r。
例如,"儿童"拼作er-tong,"花儿"拼作huar3)韵母ㄝ单用的时候写成ê。
4)i行的韵母,前面没有声母的时候写成:yi(衣),ya(呀),ye (耶),yao(腰),you(优),yan(烟),yin(因),yang(央),ying(英),yong(雍)。
u行的韵母,前面没有声母的时候写成:wu(乌),wa(蛙),wo(窝),5a,o,e开头的音节连接在其他音节后面的时候,如果音节的界限发生混淆,用隔音符号"'"隔开。
例如:pi'ao(皮袄)。
汉语拼音字母的发音方法a 嘴张大,舌位最低,舌面中部微微隆起。
o 舌头略向后缩,舌面后部隆起,口微开,唇略圆。
e 口腔大小、舌位高低与o大体相同,只是嘴角向两边展开。
i 开口度小,两唇呈扁平行,上下齿相对(齐齿),舌尖接触下齿背,使舌面前部隆起和硬腭前部相对。
u 开口度很小,双唇拢圆留一小孔,舌头向后缩。
ü发音与i基本相同,只是嘴唇撮成圆形,略向前突出,舌尖抵住下n 舌尖顶住上齿龈,挡住气流,让气流通向鼻腔,从鼻孔出来,声带颤动。
l 舌尖顶住上齿龈,不顶满,让气流从舌头两边出来,声带颤动。
ɡ舌根抬起抵住软腭,挡住气流,然后突然打开,吐出微弱的气流,声带不颤动。
k 发音部位与方法跟ɡ大体相同,只是吐出的气流比较强。
h 舌根靠近软腭,形成一条狭缝,让气流从狭缝中摩擦而出,声带不颤动。
j 舌面前部抬起贴紧硬腭前端,然后再将舌面稍稍离开,与硬腭形成一条狭缝,让气流从狭缝里挤出来,声带不颤动。
声带不颤动。
r 发音部位、方法跟sh相同,只是发音时声带要颤动。
S t e r e o M a t c h i n g 文 献 笔 记

立体匹配综述阅读心得之Classification and evaluation of cost aggregation methods for stereo correspondence学习笔记之基于代价聚合算法的分类,主要针对cost aggregration 分类,20081.?Introduction经典的全局算法有:本文主要内容有:从精度的角度对比各个算法,主要基于文献【23】给出的评估方法,同时也在计算复杂度上进行了比较,最后综合这两方面提出一个trade-off的比较。
2?Classification?of?cost?aggregation?strategies?主要分为两种:1)The?former?generalizes?the?concept?of?variable?support?by? allowing?the?support?to?have?any?shape?instead?of?being?built?u pon?rectangular?windows?only.2)The?latter?assigns?adaptive?-?rather?than?fixed?-?weights?to?th e?points?belonging?to?the?support.大部分的代价聚合都是采用symmetric方案,也就是综合两幅图的信息。
(实际上在后面的博客中也可以发现,不一定要采用symmetric的形式,而可以采用asymmetric+TAC的形式,效果反而更好)。
采用的匹配函数为(matching?(or?error)?function?):Lp distance between two vectors包括SAD、Truncated SAD [30,25]、SSD、M-estimator [12]、similarity?function?based?on?point?distinctiveness[32] 最后要指出的是,本文基于平行平面(fronto-parallel)support。
Integrating E-services with a Telecommunication
Integrating E-services with a Telecommunication E-commerce using Service-Oriented ArchitectureTung-Hsiang ChouDepartment of Information Management, National Kaohsiung First University of Science and Technology, Kaohsiung,TaiwanEmail: sam@.twYu-Min LeeDepartment of Management Information Systems, National Chengchi University, Taipei, TaiwanEmail: vivi.lee.mail@Abstract—In the past, electronic commerce only focused on customer-to-business web interaction and on business-to-business web interaction. With the emergence of business process management and of service-oriented architecture, the focus has shifted to the development of e-services that integrate business processes and that diversify functionalities available to customers. The potential of electronic commerce and its information technology also has attracted some telecommunication corporations—for example, Chunghwa Telecom, Singtel Telecom, and AT&T. They have built their electronic commerce environment on the Internet, too. Most of these worldwide telecom corporations have many kinds of operations support systems in their backend environment. In the past, enterprises had to integrate their telecom services manually, so that they could work together. However, this integration required considerable time and cost, and it worked only for the specific services that were manually linked. Adding additional services required even more effort. And then, enterprise application integration (EAI) solved these kinds of problems by working via point-to-point interfaces. In this paper, we present a research framework to describe the method. Then, we use two illustrations to explain the generality of our method, and we focus on how international telecom corporations have become concerned with the agility, the leanness, and the integration underlying electronic services (e-services) integration with enterprise application interface technology.Index Term s—electronic services, telecommunication, enterprise application integrationI.I NTRODUCTIONMany enterprises in order to increase the satisfaction of their customer, to manage electronic commerce (e-Commerce, e-commerce, EC) transactions and to rapidly and reliably deliver services to businesses and their customers, have started to consider how to develop business process management that, in enterprise operations, is more agile. In recent years, e-commerce has increasingly supported business services between enterprises and consumers. The biggest challenges that businesses face today is their need to get their diverse services, often built on different platforms, to work together when necessary. Hence, telecom corporations have adjusted their backend systems (including legacy and heterogeneous systems) so that common interfaces have integrated processes and so that the customer can access more telecom services. Hence, these corporations have questioned the feasibility underlying the e-services integration of these business process operations. By the definition proposed in [3], e-services provide value-added services whose delivery rests on the composition of existing functions. Figure 1 depicts the cooperation between e-services and backend systems when a chaoticsituation arises.Figure 1. The chaotic situation between e-services and backendsystemsIn the past, if enterprises wanted to develop an e-service, they had to develop it section by section. Over time, an enterprise would accumulate more and more e-services that rested on heterogeneous platforms, a phenomenon that was especially pronounced in the telecommunication industry. The objective of this research is to help integrate heterogeneous platforms and e-services. For a general solution herein, the research applies both integration methodology and service-oriented architecture to the development of a enterprise application integration.Hence, there will have many complexity problems in the e-services environment and these e-services are provided by the backed system and legacy system to user. Therefore, we need to propose a framework to manage a chaos e-services environment and let backend system and legacy system to be worked more efficiency. This research framework will use several information communication technologies to solve these problems.More specifically, in section 2 of this research, we discuss the related works of Next Generation Operations Systems and Software (NGOSS) and Service-oriented A rchitecture (SOA). In section 3, we will describe e-services integration design with EAI technology. Next in section 4, we will start to illustrate the data flow of implementation and section 5 illustrates case studies by using telecommunication industry. Then we conclude with some comments and some suggestions for future research directions.II.R ELATED W ORKSThis section reviews the relevant research and practice literatures in the following areas. They are the Next Generation Operations Systems and Software (NGOSS) and the Service-oriented A rchitecture (SOA). The objective is to examine the current status of these research results and their relationship with this research study. We propose to extend NGOSS and integrate it with e-services technology. We also review SOA’s research topics to identify their applicability and their feasibility in relation to enterprise’s activities.Next Generation Operations Systems and Software (NGOSS)The TeleManagement Forum (TM Forum) was founded in 1988 and is a non-profit global organization that provides leadership, strategic guidance, and practical solutions for improving the management of and the operations of information and communications services.In recent years, telecom corporations have encountered great difficulties in the integration of business-process frameworks with heterogeneous platforms. Because there are many business process workflows in telecoms such as ordering operations, billing operations, trouble management, resource management, and marketing, these corporations have invented several operations support systems to assist in the related work. Hence, TM Forum proposed Next Generation Operations Systems and Software that would support telecommunication business process.The NGOSS 6.0 is not a system, it is a methodology that TM Forum developed in 2007 [13]. There are four core dimensions of NGOSS architecture, eTOM, SID, TNA, and TAM. Figure 2 depicts the core dimensions of NGOSS both separately and in relation to one another. The NGOSS has to provide a framework for building telecom operations support systems with following views: First, the enhanced Telecom Operations Map (eTOM) describes all the enterprise processes required by a service provider and analyzes them according to different levels of detail that reflect the processes’ significance and priority for the telecom business. For such enterprises, eTOM serves as the blueprint for process direction and provides a neutral reference point for internal processes, reengineering needs, partnerships, alliances, and general working agreements with other providers. For suppliers, eTOM not only outlines potential boundaries of software components so that these components better align with the customers’ needs but also highlights the required functions, inputs, and outputs that must be supported by products [13]. This model also provides an overall concept and describes the business processes’ relationship between internal and external entities in the enterprise. Hence, the TM Forum and the International Telecommunications Union Telecommunication Standardization Sector (ITU-T) have formally approvedthe eTOM framework.Figure 2. The NGOSS frameworkSecond, the Shared Information Data (SID) model defines the information entities so that developers can help map the eTOM model describing the business process. The SID model can be the common standard that connects diverse systems to one another; therefore, the SID model constitutes a common view in the telecommunication industry.Third, the Technology Neutral A rchitecture (TNA) comprises key architectural guidelines that confirm high levels of flow-through amongst various systems. The TM Forum’s definition of ‘TNA’ includes the following points:the core architecture is applicable to both legacy and next generation implementationsthe NGOSS Contract for distributed interfacesthe NGOSS Metamodel defines the relationships of core elementsthe Distribution and Transparency Framework details capabilities that are necessary supportsfor a distributed NGOSSLastly, The Telecom A pplication Map (TA M) is a guide that can help telecommunication corporations and their suppliers use a common reference map and a common language to navigate a complex systems landscape that is typically found in mobile communication, fixed communication, data communication, and wire operators [13]. The TA Mprovides the bridge between the NGOSS framework’s building blocks (eTOM and the SID model) and real, deployable, potentially procurable applications. TA M accomplishes this objective by grouping together process functions and information data into recognized OSS and BSS applications or services [13]. TA M also provides global telecom software with a reference that helps explain the relationships among many operational systems.The research literature presents many suggestions for the development of business process operations that derive from eTOM[5][13]. From the technology viewpoint of Parkyn, eTOM can be implemented with many different technologies such as a .NET framework and J2EE solutions. Therefore, many researchers have started to survey the feasibility of NGOSS-based or eTOM-based solutionsService-Oriented Architecture (SOA)Before discussing the concept of SOA, we must first define ‘e-services’. A ccording to relevant literatures [3][11][12], e-services create value-added services and are self-describing, open components that support rapid, low-cost composition of distributed applications [9]. The Kim [8] defines ‘e-services’ as Internet-based services. The delivery of these services depends on a combination of existing backend systems, legacy systems, and e-services—a combination that tackles the problem of e-commerce business process integration [11][1][12]. In the telecommunication industry, e-services are vital to telecom corporations because the services enable the business processes to interact collaboratively with Internet users and with telecom internal operations systems in a new and digital way. Worth of note in this regard is that telecommunication business processes involve the management of many significant information services. These e-services also represent a business model in the corporation [12]. Hence, businesses that carry out e-services do so by invoking several other basic or composite processes. Casati [3] illustrated the integration of service composition into business process management. Stafford [12] listed the applications of e-services for product marketing, for the internal revenue service, and for e-commerce services. Song [11] proposed the use of e-services at FedEx, which has developed e-services and e-commerce. For example, FedEx has provided online shipping support for its customers. But most of these literatures are not describing how to implement these e-services; hence, for realizing our research goals, this research surveys feasible technology in order first to develop a common interface and second to integrate these e-services into one another. Web service is the optimal solution in integrating methodologies [5][6].However, the development of service-oriented architecture derives from these e-services and treats software resources as services available on a network [2]. According to Huhns et al. [7][9], the SOA satisfies some key features:Loose coupling is the most important key to SOA.SOA should create an environment that is moreagility, feasibility and user-friendly, whether theusers are system developers or customers or anyonein between, they can reuse the e-services each other. Implementation neutrality means that no specific program language can underlie the development ofthe services. Only general implementation canunderlie the development.Flexible configurability is necessary in SOA environment, because SOA is configured late andflexibly. Hence, the user can use the configurationto change dynamically as needed and without lossof correctness.Persistence is required for the service, although services do not need a long lifetime, but when theusers deal with the transaction among heterogeneous platforms, they must always be ableto handle exceptions. The service must exist longenough to handle this situation.Granularity means SOA’s participants should be modeled and understood at a coarse granularity, andthe developers should capture visible informationwith business contracts among participants.Teams include business partners and solve problems cooperatively or compete intelligently In order to comprehend the current research on SOA, this research has surveyed relevant research literatures. Most of the research literatures that discuss the principle of SOA does not implement SOA [2][7][9]. A lthough Chen [4] helps companies to construct stronger relationships with their trading partners by integrating business logic with collaborative commerce, this research does not integrate heterogeneous web services into SOA. Shen [10] proposes an agent-based service-oriented integration architecture that features web services, but this research is applicable only to internal-enterprise manufacturing resource sharing. Hence, this research will propose a new framework that encompasses SOA, EA I, and e-services and that applies to the telecommunication industry.III.E-SERVICES I NTEGRATION D ESIGN W ITH EAIT ECHNOLOGYIn this research, we propose a research framework that provides a context for analyzing several layers to better understand our goals, benefits, and limitations. In the past, many enterprises have implemented their e-commerce computing environment by the web technology. And they use web page to present their thinking of application for a specific function, once the customers have submitted their request to the enterprise. The webpage will process customers’ request and notify the enterprise officers. To accumulate over a long period, the enterprise will have many web pages to present to customers and each web page has hid many business process and e-service without management. Hence, this research framework divides the web page into presentation layer and interaction layer. Due to different function has located in diverse backend systems and legacy systems, this research framework also proposes an exchange layer to integrate theseheterogeneous platforms and use a processing layer to collect these diverse backend systems and legacy systems. In this framework, a telecommunication corporation’s complete computing environment can be divided into several layers: the presentation layer, the interaction layer, the exchange layer, the processing layer and the data layer.In general, the presentation layer includes customer interface such as web pages and e-services links. We propose an interaction layer where integrating e-services both receives customers’ requests and transfers these requests to several e-services. Sometimes these e-services should be aggregated or integrated with other e-services and placed in the e-services pool. The business process management will assemble relevant e-services to attend to customers’ requests. But before integrating e-services accomplishes these requests, the business process management would get more information through the exchange layer. The enterprise application integration (EA I) is responsible particularly for integrating the backend systems and the legacy systems into the exchange layer. The backend systems and the legacy systems cover a variety of information systems such as the integrated customer content system, the data warehouse system, the management system, the provision service system, and the customer service system in the processing layer. Each backend system and each legacy system in the processing layer are controlled by EAI that are enabled by the integrating e-services. Figure 3 depicts the relationships among several layers in thetelecommunication computing environment.Figure 3. The context layers in the large ebusinessPresentation Layer This layer describes the client environment. The presentation layer is based on web technology, such as a java server page, an active server page, or a hypertext markup language. The resulting collection of client-themed information includes, for example, clients’ requests, which web client then prepares. The web client transfers the requests to information collecting so that interaction layer can verify them. Interaction LayerUsing eXtensible Markup Language (XML), presentation layer delivers all of the information to interaction layer. Several steps characterize this layer. Step 1: A fter receiving clients’ information, interactionlayer will convert the customer information into an XML format. Before starting to execute the business process, the customer information conversion-and-verification will verify the XML format on the basis of XML Structure Definition (XSD).Step 2: If step 1 has a successful pass, the systemcommon component starts to process clients’ information and sends it to functional components.Step 3: The functional components will extract theinformation from the XML and will check the functional business process by using the database connection objects.Step 4: When the e-services gateway receives functionalcomponents’ requests, the e-services gateway will send the requests to the exchange layer and will wait for its response.Step 5: Once the exchange layer has sent the request-related results to the e-services, the e-services will deliver the results—through the original request route—to presentation layer. Exchange LayerWe borrow the advantages from the EA I to communicate with the processing layer and with the interaction layer. This layer also integrates several heterogeneous backend systems and legacy systems. The EA I facilitates the operation of information system communication. We also use XML standard to transmit user’s request through the web service and wait for the response from the processing layer.Processing LayerThe systems can be divided into two categories, backend systems and legacy systems. Each of them connects the exchange layer and the data layer to each other. In this layer, each system has different specific functionality such as a mobile billing, dedicated line provision and so on.Data LayerFinally, this layer collects the raw data and thehistorical data in the different databases and prepares to provide request-related information to processing layer. In order to strengthen the efficient cooperation of these e-services with one another, this research will illustrate these concepts on the basis of the collaboration model.This research proposes a collaboration model that will help identify every stage in a relevant position. In Figure 4, we depict the collaboration model that features e-services. The customers and the commercialagents send their requests into the square shape that represents information collection. A fter collecting the requests, the information collection uses the intranet to send them into e-services integration. The e-servicesintegration represented by the square shape collects several e-services and coordinates relevant e-services. The oval-shaped is in an e-service aggregator, and the business processes are based on e-service. Then, the e-services seek matched systems so that e-services integration can provide e-services aggregator with e-services. To accomplish this objective, e-services integration uses an interface of enterprise application integration. These e-services include data, business logic, and object. The e-services assemble these characteristicsaccording to different situations.Figure 4. The NGOSS-centric collaboration model in the frameworkIV.T HE D ATA F LOW OF I MPLEMENTATIONIn order to illustrate the data flow of user request, we depict the steps that characterize a website’s processing of user requests in Figure 5.Step 1: The web application receives the user request andtransfers it into an XML document.Step 2: The web application sends the XML documentthrough the firewall by using the web service.Step 3: A fter receiving the XML information, the webserver transforms this information into the specified data format by using the remote systems.Step 4: The remote system processes the result of step 3and sends the result to the web server.Step 5: The web application sends the results to the webuser. Figure 5. The process of a user request through the e-services portalA nd in order to realize these research proposes and solve research issue, we will develop a prototype toaccomplish these tasks. This prototype will enable several information technologies:Web TechnologiesMany information technologies make the web page to be ideal. A jax, Javascript/Vbscript, Html, A ctive Server Page and A dobe Flash provide user with a rich and fun interactive experience without drawbacks of most old web applications. These information technologies aim to display and invoke web services just like software resource. These web technologies also can use XML format to deliver user request.XMLXML is an abbreviation of extensible markup language and it was announced by W3C in 1998. XML can be defined by user and use a tag to describe the presentation of information. XML also has a descriptive language and a interchange format. In this research, we will use XML to be a communication message between each layer. Web ServiceWeb service is a self-contained, self-described, published, located, and invoked over a network. Web service makes distributed processing difficulties invisible and treats invoked application to be a software resource. Web service also provides a means for wrapping existing applications so developers can access them trough standard languages and protocols. It is a way of realizing service oriented architecture, focusing on the integration and enabling machine-to-machine communication. In general, web service uses XML for data description; HTTP for message transfer; the Simple Object A ccess Protocol (SOAP) for message exchange; the web services description language (WSDL) for service description; and universal description, discovery, and integration (UDDI) protocol for discovering and publishing web services.V.T HE C ASE S TUDIES OF T ELECOMMUNICATION C ORPORATION Once we have finished the work of systemdevelopment. We use two case studies to evaluate thefeasibility and validity in this research. In the feasibility, we use a real telecommunication environment to validate the functionalities of trouble management in the telecommunication corporation.A Live Case StudyThe company in question is the largest telecommunication corporation in Taiwan and is also the 423rd largest company in the world (according to Forbes’ survey). The company’s scope of services covers local phone services, long-distance phone services, international calls, mobile communication, data communication, Internet services, broadband networking, satellite communication, intelligent network, mobile data, and multimedia broadband. The company is the most experienced and largest integrated telecommunication provider in Taiwan, and providing these telecommunication services to more than 25 millioncustomers. The Table I depicts the subscribers of the major service in telecommunication corporation.TABLE I. S UBSCRIBE N UMBER IN THIS L IVE C ASESubscriber Number of Telecom's Major ServicesServices Subscriber number (Oct. 2007)Local phone service 12,985,386Mobile phone service 8,661,817Payphone service 102,971Internet access service 4,071,727The goals of this research are to establish an NGOSS-centric telecommunication e-services enabling operations support systems in an e-commerce environment. Hence,in this section, we use two illustrations to describe the situation of trouble management and QoS-management, and we then depict the implementation plan. This research will illustrate these topics in the following sections:Trouble management IllustrationThis section uses trouble management to explain the benefits that NGOSS and e-services have for integration. In the past, trouble management provided only passive information to customers.Since 2002, the TM Forum has proposed a third version of NGOSS architecture. There are three eTOM sections:(1) strategy, infrastructure, and product (SIP);(2) operations; and(3) enterprise management.The SIP section supports, at least in theory, customer operations. Enterprise management provides several services that, on behalf of telecommunication service providers, improve the efficiency of telecom business operations. Customer relations management is a key feature of eTOM. Hence, we will discuss CRM operations in eTOM. And this topic will focus the CRM process on problem management. The problem management processes help system receive trouble reports from customers, resolve problems, increase customer satisfaction, maximize Quality of Services (QoS), and repair circuits. A ccording to [13], several processes underlie eTOM architecture’s problem management:Isolate Problem and Initiate Resolution: In this initial stage, the system identifies a customer’sproblems and receives the customer’s request thatstates the problem.Report Problem: A fter receiving the customer’s request, the system should generate a trouble reportfrom the previous process and match the report withrelevant problems.Track and Manage Problem: When a telecommunication business has many problemreports, it needs a tracking mechanism to monitorthe progress of the trouble reports. The purpose ofthis process will be to track a customer’s troublereport actively.Figure 6 depicts the business process of legacy trouble management operations. In this figure, two major procedures characterize the legacy operations: one is receiving customers’ requests from the Internet, and the other is making the subsequent arrangement in the workerdatabase. A lthough the legacy trouble management operations have had a simple business process for responses to customers’ requests, the operations cannot provide customers with satisfactory service. Owing to the competitive telecommunication market, to changes in the environment, and to improved information technology, telecommunications corporations have started to provide more e-services functionality on the Internet.Figure 6. The business process of the legacy trouble management operationsIntegration between e-services and backend systems Telecom corporations have many types of backend systems such as operations support systems, customer relations management systems, and billing management systems. These systems provide several telecommunication operations business services such as applications for a new home phone, transfer of a phone service, and reactivation of a home phone. But these backend systems might derive from heterogeneous platforms. Hence, we have started to consider a common technology such as EA I that might integrate these platforms.Close Problem: If the telecommunication businesses have finished their trouble reports, the last stage will be to ensure that the problem has been resolved and to inquire into the customer’s satisfaction.QoS-management IllustrationIn the past, developers tried to integrate data and resources into each other but found the task difficult. Hence, researchers started to use interfaces. But this method grows complex when a business tries to integratem systems with n systems: The integration generates m*n interfaces so that these systems can interact each other. So the complexity constitutes an m*n problem. Therefore, the enterprise application integration (EA I) will emerge, and all the systems will have a common interface bus. Once the systems have connected to the EAI bus, all the messages will flow into the bus. A lthough the EA I has solved many integrated problems, the EA I can solve。
An Analysis of the Principal-Agent Problem note

Notes on the Principal – Agent ProblemNolan Miller•The principal – agent framework is a method for analyzing problems where one party (the principal) hires another party (the agent) to perform a certain task for her.•Note: frequently in order to make things clear in two actor models, one will be male and one will be female. I make principals female and agents male.•The hallmarks of the principal-agent problem are:1.The objectives of the principal and agent conflict. For example, the in a labor relationship,the owner of a firm wants her employee to work hard, but the agent wants to minimize the effort that he puts forth.2.There is non-contractible information. That is, the agent either:•knows something that the principal does not know, or•performs an action that the principal cannot observe, or•The principal observes one of the above, but it is not able to write contracts based on that information (i.e., the information is non-verifiable).3.The action chosen or information known by the agent cannot be inferred from the outcomealone.•One of the best illustrations of these types of informational asymmetries is illustrated by the relationship between an insurance provider and a consumer.•It may be that the consumer knows more about how likely he is to experience a loss than the insurer, or•Because the agent is insured he takes less care to avoid losses because effort is costly, or •Because the agent is insured he uses more insured services than he would otherwise, or •Because the agent is insured he chooses to take actions that differ from the actions that the insurer would like him to take (i.e., skydiving).•Problems such as these are all amenable to analysis using the principal-agent framework.•The most basic elements of a principal – agent analysis are:1.The principal designs a contract for the agent specifying the payment to be made to the agentfollowing each possible outcome.2.The agent either accepts or rejects the contract.3.If the agent rejects the contract, he receives his reservation utility (chooses his best outsideoption).4.If the agent accepts the contract, he chooses an action.5.The outcome is realized, and the principal pays the agent according to the contract.•Types of Principal – Agents can be classified based on whether the agent knows information that the principal does not or takes an action that the principal cannot observe, and when this takes place.•If the agent has private information about the outcome distribution at the time that the contract is signed, this is typically called an adverse selection problem although it issometimes (more accurately) called a monopolistic screening problem. Since it will be costly to induce the agent to reveal his information, the principal must decide if she wishes to design the contract to separate the different types of the agent, and, if so, to do it as cheaply as possible. Note, frequently in these types of models the agent does not make an action choice.•Examples:•Insurance where consumers know their loss distribution but insurers do not.•Labor contract where workers know how productive they are but employers do not.1•If different actions have different utility costs to the agent and the principal cannot observe the action the agent takes, these types of models are typically called moral hazard models.In moral hazard models, the agent’s action is typically interpreted as effort, and these types of models are sometimes called effort-aversion models. Higher levels of effort areassociated both with higher cost to the agent and with higher outcomes. Since the principal would like high effort but the agent would like low effort, the principal’s task in designing the contract is to choose the level of effort it would like to implement, given that designing a contract that will induce the agent to work hard will be costly for the agent.•Examples:•Auto insurance, where the insurer would like the driver to take great care to avoid accidents, while the driver is less inclined to take care since he does not bear the costof losses.•Employment, where owners would like employees to work hard, but employees would like to shirk.1 We won’t spend a lot of time on this type of problem, since it is similar to both competitive adverse selection problems and the principal-agent model we will study.•If the agent has no private information at the time of contracting but acquires private information after the contract is signed, these types of models are known as hiddeninformation models. Since the action that the principal would like the agent to take both depends on the agent’s private information and usually differs from the action that the agent would like to take, the principal’s task in hidden information models is to design the contract in order to induce the agent to choose the principal’s preferred action even though theprincipal cannot observe the agent’s private information.•Examples:•People with health insurance may tend to go to the emergency room even if they are not really that sick.•Managers in firms may choose projects that are likely to advance their careers rather than increase shareholder value.•Managers are more risk averse than firms.•Managers are more impatient than firms.•Asian Financial Crisis: because banks believed that they were “too big to fail,” they made excessively risky loans.•Also, U.S. S&L crisis: deposit insurance, low reserve requirements and insufficient regulation led them to make bad loans.•Notes on hidden information models:•The first example, where people tend to use too much of a service when they are insured is also frequently called moral hazard. In fact, this was the original meaningin the health care literature. However, since it is qualitatively different than theeffort-aversion story above, we lump it in as a hidden information model rather than amoral hazard model. The typical example is that people use more health care whenthey are insured than when they are not, which is not an effort-aversion story butrather a hidden information story.•For a long time there was a fixation on the first two types of models, and hidden information models have been relatively neglected in the literature. However, theyrepresent fundamental problems: how do you get your agent to make the choices youwould make when the agent’s goals conflict with yours?•As you can tell, a clear set of terms is yet to emerge from the literature.A Principal – Agent Model with Observable Effort and Effort Aversion2•The principal – agent relationship can be thought of as having two parts:•Risk sharing: the task the agent is going to perform is risky, and so there is the question of how much of the risk each party should bear.•Typically, the principal is assumed to be risk neutral. In this case, the principal doesn’t mind risk, and the agent would prefer to be bear no risk at all.•Incentives: the agent must undertake an action that the principal cannot observe. If the agent receives the same wage regardless of the outcome, he will put forth no effort.•Obviously, the solution of these two problems is in conflict. If the principal reduces the risk the agent must bear, the agent has less incentive to choose high effort. And, if the agent is given the incentive to choose high effort, he must necessarily bear some risk.•So, the study of principal-agent problems of this sort (moral hazard) can be thought of as the study of the optimal trade-off between risk sharing and incentives.•In almost all principal-agent models it is assumed that the principal is risk neutral.•Justified because the principal is often a firm, and the agent is often only one small risk to which the firm is exposed. Since the firm can diversify away its risk, it makes sense tothink of principals as risk neutral.•However, in assuming that the principal is risk-neutral, you assume away the risk bearing problem.•So, let’s begin with a quick study of risk-sharing.•To isolate the risk-sharing aspect of the P-A problem, we’ll assume that effort is observable and verifiable.•In this case, contracts can be written that specify the effort level that the agent must put forth.•The principal’s objective is therefore to specify the wage schedule (as a function of the observed outcome) and effort level that maximizes its profit subject to the constraint that the agent voluntary choose to enter into the contract with the principal.•Note: The case where effort is observable is often referred to as the “first-best case”. It is first-best because there are no incentive problems; the agent chooses the proper actionbecause the action choice is observable and contractible. If the agent does something else, he will be punished by the courts. In contrast, the “second-best case” refers to the situation where effort is not observable. In this case, the terms of the contract must be manipulated in order to induce the agent to choose the desired action. This can be modeled by addingadditional incentive compatibility constraints to the problem. Unless the principalimplements the lowest cost action in both problems, the solution to the second-best problem will result in lower profits for the principal and will be Pareto inferior to the solution to the first-best problem.2 See Macho-Stadler and Perez-Castrillo, An Introduction to the Economics of Information, Chapter 2.The Model:Outcomes: {}1,...n N x x x ∈. Outcome x n is the profit (in dollars) earned by the firm not including the cost of paying the agent .Actions: The agent chooses high effort, e H or low effort, e L . We do not put any structure on the relationship between effort and the likelihood of various outcomes. A useful way to think about high effort is that it increases the likelihood of (good) outcomes. However, before you have seen the model, it is a bit hard to guess exactly how this should be formalized. A natural place to start is to think about increasing effort increasing the likelihood of good outcomes in the sense of First Order Stochastic Dominance (FOSD). But, while it may help you to think about the problem this way, we do not yet assume that the model has this structure.Distribution: The distribution over outcomes given the effort choice is given byp n (e)∈[0,1], ()11,Nn n p e e ==∀∑Utility: The principal has utility function B(y) for money. If the outcome is x and the agent is paid w, the principal’s utility is B(x – w). B() is assumed to be increasing and (weakly) concave, i.e., '0''0B and B >≤. Thus we allow for the principal to be either risk neutral or strictly risk averse.The agent’s utility function is given by u(w,e) = v(w) – g(e) , where e is the level of effort the agent chooses and w is the wage he receives. It is assumed that v is increasing and concave, i.e., v' > 0 and v'' < 0, and that g(e H ) > g(e L ). The agent has reservation utility u 0.The timing:1. P offers A a contract (e,w 1,w 2,…,w N ) specifying the level of effort the agent should put forthand the wages he will be paid following each outcome.2. A either accepts or rejects the contract.3. If the agent rejects, he takes his reservation opportunity, u 0.4. If the agent accepts, he chooses effort as specified in the contract and is paid according to thecontract.Question: How should the payments be set so that the principal induces the agent to work for her at the lowest cost possible?3Note: We can ask this question assuming that the principal wants to implement either level of effort. Once we determine the optimal contract that implements either effort level, we can then ask which effort level the principal will want to implement. This is analogous to constructing the cost function in producer theory. First you ask how a specific level of output can be produced at the least cost. Then you choose the level of output that maximizes profit under the assumption that you will produce it using the least-cost method. 3 Frequently, when there are two parties in a model, it helps clarify things to assume one is male and the other is female. Following this practice, assume the Principal is female and the Agent is male.The first-best (i.e., effort is observable and contractible) optimal risk sharing problem can be written as:()()()*01**01max ()..:()n Nw n n n n N n n n p e B x w s t p e v w g e u ≥==−−≥∑∑The constraint here is called the agent’s Participation Constraint and it requires that the agent receive enough utility via interacting with the principal that he prefers to contract with her rather than take his reservation utility. The principal’s problem can thus be thought of as how to give the agent his reservation utility as “cheaply” (in utility terms) as possible for any given e *. NOTE: the optimal contract will depend on the action the principal is trying to implement.It is easy to show that the agent’s participation constraint will always bind. If it doesn’t,decrease all of the agent’s payments by a little bit. Since the participation constraint does not bind, this produces a solution to the problem that is feasible and lower cost. Hence theparticipation constraint must bind at the optimum.This problem can be solved using Lagrangian methods, which implies that:4()()***',.'n n n B x w n v w λ−=∀ or()()()()****'',.''n n n j j j B x w v w n j B x w v w −=∀−which is the same as saying that the marginal rate of substitution between any two states must be the same for both the principal and the agent.For specific functions B(), v() and g(), the exact payments can be determined using the above conditions and the participation constraint. But, we can make three quick observations:1. If the principal is risk neutral, B’= 1. Since the agent’s utility for money is strictlyincreasing, this implies that ()()**''n j v w v w =for all n and j. In other words, the agent is fullyinsured. He is given a constant wage contract, and the principal bears all the risk.2. If the agent is risk neutral, v’ = 1, then the opposite holds. The principal will be fullyinsured, and the agent will bear all the risk. This is the case of “selling the business to the agent”. The agent pays the principal a fixed amount, F, and is the residual claimant on the profits. As we will see, even in the second-best case where effort is not observed, when the agent is risk-neutral “selling the business to the agent” results in the first-best outcome.3. If both parties are strictly risk averse, then they will both bear some of the risk of the venture,with the payments being divided according to the above equations. But, it is important to 4 Throughout the paper, optimal solutions are denoted with “*”.note that the agent will always receive his reservation wage. Thus it is important todistinguish between the relative payments (the agent will bear some risk) and the level of the payments (the agent always expects to receive his reservation utilty). If, for example, the agent’s utility function exhibits constant absolute risk aversion, v(x) = - exp (-ax), thenadding or subtracting a constant from all payments does not change the amount of risk that the agent bears (or, as we shall see later, the incentives offered by a particular contract). Thus the level of payments and the relation between the payments can be variedindependently (at least to a certain extent).Linear Risk Sharing :One contractual form that is often observed in the real world is a linear contract, where the agent’s wage is a linear function of the outcome, w n = a + bx n . We can use this model toinvestigate under which conditions a linear contract will be optimal, at least in the case where effort is observable. Let w(x n ) be the optimal payment when the outcome is x n .Although this is not technically correct since we have a discrete outcome space, we are going to treat the problem as if x is continuous in order to get at this question.The first order condition for the above problem is given by:()()()()''0n n n B x w x v w x λ−−+≡Differentiating with respect to x n yields: 5()()()()()()()()()()()*''1''0'''1''0'''''''0'''n n n n n n n n n n n n n n n npn n p adw x dw x B x w x v dx dx dw x dw x B B x w x v dx v dx dw x dw x B B v B B dx v dx r dw x dx r r λ⎛⎞−−−+=⎜⎟⎝⎠⎛⎞−−−+=⎜⎟⎝⎠−++==+ where r p =-B’’/B’ and r a = -v’’/v’ are the principal and agent’s respective coefficients of absolute risk aversion.The above analysis shows us that, basically, 6 only in when r p and r a are constant (i.e. B(x) = -k p exp(-r p x) and v(x) = -k a exp(-r a x) ) will a linear contract be optimal.5 To get from the first line to the second, use *'/'B v λ= from the first-order condition. To get to the third line, divide by B'. To get to the fourth, use the definition of r p and r a . 6 There are other cases where efficient risk sharing will involve a linear contract. These relate to situations where agents have HARA utility functions with identical γ parameter. See Gollier, C., The Economics of Risk and Time (MIT Press: 2001) for a discussion of HARA utility.Note: the utility function mentioned above is the constant absolute risk aversion (CARA) case. But, we think that people probably have decreasing absolute risk aversion utility functions (DARA). So, this is a strong hint that the standard model may not be adequate to account for real contracts.The Optimal Level of Effort to ImplementFollowing the method outlined above, the principal can determine the least-cost contract that the agent will accept for any level of effort e*. As stated earlier, this is analogous to deriving the cost function for a firm. Using this analysis, we can consider when it will be optimal for the principal to choose e* = e H vs e* = e L. Having derived the optimal contracts, it would be a simple task to compare the principal’s expected profit when e H is implemented optimally and the principal’s expected profit when e L is implemented optimally in order to choose between the two.What might lead the principal to choose to implement e L instead of e H despite the fact that e H leads to higher expected profits? Two factors may contribute: First, if the principal implements the more productive action, it will have to compensate the agent for incurring higher effort costs since g(e H) > g(e L). Second, if the higher action results in higher expected returns but also more risky returns, then the principal may have to bear additional costs due to the additional risk, which may lead it to choose to implement the lower outcome.Moral Hazard – Effort is Costly and Unobserved•Up until now, we have considered the “first-best case” where effort is contractible. This entails:1.The principal can observe the effort level chosen by the agent.2.The principal can verify this information before a court.•We now turn to the “second-best case”, where effort is either not observed by the principal or cannot be verified before a body with the power to enforce the contract.•The story is: The principal wants to hire the agent to perform a certain task. The agent can either put forth low effort or high effort, but the principal cannot observe the agent’s effort choice. The principal does observe the outcome, but it does not perfectly reveal the agent’s effort choice. However, the principal can use the outcome to make inferences about the agent’s effort choice. For example, suppose that high outcomes are more likely under high effort. Because of this, if the principal rewards the agent (i.e. pays a relatively high wage) following a high outcome, this will give the agent an incentive to choose high effort (since it increases the probability of receiving the larger reward). But, paying the agent a high wage following a high outcome involves exposing the agent to risk. Thus the expected wage paid by the principal will be larger than in a contract that offered the agent the same expected utility via a constant wage. However, a constant-wage contract will have no incentiveproperties. The agent will simply choose the lowest-cost action. Thus the principal’s task is to design a contract that imposes just enough risk on the agent to induce him to choose the right effort level.•Thus interesting aspect of this problem is the trade-off between insurance and incentives we mentioned last time. If the agent is fully insured, he will choose the lowest cost action. If the agent is going to be induced to choose a higher level of effort, he must bear some risk.•We now turn to the “standard” moral hazard model. The timing of the game is given by:•Principal offers agent a contract•Agent either accepts or rejects•If Agent accepts, he chooses effort. Effort is costly to agent and unobserved by principal •Outcome is observed.•Principal pays agent according to contract.•Examples:•Insurance: Insurers would like consumers to make effort to avoid accidents. If consumers are fully insured, they won’t make any effort.•But, the fact that losses are often associated with risks to health or welfare beyond full insurance works against this fact.•Labor: Employers would like workers to work hard. If workers are paid a flat wage, they will have no incentive to work hard.• Education: Professors would like not to fail any students. But, if students know that theycannot fail, they will be less inclined to study.The Simplest Example: Two effort levels and two outcomesConsider the following principal – agent model. There are two possible outcomes, big(B) and small (S). The agent chooses between two effort levels, e L and e H . Let p L and p H be the probability of the big outcome under low and high effort respectively. Utility is additivelyseparable as before, u(w,e) = v(w) – g(e), where v() is an increasing, concave function of money. The agent’s reservation utility is u 0. The cost of effort is given by g(e L ) = 0 and g(e H ) = 1. The principal is risk neutral.Effort is assumed to be unobserved by the principal. If the principal wants the agent tochoose low effort, this is not a problem. The optimal contract simply offers the agent his reservation utility in each state. Thus w B = w S = v -1(u 0). The agent is fully insured and chooses low effort, but this is what the principal wants.Now suppose that the principal wants the agent to choose high effort. In this case, thecontract must be designed so that the agent prefers choosing high effort to low. That is, given the contract (w B ,w S ), it must be that:()()()()()()111H B H S L B L S p v w p v w p v w p v w +−−≥+− (IC)or()()()()1H L B S p p v w v w −−≥This constraint is known as an incentive compatibility constraint . It says that given the contract (w B ,w S ) it must be that the agent’s expected utility net of effort cost is higher when he chooses high effort than when he chooses low effort. Seen another way (as in the rearranged version of the constraint above), it says that the increase in expected utility from wages due to increasing effort must be larger than the increased cost of high effort.In addition to the contract being incentive compatible, it must be that the agent expects to receive his reservation utility by participating in the contract:()()()011H B H S p v w p v w u +−−≥ (P) This constraint is called the agent’s participation constraint . 7 It says that the contract must be such that the agent voluntarily chooses to participate in the relationship.Thus the principal’s problem is to minimize the expected cost of the contract,()1H B H S p w p w +− (OBJ) Subject to (IC) and (P).The difference between the second-best problem and the first-best problem is the addition of the incentive compatibility constraint. Since the second-best problem is derived from the first-best problem by the addition of another constraint, it follows directly that the principal’s expected profit is at least as large in the first-best problem than in the second-best problem 7 This constraint is also frequently called the agent’s individual rationality constraint, although the term participation constraint is currently used more often.(strictly larger when the principal implements high effort in both cases) and, since the agent earns u 0 in each case, that the solution in the first-best problem (weakly) Pareto dominates the solution in the second-best problem.The analysis of the second-best problem is facilitated by noting that both of theconstraints must bind. The key to understanding why is to note that the incentive compatibility constraint depends only on the relative level of the two payments, while the participation constraint depends on the absolute level of the two payments. Thus the strategy employed to show that the participation (resp. incentive compatibility) constraint binds will be to argue that if the constraint does not bind, the principal can decrease the absolute (resp. relative) level of the payments without affecting the relative (resp. absolute) level of the payments, thereby satisfying both constraints at a lower cost.First, consider the participation constraint. If the participation constraint does not bind, the principal can reduce w S by v’(w B )t and w B by v’(w S )t. If t is small, the participationconstraint will still be satisfied. For small t, the impact on the incentive compatibility constraint of the change is given by: ()()()()()()()()()()()()()(){}()()()()()()00lim ''lim ''''''''''0t H L B S S B t H L B S S S B B H L B S S B d p p v w v w t v w v w t dt p p v w v w t v w v w v w t v w p p v w v w v w v w →→⎧⎫⎡⎤−−−−⎨⎬⎣⎦⎩⎭−−−+−−−= Hence the incentive compatibility constraint is still satisfied after the change. Since the newcontract is feasible (i.e., satisfies both constraints) and has a lower expected cost to the principal, the original situation could not have been optimal. Hence the participation constraint must bind. Note that in this case we have reduced the absolute level of the payments without affecting their relative values (utilities).Similarly, consider the incentive compatibility constraint. If the incentive-compatibility constraint does not bind, the principal can decrease w B by (1-p H )v’(w S )t and increase w S by p H v’(w B )t without violating the participation constraint. The effect on the participationconstraint of the change is given by:()()()()()()()()()()()()()()(){}()()()()()()00lim 1'1'lim 1''1'1'''1''1''0t H B H S H S H B t H H S B H S H H B S H B H H B S H H B S d p v w p v w t p v w p v w t dt p p v w v w p v w t p p v w v w p v w t p p v w v w p p v w v w →→⎧⎫⎡⎤−−+−+⎨⎬⎣⎦⎩⎭−−−−+−+−−+−=Hence once again the change has produced a feasible solution with lower expected cost to the principal, and therefore there cannot be an optimal solution where the incentive-compatibility constraint does not bind. Note that in this case we have reduced the relative spread in the payments without affecting the absolute level of expected utility.Knowing that the two constraints bind, they form two equations in two unknowns, making it easy to solve for v(w S ) and v(w B ). These quantities are:()()()*0*01L S H L L B H Lp v w u p p p v w u p p =−−−=+− The difference in the utility received in the two states is given by:()()**11L L B S H LH L H L p p v w v w p p p p p p −−=+=−−− Hence, holding u 0 constant, the spread between the payments received by the agent becomes larger as the effect of effort becomes smaller. While at first this may seem counterintuitive, the reasoning that supports it goes as follows. The agent is motivated to work hard by the increase in expected utility due to choosing higher effort. The increase in expected utility can be thought of (see the IC constraint) as the increase in the probability of the high outcome times the increase in utility due to the high outcome occurring (and being paid accordingly). The increase in expected utility must outweigh the cost of effort. So, if the increase in the probability of the good outcome due to increasing effort is small, the increase in utility received following the big outcome as opposed to the small outcome must be large.Having derived the contract that implements either effort level at least cost to theprincipal, we can now consider the principal’s problem of selecting which effort level to choose. Denote the big outcome by x B and the small outcome by x S . The principal’s expected profit under high effort is:()()()**1H H B B H S S B p x w p x w =−+−−Under low effort the principal pays the agent ()10u u − in each state, giving expected benefit: ()()101.L L B L S B p x p x v u −=+−−The principal chooses to implement high effort whenever the former is larger than the latter.How are the optimal effort levels related in the first-best and second-best problems? In the current model, we can say the following. If the principal chooses to implement high effort in the second-best problem, she will also prefer to implement high effort in the first-best problem. However, it may be that the principal wants to implement high effort in the first-best problem but chooses to implement low effort in the second-best problem. This is because the additional cost that the principal must incur in order compensate the agent for his increased effort cost while simultaneously inducing him to choose high effort (which involves a risky contract, and the principal must also compensate the agent for bearing this risk) is more than the additional expected profits due to the agent choosing high effort.Risk Neutral Agents: Selling the Firm to the AgentConsider the case where the agent is risk neutral, and high effort is implemented in the first-best problem,()()()()()()110010111110H B H S L B L S H B H S p x p x v u p x p x v u p x p x v u −−−+−−−≥+−−+−−−≥。
物理量国际主单位单位公式

物理量国际主单位单位公式物理量国际主单位单位公式名称符号质量 m 千克(kg) m=ρv温度 t 摄氏度(°C )速度 v 米/秒(m/s) v=s/t密度ρ千克/立方米( kg/ m3 ) ρ=m/v力(重力) F 牛顿(牛)(N)G=mg =ρvg压强 P 帕斯卡(帕)(Pa) P=F/S功 W 焦耳(焦)(J) W=Fs ;W=Gh功率 P 瓦特(瓦)(W) P=W/t电流 I 安培(安)(A) I=U/R电压 U 伏特(伏)(V) U=IR电阻 R 欧姆(欧)(Ω) R=U/I电功 W 焦耳(焦)(J) W=UIt=U^2/RT=I^2RT=PT电功率 P 瓦特(瓦)(W) P=W/t=UI;P=Fv;P=U^2/R=I^2R热量 Q 焦耳(焦)(J) Q吸=cmΔt(Δt=t高-t低)( c是比热容)Q放=mq (q是热值水的热值是4.3×10^3J/kg·℃)比热容 c 焦/(千克°C)J/(kg°C)真空中光速3×10的8次方米/秒三亿米或三十万千米/秒g= 9.8牛顿/千克15°C空气中声速 340米/秒对人体的安全电压不高于36伏初中物理基本概念概要编辑本段一、测量长度L国际单位:米;测量工具:刻度尺;测量时要估读到最小刻度的下一位;光年的单位是长度单位,具体含义是:光沿直线传播一年的距离。
1千米=1000米1米=10分米1分米=10厘米1厘米=10毫米1毫米=1000微米 1微米=1000纳米时间t国际单位:秒;测量工具:钟表;实验室中用停表。
1时=3600秒,1秒=1000毫秒。
质量m物体中所含物质的多少叫质量。
国际单位:千克;测量工具:天平,秤;实验室用托盘天平或学生天平。
功率PP=FV编辑本段二、机械运动机械运动:物体位置发生变化的运动。
参照物:判断一个物体运动必须选取另一个物体作标准,这个被选作标准的物体叫参照物。
量 的 计 算

量的计算量的计算在科学研究和工程应用中起着重要的作用。
通过对各种物理量进行计算,可以帮助我们理解物理现象、解决实际问题,并为科学研究和工程设计提供基础数据。
本文将介绍一些常见的量的计算方法。
一、基本物理量的计算在物理学中,有一些基本物理量是无法由其他量表示的,它们通常被称为基本物理量。
例如,长度、质量、时间和电流等都是基本物理量。
下面是几个基本物理量的计算方法。
1. 长度的计算长度是空间中两点之间的距离。
常见的长度单位有米(m)、千米(km)、厘米(cm)等。
当我们知道两个点的坐标时,可以使用勾股定理计算它们之间的距离。
假设有两点A(x1, y1)和B(x2, y2),它们之间的距离d可以用以下公式表示:d = sqrt((x2 - x1)^2 + (y2 - y1)^2)2. 质量的计算质量是物体所固有的性质,是描述物体惯性的物理量。
质量的计算可以通过称重获得,通常使用千克(kg)作为单位。
在实际计算中,我们经常需要对多个物体的质量进行加减运算。
例如,在天平上放置两个物体A和B,物体A的质量为m1,物体B的质量为m2,两物体之和的质量可以表示为:m = m1 + m23. 时间的计算时间是描述事件发生顺序和持续时间的物理量。
常见的时间单位有秒(s)、分钟(min)、小时(h)等。
在计算中,我们经常需要计算时间间隔或时间差。
假设有两个时间点A和B,它们之间的时间差可以表示为:Δt = t2 - t1其中,Δt表示时间差,t1和t2分别表示时间点A和B。
4. 电流的计算电流是指电荷单位时间通过导线截面的量,是描述电路中电子流动强度的物理量。
常用的电流单位为安(A)。
电流的计算可以使用欧姆定律来进行,欧姆定律表示为:I = V / R其中,I表示电流,V表示电压,R表示电阻。
二、导出物理量的计算在实际应用中,很多物理量不能直接测量,而需要通过其他已知的物理量进行计算。
下面是几个常见的导出物理量的计算方法。
常见物理量计算方法总结

常见物理量计算⽅法总结常见物理量计算⽅法总结汪燕青⾼三备考的时间已经不多了,为帮助⼤家能在读完题⽬后迅速、准确地找到解题的切⼊点,能较快地选出、选准公式,特将⾼中物理中常见的物理量的计算⽅法总结如下,以期能达到举⼀反三、事半功倍的效果。
1、⼒的计算⽅法:①⽜顿第⼆定律;②动量定理;③动能定理;④各种⼒的计算公式:库仑⼒F=kq1q2/r2;电场⼒F=qE;匀强电场中F=qU/d;安培⼒:F=BIL(B与I垂直,匀强磁场,直线电流,L为有效长度);洛仑兹⼒f=qvB(匀强磁场,v与B垂直)。
2、位移的计算⽅法:①位移公式(匀速直线运动或匀变速直线运动、平抛运动、匀速圆周运动、类平抛运动、简谐运动);②动能定理;3、路程的计算:①若物体作单向直线运动,则转化为位移的计算;②匀速圆周运动中可⽤线速度公式v=s/t或弧长s=rΦ(即弧长等于半径与圆⼼⾓的乘积)计算;③对于空⽓阻⼒或滑动摩擦⼒,如果⼀直做负功,则做的功W=f·S,S为物体的路程;4、速度的计算:①相应的运动学公式(如匀速直线运动,匀变速直线运动,平抛运动,匀速圆周运动);②动能定理;③动量定理;④动量守恒定律;⑤能量守恒定律(包括机械能守恒定律),功能关系;⑥对于匀速圆周运动,可⽤相应的线速度公式;对于涉及天体或卫星的运动,可根据F 万=F向进⾏计算;⑦对于电磁感应问题,可⽤E=BLV计算,对于涉及匀强磁场的洛仑兹⼒,可⽤f=qvB计算;5、加速度的计算:①对于匀变速直线运动,可⽤运动学公式;对于匀速圆周运动,可⽤向⼼加速度公式;②⽤⽜顿第⼆定律;③重⼒加速度的计算则可⽤(a)⾃由落体运动公式;竖直上抛运动公式;平抛运动公式;(b)⽤mg/=GMm/r2(其中要注意r 为到天体中⼼的距离;以及黄⾦变换GM=gR2);(c)单摆的周期公式T=2 ;6、时间的计算:①对匀速直线运动或匀变速直线运动⽤相应的运动学公式;②⽤动量定理;③对匀速圆周运动:可⽤;④对平抛运动(或类平抛运动)则⽤7、质量的计算:①密度公式m= ;②⽜顿第⼆定律;③动量定理;动量守恒定律;④动能定理;机械能守恒定律;⑤天体质量的计算:(a)借助绕该天体做匀速圆周运动的其他物体,利⽤F万=F向计算;(b)根据mg/=GMm/r2计算;8、波长、波速、周期的计算:①波长:(a)可⽤v=λ/T;或者根据两质点间的距离,利⽤振动和波动知识找出这⼀距离与波长的关系(注意先写出通项公式);(b)或者直接由波形图中读出;(c)根据波的⼲涉中振动加强和振动减弱的条件计算;②波速:根据v=λ/T=λf=s/t计算;③周期:(a)T=t/N(即总时间除以总全振动次数)=λ/v=1/f;(b)利⽤质点的振动情况,由所给出的时间与周期的关系进⾏计算(要尽量写出通项公式);在进⾏这些计算时,应理解清楚在振动图中的“上坡上,下坡下”和波动图中的“上坡下,下坡上”这两句⼝诀的确切含义,千万不要弄错。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
【转】STL常用算法#include algorithm常用版本返回Typestd::find()find(_InIt _Fisrt,_InIt _Last,_Ty _Val);从两个迭代器指定的范围中查找指定值引用被查找的值的iterator或end()std::find_if()find_if(_InIt _Fisrt,_InIt _Last,?_CallBack);从两个迭代器指定的范围中查找与回调谓词匹配的实例与谓词匹配的实例的iterator或end()std::find_if_not()find_if_not(_InIt _Fisrt,_InIt _Last,_Func _CallBack); 从迭代器范围中返回第一个不符合谓词的元素第一个不符合谓词的元素的iterator或end()std::count()count(_InIt _First,_InIt _Last,_Ty _Val);求得一个元素序列中与第三个参数相符的元素的个数与第三个参数匹配的元素的int个数std::count_if()count_if(_InIt _First,_InIt _Last, _CallBack);求得一个序列中与谓词匹配的元素的个数符合条件元素的int个数std::generate()generate(_FwdIt _First,_FwdIt _Last,?_CallBack);通过特定值填充一个迭代器范围std::max()max(_Left,_Right -*,Predicate*-);通过operator或用户提供的二元谓词比较任意类型的两个元素返回较大的一个元素的const引用std::min()min(_Left,_Right -*,Predicate*-);通过operator或用户提供的二元谓词比较任意类型的两个元素较小的一个元素的const引用std::max_element()max_element(_FwdIt _First,_FwdIt _Last -*,_Pred*-);从一组任意类型的元素元素序列中查找"最大"的一个引用"最大”的元素的iteratorstd::min_element()min_element(_FwdIt _First,_FwdIt _Last -*,_Pred*-);从一组任意类型的元素元素序列中查找"最小"的一个引用"最小"的元素的iteratoradjacent_find()adjacent_find(_FwdIt?_First, _FwdIt _Last-*,_Pred*-);从一组任意类型的元素序列中查找有重复的元素引用重复的第一个元素的iterator或者end()std::all_of()all_of(_InIt _First,_InIt _Last,Pr _Pred);当一组元素序列全部与谓词匹配时返回true否则返回falsestd::any_of()any_of(_InIt _First,_InIt _Last,_Pr _Pred);当一组元素序列中任意一个元素与谓词匹配时返回true否则返回falsestd::none_of()none_of(_InIt _First,_InIt _Last,_Pr?_Pred);当一组元素序列全部都不与谓词匹配时返回true否则返回falsestd::for_each()for_each(_InIt _First,_InIt _Last,_CallBack);对指定范围内的所有元素执行一次_CallBack_CallBackl类型std::transform()transform(_InIt_SrcFirst,_InIt _SrcLast,_OutIt_DestBegin,_CallBack);对指定范围的元素执行回调后生成新的元素,然后将这些新元素保存在第三个参数指定的目标范围中引用Dest范围的past-the-end的_OutputIteratortransform(_InIt _First1,_InIt _Last,_InIt _First2,_OutIt _DestBegin,_CallBack);?对两个指定序列的元素调用二元谓词,并将结果存入到第四个参数指定的容器中引用Dest范围的past-the-end的_OutputIteratorstd::equal()equal(_InIt _First1,_InIt _Last1,_InIt _First2 -*,_Pred*-);对两个不同类型的容器比较对应位置的值,当全部相等或者全部符合谓词时返回true否则返回falsestd::copy()copy(_InIt _SrcBegin,_InIt _SrcEnd,_OutIt _DestBegin);将一个序列的元素复制到另一个序列中,Src范围与Dest范围不能相同,但可以重叠,std::copy不会向目标序列中插入元素,而会直接修改元素,使用前必须配合_Dest序列的resize()函数给Dest序列重分配足够的空间引用Dest范围past_the_end的_OutputIteratorstd::copy_backward()copy_backward(_InIt?_SrcBegin,_InIt?_SrcEnd,_OutIt _DestEnd);将Src范围的元素反向复制到Dest范围中,也就是从Src范围最后一个元素开始复制,将这个元素放在Dest范围的最后一个位置,然后再每一次复制后反向移动.第三个参数应该是_DestEnd而不是_DestBegin 引用Dest范围的_Begin()的_OutputIteratorstd::copy_ifcopy_if(_InIt?_SrcBegin,_InIt?_SrcEnd,_OutIt _DestBegin,_Pr _Pred);对一个序列中每个准备复制的元素执行一次_Callback,如果返回值为true,那么执行copy操作,否则不执行;返回了Dest范围中最后一个复制的元素的后一个位置,这是为了配合past_the_end来删除多余的元素:复制完成后使用_Dest.erase(_CopyEndIt,past_the_end);来删除Dest范围多余的元素位置返回引用Dest范围的最后一个复制的元素的后一个位置的_OutputIteratorstd::copy_n()copy_n(_InIt?_SrcBegin,_Ty _Cnt,_OutIt _DestBegin);从Src范围复制_Cnt个元素到Dest范围,第二个参数是一个指定要复制的元素个数的整数返回引用Dest范围的past_the_endstd::partition_copy()partition_copy(_InIt?_SrcBegin,_InIt?_SrcEnd,_OutIt_Dest1,_OutIt _Dest2,_Pr _Pred);对一个序列的元素进行依据谓词返回的结果进行划分复制,首先对Src 序列中的每一个元素执行一次谓词,如果返回true,那么将这个元素复制到_Dest1,如果返回false,复制到_Dest2,复制之前需要使用resize()重置Dest的空间;算法返回一个打包_Dest1和_Dest2的one_past_the_last_copied的std::pair,利用这个pair可以删除多分配的空间打包引用_Dest1和_Dest2的one_past_the_last_copied的_OutputIterator的std::pairstd::move()move(_InIt?_SrcBegin,_InIt _SrcEnd,_OutIt _DestBegin);需要给元素提供移动赋值运算符,将Src序列的元素通过移动赋值运算符移动到Dest序列,在移动操作中,SrcObject被重置了,因为DstObject 接管了SrcObject资-源的所有权,这意味着在move操作过后Src序列中的对象不能再使用返回Dest范围的引用past_the_end的_OutputIteratorStd::move_backward()move_backward(_InIt _SrcBegin,_InIt _SrcEnd,_OutIt _DstEnd)使用了和std::move()相同的移动机制,但是按照从最后一个元素向第一个元素的顺序进行移动返回Dest范围的引用_Begin()的_OutputIteratorreplace(_FwdIt _First,_FwdIt _Last,const _Ty _OldVal,const _Ty _NewVal);这个算法将一个范围中的匹配某个值的元素替换为第三个参数指定的新值std::replace_if()replace_if(_FwdIt _First,_FwdIt _Last,_Pr _Pred,const _Ty _NewVal);这个算法将一个范围中的匹配某个谓词的元素替换为第三个参数指定的新值std::remove()remove(_FwdIt _First,_FwdIt _Last,const _Ty _Val);?这个算法并不是将序列中与_Val匹配的元素直接删除,而是将它们移动到容器的末端,然后返回引用第一个被移除的元素的iterator,可以利用这个iterator和end()将被移除的元素彻底擦除返回引用第一个被移除的元素的_FwdIteratorstd::remove_if()remove_if(_FwdIt _First,_FwdIt _Last,_Pr _Pred);这个算法并不是将序列中与谓词匹配的元素直接删除,而是将它们移动到容器的末端,然后返回引用第一个被移除的元素的iterator,可以利用这个iterator和end()将被移除的元素彻底擦除返回引用第一个被移除的元素的_FwdIteratorunique(_FwdIt _First,_FwdIt _Last -*,_Pr _Pred)*-;std::unique算法是特殊的std::remove算法,和后者一样,std::unique并不是直接将重复的元素删除,而是将它们全部移动到容器的尾端,然后返回引用第一个被移除的元素的iterator,可以利用这个iterator和end()将被移除的元素彻底擦除返回引用第一个被移除的元素的_FwdIteratorstd::unique_copyunique(_FwdIt _SrcBegin,_FwdIt _SrcEnd,_OutIt _DestBegin? -*,_Pr _Pred*-);std::unique()的基本形式是就地操作数据,std::unique_copy则是将操作的结果复制到Dest范围中返回引用Dest范围的元素的_OutputIteratorstd::reverse()reverse(_BidIt _First,_BidIt _Last);将范围中的第一个元素和最后一个元素交换,第二个元素和倒数第二个元素交换,依此类推std::reverse_copy()reverse_copy(_BidIt _SrcBegin,_BidIt _SrcEnd,_OutIt _DestBegin);std::reverse是就地操作数据,std::reverse_copy将结果复制到Dest范围中返回引用Dest范围的元素的_OutputIteratorstd::sort()sort(_RanIt _First,_RanIt _Last -*,_Pr _Pred*-);将范围中的元素按operator或_CallBack进行排序std::merge()merge(_InIt _SrcBegin1,_InIt _SrcEnd1,_InIt _SrcBegin2,_InIt _SrcEnd2,_OutIt _DestBegin,?-*,_Pr _Prd*-);将两个排好序的Src序列合并成一个元素序列,然后将结果复制到Dest序列中,并且依然保持排序的顺序,结果是一个包含两个Src序列的所有元素的有序序列,注意一定要使用两个排好序的序列进行merge操作引用Dest序列的past_the_end的_OutputIteratorstd::is_sorted()sort(_FwdIt _First,_FwdIt _Last -*,_Pr _Pred*-);验证一个序列是否是有序序列.如果是,返回true,否则返回falsestd:random_shuffle()random_shuffle(_RanIt _First,_RanIt _Last -*,_Fn _Func*-将一个序列的顺序打乱,这个算法适用于洗牌之类的任务,对一个版本默认使用标准C库的rand()函数,第二个版本需要提供一个随机数生成器, 以适应不同问题领域的随机性集合算法std::includes()includes(_InIt _First1,_InIt _Last1,_InIt _First2,_InIt _Last2 -*,_Pr _Pred*-);验证第二个序列是否是第一个序列的子集,注意不是真子集,而是子集,如果是返回true,否则返回falsestd::set_union()set_union(_InIt _SrcBegin1,_InIt _SrcEnd1,_InIt _SrcBegin2,_InIt _SrcEnd2,_OutIt _DestBegin?-*,_Pr _Pred*-);计算两个有序序列的并集,然后将并集的结果存入第四个参数指定的Dest序列中,注意在计算前必须给Dest容器分配足够的空间,因为Dest范围最大是_Src1和_Src2的size()和,所以在进行合并后有可能会留下一些空间,set_union算法返回一个引用Dest范围中最后一个被添加进去的元素的后一个位置的iterator,利用它可以将Dest中多余的空间删除返回一个引用Dest范围中最后一个被添加进去的元素的后一个位置的_OutputIteratorstd::set_intersection()set_intersection(_InIt _SrcBegin1,_InIt _SrcEnd1,_InIt _SrcBegin2,_InIt _SrcEnd2,_OutIt _DestBegin?-*,_Pr _Pred*-);计算两个有序序列的交集,然后将交集的结果存入第四个参数指定的Dest序列中,注意在计算前必须给Dest容器分配足够的空间,因为Dest范围最大是两个_Src范围的size的最大值,所以在进行取交集后有可能会留下一些空间,set_union算法返回一个引用Dest范围中最后一个被添加进去的元素的后一个位置的iterator,利用它可以将Dest中多余的空间删除返回一个引用Dest范围中最后一个被添加进去的元素的后一个位置的_OutputIteratorstd?::set_difference()set_difference(_InIt _SrcBegin1,_InIt _SrcEnd1,_InIt _SrcBegin2,_InIt _SrcEnd2,_OutIt _DestBegin?-*,_Pr _Pred*-);计算两个有序序列的集合差,(集合差:所有存在于第一个集合,但是不存在与第二个集合中的所有元素),然后将求集合差的结果存入第四个参数指定的Dest序列中,注意在计算前必须给Dest容器分配足够的空间,因为Dest范围最大是两个_Src范围的size的最大值,所以在进行取交集后有可能会留下一些空间,set_union算法返回一个引用Dest范围中最后一个被添加进去的元素的后一个位置的iterator,利用它可以将Dest中多余的空间删除返回一个引用Dest范围中最后一个被添加进去的元素的后一个位置的_OutputIteratorstd::set_symmetric_difference()set_symmetric_difference(_InIt _SrcBegin1,_InIt _SrcEnd1,_InIt _SrcBegin2,_InIt _SrcEnd2,_OutIt _DestBegin?-*,_Pr _Pred*-);计算两个有序序列的对称集合差,(对称集合差:所有存在于某一个集合,但是不存在与第二个集合中的元素),然后将求对称集合差的结果存入第四个参数指定的Dest序列中,注意在计算前必须给Dest容器分配足够的空间,因为Dest范围最大是_Src1和_Src2的size()和,所以在进行取交集后有可能会留下一些空间,set_union算法返回一个引用Dest范围中最后一个被添加进去的元素的后一个位置的iterator,利用它可以将Dest中多余的空间删除返回一个引用Dest范围中最后一个被添加进去的元素的后一个位置的_OutputIteratorWarning: 务必要确保Dest范围足够大,足以保存操作的结果.对于set_union()和set_symmetric_difference(),结果大小的上限是两个输入范围的总和.对于set_intersection()和set_difference(),结果大小的上限是两个输入范围大小中的最大值advance(result1,4);--注意这里跟上面不一样mem_fun与mem_fun_ref:类成员函数的适配器,区别是一个需要指针,而另一个仅需要一般对象。
