BCP
业务连续性计划(应急计划)

业务连续性计划(应急计划)引言概述:业务连续性计划(BCP)是组织为了在面临各种突发事件时保障业务正常运转而制定的一套应急计划。
随着全球经济的不断发展和信息化程度的提高,越来越多的组织意识到制定和实施业务连续性计划的重要性。
本文将详细介绍业务连续性计划的定义、目的、内容、实施流程和不断改进的重要性。
一、定义1.1 业务连续性计划是指组织为了应对各种突发事件而制定的一套综合性计划。
1.2 BCP的目标是在面临灾难性事件时,确保组织的核心业务能够持续运行。
1.3 BCP包括预防措施、应急响应、恢复和重建等方面的内容。
二、目的2.1 保障组织的核心业务能够持续运行,减少业务中断对组织造成的损失。
2.2 提高组织对各种突发事件的应对能力,降低业务风险。
2.3 增强组织的抗灾能力,提升组织的可持续发展能力。
三、内容3.1 评估业务风险:识别潜在的业务中断风险,分析其可能性和影响。
3.2 制定应急计划:根据风险评估结果,制定相应的应急预案和流程。
3.3 实施BCP演练:定期组织业务连续性计划演练,检验其有效性和可行性。
四、实施流程4.1 确定BCP团队:组建专门的业务连续性计划团队,负责制定和实施BCP。
4.2 制定BCP计划:根据业务风险评估结果,制定详细的业务连续性计划。
4.3 培训和演练:对组织内部人员进行业务连续性计划培训,定期组织演练。
五、不断改进的重要性5.1 定期评估和更新:定期对业务连续性计划进行评估,根据实践经验不断更新和完善。
5.2 持续改进:根据演练和实践中发现的问题,及时调整和改进业务连续性计划。
5.3 提高应对能力:通过持续改进,提高组织对各种突发事件的应对能力,确保业务的稳定运行。
结语:业务连续性计划是组织应对各种突发事件的重要保障,惟独制定科学合理的BCP,并不断改进和完善,才干提高组织的抗灾能力和可持续发展能力。
希翼各个组织都能重视业务连续性计划的制定和实施,确保业务的稳定运行。
BCP学习(2):BCP详解
BCP学习(2):BCP详解⼀、什么是BCP BCP是SQL Server中负责导⼊导出数据的⼀个命令⾏⼯具,它是基于DB-Library的,并且能以并⾏的⽅式⾼效地导⼊导出⼤批量的数据。
BCP可以将数据库的表或视图直接导出,也能通过SELECT FROM语句对表或视图进⾏过滤后导出。
在导⼊导出数据时,可以使⽤默认值或是使⽤⼀个格式⽂件将⽂件中的数据导⼊到数据库或将数据库中的数据导出到⽂件中。
BCP是SQL Server 2000和SQL Server 2005⼯具中的⼀部分,BCP在SQL Server 2000和在SQL Server 2005中的版本不⼀样,实现的⽅法也不⼀样。
在SQL Server 2000中,它是通过ODBCBCP.DLL这个⽂件来实现的。
但是在SQL Server 2005中,它是通过SNAC来实现的。
⼆、BCP的主要功能(1) 导⼊。
这个动作使⽤in命令完成,后⾯跟需要导⼊的⽂件名。
(2) 导出。
这个动作使⽤out命令完成,后⾯跟需要导出的⽂件名。
(3) 使⽤SQL语句导出。
这个动作使⽤queryout命令完成,它跟out类似,只是数据源不是表或视图名,⽽是SQL语句。
(4) 导出格式⽂件。
这个动作使⽤format命令完成,后⽽跟格式⽂件名。
三、BCP的主要参数(SQL Server 2005)在CMD中敲⼊bcp.exe /? 就会看到如下的命令⾏参数:接下来详细讲解每个参数的具体含义。
· -m max_errors: 规定最⼤允许的可以操作出错的个数。
缺省是10,也就是说,如果在bcp操作中,碰到⼀个错,如果还在允许出错个数范围内,它还会继续进⾏bcp操作。
· -f format_file: 给出格式⽂件.format_file表⽰格式⽂件名。
这个选项依赖于上述的动作,如果使⽤的是in或out,format_file表⽰已经存在的格式⽂件,如果使⽤的是format则表⽰是要⽣成的格式⽂件。
bcp管理手册

bcp管理手册
BCP(Business Continuity Planning)管理手册是一个组织用来
应对突发事件和灾难的管理工具。
BCP管理手册提供了重要
信息和指导,帮助组织预防灾难、恢复业务,并确保业务的持续性。
BCP管理手册包括以下内容:
1. 管理框架和目标:BCP管理手册应明确组织的灾难恢复目标、战略和策略,以及相关的管理结构和职责。
2. 风险评估:BCP管理手册应包含组织对潜在风险的评估和
分析,包括自然灾害、技术故障、人为错误等。
这有助于确定关键业务功能和基础设施,并针对潜在威胁进行风险管理。
3. 灾难恢复计划:BCP管理手册应详细说明各个关键业务功
能的恢复计划,包括备份和恢复数据、设备备份和替代方案等。
同时,还需要明确灾难恢复团队的角色和责任。
4. 通信计划:BCP管理手册应包含有效的内部和外部通信计划,以确保在灾难发生时,相关各方都能及时获得必要的信息。
5. 演练和测试:BCP管理手册应指导组织定期进行演练和测试,以验证灾难恢复计划的有效性和可行性,并及时调整和更新计划。
6. 合规性和监督:BCP管理手册应明确相关法规、标准和要
求,并确保组织的灾难恢复计划符合这些合规性要求。
同时,还需要制定合适的监督和审计机制,以确保计划的执行和有效性。
BCP管理手册是一个组织灾难恢复管理体系的核心文件,它为组织提供了一套具体的策略和步骤,帮助组织抵御和应对各种突发事件和灾难,以确保业务的连续性和可持续发展。
(完整版)业务连续性计划BCP

业务连续性计划事先制定一个完备的业务连续性计划(Business Continuity Planning,缩写为BCP),积极防范并且应变处理灾难发生的一系列后果,将灾难的蔓延和损失控制在企业能够承担的范围以内,已成为现代企业管理范畴内的一个十分重要的任务。
【第一部分】BCP的基本要素笼统地说,BCP的目标只有一个,那就是确定并减少危险可能带来的损失,有效地保障业务的连续性。
而有关BCP的一些特定目标我们将在以下各个部分中加以描述。
BCP实施的最终结果是:●一组防范危险的评测指标;●一支执行团队,在经过培训后可以处理各种危险事件;●一套计划,提供危险发生时的路线图。
该计划应该是充分和完备的,必须详细落实到该计划实施范围内的每一个单位、人员或设备。
我们下面所要讨论的主要是与企业中IT设施相关的内容,没有涉及到企业人员在危险状况下的安全管理问题。
每个企业所制定的BCP都应该有每个企业或者所处行业独有的特色,彼此之间不会完全一致,但大致上说来,一个完备的BCP主要是由以下一些关键部分构成的:一、危险评估危险评估就是认识并分析各种潜在危险的结果。
这些危险的来源可能是:●各种区域性的天然灾难,如洪水、地震、疫病等;●人为事故或蓄意破坏造成的严重灾难,如火灾、恐怖主义袭击等;●安全威胁、硬件、网络或通信故障;●灾难性的应用系统错误。
所有的危险都应纳入企业的危险评估范围,并且应对各种危险的可能来源地进行较准确的定位。
对于每一种危险的来源都应该认识到:●危险的类型;●危险的程度;●危险发生的可能性。
比如说,如果按照有无警示性先兆来分,各类危险还可以分为:●有些危险可能没有任何先兆而突然发生,无法事先防范;●有些危险可以有一定的先兆,可以迅速启动应急计划加以防范,比如疫病的传播;●有些危险可能从来不会发生。
如果按照危险的破环类型或程度来分,它们对业务的影响可以分为:●经营场所及设备完全破环;●经营场所及设备部分破环;●经营场所及设备完好,但人员不能进入,比如疫病的隔离、恐怖威胁造成的人员输散等.显然,对于企业来说,一个完备的BCP必须尽可能多地考虑到所有可能的危险情况,只有处理灾难性事件的计划而没有处理应用系统失误的计划,这样的BCP是不完备的;反之亦然。
(完整版)业务连续性计划BCP

业务连续性计划事先制定一个完备的业务连续性计划(Business Continuity Planning,缩写为BCP),积极防范并且应变处理灾难发生的一系列后果,将灾难的蔓延和损失控制在企业能够承担的范围以内,已成为现代企业管理范畴内的一个十分重要的任务。
【第一部分】BCP的基本要素笼统地说,BCP的目标只有一个,那就是确定并减少危险可能带来的损失,有效地保障业务的连续性。
而有关BCP的一些特定目标我们将在以下各个部分中加以描述。
BCP实施的最终结果是:●一组防范危险的评测指标;●一支执行团队,在经过培训后可以处理各种危险事件;●一套计划,提供危险发生时的路线图。
该计划应该是充分和完备的,必须详细落实到该计划实施范围内的每一个单位、人员或设备。
我们下面所要讨论的主要是与企业中IT设施相关的内容,没有涉及到企业人员在危险状况下的安全管理问题。
每个企业所制定的BCP都应该有每个企业或者所处行业独有的特色,彼此之间不会完全一致,但大致上说来,一个完备的BCP主要是由以下一些关键部分构成的:一、危险评估危险评估就是认识并分析各种潜在危险的结果。
这些危险的来源可能是:●各种区域性的天然灾难,如洪水、地震、疫病等;●人为事故或蓄意破坏造成的严重灾难,如火灾、恐怖主义袭击等;●安全威胁、硬件、网络或通信故障;●灾难性的应用系统错误。
所有的危险都应纳入企业的危险评估范围,并且应对各种危险的可能来源地进行较准确的定位。
对于每一种危险的来源都应该认识到:●危险的类型;●危险的程度;●危险发生的可能性。
比如说,如果按照有无警示性先兆来分,各类危险还可以分为:●有些危险可能没有任何先兆而突然发生,无法事先防范;●有些危险可以有一定的先兆,可以迅速启动应急计划加以防范,比如疫病的传播;●有些危险可能从来不会发生。
如果按照危险的破环类型或程度来分,它们对业务的影响可以分为:●经营场所及设备完全破环;●经营场所及设备部分破环;●经营场所及设备完好,但人员不能进入,比如疫病的隔离、恐怖威胁造成的人员输散等。
bcp合成方法

bcp合成方法BCP合成方法是一种常用的化学合成方法,广泛应用于有机合成领域。
BCP是指Block Copolymer,即块共聚物,它由两种或多种不同结构的聚合物块组成。
BCP合成方法的主要目的是通过控制聚合物块的长度、结构和分布来实现对材料性质的调控。
BCP合成方法的基本原理是通过控制聚合反应的条件和选择适当的反应物,使得不同结构的聚合物块在反应中发生共聚反应。
其中,聚合反应的条件包括反应温度、反应时间、反应物的浓度和催化剂的选择等。
通过调节这些条件,可以控制聚合物块的长度和分布。
而选择适当的反应物,可以控制聚合物块的结构和化学特性。
BCP合成方法的具体步骤包括以下几个方面:1. 选择合适的反应体系:BCP合成方法可以使用不同的反应体系,如自由基聚合、阴离子聚合、阳离子聚合等。
根据所需合成的聚合物块的特性,选择合适的反应体系。
2. 设计合适的反应条件:根据反应体系的选择,确定合适的反应温度、反应时间和反应物的浓度。
这些条件需要根据具体合成需求进行优化,以实现所需的聚合物块的长度和分布。
3. 合成聚合物块:根据合适的反应条件,将反应物加入反应体系中进行反应。
反应过程中,通过控制反应时间和反应物的浓度来控制聚合物块的长度和分布。
同时,可以通过添加适当的催化剂来调控反应速率和聚合物块的结构。
4. 纯化和分离:合成得到的BCP通常需要进行纯化和分离。
纯化的方法包括溶剂萃取、重结晶等,通过这些方法可以去除杂质,得到纯净的BCP产物。
分离的方法包括凝胶渗透色谱、溶液扩散等,通过这些方法可以将不同长度的聚合物块分离开来。
5. 表征和应用:最后,需要对合成得到的BCP进行表征和应用研究。
表征的方法包括核磁共振、红外光谱、热重分析等,通过这些方法可以确定BCP的结构和性质。
应用研究主要包括将合成得到的BCP 应用于材料科学、纳米技术等领域,以实现对材料性质的调控和优化。
BCP合成方法是一种重要的化学合成方法,通过控制聚合反应的条件和选择合适的反应物,可以实现对聚合物块的长度、结构和分布的调控。
业务连续性计划

CBK Domain Business Continuity Planning
业务连续性计划
本章知识概要
业务连续性计划(BCP)和灾难恢复计划(DRP)涉及到正 常业务运作遭遇重大中断时对业务的保持。BCP和DRP涉及 到保护关键业务过程免遭重大系统和网络故障的影响所进行 的特定的准备、测试和更新活动。
© 2005 Aryasec Information Technology Limited
4
BCP概述
灾难的定义
灾难(Disaster)是突发的、导致重大损失的不幸事件,包括:
➢ 自然的(Natural),如地震(Earthquakes)、洪水(Floods)、强对流天气 (Storms)、火山爆发(Volcanic Eruptions)、自然火灾(National Fires); ➢ 系统/技术的(System/Technical),如硬件、软件中断(Outages)、系统/编程错 误(Errors); ➢ 供应系统(Supply Systems),通讯中断、配电系统(Power Distribution)中断、 管道破裂(Burst Pipes); ➢ 人为的(Man-Made ),爆炸(Explosions)、火灾(Fires)、故意破坏 (Purposeful Destruction)、航空器坠毁(Aircraft Crashes)、有害物质泄漏 (Hazardous Spills)、化学污染(Chemical Contamination)、有害代码(Malicious Code) ➢ 政治的(Political),如恐怖袭击(Terrorist Attacks)、骚乱(Riots)、罢工 (Strikes)。
➢ 针对紧急情况采取快速、准确和标准的响应; ➢ 在既定时间范围内恢复机构的关键功能; ➢ 减少事件造成的损失; ➢ 记录明确的恢复规程; ➢ 提供恢复所需的资源和联络清单; ➢ 事先对恢复规程进行测试,培训恢复团队; ➢ 记录关键记录和信息的存储、保护和获取规程; ➢ 遵循法律、法规和行业规范的要求。
bcp 参数

bcp 参数BCP(Business Continuity Planning)是指企业为应对各种突发事件和灾害,制定的一套全面的业务连续性计划。
它旨在确保企业在面临灾害或突发事件时能够持续运营,并最大限度地减少损失。
本文将从BCP的定义、重要性、实施步骤和案例分析等方面进行阐述。
一、BCP的定义和重要性BCP是指企业为防止、减轻和应对各种内外部威胁、灾害和突发事件,制定的一套全面的业务连续性计划。
它包括预防、应急响应、恢复和重建等多个阶段,旨在帮助企业保持业务连续性和恢复能力。
BCP的重要性不容忽视。
首先,BCP有助于企业降低风险。
通过提前制定应对各种灾害和突发事件的计划,企业可以减少因意外情况而造成的损失。
其次,BCP有助于企业保持良好的声誉。
当企业能够应对突发事件并保持业务连续性时,它们将赢得客户和伙伴的信任和尊重。
最后,BCP还有助于企业提高竞争力。
在面对同行业竞争激烈的市场环境中,企业具备良好的BCP能力能够更好地应对各种风险,从而在市场上立于不败之地。
二、BCP的实施步骤1. 风险评估:企业需要对可能影响业务连续性的各种风险进行评估,如自然灾害、技术故障、人为破坏等。
通过分析风险的发生概率和影响程度,确定应对重点和优先级。
2. 制定策略:根据风险评估的结果,制定相应的业务连续性策略。
这些策略包括预防策略、应急响应策略、恢复策略和重建策略。
预防策略主要是通过控制风险的发生概率来减少损失,应急响应策略则是在突发事件发生后迅速采取措施以保护员工和财产,并确保业务的持续进行。
3. 制定计划:制定详细的业务连续性计划,包括应对各种风险的具体步骤、责任人、联系方式等。
计划应该清晰明了,易于操作,并且需要定期进行演练和修订。
4. 实施与测试:根据计划进行实施,并定期进行测试。
测试可以发现计划中的漏洞和不足之处,并及时进行改进。
同时,也可以提高员工对应急措施的熟悉度和应对能力。
5. 持续改进:BCP并非一次性的工作,而是需要持续改进和更新。
bcp的合成文献

bcp的合成文献BCP的合成文献BCP(Bisphenol C)是一种合成化合物,广泛应用于聚合物工业中。
它的合成文献主要涉及到其合成方法、性质和应用等方面。
本文将对BCP的合成文献进行综述和分析。
一、BCP的合成方法BCP的合成方法有多种,其中最常用的是酚醛树脂法。
该方法是通过酚和醛的缩聚反应得到BCP。
具体的合成步骤包括酚和醛的混合、缩聚反应、固化和后处理等。
该方法具有反应条件温和、反应时间短、产率高等优点,因此被广泛应用于工业生产中。
还有一些改进的合成方法,如酚酮法、酚醛酮法等。
这些方法在BCP的合成过程中引入了不同的反应物,以改善产品的性能和降低成本。
例如,酚酮法在酚醛树脂法的基础上引入了酮类化合物,可以提高BCP的热稳定性和机械性能。
二、BCP的性质BCP是一种无色结晶体,具有很高的热稳定性和机械强度。
它在常温下是固体,具有良好的电绝缘性和耐腐蚀性。
此外,BCP还具有较低的热膨胀系数和较高的抗张强度,使其成为一种理想的工程塑料。
BCP的热稳定性是其最重要的性能之一。
研究表明,BCP的热分解温度可达到300℃以上,能够在高温环境下保持稳定。
同时,BCP还具有较好的耐化学腐蚀性,可以在酸、碱等腐蚀性介质中长期使用。
三、BCP的应用BCP由于其独特的性能,在工业中有广泛的应用。
首先,BCP可以作为一种工程塑料,用于制造各种机械零件、电子元件和汽车零部件等。
其高机械强度和热稳定性使得BCP在这些领域具有很大的优势。
BCP还可以用于制备聚酰亚胺树脂和环氧树脂等高性能聚合物材料。
这些材料具有耐高温、耐化学腐蚀等优点,被广泛应用于航空航天、电子通信等领域。
BCP还可以用于制备聚合物纳米复合材料。
研究表明,将纳米材料与BCP复合可以显著提高材料的力学性能、导电性能和耐热性能等。
因此,BCP在纳米材料领域也具有很大的应用潜力。
总结BCP是一种重要的合成化合物,具有很高的热稳定性和机械强度。
其合成方法主要包括酚醛树脂法和改进的合成方法。
时钟同步方案

时钟同步方案在现代社会,时钟同步对于各类系统和网络的正常运行至关重要。
无论是金融交易系统、通信网络还是电力系统,精确的时钟同步都是确保数据传输和相关操作的关键。
为了解决各类设备间的时钟不一致问题,许多时钟同步方案被提出并广泛应用。
本文将介绍几种常见的时钟同步方案及其原理。
一、网络时间协议(NTP)网络时间协议(Network Time Protocol,简称NTP)是一种用于计算机网络中时钟同步的协议。
NTP通过使用时钟差值来同步各个设备的时间,并且能够自动进行校准和纠正。
NTP通常使用UDP协议进行通信,其核心原理是基于时间服务器和客户端之间的时钟差异进行计算和同步。
通过层级的时间服务器结构,NTP可以提供高精度和高可靠性的时钟同步。
二、全球定位系统(GPS)全球定位系统(Global Positioning System,简称GPS)是一种基于卫星导航系统的时钟同步方案。
GPS通过接收卫星信号获取当前时间,并将其同步到设备的系统时钟中。
由于GPS卫星具有高度精确的原子钟,因此可以提供非常精准的时间同步。
使用GPS进行时钟同步需要设备具备GPS接收器,并且在设备所在的位置能够接收到卫星信号。
三、精确时间协议(PTP)精确时间协议(Precision Time Protocol,简称PTP)是一种用于以太网中时钟同步的协议。
PTP基于主从结构,通过在所有从设备上同步时间,其中一个设备充当主设备,向其他设备广播时间信息。
PTP使用硬件触发机制和时间戳来实现纳秒级的时钟同步。
在实时性要求高的应用场景中,如工业自动化和通信领域,PTP是一种常用的时钟同步方案。
四、百纳秒同步协议(BCP)百纳秒同步协议(Boundary Clock Protocol,简称BCP)是一种用于同步计算机网络中时钟的协议。
BCP采用边界时钟的方式将网络划分为不同的区域,并在每个区域内部进行时钟同步。
BCP通过定期投递时间触发帧,将更精确的时间源传递到下一个边界时钟。
BCP手册:数据备份和恢复规范

BCP手册:数据备份和恢复规范背景在现代商业环境中,数据的安全性和可恢复性对于组织的持续运营至关重要。
因此,制定并遵循一套完善的数据备份和恢复规范是必不可少的。
目标本手册的目标是确保组织能够有效地备份和恢复关键数据,以最小化潜在的业务中断和数据丢失风险。
数据备份策略1. 确定备份频率:根据数据的重要性和敏感性确定备份频率。
关键数据应进行日常备份,而非关键数据则可以选择更为灵活的备份计划。
2. 选择备份媒介:确保备份媒介具有足够的容量和可靠性。
常用的备份媒介包括磁带、硬盘和云存储等。
3. 实施完整备份:每次备份都应包括所有关键数据,以确保数据的完整性。
4. 定期验证备份:定期验证备份文件的可读性和完整性,以确保备份数据的有效性。
5. 分层备份策略:采用分层备份策略,包括完整备份、差异备份和增量备份,以优化备份时间和资源使用。
数据恢复流程1. 制定数据恢复计划:在发生数据灾难时,有一个事先制定的数据恢复计划至关重要。
该计划应包括数据恢复流程、责任人和恢复时间目标等。
2. 优先级和紧急性:根据数据的重要性和紧急性,确定需要优先恢复的数据。
确保有清晰的优先级列表以指导恢复过程。
3. 恢复测试:定期进行数据恢复测试,以验证恢复过程的有效性和数据完整性。
任何发现的问题应记录并及时解决。
4. 文档和培训:确保有清晰的数据恢复流程文档,并进行相关的培训,以使相关人员熟悉并能够有效执行数据恢复过程。
监测和持续改进1. 监测备份活动:建立监测机制,定期检查备份活动的执行情况,并记录备份成功率和时间。
任何问题和异常情况都应及时处理。
2. 数据恢复审查:定期审查数据恢复过程的效果,并提出改进意见和建议。
确保数据恢复过程的及时性和准确性。
3. 持续改进计划:在实践中不断改进数据备份和恢复规范,以适应不断变化的数据需求和技术环境。
本手册提供了数据备份和恢复的规范和指导,但具体实施应根据组织的具体需求和环境进行调整和完善。
业务连续性计划BCP

业务连续性计划事先制定一个完备的业务连续性计划(Business Continuity Planning, 缩写为 BCP),积极防范并且应变处理灾难发生的一系列后果,将灾难的蔓延和损失控制在企业能够承担的范围以内,已成为现代企业管理范畴内的一个十分重要的任务。
【第一部分】BCP的基本要素笼统地说,BCP的目标只有一个,那就是确定并减少危险可能带来的损失,有效地保障业务的连续性。
而有关 BCP的一些特定目标我们将在以下各个部分中加以描述。
BCP实施的最终结果是:●一组防范危险的评测指标;●一支执行团队,在经过培训后可以处理各种危险事件;●一套计划,提供危险发生时的路线图。
该计划应该是充分和完备的,必须详细落实到该计划实施范围内的每一个单位、人员或设备。
我们下面所要讨论的主要是与企业中IT 设施相关的内容,没有涉及到企业人员在危险状况下的安全管理问题。
每个企业所制定的BCP都应该有每个企业或者所处行业独有的特色,彼此之间不会完全一致,但大致上说来,一个完备的BCP主要是由以下一些关键部分构成的:一、危险评估危险评估就是认识并分析各种潜在危险的结果。
这些危险的来源可能是:●各种区域性的天然灾难,如洪水、地震、疫病等;●人为事故或蓄意破坏造成的严重灾难,如火灾、恐怖主义袭击等;●安全威胁、硬件、网络或通信故障;●灾难性的应用系统错误。
所有的危险都应纳入企业的危险评估范围,并且应对各种危险的可能来源地进行较准确的定位。
对于每一种危险的来源都应该认识到:●危险的类型;●危险的程度;●危险发生的可能性。
比如说,如果按照有无警示性先兆来分,各类危险还可以分为:●有些危险可能没有任何先兆而突然发生,无法事先防范;●有些危险可以有一定的先兆,可以迅速启动应急计划加以防范,比如疫病的传播;●有些危险可能从来不会发生。
如果按照危险的破环类型或程度来分,它们对业务的影响可以分为:●经营场所及设备完全破环;●经营场所及设备部分破环;●经营场所及设备完好,但人员不能进入,比如疫病的隔离、恐怖威胁造成的人员输散等。
BCP
BCP
蓄电池增压保护(Battery charge protection)简称BCP。
一、BCP简介
专利所有人为日本大阪电気化株式会社,其授权沧海电源科技进行全国推广.如有仿造,属侵犯知识产权行为.
二、BCP特点:
1、延长使用寿命:
(1)、防止过度吸气,防止电池鼓包膨胀变形,尤其是其对蓄电池的使用寿命可延长1-2年以上
(2)、减缓正极板腐蚀程度.
(3)、减少活性物质脱落.
2、行驶动力里程:提高电压的同时,电动助力车的动力输出相对提高,行驶里程延长.
三、适用范围:
BCP适用于任何电动助力车,特别是电动汽车和电动摩托车。
例如,一组48v20ah以旧换新550-650元,而改装并联两个BCP,只不过80元。
达到的效果的同时,省去了500元。
无论客户是新电池还是使用过程中的电池均可安装BCP。
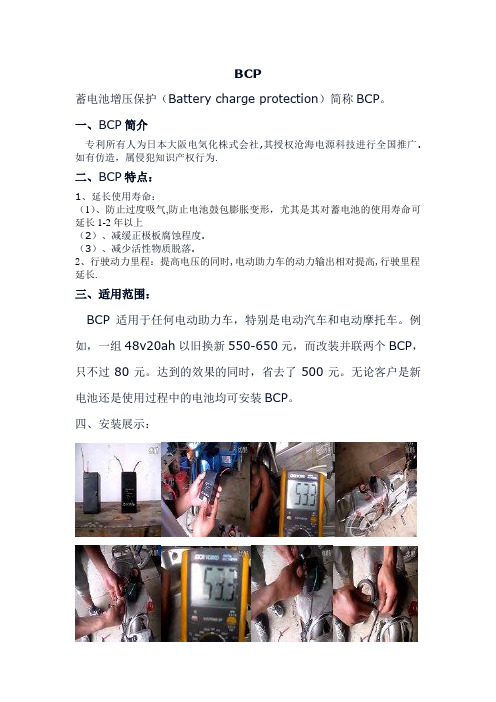
四、安装展示:。
反式钙钛矿中bcp作用

反式钙钛矿中bcp作用反式钙钛矿,又称为钙钛矿钴钨石(Perovskite Cobalt Tungstate,缩写为BCP),是一种具有重要应用潜力的新型材料。
它由钙钛矿结构的晶格构成,具有优异的物理化学性质,广泛应用于能源转换、光电器件、传感器等领域。
在本文中,我们将重点探讨反式钙钛矿BCP在不同领域中的作用。
首先,反式钙钛矿BCP在能源转换方面起到了重要作用。
钙钛矿结构具有良好的光吸收特性,使其成为太阳能电池材料的理想选择之一。
BCP可以通过光吸收产生电荷载流子,并将其输运到电极上,从而实现光电转换。
研究发现,BCP能够有效地吸收可见光和近红外光,并具有高的光电转换效率。
因此,它被广泛应用于太阳能电池领域,有望成为新一代高效的光电器件材料。
其次,反式钙钛矿BCP在光电器件领域的作用不可忽视。
由于其优异的电学性能和良好的光吸收能力,BCP可以用作光电传感器和光电二极管材料。
光电传感器是一种将光信号转换为电信号的装置,广泛应用于光通信、光学测量和图像传感等领域。
反式钙钛矿BCP具有高的光电响应速度和灵敏度,有望用于制备高性能的光电传感器。
此外,BCP还可用作光电二极管材料,用于制备高效的光电转换器件。
此外,反式钙钛矿BCP在传感器领域也有广泛应用。
传感器是一种将环境信号转换为可测量的输出信号的设备,用于检测和监测环境中的物理、化学、生物等参数。
由于BCP具有优异的电学性能和化学稳定性,因此可应用于制备传感器材料。
例如,在气敏传感领域,BCP可以用作传感电极材料,通过检测BCP电极与气体之间的电阻变化实现对气体的检测。
此外,BCP还可用于制备生物传感器,用于检测生物大分子的存在和浓度。
总结起来,反式钙钛矿BCP是一种具有良好应用前景的新型材料。
它在能源转换、光电器件和传感器等领域都起到了重要作用。
未来,随着对BCP材料性能的深入研究和理解,相信它将在更多领域中发挥重要作用,为科学研究和工程应用做出更大贡献。
BCP复原计划人,机,料,法

BCP复原计划人,机,料,法BCP集中在业务层面,主要是保证组织能能持续运作。
DRP是技术层面,确保在灾难下组织的生产系统能在预定义的时间内恢复基本运作。
一般DRP是BCP的一部分,由技术部门负责。
BCP 由运营部门或管理层代表负责。
这五大要素论中,人是处于中心位置和驾驶地位的,就像行驶的汽车一样,汽车的四只轮子是“机”、“料”、“法”、“环”四个要素,驾驶员这个“人”的要素才是主要的。
没有了驾驶员这辆车也就只能原地不动成为废物了。
一个工厂如果机器、物料、加工产品的方法也好,并且周围环境也适合生产,但这个工厂没有员工的话,那他还是没法进行生产。
人的分析:技能问题?制度是否影响人的工作?是选人的问题吗?是培训不够吗?是技能不对口吗?是人员对公司心猿意马吗?有责任人吗?人会操作机器?人适应环境吗?人明白方法吗?人认识料吗?机的分析:就是指生产中所使用的设备、工具等辅助生产用具。
生产中,设备的是否正常运作,工具的好坏都是影响生产进度,产品质量的又一要素。
选型对吗?保养问题吗?给机器的配套对应吗?作机器的人对吗?机器的操作方法对吗?机器放的环境适应吗?机器设备的管理分三个方面,即使用、点检、保养。
使用即根据机器设备的性能及操作要求来培养操作者,使其能够正确操作使用设备进行生产,这是设备管理最基础的内容。
点检指使用前后根据一定标准对设备进行状态及性能的确认,及早发现设备异常,防止设备非预期的使用,这是设备管理的关键。
保养指根据设备特性,按照一定时间间隔对设备进行检修、清洁、上油等,防止设备劣化,延长设备的使用寿命,是设备管理的重要部分。
料的分析:是真货吗?型号对吗?有保质期吗?入厂检验了吗?用的符合规范吗?料适应环境吗,料与机器配合的了吗,料和其它料会不互相影响?法的分析:是按法做的吗?看的明白吗?写的明白吗?法适合吗?有法吗?方法是给对应的人吗?方法在这个环境下行吗?环的分析:在时间轴上环境变了吗?光线、温度、湿度、海拔、污染度考虑了吗?环境是安全的吗?环境是人为的吗?小环境与大坏境能并容吗?工作场所环境。
bai-perron 结构突变点检验代码

结构突变点检验是时间序列分析中常用的一种方法,用于检验序列中是否存在突变点。
在时间序列分析中,结构突变点指的是序列中突然发生变化的点,这种变化可能是由外部因素引起的,也可能是由序列内部变化导致的。
对时间序列中的结构突变点进行检验,有助于我们发现序列中的变化规律,从而更好地理解序列的特性。
在R语言中,有许多包可以用于进行结构突变点检验,其中包括了一些基于不同统计方法的代码,而本文将介绍使用R语言中的“bcp”包进行结构突变点检验的相关代码。
bcp(Bayesian Change Point Analysis)是一种基于贝叶斯思想的结构突变点检验方法,它可以自动判断序列中的突变点数量和位置,同时给出突变点的后验概率,因此在实际应用中具有很高的灵活性和准确性。
以下是使用bcp包进行结构突变点检验的相关代码:1. 安装bcp包首先需要在R中安装bcp包,可以使用以下代码进行安装:```install.packages("bcp")```2. 载入bcp包安装完成后,可以使用以下代码载入bcp包:```library(bcp)```3. 数据准备在进行结构突变点检验之前,需要准备好待分析的时间序列数据,假设我们有一个名为“ts_data”的时间序列数据,可以使用以下代码载入数据:```ts_data <- read.csv("your_data.csv")```4. 模型拟合接下来可以使用bcp包中的函数对时间序列数据进行模型拟合,得到结构突变点的位置和后验概率。
以下是模型拟合的代码:```fit <- bcp(ts_data)```5. 结果展示可以使用summary函数对模型拟合的结果进行展示,包括突变点的位置和后验概率。
以下是展示结果的代码:```summary(fit)```通过以上代码,我们可以使用bcp包对时间序列数据进行结构突变点检验,并得到突变点的位置和后验概率。
bcp化学基团

bcp化学基团
BCP化学基团的研究及应用
BCP化学基团是一类重要的化学基团,其名称源于其由两个不同类型的单体组成的嵌段共聚物,即“block copolymer”。
BCP化学基团的结构由A区块和B区块组成,这两种区块的性质都不同,因此BCP化学基团常常被用于制备高性能材料。
BCP化学基团的研究始于20世纪60年代,当时,人们意识到通过改变共聚物分子链的结构,可以产生具有不同性质的材料,这种方法得到了广泛应用。
BCP化学基团的独特之处在于,它的结构可以通过控制单体的选择和/或共聚物的合成条件来调节,从而实现对材料性能的精确控制。
BCP化学基团在材料科学中有广泛的应用,比如在纳米技术、光电子学和生物医学等领域。
在纳米技术领域,BCP化学基团被用于制备纳米颗粒、纳米线和纳米结构,这些纳米材料在电子设备、传感器和药物传递等方面有很大的应用潜力。
在光电子学领域,BCP化学基团可以用于制备有机太阳能电池和有机发光二极管等器件,这些器件具有高效率和低成本的特点。
在生物医学领域,BCP化学基团可以用于制备药物输送系统和组织工程等,这些应用有望在治疗癌症和组织修复
方面做出贡献。
总之,BCP化学基团的研究和应用具有重要意义,它为我们提供了一种可控性强、多功能的材料设计方法,为各个领域的发展带来了巨大的机遇和挑战。
bcp蒸镀z因子

BCP(Block Copolymer)蒸镀是一种常用的材料蒸镀方法,在此过程中,薄膜沉积速率(或蒸镀速率)和材料的Z因子密切相关。
Z因子是衡量材料的蒸镀速率和沉积行为的参数。
它表示蒸发物质相对于基底材料的凝结速率以及薄膜的表面扩散行为。
具体来说,Z因子是沉积物分子速率和蒸发源分子速率之间的比率。
对于BCP蒸镀过程,Z因子可以受到多种因素的影响,包括蒸发源材料的物理性质、基底材料的特性,以及蒸发源与基底之间的相互作用等。
当Z因子小于1时,沉积速率较基底材料快,这可能导致形成较大颗粒的表面粗糙膜;当Z因子大于1时,沉积速率较基底材料慢,这可能导致形成较小颗粒的光滑膜。
需要注意的是,具体的BCP蒸镀过程中的Z因子取决于所使用的材料和实验条件。
因此,在实际应用中,通过实验和优化参数来控制和调节BCP蒸镀的Z因子,以实现所需沉积速率和薄膜品质的要求。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Technology Review#2002-4Business Continuity PlanningPadmavathy RameshJuly 2002© Copyright 2002 Tata Consultancy Services. All rights reserved.No part of this document may be reproduced or distributed in any form by any means without prior written authorization of Tata Consultancy Services.Contents1 INTRODUCTION (1)1.1 C ONTINUITY P LANNING (1)1.2 N EED (1)2 ELEMENTS OF BUSINESS CONTINUITY PLANNI NG (1)2.1 I NITIATION (1)2.2 R ISK A SSESSMENT (2)2.3 B USINESS I MPACT A NALYSIS (3)2.4 S TRATEGIES (5)2.4.1 Prevention (6)2.4.2 Response (7)2.4.3 Resumption (9)2.4.4 Recovery (10)2.4.5 Restoration (10)2.5 G OALS D EFINITION (11)3 TECHNICAL REQUIREMENTS (11)3.1 A VAILABLE O PTIONS (11)3.1.1 Storage and Server Solutions (11)3.1.2 Network Solutions (16)3.2 A C OMPARISON (17)3.3 I MPLEMENTATION (18)4 SOFTWARE DEVELOPMENT LIFE CYCLE APPRO ACH TO BCP ACTIVITIES215 DEVELOPING A PLAN (22)5.1 T YPICAL C ONTENTS (22)5.1.1 Essential Items (22)5.1.2 Preventive Safeguards (23)5.1.3 Emergency Response (23)5.1.4 Resumption (24)5.1.5 Recovery (24)5.1.6 Restoration (25)5.2 T ESTING (25)5.3 M AINTENANCE (27)6 CONCLUSION (27)APPENDIX A: SAMPLE BUSINESS IMPACT ANALY SIS QUESTIONNAIRE (29)ACKNOWLEDGEMENTS (32)REFEREN CES (32)List of IllustrationsF IGURE 1: A SYMMETRIC C LUSTER (13)F IGURE 2: S YMMETRIC C LUSTER (14)F IGURE 3: N ETWORK A TTACHED S TORAGE (NAS) (15)F IGURE 4: S TORAGE A REA N ETWORK (SAN) (16)F IGURE 5: V IRTUAL P RIVATE N ETWORK (VPN) (17)F IGURE 6: A VAILABILITY C OMPARISON (18)F IGURE 7: B USINESS C ONTINUITY P LANNING - A S UMMARY (28)1 Introduction1.1 Continuity PlanningBusiness entities today exist in a highly competitive world. They are constantly innovating to meet their business objectives of providing essential and unique services to their customers. Technology advances have enabled them to achieve their varied strategies. And yet, the threats of disaster, on account of business interruption, are not extinct – in fact, they have also evolved along with the technology. Business interruption does happen – but what is of significance is, how much of the consequences of such interruptions can the business afford? Business Continuity Planning is the act of proactively working out a way to prevent, if possible, and manage the consequences ofa disaster, limiting it to the extent that a business can afford.1.2 NeedThere are various threats and vulnerabilities to which business today is exposed. They could be:§ catastrophic events such as floods, earthquakes, or acts of terrorism§ accidents or sabotage§ outages due to an application error, hardware or network failuresSome of them come unwarned. Most of them never happen. The key is to be prepared and be able to respond to the event when it does happen, so that the organization survives; its losses are minimized; it remains viable and it can be “business as usual”, even before the customers feel the effects of the downtime. An effective Business Continuity Plan serves to secure businesses against financial disasters. The bonus — customer satisfaction, enhanced corporate image and no dip in the market share.2 Elements of Business Continuity Planning2.1 InitiationThe first step is to obtain the commitment of the management and all the stakeholders towards the plan. They have to set down the objectives of the plan, its scope and the policies. An example of a decision on scope would be whether the target is the entire organization or just some divisions, or whether it is only the data processing, or all the organization’s services. Management provides sponsorship in terms of finance and manpower. They need to weigh potential business losses versus the annual cost of creating and maintaining the Business Continuity Planning. For this, they will have to find answers to questions such as how much it would cost or how much would be considered adequate.Broadly, the objective of the Business Continuity Planning (BCP) for a business can only be – to identify and reduce risk exposures and to proactively manage the contingency. The specific objectives that a BCP can set will be described in the subsequent sections.The final outcome of the BCP exercise is:§ a set of measures to prevent disasters§ a BCP operational team, trained to handle the situation§ a plan that provides a roadmap when disaster strikes – a plan that is sufficient and complete, detailing what needs to be done with each element that falls within the plan’s scope.The discussions that follow are mainly in the context of IT services provided by an organization. They do not deal with the safety management of the firm’s personnel, in case of a disaster.2.2 Risk AssessmentRisk assessment is the exercise of identifying and analyzing the potential vulnerabilities and threats. The sources of risks could be:§ community-wide hazardous events§ accidents or sabotage causing extreme material disaster§ security threats, network and communication failures§ disastrous application errorsEach of these areas should be looked at in the light of the business and the exact possible source located. For each source identified:§ the magnitude of the risk and§ the probability of its occurrencemust be evaluated to judge the extent of risk exposure. Risk exposure is the easiest way to know how much attention needs to be paid to a source of risk.Planning is done for both — prevention and control. Accidents and sabotage can be prevented using measures of physical security and personnel practices. Vulnerability assessment and reviews of existing security measures can throw up areas where access control, software and data security, or backups are required. Application errors can be prevented by effective reviews and testing during the software releases.If needed, the expertise of external agencies can easily be called upon to analyze, devise and put in place some of the preventive measures.The tougher part is to come up with activities for controlling the effects of disaster, and this necessitates a detailed business impact analysis.The end result of the Risk Assessment should be a risk-benefit analysis statement giving the exact threats, and the estimated exposure together with the contingency andmitigation actions required, and also the benefits arising out of covering the risk. This statement should also delineate any assumptions or constraints that exist.Often, this exercise will show that the complete physical disaster has a remote probability of occurring and application crashes, or security break-ins are very frequent. However, only having a procedure for handling catastrophic disasters without a plan for application failure or vice versa is not advisable. The solution is to prepare a BCP for the worst-case, i.e., complete destruction of the site providing the services. Any other outage can then be easily tackled using a sub-set of the main plan.2.3 Business Impact AnalysisBusiness Impact Analysis (BIA) is essentially the process of identifying the critical business functions and the losses and effects if these functions are not available.It involves talking to the key people operating the business functions in order to assess: A. Impact§ how vital the function is to the overall business strategy§ how long the function could be inoperative without any impact or losses§ how the rest of the business would be affected by its outage – the operational impact§ what the revenue lost due to its outage would be – the financial impact§ whether its outage would result in violation of Service Level Agreements (SLAs), regulatory requirements, any contractual liabilities, and penalty, or whether it would create legal issues – the regulatory and legal impact§ whether it would affect relationships with customers – loss of customer confidence§ whether it would affect the market rates – decline in market rates§ whether it would affect the industry ranking – loss of competitive edge§ whether it could result in losing future sales – loss of opportunities§ what the maximum/acceptable/permissible outage would beB. Requirements for recovery§ what the resources and records required would be to continue the function§ what the bare minimum resource requirements would be§ which of the resources would be from external sources§ what other business functions it would be dependent upon, and to what extent§ what other business functions would depend on it and to what extent§ upon which external business/suppliers/vendors it would be dependent, and to what extent§ which SLAs and measures for continuity these external businesses/suppliers/vendors would follow§ what the backup needs would be§ what the time and effort required to recreate up-to-date data from the backups would be§ what precautions or verifications would need to be taken or done for recovering without a test environmentBased on these discussions, it will be possible to classify the business functions as:a) Critical functions – If these business functions are interrupted or unavailable forsome time, it can completely jeopardize the business and cause heavy damages to the business.b) Essential functions– Those functions, whose loss would seriously affect theorganization’s ability to function for long.c) Necessary functions– The organization can continue functioning; however,absence of these functions would limit their effectiveness, to a great extent.d) Desirable functions– These functions would be beneficial; however, theirabsence would not affect the capability of the organization.Based on their recovery needs, organizations can come up with standard recovery time frames for the above classifications. For example, Critical functions: < 1 day, Essential functions: 2-4 days, Necessary functions: 5-7 days and Desirable functions: > 10 days.This impact analysis helps to rank the business functions and come up with an order in which they should be brought up. In other words, it defines recovery priorities.BIA helps define the recovery objectives. In the course of this study, it might be possible to discover that when resuming operations after a disaster, it is enough to recover to a limited capacity, i.e., recover to the extent of handling 40 percent of the usual workload within 24 hours.It will also be possible to define in detail the resource requirements for making a business function operational after disaster or interruption. This will include infrastructure, manpower, documents, records, machines, phones, fax machines, whatever is needed – with complete specifications. Having adequate details is important, since in the event of disasters, there is bound to be some amount of panic and it may not be possible to come down to such details.The team and managers actually involved in the day-to-day operations of the business functions would be the best people to talk to during the impact analysis, as they would certainly know the details of the functions. Moreover, they can perform a brainstorming exercise on how an outage of their function would affect the revenue objectives, market position and customer expectations, or how they could restore normal operations, or what resources they would require to operate in normal mode.Interdependence between various functions (internal and external) is crucial information obtained as part of the analysis. While consolidating the information gathered from the questionnaires/discussions and ranking the functions to derive the recovery priority, one must not overlook functions, which by themselves are low priority, however, have some critical functions depending on them. By virtue of this dependence, they also become important.Cost considerations are not to be ignored during this exercise. Things to be kept in mind are:§ Revenue losses and opportunity losses will be directly proportional to the time taken for recovery§ Cost of a recovery strategy will be inversely proportional to the time permitted for recovery§ Cost of the possible recovery strategy must be compared with the actual loss due to the outage before accepting the strategy. If the solution proposed costs much more than the projected losses, it will not be possible to justify the investment to the management.When presenting the findings of the business impact analysis, the results must also be expressed in business terms. Quantifying the impact, possibly in terms of money, will catch the attention of the management. Stating the impact in terms of time will help in proposing concrete recovery goals. Stating the requirements in technical terms will help planning the recovery strategies. Ultimately, the business impact analysis must justify the continuity plan and aid selection of the best possible recovery strategy within the budget.2.4 StrategiesBusiness Continuity Planning should include strategies on:§ Prevention§ Response§ Resumption§ Recovery§ RestorationPrevention aims at lessening the chances of the disaster happening.Response is the reaction when the event occurs. It must stem further damage, assess the extent of damage, salvage the business entity’s reputation by providing appropriate communication to the external world and indicate a possible recovery timeframe.Resumption involves resuming only the time-sensitive business processes, either immediately after the interruption or after the declared Mean Time Between Failures (MTBF). All operations are not fully recovered.Recovery addresses the startup of less time-sensitive processes. The time duration of this naturally depends on the time taken for resumption of the time-sensitive functions. It could involve starting up these services at an alternate location.Restoration is the process of repairing and restoring the primary site. At the end of this, the business operations are resumed in totality from the original site or a completely new site, in case of a catastrophic disaster.2.4.1 PreventionStrategies for prevention would include both deterrent and preventive controls.§ Deterrent controls reduce the likelihood of the threats.§ Preventive controls safeguard the vulnerable areas to ward off any threat that occurs and reduce its impact.Having these measures in place is always more cost-effective than attempting recovery after the interruption. The aim should be to cover as many as possible of the risks identified, using deterrent and preventive controls, so that the recovery strategy has to work only on the residual risks.A wide variety of such controls exist. Some of the common ones are described below.(a) Security at the premises — It is a deterrent control and exists in the form of barriersto protect the location and prevent accidental or unauthorized entry. It could also involve manned or technology-driven surveillance at the location.(b) Personnel procedures — Areas housing the critical resources could be restrictedzones w here only authorized people are allowed to enter after some means of identification are provided. The means of identification can be varied depending on the technology used for the identification process.(c) Infrastructure-related — This includes having an appropriate sized UPS, backuppower, air conditioning, smoke/fire detectors, fire extinguishers, waterproofing, fire resistant containers for vital records and backups and also monitoring weather forecasts.(d) Software controls — The most common of these are authentication, access control,anti-virus, encryption, firewall, and intrusion detection systems.(e) Storage and recovery related — Frequent backups. The various mechanisms will bediscussed later in this paper. Offsite storage of vital records and backups lat er contribute to the resumption and recovery process.The above list distinctly highlights one aspect: most of the safeguards are closely related to the security policy and practices in an organization.Business firms will want to ensure the availability and safety of their assets (which includes information). Their security policy addresses these objectives and provides guidelines for usage and management of their assets. Armed with knowledge of the firm’s assets, their layout and the risk assessment results, the firm can come up with the necessary controls needed to implement the security policy. These controls or security practices must be reviewed from time-to-time and also be tested to see whether they are penetrable by all categories of people, i.e., by people having valid access, by having complete knowledge of the systems or by a complete outsider. Any of them can misuse the access. The reviews will help enrich or strengthen the measures.Having a security policy, putting preventive safeguards in place, monitoring the system for intrusions and ensuring action against those who violate it, is itself a deterrent control. Planning for prevention is an exercise that must be done carefully. It has to ensure that the mechanisms used are neither very restrictive, nor would they constitute a bottleneck, nor cause an availability problem, nor allow undesirable/easy access and usage.2.4.2 ResponseThe first reaction to an interruption would be to inform all the relevant people about the interruption. If it is an impending interruption about which there is a prior warning, then this notification can be done in advance. Timely notification is important, since it may provide an opportunity to stem any further damage. In a situation where there is adequate time to perform a shutdown, a switchover or an evacuation, it may even completely prevent damage. This, however, requires the presence of diagnostic or detective controls. Such controls either continuously scan themselves for a symptom of interruption (network, servers) or collect such information from external sources (natural calamities).The exact notification procedure must be laid down. It involves clearly documenting who is to be notified, how, by whom, and also the escalation mechanism.A notification call tree within the BCP team is set up. Here, the initial notification is sent to a set of people, who in turn, inform the next set of people, and so on. People belonging to this call tree have different roles. The type of information and amount of detail provided a s a part of the notification depends on the role of the person. The following groups would be involved:§ Management — would need to be informed of the status. It has the powers to authorize the emergency response and further actions. The management will also deal with the press, public, customers and shareholders.§ Damage Assessment Team — would assess the damage and rate the severity of the interruption.§ Technical Team — would serve as the key decision-makers for further activities of the BCP.§ Operations Team — would execute the actual operations of the BCP.It is also important to state an alternative for each contact. In case the primary person is not available or traceable, the backup person is to be notified. Notification can be done using various tools: pager, SMS, phone, and email. The team is equipped appropriately.The Damage Assessment Team is among the earliest (along with the management) to be notified of the event. They would be required at the site at the earliest to evaluate the extent of the damage inflicted. In case the site itself has been subject to damage, then they should start their work as soon as an entry is allowed. (Of course, if the calamity is as great as on September 11th 2001, then it is obvious that it is a disaster of the great est severity.)The assessment should be done against a plan that is closely related to the business continuity priorities. This means that they should be aware of the area in the site and processes that are crucial to the business. This would help them prioritize their examination and also focus adequately on the critical areas. This team needs to look at:§ the cause of disruption§ whether there is scope to stem additional damage§ infrastructure and equipment damage§ services affected§ vital records damaged§ what can be salvaged§ what needs repair, restoration and replacement§ requirements for insurance claims, if applicableArmed with this input (provided by the Damage Assessment Team) on the severity of damage to facilities and the extent to which the business is inoperable, the Technical Team can work ahead. Some of the questions faced by them are:§ Is it a disaster? Of what degree?§ When will the impact be felt?§ What is the extent of time to repair/resume/restore?§ Where does one begin?The BCP must have a set of predefined parameters based on the Business Impact Analysis and their continuity goals to evaluate the information available on the damage.These parameters should differentiate between an interruption and a disaster, and also rate the severity of the event. What the Technical Team uses here is a decision support mechanism based on these parameters before they declare a disaster (of any appropriate scale).While the Damage Assessment Team and Technical Team are working, the rest of the BCP team is placed on alert for a possible activation of the continuity plan. The type and extent of the disaster declared would indicate which portions of the BCP need to be implemented. Accordingly, the BCP team is notified and resumption activities are started.An optional step in the emergency response (the first action, in fact) is to move to safety all personnel on the premises and alert the police, fire service and hospitals. This is a step required only if the interruption is of the nature of an accident, act of sabotage or natural calamity.2.4.3 ResumptionThe focus shifts to the command centre once the BCP has been activated. This is a location different from the normal business facility. It is from here that the resumption, and subsequently, the recovery activities, are coordinated. The centre will have adequate communication facilities, PCs, printers, fax machines and office equipment to support the activities of the team.The first decision to be taken is – whether the critical operations can be resumed at the normal business site or at an alternate site. In situations when access to the primary site is denied or the site is damaged beyond use, the operations could move to an alternate site.Alternate sites can be of the following kinds:(a) Cold Site– A facility that is environmentally conditioned, but devoid of anyequipment. It is ready for all the equipment to move in, i.e., it has telephone points, power supply, and UPS facility, among others. It takes a little time to make this site operational. Using a cold site implies that the business entity has contracts with the providers of all the necessary equipment. These contracts are specifically for a business resumption scenario and therefore will have clauses on the time within which the setup will be completed.(b) Hot Site— It is an alternate facility having workspace for the personnel, fullyequipped with all resources and stand-by computer facilities needed to recover and support critical business functions after a disaster. It is a fully equipped site where the BCP team moves in to start work without further delay.(c) Warm site — It is a partially equipped hot site and the data is not too old.(d) Mobile site — It is a portable site with a smaller configuration. It can be positionednear the primary site, thus saving travel for the key staff.(e) Mirrored Site – It is identical in all aspects to the primary site, right down to theinformation availability. It is equivalent to having a redundant site in normal times and is naturally the most expensive option.At the alternate site (or primary site, if still usable), the work environment is restored. Communication, networks, and workstations are set up. Contact with the external world can now be resumed. It is possible that an organization might choose to function in the manual mode until the critical IT services can resume. If the recovery alternative (described in a later section) permits, the critical functions can also be resumed in the automated mode very quickly.2.4.4 RecoveryAt the site of recovery (either primary or alternative), the operating system is restored on the stand-by system. Necessary applications are restored in the order of their criticality. When the applications to serve the critical functions are restored, data restoration from backup tapes or media obtained from the offsite storage can be initiated.Data must also be synchronized i.e., to rebuild data accurately to a predetermined point of time before the interruption. The point to which the restoration is done depends on the requirements of the c ritical services. Business data comes from different sources, each of which must be reconstructed to reach the desired state of data integrity. The synchronized data must be reviewed and validated. This is mandatory because under such disastrous circumstances, it is possible that there is no test environment available and that applications will resume directly in the production environment. It is therefore necessary to have a clear method, strategy or checklist to perform this validation exercise.Once the data has reached a reliable state, transactions that have been accumulating since the disaster can be processed and all the critical functions can then resume. Gradually, other services of the business can also begin functioning.Some of the steps described above are not required for certain recovery strategies. The mechanism of the recovery strategy itself is the reason for it. A description of the technical alternatives is covered along with the recovery goals in subsequent sections. 2.4.5 RestorationEven while the recovery team is supporting operations from the alternate site, restoration of the primary site for full functionality is initiated. In case the original building/work area or primary facility is beyond repair, then a new site is restored. It is possible that the team members of the recovery and restoration team are common.It must be ensured that the site has the necessary infrastructure, equipment, hardware, software and communication facilities. It is necessary to test whether the site is capable of handling full operations. The operational data must then be uploaded at this site and the emergency site gradually dismantled.Planning for all activities described above will include defining a time span within which they must be executed. This time duration is defined keeping in mind the recovery goalsof the organization. The BCP team must remember that if at any point of time, they exceed this planned time, then the contingency must be escalated to the command centre at once, and immediate solutions must be worked out, or else they might miss their recovery targets.2.5 Goals DefinitionAt the end of the phase of Risk Assessment and Business Impact Analysis, what stand out are the essentials to keep the business moving. Classification of the business services is available in terms of services that are:§ critical§ essential§ necessary§ desirableThis makes the Continuity Priorities clear. Goals can now be quantified in terms of:§ Recovery Time Objective (RTO) – maximum permissible outage time§ Recovery Point Objective (RPO) – the furthest point to which data loss is permitted§ Performance degradation on account of any measures introduced as a part of BCP § Risks involved in the case of any measures introduced as a part of BCP§ Cost of implementing the BCPThese will drive the operational details of the BCP.3 Technical Requirements3.1 Available Options3.1.1 Storage and Server Solutionsa) Conventional Backup – is the method of backing up various servers and shippingthe tapes to a safe alternate location.b) RAID– is an effective solution for redundancy. Based on the needs, RAID of anappropriate level can be chosen.c) Remote Journaling– is the process of collecting the writes to the logs andjournals and transmitting them to a remote site. It can be done in real time, i.e., by simultaneously transmitting the writes, or can be achieved by extracting the writes and periodically transmitting them. It does not update the database but only sends the logs so that recovery can be achieved to the point of last transmission. This can。
