pix525防火墙配置
防火墙CISCO-PIX525配置手册

防火墙CISCO-PIX525的配置基础知识现在,我们通过一个相对简单的示例说明如何使用Cisco PIX对企业内部网络进行管理。
网络拓扑图如附图所示。
Cisco PIX安装2个网络接口,一个连接外部网段,另一个连接内部网段,在外部网段上运行的主要是DNS 服务器,在内部网段上运行的有WWW服务器和电子邮件服务器,通过Cisco PIX,我们希望达到的效果是:对内部网络的所有机器进行保护,WWW服务器对外只开放80端口,电子邮件服务器对外只开放25端口。
具体*作步骤如下。
2.获得最新PIX软件---- 从Cisco公司的WWW或FTP站点上,我们可以获得PIX的最新软件,主要包括如下内容。
pix44n.exe――PIX防火墙的软件映像文件。
pfss44n.exe――PIX Firewall Syslog Server服务器软件,能够提供一个Windows NT服务,用来记录PIX的运行日志。
pfm432b.exe――图形化的PIX管理软件。
rawrite.exe――用于生成PIX的启动软盘。
3.配置网络路由---- 在使用防火墙的内部网段上,需要将每台计算机的缺省网关指向防火墙,比如防火墙内部IP地址为10.0.0.250,则内部网段上的每台计算机的缺省网关都要设置为10.0.0.250。
具体设置在“控制面板”*“网络”*“TCP/IP协议”中进行。
4.配置PIX---- 在配置PIX之前,应该对网络进行详细的规划和设计,搜集需要的网络配置信息。
要获得的信息如下。
---- (1)每个PIX网络接口的IP地址。
(2)如果要进行NAT,则要提供一个IP地址池供NAT使用。
NAT是网络地址转换技术,它可以将使用保留地址的内部网段上的机器映射到一个合*的IP地址上以便进行Internet访问(3)外部网段的路由器地址。
---- 进入PIX配置界面的方*是:连接好超级终端,打开电源,在出现启动信息和出现提示符pixfirewall>后输入“enable”,并输入密码,进入特权模式;当提示符变为pixfirewall#>后,输入“configure terminal”,再进入配置界面。
PIX525基本应用第10单元

PIX的工作模式
PIX防火墙提供4种管理访问模式: 非特权模式。 PIX防火墙开机自检后,就是处于 这种模式。系统显示为pixfirewall> 特权模式。 输入enable进入特权模式,可以改变 当前配置。显示为pixfirewall# 配置模式。 输入configure terminal进入此模式,绝 大部分的系统配置都在这里进行。显示为 pixfirewall(config)# 监视模式。 PIX防火墙在开机或重启过程中,按 住Escape键或发送一个"Break"字符,进入监视模 式。这里可以更新操作系统映象和口令恢复。显 示为monitor>
PIX525介绍
PIX525介绍
基本参数:
基本规格 并发连接数 VPN支持 安全性 安全过滤带宽(MB) 用户数限制 入侵检测 其它 控制端口 RS-232 100 无用户数限制 DoS、IDS 280000 支持
电气规格 电源电压(V) 电源功率(W) 220 135
PIX525介绍
图片展示:
主要特性: 基于标准的虚拟专网 - 使管理员可以降低通 过Internet或其它公共IP网络将移动用户和 远程站点与企业网络相连的成本。 自适应安全算法 - 为所有的TCP/IP对话提 供静态安全性,以保护敏感的保密资源。 静态故障切换/热备用 - 提供高可用性,使 网络可靠性最大。 网络地址转换(NAT)-- 节省宝贵的IP地址; 扩展网络地址空间;隐藏IP地址,使之不被 外部得到。
总结
目前我们已经掌握了设置PIX的六大基本命 令,通过这六个命令我们已经可以让PIX为 我们的网络服务了。不过,要有效的利用 网络,还需要一些高级命令了。
No8.2 pix防火墙配置实验

寒水教研
控制对pix接口的icmp流量
PIX(config)#icmp deny 0 0 outside PIX(config)#icmp deny 0 0 inside
寒水教研
试验二、inside到outside的访问
Firewall VPC(out)
PC(In)
10.1.1.101
E0 10.1.1.1
E1 20.1.1.1
Dns/Web/Ftp 20.1.1.101
需求: 需求: 从内部的10.1.1.0要telnet到外部的20.1.1.101主机。 如果PIX 不做设置,则从LAN 到WAN 的流量是无法出去的。 步骤: 步骤: PIX的基本配置(配ip,配接口级别,配route) NAT转换(由inside到outside) 测试
pix防火墙配置实验 No8.2 pix防火墙配置实验
寒水教研
实验大纲
1 2 3 4 5 6
基本设置 inside到outside的访问 Nat与static的实验 ICMP 控制 保存基本配置到tftp服务器 telnet和ssh到PIX防火墙
PIX525透明模式详细配置过程

PIX525透明模式详细配置过程编者按:为了让网络管理员对技术知识有个全面的认识,IT168网络通信频道将与ChinaUnix联手,选登来自ChinaUnix上优秀的帖子和博客文章,供大家学习、阅读。
这是一篇关于如何配置PIX525防火墙为透明模式的帖子,作者从实际操作入手,逐步阐述。
文章简单易懂,非常适合正在学习中的网管朋友们。
如何连接电脑我就不多说了,网上到处都是。
但好像要注意一点,先吧超级终端打开再给防火墙加电,不然超级终端上什么都看不到。
下面就是正是配置了:由于一般的PIX系列的防火墙出场时候预装的IOS是6.X的版本而只有7.0以上才支持透明模式.所以第一步是升级IOS准备工作:找一台和防火墙在一个交换机机上的计算机安装ciscotftp软件.去上面就有.很简单汉化版.然后去cisco网站上下载一个7.0的bin文件(我下载的是pix701.bin)放到tftp服务器的根目录下正式开始:防火墙通电,按ESC进入monitor> 状态下。
monitor> address 192.1.1.1 --设置防火墙IPaddress 192.1.1.1monitor> server 192.1.1.2 --设置tftp服务器的IPserver 192.1.1.2monitor> ping 192.1.1.2 --检测一下是否能ping通Sending 5, 100-byte 0x7970 ICMP Echoes to 10.32.2.78, timeout is 4 seconds:!!!!!Success rate is 100 percent (5/5)monitor> file pix701.bin --声明你下载的那个bin文件的全称file pix704.binmonitor> tftp --开始灌入tftp pix704.bin@192.168.1.80...........................耐心等待.一直到出现非特权模式的那个">"符号.下面要吧bin文件考到flash里面去,以后启动的时候才能正常使用pixfirewall> enPassword:pixfirewall# con tpixfirewall(config)# interfaceethernet1 --进入端口模式pixfirewall(config-if)# ip address 192.1.11255.255.255.0 --配置e1口的IPpixfirewall(config-if)# nameifinside --配置e1口为防火墙的inside口INFO: Security level for "inside" set to 100 by default.pixfirewall(config-if)# noshutdown --激活inside口pixfirewall(config-if)# ping192.1.1.2 --测试一下Sending 5, 100-byte ICMP Echos to 192.1.1.2, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 mspixfirewall(config-if)#exit --退出端口模式pixfirewall(config)# copy tftpflash: --copybin 文件Address or name of remote host []?192.1.1.2 --tftp服务器IPSource filename []?pix701.bin --文件名Destination filename [pix701.bin]?pix701.bin --确认Accessingtftp://192.1.1.2/pix701.bin...!! --开始copy 耐心等待Writing file flash:pix701.bin...!!!!!!!!!!!!!5124096 bytes copied in 82.80 secs (62488 bytes/sec)pixfirewall(config)#reload --升级完成.重启!!!!!!!ps.第一次启动时间会稍长不要着急下面才是配置.也很简单了,和刚才配置差不多配置outside口和inside口并激活,只是注意不要配置IP.这可是透明模式.谁见过一根网线两端还有IP的?pixfirewall> enPassword:pixfirewall# con tpixfirewall(config)# interface ethernet0pixfirewall(config-if)# nameif outsideINFO: Security level for "outside" set to 0 by default.pixfirewall(config-if)# no shutdownpixfirewall(config-if)# exitpixfirewall(config)# interface ethernet1pixfirewall(config-if)# nameif insideINFO: Security level for "inside" set to 100 by default.pixfirewall(config-if)# no shutdownpixfirewall(config-if)# exit记住哦~~~~~~~~这里可是最重要的了,即下面的五句话:pixfirewall(config)# firewalltransparent --设置防火墙为透明模式pixfirewall(config)# access-list out-list extended permit icmp any any --设置允许通过所有的协议pixfirewall(config)# access-list out-list extended permit ip any any --设置允许通过所有的IPpixfirewall(config)# access-group out-list in interfaceoutside --把刚才的访问列表绑在outside口pixfirewall(config)# access-group out-list out interfaceoutside --把刚才的访问列表绑在outside口pixfirewall(config)# ip address 192.1.1.1255.255.255.0 --设置一个以后配置防火墙的IP。
思科防火墙设置

增加一台服务器具体要求。
新增一台服务器地址:10.165.127.15/255.255.255.128。
需要nat 转换成公网地址16.152.91.223 映射出去,并对外开通这台服务器的80端口。
在对外pix525上面增加如下:access-list acl_out permit tcp any host 16.52.91.223 eq www //开放外网对新服务器80端口static (inside,outside) 16.152.91.223 10.165.127.15 netmask 255.255.255.255 0 0 ////外高桥新服务器地址转换16.152.91.223可是为什么转换后,不能访问16.52.91.223的网页,但确可以ping通16.52.91.223,但是访问10.165.127.15的主页是正常的??具体配置如下:pix-525> enablePassword: *****pix-525# sh run: Saved:PIX Version 6.3(5)interface ethernet0 100fullinterface ethernet1 100fullnameif ethernet0 outside security0nameif ethernet1 inside security100enable password FVHQD7n.FuCW78fS level 7 encryptedenable password 2KFQnbNIdI.2KYOU encryptedpasswd 2KFQnbNIdI.2KYOU encryptedhostname wgqpix-525fixup protocol dns maximum-length 512fixup protocol ftp 21fixup protocol h323 h225 1720fixup protocol h323 ras 1718-1719fixup protocol http 80fixup protocol rsh 514fixup protocol rtsp 554fixup protocol sip 5060fixup protocol sip udp 5060fixup protocol skinny 2000fixup protocol smtp 25fixup protocol sqlnet 1521fixup protocol tftp 69namesaccess-list acl_out permit tcp any host 16.152.91.221 eq wwwaccess-list acl_out permit icmp any anyaccess-list acl_out permit tcp any host 16.152.91.220 eq httpsaccess-list acl_out permit tcp any host 16.152.91.223 eq wwwaccess-list outbound permit icmp any anyaccess-list outbound permit ip any anypager lines 24mtu outside 1500mtu inside 1500ip address outside 16.152.91.222 255.255.255.128ip address inside 10.165.127.254 255.255.255.252ip audit info action alarmip audit attack action alarmno failoverfailover timeout 0:00:00failover poll 15no failover ip address outsideno failover ip address insideno pdm history enablearp timeout 14400static (inside,outside) 16.152.91.221 10.165.127.11 netmask 255.255.255.255 0 0 static (inside,outside) 16.152.91.220 10.165.127.23 netmask 255.255.255.255 0 0 static (inside,outside) 16.152.91.223 10.165.127.15 netmask 255.255.255.255 0 0 access-group acl_out in interface outsideaccess-group outbound in interface insideroute outside 0.0.0.0 0.0.0.0 16.152.91.129 1route inside 10.165.0.0 255.255.0.0 10.165.127.253 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h225 1:00:00 timeout h323 0:05:00 mgcp 0:05:00 sip 0:30:00 sip_media 0:02:00timeout sip-disconnect 0:02:00 sip-invite 0:03:00timeout uauth 0:05:00 absoluteaaa-server TACACS+ protocol tacacs+aaa-server TACACS+ max-failed-attempts 3aaa-server TACACS+ deadtime 10aaa-server RADIUS protocol radiusaaa-server RADIUS max-failed-attempts 3aaa-server RADIUS deadtime 10aaa-server LOCAL protocol localhttp server enableno snmp-server locationno snmp-server contactsnmp-server community publicno snmp-server enable trapsfloodguard enabletelnet 10.165.6.225 255.255.255.255 insidetelnet 10.165.127.12 255.255.255.255 insidetelnet 10.165.127.250 255.255.255.255 insidetelnet 10.165.6.15 255.255.255.255 insidetelnet 10.165.6.16 255.255.255.255 insidetelnet timeout 5ssh timeout 5console timeout 0username admin password iuQeTKNaNbruxBKd encrypted privilege 2terminal width 80Cryptochecksum:b2e1195d144f48f01fe66606cd31d0f2: endwgqpix-525#最佳答案( 回答者: xintao800 )PIX防火墙提供4种管理访问模式:²非特权模式。
防火墙基本配置

PIX525(config)#telnet 192.168.1.1 255.255.255.0 inside
PIX525(config)#telnet 222.20.16.1 255.255.255.0 outside
测试telnet
在[开始]->[运行]
telnet 192.168.1.1
如何开始Cisco Firewall Pix呢?我想应该是跟Cisco 路由器使用差不多吧,于是用配置线从电脑的COM2连到PIX 525的console口,进入PIX操作系统采用windows系统里的“超级终端”,通讯参数设置为默然。初始使用有一个初始化过程,主要设置:Date(日期)、time(时间)、hostname(主机名称)、inside ip address(内部网卡IP地址)、domain(主域)等,如果以上设置正确,就能保存以上设置,也就建立了一个初始化设置了。
2、 激活以太端口
必须用enable进入,然后进入configure模式
PIX525>enable
Password:
PIX525#config t
PIX525(config)#interface ethernet0 auto
PIX525(config)#interface ethernet1 auto
PIX525(config)#access-list 100 permit ip any host 222.20.16.254 eq www
PIX525(config)#access-list 100 deny ip any any
PIX525(config)#access-group 100 in interface outside
PIX防火墙基本配置命令和配置实例

PIX防火墙基本配置命令和配置实例PIX防火墙基本配置命令和配置实例1. PIX 的配置命令(1) 配置防火墙接口的名字,并指定安全级别(nameif)Pix525(config)#nameif ethernet0 outside security0Pix525(config)#nameif ethernet1 inside security100Pix525(config)#nameif dmz security50提示:在缺省配置中,以太网0被命名为外部接口(outside),安全级别是0;以太网1被命名为内部接口(inside),安全级别是100.安全级别取值范围为1~99,数字越大安全级别越高。
若添加新的接口,语句可以这样写:Pix525(config)#nameif pix/intf3 security40 (安全级别任取)(2) 配置以太口参数(interface)Pix525(config)#interface ethernet0 auto(auto选项表明系统自适应网卡类型)Pix525(config)#interface ethernet1 100full(100full选项表示100Mbit/s以太网全双工通信)Pix525(config)#interface ethernet1 100full shutdown(shutdown选项表示关闭这个接口,若启用接口去掉shutdown)(3) 配置内外网卡的IP地址(ip address)Pix525(config)#ip address outside 61.144.51.42 255.255.255.248Pix525(config)#ip address inside 192.168.0.1 255.255.255.0很明显,Pix525防火墙在外网的ip地址是61.144.51.42,内网ip地址是192.168.0.1 (4) 指定外部地址范围(global)Global命令的配置语法:global (if_name) nat_id ip_address - ip_address [netmark global_mask]global命令把内网的IP地址翻译成外网的IP地址或一段地址范围。
Quidway S3528+Cisco PIX525配置
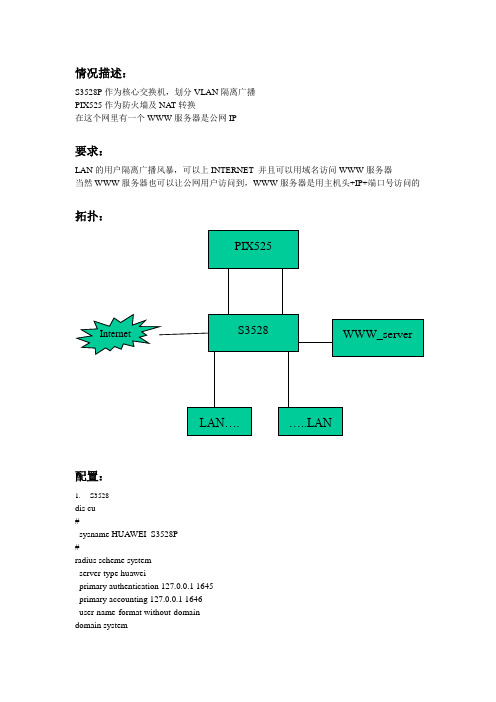
情况描述:S3528P作为核心交换机,划分VLAN隔离广播PIX525作为防火墙及NA T转换在这个网里有一个WWW服务器是公网IP要求:LAN的用户隔离广播风暴,可以上INTERNET 并且可以用域名访问WWW服务器当然WWW服务器也可以让公网用户访问到,WWW服务器是用主机头+IP+端口号访问的拓扑:配置:1.S3528dis cu#sysname HUAWEI_S3528P#radius scheme systemserver-type huaweiprimary authentication 127.0.0.1 1645primary accounting 127.0.0.1 1646user-name-format without-domaindomain systemradius-scheme systemaccess-limit disablestate activeidle-cut disableself-service-url disablemessenger time disabledomain default enable system#local-server nas-ip 127.0.0.1 key huawei #temperature-limit 0 20 80#dhcp server ip-pool cheduinetwork 192.168.70.0 mask 255.255.255.0 gateway-list 192.168.70.1dns-list 202.99.224.8 202.99.224.68#dhcp server ip-pool fuliannetwork 192.168.30.0 mask 255.255.255.0 gateway-list 192.168.30.1dns-list 202.99.224.8 202.99.224.68#dhcp server ip-pool govnetwork 192.168.50.0 mask 255.255.255.0 gateway-list 192.168.50.254dns-list 202.99.224.8 202.99.224.68#dhcp server ip-pool jiweinetwork 192.168.20.0 mask 255.255.255.0 gateway-list 192.168.20.1dns-list 202.99.224.8 202.99.224.68#dhcp server ip-pool shiweinetwork 192.168.10.0 mask 255.255.255.0 gateway-list 192.168.10.1dns-list 202.99.224.8 202.99.224.68#dhcp server ip-pool xinfangnetwork 192.168.40.0 mask 255.255.255.0 gateway-list 192.168.40.1dns-list 202.99.224.8 202.99.224.68#dhcp server ip-pool xxzxnetwork 192.168.60.0 mask 255.255.255.0gateway-list 192.168.60.1dns-list 202.99.224.8 202.99.224.68#acl number 2000rule 0 permit source 192.168.0.0 0.0.255.255#acl number 3000 match-order autorule 0 deny udp source-port eq tftp destination-port eq tftprule 1 deny tcp source-port eq 135 destination-port eq 135rule 2 deny udp source-port eq 135 destination-port eq 135rule 3 deny udp source-port eq netbios-ns destination-port eq netbios-ns rule 4 deny udp source-port eq netbios-dgm destination-port eq netbios-dgm rule 5 deny udp source-port eq netbios-ssn destination-port eq netbios-ssn rule 6 deny tcp source-port eq 139 destination-port eq 139rule 7 deny tcp source-port eq 445 destination-port eq 445rule 8 deny tcp source-port eq 593 destination-port eq 593rule 9 deny tcp source-port eq 4444 destination-port eq 5444rule 11 deny tcp destination-port eq 5554rule 12 deny tcp destination-port eq 9995rule 13 deny tcp destination-port eq 9996rule 14 deny tcp destination-port eq 3127rule 15 deny tcp destination-port eq 1025rule 16 deny tcp destination-port eq 137rule 17 deny tcp destination-port eq 138rule 18 deny tcp destination-port eq 5800rule 19 deny tcp destination-port eq 5900rule 20 deny tcp destination-port eq 8998#vlan 1#vlan 100description to-CNC#vlan 200description to-WAN#vlan 300description to-PIX_NAT#vlan 500description to-shiwei#vlan 600description to-GOV#vlan 700description to-jiwei#vlan 800description to-fulian#vlan 900description to-xinfang#vlan 1000description to-xxzx#vlan 1100description to-chedu#interface Vlan-interface100description to CNCip address 61.138.127.133 255.255.255.128 #interface Vlan-interface200description to WANip address 202.99.241.9 255.255.255.248 #interface Vlan-interface300description to pix_natip address 192.168.0.2 255.255.255.248#interface Vlan-interface500description to shiweiip address 192.168.10.1 255.255.255.0#interface Vlan-interface600description to shiweiip address 192.168.50.254 255.255.255.0 #interface Vlan-interface700description to jiweiip address 192.168.20.1 255.255.255.0#interface Vlan-interface800description to fulianip address 192.168.30.1 255.255.255.0#interface Vlan-interface900description to xinfangip address 192.168.40.1 255.255.255.0#interface Vlan-interface1000description to xxzxip address 192.168.60.1 255.255.255.0#interface Vlan-interface1100description to cheduiip address 192.168.70.1 255.255.255.0#interface Aux0/0#interface Ethernet0/1port access vlan 100packet-filter inbound ip-group 3000 rule 0 packet-filter inbound ip-group 3000 rule 1 packet-filter inbound ip-group 3000 rule 2 packet-filter inbound ip-group 3000 rule 3 packet-filter inbound ip-group 3000 rule 4 packet-filter inbound ip-group 3000 rule 5 packet-filter inbound ip-group 3000 rule 6 packet-filter inbound ip-group 3000 rule 7 packet-filter inbound ip-group 3000 rule 8 packet-filter inbound ip-group 3000 rule 9 packet-filter inbound ip-group 3000 rule 11 packet-filter inbound ip-group 3000 rule 12 packet-filter inbound ip-group 3000 rule 13 packet-filter inbound ip-group 3000 rule 14 packet-filter inbound ip-group 3000 rule 15 packet-filter inbound ip-group 3000 rule 16 packet-filter inbound ip-group 3000 rule 17 packet-filter inbound ip-group 3000 rule 18 packet-filter inbound ip-group 3000 rule 19 packet-filter inbound ip-group 3000 rule 20 #interface Ethernet0/2port access vlan 200packet-filter inbound ip-group 3000 rule 0 packet-filter inbound ip-group 3000 rule 1 packet-filter inbound ip-group 3000 rule 2 packet-filter inbound ip-group 3000 rule 3 packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5 packet-filter inbound ip-group 3000 rule 6 packet-filter inbound ip-group 3000 rule 7 packet-filter inbound ip-group 3000 rule 8 packet-filter inbound ip-group 3000 rule 9 packet-filter inbound ip-group 3000 rule 11 packet-filter inbound ip-group 3000 rule 12 packet-filter inbound ip-group 3000 rule 13 packet-filter inbound ip-group 3000 rule 14 packet-filter inbound ip-group 3000 rule 15 packet-filter inbound ip-group 3000 rule 16 packet-filter inbound ip-group 3000 rule 17 packet-filter inbound ip-group 3000 rule 18 packet-filter inbound ip-group 3000 rule 19 packet-filter inbound ip-group 3000 rule 20 #interface Ethernet0/3port access vlan 200packet-filter inbound ip-group 3000 rule 0 packet-filter inbound ip-group 3000 rule 1 packet-filter inbound ip-group 3000 rule 2 packet-filter inbound ip-group 3000 rule 3 packet-filter inbound ip-group 3000 rule 4 packet-filter inbound ip-group 3000 rule 5 packet-filter inbound ip-group 3000 rule 6 packet-filter inbound ip-group 3000 rule 7 packet-filter inbound ip-group 3000 rule 8 packet-filter inbound ip-group 3000 rule 9 packet-filter inbound ip-group 3000 rule 11 packet-filter inbound ip-group 3000 rule 12 packet-filter inbound ip-group 3000 rule 13 packet-filter inbound ip-group 3000 rule 14 packet-filter inbound ip-group 3000 rule 15 packet-filter inbound ip-group 3000 rule 16 packet-filter inbound ip-group 3000 rule 17 packet-filter inbound ip-group 3000 rule 18 packet-filter inbound ip-group 3000 rule 19 packet-filter inbound ip-group 3000 rule 20 #interface Ethernet0/4port access vlan 200packet-filter inbound ip-group 3000 rule 0 packet-filter inbound ip-group 3000 rule 1 packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3 packet-filter inbound ip-group 3000 rule 4 packet-filter inbound ip-group 3000 rule 5 packet-filter inbound ip-group 3000 rule 6 packet-filter inbound ip-group 3000 rule 7 packet-filter inbound ip-group 3000 rule 8 packet-filter inbound ip-group 3000 rule 9 packet-filter inbound ip-group 3000 rule 11 packet-filter inbound ip-group 3000 rule 12 packet-filter inbound ip-group 3000 rule 13 packet-filter inbound ip-group 3000 rule 14 packet-filter inbound ip-group 3000 rule 15 packet-filter inbound ip-group 3000 rule 16 packet-filter inbound ip-group 3000 rule 17 packet-filter inbound ip-group 3000 rule 18 packet-filter inbound ip-group 3000 rule 19 packet-filter inbound ip-group 3000 rule 20 #interface Ethernet0/5port access vlan 200packet-filter inbound ip-group 3000 rule 0 packet-filter inbound ip-group 3000 rule 1 packet-filter inbound ip-group 3000 rule 2 packet-filter inbound ip-group 3000 rule 3 packet-filter inbound ip-group 3000 rule 4 packet-filter inbound ip-group 3000 rule 5 packet-filter inbound ip-group 3000 rule 6 packet-filter inbound ip-group 3000 rule 7 packet-filter inbound ip-group 3000 rule 8 packet-filter inbound ip-group 3000 rule 9 packet-filter inbound ip-group 3000 rule 11 packet-filter inbound ip-group 3000 rule 12 packet-filter inbound ip-group 3000 rule 13 packet-filter inbound ip-group 3000 rule 14 packet-filter inbound ip-group 3000 rule 15 packet-filter inbound ip-group 3000 rule 16 packet-filter inbound ip-group 3000 rule 17 packet-filter inbound ip-group 3000 rule 18 packet-filter inbound ip-group 3000 rule 19 packet-filter inbound ip-group 3000 rule 20 #interface Ethernet0/6port access vlan 200packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1 packet-filter inbound ip-group 3000 rule 2 packet-filter inbound ip-group 3000 rule 3 packet-filter inbound ip-group 3000 rule 4 packet-filter inbound ip-group 3000 rule 5 packet-filter inbound ip-group 3000 rule 6 packet-filter inbound ip-group 3000 rule 7 packet-filter inbound ip-group 3000 rule 8 packet-filter inbound ip-group 3000 rule 9 packet-filter inbound ip-group 3000 rule 11 packet-filter inbound ip-group 3000 rule 12 packet-filter inbound ip-group 3000 rule 13 packet-filter inbound ip-group 3000 rule 14 packet-filter inbound ip-group 3000 rule 15 packet-filter inbound ip-group 3000 rule 16 packet-filter inbound ip-group 3000 rule 17 packet-filter inbound ip-group 3000 rule 18 packet-filter inbound ip-group 3000 rule 19 packet-filter inbound ip-group 3000 rule 20 #interface Ethernet0/7port access vlan 300packet-filter inbound ip-group 3000 rule 0 packet-filter inbound ip-group 3000 rule 1 packet-filter inbound ip-group 3000 rule 2 packet-filter inbound ip-group 3000 rule 3 packet-filter inbound ip-group 3000 rule 4 packet-filter inbound ip-group 3000 rule 5 packet-filter inbound ip-group 3000 rule 6 packet-filter inbound ip-group 3000 rule 7 packet-filter inbound ip-group 3000 rule 8 packet-filter inbound ip-group 3000 rule 9 packet-filter inbound ip-group 3000 rule 11 packet-filter inbound ip-group 3000 rule 12 packet-filter inbound ip-group 3000 rule 13 packet-filter inbound ip-group 3000 rule 14 packet-filter inbound ip-group 3000 rule 15 packet-filter inbound ip-group 3000 rule 16 packet-filter inbound ip-group 3000 rule 17 packet-filter inbound ip-group 3000 rule 18 packet-filter inbound ip-group 3000 rule 19 packet-filter inbound ip-group 3000 rule 20 #interface Ethernet0/8port access vlan 1100packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/9port access vlan 500packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/10port access vlan 600packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/11port access vlan 700packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/12port access vlan 800packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/13port access vlan 900packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/14port access vlan 1000packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/15port access vlan 1000packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/16port access vlan 1000packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/17port access vlan 1000packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/18port access vlan 1000packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/19port access vlan 1000packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/20port access vlan 1000packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/21port access vlan 1000packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/22packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/23packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14packet-filter inbound ip-group 3000 rule 15packet-filter inbound ip-group 3000 rule 16packet-filter inbound ip-group 3000 rule 17packet-filter inbound ip-group 3000 rule 18packet-filter inbound ip-group 3000 rule 19packet-filter inbound ip-group 3000 rule 20traffic-redirect inbound ip-group 2000 rule 0 next-hop 192.168.0.1 #interface Ethernet0/24packet-filter inbound ip-group 3000 rule 0packet-filter inbound ip-group 3000 rule 1packet-filter inbound ip-group 3000 rule 2packet-filter inbound ip-group 3000 rule 3packet-filter inbound ip-group 3000 rule 4packet-filter inbound ip-group 3000 rule 5packet-filter inbound ip-group 3000 rule 6packet-filter inbound ip-group 3000 rule 7packet-filter inbound ip-group 3000 rule 8packet-filter inbound ip-group 3000 rule 9packet-filter inbound ip-group 3000 rule 11packet-filter inbound ip-group 3000 rule 12packet-filter inbound ip-group 3000 rule 13packet-filter inbound ip-group 3000 rule 14。
Cisco PIX防火墙的基本配置

Cisco PIX防火墙的基本配置1. 同样是用一条串行电缆从电脑的COM口连到Cisco PIX 525防火墙的console口;2. 开启所连电脑和防火墙的电源,进入Windows系统自带的"终端",通讯参数可按系统默然。
进入防火墙初始化配置,在其中主要设置有:Date(日期)、time(时间)、hostname(主机名称)、inside ip address(内部网卡IP地址)、domain(主域)等,完成后也就建立了一个初始化设置了。
此时的提示符为:pix255>。
3. 输入enable命令,进入Pix 525特权用户模式,默然密码为空。
如果要修改此特权用户模式密码,则可用enable password命令,命令格式为:enable password password [encrypted],这个密码必须大于16位。
Encrypted选项是确定所加密码是否需要加密。
4、定义以太端口:先必须用enable命令进入特权用户模式,然后输入configure terminal(可简称为config t),进入全局配置模式模式。
具体配置pix525>enablePassword:pix525#config tpix525 (config)#interface ethernet0 autopix525 (config)#interface ethernet1 auto在默然情况下ethernet0是属外部网卡outside, ethernet1是属内部网卡inside, inside在初始化配置成功的情况下已经被激活生效了,但是outside必须命令配置激活。
5. clock配置时钟,这也非常重要,这主要是为防火墙的日志记录而资金积累的,如果日志记录时间和日期都不准确,也就无法正确分析记录中的信息。
这须在全局配置模式下进行。
时钟设置命令格式有两种,主要是日期格式不同,分别为:clock set hh:mm:ss month day month year和clock set hh:mm:ss day month year前一种格式为:小时:分钟:秒月日年;而后一种格式为:小时:分钟:秒日月年,主要在日、月份的前后顺序不同。
思科防火墙个人总结

防火墙硬件防火墙,是网络间的墙,防止非法侵入,过滤信息等,从结构上讲,简单的说是一种PC式的电脑主机加上闪存和防火墙操作系统。
所有从外部到内部或内部到外部的通信都必须经过它;只有有内部访问策略授权的通信才能被允许通过;系统本身具有很强的高可靠性;防火墙技术:包过滤技术(访问控制列表);状态检测我第一次亲手配置的是防火墙Cisco firewall pix 525.下面是一般用到的最基本配置1.建立用户、设置密码跟Cisco IOS路由器基本一样。
2.激活以太端口、命名端口与安全级别、配置以太网端口IP地址及静态路由,配置telnetPIX525(config)#interface ethernet0PIX525(config-if)#nameif outsidePIX525(config-if)#security-level 0PIX525(config-if)#ip address 221.12.59.243 255.255.255.128PIX525(config-if)#no shutPIX525(config)#ip address outside 221.12.59.243 255.255.255.128PIX525(config)#route outside 0.0.0.0 0.0.0.0 221.12.59.241 1PIX525(config)#telnet 172.18.32.0 255.255.224.0 insideXG-PIX-525# show nameifnameif ethernet0 outside security0nameif ethernet1 inside security100nameif gb-ethernet0 dmz security20nameif gb-ethernet1 inside1 security80XG-PIX-525# show routeoutside 0.0.0.0 0.0.0.0 221.12.59.241 1 OTHER staticinside1 172.16.0.0 255.240.0.0 172.18.254.134 1 OTHER staticinside1 172.18.254.132 255.255.255.252 172.18.254.133 1 CONNECT static dmz 192.168.254.0 255.255.255.0 192.168.254.1 1 CONNECT static outside 221.12.59.240 255.255.255.248 221.12.59.243 1 CONNECT static XG-PIX-525# show ipSystem IP Addresses:ip address outside 221.12.59.243 255.255.255.248no ip address insideip address dmz 192.168.254.1 255.255.255.0ip address inside1 172.18.254.133 255.255.255.252Current IP Addresses:ip address outside 221.12.59.243 255.255.255.248no ip address insideip address dmz 192.168.254.1 255.255.255.0ip address inside1 172.18.254.133 255.255.255.252XG-PIX-525# show telnet192.168.254.0 255.255.255.0 dmz172.18.240.0 255.255.240.0 inside1172.18.32.0 255.255.224.0 inside12.访问列表此功能与cisco IOS基本上是相似的,有permit和deny两个功能,网络协议一般有IP、TCP、UDP、ICMP、SSH等等,如:PIX525(config)#access-list 110 permit icmp any anyPIX525(config)#access-list 110 permit tcp any host 221.12.59.244 eq www PIX525(config)#access-list 110 permit tcp any host 221.12.59.243 eq ssh PIX525(config)#access-list 110 permit tcp any host 221.12.59.244 eq ftp PIX525(config)#access-group 100 in interface outside3.global指定公网地址范围:定义地址池Global(if_name) nat_id ip_address-ip-address [netmark global_mask](if_name):表示外网接口名称,一般为outside。
思科PIX防火墙命令大全

思科PIX防火墙命令大全思科PIX防火墙命令大全一、PIX防火墙的认识PIX是Cisco的硬件防火墙,硬件防火墙有工作速度快,使用方便等特点。
PIX有很多型号,并发连接数是PIX防火墙的重要参数。
PIX25是典型的设备。
PIX防火墙常见接口有:console、Failover、Ethernet、USB。
网络区域:内部网络:inside外部网络:outside中间区域:称DMZ(停火区)。
放置对外开放的服务器。
二、防火墙的配置规则没有连接的状态(没有握手或握手不成功或非法的数据包),任何数据包无法穿过防火墙。
(内部发起的连接可以回包。
通过ACL开放的服务器允许外部发起连接)inside可以访问任何outside和dmz区域。
dmz可以访问outside区域。
inside访问dmz需要配合static(静态地址转换)。
outside访问dmz需要配合acl(访问控制列表)。
三、PIX防火墙的配置模式PIX防火墙的配置模式与路由器类似,有4种管理模式:PIXfirewall>:用户模式PIXfirewall#:特权模式PIXfirewall(config)#:配置模式monitor>:ROM监视模式,开机按住[Esc]键或发送一个“Break”字符,进入监视模式。
四、PIX基本配置命令常用命令有:nameif、interface、ipaddress、nat、global、route、static等。
1、nameif设置接口名称,并指定安全级别,安全级别取值范围为1~100,数字越大安全级别越高。
例如要求设置:ethernet0命名为外部接口outside,安全级别是0。
ethernet1命名为内部接口inside,安全级别是100。
ethernet2命名为中间接口dmz,安装级别为50。
使用命令:PIX525(config)#nameif ethernet0 outside security0PIX525(config)#nameif ethernet1 inside security100PIX525(config)#nameif ethernet2 dmz security502、interface配置以太口工作状态,常见状态有:auto、100full、shutdown。
PIX525防火墙操作手册

Cisco PIX525操作手册2006年10月第一章、Cisco PIX硬件安装1.1. 打开封箱,将Cisco PIX 525取出,观察外观是否有损坏,前后面如图:1.2.添加网卡,打开机箱,插入网卡,如下图:1.3.机箱上机架,在机箱两边用螺丝将固定条固定(机箱内有固定条和螺丝),然后固定在机架上。
1.4. 连接网线、Console配置线和电源,如图:1.5. 通过超级终端开始配置Cisco PIX 525,启动Cisco PIX 525 直到屏幕显示如下信息-----------------------------------------------------------------------|| |||| |||||| ||||..:||||||:..:||||||:..c i s c o S y s t e m sPrivate Internet eXchange-----------------------------------------------------------------------Cisco Secure PIX FirewallCisco Secure PIX Firewall Version 6.2(1)Licensed Features:Failover: EnabledVPN-DES: EnabledVPN-3DES: DisabledMaximum Interfaces: 6If an encryption circuit board is present, the following export statement appears:****************************** Warning *******************************An encryption device has been discovered.This product is not authorized for use by persons located outside theUnited States and Canada that do not have export license authorityfrom Cisco Systems, Inc. and/or the U.S. Government.This product may not be exported outside the U.S. and Canada either byphysical or electronic means without the prior written approval ofCisco Systems, Inc. and/or the U.S. Government.Persons outside the U.S. and Canada may not reexport, resell, ortransfer this product by either physical or electronic means withoutprior written approval of Cisco Systems, Inc. and/or U.S. Government.******************************* Warning ******************************* If you have an activation key that supports encryption, the following statement appears:****************************** Warning ******************************* Compliance with U.S. Export Laws and Regulations - Encryption.This product performs encryption and is regulated for exportby the U.S. Government.This product is not authorized for use by persons locatedoutside the United States and Canada that do not have priorapproval from Cisco Systems, Inc. or the U.S. Government.This product may not be exported outside the U.S. and Canadaeither by physical or electronic means without PRIOR approvalof Cisco Systems, Inc. or the U.S. Government.Persons outside the U.S. and Canada may not re-export, resellor transfer this product by either physical or electronic meanswithout prior approval of Cisco Systems, Inc. or the U.S.Government.******************************* Warning ******************************* PIX Firewall then displays the following messages:The 'logging trap' command now sets only the syslog server logging level.Use the 'logging history' command to set the SNMP logging level.Cryptochecksum(unchanged): 29bd47de e4c13958 db57ee04 282ae9deCopyright (c) 1998-2002 by Cisco Systems, Inc.Restricted Rights LegendUse, duplication, or disclosure by the Government issubject to restrictions as set forth in subparagraph(c) of the Commercial Computer Software - RestrictedRights clause at FAR sec. 52.227-19 and subparagraph(c) (1) (ii) of the Rights in Technical Data and ComputerSoftware clause at DFARS sec. 252.227-7013.Cisco Systems, Inc.170 West Tasman DriveSan Jose, California 95134-1706第二章、CiscoPIX配置2.1 . CISCO PIX常规操作启动CiscoPIX后,连接上控制台终端连接到PIX上。
实验8-Cisco防火墙pix525配置实例

实验8 Cisco防火墙pix525配置实例一、引言硬件防火墙的应用,现在是越来越多,产品也很丰富。
一般国产的防火墙多带有中文的说明和一些相应的配置实例,但国外的产品几乎都没有中文的说明书。
二、物理连接Pix525的外观:是一种标准的机架式设备,高度为2U,电源开关和接线在背后。
正面有一些指示灯,如电源、工作是否正常的表示等;背面板有一些接口和扩展口,我们这次要用到的接口有三个:两个以太(RJ-45网卡)和一个配置口,其英文分别是:ETHERNET0、ETHERNET1和CONSOLE.先将防火墙固定在机架上,接好电源;用随机带来的一根蓝色的线缆将防火墙与笔记本连接起来。
注意:该线缆是扁平的,一端是RJ-45接口,要接在防火墙的console端口;另一端是串口,要接到笔记本的串口上。
三、初始化配置程序启动笔记本,防火墙通电。
1.新建一个超级终端运行windows里的超级终端程序。
其步骤如下:单击开始→所有程序→附件→通讯→超级终端,就会出现对话框:此时需要输入一个所建超级终端的名称,可输PIX515 ↙;出现下一对话框:需要选择串口的端口,我们选择com1↙;出现下一对话框:需要选择传输速率,我们选择9600↙.2.基本配置此时,出现超级终端对话框,按↙对应提示填写:Password(口令):自定。
↙Year(年):[2004] ↙Moth(月):[Feb] ↙Day(天):[20] ↙Time(时间):[10:21:30] ↙Inside IP address(内部IP地址) :192.168.10.0↙Inside network mask(内部掩码):255.255.255.0↙Host name(主机名称):FIX525↙Domain name(主域):↙随后出现以上设置的总结,提示是否保存。
选择YES,存入到flash四、具体配置在配置之前,需要了解一些具体的需求。
在本实例中,该单位是通过防火墙接入到Internet,防火墙要有路由的功能;net1接外网,net0接内网。
Cisco PIX525防火墙的开通设置

用s t a t i c 命令将需要被外 网访 问的内部主机 的I P 映射为一 个静态全局I P 地址。
f s t a t i c [ ( i n t e r n a li
—
n a me , e xt e r n al i f
—
—
~
n a m e ) ]
g l o bn t e r f a c e 命令 : a c c e s s — g r o u p I D i n i n t e r f a c e l o wi
_
l o w
_
i n t e r f a c e : 具有较低优先级的外部接 口
6 设置内部对外网的访问
使用g l o b a l 和n a t 命令可 以设 置将 部分或全 部内部主机翻
网掩码 。
M a x
—
2 . 2设置特权模式口令
e n a b l e p a s s w o r d [ p a S s w o r d ] [ 1 e v e l 1 e v e 1 ] [ e n c r y p t e d ]
c o n n s : 所允许 的并发的最 大连接数。
[ s h u t d o w n ]
h ar d wa r e
—
—
i f n a m e : 要做N A T 的网段所 连接的防火墙接口名称
n a t i d : 为此N A T 定义一个标识
l o c a l
d d r e s s s u b n e t ma s k i ns i d e t e l n e t i pa
— —
— —
i p : 外部 网分配的全局地 址, 不能是P A T 地址。
防火墙实施策略--最高级防火墙
最高级防火墙(思科pix525防火墙)配置命令:PIX525有三个以太接口,分别接入内网,外网和中间区域。
设置:(pix515只有两个口而且固定的优先级)ePix525#conf tPix525(config)#nameif ethernet0 inside security100Pix525(config)#nameif ethernet1 dmz security50Pix525(config)#nameif ethernet2 outside security0设置接口工作方式:Pix525(config)#interface ethernet0 autoPix525(config)#interface ethernet1 autoPix525(config)#interface ethernet2 auto设置接口IP地址:Pix525(config)#ip address outside 10.1.1.1 255.255.255.240Pix525(config)#ip address inside 172.16.1.2 255.255.255.0Pix525(config)#ip address dmz 172.16.6.1 255.255.255.0设置时间:clock set 9:0:0 1 5 2010-5-21指定接口的安全级别:pix525(config)#nameif ethernet0 outside security0 # outside是指pix525(config)#nameif ethernet0 dmz security50 # outside是指外部接口外部接口pix525(config)#nameif ethernet1 inside security100 # inside是指内部接口路由:route inside 172.16.0.0 255.255.0.0 172.16.1.2 1route outside 10.1.0.0 255.255.0.0 10.1.1.1NAT地址转换:将三部门网络地址分别划成一组,并转换成外部地址nat (inside) 1 172.16.3.0 255.255.255.0nat (inside) 2 172.16.4.0 255.255.255.0nat (inside) 3 172.16.4.0 255.255.255.0global (outside) 1 10.1.1.1-10.1.1.41netmask 255.255.255.0global (outside) 2 10.1.1.5-10.1.1.8 netmask 255.255.255.0global (outside) 3 10.1.1.9-10.1.1.12 netmask 255.255.255.0设置内(telnet)外部(ssh)用户登录本地服务器或设备命令:telnet 172.16.13.110 255.255.255.0 insidepassword adminenable password adminssh 130.12.1.0 255.255.255.0 outsideusername miaosen password miaosenaaa authernacation ssh local /使用本地认证认证:config#ca zeroiseconfig#ca generateconfig#ca save包过滤型防火墙的访问控制表(ACL)配置其他部分访问财务部门策略:禁止www,ftp,smtp允许管理主机访问财务access-list 100 deny tcp 172.16.4.0 255.255.255.0 172.16.3.0255.255.255.0 eq ftpaccess-list 100 deny tcp 172.16.4.0 255.255.255.0 172.16.3.0 255.255.255.0 eq wwwaccess-list 100 deny tcp 172.16.4.0 255.255.255.0 172.16.3.0255.255.255.0 eq smtpaccess-list 100 deny tcp 172.16.5.0 255.255.255.0 172.16.3.0255.255.255.0 eq ftpaccess-list 100 denny tcp 172.16.5.0 255.255.255.0 172.16.3.0 255.255.255.0 eq wwwaccess-list 100 deny tcp 172.16.5.0 255.255.255.0 172.16.3.0255.255.255.0 eq smtpaccess-list 100 permit tcp 172.16.0.0//255.255.0.0 172.16.6.0 255.255.255.0 eq smtpaccess-list 100 permit tcp 172.16.0.0//255.255.0.0 172.16.6.0 255.255.255.0 eq wwwaccess-list 100 permit tcp 172.16.0.0//255.255.0.0 172.16.6.0 255.255.255.0 eq icmpaccess-list 100 permit tcp 172.16.3.5 any 255.255.255.0access-list 100 permit tcp 172.16.13.110 172.16.3.0 255.255.255.0access-list 100 permit tcp 172.16.3.5 any 255.255.255.0地址映射:static (inside, outside) 172.16.3.5 10.1.1.1 /重要的财务主机命令主机端口重定向:PIX525(config)#static (inside,outside) tcp172.16.6.0 255.255.255.0telnet 172.16.1.2telnet netmask 255.255.255.255 0 0PIX525(config)#static (inside,outside) ftp 172.16.6.0 255.255.255.0telnet 172.16.1.2 ftp netmask 255.255.255.255 0 0PIX525(config)#static (inside,outside) tcp172.16.6.0 255.255.255.0 www 172.16.1.2 www netmask 255.255.255.255 0 0/到服务器的端口转换配置允许低级向高级的数据流(config)#conduit deny tcp host 172.16.4.0 255.255.255.0 eq www any/办公部不可上网上面已经设置可访问服务器Pix525(config)#conduit permit tcp host 172.16.3.1 eq www any/财务的一台主机可上网Pix525(config)#conduit permit icmp any any/允许内外部的ICMP消息传送配置fixup协议Fixup protocol ftp 21Fixup protocol http 80fixup protocol h323 1720fixup protocol rsh 514fixup protocol smtp 25使能化攻击:执行命令firewall defend ip-spoofing enable,使能IP欺骗攻击防范功能。
PIX配置大全

PIX配置⼤全在配置PIX防⽕墙之前,先来介绍⼀下防⽕墙的物理特性。
防⽕墙通常具有⾄少3个接⼝,但许多早期的防⽕墙只具有2个接⼝;当使⽤具有3个接⼝的防⽕墙时,就⾄少产⽣了3个⽹络,描述如下:内部区域(内⽹):内部区域通常就是指企业内部⽹络或者是企业内部⽹络的⼀部分。
它是互连⽹络的信任区域,即受到了防⽕墙的保护。
外部区域(外⽹):外部区域通常指Internet或者⾮企业内部⽹络。
它是互连⽹络中不被信任的区域,当外部区域想要访问内部区域的主机和服务,通过防⽕墙,就可以实现有限制的访问。
停⽕区(DMZ):停⽕区是⼀个隔离的⽹络,或⼏个⽹络。
位于停⽕区中的主机或服务器被称为堡垒主机。
⼀般在停⽕区内可以放置Web服务器,Mail服务器等。
停⽕区对于外部⽤户通常是可以访问的,这种⽅式让外部⽤户可以访问企业的公开信息,但却不允许他们访问企业内部⽹络。
注意:2个接⼝的防⽕墙是没有停⽕区的。
由于PIX535在企业级别不具有普遍性,因此下⾯主要说明PIX525在企业⽹络中的应⽤。
PIX防⽕墙提供4种管理访问模式:⾮特权模式。
PIX防⽕墙开机⾃检后,就是处于这种模式。
系统显⽰为pixfirewall>特权模式。
输⼊enable进⼊特权模式,可以改变当前配置。
显⽰为pixfirewall#配置模式。
输⼊configure terminal进⼊此模式,绝⼤部分的系统配置都在这⾥进⾏。
显⽰为pixfirewall(config)#监视模式。
PIX防⽕墙在开机或重启过程中,按住Escape键或发送⼀个"Break"字符,进⼊监视模式。
这⾥可以更新*作系统映象和⼝令恢复。
显⽰为monitor>配置PIX防⽕墙有6个基本命令:nameif,interface,ip address,nat,global,route.这些命令在配置PIX时是必须的。
以下是配置的基本步骤:1. 配置防⽕墙接⼝的名字,并指定安全级别(nameif)。
PIX防火墙安全测评指导书

access-list115denytcpanyanyeq135access-list115denyudpanyanyeq135
b)提供访问控制能力;
检查:登录到防火墙上,查看相关访问控制策略,分析其可用性和有效性。
防火墙配置了合理的访问控制策略。
c)内容过滤;
检查:
在showrunning输出配置中检查对HTTP、FTP、TELNET、SMTP、POP3
检查:查看网络拓扑结构,判断是否采用了冗余技术设计网络拓扑结构。
拓扑结构冗余。
d)提供硬件冗余。
检查:查看防火墙是否有硬件冗余来保证系统的高可用性。
设备硬件冗余。
存在类似如下配置:
nat (inside) 10.0.0.050 0
f)重要网段防止地址欺骗;
检查:
输入命令showrunning-config
检查配置文件中是否存在以下类似配置项:
arpinsidex.x.x.xxxxx.xxxx.xxxx
存在类似如下配置:
arpinsidex.x.x.xxxxx.xxxx.xxxx
检查:输入命令showrunning
检查配置文件中是否存在类似如下配置项:
logginghostx.x.x.x
有专门的日志服务器存放日志,对这台服务器的访问需经过授权。
2
访问控制
(G3)
a)启用访问控制功能;
检查:检查网络拓扑结构和防火墙配置,查看是否在防火墙上启用
了访问控制功能。
输入命令showrunning-config检查配置文件中是否存在以下类似配置项:access-list115denytcpanyanyeq135access-list115denyudpanyanyeq135
思科防火墙设置

增加一台服务器具体要求。
新增一台服务器地址:10.165.127.15/255.255.255.128。
需要nat 转换成公网地址16.152.91.223 映射出去,并对外开通这台服务器的80端口。
在对外pix525上面增加如下:access-list acl_out permit tcp any host 16.52.91.223 eq www //开放外网对新服务器80端口static (inside,outside) 16.152.91.223 10.165.127.15 netmask 255.255.255.255 0 0 ////外高桥新服务器地址转换16.152.91.223可是为什么转换后,不能访问16.52.91.223的网页,但确可以ping通16.52.91.223,但是访问10.165.127.15的主页是正常的??具体配置如下:pix-525> enablePassword: *****pix-525# sh run: Saved:PIX Version 6.3(5)interface ethernet0 100fullinterface ethernet1 100fullnameif ethernet0 outside security0nameif ethernet1 inside security100enable password FVHQD7n.FuCW78fS level 7 encryptedenable password 2KFQnbNIdI.2KYOU encryptedpasswd 2KFQnbNIdI.2KYOU encryptedhostname wgqpix-525fixup protocol dns maximum-length 512fixup protocol ftp 21fixup protocol h323 h225 1720fixup protocol h323 ras 1718-1719fixup protocol http 80fixup protocol rsh 514fixup protocol rtsp 554fixup protocol sip 5060fixup protocol sip udp 5060fixup protocol skinny 2000fixup protocol smtp 25fixup protocol sqlnet 1521fixup protocol tftp 69namesaccess-list acl_out permit tcp any host 16.152.91.221 eq wwwaccess-list acl_out permit icmp any anyaccess-list acl_out permit tcp any host 16.152.91.220 eq httpsaccess-list acl_out permit tcp any host 16.152.91.223 eq wwwaccess-list outbound permit icmp any anyaccess-list outbound permit ip any anypager lines 24mtu outside 1500mtu inside 1500ip address outside 16.152.91.222 255.255.255.128ip address inside 10.165.127.254 255.255.255.252ip audit info action alarmip audit attack action alarmno failoverfailover timeout 0:00:00failover poll 15no failover ip address outsideno failover ip address insideno pdm history enablearp timeout 14400static (inside,outside) 16.152.91.221 10.165.127.11 netmask 255.255.255.255 0 0 static (inside,outside) 16.152.91.220 10.165.127.23 netmask 255.255.255.255 0 0 static (inside,outside) 16.152.91.223 10.165.127.15 netmask 255.255.255.255 0 0 access-group acl_out in interface outsideaccess-group outbound in interface insideroute outside 0.0.0.0 0.0.0.0 16.152.91.129 1route inside 10.165.0.0 255.255.0.0 10.165.127.253 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h225 1:00:00 timeout h323 0:05:00 mgcp 0:05:00 sip 0:30:00 sip_media 0:02:00timeout sip-disconnect 0:02:00 sip-invite 0:03:00timeout uauth 0:05:00 absoluteaaa-server TACACS+ protocol tacacs+aaa-server TACACS+ max-failed-attempts 3aaa-server TACACS+ deadtime 10aaa-server RADIUS protocol radiusaaa-server RADIUS max-failed-attempts 3aaa-server RADIUS deadtime 10aaa-server LOCAL protocol localhttp server enableno snmp-server locationno snmp-server contactsnmp-server community publicno snmp-server enable trapsfloodguard enabletelnet 10.165.6.225 255.255.255.255 insidetelnet 10.165.127.12 255.255.255.255 insidetelnet 10.165.127.250 255.255.255.255 insidetelnet 10.165.6.15 255.255.255.255 insidetelnet 10.165.6.16 255.255.255.255 insidetelnet timeout 5ssh timeout 5console timeout 0username admin password iuQeTKNaNbruxBKd encrypted privilege 2terminal width 80Cryptochecksum:b2e1195d144f48f01fe66606cd31d0f2: endwgqpix-525#最佳答案( 回答者: xintao800 )PIX防火墙提供4种管理访问模式:²非特权模式。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
经典的防火墙配置
环境如图:
设:
ethernet0命名为外部接口outside,安全级别是0。
ethernet1被命名为内部接口inside,安全级别100。
ethernet2被命名为中间接口dmz,安全级别50。
参考配置:
PIX525#conf t ;进入配置模式PIX525(config)#nameif ethernet0 outside security0 ;设置定全级0
PIX525(config)#nameif ethernet1 inside security100 ;设置定全级100
PIX525(config)#nameif ethernet2 dmz security50 ;设置定全级50 PIX525(config)#interface ethernet0 auto ;设置自动方式
PIX525(config)#interface ethernet1 100full ;设置全双工方式PIX525(config)#interface ethernet2 100full ;设置全双工方式PIX525(config)#ip address outside 133.0.0.1 255.255.255.252 ;设置接口IP
PIX525(config)#ip address inside 10.66.1.200 255.255.0.0 ;设置接口IP
PIX525(config)#ip address dmz 10.65.1.200 255.255.0.0 ;设置接口IP
PIX525(config)#global (outside) 1 133.1.0.1-133.1.0.14 ;定义的地址池
PIX525(config)#nat (inside) 1 0 0 ;0 0表示所有
PIX525(config)#route outside 0 0 133.0.0.2 ;设置默认路由
PIX525(config)#static (dmz,outside) 133.1.0.1 10.65.1.101 ;静态NAT
PIX525(config)#static (dmz,outside) 133.1.0.2 10.65.1.102 ;静态NAT
PIX525(config)#static (inside,dmz) 10.66.1.200 10.66.1.200 ;静态NAT
PIX525(config)#access-list 101 permit ip any host 133.1.0.1 eq www;设置ACL
PIX525(config)#access-list 101 permit ip any host 133.1.0.2 eq ftp;设置ACL
PIX525(config)#access-list 101 deny ip any any ;设置ACL
PIX525(config)#access-group 101 in interface outside ;将ACL应用在outside端口
当内部主机访问外部主机时,通过nat转换成公网IP,访问internet。
当内部主机访问中间区域dmz时,将自己映射成自己访问服务器,否则内部主机将会映射成地址池的IP,到外部去找。
当外部主机访问中间区域dmz时,对133.0.0.1映射成10.65.1.101,static是双向的。
PIX的所有端口默认是关闭的,进入PIX要经过acl入口过滤。
静态路由指示内部的主机和dmz的数据包从outside口出去。
